Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 4. Using AMQ Management Console
AMQ Management Console is a web console included in the AMQ Broker installation that enables you to use a web browser to manage AMQ Broker.
AMQ Management Console is based on hawtio.
4.1. Overview
AMQ Broker is a full-featured, message-oriented middleware broker. It offers specialized queueing behaviors, message persistence, and manageability. It supports multiple protocols and client languages, freeing you to use many of your application assets.
AMQ Broker’s key features allow you to:
monitor your AMQ brokers and clients
- view the topology
- view network health at a glance
manage AMQ brokers using:
- AMQ Management Console
- Command-line Interface (CLI)
- Management API
The supported web browsers for AMQ Management Console are Firefox and Chrome. For more information on supported browser versions, see AMQ 7 Supported Configurations.
4.2. Configuring local and remote access to AMQ Management Console
The procedure in this section shows how to configure local and remote access to AMQ Management Console.
Remote access to the console can take one of two forms:
- Within a console session on a local broker, you use the Connect tab to connect to another, remote broker
- From a remote host, you connect to the console for the local broker, using an externally-reachable IP address for the local broker
Prerequisites
-
You must upgrade to at least AMQ Broker 7.1.0. As part of this upgrade, an access-management configuration file named
jolokia-access.xmlis added to the broker instance. For more information about upgrading, see Upgrading a Broker instance from 7.0.x to 7.1.0.
Procedure
-
Open the
<broker_instance_dir>/etc/bootstrap.xmlfile. Within the
webelement, observe that the web port is bound only tolocalhostby default.Copy to Clipboard Copied! Toggle word wrap Toggle overflow To enable connection to the console for the local broker from a remote host, change the web port binding to a network-reachable interface. For example:
<web bind="http://0.0.0.0:8161" path="web">
<web bind="http://0.0.0.0:8161" path="web">Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the preceding example, by specifying
0.0.0.0, you bind the web port to all interfaces on the local broker.-
Save the
bootstrap.xmlfile. -
Open the
<broker_instance_dir>/etc/jolokia-access.xmlfile. Within the
<cors>(that is, Cross-Origin Resource Sharing) element, add anallow-originentry for each HTTP origin request header that you want to allow to access the console. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the preceding configuration, you specify that the following connections are allowed:
Connection from the local host (that is, the host machine for your local broker instance) to the console.
-
The first asterisk (
*) wildcard character allows either thehttporhttpsscheme to be specified in the connection request, based on whether you have configured the console for secure connections. - The second asterisk wildcard character allows any port on the host machine to be used for the connection.
-
The first asterisk (
-
Connection from a remote host to the console for the local broker, using the externally-reachable IP address of the local broker. In this case, the externally-reachable IP address of the local broker is
192.168.0.49. -
Connection from within a console session opened on another, remote broker to the local broker. In this case, the IP address of the remote broker is
192.168.0.51.
-
Save the
jolokia-access.xmlfile. -
Open the
<broker_instance_dir>/etc/artemis.profilefile. To enable the Connect tab in the console, set the value of the
Dhawtio.disableProxyargument tofalse.-Dhawtio.disableProxy=false
-Dhawtio.disableProxy=falseCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIt is recommended that you enable remote connections from the console (that is, set the value of the
Dhawtio.disableProxyargument tofalse) only if the console is exposed to a secure network.Add a new argument,
Dhawtio.proxyWhitelist, to theJAVA_ARGSlist of Java system arguments. As a comma-separated list, specify IP addresses for any remote brokers that you want to connect to from the local broker (that is, by using the Connect tab within a console session running on the local broker). For example:-Dhawtio.proxyWhitelist=192.168.0.51
-Dhawtio.proxyWhitelist=192.168.0.51Copy to Clipboard Copied! Toggle word wrap Toggle overflow Based on the preceding configuration, you can use the Connect tab within a console session on the local broker to connect to another, remote broker with an IP address of
192.168.0.51.-
Save the
aretmis.profilefile.
Additional resources
- To learn how to access the console, see Section 4.3, “Accessing AMQ Management Console”.
For more information about:
- Cross-Origin Resource Sharing, see W3C Recommendations.
- Jolokia security, see Jolokia Protocols.
- Securing connections to the console, see Section 4.4.3, “Securing network access to AMQ Management Console”.
4.3. Accessing AMQ Management Console
The procedure in this section shows how to:
- Open AMQ Management Console from the local broker
- Connect to other brokers from within a console session on the local broker
- Open a console instance for the local broker from a remote host using the externally-reachable IP address of the local broker
Prerequisites
- You must have already configured local and remote access to the console. For more information, see Section 4.2, “Configuring local and remote access to AMQ Management Console”.
Procedure
In your web browser, navigate to the console address for the local broker.
The console address is
http://<host:port>/console/login. If you are using the default address, navigate to http://localhost:8161/console/login. Otherwise, use the values of host and port that are defined for thebindattribute of thewebelement in the<broker_instance_dir>/etc/bootstrap.xmlconfiguration file.Figure 4.1. Console login page
- Log in to AMQ Management Console using the default user name and password that you created when you created the broker.
To connect to another, remote broker from the console session of the local broker:
- In the left menu, click the Connect tab.
- In the main pane, on the Remote tab, click the Add connection button.
In the Add Connection dialog box, specify the following details:
- Name
-
Name for the remote connection, for example,
my_other_broker. - Scheme
-
Protocol to use for the remote connection. Select
httpfor a non-secured connection, orhttpsfor a secured connection. - Host
- IP address of a remote broker. You must have already configured console access for this remote broker.
- Port
-
Port on the local broker to use for the remote connection. Specify the port value that is defined for the
bindattribute of thewebelement in the<broker_instance_dir>/etc/bootstrap.xmlconfiguration file. The default value is8161. - Path
-
Path to use for console access. Specify
console/jolokia.
To test the connection, click the Test Connection button.
If the connection test is successful, click the Add button. If the connection test fails, review and modify the connection details as needed. Test the connection again.
On the Remote page, for a connection that you have added, click the Connect button.
A new web browser tab opens for the console instance on the remote broker.
In the Log In dialog box, enter the user name and password for the remote broker. Click Log In.
The console instance for the remote broker opens.
To connect to the console for the local broker from a remote host, specify the Jolokia endpoint for the local broker in a web browser. This endpoint includes the externally-reachable IP address that you specified for the local broker when configuring remote console access. For example:
http://192.168.0.49/console/jolokia
http://192.168.0.49/console/jolokiaCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.4. Configuring AMQ Management Console
Configure user access and request access to resources on the broker.
4.4.1. Securing AMQ Management Console using Red Hat Single Sign-On
Prerequisites
- Red Hat Single Sign-On 7.4
Procedure
Configure Red Hat Single Sign-On:
-
Navigate to the realm in Red Hat Single Sign-On that you want to use for securing AMQ Management Console. Each realm in Red Hat Single Sign-On includes a client named
Broker. This client is not related to AMQ. -
Create a new client in Red Hat Single Sign-On, for example
artemis-console. Navigate to the client settings page and set:
Valid Redirect URIs to the AMQ Management Console URL followed by
*, for example:https://broker.example.com:8161/console/*
https://broker.example.com:8161/console/*Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Web Origins to the same value as Valid Redirect URIs. Red Hat Single Sign-On allows you enter
+, indicating that allowed CORS origins includes the value for Valid Redirect URIs.
-
Create a role for the client, for example
guest. - Make sure all users who require access to AMQ Management Console are assigned the above role, for example, using Red Hat Single Sign-On groups.
-
Navigate to the realm in Red Hat Single Sign-On that you want to use for securing AMQ Management Console. Each realm in Red Hat Single Sign-On includes a client named
Configure the AMQ Broker instance:
Add the following to your
<broker-instance-dir>/instances/broker0/etc/login.configfile to configure AMQ Management Console to use Red Hat Single Sign-On:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Adding this configuration sets up a JAAS principal and a requirement for a bearer token from Red Hat Single Sign-On. The connection to Red Hat Single Sign-On is defined in the
keycloak-bearer-token.jsonfile, as described in the next step.Create a file
<broker-instance-dir>/etc/keycloak-bearer-token.jsonwith the following contents to specify the connection to Red Hat Single Sign-On used for the bearer token exchange:Copy to Clipboard Copied! Toggle word wrap Toggle overflow <realm-name>- the name of the realm in Red Hat Single Sign-On
<client-name>- the name of the client in Red Hat Single Sign-On
<RHSSO-URL>- the URL of Red Hat Single Sign-On
Create a file
<broker-instance-dir>/etc/keycloak-js-token.jsonwith the following contents to specify the Red Hat Single Sign-On authentication endpoint:{ "realm": "<realm-name>", "clientId": "<client-name>", "url": "<RHSSO-URL>/auth" }{ "realm": "<realm-name>", "clientId": "<client-name>", "url": "<RHSSO-URL>/auth" }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the security settings by editing the the
<broker-instance-dir>/etc/bootstrap.xmlfile.For example, to allow users with the
amqrole consume messages and allow users with theguestrole send messages, add the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Run the AMQ Broker instance and validate AMQ Management Console configuration.
4.4.2. Setting up user access to AMQ Management Console
You can access AMQ Management Console using the broker login credentials. The following table provides information about different methods to add additional broker users to access AMQ Management Console:
| Authentication Method | Description |
|---|---|
| Guest authentication | Enables anonymous access. In this configuration, any user who connects without credentials or with the wrong credentials will be authenticated automatically and assigned a specific user and role. For more information, see Configuring guest access in Configuring AMQ Broker. |
| Basic user and password authentication | For each user, you must define a username and password and assign a security role. Users can only log into AMQ Management Console using these credentials. For more information, see Configuring basic user and password authentication in Configuring AMQ Broker. |
| LDAP authentication | Users are authenticated and authorized by checking the credentials against user data stored in a central X.500 directory server. For more information, see Configuring LDAP to authenticate clients in Configuring AMQ Broker. |
4.4.3. Securing network access to AMQ Management Console
To secure AMQ Management Console when the console is being accessed over a WAN or the internet, use SSL to specify that network access uses https instead of http.
Prerequisites
The following should be located in the <broker_instance_dir>/etc/ directory:
- Java key store
- Java trust store (needed only if you require client authentication)
Procedure
-
Open the
<broker_instance_dir>/etc/bootstrap.xmlfile. In the
<web>element, add the following attributes:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - bind
-
For secure connections to the console, change the URI scheme to
https. - keyStorePath
Path of the keystore file. For example:
keyStorePath="<broker_instance_dir>/etc/keystore.jks"
keyStorePath="<broker_instance_dir>/etc/keystore.jks"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - keyStorePassword
- Key store password. This password can be encrypted.
- clientAuth
-
Specifies whether client authentication is required. The default value is
false. - trustStorePath
-
Path of the trust store file. You need to define this attribute only if
clientAuthis set totrue. - trustStorePassword
- Trust store password. This password can be encrypted.
Additional resources
-
For more information about encrypting passwords in broker configuration files, including
bootstrap.xml, see Encrypting Passwords in Configuration Files.
4.5. Managing brokers using AMQ Management Console
You can use AMQ Management Console to view information about a running broker and manage the following resources:
- Incoming network connections (acceptors)
- Addresses
- Queues
4.5.1. Viewing details about the broker
To see how the broker is configured, in the left menu, click Artemis. In the folder tree, the local broker is selected by default.
In the main pane, the following tabs are available:
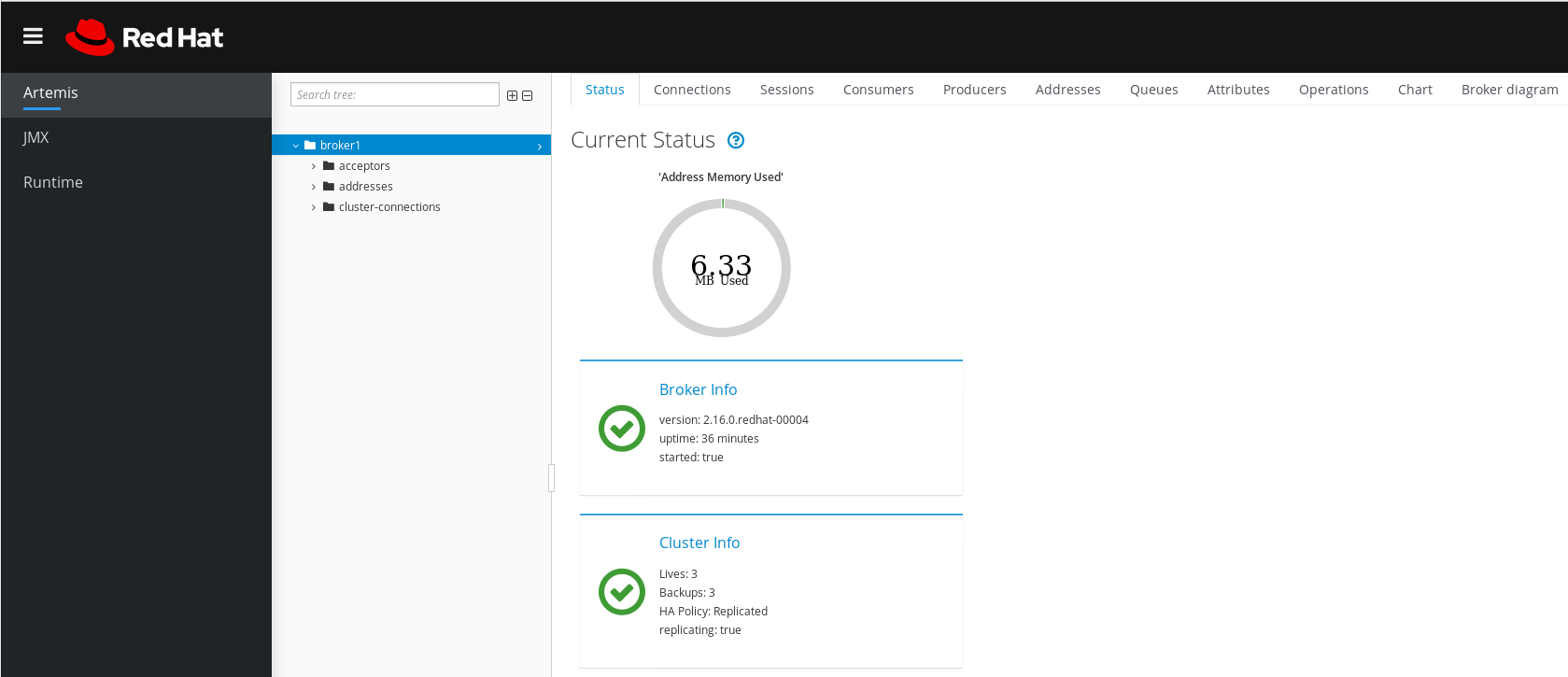
StatusDisplays information about the current status of the broker, such as uptime and cluster information. Also displays the amount of address memory that the broker is currently using. The graph shows this value as a proportion of the
global-max-sizeconfiguration parameter.Figure 4.2. Status tab
Connections- Displays information about broker connections, including client, cluster, and bridge connections.
Sessions- Displays information about all sessions currently open on the broker.
Consumers- Displays information about all consumers currently open on the broker.
Producers- Displays information about producers currently open on the broker.
Addresses- Displays information about addresses on the broker. This includes internal addresses, such as store-and-forward addresses.
Queues- Displays information about queues on the broker. This includes internal queues, such as store-and-forward queues.
Attributes- Displays detailed information about attributes configured on the broker.
Operations- Displays JMX operations that you can execute on the broker from the console. When you click an operation, a dialog box opens that enables you to specify parameter values for the operation.
Chart- Displays real-time data for attributes configured on the broker. You can edit the chart to specify the attributes that are included in the chart.
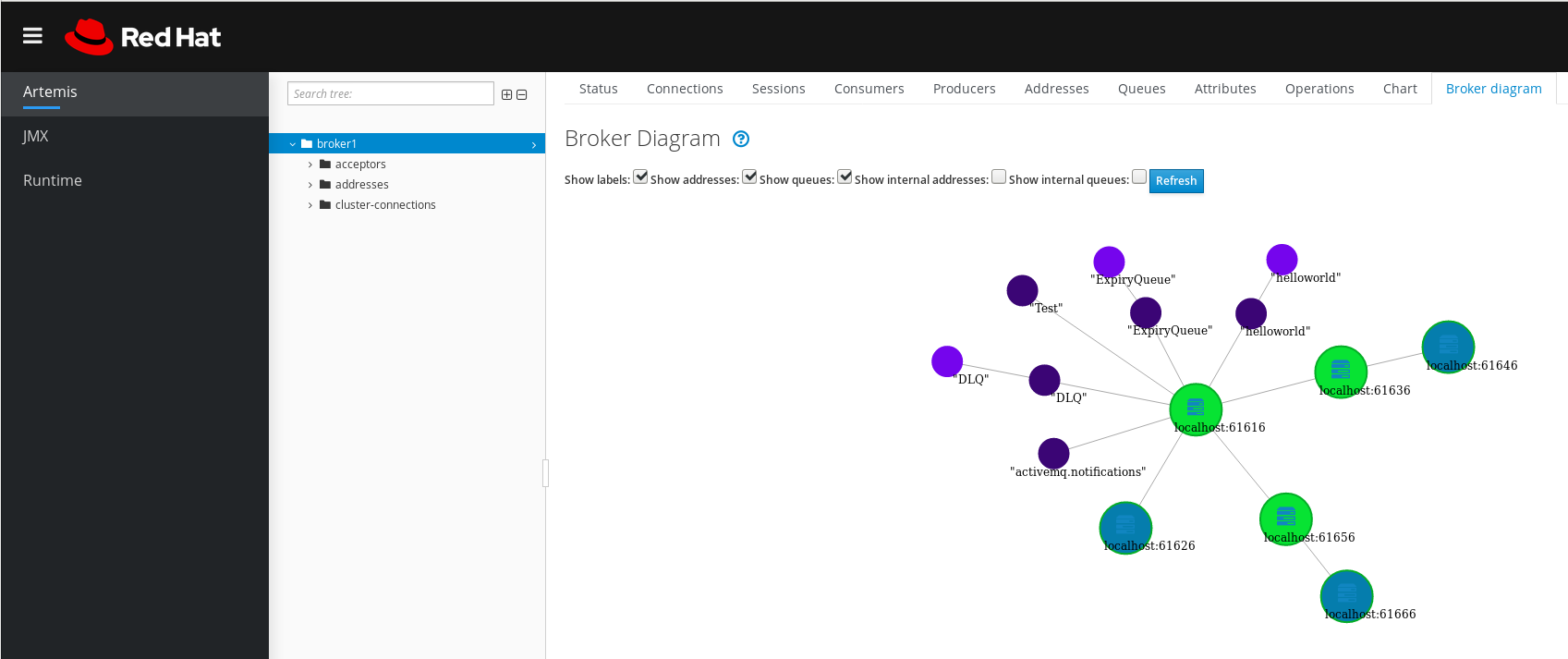
Broker diagram- Displays a diagram of the cluster topology. This includes all brokers in the cluster and any addresses and queues on the local broker.
4.5.2. Viewing the broker diagram
You can view a diagram of all AMQ Broker resources in your topology, including brokers (live and backup brokers), producers and consumers, addresses, and queues.
Procedure
- In the left menu, click Artemis.
In the main pane, click the Broker diagram tab.
The console displays a diagram of the cluster topology. This includes all brokers in the cluster and any addresses and queues on the local broker, as shown in the figure.
Figure 4.3. Broker diagram tab
- To change what items are displayed on the diagram, use the check boxes at the top of the diagram. Click Refresh.
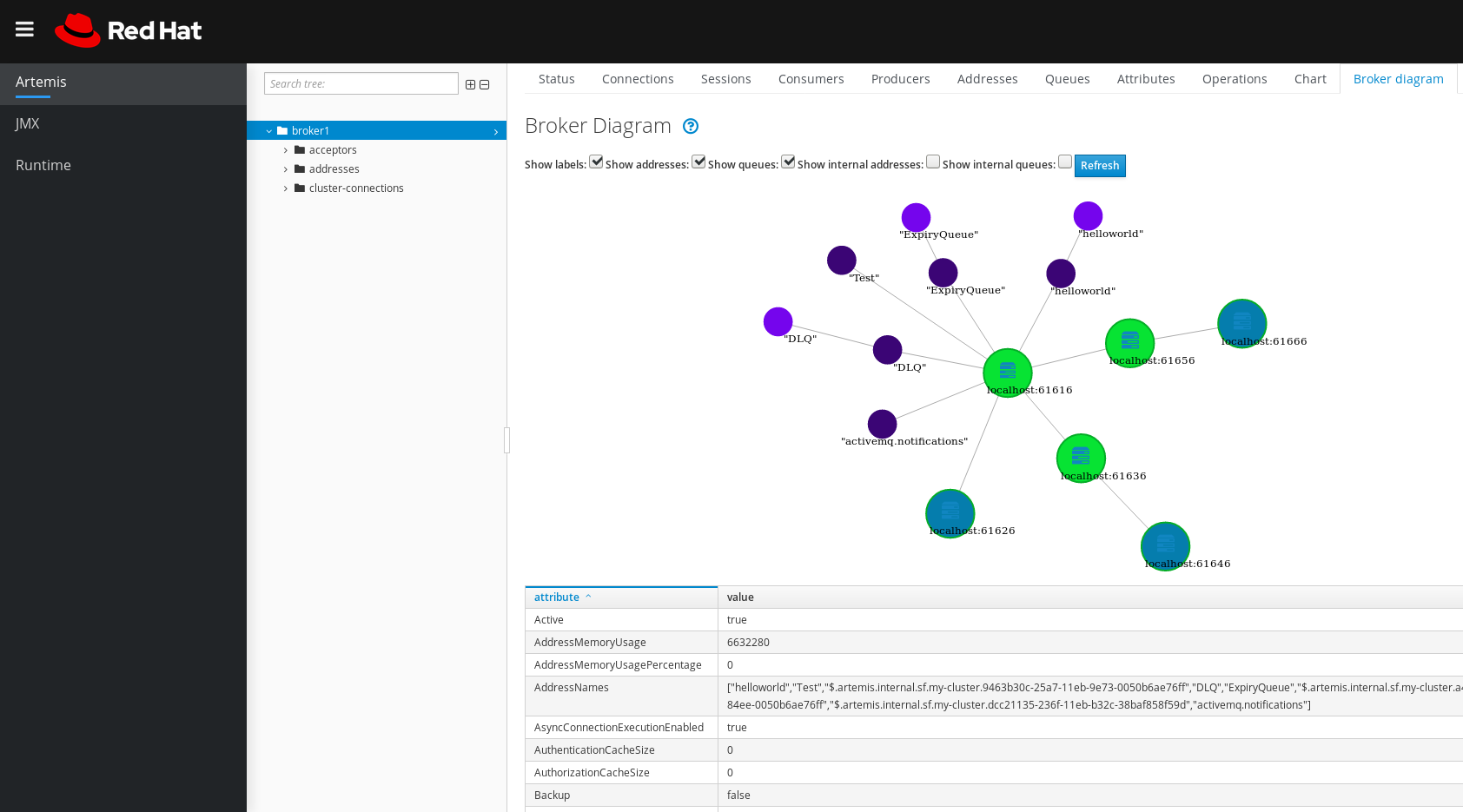
To show attributes for the local broker or an address or queue that is connected to it, click that node in the diagram. For example, the following figure shows a diagram that also includes attributes for the local broker.
Figure 4.4. Broker diagram tab, including attributes
4.5.3. Viewing acceptors
You can view details about the acceptors configured for the broker.
Procedure
- In the left menu, click Artemis.
- In the folder tree, click acceptors.
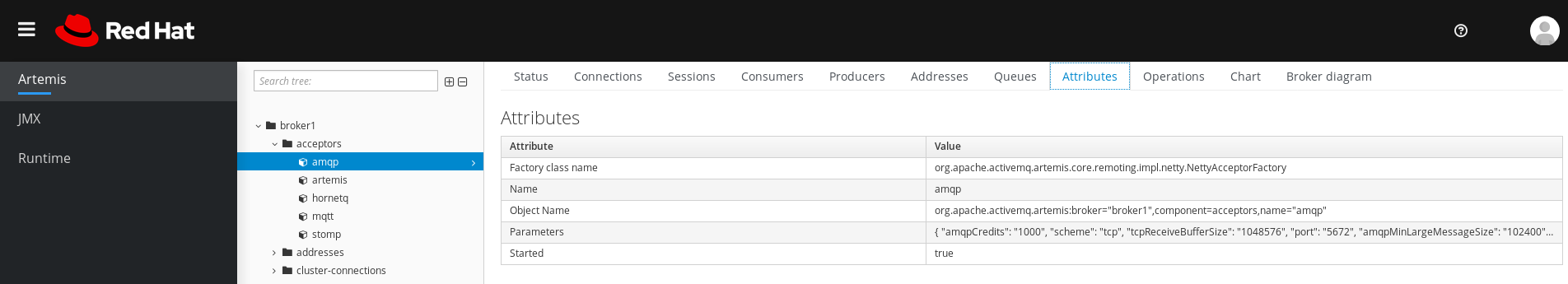
To view details about how an acceptor is configured, click the acceptor.
The console shows the corresponding attributes on the Attributes tab, as shown in the figure.
Figure 4.5. AMQP acceptor attributes
- To see complete details for an attribute, click the attribute. An additional window opens to show the details.
4.5.4. Managing addresses and queues
An address represents a messaging endpoint. Within the configuration, a typical address is given a unique name.
A queue is associated with an address. There can be multiple queues per address. Once an incoming message is matched to an address, the message is sent on to one or more of its queues, depending on the routing type configured. Queues can be configured to be automatically created and deleted.
4.5.4.1. Creating addresses
A typical address is given a unique name, zero or more queues, and a routing type.
A routing type determines how messages are sent to the queues associated with an address. Addresses can be configured with two different routing types.
| If you want your messages routed to… | Use this routing type… |
| A single queue within the matching address, in a point-to-point manner. | Anycast |
| Every queue within the matching address, in a publish-subscribe manner. | Multicast |
You can create and configure addresses and queues, and then delete them when they are no longer in use.
Procedure
- In the left menu, click Artemis.
- In the folder tree, click addresses.
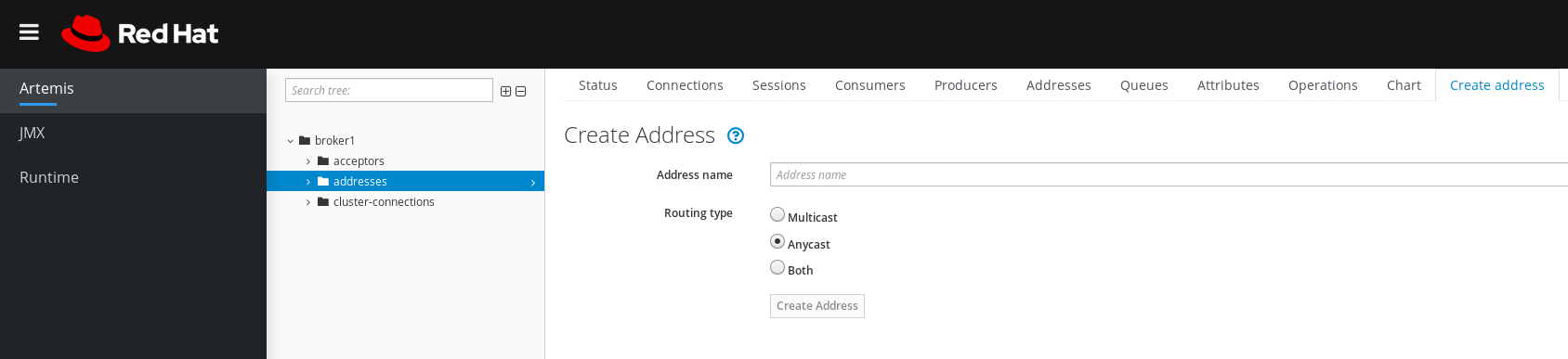
In the main pane, click the Create address tab.
A page appears for you to create an address, as shown in the figure.
Figure 4.6. Create Address page
Complete the following fields:
Address name- The routing name of the address.
Routing typeSelect one of the following options:
-
Multicast: Messages sent to the address will be distributed to all subscribers in a publish-subscribe manner. -
Anycast: Messages sent to this address will be distributed to only one subscriber in a point-to-point manner. Both: Enables you to define more than one routing type per address. This typically results in an anti-pattern and is not recommended.NoteIf an address does use both routing types, and the client does not show a preference for either one, the broker defaults to the
anycastrouting type. The one exception is when the client uses the MQTT protocol. In that case, the default routing type ismulticast.
-
- Click Create Address.
4.5.4.2. Sending messages to an address
The following procedure shows how to use the console to send a message to an address.
Procedure
- In the left menu, click Artemis.
- In the folder tree, select an address.
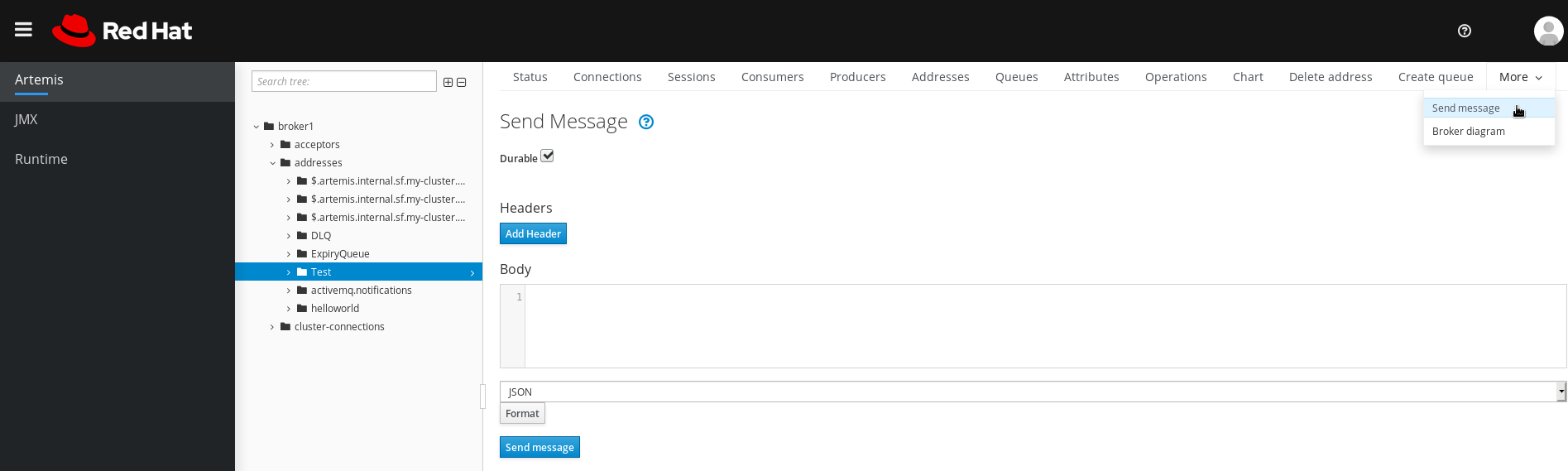
On the navigation bar in the main pane, click
. A page appears for you to create a message, as shown in the figure.
Figure 4.7. Send Message page
- If necessary, click the Add Header button to add message header information.
- Enter the message body.
- In the Format drop-down menu, select an option for the format of the message body, and then click Format. The message body is formatted in a human-readable style for the format you selected.
Click Send message.
The message is sent.
- To send additional messages, change any of the information you entered, and then click Send message.
4.5.4.3. Creating queues
Queues provide a channel between a producer and a consumer.
Prerequisites
- The address to which you want to bind the queue must exist. To learn how to use the console to create an address, see Section 4.5.4.1, “Creating addresses”.
Procedure
- In the left menu, click Artemis.
- In the folder tree, select the address to which you want to bind the queue.
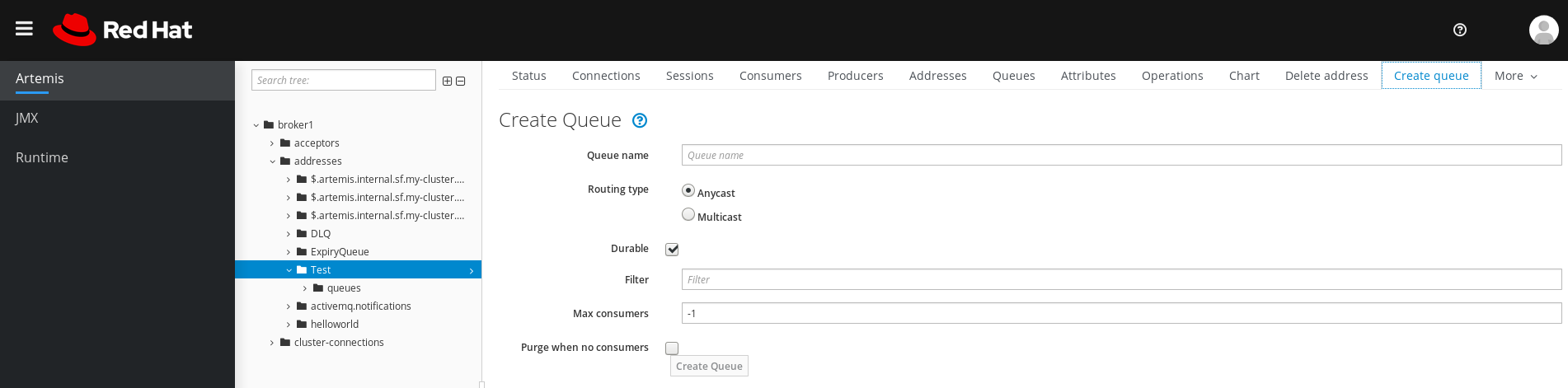
In the main pane, click the Create queue tab.
A page appears for you to create a queue, as shown in the figure.
Figure 4.8. Create Queue page
Complete the following fields:
Queue name- A unique name for the queue.
Routing typeSelect one of the following options:
-
Multicast: Messages sent to the parent address will be distributed to all queues bound to the address. -
Anycast: Only one queue bound to the parent address will receive a copy of the message. Messages will be distributed evenly among all of the queues bound to the address.
-
Durable- If you select this option, the queue and its messages will be persistent.
Filter- The username to be used when connecting to the broker.
Max Consumers- The maximum number of consumers that can access the queue at a given time.
Purge when no consumers- If selected, the queue will be purged when no consumers are connected.
- Click Create Queue.
4.5.4.4. Checking the status of a queue
Charts provide a real-time view of the status of a queue on a broker.
Procedure
- In the left menu, click Artemis.
- In the folder tree, navigate to a queue.
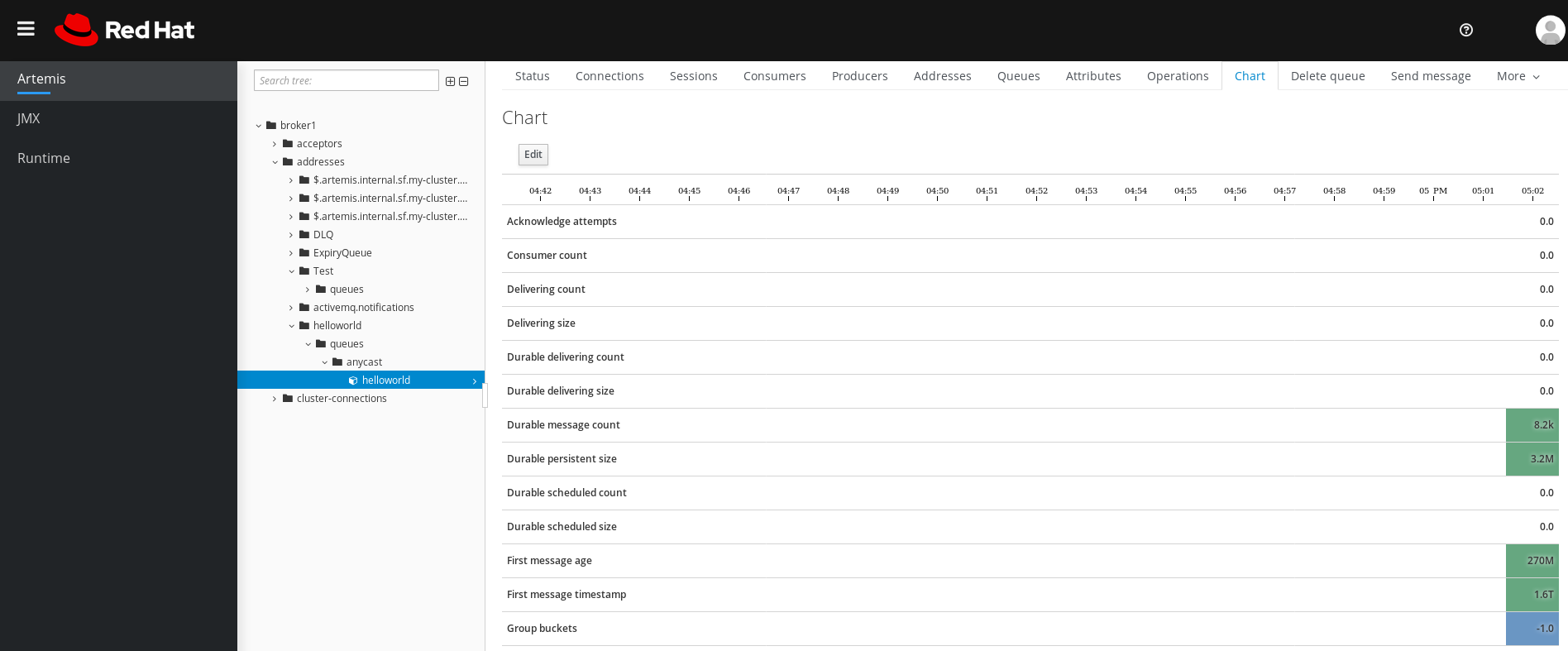
In the main pane, click the Chart tab.
The console displays a chart that shows real-time data for all of the queue attributes.
Figure 4.9. Chart tab for a queue
NoteTo view a chart for multiple queues on an address, select the
anycastormulticastfolder that contains the queues.If necessary, select different criteria for the chart:
- In the main pane, click Edit.
-
On the
Attributeslist, select one or more attributes that you want to include in the chart. To select multiple attributes, press and hold the Ctrl key and select each attribute. - Click the View Chart button. The chart is updated based on the attributes that you selected.
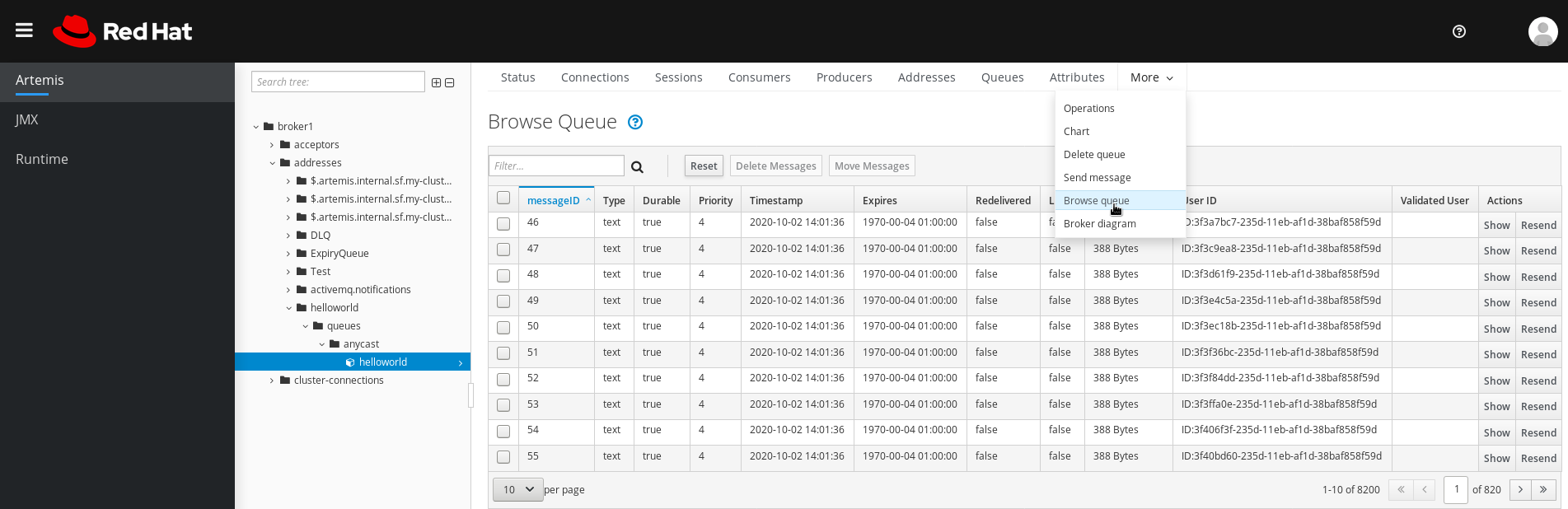
4.5.4.5. Browsing queues
Browsing a queue displays all of the messages in the queue. You can also filter and sort the list to find specific messages.
Procedure
- In the left menu, click Artemis.
In the folder tree, navigate to a queue.
Queues are located within the addresses to which they are bound.
On the navigation bar in the main pane, click
. The messages in the queue are displayed. By default, the first 200 messages are displayed.
Figure 4.10. Browse Queue page
To browse for a specific message or group of messages, do one of the following:
Expand To… Do this… Filter the list of messages
In the
Filter…text field, enter filter criteria. Click the search (that is, magnifying glass) icon.Sort the list of messages
In the list of messages, click a column header. To sort the messages in descending order, click the header a second time.
To view the content of a message, click the Show button.
You can view the message header, properties, and body.
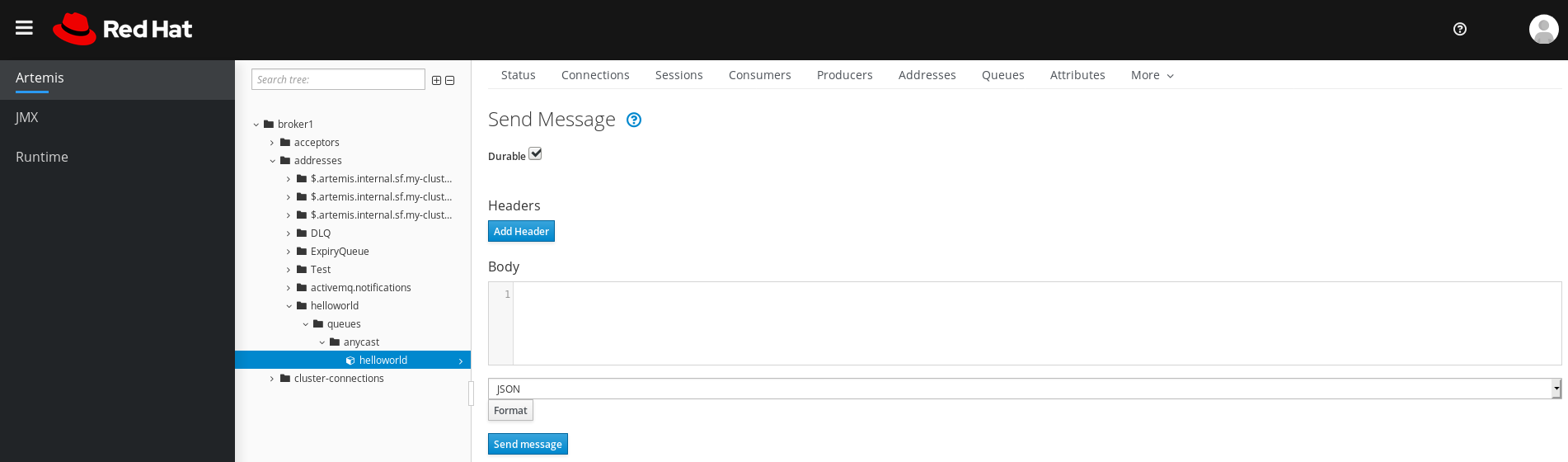
4.5.4.6. Sending messages to a queue
After creating a queue, you can send a message to it. The following procedure outlines the steps required to send a message to an existing queue.
Procedure
- In the left menu, click Artemis.
- In the folder tree, navigate to a queue.
In the main pane, click the Send message tab.
A page appears for you to compose the message.
Figure 4.11. Send Message page for a queue
- If necessary, click the Add Header button to add message header information.
- Enter the message body.
- In the Format drop-down menu, select an option for the format of the message body, and then click Format. The message body is formatted in a human-readable style for the format you selected.
- Click Send message. The message is sent.
- To send additional messages, change any of the information you entered, and click Send message.
4.5.4.7. Resending messages to a queue
You can resend previously sent messages.
Procedure
- Browse for the message you want to resend.
- Click the check box next to the message that you want to resend.
- Click the Resend button. The message is displayed.
- Update the message header and body as needed, and then click Send message.
4.5.4.8. Moving messages to a different queue
You can move one or more messages in a queue to a different queue.
Procedure
- Browse for the messages you want to move.
- Click the check box next to each message that you want to move.
In the navigation bar, click Move Messages.
A confirmation dialog box appears.
- From the drop-down menu, select the name of the queue to which you want to move the messages. Click Move.
4.5.4.9. Deleting messages or queues
You can delete a queue or purge all of the messages from a queue.
Procedure
- Browse for the queue you want to delete or purge.
Do one of the following:
Expand To… Do this… Delete a message from the queue
- Click the check box next to each message that you want to delete.
- Click the Delete button.
Purge all messages from the queue
- On the navigation bar in the main pane, click Delete queue.
- Click the Purge Queue button.
Delete the queue
- On the navigation bar in the main pane, click Delete queue.
- Click the Delete Queue button.