Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 7. Managing credentials
Credentials authenticate the controller user to launch Ansible playbooks. The passwords and SSH keys are used to authenticate against inventory hosts. By using the credentials feature of automation controller, you can require the automation controller user to enter a password or key phrase when a playbook launches.
7.1. Creating new credentials
As part of the initial setup, a demonstration credential and a Galaxy credential have been created for your use. Use the Galaxy credential as a template. It can be copied, but not edited. You can add more credentials as necessary.
Procedure
-
From the navigation panel, select
. To add a new credential, see Creating a credential in the Automation controller User Guide.
NoteWhen you set up additional credentials, the user you assign must have root access or be able to use SSH to connect to the host machine.
- Click to view its details.
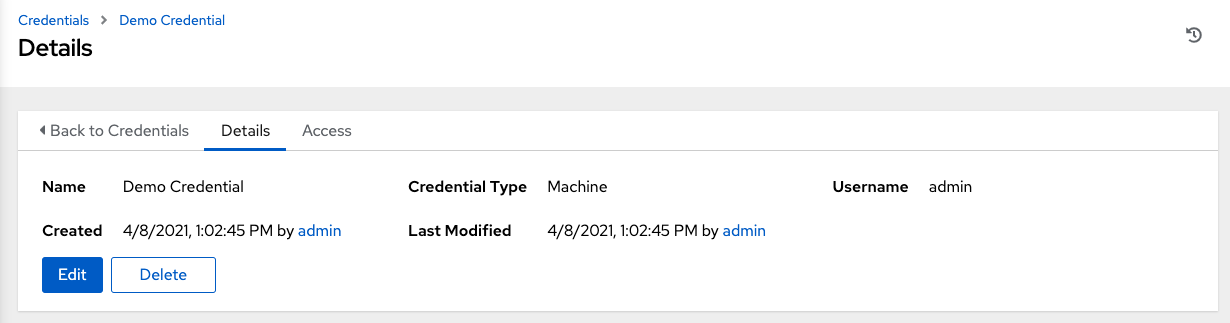
7.2. Editing a credential
As part of the initial setup, you can leave the default Demo Credential as it is, and you can edit it later.
Procedure
Edit the credential by using one of these methods:
- Go to the credential Details page and click .
-
From the navigation panel, select
. Click next to the credential name and edit the appropriate details.
- Save your changes.