This documentation is for a release that is no longer maintained
See documentation for the latest supported version.Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 3. Supported configurations for Red Hat Developer Hub
This section describes the configurations that are required to access the Red Hat Developer Hub, including:
- Custom applications configuration
- Source control configuration for Developer Hub Catalog
3.1. Adding a custom application configuration file to Red Hat OpenShift Container Platform
To access the Red Hat Developer Hub, you must add a custom application configuration file to Red Hat OpenShift Container Platform. In OpenShift Container Platform, you can use the following content as a base template to create a ConfigMap named app-config-rhdh:
You can add the custom application configuration file to OpenShift Container Platform in one of the following ways:
- The Red Hat Developer Hub Operator
- The Red Hat Developer Hub Helm chart.
3.1.1. Adding a custom application configuration file to OpenShift Container Platform using the Helm chart
You can use the Red Hat Developer Hub Helm chart to add a custom application configuration file to your OpenShift Container Platform instance.
Prerequisites
- You have created an Red Hat OpenShift Container Platform account.
Procedure
- From the OpenShift Container Platform web console, select the ConfigMaps tab.
- Click Create ConfigMap.
- From Create ConfigMap page, select the YAML view option in Configure via and make changes to the file, if needed.
- Click Create.
- Go to the Helm tab to see the list of Helm releases.
- Click the overflow menu on the Helm release that you want to use and select Upgrade.
Use either the Form view or YAML view to edit the Helm configuration.
Using Form view
-
Expand Root Schema
Backstage chart schema Backstage parameters Extra app configuration files to inline into command arguments. - Click the Add Extra app configuration files to inline into command arguments link.
Enter the value in the following fields:
-
configMapRef:
app-config-rhdh -
filename:
app-config-rhdh.yaml
-
configMapRef:
- Click Upgrade.
-
Expand Root Schema
Using YAML view
Set the value of the
upstream.backstage.extraAppConfig.configMapRefandupstream.backstage.extraAppConfig.filenameparameters as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Upgrade.
3.1.2. Adding a custom application configuration file to OpenShift Container Platform using the Operator
A custom application configuration file is a ConfigMap object that you can use to change the configuration of your Red Hat Developer Hub instance. If you are deploying your Developer Hub instance on Red Hat OpenShift Container Platform, you can use the Red Hat Developer Hub Operator to add a custom application configuration file to your OpenShift Container Platform instance by creating the ConfigMap object and referencing it in the Developer Hub custom resource (CR).
The custom application configuration file contains a sensitive environment variable, named BACKEND_SECRET. This variable contains a mandatory backend authentication key that Developer Hub uses to reference an environment variable defined in an OpenShift Container Platform secret. You must create a secret, named 'secrets-rhdh', and reference it in the Developer Hub CR.
You are responsible for protecting your Red Hat Developer Hub installation from external and unauthorized access. Manage the backend authentication key like any other secret. Meet strong password requirements, do not expose it in any configuration files, and only inject it into configuration files as an environment variable.
Prerequisites
- You have an active Red Hat OpenShift Container Platform account.
- Your administrator has installed the Red Hat Developer Hub Operator in OpenShift Container Platform. For more information, see Installing the Red Hat Developer Hub Operator.
- You have created the Red Hat Developer Hub CR in OpenShift Container Platform.
Procedure
- From the Developer perspective in the OpenShift Container Platform web console, select the Topology view, and click the Open URL icon on the Developer Hub pod to identify your Developer Hub external URL: <RHDH_URL>.
- From the Developer perspective in the OpenShift Container Platform web console, select the ConfigMaps view.
- Click Create ConfigMap.
Select the YAML view option in Configure via and use the following example as a base template to create a
ConfigMapobject, such asapp-config-rhdh.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Set the external URL of your Red Hat Developer Hub instance.
- 2
- Use an environment variable exposing an OpenShift Container Platform secret to define the mandatory Developer Hub backend authentication key.
- 3
- Set the external URL of your Red Hat Developer Hub instance.
- 4
- Set the external URL of your Red Hat Developer Hub instance.
- Click Create.
- Select the Secrets view.
- Click Create Key/value Secret.
-
Create a secret named
secrets-rhdh. Add a key named
BACKEND_SECRETand a base64 encoded string as a value. Use a unique value for each Red Hat Developer Hub instance. For example, you can use the following command to generate a key from your terminal:node -p 'require("crypto").randomBytes(24).toString("base64")'node -p 'require("crypto").randomBytes(24).toString("base64")'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Create.
- Select the Topology view.
Click the overflow menu for the Red Hat Developer Hub instance that you want to use and select Edit Backstage to load the YAML view of the Red Hat Developer Hub instance.
In the CR, enter the name of the custom application configuration config map as the value for the
spec.application.appConfig.configMapsfield, and enter the name of your secret as the value for thespec.application.extraEnvs.secretsfield. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Save.
- Navigate back to the Topology view and wait for the Red Hat Developer Hub pod to start.
- Click the Open URL icon to use the Red Hat Developer Hub platform with the configuration changes.
Additional resources
- For more information about roles and responsibilities in Developer Hub, see Role-Based Access Control (RBAC) in Red Hat Developer Hub.
3.2. Adding source control for Catalog in Red Hat Developer Hub
To populate the Catalog in Red Hat Developer Hub, you need to add software templates, and to add the templates, you must enable a supported source control such as GitHub.
Prerequisites
- You have a GitHub account.
- You have an account on the Red Hat OpenShift cluster.
- You have installed the Developer Hub, otherwise the GitHub login fails.
For more information about installation, see Installing Red Hat Developer Hub on OpenShift Container Platform.
3.2.1. Configuring GitHub authentication
The configuration of GitHub authentication is required to enable the GitHub OAuth login in Developer Hub.
Procedure
- In the Red Hat OpenShift cluster, navigate to the main page of the GitHub organization where you want to create the OAuth application.
-
Click Settings
Developer Settings OAuth Apps Register an application -
Enter the application name as
Developer Hub. Add the following URL as the Homepage URL:
https://developer-hub-<NAMESPACE_NAME>.<OPENSHIFT_ROUTE_HOST>/Add the following URL as Authorization callback URL:
https://developer-hub-<NAMESPACE_NAME>.<OPENSHIFT_ROUTE_HOST>/api/auth/github/handler/frame- Clear the Enable Device Flow checkbox.
- Click Register application to create your OAuth application.
- After creating the application, click Generate a new client secret and copy the generated client secret.
- In OpenShift, click ConfigMaps.
Generate a key/value secret named 'github-secrets' using the provided environment variables as keys, and input the values you generated for your GitHub OAuth application:
- In Red Hat OpenShift, go to the Secrets tab and click Create.
- Select Key/value secret.
-
Enter Secret name as
github-secrets. Add environment variables as Key and Value and click Create.
Expand Table 3.1. Environment variables Key Value GITHUB_OAUTH_CLIENT_IDClient ID from OAuth application
GITHUB_OAUTH_CLIENT_SECRETClient Secret from OAuth application
Modify your
app-config-rhdhConfigMap to include the GitHub authentication configuration as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Save.
- Navigate to the Helm tab and select Upgrade.
Use one of the following views to edit the Helm configuration:
Using Form view
-
Expand Root Schema
Backstage Chart Schema Backstage Parameters Backstage container environment variables from existing Secrets. - Click the Add Backstage container environment variables from existing Secrets link.
-
Enter
github-secretsas the value. - Click Upgrade.
-
Expand Root Schema
Using YAML view
Set the value of the
upstream.backstage.extraEnvVarsSecretsparameter togithub-secretsas shown in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Upgrade.
3.2.2. Configuring GitHub integration
The configuration of GitHub is required to enable the GitHub plugins in Developer Hub.
Procedure
- In the Red Hat OpenShift cluster, navigate to the main page of the GitHub organization where you want to create the OAuth application.
-
Click Settings
Developer Settings GitHub Apps New GitHub App. -
Enter the application name as
Developer Hub. Add the following URL as the Homepage URL:
https://developer-hub-<NAMESPACE_NAME>.<OPENSHIFT_ROUTE_HOST>/Add the following URL as Authorization callback URL:
https://developer-hub-<NAMESPACE_NAME>.<OPENSHIFT_ROUTE_HOST>/api/auth/github/handler/frame-
Deselect Webhook URL
Active. - Under the Where can this GitHub App be installed? section, ensure that Only on this account is selected.
- Click Register application.
- After creating the application, click Generate a new client secret and copy the generated client secret.
- Click Generate a private key at the bottom of the page and download the generated file.
- In OpenShift, click ConfigMaps.
Generate a key/value secret named 'github-secrets' using the provided environment variables as keys, and input the values you generated for your GitHub OAuth application:
- In Red Hat OpenShift, go to the Secrets tab and click Create.
- Select Key/value secret.
-
Enter Secret name as
github-secrets. - Add environment variables as Key and Value and click Create.
Expand Table 3.2. Environment variables Key Value GITHUB_APP_APP_ID
App ID from GitHub application
GITHUB_APP_CLIENT_ID
Client ID from GitHub application
GITHUB_APP_CLIENT_SECRET
Client Secret from GitHub application
GITHUB_APP_WEBHOOK_URL
Enter "none"
GITHUB_APP_WEBHOOK_SECRET
Enter "none"
GITHUB_APP_PRIVATE_KEY
Upload the private key that was downloaded
Modify your
app-config-rhdhConfigMap to include the GitHub integration configuration as follows:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Click Toplogy
developer hub Actions (drop-down) Restart rollout.
3.2.3. Enabling GitHub discovery in Red Hat Developer Hub
You can enable GitHub discoverability for your components in Developer Hub, such as any repositories that contain catalog-info.yaml file.
Prerequisites
- You have set up the GitHub integration. For more information, see Section 3.2.2, “Configuring GitHub integration”.
Procedure
- In the Developer perspective of the OpenShift Container Platform web console, go to the Helm tab.
- Click the overflow menu on a Helm release and select Upgrade.
Use one of the following views to edit the Helm configuration:
Using Form view
-
Expand Root Schema
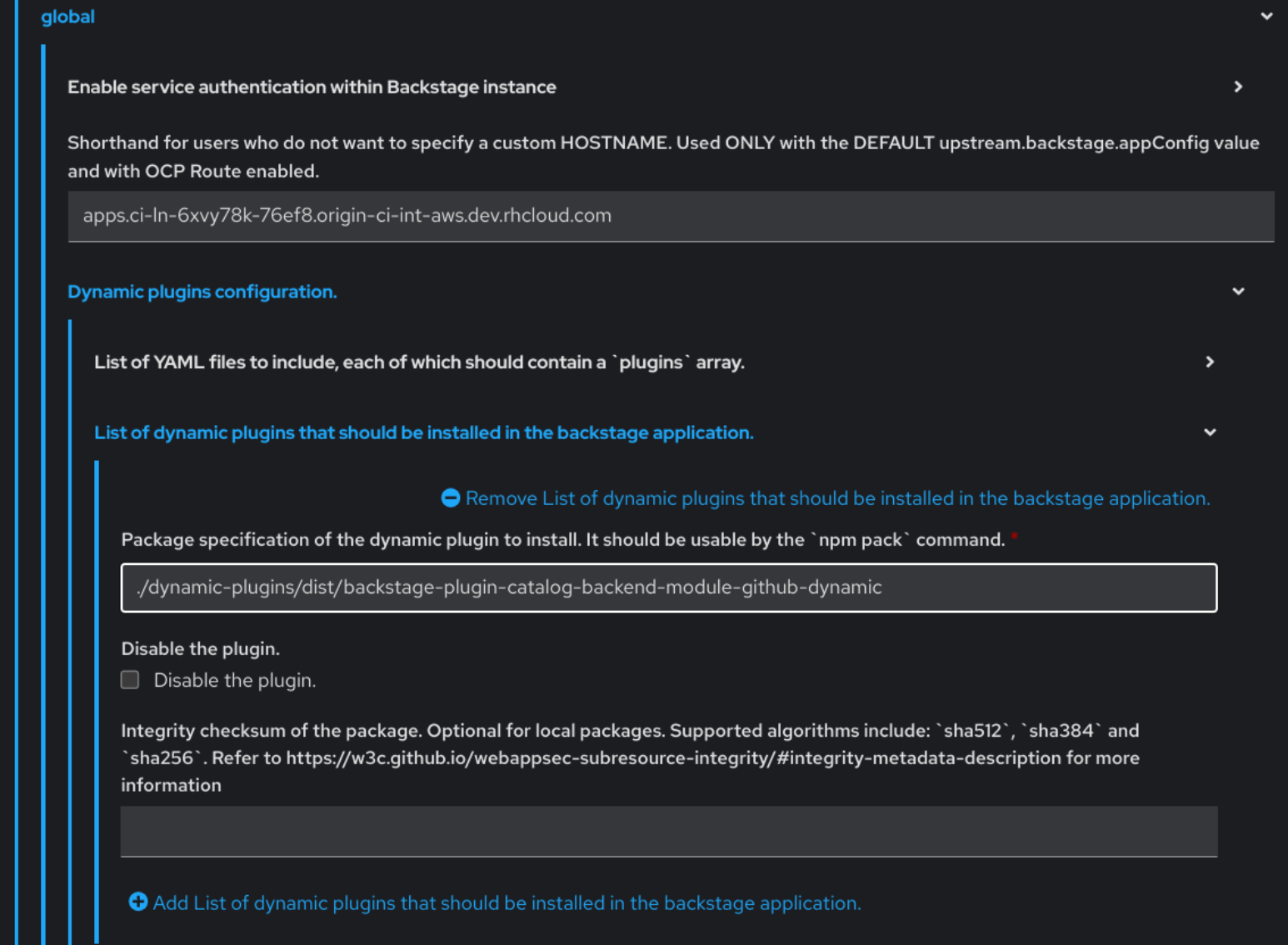
global Dynamic plugins configuration List of dynamic plugins that should be installed in the backstage application. - Click the Add List of dynamic plugins that should be installed in the backstage application link.
In the Package specification of the dynamic plugin to install. It should be usable by the
npm packcommand. field, add the following value:./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-dynamic- Click Upgrade.
-
Expand Root Schema
Using YAML view
Set the value of the
global.dynamic.plugins.packageparameter to./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-dynamicas shown in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Upgrade.
Add the following code in the ConfigMap:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the previous code, replace
${GITHUB_ORG}with the GitHub organization from where you want to discover the components. Also, if there is a single provider, then following code can be added in the ConfigMap:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
providerIdin the previous code is required to identify the provider when there is a list of them.- Click Save.
3.2.4. Enabling GitHub organization member discovery in Red Hat Developer Hub
You can also enable GitHub discoverability for the members of your GitHub organization.
Prerequisites
- You have set up the GitHub integration. For more information, see Section 3.2.2, “Configuring GitHub integration”.
Procedure
- In the Developer perspective of the OpenShift Container Platform web console, go to the Helm tab.
- Click the overflow menu on a Helm release and select Upgrade.
Use one of the following views to edit the Helm configuration:
Using Form view
-
Expand Root Schema
global Dynamic plugins configuration List of dynamic plugins that should be installed in the backstage application. - Click the Add List of dynamic plugins that should be installed in the backstage application link.
In the Package specification of the dynamic plugin to install. It should be usable by the
npm packcommand. field, add the following value:./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-org-dynamic- Click Upgrade.
-
Expand Root Schema
Using YAML view
Set the value of the
global.dynamic.plugins.packageparameter to./dynamic-plugins/dist/backstage-plugin-catalog-backend-module-github-org-dynamicas shown in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click Upgrade.
Add the following code in the ConfigMap:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
${GITHUB_URL}- Denotes a variable that you must replace with the GitHub URL.
${GITHUB_ORG}- Denotes a variable that you must replace with the GitHub organization you want to ingest users from.
- Click Save.