Ce contenu n'est pas disponible dans la langue sélectionnée.
4.10. Configuring Automated Unlocking of Encrypted Volumes using Policy-Based Decryption
The Policy-Based Decryption (PBD) is a collection of technologies that enable unlocking encrypted root and secondary volumes of hard drives on physical and virtual machines using different methods like a user password, a Trusted Platform Module (TPM) device, a PKCS#11 device connected to a system, for example, a smart card, or with the help of a special network server.
The PBD as a technology allows combining different unlocking methods into a policy creating an ability to unlock the same volume in different ways. The current implementation of the PBD in Red Hat Enterprise Linux consists of the Clevis framework and plugins called pins. Each pin provides a separate unlocking capability. For now, the only two pins available are the ones that allow volumes to be unlocked with TPM or with a network server.
The Network Bound Disc Encryption (NBDE) is a subcategory of the PBD technologies that allows binding the encrypted volumes to a special network server. The current implementation of the NBDE includes Clevis pin for Tang server and the Tang server itself.
4.10.1. Network-Bound Disk Encryption
Copier lienLien copié sur presse-papiers!
The Network-Bound Disk Encryption (NBDE) allows the user to encrypt root volumes of hard drives on physical and virtual machines without requiring to manually enter a password when systems are restarted.
In Red Hat Enterprise Linux 7, NBDE is implemented through the following components and technologies:
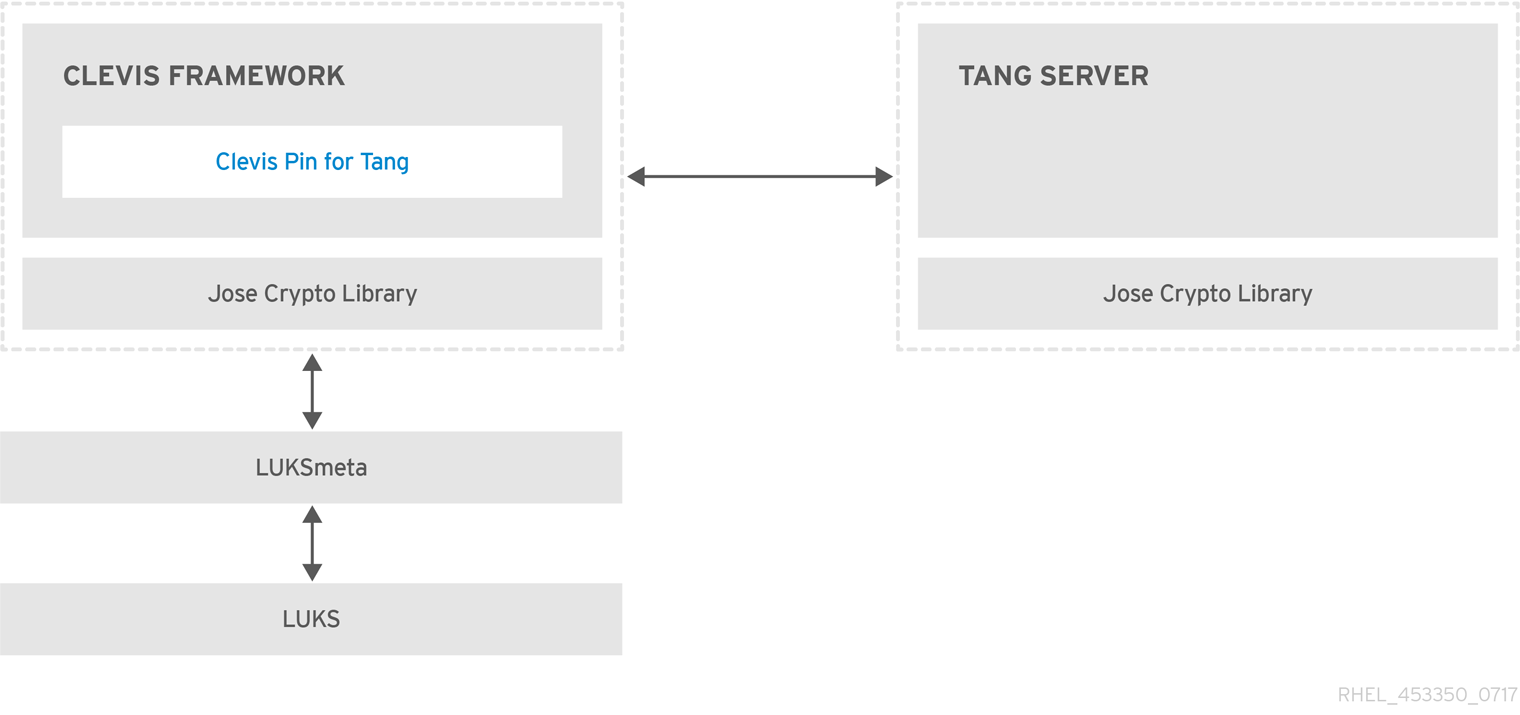
Figure 4.2. The Network-Bound Disk Encryption using Clevis and Tang
Tang is a server for binding data to network presence. It makes a system containing your data available when the system is bound to a certain secure network. Tang is stateless and does not require TLS or authentication. Unlike escrow-based solutions, where the server stores all encryption keys and has knowledge of every key ever used, Tang never interacts with any client keys, so it never gains any identifying information from the client.
Clevis is a pluggable framework for automated decryption. In NBDE, Clevis provides automated unlocking of LUKS volumes. The clevis package provides the client side of the feature.
A Clevis pin is a plug-in into the Clevis framework. One of such pins is a plug-in that implements interactions with the NBDE server — Tang.
Clevis and Tang are generic client and server components that provide network-bound encryption. In Red Hat Enterprise Linux 7, they are used in conjunction with LUKS to encrypt and decrypt root and non-root storage volumes to accomplish Network-Bound Disk Encryption.
Both client- and server-side components use the José library to perform encryption and decryption operations.
When you begin provisioning NBDE, the Clevis pin for Tang server gets a list of the Tang server's advertised asymmetric keys. Alternatively, since the keys are asymmetric, a list of Tang’s public keys can be distributed out of band so that clients can operate without access to the Tang server. This mode is called offline provisioning.
The Clevis pin for Tang uses one of the public keys to generate a unique, cryptographically-strong encryption key. Once the data is encrypted using this key, the key is discarded. The Clevis client should store the state produced by this provisioning operation in a convenient location. This process of encrypting data is the provisioning step. The provisioning state for NBDE is stored in the LUKS header leveraging the luksmeta package.
When the client is ready to access its data, it loads the metadata produced in the provisioning step and it responds to recover the encryption key. This process is the recovery step.
In NBDE, Clevis binds a LUKS volume using a pin so that it can be automatically unlocked. After successful completion of the binding process, the disk can be unlocked using the provided Dracut unlocker.
All LUKS-encrypted devices, such as those with the
/tmp, /var, and /usr/local/ directories, that contain a file system requiring to start before the network connection is established are considered to be root volumes. Additionally, all mount points that are used by services run before the network is up, such as /var/log/, var/log/audit/, or /opt, also require to be mounted early after switching to a root device. You can also identify a root volume by not having the _netdev option in the /etc/fstab file.
4.10.2. Installing an Encryption Client - Clevis
Copier lienLien copié sur presse-papiers!
To install the Clevis pluggable framework and its pins on a machine with an encrypted volume (client), enter the following command as
root:
yum install clevis
~]# yum install clevis
To decrypt data, use the
clevis decrypt command and provide the cipher text (JWE):
clevis decrypt < JWE > PLAINTEXT
~]$ clevis decrypt < JWE > PLAINTEXT
For more information, see the built-in CLI help:
4.10.3. Deploying a Tang Server with SELinux in Enforcing Mode
Copier lienLien copié sur presse-papiers!
Red Hat Enterprise Linux 7.7 and newer provides the
tangd_port_t SELinux type, and a Tang server can be deployed as a confined service in SELinux enforcing mode.
Prerequisites
- The policycoreutils-python-utils package and its dependencies are installed.
Procedure
- To install the tang package and its dependencies, enter the following command as
root:yum install tang
~]# yum install tangCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Pick an unoccupied port, for example, 7500/tcp, and allow the tangd service to bind to that port:
semanage port -a -t tangd_port_t -p tcp 7500
~]# semanage port -a -t tangd_port_t -p tcp 7500Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that a port can be used only by one service at a time, and thus an attempt to use an already occupied port implies theValueError: Port already definederror message. - Open the port in the firewall:
firewall-cmd --add-port=7500/tcp firewall-cmd --runtime-to-permanent
~]# firewall-cmd --add-port=7500/tcp ~]# firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enable the
tangdservice using systemd:systemctl enable tangd.socket Created symlink from /etc/systemd/system/multi-user.target.wants/tangd.socket to /usr/lib/systemd/system/tangd.socket.
~]# systemctl enable tangd.socket Created symlink from /etc/systemd/system/multi-user.target.wants/tangd.socket to /usr/lib/systemd/system/tangd.socket.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Create an override file:
systemctl edit tangd.socket
~]# systemctl edit tangd.socketCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the following editor screen, which opens an empty
override.conffile located in the/etc/systemd/system/tangd.socket.d/directory, change the default port for the Tang server from 80 to the previously picked number by adding the following lines:[Socket] ListenStream= ListenStream=7500
[Socket] ListenStream= ListenStream=7500Copy to Clipboard Copied! Toggle word wrap Toggle overflow Save the file and exit the editor. - Reload the changed configuration and start the
tangdservice:systemctl daemon-reload
~]# systemctl daemon-reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Check that your configuration is working:
systemctl show tangd.socket -p Listen Listen=[::]:7500 (Stream)
~]# systemctl show tangd.socket -p Listen Listen=[::]:7500 (Stream)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Start the
tangdservice:systemctl start tangd.socket
~]# systemctl start tangd.socketCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Because
tangd uses the systemd socket activation mechanism, the server starts as soon as the first connection comes in. A new set of cryptographic keys is automatically generated at the first start.
To perform cryptographic operations such as manual key generation, use the
jose utility. Enter the jose -h command or see the jose(1) man pages for more information.
Example 4.4. Rotating Tang Keys
It is important to periodically rotate your keys. The precise interval at which you should rotate them depends upon your application, key sizes, and institutional policy. For some common recommendations, see the Cryptographic Key Length Recommendation page.
To rotate keys, start with the generation of new keys in the key database directory, typically
/var/db/tang. For example, you can create new signature and exchange keys with the following commands:
DB=/var/db/tang
jose jwk gen -i '{"alg":"ES512"}' -o $DB/new_sig.jwk
jose jwk gen -i '{"alg":"ECMR"}' -o $DB/new_exc.jwk
~]# DB=/var/db/tang
~]# jose jwk gen -i '{"alg":"ES512"}' -o $DB/new_sig.jwk
~]# jose jwk gen -i '{"alg":"ECMR"}' -o $DB/new_exc.jwk
Rename the old keys to have a leading
. to hide them from advertisement. Note that the file names in the following example differs from real and unique file names in the key database directory.
mv $DB/old_sig.jwk $DB/.old_sig.jwk mv $DB/old_exc.jwk $DB/.old_exc.jwk
~]# mv $DB/old_sig.jwk $DB/.old_sig.jwk
~]# mv $DB/old_exc.jwk $DB/.old_exc.jwk
Tang immediately picks up all changes. No restart is required.
At this point, new client bindings pick up the new keys and old clients can continue to utilize the old keys. When you are sure that all old clients use the new keys, you can remove the old keys.
Warning
Be aware that removing the old keys while clients are still using them can result in data loss.
4.10.3.1. Deploying High-Availability Systems
Copier lienLien copié sur presse-papiers!
Tang provides two methods for building a high-availability deployment:
- Client Redundancy (Recommended)Clients should be configured with the ability to bind to multiple Tang servers. In this setup, each Tang server has its own keys and clients are able to decrypt by contacting a subset of these servers. Clevis already supports this workflow through its
sssplug-in.For more information about this setup, see the following man pages:tang(8), section High Availabilityclevis(1), section Shamir's Secret Sharingclevis-encrypt-sss(1)
Red Hat recommends this method for a high-availability deployment. - Key SharingFor redundancy purposes, more than one instance of Tang can be deployed. To set up a second or any subsequent instance, install the tang packages and copy the key directory to the new host using
rsyncover SSH. Note that Red Hat does not recommend this method because sharing keys increases the risk of key compromise and requires additional automation infrastructure.
4.10.4. Deploying an Encryption Client for an NBDE system with Tang
Copier lienLien copié sur presse-papiers!
Prerequisites
- The Clevis framework is installed. See Section 4.10.2, “Installing an Encryption Client - Clevis”
- A Tang server or its downloaded advertisement is available. See Section 4.10.3, “Deploying a Tang Server with SELinux in Enforcing Mode”
Procedure
To bind a Clevis encryption client to a Tang server, use the
clevis encrypt tang sub-command:
Change the http://tang.srv URL in the previous example to match the URL of the server where tang is installed. The JWE output file contains your encrypted cipher text. This cipher text is read from the PLAINTEXT input file.
To decrypt data, use the
clevis decrypt command and provide the cipher text (JWE):
clevis decrypt < JWE > PLAINTEXT
~]$ clevis decrypt < JWE > PLAINTEXT
For more information, see the
clevis-encrypt-tang(1) man page or use the built-in CLI help:
4.10.5. Deploying an Encryption Client with a TPM 2.0 Policy
Copier lienLien copié sur presse-papiers!
On systems with the 64-bit Intel or 64-bit AMD architecture, to deploy a client that encrypts using a Trusted Platform Module 2.0 (TPM 2.0) chip, use the
clevis encrypt tpm2 sub-command with the only argument in form of the JSON configuration object:
clevis encrypt tpm2 '{}' < PLAINTEXT > JWE
~]$ clevis encrypt tpm2 '{}' < PLAINTEXT > JWE
To choose a different hierarchy, hash, and key algorithms, specify configuration properties, for example:
clevis encrypt tpm2 '{"hash":"sha1","key":"rsa"}' < PLAINTEXT > JWE
~]$ clevis encrypt tpm2 '{"hash":"sha1","key":"rsa"}' < PLAINTEXT > JWE
To decrypt the data, provide the ciphertext (JWE):
clevis decrypt < JWE > PLAINTEXT
~]$ clevis decrypt < JWE > PLAINTEXT
The pin also supports sealing data to a Platform Configuration Registers (PCR) state. That way the data can only be unsealed if the PCRs hashes values match the policy used when sealing.
For example, to seal the data to the PCR with index 0 and 1 for the SHA1 bank:
clevis encrypt tpm2 '{"pcr_bank":"sha1","pcr_ids":"0,1"}' < PLAINTEXT > JWE
~]$ clevis encrypt tpm2 '{"pcr_bank":"sha1","pcr_ids":"0,1"}' < PLAINTEXT > JWE
For more information and the list of possible configuration properties, see the
clevis-encrypt-tpm2(1) man page.
4.10.6. Configuring Manual Enrollment of Root Volumes
Copier lienLien copié sur presse-papiers!
To automatically unlock an existing LUKS-encrypted root volume, install the clevis-luks subpackage and bind the volume to a Tang server using the
clevis luks bind command:
yum install clevis-luks
~]# yum install clevis-luks
This command performs four steps:
- Creates a new key with the same entropy as the LUKS master key.
- Encrypts the new key with Clevis.
- Stores the Clevis JWE object in the LUKS header with LUKSMeta.
- Enables the new key for use with LUKS.
This disk can now be unlocked with your existing password as well as with the Clevis policy. For more information, see the
clevis-luks-bind(1) man page.
Note
The binding procedure assumes that there is at least one free LUKS password slot. The
clevis luks bind command takes one of the slots.
To verify that the Clevis JWE object is successfully placed in a LUKS header, use the
luksmeta show command:
To enable the early boot system to process the disk binding, enter the following commands on an already installed system:
yum install clevis-dracut dracut -f --regenerate-all
~]# yum install clevis-dracut
~]# dracut -f --regenerate-allImportant
To use NBDE for clients with static IP configuration (without DHCP), pass your network configuration to the dracut tool manually, for example:
dracut -f --regenerate-all --kernel-cmdline "ip=192.0.2.10 netmask=255.255.255.0 gateway=192.0.2.1 nameserver=192.0.2.45"
~]# dracut -f --regenerate-all --kernel-cmdline "ip=192.0.2.10 netmask=255.255.255.0 gateway=192.0.2.1 nameserver=192.0.2.45"
Alternatively, create a .conf file in the
/etc/dracut.conf.d/ directory with the static network information. For example:
~]# cat /etc/dracut.conf.d/static_ip.conf kernel_cmdline="ip=10.0.0.103 netmask=255.255.252.0 gateway=10.0.0.1 nameserver=10.0.0.1"
~]# cat /etc/dracut.conf.d/static_ip.conf
kernel_cmdline="ip=10.0.0.103 netmask=255.255.252.0 gateway=10.0.0.1 nameserver=10.0.0.1"
Regenerate the initial RAM disk image:
dracut -f --regenerate-all
~]# dracut -f --regenerate-all
See the
dracut.cmdline(7) man page for more information.
4.10.7. Configuring Automated Enrollment Using Kickstart
Copier lienLien copié sur presse-papiers!
Clevis can integrate with Kickstart to provide a fully automated enrollment process.
- Instruct Kickstart to partition the disk such that LUKS encryption has enabled for all mount points, other than
/boot, with a temporary password. The password is temporary for this step of the enrollment process.part /boot --fstype="xfs" --ondisk=vda --size=256 part / --fstype="xfs" --ondisk=vda --grow --encrypted --passphrase=temppass
part /boot --fstype="xfs" --ondisk=vda --size=256 part / --fstype="xfs" --ondisk=vda --grow --encrypted --passphrase=temppassCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that OSPP-complaint systems require a more complex configuration, for example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Install the related Clevis packages by listing them in the
%packagessection:%packages clevis-dracut %end
%packages clevis-dracut %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Call
clevis luks bindto perform binding in the%postsection. Afterward, remove the temporary password:%post clevis luks bind -f -k- -d /dev/vda2 \ tang '{"url":"http://tang.srv","thp":"_OsIk0T-E2l6qjfdDiwVmidoZjA"}' \ <<< "temppass" cryptsetup luksRemoveKey /dev/vda2 <<< "temppass" %end%post clevis luks bind -f -k- -d /dev/vda2 \ tang '{"url":"http://tang.srv","thp":"_OsIk0T-E2l6qjfdDiwVmidoZjA"}' \ <<< "temppass" cryptsetup luksRemoveKey /dev/vda2 <<< "temppass" %endCopy to Clipboard Copied! Toggle word wrap Toggle overflow In the above example, note that we specify the thumbprint that we trust on the Tang server as part of our binding configuration, enabling binding to be completely non-interactive.You can use an analogous procedure when using a TPM 2.0 policy instead of a Tang server.
For more information on Kickstart installations, see the Red Hat Enterprise Linux 7 Installation Guide. For information on Linux Unified Key Setup-on-disk-format (LUKS), see Section 4.9.1, “Using LUKS Disk Encryption”.
4.10.8. Configuring Automated Unlocking of Removable Storage Devices
Copier lienLien copié sur presse-papiers!
To automatically unlock a LUKS-encrypted removable storage device, such as a USB drive, install the clevis-udisks2 package:
yum install clevis-udisks2
~]# yum install clevis-udisks2
Reboot the system, and then perform the binding step using the
clevis luks bind command as described in Section 4.10.6, “Configuring Manual Enrollment of Root Volumes”, for example:
clevis luks bind -d /dev/sdb1 tang '{"url":"http://tang.srv"}'
~]# clevis luks bind -d /dev/sdb1 tang '{"url":"http://tang.srv"}'
The LUKS-encrypted removable device can be now unlocked automatically in your GNOME desktop session. The device bound to a Clevis policy can be also unlocked by the
clevis luks unlock command:
clevis luks unlock -d /dev/sdb1
~]# clevis luks unlock -d /dev/sdb1
You can use an analogous procedure when using a TPM 2.0 policy instead of a Tang server.
4.10.9. Configuring Automated Unlocking of Non-root Volumes at Boot Time
Copier lienLien copié sur presse-papiers!
To use NBDE to also unlock LUKS-encrypted non-root volumes, perform the following steps:
- Install the clevis-systemd package:
yum install clevis-systemd
~]# yum install clevis-systemdCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enable the Clevis unlocker service:
systemctl enable clevis-luks-askpass.path Created symlink from /etc/systemd/system/remote-fs.target.wants/clevis-luks-askpass.path to /usr/lib/systemd/system/clevis-luks-askpass.path.
~]# systemctl enable clevis-luks-askpass.path Created symlink from /etc/systemd/system/remote-fs.target.wants/clevis-luks-askpass.path to /usr/lib/systemd/system/clevis-luks-askpass.path.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Perform the binding step using the
clevis luks bindcommand as described in Section 4.10.6, “Configuring Manual Enrollment of Root Volumes”. - To set up the encrypted block device during system boot, add the corresponding line with the
_netdevoption to the/etc/crypttabconfiguration file. See thecrypttab(5)man page for more information. - Add the volume to the list of accessible filesystems in the
/etc/fstabfile. Use the_netdevoption in this configuration file, too. See thefstab(5)man page for more information.
4.10.10. Deploying Virtual Machines in a NBDE Network
Copier lienLien copié sur presse-papiers!
The
clevis luks bind command does not change the LUKS master key. This implies that if you create a LUKS-encrypted image for use in a virtual machine or cloud environment, all the instances that run this image will share a master key. This is extremely insecure and should be avoided at all times.
This is not a limitation of Clevis but a design principle of LUKS. If you wish to have encrypted root volumes in a cloud, you need to make sure that you perform the installation process (usually using Kickstart) for each instance of Red Hat Enterprise Linux in a cloud as well. The images cannot be shared without also sharing a LUKS master key.
If you intend to deploy automated unlocking in a virtualized environment, Red Hat strongly recommends that you use systems such as lorax or virt-install together with a Kickstart file (see Section 4.10.7, “Configuring Automated Enrollment Using Kickstart”) or another automated provisioning tool to ensure that each encrypted VM has a unique master key.
4.10.11. Building Automatically-enrollable VM Images for Cloud Environments using NBDE
Copier lienLien copié sur presse-papiers!
Deploying automatically-enrollable encrypted images in a cloud environment can provide a unique set of challenges. Like other virtualization environments, it is recommended to reduce the number of instances started from a single image to avoid sharing the LUKS master key.
Therefore, the best practice is to create customized images that are not shared in any public repository and that provide a base for the deployment of a limited amount of instances. The exact number of instances to create should be defined by deployment's security policies and based on the risk tolerance associated with the LUKS master key attack vector.
To build LUKS-enabled automated deployments, systems such as Lorax or virt-install together with a Kickstart file should be used to ensure master key uniqueness during the image building process.
Cloud environments enable two Tang server deployment options which we consider here. First, the Tang server can be deployed within the cloud environment itself. Second, the Tang server can be deployed outside of the cloud on independent infrastructure with a VPN link between the two infrastructures.
Deploying Tang natively in the cloud does allow for easy deployment. However, given that it shares infrastructure with the data persistence layer of ciphertext of other systems, it may be possible for both the Tang server’s private key and the Clevis metadata to be stored on the same physical disk. Access to this physical disk permits a full compromise of the ciphertext data.
Important
For this reason, Red Hat strongly recommends maintaining a physical separation between the location where the data is stored and the system where Tang is running. This separation between the cloud and the Tang server ensures that the Tang server’s private key cannot be accidentally combined with the Clevis metadata. It also provides local control of the Tang server if the cloud infrastructure is at risk.
4.10.12. Additional Resources
Copier lienLien copié sur presse-papiers!
The How to set up Network Bound Disk Encryption with multiple LUKS devices (Clevis+Tang unlocking) Knowledgebase article.
For more information, see the following man pages:
tang(8)clevis(1)jose(1)clevis-luks-unlockers(1)tang-nagios(1)