Ce contenu n'est pas disponible dans la langue sélectionnée.
5.2. Creating Cross-forest Trusts
5.2.1. Environment and Machine Requirements
Copier lienLien copié sur presse-papiers!
Before configuring a trust agreement, make sure that both the Active Directory and Identity Management servers, machines, and environments meet the requirements and settings described in this section.
5.2.1.1. Supported Windows Platforms
Copier lienLien copié sur presse-papiers!
You can establish a trust relationship with Active Directory forests that use the following forest and domain functional levels:
- Forest functional level range: Windows Server 2008 - Windows Server 2016
- Domain functional level range: Windows Server 2008 - Windows Server 2016
The following operating systems are supported and tested for establishing a trust using the mentioned functional levels:
- Windows Server 2012 R2
- Windows Server 2016
Previous versions of Windows Server are not supported for establishing a trust.
5.2.1.2. DNS and Realm Settings
Copier lienLien copié sur presse-papiers!
To establish a trust, Active Directory and Identity Management require specific DNS configuration:
- Unique primary DNS domains
- Each system must have its own unique primary DNS domain configured. For example:
ad.example.comfor AD andidm.example.comfor IdMexample.comfor AD andidm.example.comfor IdMad.example.comfor AD andexample.comfor IdMImportant
If the IdM domain is the parent domain of the AD domain, the IdM servers must run on Red Hat Enterprise Linux 7.5 or later.
The most convenient management solution is an environment where each DNS domain is managed by integrated DNS servers, but it is possible to use any other standard-compliant DNS server as well.It is not possible for AD or IdM to share the primary DNS domain with another system for identity management. For more information, see documentation for host name and DNS configuration requirements in the Linux Domain Identity, Authentication, and Policy Guide. - Kerberos realm names as upper-case versions of primary DNS domain names
- Kerberos realm names must be the same as the primary DNS domain names, with all letters uppercase. For example, if the domain names are
ad.example.comfor AD andidm.example.comfor IdM, the Kerberos realm names are required to beAD.EXAMPLE.COMandIDM.EXAMPLE.COM. - DNS records resolvable from all DNS domains in the trust
- All machines must be able to resolve DNS records from all DNS domains involved in the trust relationship:
- When configuring IdM DNS, follow the instructions described in the section on configuring DNS services within the IdM domain and section on managing DNS forwarding in the Linux Domain Identity, Authentication, and Policy Guide.
- If you are using IdM without integrated DNS, follow the instructions described in the section describing the server installation without integrated DNS in the Linux Domain Identity, Authentication, and Policy Guide.
- No overlap between IdM and AD DNS domains
- Systems joined to IdM can be distributed over multiple DNS domains. DNS domains containing IdM clients must not overlap with DNS domains containing machines joined to AD. The primary IdM DNS domain must have proper SRV records to support AD trusts.
Note
In some environments with trusts between IdM and Active Directory, you can install an IdM client on a host that is part of the Active Directory DNS domain. The host can then benefit from the Linux-focused features of IdM. This is not a recommended configuration and has some limitations. Red Hat recommends to always deploy IdM clients in a DNS zone different from the ones owned by Active Directory and access IdM clients through their IdM host names.You can acquire a list of the required SRV records specific to your system setup by running the$ ipa dns-update-system-records --dry-runcommand.The generated list can look for example like this:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For other DNS domains that are part of the same IdM realm, it is not required for the SRV records to be configured when the trust to AD is configured. The reason is that AD domain controllers do not use SRV records to discover KDCs but rather base the KDC discovery on name suffix routing information for the trust.
Verifying the DNS Configuration
Before configuring trust, verify that the Identity Management and Active Directory servers can resolve themselves and also each other.
If running the commands described below does not display the expected results, inspect the DNS configuration on the host where the commands were executed. If the host configuration seems correct, make sure that DNS delegations from the parent to child domains are set up correctly.
Note that AD caches the results of DNS lookups, and changes you make in DNS are therefore sometimes not visible immediately. You can delete the current cache by running the
ipconfig /flushdns command.
- Verify that the IdM-hosted services are resolvable from the IdM domain server used for establishing trust
- Run a DNS query for the Kerberos over UDP and LDAP over TCP service records.
dig +short -t SRV _kerberos._udp.ipa.example.com. 0 100 88 ipamaster1.ipa.example.com. dig +short -t SRV _ldap._tcp.ipa.example.com. 0 100 389 ipamaster1.ipa.example.com.
[root@ipaserver ~]# dig +short -t SRV _kerberos._udp.ipa.example.com. 0 100 88 ipamaster1.ipa.example.com. [root@ipaserver ~]# dig +short -t SRV _ldap._tcp.ipa.example.com. 0 100 389 ipamaster1.ipa.example.com.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The commands are expected to list all IdM servers. - Run a DNS query for the TXT record with the IdM Kerberos realm name. The obtained value is expected to match the Kerberos realm that you specified when installing IdM.
dig +short -t TXT _kerberos.ipa.example.com. IPA.EXAMPLE.COM
[root@ipaserver ~]# dig +short -t TXT _kerberos.ipa.example.com. IPA.EXAMPLE.COMCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After you execute the
ipa-adtrust-installutility, as described in Section 5.2.2.1.1, “Preparing the IdM Server for Trust”, run a DNS query for the MS DC Kerberos over UDP and LDAP over TCP service records.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The commands are expected to list all IdM servers on whichipa-adtrust-installhas been executed. Note that the output is empty ifipa-adtrust-installhas not been executed on any IdM server, which is typically before establishing the very first trust relationship.
- Verify that IdM is able to resolve service records for AD
- Run a DNS query for the Kerberos over UDP and LDAP over TCP service records.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow These commands are expected to return the names of AD domain controllers. - Verify that the IdM-hosted services are resolvable from the AD server
- On the AD server, set the
nslookup.exeutility to look up service records.C:\>nslookup.exe > set type=SRV
C:\>nslookup.exe > set type=SRVCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the domain name for the Kerberos over UDP and LDAP over TCP service records.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The expected output contains the same set of IdM servers as displayed in Verify that the IdM-hosted services are resolvable from the IdM domain server used for establishing trust. - Change the service type to TXT and run a DNS query for the TXT record with the IdM Kerberos realm name.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output is expected to contain the same value as displayed in Verify that the IdM-hosted services are resolvable from the IdM domain server used for establishing trust. - After you execute the
ipa-adtrust-installutility, as described in Section 5.2.2.1.1, “Preparing the IdM Server for Trust”, run a DNS query for the MS DC Kerberos over UDP and LDAP over TCP service records.Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command is expected to list all IdM servers on which theipa-adtrust-installutility has been executed. Note that the output is empty ifipa-adtrust-installhas not been executed on any IdM server, which is typically before establishing the very first trust relationship.
- Verify that AD services are resolvable from the AD server
- On the AD server, set the
nslookup.exeutility to look up service records.C:\>nslookup.exe > set type=SRV
C:\>nslookup.exe > set type=SRVCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the domain name for the Kerberos over UDP and LDAP over TCP service records.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The expected output contains the same set of AD servers as displayed in Verify that IdM is able to resolve service records for AD.
5.2.1.3. NetBIOS Names
Copier lienLien copié sur presse-papiers!
The NetBIOS name is critical for identifying the Active Directory (AD) domain and, if IdM has a trust configured with AD, for identifying the IdM domain and services. As a consequence, you must use a different NetBIOS name for the IdM domain than the NetBIOS names used in the AD domains to which you want to establish the forest trust.
The NetBIOS name of an Active Directory or IdM domain is usually the far-left component of the corresponding DNS domain. For example, if the DNS domain is
ad.example.com, the NetBIOS name is typically AD.
Note
The maximum length of a NetBIOS name is 15 characters.
5.2.1.4. Firewalls and Ports
Copier lienLien copié sur presse-papiers!
To enable communication between AD domain controllers and IdM servers, make sure you meet the following port requirements:
- Open ports required for an AD trust and ports required by an IdM server in an AD trust on IdM servers and all AD domain controllers in both directions: from the IdM servers to the AD domain controllers and back.
- Open the port required by an IdM client in an AD trust on all AD domain controllers of the trusted AD forest. On the IdM clients, make sure the port is open in the outgoing direction (see Prerequisites for Installing a Client in the Linux Domain Identity, Authentication, and Policy Guide).
| Service | Port | Protocol |
|---|---|---|
| Endpoint resolution portmapper | 135 | TCP |
| NetBIOS-DGM | 138 | TCP and UDP |
| NetBIOS-SSN | 139 | TCP and UDP |
| Microsoft-DS | 445 | TCP and UDP |
| Endpoint mapper listener range | 1024-1300 | TCP |
| AD Global Catalog | 3268 | TCP |
| LDAP | 389 | TCP [a] and UDP |
[a]
The TCP port 389 is not required to be open on IdM servers for trust, but it is necessary for clients communicating with the IdM server.
| ||
| Service | Port | Protocol |
|---|---|---|
| Kerberos | See Port Requirements in the Linux Domain Identity, Authentication, and Policy Guide. | |
| LDAP | ||
| DNS | ||
| Service | Port | Protocol | Notes |
|---|---|---|---|
| Kerberos | 88 | UDP and TCP |
The
libkrb5 library uses UDP and falls-back to the TCP protocol if the data sent from the Kerberos Distribution Center (KDC) is too large. Active Directory attaches a Privilege Attribute Certificate (PAC) to the Kerberos ticket, which increases the size and requires in most cases to use the TCP protocol. To avoid the fall-back and resending the request, by default, SSSD in Red Hat Enterprise Linux 7.4 and later uses TCP for user authentication. To configure the size before libkrb5 uses TCP, set the udp_preference_limit in the /etc/krb.5.conf file. For details, see the krb5.conf(5) man page.
|
Additional Resources
- For advice on how to open the required ports, see Port Requirements in the Linux Domain Identity, Authentication, and Policy Guide.
5.2.1.5. IPv6 Settings
Copier lienLien copié sur presse-papiers!
The IdM system must have the IPv6 protocol enabled in the kernel. If IPv6 is disabled, then the CLDAP plug-in used by the IdM services fails to initialize.
5.2.1.6. Clock Settings
Copier lienLien copié sur presse-papiers!
Both the Active Directory server and the IdM server must have their clocks in sync.
5.2.1.7. Creating a Conditional Forwarder for the IdM Domain in AD
Copier lienLien copié sur presse-papiers!
Prepare the AD DNS server to forward queries for the IdM domain to the IdM DNS server:
- On a Windows AD domain controller, open the Active Directory (AD)
DNSconsole. - Right-click , select New Conditional Forwarder.
- Enter the IdM DNS domain name and the IP address of the IdM DNS server
- Select Store this conditional forwarder in Active Directory, and replicate it as follows, and select the replication setting that matches your environment.
- Click .

- To verify that the AD domain controller (DC) can resolve DNS entries from the IdM domain, open a command prompt and enter:
nslookup server.idm.example.com
C:\> nslookup server.idm.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the command returns the IP address of the IdM server, the conditional forwarder is working correctly.
5.2.1.8. Creating a Forward Zone for the AD Domain in IdM
Copier lienLien copié sur presse-papiers!
Prepare the IdM DNS server to forward queries for the AD domain to the AD DNS server:
- On the IdM server, create a forward zone entry for the AD DNS domain. For further details about creating a DNS forward zone in IdM see the Configuring Forward Zones section in the Linux Domain Identity, Authentication, and Policy Guide.
- If the AD DNS server does not support DNSSEC, disable DNSSEC validation on the IdM server:
- Edit the
/etc/named.conffile and set thednssec-validationparameter tono:dnssec-validation no;
dnssec-validation no;Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the
named-pkcs11service:systemctl restart named-pkcs11
# systemctl restart named-pkcs11Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- To verify that the IdM server can resolve DNS entries from the AD domain, enter:
host server.ad.example.com
# host server.ad.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the command returns the IP address of the AD DC, the forward zone is working correctly.
5.2.1.9. Supported User Name Formats
Copier lienLien copié sur presse-papiers!
IdM performs user name mapping in the local SSSD client. The default output user name format for users from trusted domains supported by SSSD is
user_name@domain. Active Directory supports several different kinds of name formats: user_name, user_name@DOMAIN_NAME, and DOMAIN_NAME\user_name.
Users can use either only their user name (
user_name) or their fully-qualified user name (user_name@domain_name), for example, to authenticate to the system.
Warning
Preferably, use the fully-qualified user name to avoid conflicts if the same user name exists in multiple domains.
If a user specifies only the user name with out the domain, SSSD searches the account in all domains configured in the
/etc/sssd/sssd.conf file and in trusted domains. If you configured a domain resolution order as described in Section 8.5.3, “Configuring the Domain Resolution Order on an IdM Client”, SSSD searches for the user in the defined order. In any case, SSSD uses the first entry found. This can lead to problems or confusion if the same user name exists in multiple domains and the first entry found is not the expected one.
By default, SSSD displays user names always in the fully-qualified format. For details about changing the format, see Section 5.5, “Changing the Format of User Names Displayed by SSSD”.
To identify the user name and the domain to which the user name belongs, SSSD uses a regular expression defined in the
re_expression option. The regular expression is used for IdM back ends or AD back ends and supports all the mentioned formats:
re_expression = (((?P<domain>[^\\]+)\\(?P<name>.+$))|((?P<name>[^@]+)@(?P<domain>.+$))|(^(?P<name>[^@\\]+)$))
re_expression = (((?P<domain>[^\\]+)\\(?P<name>.+$))|((?P<name>[^@]+)@(?P<domain>.+$))|(^(?P<name>[^@\\]+)$))5.2.2. Creating Trusts
Copier lienLien copié sur presse-papiers!
The following sections describe creating trusts in various configuration scenarios. Section 5.2.2.1, “Creating a Trust from the Command Line” contains the full procedure for configuring a trust from the command line. The other sections describe the steps which are different from this basic configuration scenario and reference the basic procedure for all other steps.
Note
If you set up a replica in an existing trust environment, the replica is not automatically configured as a trust controller. To configure the replica as an additional trust controller, follow the procedures in this section.
After creating a trust, see Section 5.2.3, “Post-installation Considerations for Cross-forest Trusts”.
5.2.2.1. Creating a Trust from the Command Line
Copier lienLien copié sur presse-papiers!
Creating a trust relationship between the IdM and Active Directory Kerberos realms involves the following steps:
- Preparing the IdM server for the trust, described in Section 5.2.2.1.1, “Preparing the IdM Server for Trust”
- Creating a trust agreement, described in Section 5.2.2.1.2, “Creating a Trust Agreement”
- Verifying the Kerberos configuration, described in Section 5.2.2.1.3, “Verifying the Kerberos Configuration”
5.2.2.1.1. Preparing the IdM Server for Trust
Copier lienLien copié sur presse-papiers!
To set up the IdM server for a trust relationship with AD, follow these steps:
- Install the required IdM, trust, and Samba packages:
yum install ipa-server ipa-server-trust-ad samba-client
[root@ipaserver ]# yum install ipa-server ipa-server-trust-ad samba-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the IdM server to enable trust services. You can skip this step if you installed the server with the
ipa-replica-install --setup-adtrustcommand.- Run the
ipa-adtrust-installutility:ipa-adtrust-install
[root@ipaserver ]# ipa-adtrust-installCopy to Clipboard Copied! Toggle word wrap Toggle overflow The utility adds DNS service records required for AD trusts. These records are created automatically if IdM was installed with an integrated DNS server.If IdM was installed without an integrated DNS server,ipa-adtrust-installprints a list of service records that you must manually add to the DNS before you can continue.Important
Red Hat strongly recommends to verify the DNS configuration as described in the section called “Verifying the DNS Configuration” every time after runningipa-adtrust-install, especially if IdM or AD do not use integrated DNS servers. - The script prompts to configure the
slapi-nisplug-in, a compatibility plug-in that allows older Linux clients to work with trusted users.Do you want to enable support for trusted domains in Schema Compatibility plugin? This will allow clients older than SSSD 1.9 and non-Linux clients to work with trusted users. Enable trusted domains support in slapi-nis? [no]: y
Do you want to enable support for trusted domains in Schema Compatibility plugin? This will allow clients older than SSSD 1.9 and non-Linux clients to work with trusted users. Enable trusted domains support in slapi-nis? [no]: yCopy to Clipboard Copied! Toggle word wrap Toggle overflow - At least one user (the IdM administrator) exists when the directory is first installed. The SID generation task can create a SID for any existing users to support the trust environment. This is a resource-intensive task; for a high number of users, this can be run separately.
Do you want to run the ipa-sidgen task? [no]: yes
Do you want to run the ipa-sidgen task? [no]: yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Make sure that DNS is properly configured, as described in Section 5.2.1.2, “DNS and Realm Settings”.
- Start the
smbservice:systemctl start smb
[root@ipaserver ~]# systemctl start smbCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, configure that the
smbservice starts automatically when the system boots:systemctl enable smb
[root@ipaserver ~]# systemctl enable smbCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Optionally, use the
smbclientutility to verify that Samba responds to Kerberos authentication from the IdM side.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.2.2.1.2. Creating a Trust Agreement
Copier lienLien copié sur presse-papiers!
Create a trust agreement for the Active Directory domain and the IdM domain by using the
ipa trust-add command:
ipa trust-add --type=type ad_domain_name --admin ad_admin_username --password
# ipa trust-add --type=type ad_domain_name --admin ad_admin_username --password
The
ipa trust-add command sets up a one-way trust by default. It is not possible to establish a two-way trust in RHEL 7.
To establish an external trust, pass the
--external=true option to the ipa trust-add command. See Section 5.1.5, “External Trusts to Active Directory” for details.
Note
The
ipa trust-add command configures the server as a trust controller by default. See Section 5.1.6, “Trust Controllers and Trust Agents” for details.
The following example establishes a two-way trust by using the
--two-way=true option:
5.2.2.1.3. Verifying the Kerberos Configuration
Copier lienLien copié sur presse-papiers!
To verify the Kerberos configuration, test if it is possible to obtain a ticket for an IdM user and if the IdM user can request service tickets.
To verify a two-way trust:
- Request a ticket for an IdM user:
kinit user
[root@ipaserver ~]# kinit userCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Request service tickets for a service within the IdM domain:
kvno -S host ipaserver.example.com
[root@ipaserver ~]# kvno -S host ipaserver.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Request service tickets for a service within the AD domain:
kvno -S cifs adserver.example.com
[root@ipaserver ~]# kvno -S cifs adserver.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the AD service ticket is successfully granted, there is a cross-realm ticket-granting ticket (TGT) listed with all of the other requested tickets. The TGT is namedkrbtgt/AD.DOMAIN@IPA.DOMAIN.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To verify a one-way trust from the IdM side:
- Request a ticket for an Active Directory user:
kinit user@AD.DOMAIN
[root@ipaserver ~]# kinit user@AD.DOMAINCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Request service tickets for a service within the IdM domain:
kvno -S host ipaserver.example.com
[root@ipaserver ~]# kvno -S host ipaserver.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the AD service ticket is successfully granted, there is a cross-realm ticket-granting ticket (TGT) listed with all of the other requested tickets. The TGT is namedkrbtgt/IPA.DOMAIN@AD.DOMAIN.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The
localauth plug-in maps Kerberos principals to local SSSD user names. This allows AD users to use Kerberos authentication and access Linux services, which support GSSAPI authentication directly.
Note
For more information about the plug-in, see Section 5.3.7.2, “Using SSH Without Passwords”.
5.2.2.3. Verifying the ID Mapping
Copier lienLien copié sur presse-papiers!
To verify the ID mapping:
- Run the following command on a Windows Active Directory domain controller (DC) to list the highest ID:
dcdiag /v /test:ridmanager /s:ad.example.com ... Available RID Pool for the Domain is 1600 to 1073741823 ...
C:\> dcdiag /v /test:ridmanager /s:ad.example.com ... Available RID Pool for the Domain is 1600 to 1073741823 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - List the ID ranges on an IdM server:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You require the first POSIX ID value in a later step. - On the Active Directory DC, display the security identifier (SID) or a user. For example, to display the SID of
administrator:wmic useraccount where name="administrator" get sid S-1-5-21-796215754-1239681026-23416912-500
C:\> wmic useraccount where name="administrator" get sid S-1-5-21-796215754-1239681026-23416912-500Copy to Clipboard Copied! Toggle word wrap Toggle overflow The last part of the SID is the relative identifier (RID). You require the user's RID in the next step.Note
If the RID is higher than the default ID range (200000), use theipa idrange-modcommand to extend the range. For example:ipa idrange-mod --range-size=1000000 AD.EXAMPLE.COM_id_range
# ipa idrange-mod --range-size=1000000 AD.EXAMPLE.COM_id_rangeCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Display the user ID of the same user on the IdM server:
id ad\\administrator uid=610600500(administrator@ad.example.com)...
[root@ipaserver ~]# id ad\\administrator uid=610600500(administrator@ad.example.com)...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - If you add the first POSIX ID value (610600000) to the RID (500), it must match the user ID displayed on the IdM server (610600500).
5.2.2.4. Creating a Trust on an Existing IdM Instance
Copier lienLien copié sur presse-papiers!
When configuring a trust for an existing IdM instance, certain settings for the IdM server and entries within its domain are already configured. However, you must set the DNS configuration for the Active Directory domain and assign Active Directory SIDs to all existing IdM users and groups.
- Prepare the IdM server for the trust, as described in Section 5.2.2.1.1, “Preparing the IdM Server for Trust”.
- Create a trust agreement, as described in Section 5.2.2.1.2, “Creating a Trust Agreement”.
- Generate SIDs for each IdM user.
Note
Do not perform this step if the SIDs were generated when theipa-adtrust-installutility was used to establish the trust.- Add a new
ipaNTSecurityIdentifierattribute, containing a SID, automatically for each entry by running theipa-sidgen-taskoperation on the back-end LDAP directory.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - After the task completes successfully, a message is recorded in the error logs that the SID generation task (
Sidgen task) finished with a status of zero (0).grep "sidgen_task_thread" /var/log/dirsrv/slapd-IDM-EXAMPLE-COM/errors [20/Jul/2012:18:17:16 +051800] sidgen_task_thread - [file ipa_sidgen_task.c, line 191]: Sidgen task starts ... [20/Jul/2012:18:17:16 +051800] sidgen_task_thread - [file ipa_sidgen_task.c, line 196]: Sidgen task finished [0].
[root@ipaserver ]# grep "sidgen_task_thread" /var/log/dirsrv/slapd-IDM-EXAMPLE-COM/errors [20/Jul/2012:18:17:16 +051800] sidgen_task_thread - [file ipa_sidgen_task.c, line 191]: Sidgen task starts ... [20/Jul/2012:18:17:16 +051800] sidgen_task_thread - [file ipa_sidgen_task.c, line 196]: Sidgen task finished [0].Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Verify the Kerberos configuration, as described in Section 5.2.2.1.3, “Verifying the Kerberos Configuration”.
5.2.2.5. Adding a Second Trust
Copier lienLien copié sur presse-papiers!
When adding a trust on an IdM server that already has one or more trust agreements configured, certain general IdM trust settings, such as installing the trust-related packages or configuring SIDs, is no longer required. To add an additional trust, you only must configure DNS and establish a trust agreement.
- Make sure that DNS is properly configured, as described in Section 5.2.1.2, “DNS and Realm Settings”.
- Create a trust agreement, as described in Section 5.2.2.1.2, “Creating a Trust Agreement”.
5.2.2.6. Creating a Trust in the Web UI
Copier lienLien copié sur presse-papiers!
Before creating a trust in the web UI, prepare the IdM server for the trust. This trust configuration is easiest to perform from the command line, as described in Section 5.2.2.1.1, “Preparing the IdM Server for Trust”.
Once the initial configuration is set, a trust agreement can be added in the IdM web UI:
- Open the IdM web UI:
https://ipaserver.example.com
https://ipaserver.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Open the IPA Server main tab, and select the Trusts subtab.
- In the Trusts subtab, click Add to open the new trust configuration window.
- Fill in the required information about the trust:
- Provide the AD domain name in the Domain field.
- To set up the trust as two-way, select the Two-way trust check box. To set up the trust as one-way, leave Two-way trust unselected.For more information about one-way and two-way trusts, see Section 5.1.4, “One-Way and Two-Way Trusts”.
- To establish an external trust to a domain in another forest, select the External Trust check box.For more information, see Section 5.1.5, “External Trusts to Active Directory”.
- The Establish using section defines how the trust is to be established:
- To establish the trust using the AD administrator's user name and password, select Administrative account and provide the required credentials.
- Alternatively, to establish the trust with a shared password, select Pre-shared password and provide the trust password.
- Define the ID configuration for the trust:
- The Range type option allows you to choose the ID range type. If you want IdM to automatically detect what kind of ID range to use, select Detect.
- To define the starting ID of the ID range, use the Base ID field. To define the size of the ID range, use the Range size field. If you want IdM to use default values for the ID range, do not specify these options.
For more information about ID ranges, see the section called “ID Ranges”.
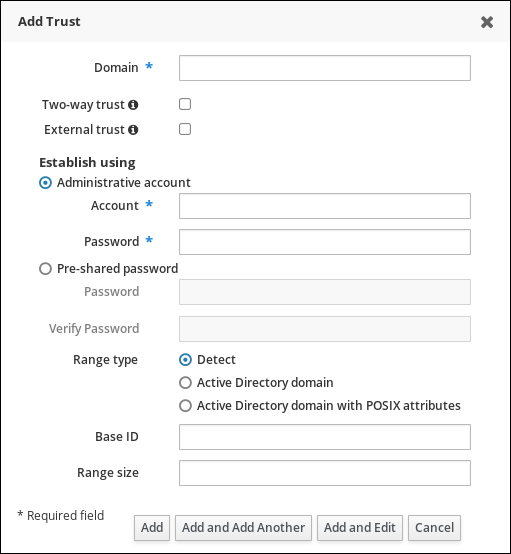
Figure 5.5. Adding a Trust in the Web UI
- Click to save the new trust.
After this, verify the Kerberos configuration, as described in Section 5.2.2.1.3, “Verifying the Kerberos Configuration”.
5.2.3. Post-installation Considerations for Cross-forest Trusts
Copier lienLien copié sur presse-papiers!
5.2.3.1. Potential Behavior Issues with Active Directory Trust
Copier lienLien copié sur presse-papiers!
5.2.3.1.1. Active Directory Users and IdM Administration
Copier lienLien copié sur presse-papiers!
Currently, Active Directory (AD) users and administrators can only see their self-service page after logging into the IdM Web UI. AD administrators cannot access the administrator's view of IdM Web UI. For details, see the Authenticating to the IdM Web UI as an AD User section in the Linux Domain Identity, Authentication, and Policy Guide.
Additionally, AD users currently cannot manage their own ID overrides. Only IdM users can add and manage ID overrides.
5.2.3.1.2. Authenticating Deleted Active Directory Users
Copier lienLien copié sur presse-papiers!
By default, every IdM client uses the SSSD service to cache user identities and credentials. If the IdM or AD back-end provider is temporarily unavailable, SSSD enables the local system to reference identities for users who have already logged in successfully once.
Because SSSD maintains a list of users locally, changes that are made on the back end might not be immediately visible to clients that run SSSD offline. On such clients, users who have previously logged into IdM resources and whose hashed passwords are stored in the SSSD cache are able to log in again even if their user accounts have been deleted in AD.
If the above conditions are met, the user identity is cached in SSSD, and the AD user is able to log into IdM resources even if the user account is deleted AD. This problem will persist until SSSD becomes online and is able to verify AD user logon against AD domain controllers.
If the client system runs SSSD online, the password provided by the user is validated by an AD domain controller. This ensures that deleted AD users are not allowed to log in.
5.2.3.1.3. Credential Cache Collections and Selecting Active Directory Principals
Copier lienLien copié sur presse-papiers!
The Kerberos credentials cache attempts to match a client principal to a server principal based on the following identifiers in this order:
- service name
- host name
- realm name
When the client and server mapping is based on the host name or real name and credential cache collections are used, unexpected behavior can occur in binding as an AD user. This is because the realm name of the Active Directory user is different than the realm name of the IdM system.
If an AD user obtains a ticket using the
kinit utility and then uses SSH to connect to an IdM resource, the principal is not selected for the resource ticket. an IdM principal is used because the IdM principal matches the realm name of the resource.
For example, if the AD user is
Administrator and the domain is ADEXAMPLE.ADREALM, the principal is Administrator@ADEXAMPLE.ADREALM.
This is set as the default principal in the Active Directory ticket cache. However, if any IdM user also has a Kerberos ticket (such as
admin), then there is a separate IdM credentials cache, with an IdM default principal. That IdM default principal is selected for a host ticket if the Active Directory user uses SSH to connect to a resource.
This is because the realm name of the IdM principal matches the realm of the IdM resource.
5.2.3.1.4. Resolving Group SIDs
Copier lienLien copié sur presse-papiers!
Losing Kerberos Tickets
Running a command to obtain a SID from the Samba service, such as
net getlocalsid or net getdomainsid, removes any existing admin ticket from the Kerberos cache.
Note
You are not required to run commands such as
net getlocalsid or net getdomainsid in order to use Active Directory trusts.
Cannot Verify Group Membership for Users
It is not possible to verify that a specific trusted user is associated with a specific IdM group, external or POSIX.
Cannot Display Remote Active Directory Group Memberships for an Active Directory User
Important
Note that this problem no longer occurs if the IdM server and client run on Red Hat Enterprise Linux 7.1 or later.
The
id utility can be used to display local group associations for Linux system users. However, id does not display Active Directory group memberships for Active Directory users, even though Samba tools do display them.
To work around this, you can use the
ssh utility to log into an IdM client machine as the given AD user. After the AD user logs in successfully for the first time, the id search detects and displays the AD group memberships:
id ADDOMAIN\user uid=1921801107(user@ad.example.com) gid=1921801107(user@ad.example.com) groups=1921801107(user@ad.example.com),129600004(ad_users),1921800513(domain users@ad.example.com)
[root@ipaserver ~]# id ADDOMAIN\user
uid=1921801107(user@ad.example.com) gid=1921801107(user@ad.example.com) groups=1921801107(user@ad.example.com),129600004(ad_users),1921800513(domain users@ad.example.com)5.2.3.2. Configuring Trust Agents
Copier lienLien copié sur presse-papiers!
After you set up a new replica in a trust environment, the replica does not automatically have the
AD trust agent role installed. To configure the replica as a trust agent:
- On an existing trust controller, run the
ipa-adtrust-install --add-agentscommand:ipa-adtrust-install --add-agents
[root@existing_trust_controller]# ipa-adtrust-install --add-agentsCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command starts an interactive configuration session and prompts you for the information required to set up the agent.For further information about the--add-agentsoption, see the ipa-adtrust-install(1) man page. - On the new replica:
- Restart the IdM service:
ipactl restart
[root@new_trust_controller]# ipactl restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Remove all entries from the SSSD cache:
sssctl cache-remove
[root@new_trust_controller]# sssctl cache-removeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note
To use thesssctlcommand, the sssd-tools package must be installed. - Optionally, verify that the replica has the
AD trust agentrole installed:ipa server-show new_replica.idm.example.com ... Enabled server roles: CA server, NTP server, AD trust agent
[root@new_trust_controller]# ipa server-show new_replica.idm.example.com ... Enabled server roles: CA server, NTP server, AD trust agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow