Fuse 6 is no longer supported
As of February 2025, Red Hat Fuse 6 is no longer supported. If you are using Fuse 6, please upgrade to Red Hat build of Apache Camel.Ce contenu n'est pas disponible dans la langue sélectionnée.
6.4. Securing the Web Services Client
Overview
src/test directory. This means that the client can easily be run using the Maven command, mvn test. To enable SSL/TLS security on the client, the Java implementation of the test client is completely replaced and a Spring file, containing the SSL/TLS configuration, is added to the src/test/resources/META-INF/spring directory. Before describing the steps you need to perform to set up the client, this section explains some details of the client's Java code and Spring configuration.
Implicit configuration
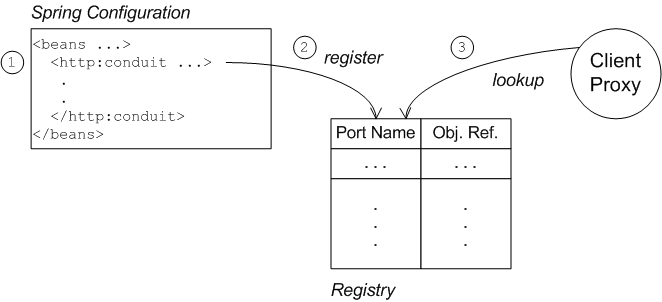
https:, most of the configuration to enable SSL/TLS security on a client proxy is contained in a http:conduit element in Spring configuration. The way in which this configuration is applied to the client proxy, however, is potentially confusing, for the following reason: the http:conduit element does not explicitly reference the client proxy and the client proxy does not explicitly reference the http:conduit element. The connection between the http:conduit element and the client proxy is established implicitly, in that they both reference the same WSDL port, as illustrated by Figure 6.3, “Client Proxy Implicitly Configured by http:conduit Element”.
Figure 6.3. Client Proxy Implicitly Configured by http:conduit Element
http:conduit element is established as follows:
- The client loads and parses the Spring configuration file containing the
http:conduitelement. - When the
http:conduitbean is created, a corresponding entry is created in the registry, which stores a reference to the bean under the specified WSDL port name (where the name is stored in QName format). - When the JAX-WS client proxy is created, it scans the registry to see if it can find a
http:conduitbean associated with the proxy's WSDL port name. If it finds such a bean, it automatically injects the configuration details into the proxy.
Certificates needed on the client side
clientKeystore.jks keystore file from the src/main/resources/certs directory. This keystore contains two entries, as follows:
- Trusted cert entry
- A trusted certificate entry containing the CA certificate that issued and signed both the server certificate and the client certificate.
- Private key entry
- A private key entry containing the client's own X.509 certificate and private key. In fact, this certificate is not strictly necessary to run the current example, because the server does not require the client to send a certificate during the TLS handshake (see Example 6.2, “httpj:engine-factory Element with SSL/TLS Enabled”).
Loading Spring definitions into the client
org.apache.cxf.bus.spring.SpringBusFactory class.
META-INF/spring/cxf-client.xml, and create an Apache CXF Bus object that incorporates those definitions:
Creating the client proxy
JaxWsProxyFactoryBean, to create a proxy.
JaxWsProxyFactoryBean approach to create a proxy, because a proxy created in this way fails to find the HTTP conduit settings specified in the Spring configuration file.
SERVICE_NAME and PORT_NAME constants are the QNames of the WSDL service and the WSDL port respectively, as defined in Example 6.1, “The ReportIncidentEndpointService WSDL Service”. The ADDRESS_URL string has the same value as the proxy Web service address and is defined as follows:
private static final String ADDRESS_URL = "https://localhost:9080/camel-example-cxf-proxy/webservices/incident";
private static final String ADDRESS_URL =
"https://localhost:9080/camel-example-cxf-proxy/webservices/incident";https, which selects HTTP over SSL/TLS.
Steps to add SSL/TLS security to the client
Create the Java client as a test case
ReportIncidentRoutesTest.java, in the src/test/java/org/apache/camel/example/reportincident sub-directory of the examples/camel-example-cxf-proxy demonstration.
CamelInstallDir/examples/camel-example-cxf-proxy demonstration, go to the src/test/java/org/apache/camel/example/reportincident sub-directory, move the existing ReportIncidentRoutesTest.java file to a backup location, then create a new ReportIncidentRoutesTest.java file and paste the code from Example 6.3, “ReportIncidentRoutesTest Java client” into this file.
Example 6.3. ReportIncidentRoutesTest Java client
Add the http:conduit element to Spring configuration
http:conduit element for the ReportIncidentEndpoint WSDL port. The http:conduit element is configured to enable SSL/TLS security for any client proxies that use the specified WSDL port.
src/test/resources/META-INF/spring sub-directory, use your favorite text editor to create the file, cxf-client.xml, and then paste the contents of Example 6.4, “http:conduit Element with SSL/TLS Enabled” into the file.
Example 6.4. http:conduit Element with SSL/TLS Enabled
- The
http:andsec:namespace prefixes are needed to define thehttp:conduitelement. In thexsi:schemaLocationelement, it is also essential to specify the locations of the correspondinghttp://cxf.apache.org/configuration/securityandhttp://cxf.apache.org/transports/http/configurationnamespaces. - The
disableCNCheckattribute of thehttp:tlsClientParameterselement is set totrue. This means that the client does not check whether the Common Name in the server's X.509 certificate matches the server hostname. For more details, see Appendix A, Managing Certificates.ImportantDisabling the CN check is not recommended in a production deployment. - In the
sec:keystoreelements, the certificate locations are specified using theresourceattribute, which finds the certificates on the classpath. When Maven runs the test, it automatically makes the contents ofsrc/main/resourcesavailable on the classpath, so that the certificates can be read from thesrc/main/resources/certsdirectory.NoteYou also have the option of specifying a certificate location using thefileattribute, which looks in the filesystem. But theresourceattribute is more suitable for use with applications packaged in bundles. - The
sec:cipherSuitesFilterelement is configured to exclude cipher suites matching.*_WITH_NULL_.*and.*_DH_anon_.*. These cipher suites are effectively incomplete and are not intended for normal use.ImportantIt is recommended that you always exclude the ciphers matching.*_WITH_NULL_.*and.*_DH_anon_.*. - The
secureSocketProtocolattribute should be set to TLSv1, to match the server protocol and to ensure that the SSLv3 protocol is not used (POODLE security vulnerability (CVE-2014-3566)).
Run the client
CamelInstallDir/examples/camel-example-cxf-proxy, and enter the following Maven command:
mvn test
mvn testIncident was 123, changed to 456 Invoked real web service: id=456 by Claus Ibsen
Incident was 123, changed to 456
Invoked real web service: id=456 by Claus Ibsen