Fuse 6 is no longer supported
As of February 2025, Red Hat Fuse 6 is no longer supported. If you are using Fuse 6, please upgrade to Red Hat build of Apache Camel.Ce contenu n'est pas disponible dans la langue sélectionnée.
1.2. Apache Camel Security
Overview
Copier lienLien copié sur presse-papiers!
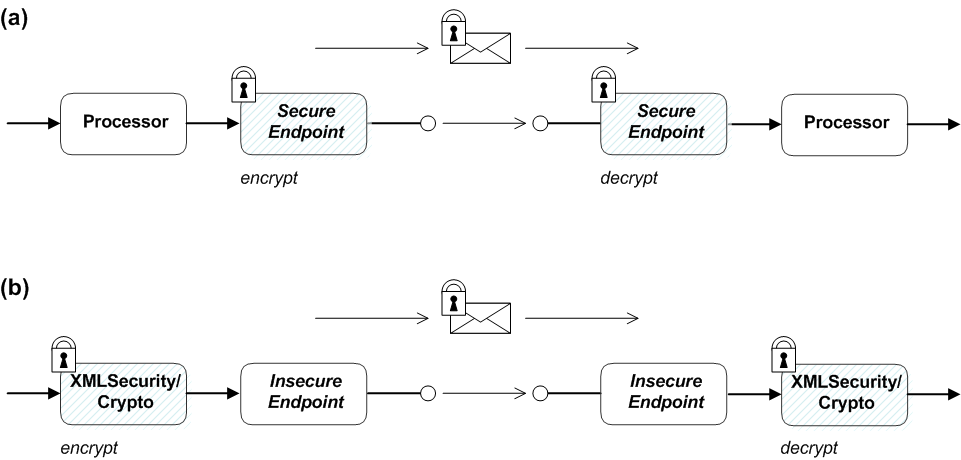
Figure 1.2, “Apache Camel Security Architecture” shows an overview of the basic options for securely routing messages between Apache Camel endpoints.
Figure 1.2. Apache Camel Security Architecture
Alternatives for Apache Camel security
Copier lienLien copié sur presse-papiers!
As shown in Figure 1.2, “Apache Camel Security Architecture”, you have the following options for securing messages:
- Endpoint security—part (a) shows a message sent between two routes with secure endpoints. The producer endpoint on the left opens a secure connection (typically using SSL/TLS) to the consumer endpoint on the right. Both of the endpoints support security in this scenario.With endpoint security, it is typically possible to perform some form of peer authentication (and sometimes authorization).
- Payload security—part (b) shows a message sent between two routes where the endpoints are both insecure. To protect the message from unauthorized snooping in this case, use a payload processor that encrypts the message before sending and decrypts the message after it is received.A limitation of payload security is that it does not provide any kind of authentication or authorization mechanisms.
Endpoint security
Copier lienLien copié sur presse-papiers!
There are several Camel components that support security features. It is important to note, however, that these security features are implemented by the individual components, not by the Camel core. Hence, the kinds of security feature that are supported, and the details of their implementation, vary from component to component. Some of the Camel components that currently support security are, as follows:
- JMS and ActiveMQ—SSL/TLS security and JAAS security for client-to-broker and broker-to-broker communication.
- Jetty—HTTP Basic Authentication and SSL/TLS security.
- CXF—SSL/TLS security and WS-Security.
- Crypto—creates and verifies digital signatures in order to guarantee message integrity.
- Netty—SSL/TLS security.
- MINA—SSL/TLS security.
- Cometd—SSL/TLS security.
- glogin and gauth—authorization in the context of Google applications.
Payload security
Copier lienLien copié sur presse-papiers!
Apache Camel provides the following payload security implementations, where the encryption and decryption steps are exposed as data formats on the
marshal() and unmarshal() operations
XMLSecurity data format
Copier lienLien copié sur presse-papiers!
The XMLSecurity data format is specifically designed to encrypt XML payloads. When using this data format, you can specify which XML element to encrypt. The default behavior is to encrypt all XML elements. This feature uses a symmetric encryption algorithm.
For more details, see http://camel.apache.org/xmlsecurity-dataformat.html.
Crypto data format
Copier lienLien copié sur presse-papiers!
The crypto data format is a general purpose encryption feature that can encrypt any kind of payload. It is based on the Java Cryptographic Extension and implements only symmetric (shared-key) encryption and decryption.
For more details, see http://camel.apache.org/crypto.html.