Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 4. Red Hat Quay tenancy model
Before creating repositories to contain your container images in Quay.io, you should consider how these repositories will be structured. With Quay.io, each repository requires a connection with either an Organization or a User. This affiliation defines ownership and access control for the repositories.
4.1. Tenancy model

- Organizations provide a way of sharing repositories under a common namespace that does not belong to a single user. Instead, these repositories belong to several users in a shared setting, such as a company.
- Teams provide a way for an Organization to delegate permissions. Permissions can be set at the global level (for example, across all repositories), or on specific repositories. They can also be set for specific sets, or groups, of users.
-
Users can log in to a registry through the web UI or a by using a client like Podman and using their respective login commands, for example,
$ podman login. Each user automatically gets a user namespace, for example,<quay-server.example.com>/<user>/<username>, orquay.io/<username>if you are using Quay.io. - Robot accounts provide automated access to repositories for non-human users like pipeline tools. Robot accounts are similar to OpenShift Container Platform Service Accounts. Permissions can be granted to a robot account in a repository by adding that account like you would another user or team.
4.2. Logging into Quay
A user account for Quay.io represents an individual with authenticated access to the platform’s features and functionalities. Through this account, you gain the capability to create and manage repositories, upload and retrieve container images, and control access permissions for these resources. This account is pivotal for organizing and overseeing your container image management within Quay.io.
Not all features on Quay.io require that users be logged in. For example, you can anonymously pull an image from Quay.io without being logged in, so long as the image you are pulling comes from a public repository.
Users have two options for logging into Quay.io:
By logging in through Quay.io.
This option provides users with the legacy UI, as well as an option to use the beta UI environment, which adheres to PatternFly UI principles.
By logging in through the Red Hat Hybrid Cloud Console.
This option uses Red Hat SSO for authentication, and is a public managed service offering by Red Hat. This option always requires users to login. Like other managed services, Quay on the Red Hat Hybrid Cloud Console enhances the user experience by adhering to PatternFly UI principles.
Differences between using Quay.io directly and Quay on the Red Hat Hybrid Cloud Console are negligible, including for users on the free tier. Whether you are using Quay.io directly, on the Hybrid Cloud Console, features that require login, such as pushing to a repository, use your Quay.io username specifications.
4.2.1. Logging into Quay.io
Use the following procedure to log into Quay.io.
Prerequisites
- You have created a Red Hat account and a Quay.io account. For more information, see "Creating a Quay.io account".
Procedure
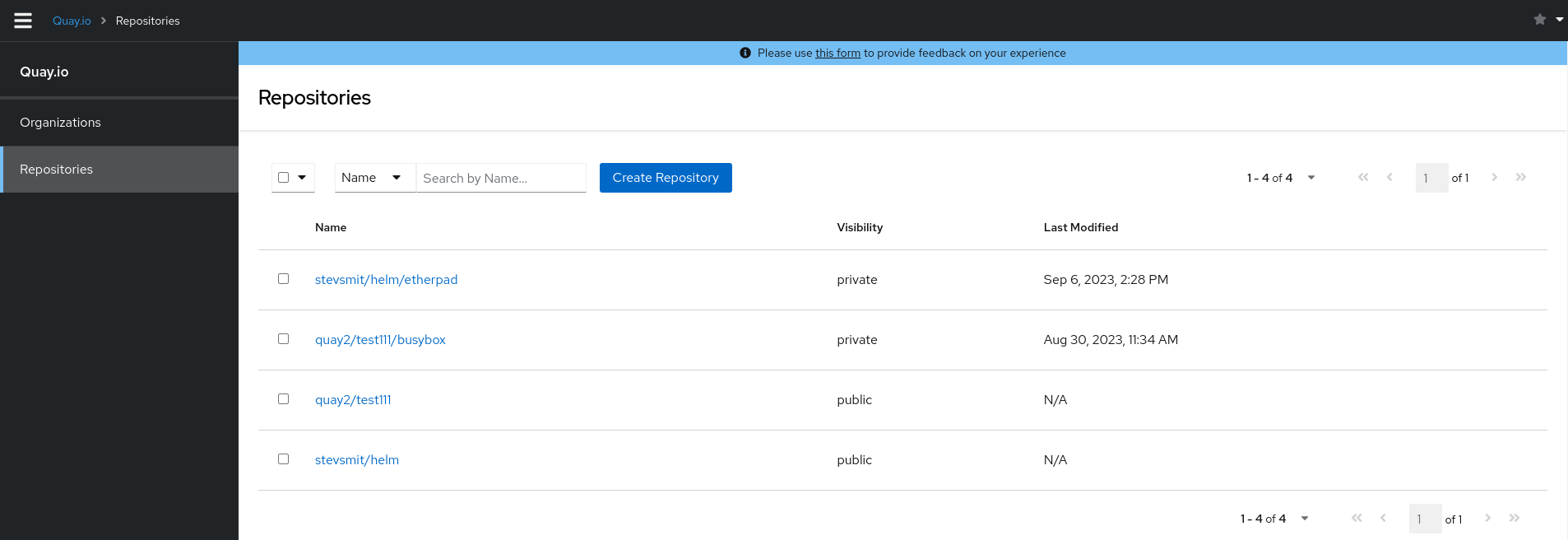
- Navigate to Quay.io.
- In the navigation pane, select Sign In and log in using your Red Hat credentials.
If it is your first time logging in, you must confirm the automatically-generated username. Click Confirm Username to log in.
You are redirected to the Quay.io repository landing page.
4.2.2. Logging into Quay through the Hybrid Cloud Console
Prerequisites
- You have created a Red Hat account and a Quay.io account. For more information, see "Creating a Quay.io account".
Procedure
Navigate to the Quay on the Red Hat Hybrid Cloud Console and log in using your Red Hat account. You are redirected to the Quay repository landing page: