Ce contenu n'est pas disponible dans la langue sélectionnée.
16.5. User Authorization
16.5.1. User Authorization Model
Copier lienLien copié sur presse-papiers!
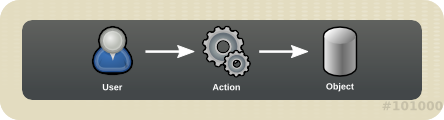
Red Hat Virtualization applies authorization controls based on the combination of the three components:
- The user performing the action
- The type of action being performed
- The object on which the action is being performed
16.5.2. User Actions
Copier lienLien copié sur presse-papiers!
For an action to be successfully performed, the
user must have the appropriate permission for the object being acted upon. Each type of action corresponds to a permission. There are many different permissions in the system, so for simplicity:
Figure 16.3. Actions
Important
Some actions are performed on more than one object. For example, copying a template to another storage domain will impact both the template and the destination storage domain. The user performing an action must have appropriate permissions for all objects the action impacts.