Questo contenuto non è disponibile nella lingua selezionata.
Chapter 3. Managing roles on the Ceph dashboard
As a storage administrator, you can create, edit, clone, and delete roles on the dashboard.
By default, there are eight system roles. You can create custom roles and give permissions to those roles. These roles can be assigned to users based on the requirements.
This section covers the following administrative tasks:
3.1. User roles and permissions on the Ceph dashboard
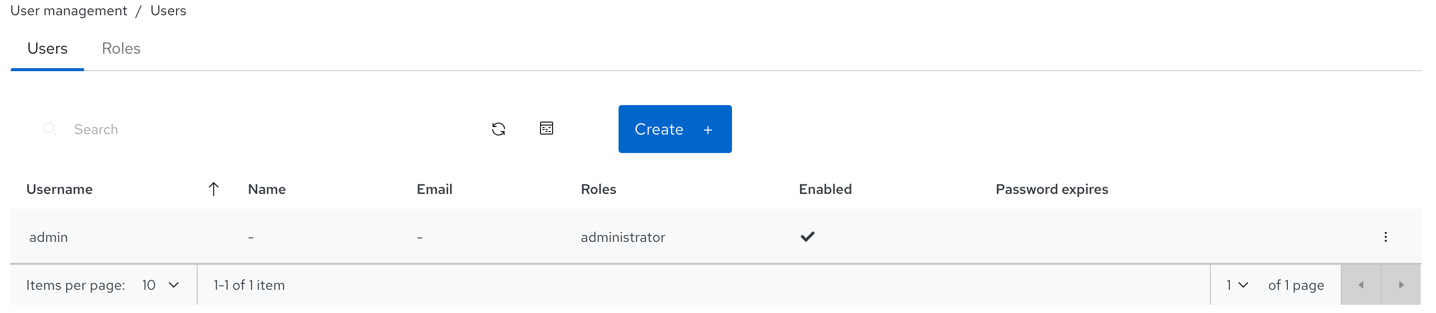
User accounts are associated with a set of roles that define the specific dashboard functionality which can be accessed. View user roles and permissions by going to Dashboard settings→User management.
The Red Hat Ceph Storage dashboard functionality or modules are grouped within a security scope. Security scopes are predefined and static. The current available security scopes on the Red Hat Ceph Storage dashboard are:
- cephfs: Includes all features related to CephFS management.
- config-opt: Includes all features related to management of Ceph configuration options.
- dashboard-settings: Allows to edit the dashboard settings.
- grafana: Include all features related to Grafana proxy.
- hosts: Includes all features related to the Hosts menu entry.
- log: Includes all features related to Ceph logs management.
- manager: Includes all features related to Ceph manager management.
- monitor: Includes all features related to Ceph monitor management.
- nfs-ganesha: Includes all features related to NFS-Ganesha management.
- osd: Includes all features related to OSD management.
- pool: Includes all features related to pool management.
- prometheus: Include all features related to Prometheus alert management.
- rbd-image: Includes all features related to RBD image management.
- rbd-mirroring: Includes all features related to RBD mirroring management.
- rgw: Includes all features related to Ceph object gateway (RGW) management.
A role specifies a set of mappings between a security scope and a set of permissions. There are four types of permissions:
- Read
- Create
- Update
- Delete
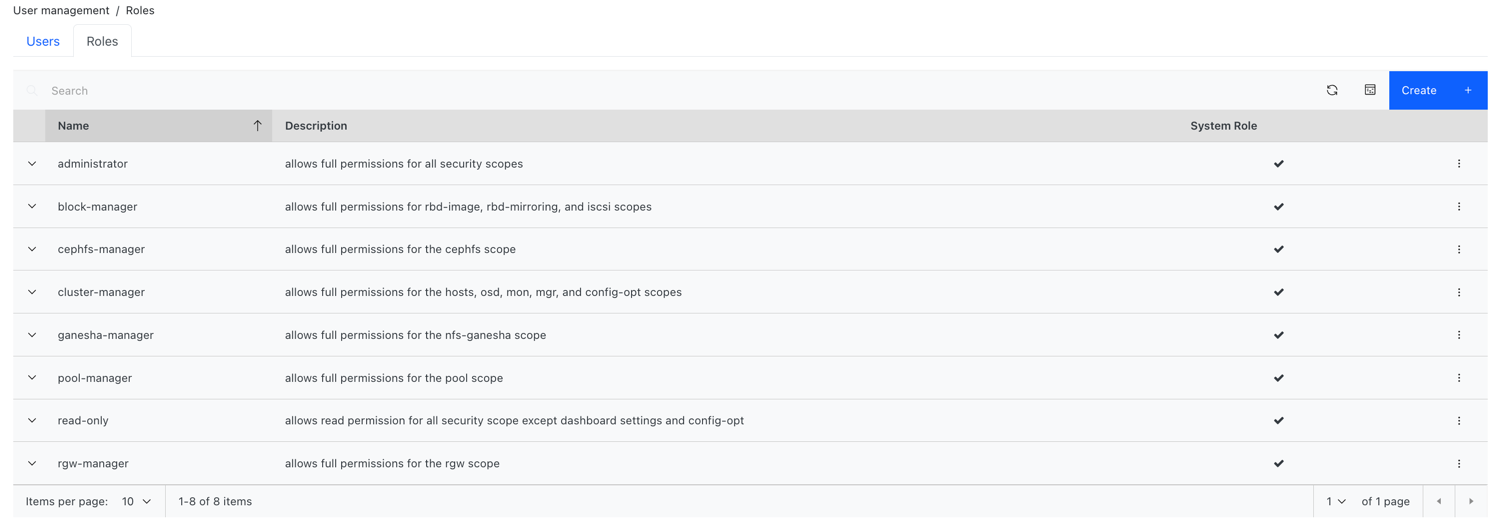
The list of system roles are:
- administrator: Allows full permissions for all security scopes.
- block-manager: Allows full permissions for RBD-image and RBD-mirroring scopes.
- cephfs-manager: Allows full permissions for the Ceph file system scope.
- cluster-manager: Allows full permissions for the hosts, OSDs, monitor, manager, and config-opt scopes.
- ganesha-manager: Allows full permissions for the NFS-Ganesha scope.
- pool-manager: Allows full permissions for the pool scope.
- read-only: Allows read permission for all security scopes except the dashboard settings and config-opt scopes.
- rgw-manager: Allows full permissions for the Ceph object gateway scope.
For example, you need to provide rgw-manager access to the users for all Ceph object gateway operations.
3.2. Creating roles on the Ceph dashboard
You can create custom roles on the dashboard and these roles can be assigned to users based on their roles.
Prerequisites
- A running Red Hat Ceph Storage cluster.
- Dashboard is installed.
- Admin-level access to the dashboard.
Procedure
- Log in to the Dashboard.
Click the Dashboard Settings icon and then click User management.
- On Roles tab, click Create.
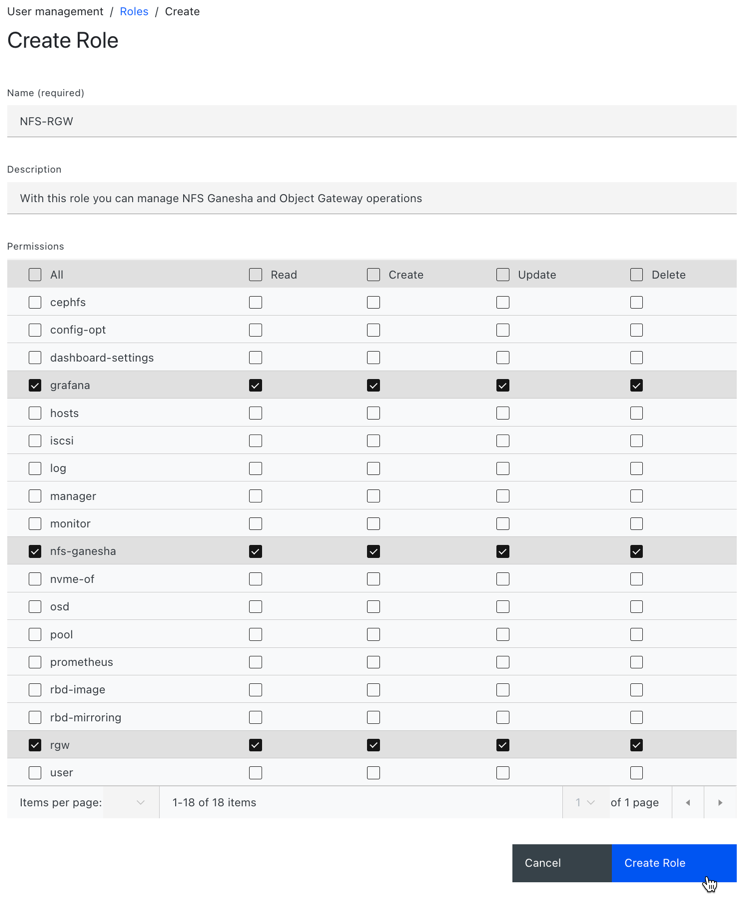
In the Create Role window, set the Name, Description, and select the Permissions for this role, and then click the Create Role button.
In this example, the user assigned with
ganesha-managerandrgw-managerroles can manage all NFS-Ganesha gateway and Ceph object gateway operations.- You get a notification that the role was created successfully.
- Click on the Expand/Collapse icon of the row to view the details and permissions given to the roles.
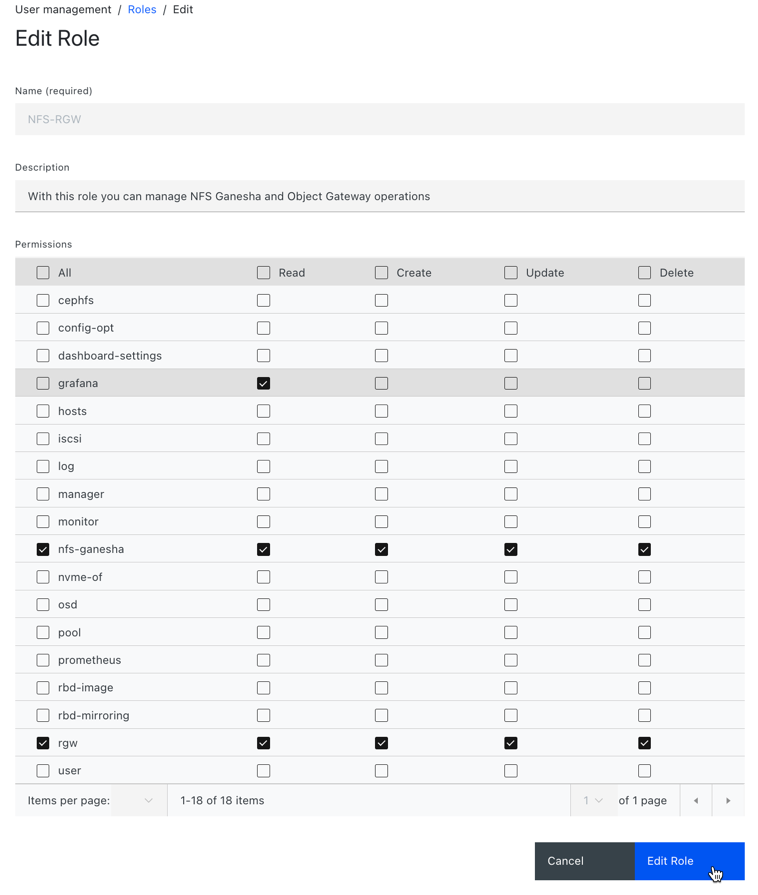
3.3. Editing roles on the Ceph dashboard
The dashboard allows you to edit roles on the dashboard.
Prerequisites
- A running Red Hat Ceph Storage cluster.
- Dashboard is installed.
- Admin-level access to the dashboard.
- A role is created on the dashboard.
Procedure
- Log in to the Dashboard.
Click the Dashboard Settings icon and then click User management.
- On Roles tab, click the role you want to edit.
In the Edit Role window, edit the parameters, and then click Edit Role.
- You get a notification that the role was updated successfully.
3.4. Cloning roles on the Ceph dashboard
When you want to assign additional permissions to existing roles, you can clone the system roles and edit it on the Red Hat Ceph Storage Dashboard.
Prerequisites
- A running Red Hat Ceph Storage cluster.
- Dashboard is installed.
- Admin-level access to the dashboard.
- Roles are created on the dashboard.
Procedure
- Log in to the Dashboard.
Click the Dashboard Settings icon and then click User management.
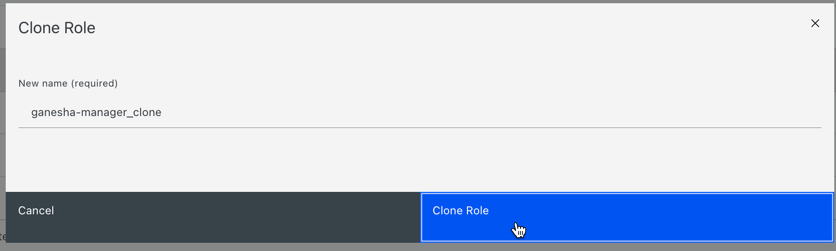
- On Roles tab, click the role you want to clone.
- Select Clone from the Edit drop-down menu.
In the Clone Role dialog box, enter the details for the role, and then click Clone Role.
- Once you clone the role, you can customize the permissions as per the requirements.
3.5. Deleting roles on the Ceph dashboard
You can delete the custom roles that you have created on the Red Hat Ceph Storage dashboard.
You cannot delete the system roles of the Ceph Dashboard.
Prerequisites
- A running Red Hat Ceph Storage cluster.
- Dashboard is installed.
- Admin-level access to the dashboard.
- A custom role is created on the dashboard.
Procedure
- Log in to the Dashboard.
Click the Dashboard Settings icon and then select User management.
- On the Roles tab, click the role you want to delete and select Delete from the action drop-down.
- In the Delete Role notification, select Yes, I am sure and click Delete Role.