Questo contenuto non è disponibile nella lingua selezionata.
4.3. Configuring Kerberos (with LDAP or NIS) Using authconfig
Both LDAP and NIS authentication stores support Kerberos authentication methods. Using Kerberos has a couple of benefits:
- It uses a security layer for communication while still allowing connections over standard ports.
- It automatically uses credentials caching with SSSD, which allows offline logins.
Note
Using Kerberos authentication requires the
krb5-libs and krb5-workstation packages.
4.3.1. Configuring Kerberos Authentication from the UI
Copia collegamentoCollegamento copiato negli appunti!
The option from the Authentication Method drop-down menu automatically opens the fields required to connect to the Kerberos realm.
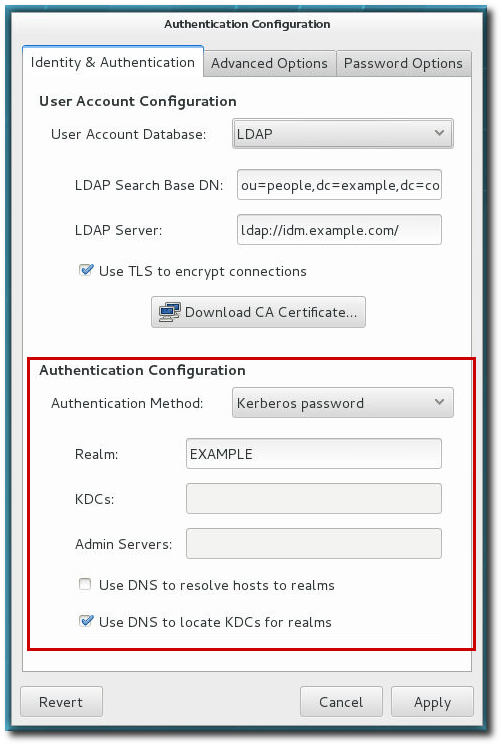
Figure 4.2. Kerberos Fields
- Realm gives the name for the realm for the Kerberos server. The realm is the network that uses Kerberos, composed of one or more key distribution centers (KDC) and a potentially large number of clients.
- KDCs gives a comma-separated list of servers that issue Kerberos tickets.
- Admin Servers gives a list of administration servers running the
kadmindprocess in the realm. - Optionally, use DNS to resolve server host name and to find additional KDCs within the realm.
4.3.2. Configuring Kerberos Authentication from the Command Line
Copia collegamentoCollegamento copiato negli appunti!
Both LDAP and NIS allow Kerberos authentication to be used in place of their native authentication mechanisms. At a minimum, using Kerberos authentication requires specifying the realm, the KDC, and the administrative server. There are also options to use DNS to resolve client names and to find additional admin servers.
authconfig NIS or LDAP options --enablekrb5 --krb5realm EXAMPLE --krb5kdc kdc.example.com:88,server.example.com:88 --krb5adminserver server.example.com:749 --enablekrb5kdcdns --enablekrb5realmdns --update
[root@server ~]# authconfig NIS or LDAP options --enablekrb5 --krb5realm EXAMPLE --krb5kdc kdc.example.com:88,server.example.com:88 --krb5adminserver server.example.com:749 --enablekrb5kdcdns --enablekrb5realmdns --update