Questo contenuto non è disponibile nella lingua selezionata.
6.2. About Active Directory and Identity Management
Within the IdM domain, information is shared among servers and replicas by copying that information, reliably and predictably, between data masters (servers and replicas). This process is replication.
A similar process can be used to share data between the IdM domain and a Microsoft Active Directory domain. This is synchronization.
Synchronization is the process of copying user data back and forth between Active Directory and Identity Management. When users are synchronized between Active Directory and Identity Management, the directory synchronization (DirSync) LDAP server extension control is used to search a directory for objects that have changed.
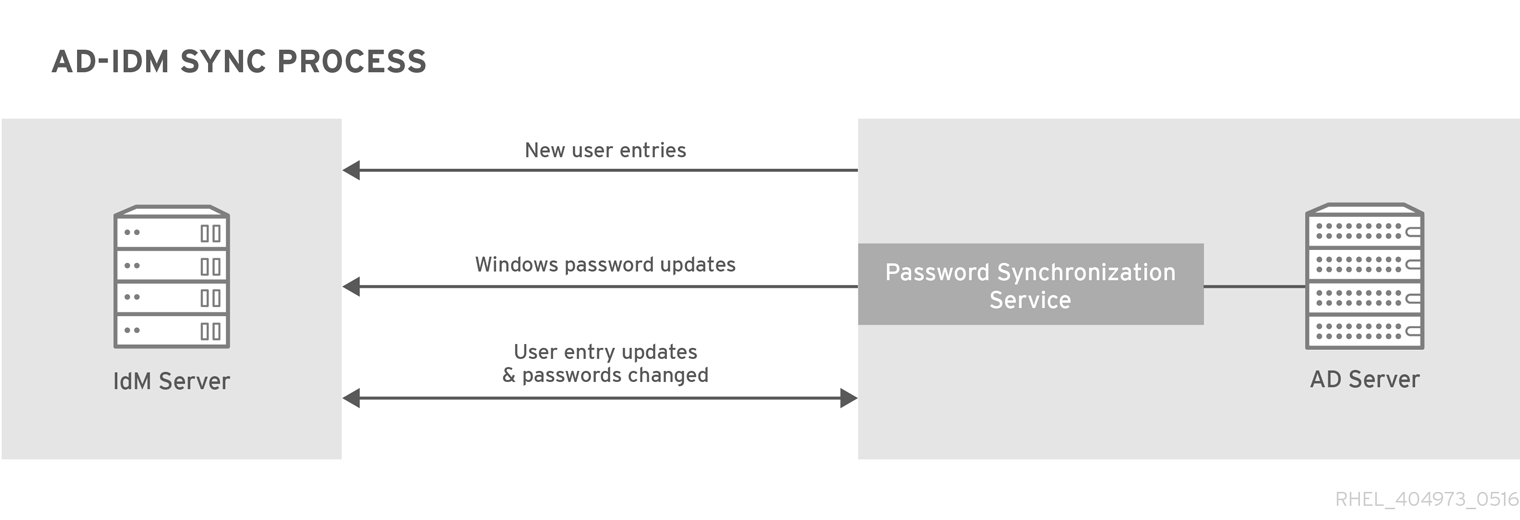
Figure 6.1. Active Directory and IdM Synchronization
Synchronization is defined in an agreement between an IdM server and an Active Directory domain controller. The agreement defines all of the information required to identify user entries that can be synchronized, such as the subtree to synchronize, as well as defining how account attributes are handled. The synchronization agreements are created with default values which can be tweaked to meet the needs of a specific domain. When two servers are involved in synchronization, they are called peers.
| Windows Information | IdM Information |
|---|---|
|
|
Synchronization is most commonly bidirectional. Information is sent back and forth between the IdM and the Windows domain in a process that is very similar to how IdM servers and replicas share information among themselves. An exception are new user entries, which are only added from the Windows domain to the IdM domain. It is possible to configure synchronization to only synchronize one way. That is unidirectional synchronization.
To prevent the risk of data conflicts, only one directory should originate or remove user entries. This is typically the Windows directory, which is the primary identity store in the IT environment, and then new accounts or account deletions are synchronized to the Identity Management peer. Either directory can modify entries.
Synchronization, then, is configured between one Identity Management server and one Active Directory domain controller. The Identity Management server propagates throughout to the IdM domain, while the domain controller propagates changes throughout the Windows domain.
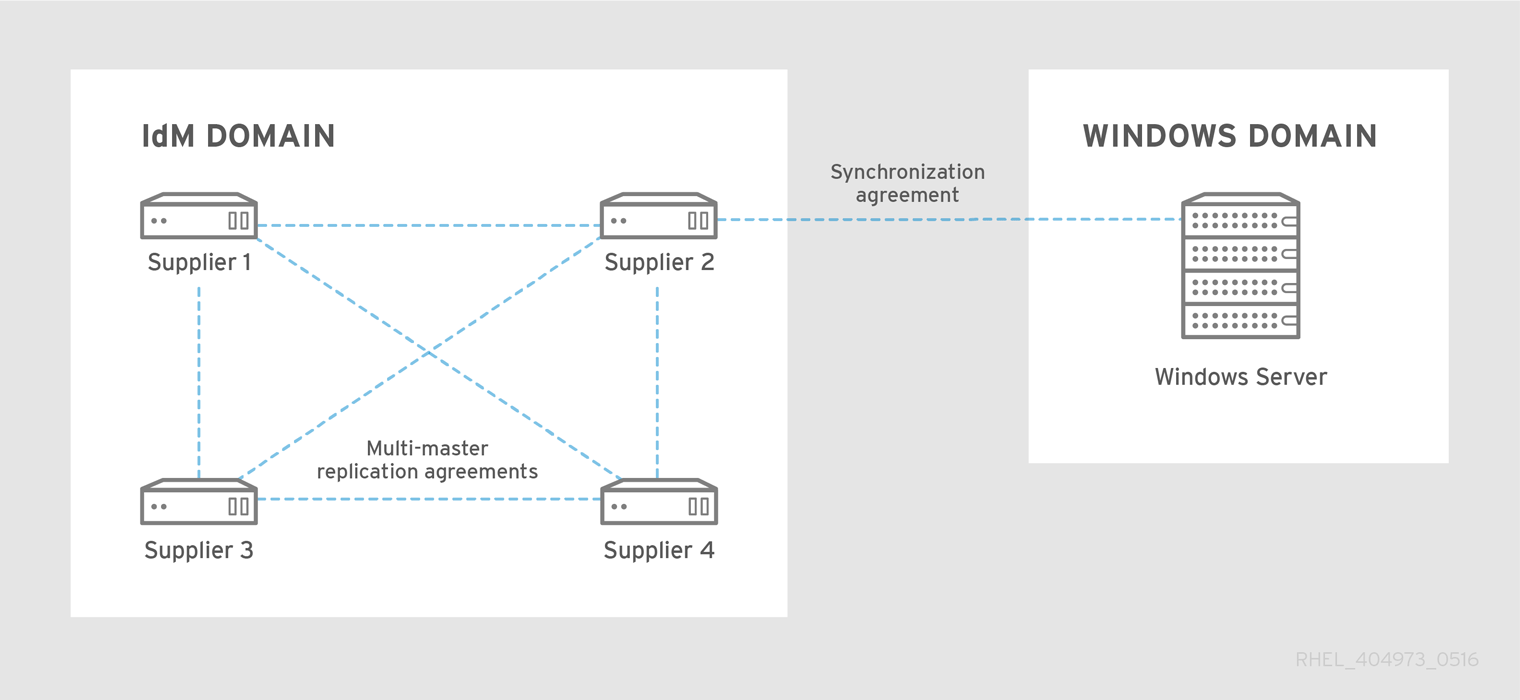
Figure 6.2. Synchronization Topology
There are some key features to IdM synchronization:
- A synchronization operation runs every five minutes. To modify the frequency, set the
winSyncIntervalattribute in the Active Directory peers DN:cn=meTowinserver.ad.example.com,cn=replica,cn=dc\3Didm\,dc\3Dexample\,dc\3Dcom,cn=mapping tree,cn=config
cn=meTowinserver.ad.example.com,cn=replica,cn=dc\3Didm\,dc\3Dexample\,dc\3Dcom,cn=mapping tree,cn=configCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Synchronization can only be configured with one Active Directory domain.
- Synchronization can only be configured with one Active Directory domain controller.
- Only user information is synchronized; group information is not.
- Both user attributes and passwords can be synchronized.
- While modifications are bidirectional (going both from Active Directory to IdM and from IdM to Active Directory), creating accounts is only unidirectional, from Active Directory to Identity Management. New accounts created in Active Directory are synchronized over to IdM automatically. However, user accounts created in IdM must also be created in Active Directory before they will be synchronized. In this situation, the synchronization process tries to find a matching account with the same value for the
uidattribute in IdM than for thesAMAccountNameattribute in Active Directory. If a match is found, the IdMntUserDomainIdattribute is set to the Active DirectoryobjectGUIDvalue. These attributes are globally unique and immutable, and entries stay synchronized, even if they are moved or renamed. - Account lock information is synchronized by default, so a user account which is disabled in one domain is disabled in the other.
- Password synchronization changes take effect immediately. If a user password is added or changed on one peer, that change is immediately propagated to the other peer server.The Password Synchronization client synchronizes new passwords or password updates.Existing passwords, which are stored in a hashed form in both IdM and Active Directory, cannot be decrypted or synchronized when the Password Synchronization client is installed, so existing passwords are not synchronized. User passwords must be changed to initiate synchronization between the peer servers.
- While there can only be one agreement, the PassSync service must be installed on every Active Directory server.
When Active Directory users are synchronized over to IdM, certain attributes (including Kerberos and POSIX attributes) will have IPA attributes automatically added to the user entries. These attributes are used by IdM within its domain. They are not synchronized back over the corresponding Active Directory user entry.
Some of the data in synchronization can be modified as part of the synchronization process. For examples, certain attributes can be automatically added to Active Directory user accounts when they are synced over to the IdM domain. These attribute changes are defined as part of the synchronization agreement and are described in Section 6.5.2, “Changing the Behavior for Synchronizing User Account Attributes”.