Questo contenuto non è disponibile nella lingua selezionata.
Chapter 7. Ensuring system integrity with Keylime
With Keylime, you can continuously monitor the integrity of remote systems and verify the state of systems at boot. You can also send encrypted files to the monitored systems, and specify automated actions triggered whenever a monitored system fails the integrity test.
7.1. How Keylime works
You can configure Keylime agents to perform one or more of the following actions:
- Runtime integrity monitoring
- Keylime runtime integrity monitoring continuously monitors the system on which the agent is deployed and measures the integrity of the files included in the allowlist and not included in the excludelist.
- Measured boot
- Keylime measured boot verifies the system state at boot.
Keylime’s concept of trust is based on the Trusted Platform Module (TPM) technology. A TPM is a hardware, firmware, or virtual component with integrated cryptographic keys. By polling TPM quotes and comparing the hashes of objects, Keylime provides initial and runtime monitoring of remote systems.
Keylime running in a virtual machine or using a virtual TPM depends upon the integrity of the underlying host. Ensure you trust the host environment before relying upon Keylime measurements in a virtual environment.
Keylime consists of three main components:
- Verifier
-
Initially and continuously verifies the integrity of the systems that run the agent. You can deploy the verifier from a package, as a container, or by using the
keylime_serverRHEL system role. - Registrar
-
Contains a database of all agents and it hosts the public keys of the TPM vendors. You can deploy the registrar from a package, as a container, or by using the
keylime_serverRHEL system role. - Agent
- Deployed to remote systems measured by the verifier.
In addition, Keylime uses the keylime_tenant utility for many functions, including provisioning the agents on the target systems.
Figure 7.1. Connections between Keylime components through configurations
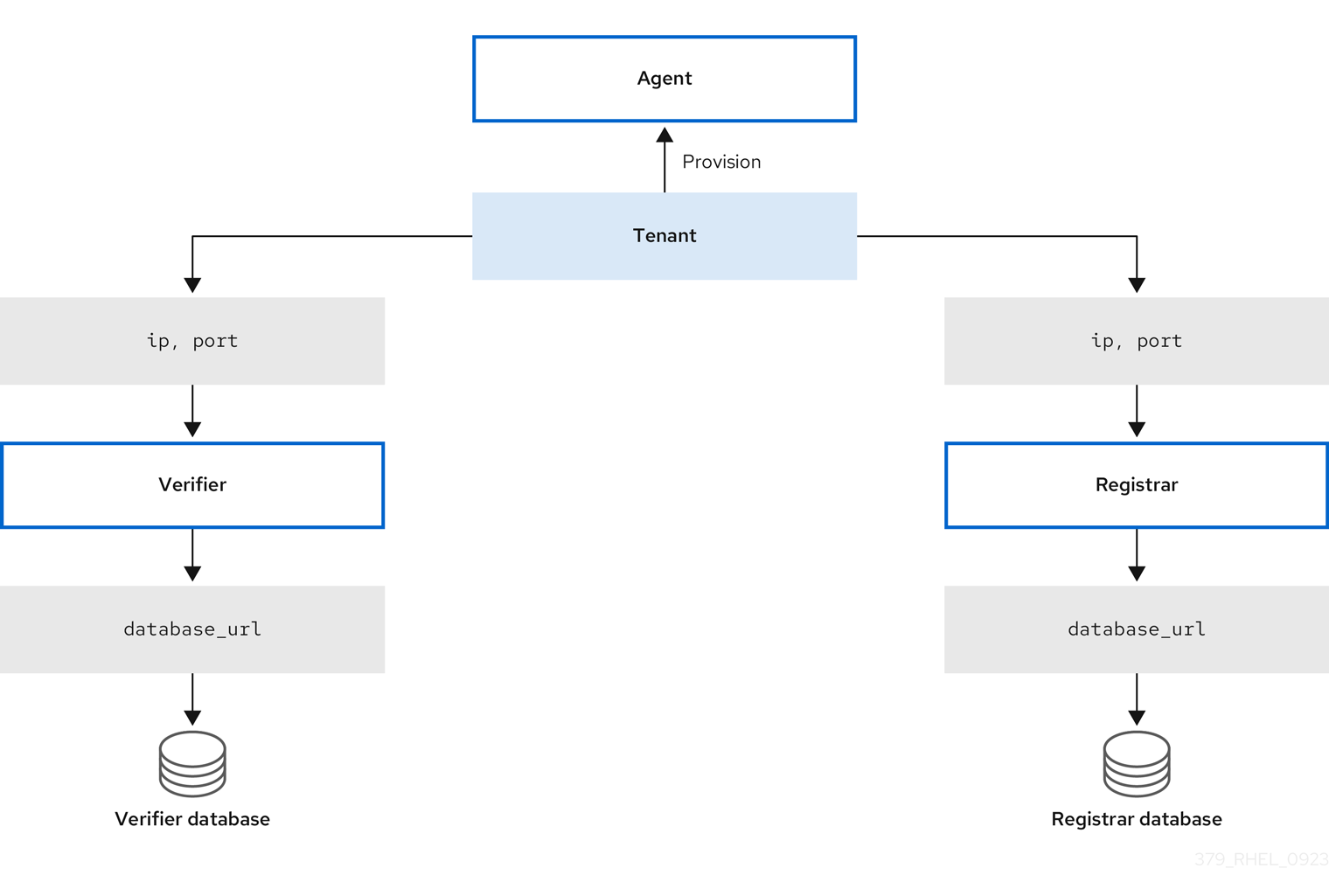
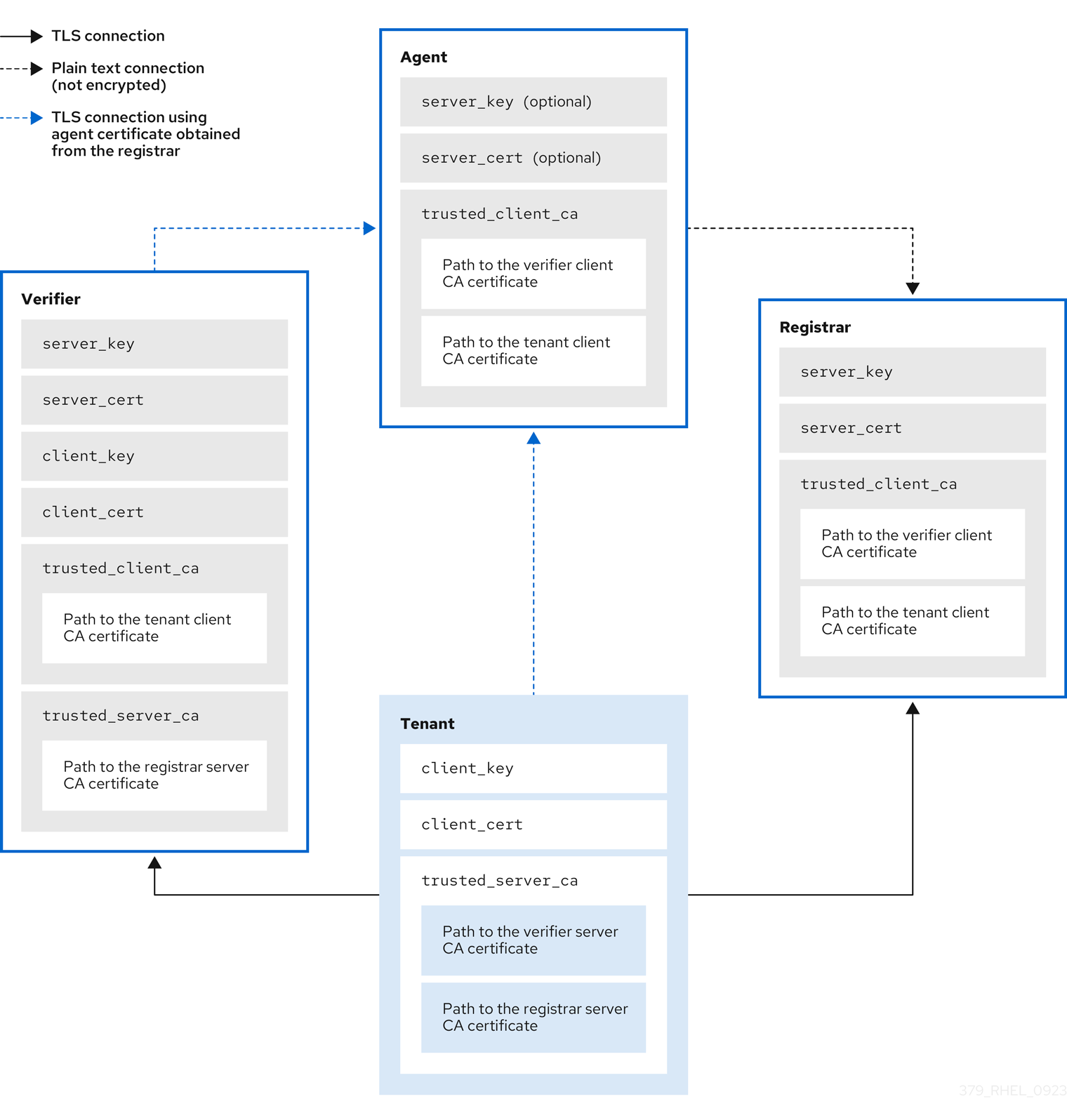
Keylime ensures the integrity of the monitored systems in a chain of trust by using keys and certificates exchanged between the components and the tenant. For a secure foundation of this chain, use a certificate authority (CA) that you can trust.
If the agent receives no key and certificate, it generates a key and a self-signed certificate with no involvement from the CA.
Figure 7.2. Connections between Keylime components certificates and keys
7.2. Deploying Keylime verifier from a package
The verifier is the most important component in Keylime. It performs initial and periodic checks of system integrity and supports bootstrapping a cryptographic key securely with the agent. The verifier uses mutual TLS encryption for its control interface.
To maintain the chain of trust, keep the system that runs the verifier secure and under your control.
You can install the verifier on a separate system or on the same system as the Keylime registrar, depending on your requirements. Running the verifier and registrar on separate systems provides better performance.
To keep the configuration files organized within the drop-in directories, use file names with a two-digit number prefix, for example /etc/keylime/verifier.conf.d/00-verifier-ip.conf. The configuration processing reads the files inside the drop-in directory in lexicographic order and sets each option to the last value it reads.
Prerequisites
-
You have
rootpermissions and network connection to the system or systems on which you want to install Keylime components. - You have valid keys and certificates from your certificate authority.
Optional: You have access to the databases where Keylime saves data from the verifier. You can use any of the following database management systems:
- SQLite (default)
- PostgreSQL
- MySQL
- MariaDB
Procedure
Install the Keylime verifier:
dnf install keylime-verifier
# dnf install keylime-verifierCopy to Clipboard Copied! Toggle word wrap Toggle overflow Define the IP address and port of verifier by creating a new
.conffile in the/etc/keylime/verifier.conf.d/directory, for example,/etc/keylime/verifier.conf.d/00-verifier-ip.conf, with the following content:[verifier] ip = <verifier_IP_address>
[verifier] ip = <verifier_IP_address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<verifier_IP_address>with the verifier’s IP address. Alternatively, useip = *orip = 0.0.0.0to bind the verifier to all available IP addresses. -
Optionally, you can also change the verifier’s port from the default value
8881by using theportoption.
-
Replace
Optional: Configure the verifier’s database for the list of agents. The default configuration uses an SQLite database in the verifier’s
/var/lib/keylime/cv_data.sqlite/directory. You can define a different database by creating a new.conffile in the/etc/keylime/verifier.conf.d/directory, for example,/etc/keylime/verifier.conf.d/00-db-url.conf, with the following content:[verifier] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>
[verifier] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>with the URL of the database, for example,postgresql://verifier:UQ?nRNY9g7GZzN7@198.51.100.1/verifierdb.Ensure that the credentials you use provide the permissions for Keylime to create the database structure.
Add certificates and keys to the verifier. You can either let Keylime generate them, or use existing keys and certificates:
-
With the default
tls_dir = generateoption, Keylime generates new certificates for the verifier, registrar, and tenant in the/var/lib/keylime/cv_ca/directory. To load existing keys and certificates in the configuration, define their location in the verifier configuration. The certificates must be accessible by the
keylimeuser, under which the Keylime services are running.Create a new
.conffile in the/etc/keylime/verifier.conf.d/directory, for example,/etc/keylime/verifier.conf.d/00-keys-and-certs.conf, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse absolute paths to define key and certificate locations. Alternatively, relative paths are resolved from the directory defined in the
tls_diroption.
-
With the default
Open the port in firewall:
firewall-cmd --add-port 8881/tcp firewall-cmd --runtime-to-permanent
# firewall-cmd --add-port 8881/tcp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use a different port, replace
8881with the port number defined in the.conffile.Start the verifier service:
systemctl enable --now keylime_verifier
# systemctl enable --now keylime_verifierCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIn the default configuration, start the
keylime_verifierbefore starting thekeylime_registrarservice because the verifier creates the CA and certificates for the other Keylime components. This order is not necessary when you use custom certificates.
Verification
Check that the
keylime_verifierservice is active and running:systemctl status keylime_verifier ● keylime_verifier.service - The Keylime verifier Loaded: loaded (/usr/lib/systemd/system/keylime_verifier.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:08 EST; 1min 45s ago# systemctl status keylime_verifier ● keylime_verifier.service - The Keylime verifier Loaded: loaded (/usr/lib/systemd/system/keylime_verifier.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:08 EST; 1min 45s agoCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.3. Deploying Keylime verifier as a container
The Keylime verifier performs initial and periodic checks of system integrity and supports bootstrapping a cryptographic key securely with the agent. You can configure the Keylime verifier as a container instead of the RPM method, without any binaries or packages on the host. The container deployment provides better isolation, modularity, and reproducibility of Keylime components.
After you start the container, the Keylime verifier is deployed with default configuration files. You can customize the configuration by using one or more of following methods:
- Mounting the host’s directories that contain the configuration files to the container. This is available in all versions of RHEL 9.
- Modifying the environment variables directly on the container. This is available in RHEL 9.3 and later versions. Modifying the environment variables overrides the values from the configuration files.
Prerequisites
-
The
podmanpackage and its dependencies are installed on the system. Optional: You have access to a database where Keylime saves data from the verifier. You can use any of the following database management systems:
- SQLite (default)
- PostgreSQL
- MySQL
- MariaDB
- You have valid keys and certificates from your certificate authority.
Procedure
Optional: Install the
keylime-verifierpackage to access the configuration files. You can configure the container without this package, but it might be easier to modify the configuration files provided with the package.dnf install keylime-verifier
# dnf install keylime-verifierCopy to Clipboard Copied! Toggle word wrap Toggle overflow Bind the verifier to all available IP addresses by creating a new
.conffile in the/etc/keylime/verifier.conf.d/directory, for example,/etc/keylime/verifier.conf.d/00-verifier-ip.conf, with the following content:[verifier] ip = *
[verifier] ip = *Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Optionally, you can also change the verifier’s port from the default value
8881by using theportoption.
-
Optionally, you can also change the verifier’s port from the default value
Optional: Configure the verifier’s database for the list of agents. The default configuration uses an SQLite database in the verifier’s
/var/lib/keylime/cv_data.sqlite/directory. You can define a different database by creating a new.conffile in the/etc/keylime/verifier.conf.d/directory, for example,/etc/keylime/verifier.conf.d/00-db-url.conf, with the following content:[verifier] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>
[verifier] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>with the URL of the database, for example,postgresql://verifier:UQ?nRNY9g7GZzN7@198.51.100.1/verifierdb.Ensure that the credentials you use have the permissions for Keylime to create the database structure.
Add certificates and keys to the verifier. You can either let Keylime generate them, or use existing keys and certificates:
-
With the default
tls_dir = generateoption, Keylime generates new certificates for the verifier, registrar, and tenant in the/var/lib/keylime/cv_ca/directory. To load existing keys and certificates in the configuration, define their location in the verifier configuration. The certificates must be accessible by the
keylimeuser, under which the Keylime processes are running.Create a new
.conffile in the/etc/keylime/verifier.conf.d/directory, for example,/etc/keylime/verifier.conf.d/00-keys-and-certs.conf, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse absolute paths to define key and certificate locations. Alternatively, relative paths are resolved from the directory defined in the
tls_diroption.
-
With the default
Open the port in firewall:
firewall-cmd --add-port 8881/tcp firewall-cmd --runtime-to-permanent
# firewall-cmd --add-port 8881/tcp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use a different port, replace
8881with the port number defined in the.conffile.Run the container:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
-poption opens the default port8881on the host and on the container. The
-voption creates a bind mount for the directory to the container.-
With the
Zoption, Podman marks the content with a private unshared label. This means only the current container can use the private volume.
-
With the
-
The
-doption runs the container detached and in the background. -
The option
-e KEYLIME_VERIFIER_SERVER_KEY_PASSWORD=<passphrase1>defines the server key passphrase. -
The option
-e KEYLIME_VERIFIER_CLIENT_KEY_PASSWORD=<passphrase2>defines the client key passphrase. -
You can override configuration options with environment variables by using the option
-e KEYLIME_VERIFIER_<ENVIRONMENT_VARIABLE>=<value>. To modify additional options, insert the-eoption separately for each environment variable. For a complete list of environment variables and their default values, see Keylime environment variables.
-
The
Verification
Check that the container is running:
podman ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 80b6b9dbf57c registry.access.redhat.com/rhel9/keylime-verifier:latest keylime_verifier 14 seconds ago Up 14 seconds 0.0.0.0:8881->8881/tcp keylime-verifier
$ podman ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 80b6b9dbf57c registry.access.redhat.com/rhel9/keylime-verifier:latest keylime_verifier 14 seconds ago Up 14 seconds 0.0.0.0:8881->8881/tcp keylime-verifierCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
7.4. Deploying Keylime registrar from a package
The registrar is the Keylime component that contains a database of all agents, and it hosts the public keys of the TPM vendors. After the registrar’s HTTPS service accepts trusted platform module (TPM) public keys, it presents an interface to obtain these public keys for checking quotes.
To maintain the chain of trust, keep the system that runs the registrar secure and under your control.
You can install the registrar on a separate system or on the same system as the Keylime verifier, depending on your requirements. Running the verifier and registrar on separate systems provides better performance.
To keep the configuration files organized within the drop-in directories, use file names with a two-digit number prefix, for example /etc/keylime/registrar.conf.d/00-registrar-ip.conf. The configuration processing reads the files inside the drop-in directory in lexicographic order and sets each option to the last value it reads.
Prerequisites
- You have network access to the systems where the Keylime verifier is installed and running. For more information, see Section 7.2, “Deploying Keylime verifier from a package”.
-
You have
rootpermissions and network connection to the system or systems on which you want to install Keylime components. You have access to the database where Keylime saves data from the registrar. You can use any of the following database management systems:
- SQLite (default)
- PostgreSQL
- MySQL
- MariaDB
- You have valid keys and certificates from your certificate authority.
Procedure
Install the Keylime registrar:
dnf install keylime-registrar
# dnf install keylime-registrarCopy to Clipboard Copied! Toggle word wrap Toggle overflow Define the IP address and port of the registrar by creating a new
.conffile in the/etc/keylime/registrar.conf.d/directory, for example,/etc/keylime/registrar.conf.d/00-registrar-ip.conf, with the following content:[registrar] ip = <registrar_IP_address>
[registrar] ip = <registrar_IP_address>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<registrar_IP_address>with the registrar’s IP address. Alternatively, useip = *orip = 0.0.0.0to bind the registrar to all available IP addresses. -
Optionally, change the port to which the Keylime agents connect by using the
portoption. The default value is8890. -
Optionally, change the TLS port to which the Keylime verifier and tenant connect by using the
tls_portoption. The default value is8891.
-
Replace
Optional: Configure the registrar’s database for the list of agents. The default configuration uses an SQLite database in the registrar’s
/var/lib/keylime/reg_data.sqlitedirectory. You can create a new.conffile in the/etc/keylime/registrar.conf.d/directory, for example,/etc/keylime/registrar.conf.d/00-db-url.conf, with the following content:[registrar] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>
[registrar] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>with the URL of the database, for example,postgresql://registrar:EKYYX-bqY2?#raXm@198.51.100.1/registrardb.Ensure that the credentials you use have the permissions for Keylime to create the database structure.
Add certificates and keys to the registrar:
-
You can use the default configuration and load the keys and certificates to the
/var/lib/keylime/reg_ca/directory. Alternatively, you can define the location of the keys and certificates in the configuration. Create a new
.conffile in the/etc/keylime/registrar.conf.d/directory, for example,/etc/keylime/registrar.conf.d/00-keys-and-certs.conf, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse absolute paths to define key and certificate locations. Alternatively, you can define a directory in the
tls_diroption and use paths relative to that directory.
-
You can use the default configuration and load the keys and certificates to the
Open the ports in firewall:
firewall-cmd --add-port 8890/tcp --add-port 8891/tcp firewall-cmd --runtime-to-permanent
# firewall-cmd --add-port 8890/tcp --add-port 8891/tcp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use a different port, replace
8890or8891with the port number defined in the.conffile.Start the
keylime_registrarservice:systemctl enable --now keylime_registrar
# systemctl enable --now keylime_registrarCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIn the default configuration, start the
keylime_verifierbefore starting thekeylime_registrarservice because the verifier creates the CA and certificates for the other Keylime components. This order is not necessary when you use custom certificates.
Verification
Check that the
keylime_registrarservice is active and running:systemctl status keylime_registrar ● keylime_registrar.service - The Keylime registrar service Loaded: loaded (/usr/lib/systemd/system/keylime_registrar.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:17 EST; 1min 42s ago ...# systemctl status keylime_registrar ● keylime_registrar.service - The Keylime registrar service Loaded: loaded (/usr/lib/systemd/system/keylime_registrar.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:17 EST; 1min 42s ago ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.5. Deploying Keylime registrar as a container
The registrar is the Keylime component that contains a database of all agents, and it hosts the public keys of the trusted platform module (TPM) vendors. After the registrar’s HTTPS service accepts TPM public keys, it presents an interface to obtain these public keys for checking quotes. You can configure the Keylime registrar as a container instead of the RPM method, without any binaries or packages on the host. The container deployment provides better isolation, modularity, and reproducibility of Keylime components.
After you start the container, the Keylime registrar is deployed with default configuration files. You can customize the configuration by using one or more of following methods:
- Mounting the host’s directories that contain the configuration files to the container. This is available in all versions of RHEL 9.
- Modifying the environment variables directly on the container. This is available in RHEL 9.3 and later versions. Modifying the environment variables overrides the values from the configuration files.
Prerequisites
-
The
podmanpackage and its dependencies are installed on the system. Optional: You have access to a database where Keylime saves data from the registrar. You can use any of the following database management systems:
- SQLite (default)
- PostgreSQL
- MySQL
- MariaDB
- You have valid keys and certificates from your certificate authority.
Procedure
Optional: Install the
keylime-registrarpackage to access the configuration files. You can configure the container without this package, but it might be easier to modify the configuration files provided with the package.dnf install keylime-registrar
# dnf install keylime-registrarCopy to Clipboard Copied! Toggle word wrap Toggle overflow Bind the registrar to all available IP addresses by creating a new
.conffile in the/etc/keylime/registrar.conf.d/directory, for example,/etc/keylime/registrar.conf.d/00-registrar-ip.conf, with the following content:[registrar] ip = *
[registrar] ip = *Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Optionally, change the port to which the Keylime agents connect by using the
portoption. The default value is8890. -
Optionally, change the TLS port to which the Keylime tenant connects by using the
tls_portoption. The default value is8891.
-
Optionally, change the port to which the Keylime agents connect by using the
Optional: Configure the registrar’s database for the list of agents. The default configuration uses an SQLite database in the registrar’s
/var/lib/keylime/reg_data.sqlitedirectory. You can create a new.conffile in the/etc/keylime/registrar.conf.d/directory, for example,/etc/keylime/registrar.conf.d/00-db-url.conf, with the following content:[registrar] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>
[registrar] database_url = <protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<protocol>://<name>:<password>@<ip_address_or_hostname>/<properties>with the URL of the database, for example,postgresql://registrar:EKYYX-bqY2?#raXm@198.51.100.1/registrardb.Ensure that the credentials you use have the permissions for Keylime to create the database structure.
Add certificates and keys to the registrar:
-
You can use the default configuration and load the keys and certificates to the
/var/lib/keylime/reg_ca/directory. Alternatively, you can define the location of the keys and certificates in the configuration. Create a new
.conffile in the/etc/keylime/registrar.conf.d/directory, for example,/etc/keylime/registrar.conf.d/00-keys-and-certs.conf, with the following content:[registrar] tls_dir = /var/lib/keylime/reg_ca server_key = </path/to/server_key> server_cert = </path/to/server_cert> trusted_client_ca = ['</path/to/ca/cert1>', '</path/to/ca/cert2>']
[registrar] tls_dir = /var/lib/keylime/reg_ca server_key = </path/to/server_key> server_cert = </path/to/server_cert> trusted_client_ca = ['</path/to/ca/cert1>', '</path/to/ca/cert2>']Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse absolute paths to define key and certificate locations. Alternatively, you can define a directory in the
tls_diroption and use paths relative to that directory.
-
You can use the default configuration and load the keys and certificates to the
Open the ports in firewall:
firewall-cmd --add-port 8890/tcp --add-port 8891/tcp firewall-cmd --runtime-to-permanent
# firewall-cmd --add-port 8890/tcp --add-port 8891/tcp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use a different port, replace
8890or8891with the port number defined in the.conffile.Run the container:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
-poption opens the default ports8890and8881on the host and on the container. The
-voption creates a bind mount for the directory to the container.-
With the
Zoption, Podman marks the content with a private unshared label. This means only the current container can use the private volume.
-
With the
-
The
-doption runs the container detached and in the background. -
The option
-e KEYLIME_VERIFIER_SERVER_KEY_PASSWORD=<passphrase1>defines the server key passphrase. -
You can override configuration options with environment variables by using the option
-e KEYLIME_REGISTRAR_<ENVIRONMENT_VARIABLE>=<value>. To modify additional options, insert the-eoption separately for each environment variable. For a complete list of environment variables and their default values, see Section 7.12, “Keylime environment variables”.
-
The
Verification
Check that the container is running:
podman ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 07d4b4bff1b6 localhost/keylime-registrar:latest keylime_registrar 12 seconds ago Up 12 seconds 0.0.0.0:8881->8881/tcp, 0.0.0.0:8891->8891/tcp keylime-registrar
$ podman ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 07d4b4bff1b6 localhost/keylime-registrar:latest keylime_registrar 12 seconds ago Up 12 seconds 0.0.0.0:8881->8881/tcp, 0.0.0.0:8891->8891/tcp keylime-registrarCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.6. Deploying a Keylime server by using RHEL system roles
You can set up the verifier and registrar, which are the Keylime server components, by using the keylime_server RHEL system role. The keylime_server role installs and configures both the verifier and registrar components together on each node.
For more information about Keylime, see How Keylime works.
Prerequisites
- You have prepared the control node and the managed nodes
- You are logged in to the control node as a user who can run playbooks on the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions on them. - The managed nodes or groups of managed nodes on which you want to run this playbook are listed in the Ansible inventory file.
Procedure
Create a playbook that defines the required role:
Create a new YAML file and open it in a text editor, for example:
vi keylime-playbook.yml
# vi keylime-playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Insert the following content:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can find out more about the variables in Variables for the keylime_server RHEL system role.
Run the playbook:
ansible-playbook <keylime-playbook.yml>
$ ansible-playbook <keylime-playbook.yml>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check that the
keylime_verifierservice is active and running on the managed host:systemctl status keylime_verifier ● keylime_verifier.service - The Keylime verifier Loaded: loaded (/usr/lib/systemd/system/keylime_verifier.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:08 EST; 1min 45s ago# systemctl status keylime_verifier ● keylime_verifier.service - The Keylime verifier Loaded: loaded (/usr/lib/systemd/system/keylime_verifier.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:08 EST; 1min 45s agoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Check that the
keylime_registrarservice is active and running:systemctl status keylime_registrar ● keylime_registrar.service - The Keylime registrar service Loaded: loaded (/usr/lib/systemd/system/keylime_registrar.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:17 EST; 1min 42s ago ...# systemctl status keylime_registrar ● keylime_registrar.service - The Keylime registrar service Loaded: loaded (/usr/lib/systemd/system/keylime_registrar.service; disabled; vendor preset: disabled) Active: active (running) since Wed 2022-11-09 10:10:17 EST; 1min 42s ago ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.7. Variables for the keylime_server RHEL system role
When setting up a Keylime server by using the keylime_server RHEL system role, you can customize the following variables for registrar and verifier.
List of keylime_server RHEL system role variables for configuring the Keylime verifier:
keylime_server_verifier_ip- Defines the IP address of the verifier.
keylime_server_verifier_tls_dir-
Specifies the directory where the keys and certificates are stored. If set to default, the verifier uses the
/var/lib/keylime/cv_cadirectory. keylime_server_verifier_server_key_passphrase- Specifies a passphrase to decrypt the server private key. If the value is empty, the private key is not encrypted.
keylime_server_verifier_server_cert: Specifies the Keylime verifier server certificate file.
keylime_server_verifier_trusted_client_ca-
Defines the list of trusted client CA certificates. You must store the files in the directory set in the
keylime_server_verifier_tls_diroption. keylime_server_verifier_client_key- Defines the file containing the Keylime verifier private client key.
keylime_server_verifier_client_key_passphrase- Defines the passphrase to decrypt the client private key file. If the value is empty, the private key is not encrypted.
keylime_server_verifier_client_cert- Defines the Keylime verifier client certificate file.
keylime_server_verifier_trusted_server_ca-
Defines the list of trusted server CA certificates. You must store the files in the directory set in the
keylime_server_verifier_tls_diroption.
List of registrar variables for setting up keylime_server RHEL system role
keylime_server_registrar_ip- Defines the IP address of the registrar.
keylime_server_registrar_tls_dir-
Specifies the directory where you store the keys and certificates for the registrar. If you set it to default, the registrar uses the
/var/lib/keylime/reg_cadirectory. keylime_server_registrar_server_key- Defines the Keylime registrar private server key file.
keylime_server_registrar_server_key_passphrase- Specifies the passphrase to decrypt the server private key of the registrar. If the value is empty, the private key is not encrypted.
keylime_server_registrar_server_cert- Specifies the Keylime registrar server certificate file.
keylime_server_registrar_trusted_client_ca-
Defines the list of trusted client CA certificates. You must store the files in the directory set in the
keylime_server_registrar_tls_diroption.
7.8. Deploying Keylime tenant from a package
Keylime uses the keylime_tenant utility for many functions, including provisioning the agents on the target systems. You can install keylime_tenant on any system, including the systems that run other Keylime components, or on a separate system, depending on your requirements.
Prerequisites
-
You have
rootpermissions and network connection to the system or systems on which you want to install Keylime components. You have network access to the systems where the other Keylime components are configured:
- Verifier
- For more information, see Section 7.2, “Deploying Keylime verifier from a package”.
- Registrar
- For more information, see Section 7.4, “Deploying Keylime registrar from a package”.
Procedure
Install the Keylime tenant:
dnf install keylime-tenant
# dnf install keylime-tenantCopy to Clipboard Copied! Toggle word wrap Toggle overflow Define the tenant’s connection to the Keylime verifier by editing the
/etc/keylime/tenant.conf.d/00-verifier-ip.conffile:[tenant] verifier_ip = <verifier_ip>
[tenant] verifier_ip = <verifier_ip>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<verifier_ip>with the IP address to the verifier’s system. -
If the verifier uses a different port than the default value
8881, add theverifier_port = <verifier_port>setting.
-
Replace
Define the tenant’s connection to the Keylime registrar by editing the
/etc/keylime/tenant.conf.d/00-registrar-ip.conffile:[tenant] registrar_ip = <registrar_ip>
[tenant] registrar_ip = <registrar_ip>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<registrar_ip>with the IP address to the registrar’s system. -
If the registrar uses a different port than the default value
8891, add theregistrar_port = <registrar_port>setting.
-
Replace
Add certificates and keys to the tenant:
-
You can use the default configuration and load the keys and certificates to the
/var/lib/keylime/cv_cadirectory. Alternatively, you can define the location of the keys and certificates in the configuration. Create a new
.conffile in the/etc/keylime/tenant.conf.d/directory, for example,/etc/keylime/tenant.conf.d/00-keys-and-certs.conf, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
trusted_server_caparameter accepts paths to the verifier and registrar server CA certificate. You can provide multiple comma-separated paths, for example if the verifier and registrar use different CAs.NoteUse absolute paths to define key and certificate locations. Alternatively, you can define a directory in the
tls_diroption and use paths relative to that directory.
-
You can use the default configuration and load the keys and certificates to the
-
Optional: If the trusted platform module (TPM) endorsement key (EK) cannot be verified by using certificates in the
/var/lib/keylime/tpm_cert_storedirectory, add the certificate to that directory. This can occur particularly when using virtual machines with emulated TPMs.
Verification
Check the status of the verifier:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow If correctly set up, and if no agent is configured, the verifier responds that it does not recognize the default agent UUID.
Check the status of the registrar:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow If correctly set up, and if no agent is configured, the registrar responds that it does not recognize the default agent UUID.
7.9. Deploying Keylime agent from a package
The Keylime agent is the component deployed to all systems to be monitored by Keylime.
By default, the Keylime agent stores all its data in the /var/lib/keylime/ directory of the monitored system.
To keep the configuration files organized within the drop-in directories, use file names with a two-digit number prefix, for example /etc/keylime/agent.conf.d/00-registrar-ip.conf. The configuration processing reads the files inside the drop-in directory in lexicographic order and sets each option to the last value it reads.
Prerequisites
-
You have
rootpermissions to the monitored system. -
The monitored system has a Trusted Platform Module (TPM). To verify, enter the
tpm2_pcrreadcommand. If the output returns several hashes, a TPM is available. You have network access to the systems where the other Keylime components are configured:
- Verifier
- For more information, see Configuring Keylime verifier.
- Registrar
- For more information, see Configuring Keylime registrar.
- Tenant
- For more information, see Configuring Keylime tenant.
- Integrity measurement architecture (IMA) is enabled on the monitored system. For more information, see Enabling integrity measurement architecture and extended verification module.
Procedure
Install the Keylime agent:
dnf install keylime-agent
# dnf install keylime-agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command installs the
keylime-agent-rustpackage.Define the agent’s IP address and port in the configuration files. Create a new
.conffile in the/etc/keylime/agent.conf.d/directory, for example,/etc/keylime/agent.conf.d/00-agent-ip.conf, with the following content:[agent] ip = '<agent_ip>'
[agent] ip = '<agent_ip>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe Keylime agent configuration uses the TOML format, which is different from the INI format used for configuration of the other components. Therefore, enter values in valid TOML syntax, for example, paths in single quotation marks and arrays of multiple paths in square brackets.
-
Replace
<agent_IP_address>with the agent’s IP address. Alternatively, useip = '*'orip = '0.0.0.0'to bind the agent to all available IP addresses. -
Optionally, you can also change the agent’s port from the default value
9002by using theport = '<agent_port>'option.
-
Replace
Define the registrar’s IP address and port in the configuration files. Create a new
.conffile in the/etc/keylime/agent.conf.d/directory, for example,/etc/keylime/agent.conf.d/00-registrar-ip.conf, with the following content:[agent] registrar_ip = '<registrar_IP_address>'
[agent] registrar_ip = '<registrar_IP_address>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<registrar_IP_address>with the registrar’s IP address. -
Optionally, you can also change the registrar’s port from the default value
8890by using theregistrar_port = '<registrar_port>'option.
-
Replace
Optional: Define the agent’s universally unique identifier (UUID). If it is not defined, the default UUID is used. Create a new
.conffile in the/etc/keylime/agent.conf.d/directory, for example,/etc/keylime/agent.conf.d/00-agent-uuid.conf, with the following content:[agent] uuid = '<agent_UUID>'
[agent] uuid = '<agent_UUID>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<agent_UUID>with the agent’s UUID, for exampled432fbb3-d2f1-4a97-9ef7-abcdef012345. You can use theuuidgenutility to generate a UUID.
-
Replace
Optional: Load existing keys and certificates for the agent. If the agent receives no
server_keyandserver_cert, it generates its own key and a self-signed certificate.Define the location of the keys and certificates in the configuration. Create a new
.conffile in the/etc/keylime/agent.conf.d/directory, for example,/etc/keylime/agent.conf.d/00-keys-and-certs.conf, with the following content:[agent] server_key = '</path/to/server_key>' server_key_password = '<passphrase1>' server_cert = '</path/to/server_cert>' trusted_client_ca = '[</path/to/ca/cert3>, </path/to/ca/cert4>]'
[agent] server_key = '</path/to/server_key>' server_key_password = '<passphrase1>' server_cert = '</path/to/server_cert>' trusted_client_ca = '[</path/to/ca/cert3>, </path/to/ca/cert4>]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse absolute paths to define key and certificate locations. The Keylime agent does not accept relative paths.
Open the port in firewall:
firewall-cmd --add-port 9002/tcp firewall-cmd --runtime-to-permanent
# firewall-cmd --add-port 9002/tcp # firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you use a different port, replace
9002with the port number defined in the.conffile.Enable and start the
keylime_agentservice:systemctl enable --now keylime_agent
# systemctl enable --now keylime_agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: From the system where the Keylime tenant is configured, verify that the agent is correctly configured and can connect to the registrar.
keylime_tenant -c regstatus --uuid <agent_uuid> Reading configuration from ['/etc/keylime/logging.conf'] ... ==\n-----END CERTIFICATE-----\n", "ip": "127.0.0.1", "port": 9002, "regcount": 1, "operational_state": "Registered"}}}
# keylime_tenant -c regstatus --uuid <agent_uuid> Reading configuration from ['/etc/keylime/logging.conf'] ... ==\n-----END CERTIFICATE-----\n", "ip": "127.0.0.1", "port": 9002, "regcount": 1, "operational_state": "Registered"}}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<agent_uuid>with the agent’s UUID.If the registrar and agent are correctly configured, the output displays the agent’s IP address and port, followed by
"operational_state": "Registered".
Create a new IMA policy by entering the following content into the
/etc/ima/ima-policyfile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This policy targets runtime monitoring of executed applications. You can adjust this policy according to your scenario. You can find the MAGIC constants in the
statfs(2)man page on your system.Update kernel parameters:
grubby --update-kernel DEFAULT --args 'ima_appraise=log ima_canonical_fmt ima_policy=tcb ima_template=ima-ng'
# grubby --update-kernel DEFAULT --args 'ima_appraise=log ima_canonical_fmt ima_policy=tcb ima_template=ima-ng'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Reboot the system to apply the new IMA policy.
Verification
Verify that the agent is running:
systemctl status keylime_agent ● keylime_agent.service - The Keylime compute agent Loaded: loaded (/usr/lib/systemd/system/keylime_agent.service; enabled; preset: disabled) Active: active (running) since ...# systemctl status keylime_agent ● keylime_agent.service - The Keylime compute agent Loaded: loaded (/usr/lib/systemd/system/keylime_agent.service; enabled; preset: disabled) Active: active (running) since ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
After the agent is configured on all systems you want to monitor, you can deploy Keylime to perform one or both of the following functions:
7.10. Configuring Keylime for runtime monitoring
To verify that the state of monitored systems is correct, the Keylime agent must be running on the monitored systems.
Because Keylime runtime monitoring uses integrity measurement architecture (IMA) to measure large numbers of files, it might have a significant impact on the performance of your system.
When provisioning the agent, you can also define a file that Keylime sends to the monitored system. Keylime encrypts the file sent to the agent, and decrypts it only if the agent’s system complies with the TPM policy and with the IMA allowlist.
You can make Keylime ignore changes of specific files or within specific directories by configuring a Keylime excludelist. The excluded files are still measured by IMA.
From Keylime version 7.3.0, provided in RHEL 9.3, the allowlist and excludelist are combined into the Keylime runtime policy.
Prerequisites
You have network access to the systems where the Keylime components are configured:
- Verifier
- For more information, see Section 7.2, “Deploying Keylime verifier from a package”.
- Registrar
- For more information, see Section 7.4, “Deploying Keylime registrar from a package”.
- Tenant
- For more information, see Section 7.8, “Deploying Keylime tenant from a package”.
- Agent
- For more information, see Section 7.9, “Deploying Keylime agent from a package”.
Procedure
On the monitored system where the Keylime agent is configured and running, install the
python3-keylimepackage, which contains thekeylime-policytool:dnf -y install python3-keylime
# dnf -y install python3-keylimeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a runtime policy from the current state of the agent system:
keylime-policy create runtime --ima-measurement --rootfs '/' --ramdisk-dir '/boot/' --output <policy.json>
# keylime-policy create runtime --ima-measurement --rootfs '/' --ramdisk-dir '/boot/' --output <policy.json>Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this command,
-
Replace
<policy.json>with the file name of the runtime policy. The following directories are automatically excluded from measurement:
-
/sys -
/run -
/proc -
/lost+found -
/dev -
/media -
/snap -
/mnt -
/var -
/tmp
-
-
Optionally, you can exclude additional specific paths from measurement by adding a
--excludelist <excludelist.txt>option. The excludelist accepts Python regular expressions with one regular expression per line. See Regular expression operations at docs.python.org for the complete list of special characters.
-
Replace
Copy the generated runtime policy to the system where the
keylime_tenantutility is configured, for example:scp <policy.json> root@<tenant.ip>:/root/<policy.json>
# scp <policy.json> root@<tenant.ip>:/root/<policy.json>Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the system where the Keylime tenant is configured, provision the agent by using the
keylime_tenantutility:keylime_tenant --command add --targethost <agent_ip> --uuid <agent_uuid> --runtime-policy <policy.json> --cert default
# keylime_tenant --command add --targethost <agent_ip> --uuid <agent_uuid> --runtime-policy <policy.json> --cert defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<agent_ip>with the agent’s IP address. -
Replace
<agent_uuid>with the agent’s UUID. -
Replace
<policy.json>with the path to the Keylime runtime policy file. With the
--certoption, the tenant generates and signs a certificate for the agent by using the CA certificates and keys located in the specified directory, or the default/var/lib/keylime/ca/directory. If the directory contains no CA certificates and keys, the tenant will generate them automatically according to the configuration in the/etc/keylime/ca.conffile and save them to the specified directory. The tenant then sends these keys and certificates to the agent.When generating CA certificates or signing agent certificates, you might be prompted for the password to access the CA private key:
Please enter the password to decrypt your keystore:.NoteKeylime encrypts the file sent to the agent, and decrypts it only if the agent’s system complies with the TPM policy and the IMA allowlist. By default, Keylime decompresses sent
.zipfiles.
As an example, with the following command,
keylime_tenantprovisions a new Keylime agent at127.0.0.1with UUIDd432fbb3-d2f1-4a97-9ef7-75bd81c00000and loads a runtime policypolicy.json. It also generates a certificate in the default directory and sends the certificate file to the agent. Keylime decrypts the file only if the TPM policy configured in/etc/keylime/verifier.confis satisfied:keylime_tenant --command add --targethost 127.0.0.1 --uuid d432fbb3-d2f1-4a97-9ef7-75bd81c00000 --runtime-policy policy.json --cert default
# keylime_tenant --command add --targethost 127.0.0.1 --uuid d432fbb3-d2f1-4a97-9ef7-75bd81c00000 --runtime-policy policy.json --cert defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou can stop Keylime from monitoring a node by using the
# keylime_tenant --command delete --uuid <agent_uuid>command.You can modify the configuration of an already registered agent by using the
keylime_tenant --command updatecommand.-
Replace
Verification
- Optional: Reboot the monitored system to verify that the settings are persistent.
Verify a successful attestation of the agent:
keylime_tenant --command cvstatus --uuid <agent.uuid> ... {"<agent.uuid>": {"operational_state": "Get Quote"..."attestation_count": 5 ...# keylime_tenant --command cvstatus --uuid <agent.uuid> ... {"<agent.uuid>": {"operational_state": "Get Quote"..."attestation_count": 5 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<agent.uuid>with the agent’s UUID.If the value of
operational_stateisGet Quoteandattestation_countis nonzero, the attestation of this agent is successful.If the value of
operational_stateisInvalid QuoteorFailedattestation fails, the command displays output similar to the following:{"<agent.uuid>": {"operational_state": "Invalid Quote", ... "ima.validation.ima-ng.not_in_allowlist", "attestation_count": 5, "last_received_quote": 1684150329, "last_successful_attestation": 1684150327}}{"<agent.uuid>": {"operational_state": "Invalid Quote", ... "ima.validation.ima-ng.not_in_allowlist", "attestation_count": 5, "last_received_quote": 1684150329, "last_successful_attestation": 1684150327}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the attestation fails, display more details in the verifier log:
journalctl --unit keylime_verifier keylime.tpm - INFO - Checking IMA measurement list... keylime.ima - WARNING - File not found in allowlist: /root/bad-script.sh keylime.ima - ERROR - IMA ERRORS: template-hash 0 fnf 1 hash 0 good 781 keylime.cloudverifier - WARNING - agent D432FBB3-D2F1-4A97-9EF7-75BD81C00000 failed, stopping polling
# journalctl --unit keylime_verifier keylime.tpm - INFO - Checking IMA measurement list... keylime.ima - WARNING - File not found in allowlist: /root/bad-script.sh keylime.ima - ERROR - IMA ERRORS: template-hash 0 fnf 1 hash 0 good 781 keylime.cloudverifier - WARNING - agent D432FBB3-D2F1-4A97-9EF7-75BD81C00000 failed, stopping pollingCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.11. Configuring Keylime for measured boot attestation
When you configure Keylime for measured boot attestation, Keylime checks that the boot process on the measured system corresponds to the state you defined.
Prerequisites
You have network access to the systems where the Keylime components are configured:
- Verifier
- For more information, see Section 7.2, “Deploying Keylime verifier from a package”.
- Registrar
- For more information, see Section 7.4, “Deploying Keylime registrar from a package”.
- Tenant
- For more information, see Section 7.8, “Deploying Keylime tenant from a package”.
- Agent
- For more information, see Section 7.9, “Deploying Keylime agent from a package”.
- Unified Extensible Firmware Interface (UEFI) is enabled on the agent system.
Procedure
On the monitored system where the Keylime agent is configured and running, install the
python3-keylimepackage, which contains thekeylime-policytool:dnf -y install python3-keylime
# dnf -y install python3-keylimeCopy to Clipboard Copied! Toggle word wrap Toggle overflow On the monitored system, generate a policy from the measured boot log of the current state of the system by using the
keylime-policytool:keylime-policy create measured-boot --eventlog-file /sys/kernel/security/tpm0/binary_bios_measurements --output <./measured_boot_reference_state.json>
# keylime-policy create measured-boot --eventlog-file /sys/kernel/security/tpm0/binary_bios_measurements --output <./measured_boot_reference_state.json>Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<./measured_boot_reference_state.json>with the path wherekeylime-policysaves the generated policy. If your UEFI system does not have Secure Boot enabled, pass the
--without-securebootargument.ImportantThe policy generated with
keylime-policyis based on the current state of the system and is very strict. Any modifications of the system including kernel updates and system updates will change the boot process and the system will fail the attestation.
-
Replace
Copy the generated policy to the system where the
keylime_tenantutility is configured, for example:scp root@<agent_ip>:<./measured_boot_reference_state.json> <./measured_boot_reference_state.json>
# scp root@<agent_ip>:<./measured_boot_reference_state.json> <./measured_boot_reference_state.json>Copy to Clipboard Copied! Toggle word wrap Toggle overflow On the system where the Keylime tenant is configured, provision the agent by using the
keylime_tenantutility:keylime_tenant --command add --targethost <agent_ip> --uuid <agent_uuid> --mb_refstate <./measured_boot_reference_state.json> --cert default
# keylime_tenant --command add --targethost <agent_ip> --uuid <agent_uuid> --mb_refstate <./measured_boot_reference_state.json> --cert defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Replace
<agent_ip>with the agent’s IP address. -
Replace
<agent_uuid>with the agent’s UUID. -
Replace
<./measured_boot_reference_state.json>with the path to the measured boot policy.
If you configure measured boot in combination with runtime monitoring, provide all the options from both use cases when entering the
keylime_tenant --command addcommand.NoteYou can stop Keylime from monitoring a node by using the
# keylime_tenant --command delete --targethost <agent_ip> --uuid <agent_uuid>command.You can modify the configuration of an already registered agent by using the
keylime_tenant --command updatecommand.-
Replace
Verification
Reboot the monitored system and verify a successful attestation of the agent:
keylime_tenant --command cvstatus --uuid <agent_uuid> ... {"<agent.uuid>": {"operational_state": "Get Quote"..."attestation_count": 5 ...# keylime_tenant --command cvstatus --uuid <agent_uuid> ... {"<agent.uuid>": {"operational_state": "Get Quote"..."attestation_count": 5 ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<agent_uuid>with the agent’s UUID.If the value of
operational_stateisGet Quoteandattestation_countis nonzero, the attestation of this agent is successful.If the value of
operational_stateisInvalid QuoteorFailedattestation fails, the command displays output similar to the following:{"<agent.uuid>": {"operational_state": "Invalid Quote", ... "ima.validation.ima-ng.not_in_allowlist", "attestation_count": 5, "last_received_quote": 1684150329, "last_successful_attestation": 1684150327}}{"<agent.uuid>": {"operational_state": "Invalid Quote", ... "ima.validation.ima-ng.not_in_allowlist", "attestation_count": 5, "last_received_quote": 1684150329, "last_successful_attestation": 1684150327}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the attestation fails, display more details in the verifier log:
journalctl -u keylime_verifier {"d432fbb3-d2f1-4a97-9ef7-75bd81c00000": {"operational_state": "Tenant Quote Failed", ... "last_event_id": "measured_boot.invalid_pcr_0", "attestation_count": 0, "last_received_quote": 1684487093, "last_successful_attestation": 0}}# journalctl -u keylime_verifier {"d432fbb3-d2f1-4a97-9ef7-75bd81c00000": {"operational_state": "Tenant Quote Failed", ... "last_event_id": "measured_boot.invalid_pcr_0", "attestation_count": 0, "last_received_quote": 1684487093, "last_successful_attestation": 0}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.12. Keylime environment variables
You can set Keylime environment variables to override the values from the configuration files, for example, when starting a container with the podman run command by using the -e option.
The environment variables have the following syntax:
KEYLIME_<SECTION>_<ENVIRONMENT_VARIABLE>=<value>
KEYLIME_<SECTION>_<ENVIRONMENT_VARIABLE>=<value>Where:
-
<SECTION>is the section of the Keylime configuration file. -
<ENVIRONMENT_VARIABLE>is the environment variable. -
<value>is the value to which you want to set the environment variable.
For example, -e KEYLIME_VERIFIER_MAX_RETRIES=6 sets the max_retries configuration option in the [verifier] section to 6.
Verifier configuration
| Configuration option | Environment variable | Default value |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
| |
|
|
| |
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
Registrar configuration
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
Tenant configuration
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
CA configuration
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Agent configuration
| Configuration option | Environment variable | Default value |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Logging configuration
| Configuration option | Environment variable | Default value |
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Configuration option | Environment variable | Default value |
|
|
| |
|
|
|
|
|
|
|
|