Questo contenuto non è disponibile nella lingua selezionata.
Chapter 3. Managing SCAP security policies in the Insights for RHEL compliance service
Create and manage your SCAP security policies entirely within the compliance service UI. Define new policies and select the rules and systems you want to associate with them, and edit existing policies as your requirements change.
Unlike most other Red Hat Insights for Red Hat Enterprise Linux services, the compliance service does not run automatically on a default schedule. In order to upload OpenSCAP data to the Insights for Red Hat Enterprise Linux application, you must run insights-client --compliance, either on-demand or on a scheduled job that you set.
3.1. Creating new SCAP policies
You must add each Insights for Red Hat Enterprise Linux-registered system to one or more security policies before you can perform a scan or see results for that scan in the compliance service UI. To create a new policy, and include specific systems and rules, complete the following steps:
If your RHEL servers span across multiple major releases of RHEL, you must create a separate policy for each major release. For example, all of your RHEL 7 servers would be on one Standard System Security Profile for RHEL policy and all of your RHEL 8 servers will be on another.
Procedure
- Navigate to the Security > Compliance > SCAP Policies page.
- Click the Create new policy button.
On the Create SCAP policy page of the wizard, select the RHEL major version of the systems you will include in the policy.
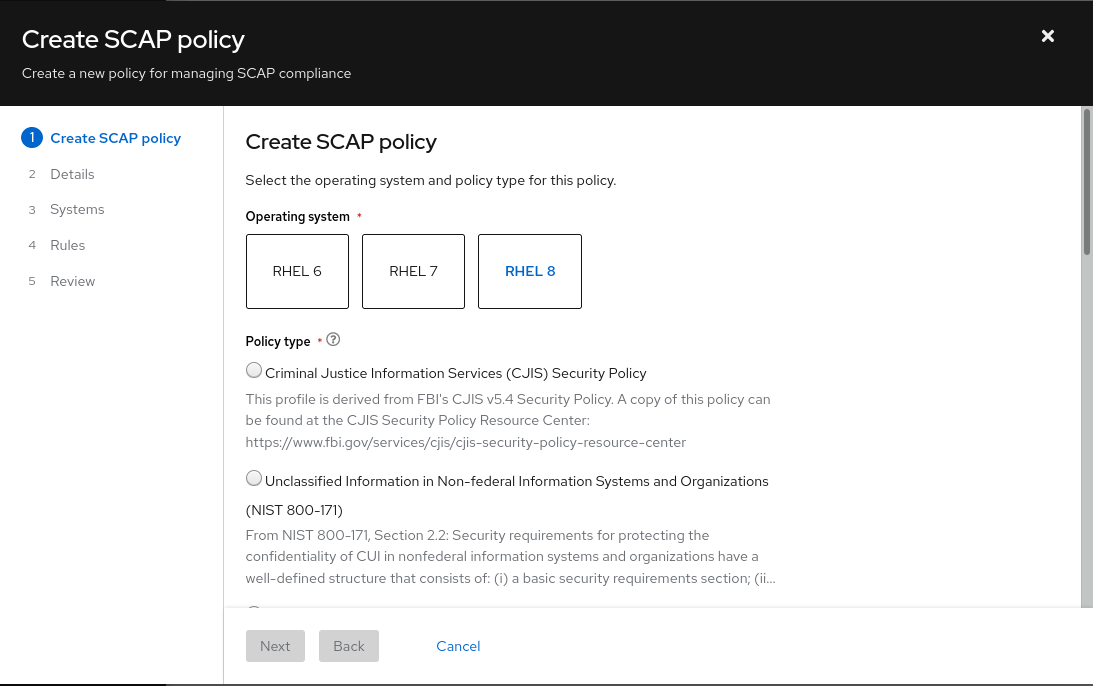
- Select one of the policy types available for that RHEL major version, then click Next.
- On the Details page, accept the name and description already provided or provide your own more meaningful entries.
- Optionally, add a Business objective to give context, for example, “CISO mandate.”
- Define a compliance threshold acceptable for your requirements and click Next.
- Select the Systems to include on this policy and click Next. Your selection of a RHEL major version in the first step automatically determines which systems can be added to this policy.
Select which Rules to include with each policy. Because each minor version of RHEL supports the use of a specific SCAP Security Guide (SSG) version (sometimes more than one, in which case we use the latest), the rule set for each RHEL minor version is slightly different and must be selected separately.
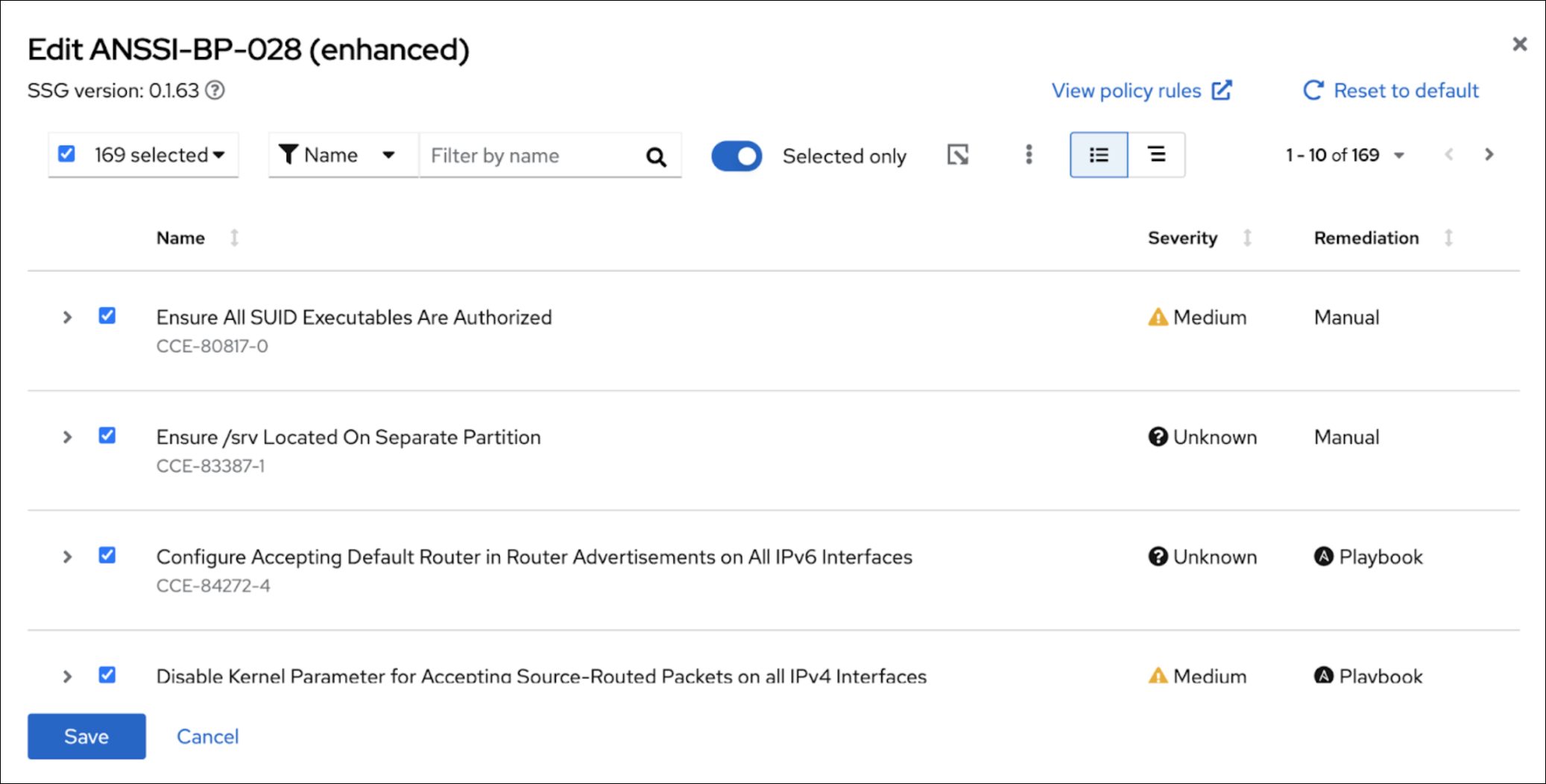
Optionally, use the filtering and search capabilities to refine the list of rules.
For example, to show only the highest severity rules, click the primary filter dropdown and select Severity. In the secondary filter, check the boxes for High and Medium.
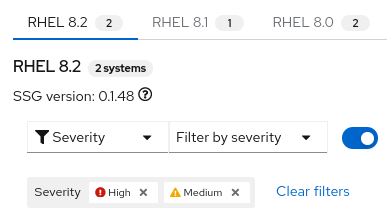
- The rules shown by default are those designated for that policy type and that version of SSG. By default, the Selected only toggle next to the filter boxes is enabled. You may remove this toggle if so desired.
- Repeat this process as needed for each RHEL minor version tab.
- After you select rules for each Red Hat Enterprise Linux minor version SSG, click Next.
- On the Review page, verify that the information shown is correct, then click Finish.
- Give the app a minute to create the policy, then click the Return to application button to view your new policy.
You have to go to the system and run the compliance scan before results will be shown in the compliance service UI.
3.2. Editing compliance policies in the Insights UI
After creating a compliance policy, you can later edit the policy to change the policy details, or which rules or systems are included.
Use the following procedures to edit a policy to suit the needs of your organization.
User Access Note
Editing the included rules and systems in a policy requires that a user be a member of a User Access Group with the Compliance adminstrator role. The Compliance admistrator role includes enhanced permissions that are not granted by default to all Insights for Red Hat Enterprise Linux users.
3.2.1. Editing policy details
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console.
Procedure
- Navigate to the Security > Compliance > SCAP policies page.
- Locate the policy you want to edit.
- Click on the policy name. This opens the policy details view.
Wherever you see a pencil icon, you can click on the icon to edit the details in that field. Editable fields include
- Compliance threshold
- Business objective
- Policy description
- After you edit a field, click the blue checkmark to the right of the field to save your input.
3.2.2. Editing included rules
Prerequisites
- You are logged in to the Red Hat Hybrid Cloud Console.
- You have Compliance administrator User Access permissions.
Procedure
- Navigate to the Security > Compliance > SCAP policies page.
- Locate the policy you want to edit.
-
On the right side of the policy row, click the More actions icon,
 , and click Edit policy.
, and click Edit policy.
- In the Edit popup, click the Rules tab.
Click on a RHEL minor version.
ImportantBecause a different SCAP Security Guide (SSG) version exists for each minor version of RHEL, you must edit the rules for each minor version of RHEL separately.
Use the Name filter and search function to locate the rules to remove.
NoteWith the Name primary filter selected, you can search by the rule name or its identifier.
Uncheck the box next to any rule you want to remove.
Or, check the box next to any rule you want to add.
- Repeat these steps for each RHEL minor version tab.
- Click Save.
Verification
- Navigate to the Security > Compliance > SCAP policies page and locate the edited policy.
- Click on the policy and verify that the included rules are consistent with the edits you made.
3.2.3. Editing included systems
- Navigate to the Security > Compliance > SCAP policies page.
- Locate the policy you want to edit.
-
On the right side of the policy row, click the More actions icon,
 , and click Edit policy.
, and click Edit policy.
In the Edit popup, click the Systems tab.
A list of all available systems is displayed.
Systems that are already included in the policy have a checkmark in the box to the left side of the system name.
Systems without a checkmark next to the system name are not included in this policy.
Search for a system by name. To include that system in the policy, check the box next to the system name.
Or, to remove the system from the policy, uncheck the box next to the system name.
- Click Save to save your changes.
Verification
- Navigate to the Security > Compliance > SCAP policies page and locate the edited policy.
- Click on the policy and verify that the included systems are consistent with the edits you made.
3.3. Editing Compliance policy details by using the Compliance API
Use the Compliance API to change policy details, or to include or exclude rules or systems. Use the REST API entry point: https://console.redhat.com/api/compliance/v2.
The Compliance API supports the GET, POST, PATCH, and DELETE HTTP methods. Use the PATCH method to update policy details. The API offers the following services for Compliance policies:
- GET /policies
- POST /policies
- DELETE /policies/{policy_id}
- GET /policies/{policy_id}
- PATCH /policies/{policy_id}
- GET /policies/{policy_id}/systems
- DELETE /policies/{policy_id}/systems/{system_id}
- PATCH /policies/{policy_id}/systems{system_id}
- GET /policies/{policy_id}/tailorings
- GET /policies/{policy_id}/tailorings/{tailoring_id}
- PATCH /policies/{policy_id}/tailorings/{tailoring_id}
- GET /policies/{policy_id}/tailorings/{tailoring_id}/rules
- DELETE /policies/{policy_id}/tailorings/{tailoring_id}/rules/{rule_id}
- PATCH /policies/{policy_id}/tailorings/{tailoring_id}/rules/{rule_id}
- GET /policies/{policy_id}/tailorings/{tailoring_id}/tailoring_file.json
Successful requests return the following responses:
- 200 — Success
- 202 — Successfully deleted (for the DELETE method)
- 202 — Successfully updated (for the PATCH method)
The API works asynchronously. You can submit the GET /policies/{policy_id} request to the Compliance API and receive a list of the policy details for the specified policy ID. You can then view the list of policy details and use the PATCH /policies/{policy_id} request to update the details.
For more information about the operations and schemas available for the Compliance service, refer to https://developers.redhat.com/api-catalog/api/compliance_v2Compliance API v2 documentation in the API Catalog.
Additional resources
3.3.1. Editing Compliance policy details
There are multiple ways to make API calls to the Insights APIs. For more information, refer to Making API calls.
The example procedure in this section uses the API Catalog at developers.redhat.com to edit policy details.
Before you edit Compliance policy details, you can use the GET /policies API call to query the API for the complete list of policy IDs and details.
Prerequisites
- You have the programming language that you want to use (for example, python) installed on your system.
- You have an access token that you obtained from your service account or from an offline access token.
- You have a service account configured with necessary permissions. To create and configure a service account, see Creating and managing a service account.
-
You have the
policy_idfor the policy that you want to edit.
Procedure
- Open the API catalog in a web browser. The API catalog lists available APIs for Insights and other services.
- Select Compliance from the catalog and click v2. The Cloud Services for RHEL Compliance API v2 page opens. The page lists the base URL of the Compliance API and any requirements for authentication.
- Under the Policies list, click the drop-down arrow next to Update a Policy. The description for the operation includes parameters that you can use to refine your API call, as well as expected responses from the server. In addition, the panel on the right side of the page generates an example API call for the PATCH operation in multiple programming languages.
- In the panel, click the drop-down and select the language you prefer (for example, Python) from the list of options. The panel displays sample code for the PATCH operation, formatted in python syntax.
Copy the sample code and paste it into a Python code file where you want to invoke the PATCH command. For example:
import requests url = "https://console.redhat.com/policies/%7Bpolicy_id%7D" headers = {"Content-Type": "application/vnd.api+json"} response = requests.patch(url, headers=headers) print(response.json())import requests url = "https://console.redhat.com/policies/%7Bpolicy_id%7D" headers = {"Content-Type": "application/vnd.api+json"} response = requests.patch(url, headers=headers) print(response.json())Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Paste the
policy_idfor the policy that you want to update in place of%7Bpolicy_id%7D. Paste the update that you want to make to the policy in place of
application/vnd.api+json. The update takes the formobject: value. For example, pastecompliance_threshold: 50to change the compliance threshold to 50.NoteTo see the fields that you can update for the policy, click the
policy_updatelink under the Request Body Schema heading next to the sample code. The link shows the available fields:business_objective,compliance_threshold, anddescriptionand their expected values.Press Enter to run your code.
If the server returns a response of 202, your API call was successful. If the code returns a response other than 202, refer to the error message included with the response code to determine how the API call failed and how to remedy the reason for the failure.
3.4. Viewing SCAP policies using the insights-client command
After you have registered your system to Insights, you can view all available compliance policies for that system using the insights-client --compliance-policies command.
Prerequisites
- The Insights client is installed on the system.
- You are logged in to a system where you have root privileges.
Procedure
At the command line, enter:
insights-client --compliance-policies
[root@insights]# insights-client --compliance-policiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
This command displays a list of compliance policies that are supported for the system. The output shows the ID and Title for the policies, and whether the policies are Assigned (shows a value of TRUE or FALSE that indicates whether the policy is assigned to the system or not).

Additional Resources
For more information about the insights-client --compliance options, see the Client Configuration Guide for Red Hat Insights.
3.5. Assign systems to SCAP policies using the insights-client command
You can assign (add) systems to SCAP policies using the insights-client --compliance-assign command.
This command option provides you the ability to create custom automation for working with your systems and the SCAP policies available to those systems.
Prerequisites
- The Insights client is installed on the system.
- You are logged in to a system where you have root privileges.
-
You have run the
insights-client --compliance-policiescommand.
Procedure
At the command line, enter
insights-client --compliance-assign <ID>.
[root@insights]# insights-client --compliance-assign <ID>.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Use a policy ID from the insights-client --compliance-policies command output.
Verification steps
- Navigate to Security > Compliance > SCAP policies.
- Click the name of the policy you assigned the system to.
- Click the Systems tab. The system is listed for the policy.
You can also run the insights-client --compliance-policies command to see if the Assigned value is set to True for the policy.
For more information about the insights-client --compliance options, see the Client Configuration Guide for Red Hat Insights.
3.6. Unassigning systems from SCAP policies using the insights-client command
You can unassign (remove) systems from SCAP policies using insights-client --compliance-unassign command. Optionally, you can use the command to create your own custom automations for your systems and SCAP policies.
Prerequisite
- The Insights client is installed on the system.
- You are logged in to a system where you have root privileges.
-
You have run the
insights-client --compliance-policiescommand.
Procedure
At the command line, enter
insights-client --compliance-unassign <ID>
[root@insights]# insights-client --compliance-unassign <ID>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Use a policy ID from the insights-client --compliance-policies command output.
Verification steps
- Navigate to Security > Compliance > SCAP policies.
- Click the name of the policy you assigned the system to.
- Click the Systems tab. The system is no longer listed.
To find out if the Assigned value is set to False for the policy, run the insights-client --compliance-policies command again.
Additional Resources
For more information about the insights-client --compliance options, see the Client Configuration Guide for Red Hat Insights.
3.7. Viewing policy rules
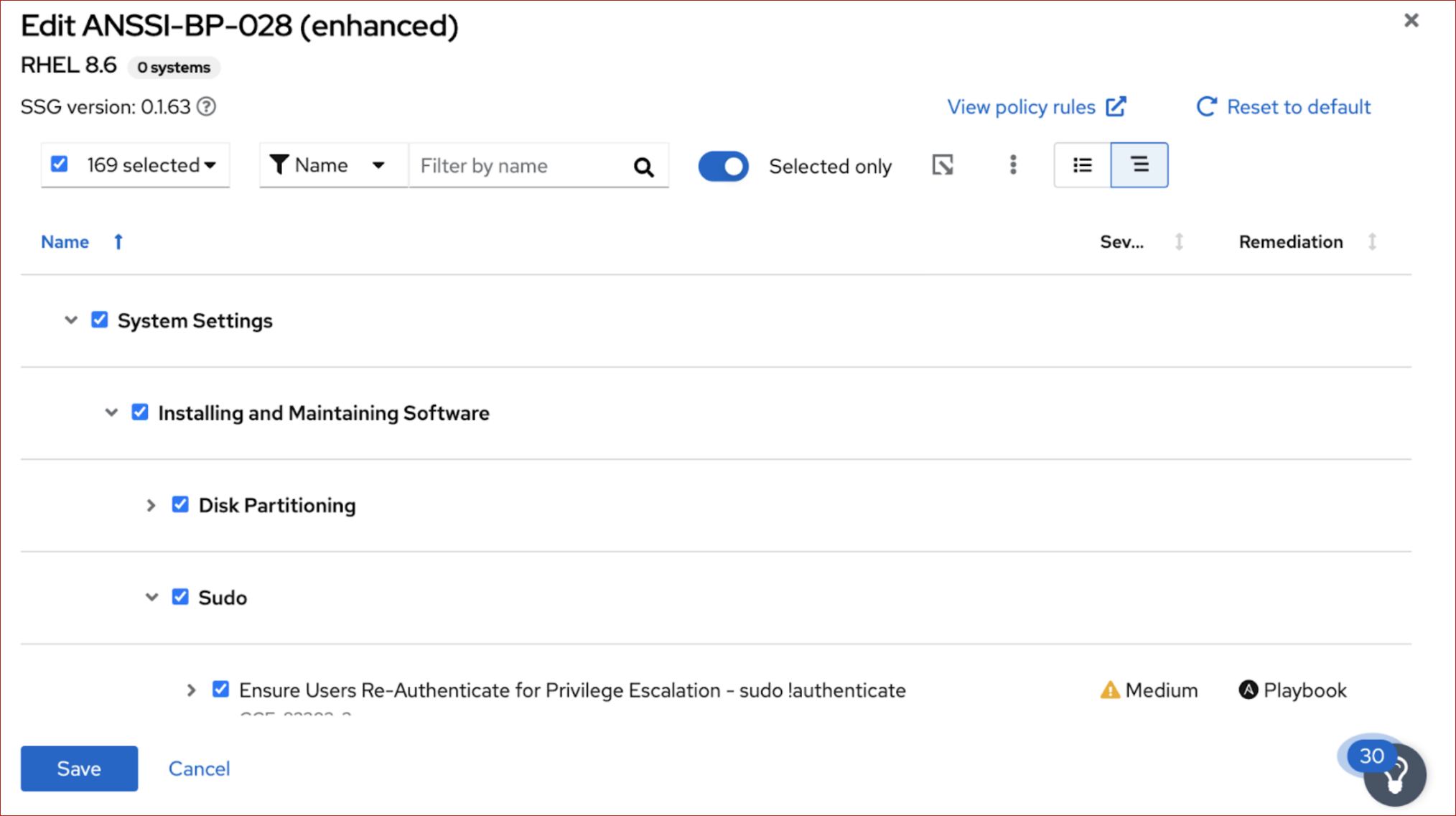
Insights Compliance displays rules in categorized groups, so that similar rules are close together. You can see rules grouped according to category or classification for the compliance checks that will take place for a policy. The nested group structure (or tree view) is the default view. The tree view provides additional contextual information that allows you to see categories of rules, and at times, multiple rules for a policy. The tree view also allows you to see rules that have editable values (for more information about editable rule values, see “Editing values for policy rules”).
You can view rules in the tree view or the classic view. In the classic view, rules appear in a linear list.
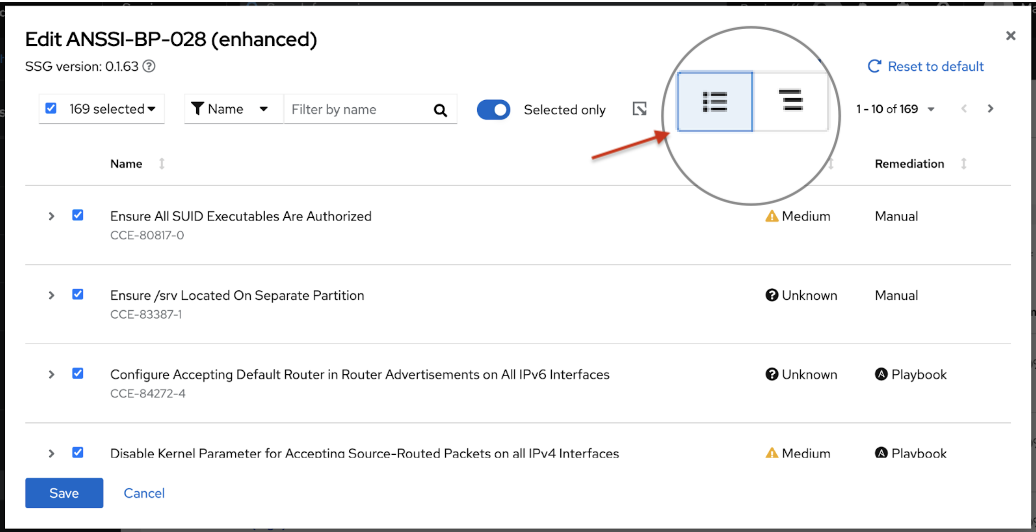
You can switch from the tree view to the classic view by toggling between the two buttons under View policy rules.
To see rules listed in tree view format, click the tree view icon (
![]() ).
).
To see rules listed in the classic view format, click the classic view icon (
![]() ).
).
- When you use the filter feature to search for a specific rule, the view automatically switches to the classic view.
- After you expand a rule to show additional information, it will stay in the expanded view, even if you switch to a different view.
You can switch views when you are:
- Editing compliance policies
- Creating new SCAP policies
- Generating Compliance Service Reports (see "Exporting reports" topics)