OpenShift Container Storage is now OpenShift Data Foundation starting with version 4.9.
Questo contenuto non è disponibile nella lingua selezionata.
Chapter 7. Bucket policies in the Multicloud Object Gateway
OpenShift Container Storage supports AWS S3 bucket policies. Bucket policies allow you to grant users access permissions for buckets and the objects in them.
7.1. About bucket policies
Bucket policies are an access policy option available for you to grant permission to your AWS S3 buckets and objects. Bucket policies use JSON-based access policy language. For more information about access policy language, see AWS Access Policy Language Overview.
7.2. Using bucket policies
Prerequisites
- A running OpenShift Container Storage Platform
- Access to the Multicloud Object Gateway, see Chapter 2, Accessing the Multicloud Object Gateway with your applications
Procedure
To use bucket policies in the Multicloud Object Gateway:
Create the bucket policy in JSON format. See the following example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow There are many available elements for bucket policies with regard to access permissions.
For details on these elements and examples of how they can be used to control the access permissions, see AWS Access Policy Language Overview.
For more examples of bucket policies, see AWS Bucket Policy Examples.
Instructions for creating S3 users can be found in Section 7.3, “Creating an AWS S3 user in the Multicloud Object Gateway”.
Using AWS S3 client, use the
put-bucket-policycommand to apply the bucket policy to your S3 bucket:aws --endpoint ENDPOINT --no-verify-ssl s3api put-bucket-policy --bucket MyBucket --policy BucketPolicy
# aws --endpoint ENDPOINT --no-verify-ssl s3api put-bucket-policy --bucket MyBucket --policy BucketPolicyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
ENDPOINTwith the S3 endpointReplace
MyBucketwith the bucket to set the policy onReplace
BucketPolicywith the bucket policy JSON fileAdd
--no-verify-sslif you are using the default self signed certificatesFor example:
aws --endpoint https://s3-openshift-storage.apps.gogo44.noobaa.org --no-verify-ssl s3api put-bucket-policy -bucket MyBucket --policy file://BucketPolicy
# aws --endpoint https://s3-openshift-storage.apps.gogo44.noobaa.org --no-verify-ssl s3api put-bucket-policy -bucket MyBucket --policy file://BucketPolicyCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information on the
put-bucket-policycommand, see the AWS CLI Command Reference for put-bucket-policy.
The principal element specifies the user that is allowed or denied access to a resource, such as a bucket. Currently, Only NooBaa accounts can be used as principals. In the case of object bucket claims, NooBaa automatically create an account obc-account.<generated bucket name>@noobaa.io.
Bucket policy conditions are not supported.
7.3. Creating an AWS S3 user in the Multicloud Object Gateway
Prerequisites
- A running OpenShift Container Storage Platform
- Access to the Multicloud Object Gateway, see Chapter 2, Accessing the Multicloud Object Gateway with your applications
Procedure
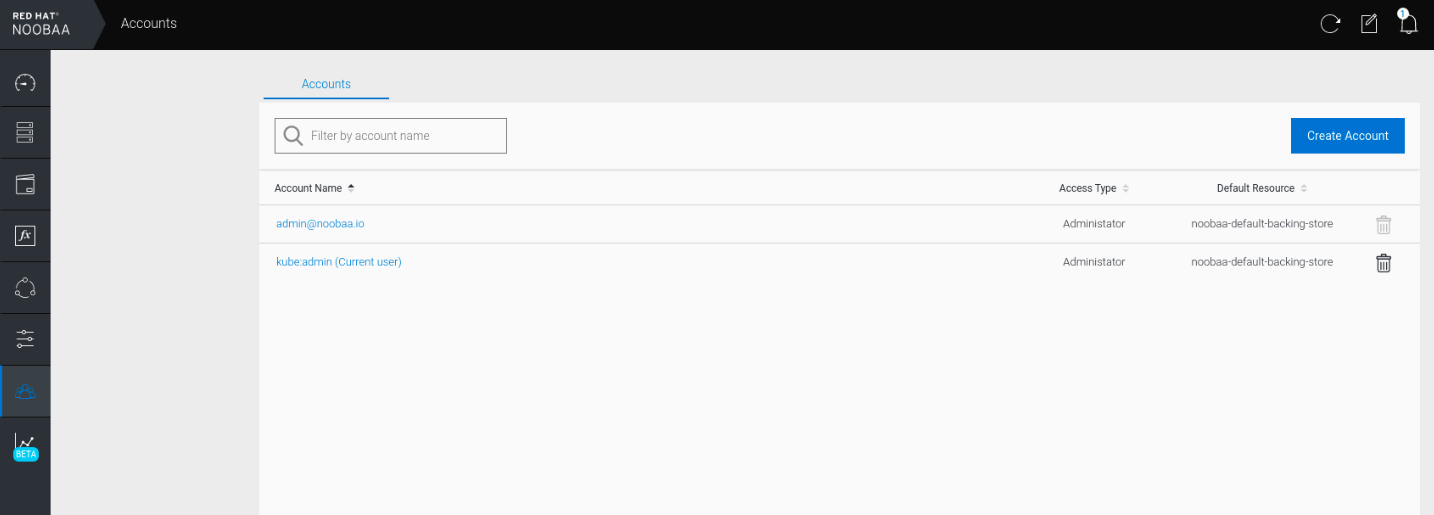
In your OpenShift Storage console, navigate to Overview
Object Service select the Multicloud Object Gateway link: Under the Accounts tab, click Create Account:
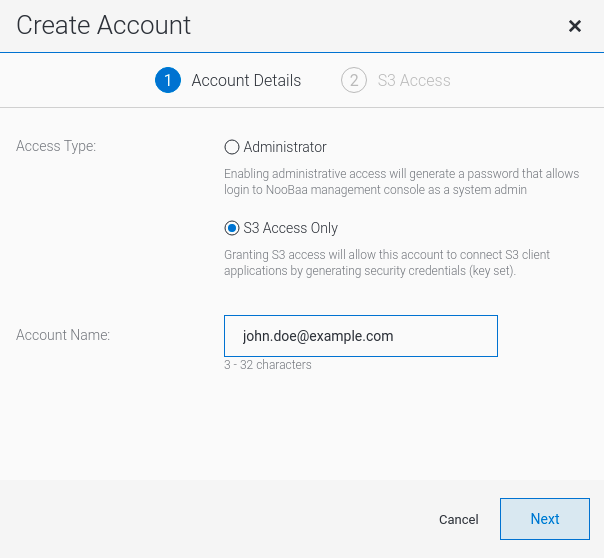
Select S3 Access Only, provide the Account Name, for example, john.doe@example.com. Click Next:
Select S3 default placement, for example, noobaa-default-backing-store. Select Buckets Permissions. A specific bucket or all buckets can be selected. Click Create: