Questo contenuto non è disponibile nella lingua selezionata.
Chapter 4. Configuring Red Hat OpenStack Platform director for Service Telemetry Framework
To collect metrics, events, or both, and to send them to the Service Telemetry Framework (STF) storage domain, you must configure the Red Hat OpenStack Platform (RHOSP) overcloud to enable data collection and transport.
STF can support both single and multiple clouds. The default configuration in RHOSP and STF set up for a single cloud installation.
- For a single RHOSP overcloud deployment with default configuration, see Section 4.1, “Deploying Red Hat OpenStack Platform overcloud for Service Telemetry Framework using director”.
- To plan your RHOSP installation and configuration STF for multiple clouds, see Section 4.3, “Configuring multiple clouds”.
As part of an RHOSP overcloud deployment, you might need to configure additional features in your environment:
- To disable the data collector services, see Section 4.2, “Disabling Red Hat OpenStack Platform services used with Service Telemetry Framework”.
4.1. Deploying Red Hat OpenStack Platform overcloud for Service Telemetry Framework using director
As part of the Red Hat OpenStack Platform (RHOSP) overcloud deployment using director, you must configure the data collectors and the data transport to Service Telemetry Framework (STF).
Procedure
- Section 4.1.1, “Getting CA certificate from Service Telemetry Framework for overcloud configuration”
- Retrieving the AMQ Interconnect password
- Retrieving the AMQ Interconnect route address
- Creating the base configuration for STF
- Configuring the STF connection for the overcloud
- Deploying the overcloud
- Validating client-side installation
Additional resources
- For more information about deploying an OpenStack cloud using director, see Installing and managing Red Hat OpenStack Platform with director.
- To collect data through AMQ Interconnect, see the amqp1 plug-in.
4.1.1. Getting CA certificate from Service Telemetry Framework for overcloud configuration
To connect your Red Hat OpenStack Platform (RHOSP) overcloud to Service Telemetry Framework (STF), retrieve the CA certificate of AMQ Interconnect that runs within STF and use the certificate in RHOSP configuration.
Procedure
View a list of available certificates in STF:
oc get secrets
$ oc get secretsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retrieve and note the content of the
default-interconnect-selfsignedSecret:oc get secret/default-interconnect-selfsigned -o jsonpath='{.data.ca\.crt}' | base64 -d$ oc get secret/default-interconnect-selfsigned -o jsonpath='{.data.ca\.crt}' | base64 -dCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.1.2. Retrieving the AMQ Interconnect password
When you configure the Red Hat OpenStack Platform (RHOSP) overcloud for Service Telemetry Framework (STF), you must provide the AMQ Interconnect password in the STF connection file.
You can disable basic authentication on the AMQ Interconnect connection by setting the value of the transports.qdr.auth parameter of the ServiceTelemetry spec to none. The transports.qdr.auth parameter is absent in versions of STF before 1.5.3, so the default behavior is that basic authentication is disabled. In a new install of STF 1.5.3 or later, the default value of transports.qdr.auth is basic, but if you upgraded to STF 1.5.3, the default value of transports.qdr.auth is none.
Procedure
- Log in to your Red Hat OpenShift Container Platform environment where STF is hosted.
Change to the
service-telemetryproject:oc project service-telemetry
$ oc project service-telemetryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retrieve the AMQ Interconnect password:
oc get secret default-interconnect-users -o json | jq -r .data.guest | base64 -d
$ oc get secret default-interconnect-users -o json | jq -r .data.guest | base64 -dCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.1.3. Retrieving the AMQ Interconnect route address
When you configure the Red Hat OpenStack Platform (RHOSP) overcloud for Service Telemetry Framework (STF), you must provide the AMQ Interconnect route address in the STF connection file.
Procedure
- Log in to your Red Hat OpenShift Container Platform environment where STF is hosted.
Change to the
service-telemetryproject:oc project service-telemetry
$ oc project service-telemetryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retrieve the AMQ Interconnect route address:
oc get routes -ogo-template='{{ range .items }}{{printf "%s\n" .spec.host }}{{ end }}' | grep "\-5671"$ oc get routes -ogo-template='{{ range .items }}{{printf "%s\n" .spec.host }}{{ end }}' | grep "\-5671" default-interconnect-5671-service-telemetry.apps.infra.watchCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.1.4. Creating the base configuration for STF
To configure the base parameters to provide a compatible data collection and transport for Service Telemetry Framework (STF), you must create a file that defines the default data collection values.
Procedure
-
Log in to the undercloud host as the
stackuser. Create a configuration file called
enable-stf.yamlin the/home/stackdirectory.ImportantSetting
PipelinePublishersto an empty list results in no metric data passing to RHOSP telemetry components, such as Gnocchi or Panko. If you need to send data to additional pipelines, the Ceilometer polling interval of30seconds, that you specify inExtraConfig, might overwhelm the RHOSP telemetry components. You must increase the interval to a larger value, such as300, which results in less telemetry resolution in STF.
enable-stf.yaml
4.1.5. Configuring the STF connection for the overcloud
To configure the Service Telemetry Framework (STF) connection, you must create a file that contains the connection configuration of the AMQ Interconnect for the overcloud to the STF deployment. Enable the collection of metrics and storage of the metrics in STF and deploy the overcloud. The default configuration is for a single cloud instance with the default message bus topics. For configuration of multiple cloud deployments, see Section 4.3, “Configuring multiple clouds”.
Prerequisites
- Retrieve the CA certificate from the AMQ Interconnect deployed by STF. For more information, see Section 4.1.1, “Getting CA certificate from Service Telemetry Framework for overcloud configuration”.
- Retrieve the AMQ Interconnect password. For more information, see Section 4.1.2, “Retrieving the AMQ Interconnect password”.
- Retrieve the AMQ Interconnect route address. For more information, see Section 4.1.3, “Retrieving the AMQ Interconnect route address”.
Procedure
-
Log in to the undercloud host as the
stackuser. -
Create a configuration file called
stf-connectors.yamlin the/home/stackdirectory. In the
stf-connectors.yamlfile, configure theMetricsQdrConnectorsaddress to connect the AMQ Interconnect on the overcloud to the STF deployment. You configure the topic addresses for Sensubility, Ceilometer, and collectd in this file to match the defaults in STF. For more information about customizing topics and cloud configuration, see Section 4.3, “Configuring multiple clouds”.stf-connectors.yaml
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
qdr::router_idconfiguration is to override the default value which uses the fully-qualified domain name (FQDN) of the host. In some cases the FQDN can result in a router ID length of greater than 61 characters which results in failed QDR connections. For deployments with shorter FQDN values this is not necessary. -
The
resource_registryconfiguration directly loads the collectd service because you do not include thecollectd-write-qdr.yamlenvironment file for multiple cloud deployments. -
Replace the
hostsub-parameter ofMetricsQdrConnectorswith the value that you retrieved in Section 4.1.3, “Retrieving the AMQ Interconnect route address”. -
Replace the
<password_from_stf>portion of thesaslPasswordsub-parameter ofMetricsQdrConnectorswith the value you retrieved in Section 4.1.2, “Retrieving the AMQ Interconnect password”. -
Replace the
caCertFileContentparameter with the contents retrieved in Section 4.1.1, “Getting CA certificate from Service Telemetry Framework for overcloud configuration”. -
Set
topicvalue ofCeilometerQdrMetricsConfig.topicto define the topic for Ceilometer metrics. The value is a unique topic identifier for the cloud such ascloud1-metering. -
Set
CollectdAmqpInstancessub-parameter to define the topic for collectd metrics. The section name is a unique topic identifier for the cloud such ascloud1-telemetry. -
Set
CollectdSensubilityResultsChannelto define the topic for collectd-sensubility events. The value is a unique topic identifier for the cloud such assensubility/cloud1-telemetry.
-
The
When you define the topics for collectd and Ceilometer, the value you provide is transposed into the full topic that the Smart Gateway client uses to listen for messages.
Ceilometer topic values are transposed into the topic address anycast/ceilometer/<TOPIC>.sample and collectd topic values are transposed into the topic address collectd/<TOPIC>. The value for sensubility is the full topic path and has no transposition from topic value to topic address.
For an example of a cloud configuration in the ServiceTelemetry object referring to the full topic address, see the section called “The clouds parameter”.
4.1.6. Deploying the overcloud
Deploy or update the overcloud with the required environment files so that data is collected and transmitted to Service Telemetry Framework (STF).
Procedure
-
Log in to the undercloud host as the
stackuser. Source the
stackrcundercloud credentials file:source ~/stackrc
$ source ~/stackrcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add your data collection and AMQ Interconnect environment files to the stack with your other environment files and deploy the overcloud:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Include the
ceilometer-write-qdr.yamlfile to ensure that Ceilometer telemetry is sent to STF. -
Include the
qdr-edge-only.yamlfile to ensure that the message bus is enabled and connected to STF message bus routers. -
Include the
enable-stf.yamlenvironment file to ensure that the defaults are configured correctly. -
Include the
stf-connectors.yamlenvironment file to define the connection to STF.
-
Include the
4.1.7. Validating client-side installation
To validate data collection from the Service Telemetry Framework (STF) storage domain, query the data sources for delivered data. To validate individual nodes in the Red Hat OpenStack Platform (RHOSP) deployment, use SSH to connect to the console.
Some telemetry data is available only when RHOSP has active workloads.
Procedure
- Log in to an overcloud node, for example, controller-0.
Ensure that the
metrics_qdrand collection agent containers are running on the node:sudo podman container inspect --format '{{.State.Status}}' metrics_qdr collectd ceilometer_agent_notification ceilometer_agent_central$ sudo podman container inspect --format '{{.State.Status}}' metrics_qdr collectd ceilometer_agent_notification ceilometer_agent_central running running running runningCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteUse this command on compute nodes:
sudo podman container inspect --format '{{.State.Status}}' metrics_qdr collectd ceilometer_agent_compute$ sudo podman container inspect --format '{{.State.Status}}' metrics_qdr collectd ceilometer_agent_computeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Return the internal network address on which AMQ Interconnect is running, for example,
172.17.1.44listening on port5666:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Return a list of connections to the local AMQ Interconnect:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow There are four connections:
- Outbound connection to STF
- Inbound connection from ceilometer
- Inbound connection from collectd
Inbound connection from our
qdstatclientThe outbound STF connection is provided to the
MetricsQdrConnectorshost parameter and is the route for the STF storage domain. The other hosts are internal network addresses of the client connections to this AMQ Interconnect.
To ensure that messages are delivered, list the links, and view the
_edgeaddress in thedelivcolumn for delivery of messages:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To list the addresses from RHOSP nodes to STF, connect to Red Hat OpenShift Container Platform to retrieve the AMQ Interconnect pod name and list the connections. List the available AMQ Interconnect pods:
oc get pods -l application=default-interconnect
$ oc get pods -l application=default-interconnect NAME READY STATUS RESTARTS AGE default-interconnect-7458fd4d69-bgzfb 1/1 Running 0 6d21hCopy to Clipboard Copied! Toggle word wrap Toggle overflow Connect to the pod and list the known connections. In this example, there are three
edgeconnections from the RHOSP nodes with connectionid22, 23, and 24:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To view the number of messages delivered by the network, use each address with the
oc execcommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.2. Disabling Red Hat OpenStack Platform services used with Service Telemetry Framework
Disable the services used when deploying Red Hat OpenStack Platform (RHOSP) and connecting it to Service Telemetry Framework (STF). There is no removal of logs or generated configuration files as part of the disablement of the services.
Procedure
-
Log in to the undercloud host as the
stackuser. Source the
stackrcundercloud credentials file:source ~/stackrc
$ source ~/stackrcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
disable-stf.yamlenvironment file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the following files from your RHOSP director deployment:
-
ceilometer-write-qdr.yaml -
qdr-edge-only.yaml -
enable-stf.yaml -
stf-connectors.yaml
-
Update the RHOSP overcloud. Ensure that you use the
disable-stf.yamlfile early in the list of environment files. By addingdisable-stf.yamlearly in the list, other environment files can override the configuration that would disable the service:openstack overcloud deploy --templates \ -e /home/stack/disable-stf.yaml \ -e [your environment files]
(undercloud)$ openstack overcloud deploy --templates \ -e /home/stack/disable-stf.yaml \ -e [your environment files]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3. Configuring multiple clouds
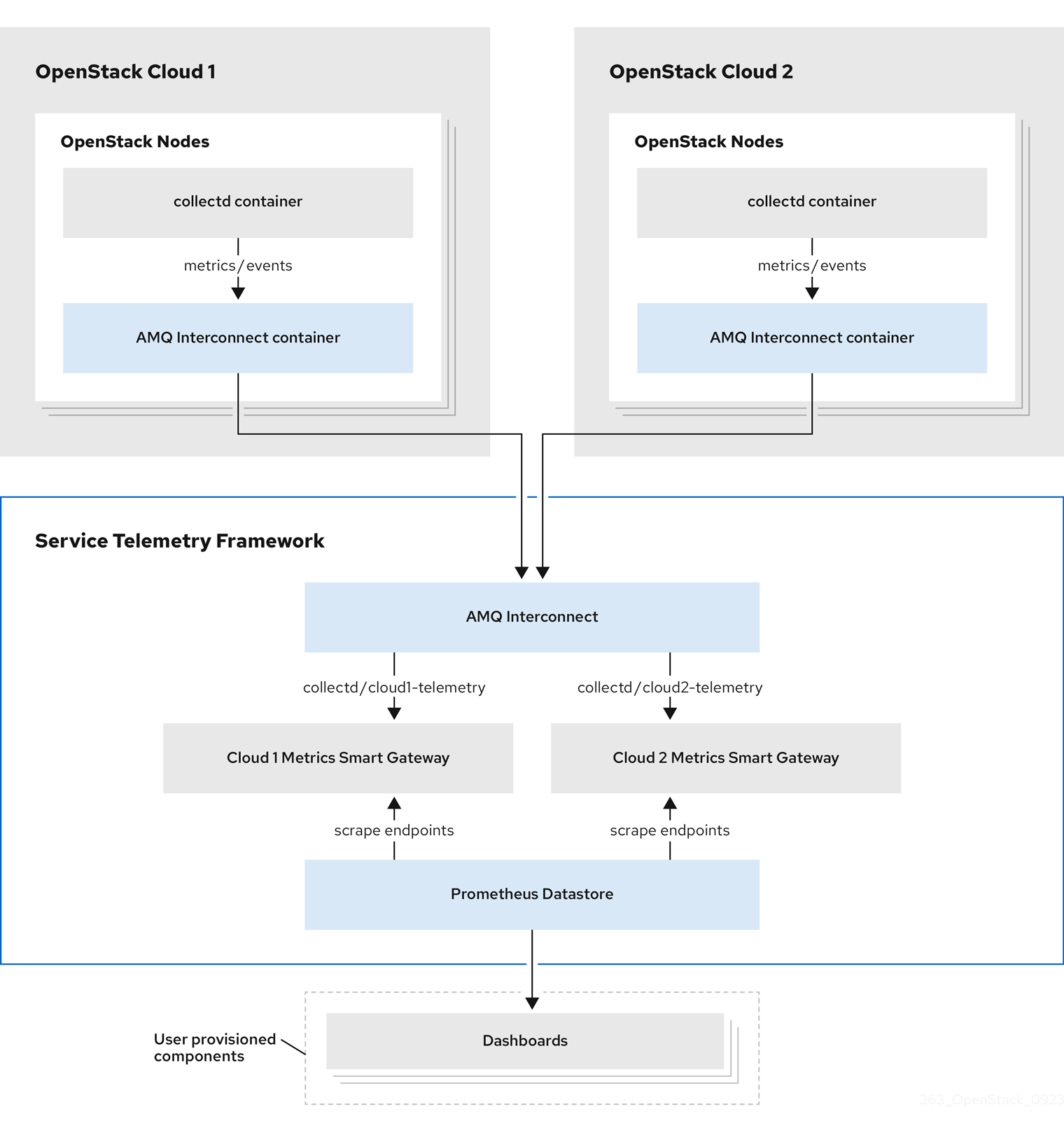
You can configure multiple Red Hat OpenStack Platform (RHOSP) clouds to target a single instance of Service Telemetry Framework (STF). When you configure multiple clouds, every cloud must send metrics and events on their own unique message bus topic. In the STF deployment, Smart Gateway instances listen on these topics to save information to the common data store. Data that is stored by the Smart Gateway in the data storage domain is filtered by using the metadata that each of Smart Gateways creates.
Ensure that you deploy each cloud with a unique cloud domain configuration. For more information about configuring the domain for your cloud deployment, see Section 4.3.4, “Setting a unique cloud domain”.
Figure 4.1. Two RHOSP clouds connect to STF
To configure the RHOSP overcloud for a multiple cloud scenario, complete the following tasks:
- Plan the AMQP address prefixes that you want to use for each cloud. For more information, see Section 4.3.1, “Planning AMQP address prefixes”.
- Deploy metrics and events consumer Smart Gateways for each cloud to listen on the corresponding address prefixes. For more information, see Section 4.3.2, “Deploying Smart Gateways”.
- Configure each cloud with a unique domain name. For more information, see Section 4.3.4, “Setting a unique cloud domain”.
- Create the base configuration for STF. For more information, see Section 4.1.4, “Creating the base configuration for STF”.
- Configure each cloud to send its metrics and events to STF on the correct address. For more information, see Section 4.3.5, “Creating the Red Hat OpenStack Platform environment file for multiple clouds”.
4.3.1. Planning AMQP address prefixes
By default, Red Hat OpenStack Platform (RHOSP) nodes retrieve data through two data collectors; collectd and Ceilometer. The collectd-sensubility plugin requires a unique address. These components send telemetry data or notifications to the respective AMQP addresses, for example, collectd/telemetry. STF Smart Gateways listen on those AMQP addresses for data. To support multiple clouds and to identify which cloud generated the monitoring data, configure each cloud to send data to a unique address. Add a cloud identifier prefix to the second part of the address. The following list shows some example addresses and identifiers:
-
collectd/cloud1-telemetry -
collectd/cloud1-notify -
sensubility/cloud1-telemetry -
anycast/ceilometer/cloud1-metering.sample -
anycast/ceilometer/cloud1-event.sample -
collectd/cloud2-telemetry -
collectd/cloud2-notify -
sensubility/cloud2-telemetry -
anycast/ceilometer/cloud2-metering.sample -
anycast/ceilometer/cloud2-event.sample -
collectd/us-east-1-telemetry -
collectd/us-west-3-telemetry
4.3.2. Deploying Smart Gateways
You must deploy a Smart Gateway for each of the data collection types for each cloud; one for collectd metrics, one for collectd events, one for Ceilometer metrics, one for Ceilometer events, and one for collectd-sensubility metrics. Configure each of the Smart Gateways to listen on the AMQP address that you define for the corresponding cloud. To define Smart Gateways, configure the clouds parameter in the ServiceTelemetry manifest.
When you deploy STF for the first time, Smart Gateway manifests are created that define the initial Smart Gateways for a single cloud. When you deploy Smart Gateways for multiple cloud support, you deploy multiple Smart Gateways for each of the data collection types that handle the metrics and the events data for each cloud. The initial Smart Gateways are defined in cloud1 with the following subscription addresses:
| collector | type | default subscription address |
| collectd | metrics | collectd/telemetry |
| collectd | events | collectd/notify |
| collectd-sensubility | metrics | sensubility/telemetry |
| Ceilometer | metrics | anycast/ceilometer/metering.sample |
| Ceilometer | events | anycast/ceilometer/event.sample |
Prerequisites
- You have determined your cloud naming scheme. For more information about determining your naming scheme, see Section 4.3.1, “Planning AMQP address prefixes”.
-
You have created your list of clouds objects. For more information about creating the content for the
cloudsparameter, see the section called “The clouds parameter”.
Procedure
- Log in to Red Hat OpenShift Container Platform.
Change to the
service-telemetrynamespace:oc project service-telemetry
$ oc project service-telemetryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
defaultServiceTelemetry object and add acloudsparameter with your configuration:WarningLong cloud names might exceed the maximum pod name of 63 characters. Ensure that the combination of the
ServiceTelemetrynamedefaultand theclouds.namedoes not exceed 19 characters. Cloud names cannot contain any special characters, such as-. Limit cloud names to alphanumeric (a-z, 0-9).Topic addresses have no character limitation and can be different from the
clouds.namevalue.oc edit stf default
$ oc edit stf defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the ServiceTelemetry object.
Verify that each Smart Gateway is running. This can take several minutes depending on the number of Smart Gateways:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3.3. Deleting the default Smart Gateways
After you configure Service Telemetry Framework (STF) for multiple clouds, you can delete the default Smart Gateways if they are no longer in use. The Service Telemetry Operator can remove SmartGateway objects that were created but are no longer listed in the ServiceTelemetry clouds list of objects. To enable the removal of SmartGateway objects that are not defined by the clouds parameter, you must set the cloudsRemoveOnMissing parameter to true in the ServiceTelemetry manifest.
If you do not want to deploy any Smart Gateways, define an empty clouds list by using the clouds: [] parameter.
The cloudsRemoveOnMissing parameter is disabled by default. If you enable the cloudsRemoveOnMissing parameter, you remove any manually-created SmartGateway objects in the current namespace without any possibility to restore.
Procedure
-
Define your
cloudsparameter with the list of cloud objects that you want the Service Telemetry Operator to manage. For more information, see the section called “The clouds parameter”. Edit the ServiceTelemetry object and add the
cloudsRemoveOnMissingparameter:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the modifications.
Verify that the Operator deleted the Smart Gateways. This can take several minutes while the Operators reconcile the changes:
oc get smartgateways
$ oc get smartgatewaysCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3.4. Setting a unique cloud domain
To ensure that telemetry from different Red Hat OpenStack Platform (RHOSP) clouds to Service Telemetry Framework (STF) can be uniquely identified and do not conflict, configure the CloudDomain parameter.
Ensure that you do not change host or domain names in an existing deployment. Host and domain name configuration is supported in new cloud deployments only.
Procedure
-
Create a new environment file, for example,
hostnames.yaml. Set the
CloudDomainparameter in the environment file, as shown in the following example:hostnames.yaml
parameter_defaults: CloudDomain: newyork-west-04 CephStorageHostnameFormat: 'ceph-%index%' ObjectStorageHostnameFormat: 'swift-%index%' ComputeHostnameFormat: 'compute-%index%'parameter_defaults: CloudDomain: newyork-west-04 CephStorageHostnameFormat: 'ceph-%index%' ObjectStorageHostnameFormat: 'swift-%index%' ComputeHostnameFormat: 'compute-%index%'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the new environment file to your deployment.
Additional resources
- Section 4.3.5, “Creating the Red Hat OpenStack Platform environment file for multiple clouds”
- Core Overcloud Parameters in the Overcloud Parameters guide
4.3.5. Creating the Red Hat OpenStack Platform environment file for multiple clouds
To label traffic according to the cloud of origin, you must create a configuration with cloud-specific instance names. Create an stf-connectors.yaml file and adjust the values of CeilometerQdrMetricsConfig and CollectdAmqpInstances to match the AMQP address prefix scheme.
If you enabled container health and API status monitoring, you must also modify the CollectdSensubilityResultsChannel parameter. For more information, see Section 6.9, “Red Hat OpenStack Platform API status and containerized services health”.
Prerequisites
- You have retrieved the CA certificate from the AMQ Interconnect deployed by STF. For more information, see Section 4.1.1, “Getting CA certificate from Service Telemetry Framework for overcloud configuration”.
- You have created your list of clouds objects. For more information about creating the content for the clouds parameter, see the clouds configuration parameter.
- You have retrieved the AMQ Interconnect route address. For more information, see Section 4.1.3, “Retrieving the AMQ Interconnect route address”.
- You have created the base configuration for STF. For more information, see Section 4.1.4, “Creating the base configuration for STF”.
- You have created a unique domain name environment file. For more information, see Section 4.3.4, “Setting a unique cloud domain”.
Procedure
-
Log in to the undercloud host as the
stackuser. -
Create a configuration file called
stf-connectors.yamlin the/home/stackdirectory. In the
stf-connectors.yamlfile, configure theMetricsQdrConnectorsaddress to connect to the AMQ Interconnect on the overcloud deployment. Configure theCeilometerQdrMetricsConfig,CollectdAmqpInstances, andCollectdSensubilityResultsChanneltopic values to match the AMQP address that you want for this cloud deployment.stf-connectors.yaml
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
qdr::router_idconfiguration is to override the default value which uses the fully-qualified domain name (FQDN) of the host. In some cases the FQDN can result in a router ID length of greater than 61 characters which results in failed QDR connections. For deployments with shorter FQDN values this is not necessary. -
The
resource_registryconfiguration directly loads the collectd service because you do not include thecollectd-write-qdr.yamlenvironment file for multiple cloud deployments. -
Replace the
hostparameter with the value that you retrieved in Section 4.1.3, “Retrieving the AMQ Interconnect route address”. -
Replace the
caCertFileContentparameter with the contents retrieved in Section 4.1.1, “Getting CA certificate from Service Telemetry Framework for overcloud configuration”. -
Replace the
hostsub-parameter ofMetricsQdrConnectorswith the value that you retrieved in Section 4.1.3, “Retrieving the AMQ Interconnect route address”. -
Set
topicvalue ofCeilometerQdrMetricsConfig.topicto define the topic for Ceilometer metrics. The value is a unique topic identifier for the cloud such ascloud1-metering. -
Set
CollectdAmqpInstancessub-parameter to define the topic for collectd metrics. The section name is a unique topic identifier for the cloud such ascloud1-telemetry. Set
CollectdSensubilityResultsChannelto define the topic for collectd-sensubility events. The value is a unique topic identifier for the cloud such assensubility/cloud1-telemetry.NoteWhen you define the topics for collectd and Ceilometer, the value you provide is transposed into the full topic that the Smart Gateway client uses to listen for messages.
Ceilometer topic values are transposed into the topic address
anycast/ceilometer/<TOPIC>.sampleand collectd topic values are transposed into the topic addresscollectd/<TOPIC>. The value for sensubility is the full topic path and has no transposition from topic value to topic address.For an example of a cloud configuration in the
ServiceTelemetryobject referring to the full topic address, see the section called “The clouds parameter”.
-
The
-
Ensure that the naming convention in the
stf-connectors.yamlfile aligns with thespec.bridge.amqpUrlfield in the Smart Gateway configuration. For example, configure theCeilometerQdrMetricsConfig.topicfield to a value ofcloud1-metering. -
Log in to the undercloud host as the
stackuser. Source the
stackrcundercloud credentials file:source stackrc
$ source stackrcCopy to Clipboard Copied! Toggle word wrap Toggle overflow Include the
stf-connectors.yamlfile and unique domain name environment filehostnames.yamlin theopenstack overcloud deploymentcommand, with any other environment files relevant to your environment:WarningIf you use the
collectd-write-qdr.yamlfile with a customCollectdAmqpInstancesparameter, data publishes to the custom and default topics. In a multiple cloud environment, the configuration of theresource_registryparameter in thestf-connectors.yamlfile loads the collectd service.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Deploy the Red Hat OpenStack Platform overcloud.
Additional resources
- For information about how to validate the deployment, see Section 4.1.7, “Validating client-side installation”.
4.3.6. Querying metrics data from multiple clouds
Data stored in Prometheus has a service label according to the Smart Gateway it was scraped from. You can use this label to query data from a specific cloud.
To query data from a specific cloud, use a Prometheus promql query that matches the associated service label; for example: collectd_uptime{service="default-cloud1-coll-meter"}.