Red Hat AMQ 6
As of February 2025, Red Hat is no longer supporting Red Hat AMQ 6. If you are using AMQ 6, please upgrade: Migrating to AMQ 7.이 콘텐츠는 선택한 언어로 제공되지 않습니다.
8.3. Add User Entries to the Directory Server
Overview
링크 복사링크가 클립보드에 복사되었습니다!
The basic prerequisite for using LDAP authentication with the OSGi container is to have an X.500 directory server running and configured with a collection of user entries. For many use cases, you will also want to configure a number of groups to manage user roles.
Goals
링크 복사링크가 클립보드에 복사되었습니다!
In this portion of the tutorial you will
Adding user entries
링크 복사링크가 클립보드에 복사되었습니다!
Perform the following steps to add user entries to the directory server:
- Ensure that the LDAP server and browser are running.
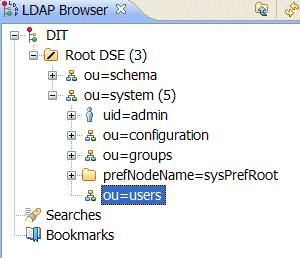
- In the LDAP Browser view, drill down to the ou=users node.
- Select the ou=users node.
- Open the context menu.
- Select
. The New Entry wizard appears. - In the Entry Creation Method pane, check Create entry from scratch.
- Click Next.The Object Classes pane opens.
- In the Object Classes pane, select
inetOrgPersonfrom the list of Available object classes on the left. - Click Add to populate the list of Selected object classes.
Figure 8.3. New Entry Wizard
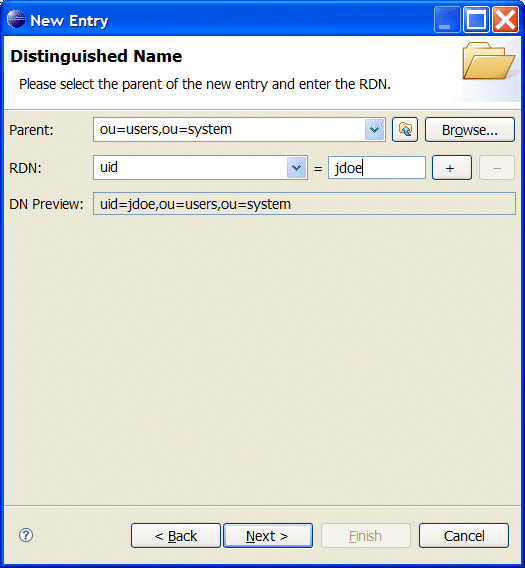
- Click .The Distinguished Name pane opens.
- In the the RDN field, enter
uidin front andjdoeafter the equals sign.Figure 8.4. Distinguished Name Step of New Entry Wizard
- Click .The Attributes pane opens.
- Fill in the remaining mandatory attributes in the Attributes pane.
- Set the cn (common name) attribute to
John Doe - Set the sn (surname) attribute to
Doe.
Figure 8.5. Attributes Step of New Entry Wizard
- Add a
userPasswordattribute to the user entry.- Open the context menu in the Attributes pane.
- Select .The New Attribute wizard appears.
- From the Attribute type drop-down list, select .
- Click .The Password Editor dialog appears.
- In the Enter New Password field, enter the password,
secret. - Click OK.The userPassword attribute will appear in the attributes editor.
- Click .
Adding groups for the roles
링크 복사링크가 클립보드에 복사되었습니다!
To add the groups that define the roles:
- Create a new organizational unit to contain the role groups.
- In the LDAP Browser view, select the ou=system node.
- Open the context menu.
- Select
. The New Entry wizard appears. - In the Entry Creation Method pane, check Create entry from scratch.
- Click Next.The Object Classes pane opens.
- Select
organizationalUnitfrom the list of Available object classes on the left. - Click Add to populate the list of Selected object classes.
- Click .The Distinguished Name pane opens.
- In the the RDN field, enter
ouin front androlesafter the equals sign. - Click .The Attributes pane opens.
- Click .
NoteThis step is required because Apache DS only allows administrators access to entries inou=system,ou=groups. - In the LDAP Browser view, drill down to the ou=roles node.
- Select the ou=roles node.
- Open the context menu.
- Select
. The New Entry wizard appears. - In the Entry Creation Method pane, check Create entry from scratch.
- Click Next.The Object Classes pane opens.
- Select
groupOfNamesfrom the list of Available object classes on the left. - Click Add to populate the list of Selected object classes.
- Click .The Distinguished Name pane opens.
- In the the RDN field, enter
cnin front andadminafter the equals sign. - Click .The Attributes pane opens and you are presented with a DN editor.
- Enter
uid=jdoe. - Click .
- Click .
- In Step 13, use
uid=janedoe. - In Step 13, use
uid=janedoe. - In Step 13, use
uid=crider.