이 콘텐츠는 선택한 언어로 제공되지 않습니다.
8. Security
Note
The Security Guide assists users and administrators in learning the processes and practices of securing workstations and servers against local and remote intrusion, exploitation and malicious activity.
8.1. System Security Services Daemon (SSSD)
링크 복사링크가 클립보드에 복사되었습니다!
The System Security Services Daemon (SSSD) is a new feature in Red Hat Enterprise Linux 6 that implements a set of services for central management of identity and authentication. Centralizing identity and authentication services enables local caching of identities, allowing users to still identify in cases where the connection to the server is interrupted. SSSD supports many types of identity and authentication services, including: Red Hat Directory Server, Active Directory, OpenLDAP, 389, Kerberos and LDAP.
Note
The Deployment Guide contains a section that describes how to install and configure the System Security Services Daemon (SSSD), and how to use the features that it provides.
8.2. Security-Enhanced Linux (SELinux)
링크 복사링크가 클립보드에 복사되었습니다!
Security-Enhanced Linux (SELinux) adds Mandatory Access Control (MAC) to the Linux kernel, and is enabled by default in Red Hat Enterprise Linux 6. A general purpose MAC architecture needs the ability to enforce an administratively-set security policy over all processes and files in the system, basing decisions on labels containing a variety of security-relevant information.
8.2.1. Confined Users
링크 복사링크가 클립보드에 복사되었습니다!
Traditionally, SELinux is used to define and control how an application interacts with the system. SELinux in Red Hat Enterprise Linux 6 introduces a set of policies that allows system administrators to control what particular users can access on a system.
8.2.2. Sandbox
링크 복사링크가 클립보드에 복사되었습니다!
SELinux in Red Hat Enterprise Linux 6 features the new security sandbox feature. The security sandbox adds a set of SELinux policies that enables a system administrator to run any application within a tightly confined SELinux domain. Using the sandbox, system administrators can test the processing of untrusted content without damaging the system.
8.2.3. X Access Control Extension (XACE)
링크 복사링크가 클립보드에 복사되었습니다!
The X Window System (commonly refered to a "X") provides the base framework for displaying the graphical user interface (GUI) on Red Hat Enterprise Linux 6. This release features the new X Access Control Extension (XACE), which permits SELinux to access decisions made within X, specifically, controlling information flow between window objects.
8.3. Backup Passphrases for Encrypted Storage Devices
링크 복사링크가 클립보드에 복사되었습니다!
Red Hat Enterprise Linux provides the ability to encrypt the data on storage devices, assisting in the prevention of unauthorized access of the data. Encryption is achieved by transforming the data into a format that can only be read using a specific encryption key. This key — which is created during the installation process, and protected by a passphrase — is the only way to decrypt the encrypted data.
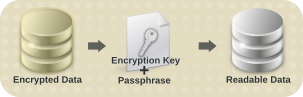
Figure 7. Decrypting Data
However, if the passphrase is misplaced, the encryption key cannot be used, and data on the encrypted storage device cannot be accessed.
Red Hat Enterprise Linux 6 provides the ability to save encryption keys and create backup passphrases. This feature allows for the recovery of an encrypted volume (including the root device) even when the original passphrase is misplaced.
8.4. sVirt
링크 복사링크가 클립보드에 복사되었습니다!
libvirt is a C language application programming interface (API) for managing and interacting with the virtualization capabilities of Red Hat Enterprise Linux 6. In this release, libvirt features the new sVirt component. sVirt integrates with SELinux, providing security mechanisms to prevent unauthorized access of guests and hosts in a virtualized environment.
8.5. Enterprise Security Client
링크 복사링크가 클립보드에 복사되었습니다!
The Enterprise Security Client (ESC) is a simple GUI that allows Red Hat Enterprise Linux to manage smart cards and tokens. New smart cards can be formatted and enrolled, meaning that new keys are generated and certificates requested for the smart card automatically. The smart card lifecycle can be managed, as well, so that lost smart cards can have their certificates revoked and expired certificates can be renewed. The ESC works in conjunction with a larger public-key infrastructure management product, either Red Hat Certificate System or Dogtag PKI.