Fuse 6 is no longer supported
As of February 2025, Red Hat Fuse 6 is no longer supported. If you are using Fuse 6, please upgrade to Red Hat build of Apache Camel.이 콘텐츠는 선택한 언어로 제공되지 않습니다.
1.2. Apache ActiveMQ Security
Overview
링크 복사링크가 클립보드에 복사되었습니다!
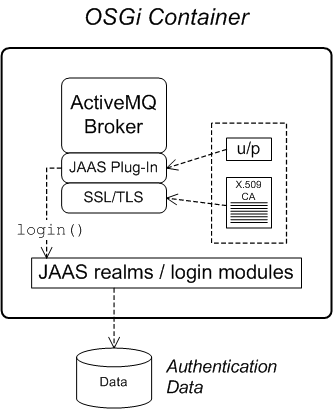
Figure 1.2, “Apache ActiveMQ Security Architecture” shows an overview of the Apache ActiveMQ security architecture. The main security features supported by Apache ActiveMQ are the SSL/TLS security layer and the JAAS security layer. The SSL/TLS security layer provides message encryption and identifies the broker to its clients, while the JAAS security layer identifies clients to the broker.
Figure 1.2. Apache ActiveMQ Security Architecture
SSL/TLS security
링크 복사링크가 클립보드에 복사되었습니다!
Apache ActiveMQ supports the use of SSL/TLS to secure client-to-broker and broker-to-broker connections, where the underlying SSL/TLS implementation is provided by the Java Secure Socket Extension (JSSE). When deploying brokers and clients in an OSGi container, you cannot configure SSL/TLS security using JSSE system properties, however. You must either use XML configuration (for example, in a Spring or a blueprint file) or set the security properties by programming.
JAAS security
링크 복사링크가 클립보드에 복사되었습니다!
Apache ActiveMQ also supports JAAS security, which typically requires clients to log on to the broker by providing username and password credentials. When deployed in an OSGi container, the broker's JAAS security must be integrated with the container's JAAS security (as described in Section 1.1, “OSGi Container Security”).
JAAS plug-ins
링크 복사링크가 클립보드에 복사되었습니다!
To enable JAAS security in a broker, you install one of the supported JAAS plug-ins. Each of the JAAS plug-ins supports a different kind of credentials or implements a somewhat different login procedure. The following JAAS plug-ins are currently supported by Apache ActiveMQ:
jaasAuthenticationPluginsupports authentication using JMS username/password credentials.jaasCertificateAuthenticationPluginsupports additional checking of the X.509 certificate received from a client (usable only in combination with SSL/TLS security).jaasDualAuthenticationPluginis a hybrid version of the other two plug-ins. This plug-in checks the client's X.509 certificate, if and only if SSL/TLS is enabled. Otherwise, it falls back to checking the JMS username/password credentials.
JAAS login modules
링크 복사링크가 클립보드에 복사되었습니다!
Apache ActiveMQ provides a number of different JAAS login module implementations, which are used to define JAAS realms. The role of a JAAS login module is to store authentication and authorization data. The following JAAS login modules are currently implemented by Apache ActiveMQ:
PropertiesLoginModule—stores username/password credentials and user group data in a pair of plain text files.LDAPLoginModule—an adapter that enables you to store username/password credentials and group data in an LDAP database.GuestLoginModule—logs all users into a default guest account. This login module is usually used in combination with a preceding login module (defined in the same login entry), where the guest login module is activated only when the preceding login attempt has failed.TextFileCertificateLoginModule—tests the X.509 certificate received from the client by comparing the Distinguished Name (DN) embedded in the client certificate with the list of DNs stored in a plain text file.