Este conteúdo não está disponível no idioma selecionado.
6.5. Managing Synchronization Agreements
6.5.1. Creating Synchronization Agreements
ipa-replica-manage connect command because it creates a connection to the Active Directory domain. To establish an encrypted connection to Active Directory, IdM must to trust the Windows CA certificate.
- Copy the root certificate authority (CA) certificate to the IdM server:
- If your Active Directory CA certificate is self-signed:
- Export the Active Directory CA certificate on the Windows server.
- Press the Super key+R combination to open the Run dialog.
- Enter
certsrv.mscand click . - Right-click on the name of the local Certificate Authority and choose Properties.
- On the General tab, select the certificate to export in the CA certificates field and click .
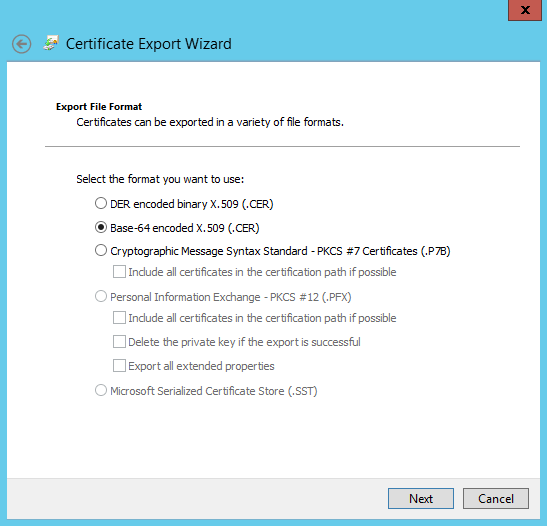
- On the Details tab, click to start the Certificate Export Wizard.
- Click , and then select Base-64 encoded X.509 (.CER).
- Specify a suitable directory and file name for the exported file. Click to export the certificate, and then click .
- Copy the exported certificate to the IdM server machine.
- If your Active Directory CA certificate is signed by an external CA:
- To find out what certificate is the CA root certificate, display the certificate chain:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow The previous example shows that the Active Directory server's CA certificate is signed byCN=Demo CA-1, which is signed byCN=Demo Root CA 2. This means thatCN=Demo Root CA 2is the root CA. - Copy the CA certificate to the IdM server.
- Remove any existing Kerberos credentials on the IdM server.
kdestroy
$ kdestroyCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Use the
ipa-replica-managecommand to create a Windows synchronization agreement. This requires the--winsyncoption. If passwords will be synchronized as well as user accounts, then also use the--passsyncoption and set a password to use for Password Synchronization.The--binddnand--bindpwoptions give the user name and password of the system account on the Active Directory server that IdM will use to connect to the Active Directory server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow --winsync: Identifies this as a Windows synchronization agreement.--binddn: IdM uses this DN of an Active Directory account to bind to the remote directory and synchronize attributes.--bindpw: Password for the synchronization account.--cacert: Full path and file name to the:- Active Directory CA certificate, if the CA was self-signed.
- external CA certificate, if the Active Directory CA was signed by an external CA.
--win-subtree: DN of the Windows directory subtree containing the users to synchronize. The default value iscn=Users,$SUFFIX.AD_server_name: Fully qualified domain name (FQDN) of the Active Directory domain controller.
- When prompted, enter the Directory Manager password.
- Optional. Configure Password Synchronization, as in Section 6.6.2, “Setting up Password Synchronization”. Without the Password Synchronization client, user attributes are synchronized between the peer servers, but passwords are not.
Note
The Password Synchronization client captures password changes and then synchronizes them between Active Directory and IdM. This means that it synchronizes new passwords or password updates.Existing passwords, which are stored in a hashed form in both IdM and Active Directory, cannot be decrypted or synchronized when the Password Synchronization client is installed, so existing passwords are not synchronized. User passwords must be changed to initiate synchronization between the peer servers.
6.5.2. Changing the Behavior for Synchronizing User Account Attributes
ldapmodify command to modify the LDAP server entry directly.
ipaWinSyncAcctDisable attribute. (Changing this means that if an account is disabled in Active Directory, it is still active in IdM and vice versa.)
General User Account Parameters
ipaWinSyncNewEntryFilter: Sets the search filter to use to find the entry which contains the list of object classes to add to new user entries.Default value:(cn=ipaConfig)ipaWinSyncNewUserOCAttr: Sets the attribute in the configuration entry which actually contains the list of object classes to add to new user entries.Default value:ipauserobjectclassesipaWinSyncHomeDirAttr: Identifies which attribute in the entry contains the default location of the POSIX home directory.Default value:ipaHomesRootDiripaWinSyncUserAttr: Sets an additional attribute with a specific value to add to Active Directory users when they are synchronized over from the Active Directory domain. If the attribute is multi-valued, then it can be set multiple times, and the synchronization process adds all of the values to the entry.Example:ipaWinSyncUserAttr: attributeName attributeValueNote
This only sets the attribute value if the entry does not already have that attribute present. If the attribute is present, then the entry's value is used when the Active Directory entry is synchronized over.ipaWinSyncForceSync: Sets whether existing IdM users that match existing AD users should be forced to be synchronized. When set totrue, such IdM users are automatically edited so that they are synchronized.Possible values:true | falseIf an IdM user account has auidparameter which is identical to thesAMAccountNamein an existing Active Directory user, then that account is not synchronized by default. This attribute tells the synchronization service to add thentUserandntUserDomainIdto the IdM user entries automatically, which allows them to be synchronized.
User Account Lock Parameters
ipaWinSyncAcctDisable: Sets which way to synchronize account lockout attributes. It is possible to control which account lockout settings are in effect. For example,to_admeans that when account lockout attribute is set in IdM, its value is synchronized over to Active Directory and overrides the local Active Directory value. By default, account lockout attributes are synchronized from both domains.Possible values:both(default),to_ad,to_ds,noneipaWinSyncInactivatedFilter: Sets the search filter to use to find the DN of the group used to hold inactivated (disabled) users. This does not need to be changed in most deployments.Default value:(&(cn=inactivated)(objectclass=groupOfNames))
Group Parameters
ipaWinSyncDefaultGroupAttr: Sets the attribute in the new user account to reference to see what the default group for the user is. The group name in the entry is then used to find thegidNumberfor the user account.Default value:ipaDefaultPrimaryGroupipaWinSyncDefaultGroupFilter: Sets the attribute in the new user account to reference to see what the default group for the user is. The group name in the entry is then used to find thegidNumberfor the user account.Default value:ipaDefaultPrimaryGroup
Realm Parameters
ipaWinSyncRealmAttr: Sets the attribute which contains the realm name in the realm entry.Default value:cnipaWinSyncRealmFilter: Sets the search filter to use to find the entry which contains the IdM realm name.Default value:(objectclass=krbRealmContainer)
6.5.3. Changing the Synchronized Windows Subtree
cn=users,cn=accounts,$SUFFIX, and for Active Directory, the default is CN=Users,$SUFFIX.
--win-subtree option. After the agreement is created, the Active Directory subtree can be changed by using the ldapmodify command to edit the nsds7WindowsReplicaSubtree value in the synchronization agreement entry.
- Get the name of the synchronization agreement, using
ldapsearch. This search returns only the values for thednandnsds7WindowsReplicaSubtreeattributes instead of the entire entry.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Modify the synchronization agreement
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.4. Configuring Uni-directional Synchronization
oneWaySync parameter on the synchronization agreement. The possible values are fromWindows (for Active Directory to Identity Management synchronization) and toWindows (for Identity Management to Active Directory synchronization).
Important
6.5.5. Deleting Synchronization Agreements
ipa-replica-manage disconnect command and then the host name of the Active Directory server.
- Delete the synchronization agreement.
ipa-replica-manage disconnect adserver.ad.example.com
# ipa-replica-manage disconnect adserver.ad.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - List the certificates in the IdM directory certificate database:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Remove the Active Directory CA certificate from the IdM server database:
certutil -D -d /etc/dirsrv/slapd-IDM-EXAMPLE-COM/ -n "CN=adserver,DC=ad,DC=example,DC=com"
# certutil -D -d /etc/dirsrv/slapd-IDM-EXAMPLE-COM/ -n "CN=adserver,DC=ad,DC=example,DC=com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.6. Winsync Agreement Failures
One of the most common synchronization agreement failures is that the IdM server cannot connect to the Active Directory server:
"Update failed! Status: [81 - LDAP error: Can't contact LDAP server]
"Update failed! Status: [81 - LDAP error: Can't contact LDAP server]
/etc/dirsrv/slapd-DOMAIN/ directory) with the name Imported CA. This can be checked using certutil:
certutil -d /etc/dirsrv/slapd-DOMAIN-NAME -D -n "Imported CA"
# certutil -d /etc/dirsrv/slapd-DOMAIN-NAME -D -n "Imported CA"For some entries in the user database, there may be an informational error message that the password is not being reset because the entry already exists:
"Windows PassSync entry exists, not resetting password"
"Windows PassSync entry exists, not resetting password"