Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
9.6. Enabling Publishing
Publishing can be enabled for only files, only LDAP, or both. Publishing should be enabled after setting up publishers, rules, and mappers. Once enabled, the server attempts to begin publishing. If publishing was not configured correctly before being enabled, publishing may exhibit undesirable behavior or may fail.
Note
Configure CRLs. CRLs must be configured before they can be published. See Chapter 7, Revoking Certificates and Issuing CRLs.
- Log into the Certificate Manager Console.
pkiconsole https://server.example.com:8443/ca
- In the Configuration tab, select Certificate Manager from the navigation tree on the left. Select Publishing.The right pane shows the details for publishing to an LDAP-compliant directory.
- To enable publishing to a file only, select Enable Publishing.
- To enable LDAP publishing, select both Enable Publishing and Enable Default LDAP Connection.
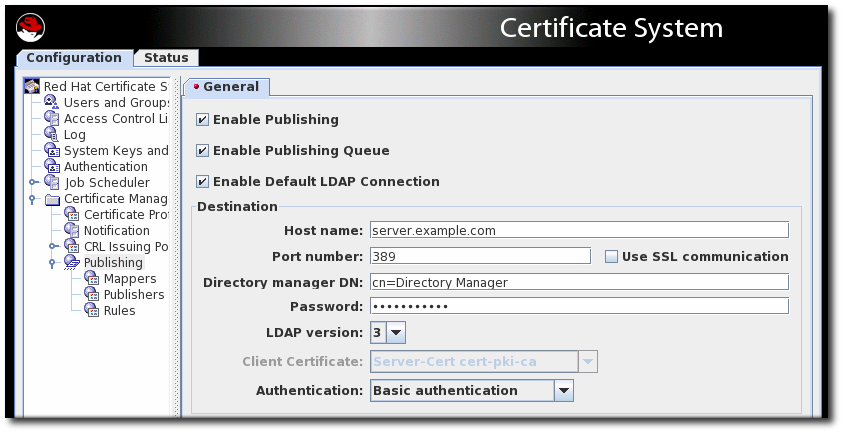 In the Destination section, set the information for the Directory Server instance.
In the Destination section, set the information for the Directory Server instance.- Host name. If the Directory Server is configured for SSL client authenticated communication, the name must match the
cncomponent in the subject DN of the Directory Server's SSL server certificate.The hostname can be the fully-qualified domain name or an IPv4 or IPv6 address. - Port number.
- Directory Manager DN. This is the distinguished name (DN) of the directory entry that has Directory Manager privileges. The Certificate Manager uses this DN to access the directory tree and to publish to the directory. The access control set up for this DN determines whether the Certificate Manager can perform publishing. It is possible to create another DN that has limited read-write permissions for only those attributes that the publishing system actually needs to write.
- Password. This is the password which the CA uses to bind to the LDAP directory to which the certificate or CRL is published. The Certificate Manager saves this password in its
password.conffile. For example:CA LDAP Publishing:password
Note
The parameter name which identifies the publishing password (CA LDAP Publishing) is set in the Certificate Manager'sCS.cfgfile in theca.publish.ldappublish.ldap.ldapauth.bindPWPromptparameter, and it can be edited. - Client certificate. This sets the certificate the Certificate Manager uses for SSL client authentication to the publishing directory. By default, the Certificate Manager uses its SSL server certificate.
- LDAP version. Select LDAP version 3.
- Authentication. The way the Certificate Manager authenticates to the Directory Server. The choices are
Basic authenticationandSSL client authentication.If the Directory Server is configured for basic authentication or for SSL communication without client authentication, selectBasic authenticationand specify values for the Directory manager DN and password.If the Directory Server is configured for SSL communication with client authentication, selectSSL client authenticationand theUse SSL communicationoption, and identify the certificate that the Certificate Manager must use for SSL client authentication to the directory.
The server attempts to connect to the Directory Server. If the information is incorrect, the server displays an error message.
Note
pkiconsole is being deprecated.