Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
3.5. Setting the Signing Algorithms for Certificates
The CA's signing certificate can sign the certificates it issues with any public key algorithm supported by the CA. For example, an ECC signing certificate can sign both ECC and RSA certificate requests as long as both ECC and RSA algorithms are supported by the CA. An RSA signing certificate can can sign a PKCS #10 request with EC keys, but may not be able to sign CRMF certificate requests with EC keys if the ECC module is not available for the CA to verify the CRMF proof of possession (POP).
ECC and RSA are public key encryption and signing algorithms. Both public key algorithms support different cipher suites, algorithms used to encrypt and decrypt data. Part of the function of the CA signing certificate is to issue and sign certificates using one of its supported cipher suites.
Each profile can define which cipher suite the CA should use to sign certificates processed through that profile. If no signing algorithm is set, then the profile uses whatever the default signing algorithm is.
3.5.1. Setting the CA's Default Signing Algorithm
- Open the CA console.
pkiconsole https://server.example.com:8443/ca
- In the Configuration tab, expand the Certificate Manager tree.
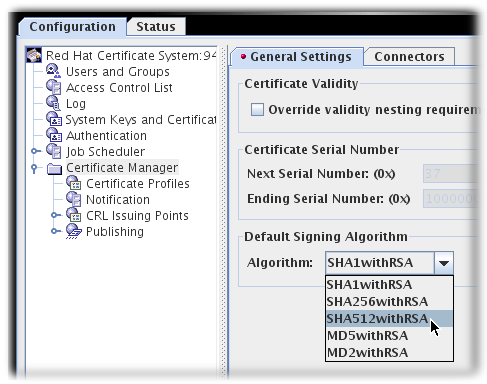
- In the General Settings tab, set the algorithm to use in the Algorithm drop-down menu.
Note
pkiconsole is being deprecated.
3.5.2. Setting the Signing Algorithm Default in a Profile
Each profile has a Signing Algorithm Default extension defined. The default has two settings: a default algorithm and a list of allowed algorithms, if the certificate request specifies a different algorithm. If no signing algorithms are specified, then the profile uses whatever is set as the default for the CA.
In the profile's
.cfg file, the algorithm is set with two parameters:
policyset.cmcUserCertSet.8.constraint.class_id=signingAlgConstraintImpl policyset.cmcUserCertSet.8.constraint.name=No Constraint policyset.cmcUserCertSet.8.constraint.params.signingAlgsAllowed=SHA256withRSA,SHA512withRSA,SHA256withEC,SHA384withRSA,SHA384withEC,SHA512withEC policyset.cmcUserCertSet.8.default.class_id=signingAlgDefaultImpl policyset.cmcUserCertSet.8.default.name=Signing Alg policyset.cmcUserCertSet.8.default.params.signingAlg=-
To configure the Signing Algorithm Default through the console:
Note
Before a profile can be edited, it must first be disabled by an agent.
- Open the CA console.
pkiconsole https://server.example.com:8443/ca
- In the Configuration tab, expand the Certificate Manager tree.
- Click the Certificate Profiles item.
- Click the Policies tab.
- Select the Signing Alg policy, and click the button.
- To set the default signing algorithm, set the value in the Defaults tab. If this is set to -, then the profile uses the CA's default.
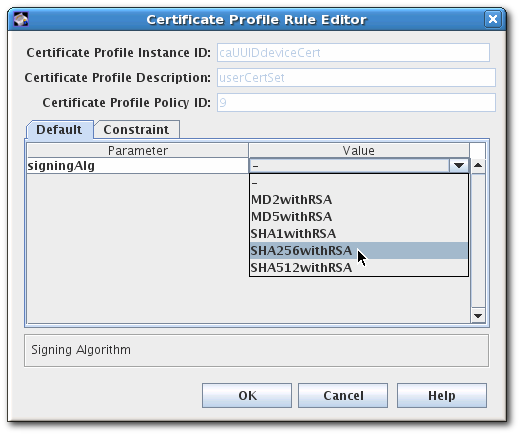
- To set a list of allowed signing algorithms which can be accepted in a certificate request, open the Constraints tab, and set the list of algorithms in the Value field for
signingAlgsAllowed.The possible values for the constraint are listed in Section B.2.10, “Signing Algorithm Constraint”.
Note
pkiconsole is being deprecated.