Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 2. Using system-wide cryptographic policies
The system-wide cryptographic policies component configures the core cryptographic subsystems, which cover the TLS, IPsec, SSH, DNSSEC, and Kerberos protocols. As an administrator, you can select one of the provided cryptographic policies for your system.
2.1. System-wide cryptographic policies
The RHEL system-wide cryptographic policies configure core subsystems, such as TLS and SSH, which ensures that applications reject weak algorithms by default. The four predefined policies are DEFAULT, LEGACY, FUTURE, and FIPS.
When a system-wide policy is set up, applications in RHEL follow it and deny using algorithms and protocols that do not meet the policy, unless you explicitly request the application to do so. That is, the policy applies to the default behavior of applications when running with the system-provided configuration but you can override it if required.
2.1.1. Predefined cryptographic policies
RHEL 10 contains the following predefined policies:
DEFAULT- The default system-wide cryptographic policy level offers secure settings for current threat models. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 2048 bits long. TLS ciphers that use the RSA key exchange are rejected.
LEGACY- Ensures maximum compatibility with Red Hat Enterprise Linux 6 and earlier; it is less secure due to an increased attack surface. CBC-mode ciphers are allowed to be used with SSH. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 2048 bits long. SHA-1 signatures are allowed outside TLS. Ciphers that use the RSA key exchange are accepted.
FUTUREA stricter forward-looking security level intended for testing a possible future policy. This policy does not allow the use of SHA-1 in DNSSEC or as an HMAC. SHA2-224 and SHA3-224 hashes are rejected. 128-bit ciphers are disabled. CBC-mode ciphers are disabled except in Kerberos. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 3072 bits long. If your system communicates on the public internet, you might face interoperability problems.
ImportantBecause a cryptographic key used by a certificate on the Customer Portal API does not meet the requirements by the
FUTUREsystem-wide cryptographic policy, theredhat-support-toolutility does not work with this policy level at the moment.To work around this problem, use the
DEFAULTcryptographic policy while connecting to the Customer Portal API.FIPSConforms with the FIPS 140 requirements. Red Hat Enterprise Linux systems in FIPS mode use this policy.
NoteYour system is not FIPS-compliant after you set the
FIPScryptographic policy. The only correct way to make your RHEL system compliant with the FIPS 140 standards is by installing it in FIPS mode.RHEL also provides the
FIPS:OSPPsystem-wide subpolicy, which contains further restrictions for cryptographic algorithms required by the Common Criteria (CC) certification. The system becomes less interoperable after you set this subpolicy. For example, you cannot use RSA and DH keys shorter than 3072 bits, additional SSH algorithms, and several TLS groups. SettingFIPS:OSPPalso prevents connecting to Red Hat Content Delivery Network (CDN) structure. Furthermore, you cannot integrate Active Directory (AD) into the IdM deployments that useFIPS:OSPP, communication between RHEL hosts that useFIPS:OSPPand AD domains might not work, or some AD accounts might not be able to authenticate.NoteYour system is not CC-compliant after you set the
FIPS:OSPPcryptographic subpolicy. The only correct way to make your RHEL system compliant with the CC standard is by following the guidance provided in thecc-configpackage. See the Common Criteria section on the Product compliance Red Hat Customer Portal page for a list of certified RHEL versions, validation reports, and links to CC guides.
Red Hat continuously adjusts all policy levels so that all libraries provide secure defaults, except when using the LEGACY policy. Even though the LEGACY profile does not provide secure defaults, it does not include any algorithms that are easily exploitable. As such, the set of enabled algorithms or acceptable key sizes in any provided policy might change during the lifetime of Red Hat Enterprise Linux.
Such changes reflect new security standards and new security research. If you must ensure interoperability with a specific system for the whole lifetime of Red Hat Enterprise Linux, opt out from the system-wide cryptographic policies for components that interact with that system or re-enable specific algorithms by using custom cryptographic policies.
The specific algorithms and ciphers described as allowed in the policy levels are available only if an application supports them:
LEGACY | DEFAULT | FIPS | FUTURE | |
|---|---|---|---|---|
| IKEv1 | no | no | no | no |
| 3DES | no | no | no | no |
| RC4 | no | no | no | no |
| DH | min. 2048-bit | min. 2048-bit | min. 2048-bit | min. 3072-bit |
| RSA | min. 2048-bit | min. 2048-bit | min. 2048-bit | min. 3072-bit |
| DSA | no | no | no | no |
| TLS v1.1 and older | no | no | no | no |
| TLS v1.2 and newer | yes | yes | yes | yes |
| SHA-1 in digital signatures and certificates | yes[a] | no | no | no |
| CBC mode ciphers | yes | no[b] | no[c] | no[d] |
| Symmetric ciphers with keys < 256 bits | yes | yes | yes | no |
[a]
SHA-1 signatures are disabled in TLS contexts
[b]
CBC ciphers are disabled for SSH
[c]
CBC ciphers are disabled for all protocols except Kerberos
[d]
CBC ciphers are disabled for all protocols except Kerberos
| ||||
You can find further details about cryptographic policies and covered applications in the crypto-policies(7) man page on your system.
2.1.2. Post-quantum cryptography
RHEL 10.0 introduced post-quantum cryptography (PQC) in its core cryptographic subsystems. The purpose of PQC is to safeguard the confidentiality, integrity, and authenticity of digital communication and stored data against future attacks that use cryptographically relevant quantum computers (CRQCs).
While CRQCs are not currently operational, continued advances in quantum computing might render classic cryptographic algorithms such as RSA and elliptic curve cryptography computationally feasible to break. PQC algorithms mitigate this anticipated long-term security risk by providing quantum-resistant equivalents. You can prevent the current risk of "harvest now, decrypt later" attacks by configuring RHEL with PQC.
Starting with RHEL 10.1, post-quantum cryptography (PQC) algorithms are enabled by default in all predefined policy levels. To turn off support for post-quantum cryptography, apply the NO-PQ subpolicy to your selected cryptographic policy.
2.2. Changing the system-wide cryptographic policy
You can change the system-wide cryptographic policy on your system by using the update-crypto-policies tool and restarting your system. With update-crypto-policies, you can quickly switch between predefined policies such as DEFAULT, LEGACY, or FUTURE.
The update-crypto-policies(8) man page on your system provides the reference of all options, corresponding files, and per-application details.
Prerequisites
- You have root privileges on the system.
Procedure
Optional: Display the current cryptographic policy:
update-crypto-policies --show DEFAULT
$ update-crypto-policies --show DEFAULTCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the new cryptographic policy:
update-crypto-policies --set <POLICY> <POLICY>
# update-crypto-policies --set <POLICY> <POLICY>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<POLICY>with the policy or subpolicy you want to set, for example,FUTURE,LEGACY, orFIPS:OSPP.Restart the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Display the current cryptographic policy:
update-crypto-policies --show <POLICY>
$ update-crypto-policies --show <POLICY>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.3. Switching the system-wide cryptographic policy to mode compatible with earlier releases
Switch to the LEGACY cryptographic policy if environments require compatibility with systems such as RHEL 6 or earlier. This action sacrifices security for interoperability with insecure protocols.
Switching to the LEGACY policy results in a less secure system and applications.
Prerequisites
-
Commands that start with the
#command prompt require administrative privileges provided bysudoor root user access. For information on how to configuresudoaccess, see Enabling unprivileged users to run certain commands.
Procedure
To switch the system-wide cryptographic policy to
LEGACY, enter:update-crypto-policies --set LEGACY Setting system policy to LEGACY
# update-crypto-policies --set LEGACY Setting system policy to LEGACYCopy to Clipboard Copied! Toggle word wrap Toggle overflow For the list of available cryptographic policies, see the
update-crypto-policies(8)man page on your system.To make your cryptographic settings effective for already running services and applications, restart the system:
reboot
$ rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
After the restart, verify the current policy is set to
LEGACY:update-crypto-policies --show LEGACY
$ update-crypto-policies --show LEGACYCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
-
For defining custom cryptographic policies, see the
Custom Policiessection in theupdate-crypto-policies(8)man page and theCrypto Policy Definition Formatsection in thecrypto-policies(7)man page on your system.
2.4. Setting up system-wide cryptographic policies in the web console
You can set up system-wide cryptographic policies in the RHEL web console. This provides a graphical interface for changing policies such as DEFAULT, LEGACY, or FUTURE.
Besides the three predefined system-wide cryptographic policies, you can also apply a combination of the LEGACY policy and the AD-SUPPORT subpolicy through the graphical interface. The LEGACY:AD-SUPPORT policy is the LEGACY policy with less secure settings that improve interoperability for Active Directory services.
Prerequisites
You have installed the RHEL 10 web console.
For instructions, see Installing and enabling the web console.
-
Commands that start with the
#command prompt require administrative privileges provided bysudoor root user access. For information on how to configuresudoaccess, see Enabling unprivileged users to run certain commands.
Procedure
- Log in to the RHEL 10 web console.
In the Configuration card of the Overview page, click your current policy value next to Crypto policy.
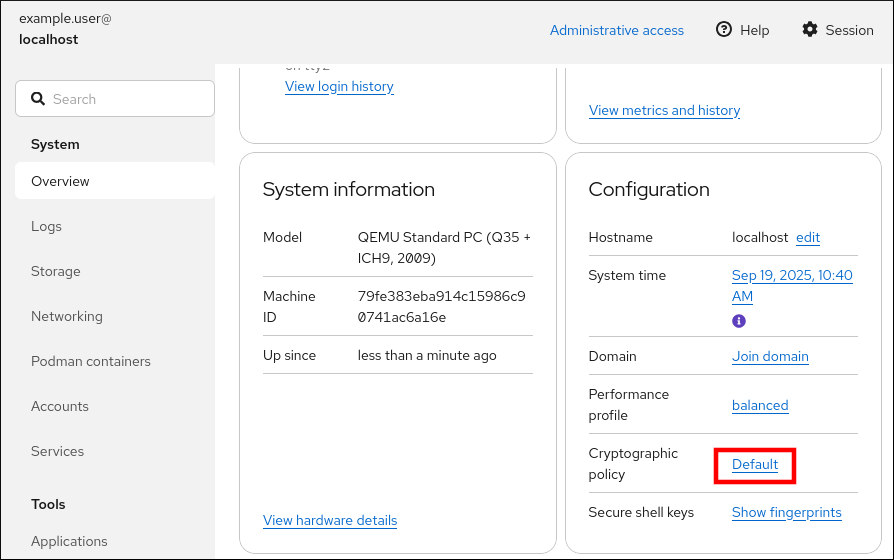
- In the Change crypto policy dialog window, click the policy you want to start using on your system.
- Click the button.
Verification
After the restart, log back in to web console, and check that the Crypto policy value corresponds to the one you selected.
Alternatively, you can enter the
update-crypto-policies --showcommand to display the current system-wide cryptographic policy in your terminal.
2.5. Examples of opting out of system-wide cryptographic policies
Review examples demonstrating how to opt out of system-wide crypto policies for applications such as OpenSSH and wget. Use these methods when specific applications require legacy ciphers or protocols.
You can customize cryptographic settings used by your application by configuring supported cipher suites and protocols directly in the application.
You can also remove a symlink related to your application from the /etc/crypto-policies/back-ends directory and replace it with your customized cryptographic settings. This configuration prevents system-wide cryptographic policies from being applied to applications that use the excluded back end. Furthermore, this modification is not supported by Red Hat.
- curl
To specify ciphers used by the
curltool, use the--ciphersoption and provide a colon-separated list of ciphers as a value. For example:curl <https://example.com> --ciphers '@SECLEVEL=0:DES-CBC3-SHA:RSA-DES-CBC3-SHA'
$ curl <https://example.com> --ciphers '@SECLEVEL=0:DES-CBC3-SHA:RSA-DES-CBC3-SHA'Copy to Clipboard Copied! Toggle word wrap Toggle overflow See the
curl(1)man page for more information.- Libreswan
- See the Enabling legacy ciphers and algorithms in Libreswan section in the Securing networks document for detailed information.
- Mozilla Firefox
-
Even though you cannot opt out of system-wide cryptographic policies in the Mozilla Firefox web browser, you can further restrict supported ciphers and TLS versions in the Firefox’s Configuration Editor. Type
about:configin the address bar and change the value of thesecurity.tls.version.minoption as required. Settingsecurity.tls.version.minto1allows TLS 1.0 as the minimum required,security.tls.version.min 2enables TLS 1.1, and so on. - OpenSSH server
To opt out of the system-wide cryptographic policies for your OpenSSH server, specify the cryptographic policy in a drop-in configuration file located in the
/etc/ssh/sshd_config.d/directory. Use a two-digit number prefix smaller than 50, so that it lexicographically precedes the50-redhat.conffile, and a.confsuffix, for example,49-crypto-policy-override.conf.See the
sshd_config(5)man page for more information.- OpenSSH client
To opt out of system-wide cryptographic policies for your OpenSSH client, perform one of the following tasks:
-
For a given user, override the global
ssh_configwith a user-specific configuration in the~/.ssh/configfile. -
For the entire system, specify the cryptographic policy in a drop-in configuration file located in the
/etc/ssh/ssh_config.d/directory, with a two-digit number prefix smaller than 50, so that it lexicographically precedes the50-redhat.conffile, and with a.confsuffix, for example,49-crypto-policy-override.conf.
See the
ssh_config(5)man page for more information.-
For a given user, override the global
- wget
To customize cryptographic settings used by the wget network downloader, use the
--secure-protocoland--ciphersoptions. For example:wget --secure-protocol=TLSv1_1 --ciphers="SECURE128" <https://example.com>
$ wget --secure-protocol=TLSv1_1 --ciphers="SECURE128" <https://example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow See the HTTPS (SSL/TLS) Options section of the
wget(1)man page for more information.
2.6. Customizing system-wide cryptographic policies with subpolicies
Adjust the set of enabled cryptographic algorithms or protocols on the system. In RHEL, you can either apply custom subpolicies on top of an existing system-wide cryptographic policy or define such a policy from scratch.
The concept of scoped policies enables different sets of algorithms for different back ends. You can limit each configuration directive to specific protocols, libraries, or services.
Furthermore, you can use wildcard characters in directives, for example, an asterisk to specify multiple values. For the complete syntax reference, see the Custom Policies section in the update-crypto-policies(8) man page and the Crypto Policy Definition Format section in the crypto-policies(7) man page on your system.
-
The
/etc/crypto-policies/state/CURRENT.polfile lists all settings in the currently applied system-wide cryptographic policy after wildcard expansion. -
To make your cryptographic policy more strict, consider using values listed in the
/usr/share/crypto-policies/policies/FUTURE.polfile. -
You can find example subpolicies in the
/usr/share/crypto-policies/policies/modules/directory.
Procedure
Checkout to the
/etc/crypto-policies/policies/modules/directory:cd /etc/crypto-policies/policies/modules/
# cd /etc/crypto-policies/policies/modules/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create subpolicies for your adjustments, for example:
touch <MYCRYPTO-1>.pmod touch <SCOPES-AND-WILDCARDS>.pmod
# touch <MYCRYPTO-1>.pmod # touch <SCOPES-AND-WILDCARDS>.pmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantUse upper-case letters in file names of policy modules.
Open the policy modules in a text editor of your choice and insert options that modify the system-wide cryptographic policy, for example:
vi <MYCRYPTO-1>.pmod
# vi <MYCRYPTO-1>.pmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow min_rsa_size = 3072 hash = SHA2-384 SHA2-512 SHA3-384 SHA3-512
min_rsa_size = 3072 hash = SHA2-384 SHA2-512 SHA3-384 SHA3-512Copy to Clipboard Copied! Toggle word wrap Toggle overflow vi <SCOPES-AND-WILDCARDS>.pmod
# vi <SCOPES-AND-WILDCARDS>.pmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save the changes in the module files.
Apply your policy adjustments to the
DEFAULTsystem-wide cryptographic policy level:update-crypto-policies --set DEFAULT:<MYCRYPTO-1>:<SCOPES-AND-WILDCARDS>
# update-crypto-policies --set DEFAULT:<MYCRYPTO-1>:<SCOPES-AND-WILDCARDS>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To make your cryptographic settings effective for already running services and applications, restart the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check that the
/etc/crypto-policies/state/CURRENT.polfile contains your changes, for example:cat /etc/crypto-policies/state/CURRENT.pol | grep rsa_size min_rsa_size = 3072
$ cat /etc/crypto-policies/state/CURRENT.pol | grep rsa_size min_rsa_size = 3072Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.7. Creating and setting a custom system-wide cryptographic policy
Apply custom subpolicies on top of an existing system-wide policy to modify enabled cryptographic algorithms or protocols. By using this granular customization, you can ensure that your system adheres to your specific security requirements.
Procedure
Create a policy file for your customizations:
cd /etc/crypto-policies/policies/ touch <MYPOLICY>.pol
# cd /etc/crypto-policies/policies/ # touch <MYPOLICY>.polCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, start by copying one of the four predefined policy levels:
cp /usr/share/crypto-policies/policies/DEFAULT.pol /etc/crypto-policies/policies/<MYPOLICY>.pol
# cp /usr/share/crypto-policies/policies/DEFAULT.pol /etc/crypto-policies/policies/<MYPOLICY>.polCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the file with your custom cryptographic policy in a text editor of your choice to fit your requirements, for example:
vi /etc/crypto-policies/policies/<MYPOLICY>.pol
# vi /etc/crypto-policies/policies/<MYPOLICY>.polCopy to Clipboard Copied! Toggle word wrap Toggle overflow See the
Custom Policiessection in theupdate-crypto-policies(8)man page and theCrypto Policy Definition Formatsection in thecrypto-policies(7)man page on your system for the complete syntax reference.Switch the system-wide cryptographic policy to your custom level:
update-crypto-policies --set <MYPOLICY>
# update-crypto-policies --set <MYPOLICY>Copy to Clipboard Copied! Toggle word wrap Toggle overflow To make your cryptographic settings effective for already running services and applications, restart the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.8. Disabling post-quantum algorithms system-wide
From RHEL 10.1, post-quantum cryptography (PQC) algorithms are enabled in all predefined policies by default. You can turn them off by applying the NO-PQ subpolicy.
Prerequisites
-
Commands that start with the
#command prompt require administrative privileges provided bysudoor root user access. For information on how to configuresudoaccess, see Enabling unprivileged users to run certain commands.
Procedure
Apply the
NO-PQcryptographic subpolicy on top of your current system-wide policy, for example:update-crypto-policies --show DEFAULT update-crypto-policies --set DEFAULT:NO-PQ
# update-crypto-policies --show DEFAULT # update-crypto-policies --set DEFAULT:NO-PQCopy to Clipboard Copied! Toggle word wrap Toggle overflow To make your cryptographic settings effective for already running services and applications, restart the system:
reboot
# rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
Check that the
/etc/crypto-policies/state/CURRENT.polfile does not contain PQC algorithm stringsMLKEM,MLDSA, andKEM-ECDH, for example:cat /etc/crypto-policies/state/CURRENT.pol | grep MLKEM
$ cat /etc/crypto-policies/state/CURRENT.pol | grep MLKEMCopy to Clipboard Copied! Toggle word wrap Toggle overflow The output of the previous command must be empty.
2.9. Enhancing security with the FUTURE cryptographic policy using the crypto_policies RHEL system role
You can use the crypto_policies RHEL system role to configure the FUTURE cryptographic policy on your managed nodes.
The FUTURE policy helps to achieve, for example:
- Future-proofing against emerging threats
- Anticipates advancements in computational power.
- Enhanced security
- Stronger encryption standards require longer key lengths and more secure algorithms.
- Compliance with high-security standards
- In some industries, for example, in healthcare, telco, and finance the data sensitivity is high, and availability of strong cryptography is critical.
Typically, FUTURE is suitable for environments handling highly sensitive data, preparing for future regulations, or adopting long-term security strategies.
Legacy systems and software do not have to support the more modern and stricter algorithms and protocols enforced by the FUTURE policy. For example, older systems might not support TLS 1.3 or larger key sizes. This could lead to interoperability problems.
Also, using strong algorithms usually increases the computational workload, which could negatively affect your system performance.
Prerequisites
- You have prepared the control node and the managed nodes.
- You are logged in to the control node as a user who can run playbooks on the managed nodes.
-
The account you use to connect to the managed nodes has
sudopermissions for these nodes.
Procedure
Create a playbook file, for example,
~/playbook.yml, with the following content:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
crypto_policies_policy: FUTURE-
Configures the required cryptographic policy (
FUTURE) on the managed node. It can be either the base policy or a base policy with some subpolicies. The specified base policy and subpolicies have to be available on the managed node. The default value isnull, which means that the configuration is not changed and thecrypto_policiesRHEL system role only collects the Ansible facts. crypto_policies_reboot_ok: true-
Causes the system to reboot after the cryptographic policy change to make sure all of the services and applications will read the new configuration files. The default value is
false.
For details about the role variables and the cryptographic configuration options, see the
/usr/share/ansible/roles/rhel-system-roles.crypto_policies/README.mdfile and theupdate-crypto-policies(8)andcrypto-policies(7)manual pages on the control node.Validate the playbook syntax:
ansible-playbook --syntax-check ~/playbook.yml
$ ansible-playbook --syntax-check ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note that this command only validates the syntax and does not protect against a wrong but valid configuration.
Run the playbook:
ansible-playbook ~/playbook.yml
$ ansible-playbook ~/playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
On the control node, create another playbook named, for example,
verify_playbook.yml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow The settings specified in the example playbook include the following:
crypto_policies_active-
An exported Ansible fact that contains the currently active policy name in the format as accepted by the
crypto_policies_policyvariable.
Validate the playbook syntax:
ansible-playbook --syntax-check ~/verify_playbook.yml
$ ansible-playbook --syntax-check ~/verify_playbook.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the playbook:
ansible-playbook ~/verify_playbook.yml TASK [debug] ************************** ok: [host] => { "crypto_policies_active": "FUTURE" }$ ansible-playbook ~/verify_playbook.yml TASK [debug] ************************** ok: [host] => { "crypto_policies_active": "FUTURE" }Copy to Clipboard Copied! Toggle word wrap Toggle overflow The
crypto_policies_activevariable shows the active policy on the managed node.