Dieser Inhalt ist in der von Ihnen ausgewählten Sprache nicht verfügbar.
Chapter 34. Using Ansible to configure HBAC and sudo rules in IdM
Using host-based access control (HBAC) in Identity Management (IdM), you can define policies that restrict access to hosts or services based on the following:
- The user attempting to log in and this user’s groups
- The host that a user is trying to access and the host groups to which that host belongs
- The service that is being used to access a host
Using sudo, a user can run programs as another user, with different privileges, for example root privileges. In IdM, you can manage sudo rules centrally. You can define sudo rules based on user groups, host groups and command groups, as well as individual users, hosts and commands.
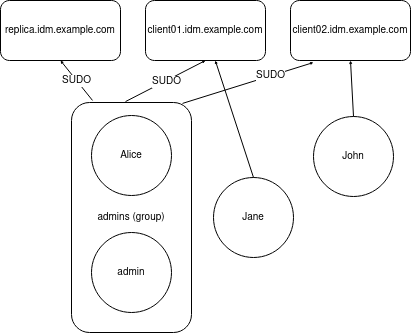
Complete this procedure to ensure the presence of the following HBAC and sudo rules for IdM users:
- jane can only access host client01.idm.example.com.
- john can only access host client02.idm.example.com.
-
Members of the
adminsgroup, which includes the defaultadminuser as well as the regular alice user, can access any IdM host. Members of the
adminsgroup can runsudowith the following commands on any IdM host:-
/usr/sbin/reboot -
/usr/bin/less -
/usr/sbin/setenforce
-
The following diagram represents the desired configuration described above:
Figure 34.1. IdM HBAC and SUDO rules diagram
Prerequisites
On the control node:
- You are using Ansible version 2.14 or later.
-
You have installed the
ansible-freeipapackage. - You have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server in the ~/MyPlaybooks/ directory.
-
You have stored your
ipaadmin_passwordin the secret.yml Ansible vault.
- The users jane, john and alice exist in IdM. Passwords are configured for these accounts.
Procedure
Create your Ansible playbook file add-hbac-and-sudo-rules-to-idm.yml with the following content:
--- - name: Playbook to manage IPA HBAC and SUDO rules hosts: ipaserver become: false gather_facts: false vars_files: - /home/<user_name>/MyPlaybooks/secret.yml module_defaults: ipahbacrule: ipaadmin_password: "{{ ipaadmin_password }}" ipagroup: ipaadmin_password: "{{ ipaadmin_password }}" ipasudocmd: ipaadmin_password: "{{ ipaadmin_password }}" ipasudocmdgroup: ipaadmin_password: "{{ ipaadmin_password }}" ipasudorule: ipaadmin_password: "{{ ipaadmin_password }}" tasks: - name: HBAC Rule for Jane - can log in to client01 ipahbacrule: # Creates the rule name: Jane_rule hbacsvc: - sshd - login host: # Host name - client01.idm.example.com user: - jane - name: HBAC Rule for John - can log in to client02 ipahbacrule: # Creates the rule name: john_rule hbacsvc: - sshd - login host: # Host name - client02.idm.example.com user: - john - name: Add user member alice to group admins ipagroup: name: admins action: member user: - alice - name: HBAC Rule for IdM administrators ipahbacrule: # Rule to allow admins full access name: admin_access # Rule name servicecat: all # All services hostcat: all # All hosts group: # User group - admins - name: Add reboot command to SUDO ipasudocmd: name: /usr/sbin/reboot state: present - name: Add less command to SUDO ipasudocmd: name: /usr/bin/less state: present - name: Add setenforce command to SUDO ipasudocmd: name: /usr/sbin/setenforce state: present - name: Create a SUDO command group ipasudocmdgroup: name: cmd_grp_1 description: "Group of important commands" sudocmd: - /usr/sbin/setenforce - /usr/bin/less - /usr/sbin/reboot action: sudocmdgroup state: present - name: Create a SUDO rule with a SUDO command group ipasudorule: name: sudo_rule_1 allow_sudocmdgroup: - cmd_grp_1 group: admins state: present - name: Disable allow_all HBAC Rule ipahbacrule: # Rule to allow admins full access name: allow_all # Rule name state: disabled # Disables rule to allow everyone the ability to loginRun the playbook:
$ ansible-playbook --vault-password-file=password_file -i inventory add-hbac-and-sudo-rules-to-idm.yml
Verification
Connect to client01 as the jane user:
~]$ ssh jane@client01 Password: Last login: Fri Aug 11 15:32:18 2023 from 192.168.122.1 [jane@client01 ~]$The output verifies that jane has logged in to client01.
Try to connect to client02 as the jane user:
~]$ ssh jane@client02 Password: Connection closed by 192.168.122.47 port 22The output verifies that jane cannot log in to client02.
Connect to client02 as the alice user:
~]$ ssh alice@client02 Password: Last login: Fri Aug 10 16:13:43 2023 from 192.168.122.1The output verifies that alice has logged in to client02.
Try to view the contents of the
/etc/sssd/sssd.conffile usinglesswithout invoking the superuser privileges:[alice@client02 ~]$ less /etc/sssd/sssd.conf /etc/sssd/sssd.conf: Permission deniedThe attempt fails as the file is not readable by anyone except the owner of the file, which is
root.Invoke the
rootprivileges to view the contents of the/etc/sssd/sssd.conffile usingless:[alice@client02 ~]$ sudo less /etc/sssd/sssd.conf [sudo] password for alice: [domain/idm.example.com] id_provider = ipa ipa_server_mode = True [...]The output verifies that alice can execute the
lesscommand on the/etc/sssd/sssd.conffile.
Additional resources