Access management and authentication
Configure role based access control, authenticators and authenticator maps in Ansible Automation Platform
Abstract
Providing feedback on Red Hat documentation
If you have a suggestion to improve this documentation, or find an error, you can contact technical support at https://access.redhat.com to open a request.
Chapter 1. Overview of access management and authentication
Ansible Automation Platform features a platform interface where you can set up centralized authentication, configure access management, and configure global and system level settings from a single location.
The first time you log in to the Ansible Automation Platform, you must enter your subscription information to activate the platform. For more information about licensing and subscriptions, see Managing Ansible Automation Platform licensing, updates and support.
A system administrator can configure access, permissions and system settings through the following tasks:
- Configuring authentication in the Ansible Automation Platform, where you set up simplified login for users by selecting from several authentication methods available and define permissions and assign them to users with authenticator maps.
- Configuring access to external applications with token-based authentication, where you can configure authentication of third-party tools and services with the platform through integrated OAuth 2 token support.
- Managing access with role based access control, where you configure user access based on their role within a platform organization.
- Configuring Ansible Automation Platform, where you can configure global and system level settings for the platform and services.
Chapter 2. Configuring authentication in the Ansible Automation Platform
Using the authentication settings in Ansible Automation Platform, you can set up a simplified login through several authentication methods, such as LDAP and SAML. Depending on the authentication method you select, you will be required to enter different information to complete the configuration. Be sure to include all the information required for your configuration needs.
2.1. Prerequisites
- A running installation of Ansible Automation Platform 2.5
- A running instance of your authentication source
- Administrator rights to the Ansible Automation Platform
- Any connection information needed to connect Ansible Automation Platform 2.5 to your source (see individual authentication types for details).
2.2. Pluggable authentication
Authentication is the process of verifying a user’s identity to the Ansible Automation Platform (that is, to establish that a user is who they say they are). This can be done in a number of ways but would traditionally be associated with a username and password.
When you log out of Ansible Automation Platform, only your session with the platform ends. Your session with the external Single Sign-On (SSO) provider stays active. To switch to a different account with the same provider, you must log out of the SSO provider’s website directly. This ensures that you can successfully sign in with a new account.
Ansible Automation Platform 2.5 uses a pluggable authentication system with a configuration wizard that provides a common, simplified method of configuring different types of authenticators such as LDAP and SAML. The pluggable system also allows you to configure multiple authenticators of the same type.
In the pluggable system we have a couple of concepts:
- Authenticator Plugin
- A plugin allows Ansible Automation Platform to connect to a source system, such as, LDAP or SAML. Ansible Automation Platform includes a variety of authenticator plugins. Authenticator plugins are similar to Ansible collections, in that all of the required code is in a package and can be versioned independently if needed.
- Authenticator
- An authenticator is an instantiation of an authenticator plugin and allows users from the specified source to log in. For example, the LDAP authenticator plugin defines a required LDAP server setting. When you instantiate an authenticator from the LDAP authentication plugin, you must provide the authenticator the LDAP server URL it needs to connect to.
- Authenticator Map
- Authenticator maps are applied to authenticators and tell Ansible Automation Platform what permissions to give a user logging into the system.
2.3. Creating an authentication method
Creating an authenticator involves the following procedures:
- Selecting an authentication type, where you select the type of authenticator plugin you want to configure, including the authentication details for the authentication type selected.
Mapping, where you define mapping rule types and triggers to control access to the system, and Mapping order, where you can define the mapping precedence.
NoteMapping order is only available if you have defined one or more authenticator maps.
2.3.1. Selecting an authentication type
On the Authentication Methods page you can select the type of authenticator plugin you want to configure.
Procedure
- From the navigation panel, select → .
- Click .
Enter a unique Name for the authenticator. The name is required, must be unique across all authenticators, and must not be longer than 512 characters. This becomes the unique identifier generated for the authenticator.
NoteChanging the name does not update the unique identifier of the authenticator. For example, if you create an authenticator with the name
My Authenticatorand later change it toMy LDAP Authenticatoryou will not be able to create another authenticator with the nameMy Authenticatorbecause the unique identifier is still in use.- Select the authenticator type from the Authentication type list. See Configuring an authentication type for the complete list of authentication plugins available.
The Authentication details section automatically updates to show the fields relevant to the selected authentication type. See the respective sections in Configuring an authentication type for the required details.
For all authentication types you can enter a Name, Additional Authenticator Fields and Create Objects.
- Enable or disable Enabled to specify if the authenticator should be enabled or disabled. If enabled, users are able to login from the authenticator. If disabled, users will not be allowed to login from the authenticator.
Enable or disable Create Object to specify whether the authenticator should create teams and organizations in the system when a user logs in.
- Enabled
- Teams and organizations defined in the authenticator maps are created and the users added to them.
- Disabled
- Organizations and teams defined in the authenticator maps will not be created automatically in the system. However, if they already exist (i.e. created by a superuser), users who trigger the maps are granted access to them.
Enable or disable Remove Users. If enabled, any access previously granted to a user is removed when they authenticate from this source. If disabled, permissions are only added or removed from the user based on the results of this authenticator’s authenticator mappings.
For example, assume a user has been granted the
is_superuserpermission in the system. And that user will log in to an authenticator whose maps will not formulate an opinion as to whether or not the user should be a superuser. If Remove Users is enabled, theis_superuserpermission will be removed from the user, the authenticator maps will not have an opinion as to whether it should be there or not so, after login the user will not have theis_superuserpermission.If Remove Users is disabled, the
is_superuserpermission will not be removed from the user. The authenticator maps will not have an opinion as to whether it should be there or not so after login the user will have theis_superuserpermission.- Click and proceed to Define authentication mapping rules and triggers.
2.3.2. Defining authentication mapping rules and triggers
Authentication map types can be used with any type of authenticator. Each map has a trigger that defines when the map should be evaluated as true.
Procedure
- From the navigation panel, select → .
- In the list view, select the authenticator name displayed in the Name column.
- Select the Mapping tab from the Details page of your authenticator.
- Click .
Select a map type from the Authentication mapping list. See Authenticator map types for detailed descriptions of the different map types. Choices include:
- Enter a unique rule Name to identify the rule.
Select a Trigger from the list. See Authenticator map triggers for more details. Choices include:
- Always
- Never
- Group
- Attribute
- Click .
- Repeat this procedure to create additional mapping rules and triggers for the authenticator.
Proceed to Adjust the Mapping order to optionally reorder the mappings for your authenticator.
NoteThe mapping order setting is only available if there is more than one authenticator map defined.
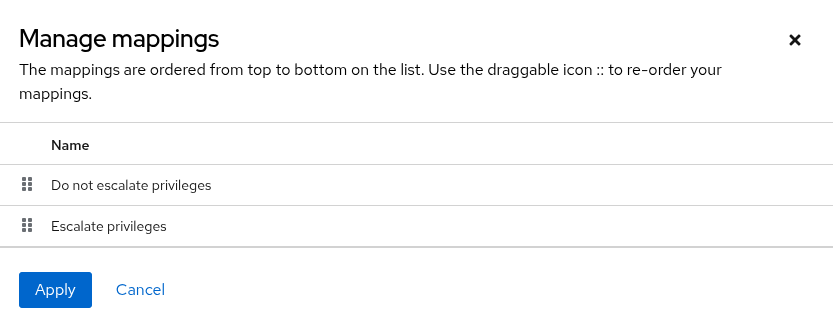
2.3.3. Adjusting the Mapping order
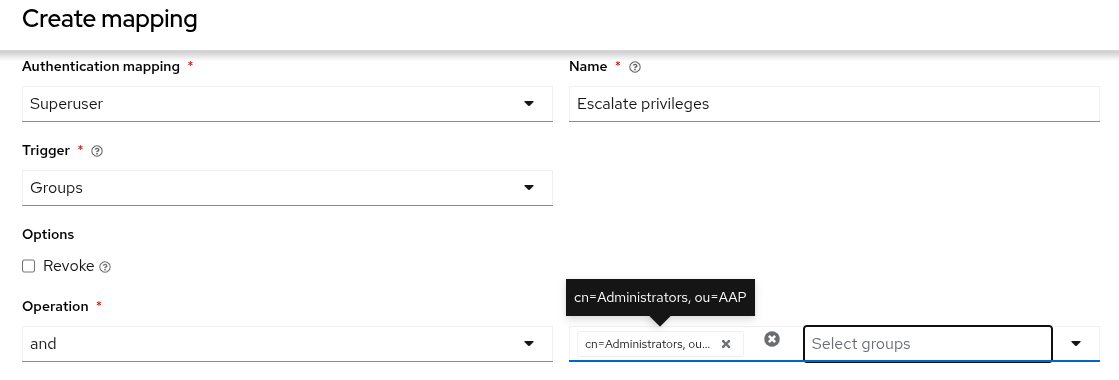
If you have one or more authenticator maps defined, you can manage the order of the maps. Authenticator maps are run in order when logging in lowest order to highest. If one authenticator map determines a user should be a member of a team but a subsequent map determines the user should not be a member of the same team the ruling form the second map will take precedence over the result of the first map. Authenticator maps with the same order are executed in an undefined order.
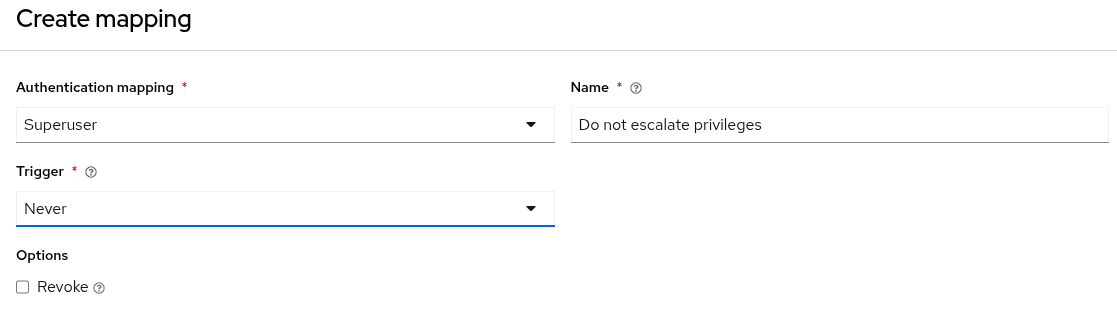
For example, if the first authenticator map is of type is_superuser and the trigger is set to never, any user logging into the system would never be granted the is_superuser flag.
And, if the second map is of type is_superuser and the trigger is based on the user having a specific group, any user logging in would initially be denied the is_superuser permission. However, any user with the specified group would subsequently be granted the is_superuser permission by the second rule.
The order of rules is important beyond whether you want to process organizations, teams or roles first. They can also be used to refine access and careful consideration is needed to avoid login issues.
For example:
- Authenticator map A denies all users access to the system
-
Authenticator map B allows the user
johnaccess to the system
When the mapping order is set to A, B; the first map denies access for all users, including john. The second map subsequently allows john access to the system and the result is that john is granted access and is able to log in to the platform.
However, when the mapping order is changed to B, A; the first map allows john access to the system. The second map subsequently denies all users access to the system (including john) and the result is that john is denied access and is unable to log in to the platform.
Procedure
- From the navigation panel, select → .
- In the list view, select the authenticator name displayed in the Name column.
- Select the Mapping tab from the Details page of your authenticator.
- Click .
Adjust the mapping order by dragging and dropping the mappings up or down in the list using the draggable icon.
NoteThe mapping precedence is determined by the order in which the mappings are listed.
- After your authenticator maps are in the correct order, click .
2.4. Enabling and disabling the local authenticator
As a platform administrator, you can enable or disable authenticators. However, disabling your local authenticator can have significant impacts and should only be done under specific circumstances. Before you disable your local authenticator, you must consider the following:
- Local account inaccessibility
-
Disabling the local authenticator prevents all local accounts, including the default
adminaccount from logging in. - Potential inaccessibility
- Disabling the local authenticator without having at least one other configured authenticator can render the Ansible Automation Platform environment completely inaccessible.
- Dependency on enterprise authentication provider
- If the local authenticator is disabled and an issue occurs with the configured enterprise authentication provider, the platform will become inaccessible until the enterprise authentication provider issue is resolved.
Prerequisites
- You have at least one other authenticator method configured.
- You have at least one administrator account that can authenticate using your alternate authenticator.
Disabling the local authenticator without an alternative authentication in place can result in a locked environment.
Procedure
- From the navigation panel, select → .
- Ensure that at least one other authenticator type is configured and enabled.
- Select your Local Authenticator.
- Toggle the Enabled switch to the off position to disable the local authenticator.
Troubleshooting
If the local authenticator is disabled without another authentication method configured, or if an issue arises with your configured enterprise authentication provider, making the Ansible Automation Platform inaccessible, you can re-enable the local authenticator from the command line as follows:
List the available authenticators and retrieve the ID of your local authenticator by running the following command:
aap-gateway-api authenticators --list
aap-gateway-api authenticators --listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the local authenticator using its ID:
aap-gateway-manage authenticators --enable :id
aap-gateway-manage authenticators --enable :idCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
:idis the ID of the local authenticator obtained from the previous step.
2.5. Configuring an authentication type
Ansible Automation Platform provides multiple authenticator plugins that you can configure to simplify the login experience for your organization. These are the authenticator plugins that are provided:
2.5.1. Configuring local authentication
As a platform administrator, you can configure local system authentication. With local authentication, users and their passwords are checked against local system accounts.
A local authenticator is automatically created by the Ansible Automation Platform installation process, and is configured with the specified admin credentials in the inventory file before installation. After successful installation, you can log in to the Ansible Automation Platform using those credentials.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this Local configuration. The configuration name is required, must be unique across all authenticators, and must not be longer than 512 characters.
- Select Local from the Authentication type list.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
2.5.2. Configuring LDAP authentication
As a platform administrator, you can configure LDAP as the source for account authentication information for Ansible Automation Platform users.
If the LDAP server you want to connect to has a certificate that is self-signed or signed by an internal certificate authority (CA), the CA certificate must be added to the system’s trusted CAs. Otherwise, connection to the LDAP server will result in an error that the certificate issuer is not recognized.
When LDAP is configured, an account is created for any user who logs in with an LDAP username and password and they can be automatically placed into organizations as either regular users or organization administrators.
Ansible Automation Platform treats usernames as case-insensitive in LDAP. It sends the username that was entered without modification to the LDAP provider for authentication. After successful authentication, the platform converts the username to lowercase and stores it in the database. For example, if a user logs in as JDOE, their platform username will be jdoe. If the user logs in again as JDoe, their username will still be jdoe.
However, if Ansible Automation Platform is configured with multiple LDAP authenticators, and the same user IDs exist across them, their usernames might differ. For instance, JDOE might have the username jdoe, while jDOE could be assigned jdoe-<some hash>.
If a user previously logged in using different case variations of their username, Ansible Automation Platform maps all case variations to the lowercase username. Existing users with other case variations are not valid for interactive log in. However, any existing OAuth tokens for the mixed case username still allow authentication. A system administrator can delete those case variation users if needed.
Users created through an LDAP login should not change their username, first name, last name, or set a local password for themselves. Any changes made to this information is overwritten the next time the user logs in to the platform.
Migration of LDAP authentication settings are not supported for 2.4 to 2.5 in the platform UI. If you are upgrading from Ansible Automation Platform 2.4 to 2.5, be sure to save your authentication provider data before upgrading.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select LDAP from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
- In the LDAP Server URI field, enter or modify the list of LDAP servers to which you want to connect. This field supports multiple addresses.
In the LDAP Bind DN text field, enter the Distinguished Name (DN) to specify the user that the Ansible Automation Platform uses to connect to the LDAP server as shown in the following example:
CN=josie,CN=users,DC=website,DC=com
CN=josie,CN=users,DC=website,DC=comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the LDAP Bind Password text field, enter the password to use for the binding user.
Select a group type from the LDAP Group Type list.
The group type defines the class name of the group, which manages the groups associated with users in your LDAP directory and is returned by the search specified in Step 14 of this procedure. The group type, along with group parameters and the group search, is used to find and assign groups to users during log in, and can also be evaluated during the mapping process. The following table lists the available group types, along with their descriptions and the necessary parameters for each. By default, LDAP groups will be mapped to Django groups by taking the first value of the cn attribute. You can specify a different attribute with
name_attr. For example,name_attr='cn'.Expand Table 2.1. Available LDAP group types LDAP Group Type Description Initializer method (init) PosixGroupTypeHandles the
posixGroupobject class. This checks for both primary group and group membership.name_attr='cn'MemberDNGroupTypeHandles the grouping mechanisms wherein the group object contains a list of its member DNs.
member_attr, name_attr='cn'GroupOfNamesTypeHandles the
groupOfNamesobject class. Equivalent toMemberDNGroupType('member').name_attr='cn'GroupOfUniqueNamesTypeHandles the
groupOfUniqueNamesobject class. Equivalent toMemberDNGroupType('uniqueMember').name_attr='cn'ActiveDirectoryGroupTypeHandles the Active Directory groups. Equivalent to
MemberDNGroupType('member').name_attr='cn'OrganizationalRoleGroupTypeHandles the
organizationalRoleobject class. Equivalent toMemberDNGroupType('roleOccupant').name_attr='cn'NestedGroupOfNamesTypeHandles the
groupOfNamesobject class. Equivalent toNestedMemberDNGroupType('member').member_attr, name_attr='cn'NestedGroupOfUniqueNamesTypeHandles the
groupOfUniqueNamesobject class. Equivalent toNestedMemberDNGroupType('uniqueMember').name_attr='cn'NestedActiveDirectoryGroupTypeHandles the Active Directory groups. Equivalent to
NestedMemberDNGroupType('member').name_attr='cn'NestedOrganizationalRoleGroupTypeHandles the
organizationalRoleobject class. Equivalent toNestedMemberDNGroupType('roleOccupant').name_attr='cn'NoteThe group types that are supported by Ansible Automation Platform use the underlying django-auth-ldap library. To specify the parameters for the selected group type, see Step 14 of this procedure.
You can use LDAP User DN Template as an alternative to user search. This approach is more efficient for user lookups than searching if it is usable in your organizational environment. Enter the name of the template as shown in the following example:
uid=%(user)s,cn=users,cn=accounts,dc=example,dc=com
uid=%(user)s,cn=users,cn=accounts,dc=example,dc=comCopy to Clipboard Copied! Toggle word wrap Toggle overflow where:
uidis the user identifier,cnis the common name anddcis the domain component.NoteIf this setting has a value it will be used instead of the LDAP User Search setting.
- LDAP Start TLS is disabled by default. StartTLS allows your LDAP connection to be upgraded from an unencrypted connection to a secure connection using Transport Layer Security (TLS). To enable StartTLS when the LDAP connection is not using SSL, set the switch to On.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
Enter any LDAP Connection Options to set for the LDAP connection. LDAP referrals are not disabled by default. Disable this setting to prevent login flow timeouts and ensure successful user logins. Option names should be strings as shown in the following example:
OPT_REFERRALS: 0 OPT_NETWORK_TIMEOUT: 30
OPT_REFERRALS: 0 OPT_NETWORK_TIMEOUT: 30Copy to Clipboard Copied! Toggle word wrap Toggle overflow See the python-LDAP Reference for possible options and values that can be set.
Depending on the selected LDAP Group Type, different parameters are available in the LDAP Group Type Parameters field to account for this.
LDAP_GROUP_TYPE_PARAMSis a dictionary, which is converted tokwargsand passed to the LDAP Group Type class selected. There are two common parameters used by group types:name_attrandmember_attr. Wherename_attrdefaults tocnandmember_attrdefaults tomember:{"name_attr": "cn", "member_attr": "member"}{"name_attr": "cn", "member_attr": "member"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow To determine the parameters that a specific LDAP Group Type requires, refer to the django_auth_ldap documentation on the classes
initparameters.In the LDAP Group Search field, specify which groups should be searched and how to search them as shown in the following example:
[ "dc=example,dc=com", "SCOPE_SUBTREE", "(objectClass=group)" ]
[ "dc=example,dc=com", "SCOPE_SUBTREE", "(objectClass=group)" ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the LDAP User Attribute Map field, enter user attributes to map LDAP fields to your Ansible Automation Platform users, for example,
emailorfirst_nameas shown in the following example:{ "first_name": "givenName", "last_name": "sn", "email": "mail" }{ "first_name": "givenName", "last_name": "sn", "email": "mail" }Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the LDAP User Search field, enter where to search for users during authentication as shown in the following example:
[ "OU=Users,DC=website,DC=com", "SCOPE_SUBTREE", "(cn=%(user)s)" ]
[ "OU=Users,DC=website,DC=com", "SCOPE_SUBTREE", "(cn=%(user)s)" ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the LDAP User DN Template is not set, the Ansible Automation Platform authenticates to LDAP using the Bind DN Template and LDAP Bind Password. After authentication, an LDAP search is performed to locate the user specified by this field. If the user is found, Ansible Automation Platform validates the provided password against the user found by the LDAP search. Multiple search queries are supported for users with
LDAPUnionby entering multiple search terms as shown in the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If non-unique users are found during multiple searches, those users will not be able to log in to Ansible Automation Platform. Based on the example provided, if a user with
uid=jdoewas found in both theou=users,dc=example,dc=comandou=employees,dc=subdivision,dc=com, neitherjdoeuser would be able to log in. All other unique users that are found in either branch would still be able to log in.NoteIf the field LDAP User DN Template is populated, it takes precedence over the LDAP User Search field and only the template will be used to authenticate users.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
2.5.2.1. Importing a certificate authority in automation controller for LDAPS integration
You can authenticate to the automation controller server by using LDAP. However, if you change to using LDAPS (LDAP over SSL/TLS) to authenticate and the TLS certificate is not trusted by platform gateway, it fails with an error such as:
2025-08-26 16:40:56,141 WARNING django_auth_ldap Caught LDAPError while authenticating: SERVER_DOWN({'result': -1, 'desc': "Can't contact LDAP server", 'ctrls': [], 'info': 'error:0A000086:SSL routines::certificate verify failed (self-signed certificate)'})
2025-08-26 16:40:56,141 WARNING django_auth_ldap Caught LDAPError while authenticating: SERVER_DOWN({'result': -1, 'desc': "Can't contact LDAP server", 'ctrls': [], 'info': 'error:0A000086:SSL routines::certificate verify failed (self-signed certificate)'})To get Ansible Automation Platform to trust the certificate coming from LDAP, perform the following procedure on all platform gateway instances.
Procedure
-
Place a copy of the LDAP servers certificate in the directory,
/etc/pki/ca-trust/source/anchors/. Run the command:
update-ca-trust
update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.5.3. Configuring SAML authentication
SAML allows the exchange of authentication and authorization data between an Identity Provider (IdP) and a Service Provider (SP). Ansible Automation Platform is a SAML SP that you can configure to talk with one or more SAML IdPs to authenticate users.
Based on groups and attributes optionally provided by the SAML IdP, users can be placed into teams and organizations in Ansible Automation Platform based on the authenticator maps tied to this authenticator. This mapping ensures that when a user logs in through SAML, Ansible Automation Platform can correctly identify the user and assign the proper attributes like first name, last name, email, and group membership.
Prerequisites
Before you configure SAML authentication in Ansible Automation Platform, be sure you do the following:
- Configure a SAML Identity Provider (IdP).
Pre-configure the SAML IdP with the settings required for integration with Ansible Automation Platform. For example, in Microsoft Entra ID you can configure the following:
- Identifier (Entity ID): This can be any value that you want, but it needs to match the one configured in your Ansible Automation Platform.
- Reply URL (Assertion Consumer Service (ACS) URL): This URL is auto generated when the SAML method is configured in Ansible Automation Platform. That value must be copied from Ansible Automation Platform and pasted in your IdP settings.
- Gather the user attributes for your SAML IdP application. Different IdPs might use different attribute names and formats. Refer to documentation for your specific IdP for the exact attribute names and the expected values.
Generate a private key and public certificate using the following command:
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -sha256 -days 3650 -nodes
$ openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -sha256 -days 3650 -nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this SAML configuration.
- Select SAML from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
- Enter the application-defined unique identifier used as the audience of the SAML service provider configuration in the SAML Service Provider Entity ID field. This is usually the base URL of your service provider, but the actual value depends on the Entity ID expected by your IdP.
-
Include the certificate content in the SAML Service Provider Public Certificate field. This information is contained in the cert.pem you created as a prerequisite and must include the
—–BEGIN CERTIFICATE—–and—–END CERTIFICATE—–. -
Include the private key content in the SAML Service Provider Private Key field. This information is contained in the key.pem you created as a prerequisite and must include the
—–BEGIN PRIVATE KEY—–and—–END PRIVATE KEY—–. - Enter the URL to redirect the user to for login initiation in the IdP Login URL field. This is the login URL from your SAML IdP application.
Enter the public cert used for secrets coming from the IdP in the IdP Public Cert field. This is the SAML certificate available for download from IdP.
NoteThe IdP in the IdP Public Cert field should contain the entire certificate, including the
—–BEGIN CERTIFICATE—–and—–END CERTIFICATE—–. You must manually enter the prefix and suffix if the IdP does not include it.- Enter the entity ID returned in the assertion in the Entity ID. This is the identifier from your IdP SAML application. You can find this value in the SAML metadata provided by your IdP.
- Enter user details in the Groups, User Email, Username, User Last Name and User First Name.
Enter a permanent ID for the user in the User Permanent ID field. This field is required.
NoteAdditional attributes might be available through your SAML IdP. Those values must be included in either the Additional Authenticators Fields or the SAML IDP to extra_data attribute mapping field. Refer to those steps for details.
- The SAML Assertion Consumer Service (ACS) URL field registers the service as a service provider (SP) with each identity provider (IdP) you have configured. Leave this field blank. After you save this authentication method, it is auto generated. This field must match the Reply URL setting in your IdP.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator. For example, to ensure all SAML IdP attributes other than Email, Username, Last Name, First Name are included for mapping, enter the following:
GET_ALL_EXTRA_DATA: true
GET_ALL_EXTRA_DATA: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can include a list of SAML IdP attributes in the SAML IDP to extra_data attribute mapping field.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
In the SAML Service Provider Organization Info field, provide the URL, display name, and the name of your app.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the SAML Service Provider Technical Contact field, give the name and email address of the technical contact for your service provider.
{ "givenName": "Some User", "emailAddress": "suser@example.com" }{ "givenName": "Some User", "emailAddress": "suser@example.com" }Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the SAML Service Provider Support Contact field, give the name and email address of the support contact for your service provider.
{ "givenName": "Some User", "emailAddress": "suser@example.com" }{ "givenName": "Some User", "emailAddress": "suser@example.com" }Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Provide extra configuration data in the SAML Service Provider extra configuration data field. For example, you can choose to enable signing requests for added security:
{ "sign_request": True, }{ "sign_request": True, }Copy to Clipboard Copied! Toggle word wrap Toggle overflow This field is the equivalent to the
SOCIAL_AUTH_SAML_SP_EXTRAin the API. For more information, see OneLogin’s SAML Python Toolkit to learn about the valid service provider extra (SP_EXTRA) parameters.Optional: Provide security settings in the SAML Security Config field. This field is the equivalent to the
SOCIAL_AUTH_SAML_SECURITY_CONFIGfield in the API.Copy to Clipboard Copied! Toggle word wrap Toggle overflow For more information and additional options, see OneLogin’s SAML Python Toolkit.
Optional: In the SAML IDP to extra_data attribute mapping field, enter values to map IDP attributes to extra_data attributes. These values will include additional user information beyond standard attributes like Email or Username to be mapped. For example:
- Department - UserType - Organization
- Department - UserType - OrganizationCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information on the values you can include, see advanced SAML settings.
ImportantMake sure you include all relevant values so that everything gets mapped correctly for your configuration. Alternatively, you can include the
GET_ALL_EXTRA_DATA: truein the Additional Authenticator Fields to allow mapping of all available SAML IdP attributes.- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
You can configure an HTTPS redirect for SAML in operator-based deployments to simplify login for your users. For the steps to configure this setting, see Enabling single sign-on (SSO) for platform gateway on OpenShift Container Platform.
2.5.3.1. Configuring transparent SAML logins
For transparent logins to work, you must first get IdP-initiated logins to work.
Procedure
-
Set the
RelayStateon the IdP to "IdP".
2.5.4. Configuring TACACS+ authentication
Terminal Access Controller Access-Control System Plus (TACACS+) is a protocol that handles remote authentication and related services for networked access control through a centralized server. TACACS+ provides authentication, authorization and accounting (AAA) services, in which you can configure Ansible Automation Platform to use as a source for authentication.
This feature is deprecated and will be removed in a future release.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select TACACS+ from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
Enter the following information:
- Hostname of TACACS+ Server: Provide the hostname or IP address of the TACACS+ server with which to authenticate. If you leave this field blank, TACACS+ authentication is disabled.
- TACACS+ Authentication Protocol: The protocol used by the TACACS+ client. The options are ascii or pap.
- Shared secret for authenticating to TACACS+ server: The secret key for TACACS+ authentication server.
- The TACACS+ client address sending enabled is disabled by default. To enable client address sending, select the checkbox.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
Click .
2.5.5. Configuring Microsoft Entra ID authentication
To set up enterprise authentication for Microsoft Entra ID, formerly known as Microsoft Azure Active Directory (AD), follow these steps:
- Configure your Ansible Automation Platform to use Microsoft Entra ID authentication using the steps in this procedure.
- Register Ansible Automation Platform in Microsoft Entra ID by following the Quickstart: Register an application with the Microsoft identity platform. This process provides you with an Application (client) ID and Application secret.
- Add the redirect URL in Microsoft Entra ID. After completing the configuration wizard for Microsoft Entra ID authentication in your platform, copy the URL displayed in the Azure AD OAuth2 Callback URL field. Then, go to your registered enterprise application in Azure and add this URL as a Redirect URL (also referred to as a Callback URL in Ansible Automation Platform) as described in How to add a redirect URI to your application. This step is required for the login flow to work correctly.
The attributes provided by Microsoft Entra ID are not set in the Ansible Automation Platform configuration for this authentication type. Instead, the social_core azuread backend provides the translation of claims provided by Microsoft Entra ID. The user attributes that allow Ansible Automation Platform to correctly identify the user and assign the proper attributes like first name, last name, email, and username include the following:
| Ansible Automation Platform attribute | Microsoft Entra ID parameter |
|---|---|
| authenticator_uid | upn |
| Username | name |
| First Name | given_name |
| Last Name | family_name |
| | email (falling back to upn) |
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select Azuread from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
- Click , copy and paste Microsoft’s Application (Client) ID to the OIDC Key field.
If your Microsoft Entra ID is configured to provide user group information within a groups claim, ensure that the platform is configured with a Groups Claim name that matches your Microsoft Entra ID configuration. This allows the platform to correctly identify and associate groups for users logging in through Microsoft Entra ID.
NoteGroups coming from Microsoft Entra ID can be identified using either unique IDs or group names. When creating group mappings for a Microsoft Entra ID authenticator, you can use either the unique ID or the group name.
By default, Microsoft Entra ID uses groups as the default group claim name. So, be sure to either set the value to the default or to any custom override you have set in your IdP. The current default is set to preserve the existing behavior unless explicitly changed.
- Following instructions for registering your application with the Microsoft identity platform, supply the key (shown at one time only) to the client for authentication.
- Copy and paste the secret key created for your Microsoft Entra ID/Microsoft Azure AD application to the OIDC Secret field.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.6. Configuring Google OAuth2 authentication
To set up social authentication for Google, you must obtain an OAuth2 key and secret for a web application. To do this, you must first create a project and set it up with Google.
For instructions, see Setting up OAuth 2.0 in the Google API Console Help documentation.
If you have already completed the setup process, you can access those credentials by going to the Credentials section of the Google API Manager Console. The OAuth2 key (Client ID) and secret (Client secret) are used to supply the required fields in the UI.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select Google OAuth from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
The Google OAuth2 Key and Google OAuth2 Secret fields are pre-populated.
If not, use the credentials Google supplied during the web application setup process. Save these settings for use in the following steps.
- Copy and paste Google’s Client ID into the Google OAuth2 Key field.
- Copy and paste Google’s Client secret into the Google OAuth2 Secret field.
Optional: Enter information for the following fields using the tooltips provided for instructions and required format:
- Access Token URL
- Access Token Method
- Authorization URL
- Revoke Token Method
- Revoke Token URL
- OIDC JWT Algorithm(s)
- OIDC JWT
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.7. Configuring generic OIDC authentication
OpenID Connect (OIDC) uses the OAuth 2.0 framework. It enables third-party applications to verify the identity and obtain basic end-user information. The main difference between OIDC and SAML is that SAML has a service provider (SP)-to-IdP trust relationship, whereas OIDC establishes the trust with the channel (HTTPS) that is used to obtain the security token. To obtain the credentials needed to set up OIDC with Ansible Automation Platform, see the documentation from the IdP of your choice that has OIDC support.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select Generic OIDC from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
Enter the following information:
- OIDC Provider URL: The URL for your OIDC provider.
- OIDC Key: The client ID from your third-party IdP.
- OIDC Secret: The client secret from your IdP.
- Optional: Select the HTTP method to be used when requesting an access token from the Access Token Method list. The default method is POST.
Optionally enter information for the following fields using the tooltips provided for instructions and required format:
- Access Token Method - The default method is POST.
- Access Token URL
- Access Token Method
- Authorization URL
- Callback URL - The OIDC Callback URL field registers the service as a service provider (SP) with each OIDC provider you have configured. Leave this field blank. After you save this authentication method, it is auto generated. Configure your IdP to allow redirects to this URL as part of the authentication flow.
- ID Key
- ID Token Issuer
- JWKS URI
- OIDC Public Key
- Revoke Token Method - The default method is GET.
- Revoke Token URL
- Response Type
- Token Endpoint Auth Method
- Userinfo URL
- Username Key
- Use the Verify OIDC Provider Certificate to enable or disable the OIDC provider SSL certificate verification.
- Use the Redirect State to enable or disable the state parameter in the redirect URI. It is recommended that this is enabled to prevent Cross Site Request Forgery (CSRF) attacks.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
2.5.7.1. Troubleshoot Generic OIDC Single Sign-On authentication failures
Authentication fails if the OIDC JWT Algorithm setting is not explicitly defined. The authentication code requires a list of acceptable algorithms, which it does not retrieve automatically from the OpenID Connect (OIDC) configuration endpoint.
2.5.7.1.1. Configuring JWT_Algorithms manually
To resolve the authentication failure, manually provide the list of supported algorithms in the platform gateway configuration.
Procedure
- From the navigation panel, select → .
- Select your OIDC authenticator from the list.
- Click and locate the OIDC JWT Algorithm(s) field.
Enter the list of supported algorithms as a YAML list or a JSON array. These algorithms are typically available from your IdP’s OpenID Connect (OIDC) discovery endpoint.
Example
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Save your changes. The system uses these specified algorithms for token verification, resolving any authentication failures related to their absence.
2.5.7.1.2. Enabling debugging for enterprise authentication
To further diagnose authentication issues, enable debug logging in platform gateway.
Procedure
-
Change the logging configuration in the platform gateway’s
settings.pyfile. Set the logging level for the
ansible_baselogger toDEBUG:LOGGING['loggers']['ansible_base']['level'] = 'DEBUG'
LOGGING['loggers']['ansible_base']['level'] = 'DEBUG'Copy to Clipboard Copied! Toggle word wrap Toggle overflow After this change, detailed
AuthTokenErrormessages are displayed in the logs, providing specific information about the cause of the failure.
2.5.7.1.3. Troubleshooting Generic OIDC scope mismatches
Authentication fails when the Identity Provider (IdP) does not support the default scopes automatically appended by the system.
To prevent the system from appending this default scope, you must add a setting to your authenticator configuration.
Procedure
- From the navigation panel, select → .
- Select your OIDC authenticator from the list.
- Click .
In the Additional Authenticator Fields section, add the following attribute and value. This input box supports either YAML or JSON. Ensure you add this key-value pair on a new line if there are other fields present:
IGNORE_DEFAULT_SCOPE: True
IGNORE_DEFAULT_SCOPE: TrueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Save your changes. The authenticator now only uses the scopes you explicitly defined, resolving any authentication failures related to unsupported scopes.
2.5.8. Configuring keycloak authentication
You can configure Ansible Automation Platform to integrate Keycloak to manage user authentication.
When using this authenticator some specific setup in your Keycloak instance is required. Refer to the Python Keycloak reference for more details.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select Keycloak from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
- Enter the location where the user’s token can be retrieved in the Keycloak Access Token URL field.
- Optional: Enter the redirect location the user is taken to during the login flow in the Keycloak Provider URL field.
- Enter the Client ID from your Keycloak installation in the Keycloak OIDC Key field.
- Enter the RS256 public key provided by your Keycloak realm in the Keycloak Public Key field.
- Enter the OIDC secret (Client Secret) from your Keycloak installation in the Keycloak OIDC Secret field.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Troubleshooting
If you receive an jwt.exceptions.InvalidAudienceError: Audience doesn’t match error, you must re-enable the audience by doing the following:
- From the navigation for your Keycloak configuration, select → → → .
- Pick a name for the mapper.
-
Select the Client ID corresponding to your client in
Included Client Audience.
2.5.9. Configuring GitHub authentication
You can connect GitHub identities to Ansible Automation Platform using OAuth. To set up GitHub authentication, you need to obtain an OAuth2 key and secret by registering your organization-owned application from GitHub using the registering the new application with GitHub.
The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select GitHub from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
When the application is registered, GitHub displays the Client ID and Client Secret:
- Copy and paste the GitHub Client ID into the GitHub OAuth2 Key field.
- Copy and paste the GitHub Client Secret into the GitHub OAuth2 Secret field.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.10. Configuring GitHub organization authentication
When defining account authentication with either an organization or a team within an organization, you should use the specific organization and team settings. Account authentication can be limited by an organization and by a team within an organization. You can also choose to permit all by specifying non-organization or non-team based settings. You can limit users who can log in to the platform by limiting only those in an organization or on a team within an organization.
To set up social authentication for a GitHub organization, you must obtain an OAuth2 key and secret for a web application using the registering the new application with GitHub.
The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select GitHub organization from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
When the application is registered, GitHub displays the Client ID and Client Secret:
- Copy and paste the GitHub Client ID into the GitHub OAuth2 Key field.
- Copy and paste the GitHub Client Secret into the GitHub OAuth2 Secret field.
-
Enter the name of your GitHub organization, as used in your organization’s URL, for example,
https://github.com/<yourorg>/in the GitHub OAuth Organization Name field. Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
-
Enter the authorization scope for users in the GitHub OAuth2 Scope field. The default is
read:org. - To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.11. Configuring GitHub team authentication
To set up social authentication for a GitHub team, you must obtain an OAuth2 key and secret for a web application using the instructions provided in registering the new application with GitHub.
The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select GitHub team from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
When the application is registered, GitHub displays the Client ID and Client Secret:
- Copy and paste the GitHub Client ID into the GitHub OAuth2 Key field.
- Copy and paste the GitHub Client Secret into the GitHub OAuth2 Secret field.
- Copy and paste GitHub’s team ID in the GitHub OAuth2 Team ID field.
-
Enter the authorization scope for users in the GitHub OAuth2 Scope field. The default is
read:org. Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.12. Configuring GitHub enterprise authentication
To set up social authentication for a GitHub enterprise, you must obtain a GitHub Enterprise URL, an API URL, OAuth2 key and secret for a web application.
To obtain the URLs, refer to the GitHub Enterprise administration documentation.
The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select GitHub enterprise from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
When the application is registered, GitHub displays the Client ID and Client Secret:
- Copy and paste the GitHub Client ID into the GitHub OAuth2 Key field.
- Copy and paste the GitHub Client Secret into the GitHub OAuth2 Secret field.
-
In the Base URL field, enter the hostname of the GitHub Enterprise instance, for example,
https://github.example.com. -
In the Github OAuth2 Enterprise API URL field, enter the API URL of the GitHub Enterprise instance, for example,
https://github.example.com/api/v3. Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.13. Configuring GitHub enterprise organization authentication
To set up social authentication for a GitHub enterprise organization, you must obtain a GitHub enterprise organization URL, an Organization API URL, an Organization OAuth2 key and secret for a web application.
To obtain the URLs, refer to the GitHub Enterprise administration documentation.
The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select GitHub enterprise organization from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
When the application is registered, GitHub displays the Client ID and Client Secret:
- Copy and paste the GitHub Client ID into the GitHub OAuth2 Key field.
- Copy and paste the GitHub Client Secret into the GitHub OAuth2 Secret field.
-
In the Base URL field, enter the hostname of the GitHub Enterprise instance, for example,
https://github.example.com. -
In the Github OAuth2 Enterprise API URL field, enter the API URL of the GitHub Enterprise instance, for example,
https://github.example.com/api/v3. -
Enter the name of your GitHub enterprise organization, as used in your organization’s URL, for example,
https://github.com/<yourorg>/in the GitHub OAuth2 Enterprise Org Name field. Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.14. Configuring GitHub enterprise team authentication
To set up social authentication for a GitHub enterprise team, you must obtain a GitHub Enterprise Organization URL, an Organization API URL, an Organization OAuth2 key and secret for a web application.
To obtain the URLs, refer to the GitHub Enterprise administration documentation.
To obtain the key and secret, you must first register your enterprise organization-owned application at https://github.com/organizations/<yourorg>/settings/applications.
The OAuth2 key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI. To register the application, you must supply it with your webpage URL, which is the Callback URL shown in the Authenticator details for your authenticator configuration. See Displaying authenticator details for instructions on accessing this information.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2key (Client ID) and secret (Client Secret) are used to supply the required fields in the UI.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select GitHub enterprise team from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
When the application is registered, GitHub displays the Client ID and Client Secret:
- Copy and paste the GitHub Client ID into the GitHub OAuth2 Key field.
- Copy and paste the GitHub Client Secret into the GitHub OAuth2 Secret field.
-
In the Base URL field, enter the hostname of the GitHub Enterprise instance, for example,
https://github.orgexample.com. -
In the Github OAuth2 Enterprise API URL field, enter the API URL of the GitHub Enterprise instance, for example,
https://github.example.com/api/v3. - Enter the OAuth2 key (Client ID) from your GitHub developer application in the GitHub OAuth2 team ID field.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
Verification
To verify that the authentication is configured correctly, log out of Ansible Automation Platform and check that the login screen displays the logo of your authentication chosen method to enable logging in with those credentials.
2.5.15. Configuring RADIUS authentication
You can configure Ansible Automation Platform to centrally use RADIUS as a source for authentication information.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name for this authentication configuration.
- Select Radius from the Authentication type list. The Authentication details section automatically updates to show the fields relevant to the selected authentication type.
- Select a legacy authenticator method from the Auto migrate users from list. After upgrading from 2.4 to 2.5, this is the legacy authenticator from which to automatically migrate users to this new authentication configuration. Refer to Ansible Automation Platform post-upgrade steps in the RPM upgrade and migration guide for important information about migrating users.
- Enter the host or IP of the RADIUS server in the RADIUS Server field. If you leave this field blank, RADIUS authentication is disabled.
- Enter the Shared secret for authenticating to RADIUS server.
Optional: Enter any Additional Authenticator Fields that this authenticator can take. These fields are not validated and are passed directly back to the authenticator.
NoteValues defined in this field override the dedicated fields provided in the UI. Any values not defined here are not provided to the authenticator.
- To automatically create organizations, users, and teams upon successful login, select Create objects.
- To enable this authentication method upon creation, select Enabled.
- To remove a user for any groups they were previously added to when they authenticate from this source, select Remove users.
- Click .
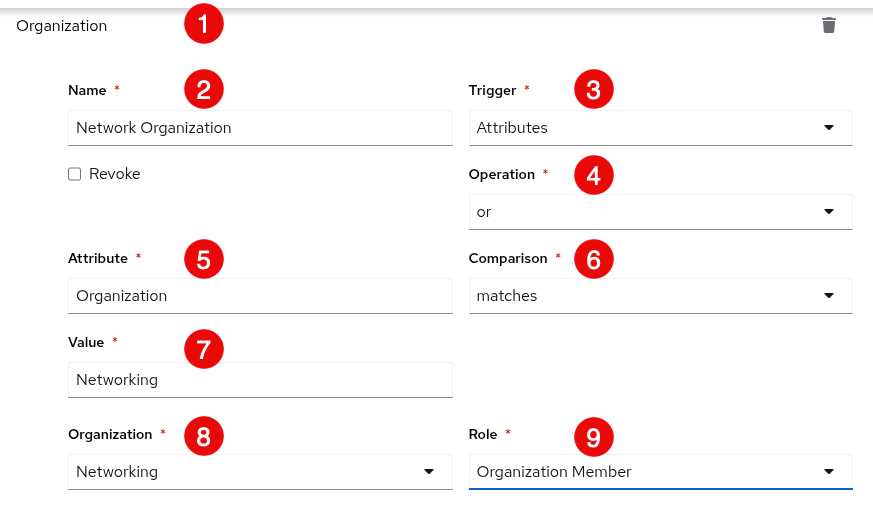
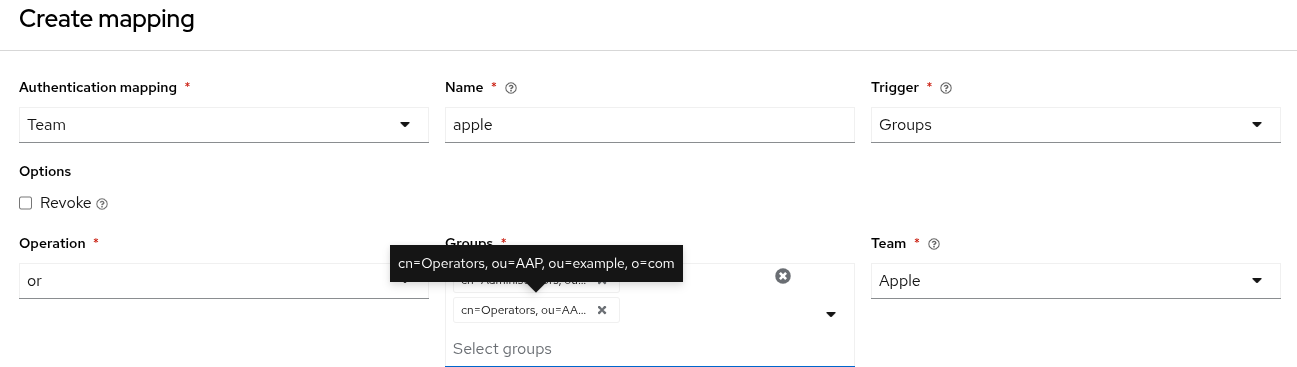
2.6. Mapping
To control which users are allowed into the Ansible Automation Platform server, and placed into Ansible Automation Platform organizations or teams based on their attributes (like username and email address) or what groups they belong to, you can configure authenticator maps.
Authenticator maps allow you to add conditions that must be met before a user is given or denied access to a resource type. Authenticator maps are associated with an authenticator and are given an order. The maps are processed in order when the user logs in. These can be thought of like firewall rules or mail filters.
2.6.1. Understanding authenticator mapping
- Authentication
- Validates a user’s identity, typically through a username and password or a trust system.
- Authorization
- Determines what an authenticated user can do once they are authenticated.
In Ansible Automation Platform, authenticators manage authentication, validating users and returning details such as their username, first name, email, and group memberships (for example, LDAP groups). Authorization comes from the authenticator’s associated maps.
During the authentication process, after a user has authenticated, the authorization system starts with a default set of permissions in memory. Then sequentially, the authenticator maps are processed and adjust permissions based on their trigger conditions. When all the authenticator’s maps are processed, the in-memory representation of the user’s permissions are reconciled with their existing permissions.
For example, here is a simplified in-memory representation of the default permissions as follows:
Access allowed = True Superuser permission = Undefined Admin of teams = None
Access allowed = True
Superuser permission = Undefined
Admin of teams = NoneAnd, you might have maps that need to be processed are processed in the following order:
- Allow rule set to never
- Allow rule based on group
- Superuser rule based on user attributes
- Team admin rule based on user group
The first Allow map, set to never, denies access to the system and the in-memory representation looks like:
Access allowed = False Superuser permission = Undefined Admin of teams = None
Access allowed = False
Superuser permission = Undefined
Admin of teams = NoneHowever, if the user matches the second Allow map (the group-based allow), the permissions change to the following:
Access allowed = True Superuser permission = Undefined Admin of teams = None
Access allowed = True
Superuser permission = Undefined
Admin of teams = NoneWhere the user is subsequently granted access to Ansible Automation Platform because they have the required groups.
Next, the Superuser map checks user attributes. If no match is found, it does not revoke existing permissions by default. Therefore, the permissions remain the same as the results from the previous map:
Access allowed = True Superuser permission = Skipped Admin of teams = None
Access allowed = True
Superuser permission = Skipped
Admin of teams = NoneTo revoke superuser access, you can select the Revoke option on the Superuser map. That way, when the user does not meet the attribute criteria, the permissions update to False like in the following:
Access allowed = True Superuser permission = False Admin of teams = None
Access allowed = True
Superuser permission = False
Admin of teams = NoneThe final Team map checks the user’s groups coming from the authenticator for admin access on the team “My Team”. If the user has the required group, the permissions update to the following:
Access allowed = True Superuser permission = False Admin of teams = “My Team”
Access allowed = True
Superuser permission = False
Admin of teams = “My Team”If the user lacks the required group, permissions remain unchanged unless the Revoke option has been selected on the map, in which case permissions update to the following:
Access allowed = True Superuser permission = False Admin of teams = Revoke admin of “My Team”
Access allowed = True
Superuser permission = False
Admin of teams = Revoke admin of “My Team”After processing all maps in the order defined, the final permissions reconcile, updating the user’s access based on the map rules.
In summary, authenticators validate users and delegate system authorization to the authenticator maps. Authenticator maps are executed in order creating an in-memory representation of the users' permissions which get reconciled with the actual permissions after all maps are executed.
By default, authenticator maps return either ALLOW or SKIPPED.
- ALLOW
- Means that a match is detected and the platform should grant the user access to the corresponding role or permission (such as, superuser, or team member).
- SKIPPED
- Means that the user did not match the trigger in the map and, the platform skips processing this map and continues to check the remaining maps. This is useful if you want to grant users additional permissions in the system without having to change the authenticator maps.
However, when the Revoke option is selected, SKIPPED becomes DENY and users who do not meet the required trigger criteria are denied access to the corresponding role or permission. This ensures that only users with matching trigger conditions are granted access.
2.6.2. Authenticator map types
Ansible Automation Platform supports the following rule types:
- Allow
- Determine if the user is allowed to log in to the system.
- Organization
- Determine if a user should be put into an organization.
- Team
- Determine if the user should be a member of a team.
- Role
- Determine if the user is a member of a role (for example, System Auditor).
- Is Superuser
- Determine if the user is a superuser in the system.
These authentication map types can be used with any type of authenticator.
2.6.3. Authenticator map triggers
Each map has a trigger that defines when the map should be evaluated as true. Trigger types include the following:
- Always
- The trigger should always be fired.
- Never
- The trigger should never be fired.
- Group
The map is true or false based on a user having, not having, or having multiple groups in the source system. See Authenticator map examples for information on using Group triggers.
When defining a group trigger, the authentication mapping expands to include the following selections:
Operation: This field includes conditional settings that trigger the handling of the rule based on the specified Groups criteria. The choices include and and or. For example, if you select and the user logging in must be a member of all of the groups specified in the Groups field for this trigger to be true. Alternatively, if you select or the user logging in must be a member of any of the specified Groups in order for the trigger to fire.
NoteIf you are only keying off one group it doesn’t matter if you select "and" or "or".
Groups: This is a list of one or more groups coming from the authentication system that the user must be a member of. The first time you create a Groups entry, you must manually enter the values. Once entered, that selection will be available from the Groups list.
See the Operation field to determine the behavior of the trigger if more than one group is specified in the trigger.
NoteGroup identifiers must be entered in lowercase. For example,
cn=johnsmith,dc=example,dc=cominstead ofCN=johnsmith,DC=example,DC=com.
- Attribute
The map is true or false based on a users attributes coming from the source system. See Authenticator map examples for information about using Attribute triggers.
When defining an attribute trigger, the authentication mapping expands to include the following selections:
Operation: This field includes conditional settings that trigger the handling of the rule based on the specified Attribute criteria. In version 2.5 this field indicates what will happen if the source system returns a list of attributes instead of a single value. For example, if the source system returns multiple emails for a user and Operation was set to and, all of the given emails must match the Comparison for the trigger to be True. If Operation was set to or, any of the returned emails will set the trigger to True if they match the Comparison in the trigger.
NoteIf you want to experiment with multiple attribute maps you can do that through the API but the UI form will remove multi-attribute maps if the authenticator is saved through the UI. When adding multiple attributes to a map, the Operation will also apply to the attributes.
-
Attribute: The name of the attribute coming from the source system this trigger will be evaluated against. For example, if you wanted the trigger to fire based on the user’s last name and the last name field in the source system was called
users_last_nameyou would enter the value ‘users_last_name’ in this field. Comparison: Tells the trigger how to evaluate the value of the users. Attribute in the source system compared to the Value specified on the trigger. Available options are: contains, matches, ends with, in, or equals. Below is a breakdown of each Comparison type:
- contains: The specified character sequence in Value is contained within the attributes value returned from the source. For example, given an attribute value of ‘John’ from the source the contains Comparison would set the trigger to True if the trigger Value was set to ‘Jo’ and False if the trigger Value was ‘Joy’.
- matches: The Value on the trigger is treated as a python regular expression and does an Regular expression match (re.match) (with case ignore on) between the specified Value and the value returned from the source system. For example, if the trigger’s Value was ‘Jo’ the trigger would return True if the value from the source was ‘John‘ or ‘Joanne‘ or any other value which matched the regular expression ‘Jo’. The trigger would return False if the sources value for the attribute was ‘Dan’ because ‘Dan’ does not match the regular expression ‘Jo’.
- ends with: The trigger will see if the value provided by the source ends with the specified Value of the trigger. For example, if the source provided a value of ‘John’ the trigger would be True if its Value was set to ‘n’ or ‘on’. The trigger would be False if its Value was set to ‘z’ because the value ‘John’ coming from the source does not end with the value ’z’ specified by the trigger.
- equal: The trigger will see if the value provided by the source is equal to (in its entirety) the specified Value of the trigger. For example, if the source returned the value ‘John’, the trigger would be True if its Value was set to ‘John’. Any value other than ‘John’ returned from the source would set this trigger to False.
- in: The in condition checks if the value matches one of several values. When in is specified as the Comparison, the Value field can be a comma-separated list. For example, if a trigger had a Value of ‘John,Donna’ the trigger would be True if the attribute coming from the source had either the value ‘John’ or ‘Donna’. Otherwise, the trigger would be False.
Value: The value that a users attribute will be matched against based on the Comparison field. See examples in the Comparison definition in this section.
NoteIf the Comparison type is in, this field can be a comma-separated list (without spaces).
2.6.4. Authenticator map examples
Use the following examples to explore the different conditions, like groups and attribute values you can implement to control user access to the platform.
Add users to an organization based on an attribute
In this example, you will add a user to the Networking organization if they have an Organization attribute with the value of Networking:
- The Organization title of the page indicates that you are configuring settings permissions on an organization.
-
Network Organizationis entered in this field and is the unique, descriptive name for this map configuration. -
Attributes is selected from the Trigger list to configure authentication based on an attribute from the source system, which in this example is
Organization. -
The operation is defined as
ormeaning that at least one condition must be true for authentication to succeed. - The Attribute coming from the source system is Organization.
-
The Comparison value is set to
matcheswhich means that when a user has the attribute Value ofNetworking, they are added to the Networking organization. -
The attribute Value coming from the source system is
Networking. -
The name of the Organization to which you are adding members is
Networking. -
Users are added to the Networking organization with the
Organization Memberrole.
Add users to a team based on the users group
In this example, you will add user to the Apple team if they have either of the following groups:
cn=Administrators,ou=AAP,ou=example,o=com
cn=Administrators,ou=AAP,ou=example,o=comor
cn=Operators,ou=AAP,ou=example,co=com
cn=Operators,ou=AAP,ou=example,co=comDo not escalate privileges
In this example, you never escalate users to a superuser. But note, this rule does not revoke a user’s superuser permission because the revoke option is not set.
Escalate privileges based on a user having a group
In this example, you escalate user privileges to superuser if they belong to the following group:
cn=Administrators,ou=AAP
cn=Administrators,ou=AAPUsing mapping order to create exceptions
Since maps are executed in order, it is possible to create exceptions. Expanding on the previous example for Do not escalate privileges, you can add another rule with a higher order, such as, Escalate privileges.
The first rule (Do not escalate privileges) prevents any user from being escalated to a superuser, but the second rule (Escalate privileges) alters that decision to grant superuser privileges to a user if they are in the Administrators group.
2.6.5. Allow mapping
With allow mapping, you can control which users have access to the system by defining the conditions that must be met.
Procedure
- After configuring the authentication details for your authentication method, select the Mapping tab.
- Select Allow from the Add authentication mapping list.
- Enter a unique rule Name to identify the rule.
- Select a Trigger from the list. See Authenticator map triggers for more information about map triggers.
- Select Revoke to deny user access to the system when the trigger conditions are not matched.
- Click .
2.6.6. Organization mapping
You can control which users are placed into which Ansible Automation Platform organizations based on attributes like their username and email address or based on groups provided from an authenticator.
When organization mapping is positively evaluated, a specified organization is created, if it does not exist if the authenticator tied to the map is allowed to create objects.
Procedure
- After configuring the authentication details for your authentication method, select the Mapping tab.
- Select Organization from the Add authentication mapping list.
- Enter a unique rule Name to identify the rule.
- Select a Trigger from the list. See Authenticator map triggers for more information about map triggers.
- Select Revoke to remove the user’s access to the selected organization role when the trigger conditions are not matched.
- Select the Organization to which matching users are added or blocked.
- Select a Role to be applied or removed for matching users (for example, Organization Admin or Organization Member).
- Click .
2.6.7. Team mapping
Team mapping is the mapping of team members (users) from authenticators.
You can define the options for each team’s membership. For each team, you can specify which users are automatically added as members of the team and also which users can administer the team.
Team mappings can be specified separately for each account authentication.
When Team mapping is positively evaluated, a specified team and its organization are created, if they don’t exist if the related authenticator is allowed to create objects.
When configuring team mappings with an Attribute trigger, use the or operation. The and operation requires every single value in a list to match the comparison criteria for the trigger to be successful. This is rarely the intended behavior, as you typically want a match on at least one value in the list.
Procedure
- After configuring the authentication details for your authentication method, select the Mapping tab.
- Select Team from the Add authentication mapping list.
- Enter a unique rule Name to identify the rule.
- Select a Trigger from the list. See Authenticator map triggers for more information about map triggers.
- Select Revoke to remove the user’s access to the selected organization role and deny user access to the system when the trigger conditions are not matched.
- Select the Team and Organization to which matching users are added or blocked.
- Select a Role to be applied or removed for matching users (for example, Team Admin or Team Member).
- Click .
2.6.8. Role mapping
Role mapping is the mapping of a user either to a global role, such as Platform Auditor, or team or organization role.
When a Team or Organization is specified together with the appropriate Role, the behavior is identical with Organization mapping or Team mapping.
Role mapping can be specified separately for each account authentication.
Procedure
- After configuring the authentication details for your authentication method, select the Mapping tab.
- Select Role from the Add authentication mapping list.
- Enter a unique rule Name to identify the rule.
- Select a Trigger from the list. See Authenticator map triggers for more information about map triggers.
- Select Revoke to remove the role for the user when none of the trigger conditions are matched.
- Select a Role to be applied or removed for matching users.
- Click .
2.6.9. Superuser mapping
Superuser mapping is the mapping of a user to the superuser role, such as System Administrator.
Procedure
- After configuring the authentication details for your authentication method, select the Mapping tab.
- Select Superuser from the Add authentication mapping list.
- Enter a unique rule Name to identify the rule.
- Select a Trigger from the list. See Authenticator map triggers for more information about map triggers.
- Select Revoke to remove the superuser role from the user when none of the trigger conditions are matched.
- Click .
2.6.10. Reviewing authenticator map results
As a platform administrator, you can review the authenticator map results through the users page in the API, api/gateway/v1/users/X, to see how the maps were evaluated when the user logged in to the platform.
2.7. Managing authentication in Ansible Automation Platform
After you have configured your authentication settings, you can view a list of authenticators, search, sort and view the details for each authenticator configured on the system.
2.7.1. Authentication list view
On the Authentication Methods page, you can view and manage the configured authentication methods for your organization.
Procedure
From the navigation panel, select → .
The Authentication Methods page is displayed.
- Click and follow the steps for creating an authentication method in Configuring an authentication type. Otherwise, proceed to step 3.
- From the menu bar, you can sort the list of authentication methods by using the arrows in the menu bar for Order, Name and Authentication type.
- Click the toggles to Enable or Disable authenticators.
2.7.2. Searching for an authenticator
You can search for a previously configured authenticator from the Authentication list view.
Procedure
- From the navigation panel, select → .
- In the search bar, enter an appropriate keyword for the authentication method you want to search for and click the arrow icon.
- If you don’t find what you’re looking for, you can narrow your search. From the filter list, select Name or Authentication type depending on the search term you want to use.
- Scroll through the list of search results and select the authenticator you want to review.
2.7.3. Displaying authenticator details
After you locate the authenticator you want to review, you can display the configuration details:
Procedure
- From the navigation panel, select → .
In the list view, select the authenticator name displayed in the Name column.
The authenticator Details page is displayed.
- From the Details page, you can review the configuration settings applied to the authenticator.
2.7.4. Editing an authenticator
You can modify the settings of previously configured authenticators from the Authentication list view.
Procedure
- From the navigation panel, select → .
In the list view, you can either:
-
Select the
 icon next to authenticator you want to modify, or
icon next to authenticator you want to modify, or
- Select the authenticator name displayed in the Name column and click from the Details page.
-
Select the
- Modify the authentication details or mapping configurations as required.
- Click .
2.7.5. Deleting an authenticator
You can modify the settings of previously configured authenticators from the Authentication list view.
Procedure
- From the navigation panel, select → .
- In the list view, select the checkbox next to the authenticator you want to delete.
Select Delete authentication from the ⋮ list.
NoteYou can delete multiple authenticators by selecting the checkbox next to each authenticator you want to remove, and clicking Delete selected authentication from the ⋮ list on the menu bar.
2.7.6. Google Cloud Platform network configuration for increased authentication performance
In a Google Cloud Platform (GCP) environment, a high volume of traffic can lead to authentication and performance issues because of the low default port limit set on the GCP Cloud NAT gateway. While this configuration affects all GCP deployments, the highest risk for hitting this limit occurs when Ansible Automation Platform is deployed on OpenShift (version 4.17 and above).
The default setting for the Cloud NAT gateway’s Minimum ports per VM instance in OpenShift installations on GCP (version 4.17 and above) is 64. This low port limit can be quickly exhausted when platform gateway handles concurrent external network connections, such as Single Sign-On (SSO) requests. When the limit is reached, it prevents new outgoing connections, causing authentication failures or severe performance degradation.
2.7.6.1. Increasing the minimum ports
To address this limitation, manually increase the Minimum ports per VM instance setting for the Cloud NAT gateway associated with the worker nodes.
Use the Google Cloud Console to apply this workaround.
Procedure
- Go to the Cloud NAT service.
- Locate and select the NAT gateway configured for your OpenShift cluster’s worker nodes.
Increase the default value of 64 for the Minimum ports per VM instance setting to a higher value to accommodate your anticipated traffic volume.
Increasing this limit ensures enough available ports for external communication, reducing the likelihood of performance issues during high-volume authentication and external communication tasks.
Chapter 3. Configuring access to external applications with token-based authentication
Token-based authentication permits authentication of third-party tools and services with the platform through integrated OAuth 2 token support. Ansible Automation Platform utilizes both OAuth Tokens and Personal Access Tokens (PATs).
- OAuth Tokens
- OAuth Tokens are tied to specific applications and allow applications to access data without disclosing user login information.
- Personal Access Tokens
- PATs are personal to a user and not tied to a specific application. They are created directly by a user for their own use.
The default expiration for access tokens has been updated from 1000 years to 1 year. This change ensures frequent token rotation for increased credential security.
Access tokens in controller 2.4 and previous versions of the platform gateway were valid for 1000 years. Any existing tokens created prior to the 2.5.20250604 patch release will retain a 1000 year expiration.
You can customize this setting to meet your specific requirements by modifying the expiration time in your settings.py file as follows:
OAUTH2_PROVIDER__ACCESS_TOKEN_EXPIRE_SECONDS = 31536000
OAUTH2_PROVIDER__ACCESS_TOKEN_EXPIRE_SECONDS = 31536000
For more information about the settings.py file and how it can be used to configure aspects of the platform, see settings.py in Operating Ansible Automation Platform.
For more information about the OAuth2 specification, see The OAuth 2.0 Authorization Framework.
For more information about using the manage utility to create tokens, see Token and session management.
3.1. Applications
Create and configure token-based authentication for external applications such as ServiceNow and Jenkins. With token-based authentication, external applications can easily integrate with Ansible Automation Platform.
Automation controller OAuth applications on the platform UI are not supported for 2.4 to 2.5 migration. See this Knowledgebase article for more information.
As a platform administrator, you can configure a custom external application URL within the platform, providing seamless integration with external services. This functionality is currently available as a Technology Preview. Once configured, the external application URL appears in the platform UI navigation panel, providing users with easy access to the application. This feature streamlines workflows by ensuring quick access to external services from within the platform UI.
Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process.
For more information about the support scope of Red Hat Technology Preview features, see Technology Preview Features Support Scope.
With OAuth 2 you can use tokens to share data with an application without disclosing login information. You can configure these tokens as read-only.
You can create an application that is representative of the external application you are integrating with, then use it to create tokens for the application to use on behalf of its users.
Associating these tokens with an application resource enables you to manage all tokens issued for a particular application. By separating the issue of tokens under OAuth Applications, you can revoke all tokens based on the application without having to revoke all tokens in the system.
3.1.1. Getting started with OAuth Applications
You can access the OAuth Applications page from the navigation panel by selecting → . From there you can view, create, sort and search for applications currently managed by Ansible Automation Platform and automation controller.
If no applications exist, you can create one by clicking .
Access rules for applications are as follows:
- Platform administrators can view and manipulate all applications in the system.
- Platform auditors can only view applications in the system.
- Tokens, on the other hand, are resources used to authenticate incoming requests and mask the permissions of the underlying user.
Access rules for tokens are as follows:
- Users can create personal access tokens for themselves.
- Platform administrators are able to view and manipulate every token in the system.
- Platform auditors can only view tokens in the system.
- Other normal users are only able to view and manipulate their own tokens.
Users can only view the token or refresh the token value at the time of creation.
3.1.1.1. Application functions
Several OAuth 2 utilities are available for authorization, token refresh, and revoke. You can specify the following grant types when creating an application:
- Password
- This grant type is ideal for users who have native access to the web application and must be used when the client is the resource owner.
- Authorization code
- This grant type should be used when access tokens must be issued directly to an external application or service.
You can only use the authorization code type to acquire an access token when using an application. When integrating an external web application with Ansible Automation Platform, that web application might need to create OAuth2 tokens on behalf of users in that other web application. Creating an application in the platform with the authorization code grant type is the preferred way to do this because:
- This allows an external application to obtain a token from Ansible Automation Platform for a user, using their credentials.
- Compartmentalized tokens issued for a particular application enables those tokens to be easily managed. For example, revoking all tokens associated with that application without having to revoke all tokens in the system.
3.1.1.1.1. Requesting an access token after expiration
The default expiration for access tokens is 1 year.
The best way to set up application integrations using the Authorization code grant type is to allowlist the origins for those cross-site requests. More generally, you must allowlist the service or application you are integrating with the platform, for which you want to provide access tokens.
To do this, have your administrator add this allowlist to their local Ansible Automation Platform settings file:
CORS_ORIGIN_ALLOW_ALL = True
CORS_ALLOWED_ORIGIN_REGEXES = [
r"http://django-oauth-toolkit.herokuapp.com*",
r"http://www.example.com*"
]
CORS_ORIGIN_ALLOW_ALL = True
CORS_ALLOWED_ORIGIN_REGEXES = [
r"http://django-oauth-toolkit.herokuapp.com*",
r"http://www.example.com*"
]
Where http://django-oauth-toolkit.herokuapp.com and http://www.example.com are applications requiring tokens with which to access the platform.
3.1.2. Creating a new application
When integrating an external web application with Ansible Automation Platform, the web application might need to create OAuth2 tokens on behalf of users of the web application.
Creating an application with the Authorization Code grant type is the preferred way to do this for the following reasons:
- External applications can obtain a token for users, using their credentials.
- Compartmentalized tokens issued for a particular application, enables those tokens to be easily managed. For example, revoking all tokens associated with that application.
Procedure
- From the navigation panel, select → .
- Click . The Create Application page opens.
Enter the following details:
- Name
- (required) Enter a name for the application you want to create.
- URL
- (optional) Enter the URL of the external application. This link is added to the navigation panel for easy access. This setting is currently offered as a Technology Preview only.
- Description
- (optional) Include a short description for your application.
- Organization
- (required) Select an organization with which this application is associated.
- Authorization grant type
- (required) Select one of the grant types to use for the user to get tokens for this application. For more information, see Application functions for more information about grant types.
- Client Type
- (required) Select the level of security of the client device.
- Redirect URIS
- Provide a list of allowed URIs, separated by spaces. You need this if you specified the grant type to be Authorization code.
Click , or click to abandon your changes.
The Client ID and Client Secret display in a window. This will be the only time the client secret will be shown.
NoteThe Client Secret is only created when the Client type is set to Confidential.
- Click the copy icon and save the client ID and client secret to integrate an external application with Ansible Automation Platform.
3.2. Adding tokens
You can view a list of users that have tokens to access an application by selecting the Tokens tab in the OAuth Applications details page.
You can only create OAuth 2 Tokens for your own user, which means you can only configure or view tokens from your own user profile.
When authentication tokens have been configured, you can select the application to which the token is associated and the level of access that the token has.
Procedure
- From the navigation panel, select → .
- Select the username for your user profile to configure OAuth 2 tokens.
Select the Tokens tab.
When no tokens are present, the Tokens screen prompts you to add them.
- Click to open the Create Token window.
Enter the following details:
- Application
Enter the name of the application with which you want to associate your token. Alternatively, you can search for it by clicking . This opens a separate window that enables you to choose from the available options. Select Name from the filter list to filter by name if the list is extensive.
NoteTo create a Personal Access Token (PAT) that is not linked to any application, leave the Application field blank.
- Description
- (optional) Provide a short description for your token.
- Scope
(required) Specify the level of access you want this token to have. The scope of an OAuth 2 token can be set as one of the following:
- Write: Allows requests sent with this token to add, edit and delete resources in the system.
- Read: Limits actions to read only. Note that the write scope includes read scope.
Click , or click to abandon your changes.
The Token information is displayed with Token and Refresh Token information, and the expiration date of the token. This will be the only time the token and refresh token will be shown. You can view the token association and token information from the list view.
- Click the copy icon and save the token and refresh token for future use.
Verification
You can verify that the application now shows the user with the appropriate token using the Tokens tab on the Applications details page.
- From the navigation panel, select → .
- Select the application you want to verify from the Applications list view.
Select the Tokens tab.
Your token should be displayed in the list of tokens associated with the application you chose.
Additional resources
3.2.1. Application token functions
The refresh and revoke functions associated with tokens, for tokens at the /o/ endpoints can currently only be carried out with application tokens.
3.2.1.1. Refresh an existing access token
The following example shows an existing access token with a refresh token provided:
The /o/token/ endpoint is used for refreshing the access token:
curl -X POST \
-d "grant_type=refresh_token&refresh_token=AL0NK9TTpv0qp54dGbC4VUZtsZ9r8z" \
-u "gwSPoasWSdNkMDtBN3Hu2WYQpPWCO9SwUEsKK22l:fI6ZpfocHYBGfm1tP92r0yIgCyfRdDQt0Tos9L8a4fNsJjQQMwp9569eIaUBsaVDgt2eiwOGe0bg5m5vCSstClZmtdy359RVx2rQK5YlIWyPlrolpt2LEpVeKXWaiybo" \
http://<gateway>/o/token/ -i
curl -X POST \
-d "grant_type=refresh_token&refresh_token=AL0NK9TTpv0qp54dGbC4VUZtsZ9r8z" \
-u "gwSPoasWSdNkMDtBN3Hu2WYQpPWCO9SwUEsKK22l:fI6ZpfocHYBGfm1tP92r0yIgCyfRdDQt0Tos9L8a4fNsJjQQMwp9569eIaUBsaVDgt2eiwOGe0bg5m5vCSstClZmtdy359RVx2rQK5YlIWyPlrolpt2LEpVeKXWaiybo" \
http://<gateway>/o/token/ -i
Where refresh_token is provided by refresh_token field of the preceding access token.
The authentication information is of format <client_id>:<client_secret>, where client_id and client_secret are the corresponding fields of the underlying related application of the access token.
The special OAuth 2 endpoints only support using the x-www-form-urlencoded Content-type, so as a result, none of the /o/* endpoints accept application/json.
On success, a response displays in JSON format containing the new (refreshed) access token with the same scope information as the previous one:
The refresh operation replaces the existing token by deleting the original and then immediately creating a new token with the same scope and related application as the original one.
Verify that the new token is present and the old one is deleted in the api/gateway/v1/tokens/ endpoint.
3.2.1.2. Revoke an access token
You can revoke an access token by deleting the token in the platform UI, or by using the /o/revoke-token/ endpoint.
Revoking an access token by this method is the same as deleting the token resource object, but it enables you to delete a token by providing its token value, and the associated client_id (and client_secret if the application is confidential). For example:
curl -X POST -d "token=rQONsve372fQwuc2pn76k3IHDCYpi7" \ -u "gwSPoasWSdNkMDtBN3Hu2WYQpPWCO9SwUEsKK22l:fI6ZpfocHYBGfm1tP92r0yIgCyfRdDQt0Tos9L8a4fNsJjQQMwp9569eIaUBsaVDgt2eiwOGe0bg5m5vCSstClZmtdy359RVx2rQK5YlIWyPlrolpt2LEpVeKXWaiybo" \ http://<gateway>/o/revoke_token/ -i
curl -X POST -d "token=rQONsve372fQwuc2pn76k3IHDCYpi7" \
-u "gwSPoasWSdNkMDtBN3Hu2WYQpPWCO9SwUEsKK22l:fI6ZpfocHYBGfm1tP92r0yIgCyfRdDQt0Tos9L8a4fNsJjQQMwp9569eIaUBsaVDgt2eiwOGe0bg5m5vCSstClZmtdy359RVx2rQK5YlIWyPlrolpt2LEpVeKXWaiybo" \
http://<gateway>/o/revoke_token/ -i-
The special OAuth 2 endpoints only support using the
x-www-form-urlencodedContent-type, so as a result, none of the/o/*endpoints acceptapplication/json. -
The Allow External Users to Create Oauth2 Tokens (
ALLOW_OAUTH2_FOR_EXTERNAL_USERSin the API) setting is disabled by default. External users refer to users authenticated externally with a service such as LDAP, or any of the other SSO services. This setting ensures external users cannot create their own tokens. If you enable then disable it, any tokens created by external users in the meantime will still exist, and are not automatically revoked. This setting can be configured from the → menu.
Alternatively, to revoke OAuth2 tokens, you can use the manage utility, see Revoke oauth2 tokens.
On success, a response of 200 OK is displayed. Verify the deletion by checking whether the token is present in the api/gateway/v1/tokens/ endpoint.
3.2.2. Token and session management
Ansible Automation Platform supports the following commands for OAuth2 token management:
3.2.2.1. create_oauth2_token
Use the following command to create OAuth2 tokens (specify the username for example_user):
aap-gateway-manage create_oauth2_token --user example_user
$ aap-gateway-manage create_oauth2_token --user example_user
New OAuth2 token for example_user: j89ia8OO79te6IAZ97L7E8bMgXCON2Ensure that you provide a valid user when creating tokens. Otherwise, an error message that you attempted to issue the command without specifying a user, or supplied a username that does not exist, is displayed.
3.2.2.2. revoke_oauth2_tokens
Use this command to revoke OAuth2 tokens, both application tokens and personal access tokens (PAT). It revokes all application tokens (but not their associated refresh tokens), and revokes all personal access tokens. However, you can also specify a user for whom to revoke all tokens.
To revoke all existing OAuth2 tokens use the following command:
aap-gateway-manage revoke_oauth2_tokens
$ aap-gateway-manage revoke_oauth2_tokensTo revoke all OAuth2 tokens and their refresh tokens use the following command:
aap-gateway-manage revoke_oauth2_tokens --revoke_refresh
$ aap-gateway-manage revoke_oauth2_tokens --revoke_refresh
To revoke all OAuth2 tokens for the user with id=example_user (specify the username for example_user):
aap-gateway-manage revoke_oauth2_tokens --user example_user
$ aap-gateway-manage revoke_oauth2_tokens --user example_user
To revoke all OAuth2 tokens and refresh token for the user with id=example_user:
aap-gateway-manage revoke_oauth2_tokens --user example_user --revoke_refresh
$ aap-gateway-manage revoke_oauth2_tokens --user example_user --revoke_refresh3.2.2.3. cleartokens
Use this command to clear tokens which have already been revoked.
For more information, see cleartokens in Django’s Oauth Toolkit documentation.
3.2.2.4. clearsessions
Use this command to delete all sessions that have expired.
For more information, see Clearing the session store in Django’s Oauth Toolkit documentation.
For more information on OAuth2 token management in the UI, see the Applications.
3.3. Manage OAuth2 token creation for external users
Red Hat Ansible Automation Platform is designed with a default security posture that prevents users authenticated through external providers, such as LDAP, SAML, or SSO, from creating OAuth2 tokens for programmatic API access. When an external user tries to generate such a token, the following message appears: 403: Forbidden' error with the message: '(access_denied) OAuth2 Tokens cannot be created by users associated with an external authentication provider.
This default behavior is a deliberate security measure. Ansible Automation Platform prioritizes centralized control over token generation, which encourages administrators to select the appropriate method for enabling OAuth 2.0 user token generation for external authentication providers.
It is important to understand that an OAuth2 token is created within Ansible Automation Platform, and Ansible Automation Platform itself manages its lifecycle, including its expiration. This lifecycle is independent of the user’s session with their external Identity Provider (IdP). For example, if a user generates an Ansible Automation Platform token and their account is later disabled in the external IdP, the Ansible Automation Platform token remains valid until it expires or is manually revoked. Being aware of this interaction is crucial for a secure configuration, as it highlights the need for compensating controls if you enable token creation for external users.
3.3.1. Enabling OAuth2 token creation for external users
To enable external users to create OAuth2 tokens, change the appropriate setting in your Ansible Automation Platform environment. Ensure the implementation of compensating security controls after enabling this setting.
Procedure
- From the navigation panel, go to → .
- Click settings.
- Change the Allow external users to create OAuth2 tokens setting to Enabled.
- Click .
Next steps
Implement the recommended security controls as described in Implementing security controls for external user OAuth2 tokens.
3.3.2. Implementing security controls for external user OAuth2 tokens
After enabling OAuth2 token creation for external users, implement the following compensating controls to keep a strong security posture.
Procedure
Limit token lifetime: Configure a shorter duration for OAuth2 tokens to reduce the window of exposure.
-
In your Ansible Automation Platform settings, adjust the
OAUTH2_ACCESS_TOKEN_EXPIRE_SECONDS value. A value of 28800 (8 hours) is recommended, limiting token validity to a standard workday.
-
In your Ansible Automation Platform settings, adjust the
Enforce strict role-based access control (RBAC): Grant users only the minimum necessary permissions.
- Assign users who create tokens to Teams with highly restrictive roles. Avoid granting broad permissions that could lead to privilege escalation.
- Establish a clear offboarding process: Integrate token revocation into your organizational offboarding procedures. Your HR and IT offboarding processes must include a step for an Ansible Automation Platform administrator to revoke all active tokens for a departing user. Tokens can be manually revoked from the user’s profile under the Tokens tab.
- Audit and monitor: Regularly review token-related activities for legitimacy in the Activity Stream.
Chapter 4. Managing access with role-based access control
Role-based access control (RBAC) restricts user access based on their role within an organization to which they are assigned in Ansible Automation Platform. The roles in RBAC refer to the levels of access that users have to the Ansible Automation Platform components and resources.
You can control what users can do with the components of Ansible Automation Platform at a broad or granular level depending on your RBAC policy. You can designate whether the user is a system administrator or normal user and align roles and access permissions with their positions within the organization.
Roles can be defined with multiple permissions that can then be assigned to resources, teams and users. The permissions that make up a role dictate what the assigned role allows. Permissions are allocated with only the access needed for a user to perform the tasks appropriate for their role.
4.1. Organizations
An organization is a logical collection of users, teams, and resources. It is the highest level object in the Ansible Automation Platform object hierarchy. After you have created an organization, Ansible Automation Platform displays the organization details. You can then manage access and execution environments for the organization. Ansible Automation Platform automatically creates a default organization and the system administrator is automatically assigned to this organization. If you have a Self-support level license, you have only the default organization available and must not delete it.
4.1.1. Organizations list view
The Organizations page displays the existing organizations for your installation. From here, you can search for a specific organization, filter the list of organizations, or change the sort order for the list.
Procedure
- From the navigation panel, select → .
- In the Search bar, enter an appropriate keyword for the organization you want to search for and click the arrow icon.
- From the menu bar, you can sort the list of organizations by using the arrows for Name to toggle your sorting preference.
- You can also sort the list by selecting Name, Created or Last modified from the Sort list.
- You can view organization details by clicking an organization Name on the Organizations page.
4.1.2. Creating an organization
Ansible Automation Platform automatically creates a default organization. If you have a self-support level license, you have only the default organization available and cannot delete it.
Procedure
- From the navigation panel, select → .
- Click .
Enter the Name and optionally provide a Description for your organization.
NoteIf automation controller is enabled on the platform, continue with Step 4. Otherwise, proceed to Step 6.
- Select the name of the Execution environment or search for one that exists that members of this team can run automation.
- Enter the name of the Instance Groups on which to run this organization.
- Optional: Enter the Galaxy credentials or search from a list of existing ones.
Select the Max hosts for this organization. The default is 0. When this value is 0, it signifies no limit. If you try to add a host to an organization that has reached or exceeded its cap on hosts, an error message displays:
You have already reached the maximum number of 1 hosts allowed for your organization. Contact your System Administrator for assistance.
You have already reached the maximum number of 1 hosts allowed for your organization. Contact your System Administrator for assistance.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click .
If you selected more than 1 instance group, you can manage the order by dragging and dropping the instance group up or down in the list and clicking .
NoteThe execution precedence is determined by the order in which the instance groups are listed.
- Click and verify the organization settings.
- Click .
4.1.3. Access to organizations
You can manage access to an organization by selecting an organization from the Organizations list view and selecting the associated tabs for providing access to Users, Administrators or Teams.
4.1.3.1. Adding a user to an organization
You can provide a user with access to an organization by adding them to the organization and managing the roles associated with the user. To add a user to an organization, the user must already exist. For more information, see Creating a user. To add roles for a user, the role must already exist. See Creating a role for more information.
The following tab selections are available when adding users to an organization. When user accounts from the automation controller organization have been migrated to Ansible Automation Platform 2.5 during the upgrade process, the Automation Execution tab shows content based on whether the users were added to the organization prior to migration.
- Ansible Automation Platform
- Reflects all users added to the organization at the platform level. From this tab, you can add users as organization members and, optionally provide specific organization level roles.
- Automation Execution
- Reflects users that were added directly to the automation controller organization prior to an upgrade and migration. From this tab, you can only view existing memberships in automation controller and remove those memberships but not you can not add new memberships.
New user memberships to an organization must be added at the platform level.
Procedure
- From the navigation panel, select → .
- From the Organizations list view, select the organization to which you want to add a user.
- Click the Users tab to add users.
- Select the Ansible Automation Platform tab and click to add user access to the team, or select the Automation Execution tab to view or remove user access from the team.
- Select one or more users from the list by clicking the checkbox next to the name to add them as members.
- Click .
Select the roles you want the selected user to have. Scroll down for a complete list of roles.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Click to review the roles settings.
Click to apply the roles to the selected users, and to add them as members. The Add roles dialog displays the updated roles assigned for each user.
NoteA user with associated roles retains them if they are reassigned to another organization.
- To remove a particular user from the organization, select Remove user from the More actions ⋮ list next to the user. This launches a confirmation dialog, asking you to confirm the removal.
- To manage roles for users in an organization, click the ⚙ icon next to the user and select Manage roles.
4.1.3.2. Adding an administrator to an organization
You can add administrators to an organization which allows them to manage the membership and settings of the organization. For example, they can create new users and teams within the organization, and grant permission to users within the organization. To add an administrator to an organization, the user must already exist.
Procedure
- From the navigation panel, select → .
- From the Organizations list view, select the organization to which you want to add a user, administrator, or team.
- Click the Administrators tab.
- Click .
- Select the users from the list by clicking the checkbox next to the name to assign the administrator role to them for this organization.
- Click .
To remove a particular administrator from the organization, select Remove administrator from the More actions ⋮ list next to the administrator name. This launches a confirmation dialog, asking you to confirm the removal.
NoteIf the user had previously been added as a member to this organization, they will continue to be a member of this organization. However, if they were added to the organization when the administrator assignment was made, they will be removed from the organization.
4.1.3.3. Adding a team to an organization
You can provide team access to an organization by adding roles to the team. To add roles to a team, the team must already exist in the organization. For more information, see Creating a team. To add roles for a team, the role must already exist. See Creating a role for more information.
Procedure
- From the navigation panel, select → .
- From the Organizations list view, select the organization to which you want to add team access.
- Click the Teams tab. If no teams exist, click to create a team and add it to this organization.
- Click .
Select the roles you want the selected team to have. Scroll down for a complete list of roles.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Click to review the roles settings.
- Click to apply the roles to the selected teams. The Add roles dialog displays the updated roles assigned for each team.
Click .
NoteA team with associated roles retains them if they are reassigned to another organization.
- To manage roles for teams in an organization, click the ⚙ icon next to the user and select Manage roles.
4.1.3.4. Deleting an organization
Before you can delete an organization, you must be an Organization administrator or System administrator. When you delete an organization, the organization, team, users and resources are permanently removed from Ansible Automation Platform.
When you attempt to delete items that are used by other resources, a message is displayed warning you that the deletion might impact other resources and prompts you to confirm the deletion. Some screens contain items that are invalid or have been deleted previously, and will fail to run.
Procedure
- From the navigation panel, select → .
- Click the ⋮ icon next to the organization you want removed and select Delete organization.
Select the confirmation checkbox and click to proceed with the deletion. Otherwise, click .
NoteYou can delete multiple organizations by selecting the checkbox next to each organization you want to remove, and selecting Delete selected organizations from the More actions ⋮ list on the menu bar.
4.1.4. Working with notifiers
When automation controller is enabled on the platform, you can review any notifier integrations you have set up and manage their settings within the organization resource.
Procedure
- From the navigation panel, select → .
- From the Organizations list view, select the organization to which you want to manage notifications.
- Select the Notification tab.
- Use the toggles to enable or disable the notifications to use with your particular organization. For more information, see Enable and disable notifications.
- If no notifiers have been set up, select → → from the navigation panel.
Additional resources
4.1.5. Working with execution environments
When automation controller is enabled on the platform, you can review any execution environments you have set up and manage their settings within the organization resource.
For more information about execution environments, see Execution environments in Using automation execution guide.
Procedure
- From the navigation panel, select → .
- From the Organizations list view, select the organization whose execution environments you want to manage.
- Select the Execution Environments tab.
- If no execution environments are available, click to create one. Alternatively, you can create an execution environment from the navigation panel by selecting → → .
Click .
NoteAfter creating a new execution environments, return to → and select the organization in which you created the execution environment to update the list on that tab.
- Select the execution environments to use with your particular organization.
4.2. Teams
A team is a subdivision of an organization with associated users, and resources. Teams provide a means to implement role-based access control schemes and delegate responsibilities across organizations. For example, you can grant permissions to a Team rather than each user on the team.
You can create as many teams as needed for your organization. Teams can only be assigned to one organization while an organization can be made up of multiple teams. Each team can be assigned roles, the same way roles are assigned for users. Teams can also scalably assign ownership for credentials, preventing multiple interface click-throughs to assign the same credentials to the same user.
4.2.1. Teams list view
The Teams page displays the existing teams for your installation. From here, you can search for a specific team, filter the list of teams by team name or organization, or change the sort order for the list.
Procedure
- From the navigation panel, select → .
- In the Search bar, enter an appropriate keyword for the team you want to search for and click the arrow icon.
- From the menu bar, you can sort the list of teams by using the arrows for Name and Organization to toggle your sorting preference.
- You can view team details by clicking a team Name on the Teams page.
- You can view organization details by clicking the link in the Organization column.
4.2.2. Creating a team
You can create new teams, assign an organization to the team, and manage the users and administrators associated with each team. Users associated with a team inherit the permissions associated with the team and any organization permissions to which the team has membership.
To add a user or administrator to a team, the user must have already been created.
Procedure
- From the navigation panel, select → .
- Click .
- Enter a Name and optionally give a Description for the team.
Select an Organization to be associated with this team.
NoteEach team can only be assigned to one organization.
Click .
The Details page opens, where you can review and edit your team information.
4.2.3. Adding users to a team
To add a user to a team, the user must already have been created. For more information, see Creating a user. Adding a user to a team adds them as a member only. Use the Roles tab to assign a role for different resources to the selected team.
The following tab selections are available when adding users to a team. When user accounts from automation controller or automation hub organizations have been migrated to Ansible Automation Platform 2.5 during the upgrade process, the Automation Execution and Automation Content tabs show content based on whether the users were added to those organizations prior to migration.
- Ansible Automation Platform
- Reflects all users added to the organization at the platform level. From this tab, you can add users as organization members and, optionally provide specific organization level roles.
- Automation Execution
- Reflects users that were added directly to the automation controller organization prior to an upgrade and migration. From this tab, you can only view existing memberships in automation controller and remove those memberships but you can not add new memberships. New organization memberships must be added through the platform.
- Automation Content
- Reflects users that were added directly to the automation hub organization prior to an upgrade and migration. From this tab, you can only view existing memberships in automation hub and remove those memberships but you can not add new memberships.
New user memberships to a team must be added at the platform level.
Procedure
- From the navigation panel, select → .
- Select the team to which you want to add users.
- Select the Users tab.
- Select the Ansible Automation Platform tab and click to add user access to the team, or select the Automation Execution or Automation Content tab to view or remove user access from the team.
- Select one or more users from the list by clicking the checkbox next to the name to add them as members of this team.
- Click .
4.2.4. Removing users from a team
You can remove a user from a team from the Team list view.
Procedure
- From the navigation panel, select → .
- Select the team from which you want to remove users.
- Select the Users tab.
- Click the Remove user icon next to the user you want to remove as a member of the team.
You can delete multiple users by selecting the checkbox next to each user you want to remove, and selecting Remove selected users from the More actions ⋮ list.
NoteIf the user is a Team administrator, you can remove their membership to the team from the Administrators tab.
This launches a confirmation dialog, asking you to confirm the removal.
4.2.5. Adding administrators to a team
You can add administrators to a team which allows them to manage the membership and settings of that team. For example, they can create new users and grant permission to users within the team. To add an administrator to a team, the administrator must already have been created. For more information, see Creating a user.
Procedure
- From the navigation panel, select → .
- Select the team to which you want to add an administrator.
- Select the Administrators tab and click .
- Select one or more users from the list by clicking the checkbox next to the name to add them as administrators of this team.
- Click .
4.2.6. Adding roles to a team
You can assign permissions to teams, such as edit and administer resources and other elements. You can set permissions through an inventory, project, job template and other resources, or within the Organizations view.
Teams cannot be assigned to an organization by adding roles. Refer to the steps provided in Adding a team to an organization for detailed instructions.
Procedure
- From the navigation panel, select → .
- Select the team Name to which you want to add roles.
Select the Roles tab and click .
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Select a Resource type and click .
- Select the resources to receive the new roles and click .
- Select the roles to apply to the resources and click .
Review the settings and click .
The Add roles dialog displays indicating whether the role assignments were successfully applied, click to close the dialog.
4.2.7. Removing roles from a team
You can remove roles from a team by selecting the - icon next to the resource. This launches a confirmation dialog, asking you to confirm the removal.
Procedure
- From the navigation panel, select → .
- Select the team Name from which you want to remove roles.
Select the Roles tab.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Select the checkbox next to each resource you want to remove and click Remove selected roles from the ⋮ list on the menu bar.
- Select the checkbox to confirm removal of the selected roles and click Remove role.
4.2.8. Deleting a team
Before you can delete a team, you must have team permissions. When you delete a team, the inherited permissions members got from that team are revoked.
Procedure
- From the navigation panel, select → .
- Select the checkbox for the team that you want to remove.
Select the ⋮ icon and select Delete team.
NoteYou can delete multiple teams by selecting the checkbox next to each team you want to remove, and selecting Delete teams from the More actions ⋮ list.
4.3. Users
Users associated with an organization are shown in the Users tab of the organization.
You can add other users to an organization, including a normal user or system administrator, but first, you must create them.
Ansible Automation Platform automatically creates a default admin user so they can log in and set up Ansible Automation Platform for their organization. This user can not be deleted or modified.
You can sort or search the User list by Username, First name, Last name, or Email. Click the arrows in the header to toggle your sorting preference. You can view User type and Email beside the user name on the Users page.
4.3.1. Users list view
The Users page displays the existing users for your installation. From here, you can search for a specific user, filter the list of users, or change the sort order for the list.
When user accounts have been migrated to Ansible Automation Platform 2.5 during the upgrade process, these accounts are also displayed in the Users list view. Users previously designated as automation controller or automation hub administrators are labeled as Normal in the User type column. You can see whether these users have administrator privileges, by editing the account. See Editing a user for instructions.
Procedure
- From the navigation panel, select → .
- In the Search bar, enter an appropriate keyword for the user you want to search for and click the arrow icon.
- From the menu bar, you can sort the list of users by using the arrows for Username, Email, First name, Last name or Last login to toggle your sorting preference.
- You can view user details by selecting a Username from the Users list view.
4.3.2. Creating a user
There are three types of users in Ansible Automation Platform:
- Normal user
- Normal users have read and write access limited to the resources (such as inventory, projects, and job templates) for which that user has been granted the appropriate roles and privileges. Normal users are the default type of user when no other User type is specified.
- Ansible Automation Platform Administrator
- An administrator (also known as a Superuser) has full system administration privileges, with full read and write privileges over the entire installation. An administrator is typically responsible for managing all aspects of and delegating responsibilities for day-to-day work to various users.
- Ansible Automation Platform Auditor
- Auditors have read-only capability for all objects within the environment.
Procedure
- From the navigation panel, select → .
- Click .
- Enter the details about your new user in the fields on the Create user page. Fields marked with an asterisk (*) are required.
Normal users are the default when no User type is specified. To define a user as an administrator or auditor, select a User type checkbox.
NoteIf you are modifying your own password, log out and log back in again for it to take effect.
- Select the Organization to be assigned for this user. For information about creating a new organization, see Creating an organization.
- Click .
Next steps
When the user is successfully created, the User dialog opens. From here, you can review and change the user’s Teams, Roles, Tokens and other membership details.
If the user is not newly-created, the details screen displays the last login activity of that user.
If you log in as yourself, and view the details of your user profile, you can manage tokens from your user profile by selecting the Tokens tab For more information, see Adding a token.
4.3.3. Editing a user
You can modify the properties of a user account after it is created.
In upgrade scenarios, there might be pre-existing user accounts from automation controller or automation hub services. When editing these user accounts, the User type checkboxes indicate whether the account had one of the following service level administrator privileges:
- Automation Execution Administrator
- A previously defined automation controller administrator with full read and write privileges over automation execution resources only.
- Automation Decisions Administrator
- A previously defined Event-Driven Ansible administrator with full read and write privileges over automation decision resources only.
- Automation Content Administrator
- A previously defined automation hub administrator with full read and write privileges over automation content resources only.
Platform administrators can revoke or assign administrator permissions for the individual services and designate the user as either an Ansible Automation Platform Administrator, Ansible Automation Platform Auditor or normal user. Assigning administrator privileges to all of the individual services automatically designates the user as an Ansible Automation Platform Administrator. See Creating a user for more information about user types.
To see whether a user had service level auditor privileges, you must refer to the API.
Users previously designated as automation controller or automation hub administrators are labeled as Normal in the User type column in the Users list view. You can see whether these users have administrator privileges, from the Edit Users page.
Procedure
- From the navigation panel, select → .
- Select the checkbox for the user that you want to modify.
- Click the Pencil icon and select Edit user.
The Edit user page is displayed where you can modify user details such as, Password, Email, User type, and Organization.
NoteIf the user account was migrated to Ansible Automation Platform 2.5 during the upgrade process and had administrator privileges for an individual service, additional User type checkboxes will be available. You can use these checkboxes to revoke or add individual privileges or designate the user as a platform administrator, system auditor or normal user.
- After your changes are complete, click Save user.
4.3.4. Deleting a user
Before you can delete a user, you must have normal user or system administrator permissions. When you delete a user account, the name and email of the user are permanently removed from Ansible Automation Platform.
Procedure
- From the navigation panel, select → .
- Select the checkbox for the user that you want to remove.
Click the ⋮ icon next to the user you want removed and select Delete user.
NoteYou can delete multiple users by selecting the checkbox next to each user you want to remove, and clicking Delete users from the More actions ⋮ list.
4.3.5. Adding roles for a user
You can grant access for users to use, read, or write credentials by assigning roles to them.
Users cannot be assigned to an organization by adding roles. Refer to the steps provided in Adding a user to an organization for detailed instructions.
Procedure
- From the navigation panel, select → .
- From the Users list view, click the user to which you want to add roles.
- Select the Roles tab to display the set of roles assigned to this user. These provide the ability to read, modify, and administer resources.
To add new roles, click .
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Select a Resource type and click .
- Select the resources that will receive new roles and click .
- Select the roles that will be applied to the resources and click .
Review the settings and click .
The Add roles dialog displays indicating whether the role assignments were successfully applied. Click to close the dialog.
4.3.6. Removing roles from a user
You can remove roles from a user by selecting the - icon next to the resource. This launches a confirmation dialog, asking you to confirm the removal.
Procedure
- From the navigation panel, select → .
- Select the user Name from which you want to remove roles.
Select the Roles tab.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Select the checkbox next to each resource you want to remove and click Remove selected roles from the More actions ⋮ list on the menu bar.
- Select the checkbox to confirm removal of the selected roles and click .
4.4. Resources
You can manage user access to Ansible Automation Platform resources and what users can do with those resources. Users are granted access through the roles to which they are assigned or through roles inherited through the role hierarchy, for example, through the roles they inherit through team membership. Ansible Automation Platform resources differ depending on the functionality you are configuring. For example, resources can be job templates and projects for automation execution or decision environments and rulebook activations for automation decisions.
4.4.1. Providing team access to a resource
You can grant users access based on their team membership. When you add a user as a member of a team, they inherit access to the roles and resources defined for that team.
Direct team access cannot be granted to → resources.
Procedure
- From the navigation panel, select a resource to which you want to provide team access. For example, → .
- Select the Team Access tab.
- Click .
- Click the checkbox beside the team to assign that team to your chosen type of resource and click .
- Select the roles you want applied to the team for the chosen resource and click .
- Review the settings and click . The Add roles dialog displays indicating whether the role assignments were successfully applied.
- You can remove resource access for a team by selecting the Remove role icon next to the team. This launches a confirmation dialog, asking you to confirm the removal.
4.4.2. Providing user access to a resource
You can grant users access to resources through the roles to which they are assigned.
Direct user access cannot be granted to → resources.
Procedure
- From the navigation panel, select a resource to which you want to provide team access. For example, → .
- Select the User access tab.
- Click .
- Click the checkbox beside the user to assign that user to your chosen type of resource and click .
- Select the roles you want applied to the user for the chosen resource and click .
- Review the settings and click . The Add roles dialog displays indicating whether the role assignments were successfully applied.
- You can remove resource access for a user by selecting the Remove role icon next to the user. This launches a confirmation dialog, asking you to confirm the removal.
Chapter 5. Roles
Roles are units of organization in the Red Hat Ansible Automation Platform. When you assign a role to a team or user, you are granting access to use, read, or write credentials. Because of the file structure associated with a role, roles become redistributable units that enable you to share behavior among resources, or with other users. All access that is granted to use, read, or write credentials is handled through roles, and roles are defined for a resource.
5.1. Displaying roles
You can display the roles assigned for component resources from the menu.
Procedure
- From the navigation panel, select → .
Select a tab for the component resource for which you want to create custom roles.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- From the table header, you can sort the list of roles by using the arrows for Name, Description, Created and Editable or by making sort selections in the Sort list.
- You can filter the list of roles by selecting Name or Editable from the filter list and clicking the arrow.
5.2. Creating a role
Ansible Automation Platform services provide a set of predefined roles with permissions sufficient for standard automation tasks. It is also possible to configure custom roles, and assign one or more permission filters to them. Permission filters define the actions allowed for a specific resource type.
Procedure
- From the navigation panel, select → .
Select a tab for the component resource for which you want to create custom roles.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Click .
- Provide a Name and optionally include a Description for the role.
- Select a Content Type.
- Select the Permissions you want assigned to this role.
- Click to create your new role.
5.3. Editing a role
Built-in roles cannot be changed, however, you can modify custom roles from the Roles list view. The Editable column in the Roles list view indicates whether a role is Built-in or Editable.
Procedure
- From the navigation panel, select → .
Select a tab for the component resource for which you want to modify a custom role.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
-
Click the Edit role icon
 next to the role you want and modify the role settings as needed.
next to the role you want and modify the role settings as needed.
- Click to save your changes.
5.4. Deleting a role
Built-in roles cannot be deleted, however, you can delete custom roles from the Roles list view.
Procedure
- From the navigation panel, select → .
Select a tab for the component resource for which you want to create custom roles.
NoteIf you have multiple Ansible Automation Platform components installed, you will see selections for the roles associated with each component in the Roles menu bar. For example, Automation Execution for automation controller roles, Automation Decisions for Event-Driven Ansible roles.
- Click the More Actions icon ⋮ next to the role you want and select Delete role.
- To delete roles in bulk, select the roles you want to delete from the Roles list view, click the More Actions icon ⋮, and select Delete roles.
Chapter 6. Configuring Ansible Automation Platform
You can configure Ansible Automation Platform from the Settings menu using the following selections:
- Subscriptions
- Platform gateway
- User Preferences
- Troubleshooting
The other selections available from the Settings menu are specific to automation execution. For more information, refer to the Configuring automation execution guide.
6.1. Configuring subscriptions
You can use the Subscription menu to view the details of your subscription, such as compliance, host-related statistics, or expiry, or you can apply a new subscription.
Ansible subscriptions require a service account from console.redhat.com. You must create a service account and use the client ID and client secret to activate your subscription.
If you enter your client ID and client secret but cannot locate your subscription, you might not have the correct permissions set on your service account. For more information and troubleshooting guidance for service accounts, see Configure Ansible Automation Platform to authenticate through service account credentials.
For Red Hat Satellite, input your Satellite username and Satellite password in the fields below.
Procedure
- From the navigation panel, select → . The Subscription page is displayed.
- Click .
- You can either enter your service account or Satellite credentials, or attach a current Subscription Manifest in the Welcome page.
- Click and agree to the terms of the license agreement.
- Click to review the subscription settings.
- Click to complete the configuration.
6.2. Platform gateway
The platform gateway is the service that handles authentication and authorization for Ansible Automation Platform. It provides a single ingress into the Platform and serves the Platform’s user interface.
From the → menu, you can configure Platform gateway, Security, Session, Platform Security, Custom Login, and Other settings.
Procedure
- From the navigation panel, select → .
- The Platform gateway settings page is displayed.
- To configure the options, click .
You can configure the following platform gateway options:
- Platform gateway proxy url: URL to the platform gateway proxy layer.
- Platform gateway proxy url ignore cert: Ignore the certificate to the platform gateway proxy layer.
- Click to save the changes or proceed to configure the other platform options available.
6.2.1. Configuring platform security
From the Platform gateway settings page, you can configure platform security settings.
Procedure
- From the navigation panel, select → .
- The Platform gateway settings page is displayed.
- To configure the options, click .
You can configure the following Security settings:
- Allow admin to set insecure: Whether a superuser account can save an insecure password when editing any local user account.
Gateway basic auth enabled: Enable basic authentication to the platform gateway API.
Turning this off prevents all basic authentication (local users), so customers need to make sure they have their alternative authentication mechanisms correctly configured before doing so.
Turning it off with only local authentication configured also prevents all access to the UI.
Social auth username is full email: Enabling this setting alerts social authentication to use the full email as username instead of the full name.
Gateway token name: The header name to push from the proxy to the backend service.
WarningIf this name is changed, backends must be updated to compensate.
- Gateway access token expiration: How long the access tokens are valid for.
Jwt private key: The private key used to encrypt the JWT tokens sent to backend services.
This should be a private RSA key and one should be generated automatically on installation.
NoteUse caution when rotating the key as it will cause current sessions to fail until their JWT keys are reset.
(Read only) Jwt public key: The private key used to encrypt the JWT tokens sent to backend services.
This should be a private RSA key and one should be generated automatically on installation.
NoteSee other services' documentation on how they consume this key.
- Click to save the changes or proceed to configure the other platform options available.
6.2.2. Configuring platform sessions
From the Platform gateway settings page, you can configure platform session settings.
Procedure
- From the navigation panel, select → .
- The Platform gateway settings page is displayed.
- To configure the options, click .
- Enter the time in seconds before a session expires in the Session cookie age field.
- Click to save the changes or proceed to configure the other platform options available.
6.2.3. Configuring a platform password security policy
From the Platform gateway settings page, you can configure a password security policy.
Procedure
- From the navigation panel, select → .
- The Platform gateway settings page is displayed.
- To configure the options, click .
You can configure the following Password Security options:
- Password minimum uppercase letters: How many uppercase characters need to be in a local password.
- Password minimum length: The minimum length of a local password.
- Password minimum numerical digits: How many numerical characters need to be in a local password.
- Password minimum special characters: How many special characters need to be in a local password.
- Click to save the changes or proceed to configure the other platform options available.
6.2.4. Configuring a custom platform log in
From the Platform gateway settings page, you can configure the custom log in options.
Procedure
- From the navigation panel, select → .
- The Platform gateway settings page is displayed.
- To configure the options, click .
You can configure the following Custom Login options:
-
Custom login info: Provide specific information (such as a legal notice or a disclaimer) to a text box in the login modal. For example, you can include a company banner with a statement such as, “This is only to be used for
<COMPANY_NAME>, etc.” - Custom logo : Provide an image file for setting up a custom logo (must be a data URL with a base64-encoded GIF, PNG, or JPEG image).
-
Custom login info: Provide specific information (such as a legal notice or a disclaimer) to a text box in the login modal. For example, you can include a company banner with a statement such as, “This is only to be used for
- Click to save the changes or proceed to configure the other platform options available.
6.2.5. Configuring additional platform options
From the Platform gateway settings page, you can configure additional platform options.
Procedure
- From the navigation panel, select → .
- The Platform gateway settings page is displayed.
- Click .
You can configure the following Other settings:
Jwt expiration buffer in seconds: The number of seconds before a JWT token’s expiration to revoke from the cache.
When authentication happens a JWT token is created for the user and that token is cached. When subsequent calls happen to services such as automation controller or Event-Driven Ansible, the token is taken from the cache and sent to the service. Both the token and the cache of the token have an expiration time. If the token expires while in the cache the authentication process attempts results in a 401 error (unauthorized). This setting gives Red Hat Ansible Automation Platform a buffer by removing the JWT token from the cache before the token expires. When a token is revoked from cache a new token with a new expiration is generated and cached for the user. As a result, expired tokens from the cache are never used. This setting defaults to 2 seconds. If you have a large latency between platform gateway and your services and observe 401 responses you must increase this setting to lower the number of 401 responses.
- Status endpoint backend timeout seconds: Timeout (in seconds) for the status endpoint to wait when trying to connect to a backend.
- Status endpoint backend verify: Specifies whether SSL certificates of the services are verified when calling individual nodes for statuses.
- Request timeout: Specifies, in seconds, the length of time before the proxy will report a timeout and generate a 504.
- *Allow external users to create OAuth2 tokens *: For security reasons, users from external authentication providers, such as LDAP, SAML, SSO, Radius, and others, are not allowed to create OAuth2 tokens. To change this behavior, enable this setting. Existing tokens are not deleted when this setting is turned off.
- Click to save the changes or proceed to configure the other platform options available.
6.3. User preferences
You can use the User preferences page to customize your platform experience. Use this menu to control theming, layout options and formatting.
User preferences are stored locally in your browser. This means that they are unique to you and your machine.
Procedure
- From the navigation panel, select → .
- The User Preferences page is displayed.
- Click .
You can configure the following options:
Refresh interval: Select the refresh interval for the page.
This refreshes the data on the page at the selected interval.
The refresh happens in the background and does not reload the page.
Color theme: Select from:
- Dark theme
- Light theme
- System default
Table layout: Select from:
- Comfortable
- Compact
Form columns: Select from:
- Multiple columns of inputs
- Single column of inputs
Date format Select from:
- Shows dates Relative to the current time
- Shows dates as Date and time
- Preferred data format: Sets the default format for when editing and displaying data.
- Click .
6.4. Troubleshooting options
You can use the Troubleshooting page to enable or disable certain flags that aid in debugging issues within Ansible Automation Platform.
Procedure
- From the navigation panel, select → → .
- The Troubleshooting page is displayed.
- Click .
You can select the following options:
- Enable or Disable tmp dir cleanup: Select this to enable or disable the cleanup of tmp directories generated during execution of a job after job execution completes.
- Debug Web Requests: Select this to enable or disable web request profiling for debugging slow web requests.
- Release Receptor Work: Select this to turn on or off the deletion of job pods after they complete or fail. This can be helpful in debugging why a job failed.
- Keep receptor work on error: Select this to prevent receptor work from being released when an error is detected.
- Click to save your changes.