5.5. Renewing Certificates
This section discusses how to renew certificates. For more information on how to set up certificate renewal, see Section 3.4, “Configuring Profiles to Enable Renewal”.
Renewing a certificate consists in regenerating the certificate with the same properties to be used for the same purpose as the original certificate. In general, there are two types of renewals:
- Same key Renewal takes the original key, profile, and request of the certificate and recreates a new certificate with a new validity period and expiration date using the identical key. This can be done by either of the following methods:
- resubmitting the original certificate request (CSR) through the original profile, or
- regenerating a CSR with the original keys by using supporting tools such as certutil
- Re-keying a certificate requires regeneration of a certificate request with the same information, so that a new key pair is generated. The CSR is then submitted through the original profile.
5.5.1. Same Keys Renewal
Copy linkLink copied to clipboard!
5.5.1.1. Reusing CSR
Copy linkLink copied to clipboard!
There are three approval methods for same key renewal at the end entity portal.
- Agent-approved method requires submitting the serial number of the certificate to be renewed; This method would require a CA agent’s approval.
- Directory-based renewal requires submitting the serial number of the certificate to be renewed, and the CA draws the information from its current certificate directory entry. The certificate is automatically approved if the ldap uid/pwd is authenticated successfully.
- Certificate-based renewal uses the certificate in the browser database to authenticate and have the same certificate re-issued.
5.5.1.1.1. Agent-Approved or Directory-Based Renewals
Copy linkLink copied to clipboard!
Sometimes, a certificate renewal request has to be manually approved, either by a CA agent or by providing login information for the user directory.
- Open the end-entities services page for the CA which issued the certificate (or its clone).
https://server.example.com:8443/ca/ee/ca
https://server.example.com:8443/ca/ee/caCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the name of the renewal form to use.
- Enter the serial number of the certificate to renew. This can be in decimal or hexadecimal form.
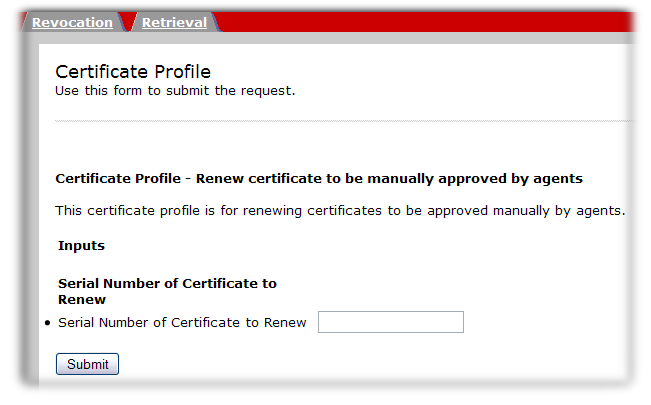
- Click the renew button.
- The request is submitted. For directory-based renewals, the renewed certificate is automatically returned. Otherwise, the renewal request will be approved by an agent.

5.5.1.1.2. Certificate-Based Renewal
Copy linkLink copied to clipboard!
Some user certificates are stored directly in your browser, so some renewal forms will simply check your browser certificate database for a certificate to renew. If a certificate can be renewed, then the CA automatically approved and reissued it.
Important
If the certificate which is being renewed has already expired, then it probably cannot be used for certificate-based renewal. The browser client may disallow any SSL client authentication with an expired certificate.
In that case, the certificate must be renewed using one of the other renewal methods.
- Open the end-entities services page for the CA which issued the certificate (or its clone).
https://server.example.com:8443/ca/ee/ca
https://server.example.com:8443/ca/ee/caCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the name of the renewal form to use.
- There is no input field, so click the button.
- When prompted, select the certificate to renew.

- The request is submitted and the renewed certificate is automatically returned.

5.5.1.2. Renewal by generating CSR with same keys
Copy linkLink copied to clipboard!
Sometimes, the original CSR might not be available. The
certutil tool allows one to regenerate a CSR with the same keys, provided that the key pair is in the NSS database. This can be achieved by doing the following:
- Find the corresponding key id in the NSS db:
Certutil -d <nssdb dir> -K
Certutil -d <nssdb dir> -KCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Generate a CSR using a specific key:
Certutil -d <nssdb dir> -R -k <key id> -s <subject DN> -o <CSR output file>
Certutil -d <nssdb dir> -R -k <key id> -s <subject DN> -o <CSR output file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, instead of keyid, if a key is associated with a certificate in the NSS db, nickname could be used:
- Generate a CSR using an existing nickname:
Certutil -d <nssdb dir> -R -k <nickname> -s <subject DN> -o <CSR output file>
Certutil -d <nssdb dir> -R -k <nickname> -s <subject DN> -o <CSR output file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.5.2. Renewal by Re-keying Certificates
Copy linkLink copied to clipboard!
Since renewal by re-keying is basically generating a new CSR with the same info as the old certificate, just follow any one of the methods described in Section 5.2, “Creating Certificate Signing Requests”. Be mindful to enter the same information as the old certificate.