Chapter 2. Using CDK
This section describes how to use the minishift command-line interface (CLI). It covers the basic commands as well as advanced features like profiles, image caching, add-ons and host folders.
For details about using the minishift and oc commands to manage your local OpenShift cluster, see Chapter 3, Interacting with OpenShift using Container Development Kit.
2.1. Basic Usage
2.1.1. Overview
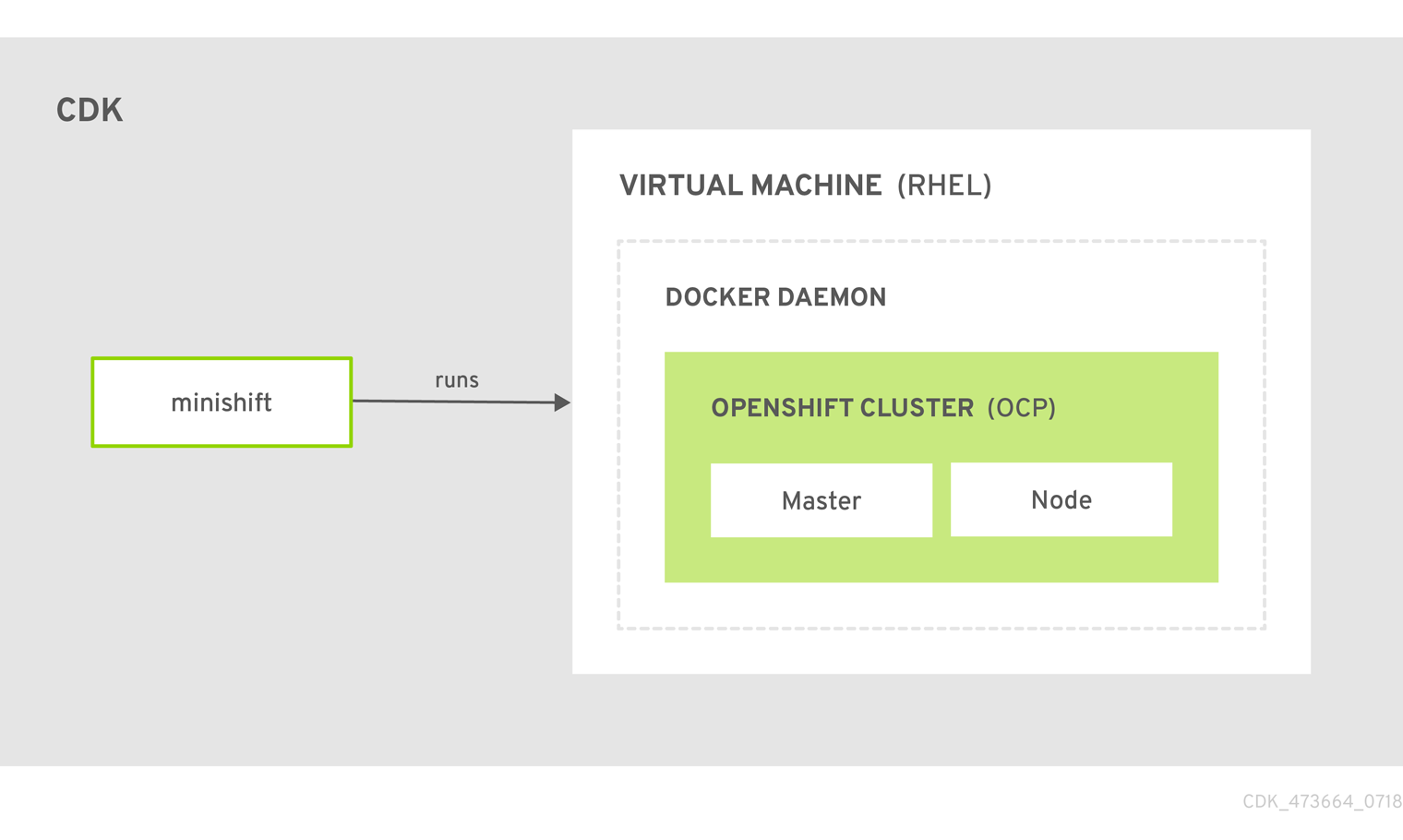
When you use CDK, you interact with the following components:
- the CDK virtual machine (VM)
- the Docker daemon running on the VM
- the OpenShift cluster running on the Docker daemon
The CDK architecture diagram outlines these components. The minishift binary, placed on the PATH for easy execution, is used to start, stop, and delete the CDK VM. The VM itself is bootstrapped off of a Red Hat Enterprise Linux Live ISO.
Some CDK commands, for example docker-env, interact with the Docker daemon, whilst others communicate with the OpenShift cluster, for example the openshift command.
Once the OpenShift cluster is up and running, you interact with it using the oc binary. CDK caches this binary under $MINISHIFT_HOME (per default ~/.minishift). minishift oc-env is an easy way to add the oc binary to your PATH.
For more details about using CDK to manage your local OpenShift cluster, see Chapter 3, Interacting with OpenShift using Container Development Kit.
Figure 2.1. : CDK architecture
2.1.2. CDK Life-cycle
2.1.2.1. The minishift setup-cdk Command
The minishift setup-cdk command copies a Red Hat Enterprise Linux ISO image to the CDK cache, creates a default configuration file, installs and enables default add-ons, and creates a marker file to confirm that the command has been run.
The command also copies the oc binary to your host so that you can interact with OpenShift through the oc command line tool or through the Web console, which can be accessed through the URL provided in the output of the minishift start command.
2.1.2.2. The minishift start Command
The minishift start command creates and configures the CDK VM and provisions a local, single-node OpenShift cluster within the CDK VM.
2.1.2.3. The minishift stop Command
The minishift stop command stops your OpenShift cluster and shuts down the CDK VM, but preserves the OpenShift cluster state.
Starting CDK again will restore the OpenShift cluster, allowing you to continue working from the last session. However, you must enter the same parameters that you used in the original start command.
See the Persistent Configuration section for more information on how to persist CDK settings.
2.1.2.4. The minishift delete Command
The minishift delete command deletes the OpenShift cluster, and also shuts down and deletes the CDK VM. No data or state are preserved.
2.1.3. Runtime Options
The runtime behavior of CDK can be controlled through flags, environment variables, and persistent configuration options.
The following precedence order is applied to control the behavior of CDK. Each action in the following list takes precedence over the action below it:
- Use command line flags as specified in the Flags section.
- Set environment variables as described in the Environment Variables section.
- Use persistent configuration options as described in the Persistent Configuration section.
- Accept the default value as defined by CDK.
2.1.3.1. Flags
You can use command line flags with CDK to specify options and direct its behavior. This has the highest precedence. Almost all commands have flags, although different commands might have different flags. Some of the commonly-used command line flags of the minishift start command are cpus, memory or vm-driver.
2.1.3.2. Environment Variables
CDK allows you to specify command line flags you commonly use through environment variables. To do so, apply the following rules to the flag you want to set as an environment variable.
-
Apply
MINISHIFT_as a prefix to the flag you want to set as an environment variable. For example, thevm-driverflag of theminishift startcommand becomesMINISHIFT_vm-driver. -
Use uppercase characters for the flag, so
MINISHIFT_vm-driverin the above example becomesMINISHIFT_VM-DRIVER. -
Replace
-with_, soMINISHIFT_VM-DRIVERbecomesMINISHIFT_VM_DRIVER.
Environment variables can be used to replace any option of any CDK command. A common example is the URL of the ISO to be used. Usually, you specify it with the iso-url flag of the minishift start command. Applying the above rules, you can also specify this URL by setting the environment variable as MINISHIFT_ISO_URL.
You can also use the MINISHIFT_HOME environment variable, to choose a different home directory for CDK. By default, the minishift command places all runtime state into ~/.minishift. This environment variable is currently experimental and semantics might change in future releases.
To use MINISHIFT_HOME, you should set the new home directory when you first set up CDK. For example, this sets the minishift home directory to ~/.mynewdir on a Linux system:
minishift setup-cdk --minishift-home ~/.mynewdir export MINISHIFT_HOME=~/.mynewdir echo 'export MINISHIFT_HOME=~/.mynewdir' >> ~/.bashrc
$ minishift setup-cdk --minishift-home ~/.mynewdir
$ export MINISHIFT_HOME=~/.mynewdir
$ echo 'export MINISHIFT_HOME=~/.mynewdir' >> ~/.bashrc2.1.3.3. Persistent Configuration
Using persistent configuration allows you to control CDK behavior without specifying actual command line flags, similar to the way you use environment variables. You can also define global configuration using the --global flag. Global configuration is applicable to all profiles.
CDK maintains a configuration file in $MINISHIFT_HOME/config/config.json. This file can be used to set commonly-used command line flags persistently for individual profiles. The global configuration file is maintained at MINISHIFT_HOME/config/global.json.
-
Persistent configuration can only be applied to the set of supported configuration options that are listed in the synopsis of the
minishift configsub-command. This is different from environment variables, which can be used to replace any option of any command. -
By default,
minishiftpersists start flags to persistent configuration. Useminishift config set save-start-flags falseto disable this behavior.
2.1.3.3.1. Setting Persistent Configuration Values
The easiest way to change a persistent configuration option is with the minishift config set sub-command. For example:
# Set default memory 4096 MB minishift config set memory 4096
# Set default memory 4096 MB
$ minishift config set memory 4096
The easiest way to set a persistent configuration option across all profiles is with the minishift config set --global sub-command.
For example, you can set the default memory to 8192 MB for every profile as follows:
minishift config set --global memory 8192
$ minishift config set --global memory 8192
Flags which can be used multiple times per command invocation, like docker-env or insecure-registry, need to be comma-separated when used with the config set command. For example, from the CLI, you can use insecure-registry like this:
minishift start --insecure-registry hub.foo.com --insecure-registry hub.bar.com
$ minishift start --insecure-registry hub.foo.com --insecure-registry hub.bar.comTo configure the same registries in the persistent configuration, run the following command:
minishift config set insecure-registry hub.foo.com,hub.bar.com
$ minishift config set insecure-registry hub.foo.com,hub.bar.com
To view all persistent configuration values, you can use the minishift config view sub-command:
minishift config view - memory: 4096
$ minishift config view
- memory: 4096
To view all persistent configuration values in the global configuration file, you can use the minishift config view --global sub-command:
minishift config view --global - memory: 8192
$ minishift config view --global
- memory: 8192
Alternatively, you can display a single value with the minishift config get sub-command:
minishift config get memory 4096
$ minishift config get memory
40962.1.3.3.2. Unsetting Persistent Configuration Values
To remove a persistent configuration option, you can use the minishift config unset sub-command. For example:
minishift config unset memory
$ minishift config unset memoryThe precedence for user-defined values is as follows:
- Command line flags.
- Environment variables.
- Instance-specific configuration.
- Global configuration.
2.1.4. Persistent Volumes
As part of the OpenShift cluster provisioning, 100 persistent volumes are created for your OpenShift cluster. This allows applications to make persistent volumes claims. The location of the persistent data is determined in the host-pv-dir flag of the minishift start command and defaults to /var/lib/minishift/openshift.local.pv on the CDK VM.
2.1.5. HTTP/HTTPS Proxies
If you are behind an HTTP/HTTPS proxy, you need to supply proxy options to allow Docker and OpenShift to work properly. To do this, pass the required flags during minishift start.
For example:
minishift start --http-proxy http://YOURPROXY:PORT --https-proxy https://YOURPROXY:PORT
$ minishift start --http-proxy http://YOURPROXY:PORT --https-proxy https://YOURPROXY:PORT
In an authenticated proxy environment, the proxy_user and proxy_password must be a part of proxy URI.
minishift start --http-proxy http://<proxy_username>:<proxy_password>@YOURPROXY:PORT \
--https-proxy https://<proxy_username>:<proxy_password>@YOURPROXY:PORT
$ minishift start --http-proxy http://<proxy_username>:<proxy_password>@YOURPROXY:PORT \
--https-proxy https://<proxy_username>:<proxy_password>@YOURPROXY:PORT
You can also use the --no-proxy flag to specify a comma-separated list of hosts that should not be proxied.
Using the proxy options will transparently configure the Docker daemon as well as OpenShift to use the specified proxies.
-
minishift starthonors the environment variablesHTTP_PROXY,HTTPS_PROXYandNO_PROXY. The environment variables can be specified in lower case or upper case. The lower case variables take higher precedence over upper case variables. If these variables are set, they are implicitly used duringminishift startunless explicitly overridden by the corresponding command line flags. - CDK does not escape the special characters in environment variables for proxies. Special characters must be manually escaped.
-
Use the
minishift start --openshift-versionflag to request a specific version of OpenShift Container Platform. You can list all CDK-compatible OpenShift Container Platform versions with theminishift openshift version listcommand.
2.1.6. Networking
The CDK VM is exposed to the host system with a host-only IP address that can be obtained with the minishift ip command.
2.1.7. Connecting to the CDK VM with SSH
You can use the minishift ssh command to interact with the CDK VM.
You can run minishift ssh without a sub-command to open an interactive shell and run commands on the CDK VM in the same way that you run commands interactively on any remote machine using SSH.
You can also run minishift ssh with a sub-command to send the sub-command directly to the CDK VM and return the result to your local shell. For example:
minishift ssh -- docker ps CONTAINER IMAGE COMMAND CREATED STATUS NAMES 71fe8ff16548 openshift3/ose:v3.11.374 "/usr/bin/openshift s" 4 minutes ago Up 4 minutes origin
$ minishift ssh -- docker ps
CONTAINER IMAGE COMMAND CREATED STATUS NAMES
71fe8ff16548 openshift3/ose:v3.11.374 "/usr/bin/openshift s" 4 minutes ago Up 4 minutes origin2.2. CDK Profiles
2.2.1. Overview
You must run minishift setup-cdk before using profiles.
A profile is an instance of the Minishift VM along with all of its configuration and state. The profile feature allows you to create and manage these isolated instances of Minishift.
Each CDK profile is created with its own configuration (memory, CPU, disk size, add-ons, and so on) and is independent of other profiles. Refer to the use of environment variables if you want to make sure that certain configuration settings, for example cpus or memory, get applied to all profiles.
The active profile is the profile against which all commands are executed, unless the global --profile flag is used. You can determine the active profile by using the minishift profile list command. You can execute single commands against a non-active profile by using the --profile flag, for example minishift --profile profile-demo console to open the OpenShift console for the specified profile-demo profile.
On top of the --profile flag, there are commands for listing, deleting and setting the active profile. These commands are described in the following sections.
Even though profiles are independent of each other, they share the same cache for ISOs, oc binaries and container images. minishift delete --clear-cache will affect all profiles for this reason. We recommend using --clear-cache with caution.
2.2.2. Creating Profiles
There are two ways to create a new profile.
Profile names can only consist of alphanumeric characters. Underscores ( _ ) and hyphens ( - ) are allowed as separators.
2.2.2.1. Using the --profile Flag
When you run the minishift start command with the --profile flag the profile is created if it does not already exist. For example:
See also Example Workflow for Profile Configuration.
A profile automatically becomes the active profile when a CDK instance is started successfully via minishift start.
2.2.2.2. Using the profile set Command
The other option to create a profile is to use the profile set command. If the specified profile does not exist, it is implicitly created:
minishift profile set demo Profile 'demo' set as active profile
$ minishift profile set demo
Profile 'demo' set as active profileThe default profile is minishift. It will be present by default and it does not need to be created.
2.2.3. Listing Profiles
You can list all existing profiles with the minishift profile list command. You can also see the active profile highlighted in the output.
minishift profile list - minishift Running (Active) - profile-demo Does Not Exist
$ minishift profile list
- minishift Running (Active)
- profile-demo Does Not Exist2.2.4. Switching Profiles
To switch between profiles use the minishift profile set command:
minishift profile set profile-demo Profile 'profile-demo' set as active profile
$ minishift profile set profile-demo
Profile 'profile-demo' set as active profileOnly one profile can be active at any time.
2.2.5. Deleting Profiles
To delete a profile, run:
minishift profile delete profile-demo You are deleting the active profile. It will remove the VM and all related artifacts. Do you want to continue [y/N]?: y Deleted: /Users/user/.minishift/profiles/profile-demo Profile 'profile-demo' deleted successfully Switching to default profile 'minishift' as the active profile.
$ minishift profile delete profile-demo
You are deleting the active profile. It will remove the VM and all related artifacts. Do you want to continue [y/N]?: y
Deleted: /Users/user/.minishift/profiles/profile-demo
Profile 'profile-demo' deleted successfully
Switching to default profile 'minishift' as the active profile.The default profile minishift cannot be deleted.
2.2.6. Example Workflow for Profile Configuration
You have two options to create a new profile and configure its persistent configuration. The first option is to implicitly create the new profile by making it the active profile using the profile set command. Once the profile is active you can run any minishift config command. Lastly, start the instance:
minishift profile set profile-demo minishift config set memory 8GB minishift config set cpus 4 minishift addon enable anyuid minishift start
$ minishift profile set profile-demo
$ minishift config set memory 8GB
$ minishift config set cpus 4
$ minishift addon enable anyuid
$ minishift start
The alternative is to execute a series of commands each specifying the targeted profile explicitly using the --profile flag:
minishift --profile profile-demo config set memory 8GB minishift --profile profile-demo config set cpus 4 minishift --profile profile-demo addon enable anyuid minishift --profile profile-demo start
$ minishift --profile profile-demo config set memory 8GB
$ minishift --profile profile-demo config set cpus 4
$ minishift --profile profile-demo addon enable anyuid
$ minishift --profile profile-demo start2.3. Image Caching
2.3.1. Overview
To speed up the provisioning of the OpenShift cluster and to minimize network traffic, container images can be cached on the host. These images can then be imported into the running Docker daemon, either explicitly on request or implicitly during minishift start. The following sections describe image caching and its configuration in more detail.
The format in which images are cached has changed with CDK version 3.3.0. Prior to 3.3.0, the images were stored as tar files. As of 3.3.0, images are stored in the OCI image format.
If you used image caching prior to CDK 3.3.0, your cache will need to be recreated. If you want to remove the obsolete pre-3.3.0 images, you can clear your cache via:
minishift delete --clear-cache
$ minishift delete --clear-cache2.3.2. Explicit Image Caching
CDK provides the image command together with its sub-commands to control the behavior of image caching. To export and import images from the Docker daemon of the CDK VM, use minishift image export and minishift image import.
2.3.2.1. Importing and Exporting Single Images
Once the CDK VM is running, images can be explicitly exported from the Docker daemon:
minishift image export <image-name-0> <image-name-1> ... Pulling image <image-name-0> .. OK Exporting <image-name-0>. OK Pulling image <image-name-1> .. OK Exporting <image-name-2>. OK
$ minishift image export <image-name-0> <image-name-1> ...
Pulling image <image-name-0> .. OK
Exporting <image-name-0>. OK
Pulling image <image-name-1> .. OK
Exporting <image-name-2>. OKImages which are not available in the Docker daemon will be pulled prior to being exported to the host.
To import previously cached images, use the minishift image import command:
minishift image import <image-name-0> <image-name-1> ... Importing <image-name-0> . OK
$ minishift image import <image-name-0> <image-name-1> ...
Importing <image-name-0> . OK2.3.2.2. Listing Cached Images
The minishift image list command lists either the currently cached images or the images available in the CDK Docker daemon.
To view currently cached images on the host:
minishift image list registry.access.redhat.com/openshift3/ose-docker-registry:v3.11.374 registry.access.redhat.com/openshift3/ose-haproxy-router:v3.11.374 registry.access.redhat.com/openshift3/ose:v3.11.374
$ minishift image list
registry.access.redhat.com/openshift3/ose-docker-registry:v3.11.374
registry.access.redhat.com/openshift3/ose-haproxy-router:v3.11.374
registry.access.redhat.com/openshift3/ose:v3.11.374To view images available in the Docker daemon:
2.3.2.3. Persisting Cached Image Names
In order to avoid having to type the image names explicitly as part of the image export or image import command, you can store a list of image names for import and export in the persistent configuration.
Use minishift image cache-config view to view the list of currently configured images and minishift image cache-config add to add images to the list:
minishift image cache-config view minishift image cache-config add alpine:latest busybox:latest minishift image cache-config view alpine:latest busybox:latest
$ minishift image cache-config view
$ minishift image cache-config add alpine:latest busybox:latest
$ minishift image cache-config view
alpine:latest
busybox:latest
To remove images from the list use minishift image cache-config remove:
minishift image cache-config remove alpine:latest minishift image cache-config view busybox:latest
$ minishift image cache-config remove alpine:latest
$ minishift image cache-config view
busybox:latest
Once the image names are stored in the persistent configuration, you can run minishift image export and minishift image import without any arguments.
2.3.2.4. Exporting and Importing All Images
You can export and import all images using the --all flag. For the export command, this means that all images currently available on the Docker daemon will be exported to the host. For the import command, it means that all images available in the local CDK cache will be imported into the Docker daemon of the CDK VM.
Exporting and importing all images can take a long time and locally cached images can take up a considerable amount of disk space. We recommend using this feature with caution.
2.3.3. Implicit Image Caching
Image caching is enabled by default for CDK. It occurs in a background process after the minishift start command is completed for the first time. Once the images are cached under $MINISHIFT_HOME/cache/image, successive CDK VM creations will use these cached images.
To disable this feature you need to disable the image-caching property in the persistent configuration using the minishift config set command:
minishift config set image-caching false
$ minishift config set image-caching false
Implicit image caching will transparently add the required OpenShift images to the list of cached images as specified per cache-images configuration option. See Persisting Cached Image Names.
Each time an image exporting background process runs, a log file is generated under $MINISHIFT_HOME/logs which can be used to verify the progress of the export.
You can re-enable the caching of the OpenShift images by setting image-caching to true or removing the setting altogether using minishift config unset:
minishift config unset image-caching
$ minishift config unset image-caching2.3.4. Delete Image from Local Cache
Images are cached under $MINISHIFT_HOME/cache/images and stored as an SHA256 blob along with an index which contains details about matching the SHA with an image name.
To delete an image from the local cache, use the minishift image delete command:
minishift image delete <image-name-0> <image-name-1> ... Deleting <image-name-0> from the local cache OK Deleting <image-name-1> from the local cache OK
$ minishift image delete <image-name-0> <image-name-1> ...
Deleting <image-name-0> from the local cache OK
Deleting <image-name-1> from the local cache OK2.4. Add-ons
2.4.1. Overview
CDK allows you to extend the vanilla OpenShift setup provided by cluster up with an add-on mechanism.
Add-ons are directories that contain a text file with the .addon extension. The directory can also contain other resource files such as JSON template files. However, only one .addon file is allowed per add-on.
The following example shows the contents of an add-on file, including the name and description of the add-on, additional metadata, and the actual add-on commands to apply.
Example: anyuid add-on definition file
- 1
- (Required) Name of the add-on.
- 2
- (Required) Description of the add-on.
- 3
- (Optional) Comma separated list of required interpolation variables. See Variable Interpolation.
- 4
- (Optional) OpenShift version required to run a specific add-on. See OpenShift Version Semantics.
- 5
- (Optional) CDK version required to run a specific add-on. See Minishift Version Semantics.
- 6
- Run an actual add-on command and store its output in a variable. See Internal Variables.
- 7
- Actual add-on command. In this case, the command executes the oc binary using the
mytokenvariable value. - 8
- Actual add-on command. In this case, the command executes the oc binary.
- Comment lines, starting with the '#' character, can be inserted anywhere in the file.
-
Commands starting with the
!character ignore execution failure. With the help of this, add-on will be idempotent i.e. a command can be executed multiple times without changing the final behavior of the add-on.
Enabled add-ons are applied during minishift start, immediately after the initial cluster provisioning is successfully completed.
2.4.2. OpenShift-Version Semantics
As part of the add-on metadata you can specify the OpenShift version which needs to be running in order to apply the add-on. To do so, you can specify the optional OpenShift-Version metadata field. The semantics are as follows:
| >3.6.0 | OpenShift version higher than 3.6.0 needs to be running in order to apply the add-on. |
| >=3.6.0 | OpenShift version 3.6.0 or higher needs to be running in order to apply the add-on. |
| 3.6.0 | OpenShift version 3.6.0 needs to be running in order to apply the add-on. |
| >=3.5.0, <3.8.0 | OpenShift version should higher or equal to 3.5.0 but lower than 3.8.0. |
| >=3.5.0, <=3.8.0 | OpenShift version should higher or equal to 3.5.0 but lower or equal to 3.8.0. |
- If the metadata field OpenShift-Version is not specified in the add-on header, the add-on can be applied against any version of OpenShift.
- OpenShift-Version only supports versions in the form of <major>.<minor>.<patch>.
2.4.3. Minishift-Version Semantics
As part of the add-on metadata you can specify the Minishift version which needs to be running in order to apply the add-on. To do so, you can specify the optional Minishift-Version metadata field. The semantics are as follows:
| >1.22.0 | Minishift version greater than 1.22.0 needs to be running in order to apply the add-on. |
| >=1.22.0 | Minishift version greater than or equal to 1.22.0 needs to be running in order to apply the add-on. |
| 1.22.0 | Minishift version 1.22.0 needs to be running in order to apply the add-on. |
| >=1.21.0, <1.25.0 | Minishift version must be greater than or equal to 1.21.0, but less than 1.25.0. |
| >=1.22.0, <=1.25.0 | Minishift version must be greater than or equal to 1.22.0, but less than or equal to 1.25.0. |
- If the metadata field Minishift-Version is not specified in the add-on header, the add-on can be applied against any version of CDK.
- Minishift-Version only supports versions in the form of <major>.<minor>.<patch>.
2.4.4. Defining Add-on Dependencies
Add-on dependencies can be defined using the Depends-On metadata field. Multiple dependencies may be defined using a comma-separated list of add-on names.
Example: Defining add-on dependency in add-on definition file
# Name: example # Description: Shows the use of the Depends-On metadata field # Depends-On: anyuid, admin-user echo Depends on the anyuid and admin-user add-ons, requiring them to be installed.
# Name: example
# Description: Shows the use of the Depends-On metadata field
# Depends-On: anyuid, admin-user
echo Depends on the anyuid and admin-user add-ons, requiring them to be installed.2.4.5. Add-on Commands
This section describes the commands that an add-on file can contain. They form a small domain-specific language for CDK add-ons:
- ssh
-
If the add-on command starts with
ssh, you can run any command within the CDK-managed VM. This is similar to runningminishift sshand then executing any command on the VM. For more information aboutminishift sshcommand usage, see Connecting to the CDK VM with SSH. - oc
If the add-on command starts with
oc, it uses theocbinary that is cached on your host to execute the specifiedoccommand. This is similar to runningoc --as system:admin …from the command line.NoteThe
occommand is executed as system:admin.- openshift
-
If the add-on command starts with
openshift, it uses theocbinary present in the OpenShift container to execute the command. This means that any file parameters or other system-specific parameters must match the environment of the container instead of your host. - docker
-
If the add-on command starts with
docker, it executes adockercommand against the Docker daemon within the CDK VM. This is the same daemon on which the single-node OpenShift cluster is running as well. This is similar to runningeval $(minishift docker-env)on your host and then executing anydockercommand. See alsominishift docker-env. - echo
-
If the add-on command starts with
echo, the arguments following theechocommand are printed to the console. This can be used to provide additional feedback during add-on execution. - sleep
-
If the add-on command starts with
sleep, it waits for the specified number of seconds. This can be useful in cases where you know that a command such asocmight take a few seconds before a certain resource can be queried. - cat
-
If the add-on command starts with
cat, the arguments following thecatcommand must be a valid file path. This will print the contents of a valid file to the console or display an error message if the file path is invalid. This can be useful to use file contents with another command.
Trying to use an undefined command will cause an error when the add-on gets parsed.
2.4.6. Variable Interpolation
CDK allows the use of variables within the add-on commands. Variables have the format #{<variable-name>}. The following example shows how the OpenShift routing suffix can be interpolated into an openshift command to create a new certificate as part of securing the OpenShift registry. The used variable #{routing-suffix} is part of the built-in add-on variables.
Example: Usage of the routing-suffix variable
2.4.6.1. Built-in Variables
There exist several built-in variables which are available for interpolation at all times. The following table shows these variables.
| Variable | Description |
|---|---|
| ip | IP of the CDK VM. |
| routing-suffix | OpenShift routing suffix for the application. |
| addon-name | Name of the current add-on. |
| user | User used by CDK for execution of commands through SSH. |
2.4.6.2. Dynamic Variables
The commands minishift start as well as minishift addons apply also provide an --addon-env flag which allows to dynamically pass variables for interpolation, for example:
minishift addons apply --addon-env PROJECT_USER=user acme
$ minishift addons apply --addon-env PROJECT_USER=user acme
The --addon-env flag can be specified multiple times to define more than one variables for interpolation.
Specifying dynamic variables also works in conjunction with setting persistent configuration values.
minishift config set addon-env PROJECT_USER=user minishift addons apply acme
$ minishift config set addon-env PROJECT_USER=user
$ minishift addons apply acme
Multiple variables must be comma separated when the minishift config set command is used.
There is also the possibility to dynamically interpolate a variable with the value of an environment variable at the time the add-on gets applied. For this the variable value needs to be prefixed with env.
minishift config set addon-env PROJECT_USER=env.USER minishift addons apply acme
$ minishift config set addon-env PROJECT_USER=env.USER
$ minishift addons apply acme - 1
- Using the env prefix ensures that instead of literally replacing '#{PROJECT_USER}' with 'env.USER', the value of the environment variable
USERis used. If the environment variable is not set, interpolation does not occur. - 2
- When the add-on is applied, each occurrence of
#{PROJECT_USER}within an add-on command gets replaced with the value of the environment variableUSER.
As an add-on developer, you can enforce that a variable value is provided when the add-on gets applied by adding the variable name to the Required-Vars metadata header. Multiple variables need to be comma separated.
# Name: acme # Description: ACME add-on # Required-Vars: PROJECT_USER
# Name: acme
# Description: ACME add-on
# Required-Vars: PROJECT_USER
You can also provide default values for variables using the Var-Defaults metadata header. Var-Defaults needs to be specified in the format of <key>=<value>. Multiple default key/value pairs need to be comma separated.
# Name: acme # Description: ACME add-on # Required-Vars: PROJECT_USER # Var-Defaults: PROJECT_USER=user
# Name: acme
# Description: ACME add-on
# Required-Vars: PROJECT_USER
# Var-Defaults: PROJECT_USER=user-
=and,are metacharacters and cannot be used as part of keys or values. An empty value will be set if "NULL", "Null", or "null" is specified as the value for a Var-Defaults key. For example:
Var-Defaults: PROJECT_USER=null
# Var-Defaults: PROJECT_USER=nullCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Variable values specified via the command line using the
--addon-envor set viaminishift config set addon-envhave precedence over Var-Defaults.
2.4.6.3. Internal Variables
Add-ons allow the definition of variables. These variables can be used to store the output of an add-on command.
For example, you can save oc command output in a mytoken variable and use it in subsequent add-on commands like so:
mytoken := oc sa get-token oauth-client
oc new-app -p OPENSHIFT_OAUTH_CLIENT_SECRET=#{mytoken}
mytoken := oc sa get-token oauth-client
oc new-app -p OPENSHIFT_OAUTH_CLIENT_SECRET=#{mytoken}2.4.7. Default Add-ons
CDK provides a set of built-in add-ons that offer some common OpenShift customization to assist with development. During minishift setup-cdk, Minishift automatically installs and enables the xpaas, anyuid, and admin-user add-ons. To install the default add-ons, run:
minishift addons install --defaults
$ minishift addons install --defaultsThis command extracts the default add-ons to the add-on installation directory $MINISHIFT_HOME/addons. To view the list of installed add-ons, you can then run:
minishift addons list --verbose=true
$ minishift addons list --verbose=trueThis command prints a list of installed add-ons. You should at least see the anyuid add-on listed. This is an important add-on that allows you to run images that do not use a pre-allocated UID. By default, this is not allowed in OpenShift.
| Add-on Name | Description |
|---|---|
| anyuid | Changes the default security context constraints to allow pods to run with arbitrary UID. |
| admin-user | Creates a user named 'admin' and assigns the cluster-admin role to it. |
| che | Runs an instance of the Eclipse Che integrated development environment. |
| eap-cd | Imports JBoss EAP CD templates. |
| htpasswd-identity-provider | User can change and add default login username and password for the OpenShift instance. |
| registry-route | Creates an edge terminated route for the OpenShift registry. |
| xpaas | Imports xPaaS templates. |
The eap-cd add-on provides templates for JBoss EAP CD 19. To use a more recent version of JBoss EAP CD, use the upstream eap-cd add-on. See Add-ons by the Community for more information on how to install the upstream add-on.
2.4.7.1. Add-ons by the Community
Apart from the several default add-ons, there are a number of community developed add-ons for CDK. Community add-ons can be found in the minishift-addons repository. You can get all the information about these add-ons in the repository. The instructions for installing them can be found in the README.
2.4.8. Installing Add-ons
Add-ons are installed with the minishift addons install command.
The following example shows how to install an add-on.
Example: Installing an add-on
minishift addons install <path_to_addon_directory>
$ minishift addons install <path_to_addon_directory>2.4.9. Enabling and Disabling Add-ons
Add-ons are enabled with the minishift addons enable command and disabled with the minishift addons disable command. Enabled add-ons automatically get executed during minishift start.
The following examples show how to enable and disable the anyuid add-on.
Example: Enabling the anyuid add-on
minishift addons enable anyuid
$ minishift addons enable anyuidExample: Disabling the anyuid add-on
minishift addons disable anyuid
$ minishift addons disable anyuid2.4.9.1. Add-on Priorities
When you enable an add-on, you can also specify a priority, which determines the order that the add-ons are applied.
The following example shows how to enable the registry add-on with a higher priority value.
Example: Enabling the registry add-on with priority
minishift addons enable registry --priority=5
$ minishift addons enable registry --priority=5The add-on priority attribute determines the order in which add-ons are applied. By default, an add-on has the priority 0. Add-ons with a lower priority value are applied first.
In the following example, the anyuid, registry, and eap add-ons are enabled with the respective priorities of 0, 5 and 10. This means that anyuid is applied first, followed by registry, and lastly the eap add-on.
Example: List command output with explicit priorities
minishift addons list - anyuid : enabled P(0) - registry : enabled P(5) - eap : enabled P(10)
$ minishift addons list
- anyuid : enabled P(0)
- registry : enabled P(5)
- eap : enabled P(10)If two add-ons have the same priority the order in which they are getting applied is not determined.
2.4.10. Applying Add-ons
Add-ons can be explicitly executed with the minishift addons apply command. You can use the apply command for both enabled and disabled add-ons. To apply multiple add-ons with a single command, specify add-on names separated by space.
The following example shows how to explicitly apply the anyuid and the admin-user add-ons.
Example: Applying anyuid and admin-user add-ons
minishift addons apply anyuid admin-user
$ minishift addons apply anyuid admin-user2.4.11. Removing Add-ons
Add-ons can be removed with the minishift addons remove command. It is the mirror command to minishift addons apply and similarly can be used regardless of whether the add-on is enabled or not. Provided the specified add-on is installed and has a <addon_name>.addon.remove file, minishift addons remove will execute the commands specified in this file.
To remove multiple add-ons with a single command, specify the add-on names separated by a space. The following example shows how to explicitly remove the admin-user add-on.
Example: Removing admin-user add-on
minishift addons remove admin-user -- Removing addon 'admin-user':. admin user deleted
$ minishift addons remove admin-user
-- Removing addon 'admin-user':.
admin user deleted2.4.12. Uninstalling Add-ons
Add-ons can be uninstalled with the minishift addons uninstall command. It is the mirror command to minishift addons install and can be used regardless of whether the add-on is enabled or not. Provided the specified add-on is installed, minishift addons uninstall will delete the corresponding add-on directory from $MINISHIFT_HOME/addons.
The following example shows how to explicitly uninstall the admin-user add-on:
Example: Uninstalling admin-user add-on
minishift addons uninstall admin-user Add-on 'admin-user' uninstalled
$ minishift addons uninstall admin-user
Add-on 'admin-user' uninstalled2.4.13. Writing Custom Add-ons
To write a custom add-on, you should create a directory and in it create at least one text file with the extension .addon, for example admin-role.addon.
This file needs to contain the Name and Description metadata fields, as well as the commands that you want to execute as a part of the add-on.
The following example shows the definition of an add-on that gives the developer user cluster-admin privileges.
Example: Add-on definition for admin-role
# Name: admin-role # Description: Gives the developer user cluster-admin privileges oc adm policy add-role-to-user cluster-admin developer
# Name: admin-role
# Description: Gives the developer user cluster-admin privileges
oc adm policy add-role-to-user cluster-admin developerAfter you define the add-on, you can install it by running:
minishift addons install <ADDON_DIR_PATH>
$ minishift addons install <ADDON_DIR_PATH>You can also write metadata with multiple lines.
Example: Add-on definition which contain multiline description
You can also edit your add-on directly in the CDK add-on install directory $MINISHIFT_HOME/addons. Be aware that if there is an error in the add-on, it will not show when you run any addons commands, and it will not be applied during the minishift start process.
To provide add-on removal instructions, you can create text file with the extension .addon.remove, for example admin-user.addon.remove. Similar to the .addon file, it needs the Name and Description metadata fields. If a .addon.remove file exists, it can be applied via the remove command.
2.5. Host Folders
2.5.1. Overview
Host folders are directories on the host which are shared between the host and the CDK VM. This allows for two way file synchronization between the host and the VM. The following sections discuss usage of the minishift hostfolder command.
2.5.2. The minishift hostfolder Command
CDK provides the minishift hostfolder command to list, add, mount, unmount and remove host folders. You can use the hostfolder command to mount multiple shared folders onto custom specified mount points.
2.5.2.1. Prerequisites
2.5.2.1.1. SSHFS
SSHFS is the default technology for sharing host folders. It works without prerequisites.
2.5.2.1.2. CIFS
Host folders can be shared using CIFS. It is possible to use CIFS on Windows, macOS, and Linux.
On macOS, you can enable CIFS-based shares under System Preferences > Sharing. See How to connect with File Sharing on your Mac for detailed setup instructions.
On Linux, follow your distribution-specific instructions to install Samba. Refer to Samba File and Print Server in RHEL to learn how to configure the Samba implementation of CIFS in Red Hat Enterprise Linux.
2.5.2.2. Displaying Host Folders
The minishift hostfolder list command gives you an overview of the defined host folders, their names, mount points, remote paths and whether they are currently mounted.
An example output could look like:
minishift hostfolder list Name Type Source Mountpoint Mounted test sshfs /Users/user/test /mnt/sda1/test N
$ minishift hostfolder list
Name Type Source Mountpoint Mounted
test sshfs /Users/user/test /mnt/sda1/test NIn this example, there is an SSHFS based host folder with the name test which mounts /Users/user/test onto /mnt/sda1/test in the CDK VM. The share is currently not mounted.
2.5.2.3. Adding Host Folders
The minishift hostfolder add command allows you to define a new host folder.
The exact syntax to use depends on the host folder type. Independent of the type you can choose between non-interactive and interactive configuration. The default is non-interactive. By specifying the --interactive flag you can select the interactive configuration mode.
The following sections give examples for configuring CIFS and SSHFS host folders.
2.5.2.3.1. CIFS
Adding a CIFS based hostfolder
minishift hostfolder add -t cifs --source //192.168.99.1/MYSHARE --target /mnt/sda1/myshare --options username=user,password=mysecret,domain=MYDOMAIN myshare
$ minishift hostfolder add -t cifs --source //192.168.99.1/MYSHARE --target /mnt/sda1/myshare --options username=user,password=mysecret,domain=MYDOMAIN myshare
The above command will create a new host folder with the name of myshare. The source of the host folder is the UNC path //192.168.99.1/MYSHARE which is required. The target or mount point is /mnt/sda1/myshare within the CDK VM. Using the --options flag host folder type specific options can be specified using a list of comma separated key/value pairs. In the case of a CIFS host folder the required options are the user name for the CIFS share as well as the password. Via the --options flag the domain of the share can be specified as well. Often this can be left out, but for example on Windows, when your account is linked to a Microsoft account, you must use the Microsoft account email address as user name as well as your machine name as displayed by $env:COMPUTERNAME as a domain.
On Windows hosts, the minishift hostfolder add command also provides a users-share option. When this option is specified, no UNC path needs to be specified and C:\Users is assumed.
2.5.2.3.2. SSHFS
Adding an SSHFS based hostfolder
minishift hostfolder add -t sshfs --source /Users/user/myshare --target /mnt/sda1/myshare myshare
$ minishift hostfolder add -t sshfs --source /Users/user/myshare --target /mnt/sda1/myshare myshareFor the case of an SSHFS based host folder only the source and target of the host folder need to be specified.
When adding host folders, one can give type-specific options to be used while mounting by using the --options flag. For example:
minishift hostfolder add -t sshfs --source ~/myshare/ --target /mnt/sda1/myshare --options "-o compression=no" myshare
$ minishift hostfolder add -t sshfs --source ~/myshare/ --target /mnt/sda1/myshare --options "-o compression=no" myshare2.5.2.3.3. Instance-Specific Host Folders
By default, host folder definitions are persistent, similar to other persistent configuration options. This means that these host folder definitions will survive the deletion and subsequent re-creation of a CDK VM.
In some cases you might want to define a host folder just for a specific CDK instance. To do so, you can use the --instance-only flag of the minishift hostfolder add command. Host folder definitions that are created with the --instance-only flag will be removed together with any other instance-specific state during minishift delete.
2.5.2.4. Mounting Host Folders
After you have added host folders, you use the minishift hostfolder mount command to mount a host folder by its name:
minishift hostfolder mount myshare
$ minishift hostfolder mount myshareYou can verify that the host folder is mounted by running:
minishift hostfolder list Name Mountpoint Remote path Mounted myshare /mnt/sda1/myshare //192.168.99.1/MYSHARE Y
$ minishift hostfolder list
Name Mountpoint Remote path Mounted
myshare /mnt/sda1/myshare //192.168.99.1/MYSHARE YAlternatively, you can list the actual content of the mounted host folder:
minishift ssh "ls -al /mnt/sda1/myshare"
$ minishift ssh "ls -al /mnt/sda1/myshare"
When mounting SSHFS based host folders an SFTP server process is started on port 2022 of the host. Make sure that your network and firewall settings allow this port to be opened. If you need to configure this port you can make use of CDK’s persistent configuration using the key hostfolders-sftp-port, for example:
minishift config set hostfolders-sftp-port 2222
$ minishift config set hostfolders-sftp-port 22222.5.2.4.1. Auto-Mounting Host Folders
Host folders can also be mounted automatically each time you run minishift start. To set auto-mounting, you need to set the hostfolders-automount option in the CDK configuration file.
minishift config set hostfolders-automount true
$ minishift config set hostfolders-automount true
After the hostfolders-automount option is set, CDK will attempt to mount all defined host folders during minishift start.
2.5.2.5. Unmounting Host Folders
You use the minishift hostfolder umount command to unmount a host folder.
minishift hostfolder umount myshare minishift hostfolder list Name Mountpoint Remote path Mounted myshare /mnt/sda1/myshare //192.168.99.1/MYSHARE N
$ minishift hostfolder umount myshare
$ minishift hostfolder list
Name Mountpoint Remote path Mounted
myshare /mnt/sda1/myshare //192.168.99.1/MYSHARE N2.5.2.6. Deleting Host Folders
You use the minishift hostfolder remove command to remove a host folder definition.
2.6. Assign Static IP Address
2.6.1. Overview
Most hypervisors do not support extending the lease time when the IP is assigned using DHCP. This might lead to a new IP being assigned to the VM after a restart as it will conflict with the security certificates generated for the old IP. This will make CDK completely unusable until a new instance is set up by running minishift delete followed by minishift start.
To prevent this, CDK includes the functionality to set a static IP address to the VM. This will prevent the IP address from changing between restarts. However, it will not work on all of the driver plug-ins at the moment due to the way the IP address is resolved.
- Assigning a static IP address to the CDK VM is only officially supported for Hyper-V.
- The CDK VM cannot be assigned a static IP address when using the KVM driver plug-in.
2.6.2. Assign IP Address to Hyper-V
Since the Internal Virtual Switch for Hyper-V does not provide a DHCP offer option, an IP address needs to be provided in a different way. Functionality is provided to assign an IP address on startup using the Data Exchange Service for Hyper-V.
To make this work, you need to create a Virtual Switch using NAT.
WinNAT is limited to one NAT network per host. For more details about capabilities and limitations, please see the WinNAT capabilities and limitations blog.
The following command will attempt to assign an IP address for use on the Internal Virtual Switch 'MyInternal':
PS> minishift.exe config set hyperv-virtual-switch "MyInternal" PS> minishift.exe start ` --network-ipaddress 192.168.1.10 ` --network-gateway 192.168.1.1 ` --network-nameserver 8.8.8.8
PS> minishift.exe config set hyperv-virtual-switch "MyInternal"
PS> minishift.exe start `
--network-ipaddress 192.168.1.10 `
--network-gateway 192.168.1.1 `
--network-nameserver 8.8.8.8If you want to use the 'DockerNAT' network, the following commands are needed to setup the correct NAT networking and assign an IP in the range expected:
Be sure to specify a valid gateway and nameserver. Failing to do so will result in connectivity issues.
2.6.3. Set Fixed IP Address
This feature is not supported on KVM as the driver plug-in relies on the DHCP offer to determine the IP address.
The following command will set the IP address that was assigned as fixed:
minishift ip --set-static
$ minishift ip --set-staticIf you prefer to use dynamic assignment, you can use:
minishift ip --set-dhcp
$ minishift ip --set-dhcp
Use minishift config set static-ip false to stop automatically assigning a static IP address for supported hypervisors.
2.7. CDK Docker daemon
2.7.1. Overview
When running OpenShift in a single VM, you can reuse the Docker daemon managed by CDK for other Docker use-cases as well. By using the same Docker daemon as CDK, you can speed up your local development.
2.7.2. Console Configuration
In order to configure your console to reuse the CDK Docker daemon, follow these steps:
- Make sure that you have the Docker client binary installed on your machine. For information about specific binary installations for your operating system, see the Docker installation site.
-
Start CDK with the
minishift startcommand. Run the
minishift docker-envcommand to display the command you need to type into your shell in order to configure your Docker client. The command output will differ depending on OS and shell type.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Test the connection by running the following command:
docker ps
$ docker psCopy to Clipboard Copied! Toggle word wrap Toggle overflow If successful, the shell will print a list of running containers.
2.8. Experimental Features
2.8.1. Overview
If you want to get early access to some upcoming features and experiment, you can set the environment variable MINISHIFT_ENABLE_EXPERIMENTAL, which makes additional feature flags available:
export MINISHIFT_ENABLE_EXPERIMENTAL=y
$ export MINISHIFT_ENABLE_EXPERIMENTAL=yExperimental features are not officially supported, and might break or result in unexpected behavior. To share your feedback on these features, you are welcome to contact the Minishift community.
2.8.2. Enabling Experimental oc cluster up Flags
By default, CDK does not expose all oc cluster up flags in the CDK CLI.
You can set the MINISHIFT_ENABLE_EXPERIMENTAL environment variable to enable the following options for the minishift start command:
extra-clusterup-flags-
Enables passing flags directly to
oc cluster upthat are not directly exposed in the CDK CLI.
For example, the following command will provision the OpenShift service catalog:
MINISHIFT_ENABLE_EXPERIMENTAL=y minishift start --extra-clusterup-flags "--enable='*,service-catalog'"
$ MINISHIFT_ENABLE_EXPERIMENTAL=y minishift start --extra-clusterup-flags "--enable='*,service-catalog'"
The recommended way to enable service catalog is by using the minishift openshift component add command.
2.8.3. Local Proxy Server
To help in the situation when security certificates are used in an organization, but cannot be easily shared with the instance, CDK can run a local proxy server on the host, which the CDK instance can use to access external resources.
Enabling the proxy server is done using the following command:
minishift config set local-proxy true
$ minishift config set local-proxy trueThis will start a proxy server on the host which will be automatically assigned to the CDK instance.
When the corporate or upstream proxy is known, you can specify this with the following configuration option:
minishift config set local-proxy-upstream http(s)://[username:password@]host:port
$ minishift config set local-proxy-upstream http(s)://[username:password@]host:portWhen this option is used, all traffic will be re-encrypted with a CDK-specific certificate. For this reason, this proxy should only be used for development and use with CDK.
To allow external traffic to your local host you might have to enable port 3128/tcp in your host firewall.
2.8.4. Local DNS Server
CDK provides a DNS server for offline usage or the possibility of overriding DNS records while testing. This will allow you to access the OpenShift routes without Internet.
The DNS server is specific to a profile.
Starting the DNS server can be done as follows:
minishift dns start
$ minishift dns startAfter starting the DNS server you need to configure your device settings to use this nameserver. The start command will show you a temporary option that can be used when you entered offline usage.
In the current implementation you need to start the server and do required changes in the host settings manually. The DNS configuration is not permanent and might reset when the network state of the device changes.
Stopping the DNS server can be done as follows:
minishift dns stop
$ minishift dns stopTo get the status of the DNS server:
minishift dns status
$ minishift dns status2.8.4.1. Local DNS Setup for macOS
Recent versions of macOS do not send out DNS queries in offline mode, and the process for using a local DNS server from CDK is more involved than other operating systems.
2.8.4.1.1. Enable tap devices
Check for the presence of tap devices in /dev:
ls /dev | grep tap
$ ls /dev | grep tap
If no tap devices are present, install the tuntap package:
brew install tuntap
$ brew install tuntap2.8.4.1.2. Use a tap device to create a network service
As root, open the /Library/Preferences/SystemConfiguration/preferences.plist file and add the following XML under the <key>NetworkServices</key> element:
2.8.4.1.3. Adding the Network Service to ServiceOrder array
In the /Library/Preferences/SystemConfiguration/preferences.plist file, look for the <key>ServiceOrder</key> element. As root, append the UUID for our MiniTap network service to this array.
- 1
- The UUID for MiniTap network service.
2.8.4.1.4. Adding the Network Service to Service dictionary
In the /Library/Preferences/SystemConfiguration/preferences.plist file, look for the <key>Service</key> element. As root, append the following XML to its dictionary:
Reboot macOS and you should see a MiniTap service in the Network Preferences GUI. This service will be disconnected. To turn it on, issue the following commands:
exec 4<>/dev/tap0 ifconfig tap0 10.10.90.1 255.255.0.0 ifconfig tap0 up
$ exec 4<>/dev/tap0
$ ifconfig tap0 10.10.90.1 255.255.0.0
$ ifconfig tap0 up 2.8.4.1.5. Adding resolver config
Create the file /etc/resolver/nip.io with the following content:
nameserver <ip_address_of_the_minishfit_vm> search_order 1
nameserver <ip_address_of_the_minishfit_vm>
search_order 12.8.5. CDK System Tray
To help the users of CDK on macOS and Windows perform simple tasks like starting and stopping a profile from the GUI, the binaries for these platforms have been compiled to include an experimental system tray.
By default, the system tray is automatically started on running minishift start. To disable this behavior, use the following command:
minishift config set auto-start-tray false
$ minishift config set auto-start-tray falseTo start the system tray:
minishift service start systemtray
$ minishift service start systemtray2.8.6. Timezone Setup
If you want to set a different timezone from the default, use the following command:
minishift timezone --set <Valid_Timezone>
$ minishift timezone --set <Valid_Timezone>To see the available timezones, use the following command:
minishift timezone --list
$ minishift timezone --listTo check the current timezone of the CDK instance, use the following command:
minishift timezone
$ minishift timezone2.9. Run Against an Existing Machine
2.9.1. Overview
CDK can be run against an existing remote machine using vm-driver as generic.
CentOS 7, Red Hat Enterprise Linux 7, and Fedora > 26 are the suggested Linux distributions for this feature.
2.9.2. Configuring an Existing Remote Machine
To use an existing machine with CDK, it needs to be configured as follows:
Establish password-less SSH from the host to the existing remote machine:
Host$ ssh-copy-id <user>@<remote_IP_address> # Ensure that the user has sudo access without a password or use root Host$ ssh <user>@<remote_IP_address> # Ensure that this login works without a password
Host$ ssh-copy-id <user>@<remote_IP_address> # Ensure that the user has sudo access without a password or use root Host$ ssh <user>@<remote_IP_address> # Ensure that this login works without a passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Skip the following steps if you are using CentOS 7, Red Hat Enterprise Linux 7 or Fedora (version > 26).
Configure the existing remote machine:
Remote_Machine$ yum install -y docker net-tools firewalld Remote_Machine$ systemctl start docker Remote_Machine$ systemctl enable docker Remote_Machine$ systemctl start firewalld Remote_Machine$ systemctl enable firewalld
Remote_Machine$ yum install -y docker net-tools firewalld Remote_Machine$ systemctl start docker Remote_Machine$ systemctl enable docker Remote_Machine$ systemctl start firewalld Remote_Machine$ systemctl enable firewalldCopy to Clipboard Copied! Toggle word wrap Toggle overflow Allow the
2376,8443, and80TCP ports through the firewall on the remote machine to have communication from the host:Remote_Machine$ firewall-cmd --permanent --add-port 2376/tcp --add-port 8443/tcp --add-port 80/tcp
Remote_Machine$ firewall-cmd --permanent --add-port 2376/tcp --add-port 8443/tcp --add-port 80/tcpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Determine the Docker bridge network container subnet:
Remote_Machine$ docker network inspect -f "{{range .IPAM.Config }}{{ .Subnet }}{{end}}" bridgeRemote_Machine$ docker network inspect -f "{{range .IPAM.Config }}{{ .Subnet }}{{end}}" bridgeCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command displays a subnet, such as
172.17.0.0/16.Using the Docker bridge network container subnet, create a minishift zone for the firewall with the subnet as its source:
Remote_Machine$ firewall-cmd --permanent --new-zone minishift Remote_Machine$ firewall-cmd --permanent --zone minishift --add-source <subnet>
Remote_Machine$ firewall-cmd --permanent --new-zone minishift Remote_Machine$ firewall-cmd --permanent --zone minishift --add-source <subnet>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Allow the
53and8053UDP ports through the firewall on the remote machine to allow containers to access the OpenShift master API and DNS endpoints:Remote_Machine$ firewall-cmd --permanent --zone minishift --add-port 53/udp --add-port 8053/udp
Remote_Machine$ firewall-cmd --permanent --zone minishift --add-port 53/udp --add-port 8053/udpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the firewall on the remote machine:
Remote_Machine$ firewall-cmd --reload
Remote_Machine$ firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.9.3. Running Against an Existing Remote Machine
Use the following command on the host to run CDK against a remote machine:
minishift start --vm-driver generic --remote-ipaddress <remote_IP_address> --remote-ssh-user <username> --remote-ssh-key <private_ssh_key> minishift addon apply htpasswd-identity-provider --addon-env USER_PASSWORD=<NEW_PASSWORD>
$ minishift start --vm-driver generic --remote-ipaddress <remote_IP_address> --remote-ssh-user <username> --remote-ssh-key <private_ssh_key>
$ minishift addon apply htpasswd-identity-provider --addon-env USER_PASSWORD=<NEW_PASSWORD>
The value of the --remote-ssh-key flag must be the location of a private SSH key on the host machine.
To change the default username and password, you must apply the htpasswd-identity-provider add-on with the desired username and password after running the minishift start command. By default, CDK uses the Allow All identity provider. The Allow All identity provider allows any non-empty username and password to log in.
2.10. Converting an Existing Docker Compose Project
2.10.1. Installing Kompose
Kompose is a tool for converting Docker Compose to container orchestrators such as OpenShift and Kubernetes. Kompose may be installed manually or via a package manager (Chocolatey on Microsoft Windows, Homebrew on macOS, or Yum on Red Hat Enterprise Linux).
2.10.1.1. Manually
- Download the binary for your operating system from the Kompose GitHub Releases page.
-
Add the binary to a location in your
PATH.
2.10.1.2. With Chocolatey
On Microsoft Windows, you can install Kompose via Chocolatey:
PS> choco.exe install kubernetes-kompose
PS> choco.exe install kubernetes-kompose2.10.1.3. With Homebrew
On macOS, you can install Kompose via Homebrew:
brew install kompose
$ brew install kompose2.10.1.4. On Red Hat Enterprise Linux
Kompose can be installed from the command line by enabling the Red Hat Developer Tools and Red Hat Software Collections repositories:
subscription-manager repos --enable rhel-7-server-devtools-rpms subscription-manager repos --enable rhel-server-rhscl-7-rpms yum install kompose -y
$ subscription-manager repos --enable rhel-7-server-devtools-rpms
$ subscription-manager repos --enable rhel-server-rhscl-7-rpms
$ yum install kompose -y2.10.2. Using Kompose
To convert your Docker Compose project using Kompose, follow these steps:
Start CDK so you have an OpenShift cluster to communicate with.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Download an example Docker Compose file, or use your own.
wget https://raw.githubusercontent.com/kubernetes/kompose/master/examples/docker-compose.yaml
wget https://raw.githubusercontent.com/kubernetes/kompose/master/examples/docker-compose.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Convert your Docker Compose file to OpenShift. Run
kompose convert --provider=openshiftin the same directory as your docker-compose.yaml file.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can convert and deploy directly to OpenShift with
kompose up --provider=openshift.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Access the newly deployed application with CDK.
After deployment, you must create an OpenShift route in order to access the service.
Create a route for the
frontendservice usingoc.oc expose service/frontend route "frontend" exposed
$ oc expose service/frontend route "frontend" exposedCopy to Clipboard Copied! Toggle word wrap Toggle overflow Access the
frontendservice withminishift.minishift openshift service frontend --namespace=myproject --in-browser Opening the service myproject/frontend in the default browser...
$ minishift openshift service frontend --namespace=myproject --in-browser Opening the service myproject/frontend in the default browser...Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also access the GUI of OpenShift for an overview of the deployed containers.
minishift console Opening the OpenShift Web console in the default browser...
$ minishift console Opening the OpenShift Web console in the default browser...Copy to Clipboard Copied! Toggle word wrap Toggle overflow