Chapter 3. Core Server Configuration Reference
The chapter provides an alphabetical reference for all core (server-related) attributes. Section 2.2.1.1, “Overview of the Directory Server Configuration” contains a good overview of the Red Hat Directory Server configuration files.
3.1. Core Server Configuration Attributes Reference
This section contains reference information on the configuration attributes that are relevant to the core server functionality. For information on changing server configuration, see Section 2.2.1.2, “Accessing and Modifying Server Configuration”. For a list of server features that are implemented as plug-ins, see Section 4.1, “Server Plug-in Functionality Reference”. For help with implementing custom server functionality, contact Directory Server support.
The configuration information stored in the dse.ldif file is organized as an information tree under the general configuration entry cn=config, as shown in the following diagram.
Figure 3.1. Directory Information Tree Showing Configuration Data
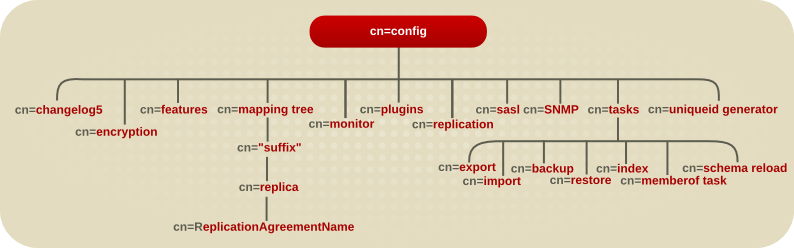
Most of these configuration tree nodes are covered in the following sections.
The cn=plugins node is covered in Chapter 4, Plug-in Implemented Server Functionality Reference. The description of each attribute contains details such as the DN of its directory entry, its default value, the valid range of values, and an example of its use.
Some of the entries and attributes described in this chapter may change in future releases of the product.
3.1.1. cn=config
General configuration entries are stored in the cn=config entry. The cn=config entry is an instance of the nsslapdConfig object class, which in turn inherits from extensibleObject object class.
3.1.1.1. nsslapd-accesslog (Access Log)
This attribute specifies the path and filename of the log used to record each LDAP access. The following information is recorded by default in the log file:
- IP address (IPv4 or IPv6) of the client machine that accessed the database.
- Operations performed (for example, search, add, and modify).
- Result of the access (for example, the number of entries returned or an error code).
For more information on turning access logging off, see the "Monitoring Server and Database Activity" chapter in the Red Hat Directory Server Administration Guide.
For access logging to be enabled, this attribute must have a valid path and parameter, and the nsslapd-accesslog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of access logging.
| Attribute | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on filename | Enabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off filename | Disabled |
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename. |
| Default Value | /var/log/dirsrv/slapd-instance/access |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog: /var/log/dirsrv/slapd-instance/access |
3.1.1.2. nsslapd-accesslog-level (Access Log Level)
This attribute controls what is logged to the access log.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | * 0 - No access logging * 4 - Logging for internal access operations * 256 - Logging for connections, operations, and results * 512 - Logging for access to an entry and referrals
* These values can be added together to provide the exact type of logging required; for example, |
| Default Value | 256 |
| Syntax | Integer |
| Example | nsslapd-accesslog-level: 256 |
3.1.1.3. nsslapd-accesslog-list (List of Access Log Files)
This read-only attribute, which cannot be set, provides a list of access log files used in access log rotation.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-list: accesslog2,accesslog3 |
3.1.1.4. nsslapd-accesslog-logbuffering (Log Buffering)
When set to off, the server writes all access log entries directly to disk. Buffering allows the server to use access logging even when under a heavy load without impacting performance. However, when debugging, it is sometimes useful to disable buffering in order to see the operations and their results right away instead of having to wait for the log entries to be flushed to the file. Disabling log buffering can severely impact performance in heavily loaded servers.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logbuffering: off |
3.1.1.5. nsslapd-accesslog-logexpirationtime (Access Log Expiration Time)
This attribute specifies the maximum age that a log file is allowed to reach before it is deleted. This attribute supplies only the number of units. The units are provided by the nsslapd-accesslog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logexpirationtime: 2 |
3.1.1.6. nsslapd-accesslog-logexpirationtimeunit (Access Log Expiration Time Unit)
This attribute specifies the units for nsslapd-accesslog-logexpirationtime attribute. If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | month |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logexpirationtimeunit: week |
3.1.1.7. nsslapd-accesslog-logging-enabled (Access Log Enable Logging)
Disables and enables accesslog logging but only in conjunction with the nsslapd-accesslog attribute that specifies the path and parameter of the log used to record each database access.
For access logging to be enabled, this attribute must be switched to on, and the nsslapd-accesslog configuration attribute must have a valid path and parameter. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of access logging.
| Attribute | Value | Logging Enabled or Disabled |
|---|---|---|
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | on filename | Enabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off empty string | Disabled |
| nsslapd-accesslog-logging-enabled nsslapd-accesslog | off filename | Disabled |
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logging-enabled: off |
3.1.1.8. nsslapd-accesslog-logmaxdiskspace (Access Log Maximum Disk Space)
This attribute specifies the maximum amount of disk space in megabytes that the access logs are allowed to consume. If this value is exceeded, the oldest access log is deleted.
When setting a maximum disk space, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by the Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the access log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the access log is unlimited in size. |
| Default Value | 500 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logmaxdiskspace: 500 |
3.1.1.9. nsslapd-accesslog-logminfreediskspace (Access Log Minimum Free Disk Space)
This attribute sets the minimum allowed free disk space in megabytes. When the amount of free disk space falls below the value specified on this attribute, the oldest access logs are deleted until enough disk space is freed to satisfy this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logminfreediskspace: -1 |
3.1.1.10. nsslapd-accesslog-logrotationsync-enabled (Access Log Rotation Sync Enabled)
This attribute sets whether access log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For access log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-accesslog-logrotationsynchour and nsslapd-accesslog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate access log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-accesslog-logrotationsynchour and nsslapd-accesslog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logrotationsync-enabled: on |
3.1.1.11. nsslapd-accesslog-logrotationsynchour (Access Log Rotation Sync Hour)
This attribute sets the hour of the day for rotating access logs. This attribute must be used in conjunction with nsslapd-accesslog-logrotationsync-enabled and nsslapd-accesslog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logrotationsynchour: 23 |
3.1.1.12. nsslapd-accesslog-logrotationsyncmin (Access Log Rotation Sync Minute)
This attribute sets the minute of the day for rotating access logs. This attribute must be used in conjunction with nsslapd-accesslog-logrotationsync-enabled and nsslapd-accesslog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logrotationsyncmin: 30 |
3.1.1.13. nsslapd-accesslog-logrotationtime (Access Log Rotation Time)
This attribute sets the time between access log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-accesslog-logrotationtimeunit attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation since the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-accesslog-maxlogsperdir attribute value to 1 or set the nsslapd-accesslog-logrotationtime attribute to -1. The server checks the nsslapd-accesslog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-accesslog-logrotationtime attribute. See Section 3.1.1.16, “nsslapd-accesslog-maxlogsperdir (Access Log Maximum Number of Log Files)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the time between access log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-accesslog-logrotationtime: 100 |
3.1.1.14. nsslapd-accesslog-logrotationtimeunit (Access Log Rotation Time Unit)
This attribute sets the units for the nsslapd-accesslog-logrotationtime attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | day |
| Syntax | DirectoryString |
| Example | nsslapd-accesslog-logrotationtimeunit: week |
3.1.1.15. nsslapd-accesslog-maxlogsize (Access Log Maximum Log Size)
This attribute sets the maximum access log size in megabytes. When this value is reached, the access log is rotated. That means the server starts writing log information to a new log file. If the nsslapd-accesslog-maxlogsperdir attribute is set to 1, the server ignores this attribute.
When setting a maximum log size, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by the Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the access log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-accesslog-maxlogsize: 100 |
3.1.1.16. nsslapd-accesslog-maxlogsperdir (Access Log Maximum Number of Log Files)
This attribute sets the total number of access logs that can be contained in the directory where the access log is stored. Each time the access log is rotated, a new log file is created. When the number of files contained in the access log directory exceeds the value stored in this attribute, then the oldest version of the log file is deleted. For performance reasons, Red Hat recommends not setting this value to 1 because the server does not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-accesslog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-accesslog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 3.1.1.13, “nsslapd-accesslog-logrotationtime (Access Log Rotation Time)” for more information.
Note that, depending on the values set in nsslapd-accesslog-logminfreediskspace and nsslapd-accesslog-maxlogsize, the actual number of logs could be less than what you configure in nsslapd-accesslog-maxlogsperdir. For example, if nsslapd-accesslog-maxlogsperdir uses the default (10 files) and you set nsslapd-accesslog-logminfreediskspace to 500 MB and nsslapd-accesslog-maxlogsize to 100 MB, Directory Server keeps only 5 access files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 10 |
| Syntax | Integer |
| Example | nsslapd-accesslog-maxlogsperdir: 10 |
3.1.1.17. nsslapd-accesslog-mode (Access Log File Permission)
This attribute sets the access mode or file permission with which access log files are to be created. The valid values are any combination of 000 to 777 (these mirror the numbered or absolute UNIX file permissions). The value must be a 3-digit number, the digits varying from 0 through 7:
-
0- None -
1- Execute only -
2- Write only -
3- Write and execute -
4- Read only -
5- Read and execute -
6- Read and write -
7- Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-accesslog-mode: 600 |
3.1.1.18. nsslapd-allow-anonymous-access
If a user attempts to connect to the Directory Server without supplying any bind DN or password, this is an anonymous bind. Anonymous binds simplify common search and read operations, like checking the directory for a phone number or email address, by not requiring users to authenticate to the directory first.
However, there are risks with anonymous binds. Adequate ACIs must be in place to restrict access to sensitive information and to disallow actions like modifies and deletes. Additionally, anonymous binds can be used for denial of service attacks or for malicious people to gain access to the server.
Anonymous binds can be disabled to increase security (off). By default, anonymous binds are allowed (on) for search and read operations. This allows access to regular directory entries, which includes user and group entries as well as configuration entries like the root DSE. A third option, rootdse, allows anonymous search and read access to search the root DSE itself, but restricts access to all other directory entries.
Optionally, resource limits can be placed on anonymous binds using the nsslapd-anonlimitsdn attribute as described in Section 3.1.1.22, “nsslapd-anonlimitsdn”.
Changes to this value will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off | rootdse |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-allow-anonymous-access: on |
3.1.1.19. nsslapd-allow-hashed-passwords
This parameter disables the pre-hashed password checks. By default, the Directory Server does not allow pre-hashed passwords to be set by anyone other than the Directory Manager. You can delegate this privilege to other users when you add them to the Password Administrators group. However in some scenarios, like when the replication partner already controls the pre-hashed passwords checking, this feature has to be disabled on the Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-allow-hashed-passwords: off |
3.1.1.20. nsslapd-allow-unauthenticated-binds
Unauthenticated binds are connections to Directory Server where a user supplies an empty password. Using the default settings, Directory Server denies access in this scenario for security reasons.
Red Hat recommends not enabling unauthenticated binds. This authentication method enables users to bind without supplying a password as any account, including the Directory Manager. After the bind, the user can access all data with the permissions of the account used to bind.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-allow-unauthenticated-binds: off |
3.1.1.21. nsslapd-allowed-sasl-mechanisms
Per default, the root DSE lists all mechanisms the SASL library supports. However in some environments only certain ones are preferred. The nsslapd-allowed-sasl-mechanisms attribute allows you to enable only some defined SASL mechanisms.
The mechanism names must consist of uppercase letters, numbers, and underscores. Each mechanism can be separated by commas or spaces.
The EXTERNAL mechanism is actually not used by any SASL plug-in. It is internal to the server, and is mainly used for TLS client authentication. Hence, the EXTERNAL mechanism cannot be restricted or controlled. It will always appear in the supported mechanisms list, regardless what is set in the nsslapd-allowed-sasl-mechanisms attribute.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid SASL mechanism |
| Default Value | None (all SASL mechanisms allowed) |
| Syntax | DirectoryString |
| Example | nsslapd-allowed-sasl-mechanisms: GSSAPI, DIGEST-MD5, OTP |
3.1.1.22. nsslapd-anonlimitsdn
Resource limits can be set on authenticated binds. The resource limits can set a cap on how many entries can be searched in a single operation (nsslapd-sizeLimit), a time limit (nsslapd-timelimit) and time out period (nsslapd-idletimeout) for searches, and the total number of entries that can be searched (nsslapd-lookthroughlimit). These resource limits prevent denial of service attacks from tying up directory resources and improve overall performance.
Resource limits are set on a user entry. An anonymous bind, obviously, does not have a user entry associated with it. This means that resource limits usually do not apply to anonymous operations.
To set resource limits for anonymous binds, a template entry can be created, with the appropriate resource limits. The nsslapd-anonlimitsdn configuration attribute can then be added that points to this entry and applies the resource limits to anonymous binds.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-anonlimitsdn: cn=anon template,ou=people,dc=example,dc=com |
3.1.1.23. nsslapd-attribute-name-exceptions
This attribute allows non-standard characters in attribute names to be used for backwards compatibility with older servers, such as "_" in schema-defined attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-attribute-name-exceptions: on |
3.1.1.24. nsslapd-auditlog (Audit Log)
This attribute sets the path and filename of the log used to record changes made to each database.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance/audit |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog: /var/log/dirsrv/slapd-instance/audit |
For audit logging to be enabled, this attribute must have a valid path and parameter, and the nsslapd-auditlog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of audit logging.
| Attributes in dse.ldif | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on filename | Enabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off filename | Disabled |
3.1.1.25. nsslapd-auditlog-display-attrs
With the nsslapd-auditlog-display-attrs attribute you can set attributes that Directory Server displays in the audit log to provide useful identifying information about the entry being modified. By adding attributes to the audit log, you can check the current state of certain attributes in the entry and details of the entry update.
You can display attributes in the log by choosing one of the following options:
- To display a certain attribute of the entry that Directory Server modifies, provide the attribute name as a value.
- To display more than one attribute, provide the space separated list of attribute names as a value.
- To display all attributes of the entry, use an asterisk (*) as a value.
Provide the space separated list of attributes that Directory Server must display in the audit log, or use an asterisk (*) as a value to display all attributes of an entry being modified.
For example, you want to add cn attribute to the audit log output. When you set nsslapd-auditlog-display-attrs attribute to cn, the audit log displays the following output:
time: 20221027102743
dn: uid=73747737483,ou=people,dc=example,dc=com
#cn: Frank Lee
result: 0
changetype: modify
replace: description
description: Adds cn attribute to the audit log
-
replace: modifiersname
modifiersname: cn=dm
-
replace: modifytimestamp
modifytimestamp: 20221027142743Z| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid attribute name. Use an asterisk (*) if you want to display all attributes of an entry in the audit log. |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-display-attrs: cn ou |
3.1.1.26. nsslapd-auditlog-list
Provides a list of audit log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-list: auditlog2,auditlog3 |
3.1.1.27. nsslapd-auditlog-logexpirationtime (Audit Log Expiration Time)
This attribute sets the maximum age that a log file is allowed to be before it is deleted. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-auditlog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logexpirationtime: 1 |
3.1.1.28. nsslapd-auditlog-logexpirationtimeunit (Audit Log Expiration Time Unit)
This attribute sets the units for the nsslapd-auditlog-logexpirationtime attribute. If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logexpirationtimeunit: day |
3.1.1.29. nsslapd-auditlog-logging-enabled (Audit Log Enable Logging)
Turns audit logging on and off.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logging-enabled: off |
For audit logging to be enabled, this attribute must have a valid path and parameter and the nsslapd-auditlog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of audit logging.
| Attribute | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | on filename | Enabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off empty string | Disabled |
| nsslapd-auditlog-logging-enabled nsslapd-auditlog | off filename | Disabled |
3.1.1.30. nsslapd-auditlog-logmaxdiskspace (Audit Log Maximum Disk Space)
This attribute sets the maximum amount of disk space in megabytes that the audit logs are allowed to consume. If this value is exceeded, the oldest audit log is deleted.
When setting a maximum disk space, consider the total number of log files that can be created due to log file rotation. Also remember that there are three different log files (access log, audit log, and error log) maintained by the Directory Server, each of which consumes disk space. Compare these considerations with the total amount of disk space for the audit log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the audit log is unlimited in size. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logmaxdiskspace: 10000 |
3.1.1.31. nsslapd-auditlog-logminfreediskspace (Audit Log Minimum Free Disk Space)
This attribute sets the minimum permissible free disk space in megabytes. When the amount of free disk space falls below the value specified by this attribute, the oldest audit logs are deleted until enough disk space is freed to satisfy this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 (unlimited) | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logminfreediskspace: -1 |
3.1.1.32. nsslapd-auditlog-logrotationsync-enabled (Audit Log Rotation Sync Enabled)
This attribute sets whether audit log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For audit log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-auditlog-logrotationsynchour and nsslapd-auditlog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate audit log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-auditlog-logrotationsynchour and nsslapd-auditlog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logrotationsync-enabled: on |
3.1.1.33. nsslapd-auditlog-logrotationsynchour (Audit Log Rotation Sync Hour)
This attribute sets the hour of the day for rotating audit logs. This attribute must be used in conjunction with nsslapd-auditlog-logrotationsync-enabled and nsslapd-auditlog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditlog-logrotationsynchour: 23 |
3.1.1.34. nsslapd-auditlog-logrotationsyncmin (Audit Log Rotation Sync Minute)
This attribute sets the minute of the day for rotating audit logs. This attribute must be used in conjunction with nsslapd-auditlog-logrotationsync-enabled and nsslapd-auditlog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditlog-logrotationsyncmin: 30 |
3.1.1.35. nsslapd-auditlog-logrotationtime (Audit Log Rotation Time)
This attribute sets the time between audit log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-auditlog-logrotationtimeunit attribute. If the nsslapd-auditlog-maxlogsperdir attribute is set to 1, the server ignores this attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation, as the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-auditlog-maxlogsperdir attribute value to 1 or set the nsslapd-auditlog-logrotationtime attribute to -1. The server checks the nsslapd-auditlog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-auditlog-logrotationtime attribute. See Section 3.1.1.38, “nsslapd-auditlog-maxlogsperdir (Audit Log Maximum Number of Log Files)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the time between audit log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-logrotationtime: 100 |
3.1.1.36. nsslapd-auditlog-logrotationtimeunit (Audit Log Rotation Time Unit)
This attribute sets the units for the nsslapd-auditlog-logrotationtime attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditlog-logrotationtimeunit: day |
3.1.1.37. nsslapd-auditlog-maxlogsize (Audit Log Maximum Log Size)
This attribute sets the maximum audit log size in megabytes. When this value is reached, the audit log is rotated. That means the server starts writing log information to a new log file. If nsslapd-auditlog-maxlogsperdir to 1, the server ignores this attribute.
When setting a maximum log size, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by the Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the audit log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-auditlog-maxlogsize: 50 |
3.1.1.38. nsslapd-auditlog-maxlogsperdir (Audit Log Maximum Number of Log Files)
This attribute sets the total number of audit logs that can be contained in the directory where the audit log is stored. Each time the audit log is rotated, a new log file is created. When the number of files contained in the audit log directory exceeds the value stored on this attribute, then the oldest version of the log file is deleted. The default is 1 log. If this default is accepted, the server will not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-auditlog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-auditlog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 3.1.1.35, “nsslapd-auditlog-logrotationtime (Audit Log Rotation Time)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditlog-maxlogsperdir: 10 |
3.1.1.39. nsslapd-auditlog-mode (Audit Log File Permission)
This attribute sets the access mode or file permissions with which audit log files are to be created. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. The value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-auditlog-mode: 600 |
3.1.1.40. nsslapd-auditfaillog (Audit Fail Log)
This attribute sets the path and filename of the log used to record failed LDAP modifications.
If nsslapd-auditfaillog-logging-enabled is enabled, and nsslapd-auditfaillog is not set, the audit fail events are logged to the file specified in nsslapd-auditlog.
If you set the nsslapd-auditfaillog parameter to the same path as nsslapd-auditlog, both are logged in the same file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance/audit |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog: /var/log/dirsrv/slapd-instance/audit |
To enable the audit fail log, this attribute must have a valid path and the nsslapd-auditfaillog-logging-enabled attribute must be set to on
3.1.1.41. nsslapd-auditfaillog-list
Provides a list of audit fail log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-list: auditfaillog2,auditfaillog3 |
3.1.1.42. nsslapd-auditfaillog-logexpirationtime (Audit Fail Log Expiration Time)
This attribute sets the maximum age of a log file before it is removed. It supplies to the number of units. Specify the units, such as day, week, month, and so forth in the nsslapd-auditfaillog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logexpirationtime: 1 |
3.1.1.43. nsslapd-auditfaillog-logexpirationtimeunit (Audit Fail Log Expiration Time Unit)
This attribute sets the units for the nsslapd-auditfaillog-logexpirationtime attribute. If the unit is unknown by the server, the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logexpirationtimeunit: day |
3.1.1.44. nsslapd-auditfaillog-logging-enabled (Audit Fail Log Enable Logging)
Turns on and off logging of failed LDAP modifications.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logging-enabled: off |
3.1.1.45. nsslapd-auditfaillog-logmaxdiskspace (Audit Fail Log Maximum Disk Space)
This attribute sets the maximum amount of disk space in megabytes the audit fail logs are can consume. If the size exceed the limit, the oldest audit fail log is deleted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the audit fail log is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logmaxdiskspace: 10000 |
3.1.1.46. nsslapd-auditfaillog-logminfreediskspace (Audit Fail Log Minimum Free Disk Space)
This attribute sets the minimum permissible free disk space in megabytes. When the amount of free disk space is lower than the specified value, the oldest audit fail logs are deleted until enough disk space is freed.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 (unlimited) | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logminfreediskspace: -1 |
3.1.1.47. nsslapd-auditfaillog-logrotationsync-enabled (Audit Fail Log Rotation Sync Enabled)
This attribute sets whether audit fail log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For audit fail log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-auditfaillog-logrotationsynchour and nsslapd-auditfaillog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate audit fail log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-auditfaillog-logrotationsynchour and nsslapd-auditfaillog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logrotationsync-enabled: on |
3.1.1.48. nsslapd-auditfaillog-logrotationsynchour (Audit Fail Log Rotation Sync Hour)
This attribute sets the hour of the day the audit fail log is rotated. This attribute must be used in conjunction with nsslapd-auditfaillog-logrotationsync-enabled and nsslapd-auditfaillog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logrotationsynchour: 23 |
3.1.1.49. nsslapd-auditfaillog-logrotationsyncmin (Audit Fail Log Rotation Sync Minute)
This attribute sets the minute the audit fail log is rotated. This attribute must be used in conjunction with nsslapd-auditfaillog-logrotationsync-enabled and nsslapd-auditfaillog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value |
None (because |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logrotationsyncmin: 30 |
3.1.1.50. nsslapd-auditfaillog-logrotationtime (Audit Fail Log Rotation Time)
This attribute sets the time between audit fail log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-auditfaillog-logrotationtimeunit attribute. If the nsslapd-auditfaillog-maxlogsperdir attribute is set to 1, the server ignores this attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation, as the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-auditfaillog-maxlogsperdir attribute value to 1 or set the nsslapd-auditfaillog-logrotationtime attribute to -1. The server checks the nsslapd-auditfaillog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-auditfaillog-logrotationtime attribute. See Section 3.1.1.53, “nsslapd-auditfaillog-maxlogsperdir (Audit Fail Log Maximum Number of Log Files)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the time between audit fail log file rotation is unlimited. |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-logrotationtime: 100 |
3.1.1.51. nsslapd-auditfaillog-logrotationtimeunit (Audit Fail Log Rotation Time Unit)
This attribute sets the units for the nsslapd-auditfaillog-logrotationtime attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-auditfaillog-logrotationtimeunit: day |
3.1.1.52. nsslapd-auditfaillog-maxlogsize (Audit Fail Log Maximum Log Size)
This attribute sets the maximum audit fail log size in megabytes. When this value is reached, the audit fail log is rotated. That means the server starts writing log information to a new log file. If the nsslapd-auditfaillog-maxlogsperdir parameter is set to 1, the server ignores this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-maxlogsize: 50 |
3.1.1.53. nsslapd-auditfaillog-maxlogsperdir (Audit Fail Log Maximum Number of Log Files)
This attribute sets the total number of audit fail logs that can be contained in the directory where the audit log is stored. Each time the audit fail log is rotated, a new log file is created. When the number of files contained in the audit log directory exceeds the value stored on this attribute, then the oldest version of the log file is deleted. The default is 1 log. If this default is accepted, the server will not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-auditfaillog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-auditfaillog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 3.1.1.50, “nsslapd-auditfaillog-logrotationtime (Audit Fail Log Rotation Time)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-maxlogsperdir: 10 |
3.1.1.54. nsslapd-auditfaillog-mode (Audit Fail Log File Permission)
This attribute sets the access mode or file permissions with which audit fail log files are to be created. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. The value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-auditfaillog-mode: 600 |
3.1.1.55. nsslapd-bakdir (Default Backup Directory)
This parameter sets the path to the default backup directory. The Directory Server user must have write permissions in the configured directory.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any local directory path. |
| Default Value | /var/lib/dirsrv/slapd-instance/bak |
| Syntax | DirectoryString |
| Example | nsslapd-bakdir: /var/lib/dirsrv/slapd-instance/bak |
3.1.1.56. nsslapd-certdir (Certificate and Key Database Directory)
This parameter defines the full path to the directory that Directory Server uses to store the Network Security Services (NSS) database of the instance. This database contains the private keys and certificates of the instance.
As a fallback, Directory Server extracts the private key and certificates to this directory, if the server cannot extract them to the /tmp/ directory in a private name space. For details about private name spaces, see the PrivateTmp parameter description in the systemd.exec(5) man page.
The directory specified in nsslapd-certdir must be owned by the user ID of the server, and only this user ID must have read-write permissions in this directory. For security reasons, no other users should have permissions to read or write to this directory.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | An absolute path |
| Default Value | /etc/dirsrv/slapd-instance_name/ |
| Syntax | DirectoryString |
| Example | nsslapd-certdir: /etc/dirsrv/slapd-instance_name/ |
3.1.1.57. nsslapd-certmap-basedn (Certificate Map Search Base)
This attribute can be used when client authentication is performed using TLS certificates in order to avoid limitations of the security subsystem certificate mapping, configured in the /etc/dirsrv/slapd-instance_name/certmap.conf file. Depending on the configuration in this file, the certificate mapping may be done using a directory subtree search based at the root DN. If the search is based at the root DN, then the nsslapd-certmap-basedn attribute may force the search to be based at some entry other than the root. The valid value for this attribute is the DN of the suffix or subtree to use for certificate mapping.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-certmap-basedn: ou=People,dc=example,dc=com |
3.1.1.58. nsslapd-config
This read-only attribute is the config DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid configuration DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-config: cn=config |
3.1.1.59. nsslapd-cn-uses-dn-syntax-in-dns
This parameter allows you to enable a DN inside a CN value.
The Directory Server DN normalizer follows RFC4514 and keeps a white space if the RDN attribute type is not based on the DN syntax. However the Directory Server’s configuration entry sometimes uses a cn attribute to store a DN value. For example in dn: cn="dc=A,dc=com", cn=mapping tree,cn=config, the cn should be normalized following the DN syntax.
If this configuration is required, enable the nsslapd-cn-uses-dn-syntax-in-dns parameter.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-cn-uses-dn-syntax-in-dns: off |
3.1.1.60. nsslapd-connection-buffer
This attribute sets the connection buffering behavior. Possible values:
-
0: Disable buffering. Only single Protocol Data Units (PDU) are read at a time. -
1: Regular fixed sizeLDAP_SOCKET_IO_BUFFER_SIZEof512bytes. -
2: Adaptable buffer size.
The value 2 provides a better performance if the client sends a large amount of data at once. This is, for example, the case for large add and modify operations, or when many asynchronous requests are received over a single connections like during a replication.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 | 1 | 2 |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-connection-buffer: 1 |
3.1.1.61. nsslapd-connection-nocanon
This option allows you to enable or disable the SASL NOCANON flag. Disabling avoids the Directory Server looking up DNS reverse entries for outgoing connections.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-connection-nocanon: on |
3.1.1.62. nsslapd-conntablesize
This attribute sets the connection table size, which determines the total number of connections supported by the server.
Increase the value of this attribute if Directory Server is refusing connections because it is out of connection slots. When this occurs, the Directory Server’s error log file records the message Not listening for new connections — too many fds open.
It may be necessary to increase the operating system limits for the number of open files and number of open files per process, and it may be necessary to increase the ulimit for the number of open files (ulimit -n) in the shell that starts Directory Server.
The size of the connection table is cap with nsslapd-maxdescriptor. See Section 3.1.1.119, “nsslapd-maxdescriptors (Maximum File Descriptors)” for more information.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Operating-system dependent |
| Default Value |
The maximum number of files that the Directory Server process can open. See the |
| Syntax | Integer |
| Example | nsslapd-conntablesize: 4093 |
3.1.1.63. nsslapd-counters
The nsslapd-counters attribute enables and disables Directory Server database and server performance counters.
There can be a performance impact by keeping track of the larger counters. Turning off 64-bit integers for counters can have a minimal improvement on performance, although it negatively affects long term statistics tracking.
This parameter is enabled by default. To disable counters, stop the Directory Server, edit the dse.ldif file directly, and restart the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-counters: on |
3.1.1.64. nsslapd-csnlogging
This attribute sets whether change sequence numbers (CSNs), when available, are to be logged in the access log. By default, CSN logging is turned on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-csnlogging: on |
3.1.1.65. nsslapd-defaultnamingcontext
This attribute gives the naming context, of all configured naming contexts, which clients should use by default as a search base. This value is copied over to the root DSE as the defaultNamingContext attribute, which allows clients to query the root DSE to obtain the context and then to initiate a search with the appropriate base.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any root suffix DN |
| Default Value | The default user suffix |
| Syntax | DN |
| Example | nsslapd-defaultnamingcontext: dc=example,dc=com |
3.1.1.66. nsslapd-disk-monitoring
This attribute enables a thread which runs every ten (10) seconds to check the available disk space on the disk or mount where the Directory Server database is running. If the available disk space drops below a configured threshold, then the server begins reducing logging levels, disabling access or audit logs, and deleting rotated logs. If that does not free enough available space, then the server shuts down gracefully (after a wanring and grace period).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring: on |
3.1.1.67. nsslapd-disk-monitoring-grace-period
Sets a grace period to wait before shutting down the server after it hits half of the disk space limit set in Section 3.1.1.70, “nsslapd-disk-monitoring-threshold”. This gives the administrator time to clean out the disk and prevent a shutdown.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any integer (sets value in minutes) |
| Default Value | 60 |
| Syntax | Integer |
| Example | nsslapd-disk-monitoring-grace-period: 45 |
3.1.1.68. nsslapd-disk-monitoring-logging-critical
Sets whether to shut down the server if the log directories pass the halfway point set in the disk space limit, Section 3.1.1.70, “nsslapd-disk-monitoring-threshold”.
If this is enabled, then logging is not disabled and rotated logs are not deleted as means of reducing disk usage by the server. The server simply goes toward a shutdown process.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring-logging-critical: on |
3.1.1.69. nsslapd-disk-monitoring-readonly-on-threshold
If the free disk space reaches half of the value you set in the nsslapd-disk-monitoring-threshold parameter, Directory Server shuts down the instance after the grace period set in nsslapd-disk-monitoring-grace-period is reached. However, if the disk runs out of space before the instance is down, data can be corrupted. To prevent this problem, enable the nsslapd-disk-monitoring-readonly-on-threshold parameter, the Directory Server sets the instance to read-only mode when the threshold is reached.
With this setting, Directory Server does not start if the free disk space is below half of the threshold configured in the nsslapd-disk-monitoring-threshold.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring-readonly-on-threshold: off |
3.1.1.70. nsslapd-disk-monitoring-threshold
Sets the threshold, in bytes, to use to evaluate whether the server has enough available disk space. Once the space reaches half of this threshold, then the server begins a shut down process.
For example, if the threshold is 2MB (the default), then once the available disk space reaches 1MB, the server will begin to shut down.
By default, the threshold is evaluated backs on the disk space used by the configuration, transaction, and database directories for the Directory Server instance. If the Section 3.1.1.68, “nsslapd-disk-monitoring-logging-critical” attribute is enabled, then the log directory is included in the evaluation.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | * 0 to the maximum 32-bit integer value (2147483647) on 32-bit systems * 0 to the maximum 64-bit integer value (9223372036854775807) on 64-bit systems |
| Default Value | 2000000 (2MB) |
| Syntax | DirectoryString |
| Example | nsslapd-disk-monitoring-threshold: 2000000 |
3.1.1.71. nsslapd-dn-validate-strict
The Section 3.1.1.168, “nsslapd-syntaxcheck” attribute enables the server to verify that any new or modified attribute value matches the required syntax for that attribute.
However, the syntax rules for DNs have grown increasingly strict. Attempting to enforce DN syntax rules in RFC 4514 could break many servers using older syntax definitions. By default, then nsslapd-syntaxcheck validates DNs using RFC 1779 or RFC 2253.
The nsslapd-dn-validate-strict attribute explicitly enables strict syntax validation for DNs, according to section 3 in RFC 4514. If this attribute is set to off (the default), the server normalizes the value before checking it for syntax violations.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-dn-validate-strict: off |
3.1.1.72. nsslapd-ds4-compatible-schema
Makes the schema in cn=schema compatible with 4.x versions of Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ds4-compatible-schema: off |
3.1.1.73. nsslapd-enable-turbo-mode
The Directory Server turbo mode is a feature that enables a worker thread to be dedicated to a connection and continuously read incoming operations from that connection. This can improve the performance on very active connections, and the feature is enabled by default.
Worker threads are processing the LDAP operation received by the server. The number of worker threads is defined in the nsslapd-threadnumber parameter. Every five seconds, each worker thread evaluates if the activity level of its current connection is one of the highest among all established connections. Directory Server measures the activity as the number of operations initiated since the last check, and switches a worker thread in turbo mode if the activity of the current connection is one of the highest.
If you encounter long execution times (etime value in log files) for bind operations, such as one second or longer, deactivating the turbo mode can improve the performance. However, in some cases, long bind times are a symptom of networking or hardware issues. In these situations, disabling the turbo mode does not result in improved performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-enable-turbo-mode: on |
3.1.1.74. nsslapd-enable-upgrade-hash
During a simple bind, Directory Server has access to the plain text password due to the nature of bind operations. If the nsslapd-enable-upgrade-hash parameter is enabled and a user authenticates, Directory Server checks if the userPassword attribute of the user uses the hashing algorithm set in the passwordStorageScheme attribute. If the algorithm is different, the server hashes the plain text password with the algorithm from passwordStorageScheme and updates the value of the user’s userPassword attribute.
For example, if you import a user entry with a password that is hashed using a weak algorithm, the server automatically re-hashes the passwords on the first login of the user using the algorithm set in passwordStorageScheme, which is, by default, PBKDF2_SHA256.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-enable-upgrade-hash: on |
3.1.1.75. nsslapd-enquote-sup-oc (Enable Superior Object Class Enquoting)
This attribute is deprecated and will be removed in a future version of Directory Server.
This attribute controls whether quoting in the objectclass attributes contained in the cn=schema entry conforms to the quoting specified by Internet draft RFC 2252. By default, the Directory Server conforms to RFC 2252, which indicates that this value should not be quoted. Only very old clients need this value set to on, so leave it off.
Turning this attribute on or off does not affect Directory Server Console.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-enquote-sup-oc: off |
3.1.1.76. nsslapd-entryusn-global
The nsslapd-entryusn-global parameter defines if the USN plug-in assigns unique update sequence numbers (USN) across all back end databases or to each database individually. For unique USNs across all back end databases, set this parameter to on.
For further details, see Section 6.8, “entryusn”.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-entryusn-global: off |
3.1.1.77. nsslapd-entryusn-import-initval
Entry update sequence numbers (USNs) are not preserved when entries are exported from one server and imported into another, including when initializing a database for replication. By default, the entry USNs for imported entries are set to zero.
It is possible to configure a different initial value for entry USNs using nsslapd-entryusn-import-initval. This sets a starting USN which is used for all imported entries.
There are two possible values for nsslapd-entryusn-import-initval:
- An integer, which is the explicit start number used for every imported entry.
- next, which means that every imported entry uses whatever the highest entry USN value was on the server before the import operation, incremented by one.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any integer | next |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-entryusn-import-initval: next |
3.1.1.78. nsslapd-errorlog (Error Log)
This attribute sets the path and filename of the log used to record error messages generated by the Directory Server. These messages can describe error conditions, but more often they contain informative conditions, such as:
- Server startup and shutdown times.
- The port number that the server uses.
This log contains differing amounts of information depending on the current setting of the Log Level attribute. See Section 3.1.1.79, “nsslapd-errorlog-level (Error Log Level)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid filename |
| Default Value | /var/log/dirsrv/slapd-instance/errors |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog: /var/log/dirsrv/slapd-instance/errors |
For error logging to be enabled, this attribute must have a valid path and filename, and the nsslapd-errorlog-logging-enabled configuration attribute must be switched to on. The table lists the four possible combinations of values for these two configuration attributes and their outcome in terms of disabling or enabling of error logging.
| Attributes in dse.ldif | Value | Logging enabled or disabled |
|---|---|---|
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | on empty string | Disabled |
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | on filename | Enabled |
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | off empty string | Disabled |
| nsslapd-errorlog-logging-enabled nsslapd-errorlog | off filename | Disabled |
3.1.1.79. nsslapd-errorlog-level (Error Log Level)
This attribute sets the level of logging for the Directory Server. The log level is additive; that is, specifying a value of 3 includes both levels 1 and 2.
The default value for nsslapd-errorlog-level is 16384.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | * 1 — Trace function calls. Logs a message when the server enters and exits a function. * 2 — Debug packet handling. * 4 — Heavy trace output debugging. * 8 — Connection management. * 16 — Print out packets sent/received. * 32 — Search filter processing. * 64 — Config file processing. * 128 — Access control list processing. * 1024 — Log communications with shell databases. * 2048 — Log entry parsing debugging. * 4096 — Housekeeping thread debugging. * 8192 — Replication debugging. * 16384 — Default level of logging used for critical errors and other messages that are always written to the error log; for example, server startup messages. Messages at this level are always included in the error log, regardless of the log level setting. * 32768 — Database cache debugging.
* 65536 — Server plug-in debugging. It writes an entry to the log file when a server plug-in calls
* 262144 — Access control summary information, much less verbose than level * 524288 — LMDB database debugging. |
| Default Value | 16384 |
| Syntax | Integer |
| Example | nsslapd-errorlog-level: 8192 |
3.1.1.80. nsslapd-errorlog-list
This read-only attribute provides a list of error log files.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-list: errorlog2,errorlog3 |
3.1.1.81. nsslapd-errorlog-logexpirationtime (Error Log Expiration Time)
This attribute sets the maximum age that a log file is allowed to reach before it is deleted. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-errorlog-logexpirationtimeunit attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) A value of -1 or 0 means that the log never expires. |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logexpirationtime: 1 |
3.1.1.82. nsslapd-errorlog-logexpirationtimeunit (Error Log Expiration Time Unit)
This attribute sets the units for the nsslapd-errorlog-logexpirationtime attribute. If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day |
| Default Value | month |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logexpirationtimeunit: week |
3.1.1.83. nsslapd-errorlog-logging-enabled (Enable Error Logging)
Turns error logging on and off.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logging-enabled: on |
3.1.1.84. nsslapd-errorlog-logmaxdiskspace (Error Log Maximum Disk Space)
This attribute sets the maximum amount of disk space in megabytes that the error logs are allowed to consume. If this value is exceeded, the oldest error log is deleted.
When setting a maximum disk space, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by the Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the disk space allowed to the error log is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logmaxdiskspace: 10000 |
3.1.1.85. nsslapd-errorlog-logminfreediskspace (Error Log Minimum Free Disk Space)
This attribute sets the minimum allowed free disk space in megabytes. When the amount of free disk space falls below the value specified on this attribute, the oldest error log is deleted until enough disk space is freed to satisfy this attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 (unlimited) | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logminfreediskspace: -1 |
3.1.1.86. nsslapd-errorlog-logrotationsync-enabled (Error Log Rotation Sync Enabled)
This attribute sets whether error log rotation is to be synchronized with a particular time of the day. Synchronizing log rotation this way can generate log files at a specified time during a day, such as midnight to midnight every day. This makes analysis of the log files much easier because they then map directly to the calendar.
For error log rotation to be synchronized with time-of-day, this attribute must be enabled with the nsslapd-errorlog-logrotationsynchour and nsslapd-errorlog-logrotationsyncmin attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate error log files every day at midnight, enable this attribute by setting its value to on, and then set the values of the nsslapd-errorlog-logrotationsynchour and nsslapd-errorlog-logrotationsyncmin attributes to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logrotationsync-enabled: on |
3.1.1.87. nsslapd-errorlog-logrotationsynchour (Error Log Rotation Sync Hour)
This attribute sets the hour of the day for rotating error logs. This attribute must be used in conjunction with nsslapd-errorlog-logrotationsync-enabled and nsslapd-errorlog-logrotationsyncmin attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 23 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logrotationsynchour: 23 |
3.1.1.88. nsslapd-errorlog-logrotationsyncmin (Error Log Rotation Sync Minute)
This attribute sets the minute of the day for rotating error logs. This attribute must be used in conjunction with nsslapd-errorlog-logrotationsync-enabled and nsslapd-errorlog-logrotationsynchour attributes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 through 59 |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logrotationsyncmin: 30 |
3.1.1.89. nsslapd-errorlog-logrotationtime (Error Log Rotation Time)
This attribute sets the time between error log file rotations. This attribute supplies only the number of units. The units (day, week, month, and so forth) are given by the nsslapd-errorlog-logrotationtimeunit (Error Log Rotation Time Unit) attribute.
Directory Server rotates the log at the first write operation after the configured interval has expired, regardless of the size of the log.
Although it is not recommended for performance reasons to specify no log rotation, as the log grows indefinitely, there are two ways of specifying this. Either set the nsslapd-errorlog-maxlogsperdir attribute value to 1 or set the nsslapd-errorlog-logrotationtime attribute to -1. The server checks the nsslapd-errorlog-maxlogsperdir attribute first, and, if this attribute value is larger than 1, the server then checks the nsslapd-errorlog-logrotationtime attribute. See Section 3.1.1.92, “nsslapd-errorlog-maxlogsperdir (Maximum Number of Error Log Files)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647), where a value of -1 means that the time between error log file rotation is unlimited). |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-logrotationtime: 100 |
3.1.1.90. nsslapd-errorlog-logrotationtimeunit (Error Log Rotation Time Unit)
This attribute sets the units for nsslapd-errorlog-logrotationtime (Error Log Rotation Time). If the unit is unknown by the server, then the log never expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | month | week | day | hour | minute |
| Default Value | week |
| Syntax | DirectoryString |
| Example | nsslapd-errorlog-logrotationtimeunit: day |
3.1.1.91. nsslapd-errorlog-maxlogsize (Maximum Error Log Size)
This attribute sets the maximum error log size in megabytes. When this value is reached, the error log is rotated, and the server starts writing log information to a new log file. If nsslapd-errorlog-maxlogsperdir is set to 1, the server ignores this attribute.
When setting a maximum log size, consider the total number of log files that can be created due to log file rotation. Also, remember that there are three different log files (access log, audit log, and error log) maintained by the Directory Server, each of which consumes disk space. Compare these considerations to the total amount of disk space for the error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 | 1 to the maximum 32 bit integer value (2147483647) where a value of -1 means the log file is unlimited in size. |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsslapd-errorlog-maxlogsize: 100 |
3.1.1.92. nsslapd-errorlog-maxlogsperdir (Maximum Number of Error Log Files)
This attribute sets the total number of error logs that can be contained in the directory where the error log is stored. Each time the error log is rotated, a new log file is created. When the number of files contained in the error log directory exceeds the value stored on this attribute, then the oldest version of the log file is deleted. The default is 1 log. If this default is accepted, the server does not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-errorlog-logrotationtime attribute to establish whether log rotation is specified. If the nsslapd-errorlog-logrotationtime attribute has a value of -1, then there is no log rotation. See Section 3.1.1.89, “nsslapd-errorlog-logrotationtime (Error Log Rotation Time)” for more information.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 1 |
| Syntax | Integer |
| Example | nsslapd-errorlog-maxlogsperdir: 10 |
3.1.1.93. nsslapd-errorlog-mode (Error Log File Permission)
This attribute sets the access mode or file permissions with which error log files are to be created. The valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file permissions. That is, the value must be a combination of a 3-digit number, the digits varying from 0 through 7:
- 0 - None
- 1 - Execute only
- 2 - Write only
- 3 - Write and execute
- 4 - Read only
- 5 - Read and execute
- 6 - Read and write
- 7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the second digit represents the group’s permissions, and the third digit represents everyone’s permissions. When changing the default value, remember that 000 does not allow access to the logs and that allowing write permissions to everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log rotates to a new file.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 000 through 777 |
| Default Value | 600 |
| Syntax | Integer |
| Example | nsslapd-errorlog-mode: 600 |
3.1.1.94. nsslapd-force-sasl-external
When establishing a TLS connection, a client sends its certificate first and then issues a BIND request using the SASL/EXTERNAL mechanism. Using SASL/EXTERNAL tells the Directory Server to use the credentials in the certificate for the TLS handshake. However, some clients do not use SASL/EXTERNAL when they send their BIND request, so the Directory Server processes the bind as a simple authentication request or an anonymouse request and the TLS connection fails.
The nsslapd-force-sasl-external attribute forces clients in certificate-based authentication to send the BIND request using the SASL/EXTERNAL method.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | String |
| Example | nsslapd-force-sasl-external: on |
3.1.1.95. nsslapd-groupevalnestlevel
This attribute is deprecated, and documented here only for historical purposes.
The Access Control Plug-in does not use the value specified by the nsslapd-groupevalnestlevel attribute to set the number of levels of nesting that access control performs for group evaluation. Instead, the number of levels of nesting is hardcoded as 5.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 5 |
| Default Value | 5 |
| Syntax | Integer |
| Example | nsslapd-groupevalnestlevel: 5 |
3.1.1.96. nsslapd-haproxy-trusted-ip (HAProxy Trusted IP)
The nsslapd-haproxy-trusted-ip attribute configures the list of trusted proxy servers. When you set nsslapd-haproxy-trusted-ip, Directory Server uses HAProxy protocol to receive client IP addresses via an additional TCP header to evaluate access control instructions (ACIs) correctly and log the client traffic.
If an untrusted proxy server initiates a bind request, Directory Server rejects the request and records the following message to the error log file:
[time_stamp] conn=5 op=-1 fd=64 Disconnect - Protocol error - Unknown Proxy - P4
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | IPv4 or IPv6 addresses |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-haproxy-trusted-ip: 127.0.0.1 |
3.1.1.97. nsslapd-idletimeout (Default Idle Timeout)
This attribute sets the amount of time in seconds after which an idle LDAP client connection is closed by the server. A value of 0 means that the server never closes idle connections. This setting applies to all connections and all users. Idle timeout is enforced when the connection table is walked, when poll() does not return zero. Therefore, a server with a single connection never enforces the idle timeout.
Use the nsIdleTimeout operational attribute, which can be added to user entries, to override the value assigned to this attribute. For details, see the "Setting Resource Limits Based on the Bind DN" section in the Red Hat Directory Server Administration Guide.
For very large databases, with millions of entries, this attribute must have a high enough value that the online initialization process can complete or replication will fail when the connection to the server times out. Alternatively, the nsIdleTimeout attribute can be set to a high value on the entry used as the supplier bind DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 3600 |
| Syntax | Integer |
| Example | nsslapd-idletimeout: 3600 |
3.1.1.98. nsslapd-ignore-virtual-attrs
This parameter allows to disable the virtual attribute lookup in a search entry.
If you do not require virtual attributes, you can disable virtual attribute lookups in search results to increase the speed of searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ignore-virtual-attrs: off |
3.1.1.99. nsslapd-instancedir (Instance Directory)
This attribute is deprecated. There are now separate configuration parameters for instance-specific paths, such as nsslapd-certdir and nsslapd-lockdir. See the documentation for the specific directory path that is set.
3.1.1.100. nsslapd-ioblocktimeout (IO Block Time Out)
This attribute sets the amount of time in milliseconds after which the connection to a stalled LDAP client is closed. An LDAP client is considered to be stalled when it has not made any I/O progress for read or write operations.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to the maximum 32 bit integer value (2147483647) in ticks |
| Default Value | 10000 |
| Syntax | Integer |
| Example | nsslapd-ioblocktimeout: 10000 |
3.1.1.101. nsslapd-lastmod (Track Modification Time)
This attribute sets whether the Directory Server maintains the creatorsName, createTimestamp, modifiersName, and modifyTimestamp operational attributes for newly created or updated entries.
Red Hat recommends not disabling tracking these attributes. If disabled, entries do not get a unique ID assigned in the nsUniqueID attribute and replication does not work.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-lastmod: on |
3.1.1.102. nsslapd-ldapiautobind (Enable Autobind)
The nsslapd-ldapiautobind sets whether the server will allow users to autobind to Directory Server using LDAPI. Autobind maps the UID or GUID number of a system user to a Directory Server user, and automatically authenticates the user to Directory Server based on those credentials. The Directory Server connection occurs over UNIX socket.
Along with enabling autobind, configuring autobind requires configuring mapping entries. The nsslapd-ldapimaprootdn maps a root user on the system to the Directory Manager. The nsslapd-ldapimaptoentries maps regular users to Directory Server users, based on the parameters defined in the nsslapd-ldapiuidnumbertype, nsslapd-ldapigidnumbertype, and nsslapd-ldapientrysearchbase attributes.
Autobind can only be enabled if LDAPI is enabled, meaning the nsslapd-ldapilisten is on and the nsslapd-ldapifilepath attribute is set to an LDAPI socket.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ldapiautobind: off |
3.1.1.103. nsslapd-ldapientrysearchbase (Search Base for LDAPI Authentication Entries)
With autobind, it is possible to map system users to Directory Server user entries, based on the system user’s UID and GUID numbers. This requires setting Directory Server parameters for which attribute to use for the UID number (nsslapd-ldapiuidnumbertype) and GUID number (nsslapd-ldapigidnumbertype) and setting the search base to use to search for matching user entries.
The nsslapd-ldapientrysearchbase gives the subtree to search for user entries to use for autobind.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | DN |
| Default Value |
The suffix created when the server instance was created, such as |
| Syntax | DN |
| Example | nsslapd-ldapientrysearchbase: ou=people,dc=example,dc=om |
3.1.1.104. nsslapd-ldapifilepath (File Location for LDAPI Socket)
LDAPI connects a user to an LDAP server over a UNIX socket rather than TCP. In order to configure LDAPI, the server must be configured to communicate over a UNIX socket. The UNIX socket to use is set in the nsslapd-ldapifilepath attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any directory path |
| Default Value | /var/run/dirsrv/slapd-example.socket |
| Syntax | Case-exact string |
| Example | nsslapd-ldapifilepath: /var/run/slapd-example.socket |
3.1.1.105. nsslapd-ldapigidnumbertype (Attribute Mapping for System GUID Number)
Autobind can be used to authenticate system users to the server automatically and connect to the server using a UNIX socket. To map the system user to a Directory Server user for authentication, the system user’s UID and GUID numbers should be mapped to be a Directory Server attribute. The nsslapd-ldapigidnumbertype attribute points to the Directory Server attribute to map system GUIDs to user entries.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and nsslapd-ldapifilepath), autobind is enabled (nsslapd-ldapiautobind), and autobind mapping is enabled for regular users (nsslapd-ldapimaptoentries).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any Directory Server attribute |
| Default Value | gidNumber |
| Syntax | DirectoryString |
| Example | nsslapd-ldapigidnumbertype: gidNumber |
3.1.1.106. nsslapd-ldapilisten (Enable LDAPI)
The nsslapd-ldapilisten enables LDAPI connections to the Directory Server. LDAPI allows users to connect to the Directory Server over a UNIX socket rather than a standard TCP port. Along with enabling LDAPI by setting nsslapd-ldapilisten to on, there must also be a UNIX socket set for LDAPI in the nsslapd-ldapifilepath attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ldapilisten: on |
3.1.1.107. nsslapd-ldapimaprootdn (Autobind Mapping for Root User)
With autobind, a system user is mapped to a Directory Server user and then automatically authenticated to the Directory Server over a UNIX socket.
The root system user (the user with a UID of 0) is mapped to whatever Directory Server entry is specified in the nsslapd-ldapimaprootdn attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any DN |
| Default Value | cn=Directory Manager |
| Syntax | DN |
| Example | nsslapd-ldapimaprootdn: cn=Directory Manager |
3.1.1.108. nsslapd-ldapimaptoentries (Enable Autobind Mapping for Regular Users)
With autobind, a system user is mapped to a Directory Server user and then automatically authenticated to the Directory Server over a UNIX socket. This mapping is automatic for root users, but it must be enabled for regular system users through the nsslapd-ldapimaptoentries attribute. Setting this attribute to on enables mapping for regular system users to Directory Server entries. If this attribute is not enabled, then only root users can use autobind to authenticate to the Directory Server, and all other users connect anonymously.
The mappings themselves are configured through the nsslapd-ldapiuidnumbertype and nsslapd-ldapigidnumbertype attributes, which map Directory Server attributes to the user’s UID and GUID numbers.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and nsslapd-ldapifilepath) and autobind is enabled (nsslapd-ldapiautobind).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-ldapimaptoentries: on |
3.1.1.109. nsslapd-ldapiuidnumbertype
Autobind can be used to authenticate system users to the server automatically and connect to the server using a UNIX socket. To map the system user to a Directory Server user for authentication, the system user’s UID and GUID numbers must be mapped to be a Directory Server attribute. The nsslapd-ldapiuidnumbertype attribute points to the Directory Server attribute to map system UIDs to user entries.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and nsslapd-ldapifilepath), autobind is enabled (nsslapd-ldapiautobind), and autobind mapping is enabled for regular users (nsslapd-ldapimaptoentries).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any Directory Server attribute |
| Default Value | uidNumber |
| Syntax | DirectoryString |
| Example | nsslapd-ldapiuidnumbertype: uidNumber |
3.1.1.110. nsslapd-ldifdir
Directory Server exports files in LDAP Data Interchange Format (LDIF) format to the directory set in this parameter when using the db2ldif or db2ldif.pl. The directory must be owned by the Directory Server user and group. Only this user and group must have read and write access in this directory.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any directory writable by the Directory Server user |
| Default Value | /var/lib/dirsrv/slapd-instance_name/ldif/ |
| Syntax | DirectoryString |
| Example | nsslapd-ldifdir: /var/lib/dirsrv/slapd-instance_name/ldif/ |
3.1.1.111. nsslapd-listen-backlog-size
This attribute sets the maximum of the socket connection backlog. The listen service sets the number of sockets available to receive incoming connections. The backlog setting sets a maximum length for how long the queue for the socket (sockfd) can grow before refusing connections.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | The maximum 64-bit integer value (9223372036854775807) |
| Default Value | 128 |
| Syntax | Integer |
| Example | nsslapd-listen-backlog-size: 128 |
3.1.1.112. nsslapd-listenhost (Listen to IP Address)
This attribute allows multiple Directory Server instances to run on a multihomed machine (or makes it possible to limit listening to one interface of a multihomed machine). There can be multiple IP addresses associated with a single hos tname, and these IP addresses can be a mix of both IPv4 and IPv6. This parameter can be used to restrict the Directory Server instance to a single IP interface.
If a host name is given as the nsslapd-listenhost value, then the Directory Server responds to requests for every interface associated with the host name. If a single IP interface (either IPv4 or IPv6) is given as the nsslapd-listenhost value, Directory Server only responds to requests sent to that specific interface. Either an IPv4 or IPv6 address can be used.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any local host name, IPv4 or IPv6 address |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-listenhost: ldap.example.com |
3.1.1.113. nsslapd-localhost (Local Host)
This attribute specifies the host machine on which the Directory Server runs. This attribute creates the referral URL that forms part of the MMR protocol. In a high-availability configuration with failover nodes, that referral should point to the virtual name of the cluster, not the local host name.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any fully qualified host name. |
| Default Value | Hostname of installed machine. |
| Syntax | DirectoryString |
| Example | nsslapd-localhost: phonebook.example.com |
3.1.1.114. nsslapd-localuser (Local User)
This attribute sets the user as whom the Directory Server runs. The group as which the user runs is derived from this attribute by examining the user’s primary group. Should the user change, then all of the instance-specific files and directories for this instance need to be changed to be owned by the new user, using a tool such as chown.
The value for the nsslapd-localuser is set initially when the server instance is configured.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid user |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-localuser: dirsrv |
3.1.1.115. nsslapd-lockdir (Server Lock File Directory)
This is the full path to the directory the server uses for lock files. The default value is /var/lock/dirsrv/slapd-instance. Changes to this value will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Absolute path to a directory owned by the server user ID with write access to the server ID |
| Default Value | /var/lock/dirsrv/slapd-instance |
| Syntax | DirectoryString |
| Example | nsslapd-lockdir: /var/lock/dirsrv/slapd-instance |
3.1.1.116. nsslapd-localssf
The nsslapd-localssf parameter sets the security strength factor (SSF) for LDAPI connections. Directory Server allows LDAPI connections only if the value set in nsslapd-localssf is greater or equal than the value set in the nsslapd-minssf parameter. Therefore, LDAPI connections meet the minimum SSF set in nsslapd-minssf.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32-bit integer value (2147483647) |
| Default Value | 71 |
| Syntax | Integer |
| Example | nsslapd-localssf: 71 |
3.1.1.117. nsslapd-logging-hr-timestamps-enabled (Enable or Disable High-resolution Log Timestamps)
Controls whether logs will use high resolution timestamps with nanosecond precision, or standard resolution timestamps with one second precision. Enabled by default. Set this option to off to revert log timestamps back to one second precision.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values |
|
| Default Value |
|
| Syntax | DirectoryString |
| Example | nsslapd-logging-hr-timestamps-enabled: on |
3.1.1.118. nsslapd-maxbersize (Maximum Message Size)
Defines the maximum size in bytes allowed for an incoming message. This limits the size of LDAP requests that can be handled by the Directory Server. Limiting the size of requests prevents some kinds of denial of service attacks.
The limit applies to the total size of the LDAP request. For example, if the request is to add an entry and if the entry in the request is larger than the configured value or the default, then the add request is denied. However, the limit is not applied to replication processes. Be cautious before changing this attribute.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 - 2 gigabytes (2,147,483,647 bytes)
Zero |
| Default Value | 2097152 |
| Syntax | Integer |
| Example | nsslapd-maxbersize: 2097152 |
3.1.1.119. nsslapd-maxdescriptors (Maximum File Descriptors)
This attribute sets the maximum, platform-dependent number of file descriptors that the Directory Server tries to use. A file descriptor is used whenever a client connects to the server. File descriptors are also used by access logs, error logs, audit logs, database files (indexes and transaction logs), and as sockets for outgoing connections to other servers for replication and chaining.
The number of descriptors available for TCP/IP to serve client connections is determined by the nsslapd-conntablesize attribute. The default value for this attribute is set to the file descriptor soft limit, which defaults to 1024. However, if you configure this attribute manually, the server updates the process file descriptor soft limit to match.
If this value is set too high, the Directory Server queries the operating system for the maximum allowable value, and then uses that value. It also issues an information message in the error log. If this value is set to an invalid value remotely, by using the Directory Server Console or ldapmodify, the server rejects the new value, keeps the old value, and responds with an error.
Some operating systems let users configure the number of file descriptors available to a process. See the operating system documentation for details on file descriptor limits and configuration. The dsktune program (explained in the Red Hat Directory Server Installation Guide) can be used to suggest changes to the system kernel or TCP/IP tuning attributes, including increasing the number of file descriptors if necessary. Increased the value on this attribute if the Directory Server is refusing connections because it is out of file descriptors. When this occurs, the following message is written to the Directory Server’s error log file:
Not listening for new connections -- too many fds open
See Section 3.1.1.62, “nsslapd-conntablesize” for more information about increasing the number of incoming connections.
UNIX shells usually have configurable limits on the number of file descriptors. See the operating system documentation for further information about limit and ulimit, as these limits can often cause problems.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 65535 |
| Default Value | 4096 |
| Syntax | Integer |
| Example | nsslapd-maxdescriptors: 4096 |
3.1.1.120. nsslapd-maxsasliosize (Maximum SASL Packet Size)
When a user is authenticated to the Directory Server over SASL GSS-API, the server must allocate a certain amount of memory to the client to perform LDAP operations, according to how much memory the client requests. It is possible for an attacker to send such a large packet size that it crashes the Directory Server or ties it up indefinitely as part of a denial of service attack.
The packet size which the Directory Server will allow for SASL clients can be limited using the nsslapd-maxsasliosize attribute. This attribute sets the maximum allowed SASL IO packet size that the server will accept.
When an incoming SASL IO packet is larger than the nsslapd-maxsasliosize limit, the server immediately disconnects the client and logs a message to the error log, so that an administrator can adjust the setting if necessary.
This attribute value is specified in bytes.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | * -1 (unlimited) to the maximum 32-bit integer value (2147483647) on 32-bit systems * -1 (unlimited) to the maximum 64-bit integer value (9223372036854775807) on 64-bit systems |
| Default Value | 2097152 (2MB) |
| Syntax | Integer |
| Example | nsslapd-maxsasliosize: 2097152 |
3.1.1.121. nsslapd-maxthreadsperconn (Maximum Threads per Connection)
Defines the maximum number of threads that a connection should use. For normal operations where a client binds and only performs one or two operations before unbinding, use the default value. For situations where a client binds and simultaneously issues many requests, increase this value to allow each connection enough resources to perform all the operations. This attribute is not available from the server console.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to maximum threadnumber |
| Default Value | 5 |
| Syntax | Integer |
| Example | nsslapd-maxthreadsperconn: 5 |
3.1.1.122. nsslapd-minssf
A security strength factor is a relative measurement of how strong a connection is according to its key strength. The SSF determines how secure an TLS or SASL connection is. The nsslapd-minssf attribute sets a minimum SSF requirement for any connection to the server; any connection attempts that are weaker than the minimum SSF are rejected.
TLS and SASL connections can be mixed in a connection to the Directory Server. These connections generally have different SSFs. The higher of the two SSFs is used to compare to the minimum SSF requirement.
Setting the SSF value to 0 means that there is no minimum setting.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any positive integer |
| Default Value | 0 (off) |
| Syntax | DirectoryString |
| Example | nsslapd-minssf: 128 |
3.1.1.123. nsslapd-minssf-exclude-rootdse
A security strength factor is a relative measurement of how strong a connection is according to its key strength. The SSF determines how secure an TLS or SASL connection is.
The nsslapd-minssf-exclude-rootdse attribute sets a minimum SSF requirement for any connection to the server except for queries for the root DSE. This enforces appropriate SSF values for most connections, while still allowing clients to get required information about the server configuration from the root DSE without having to establish a secure connection first.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any positive integer |
| Default Value | 0 (off) |
| Syntax | DirectoryString |
| Example | nsslapd-minssf-exclude-rootdse: 128 |
3.1.1.124. nsslapd-moddn-aci
This parameter controls the ACI checks when directory entries are moved from one subtree to another and using source and target restrictions in moddn operations. For backward compatibility, you can disable the ACI checks.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-moddn-aci: on |
3.1.1.125. nsslapd-malloc-mmap-threshold
If a Directory Server instance is started as a service using the systemctl utility, environment variables are not passed to the server unless you set them in the /etc/sysconfig/dirsrv or /etc/sysconfig/dirsrv-instance_name file. For further details, see the systemd.exec(3) man page.
Instead of manually editing the service files to set the M_MMAP_THRESHOLD environment variable, the nsslapd-malloc-mmap-threshold parameter enables you to set the value in the Directory Server configuration. For further details, see the M_MMAP_THRESHOLD parameter description in the mallopt(3) man page.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 - 33554432 |
| Default Value |
See the |
| Syntax | Integer |
| Example | nsslapd-malloc-mmap-threshold: 33554432 |
3.1.1.126. nsslapd-malloc-mxfast
If a Directory Server instance is started as a service using the systemctl utility, environment variables are not passed to the server unless you set them in the /etc/sysconfig/dirsrv or /etc/sysconfig/dirsrv-instance_name file. For further details, see the systemd.exec(3) man page.
Instead of manually editing the service files to set the M_MXFAST environment variable, the nsslapd-malloc-mxfast parameter enables you to set the value in the Directory Server configuration. For further details, see the M_MXFAST parameter description in the mallopt(3) man page.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 - 80 * (sizeof(size_t) / 4) |
| Default Value |
See the |
| Syntax | Integer |
| Example | nsslapd-malloc-mxfast: 1048560 |
3.1.1.127. nsslapd-malloc-trim-threshold
If a Directory Server instance is started as a service using the systemctl utility, environment variables are not passed to the server unless you set them in the /etc/sysconfig/dirsrv or /etc/sysconfig/dirsrv-instance_name file. For further details, see the systemd.exec(3) man page.
Instead of manually editing the service files to set the M_TRIM_THRESHOLD environment variable, the nsslapd-malloc-trim-threshold parameter enables you to set the value in the Directory Server configuration. For further details, see the M_TRIM_THRESHOLD parameter description in the mallopt(3) man page.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 2^31-1 |
| Default Value |
See the |
| Syntax | Integer |
| Example | nsslapd-malloc-trim-threshold: 131072 |
3.1.1.128. nsslapd-nagle
When the value of this attribute is off, the TCP_NODELAY option is set so that LDAP responses (such as entries or result messages) are sent back to a client immediately. When the attribute is turned on, default TCP behavior applies; specifically, sending data is delayed so that additional data can be grouped into one packet of the underlying network MTU size, typically 1500 bytes for Ethernet.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-nagle: off |
3.1.1.129. nsslapd-ndn-cache-enabled
Normalizing distinguished names (DN) is a resource intensive task. If the nsslapd-ndn-cache-enabled parameter is enabled, Directory Server caches normalized DNs in memory. Update the nsslapd-ndn-cache-max-size parameter to set the maximum size of this cache.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ndn-cache-enabled: on |
3.1.1.130. nsslapd-ndn-cache-max-size
Normalizing distinguished names (DN) is a resource intensive task. If the nsslapd-ndn-cache-enabled parameter is enabled, Directory Server caches normalized DNs in memory. The nsslapd-ndn-cache-max-size parameter sets the maximum size of this cache.
If a DN requested is not cached already, it is normalized and added. When the cache size limit is exceeded, Directory Server removes the least recently used 10,000 DNs from the cache. However, a minimum of 10,000 DNs is always kept cached.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32-bit integer value (2147483647) |
| Default Value | 20971520 |
| Syntax | Integer |
| Example | nsslapd-ndn-cache-max-size: 20971520 |
3.1.1.131. nsslapd-outbound-ldap-io-timeout
This attribute limits the I/O wait time for all outbound LDAP connections. The default is 300000 milliseconds (5 minutes). A value of 0 means that the server does not impose a limit on I/O wait time.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to the maximum 32-bit integer value (2147483647) |
| Default Value | 300000 |
| Syntax | DirectoryString |
| Example | nsslapd-outbound-ldap-io-timeout: 300000 |
3.1.1.132. nsslapd-pagedsizelimit (Size Limit for Simple Paged Results Searches)
This attribute sets the maximum number of entries to return from a search operation specifically which uses the simple paged results control. This overrides the nsslapd-sizelimit attribute for paged searches.
If this value is set to zero, then the nsslapd-sizelimit attribute is used for paged searches as well as non-paged searches.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsslapd-pagedsizelimit: 10000 |
3.1.1.133. nsslapd-plug-in
This read-only attribute lists the DNs of the plug-in entries for the syntax and matching rule plug-ins loaded by the server.
3.1.1.134. nsslapd-plugin-binddn-tracking
Sets the bind DN used for an operation as the modifier of an entry, even if the operation itself was initiated by a server plug-in. The specific plug-in which performed the operation is listed in a separate operational attribute, internalModifiersname.
One change can trigger other, automatic changes in the directory tree. When a user is deleted, for example, that user is automatically removed from any groups it belonged to by the Referential Integrity Plug-in. The initial deletion of the user is performed by whatever user account is bound to the server, but the updates to the groups (by default) are shown as being performed by the plug-in, with no information about which user initiated that update. The nsslapd-plugin-binddn-tracking attribute allows the server to track which user originated an update operation, as well as the internal plug-in which actually performed it. For example:
dn: cn=my_group,ou=groups,dc=example,dc=com modifiersname: uid=jsmith,ou=people,dc=example,dc=com internalModifiersname: cn=referential integrity plugin,cn=plugins,cn=config
This attribute is disabled by default.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-plugin-binddn-tracking: on |
3.1.1.135. nsslapd-plugin-logging
By default, even if access logging is set to record internal operations, plug-in internal operations are not logged in the access log file. Instead of enabling the logging in each plug-in’s configuration, you can control it globally with this parameter.
When enabled, plug-ins use this global setting and log access and audit events if enabled.
If nsslapd-plugin-logging is enabled and nsslapd-accesslog-level is set to record internal operations, unindexed searches and other internal operations are logged into the access log file.
In case nsslapd-plugin-logging is not set, unindexed searches from plug-ins are still logged in the Directory Server error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-plugin-logging: off |
3.1.1.136. nsslapd-port (Port Number)
This attribute gives the TCP/IP port number used for standard LDAP communications. To run TLS over this port, use the Start TLS extended operation. This selected port must be unique on the host system; make sure no other application is attempting to use the same port number. Specifying a port number of less than 1024 means the Directory Server has to be started as root.
The server sets its uid to the nsslapd-localuser value after startup. When changing the port number for a configuration directory, the corresponding server instance entry in the configuration directory must be updated.
The server has to be restarted for the port number change to be taken into account.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 65535 |
| Default Value | 389 |
| Syntax | Integer |
| Example | nsslapd-port: 389 |
Set the port number to zero (0) to disable the LDAP port if the LDAPS port is enabled.
3.1.1.137. nsslapd-privatenamespaces
This read-only attribute contains the list of the private naming contexts cn=config, cn=schema, and cn=monitor.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | cn=config, cn=schema, and cn=monitor |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-privatenamespaces: cn=config |
3.1.1.138. nsslapd-pwpolicy-inherit-global (Inherit Global Password Syntax)
When the fine-grained password syntax is not set, new or updated passwords are not checked even though the global password syntax is configured. To inherit the global fine-grained password syntax, set this attribute to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-pwpolicy-inherit-global: off |
3.1.1.139. nsslapd-pwpolicy-local (Enable Subtree- and User-Level Password Policy)
Turns fine-grained (subtree- and user-level) password policy on and off.
If this attribute has a value of off, all entries (except for cn=Directory Manager) in the directory are subjected to the global password policy; the server ignores any defined subtree/user level password policy.
If this attribute has a value of on, the server checks for password policies at the subtree- and user-level and enforce those policies.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-pwpolicy-local: off |
3.1.1.140. nsslapd-readonly (Read Only)
This attribute sets whether the whole server is in read-only mode, meaning that neither data in the databases nor configuration information can be modified. Any attempt to modify a database in read-only mode returns an error indicating that the server is unwilling to perform the operation.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-readonly: off |
3.1.1.141. nsslapd-referral (Referral)
This multi-valued attribute specifies the LDAP URLs to be returned by the suffix when the server receives a request for an entry not belonging to the local tree; that is, an entry whose suffix does not match the value specified on any of the suffix attributes. For example, assume the server contains only entries:
ou=People,dc=example,dc=com
but the request is for this entry:
ou=Groups,dc=example,dc=com
In this case, the referral would be passed back to the client in an attempt to allow the LDAP client to locate a server that contains the requested entry. Although only one referral is allowed per Directory Server instance, this referral can have multiple values.
To use TLS communications, the referral attribute should be in the form ldaps://server-location.
Start TLS does not support referrals.
For more information on managing referrals, see the "Configuring Directory Databases" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-referral: ldap://ldap.example.com/dc=example,dc=com |
3.1.1.142. nsslapd-referralmode (Referral Mode)
When set, this attribute sends back the referral for any request on any suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-referralmode: ldap://ldap.example.com |
3.1.1.143. nsslapd-require-secure-binds
This parameter requires that a user authenticate to the directory over a protected connection such as TLS, StartTLS, or SASL, rather than a regular connection.
This only applies to authenticated binds. Anonymous binds and unauthenticated binds can still be completed over a standard channel, even if nsslapd-require-secure-binds is turned on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-require-secure-binds: on |
3.1.1.144. nsslapd-requiresrestart
This parameter lists what other core configuration attributes require that the server be restarted after a modification. This means that if any attribute listed in nsslapd-requiresrestart is changed, the new setting does not take effect until after the server is restarted. The list of attributes can be returned in an ldapsearch:
ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -b "cn=config" -s sub -x "(objectclass=*)" | grep nsslapd-requiresrestart
This attribute is multi-valued.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any core server configuration attribute |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-requiresrestart: nsslapd-cachesize |
3.1.1.145. nsslapd-reservedescriptors (Reserved File Descriptors)
This attribute specifies the number of file descriptors that Directory Server reserves for managing non-client connections, such as index management and managing replication. The number of file descriptors that the server reserves for this purpose subtracts from the total number of file descriptors available for servicing LDAP client connections (See Section 3.1.1.119, “nsslapd-maxdescriptors (Maximum File Descriptors)”).
Most installations of Directory Server should never need to change this attribute. However, consider increasing the value on this attribute if all of the following are true:
- The server is replicating to a large number of consumer servers (more than 10), or the server is maintaining a large number of index files (more than 30).
- The server is servicing a large number of LDAP connections.
- There are error messages reporting that the server is unable to open file descriptors (the actual error message differs depending on the operation that the server is attempting to perform), but these error messages are not related to managing client LDAP connections.
Increasing the value on this attribute may result in more LDAP clients being unable to access the directory. Therefore, the value on this attribute is increased, also increase the value on the nsslapd-maxdescriptors attribute. It may not be possible to increase the nsslapd-maxdescriptors value if the server is already using the maximum number of file descriptors that the operating system allows a process to use; see the operating system documentation for details. If this is the case, then reduce the load on the server by causing LDAP clients to search alternative directory replicas. See Section 3.1.1.62, “nsslapd-conntablesize” for information about file descriptor usage for incoming connections.
To assist in computing the number of file descriptors set for this attribute, use the following formula:
nsslapd-reservedescriptor = 20 + (NldbmBackends * 4) + NglobalIndex + ReplicationDescriptor + ChainingBackendDescriptors + PTADescriptors + SSLDescriptors
- NldbmBackends is the number of ldbm databases.
- NglobalIndex is the total number of configured indexes for all databases including system indexes. (By default 8 system indexes and 17 additional indexes per database).
- ReplicationDescriptor is eight (8) plus the number of replicas in the server that can act as a supplier or hub (NSupplierReplica).
-
ChainingBackendDescriptors is NchainingBackend times the nsOperationConnectionsLimit (a chaining or database link configuration attribute;
10by default). -
PTADescriptors is
3if PTA is configured and0if PTA is not configured. -
SSLDescriptors is
5(4 files + 1 listensocket) if TLS is configured and0if TLS is not configured.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 65535 |
| Default Value | 64 |
| Syntax | Integer |
| Example | nsslapd-reservedescriptors: 64 |
3.1.1.146. nsslapd-return-exact-case (Return Exact Case)
Returns the exact case of attribute type names as requested by the client. Although LDAPv3-compliant clients must ignore the case of attribute names, some client applications require attribute names to match exactly the case of the attribute as it is listed in the schema when the attribute is returned by the Directory Server as the result of a search or modify operation. However, most client applications ignore the case of attributes; therefore, by default, this attribute is disabled. Do not modify it unless there are legacy clients that can check the case of attribute names in results returned from the server.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-return-exact-case: off |
3.1.1.147. nsslapd-rewrite-rfc1274
This attribute is deprecated and will be removed in a later version.
This attribute is used only for LDAPv2 clients that require attribute types to be returned with their RFC 1274 names. Set the value to on for those clients. The default is off.
3.1.1.148. nsslapd-rootdn (Manager DN)
This attribute sets the distinguished name (DN) of an entry that is not subject to access control restrictions, administrative limit restrictions for operations on the directory, or resource limits in general. There does not have to be an entry corresponding to this DN, and by default there is not an entry for this DN, thus values like cn=Directory Manager are acceptable.
For information on changing the root DN, see the "Creating Directory Entries" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid distinguished name |
| Default Value | |
| Syntax | DN |
| Example | nsslapd-rootdn: cn=Directory Manager |
3.1.1.149. nsslapd-rootpw (Root Password)
This attribute sets the password associated with the Manager DN. When the root password is provided, it is encrypted according to the encryption method selected for the nsslapd-rootpwstoragescheme attribute. When viewed from the server console, this attribute shows the value *. When viewed from the dse.ldif file, this attribute shows the encryption method followed by the encrypted string of the password. The example shows the password as displayed in the dse.ldif file, not the actual password.
When the root DN is configred at server setup, a root password is required. However, it is possible for the root password to be deleted from dse.ldif by directly editing the file. In this situation, the root DN can only obtain the same access to the directory is allowed for anonymous access. Always make sure that a root password is defined in dse.ldif when a root DN is configured for the database. The pwdhash command-line utility can create a new root password. For more information, see Section 9.6, “pwdhash”.
When resetting the Directory Manager’s password from the command line, do not use curly braces ({}) in the password. The root password is stored in the format {password-storage-scheme}hashed_password. Any characters in curly braces are interpreted by the server as the password storage scheme for the root password. If that text is not a valid storage scheme or if the password that follows is not properly hashed, then the Directory Manager cannot bind to the server.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid password, encrypted by any one of the encryption methods which are described in Section 4.1.43, “Password Storage Schemes”. |
| Default Value | |
| Syntax | DirectoryString {encryption_method }encrypted_Password |
| Example | nsslapd-rootpw: {SSHA}9Eko69APCJfF |
3.1.1.150. nsslapd-rootpwstoragescheme (Root Password Storage Scheme)
This attribute sets the method used to encrypt the Directory Server’s manager password stored in the nsslapd-rootpw attribute. For further details, such as recommended strong password storage schemes, see Section 4.1.43, “Password Storage Schemes”.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | PBKDF2_SHA256 |
| Syntax | DirectoryString |
| Example | nsslapd-rootpwstoragescheme: PBKDF2_SHA256 |
3.1.1.151. nsslapd-rundir
This parameter sets the absolute path to the directory in which Directory Server stores run-time information, such as the PID file. The directory must be owned by the Directory Server user and group. Only this user and group must have read and write access in this directory.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any directory writable by the Directory Server user |
| Default Value | /var/run/dirsrv/ |
| Syntax | DirectoryString |
| Example | nsslapd-rundir: /var/run/dirsrv/ |
3.1.1.152. nsslapd-sasl-mapping-fallback
By default, only first matching SASL mapping is checked. If this mapping fails, the bind operation will fail even if there are other matching mappings that might have worked. SASL mapping fallback will keep checking all of the matching mappings.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-sasl-mapping-fallback: off |
3.1.1.153. nsslapd-sasl-max-buffer-size
This attribute sets the maximum SASL buffer size.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 67108864 (64 kilobytes) |
| Syntax | Integer |
| Example | nsslapd-sasl-max-buffer-size: 67108864 |
3.1.1.154. nsslapd-saslpath
Sets the absolute path to the directory containing the Cyrus-SASL SASL2 plug-ins. Setting this attribute allows the server to use custom or non-standard SASL plug-in libraries. This is usually set correctly during installation, and Red Hat strongly recommends not changing this attribute. If the attribute is not present or the value is empty, this means the Directory Server is using the system provided SASL plug-in libraries which are the correct version.
If this parameter is set, the server uses the specified path for loading SASL plug-ins. If this parameter is not set, the server uses the SASL_PATH environment variable. If neither nsslapd-saslpath or SASL_PATH are set, the server attempts to load SASL plug-ins from the default location, /usr/lib/sasl2.
Changes made to this attribute will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Path to plug-ins directory. |
| Default Value | Platform dependent |
| Syntax | DirectoryString |
| Example | nsslapd-saslpath: /usr/lib/sasl2 |
3.1.1.155. nsslapd-schema-ignore-trailing-spaces (Ignore Trailing Spaces in Object Class Names)
Ignores trailing spaces in object class names. By default, the attribute is turned off. If the directory contains entries with object class values that end in one or more spaces, turn this attribute on. It is preferable to remove the trailing spaces because the LDAP standards do not allow them.
For performance reasons, server restart is required for changes to take effect.
An error is returned by default when object classes that include trailing spaces are added to an entry. Additionally, during operations such as add, modify, and import (when object classes are expanded and missing superiors are added) trailing spaces are ignored, if appropriate. This means that even when nsslapd-schema-ignore-trailing-spaces is on, a value such as top is not added if top is already there. An error message is logged and returned to the client if an object class is not found and it contains trailing spaces.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-schema-ignore-trailing-spaces: on |
3.1.1.156. nsslapd-schemacheck (Schema Checking)
This attribute sets whether the database schema is enforced when entries are added or modified. When this attribute has a value of on, Directory Server will not check the schema of existing entries until they are modified. The database schema defines the type of information allowed in the database. The default schema can be extended using the object classes and attribute types. For information on how to extend the schema using the Directory Server Console, see the "Extending the Directory Schema" chapter in the Red Hat Directory Server Administration Guide.
Red Hat strongly discourages turning off schema checking. This can lead to severe interoperability problems. This is typically used for very old or non-standard LDAP data that must be imported into the Directory Server. If there are not a lot of entries that have this problem, consider using the extensibleObject object class in those entries to disable schema checking on a per entry basis.
Schema checking works by default when database modifications are made using an LDAP client, such as ldapmodify or when importing a database from LDIF using ldif2db. If schema checking is turned off, every entry has to be verified manually to see that they conform to the schema. If schema checking is turned on, the server sends an error message listing the entries which do not match the schema. Ensure that the attributes and object classes created in the LDIF statements are both spelled correctly and identified in dse.ldif. Either create an LDIF file in the schema directory or add the elements to 99user.ldif.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-schemacheck: on |
3.1.1.157. nsslapd-schemadir
This is the absolute path to the directory containing the Directory Server instance-specific schema files. When the server starts up, it reads the schema files from this directory, and when the schema is modified through LDAP tools, the schema files in this directory are updated. This directory must be owned by the server user ID, and that user must have read and write permissions to the directory.
Changes made to this attribute will not take effect until the server is restarted.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid path |
| Default Value | /etc/dirsrv/instance_name/schema |
| Syntax | DirectoryString |
| Example | nsslapd-schemadir: /etc/dirsrv/instance_name/schem |
3.1.1.158. nsslapd-schemamod
Online schema modifications require a lock protection that are impacting the performance. If schema modifications are disabled, setting this parameter to off can increase the performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-schemamod: on |
3.1.1.159. nsslapd-schemareplace
Determines whether modify operations that replace attribute values are allowed on the cn=schema entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off | replication-only |
| Default Value | replication-only |
| Syntax | DirectoryString |
| Example | nsslapd-schemareplace: replication-only |
3.1.1.160. nsslapd-search-return-original-type-switch
If the attribute list passed to a search contains a space followed by other characters, the same string is returned to the client. For example:
# ldapsearch -b <basedn> "(filter)" "sn someothertext" dn: <matched dn> sn someothertext: <sn>
This behavior is disabled by default, but can be enabled using this configuration parameter.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-search-return-type-switch: off |
3.1.1.161. nsslapd-securelistenhost
This attribute allows multiple Directory Server instances to run on a multihomed machine (or makes it possible to limit listening to one interface of a multihomed machine). There can be multiple IP addresses associated with a single host name, and these IP addresses can be a mix of both IPv4 and IPv6. This parameter can be used to restrict the Directory Server instance to a single IP interface; this parameter also specifically sets what interface to use for TLS traffic rather than regular LDAP connections.
If a host name is given as the nsslapd-securelistenhost value, then the Directory Server responds to requests for every interface associated with the host name. If a single IP interface (either IPv4 or IPv6) is given as the nsslapd-securelistenhost value, Directory Server only responds to requests sent to that specific interface. Either an IPv4 or IPv6 address can be used.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any secure host name, IPv4 or IPv6 address |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-securelistenhost: ldaps.example.com |
3.1.1.162. nsslapd-securePort (Encrypted Port Number)
This attribute sets the TCP/IP port number used for TLS communications. This selected port must be unique on the host system; make sure no other application is attempting to use the same port number. Specifying a port number of less than 1024 requires that Directory Server be started as root. The server sets its uid to the nsslapd-localuser value after startup.
The server only listens to this port if it has been configured with a private key and a certificate, and nsslapd-security is set to on; otherwise, it does not listen on this port.
The server has to be restarted for the port number change to be taken into account.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 65535 |
| Default Value | 636 |
| Syntax | Integer |
| Example | nsslapd-securePort: 636 |
3.1.1.163. nsslapd-security (Security)
This attribute sets whether the Directory Server is to accept TLS communications on its encrypted port. This attribute should be set to on for secure connections. To run with security on, the server must be configured with a private key and server certificate in addition to the other TLS configuration.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-security: off |
3.1.1.164. nsslapd-sizelimit (Size Limit)
This attribute sets the maximum number of entries to return from a search operation. If this limit is reached, ns-slapd returns any entries it has located that match the search request, as well as an exceeded size limit error.
When no limit is set, ns-slapd returns every matching entry to the client regardless of the number found. To set a no limit value whereby the Directory Server waits indefinitely for the search to complete, specify a value of -1 for this attribute in the dse.ldif file.
This limit applies to everyone, regardless of their organization.
A value of -1 on this attribute in dse.ldif file is the same as leaving the attribute blank in the server console, in that it causes no limit to be used. This cannot have a null value in dse.ldif file, as it is not a valid integer. It is possible to set it to 0, which returns size limit exceeded for every search.
The corresponding user-level attribute is nsSizeLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) |
| Default Value | 2000 |
| Syntax | Integer |
| Example | nsslapd-sizelimit: 2000 |
3.1.1.165. nsslapd-snmp-index
This parameter controls the SNMP index number of the Directory Server instance.
If you have multiple Directory Server instances on the same host listening all on port 389 but on different network interfaces, this parameter allows you to set different SNMP index numbers for each instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-snmp-index: 0 |
3.1.1.166. nsslapd-SSLclientAuth
The nsslapd-SSLclientAuth parameter will be deprecated in a future release and is currently maintained for backward compatibility. Use the new parameter nsSSLClientAuth, stored under cn=encryption,cn=config, instead. See Section 3.1.4.5, “nsSSLClientAuth”.
3.1.1.167. nsslapd-ssl-check-hostname (Verify Hostname for Outbound Connections)
This attribute sets whether an TLS-enabled Directory Server should verify authenticity of a request by matching the host name against the value assigned to the common name (cn) attribute of the subject name (subjectDN field) in the certificate being presented. By default, the attribute is set to on. If it is on and if the host name does not match the cn attribute of the certificate, appropriate error and audit messages are logged.
For example, in a replicated environment, messages similar to the following are logged in the supplier server’s log files if it finds that the peer server’s host name does not match the name specified in its certificate:
[DATE] - SSL alert: ldap_sasl_bind("",LDAP_SASL_EXTERNAL) 81 (Netscape runtime error -12276 -
Unable to communicate securely with peer: requested domain name does not
match the server's certificate.)
[DATE] NSMMReplicationPlugin - agmt="cn=SSL Replication Agreement to host1" (host1.example.com:636):
Replication bind with SSL client authentication failed:
LDAP error 81 (Can't contact LDAP server)Red Hat recommends turning this attribute on to protect Directory Server’s outbound TLS connections against a man in the middle (MITM) attack.
DNS and reverse DNS must be set up correctly in order for this to work; otherwise, the server cannot resolve the peer IP address to the host name in the subject DN in the certificate.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsslapd-ssl-check-hostname: on |
3.1.1.168. nsslapd-syntaxcheck
This attribute validates all modifications to entry attributes to make sure that the new or changed values conform to the required syntax for that attribute type. Any changes which do not conform to the proper syntax are rejected, when this attribute is enabled. All attribute values are validated against the syntax definitions in RFC 4514.
By default, this is turned on.
Syntax validation is only run against new or modified attributes; it does not validate the syntax of existing attribute values. Syntax validation is triggered for LDAP operations such as adds and modifies; it does not happen after operations like replication, since the validity of the attribute syntax should be checked on the originating supplier.
This validates all supported attribute types for Directory Server, with the exception of binary syntaxes (which cannot be verified) and non-standard syntaxes, which do not have a defined required format. The unvalidated syntaxes are as follows:
- Fax (binary)
- OctetString (binary)
- JPEG (binary)
- Binary (non-standard)
- Space Insensitive String (non-standard)
- URI (non-standard)
The nsslapd-syntaxcheck attribute sets whether to validate and reject attribute modifications. This can be used with the Section 3.1.1.169, “nsslapd-syntaxlogging” attribute to write warning messages about invalid attribute values to the error logs.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nnsslapd-syntaxcheck: on |
3.1.1.169. nsslapd-syntaxlogging
This attribute sets whether to log syntax validation failures to the errors log. By default, this is turned off.
If the Section 3.1.1.168, “nsslapd-syntaxcheck” attribute is enabled (the default) and the nsslapd-syntaxlogging attribute is also enabled, then any invalid attribute change is rejected and written to the errors log. If only nsslapd-syntaxlogging is enabled and nsslapd-syntaxcheck is disabled, then invalid changes are allowed to proceed, but a warning message is written to the error log.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nnsslapd-syntaxlogging: off |
3.1.1.170. nsslapd-threadnumber (Thread Number)
This performance tuning-related value sets the number of threads, Directory Server creates at startup. If the value is set to -1 (default), Directory Server enables the optimized auto-tuning based on the available hardware. Note that if auto-tuning is enabled, the nsslapd-threadnumber shows the auto-generated number of threads while Directory Server is running.
Red Hat recommends to use the auto-tuning setting for optimized performance.
For further details, see the corresponding section in the Red Hat Directory Server Performance Tuning Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum number of threads supported by the system’s thread and processor. limits |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsslapd-threadnumber: -1 |
3.1.1.171. nsslapd-timelimit (Time Limit)
This attribute sets the maximum number of seconds allocated for a search request. If this limit is reached, Directory Server returns any entries it has located that match the search request, as well as an exceeded time limit error.
When no limit is set, ns-slapd returns every matching entry to the client regardless of the time it takes. To set a no limit value whereby Directory Server waits indefinitely for the search to complete, specify a value of -1 for this attribute in the dse.ldif file. A value of zero (0) causes no time to be allowed for searches. The smallest time limit is 1 second.
A value of -1 on this attribute in thedse.ldif is the same as leaving the attribute blank in the server console in that it causes no limit to be used. However, a negative integer cannot be set in this field in the server console, and a null value cannot be used in the dse.ldif entry, as it is not a valid integer.
The corresponding user-level attribute is nsTimeLimit.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | -1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 3600 |
| Syntax | Integer |
| Example | nsslapd-timelimit: 3600 |
3.1.1.172. nsslapd-tmpdir
This is the absolute path of the directory the server uses for temporary files. The directory must be owned by the server user ID and the user must have read and write access. No other user ID should have read or write acces to the directory. The default value is /tmp.
Changes made to this attribute will not take effect until the server is restarted.
3.1.1.173. nsslapd-unhashed-pw-switch
When you update the userPassword attribute, Directory Server encrypts the password and stores it in userPassword. However, in certain situations, for example, when synchronizing passwords with Active Directory (AD), Directory Server must pass the unencrypted password to a plug-in. In this case, the server stores the unencrypted password in the temporary unhashed#user#password attribute in the so-called entry extension and, depending on the scenario, also in the changelog. Note that Directory Server does not store the temporary unhashed#user#password attribute on the server’s hard disk.
The nsslapd-unhashed-pw-switch parameter controls whether and how Directory Server stores the unencrypted password. For example, you must set nsslapd-unhashed-pw-switch to on to synchronize passwords from Directory Server to Active Directory.
You can set the parameter to one of the following values:
-
off: Directory Server neither stores the unencrypted password in the entry extension nor in the changelog. Set this value if you do not use password synchronization with AD or any plug-ins that requires access to the unencrypted password. -
on: Directory Server stores the unencrypted password in the entry extension and in the changelog. Set this value if you configure password synchronization with AD. -
nolog: Directory Server stores the unencrypted password only in the entry extension but not in the changelog. Set this value if local Directory Server plug-ins require access to the unencrypted password, but no password synchronization with AD is configured.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | off | on | nolog |
| Default Value | off |
| Syntax | DirectoryString |
| Example | nsslapd-unhashed-pw-switch: off |
3.1.1.174. nsslapd-validate-cert
If the Directory Server is configured to run in TLS and its certificate expires, then the Directory Server cannot be started. The nsslapd-validate-cert parameter sets how the Directory Server should respond when it attempts to start with an expired certificate:
-
warnallows the Directory Server to start successfully with an expired certificate, but it sends a warning message that the certificate has expired. This is the default setting. -
onvalidates the certificate and will prevent the server from restarting if the certificate is expired. This sets a hard failure for expired certificates. -
offdisables all certificate expiration validation, so the server can start with an expired certificate without logging a warning.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | warn | on | off |
| Default Value | warn |
| Syntax | DirectoryString |
| Example | nsslapd-validate-cert: warn |
3.1.1.175. nsslapd-verify-filter-schema
The nsslapd-verify-filter-schema parameter defines how Directory Server verifies search filters with attributes that are not specified in the schema.
You can set nsslapd-verify-filter-schema to one of the following options:
-
reject-invalid: Directory Server rejects the filter with an error if it contains any unknown element. process-safe: Directory Server replaces unknown components with an empty set, and logs a warning with thenotes=Fflag in the/var/log/dirsrv/slapd-instance_name/accesslog file.Before you switch
nsslapd-verify-filter-schemafromwarn-invalidorofftoprocess-safe, monitor the access log and fix queries from applications that cause log entries withnotes=Fflag. Otherwise, the operation result changes and Directory Server might not return all the matching entries.-
warn-invalid: Directory Server logs a warning with thenotes=Fflag in the/var/log/dirsrv/slapd-instance_name/accesslog file, and continues scanning the full database. -
off: Directory Server does not verify filters.
Note that, for example, if you set nsslapd-verify-filter-schema to warn-invalid or off, a filter, such as (&(non_exististent_attribute=example)(uid=user_name)) evaluates the uid=user_name entry and returns it only if it contains contains non_exististent_attribute=example. If you set nsslapd-verify-filter-schema to process-safe, Directory Server does not evaluate that entry and does not return it.
Setting nsslapd-verify-filter-schema to reject-invalid or process-safe can prevent high load due to unindexed searches for attributes that are not specified in the schema.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | reject-invalid, process-safe, warn-invalid, off |
| Default Value | warn-invalid |
| Syntax | DirectoryString |
| Example | nsslapd-verify-filter-schema: warn-invalid |
3.1.1.176. nsslapd-versionstring
This attribute sets the server version number. The build data is automatically appended when the version string is displayed.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any valid server version number. |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-versionstring: Red Hat-Directory/11.3 |
3.1.1.177. nsslapd-workingdir
This is the absolute path of the directory that the server uses as its current working directory after startup. This is the value that the server would return as the value of the getcwd() function, and the value that the system process table shows as its current working directory. This is the directory a core file is generated in. The server user ID must have read and write access to the directory, and no other user ID should have read or write access to it. The default value for this attribute is the same directory containing the error log, which is usually /var/log/dirsrv/slapd-instance.
Changes made to this attribute will not take effect until the server is restarted.
3.1.1.178. passwordAllowChangeTime
This attribute specifies the length of time that must pass before the user is allowed to change his password.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any integer |
| Default Value | |
| Syntax | DirectoryString |
| Example | passwordAllowChangeTime: 5h |
3.1.1.179. passwordChange (Password Change)
Indicates whether users may change their passwords.
This can be abbreviated to pwdAllowUserChange.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | passwordChange: on |
3.1.1.180. passwordCheckSyntax (Check Password Syntax)
This attribute sets whether the password syntax is checked before the password is saved. The password syntax checking mechanism checks that the password meets or exceeds the password minimum length requirement and that the string does not contain any trivial words, such as the user’s name or user ID or any attribute value stored in the uid, cn, sn, givenName, ou, or mail attributes of the user’s directory entry.
Password syntax includes several different categories for checking:
- The length of string or tokens to use to compare when checking for trivial words in the password (for example, if the token length is three, then no string of three sequential characters in the user’s UID, name, email address, or other parameters can be used in the password)
- Minimum number of number characters (0-9)
- Minimum number of uppercase ASCII alphabetic characters
- Minimum number of lowercase ASCII alphabetic characters
-
Minimum number of special ASCII characters, such as
!@#$ - Minimum number of 8-bit characters
- Minimum number of character categories required per password; a category can be upper- or lower-case letters, special characters, digits, or 8-bit characters
This can be abbreviated to pwdCheckSyntax.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordCheckSyntax: off |
3.1.1.181. passwordDictCheck
If set to on, the passwordDictCheck parameter checks the password against the CrackLib dictionary. Directory Server rejects the password if the new password contains a dictionary word.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordDictCheck: off |
3.1.1.182. passwordExp (Password Expiration)
Indicates whether user passwords expire after a given number of seconds. By default, user passwords do not expire. Once password expiration is enabled, set the number of seconds after which the password expires using the passwordMaxAge attribute.
For more information on password policies, see the "Managing User Accounts" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordExp: on |
3.1.1.183. passwordExpirationTime
This attribute specifies the length of time that passes before the user’s password expires.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any date, in integers |
| Default Value | none |
| Syntax | GeneralizedTime |
| Example | passwordExpirationTime: 202009011953 |
3.1.1.184. passwordExpWarned
This attribute indicates that a password expiration warning has been sent to the user.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | true | false |
| Default Value | none |
| Syntax | DirectoryString |
| Example | passwordExpWarned: true |
3.1.1.185. passwordGraceLimit (Password Expiration)
This attribute is only applicable if password expiration is enabled. After the user’s password has expired, the server allows the user to connect for the purpose of changing the password. This is called a grace login. The server allows only a certain number of attempts before completely locking out the user. This attribute is the number of grace logins allowed. A value of 0 means the server does not allow grace logins.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | 0 (off) to any reasonable integer |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordGraceLimit: 3 |
3.1.1.186. passwordHistory (Password History)
Enables password history. Password history refers to whether users are allowed to reuse passwords. By default, password history is disabled, and users can reuse passwords. If this attribute is set to on, the directory stores a given number of old passwords and prevents users from reusing any of the stored passwords. Set the number of old passwords the Directory Server stores using the passwordInHistory attribute.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordHistory: on |
3.1.1.187. passwordInHistory (Number of Passwords to Remember)
Indicates the number of passwords the Directory Server stores in history. Passwords that are stored in history cannot be reused by users. By default, the password history feature is disabled, meaning that the Directory Server does not store any old passwords, and so users can reuse passwords. Enable password history using the passwordHistory attribute.
To prevent users from rapidly cycling through the number of passwords that are tracked, use the passwordMinAge attribute.
This can be abbreviated to pwdInHistory.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 24 passwords |
| Default Value | 6 |
| Syntax | Integer |
| Example | passwordInHistory: 7 |
3.1.1.188. passwordIsGlobalPolicy (Password Policy and Replication)
This attribute controls whether password policy attributes are replicated.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordIsGlobalPolicy: off |
3.1.1.189. passwordLegacyPolicy
Enables legacy password behavior. Older LDAP clients expected to receive an error to lock a user account once the maximum failure limit was exceeded. For example, if the limit were three failures, then the account was locked at the fourth failed attempt. Newer clients, however, expect to receive the error message when the failure limit is reached. For example, if the limit is three failures, then the account should be locked at the third failed attempt.
Because locking the account when the failure limit is exceeded is the older behavior, it is considered legacy behavior. It is enabled by default, but can be disabled to allow the new LDAP clients to receive the error at the expected time.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | passwordLegacyPolicy: on |
3.1.1.190. passwordLockout (Account Lockout)
Indicates whether users are locked out of the directory after a given number of failed bind attempts. By default, users are not locked out of the directory after a series of failed bind attempts. If account lockout is enabled, set the number of failed bind attempts after which the user is locked out using the passwordMaxFailure attribute.
This can be abbreviated to pwdLockOut.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordLockout: off |
3.1.1.191. passwordLockoutDuration (Lockout Duration)
Indicates the amount of time in seconds during which users are locked out of the directory after an account lockout. The account lockout feature protects against hackers who try to break into the directory by repeatedly trying to guess a user’s password. Enable and disable the account lockout feature using the passwordLockout attribute.
This can be abbreviated to pwdLockoutDuration.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 3600 |
| Syntax | Integer |
| Example | passwordLockoutDuration: 3600 |
3.1.1.192. passwordMaxAge (Password Maximum Age)
Indicates the number of seconds after which user passwords expire. To use this attribute, password expiration has to be enabled using the passwordExp attribute.
This can be abbreviated to pwdMaxAge.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 8640000 (100 days) |
| Syntax | Integer |
| Example | passwordMaxAge: 100 |
3.1.1.193. passwordBadWords
The passwordBadWords parameter defines a comma-separated list of strings that users are not allowed to use in a password.
Note that Directory Server does a case-insensitive comparison of the strings.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any string |
| Default Value | "" |
| Syntax | DirectoryString |
| Example | passwordBadWords: example |
3.1.1.194. passwordMaxClassChars
If you set the passwordMaxClassChars parameter to a value higher than 0, Directory Server prevents setting a password that has more consecutive characters from the same category than the value set in the parameter. If enabled, Directory Server checks for consecutive characters of the following categories:
- digits
- alpha characters
- lower case
- upper case
For example, if you set passwordMaxClassChars to 3, passwords containing, for example, jdif or 1947 are not allowed.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 (disabled) to maximum 32-bit integer (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxClassChars: 0 |
3.1.1.195. passwordMaxFailure (Maximum Password Failures)
Indicates the number of failed bind attempts after which a user is locked out of the directory. By default, account lockout is disabled. Enable account lockout by modifying the passwordLockout attribute.
This can be abbreviated to pwdMaxFailure.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to maximum integer bind failures |
| Default Value | 3 |
| Syntax | Integer |
| Example | passwordMaxFailure: 3 |
3.1.1.196. passwordMaxRepeats (Password Syntax)
Maximum number of times the same character can appear sequentially in the password. Zero (0) is off. Integer values reject any password which used a character more than that number of times; for example, 1 rejects characters that are used more than once (aa) and 2 rejects characters used more than twice (aaa).
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxRepeats: 1 |
3.1.1.197. passwordMaxSeqSets
If you set the passwordMaxSeqSets parameter to a value higher than 0, Directory Server rejects passwords with duplicate monotonic sequences exceeding the length set in the parameter. For example, if you set passwordMaxSeqSets to 2, setting the password to azXYZ_XYZ-g is not allowed, because XYZ appears twice in the password.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxSeqSets: 0 |
3.1.1.198. passwordMaxSequence
If you set the passwordMaxSequence parameter to a value higher than 0, Directory Server rejects new passwords with a monotonic sequence longer than the value set in passwordMaxSequence. For example, if you set the parameter to 3, Directory Server rejects passwords containing strings such as 1234 or dcba.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMaxSequence: 0 |
3.1.1.199. passwordMin8Bit (Password Syntax)
This sets the minimum number of 8-bit characters the password must contain.
The 7-bit checking for userPassword must be disabled to use this.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMin8Bit: 0 |
3.1.1.200. passwordMinAge (Password Minimum Age)
Indicates the number of seconds that must pass before a user can change their password. Use this attribute in conjunction with the passwordInHistory (number of passwords to remember) attribute to prevent users from quickly cycling through passwords so that they can use their old password again. A value of zero (0) means that the user can change the password immediately.
This can be abbreviated to pwdMaxFailure.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to valid maximum integer |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinAge: 150 |
3.1.1.201. passwordMinAlphas (Password Syntax)
This attribute sets the minimum number of alphabetic characters password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinAlphas: 4 |
3.1.1.202. passwordMinCategories (Password Syntax)
This sets the minimum number of character categories that are represented in the password. The categories are:
- Lowercase alphabetic characters
- Uppercase alphabetic characters
- Numbers
- Special ASCII charactes, such as $ and punctuation marks
- 8-bit characters
For example, if the value of this attribute were set to 2, and the user tried to change the password to aaaaa, the server would reject the password because it contains only lower case characters, and therefore contains characters from only one category. A password of aAaAaA would pass because it contains characters from two categories, uppercase and lowercase.
The default is 3, which means that if password syntax checking is enabled, valid passwords have to have three categories of characters.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 5 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinCategories: 2 |
3.1.1.203. PasswordMinDigits (Password Syntax)
This sets the minimum number of digits a password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinDigits: 3 |
3.1.1.204. passwordMinLength (Password Minimum Length)
This attribute specifies the minimum number of characters that must be used in Directory Server user password attributes. In general, shorter passwords are easier to crack. Directory Server enforces a minimum password of eight characters. This is long enough to be difficult to crack but short enough that users can remember the password without writing it down.
This can be abbreviated to pwdMinLength.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 2 to 512 characters |
| Default Value | 8 |
| Syntax | Integer |
| Example | passwordMinLength: 8 |
3.1.1.205. PasswordMinLowers (Password Syntax)
This attribute sets the minimum number of lower case letters password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinLowers: 1 |
3.1.1.206. PasswordMinSpecials (Password Syntax)
This attribute sets the minimum number of special, or not alphanumeric, characters a password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinSpecials: 1 |
3.1.1.207. PasswordMinTokenLength (Password Syntax)
This attribute sets the smallest attribute value length that is used for trivial words checking. For example, if the PasswordMinTokenLength is set to 3, then a givenName of DJ does not result in a policy that rejects DJ from being in the password, but the policy rejects a password comtaining the givenName of Bob.
Directory Server checks the minimum token length against values in the following attributes:
-
uid -
cn -
sn -
givenName -
mail -
ou
If Directory Server should check additional attributes, you can set them in the passwordUserAttributes parameter. For details, see Section 3.1.1.212, “passwordUserAttributes”.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to 64 |
| Default Value | 3 |
| Syntax | Integer |
| Example | passwordMinTokenLength: 3 |
3.1.1.208. PasswordMinUppers (Password Syntax)
This sets the minimum number of uppercase letters password must contain.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 0 to 64 |
| Default Value | 0 |
| Syntax | Integer |
| Example | passwordMinUppers: 2 |
3.1.1.209. passwordMustChange (Password Must Change)
Indicates whether users must change their passwords when they first bind to the Directory Server or when the password has been reset by the Manager DN.
This can be abbreviated to pwdMustChange.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordMustChange: off |
3.1.1.210. passwordPalindrome
If you enable the passwordPalindrome parameter, Directory Server rejects a password if the new password contains a palindrome.
A palindrome is a string which reads the same forward as backward, such as abc11cba.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordPalindrome: off |
3.1.1.211. passwordResetFailureCount (Reset Password Failure Count After)
Indicates the amount of time in seconds after which the password failure counter resets. Each time an invalid password is sent from the user’s account, the password failure counter is incremented. If the passwordLockout attribute is set to on, users are locked out of the directory when the counter reaches the number of failures specified by the passwordMaxFailure attribute (within 600 seconds by default). After the amount of time specified by the passwordLockoutDuration attribute, the failure counter is reset to zero (0).
This can be abbreviated to pwdFailureCountInterval.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 600 |
| Syntax | Integer |
| Example | passwordResetFailureCount: 600 |
3.1.1.212. passwordUserAttributes
By default, if you set a minimum token length in the passwordMinTokenLength parameter, Directory Server checks the tokens only against certain attributes. For details, see Section 3.1.1.207, “PasswordMinTokenLength (Password Syntax)”.
The passwordUserAttributes parameter enables you to set a comma-separated list of additional attributes that Directory Server should check.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | Any string |
| Default Value | "" |
| Syntax | DirectoryString |
| Example | passwordUserAttributes: telephoneNumber, l |
3.1.1.213. passwordSendExpiringTime
When a client requests the password expiring control, Directory Server returns the "time to expire" value only if the password is within the warning period. To provide compatibility with existing clients that always expect this value to be returned - regardless if the password expiration time is within the warning period - the passwordSendExpiringTime parameter can be set to on.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordSendExpiringTime: off |
3.1.1.214. passwordStorageScheme (Password Storage Scheme)
This attribute sets the method used to encrypt user passwords stored in userPassword attributes. For further details, such as recommended strong password storage schemes, see Section 4.1.43, “Password Storage Schemes”.
Red Hat recommends not setting this attribute. I the value is not set, Directory Server automatically uses the strongest supported password storage scheme available. If a future Directory Server update changes the default value to increase security, passwords will be automatically encrypted using the new storage scheme if a user set a passwords.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | |
| Default Value | PBKDF2_SHA256 |
| Syntax | DirectoryString |
| Example | passwordStorageScheme: PBKDF2_SHA256 |
3.1.1.215. passwordTPRDelayExpireAt
The passwordTPRDelayExpireAt attribute is part of the password policy. After the administrator sets a temporary password to a user account, passwordTPRDelayExpireAt defines the time in seconds before the temporary password expires.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | -1 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | passwordTPRDelayExpireAt: 3600 |
3.1.1.216. passwordTPRDelayValidFrom
The passwordTPRDelayValidFrom attribute is part of the password policy. After the administrator sets a temporary password to a user account, passwordTPRDelayValidFrom defines the time in seconds before a temporary password can be used.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | -1 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | passwordTPRDelayValidFrom: 60 |
3.1.1.217. passwordTPRMaxUse
The passwordTPRMaxUse attribute is part of the password policy. The attribute sets the number of times a user can authenticate successfully or not before the temporary password expires. If the authentication is successful, Directory Server only allows the user to change the password before other operations are possible. If the user does not change the password, the operation is terminated. The counter of the number of authentication attempts is increased regardless whether the authentication was successful or not.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | -1 (disabled) to the maximum 32 bit integer value (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | passwordTPRMaxUse: 5 |
3.1.1.218. passwordTrackUpdateTime
Sets whether to record a separate timestamp specifically for the last time that the password for an entry was changed. If this is enabled, then it adds the pwdUpdateTime operational attribute to the user account entry (separate from other update times, like modifyTime).
Using this timestamp can make it easier to synchronize password changes between different LDAP stores, such as Active Directory.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordTrackUpdateTime: off |
3.1.1.219. passwordUnlock (Unlock Account)
Indicates whether users are locked out of the directory for a specified amount of time or until the administrator resets the password after an account lockout. The account lockout feature protects against hackers who try to break into the directory by repeatedly trying to guess a user’s password. If this passwordUnlock attribute is set to off and the operational attribute accountUnlockTime has a value of 0, then the account is locked indefinitely.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | passwordUnlock: off |
3.1.1.220. passwordWarning (Send Warning)
Indicates the number of seconds before a user’s password is due to expire that the user receives a password expiration warning control on their next LDAP operation. Depending on the LDAP client, the user may also be prompted to change their password at the time the warning is sent.
This can be abbreviated to pwdExpireWarning.
For more information on password policies, see the "Managing User Authentication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | 1 to the maximum 32 bit integer value (2147483647) in seconds |
| Default Value | 86400 (1 day) |
| Syntax | Integer |
| Example | passwordWarning: 86400 |
3.1.1.221. passwordAdminSkipInfoUpdate
You can add a new passwordAdminSkipInfoUpdate: on/off setting under the cn=config entry to provide a fine grained control over password updates performed by password administrators. When you set this setting to on, only the password is changed and the password state attributes in the user entry are not updated. Such attributes are, for example, passwordHistory, passwordExpirationTime, passwordRetryCount, pwdReset and, passwordExpWarned.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | passwordAdminSkipInfoUpdate: on |
The passwords administrators can not only bypass password syntax checks, but also password expiration settings that are configured in the global and local password policies and that use expiration timestamp (passwordExpirationTime) and must change the password (pwdMustChange) attributes by using the setting `passwordAdminSkipInfoUpdate: on/off.
3.1.1.222. retryCountResetTime
The retryCountResetTime attribute contains the date and time in UTC-format after which the passwordRetryCount attribute will be reset to 0.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Range | Any valid time stamp in UTC format |
| Default Value | none |
| Syntax | Generalized Time |
| Example | retryCountResetTime: 20190618094419Z |
3.1.2. cn=changelog5,cn=config
Multi-supplier replication changelog configuration entries are stored under the cn=changelog5 entry. The cn=changelog5,cn=config entry is an instance of the extensibleObject object class.
The cn=changelog5 entry must contain the following object classes:
-
top -
extensibleObject
Two different types of changelogs are maintained by Directory Server. The first type, which is stored here and referred to as the changelog, is used by multi-supplier replication; the second changelog, which is actually a plug-in and referred to as the retro changelog, is for compatibility with some legacy applications. See Section 4.1.48, “Retro Changelog Plug-in” for further information about the Retro Changelog Plug-in.
3.1.2.1. cn
This required attribute sets the relative distinguished name (RDN) of a changelog entry.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Values | Any string |
| Default Value | changelog5 |
| Syntax | DirectoryString |
| Example | cn=changelog5 |
3.1.2.2. nsslapd-changelogcompactdb-interval
The Berkeley database does not reuse free pages unless the database is explicitly compacted. The compact operation returns the unused pages to the file system and the database file size shrinks. This parameter defines the interval in seconds when the changelog database is compacted. Note that compacting the database is resource-intensive, and thus should not be done to frequently.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Values | 0 (no compaction) to 2147483647 seconds |
| Default Value | 2592000 (30 days) |
| Syntax | Integer |
| Example | nsslapd-changelogcompactdb-interval: 2592000 |
3.1.2.3. nsslapd-changelogdir
This required attribute specifies the name of the directory in which the changelog entry is created. Whenever a changelog configuration entry is created, it must contain a valid directory; otherwise, the operation is rejected. The GUI proposes by default that this entry be stored in /var/lib/dirsrv/slapd-instance/changelogdb/.
If the cn=changelog5 entry is removed, the directory specified in the nsslapd-changelogdir parameter, including any subdirectories, are removed, with all of their contents.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Values | Any valid path to the directory storing the changelog |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-changelogdir: /var/lib/dirsrv/slapd-instance/changelogdb/ |
3.1.2.4. nsslapd-changelogmaxage (Max Changelog Age)
When synchronizing with a consumer, Directory Server stores each update in the changelog with a time stamp. The nsslapd-changelogmaxage parameter sets the maximum age of a record stored in the changelog. Older records that were successfully transferred to all replicas are removed automatically. By default, Directory Server removes records that are older than seven days. However, if you disabled nsslapd-changelogmaxage and nsslapd-changelogmaxentries parameters, Directory Server keeps all records in the changelog, and it can lead to the excessive growth of the changelog file.
Retro changelog has its own nsslapd-changelogmaxage attribute that is described in section Retro changelog nsslapd-changelogmaxage
The trim operation is executed in intervals set in the nsslapd-changelogtrim-interval parameter.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Range | 0 (meaning that entries are not removed according to their age) to maximum 32-bit integer (2147483647) |
| Default Value | 7d |
| Syntax |
DirectoryString IntegerAgeID where AgeID is |
| Example | nsslapd-changelogmaxage: 4w |
3.1.2.5. nsslapd-changelogmaxentries (Max Changelog Records)
When synchronizing with a consumer, Directory Server stores each update in the changelog. The nsslapd-changelogmaxentries parameter sets the maximum number of records stored in the changelog. If the number of the oldest records, that were successfully transferred to all replicas, exceeds the nsslapd-changelogmaxentries value, Directory Server automatically removes them from the changelog. If you disabled nsslapd-changelogmaxentries and nsslapd-changelogmaxage parameters, Directory Server keeps all records in the changelog, and it can lead to the excessive growth of the changelog file.
Directory Server does not automatically reduce the file size of the replication changelog if you set a lower value in the nsslapd-changelogmaxentries parameter. For further details, see the corresponding sections in the Red Hat Directory Administration Guide.
Directory Server executes the trim operation in intervals set in the nsslapd-changelogtrim-interval parameter.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Range | 0 (meaning that the only maximum limit is the disk size) to maximum 32-bit integer (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsslapd-changelogmaxentries: 5000 |
3.1.2.6. nsslapd-changelogtrim-interval (Replication Changelog Trimming Interval)
Directory Server repeatedly runs a trimming process on the changelog. To change the time between two runs, update the nsslapd-changelogtrim-interval parameter and set the interval in seconds.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Range | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 300 (5 minutes) |
| Syntax | DirectoryString |
| Example | nsslapd-changelogtrim-interval: 300 |
3.1.2.7. nsslapd-encryptionalgorithm (Encryption Algorithm)
This attribute specifies the encryption algorithm used to encrypt the changelog. To enable the changelog encryption, the server certificate must be installed on the directory server. For information on the changelog, see Section 3.1.2.3, “nsslapd-changelogdir”.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Range | AES or 3DES |
| Default Value | None |
| Syntax | DirectoryString |
| Example | nsslapd-encryptionalgorithm: AES |
3.1.2.8. nsSymmetricKey
This attribute stores the internally-generated symmetric key. For information on the changelog, see Section 3.1.2.3, “nsslapd-changelogdir”.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=changelog5,cn=config |
| Valid Range | Base 64-encoded key |
| Default Value | None |
| Syntax | DirectoryString |
| Example | None |
3.1.3. Changelog Attributes
The changelog attributes contain the changes logged in the changelog.
3.1.3.1. changes
This attribute contains the changes made to the entry for add and modify operations in LDIF format.
| OID | 2.16.840.1.113730.3.1.8 |
| Syntax | Binary |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.2. changeLog
This attribute contains the distinguished name of the entry which contains the set of entries comprising the server’s changelog.
| OID | 2.16.840.1.113730.3.1.35 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.3. changeNumber
This attribute is always present. It contains an integer which uniquely identifies each change made to a directory entry. This number is related to the order in which the change occurred. The higher the number, the later the change.
| OID | 2.16.840.1.113730.3.1.5 |
| Syntax | Integer |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.4. changeTime
This attribute defines a time, in a YYMMDDHHMMSS format, when the entry was added.
| OID | 2.16.840.1.113730.3.1.77 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.1.3.5. changeType
This attribute specifies the type of LDAP operation, add, delete, modify, or modrdn. For example:
changeType: modify
| OID | 2.16.840.1.113730.3.1.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.6. deleteOldRdn
In the case of modrdn operations, this attribute specifies whether the old RDN was deleted.
A value of zero (0) will delete the old RDN. Any other non-zero value will keep the old RDN. (Non-zero values can be negative or positive integers.)
| OID | 2.16.840.1.113730.3.1.10 |
| Syntax | Boolean |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.7. filterInfo
This is used by the changelog for processing replication.
| OID | 2.16.840.1.113730.3.1.206 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.1.3.8. newRdn
In the case of modrdn operations, this attribute specifies the new RDN of the entry.
| OID | 2.16.840.1.113730.3.1.9 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.9. newSuperior
In the case of modrdn operations, this attribute specifies the new parent (superior) entry for the moved entry.
| OID | 2.16.840.1.113730.3.1.11 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.3.10. targetDn
This attribute contains the DN of the entry that was affected by the LDAP operation. In the case of a modrdn operation, the targetDn attribute contains the DN of the entry before it was modified or moved.
| OID | 2.16.840.1.113730.3.1.6 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Changelog Internet Draft |
3.1.4. cn=encryption
Encryption related attributes are stored under the cn=encryption,cn=config entry. The cn=encryption,cn=config entry is an instance of the nsslapdEncryptionConfig object class.
3.1.4.1. allowWeakCipher
This attribute controls whether weak ciphers are allowed or rejected. The default depends on the value set in the nsSSL3Ciphers parameter.
Ciphers are considered weak, if:
They are exportable.
Exportable ciphers are labeled
EXPORTin the cipher name. For example, inTLS_RSA_EXPORT_WITH_RC4_40_MD5.They are symmetrical and weaker than the 3DES algorithm.
Symmetrical ciphers use the same cryptographic keys for both encryption and decryption.
- The key length is shorter than 128 bits.
The server has to be restarted for changes to this attribute to take effect.
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value |
|
| Syntax | DirectoryString |
| Example | allowWeakCipher: on |
3.1.4.2. allowWeakDHParam
The network security services (NSS) libraries linked with Directory Server requires minimum of 2048-bit Diffie-Hellman (DH) parameters. However, some clients connecting to Directory Server, such as Java 1.6 and 1.7 clients, only support 1024-bit DH parameters. The allowWeakDHParam parameter allows you to enable support for weak 1024-bit DH parameters in Directory Server.
The server has to be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | off |
| Syntax | DirectoryString |
| Example | allowWeakDHParam: off |
3.1.4.3. nsSSL3Ciphers
This attribute specifies the set of TLS encryption ciphers Directory Server uses during encrypted communications.
The value set in this parameter influences the default value of the allowWeakCipher parameter. For details, see Section 3.1.4.1, “allowWeakCipher”.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | Comma separated list of NSS supported ciphers. Additionally, the following parameters are possible: * default: Enables the default ciphers advertised by NSS except weak ciphers. For further information, see List supported cipher suites for SSL connections.
* +all: All ciphers are enabled. This includes weak ciphers, if the * -all: All ciphers are disabled. |
| Default Value | default |
| Syntax | DirectoryString
Use the plus (
To enable all ciphers — except |
| Example | nsSSL3Ciphers: +TLS_RSA_AES_128_SHA,+TLS_RSA_AES_256_SHA,+TLS_RSA_WITH_AES_128_GCM_SHA256,-RSA_NULL_SHA |
For details how to list all supported ciphers, see the corresponding section in the Red Hat Directory Server Administration Guide.
3.1.4.4. nsSSLActivation
This attribute shows whether an TLS cipher family is enabled for a given security module.
| Entry DN | cn=encryptionType,cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsSSLActivation: on |
3.1.4.5. nsSSLClientAuth
This attribute shows how the Directory Server enforces client authentication. It accepts the following values:
-
off- the Directory Server will not accept client authentication -
allowed(default) - the Directory Server will accept client authentication, but not require it required- all clients must use client authentication.ImportantThe Directory Server Console does not support client authentication. Therefore, if the
nsSSLClientAuthattribute is set torequired, the Console cannot be used to manage the instance.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | off | allowed | required |
| Default Value | allowed |
| Syntax | DirectoryString |
| Example | nsSSLClientAuth: allowed |
3.1.4.6. nsSSLEnabledCiphers
Directory Server generates the multi-valued nsSSLEnabledCiphers attribute automatically. The attribute is read-only and displays the ciphers Directory Server currently uses. The list might not be the same as you set in the nsSSL3Ciphers attribute. For example, if you set weak ciphers in the nsSSL3Ciphers attribute, but allowWeakCipher is disabled, the nsSSLEnabledCiphers attribute neither lists the weak ciphers nor does Directory Server use them.
| Parameter | Description |
|---|---|
| Entry DN | cn=config |
| Valid Values | The values of this attribute are auto-generated and read-only. |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsSSLClientAuth: TLS_RSA_WITH_AES_256_CBC_SHA::AES::SHA1::256 |
3.1.4.7. nsSSLPersonalitySSL
This attribute contains the certificate name to use for SSL.
| Entry DN | cn=encryption,cn=config |
| Valid Values | A certificate nickname |
| Default Value | |
| Syntax | DirectoryString |
| Example: | nsSSLPersonalitySSL: Server-Cert |
3.1.4.8. nsSSLSessionTimeout
This attribute sets the lifetime duration of a TLS connection. The minimum timeout value is 5 seconds. If a smaller value is set, then it is automatically replaced by 5 seconds. A value greater than the maximum value in the valid range below is replaced by the maximum value in the range.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Range | 5 seconds to 24 hours |
| Default Value | 0, which means use the maximum value in the valid range above. |
| Syntax | Integer |
| Example | nsSSLSessionTimeout: 5 |
3.1.4.9. nsSSLSupportedCiphers
This attribute contains the supported ciphers for the server.
| Entry DN | cn=encryption,cn=config |
| Valid Values | A specific family, cipher, and strength string |
| Default Value | |
| Syntax | DirectoryString |
| Example: | nsSSLSupportedCiphers: TLS_RSA_WITH_AES_256_CBC_SHA::AES::SHA1::256 |
3.1.4.10. nsSSLToken
This attribute contains the name of the token (security module) used by the server.
| Entry DN | cn=encryption,cn=config |
| Valid Values | A module name |
| Default Value | |
| Syntax | DirectoryString |
| Example: | nsSSLToken: internal (software) |
3.1.4.11. nsTLS1
Enables TLS version 1. The ciphers used with TLS are defined in the nsSSL3Ciphers attribute.
If the sslVersionMin and sslVersionMax parameters are set in conjunction with nsTLS1, Directory Server selects the most secure settings from these parameters.
The server has to be restarted for changes to this attribute to go into effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsTLS1: on |
3.1.4.12. nsTLSAllowClientRenegotiation
Directory Server uses the SSL_OptionSet() network security services (NSS) function with the SSL_ENABLE_RENEGOTIATION option to control the TLS renegotiation behavior of NSS.
The nsTLSAllowClientRenegotiation attribute controls which values Directory Server passes to the SSL_ENABLE_RENEGOTIATION option:
-
If you set
nsTLSAllowClientRenegotiation: on, Directory Server passesSSL_RENEGOTIATE_REQUIRES_XTNto theSSL_ENABLE_RENEGOTIATIONoption. In this case, NSS allows secure renegotiations attempts using RFC 5746. -
If you set
nsTLSAllowClientRenegotiation: off, Directory Server passesSSL_RENEGOTIATE_NEVERto theSSL_ENABLE_RENEGOTIATIONoption. In this case, NSS denies all renegotiations attempts, even secure ones.
For further details about the NSS TLS renegotiation behavior, see the The RFC 5746 implementation in NSS (Network Security Services) section in the Is Red Hat affected by TLS renegotiation MITM attacks (CVE-2009-3555)? article.
The service must be restarted for changes to this attribute to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=encryption,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsTLSAllowClientRenegotiation: on |
3.1.4.13. sslVersionMin
The sslVersionMin parameter sets the minimum version of the TLS protocol Directory Server uses. However, by default, Directory Server sets this parameter automatically based on the system-wide crypto policy. If you set the crypto policy profile in the /etc/crypto-policies/config file to:
-
DEFAULT,FUTURE, orFIPS, Directory Server setssslVersionMintoTLS1.2 -
LEGACY, Directory Server setssslVersionMintoTLS1.0
Alternatively, you can manually set sslVersionMin to higher value than the one defined in the crypto policy.
The service must be restarted for changes to this attribute to take effect.
| Entry DN | cn=encryption,cn=config |
| Valid Values |
TLS protocol versions, such as |
| Default Value | Depends on the system-wide crypto policy profile you set. |
| Syntax | DirectoryString |
| Example: | sslVersionMin: TLS1.2 |
3.1.4.14. sslVersionMax
Sets the maximum version of the TLS protocol to be used. By default this value is set to the newest available protocol version in the NSS library installed on the system.
The server has to be restarted for changes to this attribute to go into effect.
If the sslVersionMin and sslVersionMax parameters are set in conjunction with nsTLS1, Directory Server selects the most secure settings from these parameters.
| Entry DN | cn=encryption,cn=config |
| Valid Values |
TLS protocol version such as |
| Default Value | Newest available protocol version in the NSS library installed on the system |
| Syntax | DirectoryString |
| Example: | sslVersionMax: TLS1.2 |
3.1.5. cn=features
There are not attributes for the cn=features entry itself. This entry is only used as a parent container entry, with the nsContainer object class.
The child entries contain an oid attribute to identify the feature and the directoryServerFeature object class, plus optional identifying information about the feature, such as specific ACLs. For example:
dn: oid=2.16.840.1.113730.3.4.9,cn=features,cn=config objectClass: top objectClass: directoryServerFeature oid: 2.16.840.1.113730.3.4.9 cn: VLV Request Control aci: (targetattr != "aci")(version 3.0; acl "VLV Request Control"; allow( read, search, compare, proxy ) userdn = "ldap:///all";) creatorsName: cn=server,cn=plugins,cn=config modifiersName: cn=server,cn=plugins,cn=config createTimestamp: 20200129132357Z modifyTimestamp: 20200129132357Z
3.1.5.1. oid
The oid attribute contains an object identifier assigned to a directory service feature. oid is used as the naming attribute for these directory features.
| OID | 2.16.840.1.113730.3.1.215 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.1.6. cn=mapping tree
Configuration attributes for suffixes, replication, and Windows synchronization are stored under
cn=mapping tree,cn=config. Configuration attributes related to suffixes are found under the suffix subentrycn=suffix,cn=mapping tree,cn=config.For example, a suffix is the root entry in the directory tree, such as
dc=example,dc=com.-
Replication configuration attributes are stored under
cn=replica,cn=suffix,cn=mapping tree,cn=config. -
Replication agreement attributes are stored under
cn=replicationAgreementName,cn=replica,cn=suffix,cn=mapping tree,cn=config. -
Windows synchronization agreement attributes are stored under
cn=syncAgreementName,cn=replica,cn=suffix,cn=mapping tree,cn=config.
3.1.7. Suffix Configuration Attributes under cn=suffix_DN
Suffix configurations are stored under the cn="suffix_DN",cn=mapping tree,cn=config entry. These entries are instances of the nsMappingTree object class. The extensibleObject object class enables entries that belong to it to hold any user attribute. For suffix configuration attributes to be taken into account by the server, these object classes, in addition to the top object class, must be present in the entry.
You must write the suffix DN in quotes because it contains characters such as equals signs (=), commas (,), and space characters. By using quotes, the DN appears correctly as a value in another DN. For example: cn="dc=example,dc=com",cn=mapping tree,cn=config
For further details, see the corresponding section in the Directory Server Administration Guide.
3.1.7.1. cn
This mandatory attribute sets the relative distinguished name (RDN) of a new suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid LDAP DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: dn=example,dc=com |
3.1.7.2. nsslapd-backend
This parameter sets the name of the database or database link used to process requests. It is multi-valued, with one database or database link per value. This attribute is required when the value of the nsslapd-state attribute is set to backend or referral on update.
Set the value to the name of the back-end database entry instance under cn=ldbm database,cn=plugins,cn=config. For example: o=userroot,cn=ldbm database,cn=plugins,cn=config
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid partition name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-backend: userRoot |
3.1.7.3. nsslapd-distribution-function
The nssldap-distribution-function parameter sets the name of the custom distribution function. You must set this attribute when you set more than one database in the nsslapd-backend attribute.
For further details about the custom distribution function, see the corresponding section in the Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid distribution function |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-distribution-plugin: distribution_function_name |
3.1.7.4. nsslapd-distribution-plugin
The nssldap-distribution-plugin sets the shared library to be used with the custom distribution function. You must set this attribute when you set more than one database in the nsslapd-backend attribute.
For further details about the custom distribution function, see the corresponding section in the Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid distribution plug-in |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-distribution-plugin: /path/to/shared/library |
3.1.7.5. nsslapd-parent
If you want to create a sub suffix, use the nsslapd-parent attribute to define the parent suffix.
If the attribute is not set, the new suffix is created as a root suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid partition name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-parent-suffix: dc=example,dc=com |
3.1.7.6. nsslapd-referral
This attribute sets the LDAP URL of the referral to be returned by the suffix. You can add the nssldap-referral attribute multiple times to set multiple referral URLs.
You must set this attribute if you set the nsslapd-state parameter to referral or on update.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssldap-referral: ldap://example.com/ |
3.1.7.7. nsslapd-state
This parameter determines how a suffix handles operations. The attribute takes the following values:
-
backend: The back-end database processes all operations. -
disabled: The database is not available for processing operations. The server returns aNo such search objecterror in response to requests made by client applications. -
referral: Directory Server returns a referral URL for requests to this suffix. -
referral on update: The database is used for all operations. Only for update requests is a referral sent.
| Parameter | Description |
|---|---|
| Entry DN | cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | backend | disabled | referral | referral on update |
| Default Value | backend |
| Syntax | DirectoryString |
| Example | nsslapd-state: backend |
3.1.8. Replication Attributes under cn=replica,cn=suffixDN,cn=mapping tree,cn=config
Replication configuration attributes are stored under cn=replica,cn=suffix, cn=mapping tree,cn=config. The cn=replica entry is an instance of the nsDS5Replica object class. For replication configuration attributes to be taken into account by the server, this object class (in addition to the top object class) must be present in the entry. For further information about replication, see the "Managing Replication" chapter in the Red Hat Directory Server Administration Guide.
The cn=replica,cn=suffix,cn=mapping tree,cn=config entry must contain the following object classes:
-
top -
extensibleObject -
nsds5replica
3.1.8.1. cn
Sets the naming attribute for the replica. The cn attribute must be set to replica.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
The value must be set to |
| Default Value | replica |
| Syntax | DirectoryString |
| Example | cn=replica |
3.1.8.2. nsds5DebugReplicaTimeout
This attribute gives an alternate timeout period to use when the replication is run with debug logging. This can set only the time or both the time and the debug level:
nsds5debugreplicatimeout: seconds[:debuglevel]| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any numeric string |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5debugreplicatimeout: 60:8192 |
3.1.8.3. nsDS5Flags
This attribute sets replica properties that were previously defined in flags. At present only one flag exists, which sets whether the log changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 * 0: The replica does not write to the changelog; this is the default for consumers. * 1: The replica writes to the changelog; this is the default for hubs and suppliers. |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsDS5Flags: 0 |
3.1.8.4. nsDS5ReplConflict
Although this attribute is not in the cn=replica entry, it is used in conjunction with replication. This multi-valued attribute is included on entries that have a change conflict that cannot be resolved automatically by the synchronization process. To check for replication conflicts requiring administrator intervention, perform an LDAP search for (nsDS5ReplConflict=*). For example:
# ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s sub -b dc=example,dc=com "(|(objectclass=nsTombstone)(nsDS5ReplConflict=*))" dn nsDS5ReplConflict nsUniqueID
Using the search filter "(objectclass=nsTombstone)" also shows tombstone (deleted) entries. The value of the nsDS5ReplConflict contains more information about which entries are in conflict, usually by referring to them by their nsUniqueID. It is possible to search for a tombstone entry by its nsUniqueID. For example:
# ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s sub -b dc=example,dc=com "(|(objectclass=nsTombstone)(nsUniqueID=66a2b699-1dd211b2-807fa9c3-a58714648))"
3.1.8.5. nsDS5ReplicaAutoReferral
This attribute sets whether the Directory Server follows configured referrals for the database.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaAutoReferral: on |
3.1.8.6. nsState
This attribute stores information on the state of the clock. It is designed only for internal use to ensure that the server cannot generate a change sequence number (csn) inferior to existing ones required for detecting backward clock errors.
3.1.8.7. nsDS5ReplicaAbortCleanRUV
This read-only attribute specifies whether the background task that removes old RUV entries for obsolete or missing suppliers is being aborted. See Section 3.1.16.13, “cn=abort cleanallruv” for more information about this task. A value of 0 means that the task is inactive, and a value of 1 means that the task is active.
This attribute is present to allow the abort task to be resumed after a server restart. When the task completes, the attribute is deleted.
The server ignores the modify request if this value is set manually.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | None |
| Syntax | Integer |
| Example | nsDS5ReplicaAbortCleanRUV: 1 |
3.1.8.8. nsds5ReplicaBackoffMin and nsds5ReplicaBackoffMax
These attributes are used in environments with heavy replication traffic, where updates need to be sent as fast as possible.
By default, if a remote replica is busy, the replication protocol will go into a "back off" state, and it will retry to send it updates at the next interval of the back-off timer. By default, the timer starts at 3 seconds, and has a maximum wait period of 5 minutes. As these default settings maybe not be sufficient under certain circumstances, you can use nsds5ReplicaBackoffMin and nsds5ReplicaBackoffMax to configure the minimum and maximum wait times.
The configuration settings can be applied while the server is online, and do not require a server restart. If invalid settings are used, then the default values are used instead. The configuration must be handled through CLI tools.
3.1.8.9. nsDS5ReplicaBindDN
This multi-valued attribute specifies the DN to use when binding. Although there can be more than one value in this cn=replica entry, there can only be one supplier bind DN per replication agreement. Each value should be the DN of a local entry on the consumer server. If replication suppliers are using client certificate-based authentication to connect to the consumers, configure the certificate mapping on the consumer to map the subjectDN in the certificate to a local entry.
For security reasons, do not set this attribute to cn=Directory Manager.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindDN: cn=replication manager,cn=config |
3.1.8.10. nsDS5ReplicaBindDNGroup
The nsDS5ReplicaBindDNGroup attribute specifies a group DN. This group is then expanded and its members, including the members of its subgroups, are added to the replicaBindDNs attribute at startup or when the replica object is modified. This extends the current functionality provided by the nsDS5ReplicaBindDN attribute, as it allows to set a group DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid group DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindDNGroup: cn=sample_group,ou=groups,dc=example,dc=com |
3.1.8.11. nsDS5ReplicaBindDNGroupCheckInterval
Directory Server checks for any changes in the groups specified in the nsDS5ReplicaBindDNGroup attribute and automatically rebuilds the list for the replicaBindDN parameter accordingly. These operations have a negative effect on performance and are therefore performed only at a specified interval set in the nsDS5ReplicaBindDNGroupCheckInterval attribute.
This attribute accepts the following values:
-
-1: Disables the dynamic check at runtime. The administrator must restart the instance when thensDS5ReplicaBindDNGroupattribute changes. -
0: Directory Server rebuilds the lists immediately after the groups are changed. - Any positive 32-bit integer value: Minimum number of seconds that are required to pass since the last rebuild.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | -1 to maximum 32-bit integer (2147483647) |
| Default Value | -1 |
| Syntax | Integer |
| Example | nsDS5ReplicaBindDNGroupCheckInterval: 0 |
3.1.8.12. nsDS5ReplicaChangeCount
This read-only attribute shows the total number of entries in the changelog and whether they still remain to be replicated. When the changelog is purged, only the entries that are still to be replicated remain.
See Section 3.1.8.18, “nsDS5ReplicaPurgeDelay” and Section 3.1.8.23, “nsDS5ReplicaTombstonePurgeInterval” for more information about purge operation properties.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | -1 to maximum 32-bit integer (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaChangeCount: 675 |
3.1.8.13. nsDS5ReplicaCleanRUV
This read-only attribute specifies whether the background task that removes old RUV entries for obsolete or missing suppliers is active. See Section 3.1.16.12, “cn=cleanallruv” for more information about this task. A value of 0 means that the task is inactive, and a value of 1 means that the task is active.
This attribute is present to allow the cleanup task to be resumed after a server restart. When the task completes, the attribute is deleted.
The server ignores the modify request if this value is set manually.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | None |
| Syntax | Integer |
| Example | nsDS5ReplicaCleanRUV: 0 |
3.1.8.14. nsDS5ReplicaId
This attribute sets the unique ID for suppliers in a given replication environment.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range |
For suppliers:
For consumers and hubs: |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaId: 1 |
3.1.8.15. nsDS5ReplicaLegacyConsumer
If this attribute is absent or has a value of false, then it means that the replica is not a legacy consumer.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaLegacyConsumer: false |
3.1.8.16. nsDS5ReplicaName
This attribute specifies the name of the replica with a unique identifier for internal operations. If it is not specified, this unique identifier is allocated by the server when the replica is created.
It is recommended that the server be permitted to generate this name. However, in certain circumstances, for example, in replica role changes (supplier to hub etc.), this value needs to be specified. Otherwise, the server will not use the correct changelog database, and replication fails.
This attribute is destined for internal use only.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString (a UID identifies the replica) |
| Example | nsDS5ReplicaName: 66a2b699-1dd211b2-807fa9c3-a58714648 |
3.1.8.17. nsds5ReplicaProtocolTimeout
When stopping the server, disabling replication, or removing a replication agreement, there is a timeout on how long to wait before stopping replication when the server is under load. The nsds5ReplicaProtocolTimeout attribute can be used to configure this timeout and its default value is 120 seconds.
There may be scenarios where a timeout of 2 minutes is too long, or not long enough. For example, a particular replication agreement may need more time before ending a replication session during a shutdown.
This attribute can be added to the main replication configuration entry for a back end:
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=dc\3Dexample\2Cdc\3Dcom,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default value | 120 |
| Syntax | Integer |
| Example | nsds5ReplicaProtocolTimeout: 120 |
The nsds5ReplicaProtocolTimeout attribute can also be added to a replication agreement. The replication agreement protocol timeout overrides the timeout set in the main replica configuration entry. This allows different timeouts for different replication agreements. If a replication session is in progress, a new timeout will abort that session and allow the server to shutdown.
3.1.8.18. nsDS5ReplicaPurgeDelay
This attribute controls the maximum age of deleted entries (tombstone entries) and state information.
The Directory Server stores tombstone entries and state information so that when a conflict occurs in a multi-supplier replication process, the server resolves the conflicts based on the timestamp and replica ID stored in the change sequence numbers.
An internal Directory Server housekeeping operation periodically removes tombstone entries which are older than the value of this attribute (in seconds). State information which is older than the nsDS5ReplicaPurgeDelay value is removed when an entry which contains the state information is modified.
Not every tombstone and state information may be removed because, with multi-supplier replication, the server may need to keep a small number of the latest updates to prime replication, even if they are older than the value of the attribute.
This attribute specifies the interval, in seconds, to perform internal purge operations on an entry. When setting this attribute, ensure that the purge delay is longer than the longest replication cycle in the replication policy to preserve enough information to resolve replication conflicts and to prevent the copies of data stored in different servers from diverging.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 (keep forever) to maximum 32-bit integer (2147483647) |
| Default Value | 604800 [1 week (60x60x24x7)] |
| Syntax | Integer |
| Example | nsDS5ReplicaPurgeDelay: 604800 |
3.1.8.19. nsDS5ReplicaReapActive
This read-only attribute specifies whether the background task that removes old tombstones (deleted entries) from the database is active. See Section 3.1.8.23, “nsDS5ReplicaTombstonePurgeInterval” for more information about this task. A value of 0 means that the task is inactive, and a value of 1 means that the task is active. The server ignores the modify request if this value is set manually.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaReapActive: 0 |
3.1.8.20. nsDS5ReplicaReferral
This multi-valued attribute specifies the user-defined referrals. This should only be defined on a consumer. User referrals are only returned when a client attempts to modify data on a read-only consumer. This optional referral overrides the referral that is automatically configured by the consumer by the replication protocol.
The URL can use the format ldap[s]://host_name:port_number or ldap[s]://IP_address:port_number, with an IPv4 or IPv6 address.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid LDAP URL |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaReferral: ldap://server.example.com:389 |
3.1.8.21. nsDS5ReplicaReleaseTimeout
This attribute, when used on suppliers and hubs in multi-supplier scenarios, determines a timeout period (in seconds) after which a supplier will release a replica. This is useful in situations when problems such as a slow network connection causes one supplier to acquire access to a replica and hold it for a long time, preventing all other suppliers from accessing it and sending updates. If this attribute is set, replicas are released by suppliers after the specified period, resulting in improved replication performance.
Setting this attribute to 0 disables the timeout. Any other value determines the length of the timeout in seconds.
Avoid setting this attribute to values between 1 and 30. In most scenarios, short timeouts decrease the replication performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default Value | 60 |
| Syntax | Integer |
| Example | nsDS5ReplicaReleaseTimeout: 60 |
3.1.8.22. nsDS5ReplicaRoot
This attribute sets the DN at the root of a replicated area. This attribute must have the same value as the suffix of the database being replicated and cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Suffix of the database being replicated, which is the suffix DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaRoot: "dc=example,dc=com" |
3.1.8.23. nsDS5ReplicaTombstonePurgeInterval
This attribute specifies the time interval in seconds between purge operation cycles.
Periodically, the server runs an internal housekeeping operation to purge old update and state information from the changelog and the main database. See Section 3.1.8.18, “nsDS5ReplicaPurgeDelay”.
When setting this attribute, remember that the purge operation is time-consuming, especially if the server handles many delete operations from clients and suppliers.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default Value | 86400 (1 day) |
| Syntax | Integer |
| Example | nsDS5ReplicaTombstonePurgeInterval: 86400 |
3.1.8.24. nsDS5ReplicaType
Defines the type of replication relationship that exists between this replica and the others.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 | 2 | 3 * 0 means unknown * 1 means primary (not yet used) * 2 means consumer (read-only) * 3 consumer/supplier (updateable) |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaType: 2 |
3.1.8.25. nsds5Task
This attribute launches a replication task, such as dumping the database contents to an LDIF file or removing obsolete suppliers from the replication topology.
You can set the nsds5Task attribute to one of the following values:
-
cl2ldif: Exports the changelog to an LDIF file in the/var/lib/dirsrv/slapd-instance_name/changelogdb/directory. -
ldif2cl: Imports the changelog from an LDIF file stored in the/var/lib/dirsrv/slapd-instance_name/changelogdb/directory. -
cleanruv: Removes a Replica Update Vector (RUV) from the suppliers where you run the operation. -
cleanallruv: Removes RUVs from all servers in a replication topology.
You do not have to restart the server for this setting to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
*
*
*
* |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5Task: cleanallruv |
3.1.9. Replication Attributes under cn=ReplicationAgreementName,cn=replica,cn=suffixName,cn=mapping tree,cn=config
The replication attributes that concern the replication agreement are stored under cn=ReplicationAgreementName, cn=replica,cn=suffixDN, cn=mapping tree,cn=config. The cn=ReplicationAgreementName entry is an instance of the nsDS5ReplicationAgreement object class. Replication agreements are configured only on supplier replicas.
3.1.9.1. cn
This attribute is used for naming. Once this attribute has been set, it cannot be modified. This attribute is required for setting up a replication agreement.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
Any valid |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: SupplierAtoSupplierB |
3.1.9.2. description
Free form text description of the replication agreement. This attribute can be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | description: Replication Agreement between Server A and Server B. |
3.1.9.3. nsDS5ReplicaBindDN
This attribute sets the DN to use when binding to the consumer during replication. The value of this attribute must be the same as the one in cn=replica on the consumer replica. This may be empty if certificate-based authentication is used, in which case the DN used is the subject DN of the certificate, and the consumer must have appropriate client certificate mapping enabled. This can also be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid DN (can be empty if client certificates are used) |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindDN: cn=replication manager,cn=config |
3.1.9.4. nsDS5ReplicaBindMethod
This attribute sets the method for the server to use to bind to the consumer server.
The nsDS5ReplicaBindMethod supports the following values:
-
Empty or
SIMPLE: The server uses password-based authentication. When using this bind method, additionally, set thensds5ReplicaBindDNandnsds5ReplicaCredentialsparameters to provide a user name and password. -
SSLCLIENTAUTH: Enables certificate-based authentication between the supplier and consumer. For this, the consumer server must have a certificate mapping configured to map the supplier’s certificate to the replication manager entry. SASL/GSSAPI: Enables Kerberos authentication using SASL. This requires that the supplier server have a Kerberos keytab, and the consumer server a SASL mapping entry configured to map the supplier’s Kerberos principal to the replication manager entry.For further details, see the following sections in the Red Hat Directory Server Administration Guide:
-
SASL/DIGEST-MD5: Enables password-based authentication using SASL with theDIGEST-MD5mechanism. When using this bind method, additionally, set thensds5ReplicaBindDNandnsds5ReplicaCredentialsparameters to provide a user name and password.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | SIMPLE | SSLCLIENTAUTH | SASL/GSSAPI | SASL/DIGEST |
| Default Value | SIMPLE |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaBindMethod: SIMPLE |
3.1.9.5. nsds5ReplicaBootstrapBindDN
The nsds5ReplicaBootstrapBindDN parameter sets the fall-back bind distinguished name (DN) that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapBindDN: cn=replication manager,cn=config |
3.1.9.6. nsds5ReplicaBootstrapBindMethod
The nsds5ReplicaBootstrapBindMethod parameter sets the password for the fall-back login mechanism that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | SIMPLE | SSLCLIENTAUTH | SASL/GSSAPI | SASL/DIGEST |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapBindMethod: SIMPLE |
3.1.9.7. nsds5ReplicaBootstrapCredentials
The nsds5ReplicaBootstrapCredentials parameter sets the password for the fall-back bind distinguished name (DN) that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
Directory Server automatically hashes the password using the AES reversible password encryption algorithm when you set the parameter in clear text.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid string. |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapCredentials: password |
3.1.9.8. nsds5ReplicaBootstrapTransportInfo
The nsds5ReplicaBootstrapTransportInfo parameter sets the encryption method for the connection to and from the replica for the fall-back connection that Directory Server uses when the supplier fails to bind to a consumer due to an LDAP_INVALID_CREDENTIALS (err=49), LDAP_INAPPROPRIATE_AUTH (err=48), or LDAP_NO_SUCH_OBJECT (err=32) error.
In these cases, Directory Server uses the information from the nsds5ReplicaBootstrapBindDN, nsds5ReplicaBootstrapCredentials, nsds5ReplicaBootstrapBindMethod, and nsds5ReplicaBootstrapTransportInfo parameters to establish the connection. If the server also fails to establish the connection using these bootstrap settings, the server stops trying to connect.
The attribute takes the following values:
-
TLS: The connection uses theStartTLScommand to start the encryption. -
SSL: The connection uses LDAPS with TLS encryption. -
LDAP: The connection is not encrypted.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | TLS | SSL | LDAP |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaBootstrapTransportInfo: SSL |
3.1.9.9. nsDS5ReplicaBusyWaitTime
This attribute sets the amount of time in seconds a supplier should wait after a consumer sends back a busy response before making another attempt to acquire access. The default value is three (3) seconds. If the attribute is set to a negative value, Directory Server sends the client a message and an LDAP_UNWILLING_TO_PERFORM error code.
The nsDS5ReplicaBusyWaitTime attribute works in conjunction with the nsDS5ReplicaSessionPauseTime attribute. The two attributes are designed so that the nsDS5ReplicaSessionPauseTime interval is always at least one second longer than the interval specified for nsDS5ReplicaBusyWaitTime. The longer interval gives waiting suppliers a better chance to gain consumer access before the previous supplier can re-access the consumer.
Set the nsDS5ReplicaBusyWaitTime attribute at any time by using changetype:modify with the replace operation. The change takes effect for the next update session if one is already in progress.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid integer |
| Default Value | 3 |
| Syntax | Integer |
| Example | nsDS5ReplicaBusyWaitTime: 3 |
3.1.9.10. nsDS5ReplicaChangesSentSinceStartup
This read-only attribute shows the number of changes sent to this replica since the server started. The actual value in the attribute is stored as a binary blob; in the Directory Server Console, this value is a ratio, in the form replica_id:changes_sent/changes_skipped. For example, for 100 changes sent and no changes skipped for replica 7, the attribute value is displayed in the Console as 7:100/0.
In the command line, the attribute value is shown in a binary form. For example:
nsds5replicaChangesSentSinceStartup:: MToxLzAg
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsds5replicaChangesSentSinceStartup:: MToxLzAg |
3.1.9.11. nsDS5ReplicaCredentials
This attribute sets the credentials for the bind DN specified in the nsDS5ReplicaBindDN attribute. Directory Server uses this password to connect to the consumer.
The example below shows the encrypted value, as stored in the /etc/dirsrv/slapd-instance_name/dse.ldif file and not the actual password. To set a value, set it in clear text, for example nsDS5ReplicaCredentials: password. Directory Server then encrypts the password using the AES reversible password encryption schema when it stores the value.
When you use certificate-based authentication, this attribute does not have a value set.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid password |
| Default Value | |
| Syntax | DirectoryString {AES-Base64-algorithm-id}encoded_password |
| Example | nsDS5ReplicaCredentials: {AES-TUhNR0NT…}VoglUB8GG5A… |
3.1.9.12. nsds5ReplicaEnabled
This attribute sets whether a replication agreement is active, meaning whether replication is occurring per that agreement. The default is on, so that replication is enabled.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nsds5ReplicaEnabled: off |
3.1.9.13. nsds5ReplicaFlowControlPause
This parameters sets the time in milliseconds to pause after reaching the number of entries and updates set in the nsds5ReplicaFlowControlWindow parameter is reached. Updating both the nsds5ReplicaFlowControlWindow and nsds5ReplicaFlowControlPause parameters enables you to fine-tune the replication throughput. For further details, see Section 3.1.9.14, “nsds5ReplicaFlowControlWindow”.
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=replication_agreement_name,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | 0 to maximum 64-bit long |
| Default Value | 2000 |
| Syntax | Integer |
| Example | nsds5ReplicaFlowControlPause: 2000 |
3.1.9.14. nsds5ReplicaFlowControlWindow
This attribute sets the maximum number of entries and updates sent by a supplier, which are not acknowledged by the consumer. After reaching the limit, the supplier pauses the replication agreement for the time set in the nsds5ReplicaFlowControlPause parameter. Updating both the nsds5ReplicaFlowControlWindow and nsds5ReplicaFlowControlPause parameters enables you to fine-tune the replication throughput.
Update this setting if the supplier sends entries and updates faster than the consumer can import or update, and acknowledge the data. In this case, the following message is logged in the supplier’s error log file:
Total update flow control gives time (2000 msec) to the consumer before sending more entries [ msgid sent: xxx, rcv: yyy]) If total update fails you can try to increase nsds5ReplicaFlowControlPause and/or decrease nsds5ReplicaFlowControlWindow in the replica agreement configuration
This setting does not require restarting the server to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=replication_agreement_name,cn=replica,cn=suffix_DN,cn=mapping tree,cn=config |
| Valid Values | 0 to maximum 64-bit long |
| Default Value | 1000 |
| Syntax | Integer |
| Example | nsds5ReplicaFlowControlWindow: 1000 |
3.1.9.15. nsDS5ReplicaHost
This attribute sets the host name for the remote server containing the consumer replica. Once this attribute has been set, it cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid host server name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaHost: ldap2.example.com |
3.1.9.16. nsDS5ReplicaLastInitEnd
This optional, read-only attribute states when the initialization of the consumer replica ended.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastInitEnd: 20200504121603Z |
3.1.9.17. nsDS5ReplicaLastInitStart
This optional, read-only attribute states when the initialization of the consumer replica started.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastInitStart: 20200503030405 |
3.1.9.18. nsDS5ReplicaLastInitStatus
This optional, read-only attribute provides status for the initialization of the consumer. There is typically a numeric code followed by a short string explaining the status. Zero (0) means success.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 (Consumer Initialization Succeeded), followed by any other status message. |
| Default Value | |
| Syntax | String |
| Example | nsDS5ReplicaLastInitStatus: 0 Consumer Initialization Succeeded |
3.1.9.19. nsDS5ReplicaLastUpdateEnd
This read-only attribute states when the most recent replication schedule update ended.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastUpdateEnd: 20200502175801Z |
3.1.9.20. nsDS5ReplicaLastUpdateStart
This read-only attribute states when the most recent replication schedule update started.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values |
YYYYMMDDhhmmssZ is the date/time in Generalized Time form at which the connection was opened. This value gives the time in relation to Greenwich Mean Time. The hours are set with a 24-hour clock. The |
| Default Value | |
| Syntax | GeneralizedTime |
| Example | nsDS5ReplicaLastUpdateStart: 20200504122055Z |
3.1.9.21. nsds5replicaLastUpdateStatus
In the read-only nsds5replicaLastUpdateStatus attribute of each replication agreement, Directory Server displays the latest status of the agreement. For a list of status, see Appendix B, Replication Agreement Status.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5replicaLastUpdateStatus: Error (0) Replica acquired successfully: Incremental update succeeded |
3.1.9.22. nsDS5ReplicaPort
This attribute sets the port number for the remote server containing the replica. Once this attribute has been set, it cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Port number for the remote server containing the replica |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaPort:389 |
3.1.9.23. nsDS5ReplicaReapActive
This read-only attribute specifies whether the background task that removes old tombstones (deleted entries) from the database is active. See Section 3.1.8.23, “nsDS5ReplicaTombstonePurgeInterval” for more information about this task. A value of zero (0) means that the task is inactive, and a value of 1 means that the task is active. If this value is set manually, the server ignores the modify request.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 0 | 1 |
| Default Value | |
| Syntax | Integer |
| Example | nsDS5ReplicaReapActive: 0 |
3.1.9.24. nsDS5BeginReplicaRefresh
Initializes the replica. This attribute is absent by default. However, if this attribute is added with a value of start, then the server initializes the replica and removes the attribute value. To monitor the status of the initialization procedure, poll for this attribute. When initialization is finished, the attribute is removed from the entry, and the other monitoring attributes can be used for detailed status inquiries.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | stop | start |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5BeginReplicaRefresh: start |
3.1.9.25. nsDS5ReplicaRoot
This attribute sets the DN at the root of a replicated area. This attribute must have the same value as the suffix of the database being replicated and cannot be modified.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Suffix of the database being replicated - same as suffixDN above |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaRoot: "dc=example,dc=com" |
3.1.9.26. nsDS5ReplicaSessionPauseTime
This attribute sets the amount of time in seconds a supplier should wait between update sessions. The default value is 0. If the attribute is set to a negative value, Directory Server sends the client a message and an LDAP_UNWILLING_TO_PERFORM error code.
The nsDS5ReplicaSessionPauseTime attribute works in conjunction with the nsDS5ReplicaBusyWaitTime attribute. The two attributes are designed so that the nsDS5ReplicaSessionPauseTime interval is always at least one second longer than the interval specified for nsDS5ReplicaBusyWaitTime. The longer interval gives waiting suppliers a better chance to gain consumer access before the previous supplier can re-access the consumer.
-
If either attribute is specified but not both,
nsDS5ReplicaSessionPauseTimeis set automatically to1second more thannsDS5ReplicaBusyWaitTime. -
If both attributes are specified, but
nsDS5ReplicaSessionPauseTimeis less than or equal tonsDS5ReplicaBusyWaitTime,nsDS5ReplicaSessionPauseTimeis set automatically to1second more thannsDS5ReplicaBusyWaitTime.
When setting the values, ensure that the nsDS5ReplicaSessionPauseTime interval is at least 1 second longer than the interval specified for nsDS5ReplicaBusyWaitTime. Increase the interval as needed until there is an acceptable distribution of consumer access among the suppliers.
Set the nsDS5ReplicaSessionPauseTime attribute at any time by using changetype:modify with the replace operation. The change takes effect for the next update session if one is already in progress.
If Directory Server has to reset the value of nsDS5ReplicaSessionPauseTime automatically, the value is changed internally only. The change is not visible to clients, and it is not saved to the configuration file. From an external viewpoint, the attribute value appears as originally set.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid integer |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsDS5ReplicaSessionPauseTime: 0 |
3.1.9.27. nsds5ReplicaStripAttrs
Fractional replication allows a list of attributes which are removed from replication updates (nsDS5ReplicatedAttributeList). However, a change to an excluded attribute still triggers a modify event and generates an empty replication update.
The nsds5ReplicaStripAttrs attribute adds a list of attributes which cannot be sent in an empty replication event and are stripped from the update sequence. This logically includes operational attribtes like modifiersName.
If a replication event is not empty, the stripped attributes are replicated. These attributes are removed from updates only if the event would otherwise be emtpy.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | A space-separated list of any supported directory attribute |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsds5ReplicaStripAttrs: modifiersname modifytimestamp |
3.1.9.28. nsDS5ReplicatedAttributeList
This allowed attribute specifies any attributes that are not replicated to a consumer server. Fractional replication allows databases to be replicated across slow connections or to less secure consumers while still protecting sensitive information. By default, all attributes are replicated, and this attribute is not present. For more information on fractional replication, see the "Managing Replication" chapter in the Red Hat Directory Server Administration Guide.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicatedAttributeList: (objectclass=*) $ EXCLUDE accountlockout memberof |
3.1.9.29. nsDS5ReplicatedAttributeListTotal
This allowed attribute specifies any attributes that are not replicated to a consumer server during a total update.
Fractional replication only replicates specified attributes. This improves the overall network performance. However, there may be times when administrators want to restrict some attributes using fractional replication during an incremental update but allow those attributes to be replicated during a total update (or vice versa).
By default, all attributes are replicated. nsDS5ReplicatedAttributeList sets the incremental replication list; if only nsDS5ReplicatedAttributeList is set, then this list applies to total updates as well.
nsDS5ReplicatedAttributeListTotal sets the list of attributes to exclude only from a total update.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicatedAttributeListTotal: (objectclass=*) $ EXCLUDE accountlockout |
3.1.9.30. nsDS5ReplicaTimeout
This allowed attribute specifies the number of seconds outbound LDAP operations waits for a response from the remote replica before timing out and failing. If the server writes Warning: timed out waiting messages in the error log file, then increase the value of this attribute.
Find out the amount of time the operation actually lasted by examining the access log on the remote machine, and then set the nsDS5ReplicaTimeout attribute accordingly to optimize performance.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer value (2147483647) in seconds |
| Default Value | 120 |
| Syntax | Integer |
| Example | nsDS5ReplicaTimeout: 120 |
3.1.9.31. nsDS5ReplicaTransportInfo
This attribute sets the type of transport used for transporting data to and from the replica. This attribute cannot be modified once it is set.
The attribute takes the following values:
-
StartTLS: The connection uses encryption using theStartTLScommand. -
LDAPS: The connection uses TLS encryption. -
LDAP: The connection uses the unencrypted LDAP protocol. This value is also used, if thensDS5ReplicaTransportInfoattribute is not set.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | StartTLS | LDAPS | LDAP |
| Default Value | absent |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaTransportInfo: StartTLS |
3.1.9.32. nsDS5ReplicaUpdateInProgress
This read-only attribute states whether or not a replication update is in progress.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | true | false |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS5ReplicaUpdateInProgress: true |
3.1.9.33. nsDS5ReplicaUpdateSchedule
This multi-valued attribute specifies the replication schedule and can be modified. Changes made to this attribute take effect immediately. Modifying this value can be useful to pause replication and resume it later. For example, if this value to 0000-0001 0, this in effect causes the server to stop sending updates for this replication agreement. The server continues to store them for replay later. If the value is later changed back to 0000-2359 0123456, this makes replication immediately resume and sends all pending changes.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | Time schedule presented as XXXX-YYYY 0123456, where XXXX is the starting hour, YYYY is the finishing hour, and the numbers 0123456 are the days of the week starting with Sunday. |
| Default Value | 0000-2359 0123456 (all the time) |
| Syntax | Integer |
| Example | nsDS5ReplicaUpdateSchedule: 0000-2359 0123456 |
3.1.9.34. nsDS5ReplicaWaitForAsyncResults
In a replication environment, the nsDS5ReplicaWaitForAsyncResults parameter sets the time in milliseconds for which a supplier waits if the consumer is not ready before resending data.
Note that if you set the parameter to 0, the default value is used.
| Parameter | Description |
|---|---|
| Entry DN | cn=ReplicationAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsDS5ReplicaWaitForAsyncResults: 100 |
3.1.9.35. nsDS50ruv
This attribute stores the last replica update vector (RUV) read from the consumer of this replication agreement. It is always present and must not be changed.
3.1.9.36. nsruvReplicaLastModified
This attribute contains the most recent time that an entry in the replica was modified and the changelog was updated.
3.1.9.37. nsds5ReplicaProtocolTimeout
When stopping the server, disabling replication, or removing a replication agreement, there is a timeout on how long to wait before stopping replication when the server is under load. The nsds5ReplicaProtocolTimeout attribute can be used to configure this timeout and its default value is 120 seconds.
There may be scenarios where a timeout of 2 minutes is too long, or not long enough. For example, a particular replication agreement may need more time before ending a replication session during a shutdown.
This attribute can be added to the main replication configuration entry for a back end:
| Parameter | Description |
|---|---|
| Entry DN | cn=replica,cn=dc\3Dexample\2Cdc\3Dcom,cn=mapping tree,cn=config |
| Valid Range | 0 to maximum 32-bit integer (2147483647) in seconds |
| Default value | 120 |
| Syntax | Integer |
| Example | nsds5ReplicaProtocolTimeout: 120 |
The nsds5ReplicaProtocolTimeout attribute can also be added to a replication agreement. The replication agreement protocol timeout overrides the timeout set in the main replica configuration entry. This allows different timeouts for different replication agreements. If a replication session is in progress, a new timeout will abort that session and allow the server to shutdown.
3.1.10. Synchronization Attributes under cn=syncAgreementName,cn=WindowsReplica,cn=suffixName,cn=mapping tree,cn=config
The synchronization attributes that concern the synchronization agreement are stored under cn=syncAgreementName, cn=WindowsReplica,cn=suffixDN, cn=mapping tree,cn=config. The cn=syncAgreementName entry is an instance of the nsDSWindowsReplicationAgreement object class. For synchronization agreement configuration attributes to be taken into account by the server, this object class (in addition to the top object class) must be present in the entry. Synchronization agreements are configured only on databases that are enabled to synchronize with Windows Active Directory servers.
| cn | nsDS5ReplicaLastUpdateEnd |
| description | nsDS5ReplicaLastUpdateStart |
| nsDS5ReplicaBindDN (the Windows sync manager ID) | nsDS5ReplicaLastUpdateStatus |
| nsDS5ReplicaBindMethod | nsDS5ReplicaPort |
| nsDS5ReplicaBusyWaitTime | nsDS5ReplicaRoot |
| nsDS5ReplicaChangesSentSinceStartup | nsDS5ReplicaSessionPauseTime |
| nsDS5ReplicaCredentials (the Windows sync manager password) | nsDS5ReplicaTimeout |
| nsDS5ReplicaHost (the Windows host) | nsDS5ReplicaTransportInfo |
| nsDS5ReplicaLastInitEnd | nsDS5ReplicaUpdateInProgress |
| nsDS5ReplicaLastInitStart | nsDS5ReplicaUpdateSchedule |
| nsDS5ReplicaLastInitStatus | nsDS50ruv |
| winSyncMoveAction | winSyncInterval |
| nsds5ReplicaStripAttrs |
3.1.10.1. nsds7DirectoryReplicaSubtree
The suffix or DN of the Directory Server subtree that is being synchronized.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid suffix or subsuffix |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7DirectoryReplicaSubtree: ou=People,dc=example,dc=com |
3.1.10.2. nsds7DirsyncCookie
This string is created by Active Directory DirSync and gives the state of the Active Directory Server at the time of the last synchronization. The old cookie is sent to Active Directory with each Directory Server update; a new cookie is returned along with the Windows directory data. This means only entries which have changed since the last synchronization are retrieved.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7DirsyncCookie::khDKJFBZsjBDSCkjsdhIU74DJJVBXDhfvjmfvbhzxj |
3.1.10.3. nsds7NewWinGroupSyncEnabled
This attribute sets whether a new group created in the Windows sync peer is automatically synchronized by creating a new group on the Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7NewWinGroupSyncEnabled: on |
3.1.10.4. nsds7NewWinUserSyncEnabled
This attribute sets whether a new entry created in the Windows sync peer is automatically synchronized by creating a new entry on the Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | on | off |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7NewWinUserSyncEnabled: on |
3.1.10.5. nsds7WindowsDomain
This attribute sets the name of the Windows domain to which the Windows sync peer belongs.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid domain name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7WinndowsDomain: DOMAINWORLD |
3.1.10.6. nsds7WindowsReplicaSubtree
The suffix or DN of the Windows subtree that is being synchronized.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | Any valid suffix or subsuffix |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsDS7WindowsReplicaSubtree: cn=Users,dc=domain,dc=com |
3.1.10.7. oneWaySync
This attribute sets which direction to perform synchronization. This can either be from the Active Directory server to the Directory Server or from the Directory Server to the Active Directory server.
If this attribute is absent (the default), then the synchronization agreement is bi-directional, so changes made in both domains are synchronized.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | toWindows | fromWindows | null |
| Default Value | |
| Syntax | DirectoryString |
| Example | oneWaySync: fromWindows |
3.1.10.8. winSyncInterval
This attribute sets how frequently, in seconds, the Directory Server polls the Windows sync peer to look for changes in the Active Directory entries. If this entry is not set, the Directory Server checks the Windows server every five (5) minutes, meaning the default value is 300 (300 seconds).
This value can be set lower to write Active Directory changes over to the Directory Server faster or raised if the directory searches are taking too long.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | 1 to the maximum 32-bit integer value (2147483647) |
| Default Value | 300 |
| Syntax | Integer |
| Example | winSyncInterval: 600 |
3.1.10.9. winSyncMoveAction
The synchronization process starts at the root DN to begin evaluating entries for synchronization. Entries are correlated based on the samAccount in the Active Directory and the uid attribute in Directory Server. The synchronization plug-in notes if a previously synced entry (based on the samAccount/uid relationship) is removed from the synced subtree either because it is deleted or moved, then the synchronization plug-in recognizes that the entry is no longer to be synced.
The winSyncMoveAction attribute for the synchronization agreement sets instructions on how to handle these moved entries:
-
nonetakes no action, so if a synced Directory Server entry exists, it may be synced over to or create an Active Directory entry within scope. If no synced Directory Server entry exists, nothing happens at all (this is the default behavior). unsyncremoves any sync-related attributes (ntUserorntGroup) from the Directory Server entry but otherwise leaves the Directory Server entry intact. The Active Directory and Directory Server entries exist in tandem.ImportantThere is a risk when unsyncing entries that the Active Directory entry may be deleted at a later time, and the Directory Server entry will be left intact. This can create data inconsistency issues, especially if the Directory Server entry is ever used to recreate the entry on the Active Directory side later.
deletedeletes the corresponding entry on the Directory Server side, regardless of whether it was ever synced with Active Directory (this was the default behavior in 9.0).ImportantYou almost never want to delete a Directory Server entry without deleting the corresponding Active Directory entry. This option is available only for compatibility with Directory Server 9.0 systems.
| Parameter | Description |
|---|---|
| Entry DN | cn=syncAgreementName,cn=replica,cn=suffixDN,cn=mapping tree,cn=config |
| Valid Values | none | delete | unsync |
| Default Value | none |
| Syntax | DirectoryString |
| Example | winSyncMoveAction: unsync |
3.1.11. cn=monitor
Information used to monitor the server is stored under cn=monitor. This entry and its children are read-only; clients cannot directly modify them. The server updates this information automatically. This section describes the cn=monitor attributes. The only attribute that can be changed by a user to set access control is the aci attribute.
If the nsslapd-counters attribute in cn=config is set to on (the default setting), then all of the counters kept by the Directory Server instance increment using 64-bit integers, even on 32-bit machines or with a 32-bit version of Directory Server. For the cn=monitor entry, the 64-bit integers are used with the opsinitiated, opscompleted, entriessent, and bytessent counters.
The nsslapd-counters attribute enables 64-bit support for these specific database and server counters. The counters which use 64-bit integers are not configurable; the 64-bit integers are either enabled for all the allowed counters or disabled for all allowed counters.
connection
This attribute lists open connections and associated status and performance related information and values. These are given in the following format:
connection: A:YYYYMMDDhhmmssZ:B:C:D:E:F:G:H:I:IP_addressFor example:
connection: 69:20200604081953Z:6086:6086:-:cn=proxy,ou=special_users,dc=example,dc=test:0:11:27:7448846:ip=192.0.2.1-
A is the connection number, which is the number of the slot in the connection table associated with this connection. This is the number logged as
slot=A in the access log message when this connection was opened, and usually corresponds to the file descriptor associated with the connection. The attributedTableSizeshows the total size of the connection table. - YYYYMMDDhhmmssZ is the date and time, in GeneralizedTime form, at which the connection was opened. This value gives the time in relation to Greenwich Mean Time.
- B is the number of operations received on this connection.
- C is the number of completed operations.
-
D is
rif the server is in the process of reading BER from the network, empty otherwise. This value is usually empty (as in the example). -
E this is the bind DN. This may be empty or have value of
NULLDNfor anonymous connections. -
F is the connection maximum threads state:
1is in max threads,0is not. - G is the number of times this thread has hit the maximum threads value.
- H is the number of operations attempted that were blocked by the maximum number of threads.
-
I is the connection ID as reported in the logs as
conn=connection_ID. - IP_address is the IP address of the LDAP client.
B and C for the initiated and completed operations should ideally be equal.
currentConnections
This attribute shows the number of currently open and active Directory Server connections.
totalConnections
This attribute shows the total number of Directory Server connections. This number includes connections that have been opened and closed since the server was last started in addition to the currentConnections.
dTableSize
This attribute shows the size of the Directory Server connection table. Each connection is associated with a slot in this table, and usually corresponds to the file descriptor used by this connection. See Section 3.1.1.62, “nsslapd-conntablesize” for more information.
readWaiters
This attribute shows the number of connections where some requests are pending and not currently being serviced by a thread in Directory Server.
opsInitiated
This attribute shows the number of Directory Server operations initiated.
opsCompleted
This attribute shows the number of Directory Server operations completed.
entriesSent
This attribute shows the number of entries sent by Directory Server.
bytesSent
This attribute shows the number of bytes sent by Directory Server.
currentTime
This attribute shows the current time, given in Greenwich Mean Time (indicated by generalizedTime syntax Z notation; for example, 20200202131102Z).
startTime
This attribute shows the Directory Server start time given in Greenwich Mean Time, indicated by generalizedTime syntax Z notation. For example, 20200202131102Z.
version
This attribute shows the Directory Server vendor, version, and build number. For example, Red Hat/11.3.1 B2020.274.08.
threads
This attribute shows the number of threads used by the Directory Server. This should correspond to nsslapd-threadnumber in cn=config.
nbackEnds
This attribute shows the number of Directory Server database back ends.
backendMonitorDN
This attribute shows the DN for each Directory Server database backend. For further information on monitoring the database, see the following sections:
- Section 4.4.9, “Database Attributes under cn=attributeName,cn=encrypted attributes,cn=database_name,cn=ldbm database,cn=plugins,cn=config”
- Section 4.4.5, “Database Attributes under cn=database,cn=monitor,cn=ldbm database,cn=plugins,cn=config”
- Section 4.5.4, “Database Link Attributes under cn=monitor,cn=database instance name,cn=chaining database,cn=plugins,cn=config”
3.1.12. cn=replication
This entry has no attributes. When configuring legacy replication, those entries are stored under this cn=replication node, which serves as a placeholder.
3.1.13. cn=sasl
Entries which contain SASL mapping configurations are stored under cn=mapping,cn=sasl,cn=config. The cn=sasl entry is an instance of the nsContainer object class. Each mapping underneath it is an instance of the nsSaslMapping object class.
3.1.13.1. nsSaslMapBaseDNTemplate
This attribute contains the search base DN template used in SASL identity mapping.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | Any valid DN |
| Default Value | |
| Syntax | IA5String |
| Example | nsSaslMapBaseDNTemplate: ou=People,dc=example,dc=com |
3.1.13.2. nsSaslMapFilterTemplate
This attribute contains the search filter template used in SASL identity mapping.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | IA5String |
| Example | nsSaslMapFilterTemplate: (cn=\1) |
3.1.13.3. nsSaslMapPriority
Directory Server enables you to set multiple simple authentication and security layer (SASL) mappings. If SASL fallback is enabled by the nsslapd-sasl-mapping-fallback parameter, you can set the nsSaslMapPriority attribute to prioritize the individual SASL mappings.
This setting does not require a server restart to take effect.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | 1 (highest priority) - 100 (lowest priority) |
| Default Value | 100 |
| Syntax | Integer |
| Example | nsSaslMapPriority: 100 |
3.1.13.4. nsSaslMapRegexString
This attribute contains a regular expression used to map SASL identity strings.
| Parameter | Description |
|---|---|
| Entry DN | cn=mapping_name,cn=mapping,cn=sasl,cn=config |
| Valid Values | Any valid regular expression |
| Default Value | |
| Syntax | IA5String |
| Example | nsSaslMapRegexString: \(.*\) |
3.1.14. cn=SNMP
SNMP configuration attributes are stored under cn=SNMP,cn=config. The cn=SNMP entry is an instance of the nsSNMP object class.
3.1.14.1. nssnmpenabled
This attribute sets whether SNMP is enabled.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | on | off |
| Default Value | on |
| Syntax | DirectoryString |
| Example | nssnmpenabled: off |
3.1.14.2. nssnmporganization
This attribute sets the organization to which the Directory Server belongs.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Organization name |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmporganization: Red Hat, Inc. |
3.1.14.3. nssnmplocation
This attribute sets the location within the company or organization where the Directory Server resides.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Location |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmplocation: B14 |
3.1.14.4. nssnmpcontact
This attribute sets the email address of the person responsible for maintaining the Directory Server.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Contact email address |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmpcontact: jerome@example.com |
3.1.14.5. nssnmpdescription
Provides a unique description of the Directory Server instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Description |
| Default Value | |
| Syntax | DirectoryString |
| Example | nssnmpdescription: Employee directory instance |
3.1.14.6. nssnmpmasterhost
nssnmpmasterhost is deprecated. This attribute is deprecated with the introduction of net-snmp. The attribute still appears in dse.ldif but without a default value.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | machine host name or localhost |
| Default Value | <blank> |
| Syntax | DirectoryString |
| Example | nssnmpmasterhost: localhost |
3.1.14.7. nssnmpmasterport
The nssnmpmasterport attribute was deprecated with the introduction of net-snmp. The attribute still appears in dse.ldif but without a default value.
| Parameter | Description |
|---|---|
| Entry DN | cn=SNMP,cn=config |
| Valid Values | Operating system dependent port number. See the operating system documentation for further information. |
| Default Value | <blank> |
| Syntax | Integer |
| Example | nssnmpmasterport: 199 |
3.1.15. SNMP Statistic Attributes
Table 3.7, “SNMP Statistic Attributes” contains read-only attributes which list the statistics available for LDAP and SNMP clients. Unless otherwise noted, the value for the given attribute is the number of requests received by the server or results returned by the server since startup. Some of these attributes are not used by or are not applicable to the Directory Server but are still required to be present by SNMP clients.
If the nsslapd-counters attribute in cn=config is set to on (the default setting), then all of the counters kept by the Directory Server instance increment using 64-bit integers, even on 32-bit machines or with a 32-bit version of Directory Server. All of the SNMP statistics attributes use the 64-bit integers, if it is configured.
The nsslapd-counters attribute enables 64-bit integers for these specific database and server counters. The counters which use 64-bit integers are not configurable; 64-bit integers are either enabled for all the allowed counters or disabled for all allowed counters.
| Attribute | Description |
|---|---|
| AnonymousBinds | This shows the number of anonymous bind requests. |
| UnAuthBinds | This shows the number of unauthenticated (anonymous) binds. |
| SimpleAuthBinds | This shows the number of LDAP simple bind requests (DN and password). |
| StrongAuthBinds | This shows the number of LDAP SASL bind requests, for all SASL mechanisms. |
| BindSecurityErrors | This shows the number of number of times an invalid password was given in a bind request. |
| InOps | This shows the total number of all requests received by the server. |
| ReadOps |
Not used. This value is always |
| CompareOps | This shows the number of LDAP compare requests. |
| AddEntryOps | This shows the number of LDAP add requests. |
| RemoveEntryOps | This shows the number of LDAP delete requests. |
| ModifyEntryOps | This shows the number of LDAP modify requests. |
| ModifyRDNOps | This shows the number of LDAP modify RDN (modrdn) requests. |
| ListOps |
Not used. This value is always |
| SearchOps | This shows the number of LDAP search requests. |
| OneLevelSearchOps | This shows the number of one-level search operations. |
| WholeSubtreeSearchOps | This shows the number of subtree-level search operations. |
| Referrals | This shows the number of LDAP referrals returned. |
| Chainings |
Not used. This value is always |
| SecurityErrors | This shows the number of errors returned that were security related, such as invalid passwords, unknown or invalid authentication methods, or stronger authentication required. |
| Errors | This shows the number of errors returned. |
| Connections | This shows the number of currently open connections. |
| ConnectionSeq | This shows the total number of connections opened, including both currently open and closed connections. |
| BytesRecv | This shows the number of bytes received. |
| BytesSent | This shows the number of bytes sent. |
| EntriesReturned | This shows the number of entries returned as search results. |
| ReferralsReturned | This provides information on referrals returned as search results (continuation references). |
| MasterEntries |
Not used. This value is always |
| CopyEntries |
Not used. This value is always |
| CacheEntries[a] |
If the server has only one database back end, this is the number of entries cached in the entry cache. If the server has more than one database back end, this value is |
| CacheHits |
If the server has only one database back end, this is the number of entries returned from the entry cache, rather than from the database, for search results. If the server has more than one database back end, this value is |
| SlaveHits |
Not used. This value is always |
[a]
CacheEntries and CacheHits are updated every ten (10) seconds. Red Hat strongly encourages using the database back end specific monitor entries for this and other database information.
| |
3.1.16. cn=tasks
Some core Directory Server tasks can be initiated by editing a directory entry using LDAP tools. These task entries are contained in cn=tasks. Each task can be invoked by updating an entry such as the following:
dn: cn=task_id,cn=task_type,cn=tasks,cn=config ...
In Red Hat Directory Server deployments before Directory Server 8.0, many Directory Server tasks were managed by the Administration Server. These tasks were moved to the core Directory Server configuration in version 8.0 and are invoked and administered by Directory Server under the cn=tasks entry.
There following tasks are managed under the cn=tasks entry:
- Section 3.1.16.2, “cn=import”
- Section 3.1.16.3, “cn=export”
- Section 3.1.16.4, “cn=backup”
- Section 3.1.16.5, “cn=restore”
- Section 3.1.16.6, “cn=index”
- Section 3.1.16.7, “cn=schema reload task”
- Section 3.1.16.8, “cn=memberof task”
- Section 3.1.16.9, “cn=fixup linked attributes”
- Section 3.1.16.10, “cn=syntax validate”
- Section 3.1.16.11, “cn=USN tombstone cleanup task”
- Section 3.1.16.12, “cn=cleanallruv”
- Section 3.1.16.13, “cn=abort cleanallruv”
- Section 3.1.16.14, “cn=automember rebuild membership”
- Section 3.1.16.15, “cn=automember export updates”
- Section 3.1.16.16, “cn=automember map updates”
The common attributes for these tasks are listed in Section 3.1.16.1, “Task Invocation Attributes for Entries under cn=tasks”.
The cn=tasks entry itself has no attributes and serves as the parent and container entry for the individual task entries.
Task entries are not permanent configuration entries. They only exist in the configuration file for as long as the task operation is running or until the ttl period expires. Then, the entry is deleted automatically by the server.
3.1.16.1. Task Invocation Attributes for Entries under cn=tasks
Five tasks which administer Directory Server instances have configuration entries which initiate and identify individual operations. These task entries are instances of the same object class, extensibleObject, and have certain common attributes which describe the state and behavior of Directory Server tasks. The task types can be import, export, backup, restore, index, schema reload, and memberof.
cn
The cn attribute identifies a new task operation to initiate. The cn attribute value can be anything, as long as it defines a new task.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: example task entry name |
nsTaskStatus
This attribute contains changing information about the status of the task, such as cumulative statistics or its current output message. The entire contents of the attribute may be updated periodically for as long as the process is running.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | case-exact string |
| Example | nsTaskStatus: Loading entries…. |
nsTaskLog
This entry contains all of the log messages for the task, including bothwarning and information messages. New messages are appended to the end of the entry value, so this attribute value grows larger, without erasing the original contents, by default.
Successful task operations, which have an nsTaskExitCode of 0, are only recorded in the nsTaskLog attribute. Any non-zero response, which indicates an error, may be recorded in the error log as an error, but the error message is only recorded in the nsTaskLog attribute. For this reason, use the information in the nsTaskLog attribute to find out what errors actuall occurred.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsTaskLog: example… |
nsTaskExitCode
This attribute contains the exit code for the task. This attribute only exists after the task is completed and any value is only valid if the task is complete. The result code can be any LDAP exit code, as listed in Section 7.4, “LDAP Result Codes”, but only a 0 value equals success; any other result code is an error.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 (success) to 97[a] |
| Default Value | |
| Syntax | Integer |
| Example | nsTaskExitCode: 0 |
[a]
Any response other than 0 is an error.
| |
nsTaskCurrentItem
This attribute shows the number of subtask which the task operation has completed, assuming the task can be broken down into subtasks. If there is only one task, then nsTaskCurrentItem is 0 while the task is running, and 1 when the task is complete. In this way, the attribute is analogous to a progress bar. When the nsTaskCurrentItem attribute has the same value as nsTaskTotalItems, then the task is completed.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsTaskCurrentItem: 148 |
nsTaskTotalItems
This attribute shows the total number of subtasks that must be completed for the task operation. When the nsTaskCurrentItem attribute has the same value as nsTaskTotalItems, then the task is completed.
This attribute value is set by the server and should not be edited.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | Integer |
| Example | nsTaskTotalItems: 152 |
nsTaskCancel
This attribute allows a task to be aborted while in progress. This attribute can be modified by users.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | |
| Syntax | Case-insensitive string |
| Example | nsTaskCancel: true |
ttl
This attribute sets the amount of time (in seconds) the task entry will remain in the DSE after the task has finished or aborted. Setting a ttl attribute allows the task entry to be polled for new status information without missing the exit code. Setting the ttl attribute to 0 means that the entry is not cached.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=task_type,cn=tasks,cn=config |
| Valid Values | 0 (cannot be cached) to the maximum 32 bit integer value (2147483647) |
| Default Value | |
| Syntax | DirectoryString |
| Example | ttl: 120 |
3.1.16.2. cn=import
An LDIF file or multiple LDIF files can be imported through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=import entry is a container entry for import task operations. The cn=import entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID, cn=import, cn=tasks, cn=config, uses the following attributes to define the import task.
An import task entry under cn=import must contain the LDIF file to import (in the nsFilename attribute) and the name of the instance into which to import the file (in the nsInstance attribute). Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example import,cn=import,cn=tasks,cn=config objectclass: extensibleObject cn: example import nsFilename: /home/files/example.ldif nsInstance: userRoot
As the import operation runs, the task entry will contain all of the server-generated task attributes listed in Section 3.1.16.1, “Task Invocation Attributes for Entries under cn=tasks”.
There are some optional attributes which can be used to refine the import operation, similar to the options for the ldif2db and ldif2db.pl scripts:
-
nsIncludeSuffix, which is analogous to the
-soption to specify the suffix to import -
nsExcludeSuffix, analogous to the
-xoption to specify a suffix or subtree to exclude from the import -
nsImportChunkSize, analogous to the
-coption to override starting a new pass during the import and merge the chunks - nsImportIndexAttrs, which sets whether to import attribute indexes (with no corollary in the script options)
-
nsUniqueIdGenerator, analogous to the
-goption to generate unique ID numbers for the entries -
nsUniqueIdGeneratorNamespace, analogous to the
-Goption to generate a unique, name-based ID for the entries
nsFilename
The nsFilename attribute contains the path and filenames of the LDIF files to import into the Directory Server instance. To import multiple files, add multiple instances of this attribute. For example:
nsFilename: file1.ldif nsFilename: file2.ldif
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-exact string, multi-valued |
| Example | nsFilename: /home/jsmith/example.ldif |
nsInstance
This attribute supplies the name of the database instance into which to import the files, such as userRoot or slapd-example.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | The name of a Directory Server instance database (any string) |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsInstance: userRoot |
nsIncludeSuffix
This attribute identifies a specific suffix or subtree to import from the LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsIncludeSuffix: ou=people,dc=example,dc=com |
nsExcludeSuffix
This attribute identifies suffixes or subtrees in the LDIF file to exclude from the import.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsExcludeSuffix: ou=machines,dc=example,dc=com |
nsImportChunkSize
This attribute defines the number of chunks to have during the import operation, which overrides the server’s detection during the import of when to start a new pass and merges the chunks.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | 0 to the maximum 32 bit integer value (2147483647) |
| Default Value | 0 |
| Syntax | Integer |
| Example | nsImportChunkSize: 10 |
nsImportIndexAttrs
This attribute sets whether to index the attributes that are imported into database instance.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsImportIndexAttrs: true |
nsUniqueIdGenerator
This sets whether to generate a unique ID for the imported entries. By default, this attribute generates time-based IDs.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | none (no unique ID) | empty (time-based ID) | deterministic namespace (name-based ID) |
| Default Value | empty |
| Syntax | Case-insensitive string |
| Example | nsUniqueIdGenerator: |
nsUniqueIdGeneratorNamespace
This attribute defines how to generate name-based IDs; the attribute sets the namespace to use to generate the IDs. This option is useful to import the same LDIF file into two Directory Server instances when the entries need to have the same IDs.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=import,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-insensitive string |
| Example | nsUniqueIdGeneratorNamespace: example |
3.1.16.3. cn=export
A database or multiple databases can be exported through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=export,cn=tasks,cn=config entry is a container for export task operations. These tasks are stored within this container and named cn=task_name,cn=export,cn=tasks,cn=config.
While the export operation is running, the task entry contains all of the server-generated task attributes listed in Section 3.1.16.1, “Task Invocation Attributes for Entries under cn=tasks”.
You can create export tasks manually or use the db2ldif.pl command. The following table displays the db2ldif.pl command-line options and their corresponding attributes:
db2ldif.pl option | Task attribute | Description |
|---|---|---|
|
|
| Sets the path to the exported LDIF file. |
|
|
| If enabled, use only the main database file only. |
|
|
| If enabled, store output in multiple files. |
|
|
| Sets the database name. |
|
|
| Enables you to suppress printing the sequence number. |
|
|
| If set, the export will include attributes to initialize a replica. |
|
|
| Sets the suffix to include in the exported file. |
|
|
| Enables you not to export the unique ID. |
|
|
| If set, long lines are not wrapped. |
|
|
| Sets the suffix to exclude in the exported file. |
nsFilename
The nsFilename attribute contains the path and filenames of the LDIF files to which to export the Directory Server instance database.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | Case-exact string, multi-valued |
| Example | nsFilename: /home/jsmith/example.ldif |
nsInstance
This attribute supplies the name of the database instance from which to export the database, such as userRoot or userRoot.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | The name of a Directory Server instance (any string) |
| Default Value | |
| Syntax | Case-exact string, multi-valued |
| Example | nsInstance: userRoot |
nsIncludeSuffix
This attribute identifies a specific suffix or subtree to export to an LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsIncludeSuffix: ou=people,dc=example,dc=com |
nsExcludeSuffix
This attribute identifies suffixes or subtrees in the database to exclude from the exported LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN, multi-valued |
| Example | nsExcludeSuffix: ou=machines,dc=example,dc=com |
nsUseOneFile
This attribute sets whether to export all Directory Server instances to a single LDIF file or separate LDIF files.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsUseOneFile: true |
nsExportReplica
This attribute identifies whether the exported database will be used in replication. For replicas, the proper attributes and settings will be included with the entry to initialize the replica automatically.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | Case-insensitive string |
| Example | nsExportReplica: true |
nsPrintKey
This attribute sets whether to print the entry ID number as the entry is processed by the export task.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsPrintKey: false |
nsUseId2Entry
The nsUseId2Entry attribute uses the main database index, id2entry, to define the exported LDIF entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | Case-insensitive string |
| Example | nsUseId2Entry: true |
nsNoWrap
This attribute sets whether to wrap long lines in the LDIF file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | false |
| Syntax | Case-insensitive string |
| Example | nsNoWrap: false |
nsDumpUniqId
This attribute sets that the unique IDs for the exported entries are not exported.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=export,cn=tasks,cn=config |
| Valid Values | true | false |
| Default Value | true |
| Syntax | Case-insensitive string |
| Example | nsDumpUniqId: true |
3.1.16.4. cn=backup
A database can be backed up through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=backup entry is a container entry for backup task operations. The cn=backup entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID, cn=backup, cn=tasks, cn=config, uses the following attributes to define the backup task.
A backup task entry under cn=backup must contain the location of the directory to which to copy the archive copy (in the nsArchiveDir attribute) and the type of database being backed up (in the nsDatabaseType attribute). Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example backup,cn=backup,cn=tasks,cn=config objectclass: extensibleObject cn: example backup nsArchiveDir: /export/backups/ nsDatabaseType: ldbm database
As the backup operation runs, the task entry will contain all of the server-generated task attributes listed in Section 3.1.16.1, “Task Invocation Attributes for Entries under cn=tasks”.
nsArchiveDir
This attribute gives the location of the directory to which to write the backup.
The backup directory here should usually be the same as the one configured in the nsslapd-bakdir attribute.
If this attribute is not included with the cn=backup task, the task will fail with an LDAP object class violation error (65).
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=backup,cn=tasks,cn=config |
| Valid Values | Any local directory location |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsArchiveDir: /export/backups |
nsDatabaseType
This attribute gives the kind of database being archived. Setting the database types signals what kind of backup plug-in the Directory Server should use to archive the database.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=backup,cn=tasks,cn=config |
| Valid Values | ldbm database |
| Default Value | ldbm database |
| Syntax | Case-exact string |
| Example | nsDatabaseType: ldbm database |
3.1.16.5. cn=restore
A database can be restored through the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=restore entry is a container entry for task operations to restore a database. The cn=restore entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID, cn=restore, cn=tasks, cn=config, uses the following attributes to define the restore task.
A restore task entry under cn=restore must contain the location of the directory from which to retrieve the archive copy (in the nsArchiveDir attribute) and the type of database being restored (in the nsDatabaseType attribute). Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example restore,cn=restore,cn=tasks,cn=config objectclass: extensibleObject cn: example restore nsArchiveDir: /export/backups/ nsDatabaseType: ldbm database
As the restore operation runs, the task entry will contain all of the server-generated task attributes listed in Section 3.1.16.1, “Task Invocation Attributes for Entries under cn=tasks”.
nsArchiveDir
This attribute gives the location of the directory to which to write the backup.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=restore,cn=tasks,cn=config |
| Valid Values | Any local directory location |
| Default Value | |
| Syntax | Case-exact string |
| Example | nsArchiveDir: /export/backups |
nsDatabaseType
This attribute gives the kind of database being archived. Setting the database types signals what kind of backup plug-in the Directory Server should use to archive the database.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=restore,cn=tasks,cn=config |
| Valid Values | ldbm database |
| Default Value | ldbm database |
| Syntax | Case-exact string |
| Example | nsDatabaseType: ldbm database |
3.1.16.6. cn=index
Directory attributes can be indexed though the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory.
The cn=index entry is a container entry for index task operations. The cn=index entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID, cn=index, cn=tasks, cn=config, uses the following attributes to define the backup task.
An index task entry under cn=index can create a standard index by identifying the attribute to be indexed and the type of index to create, both defined in the nsIndexAttribute attribute.
Alternatively, the index task can be used to generate virtual list view (VLV) indexes for an attribute using the nsIndexVLVAttribute attribute. This is the same as running the vlvindex script.
For example:
dn: cn=example presence index,cn=index,cn=tasks,cn=config objectclass: top objectclass: extensibleObject cn: example presence index nsInstance: userRoot nsIndexAttribute: cn:pres dn: cn=example VLV index,cn=index,cn=tasks,cn=config objectclass: extensibleObject cn: example VLV index nsIndexVLVAttribute: "by MCC ou=people,dc=example,dc=com"
As the index operation runs, the task entry will contain all of the server-generated task attributes listed in Section 3.1.16.1, “Task Invocation Attributes for Entries under cn=tasks”.
nsIndexAttribute
This attribute gives the name of the attribute to index and the types of indexes to apply. The format of the attribute value is the attribute name and a comma-separated list of index types, enclosed in double quotation marks. For example:
nsIndexAttribute: attribute:index1,index2| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=index,cn=tasks,cn=config |
| Valid Values | * Any attribute
* The index type, which can be |
| Default Value | |
| Syntax | Case-insensitive string, multi-valued |
| Example | * nsIndexAttribute: cn:pres,eq * nsIndexAttribute: description:sub |
nsIndexVLVAttribute
This attribute gives the name of the target entry for a VLV index. A virtual list view is based on a browsing index entry (as described in the Administration Guide), which defines the virtual list base DN, scope, and filter. The nsIndexVLVAttribute value is the browsing index entry, and the VLV creation task is run according to the browsing index entry parameters.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=index,cn=tasks,cn=config |
| Valid Values | RDN of the subentry of the VLV entry definition |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsIndexVLVAttribute: "browsing index sort identifier" |
3.1.16.7. cn=schema reload task
The directory schema is loaded when the directory instance is started or restarted. Any changes to the directory schema, including adding custom schema elements, are not loaded automatically and available to the instance until the server is restarted or by initiating a schema reload task.
Custom schema changes can be reloaded dynamically, without having to restart the Directory Server instance. This is done by initiating a schema reload task through creating a new task entry under the cn=tasks entry.
The custom schema file can be located in any directory; if not specified with the schemadir attribute, the server reloads the schema from the default /etc/dirsrv/slapd-instance/schema directory.
Any schema loaded from another directory must be copied into the schema directory or the schema will be lost when the server.
The schemd reload task is initiated though the command line by creating a special task entry which defines the parameters of the task and initiates the task. As soon as the task is complete, the task entry is removed from the directory. For example:
dn: cn=example schema reload,cn=schema reload task,cn=tasks,cn=config objectclass: extensibleObject cn:example schema reload schemadir: /export/schema
The cn=schema reload task entry is a container entry for schema reload operations. The cn=schema reload task entry itself has no attributes, but each of the task entries within this entry, such as cn=task_ID, cn=schema reload task, cn=tasks, cn=config, uses the schema reload attributes to define the individual reload task.
cn
The cn attribute identifies a new task operation to initiate. The cn attribute value can be anything, as long as it defines a new task.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=schema reload task,cn=tasks,cn=config |
| Valid Values | Any string |
| Default Value | |
| Syntax | DirectoryString |
| Example | cn: example reload task ID |
schemadir
This contains the full path to the directory containing the custom schema file.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=schema reload task,cn=tasks,cn=config |
| Valid Values | Any local directory path |
| Default Value | /etc/dirsrv/schema |
| Syntax | DirectoryString |
| Example | schemadir: /export/schema/ |
3.1.16.8. cn=memberof task
The memberOf attribute is created and managed by the Directory Server automatically to display group membership on the members' user entries. When the member attribute on a group entry is changed, all of the members' associated directory entries are automatically updated with their corresponding memberOf attributes.
The cn=memberof task (and the related fixup-memberof.pl script) is used to create the initial memberOf attributes on the member’s user entries in the directory. After the memberOf attributes are created, then the MemberOf Plug-in manages the memberOf attributes automatically.
The memberOf update task must give the DN of the entry or subtree to run the update task against (set in the basedn attribute). Optionally, the task can include a filter to identify the members' user entries to update (set in the filter attribute). For example:
dn: cn=example memberOf,cn=memberof task,cn=tasks,cn=config objectclass: extensibleObject cn:example memberOf basedn: ou=people,dc=example,dc=com filter: (objectclass=groupofnames)
When the task is complete, the task entry is removed from the directory.
The cn=memberof task entry is a container entry for memberOf update operations. The cn=memberof task entry itself has no attributes, but each of the task entries beneath this entry, such as cn=task_ID, cn=memberof task, cn=tasks, cn=config, uses its attributes to define the individual update task.
basedn
This attribute gives the base DN to use to search for the user entries to update the memberOf attribute.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=memberof task,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | |
| Syntax | DN |
| Example | basedn: ou=people,dc=example,dc=com |
filter
This attribute gives an optional LDAP filter to use to select which user entries to update the memberOf attribute. Each member of a group has a corresponding user entry in the directory.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=memberof task,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | (objectclass=*) |
| Syntax | DirectoryString |
| Example | filter: (l=Sunnyvale) |
3.1.16.9. cn=fixup linked attributes
The Directory Server has a Linked Attributes Plug-in which allows one attribute, set in one entry, to update another attribute in another entry automatically. Both entries have DNs for values. The DN value in the first entry points to the entry for the plug-in to update; the attribute in the second entry contains a DN back-pointer to the first entry.
This is similar to the way that the MemberOf Plug-in uses the member attribute in group entries to set memberOf attribute in user entries. With linked attributes, any attribute can be defined as a "link," and then another attribute is "managed" in affected entries.
The cn=fixup linked attributes (and the related fixup-linkedattrs.pl script) creates the managed attributes — based on link attributes that already exist in the database — in the user entries once the linking plug-in instance is created. After the linked and managed attributes are set, the Linked Attributes Plug-in maintains the managed attributes dynamically, as users change the link attributes.
The linked attributes update task can specify which linked attribute plug-in instance to update, set in the optional linkdn attribute. If this attribute is not set on the task entry, then all configured linked attributes are updated.
dn: cn=example,cn=fixup linked attributes,cn=tasks,cn=config objectclass: extensibleObject cn:example linkdn: cn=Example Link,cn=Linked Attributes,cn=plugins,cn=config
When the task is complete, the task entry is removed from the directory.
The cn=fixup linked attributes entry is a container entry for any linked attribute update operation. The cn=fixup linked attributes entry itself has no attributes related to individual tasks, but each of the task entries beneath this entry, such as cn=task_ID, cn=fixup linked attributes, cn=tasks, cn=config, uses its attributes to define the individual update task.
linkdn
Each linked-managed attribute pair is configured in a linked attributes plug-in instance. The linkdn attribute sets the specific linked attribute plug-in used to update the entries by giving the plug-in instance DN. For example:
linkdn: cn=Manager Attributes,cn=Linked Attributes,cn=plugins,cn=config
If no plug-in instance is given, then all linked attributes are updated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=fixup linked attributes,cn=tasks,cn=config |
| Valid Values | A DN (for an instance of the Linked Attributes plug-in) |
| Default Value | None |
| Syntax | DN |
| Example | linkdn: cn=Manager Links,cn=Linked Attributes,cn=plugins,cn=config |
3.1.16.10. cn=syntax validate
Syntax validation checks every modification to attributes to make sure that the new value has the required syntax for that attribute type. Attribute syntaxes are validated against the definitions in RFC 4514.
Syntax validation is enabled by default. However, syntax validation only audits changes to attribute values, such as when an attribute is added or modified. It does not validate the syntax of existing attribute values.
Validation of the existing syntax can be done with the syntax validation task. This task checks entries under a specified subtree (in the basedn attribute) and, optionally, only entries which match a specified filter (in the filter attribute).
dn: cn=example,cn=syntax validate,cn=tasks,cn=config objectclass: extensibleObject cn:example basedn: ou=people,dc=example,dc=com filter: "(objectclass=inetorgperson)"
When the task is complete, the task entry is removed from the directory.
If syntax validation is disabled or if a server is migrated, then there may be data in the server which does not conform to attribute syntax requirements. The syntax validation task can be run to evaluate those existing attribute values before enabling syntax validation.
The cn=syntax validate entry is a container entry for any syntax validation operation. The cn=syntax validate entry itself has no attributes that are specific to any task. Each of the task entries beneath this entry, such as cn=task_ID, cn=syntax validate, cn=tasks, cn=config, uses its attributes to define the individual update task.
basedn
Gives the subtree against which to run the syntax validation task. For example:
basedn: ou=people,dc=example,dc=com
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=syntax validate,cn=tasks,cn=config |
| Valid Values | Any DN |
| Default Value | None |
| Syntax | DN |
| Example | basedn: dc=example,dc=com |
filter
Contains an optional LDAP filter which can be used to identify specific entries beneath the given basedn against which to run the syntax validation task. If this attribute is not set on the task, then every entry within the basedn is audited. For example:
filter: "(objectclass=person)"
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=syntax validate,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | "(objectclass=*)" |
| Syntax | DirectoryString |
| Example | filter: "(objectclass=*)" |
3.1.16.11. cn=USN tombstone cleanup task
If the USN Plug-in is enabled, then update sequence numbers (USNs) are set on every entry whenever a directory write operation, like add or modify, occurs on that entry. This is reflected in the entryUSN operational attribute. This USN is set even when an entry is deleted, and the tombstone entries are maintained by the Directory Server instance.
The cn=USN tombstone cleanup task (and the related usn-tombstone-cleanup.pl script) deletes the tombstone entries maintained by the instance according to the back end database (in the backend attribute) or the suffix (in the suffix attribute). Optionally, only a subset of tombstone entries can be deleted by specifying a maximum USN to delete (in the max_usn_to_delete attribute), which preserves the most recent tombstone entries.
dn: cn=example,cn=USN tombstone cleanup task,cn=tasks,cn=config objectclass: extensibleObject cn:example backend: userroot max_usn_to_delete: 500
This task can only be launched if replication is not enabled. Replication maintains its own tombstone store, and these tombstone entries cannot be deleted by the USN Plug-in; they must be maintained by the replication processes. Thus, Directory Server prevents users from running the cleanup task for replicated databases.
Attempting to create this task entry for a replicated back end will return this error in the command line:
ldap_add: DSA is unwilling to perform
In the error log, there is a more explicit message that the suffix cannot have tombstone removed because it is replicated.
[...] usn-plugin - Suffix dc=example,dc=com is replicated. Unwilling to perform cleaning up tombstones.
When the task is complete, the task entry is removed from the directory.
The cn=USN tombstone cleanup task entry is a container entry for all USN tombstone delete operations. The cn=USN tombstone cleanup task entry itself has no attributes related to any individual task, but each of the task entries beneath this entry, such as cn=task_ID, cn=USN tombstone cleanup task, cn=tasks, cn=config, uses its attributes to define the individual update task.
backend
This gives the Directory Server instance back end, or database, to run the cleanup operation against. If the back end is not specified, then the suffix must be specified.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config |
| Valid Values | Database name |
| Default Value | None |
| Syntax | DirectoryString |
| Example | backend: userroot |
max_usn_to_delete
This gives the highest USN value to delete when removing tombstone entries. All tombstone entries up to and including that number are deleted. Tombstone entries with higher USN values (that means more recent entries) are not deleted.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config |
| Valid Values | Any integer |
| Default Value | None |
| Syntax | Integer |
| Example | max_usn_to_delete: 500 |
suffix
This gives the suffix or subtree in the Directory Server to run the cleanup operation against. If the suffix is not specified, then the back end must be given.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=USN tombstone cleanup task,cn=tasks,cn=config |
| Valid Values | Any subtree DN |
| Default Value | None |
| Syntax | DN |
| Example | suffix: dc=example,dc=com |
3.1.16.12. cn=cleanallruv
Information about the replication topology — all of the suppliers which are supplying updates to each other and other replicas within the same replication group — is contained in a set of metadata called the replica update vector (RUV). The RUV contains information about the supplier like its ID and URL, its latest change state number for changes made on the local server, and the CSN of the first change. Both suppliers and consumers store RUV information, and they use it to control replication updates.
When one supplier is removed from the replication topology, it may remain in another replica’s RUV. When the other replica is restarted, it can record errors in its log that the replication plug-in does not recognize the (removed) supplier.
[09/Sep/2020:09:03:43 -0600] NSMMReplicationPlugin - ruv_compare_ruv: RUV [changelog max RUV] does not
contain element [{replica 55 ldap://server.example.com:389} 4e6a27ca000000370000 4e6a27e8000000370000]
which is present in RUV [database RUV]
......
[09/Sep/2020:09:03:43 -0600] NSMMReplicationPlugin - replica_check_for_data_reload: Warning: for replica
dc=example,dc=com there were some differences between the changelog max RUV and the database RUV. If
there are obsolete elements in the database RUV, you should remove them using the CLEANRUV task. If they
are not obsolete, you should check their status to see why there are no changes from those servers in the changelog.When the supplier is permanently removed from the topology, then any lingering metadata about that supplier should be purged from every other supplier’s RUV entry.
The cn=cleanallruv task propagates through all servers in the replication topology and removes the RUV entries associated with the specified missing or obsolete supplier.
When the task is complete, the task entry is removed from the directory.
The cn=cleanallruv entry is a container entry for all clean RUV operations. The cn=cleanallruv entry itself has no attributes related to any individual task, but each of the task entries beneath this entry, such as cn=task_ID,cn=cleanallruv, cn=tasks,cn=config, uses its attributes to define the individual update task.
Each clean RUV task must specify the replica ID number of the replica RUV entries to remove, the based DN of the replicated database, and whether remaining updates from the missing supplier should be applied before removing the RUV data.
dn: cn=clean 55,cn=cleanallruv,cn=tasks,cn=config objectclass: extensibleObject replica-base-dn: dc=example,dc=com replica-id: 55 replica-force-cleaning: no cn: clean 55
replica-base-dn
This gives the Directory Server base DN associated with the replicated database. This is the base DN for the replicated suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=cleanallruv,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-base-dn: dc=example,dc=com |
replica-id
This gives the replica ID (defined in the nsDS5ReplicaId attribute for the replica configuration entry) of the replica to be removed from the replication topology.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=cleanallruv,cn=tasks,cn=config |
| Valid Values | 0 to 65534 |
| Default Value | None |
| Syntax | Integer |
| Example | replica-id: 55 |
replica-force-cleaning
This sets whether any outstanding updates from the replica to be removed should be applied (no) or whether the clean RUV operation should force-continue and lose any remaining updates (yes).
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=cleanallruv,cn=tasks,cn=config |
| Valid Values | no | yes |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-force-cleaning: no |
3.1.16.13. cn=abort cleanallruv
The Section 3.1.16.12, “cn=cleanallruv” task can take several minutes to propagate among all servers in the replication topology, even longer if the task processes all updates first. For performance or other maintenance considerations, it is possible to terminate a clean RUV task, and that termination is also propagated across all servers in the replication topology.
The termination task is an isntance of the cn=abort cleanallruv entry.
When the task is complete, the task entry is removed from the directory.
The cn=abort cleanallruv entry is a container entry for all clean RUV operations. The cn=abort cleanallruv entry itself has no attributes related to any individual task, but each of the task entries beneath this entry, such as cn=task_ID,cn=abort cleanallruv, cn=tasks,cn=config, uses its attributes to define the individual update task.
Each clean RUV task must specify the replica ID number of the replica RUV entries to which are currently being removed, the based DN of the replicated database, and whether the terminate task should complete when it has completed on all servers in the topology or just locally.
dn: cn=abort 55,cn=abort cleanallruv,cn=tasks,cn=config objectclass: extensibleObject replica-base-dn: dc=example,dc=com replica-id: 55 replica-certify-all: yes cn: abort 55
replica-base-dn
This gives the Directory Server base DN associated with the replicated database. This is the base DN for the replicated suffix.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-base-dn: dc=example,dc=com |
replica-id
This gives the replica ID (defined in the nsDS5ReplicaId attribute for the replica configuration entry) of the replica in the process of being removed from the replication topology.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config |
| Valid Values | 0 to 65534 |
| Default Value | None |
| Syntax | Integer |
| Example | replica-id: 55 |
replica-certify-all
This sets whether the task should complete successfully on all servers in the replication topology before completing the task locally (yes) or whether the task should show complete as soon as it completes locally (no).
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=abort cleanallruv,cn=tasks,cn=config |
| Valid Values | no | yes |
| Default Value | None |
| Syntax | DirectoryString |
| Example | replica-certify-all: yes |
3.1.16.14. cn=automember rebuild membership
The Auto Member Plug-in only runs when new entries are added to the directory. The plug-in ignores existing entries or entries which are edited to match an automembership rule.
The cn=automember rebuild membership task runs the current automembership rules against existing entries to update or rebuild group membership. All configured automembership rules are run against the identified entries (though not all rules may apply to a given entry).
basedn
This gives the Directory Server base DN to use to search for user entries. The entries in the specified DN are then updated according to the automembership rules.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | basedn: dc=example,dc=com |
filter
This attribute gives an LDAP filter to use to identify which user entries to update according to the configured automembership rules.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | None |
| Syntax | DirectoryString |
| Example | filter: (uid=*) |
scope
This attribute gives an LDAP search scope to use when searching the given base DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember rebuild membership,cn=tasks,cn=config |
| Valid Values | sub | base | one |
| Default Value | None |
| Syntax | DirectoryString |
| Example | scope: sub |
3.1.16.15. cn=automember export updates
This task runs against existing entries in the directory and exports the results of what users would have been added to what groups, based on the rules. This is useful for testing existing rules against existing users to see how your real deployment are performing.
The automembership-related changes are not executed. The proposed changes are written to a specified LDIF file.
basedn
This gives the Directory Server base DN to use to search for user entries. A test-run of the automembership rules will be run against the identified entries.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | basedn: dc=example,dc=com |
filter
This attribute gives an LDAP filter to use to identify which user entries to test-run the automembership rules.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | Any LDAP filter |
| Default Value | None |
| Syntax | DirectoryString |
| Example | filter: (uid=*) |
scope
This attribute gives an LDAP search scope to use when searching the given base DN.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | sub | base | one |
| Default Value | None |
| Syntax | DirectoryString |
| Example | scope: sub |
ldif
This attribute sets the full path and filename of an LDIF file to which to write the proposed changes from the test-run of the automembership rules. This file must be local to the system from which the task is initiated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember export updates,cn=tasks,cn=config |
| Valid Values | Local path and filename |
| Default Value | None |
| Syntax | DirectoryString |
| Example | ldif: /tmp/automember-results.ldif |
3.1.16.16. cn=automember map updates
This task runs against entries within an LDIF file (new entries or, potentially, test entries) and then writes the proposed changes to those user entries to an LDIF file. This can be very useful for testing a new rule, before applying it to (real) new or existing user entries.
The automembership-related changes are not executed. The proposed changes are written to a specified LDIF file.
ldif_in
This attribute sets the full path and filename of an LDIF file from which to import entries to test with the configured automembership rules. These entries are not imported into the directory and the changes are not performed. The entries are loaded and used by the test-run only.
This file must be local to the system from which the task is initiated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember map updates,cn=tasks,cn=config |
| Valid Values | Local path and filename |
| Default Value | None |
| Syntax | DirectoryString |
| Example | ldif_in: /tmp/automember-test-users.ldif |
ldif_out
This attribute sets the full path and filename of an LDIF file to which to write the proposed changes from the test-run of the automembership rules. This file must be local to the system from which the task is initiated.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=automember map updates,cn=tasks,cn=config |
| Valid Values | Local path and filename |
| Default Value | None |
| Syntax | DirectoryString |
| Example | ldif_out: /tmp/automember-results.ldif |
3.1.16.17. cn=des2aes
This task searches for all reversible password entries in the specified user database which are encoded using the outdated DES cipher, and converts them to the more secure AES cipher.
Previously, this task was being performed automatically on all suffixes during Directory Server startup. However, since the search for DES passwords was typically unindexed, it could take a very long time to perform on suffixes containing large amounts of entries, which in turn caused Directory Server to time out and fail to start. For that reason, the search is now performed only on cn=config, but to convert passwords in any other database you must run this task manually.
suffix
This multivalued attribute specifies a suffix to check for DES passwords and convert them to AES. If this attribute is omitted then all the back ends/suffixes are checked.
| Parameter | Description |
|---|---|
| Entry DN | cn=task_name,cn=des2aes,cn=tasks,cn=config |
| Valid Values | Directory suffix DN |
| Default Value | None |
| Syntax | DirectoryString |
| Example | suffix: dc=example,dc=com |
3.1.17. cn=uniqueid generator
The unique ID generator configuration attributes are stored under cn=uniqueid generator,cn=config. The cn=uniqueid generator entry is an instance of the extensibleObject object class.
nsstate
This attribute saves the state of the unique ID generator across server restarts. This attribute is maintained by the server. Do not edit it.
| Parameter | Description |
|---|---|
| Entry DN | cn=uniqueid generator,cn=config |
| Valid Values | |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsstate: AbId0c3oMIDUntiLCyYNGgAAAAAAAAAA |
3.1.18. Root DSE Configuration Parameters
3.1.18.1. nsslapd-return-default-opattr
Directory Server does not display the operational attributes in Root DSE searches. For example, if you are running the ldapsearch utility with the -s base -b "" parameters, only the user attributes are displayed. For clients expecting operational attributes in Root DSE search output, you can enable this behavior to provide backward compatibility:
- Stop the Directory Server instance.
Edit the
/etc/dirsrv/slapd-instance_name/dse.ldiffile and add the following parameters to thedn:section:nsslapd-return-default-opattr: supportedsaslmechanisms nsslapd-return-default-opattr: nsBackendSuffix nsslapd-return-default-opattr: subschemasubentry nsslapd-return-default-opattr: supportedldapversion nsslapd-return-default-opattr: supportedcontrol nsslapd-return-default-opattr: ref nsslapd-return-default-opattr: vendorname nsslapd-return-default-opattr: vendorVersion nsslapd-return-default-opattr: supportedextension nsslapd-return-default-opattr: namingcontexts
- Start the Directory Server instance.
| Parameter | Description |
|---|---|
| Entry DN | Root DSE |
| Valid Values | supportedsaslmechanisms | nsBackendSuffix | subschemasubentry | supportedldapversion | supportedcontrol | ref | vendorname | vendorVersion |
| Default Value | |
| Syntax | DirectoryString |
| Example | nsslapd-return-default-opattr: supportedsaslmechanisms |
3.2. Configuration Object Classes
Many configuration entries simply use the extensibleObject object class, but some require other object classes. These configuration object classes are listed here.
3.2.1. changeLogEntry (Object Class)
This object class is used for entries which store changes made to the Directory Server entries.
To configure Directory Server to maintain a changelog that is compatible with the changelog implemented in Directory Server 4.1x, enable the Retro Changelog Plug-in. Each entry in the changelog has the changeLogEntry object class.
This object class is defined in Changelog Internet Draft.
Superior Class
top
OID
2.16.840.1.113730.3.2.1
| objectClass | Defines the object classes for the entry. |
| Contains a number assigned arbitrarily to the changelog. | |
| The time at which a change took place. | |
| The type of change performed on an entry. | |
| The distinguished name of an entry added, modified or deleted on a supplier server. |
| Changes made to the Directory Server. | |
| A flag that defines whether the old Relative Distinguished Name (RDN) of the entry should be kept as a distinguished attribute of the entry or should be deleted. | |
| New RDN of an entry that is the target of a modRDN or modDN operation. | |
| Name of the entry that becomes the immediate superior of the existing entry when processing a modDN operation. |
3.2.2. directoryServerFeature (Object Class)
This object class is used specifically for entries which identify a feature of the directory service. This object class is defined by Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.40
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| cn | Specifies the common name of the entry. |
| multiLineDescription | Gives a text description of the entry. |
| oid | Specifies the OID of the feature. |
3.2.3. nsBackendInstance (Object Class)
This object class is used for the Directory Server back end, or database, instance entry. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.109
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn | Gives the common name of the entry. |
3.2.4. nsChangelog4Config (Object Class)
In order for Directory Server 11.3 to replicate between Directory Server 4.x servers, the Directory Server 11.3 instance must have a special changelog configured. This object class defines the configuration for the retro changelog.
This object class is defined for the Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.82
| Attribute | Definition |
|---|---|
| cn (common Name) | Gives the common name of the entry. |
3.2.5. nsDS5Replica (Object Class)
This object class is for entries which define a replica in database replication. Many of these attributes are set within the back end and cannot be modified.
Information on the attributes for this object class are listed with the core configuration attributes in chapter 2 of the Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.108
| objectClass | Defines the object classes for the entry. |
| nsDS5ReplicaId | Specifies the unique ID for suppliers in a replication environment. |
| nsDS5ReplicaRoot | Specifies the suffix DN at the root of a replicated area. |
| cn | Gives the name for the replica. |
| nsDS5Flags | Specifies information that has been previously set in flags. |
| nsDS5ReplicaAutoReferral | Sets whether the server will follow configured referrals for the Directory Server database. |
| nsDS5ReplicaBindDN | Specifies the DN to use when a supplier server binds to a consumer. |
| nsDS5ReplicaChangeCount | Gives the total number of entries in the changelog and whether they have been replicated. |
| nsDS5ReplicaLegacyConsumer | Specifies whether the replica is a legacy consumer. |
| nsDS5ReplicaName | Specifies the unique ID for the replica for internal operations. |
| nsDS5ReplicaPurgeDelay | Specifies the time in seconds before the changelog is purged. |
| nsDS5ReplicaReferral | Specifies the URLs for user-defined referrals. |
| nsDS5ReplicaReleaseTimeout | Specifies a timeout after which a supplier will release a replica, whether or not it has finished sending its updates. |
| nsDS5ReplicaTombstonePurgeInterval | Specifies the time interval in seconds between purge operation cycles. |
| nsDS5ReplicaType | Defines the type of replica, such as a read-only consumer. |
| nsDS5Task | Launches a replication task, such as dumping the database contents to LDIF; this is used internally by the Directory Server supplier. |
| nsState | Stores information on the clock so that proper change sequence numbers are generated. |
3.2.6. nsDS5ReplicationAgreement (Object Class)
Entries with the nsDS5ReplicationAgreement object class store the information set in a replication agreement. Information on the attributes for this object class are in chapter 2 of the Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.103
| objectClass | Defines the object classes for the entry. |
| cn | Used for naming the replication agreement. |
| description | Contains a free text description of the replication agreement. |
| nsDS5BeginReplicaRefresh | Initializes a replica manually. |
| nsds5debugreplicatimeout | Gives an alternate timeout period to use when the replication is run with debug logging. |
| nsDS5ReplicaBindDN | Specifies the DN to use when a supplier server binds to a consumer. |
| nsDS5ReplicaBindMethod | Specifies the method (SSL or simple authentication) to use for binding. |
| nsDS5ReplicaBusyWaitTime | Specifies the amount of time in seconds a supplier should wait after a consumer sends back a busy response before making another attempt to acquire access. |
| nsDS5ReplicaChangesSentSinceStartup | The number of changes sent to this replica since the server started. |
| nsDS5ReplicaCredentials | Specifies the password for the bind DN. |
| nsDS5ReplicaHost | Specifies the host name for the consumer replica. |
| nsDS5ReplicaLastInitEnd | States when the initialization of the consumer replica ended. |
| nsDS5ReplicaLastInitStart | States when the initialization of the consumer replica started. |
| nsDS5ReplicaLastInitStatus | The status for the initialization of the consumer. |
| nsDS5ReplicaLastUpdateEnd | States when the most recent replication schedule update ended. |
| nsDS5ReplicaLastUpdateStart | States when the most recent replication schedule update started. |
| nsDS5ReplicaLastUpdateStatus | Provides the status for the most recent replication schedule updates. |
| nsDS5ReplicaPort | Specifies the port number for the remote replica. |
| nsDS5ReplicaRoot | Specifies the suffix DN at the root of a replicated area. |
| nsDS5ReplicaSessionPauseTime | Specifies the amount of time in seconds a supplier should wait between update sessions. |
| nsDS5ReplicatedAttributeList | Specifies any attributes that will not be replicated to a consumer server. |
| nsDS5ReplicaTimeout | Specifies the number of seconds outbound LDAP operations will wait for a response from the remote replica before timing out and failing. |
| nsDS5ReplicaTransportInfo | Specifies the type of transport used for transporting data to and from the replica. |
| nsDS5ReplicaUpdateInProgress | States whether a replication schedule update is in progress. |
| nsDS5ReplicaUpdateSchedule | Specifies the replication schedule. |
| nsDS50ruv | Manages the internal state of the replica using the replication update vector. |
| nsruvReplicaLastModified | Contains the most recent time that an entry in the replica was modified and the changelog was updated. |
| nsds5ReplicaStripAttrs |
With fractional replication, an update to an excluded attribute still triggers a replication event, but that event is empty. This attribute sets attributes to strip from the replication update. This prevents changes to attributes like |
3.2.7. nsDSWindowsReplicationAgreement (Object Class)
Stores the synchronization attributes that concern the synchronization agreement. Information on the attributes for this object class are in chapter 2 of the Red Hat Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.503
| objectClass | Defines the object classes for the entry. |
| cn | Gives the name of the synchronization agreement. |
| description | Contains a text description of the synchronization agreement. |
| nsDS5BeginReplicaRefresh | Initiates a manual synchronization. |
| nsds5debugreplicatimeout | Gives an alternate timeout period to use when the synchronization is run with debug logging. |
| nsDS5ReplicaBindDN | Specifies the DN to use when the Directory Server binds to the Windows server. |
| nsDS5ReplicaBindMethod | Specifies the method (SSL or simple authentication) to use for binding. |
| nsDS5ReplicaBusyWaitTime | Specifies the amount of time in seconds the Directory Server should wait after the Windows server sends back a busy response before making another attempt to acquire access. |
| nsDS5ReplicaChangesSentSinceStartup | Shows the number of changes sent since the Directory Server started. |
| nsDS5ReplicaCredentials | Specifies the credentials for the bind DN. |
| nsDS5ReplicaHost | Specifies the host name for the Windows domain controller of the Windows server being synchronized. |
| nsDS5ReplicaLastInitEnd | States when the last total update (resynchronization) of the Windows server ended. |
| nsDS5ReplicaLastInitStart | States when the last total update (resynchronization) of the Windows server started. |
| nsDS5ReplicaLastInitStatus | The status for the total update (resynchronization) of the Windows server. |
| nsDS5ReplicaLastUpdateEnd | States when the most recent update ended. |
| nsDS5ReplicaLastUpdateStart | States when the most recent update started. |
| nsDS5ReplicaLastUpdateStatus | Provides the status for the most recent updates. |
| nsDS5ReplicaPort | Specifies the port number for the Windows server. |
| nsDS5ReplicaRoot | Specifies the root suffix DN of the Directory Server. |
| nsDS5ReplicaSessionPauseTime | Specifies the amount of time in seconds the Directory Server should wait between update sessions. |
| nsDS5ReplicaTimeout | Specifies the number of seconds outbound LDAP operations will wait for a response from the Windows server before timing out and failing. |
| nsDS5ReplicaTransportInfo | Specifies the type of transport used for transporting data to and from the Windows server. |
| nsDS5ReplicaUpdateInProgress | States whether an update is in progress. |
| nsDS5ReplicaUpdateSchedule | Specifies the synchronization schedule. |
| nsDS50ruv | Manages the internal state of the Directory Server sync peer using the replication update vector (RUV). |
| nsds7DirectoryReplicaSubtree | Specifies the Directory Server suffix (root or sub) that is synced. |
| nsds7DirsyncCookie | Contains a cookie set by the sync service that functions as an RUV. |
| nsds7NewWinGroupSyncEnabled | Specifies whether new Windows group accounts are automatically created on the Directory Server. |
| nsds7NewWinUserSyncEnabled | Specifies whether new Windows user accounts are automatically created on the Directory Server. |
| nsds7WindowsDomain |
Identifies the Windows domain being synchronized; analogous to |
| nsds7WindowsReplicaSubtree | Specifies the Windows server suffix (root or sub) that is synced. |
| nsruvReplicaLastModified | Contains the most recent time that an entry in the Directory Server sync peer was modified and the changelog was updated. |
| winSyncInterval |
Sets how frequently, in seconds, the Directory Server polls the Windows server for updates to write over. If this is not set, the default is |
| winSyncMoveAction | Sets how the sync plug-in handles corresponding entries that are discovered in Active Directory outside of the synced subtree. The sync process can ignore these entries (none, the default) or it can assume that the entries were moved intentionally to remove them from synchronization, and it can then either delete the corresponding Directory Server entry (delete) or remove the synchronization attributes and no longer sync the entry (unsync). |
3.2.8. nsEncryptionConfig
The nsEncryptionConfig object class stores the configuration information for allowed encryption options, such as protocols and cipher suites. This is defined in the Administrative Services.
Superior Class
top
OID
nsEncryptionConfig-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn (commonName) | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| nsSSL3SessionTimeout | Sets the timeout period for an SSLv3 cipher session. |
| nsSSLClientAuth | Sets how the server handles client authentication. There are three possible values: allow, disallow, or require. |
| nsSSLSessionTimeout | Sets the timeout period for a cipher session. |
| nsSSLSupportedCiphers | Contains a list of all ciphers available to be used with secure connections to the server. |
| nsTLS1 | Sets whether TLS version 1 is enabled for the server. |
3.2.9. nsEncryptionModule
The nsEncryptionModule object class stores the encryption module information. This is defined in the Administrative Services.
Superior Class
top
OID
nsEncryptionModule-oid
| Attribute | Definition |
|---|---|
| objectClass | Defines the object classes for the entry. |
| cn (commonName) | Gives the common name of the device. |
| Attribute | Definition |
|---|---|
| nsSSLActivation | Sets whether to enable a cipher family. |
| nsSSLPersonalitySSL | Contains the name of the certificate used by the server for SSL. |
| nsSSLToken | Identifies the security token used by the server. |
3.2.10. nsMappingTree (Object Class)
A mapping tree maps a suffix to the back end. Each mapping tree entry uses the nsMappingTree object class. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.110
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cn | Gives the common name of the entry. |
3.2.11. nsSaslMapping (Object Class)
This object class is used for entries which contain an identity mapping configuration for mapping SASL attributes to the Directory Server attributes.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.317
| objectClass | Defines the object classes for the entry. |
| cn | Gives the name of the SASL mapping entry. |
| Contains the search base DN template. | |
| Contains the search filter template. | |
| Contains a regular expression to match SASL identity strings. |
3.2.12. nsslapdConfig (Object Class)
The nsslapdConfig object class defines the configuration object, cn=config, for the Directory Server instance.
This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.39
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| cn | Gives the common name of the entry. |
3.2.13. passwordPolicy (Object Class)
Both local and global password policies take the passwordPolicy object class. This object class is defined in Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.13
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| Attribute | Definition |
|---|---|
| Sets the number of seconds after which user passwords expire. | |
|
Identifies whether the user’s password expires after an interval given by the | |
| Section 3.1.1.204, “passwordMinLength (Password Minimum Length)” | Sets the minimum number of characters that must be used in passwords. |
| Section 3.1.1.187, “passwordInHistory (Number of Passwords to Remember)” | Sets the number of passwords the directory stores in the history. |
| Identifies whether or not users is allowed to change their own password. | |
| Sets the number of seconds before a warning message is sent to users whose password is about to expire. | |
| Identifies whether or not users are locked out of the directory after a given number of failed bind attempts. | |
| Section 3.1.1.195, “passwordMaxFailure (Maximum Password Failures)” | Sets the number of failed bind attempts after which a user will be locked out of the directory. |
| Identifies whether a user is locked out until the password is reset by an administrator or whether the user can log in again after a given lockout duration. The default is to allow a user to log back in after the lockout period. | |
| Section 3.1.1.191, “passwordLockoutDuration (Lockout Duration)” | Sets the time, in seconds, that users will be locked out of the directory. |
| Section 3.1.1.180, “passwordCheckSyntax (Check Password Syntax)” | Identifies whether the password syntax is checked by the server before the password is saved. |
| Section 3.1.1.209, “passwordMustChange (Password Must Change)” | Identifies whether or not to change their passwords when they first login to the directory or after the password is reset by the Directory Manager. |
| Section 3.1.1.214, “passwordStorageScheme (Password Storage Scheme)” | Sets the type of encryption used to store Directory Server passwords. |
| Sets the number of seconds that must pass before a user can change their password. | |
| Section 3.1.1.211, “passwordResetFailureCount (Reset Password Failure Count After)” | Sets the time, in seconds, after which the password failure counter will be reset. Each time an invalid password is sent from the user’s account, the password failure counter is incremented. |
| Section 3.1.1.185, “passwordGraceLimit (Password Expiration)” | Sets the number of grace logins permitted when a user’s password is expired. |
| Sets the minimum number of numeric characters (0 through 9) which must be used in the password. | |
| Sets the minimum number of alphabetic chracters that must be used in the password. | |
| Sets the minimum number of upper case alphabetic characters, A to Z, which must be used in the password. | |
| Sets the minimum number of lower case alphabetic characters, a to z, which must be used in the password. | |
|
Sets the minimum number of special ASCII characters, such as | |
| Sets the minimum number of 8-bit chracters used in the password. | |
| Sets the maximum number of times that the same character can be used in row. | |
| Section 3.1.1.202, “passwordMinCategories (Password Syntax)” | Sets the minimum number of categories which must be used in the password. |
| Section 3.1.1.207, “PasswordMinTokenLength (Password Syntax)” | Sets the length to check for trivial words. |
| Sets a delay when temporary passwords become valid. | |
| Sets the number of seconds a temporary password is valid. | |
| Section 3.1.1.217, “passwordTPRMaxUse”Sets the maximum number off attempts a temporary password can be used |
3.3. Root DSE Attributes
The attributes in this section are used to define the root directory server entry (DSE) for the server instance. The information defined in the DSE relates to the actual configuration of the server instance, such as the controls, mechanisms, or features supported in that version of the server software. It also contains information specific to the instance, like its build number and installation date.
The DSE is a special entry, outside the normal DIT, and can be returned by searching with a null search base. For example:
# ldapsearch -D "cn=Directory Manager" -W -p 389 -h server.example.com -x -s base -b "" "objectclass=*"
3.3.1. dataversion
This attribute contains a timestamp which shows the most recent edit time for any data in the directory.
dataversion: 020090923175302020090923175302
| OID | |
| Syntax | GeneralizedTime |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
3.3.2. defaultNamingContext
Corresponds to the naming context, out of all configured naming contexts, which clients should use by default.
| OID | |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
3.3.3. lastusn
The USN Plug-in assigns a sequence number to every entry whenever a write operation — add, modify, delete, and modrdn — is performed for that entry. The USN is assigned in the entryUSN operational attribute for the entry.
The USN Plug-in has two modes: local and global.
In local mode, each database maintained for a server instance has its own instance of the USN Plug-in with a separate USN counter per back end database. The most recent USN assigned for any entry in the database is displayed in the lastusn attribute. When the USN Plug-in is set to local mode, the lastUSN attribute shows both the database which assigned the USN and the USN:
lastusn;database_name:USN
For example:
lastusn;example1: 213 lastusn;example2: 207
In global mode, when the database uses a shared USN counter, the lastUSN value shows the latest USN assigned by any database:
lastusn: 420
This attribute does not count internal server operations. Only normal write operations in the back end database — add, modify, delete, and modrdn — increment the USN count.
| Syntax | Integer |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.3.4. namingContexts
Corresponds to a naming context the server is controlling or shadowing. When the Directory Server does not control any information (such as when it is an LDAP gateway to a public X.500 directory), this attribute is absent. When the Directory Server believes it contains the entire directory, the attribute has a single value, and that value is the empty string (indicating the null DN of the root).This attribute permits a client contacting a server to choose suitable base objects for searching.
| OID | 1.3.6.1.4.1.1466.101.120.5 |
| Syntax | DN |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
3.3.5. netscapemdsuffix
This attribute contains the DN for the top suffix of the directory tree for machine data maintained in the server. The DN itself points to an LDAP URL. For example:
cn=ldap://dc=server_name,dc=example,dc=com:389| OID | 2.16.840.1.113730.3.1.212 |
| Syntax | DN |
| Multi- or Single-Valued | Single-valued |
| Defined in | Directory Server |
3.3.6. supportedControl
The values of this attribute are the object identifiers (OIDs) that identify the controls supported by the server. When the server does not support controls, this attribute is absent.
| OID | 1.3.6.1.4.1.1466.101.120.13 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
3.3.7. supportedExtension
The values of this attribute are the object identifiers (OIDs) that identify the extended operations supported by the server. When the server does not support extended operations, this attribute is absent.
| OID | 1.3.6.1.4.1.1466.101.120.7 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
3.3.8. supportedFeatures
This attribute contains features supported by the current version of Red Hat Directory Server.
| OID | 1.3.6.1.4.1.4203.1.3.5 |
| Syntax | OID |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
3.3.9. supportedLDAPVersion
This attribute identifies the versions of the LDAP protocol implemented by the server.
| OID | 1.3.6.1.4.1.1466.101.120.15 |
| Syntax | Integer |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
3.3.10. supportedSASLMechanisms
This attribute identifies the names of the SASL mechanisms supported by the server. When the server does not support SASL attributes, this attribute is absent.
| OID | 1.3.6.1.4.1.1466.101.120.14 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in |
3.3.11. vendorName
This attribute contains the name of the server vendor.
| OID | 1.3.6.1.1.4 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
3.3.12. vendorVersion
This attribute shows the vendor’s version number for the server.
| OID | 1.3.6.1.1.5 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Single-valued |
| Defined in |
3.4. Legacy Attributes
The attributes were standard with Directory Server 4.x and older. This are still included with the schema for compatibility, but are not for current versions of the Directory Server.
3.4.1. Legacy Server Attributes
These attributes were originally used to configure the server instance entries for Directory Server 4.x and older servers.
3.4.1.1. LDAPServer (Object Class)
This object class identifies the LDAP server information. It is defined by Directory Server.
Superior Class
top
OID
2.16.840.1.113730.3.2.35
| Attribute | Definition |
|---|---|
| objectClass | Gives the object classes assigned to the entry. |
| cn | Specifies the common name of the entry. |
| Attribute | Definition |
|---|---|
| description | Gives a text description of the entry. |
| l (localityName) | Gives the city or geographical location of the entry. |
| ou (organizationalUnitName) | Gives the organizational unit or division to which the account belongs. |
| seeAlso | Contains a URL to another entry or site with related information. |
| generation | Store the server generation string. |
| changeLogMaximumAge | Specifies changelog maximum age. |
| changeLogMaximumSize | Specifies maximum changelog size. |
3.4.1.2. changeLogMaximumAge
This sets the maximum age for the changelog maintained by the server.
| OID | 2.16.840.1.113730.3.1.200 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.4.1.3. changeLogMaximumConcurrentWrites
This attribute sets the maximum number of concurrent writes that can be written to the changelog.
| OID | 2.16.840.1.113730.3.1.205 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.4.1.4. changeLogMaximumSize
This attribute sets the maximum size for the changelog.
| OID | 2.16.840.1.113730.3.1.201 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.4.1.5. generation
This attribute contains a byte vector that uniquely identifies that specific server and version. This number distinguishes between servers during replication.
| OID | 2.16.840.1.113730.3.1.612 |
| Syntax | IA5String |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.4.1.6. nsSynchUniqueAttribute
This attribute is used for Windows synchonization.
| OID | 2.16.840.1.113730.3.1.407 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |
3.4.1.7. nsSynchUserIDFormat
This attribute is used for Windows synchonization.
| OID | 2.16.840.1.113730.3.1.406 |
| Syntax | DirectoryString |
| Multi- or Single-Valued | Multi-valued |
| Defined in | Directory Server |