8.3.4. Customizing Security Profiles
After selecting the security profile that suits your security policy, you can further adjust it by clicking the button. This will open the new Customization window that allows you to modify the currently selected XCCDF profile without actually changing the respective XCCDF file.
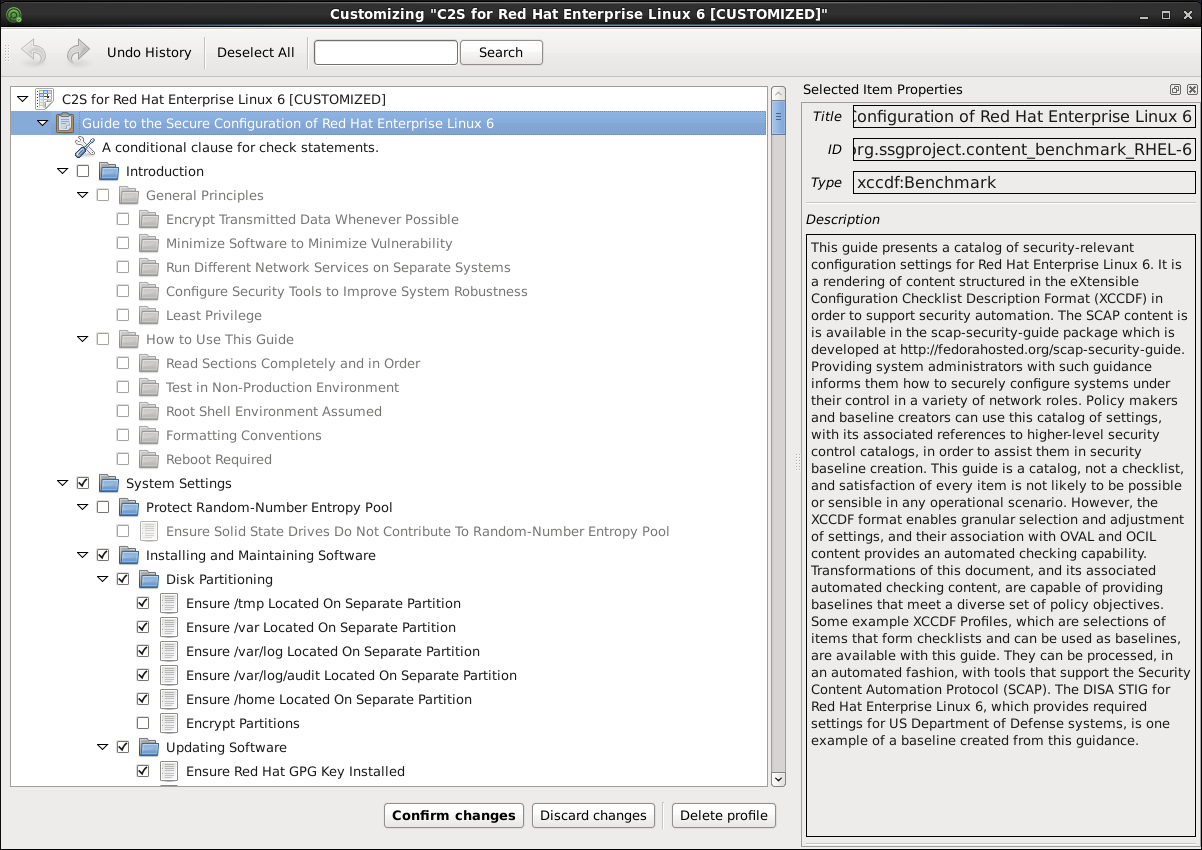
Figure 8.4. Customizing the Selected Security Profile
The Customization window contains a complete set of XCCDF elements relevant to the selected security profile with detailed information about each element and its functionality. You can enable or disable these elements by selecting or de-selecting the respective check boxes in the main field of this window. The Customization window also supports undo and redo functionality; you can undo or redo your selections by clicking the respective arrow icon in the top left corner of the window.
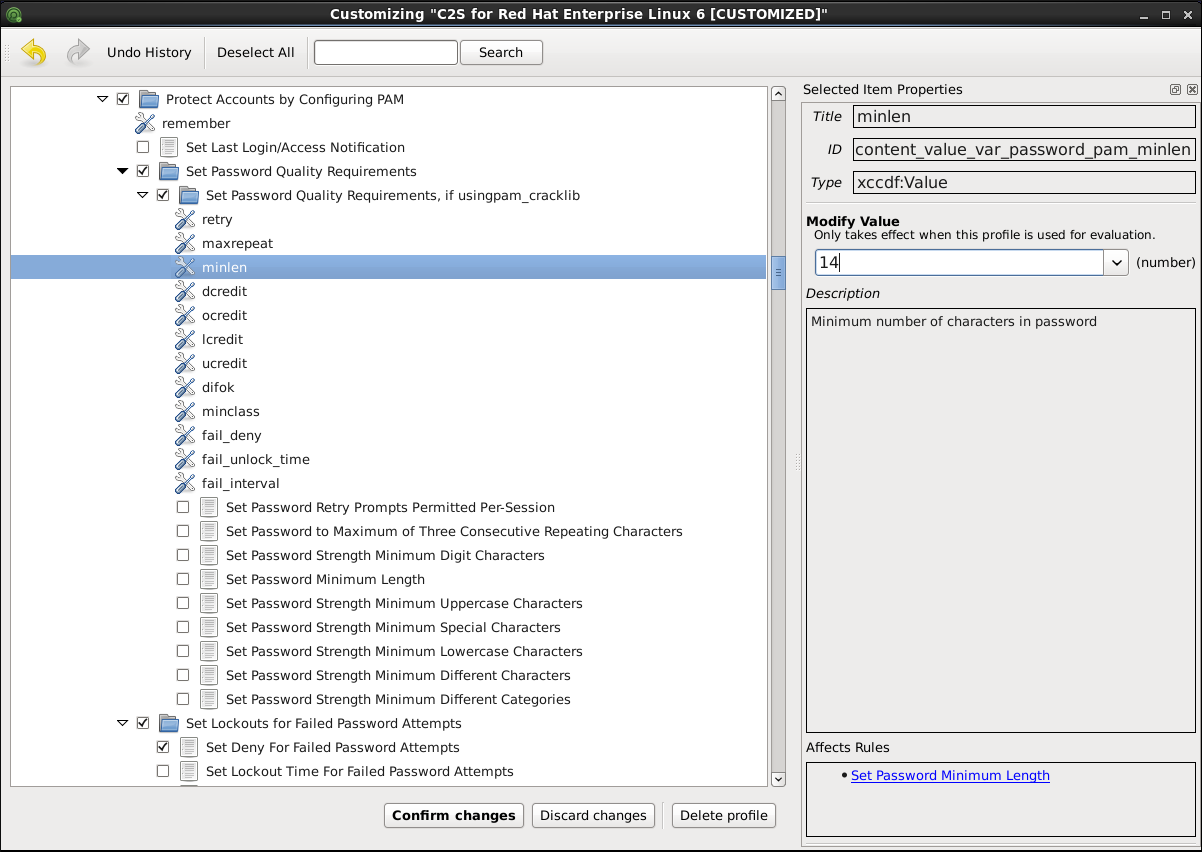
You can also change variables that will later be used for evaluation. Find the desired item in the Customization window, navigate to the right part and use the
Modify value field.
Figure 8.5. Setting a value for the selected item in the Customization window
After you have finished your profile customizations, confirm the changes by clicking the button. Your changes are now in the memory and do not persist if SCAP Workbench is closed or certain changes, such as selecting a new SCAP content or choosing another customization option, are made. To store your changes, click the button in the SCAP Workbench window. This action allows you to save your changes to the security profile as an XCCDF customization file in the chosen directory. Note that this customization file can be further selected with other profiles.