Chapter 6. Ports required for communication between IdM and AD
To enable communication between your Active Directory (AD) and Identity Management (IdM) environments, open the following ports on the firewalls of your AD Domain Controllers and IdM servers.
| Service | Port | Protocol |
|---|---|---|
| Endpoint resolution portmapper | 135 | TCP |
| NetBIOS-DGM | 138 | TCP and UDP |
| NetBIOS-SSN | 139 | TCP and UDP |
| Microsoft-DS | 445 | TCP and UDP |
| Dynamic RPC | 49152-65535 | TCP |
| AD Global Catalog | 3268 | TCP |
| LDAP | 389 | TCP and UDP |
The TCP port 389 is not required to be open on IdM servers for trust, but it is necessary for clients communicating with the IdM server.
The TCP port 135 is required for the DCE RPC end-point mapper to work and is used during the IdM-AD trust creation.
To open ports, you can use the following methods:
firewalldservice — you can enable the particular ports or enable the following services which includes the ports:- FreeIPA trust setup
- FreeIPA with LDAP
- Kerberos
- DNS
For details, see the
firewall-cmdman page.
If you are using RHEL 8.2 and earlier, the freeipa-trust firewalld service includes an RPC port range of 1024-1300, which is incorrect. On RHEL 8.2 and earlier, you must manually open the TCP port range 49152-65535 in addition to enabling the freeipa-trust firewalld service.
This issue has been fixed for RHEL 8.3 and later in Bug 1850418 - update freeipa-trust.xml definition to include correct dynamic RPC range.
The RHEL web console, which is a UI with firewall settings based on the
firewalldservice.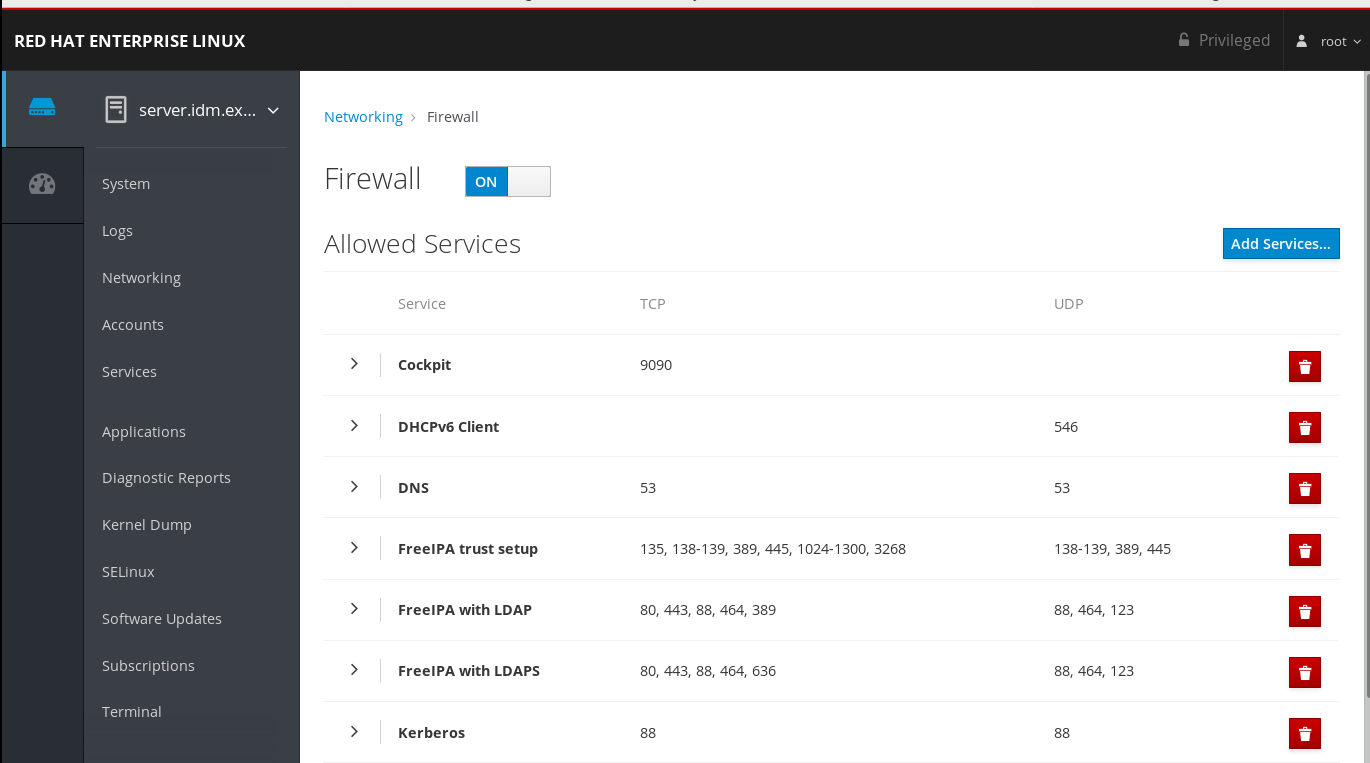
For details about firewall configuration through the web console, see Enabling services on the firewall using the web console
NoteIf you are using RHEL 8.2 and earlier, the
FreeIPA Trust Setupservice includes an RPC port range of1024-1300, which is incorrect. On RHEL 8.2 and earlier, you must manually open the TCP port range49152-65535in addition to enabling theFreeIPA Trust Setupservice in the RHEL web console.This issue has been fixed for RHEL 8.3 and later in Bug 1850418 - update freeipa-trust.xml definition to include correct dynamic RPC range.
| Service | Port | Protocol |
|---|---|---|
| Kerberos | 88, 464 | TCP and UDP |
| LDAP | 389 | TCP |
| DNS | 53 | TCP and UDP |
| Service | Port | Protocol |
|---|---|---|
| Kerberos | 88 | UDP and TCP |
The libkrb5 library uses UDP and falls back to the TCP protocol if the data sent from the Key Distribution Center (KDC) is too large. Active Directory attaches a Privilege Attribute Certificate (PAC) to the Kerberos ticket, which increases the size and requires to use the TCP protocol. To avoid the fall-back and resending the request, by default, SSSD in Red Hat Enterprise Linux 7.4 and later uses TCP for user authentication. If you want to configure the size before libkrb5 uses TCP, set the udp_preference_limit in the /etc/krb5.conf file. For details, see the krb5.conf(5) man page.
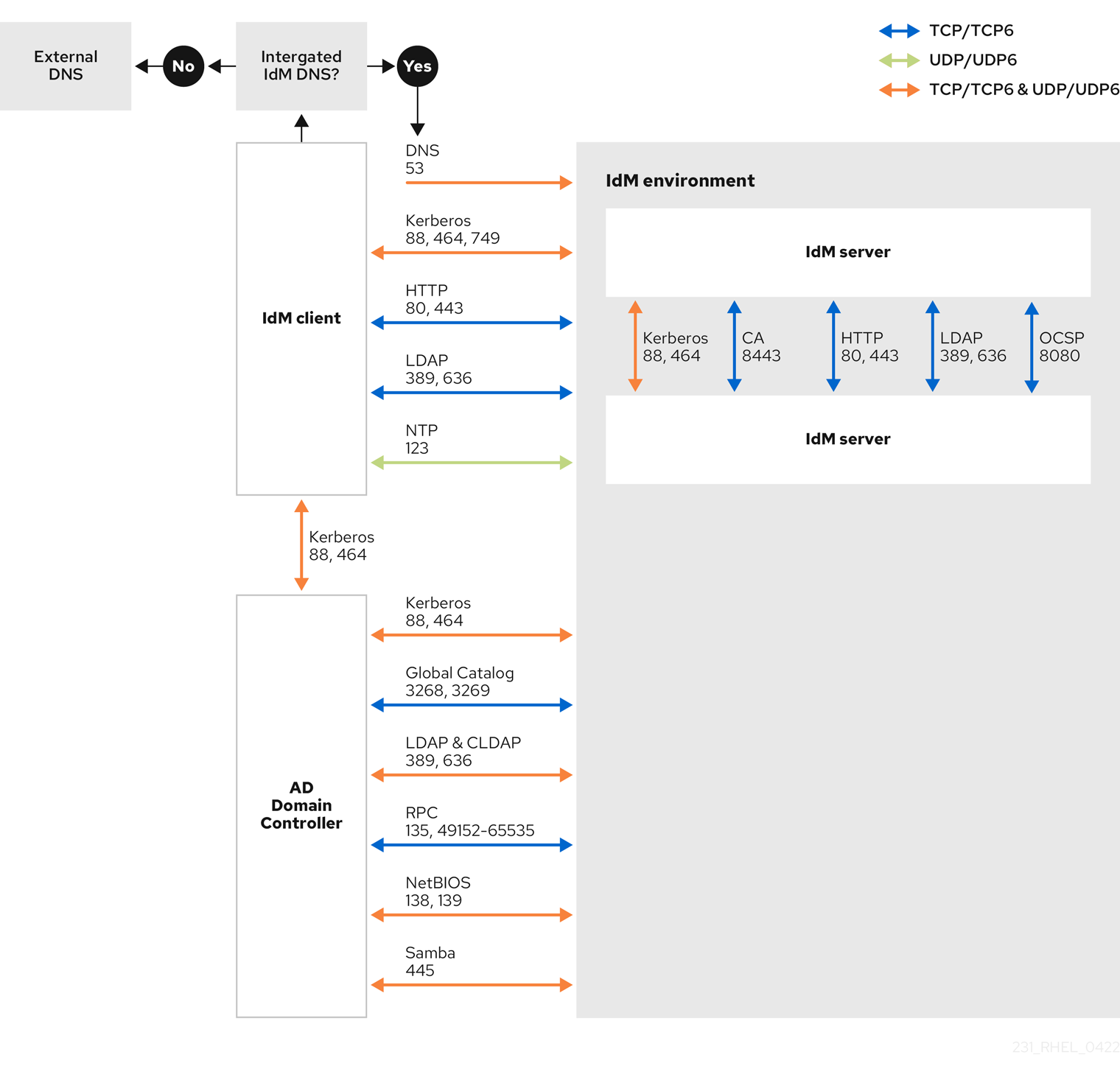
The following diagram shows communication sent by IdM clients, and received and responded to by IdM servers and AD Domain Controllers. To set the incoming and outgoing ports and protocols on your firewall, Red Hat recommends using the firewalld service, which already has definitions for FreeIPA services.
Additional resources
- For more information about the Dynamic RPC port range in Windows Server 2008 and later, see The default dynamic port range for TCP/IP has changed since Windows Vista and in Windows Server 2008.