Chapter 18. Configuring Firewall-as-a-Service (FWaaS)
18.1. Overview of firewall-as-a-service (FWaaS)
The Firewall-as-a-Service (FWaaS) plug-in adds perimeter firewall management to OpenStack Networking (neutron). FWaaS uses iptables to apply firewall policy to all virtual routers within a project, and supports one firewall policy and logical firewall instance for each project.
FWaaS operates at the perimeter by filtering traffic at the OpenStack Networking (neutron) router. This distinguishes FWaaS from security groups, which operate at the instance level.
FWaaS is currently in Technology Preview; untested operation is not recommended. FWaaS is not available in future releases.
The following example diagram illustrates the flow of ingress and egress traffic for the VM2 instance:
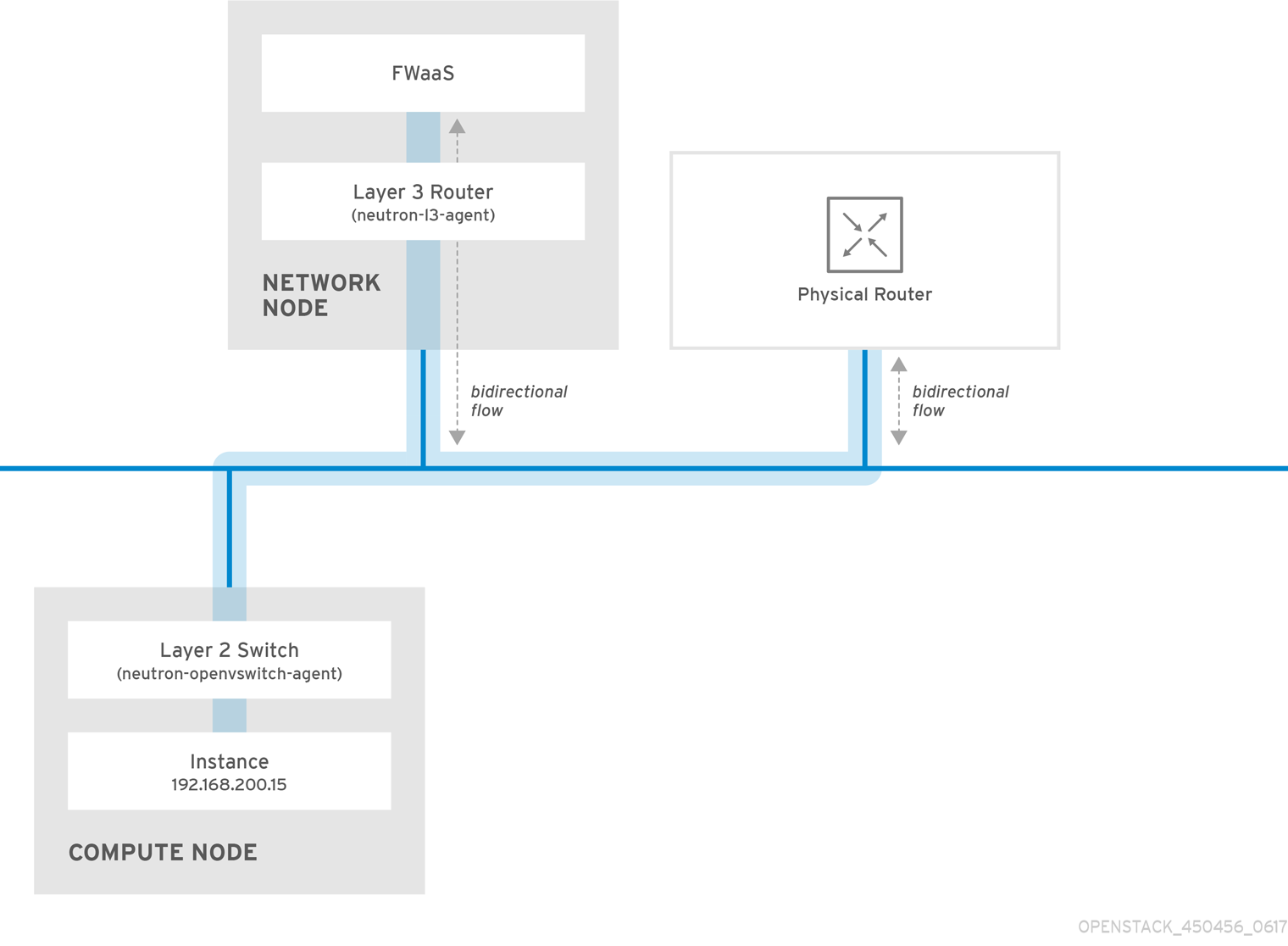
Figure 1. FWaaS architecture
18.2. Enabling firewall-as-a-service (FWaaS)
Install the FWaaS packages:
dnf install openstack-neutron-fwaas python-neutron-fwaas
# dnf install openstack-neutron-fwaas python-neutron-fwaasCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the FWaaS plugin in the
/var/lib/config-data/neutron/etc/neutron/neutron.conffile:service_plugins = neutron.services.firewall.fwaas_plugin.FirewallPlugin
service_plugins = neutron.services.firewall.fwaas_plugin.FirewallPluginCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure FWaaS in the
fwaas_driver.inifile:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the FWaaS dashboard management option in the local_settings.py file, usually located on the Controller node:
/usr/share/openstack-dashboard/openstack_dashboard/local/local_settings.py 'enable_firewall' = True
/usr/share/openstack-dashboard/openstack_dashboard/local/local_settings.py 'enable_firewall' = TrueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart
neutron-serverto apply the changes.systemctl restart neutron-server
# systemctl restart neutron-serverCopy to Clipboard Copied! Toggle word wrap Toggle overflow
18.3. Configuring firewall-as-a-service (FWaaS)
First, create the firewall rules and create a policy to contain them, then create a firewall and apply the policy:
Create a firewall rule:
neutron firewall-rule-create --protocol <tcp|udp|icmp|any> --destination-port <port-range> --action <allow|deny>
$ neutron firewall-rule-create --protocol <tcp|udp|icmp|any> --destination-port <port-range> --action <allow|deny>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI requires a protocol value. If the rule is protocol agnostic, you can use the value
any.Create a firewall policy:
neutron firewall-policy-create --firewall-rules "<firewall-rule IDs or names separated by space>" myfirewallpolicy
$ neutron firewall-policy-create --firewall-rules "<firewall-rule IDs or names separated by space>" myfirewallpolicyCopy to Clipboard Copied! Toggle word wrap Toggle overflow The order of the rules that you specify in the
neutron firewall-policy-createcommand is important. You can create an empty firewall policy and add rules later, either with the update operation (when adding multiple rules) or with the insert-rule operations (when adding a single rule).
FWaaS always adds a default deny all rule at the lowest precedence of each policy. Consequently, a firewall policy with no rules blocks all traffic by default.
18.4. Creating firewalls
Use the
openstack security group createcommand, to create a firewall:openstack security group create <firewall-policy-uuid>
$ openstack security group create <firewall-policy-uuid>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The firewall remains in PENDING_CREATE state until you create an OpenStack Networking router and attach an interface.