Chapter 6. Red Hat Quay Robot Account overview
Robot Accounts are used to set up automated access to the repositories in your Red Hat Quay registry. They are similar to OpenShift Container Platform service accounts.
Setting up a Robot Account results in the following:
- Credentials are generated that are associated with the Robot Account.
- Repositories and images that the Robot Account can push and pull images from are identified.
- Generated credentials can be copied and pasted to use with different container clients, such as Docker, Podman, Kubernetes, Mesos, and so on, to access each defined repository.
Each Robot Account is limited to a single user namespace or Organization. For example, the Robot Account could provide access to all repositories for the user quayadmin. However, it cannot provide access to repositories that are not in the user’s list of repositories.
Robot Accounts can be created using the Red Hat Quay UI, or through the CLI using the Red Hat Quay API. After creation, Red Hat Quay administrators can leverage more advanced features with Robot Accounts, such as keyless authentication.
6.1. Creating a robot account by using the UI
Use the following procedure to create a robot account using the v2 UI.
Procedure
- On the v2 UI, click Organizations.
-
Click the name of the organization that you will create the robot account for, for example,
test-org. -
Click the Robot accounts tab
Create robot account. -
In the Provide a name for your robot account box, enter a name, for example,
robot1. The name of your Robot Account becomes a combination of your username plus the name of the robot, for example,quayadmin+robot1 Optional. The following options are available if desired:
- Add the robot account to a team.
- Add the robot account to a repository.
- Adjust the robot account’s permissions.
On the Review and finish page, review the information you have provided, then click Review and finish. The following alert appears: Successfully created robot account with robot name: <organization_name> + <robot_name>.
Alternatively, if you tried to create a robot account with the same name as another robot account, you might receive the following error message: Error creating robot account.
- Optional. You can click Expand or Collapse to reveal descriptive information about the robot account.
-
Optional. You can change permissions of the robot account by clicking the kebab menu
Set repository permissions. The following message appears: Successfully updated repository permission. Optional. You can click the name of your robot account to obtain the following information:
- Robot Account: Select this obtain the robot account token. You can regenerate the token by clicking Regenerate token now.
- Kubernetes Secret: Select this to download credentials in the form of a Kubernetes pull secret YAML file.
-
Podman: Select this to copy a full
podman logincommand line that includes the credentials. -
Docker Configuration: Select this to copy a full
docker logincommand line that includes the credentials.
6.2. Creating a robot account by using the Red Hat Quay API
Use the following procedure to create a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to create a new robot account for an organization using the
PUT /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to create a new robot account for the current user with the
PUT /api/v1/user/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3. Bulk managing robot account repository access
Use the following procedure to manage, in bulk, robot account repository access by using the Red Hat Quay v2 UI.
Prerequisites
- You have created a robot account.
- You have created multiple repositories under a single organization.
Procedure
- On the Red Hat Quay v2 UI landing page, click Organizations in the navigation pane.
- On the Organizations page, select the name of the organization that has multiple repositories. The number of repositories under a single organization can be found under the Repo Count column.
- On your organization’s page, click Robot accounts.
-
For the robot account that will be added to multiple repositories, click the kebab icon
Set repository permissions. On the Set repository permissions page, check the boxes of the repositories that the robot account will be added to. For example:
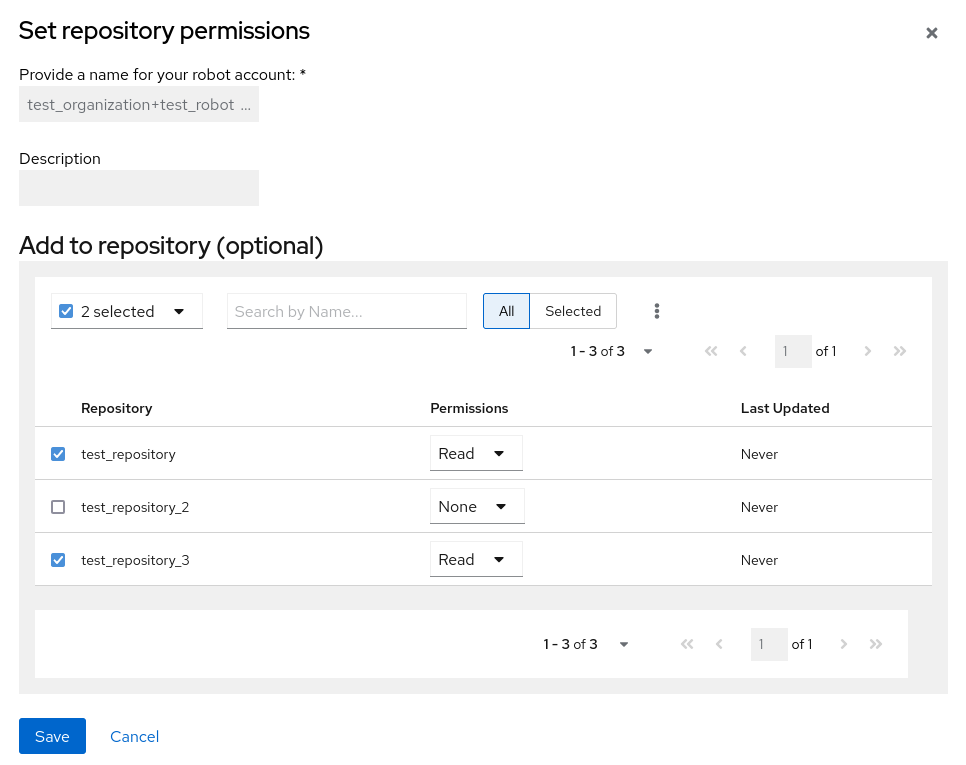
- Set the permissions for the robot account, for example, None, Read, Write, Admin.
- Click save. An alert that says Success alert: Successfully updated repository permission appears on the Set repository permissions page, confirming the changes.
-
Return to the Organizations
Robot accounts page. Now, the Repositories column of your robot account shows the number of repositories that the robot account has been added to.
6.4. Disabling robot accounts by using the UI
Red Hat Quay administrators can manage robot accounts by disallowing users to create new robot accounts.
Robot accounts are mandatory for repository mirroring. Setting the ROBOTS_DISALLOW configuration field to true breaks mirroring configurations. Users mirroring repositories should not set ROBOTS_DISALLOW to true in their config.yaml file. This is a known issue and will be fixed in a future release of Red Hat Quay.
Use the following procedure to disable robot account creation.
Prerequisites
- You have created multiple robot accounts.
Procedure
Update your
config.yamlfield to add theROBOTS_DISALLOWvariable, for example:ROBOTS_DISALLOW: true
ROBOTS_DISALLOW: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart your Red Hat Quay deployment.
Verification: Creating a new robot account
- Navigate to your Red Hat Quay repository.
- Click the name of a repository.
- In the navigation pane, click Robot Accounts.
- Click Create Robot Account.
-
Enter a name for the robot account, for example,
<organization-name/username>+<robot-name>. -
Click Create robot account to confirm creation. The following message appears:
Cannot create robot account. Robot accounts have been disabled. Please contact your administrator.
Verification: Logging into a robot account
On the command-line interface (CLI), attempt to log in as one of the robot accounts by entering the following command:
podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following error message is returned:
Error: logging into "<quay-server.example.com>": invalid username/password
Error: logging into "<quay-server.example.com>": invalid username/passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can pass in the
log-level=debugflag to confirm that robot accounts have been deactivated:podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.
... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5. Regenerating a robot account token by using the Red Hat Quay API
Use the following procedure to regenerate a robot account token using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to regenerate a robot account token for an organization using the
POST /api/v1/organization/{orgname}/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to regenerate a robot account token for the current user with the
POST /api/v1/user/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.6. Deleting a robot account by using the UI
Use the following procedure to delete a robot account using the Red Hat Quay UI.
Procedure
- Log into your Red Hat Quay registry:
- Click the name of the Organization that has the robot account.
- Click Robot accounts.
- Check the box of the robot account to be deleted.
- Click the kebab menu.
- Click Delete.
-
Type
confirminto the textbox, then click Delete.
6.7. Deleting a robot account by using the Red Hat Quay API
Use the following procedure to delete a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
-
You have set
BROWSER_API_CALLS_XHR_ONLY: falsein yourconfig.yamlfile.
Procedure
Enter the following command to delete a robot account for an organization using the
DELETE /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/organization/{orgname}/robotscommand to see if details are returned for the robot account:curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"robots": []}{"robots": []}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to delete a robot account for the current user with the
DELETE /api/v1/user/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account for the current user with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/user/robots/{robot_shortname}command to see if details are returned for the robot account:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"message":"Could not find robot with specified username"}{"message":"Could not find robot with specified username"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.8. Keyless authentication with robot accounts
In previous versions of Red Hat Quay, robot account tokens were valid for the lifetime of the token unless deleted or regenerated. Tokens that do not expire have security implications for users who do not want to store long-term passwords or manage the deletion, or regeneration, or new authentication tokens.
With Red Hat Quay 3.13, Red Hat Quay administrators are provided the ability to exchange external OIDC tokens for short-lived, or ephemeral robot account tokens with either Red Hat Single Sign-On (based on the Keycloak project) or Microsoft Entra ID. This allows robot accounts to leverage tokens that last one hour, which are are refreshed regularly and can be used to authenticate individual transactions.
This feature greatly enhances the security of your Red Hat Quay registry by mitigating the possibility of robot token exposure by removing the tokens after one hour.
Configuring keyless authentication with robot accounts is a multi-step procedure that requires setting a robot federation, generating an OAuth2 token from your OIDC provider, and exchanging the OAuth2 token for a robot account access token.
6.8.1. Generating an OAuth2 token with Red Hat Sign Sign-On
The following procedure shows you how to generate an OAuth2 token using Red Hat Single Sign-On. Depending on your OIDC provider, these steps will vary.
Procedure
On the Red Hat Single Sign-On UI:
- Click Clients and then the name of the application or service that can request authentication of a user.
On the Settings page of your client, ensure that the following options are set or enabled:
- Client ID
- Valid redirect URI
- Client authentication
- Authorization
- Standard flow
Direct access grants
NoteSettings can differ depending on your setup.
- On the Credentials page, store the Client Secret for future use.
-
On the Users page, click Add user and enter a username, for example,
service-account-quaydev. Then, click Create. - Click the name of of the user, for example service-account-quaydev on the Users page.
-
Click the Credentials tab
Set password and provide a password for the user. If warranted, you can make this password temporary by selecting the Temporary option. Click the Realm settings tab
OpenID Endpoint Configuration. Store the /protocol/openid-connect/tokenendpoint. For example:http://localhost:8080/realms/master/protocol/openid-connect/token
http://localhost:8080/realms/master/protocol/openid-connect/tokenCopy to Clipboard Copied! Toggle word wrap Toggle overflow
On a web browser, navigate to the following URL:
http://<keycloak_url>/realms/<realm_name>/protocol/openid-connect/auth?response_type=code&client_id=<client_id>
http://<keycloak_url>/realms/<realm_name>/protocol/openid-connect/auth?response_type=code&client_id=<client_id>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - When prompted, log in with the service-account-quaydev user and the temporary password you set. Complete the login by providing the required information and setting a permanent password if necessary.
You are redirected to the URI address provided for your client. For example:
https://localhost:3000/cb?session_state=5c9bce22-6b85-4654-b716-e9bbb3e755bc&iss=http%3A%2F%2Flocalhost%3A8080%2Frealms%2Fmaster&code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43
https://localhost:3000/cb?session_state=5c9bce22-6b85-4654-b716-e9bbb3e755bc&iss=http%3A%2F%2Flocalhost%3A8080%2Frealms%2Fmaster&code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43Copy to Clipboard Copied! Toggle word wrap Toggle overflow Take note of the
codeprovided in the address. For example:code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43
code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThis is a temporary code that can only be used one time. If necessary, you can refresh the page or revisit the URL to obtain another code.
On your terminal, use the following
curl -X POSTcommand to generate a temporary OAuth2 access token:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJTVmExVHZ6eDd2cHVmc1dkZmc1SHdua1ZDcVlOM01DN1N5T016R0QwVGhVIn0...", "expires_in":60,"refresh_expires_in":1800,"refresh_token":"eyJhbGciOiJIUzUxMiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJiNTBlZTVkMS05OTc1LTQwMzUtYjNkNy1lMWQ5ZTJmMjg0MTEifQ.oBDx6B3pUkXQO8m-M3hYE7v-w25ak6y70CQd5J8f5EuldhvTwpWrC1K7yOglvs09dQxtq8ont12rKIoCIi4WXw","token_type":"Bearer","not-before-policy":0,"session_state":"5c9bce22-6b85-4654-b716-e9bbb3e755bc","scope":"profile email"}{"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJTVmExVHZ6eDd2cHVmc1dkZmc1SHdua1ZDcVlOM01DN1N5T016R0QwVGhVIn0...", "expires_in":60,"refresh_expires_in":1800,"refresh_token":"eyJhbGciOiJIUzUxMiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJiNTBlZTVkMS05OTc1LTQwMzUtYjNkNy1lMWQ5ZTJmMjg0MTEifQ.oBDx6B3pUkXQO8m-M3hYE7v-w25ak6y70CQd5J8f5EuldhvTwpWrC1K7yOglvs09dQxtq8ont12rKIoCIi4WXw","token_type":"Bearer","not-before-policy":0,"session_state":"5c9bce22-6b85-4654-b716-e9bbb3e755bc","scope":"profile email"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Store the
access_tokenfrom the previously step, as it will be exchanged for a Red Hat Quay robot account token in the following procedure.
6.8.2. Setting up a robot account federation by using the Red Hat Quay v2 UI
The following procedure shows you how to set up a robot account federation by using the Red Hat Quay v2 UI. This procedure uses Red Hat Single Sign-On, which is based on the Keycloak project. These steps, and the information used to set up a robot account federation, will vary depending on your OIDC provider.
Prerequisites
-
You have created an organization. The following example uses
fed_test. -
You have created a robot account. The following example uses
fest_test+robot1. - You have configured a OIDC for your Red Hat Quay deployment. The following example uses Red Hat Single Sign-On.
Procedure
On the Red Hat Single Sign-On main page:
-
Select the appropriate realm that is authenticated for use with Red Hat Quay. Store the issuer URL, for example,
https://keycloak-auth-realm.quayadmin.org/realms/quayrealm. -
Click Users
the name of the user to be linked with the robot account for authentication. You must use the same user account that you used when generating the OAuth2 access token. On the Details page, store the ID of the user, for example,
449e14f8-9eb5-4d59-a63e-b7a77c75f770.NoteThe information collected in this step will vary depending on your OIDC provider. For example, with Red Hat Single Sign-On, the ID of a user is used as the Subject to set up the robot account federation in a subsequent step. For a different OIDC provider, like Microsoft Entra ID, this information is stored as the Subject.
-
Select the appropriate realm that is authenticated for use with Red Hat Quay. Store the issuer URL, for example,
On your Red Hat Quay registry:
- Navigate to Organizations and click the name of your organization, for example, fed_test.
- Click Robot Accounts.
-
Click the menu kebab
Set robot federation. - Click the + symbol.
In the popup window, include the following information:
-
Issuer URL:
https://keycloak-auth-realm.quayadmin.org/realms/quayrealm. For Red Hat Single Sign-On, this is the the URL of your Red Hat Single Sign-On realm. This might vary depending on your OIDC provider. -
Subject:
449e14f8-9eb5-4d59-a63e-b7a77c75f770. For Red Hat Single Sign-On, the Subject is the ID of your Red Hat Single Sign-On user. This varies depending on your OIDC provider. For example, if you are using Microsoft Entra ID, the Subject will be the Subject or your Entra ID user.
-
Issuer URL:
- Click Save.
6.8.3. Exchanging an OAuth2 access token for a Red Hat Quay robot account token
The following procedure leverages the access token generated in the previous procedure to create a new Red Hat Quay robot account token. The new Red Hat Quay robot account token is used for authentication between your OIDC provider and Red Hat Quay.
The following example uses a Python script to exchange the OAuth2 access token for a Red Hat Quay robot account token.
Prerequisites
-
You have the
python3CLI tool installed.
Procedure
Save the following Python script in a
.pyfile, for example,robot_fed_token_auth.pyCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- If your Red Hat Quay deployment is using custom SSL/TLS certificates, the response must be
response = requests.get(URL,auth=(robot_user,fed_token),verify=False), which includes theverify=Falseflag.
Export the OAuth2 access token as
TOKEN. For example:export TOKEN = eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJTVmExVHZ6eDd2cHVmc1dkZmc1SHdua1ZDcVlOM01DN1N5T016R0QwVGhVIn0...
$ export TOKEN = eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJTVmExVHZ6eDd2cHVmc1dkZmc1SHdua1ZDcVlOM01DN1N5T016R0QwVGhVIn0...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the
robot_fed_token_auth.pyscript by entering the following command:python3 robot_fed_token_auth.py
$ python3 robot_fed_token_auth.pyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
<Response [200]> {"token": "291cmNlX2FjY2VzcyI6eyJhY2NvdW50Ijp7InJvbGVzIjpbIm1hbmFnZS1hY2NvdW50IiwibWFuYWdlLWFjY291bnQtbGlua3MiLCJ2aWV3LXByb2ZpbGUiXX19LCJzY29wZSI6InByb2ZpbGUgZW1haWwiLCJlbWFpbF92ZXJpZ..."}<Response [200]> {"token": "291cmNlX2FjY2VzcyI6eyJhY2NvdW50Ijp7InJvbGVzIjpbIm1hbmFnZS1hY2NvdW50IiwibWFuYWdlLWFjY291bnQtbGlua3MiLCJ2aWV3LXByb2ZpbGUiXX19LCJzY29wZSI6InByb2ZpbGUgZW1haWwiLCJlbWFpbF92ZXJpZ..."}Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThis token expires after one hour. After one hour, a new token must be generated.
Export the robot account access token as
QUAY_TOKEN. For example:export QUAY_TOKEN=291cmNlX2FjY2VzcyI6eyJhY2NvdW50Ijp7InJvbGVzIjpbIm1hbmFnZS1hY2NvdW50IiwibWFuYWdlLWFjY291bnQtbGlua3MiLCJ2aWV3LXByb2ZpbGUiXX19LCJzY29wZSI6InByb2ZpbGUgZW1haWwiLCJlbWFpbF92ZXJpZ
$ export QUAY_TOKEN=291cmNlX2FjY2VzcyI6eyJhY2NvdW50Ijp7InJvbGVzIjpbIm1hbmFnZS1hY2NvdW50IiwibWFuYWdlLWFjY291bnQtbGlua3MiLCJ2aWV3LXByb2ZpbGUiXX19LCJzY29wZSI6InByb2ZpbGUgZW1haWwiLCJlbWFpbF92ZXJpZCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.8.4. Pushing and pulling images
After you have generated a new robot account access token and exported it, you can log in and the robot account using the access token and push and pull images.
Prerequisites
- You have exported the OAuth2 access token into a new robot account access token.
Procedure
Log in to your Red Hat Quay registry using the
fest_test+robot1robot account and theQUAY_TOKENaccess token. For example:podman login <quay-server.example.com> -u fed_test+robot1 -p $QUAY_TOKEN
$ podman login <quay-server.example.com> -u fed_test+robot1 -p $QUAY_TOKENCopy to Clipboard Copied! Toggle word wrap Toggle overflow Pull an image from a Red Hat Quay repository for which the robot account has the proper permissions. For example:
podman pull <quay-server.example.com/<repository_name>/<image_name>>
$ podman pull <quay-server.example.com/<repository_name>/<image_name>>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Attempt to pull an image from a Red Hat Quay repository for which the robot account does not have the proper permissions. For example:
podman pull <quay-server.example.com/<different_repository_name>/<image_name>>
$ podman pull <quay-server.example.com/<different_repository_name>/<image_name>>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Error: initializing source docker://quay-server.example.com/example_repository/busybox:latest: reading manifest in quay-server.example.com/example_repository/busybox: unauthorized: access to the requested resource is not authorized
Error: initializing source docker://quay-server.example.com/example_repository/busybox:latest: reading manifest in quay-server.example.com/example_repository/busybox: unauthorized: access to the requested resource is not authorizedCopy to Clipboard Copied! Toggle word wrap Toggle overflow After one hour, the credentials for this robot account are set to expire. Afterwards, you must generate a new access token for this robot account.