Chapter 10. LDAP Authentication Setup for Red Hat Quay
Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Red Hat Quay supports using LDAP as an identity provider.
10.1. Considerations when enabling LDAP
Prior to enabling LDAP for your Red Hat Quay deployment, you should consider the following.
Existing Red Hat Quay deployments
Conflicts between usernames can arise when you enable LDAP for an existing Red Hat Quay deployment that already has users configured. For example, one user, alice, was manually created in Red Hat Quay prior to enabling LDAP. If the username alice also exists in the LDAP directory, Red Hat Quay automatically creates a new user, alice-1, when alice logs in for the first time using LDAP. Red Hat Quay then automatically maps the LDAP credentials to the alice account. For consistency reasons, this might be erroneous for your Red Hat Quay deployment. It is recommended that you remove any potentially conflicting local account names from Red Hat Quay prior to enabling LDAP.
Manual User Creation and LDAP authentication
When Red Hat Quay is configured for LDAP, LDAP-authenticated users are automatically created in Red Hat Quay’s database on first log in, if the configuration option FEATURE_USER_CREATION is set to True. If this option is set to False, the automatic user creation for LDAP users fails, and the user is not allowed to log in. In this scenario, the superuser needs to create the desired user account first. Conversely, if FEATURE_USER_CREATION is set to True, this also means that a user can still create an account from the Red Hat Quay login screen, even if there is an equivalent user in LDAP.
10.2. Configuring LDAP for Red Hat Quay
Use the following procedure to configure LDAP for your Red Hat Quay deployment.
Procedure
You can use the Red Hat Quay config tool to configure LDAP.
Using the Red Hat Quay config tool, locate the Authentication section. Select LDAP from the dropdown menu, and update the LDAP configuration fields as required.
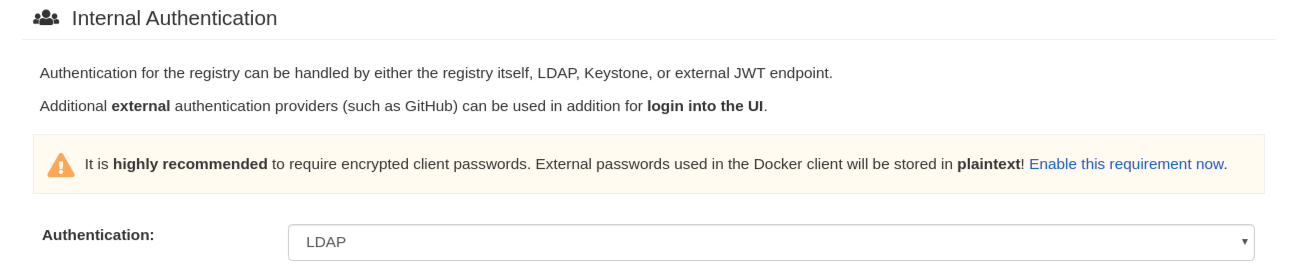
Optional. On the Team synchronization box, and click Enable Team Syncrhonization Support. With team synchronization enabled, Red Hat Quay administrators who are also superusers can set teams to have their membership synchronized with a backing group in LDAP.

-
For Resynchronization duration enter 60m. This option sets the resynchronization duration at which a team must be re-synchronized. This field must be set similar to the following examples:
30m,1h,1d. Optional. For Self-service team syncing setup, you can click Allow non-superusers to enable and manage team syncing to allow superusers the ability to enable and manage team syncing under the organizations that they are administrators for.
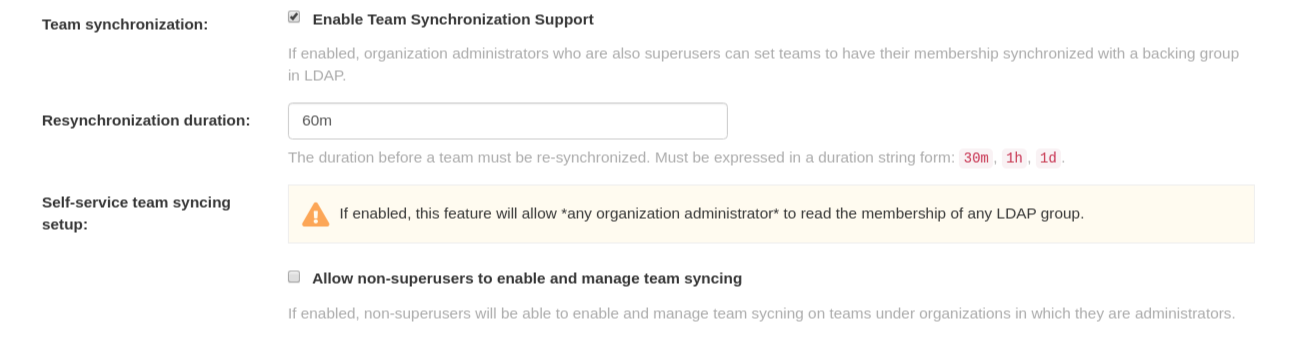
Locate the LDAP URI box and provide a full LDAP URI, including the ldap:// or ldaps:// prefix, for example,
ldap://117.17.8.101.
Under Base DN, provide a name which forms the base path for looking up all LDAP records, for example,
o=<organization_id>,dc=<example_domain_component>,dc=com.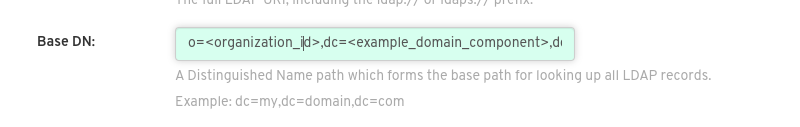
Under User Relative DN, provide a list of Distinguished Name path(s), which form the secondary base path(s) for looking up all user LDAP records relative to the Base DN defined above. For example,
uid=<name>,ou=Users,o=<organization_id>,dc=<example_domain_component>,dc=com. This path, or these paths, is tried if the user is not found through the primary relative DN.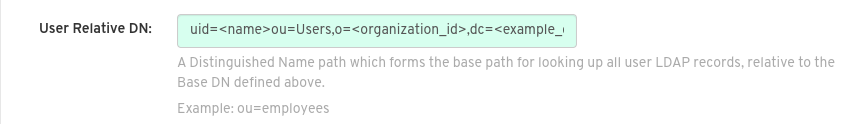 Note
NoteUser Relative DN is relative to Base DN, for example,
ou=Usersand notou=Users,dc=<example_domain_component>,dc=com.Optional. Provide Secondary User Relative DNs if there are multiple Organizational Units where user objects are located. You can type in the Organizational Units and click Add to add multiple RDNs. For example,
ou=Users,ou=NYC and ou=Users,ou=SFO.The User Relative DN searches with subtree scope. For example, if your organization has Organization Units
NYCandSFOunder the Users OU (that is,ou=SFO,ou=Usersandou=NYC,ou=Users), Red Hat Quay can authenticate users from both theNYCandSFOOrganizational Units if the User Relative DN is set toUsers(ou=Users).Optional. Fill in the Additional User Filter Expression field for all user lookup queries if desired. Distinguished Names used in the filter must be full based. The Base DN is not added automatically added to this field, and you must wrap the text in parentheses, for example,
(memberOf=cn=developers,ou=groups,dc=<example_domain_component>,dc=com).
Fill in the Administrator DN field for the Red Hat Quay administrator account. This account must be able to login and view the records for all users accounts. For example:
uid=<name>,ou=Users,o=<organization_id>,dc=<example_domain_component>,dc=com.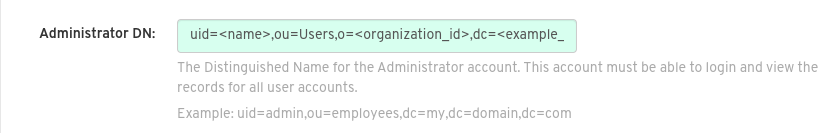
Fill in the Administrator DN Password field. This is the password for the administrator distinguished name.
ImportantThe password for this field is stored in plaintext inside of the
config.yamlfile. Setting up a dedicated account of using a password hash is highly recommended.Optional. Fill in the UID Attribute field. This is the name of the property field in the LDAP user records that stores your user’s username. Most commonly, uid is entered for this field. This field can be used to log into your Red Hat Quay deployment.

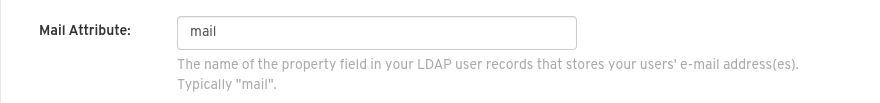
Optional. Fill in the Mail Attribute field. This is the name of the property field in your LDAP user records that stores your user’s e-mail addresses. Most commonly, mail is entered for this field. This field can be used to log into your Red Hat Quay deployment.
 Note
Note- The username to log in must exist in the User Relative DN.
-
If you are using Microsoft Active Directory to setup your LDAP deployment, you must use
sAMAccountNamefor your UID attribute.
Optional. You can add a custom SSL/TLS certificate by clicking Choose File under the Custom TLS Certificate optionl. Additionally, you can enable fallbacks to insecure, non-TLS connections by checking the Allow fallback to non-TLS connections box.
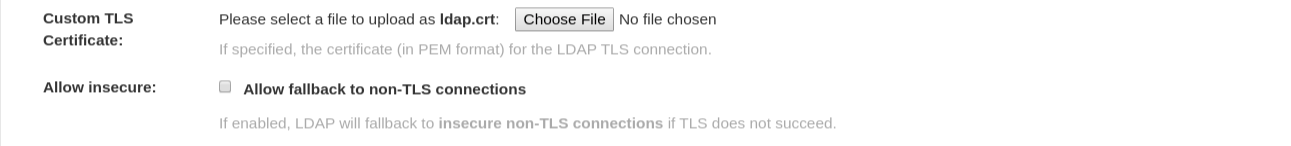
If you upload an SSl/TLS certificate, you must provide an ldaps:// prefix, for example,
LDAP_URI: ldaps://ldap_provider.example.org.
Alternatively, you can update your
config.yamlfile directly to include all relevant information. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - After you have added all required LDAP fields, click the Save Configuration Changes button to validate the configuration. All validation must succeed before proceeding. Additional configuration can be performed by selecting the Continue Editing button.
10.3. Enabling the LDAP_RESTRICTED_USER_FILTER configuration field
The LDAP_RESTRICTED_USER_FILTER configuration field is a subset of the LDAP_USER_FILTER configuration field. When configured, this option allows Red Hat Quay administrators the ability to configure LDAP users as restricted users when Red Hat Quay uses LDAP as its authentication provider.
Use the following procedure to enable LDAP restricted users on your Red Hat Quay deployment.
Prerequisites
- Your Red Hat Quay deployment uses LDAP as its authentication provider.
-
You have configured the
LDAP_USER_FILTERfield in yourconfig.yamlfile.
Procedure
In your deployment’s
config.yamlfile, add theLDAP_RESTRICTED_USER_FILTERparameter and specify the group of restricted users, for example,members:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Start, or restart, your Red Hat Quay deployment.
After enabling the LDAP_RESTRICTED_USER_FILTER feature, your LDAP Red Hat Quay users are restricted from reading and writing content, and creating organizations.
10.4. Enabling the LDAP_SUPERUSER_FILTER configuration field
With the LDAP_SUPERUSER_FILTER field configured, Red Hat Quay administrators can configure Lightweight Directory Access Protocol (LDAP) users as superusers if Red Hat Quay uses LDAP as its authentication provider.
Use the following procedure to enable LDAP superusers on your Red Hat Quay deployment.
Prerequisites
- Your Red Hat Quay deployment uses LDAP as its authentication provider.
-
You have configured the
LDAP_USER_FILTERfield field in yourconfig.yamlfile.
Procedure
In your deployment’s
config.yamlfile, add theLDAP_SUPERUSER_FILTERparameter and add the group of users you want configured as super users, for example,root:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Start, or restart, your Red Hat Quay deployment.
After enabling the LDAP_SUPERUSER_FILTER feature, your LDAP Red Hat Quay users have superuser privileges. The following options are available to superusers:
- Manage users
- Manage organizations
- Manage service keys
- View the change log
- Query the usage logs
- Create globally visible user messages
10.5. Common LDAP configuration issues
The following errors might be returned with an invalid configuration.
- Invalid credentials. If you receive this error, the Administrator DN or Administrator DN password values are incorrect. Ensure that you are providing accurate Administrator DN and password values.
*Verification of superuser %USERNAME% failed. This error is returned for the following reasons:
- The username has not been found.
- The user does not exist in the remote authentication system.
- LDAP authorization is configured improperly.
Cannot find the current logged in user. When configuring LDAP for Red Hat Quay, there may be situations where the LDAP connection is established successfully using the username and password provided in the Administrator DN fields. However, if the current logged-in user cannot be found within the specified User Relative DN path using the UID Attribute or Mail Attribute fields, there are typically two potential reasons for this:
- The current logged in user does not exist in the User Relative DN path.
The Administrator DN does not have rights to search or read the specified LDAP path.
To fix this issue, ensure that the logged in user is included in the User Relative DN path, or provide the correct permissions to the Administrator DN account.
10.6. LDAP configuration fields
For a full list of LDAP configuration fields, see LDAP configuration fields