Provisioning hosts
Configure provisioning resources and networking, provision physical machines, provision virtual machines on cloud providers or virtualization infrastructure, create hosts manually or by using the Discovery service
Abstract
Providing feedback on Red Hat documentation
We appreciate your feedback on our documentation. Let us know how we can improve it.
Use the Create Issue form in Red Hat Jira to provide your feedback. The Jira issue is created in the Red Hat Satellite Jira project, where you can track its progress.
Prerequisites
- Ensure you have registered a Red Hat account.
Procedure
- Click the following link: Create Issue. If Jira displays a login error, log in and proceed after you are redirected to the form.
- Complete the Summary and Description fields. In the Description field, include the documentation URL, chapter or section number, and a detailed description of the issue. Do not modify any other fields in the form.
- Click Create.
Chapter 1. Introduction to provisioning
Provisioning is a process that starts with a bare physical or virtual machine and ends with a fully configured, ready-to-use operating system. Using Red Hat Satellite, you can define and automate fine-grained provisioning for a large number of hosts.
1.1. Provisioning methods in Red Hat Satellite
With Red Hat Satellite, you can provision hosts by using the following methods.
- Bare-metal hosts
Satellite provisions bare-metal hosts primarily by using PXE boot and MAC address identification. When provisioning bare-metal hosts with Satellite, you can do the following:
- Create host entries and specify the MAC address of the physical host to provision.
- Boot blank hosts to use the Satellite Discovery service, which creates a pool of hosts that are ready for provisioning.
- Cloud providers
Satellite connects to private and public cloud providers to provision instances of hosts from images stored in the cloud environment. When provisioning from cloud with Satellite, you can do the following:
- Select which hardware profile to use.
- Provision cloud instances from specific providers by using their APIs.
- Virtualization infrastructure
Satellite connects to virtualization infrastructure services, such as Red Hat Virtualization and VMware. When provisioning virtual machines with Satellite, you can do the following:
- Provision virtual machines from virtual image templates.
- Use the same PXE-based boot methods that you use to provision bare-metal hosts.
1.2. Supported host platforms in provisioning
Satellite supports the following operating systems and architectures for host provisioning.
- Supported host operating systems
The hosts can use the following operating systems:
- Red Hat Enterprise Linux 9 and 8
- Red Hat Enterprise Linux 7 with the ELS Add-On
- Supported host architectures
The hosts can use the following architectures:
- AMD and Intel 64-bit architectures
- The 64-bit ARM architecture
- IBM Power Systems, Little Endian
- 64-bit IBM Z architectures
1.3. Supported cloud providers
You can connect the following cloud providers as compute resources to Satellite:
- Red Hat OpenStack Services on OpenShift
- Amazon EC2
- Google Compute Engine
- Microsoft Azure
1.4. Supported virtualization infrastructures
You can connect the following virtualization infrastructures as compute resources to Satellite:
- KVM (libvirt)
- Red Hat Virtualization (deprecated)
- VMware
- OpenShift Virtualization
1.5. Network boot provisioning workflow
The provisioning process follows a basic PXE workflow:
- You create a host and select a domain and subnet. Satellite requests an available IP address from the DHCP Capsule Server that is associated with the subnet or from the PostgreSQL database in Satellite. Satellite loads this IP address into the IP address field in the Create Host window. When you complete all the options for the new host, submit the new host request.
Depending on the configuration specifications of the host and its domain and subnet, Satellite creates the following settings:
- A DHCP record on Capsule Server that is associated with the subnet.
- A forward DNS record on Capsule Server that is associated with the domain.
- A reverse DNS record on the DNS Capsule Server that is associated with the subnet.
- PXELinux, Grub, Grub2, and iPXE configuration files for the host in the TFTP Capsule Server that is associated with the subnet.
- A Puppet certificate on the associated Puppet server.
- A realm on the associated identity server.
- The host is configured to boot from the network as the first device and HDD as the second device.
- The new host requests a DHCP reservation from the DHCP server.
-
The DHCP server responds to the reservation request and returns TFTP
next-serverandfilenameoptions. - The host requests the boot loader and menu from the TFTP server according to the PXELoader setting.
- A boot loader is returned over TFTP.
- The boot loader fetches configuration for the host through its provisioning interface MAC address.
- The boot loader fetches the operating system installer kernel, init RAM disk, and boot parameters.
- The installer requests the provisioning template from Satellite.
- Satellite renders the provision template and returns the result to the host.
The installer performs installation of the operating system.
- The installer registers the host to Satellite by using Subscription Manager.
-
The installer notifies Satellite of a successful build in the
postinstallscript.
- The PXE configuration files revert to a local boot template.
- The host reboots.
- The new host requests a DHCP reservation from the DHCP server.
-
The DHCP server responds to the reservation request and returns TFTP
next-serverandfilenameoptions. - The host requests the bootloader and menu from the TFTP server according to the PXELoader setting.
- A boot loader is returned over TFTP.
- The boot loader fetches the configuration for the host through its provision interface MAC address.
- The boot loader initiates boot from the local drive.
- If you configured the host to use Puppet classes, the host uses the modules to configure itself.
The fully provisioned host performs the following workflow:
- The host is configured to boot from the network as the first device and HDD as the second device.
- The new host requests a DHCP reservation from the DHCP server.
-
The DHCP server responds to the reservation request and returns TFTP
next-serverandfilenameoptions. - The host requests the boot loader and menu from the TFTP server according to the PXELoader setting.
- A boot loader is returned over TFTP.
- The boot loader fetches the configuration settings for the host through its provisioning interface MAC address.
For BIOS hosts:
- The boot loader returns non-bootable device so BIOS skips to the next device (boot from HDD).
For EFI hosts:
- The boot loader finds Grub2 on a ESP partition and chainboots it.
- If the host is unknown to Satellite, a default bootloader configuration is provided. When Discovery service is enabled, it boots into discovery, otherwise it boots from HDD.
This workflow differs depending on custom options. For example:
- Discovery
- If you use the discovery service, Satellite automatically detects the MAC address of the new host and restarts the host after you submit a request. Note that TCP port 8443 must be reachable by the Capsule to which the host is attached for Satellite to restart the host.
- PXE-less Provisioning
- After you submit a new host request, you must boot the specific host with the boot disk that you download from Satellite and transfer by using an external storage device.
- Compute Resources
-
Satellite creates the virtual machine and retrieves the MAC address and stores the MAC address in Satellite. If you use image-based provisioning, the host does not follow the standard PXE boot and operating system installation. The compute resource creates a copy of the image for the host to use. Depending on image settings in Satellite, seed data can be passed in for initial configuration, for example by using
cloud-init. Satellite can connect to the host by using SSH and execute a template to finish the customization.
1.6. Required boot order for network boot
- For physical or virtual BIOS hosts
- Set the first booting device as boot configuration with network.
- Set the second booting device as boot from hard drive. Satellite manages TFTP boot configuration files, so hosts can be easily provisioned just by rebooting.
- For physical or virtual EFI hosts
- Set the first booting device as boot configuration with network.
- Depending on the EFI firmware type and configuration, the operating system installer typically configures the operating system boot loader as the first entry.
-
To reboot into installer again, use the
efibootmgrutility to switch back to boot from network.
Chapter 2. Configuring provisioning resources
2.1. Provisioning contexts
A provisioning context is the combination of an organization and location that you specify for Satellite components. The organization and location that a component belongs to sets the ownership and access for that component.
Organizations divide Red Hat Satellite components into logical groups based on ownership, purpose, content, security level, and other divisions. You can create and manage multiple organizations through Red Hat Satellite and assign components to each individual organization. This ensures Satellite Server provisions hosts within a certain organization and only uses components that are assigned to that organization. For more information about organizations, see Managing Organizations in Administering Red Hat Satellite.
Locations function similar to organizations. The difference is that locations are based on physical or geographical setting. Users can nest locations in a hierarchy. For more information about locations, see Managing Locations in Administering Red Hat Satellite.
2.2. Setting the provisioning context
When you set a provisioning context, you define which organization and location to use for provisioning hosts.
The organization and location menus are located in the menu bar, on the upper left of the Satellite web UI. If you have not selected an organization and location to use, the menu displays: Any Organization and Any Location.
Procedure
- Click Any Organization and select the organization.
- Click Any Location and select the location to use.
Each user can set their default provisioning context in their account settings. Click the user name in the upper right of the Satellite web UI and select My account to edit your user account settings.
CLI procedure
When using the CLI, include either
--organizationor--organization-labeland--locationor--location-idas an option. For example:hammer host list --organization "My_Organization" --location "My_Location"
# hammer host list --organization "My_Organization" --location "My_Location"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command outputs hosts allocated to
My_OrganizationandMy_Location.
2.3. Creating operating systems
An operating system is a collection of resources that define how Satellite Server installs a base operating system on a host. Operating system entries combine previously defined resources, such as installation media, partition tables, provisioning templates, and others.
Importing operating systems from Red Hat’s CDN creates new entries on the Hosts > Provisioning Setup > Operating Systems page. To import operating systems from Red Hat’s CDN, enable the Red Hat repositories of the operating systems and synchronize the repositories to Satellite. For more information, see Enabling Red Hat Repositories and Synchronizing Repositories in Managing content.
You can also add custom operating systems using the following procedure. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Operating systems and click New Operating system.
- In the Name field, enter a name to represent the operating system entry.
- In the Major field, enter the number that corresponds to the major version of the operating system.
- In the Minor field, enter the number that corresponds to the minor version of the operating system.
- In the Description field, enter a description of the operating system.
- From the Family list, select the operating system’s family.
- From the Root Password Hash list, select the encoding method for the root password.
- From the Architectures list, select the architectures that the operating system uses.
- Click the Partition table tab and select the possible partition tables that apply to this operating system.
- Optional: If you use non-Red Hat content, click the Installation Media tab and select the installation media that apply to this operating system. For more information, see Adding Installation Media to Satellite.
- Click the Templates tab and select a PXELinux template, a Provisioning template, and a Finish template for your operating system to use. You can select other templates, for example an iPXE template, if you plan to use iPXE for provisioning.
- Click Submit to save your provisioning template.
CLI procedure
Create the operating system using the
hammer os createcommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.4. Updating the details of multiple operating systems
Use this procedure to update the details of multiple operating systems. This example shows you how to assign each operating system a partition table called Kickstart default, a configuration template called Kickstart default PXELinux, and a provisioning template called Kickstart Default.
Procedure
On Satellite Server, run the following Bash script:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display information about the updated operating system to verify that the operating system is updated correctly:
hammer os info --id 1
# hammer os info --id 1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.5. Creating architectures
An architecture in Satellite represents a logical grouping of hosts and operating systems. Architectures are created by Satellite automatically when hosts check in with Puppet. The x86_64 architecture is already preset in Satellite.
Use this procedure to create an architecture in Satellite.
Supported architectures
Only Intel x86_64 architecture is supported for provisioning using PXE, Discovery, and boot disk. For more information, see the Red Hat Knowledgebase solution Supported architectures and provisioning scenarios in Satellite 6.
Procedure
- In the Satellite web UI, navigate to Hosts > Provisioning Setup > Architectures.
- Click Create Architecture.
- In the Name field, enter a name for the architecture.
- From the Operating Systems list, select an operating system. If none are available, you can create and assign them under Hosts > Provisioning Setup > Operating Systems.
- Click Submit.
CLI procedure
Enter the
hammer architecture createcommand to create an architecture. Specify its name and operating systems that include this architecture:hammer architecture create \ --name "My_Architecture" \ --operatingsystems "My_Operating_System"
# hammer architecture create \ --name "My_Architecture" \ --operatingsystems "My_Operating_System"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.6. Creating hardware models
Use this procedure to create a hardware model in Satellite so that you can specify which hardware model a host uses.
Procedure
- In the Satellite web UI, navigate to Hosts > Provisioning Setup > Hardware Models.
- Click Create Model.
- In the Name field, enter a name for the hardware model.
- Optionally, in the Hardware Model and Vendor Class fields, you can enter corresponding information for your system.
- In the Info field, enter a description of the hardware model.
- Click Submit to save your hardware model.
CLI procedure
Create a hardware model using the
hammer model createcommand. The only required parameter is--name. Optionally, enter the hardware model with the--hardware-modeloption, a vendor class with the--vendor-classoption, and a description with the--infooption:hammer model create \ --hardware-model "My_Hardware_Model" \ --info "My_Description" \ --name "My_Hardware_Model_Name" \ --vendor-class "My_Vendor_Class"
# hammer model create \ --hardware-model "My_Hardware_Model" \ --info "My_Description" \ --name "My_Hardware_Model_Name" \ --vendor-class "My_Vendor_Class"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.7. Using a synchronized Kickstart repository for a host’s operating system
Satellite contains a set of synchronized Kickstart repositories that you use to install the provisioned host’s operating system. For more information about adding repositories, see Syncing Repositories in Managing content.
Use this procedure to set up a Kickstart repository.
Prerequisites
You must enable both BaseOS and Appstream Kickstart before provisioning.
Procedure
Add the synchronized Kickstart repository that you want to use to the existing content view, or create a new content view and add the Kickstart repository.
For Red Hat Enterprise Linux 8, ensure that you add both Red Hat Enterprise Linux 8 for x86_64 - AppStream Kickstart x86_64 8 and Red Hat Enterprise Linux 8 for x86_64 - BaseOS Kickstart x86_64 8 repositories.
If you use a disconnected environment, you must import the Kickstart repositories from a Red Hat Enterprise Linux binary DVD.
- Publish a new version of the content view where the Kickstart repository is added and promote it to a required lifecycle environment. For more information, see Managing content views in Managing content.
- When you create a host, in the Operating System tab, for Media Selection, select the Synced Content checkbox.
To view the Kickstart tree, enter the following command:
hammer medium list --organization "My_Organization"
# hammer medium list --organization "My_Organization"2.8. Adding installation media to Satellite
Installation media are sources of packages that Satellite Server uses to install a base operating system on a machine from an external repository. You can use this parameter to install third-party content. Red Hat content is delivered through repository syncing instead.
You can view installation media by navigating to Hosts > Provisioning Setup > Installation Media.
Installation media must be in the format of an operating system installation tree and must be accessible from the machine hosting the installer through an HTTP URL.
By default, Satellite includes installation media for some official Linux distributions. Note that some of those installation media are targeted for a specific version of an operating system. For example CentOS mirror (7.x) must be used for CentOS 7 or earlier, and CentOS mirror (8.x) must be used for CentOS 8 or later.
If you want to improve download performance when using installation media to install operating systems on multiple hosts, you must modify the Path of the installation medium to point to the closest mirror or a local copy.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Provisioning Setup > Installation Media.
- Click Create Medium.
- In the Name field, enter a name to represent the installation media entry.
In the Path enter the URL that contains the installation tree. You can use following variables in the path to represent multiple different system architectures and versions:
-
$arch– The system architecture. -
$version– The operating system version. -
$major– The operating system major version. $minor– The operating system minor version.Example HTTP path:
http://download.example.com/centos/$version/Server/$arch/os/
http://download.example.com/centos/$version/Server/$arch/os/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
-
From the Operating system family list, select the distribution or family of the installation medium. For example, CentOS and Fedora are in the
Red Hatfamily. - Click the Organizations and Locations tabs, to change the provisioning context. Satellite Server adds the installation medium to the set provisioning context.
- Click Submit to save your installation medium.
CLI procedure
Create the installation medium using the
hammer medium createcommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.9. Creating partition tables
A partition table is a type of template that defines the way Satellite Server configures the disks available on a new host. A Partition table uses the same ERB syntax as provisioning templates. Red Hat Satellite contains a set of default partition tables to use, including a Kickstart default. You can also edit partition table entries to configure the preferred partitioning scheme, or create a partition table entry and add it to the operating system entry.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Partition Tables.
- Click Create Partition Table.
- In the Name field, enter a name for the partition table.
- Select the Default checkbox if you want to set the template to automatically associate with new organizations or locations.
- Select the Snippet checkbox if you want to identify the template as a reusable snippet for other partition tables.
- From the Operating System Family list, select the distribution or family of the partitioning layout. For example, Red Hat Enterprise Linux, CentOS, and Fedora are in the Red Hat family.
In the Template editor field, enter the layout for the disk partition.
The format of the layout must match that for the intended operating system. For example, Red Hat Enterprise Linux requires a layout that matches a Kickstart file, such as:
zerombr clearpart --all --initlabel autopart
zerombr clearpart --all --initlabel autopartCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information, see Section 2.11, “Dynamic partition example”.
You can also use the file browser in the template editor to import the layout from a file.
- In the Audit Comment field, add a summary of changes to the partition layout.
- Click the Organizations and Locations tabs to add any other provisioning contexts that you want to associate with the partition table. Satellite adds the partition table to the current provisioning context.
- Click Submit to save your partition table.
CLI procedure
Create a plain text file, such as
~/My_Partition_Table, that contains the partition layout.The format of the layout must match that for the intended operating system. For example, Red Hat Enterprise Linux requires a layout that matches a Kickstart file, such as:
zerombr clearpart --all --initlabel autopart
zerombr clearpart --all --initlabel autopartCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information, see Section 2.11, “Dynamic partition example”.
Create the installation medium using the
hammer partition-table createcommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.10. Associating partition tables with disk encryption
Satellite contains partition tables that encrypt the disk of your host by using Linux Unified Key Setup (LUKS) during host provisioning. Encrypted disks on hosts protect data at rest. Optionally, you can also bind the disk to a Tang server through Clevis for decryption during boot.
Associate the partition table with your operating system entry. Then, you assign the partition table to your host group or select it manually during provisioning.
Prerequisites
-
Your host has access to the
AppStreamrepository to installclevisduring provisioning.
Procedure
- In the Satellite web UI, navigate to Hosts > Provisioning Setup > Operating Systems.
- Select your Red Hat Enterprise Linux entry.
-
On the Partition Table tab, associate
Kickstart default encryptedwith your operating system entry. -
Create a host group that uses the
Kickstart default encryptedpartition table. For more information, see Creating a host group in Managing hosts. Decrypt the disk of your host during boot time by using one of the following options:
-
LUKS encryption: Add the host parameter
disk_enc_passphraseas type string and your cleartext passphrase of the LUKS container as the value. Clevis and Tang: Add the host parameter
disk_enc_tang_serversas type array and your list of Tang servers (example:["1.2.3.4"]or["server.example.com", "5.6.7.8"]).If you set
disk_enc_tang_servers, do not setdisk_enc_passphrasebecause the passphrase slot is removed from the LUKS container after provisioning.
-
LUKS encryption: Add the host parameter
2.11. Dynamic partition example
Using an Anaconda Kickstart template, the following section instructs Anaconda to erase the whole disk, automatically partition, enlarge one partition to maximum size, and then proceed to the next sequence of events in the provisioning process:
zerombr
clearpart --all --initlabel
autopart <%= host_param('autopart_options') %>
zerombr
clearpart --all --initlabel
autopart <%= host_param('autopart_options') %>Dynamic partitioning is executed by the installation program. Therefore, you can write your own rules to specify how you want to partition disks according to runtime information from the node, for example, disk sizes, number of drives, vendor, or manufacturer.
If you want to provision servers and use dynamic partitioning, add the following example as a template. When the #Dynamic entry is included, the content of the template loads into a %pre shell scriplet and creates a /tmp/diskpart.cfg that is then included into the Kickstart partitioning section.
2.12. Provisioning templates
A provisioning template defines the way Satellite Server installs an operating system on a host.
Red Hat Satellite includes many template examples. In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates to view them. You can create a template or clone a template and edit the clone. For help with templates, navigate to Hosts > Templates > Provisioning Templates > Create Template > Help.
Templates supported by Red Hat are indicated by a Red Hat icon.
To hide unsupported templates, in the Satellite web UI navigate to Administer > Settings. On the Provisioning tab, set the value of Show unsupported provisioning templates to false and click Submit. You can also filter out the supported templates by making the following query "supported = true".
If you clone a supported template, the cloned template will be unsupported.
Templates accept the Embedded Ruby (ERB) syntax. For more information, see Template Writing Reference in Managing hosts.
You can download provisioning templates. Before you can download the template, you must create a debug certificate. For more information, see Creating an Organization Debug Certificate in Administering Red Hat Satellite.
You can synchronize templates between Satellite Server and a Git repository or a local directory. For more information, see Synchronizing template repositories in Administering Red Hat Satellite.
To view the history of changes applied to a template, navigate to Hosts > Templates > Provisioning Templates, select one of the templates, and click History. Click Revert to override the content with the previous version. You can also revert to an earlier change. Click Show Diff to see information about a specific change:
- The Template Diff tab displays changes in the body of a provisioning template.
- The Details tab displays changes in the template description.
- The History tab displays the user who made a change to the template and date of the change.
2.13. Kinds of provisioning templates
There are various kinds of provisioning templates:
- Provision
The main template for the provisioning process. For example, a Kickstart template. For more information about Kickstart syntax and commands, see the following resources:
- Automated installation workflow in Automatically installing RHEL 9
- Automated installation workflow in Automatically installing RHEL 8
- Kickstart Syntax Reference in the Red Hat Enterprise Linux 7 Installation Guide
- PXELinux, PXEGrub, PXEGrub2
- PXE-based templates that deploy to the template Capsule associated with a subnet to ensure that the host uses the installer with the correct kernel options. For BIOS provisioning, select PXELinux template. For UEFI provisioning, select PXEGrub2.
- Finish
Post-configuration scripts to execute using an SSH connection when the main provisioning process completes. You can use Finish templates only for image-based provisioning in virtual or cloud environments that do not support user_data. Do not confuse an image with a foreman discovery ISO, which is sometimes called a Foreman discovery image. An image in this context is an install image in a virtualized environment for easy deployment.
When a finish script successfully exits with the return code
0, Red Hat Satellite treats the code as a success and the host exits the build mode.Note that there are a few finish scripts with a build mode that uses a call back HTTP call. These scripts are not used for image-based provisioning, but for post configuration of operating-system installations such as Debian, Ubuntu, and BSD. Red Hat does not support provisioning of operating systems other than Red Hat Enterprise Linux.
- user_data
Post-configuration scripts for providers that accept custom data, also known as seed data. You can use the user_data template to provision virtual machines in cloud or virtualised environments only. This template does not require Satellite to be able to reach the host; the cloud or virtualization platform is responsible for delivering the data to the image.
Ensure that the image that you want to provision has the software to read the data installed and set to start during boot. For example,
cloud-init, which expects YAML input, orignition, which expects JSON input.- cloud_init
Some environments, such as VMWare, either do not support custom data or have their own data format that limits what can be done during customization. In this case, you can configure a cloud-init client with the
foremanplugin, which attempts to download the template directly from Satellite over HTTP or HTTPS. This technique can be used in any environment, preferably virtualized.Ensure that you meet the following requirements to use the
cloud_inittemplate:- Ensure that the image that you want to provision has the software to read the data installed and set to start during boot.
A provisioned host is able to reach Satellite from the IP address that matches the host’s provisioning interface IP.
Note that cloud-init does not work behind NAT.
- Bootdisk
- Templates for PXE-less boot methods.
- Kernel Execution (kexec)
Kernel execution templates for PXE-less boot methods.
NoteKernel Execution is a Technology Preview feature. Technology Preview features are not fully supported under Red Hat Subscription Service Level Agreements (SLAs), may not be functionally complete, and are not intended for production use. However, these features provide early access to upcoming product innovations, enabling customers to test functionality and provide feedback during the development process.
- Script
- An arbitrary script not used by default but useful for custom tasks.
- ZTP
- Zero Touch Provisioning templates.
- POAP
- PowerOn Auto Provisioning templates.
- iPXE
-
Templates for
iPXEorgPXEenvironments to use instead of PXELinux.
2.14. Creating provisioning templates
A provisioning template defines the way Satellite Server installs an operating system on a host. Use this procedure to create a new provisioning template.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates and click Create Template.
- In the Name field, enter a name for the provisioning template.
- Fill in the rest of the fields as required. The Help tab provides information about the template syntax and details the available functions, variables, and methods that can be called on different types of objects within the template.
CLI procedure
-
Before you create a template with the CLI, create a plain text file that contains the template. This example uses the
~/my-templatefile. Create the template using the
hammer template createcommand and specify the type with the--typeoption:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.15. Cloning provisioning templates
A provisioning template defines the way Satellite Server installs an operating system on a host. Use this procedure to clone a template and add your updates to the clone.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
- Find the template that you want to use.
- Click Clone to duplicate the template.
- In the Name field, enter a name for the provisioning template.
- Select the Default checkbox to set the template to associate automatically with new organizations or locations.
- In the Template editor field, enter the body of the provisioning template. You can also use the Template file browser to upload a template file.
- In the Audit Comment field, enter a summary of changes to the provisioning template for auditing purposes.
- Click the Type tab and if your template is a snippet, select the Snippet checkbox. A snippet is not a standalone provisioning template, but a part of a provisioning template that can be inserted into other provisioning templates.
- From the Type list, select the type of the template. For example, Provisioning template.
- Click the Association tab and from the Applicable Operating Systems list, select the names of the operating systems that you want to associate with the provisioning template.
- Optionally, click Add combination and select a host group from the Host Group list or an environment from the Environment list to associate provisioning template with the host groups and environments.
- Click the Organizations and Locations tabs to add any additional contexts to the template.
- Click Submit to save your provisioning template.
2.16. Creating custom provisioning snippets
You can execute custom code before and/or after the host provisioning process.
Prerequisites
Check your provisioning template to ensure that it supports the custom snippets you want to use.
You can view all provisioning templates under Hosts > Templates > Provisioning Templates.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates and click Create Template.
In the Name field, enter a name for your custom provisioning snippet. The name must start with the name of a provisioning template that supports including custom provisioning snippets:
-
Append
custom preto the name of a provisioning template to run code before provisioning a host. -
Append
custom postto the name of a provisioning template to run code after provisioning a host.
-
Append
- On the Type tab, select Snippet.
- Click Submit to create your custom provisioning snippet.
CLI procedure
- Create a plain text file that contains your custom snippet.
Create the template using
hammer:hammer template create \ --file "/path/to/My_Snippet" \ --locations "My_Location" \ --name "My_Template_Name_custom_pre" \ --organizations "_My_Organization" \ --type snippet
# hammer template create \ --file "/path/to/My_Snippet" \ --locations "My_Location" \ --name "My_Template_Name_custom_pre" \ --organizations "_My_Organization" \ --type snippetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.17. Custom provisioning snippet example for Red Hat Enterprise Linux
You can use Custom Post snippets to call external APIs from within the provisioning template directly after provisioning a host.
Kickstart default finish custom post Example for Red Hat Enterprise Linux
2.18. Associating templates with operating systems
You can associate templates with operating systems in Satellite. The following example adds a provisioning template to an operating system entry.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
- Select a provisioning template.
- On the Association tab, select all applicable operating systems.
- Click Submit to save your changes.
CLI procedure
Optional: View all templates:
hammer template list
# hammer template listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: View all operating systems:
hammer os list
# hammer os listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Associate a template with an operating system:
hammer template add-operatingsystem \ --id My_Template_ID \ --operatingsystem-id My_Operating_System_ID
# hammer template add-operatingsystem \ --id My_Template_ID \ --operatingsystem-id My_Operating_System_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.19. Creating compute profiles
You can use compute profiles to predefine virtual machine hardware details such as CPUs, memory, and storage.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
A default installation of Red Hat Satellite contains three predefined profiles:
-
1-Small -
2-Medium -
3-Large
You can apply compute profiles to all supported compute resources:
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles and click Create Compute Profile.
- In the Name field, enter a name for the profile.
- Click Submit. A new window opens with the name of the compute profile.
- In the new window, click the name of each compute resource and edit the attributes you want to set for this compute profile.
CLI procedure
Create a new compute profile:
hammer compute-profile create --name "My_Compute_Profile"
# hammer compute-profile create --name "My_Compute_Profile"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set attributes for the compute profile:
hammer compute-profile values create \ --compute-attributes "flavor=m1.small,cpus=2,memory=4GB,cpu_mode=default \ --compute-resource "My_Compute_Resource" \ --compute-profile "My_Compute_Profile" \ --volume size=40GB
# hammer compute-profile values create \ --compute-attributes "flavor=m1.small,cpus=2,memory=4GB,cpu_mode=default \ --compute-resource "My_Compute_Resource" \ --compute-profile "My_Compute_Profile" \ --volume size=40GBCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: To update the attributes of a compute profile, specify the attributes you want to change. For example, to change the number of CPUs and memory size:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: To change the name of the compute profile, use the
--new-nameattribute:hammer compute-profile update \ --name "My_Compute_Profile" \ --new-name "My_New_Compute_Profile"
# hammer compute-profile update \ --name "My_Compute_Profile" \ --new-name "My_New_Compute_Profile"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Additional resources
-
For more information about creating compute profiles by using Hammer, enter
hammer compute-profile --help.
2.20. Setting a default encrypted root password for hosts
If you do not want to set a plain text default root password for the hosts that you provision, you can use a default encrypted password.
The default root password can be inherited by a host group and consequentially by hosts in that group.
If you change the password and reprovision the hosts in the group that inherits the password, the password will be overwritten on the hosts.
Procedure
Generate an encrypted password:
python3 -c 'import crypt,getpass;pw=getpass.getpass(); print(crypt.crypt(pw)) if (pw==getpass.getpass("Confirm: ")) else exit()'$ python3 -c 'import crypt,getpass;pw=getpass.getpass(); print(crypt.crypt(pw)) if (pw==getpass.getpass("Confirm: ")) else exit()'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the password for later use.
- In the Satellite web UI, navigate to Administer > Settings.
- On the Settings page, select the Provisioning tab.
- In the Name column, navigate to Root password, and click Click to edit.
- Paste the encrypted password, and click Save.
2.21. Using noVNC to access virtual machines
You can use your browser to access the VNC console of VMs created by Satellite.
Satellite supports using noVNC on the following virtualization platforms:
- VMware
- Libvirt
- Red Hat Virtualization
Prerequisites
- You must have a virtual machine created by Satellite.
- For existing virtual machines, ensure that the Display type in the Compute Resource settings is VNC.
- You must import the Katello root CA certificate into your Satellite Server. Adding a security exception in the browser is not enough for using noVNC. For more information, see Installing the Katello root CA certificate in Configuring authentication for Red Hat Satellite users.
Procedure
On your Satellite Server, configure the firewall to allow VNC service on ports 5900 to 5930.
firewall-cmd --add-port=5900-5930/tcp firewall-cmd --add-port=5900-5930/tcp --permanent
# firewall-cmd --add-port=5900-5930/tcp # firewall-cmd --add-port=5900-5930/tcp --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the Satellite web UI, navigate to Infrastructure > Compute Resources and select the name of a compute resource.
- In the Virtual Machines tab, select the name of your virtual machine. Ensure the machine is powered on and then select Console.
2.22. Removing a virtual machine upon host deletion
By default, when you delete a host provisioned by Satellite, Satellite does not remove the actual VM on the compute resource. You can configure Satellite to remove the VM when deleting the host entry on Satellite.
If you do not remove the associated VM and attempt to create a new VM with the same FQDN later, it will fail because that VM already exists in the compute resource. You can still re-register the existing VM to Satellite.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Prerequisites
-
Your Satellite account has a role that grants the
view_settingsandedit_settingspermissions.
Procedure
- In the Satellite web UI, navigate to Administer > Settings > Provisioning.
- Change the value of the Destroy associated VM on host delete setting to Yes.
CLI procedure
Configure Satellite to remove a VM upon host deletion by using Hammer:
hammer settings set \ --name destroy_vm_on_host_delete \ --value true \ --location "My_Location" \ --organization "My_Organization"
# hammer settings set \ --name destroy_vm_on_host_delete \ --value true \ --location "My_Location" \ --organization "My_Organization"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 3. Configuring networking
Each provisioning type requires some network configuration. Use this chapter to configure network services on your Capsules.
New hosts must have access to either your Satellite Server or any Capsule Server. If your hosts are on isolated networks and cannot connect to Satellite Server directly, you must provision your hosts from Capsule Servers. Provisioning by using Capsule Servers can save on network bandwidth.
Configuring Capsules has two basic requirements:
Configuring network services. This includes:
- Content delivery services
- Network services (DHCP, DNS, and TFTP)
- Puppet configuration
- Defining network resource data in Satellite Server to help configure network interfaces on new hosts.
The following instructions have similar applications to configuring Capsule Servers managing a specific network. To configure Satellite to use external DHCP, DNS, and TFTP services, see Configuring External Services in Installing Satellite Server in a connected network environment.
3.1. Facts and NIC filtering
Facts describe aspects such as total memory, operating system version, or architecture as reported by the host. You can find facts in Monitor > Facts and search hosts through facts or use facts in templates.
Satellite collects facts from multiple sources:
-
subscription manager -
ansible -
puppet
Satellite is an inventory system for hosts and network interfaces. For hypervisors or container hosts, adding thousands of interfaces per host and updating the inventory every few minutes is inadequate. For each individual NIC reported, Satellite creates a NIC entry and those entries are never removed from the database. Parsing all the facts and comparing all records in the database makes Satellite extremely slow and unusable. To optimize the performance of various actions, most importantly fact import, you can use the options available on the Facts tab under Administer > Settings.
3.2. Optimizing performance by removing NICs from database
Filter and exclude the connections using the Exclude pattern for facts stored in Satellite and Ignore interfaces with matching identifier option. By default, these options are set to most common hypervisors. If you name the virtual interfaces differently, you can update this filter to use it according to your requirements.
Procedure
- In the Satellite web UI, navigate to Administer > Settings and select the Facts tab.
-
To filter out all interfaces starting with specific names, for example,
blu, addblu*to theIgnore interfaces with matching identifieroption. To prevent databases from storing facts related to interfaces starting with specific names, for example,
blu, addblu*to theExclude pattern for facts stored in Satelliteoption.By default, it contains the same list as the
Ignore interfaces with matching identifieroption. You can override it based on the your requirements. This filters out facts completely without storing them.To remove facts from the database, enter the following command:
foreman-rake facts:clean
# foreman-rake facts:cleanCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command removes all facts matching with the filter added in Administer > Settings > Facts > the
Exclude pattern for facts stored in Satelliteoption.To remove interfaces from the database, enter the following command:
foreman-rake interfaces:clean
# foreman-rake interfaces:cleanCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command removes all interfaces matching with the filter added in Administer > Settings > Facts > the
Ignore interfaces with matching identifieroption.
3.3. Network resources
Satellite contains networking resources that you must set up and configure to create a host. It includes the following networking resources:
- Domain
-
You must assign every host that is managed by Satellite to a domain. Using the domain, Satellite can manage A, AAAA, and PTR records. Even if you do not want Satellite to manage your DNS servers, you still must create and associate at least one domain. Domains are included in the naming conventions Satellite hosts, for example, a host with the name
test123in theexample.comdomain has the fully qualified domain nametest123.example.com. - Subnet
You must assign every host managed by Satellite to a subnet. Using subnets, Satellite can then manage IPv4 reservations. If there are no reservation integrations, you still must create and associate at least one subnet. When you manage a subnet in Satellite, you cannot create DHCP records for that subnet outside of Satellite. In Satellite, you can use IP Address Management (IPAM) to manage IP addresses with one of the following options:
DHCP: DHCP Capsule manages the assignment of IP addresses by finding the next available IP address starting from the first address of the range and skipping all addresses that are reserved. Before assigning an IP address, Capsule sends an ICMP and TCP pings to check whether the IP address is in use. Note that if a host is powered off, or has a firewall configured to disable connections, Satellite makes a false assumption that the IP address is available. This check does not work for hosts that are turned off, therefore, the DHCP option can only be used with subnets that Satellite controls and that do not have any hosts created externally.
The Capsule DHCP module retains the offered IP addresses for a short period of time to prevent collisions during concurrent access, so some IP addresses in the IP range might remain temporarily unused.
- Internal DB: Satellite finds the next available IP address from the Subnet range by excluding all IP addresses from the Satellite database in sequence. The primary source of data is the database, not DHCP reservations. This IPAM is not safe when multiple hosts are being created in parallel; in that case, use DHCP or Random DB IPAM instead.
- Random DB: Satellite finds the next available IP address from the Subnet range by excluding all IP addresses from the Satellite database randomly. The primary source of data is the database, not DHCP reservations. This IPAM is safe to use with concurrent host creation as IP addresses are returned in random order, minimizing the chance of a conflict.
- EUI-64: Extended Unique Identifier (EUI) 64bit IPv6 address generation, as per RFC2373, is obtained through the 48-bit MAC address.
- External IPAM: Delegates IPAM to an external system through Capsule feature. Satellite currently does not ship with any external IPAM implementations, but several plugins are in development.
None: IP address for each host must be entered manually.
Options DHCP, Internal DB and Random DB can lead to DHCP conflicts on subnets with records created externally. These subnets must be under exclusive Satellite control.
For more information about adding a subnet, see Section 3.9, “Adding a subnet to Satellite Server”.
- DHCP Ranges
- You can define the same DHCP range in Satellite Server for both discovered and provisioned systems, but use a separate range for each service within the same subnet.
3.4. Satellite and DHCP options
Satellite manages DHCP reservations through a DHCP Capsule. Satellite also sets the next-server and filename DHCP options.
The next-server option
The next-server option provides the IP address of the TFTP server to boot from. This option is not set by default and must be set for each TFTP Capsule. You can use the satellite-installer command with the --foreman-proxy-tftp-servername option to set the TFTP server in the /etc/foreman-proxy/settings.d/tftp.yml file:
satellite-installer --foreman-proxy-tftp-servername 1.2.3.4
# satellite-installer --foreman-proxy-tftp-servername 1.2.3.4Each TFTP Capsule then reports this setting through the API and Satellite can retrieve the configuration information when it creates the DHCP record.
When the PXE loader is set to none, Satellite does not populate the next-server option into the DHCP record.
If the next-server option remains undefined, Satellite calls the Capsule API to retrieve the server name as specified by the --foreman-proxy-tftp-servername argument in a satellite-installer run. If the Capsule API call does not return a server name, Satellite uses the hostname of the Capsule.
The filename option
The filename option contains the full path to the file that downloads and executes during provisioning. The PXE loader that you select for the host or host group defines which filename option to use. When the PXE loader is set to none, Satellite does not populate the filename option into the DHCP record. Depending on the PXE loader option, the filename changes as follows:
| PXE loader option | filename entry | Notes |
|---|---|---|
| PXELinux BIOS |
| |
| PXELinux UEFI |
| |
| iPXE Chain BIOS |
| |
| PXEGrub2 UEFI |
| x64 can differ depending on architecture |
| iPXE UEFI HTTP |
|
Requires the |
| Grub2 UEFI HTTP |
|
Requires the |
3.5. Troubleshooting DHCP problems in Satellite
Satellite can manage an ISC DHCP server on Satellite Server or Capsule Servers. Satellite can list, create, and delete DHCP reservations and leases. However, there are several problems that you might encounter on occasions.
Out of sync DHCP records
When an error occurs during DHCP orchestration, DHCP records in the Satellite database and the DHCP server might not match. To fix this, you must add missing DHCP records from the Satellite database to the DHCP server and then remove unwanted records from the DHCP server as per the following steps:
Procedure
To preview the DHCP records that are going to be added to the DHCP server, enter the following command:
foreman-rake orchestration:dhcp:add_missing subnet_name=NAME
# foreman-rake orchestration:dhcp:add_missing subnet_name=NAMECopy to Clipboard Copied! Toggle word wrap Toggle overflow If you are satisfied by the preview changes in the previous step, apply them by entering the above command with the
perform=1argument:foreman-rake orchestration:dhcp:add_missing subnet_name=NAME perform=1
# foreman-rake orchestration:dhcp:add_missing subnet_name=NAME perform=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow To keep DHCP records in Satellite and in the DHCP server synchronized, you can remove unwanted DHCP records from the DHCP server. Note that Satellite assumes that all managed DHCP servers do not contain third-party records, therefore, this step might delete those unexpected records. To preview what records are going to be removed from the DHCP server, enter the following command:
foreman-rake orchestration:dhcp:remove_offending subnet_name=NAME
# foreman-rake orchestration:dhcp:remove_offending subnet_name=NAMECopy to Clipboard Copied! Toggle word wrap Toggle overflow If you are satisfied by the preview changes in the previous step, apply them by entering the above command with the
perform=1argument:foreman-rake orchestration:dhcp:remove_offending subnet_name=NAME perform=1
# foreman-rake orchestration:dhcp:remove_offending subnet_name=NAME perform=1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
PXE loader option change
When the PXE loader option is changed for an existing host, this causes a DHCP conflict. The only workaround is to overwrite the DHCP entry.
Incorrect permissions on DHCP files
An operating system update can update the dhcpd package. This causes the permissions of important directories and files to reset so that the DHCP Capsule cannot read the required information.
For more information, see DHCP error while provisioning host from Satellite server Error ERF12-6899 ProxyAPI::ProxyException: Unable to set DHCP entry RestClient::ResourceNotFound 404 Resource Not Found on Red Hat Knowledgebase.
Changing the DHCP Capsule entry
Satellite manages DHCP records only for hosts that are assigned to subnets with a DHCP Capsule set. If you create a host and then clear or change the DHCP Capsule, when you attempt to delete the host, the action fails.
If you create a host without setting the DHCP Capsule and then try to set the DHCP Capsule, this causes DHCP conflicts.
Deleted hosts entries in the dhcpd.leases file
Any changes to a DHCP lease are appended to the end of the dhcpd.leases file. Because entries are appended to the file, it is possible that two or more entries of the same lease can exist in the dhcpd.leases file at the same time. When there are two or more entries of the same lease, the last entry in the file takes precedence. Group, subgroup and host declarations in the lease file are processed in the same manner. If a lease is deleted, { deleted; } is appended to the declaration.
3.6. Prerequisites for image-based provisioning
Post-boot configuration method
Images that use the finish post-boot configuration scripts require a managed DHCP server, for example, your Satellite Server or Capsule Servers. The host must be created with a subnet associated with a DHCP Capsule, and the IP address of the host must be a valid IP address from the DHCP range.
It is possible to use an external DHCP service, but IP addresses must be entered manually. The SSH credentials corresponding to the configuration in the image must be configured in Satellite to enable the post-boot configuration to be made.
Check the following items when troubleshooting a virtual machine booted from an image that depends on post-configuration scripts:
- The host has a subnet assigned in Satellite Server.
- The subnet has a DHCP Capsule assigned in Satellite Server.
- The host has a valid IP address assigned in Satellite Server.
- The IP address acquired by the virtual machine by using DHCP matches the address configured in Satellite Server.
- The virtual machine created from an image responds to SSH requests.
- The virtual machine created from an image authorizes the user and password, over SSH, which is associated with the image being deployed.
- Satellite Server has access to the virtual machine via SSH keys. This is required for the virtual machine to receive post-configuration scripts from Satellite Server.
Pre-boot initialization configuration method
Images that use the cloud-init scripts require a DHCP server to avoid having to include the IP address in the image. A managed DHCP Capsule is preferred. The image must have the cloud-init service configured to start when the system boots and fetch a script or configuration data to use in completing the configuration.
Check the following items when troubleshooting a virtual machine booted from an image that depends on initialization scripts included in the image:
- There is a DHCP server on the subnet.
-
The virtual machine has the
cloud-initservice installed and enabled.
For information about the differing levels of support for finish and cloud-init scripts in virtual-machine images, see the Red Hat Knowledgebase Solution What are the supported compute resources for the finish and cloud-init scripts on the Red Hat Customer Portal.
3.7. Configuring network services
Some provisioning methods use Capsule Server services. For example, a network might require Capsule Server to act as a DHCP server. A network can also use PXE boot services to install the operating system on new hosts. This requires configuring Capsule Server to use the main PXE boot services: DHCP, DNS, and TFTP.
Use the satellite-installer command with the options to configure these services on Satellite Server.
To configure these services on an external Capsule Server, run satellite-installer.
Procedure
Enter the
satellite-installercommand to configure the required network services:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Find Capsule Server that you configure:
hammer capsule list
# hammer capsule listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Refresh features of Capsule Server to view the changes:
hammer capsule refresh-features --name "satellite.example.com"
# hammer capsule refresh-features --name "satellite.example.com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the services configured on Capsule Server:
hammer capsule info --name "satellite.example.com"
# hammer capsule info --name "satellite.example.com"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.7.1. Multiple subnets or domains using installer
The satellite-installer options allow only for a single DHCP subnet or DNS domain. One way to define more than one subnet is by using a custom configuration file.
For every additional subnet or domain, create an entry in /etc/foreman-installer/custom-hiera.yaml file:
Execute satellite-installer to perform the changes and verify that the /etc/dhcp/dhcpd.conf contains appropriate entries. Subnets must be then defined in Satellite database.
3.7.2. DHCP options for network configuration
- --foreman-proxy-dhcp
-
Enables the DHCP service. You can set this option to
trueorfalse. - --foreman-proxy-dhcp-managed
-
Enables Foreman to manage the DHCP service. You can set this option to
trueorfalse. - --foreman-proxy-dhcp-gateway
- The DHCP pool gateway. Set this to the address of the external gateway for hosts on your private network.
- --foreman-proxy-dhcp-interface
-
Sets the interface for the DHCP service to listen for requests. Set this to
eth1. - --foreman-proxy-dhcp-nameservers
-
Sets the addresses of the nameservers provided to clients through DHCP. Set this to the address for Satellite Server on
eth1. - --foreman-proxy-dhcp-range
- A space-separated DHCP pool range for Discovered and Unmanaged services.
- --foreman-proxy-dhcp-server
- Sets the address of the DHCP server to manage.
Run satellite-installer --help to view more options related to DHCP and other Capsule services.
3.7.3. DNS options for network configuration
- --foreman-proxy-dns
-
Enables the DNS feature. You can set this option to
trueorfalse. - --foreman-proxy-dns-provider
- Selects the provider to be used.
- --foreman-proxy-dns-managed
-
Let the installer manage ISC BIND. This is only relevant when using the
nsupdateandnsupdate_gssproviders. You can set this option totrueorfalse. - --foreman-proxy-dns-forwarders
- Sets the DNS forwarders. Only used when ISC BIND is managed by the installer. Set this to your DNS recursors.
- --foreman-proxy-dns-interface
-
Sets the interface to listen for DNS requests. Only used when ISC BIND is managed by the installer. Set this to
eth1. - --foreman-proxy-dns-reverse
- The DNS reverse zone name. Only used when ISC BIND is managed by the installer.
- --foreman-proxy-dns-server
-
Sets the address of the DNS server. Only used by the
nsupdate,nsupdate_gss, andinfobloxproviders. - --foreman-proxy-dns-zone
- Sets the DNS zone name. Only used when ISC BIND is managed by the installer.
Run satellite-installer --help to view more options related to DNS and other Capsule services.
3.7.4. TFTP options for network configuration
- --foreman-proxy-tftp
-
Enables TFTP service. You can set this option to
trueorfalse. - --foreman-proxy-tftp-managed
-
Enables Foreman to manage the TFTP service. You can set this option to
trueorfalse. - --foreman-proxy-tftp-servername
- Sets the TFTP server to use. Ensure that you use Capsule’s IP address.
Run satellite-installer --help to view more options related to TFTP and other Capsule services.
3.7.5. Using TFTP services through NAT
You can use Satellite TFTP services through NAT. To do this, on all NAT routers or firewalls, you must enable a TFTP service on UDP port 69 and enable the TFTP state tracking feature. For more information, see the documentation for your NAT device.
Using NAT on Red Hat Enterprise Linux 7:
Allow the TFTP service in the firewall configuration:
firewall-cmd --add-service=tftp
# firewall-cmd --add-service=tftpCopy to Clipboard Copied! Toggle word wrap Toggle overflow Make the changes persistent:
firewall-cmd --runtime-to-permanent
# firewall-cmd --runtime-to-permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Using NAT on Red Hat Enterprise Linux 6:
Configure the firewall to allow TFTP service UDP on port 69:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Load the
ip_conntrack_tftpkernel TFTP state module. In the/etc/sysconfig/iptables-configfile, locateIPTABLES_MODULESand addip_conntrack_tftpas follows:IPTABLES_MODULES="ip_conntrack_tftp"
IPTABLES_MODULES="ip_conntrack_tftp"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.8. Adding a domain to Satellite Server
Satellite Server defines domain names for each host on the network. Satellite Server must have information about the domain and Capsule Server responsible for domain name assignment.
Checking for existing domains
Satellite Server might already have the relevant domain created as part of Satellite Server installation. Switch the context to Any Organization and Any Location then check the domain list to see if it exists.
DNS server configuration considerations
During the DNS record creation, Satellite performs conflict DNS lookups to verify that the host name is not in active use. This check runs against one of the following DNS servers:
- The system-wide resolver if Administer > Settings > Query local nameservers is set to true.
- The nameservers that are defined in the subnet associated with the host.
- The authoritative NS-Records that are queried from the SOA from the domain name associated with the host.
If you experience timeouts during DNS conflict resolution, check the following settings:
- The subnet nameservers must be reachable from Satellite Server.
- The domain name must have a Start of Authority (SOA) record available from Satellite Server.
-
The system resolver in the
/etc/resolv.conffile must have a valid and working configuration.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Domains and click Create Domain.
- In the DNS Domain field, enter the full DNS domain name.
- In the Fullname field, enter the plain text name of the domain.
- Click the Parameters tab and configure any domain level parameters to apply to hosts attached to this domain. For example, user defined Boolean or string parameters to use in templates.
- Click Add Parameter and fill in the Name and Value fields.
- Click the Locations tab, and add the location where the domain resides.
- Click the Organizations tab, and add the organization that the domain belongs to.
- Click Submit to save the changes.
CLI procedure
Use the
hammer domain createcommand to create a domain:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9. Adding a subnet to Satellite Server
You must add information for each of your subnets to Satellite Server because Satellite configures interfaces for new hosts. To configure interfaces, Satellite Server must have all the information about the network that connects these interfaces.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Subnets, and in the Subnets window, click Create Subnet.
- In the Name field, enter a name for the subnet.
- In the Description field, enter a description for the subnet.
- In the Network address field, enter the network address for the subnet.
- In the Network prefix field, enter the network prefix for the subnet.
- In the Network mask field, enter the network mask for the subnet.
- In the Gateway address field, enter the external gateway for the subnet.
- In the Primary DNS server field, enter a primary DNS for the subnet.
- In the Secondary DNS server, enter a secondary DNS for the subnet.
- From the IPAM list, select the method that you want to use for IP address management (IPAM). For more information about IPAM, see Section 3.3, “Network resources”.
- Enter the information for the IPAM method that you select. Click the Remote Execution tab and select the Capsule that controls the remote execution.
- Click the Domains tab and select the domains that apply to this subnet.
- Click the Capsules tab and select the Capsule that applies to each service in the subnet, including DHCP, TFTP, and reverse DNS services.
- Click the Parameters tab and configure any subnet level parameters to apply to hosts attached to this subnet. For example, user defined Boolean or string parameters to use in templates.
- Click the Locations tab and select the locations that use this Capsule.
- Click the Organizations tab and select the organizations that use this Capsule.
- Click Submit to save the subnet information.
CLI procedure
Create the subnet with the following command:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 4. Using PXE to provision hosts
You can provision bare-metal instances with Satellite by using one of the following methods:
- Unattended Provisioning
- New hosts are identified by a MAC address. Satellite Server provisions the host by using a PXE boot process.
- Unattended Provisioning with Discovery
- New hosts use PXE boot to load the Satellite Discovery service. This service identifies hardware information about the host and lists it as an available host to provision. For more information, see Chapter 6, Discovering hosts on a network.
- PXE-less Provisioning
- New hosts are provisioned with a boot disk image that Satellite Server generates.
BIOS and UEFI support
With Red Hat Satellite, you can perform both BIOS and UEFI based PXE provisioning. Both BIOS and UEFI interfaces work as interpreters between the operating system and firmware of a computer, initializing hardware components and starting the operating system at boot time.
PXE loaders
In Satellite provisioning, the PXE loader option defines the DHCP filename option to use during provisioning.
-
For BIOS systems, use the PXELinux BIOS option to enable a provisioned host to download the
pxelinux.0file over TFTP. -
For UEFI systems, use the PXEGrub2 UEFI option to enable a TFTP client to download
grub2/grubx64.efifile, or use the PXEGrub2 UEFI HTTP option to enable an UEFI HTTP client to downloadgrubx64.efifrom Capsule with the HTTP Boot feature.
For more information about supported workflows, see Supported architectures and provisioning scenarios.
Bonded network interfaces
You can configure a bonded interface that Satellite will use during the installation process, for example, to download installation content. After provisioning completes, the provisioned system can also use the bonded interface.
Satellite cannot PXE boot a bonded interface that requires configuration on a network switch as well as on your host.
After your host loads the kernel of an installer or the kernel of an operating system, bonding works as expected. Therefore, you can use a boot disk to work around PXE boot limitations when your bonded interface requires configuration on both a switch and your host.
4.1. Prerequisites for bare-metal provisioning
The requirements for bare-metal provisioning include:
A Capsule Server managing the network for bare-metal hosts. For unattended provisioning and discovery-based provisioning, Satellite Server requires PXE server settings.
For more information about networking requirements, see Chapter 3, Configuring networking.
For more information about the Discovery service, Chapter 6, Discovering hosts on a network.
- A bare-metal host or a blank VM.
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
For information about the security token for unattended and PXE-less provisioning, see Section 4.2, “Configuring the security token validity duration”.
4.2. Configuring the security token validity duration
When performing any kind of provisioning, as a security measure, Satellite automatically generates a unique token and adds this token to the kickstart URL in the PXE configuration file (PXELinux, Grub2). By default, the token is valid for 360 minutes. When you provision a host, ensure that you reboot the host within this time frame. If the token expires, it is no longer valid and you receive a 404 error and the operating system installer download fails.
Procedure
- In the Satellite web UI, navigate to Administer > Settings, and click the Provisioning tab.
-
Find the Token duration option and click the edit icon and edit the duration, or enter
0to disable token generation. If token generation is disabled, an attacker can spoof client IP address and download kickstart from Satellite Server, including the encrypted root password.
4.3. Creating hosts with unattended provisioning
Unattended provisioning is the simplest form of host provisioning. You enter the host details on Satellite Server and boot your host. Satellite Server automatically manages the PXE configuration, organizes networking services, and provides the operating system and configuration for the host.
This method of provisioning hosts uses minimal interaction during the process.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- In the MAC address field, enter a MAC address of the provisioning interface of the host. This ensures the identification of the host during the PXE boot process.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and verify that all fields contain values. Confirm each aspect of the operating system.
Optional: Click Resolve in Provisioning template to check the new host can identify the right provisioning templates to use.
For more information about associating provisioning templates, see Section 2.12, “Provisioning templates”.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. Click Submit to save the host details.
For more information about network interfaces, see Adding network interfaces in Managing hosts.
This creates the host entry and the relevant provisioning settings. This also includes creating the necessary directories and files for PXE booting the bare-metal host. If you start the physical host and set its boot mode to PXE, the host detects the DHCP service of Satellite Server’s integrated Capsule, receives HTTP endpoint of the Kickstart tree and installs the operating system.
When the installation completes, the host also registers to Satellite Server using the activation key and installs the necessary configuration and management tools from the Red Hat Satellite Client 6 repository.
CLI procedure
Create the host with the
hammer host createcommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure the network interface options are set using the
hammer host interface updatecommand:hammer host interface update \ --host "_My_Host_Name_" \ --managed true \ --primary true \ --provision true
# hammer host interface update \ --host "_My_Host_Name_" \ --managed true \ --primary true \ --provision trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.4. Creating hosts with PXE-less provisioning
Some hardware does not provide a PXE boot interface. In Satellite, you can provision a host without PXE boot. This is also known as PXE-less provisioning and involves generating a boot ISO that hosts can use. Using this ISO, the host can connect to Satellite Server, boot the installation media, and install the operating system.
Satellite also provides a PXE-less discovery service that operates without PXE-based services, such as DHCP and TFTP. For more information, see Section 6.4, “Discovery in PXE-less mode”.
Boot ISO types
There are the following types of boot ISOs:
- Full host image
- A boot ISO that contains the kernel and initial RAM disk image for the specific host. This image is useful if the host fails to chainload correctly. The provisioning template still downloads from Satellite Server.
- Subnet image
- A boot ISO that is not associated with a specific host. The ISO sends the host’s MAC address to Capsule Server, which matches it against the host entry. The image does not store IP address details and requires access to a DHCP server on the network to bootstrap. This image is generic to all hosts with a provisioning NIC on the same subnet. The image is based on iPXE boot firmware, only a limited number of network cards is supported.
The Full host image is based on SYSLINUX and Grub and works with most network cards. When using a Subnet image, see supported hardware on ipxe.org for a list of network card drivers expected to work with an iPXE-based boot disk.
Full host image contains a provisioning token, therefore the generated image has limited lifespan. For more information about configuring security tokens, read Section 4.2, “Configuring the security token validity duration”.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- In the MAC address field, enter a MAC address of the provisioning interface of the host. This ensures the identification of the host during the PXE boot process.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and verify that all fields contain values. Confirm each aspect of the operating system.
Click Resolve in Provisioning Templates to check the new host can identify the right provisioning templates to use.
For more information about associating provisioning templates, see Section 2.12, “Provisioning templates”.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save the host details. This creates a host entry and the host details page appears.
Download the boot disk from Satellite Server.
- For Full host image, on the host details page, click the vertical ellipsis and select Full host 'My_Host_Name' image.
- For Subnet image, navigate to Infrastructure > Subnets, click the dropdown menu in the Actions column of the required subnet and select Subnet generic image.
-
Write the ISO to a USB storage device using the
ddutility orlivecd-toolsif required. When you start the host and boot from the ISO or the USB storage device, the host connects to Satellite Server and starts installing operating system from its Kickstart tree.
When the installation completes, the host also registers to Satellite Server using the activation key and installs the necessary configuration and management tools from the Red Hat Satellite Client 6 repository.
CLI procedure
Create the host using the
hammer host createcommand.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your network interface options are set using the
hammer host interface updatecommand.hammer host interface update \ --host "My_Host_Name" \ --managed true \ --primary true \ --provision true
# hammer host interface update \ --host "My_Host_Name" \ --managed true \ --primary true \ --provision trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Download the boot disk from Satellite Server using the
hammer bootdiskcommand:For Full host image:
hammer bootdisk host \ --full true \ --host My_Host_Name
# hammer bootdisk host \ --full true \ --host My_Host_NameCopy to Clipboard Copied! Toggle word wrap Toggle overflow For Subnet image:
hammer bootdisk subnet --subnet My_Subnet_Name
# hammer bootdisk subnet --subnet My_Subnet_NameCopy to Clipboard Copied! Toggle word wrap Toggle overflow
This creates a boot ISO for your host to use.
-
Write the ISO to a USB storage device using the
ddutility orlivecd-toolsif required. When you start the physical host and boot from the ISO or the USB storage device, the host connects to Satellite Server and starts installing operating system from its Kickstart tree.
When the installation completes, the host also registers to Satellite Server using the activation key and installs the necessary configuration and management tools from the Red Hat Satellite Client 6 repository.
4.5. Creating hosts with UEFI HTTP boot provisioning
You can provision hosts from Satellite using the UEFI HTTP Boot. This is the only method with which you can provision hosts in IPv6 network.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Prerequisites
- Ensure that you meet the requirements for HTTP booting. For more information, see HTTP Booting Requirements in Overview, concepts, and deployment considerations.
Procedure
On Capsule that you use for provisioning, update the
grub2-efipackage to the latest version:satellite-maintain packages update grub2-efi
# satellite-maintain packages update grub2-efiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable
foreman-proxy-http,foreman-proxy-httpboot, andforeman-proxy-tftpfeatures.satellite-installer \ --foreman-proxy-http true \ --foreman-proxy-httpboot true \ --foreman-proxy-tftp true
# satellite-installer \ --foreman-proxy-http true \ --foreman-proxy-httpboot true \ --foreman-proxy-tftp trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Ensure that the Capsule has TFTP and HTTPBoot features recognized. In the Satellite web UI, navigate to Infrastructure > Capsules and click on Capsule to see the list of recognized features. Click Refresh Features if any of the features are missing.
- Ensure that Capsule is associated with the provisioning subnet. In the Satellite web UI, navigate to Infrastructure > Subnets > Edit Subnet > Capsules and select the Capsule for both TFTP and HTTPBoot options.
- Click OK to save.
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- In the MAC address field, enter a MAC address of the provisioning interface of the host. This ensures the identification of the host during the PXE boot process.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and verify that all fields contain values. Confirm each aspect of the operating system.
- From the PXE Loader list, select Grub2 UEFI HTTP.
Optional: Click Resolve in Provisioning template to check the new host can identify the right provisioning templates to use.
For more information about associating provisioning templates, see Section 2.14, “Creating provisioning templates”.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. Click Submit to save the host details.
For more information about network interfaces, see Adding network interfaces in Managing hosts.
- Set the host to boot in UEFI mode from network.
- Start the host.
- From the boot menu, select Kickstart default PXEGrub2.
This creates the host entry and the relevant provisioning settings. This also includes creating the necessary directories and files for UEFI booting the bare-metal host. When you start the physical host and set its boot mode to UEFI HTTP, the host detects the defined DHCP service, receives HTTP endpoint of Capsule with the Kickstart tree and installs the operating system.
When the installation completes, the host also registers to Satellite Server using the activation key and installs the necessary configuration and management tools from the Red Hat Satellite Client 6 repository.
CLI procedure
On Capsule that you use for provisioning, update the
grub2-efipackage to the latest version:satellite-maintain packages update grub2-efi
# satellite-maintain packages update grub2-efiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable
foreman-proxy-http,foreman-proxy-httpboot, andforeman-proxy-tftp truefeatures:satellite-installer \ --foreman-proxy-http true \ --foreman-proxy-httpboot true \ --foreman-proxy-tftp true
# satellite-installer \ --foreman-proxy-http true \ --foreman-proxy-httpboot true \ --foreman-proxy-tftp trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the host with the
hammer host createcommand.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure the network interface options are set using the
hammer host interface updatecommand:hammer host interface update \ --host "My_Host_Name" \ --managed true \ --primary true \ --provision true
# hammer host interface update \ --host "My_Host_Name" \ --managed true \ --primary true \ --provision trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Set the host to boot in UEFI mode from network.
- Start the host.
- From the boot menu, select Kickstart default PXEGrub2.
This creates the host entry and the relevant provisioning settings. This also includes creating the necessary directories and files for UEFI booting the bare-metal host. When you start the physical host and set its boot mode to UEFI HTTP, the host detects the defined DHCP service, receives HTTP endpoint of Capsule with the Kickstart tree and installs the operating system.
When the installation completes, the host also registers to Satellite Server using the activation key and installs the necessary configuration and management tools from the Red Hat Satellite Client 6 repository.
4.6. Deploying SSH keys during provisioning
Use this procedure to deploy SSH keys added to a user during provisioning. For information on adding SSH keys to a user, see Managing SSH Keys for a User in Administering Red Hat Satellite.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
- Create a provisioning template, or clone and edit an existing template. For more information, see Section 2.14, “Creating provisioning templates”.
- In the template, click the Template tab.
In the Template editor field, add the
create_userssnippet to the%postsection:<%= snippet('create_users') %><%= snippet('create_users') %>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Select the Default checkbox.
- Click the Association tab.
- From the Application Operating Systems list, select an operating system.
- Click Submit to save the provisioning template.
Create a host that is associated with the provisioning template or rebuild a host using the operating system associated with the modified template. For more information, see Creating a Host in Managing hosts.
The SSH keys of the Owned by user are added automatically when the
create_userssnippet is executed during the provisioning process. You can set Owned by to an individual user or a user group. If you set Owned by to a user group, the SSH keys of all users in the user group are added automatically.
Chapter 5. Using iPXE to reduce provisioning times
iPXE is an open-source network-boot firmware. It provides a full PXE implementation enhanced with additional features, such as booting from an HTTP server. For more information about iPXE, see iPXE website.
You can use iPXE if the following restrictions prevent you from using PXE:
- A network with unmanaged DHCP servers.
- A PXE service that is unreachable because of, for example, a firewall restriction.
- A TFTP UDP-based protocol that is unreliable because of, for example, a low-bandwidth network.
5.1. Prerequisites for using iPXE
You can use iPXE to boot virtual machines in the following cases:
- Your virtual machines run on a hypervisor that uses iPXE as primary firmware.
- Your virtual machines are in BIOS mode. In this case, you can configure PXELinux to chainboot iPXE and boot by using the HTTP protocol.
For booting virtual machines in UEFI mode by using HTTP, you can follow Section 4.5, “Creating hosts with UEFI HTTP boot provisioning” instead.
Supportability
Red Hat does not officially support iPXE in Red Hat Satellite. For more information, see Supported architectures and kickstart scenarios in Satellite 6 in the Red Hat Knowledgebase.
Host requirements
- The MAC address of the provisioning interface matches the host configuration.
- The provisioning interface of the host has a valid DHCP reservation.
- The NIC is capable of PXE booting. For more information, see supported hardware on ipxe.org for a list of hardware drivers expected to work with an iPXE-based boot disk.
- The NIC is compatible with iPXE.
5.2. Configuring iPXE environment
Configure an iPXE environment on all Capsules that you want to use for iPXE provisioning.
In Red Hat Enterprise Linux, security-related features of iPXE are not supported and the iPXE binary is built without security features. For this reason, you can only use HTTP but not HTTPS. For more information, see Red Hat Enterprise Linux HTTPS support in iPXE.
Prerequisites
If you want to use Capsule Servers instead of your Satellite Server, ensure that you have configured your Capsule Servers accordingly.
ImportantIt is essential to add your Capsule Server to the list of trusted proxies on Satellite Server!
For more information, see Configuring Capsule for Host Registration and Provisioning in Installing Capsule Server.
Procedure
Enable the TFTP and HTTPboot services on your Capsule:
satellite-installer \ --foreman-proxy-httpboot true \ --foreman-proxy-tftp true
# satellite-installer \ --foreman-proxy-httpboot true \ --foreman-proxy-tftp trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the
ipxe-bootimgspackage on your Capsule:satellite-maintain packages install ipxe-bootimgs
# satellite-maintain packages install ipxe-bootimgsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy iPXE firmware to the TFTP directory.
Copy the iPXE firmware with the Linux kernel header:
cp /usr/share/ipxe/ipxe.lkrn /var/lib/tftpboot/
# cp /usr/share/ipxe/ipxe.lkrn /var/lib/tftpboot/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy the UNDI iPXE firmware:
cp /usr/share/ipxe/undionly.kpxe /var/lib/tftpboot/undionly-ipxe.0
# cp /usr/share/ipxe/undionly.kpxe /var/lib/tftpboot/undionly-ipxe.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Correct the SELinux file contexts:
restorecon -RvF /var/lib/tftpboot/
# restorecon -RvF /var/lib/tftpboot/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the HTTP URL.
If you want to use Satellite Server for booting, run the following command on Satellite Server:
satellite-installer \ --foreman-proxy-dhcp-ipxefilename "http://satellite.example.com/unattended/iPXE?bootstrap=1"
# satellite-installer \ --foreman-proxy-dhcp-ipxefilename "http://satellite.example.com/unattended/iPXE?bootstrap=1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you want to use Capsule Server for booting, run the following command on Capsule Server:
satellite-installer --foreman-proxy-dhcp-ipxe-bootstrap true
# satellite-installer --foreman-proxy-dhcp-ipxe-bootstrap trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3. Booting virtual machines
Some virtualization hypervisors use iPXE as primary firmware for PXE booting. If you use such a hypervisor, you can boot virtual machines without TFTP and PXELinux.
Booting a virtual machine has the following workflow:
- Virtual machine starts.
- iPXE retrieves the network credentials, including an HTTP URL, by using DHCP.
- iPXE loads the iPXE bootstrap template from Capsule.
- iPXE loads the iPXE template with MAC as a URL parameter from Capsule.
- iPXE loads the kernel and initial RAM disk of the installer.
Prerequisites
Your hypervisor must support iPXE. The following virtualization hypervisors support iPXE:
- libvirt
- Red Hat Virtualization (deprecated)
- You have configured your iPXE environment. For more information, see Section 5.2, “Configuring iPXE environment”.
You can use the original templates shipped in Satellite as described below. If you require modification to an original template, clone the template, edit the clone, and associate the clone instead of the original template. For more information, see Section 2.15, “Cloning provisioning templates”.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
-
Search for the
Kickstart default iPXEtemplate. - Click the name of the template.
- Click the Association tab and select the operating systems that your host uses.
- Click the Locations tab and add the location where the host resides.
- Click the Organizations tab and add the organization that the host belongs to.
- Click Submit to save the changes.
- In the Satellite web UI, navigate to Hosts > Operating systems and select the operating system of your host.
- Click the Templates tab.
-
From the iPXE template list, select the
Kickstart default iPXEtemplate. - Click Submit to save the changes.
- In the Satellite web UI, navigate to Hosts > All Hosts.
- In the Hosts page, select the host that you want to use.
- Select the Operating System tab.
-
Set PXE Loader to
iPXE Embedded. - Select the Templates tab.
- In Provisioning Templates, click Resolve and verify that the iPXE template resolves to the required template.
- Click Submit to save host settings.
5.4. Chainbooting iPXE from PXELinux
You can set up iPXE to use a built-in driver for network communication (ipxe.lkrn) or Universal Network Device Interface (UNDI) (undionly-ipxe.0). You can choose to load either file depending on the networking hardware capabilities and iPXE driver availability.
UNDI is a minimalistic UDP/IP stack that implements TFTP client. However, UNDI cannot support other protocols like HTTP. To use HTTP with iPXE, use the iPXE build with built-in drivers (ipxe.lkrn).
Chainbooting iPXE has the following workflow:
- Host powers on.
- PXE driver retrieves the network credentials by using DHCP.
-
PXE driver retrieves the PXELinux firmware
pxelinux.0by using TFTP. - PXELinux searches for the configuration file on the TFTP server.
-
PXELinux chainloads iPXE
ipxe.lkrnorundionly-ipxe.0. - iPXE retrieves the network credentials, including an HTTP URL, by using DHCP again.
- iPXE chainloads the iPXE template from your Templates Capsule.
- iPXE loads the kernel and initial RAM disk of the installer.
Prerequisites
- You have configured your iPXE environment. For more information, see Section 5.2, “Configuring iPXE environment”.
You can use the original templates shipped in Satellite as described below. If you require modification to an original template, clone the template, edit the clone, and associate the clone instead of the original template. For more information, see Section 2.15, “Cloning provisioning templates”.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
Search for the required PXELinux template:
-
PXELinux chain iPXEto useipxe.lkrn -
PXELinux chain iPXE UNDIto useundionly-ipxe.0
-
- Click the name of the template you want to use.
- Click the Association tab and select the operating systems that your host uses.
- Click the Locations tab and add the location where the host resides.
- Click the Organizations tab and add the organization that the host belongs to.
- Click Submit to save the changes.
-
On the Provisioning Templates page, search for the
Kickstart default iPXEtemplate. - Click the name of the template.
- Click the Association tab and associate the template with the operating system that your host uses.
- Click the Locations tab and add the location where the host resides.
- Click the Organizations tab and add the organization that the host belongs to.
- Click Submit to save the changes.
- In the Satellite web UI, navigate to Hosts > Operating systems and select the operating system of your host.
- Click the Templates tab.
- From the PXELinux template list, select the template you want to use.
-
From the iPXE template list, select the
Kickstart default iPXEtemplate. - Click Submit to save the changes.
- In the Satellite web UI, navigate to Configure > Host Groups, and select the host group you want to configure.
- Select the Operating System tab.
- Select the Architecture and Operating system.
Set the PXE Loader:
-
Select
PXELinux BIOSto chainboot iPXE (ipxe.lkrn) from PXELinux. -
Select
iPXE Chain BIOSto loadundionly-ipxe.0directly.
-
Select
Chapter 6. Discovering hosts on a network
Red Hat Satellite can detect hosts on a network that are not in your Satellite inventory. These hosts boot the Discovery image that performs hardware detection and relays this information back to Satellite Server. This method creates a list of ready-to-provision hosts in Satellite Server without needing to enter the MAC address of each host.
6.1. Prerequisites for using Discovery
Ensure that the DHCP range of all subnets that you plan to use for Discovery does not overlap with the DHCP lease pool configured for the managed DHCP service. The DHCP range is set in the Satellite web UI, whereas the lease pool range is set by using the
satellite-installercommand.For example, in the 10.1.0.0/16 network range, you can allocate the following IP address blocks:
- 10.1.0.0 to 10.1.127.255 for leases.
- 10.1.128.0 to 10.1.255.254 for reservations.
- Ensure the host or virtual machine being discovered has at least 1200 MB of memory. Insufficient memory can cause various random kernel panic errors because the Discovery image is extracted in memory.
6.2. Installing the Discovery service
The Discovery service is enabled by default on Satellite Server. Additionally, you can enable the Discovery service on any Capsule Servers that provide the TFTP service.
The Discovery service requires a Discovery image, which is provided with Red Hat Satellite. The Discovery image uses a minimal operating system that is booted on hosts to acquire initial hardware information and check in with Satellite.
The Foreman Discovery image provided with Satellite is based on Red Hat Enterprise Linux 8.
Procedure
Install
foreman-discovery-imageon Satellite Server:satellite-maintain packages install foreman-discovery-image
# satellite-maintain packages install foreman-discovery-imageCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
foreman-discovery-imagepackage installs the Discovery ISO to the/usr/share/foreman-discovery-image/directory. The package also extracts the PXE boot image to the/var/lib/tftpboot/boot/fdi-imagedirectory.If you want to use Capsule Server, install the Discovery plugin on Capsule Server:
satellite-installer \ --enable-foreman-proxy-plugin-discovery
# satellite-installer \ --enable-foreman-proxy-plugin-discoveryCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you want to use Capsule Server, install
foreman-discovery-imageon Capsule Server:satellite-maintain packages install foreman-discovery-image
# satellite-maintain packages install foreman-discovery-imageCopy to Clipboard Copied! Toggle word wrap Toggle overflow The package also extracts the PXE boot image to the
/var/lib/tftpboot/boot/fdi-imagedirectory.Configure the Discovery Capsule for the subnet with discoverable hosts:
- In the Satellite web UI, navigate to Infrastructure > Subnets.
- Select a subnet.
- On the Capsules tab, select the Discovery Capsule that you want to use.
Perform this for each subnet that you want to use.
6.3. Discovery in PXE mode
Satellite provides a PXE-based Discovery service that uses DHCP and TFTP services. You discover unknown nodes by booting them into the Discovery kernel and initial RAM disk images from Satellite Server or Capsule Server. When a discovered node is scheduled for installation, it reboots and continues with the configured PXE-based host provisioning.
Figure 6.1. Discovery workflow in PXE mode
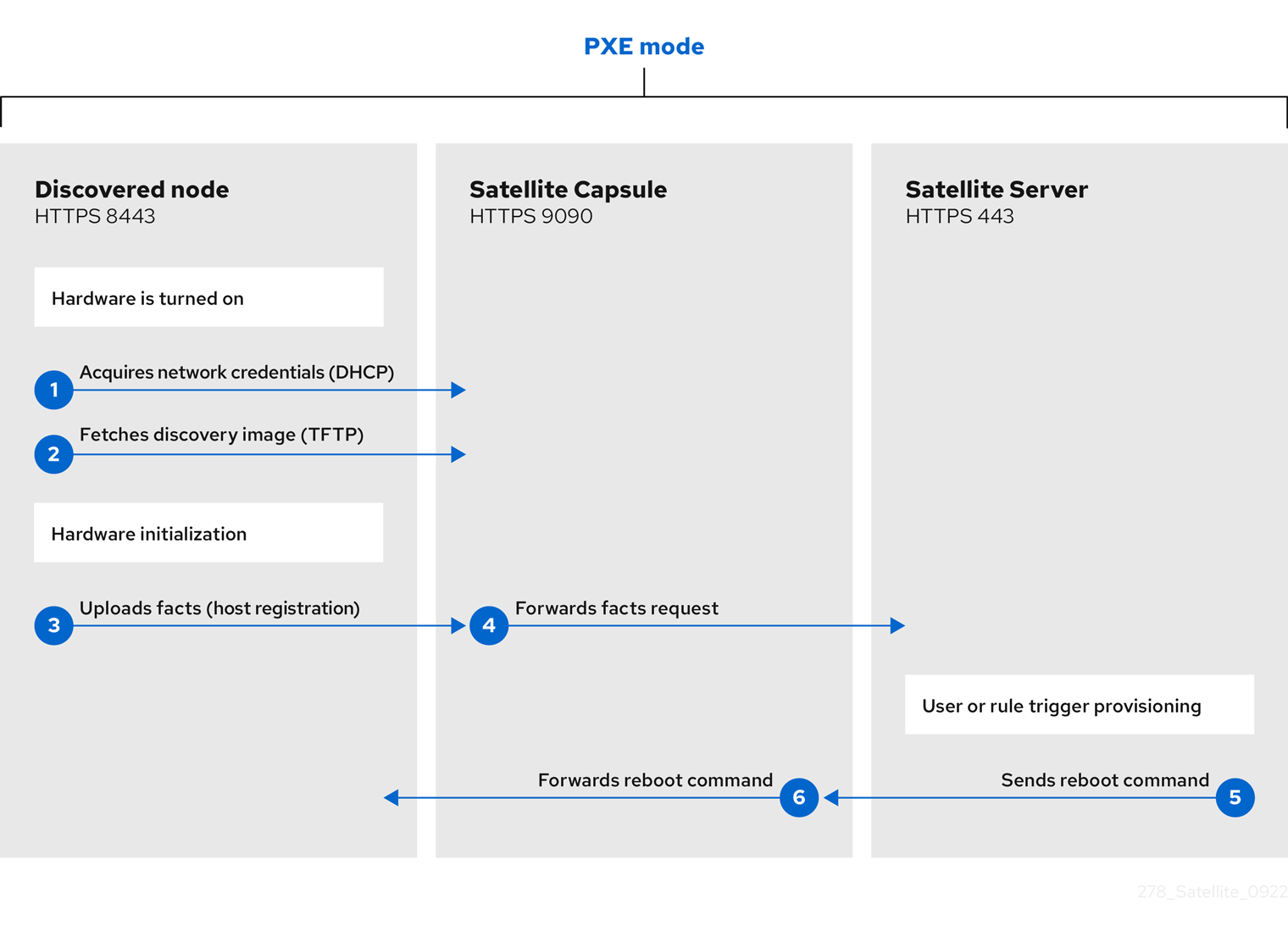
6.3.1. Setting Discovery as the default PXE boot option
Set the Discovery service as the default service that boots for hosts that are not present in your current Satellite inventory.
When you start an unknown host in PXE mode, Satellite Server or Capsule Server provides a boot menu with a default boot option. The boot menu has two basic options: local and discovery. The default setting of the global PXE templates is to select local to boot the host from the local hard drive. Change the setting to select discovery to boot from the Discovery image.
Prerequisites
-
Your Satellite account has the
view_settings,edit_settings, andview_provisioning_templatespermissions.
Procedure
- In the Satellite web UI, navigate to Administer > Settings.
-
On the Provisioning tab, enter
discoveryin the Default PXE global template entry field. - Navigate to Hosts > Templates > Provisioning Templates.
Click Build PXE Default.
The boot menus are built as the following files:
-
/var/lib/tftpboot/pxelinux.cfg/default -
/var/lib/tftpboot/grub2/grub.cfg
Satellite propagates the default boot menus to all TFTP Capsules.
-
6.3.2. Performing Discovery in PXE mode
Discovery in PXE mode uses the Discovery PXE boot images and runs unattended.
Prerequisites
- You have installed the Discovery service and image. For more information, see Section 6.2, “Installing the Discovery service”.
- You have set Discovery as the default booting option. For more information, see Section 6.3.1, “Setting Discovery as the default PXE boot option”.
Procedure
- Power on or reboot your host. After a few minutes, the Discovery image completes booting and the host displays a status screen.
Verification
- Satellite web UI displays a notification about a new discovered host.
Next steps
- In the Satellite web UI, navigate to Hosts > Discovered Hosts and view the newly discovered host. For more information about provisioning discovered hosts, see Section 6.6, “Creating hosts from discovered hosts”.
6.3.3. Customizing the Discovery PXE boot
Satellite builds PXE boot menus from the following global provisioning templates:
-
PXELinux global defaultfor BIOS provisioning. -
PXEGrub global defaultandPXEGrub2 global defaultfor UEFI provisioning.
The PXE boot menus are available on Satellite Server and Capsules that have TFTP enabled.
The Discovery menu item uses a Linux kernel for the operating system and passes kernel parameters to configure the Discovery service. You can customize the passed kernel parameters by changing the following snippets:
pxelinux_discovery: This snippet is included in thePXELinux global defaulttemplate.This snippet renders the Discovery boot menu option. The
KERNELandAPPENDoptions boot the Discovery kernel and initial RAM disk. TheAPPENDoption contains kernel parameters.-
pxegrub_discovery: This snippet is included in thePXEGrub global defaulttemplate. However, Discovery is not implemented for GRUB 1.x. pxegrub2_discovery: This snippet is included in thePXEGrub2 global defaulttemplate.This snippet renders the Discovery GRUB2 menu entry. The
commonvariable contains kernel parameters.
For information about the kernel parameters, see Section 6.9, “Kernel parameters for Discovery customization”.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
- Clone and edit the snippet you want to customize. For more information, see Section 2.15, “Cloning provisioning templates”.
- Clone and edit the template that contains the original snippet. Include your custom snippet instead of the original snippet. For more information, see Section 2.15, “Cloning provisioning templates”.
- Navigate to Administer > Settings.
- Click the Provisioning tab.
- In the appropriate Global default PXE\ template* setting, select your custom template.
- Navigate to Hosts > Templates > Provisioning Templates.
- Click Build PXE Default. This refreshes the default PXE boot menus on Satellite Server and any TFTP Capsules.
6.3.4. Discovering hosts from multiple Capsule Servers
Satellite deploys the same template to all TFTP Capsules and there is no variable or macro available to render the host name of Capsule. The hard-coded proxy.url does not work with two or more TFTP Capsules.
As a workaround, every time you click Build PXE Defaults, edit the configuration file in the TFTP directory on all Capsule Servers by using SSH, or use a common DNS alias for appropriate subnets. To use Capsule Server to proxy the Discovery steps, edit /var/lib/tftpboot/pxelinux.cfg/default or /var/lib/tftpboot/grub2/grub.cfg, and change the URL to the Capsule Server FQDN you want to use.
6.4. Discovery in PXE-less mode
Satellite provides a PXE-less Discovery service for environments without DHCP and TFTP services. You discover unknown nodes by using the Discovery ISO from Satellite Server. When a discovered node is scheduled for installation, the kexec command reloads a Linux kernel with an operating system installer without rebooting the node.
Discovery kexec is a Technology Preview feature only.
Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process. For more information, see Technology Preview Features – Scope of Support.
Known issues
- The console might freeze during the process.
- On some hardware, you might experience graphical hardware problems.
Figure 6.2. Discovery workflow in PXE-less mode
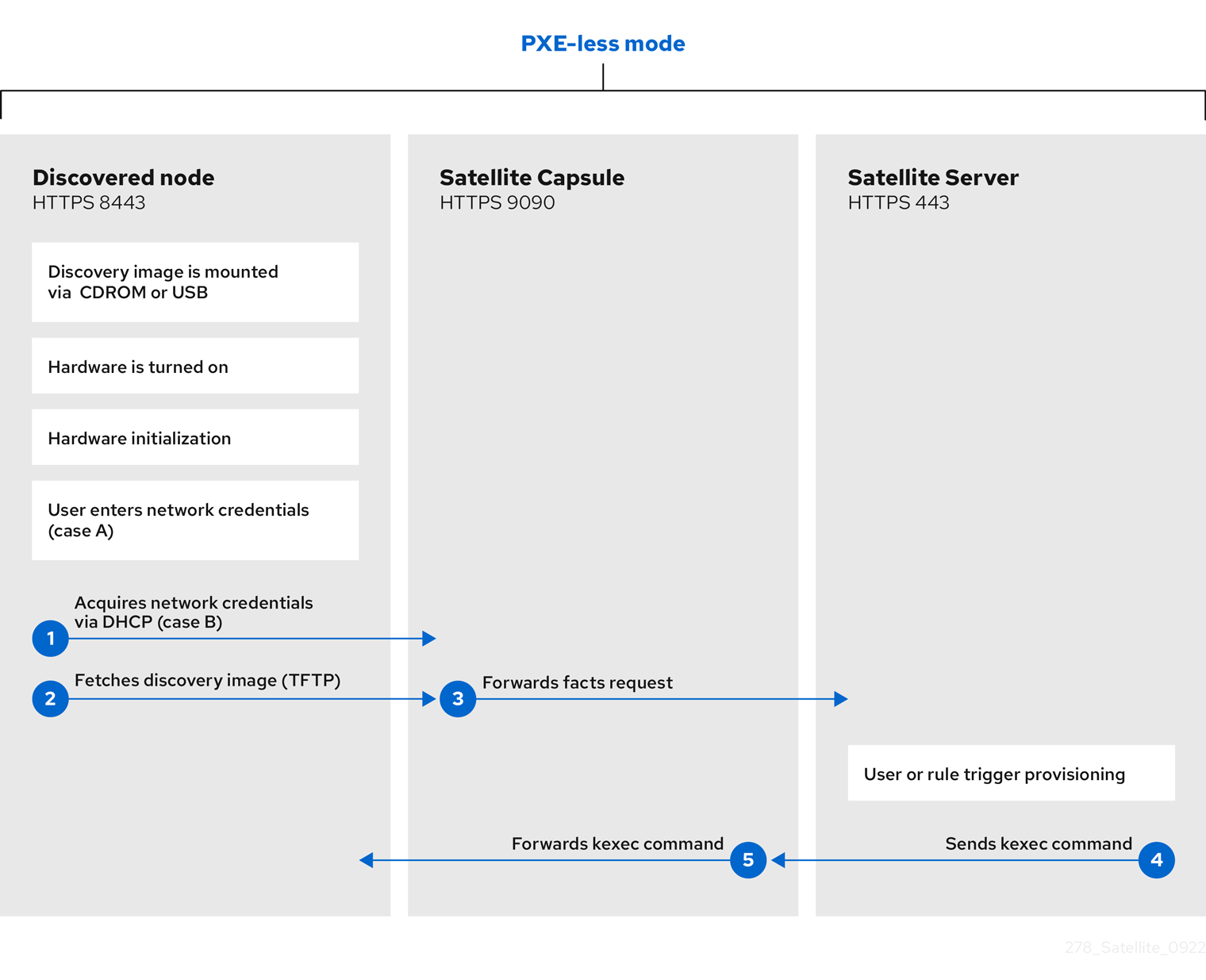
6.4.1. Performing Discovery in PXE-less mode
Discovery in PXE-less mode uses the Discovery ISO and requires you to attend to the process.
Prerequisites
- You have installed the Foreman Discovery image. For more information, see Section 6.2, “Installing the Discovery service”.
Procedure
Copy the Discovery ISO to a CD, DVD, or a USB flash drive. For example, to copy to a USB drive at
/dev/sdb:dd bs=4M \ if=/usr/share/foreman-discovery-image/foreman-discovery-image-version.iso \ of=/dev/sdb
# dd bs=4M \ if=/usr/share/foreman-discovery-image/foreman-discovery-image-version.iso \ of=/dev/sdbCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Insert the Discovery boot media into a host, start the host, and boot from the media.
The Discovery image displays options for either Manual network setup or Discovery with DHCP:
Manual network setup:
- On the Primary interface screen, select the primary network interface that connects to Satellite Server or Capsule Server. Optionally, enter a VLAN ID. Hit Select to continue.
- On the Network configuration screen, enter the Address, Gateway, and DNS. Hit Next to continue.
Discovery with DHCP:
- On the Primary interface screen, select the primary network interface that connects to Satellite Server or Capsule Server. Optionally, enter a VLAN ID. Hit Select to continue.
- The Discovery image attempts to automatically configure the network interface by using a DHCP server, such as one that a Capsule Server provides.
On the Credentials screen, enter the following options:
- In the Server URL field, enter the URL of Satellite Server or Discovery Capsule Server. If you refer to a Capsule Server, include the Capsule port number.
-
In the Connection type field, select the connection type:
Serverfor Satellite Server orForeman Proxyfor Capsule Server.
Hit Next to continue.
- Optional: On the Custom facts screen, enter custom facts for the Facter tool to relay back to Satellite Server. Enter a name and value for each custom fact you need.
- Hit Confirm to proceed.
Verification
- Satellite web UI displays a notification about a new discovered host.
Next steps
- In the Satellite web UI, navigate to Hosts > Discovered Hosts and view the newly discovered host. For more information about provisioning discovered hosts, see Section 6.6, “Creating hosts from discovered hosts”.
6.4.2. Customizing the Discovery ISO
You can create a customized Discovery ISO to automate the image configuration process after booting. The Discovery image uses a Linux kernel for the operating system, which passes kernel parameters to configure the Discovery service.
Satellite Server provides the discovery-remaster tool in the foreman-discovery-image package. By using this tool, remaster the image to include custom kernel parameters.
Procedure
Run the
discovery-remastertool. Enter the kernel parameters as a single string. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about kernel parameters, see Section 6.9, “Kernel parameters for Discovery customization”.
Copy the new ISO to either a CD, DVD, or a USB stick. For example, to copy to a USB stick at
/dev/sdb:dd bs=4M \ if=/usr/share/foreman-discovery-image/foreman-discovery-image-version.iso \ of=/dev/sdb
# dd bs=4M \ if=/usr/share/foreman-discovery-image/foreman-discovery-image-version.iso \ of=/dev/sdbCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5. Automatic contexts for discovered hosts
Satellite Server assigns an organization and location to discovered hosts automatically according to the following sequence of rules:
- If a discovered host uses a subnet defined in Satellite, the host uses the first organization and location associated with the subnet.
- If the default location and organization is configured in global settings, the discovered hosts are placed in this organization and location. To configure these settings, navigate to Administer > Settings > Discovery and select values for the Discovery organization and Discovery location settings. Ensure that the subnet of discovered host also belongs to the selected organization and location, otherwise Satellite refuses to set it for security reasons.
- If none of the previous conditions is met, Satellite assigns the first organization and location ordered by name.
You can change the organization or location manually by using the bulk actions on the Discovered Hosts page. Select the discovered hosts to modify and, from the Select Action menu, select Assign Organization or Assign Location.
6.6. Creating hosts from discovered hosts
Provisioning discovered hosts follows a provisioning process that is similar to PXE provisioning. The main difference is that instead of manually entering the host’s MAC address, you can select the host to provision from the list of discovered hosts.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Prerequisites
- Configure a domain and subnet on Satellite. For more information about networking requirements, see Chapter 3, Configuring networking.
- You have one or more discovered hosts in your Satellite inventory.
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
-
You have associated a
Discovery kexec-kind template andprovisioning-kind template with the operating system. For more information, see Section 2.18, “Associating templates with operating systems”.
For information about the security tokens, see Section 4.2, “Configuring the security token validity duration”.
Procedure
- In the Satellite web UI, navigate to Hosts > Discovered hosts.
- Select the host you want to provision and click Provision to the right of the list.
Select one of the following options:
- To provision a host from a host group, select a host group, organization, and location, and then click Create Host.
- To provision a host with further customization, click Customize Host and enter the additional details you want to specify for the new host.
Verify that the fields are populated with values. Note in particular:
- The Name from the Host tab becomes the DNS name.
- Satellite Server automatically assigns an IP address for the new host.
- Satellite Server automatically populates the MAC address from the Discovery results.
- Ensure that Satellite Server automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click the Operating System tab, and verify that all fields contain values. Confirm each aspect of the operating system.
In Provisioning templates, click Resolve to check if the new host can identify the correct provisioning templates. The host must resolve to the following provisioning templates:
-
Discovery kexec:
Discovery Red Hat kexec -
Provisioning template:
Kickstart default
-
Discovery kexec:
- Click Submit to save the host details.
When the host provisioning is complete, the discovered host moves to Hosts > All Hosts.
CLI procedure
Identify the discovered host to provision:
hammer discovery list
# hammer discovery listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Select the host and provision it by using a host group. Set a new host name with the
--new-nameoption:Copy to Clipboard Copied! Toggle word wrap Toggle overflow This removes the host from the discovered host listing and creates a host entry with the provisioning settings. The Discovery image automatically reboots the host to PXE or initiates kernel execution. The host detects the DHCP service and starts installing the operating system. The rest of the process is identical to the normal PXE workflow described in Section 4.3, “Creating hosts with unattended provisioning”.
6.7. Creating Discovery rules
As a method of automating the provisioning process for discovered hosts, Satellite provides a feature to create Discovery rules. These rules define how discovered hosts automatically provision themselves, based on the assigned host group. For example, you can automatically provision hosts with a high CPU count as hypervisors. Likewise, you can provision hosts with large hard disks as storage servers.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
NIC considerations
Auto provisioning does not currently allow configuring network interface cards (NICs). All systems are being provisioned with the NIC configuration that was detected during discovery. However, you can set the NIC in the kickstart scriptlet, by using a script, or by using configuration management at a later stage.
Procedure
- In the Satellite web UI, navigate to Configure > Discovery rules, and select Create Rule.
- In the Name field, enter a name for the rule.
-
In the Search field, enter the rules to determine whether to provision a host. This field provides suggestions for values you enter and allows operators for multiple rules. For example:
cpu_count > 8. - From the Host Group list, select the host group to use as a template for this host.
In the Hostname field, enter the pattern to determine host names for multiple hosts. This uses the same ERB syntax that provisioning templates use. The host name can use the
@hostattribute for host-specific values and therandmacro for a random number or thesequence_hostgroup_param_nextmacro for incrementing the value. For more information about provisioning templates, see Section 2.12, “Provisioning templates” and the API documentation.-
myhost-<%= sequence_hostgroup_param_next("EL7/MyHostgroup", 10, "discovery_host") %> -
myhost-<%= rand(99999) %> -
abc-<%= @host.facts['bios_vendor'] %>-<%= rand(99999) %> -
xyz-<%= @host.hostgroup.name %> -
srv-<%= @host.discovery_rule.name %> server-<%= @host.ip.gsub('.','-') + '-' + @host.hostgroup.subnet.name %>When creating host name patterns, ensure that the resulting host names are unique, do not start with numbers, and do not contain underscores or dots. A good approach is to use unique information provided by Facter, such as the MAC address, BIOS, or serial ID.
-
-
In the Hosts limit field, enter the maximum number of hosts that you can provision with the rule. Enter
0for unlimited. - In the Priority field, enter a number to set the precedence the rule has over other rules. Rules with lower values have a higher priority.
- From the Enabled list, select whether you want to enable the rule.
- To set a different provisioning context for the rule, click the Organizations and Locations tabs and select the contexts you want to use.
- Click Submit to save your rule.
In the Satellite web UI, navigate to Hosts > Discovered Host and select one of the following two options:
- From the Discovered hosts list on the right, select Auto-Provision to automatically provisions a single host.
- On the upper right of the window, click Auto-Provision All to automatically provisions all hosts.
CLI procedure
Create the rule by using Hammer:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Automatically provision a host with the
hammer discovery auto-provisioncommand:hammer discovery auto-provision --name "macabcdef123456"
# hammer discovery auto-provision --name "macabcdef123456"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.8. Extending the Discovery image
You can extend the Satellite Discovery image with custom facts, software, or device drivers. You can also provide a compressed archive file containing extra code for the image to use.
Procedure
Create the following directory structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The
autostart.ddirectory contains scripts that are executed in POSIX order by the Discovery kernel when it starts but before the host is registered to Satellite. -
The
bindirectory is added to the$PATHvariable; you can place binary files in this directory and use them in theautostartscripts. -
The
factsdirectory is added to theFACTERLIBvariable so that custom facts can be configured and sent to Satellite. -
The
libdirectory is added to theLD_LIBRARY_PATHvariable andlib/rubyis added to theRUBYLIBvariable, so that binary files in/bincan be executed correctly.
-
The
After creating the directory structure, create a
.zipfile archive with the following command:zip -r my_extension.zip .
# zip -r my_extension.zip .Copy to Clipboard Copied! Toggle word wrap Toggle overflow Inform the Discovery kernel of the extensions it must use. Place your zip files on your TFTP server with the Discovery image and customize the Discovery PXE boot with the
fdi.zipsparameter where the paths are relative to the TFTP root.For example, if you have two archives at
$TFTP/zip1.zipand$TFTP/boot/zip2.zip, use the following syntax:fdi.zips=zip1.zip,boot/zip2.zip
fdi.zips=zip1.zip,boot/zip2.zipCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information, see Section 6.3.3, “Customizing the Discovery PXE boot”.
You can append new directives and options to the existing environment variables (PATH, LD_LIBRARY_PATH, RUBYLIB and FACTERLIB). If you want to specify the path explicitly in your scripts, the .zip file contents are extracted to the /opt/extension directory on the image.
You can create multiple .zip files but be aware that they are extracted to the same location on the Discovery image. Files extracted from in later .zip files overwrite earlier versions if they contain the same file name.
6.9. Kernel parameters for Discovery customization
Discovery uses a Linux kernel for the operating system and passes kernel parameters to configure the Discovery service. These kernel parameters include the following entries:
- fdi.cachefacts
- Number of fact uploads without caching. By default, Satellite does not cache any uploaded facts.
- fdi.countdown
-
Number of seconds to wait until the text-user interface is refreshed after the initial discovery attempt. This value defaults to 45 seconds. Increase this value if the status page reports the IP address as
N/A. - fdi.dhcp_timeout
- NetworkManager DHCP timeout. The default value is 300 seconds.
- fdi.dns_nameserver
- Nameserver to use for DNS SRV record.
- fdi.dns_ndots
-
ndotsoption to use for DNS SRV record. - fdi.dns_search
- Search domain to use for DNS SRV record.
- fdi.initnet
-
By default, the image initializes all network interfaces (value
all). When this setting is set tobootif, only the network interface it was network-booted from will be initialized. - fdi.ipv4.method
-
By default, NetworkManager IPv4 method setting is set to
auto. This option overrides it, set it toignoreto disable the IPv4 stack. This option works only in DHCP mode. - fdi.ipv6.method
-
By default, NetworkManager IPv6 method setting is set to
auto. This option overrides it, set it toignoreto disable the IPv6 stack. This option only works in DHCP mode. - fdi.ipwait
- Duration in seconds to wait for IP to be available in HTTP proxy SSL cert start. By default, Satellite waits for 120 seconds.
- fdi.nmwait
-
nmcli -waitoption for NetworkManager. By default,nmcliwaits for 120 seconds. - fdi.proxy_cert_days
- Number of days the self-signed HTTPS cert is valid for. By default, the certificate is valid for 999 days.
- fdi.pxauto
- To set automatic or semi-automatic mode. If set to 0, the image uses semi-automatic mode, which allows you to confirm your choices through a set of dialog options. If set to 1, the image uses automatic mode and proceeds without any confirmation.
- fdi.pxfactname1, fdi.pxfactname2 … fdi.pxfactnameN
- Use to specify custom fact names.
- fdi.pxfactvalue1, fdi.pxfactvalue2 … fdi.pxfactvalueN
-
The values for each custom fact. Each value corresponds to a fact name. For example,
fdi.pxfactvalue1sets the value for the fact named withfdi.pxfactname1. - fdi.pxip, fdi.pxgw, fdi.pxdns
-
Manually configures IP address (
fdi.pxip), the gateway (fdi.pxgw), and the DNS (fdi.pxdns) for the primary network interface. If you omit these parameters, the image uses DHCP to configure the network interface. You can add multiple DNS entries in a comma-separated [1] list, for examplefdi.pxdns=192.168.1.1,192.168.200.1. - fdi.pxmac
-
The MAC address of the primary interface in the format of
AA:BB:CC:DD:EE:FF. This is the interface you aim to use for communicating with Capsule Server. In automated mode, the first NIC (using network identifiers in alphabetical order) with a link is used. In semi-automated mode, a screen appears and requests you to select the correct interface. - fdi.rootpw
-
By default, the
rootaccount is locked. Use this option to set a root password. You can enter both clear and encrypted passwords. - fdi.ssh
-
By default, the SSH service is disabled. Set this to
1ortrueto enable SSH access. - fdi.uploadsleep
- Duration in seconds between facter runs. By default, facter runs every 30 seconds.
- fdi.vlan.primary
VLAN tagging ID to set for the primary interface. If you want to use tagged VLAN provisioning and you want the Discovery service to send a discovery request, add the following parameter to the Discovery snippet:
fdi.vlan.primary=My_VLAN_ID
fdi.vlan.primary=My_VLAN_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow - fdi.zips
- Filenames with extensions to be downloaded and started during boot. For more information, see Section 6.8, “Extending the Discovery image”.
- fdi.zipserver
- TFTP server to use to download extensions from. For more information, see Section 6.8, “Extending the Discovery image”.
- net.ifnames and biosdevname
Because network interface names are not expected to always be the same between major versions of Red Hat Enterprise Linux, hosts can be created with incorrect network configurations. You can disable the new naming scheme by a kernel command line parameter:
-
For Dell servers, use the
biosdevname=1parameter. -
For other hardware or virtual machines, use the
net.ifnames=1parameter.
-
For Dell servers, use the
- proxy.type
-
The proxy type. By default, this parameter is set to
foreman, where communication goes directly to Satellite Server. Set this parameter toproxyif you point to Capsule inproxy.url. - proxy.url
The URL of the server providing the Discovery service. By default, this parameter contains the
foreman_server_urlmacro as its argument. This macro resolves to the full URL of Satellite Server. There is no macro for a Capsule URL. You have to set a Capsule explicitly. For example:proxy.url=https://capsule.example.com:9090 proxy.type=proxy
proxy.url=https://capsule.example.com:9090 proxy.type=proxyCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can use an IP address or FQDN in this parameter. Add a SSL port number if you point to Capsule.
; as a list separator but currently also accepts ,. For more information, see man nm-settings-keyfile and Shell-like scripting in GRUB
6.10. Troubleshooting Discovery
If a machine is not listed in the Satellite web UI in Hosts > Discovered Hosts, it means that Discovery has failed. Inspect the following configuration areas to help isolate the problem:
Inspecting prerequisites
- Ensure that your Satellite and hosts meet the requirements. For more information, see Section 6.1, “Prerequisites for using Discovery”.
Inspecting problems on Satellite
- Ensure you have set Discovery for booting and built the PXE boot configuration files. For more information, see Section 6.3.1, “Setting Discovery as the default PXE boot option”.
Verify that these configuration files are present on your TFTP Capsule and have
discoveryset as the default boot option:-
/var/lib/tftpboot/pxelinux.cfg/default -
/var/lib/tftpboot/grub2/grub.cfg
-
-
Verify that the values of the
proxy.urlandproxy.typeoptions in the PXE Discovery snippet you are using. The default snippets are namedpxelinux_discovery,pxegrub_discovery, orpxegrub2_discovery.
Inspecting problems with networking
- Ensure adequate network connectivity between hosts, Capsule Server, and Satellite Server.
- Ensure that the DHCP server provides IP addresses to the booted Discovery image correctly.
-
Ensure that DNS is working correctly for the discovered hosts or use an IP address in the
proxy.urloption in the PXE Discovery snippet included in the PXE template you are using.
Inspecting problems on the host
If the host boots into the Discovery image but Discovery is not successful, enable the root account and SSH access on the Discovery image. You can enable SSH and set the root password by using the following Discovery kernel options:
fdi.ssh=1 fdi.rootpw=My_Password
fdi.ssh=1 fdi.rootpw=My_PasswordCopy to Clipboard Copied! Toggle word wrap Toggle overflow Using TTY2 or higher, log in to a Discovery-booted host to review system logs. For example, these logs are useful for troubleshooting:
discover-host- Initial facts upload
foreman-discovery- Facts refresh, reboot remote commands
nm-prepare- Boot script which pre-configures NetworkManager
NetworkManager- Networking information
-
For gathering important system facts, use the
discovery-debugcommand on the Discovery-booted host. It prints out system logs, network configuration, list of facts, and other information on the standard output. You can redirect this output to a file and copy it with thescpcommand for further investigation.
Additional resources
For more information about changing the Discovery kernel options, see the following resources:
Chapter 7. Configuring Satellite to provision from a Red Hat Image Builder image
In Satellite, you can enable integration with the RHEL web console to perform actions and monitor your hosts. Using the RHEL web console, you can access Red Hat Image Builder and build images. Afterwards, you can use these images to provision hosts.
Additional resources
- Host management and monitoring by using the RHEL web console in Managing hosts
7.1. Provisioning from a Red Hat Image Builder image on Capsule
You can upload a Red Hat Image Builder image to Satellite and use this image to provision hosts by using network boot.
When you provision from a Red Hat Image Builder image, Anaconda installer partitions disks, downloads and mounts the image, and copies files over to a host.
Prerequisites
- An existing TAR image created by using Red Hat Image Builder in the RHEL web console. Ensure that your blueprint to build the image includes the required packages.
- If you want to use Capsule Server URL, then the referenced lifecycle environment, such as Library, must be synchronized to that Capsule Server. For more information, see Adding lifecycle environments to Capsule Servers in Installing Capsule Server.
Procedure
- On Satellite, create a custom product, add a custom file type repository to this product, and upload the image to the repository. For more information, see Importing individual ISO images and files in Managing content.
- In the Satellite web UI, navigate to Configure > Host Groups.
- Select the host group that you want to use.
- Click the Parameters tab, and then click Add Parameter.
Create a parameter named
kickstart_liveimgwith type string and set the value to the full URL of the image location or the file name of the image inside a published content view, for example:-
Full URL:
https://capsule.example.com/pulp/content/My_Organization_Label/Library/custom/My_Product_Label/My_Repository_Label/My_Image_Name.tar Image file name:
My_Image_Name.tarYou can use the image file name only if the host is subscribed to a single content view and lifecycle environment, and the
kt_activation_keysparameter is defined for the host. The content view must be published.If a content source is assigned to the host, Satellite will use the content source Capsule of the host. If a content source is not assigned, Satellite will use Satellite Server.
-
Full URL:
- Click Submit to save your changes.
7.2. Provisioning from a Red Hat Image Builder image on an HTTP server
You can upload a Red Hat Image Builder image to an HTTP server and use this image to provision hosts by using network boot.
When you provision from a Red Hat Image Builder image, Anaconda installer partitions disks, downloads and mounts the image, and copies files over to a host.
Prerequisites
- An existing TAR image created by using Red Hat Image Builder in the RHEL web console. Ensure that your blueprint to build the image includes the required packages.
Procedure
- Copy the image to an existing HTTP server that your hosts can reach.
- In the Satellite web UI, navigate to Configure > Host Groups.
- Select the host group that you want to use.
- Click the Parameters tab, and then click Add Parameter.
-
Create a parameter named
kickstart_liveimgwith type string and set the value to the URL of the image location, such ashttps://webserver.example.com/path/My_Image_Name.tar. - Click Submit to save your changes.
7.3. Packages required in a Red Hat Image Builder image
For the use in Satellite, the Red Hat Image Builder image must contain the following minimum of packages:
-
NetworkManager -
authselect -
chrony -
dnf -
dracut -
efibootmgr -
firewalld -
grub2 -
grub2-efi -
grub2-tools-extra -
insights-client– required only if you plan to use Insights reporting -
iproute -
iputils -
kernel -
kernel-core -
lvm2 -
subscription-manager -
wget
Chapter 8. Provisioning virtual machines on KVM (libvirt)
Kernel-based Virtual Machines (KVMs) use an open source virtualization daemon and API called libvirt running on Red Hat Enterprise Linux. Satellite can connect to the libvirt API on a KVM server, provision hosts on the hypervisor, and control certain virtualization functions.
Only Virtual Machines created through Satellite can be managed. Virtual Machines with other than directory storage pool types are unsupported.
You can use KVM provisioning to create hosts over a network connection or from an existing image.
Prerequisites
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
- A Capsule Server managing a network on the KVM server. Ensure no other DHCP services run on this network to avoid conflicts with Capsule Server. For more information about network service configuration for Capsule Servers, see Configuring Networking in Provisioning hosts.
- A Red Hat Enterprise Linux server running KVM virtualization tools (libvirt daemon). For more information, see the Red Hat Enterprise Linux 8 Configuring and managing virtualization.
-
An existing virtual machine image if you want to use image-based provisioning. Ensure that this image exists in a storage pool on the KVM host. The
defaultstorage pool is usually located in/var/lib/libvirt/images. Only directory pool storage types can be managed through Satellite. Optional: The examples in these procedures use the root user for KVM. If you want to use a non-root user on the KVM server, you must add the user to the
libvirtgroup on the KVM server:usermod -a -G libvirt non_root_user
# usermod -a -G libvirt non_root_userCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Additional resources
- For a list of permissions a non-admin user requires to provision hosts, see Appendix E, Permissions required to provision hosts.
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
8.1. Configuring Satellite Server for KVM connections
Before adding the KVM connection, create an SSH key pair for the foreman user to ensure a secure connection between Satellite Server and KVM.
Procedure
On Satellite Server, switch to the
foremanuser:su foreman -s /bin/bash
# su foreman -s /bin/bashCopy to Clipboard Copied! Toggle word wrap Toggle overflow Generate the key pair:
ssh-keygen
$ ssh-keygenCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy the public key to the KVM server:
ssh-copy-id root@kvm.example.com
$ ssh-copy-id root@kvm.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Exit the bash shell for the
foremanuser:exit
$ exitCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the
libvirt-clientpackage:satellite-maintain packages install libvirt-client
# satellite-maintain packages install libvirt-clientCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the following command to test the connection to the KVM server:
su foreman -s /bin/bash -c 'virsh -c qemu+ssh://root@kvm.example.com/system list'
# su foreman -s /bin/bash -c 'virsh -c qemu+ssh://root@kvm.example.com/system list'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2. Adding a KVM connection to Satellite Server
Use this procedure to add KVM as a compute resource in Satellite. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click Create Compute Resource.
- In the Name field, enter a name for the new compute resource.
- From the Provider list, select Libvirt.
- In the Description field, enter a description for the compute resource.
In the URL field, enter the connection URL to the KVM server. For example:
qemu+ssh://root@kvm.example.com/system
qemu+ssh://root@kvm.example.com/systemCopy to Clipboard Copied! Toggle word wrap Toggle overflow - From the Display type list, select either VNC or Spice.
Optional: To secure console access for new hosts with a randomly generated password, select the Set a randomly generated password on the display connection checkbox. You can retrieve the password for the VNC console to access the guest virtual machine console from the output of the following command executed on the KVM server:
virsh edit your_VM_name <graphics type='vnc' port='-1' autoport='yes' listen='0.0.0.0' passwd='your_randomly_generated_password'>
# virsh edit your_VM_name <graphics type='vnc' port='-1' autoport='yes' listen='0.0.0.0' passwd='your_randomly_generated_password'>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The password is randomly generated every time the console for the virtual machine is opened, for example, with virt-manager.
- Click Test Connection to ensure that Satellite Server connects to the KVM server without fault.
- Verify that the Locations and Organizations tabs are automatically set to your current context. If you want, add additional contexts to these tabs.
- Click Submit to save the KVM connection.
CLI procedure
To create a compute resource, enter the
hammer compute-resource createcommand:hammer compute-resource create --name "My_KVM_Server" \ --provider "Libvirt" --description "KVM server at kvm.example.com" \ --url "qemu+ssh://root@kvm.example.com/system" --locations "New York" \ --organizations "My_Organization"
# hammer compute-resource create --name "My_KVM_Server" \ --provider "Libvirt" --description "KVM server at kvm.example.com" \ --url "qemu+ssh://root@kvm.example.com/system" --locations "New York" \ --organizations "My_Organization"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.3. Adding KVM images to Satellite Server
To create hosts using image-based provisioning, you must add information about the image, such as access details and the image location, to your Satellite Server.
Note that you can manage only directory pool storage types through Satellite.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click the name of the KVM connection.
- Click Create Image.
- In the Name field, enter a name for the image.
- From the Operating System list, select the base operating system of the image.
- From the Architecture list, select the operating system architecture.
-
In the Username field, enter the SSH user name for image access. This is normally the
rootuser. - In the Password field, enter the SSH password for image access.
In the Image path field, enter the full path that points to the image on the KVM server. For example:
/var/lib/libvirt/images/TestImage.qcow2
/var/lib/libvirt/images/TestImage.qcow2Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Optional: Select the User Data checkbox if the image supports user data input, such as
cloud-initdata. - Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. Use the--uuidfield to store the full path of the image location on the KVM server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.4. Adding KVM details to a compute profile
Use this procedure to add KVM hardware settings to a compute profile. When you create a host on KVM using this compute profile, these settings are automatically populated.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles.
- In the Compute Profiles window, click the name of an existing compute profile, or click Create Compute Profile, enter a Name, and click Submit.
- Click the name of the KVM compute resource.
- In the CPUs field, enter the number of CPUs to allocate to the new host.
- In the Memory field, enter the amount of memory to allocate to the new host.
- From the Image list, select the image to use if performing image-based provisioning.
- From the Network Interfaces list, select the network parameters for the host’s network interface. You can create multiple network interfaces. However, at least one interface must point to a Capsule-managed network.
- In the Storage area, enter the storage parameters for the host. You can create multiple volumes for the host.
- Click Submit to save the settings to the compute profile.
CLI procedure
To create a compute profile, enter the following command:
hammer compute-profile create --name "Libvirt CP"
# hammer compute-profile create --name "Libvirt CP"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To add the values for the compute profile, enter the following command:
hammer compute-profile values create --compute-profile "Libvirt CP" \ --compute-resource "My_KVM_Server" \ --interface "compute_type=network,compute_model=virtio,compute_network=examplenetwork" \ --volume "pool_name=default,capacity=20G,format_type=qcow2" \ --compute-attributes "cpus=1,memory=1073741824"
# hammer compute-profile values create --compute-profile "Libvirt CP" \ --compute-resource "My_KVM_Server" \ --interface "compute_type=network,compute_model=virtio,compute_network=examplenetwork" \ --volume "pool_name=default,capacity=20G,format_type=qcow2" \ --compute-attributes "cpus=1,memory=1073741824"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.5. Creating hosts on KVM
In Satellite, you can use KVM provisioning to create hosts over a network connection or from an existing image:
- If you want to create a host over a network connection, the new host must be able to access your Satellite Server or Capsule Servers on a KVM virtual network, so that the host has access to PXE provisioning services. This new host entry triggers the KVM server to create and start a virtual machine. If the virtual machine detects the defined Capsule Server through the virtual network, the virtual machine boots to PXE and begins to install the chosen operating system.
- If you want to create a host with an existing image, the new host entry triggers the KVM server to create the virtual machine using a pre-existing image as a basis for the new volume.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
DHCP conflicts
For network-based provisioning, if you use a virtual network on the KVM server for provisioning, select a network that does not provide DHCP assignments. This causes DHCP conflicts with Satellite Server when booting new hosts.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the KVM connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine settings. The KVM-specific fields are populated with settings from your compute profile. Modify these settings if required.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. KVM assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and confirm that all fields automatically contain values.
Select the Provisioning Method that you want to use:
- For network-based provisioning, click Network Based.
- For image-based provisioning, click Image Based.
- Click Resolve in Provisioning templates to check the new host can identify the right provisioning templates to use.
- Click the Virtual Machine tab and confirm that these settings are populated with details from the host group and compute profile. Modify these settings to suit your needs.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save the host entry.
CLI procedure
To use network-based provisioning, create the host with the
hammer host createcommand and include--provision-method build. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow To use image-based provisioning, create the host with the
hammer host createcommand and include--provision-method image. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
Chapter 9. Provisioning virtual machines on Red Hat Virtualization
Red Hat Virtualization is an enterprise-grade server and desktop virtualization platform. In Red Hat Satellite, you can manage virtualization functions through Red Hat Virtualization’s REST API. This includes creating virtual machines and controlling their power states.
You can use Red Hat Virtualization provisioning to create virtual machines over a network connection or from an existing image.
You can use cloud-init to configure the virtual machines that you provision. Using cloud-init avoids any special configuration on the network, such as a managed DHCP and TFTP, to finish the installation of the virtual machine. This method does not require Satellite to connect to the provisioned virtual machine over SSH to run the finish script.
Prerequisites
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
- A Capsule Server managing a logical network on the Red Hat Virtualization environment. Ensure no other DHCP services run on this network to avoid conflicts with Capsule Server. For more information, see Configuring Networking in Provisioning hosts.
-
An existing template, other than the
blanktemplate, if you want to use image-based provisioning. For more information about creating templates for virtual machines, see Templates in the Red Hat Virtualization Virtual Machine Management Guide. An administration-like user on Red Hat Virtualization for communication with Satellite Server. Do not use the
admin@internaluser for this communication. Instead, create a new Red Hat Virtualization user with the following permissions:- System > Configure System > Login Permissions
- Network > Configure vNIC Profile > Create
- Network > Configure vNIC Profile > Edit Properties
- Network > Configure vNIC Profile > Delete
- Network > Configure vNIC Profile > Assign vNIC Profile to VM
- Network > Configure vNIC Profile > Assign vNIC Profile to Template
- Template > Provisioning Operations > Import/Export
- VM > Provisioning Operations > Create
- VM > Provisioning Operations > Delete
- VM > Provisioning Operations > Import/Export
- VM > Provisioning Operations > Edit Storage
- Disk > Provisioning Operations > Create
Disk > Disk Profile > Attach Disk Profile
For more information about how to create a user and add permissions in Red Hat Virtualization, see Administering User Tasks From the Administration Portal in the Red Hat Virtualization Administration Guide.
Additional resources
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
9.1. Adding the Red Hat Virtualization connection to Satellite Server
Use this procedure to add Red Hat Virtualization as a compute resource in Satellite. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click Create Compute Resource.
- In the Name field, enter a name for the new compute resource.
- From the Provider list, select RHV.
- In the Description field, enter a description for the compute resource.
-
In the URL field, enter the connection URL for the Red Hat Virtualization Manager’s API in the following form:
https://rhv.example.com/ovirt-engine/api/v4. - In the User field, enter the name of a user with permissions to access Red Hat Virtualization Manager’s resources.
- In the Password field, enter the password of the user.
- Click Load Datacenters to populate the Datacenter list with data centers from your Red Hat Virtualization environment.
- From the Datacenter list, select a data center.
- From the Quota ID list, select a quota to limit resources available to Satellite.
- In the X509 Certification Authorities field, enter the certificate authority for SSL/TLS access. Alternatively, if you leave the field blank, a self-signed certificate is generated on the first API request by the server.
- Click the Locations tab and select the location you want to use.
- Click the Organizations tab and select the organization you want to use.
- Click Submit to save the compute resource.
CLI procedure
Enter the
hammer compute-resource createcommand withOvirtfor--providerand the name of the data center you want to use for--datacenter.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2. Preparing cloud-init images in Red Hat Virtualization
To use cloud-init during provisioning, you must prepare an image with cloud-init installed in Red Hat Virtualization, and then import the image to Satellite to use for provisioning.
Procedure
- In Red Hat Virtualization, create a virtual machine to use for image-based provisioning in Satellite.
On the virtual machine, install
cloud-init:dnf install cloud-init
# dnf install cloud-initCopy to Clipboard Copied! Toggle word wrap Toggle overflow To the
/etc/cloud/cloud.cfgfile, add the following information:datasource_list: ["NoCloud", "ConfigDrive"]
datasource_list: ["NoCloud", "ConfigDrive"]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - In Red Hat Virtualization, create an image from this virtual machine.
When you add this image to Satellite, ensure that you select the User Data checkbox.
9.3. Adding Red Hat Virtualization images to Satellite Server
To create hosts using image-based provisioning, you must add information about the image, such as access details and the image location, to your Satellite Server.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click the name of the Red Hat Virtualization connection.
- Click Create Image.
- In the Name field, enter a name for the image.
- From the Operating System list, select the base operating system of the image.
- From the Architecture list, select the operating system architecture.
-
In the Username field, enter the SSH user name for image access. This is normally the
rootuser. - In the Password field, enter the SSH password for image access.
- From the Image list, select an image from the Red Hat Virtualization compute resource.
-
Optional: Select the User Data checkbox if the image supports user data input, such as
cloud-initdata. - Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. Use the--uuidoption to store the template UUID on the Red Hat Virtualization server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4. Preparing a cloud-init template
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates, and click Create Template.
- In the Name field, enter a name for the template.
In the Editor field, enter the following template details:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the Type tab and from the Type list, select User data template.
- Click the Association tab, and from the Applicable Operating Systems list, select the operating system that you want associate with the template.
- Click the Locations tab, and from the Locations list, select the location that you want to associate with the template.
- Click the Organizations tab, and from the Organization list, select the organization that you want to associate with the template.
- Click Submit.
- In the Satellite web UI, navigate to Hosts > Provisioning Setup > Operating Systems.
- Select the operating system you want to associate with the template.
- Click the Templates tab, and from the User data template list, select the name of the new template.
- Click Submit.
9.5. Adding Red Hat Virtualization details to a compute profile
Use this procedure to add Red Hat Virtualization hardware settings to a compute profile. When you create a host on KVM using this compute profile, these settings are automatically populated.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles.
- In the Compute Profiles window, click the name of an existing compute profile, or click Create Compute Profile, enter a Name, and click Submit.
- Click the name of the Red Hat Virtualization compute resource.
- From the Cluster list, select the target host cluster in the Red Hat Virtualization environment.
- From the Template list, select the RHV template to use for the Cores and Memory settings.
- In the Cores field, enter the number of CPU cores to allocate to the new host.
- In the Memory field, enter the amount of memory to allocate to the new host.
- From the Image list, select image to use for image-based provisioning.
In the Network Interfaces area, enter the network parameters for the host’s network interface. You can create multiple network interfaces. However, at least one interface must point to a Capsule-managed network. For each network interface, enter the following details:
- In the Name field, enter the name of the network interface.
- From the Network list, select The logical network that you want to use.
In the Storage area, enter the storage parameters for the host. You can create multiple volumes for the host. For each volume, enter the following details:
- In the Size (GB) enter the size, in GB, for the new volume.
- From the Storage domain list, select the storage domain for the volume.
- From the Preallocate disk, select either thin provisioning or preallocation of the full disk.
- From the Bootable list, select whether you want a bootable or non-bootable volume.
- Click Submit to save the compute profile.
CLI procedure
To create a compute profile, enter the following command:
hammer compute-profile create --name "Red Hat Virtualization CP"
# hammer compute-profile create --name "Red Hat Virtualization CP"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To set the values for the compute profile, enter the following command:
hammer compute-profile values create --compute-profile "Red Hat Virtualization CP" \ --compute-resource "My_RHV" \ --interface "compute_interface=Interface_Type,compute_name=eth0,compute_network=satnetwork" \ --volume "size_gb=20G,storage_domain=Data,bootable=true" \ --compute-attributes "cluster=Default,cores=1,memory=1073741824,start=true""
# hammer compute-profile values create --compute-profile "Red Hat Virtualization CP" \ --compute-resource "My_RHV" \ --interface "compute_interface=Interface_Type,compute_name=eth0,compute_network=satnetwork" \ --volume "size_gb=20G,storage_domain=Data,bootable=true" \ --compute-attributes "cluster=Default,cores=1,memory=1073741824,start=true""Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.6. Creating hosts on Red Hat Virtualization
In Satellite, you can use Red Hat Virtualization provisioning to create hosts over a network connection or from an existing image:
- If you want to create a host over a network connection, the new host must be able to access your Satellite Server or Capsule Servers on a Red Hat Virtualization virtual network, so that the host has access to PXE provisioning services. This new host entry triggers the Red Hat Virtualization server to create and start a virtual machine. If the virtual machine detects the defined Capsule Server through the virtual network, the virtual machine boots to PXE and begins to install the chosen operating system.
- If you want to create a host with an existing image, the new host entry triggers the Red Hat Virtualization server to create the virtual machine using a pre-existing image as a basis for the new volume.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
DHCP conflicts
For network-based provisioning, if you use a virtual network on the Red Hat Virtualization server for provisioning, select a network that does not provide DHCP assignments. This causes DHCP conflicts with Satellite Server when booting new hosts.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the Red Hat Virtualization connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine settings. The Red Hat Virtualization-specific fields are populated with settings from your compute profile. Modify these settings if required.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. Red Hat Virtualization assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and confirm that all fields automatically contain values.
Select the Provisioning Method that you want to use:
- For network-based provisioning, click Network Based.
- For image-based provisioning, click Image Based.
- Click Resolve in Provisioning templates to check the new host can identify the right provisioning templates to use.
- Click the Virtual Machine tab and confirm that these settings are populated with details from the host group and compute profile. Modify these settings to suit your needs.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save the host entry.
CLI procedure
To use network-based provisioning, create the host with the
hammer host createcommand and include--provision-method build. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow To use image-based provisioning, create the host with the
hammer host createcommand and include--provision-method image. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
Chapter 10. Provisioning virtual machines in VMware vSphere
VMware vSphere is an enterprise-level virtualization platform from VMware. Red Hat Satellite can interact with the vSphere platform, including creating new virtual machines and controlling their power management states.
10.1. Prerequisites for VMware provisioning
The requirements for VMware vSphere provisioning include:
A supported version of VMware vCenter Server. The following versions have been fully tested with Satellite:
- vCenter Server 8.0
- vCenter Server 7.0
- A Capsule Server managing a network on the vSphere environment. Ensure no other DHCP services run on this network to avoid conflicts with Capsule Server. For more information, see Chapter 3, Configuring networking.
- An existing VMware template if you want to use image-based provisioning.
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
10.2. Creating a VMware user
The VMware vSphere server requires an administration-like user for Satellite Server communication. For security reasons, do not use the administrator user for such communication. Instead, create a user with the following permissions:
For VMware vCenter Server version 8.0 or 7.0, set the following permissions:
- All Privileges → Datastore → Allocate Space, Browse datastore, Update Virtual Machine files, Low level file operations
- All Privileges → Network → Assign Network
- All Privileges → Resource → Assign virtual machine to resource pool
- All Privileges → Virtual Machine → Change Config (All)
- All Privileges → Virtual Machine → Interaction (All)
- All Privileges → Virtual Machine → Edit Inventory (All)
- All Privileges → Virtual Machine → Provisioning (All)
- All Privileges → Virtual Machine → Guest Operations (All)
10.3. Adding a VMware connection to Satellite Server
Use this procedure to add a VMware vSphere connection in Satellite Server’s compute resources. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Prerequisites
- Ensure that the host and network-based firewalls are configured to allow communication from Satellite Server to vCenter on TCP port 443.
- Verify that Satellite Server and vCenter can resolve each other’s host names.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources, and in the Compute Resources window, click Create Compute Resource.
- In the Name field, enter a name for the resource.
- From the Provider list, select VMware.
- In the Description field, enter a description for the resource.
- In the VCenter/Server field, enter the IP address or host name of the vCenter server.
- In the User field, enter the user name with permission to access the vCenter’s resources.
- In the Password field, enter the password for the user.
- Click Load Datacenters to populate the list of data centers from your VMware vSphere environment.
- From the Datacenter list, select a specific data center to manage from this list.
- In the Fingerprint field, ensure that this field is populated with the fingerprint from the data center.
- From the Display Type list, select a console type, for example, VNC or VMRC. Note that VNC consoles are unsupported on VMware ESXi 6.5 and later.
- Optional: In the VNC Console Passwords field, select the Set a randomly generated password on the display connection checkbox to secure console access for new hosts with a randomly generated password.
- From the Enable Caching list, you can select whether to enable caching of compute resources. For more information, see Section 10.10, “Caching of compute resources”.
- Click the Locations and Organizations tabs and verify that the values are automatically set to your current context. You can also add additional contexts.
- Click Submit to save the connection.
CLI procedure
Create the connection with the
hammer compute-resource createcommand. SelectVmwareas the--providerand set the instance UUID of the data center as the--uuid:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.4. Adding VMware images to Satellite Server
VMware vSphere uses templates as images for creating new virtual machines. If using image-based provisioning to create new hosts, you need to add VMware template details to your Satellite Server. This includes access details and the template name.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your VMware compute resource.
- Click Create Image.
- In the Name field, enter a name for the image.
- From the Operating System list, select the base operating system of the image.
- From the Architecture list, select the operating system architecture.
-
In the Username field, enter the SSH user name for image access. By default, this is set to
root. -
If your image supports user data input such as
cloud-initdata, click the User data checkbox. - Optional: In the Password field, enter the SSH password to access the image.
- From the Image list, select an image from VMware.
- Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. Use the--uuidfield to store the relative template path on the vSphere environment:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.5. Adding VMware details to a compute profile
You can predefine certain hardware settings for virtual machines on VMware vSphere. You achieve this through adding these hardware settings to a compute profile. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles.
- Select a compute profile.
- Select a VMware compute resource.
- In the CPUs field, enter the number of CPUs to allocate to the host.
- In the Cores per socket field, enter the number of cores to allocate to each CPU.
- In the Memory field, enter the amount of memory in MiB to allocate to the host.
- In the Firmware checkbox, select either BIOS or UEFI as firmware for the host. By default, this is set to automatic.
- In the Cluster list, select the name of the target host cluster on the VMware environment.
- From the Resource pool list, select an available resource allocations for the host.
- In the Folder list, select the folder to organize the host.
- From the Guest OS list, select the operating system you want to use in VMware vSphere.
- From the Virtual H/W version list, select the underlying VMware hardware abstraction to use for virtual machines.
- If you want to add more memory while the virtual machine is powered on, select the Memory hot add checkbox.
- If you want to add more CPUs while the virtual machine is powered on, select the CPU hot add checkbox.
- If you want to add a CD-ROM drive, select the CD-ROM drive checkbox.
- From the Boot order list, define the order in which the virtual machines tried to boot.
- Optional: In the Annotation Notes field, enter an arbitrary description.
- If you use image-based provisioning, select the image from the Image list.
- From the SCSI controller list, select the disk access method for the host.
- If you want to use eager zero thick provisioning, select the Eager zero checkbox. By default, the disk uses lazy zero thick provisioning.
- From the Network Interfaces list, select the network parameters for the host’s network interface. At least one interface must point to a Capsule-managed network.
- Optional: Click Add Interface to create another network interfaces.
- Click Submit to save the compute profile.
CLI procedure
Create a compute profile:
hammer compute-profile create --name "My_Compute_Profile"
# hammer compute-profile create --name "My_Compute_Profile"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set VMware details to a compute profile:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.6. Creating hosts on VMware
The VMware vSphere provisioning process provides the option to create hosts over a network connection or using an existing image.
For network-based provisioning, you must create a host to access either Satellite Server or Capsule Servers on a VMware vSphere virtual network, so that the host has access to PXE provisioning services. The new host entry triggers the VMware vSphere server to create the virtual machine. If the virtual machine detects the defined Capsule through the virtual network, the virtual machine boots to PXE and begins to install the chosen operating system.
DHCP conflicts
If you use a virtual network on the VMware vSphere server for provisioning, ensure that you select a virtual network that does not provide DHCP assignments. This causes DHCP conflicts with Satellite Server when booting new hosts.
For image-based provisioning, use the pre-existing image as a basis for the new volume.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the VMware vSphere connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine-based settings.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. VMware assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- In the interface window, review the VMware-specific fields that are populated with settings from our compute profile. Modify these settings to suit your needs.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and confirm that all fields automatically contain values.
Select the Provisioning Method that you want:
- For network-based provisioning, click Network Based.
- For image-based provisioning, click Image Based.
- For boot-disk provisioning, click Boot disk based.
- Click Resolve in Provisioning templates to check the new host can identify the right provisioning templates to use.
- Click the Virtual Machine tab and confirm that these settings are populated with details from the host group and compute profile. Modify these settings to suit your requirements.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to provision your host on VMware.
CLI procedure
Create the host from a network with the
hammer host createcommand and include--provision-method buildto use network-based provisioning:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the host from an image with the
hammer host createcommand and include--provision-method imageto use image-based provisioning:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
10.7. Using VMware cloud-init and userdata templates for provisioning
You can use VMware with the Cloud-init and Userdata templates to insert user data into the new virtual machine, to make further VMware customization, and to enable the VMware-hosted virtual machine to call back to Satellite.
You can use the same procedures to set up a VMware compute resource within Satellite, with a few modifications to the workflow.
Figure 10.1. VMware cloud-init provisioning overview
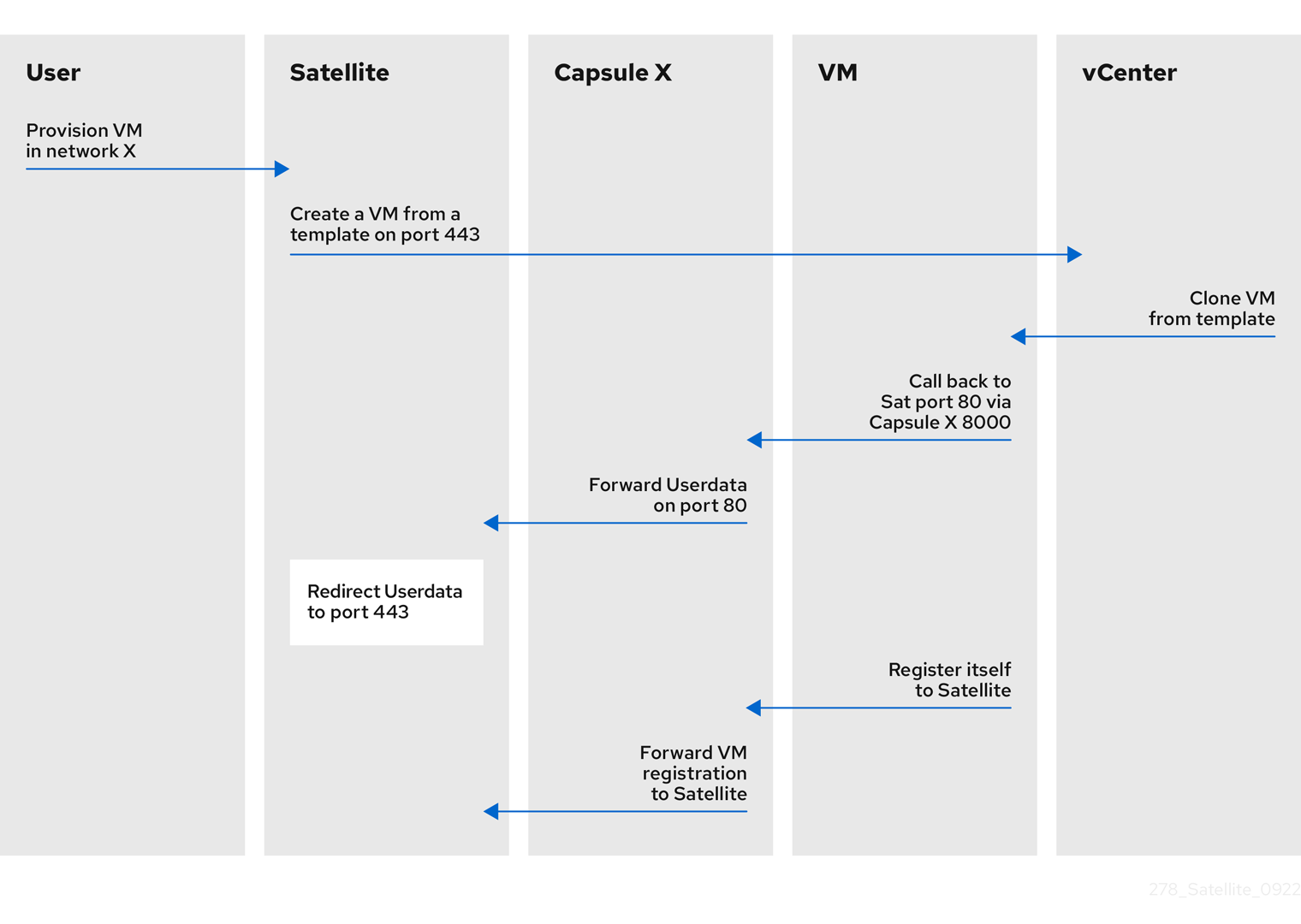
When you set up the compute resource and images for VMware provisioning in Satellite, the following sequence of provisioning events occurs:
- The user provisions one or more virtual machines using the Satellite web UI, API, or hammer
- Satellite calls the VMware vCenter to clone the virtual machine template
-
Satellite
userdataprovisioning template adds customized identity information -
When provisioning completes, the
Cloud-initprovisioning template instructs the virtual machine to call back to Capsule whencloud-initruns - VMware vCenter clones the template to the virtual machine
- VMware vCenter applies customization for the virtual machine’s identity, including the host name, IP, and DNS
-
The virtual machine builds,
cloud-initis invoked and calls back Satellite on port80, which then redirects to443
Prerequisites
-
Configure port and firewall settings to open any necessary connections. Because of the
cloud-initservice, the virtual machine always calls back to Satellite even if you register the virtual machine to Capsule. For more information, see Port and firewall requirements in Installing Satellite Server in a connected network environment and Port and firewall requirements in Installing Capsule Server. If you want to use Capsule Servers instead of your Satellite Server, ensure that you have configured your Capsule Servers accordingly.
ImportantIt is essential to add your Capsule Server to the list of trusted proxies on Satellite Server!
For more information, see Configuring Capsule for Host Registration and Provisioning in Installing Capsule Server.
Back up the following configuration files:
-
/etc/cloud/cloud.cfg.d/01_network.cfg -
/etc/cloud/cloud.cfg.d/10_datasource.cfg -
/etc/cloud/cloud.cfg
-
Associating the Userdata and Cloud-init templates with the operating system
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
- Search for the CloudInit default template and click its name.
- Click the Association tab.
- Select all operating systems to which the template applies and click Submit.
- Repeat the steps above for the UserData open-vm-tools template.
- Navigate to Hosts > Provisioning Setup > Operating Systems.
- Select the operating system that you want to use for provisioning.
- Click the Templates tab.
- From the Cloud-init template list, select CloudInit default.
- From the User data template list, select UserData open-vm-tools.
- Click Submit to save the changes.
Preparing an image to use the cloud-init template
To prepare an image, you must first configure the settings that you require on a virtual machine that you can then save as an image to use in Satellite.
To use the cloud-init template for provisioning, you must configure a virtual machine so that cloud-init is installed, enabled, and configured to call back to Satellite Server.
For security purposes, you must install a CA certificate to use HTTPS for all communication. This procedure includes steps to clean the virtual machine so that no unwanted information transfers to the image you use for provisioning.
If you have an image with cloud-init, you must still follow this procedure to enable cloud-init to communicate with Satellite because cloud-init is disabled by default.
Procedure
On the virtual machine that you use to create the image, install the required packages:
dnf install cloud-init open-vm-tools perl-interpreter perl-File-Temp
# dnf install cloud-init open-vm-tools perl-interpreter perl-File-TempCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Red Hat Enterprise Linux 9, you also require the
dbus-toolspackage for network connectivity.Disable network configuration by
cloud-init:cat << EOM > /etc/cloud/cloud.cfg.d/01_network.cfg network: config: disabled EOM
# cat << EOM > /etc/cloud/cloud.cfg.d/01_network.cfg network: config: disabled EOMCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure
cloud-initto fetch data from Satellite:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you intend to provision through Capsule Server, use the URL of your Capsule Server in the
seedfromoption, such ashttps://capsule.example.com:9090/userdata/.Configure modules to use in
cloud-init:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Download the
katello-server-ca.crtfile from Satellite Server:wget -O /etc/pki/ca-trust/source/anchors/cloud-init-ca.crt https://satellite.example.com/pub/katello-server-ca.crt
# wget -O /etc/pki/ca-trust/source/anchors/cloud-init-ca.crt https://satellite.example.com/pub/katello-server-ca.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you intend to provision through Capsule Server, download the file from your Capsule Server, such as
https://capsule.example.com/pub/katello-server-ca.crt.Update the record of certificates:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow Stop the
rsyslogandauditdservices:systemctl stop rsyslog systemctl stop auditd
# systemctl stop rsyslog # systemctl stop auditdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Clean packages on the image:
On Red Hat Enterprise Linux 8 and later:
dnf remove --oldinstallonly
# dnf remove --oldinstallonlyCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Red Hat Enterprise Linux 7 and earlier:
package-cleanup --oldkernels --count=1 dnf clean all
# package-cleanup --oldkernels --count=1 # dnf clean allCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Reduce logspace, remove old logs, and truncate logs:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove
udevhardware rules:rm -f /etc/udev/rules.d/70*
# rm -f /etc/udev/rules.d/70*Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the
ifcfgscripts related to existing network configurations:rm -f /etc/sysconfig/network-scripts/ifcfg-ens* rm -f /etc/sysconfig/network-scripts/ifcfg-eth*
# rm -f /etc/sysconfig/network-scripts/ifcfg-ens* # rm -f /etc/sysconfig/network-scripts/ifcfg-eth*Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the SSH host keys:
rm -f /etc/ssh/ssh_host_*
# rm -f /etc/ssh/ssh_host_*Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove root user’s SSH history:
rm -rf ~root/.ssh/known_hosts
# rm -rf ~root/.ssh/known_hostsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove root user’s shell history:
rm -f ~root/.bash_history unset HISTFILE
# rm -f ~root/.bash_history # unset HISTFILECopy to Clipboard Copied! Toggle word wrap Toggle overflow - Create an image from this virtual machine.
- Add your image to Satellite.
10.8. Deleting a VM on VMware
You can delete VMs running on VMware from within Satellite.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your VMware provider.
- On the Virtual Machines tab, click Delete from the Actions menu. This deletes the virtual machine from the VMware compute resource while retaining any associated hosts within Satellite. If you want to delete the orphaned host, navigate to Hosts > All Hosts and delete the host manually.
Additional resources
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
10.9. Importing a virtual machine from VMware into Satellite
You can import existing virtual machines running on VMware into Satellite.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your VMware compute resource.
- On the Virtual Machines tab, click Import as managed Host or Import as unmanaged Host from the Actions menu. The following page looks identical to creating a host with the compute resource being already selected. For more information, see Creating a host in Satellite in Managing hosts.
- Click Submit to import the virtual machine into Satellite.
10.10. Caching of compute resources
Caching of compute resources speeds up rendering of VMware information.
10.10.1. Enabling caching of compute resources
To enable or disable caching of compute resources:
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Click the Edit button to the right of the VMware server you want to update.
- Select the Enable caching checkbox.
10.10.2. Refreshing the compute resources cache
Refresh the cache of compute resources to update compute resources information.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select a VMware server you want to refresh the compute resources cache for and click Refresh Cache.
CLI procedure
Use this API call to refresh the compute resources cache:
curl -H "Accept:application/json" \ -H "Content-Type:application/json" -X PUT \ -u username:password -k \ https://satellite.example.com/api/compute_resources/compute_resource_id/refresh_cache
# curl -H "Accept:application/json" \ -H "Content-Type:application/json" -X PUT \ -u username:password -k \ https://satellite.example.com/api/compute_resources/compute_resource_id/refresh_cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use
hammer compute-resource listto determine the ID of the VMware server you want to refresh the compute resources cache for.
Chapter 11. Provisioning virtual machines on OpenShift Virtualization
OpenShift Virtualization addresses the needs of development teams that have adopted or want to adopt Red Hat OpenShift Container Platform but possess existing virtual machine (VM) workloads that cannot be easily containerized. This technology provides a unified development platform where developers can build, modify, and deploy applications residing in application containers and VMs in a shared environment. These capabilities support rapid application modernization across the open hybrid cloud.
You can create a compute resource for OpenShift Virtualization so that you can provision and manage virtual machines in OpenShift Container Platform by using Satellite.
Note that template provisioning is not supported for this release.
The OpenShift Virtualization compute resource is a Technology Preview feature only. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process. For more information about the support scope of Red Hat Technology Preview features, see https://access.redhat.com/support/offerings/techpreview/.
Prerequisites
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
-
You must have
cluster-adminpermissions for the OpenShift Container Platform cluster. - A Capsule Server managing a network on the OpenShift Container Platform cluster. Ensure that no other DHCP services run on this network to avoid conflicts with Capsule Server. For more information about network service configuration for Capsule Servers, see Configuring Networking in Provisioning hosts.
Additional resources
- For a list of permissions a non-admin user requires to provision hosts, see Appendix E, Permissions required to provision hosts.
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
11.1. Adding an OpenShift Virtualization connection to Satellite Server
Use this procedure to add OpenShift Virtualization as a compute resource in Satellite.
Procedure
Enter the following
satellite-installercommand to enable the OpenShift Virtualization plugin for Satellite:satellite-installer --enable-foreman-plugin-kubevirt
# satellite-installer --enable-foreman-plugin-kubevirtCopy to Clipboard Copied! Toggle word wrap Toggle overflow Obtain a token to use for HTTP and HTTPs authentication:
Log in to the OpenShift Container Platform cluster and list the secrets that contain tokens:
oc get secrets
$ oc get secretsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Obtain the token for your secret:
oc get secrets MY_SECRET -o jsonpath='{.data.token}' | base64 -d | xargs$ oc get secrets MY_SECRET -o jsonpath='{.data.token}' | base64 -d | xargsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Record the token to use later in this procedure.
- In the Satellite web UI, navigate to Infrastructure > Compute Resources, and click Create Compute Resource.
- In the Name field, enter a name for the new compute resource.
- From the Provider list, select OpenShift Virtualization.
- In the Description field, enter a description for the compute resource.
- In the Hostname field, enter the FQDN, hostname, or IP address of the OpenShift Container Platform cluster.
- In the API Port field, enter the port number that you want to use for provisioning requests from Satellite to OpenShift Virtualization.
- In the Namespace field, enter the user name of the OpenShift Container Platform cluster.
- In the Token field, enter the bearer token for HTTP and HTTPs authentication.
- Optional: In the X509 Certification Authorities field, enter a certificate to enable client certificate authentication for API server calls.
Chapter 12. Provisioning cloud instances on Red Hat OpenStack Services on OpenShift
Red Hat OpenStack Services on OpenShift provides the foundation to build a private or public Infrastructure-as-a-Service (IaaS) cloud. It offers a massively scalable, fault-tolerant platform for the development of cloud-enabled workloads. In Satellite, you can interact with Red Hat OpenStack Services on OpenShift REST API to create cloud instances and control their power management states.
Prerequisites
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
- A Capsule Server managing a network in your OpenStack environment. For more information, see Configuring Networking in Provisioning hosts.
- An image added to OpenStack Image Storage (glance) service for image-based provisioning. For more information, see the Red Hat OpenStack Services on OpenShift Instances and Images Guide.
Additional resources
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
12.1. Adding a Red Hat OpenStack Services on OpenShift connection to Satellite Server
You can add Red Hat OpenStack Services on OpenShift as a compute resource in Satellite. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Click Create Compute Resource.
- In the Name field, enter a name for the new compute resource.
- From the Provider list, select RHEL OpenStack Platform.
- Optional: In the Description field, enter a description for the compute resource.
-
In the URL field, enter the URL for the OpenStack Authentication keystone service’s API at the
tokensresource, such ashttp://openstack.example.com:5000/v2.0/tokensorhttp://openstack.example.com:5000/v3/auth/tokens. - In the Username and Password fields, enter the user authentication for Satellite to access the environment.
- Optional: In the Project (Tenant) name field, enter the name of your tenant (v2) or project (v3) for Satellite Server to manage.
- In the User domain field, enter the user domain for v3 authentication.
- In the Project domain name field, enter the project domain name for v3 authentication.
- In the Project domain ID field, enter the project domain ID for v3 authentication.
- Optional: Select Allow external network as main network to use external networks as primary networks for hosts.
- Optional: Click Test Connection to verify that Satellite can connect to your compute resource.
- Click the Locations and Organizations tabs and verify that the location and organization that you want to use are set to your current context. Add any additional contexts that you want to these tabs.
- Click Submit to save the Red Hat OpenStack Services on OpenShift connection.
CLI procedure
To create a compute resource, enter the
hammer compute-resource createcommand:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.2. Adding Red Hat OpenStack Services on OpenShift images to Satellite Server
To create hosts using image-based provisioning, you must add information about the image, such as access details and the image location, to your Satellite Server.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click the name of the Red Hat OpenStack Services on OpenShift connection.
- Click Create Image.
- In the Name field, enter a name for the image.
- From the Operating System list, select the base operating system of the image.
- From the Architecture list, select the operating system architecture.
-
In the Username field, enter the SSH user name for image access. This is normally the
rootuser. - In the Password field, enter the SSH password for image access.
- From the Image list, select an image from the Red Hat OpenStack Services on OpenShift compute resource.
-
Optional: Select the User Data checkbox if the image supports user data input, such as
cloud-initdata. - Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. Use the--uuidfield to store the full path of the image location on the Red Hat OpenStack Services on OpenShift server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.3. Adding Red Hat OpenStack Services on OpenShift details to a compute profile
Use this procedure to add Red Hat OpenStack Services on OpenShift hardware settings to a compute profile. When you create a host on Red Hat OpenStack Services on OpenShift using this compute profile, these settings are automatically populated.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles.
- In the Compute Profiles window, click the name of an existing compute profile, or click Create Compute Profile, enter a Name, and click Submit.
- Click the name of the Red Hat OpenStack Services on OpenShift compute resource.
- From the Flavor list, select the hardware profile on Red Hat OpenStack Services on OpenShift to use for the host.
- From the Availability zone list, select the target cluster to use within the Red Hat OpenStack Services on OpenShift environment.
- From the Image list, select the image to use for image-based provisioning.
- From the Tenant list, select the tenant or project for the Red Hat OpenStack Services on OpenShift instance.
- From the Security Group list, select the cloud-based access rules for ports and IP addresses.
- From the Internal network, select the private networks for the host to join.
- From the Floating IP network, select the external networks for the host to join and assign a floating IP address.
- From the Boot from volume, select whether a volume is created from the image. If not selected, the instance boots the image directly.
- In the New boot volume size (GB) field, enter the size, in GB, of the new boot volume.
- Click Submit to save the compute profile.
CLI procedure
Set Red Hat OpenStack Services on OpenShift details to a compute profile:
hammer compute-profile values create --compute-resource "My_Laptop" \ --compute-profile "My_Compute_Profile" \ --compute-attributes "availability_zone=My_Zone,image_ref=My_Image,flavor_ref=m1.small,tenant_id=openstack,security_groups=default,network=My_Network,boot_from_volume=false"
# hammer compute-profile values create --compute-resource "My_Laptop" \ --compute-profile "My_Compute_Profile" \ --compute-attributes "availability_zone=My_Zone,image_ref=My_Image,flavor_ref=m1.small,tenant_id=openstack,security_groups=default,network=My_Network,boot_from_volume=false"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.4. Creating image-based hosts on Red Hat OpenStack Services on OpenShift
In Satellite, you can use Red Hat OpenStack Services on OpenShift provisioning to create hosts from an existing image. The new host entry triggers the Red Hat OpenStack Services on OpenShift server to create the instance using the pre-existing image as a basis for the new volume.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the Red Hat OpenStack Services on OpenShift connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine settings.
- From the Lifecycle Environment list, select the environment.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. Red Hat OpenStack Services on OpenShift assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and confirm that all fields automatically contain values.
- If you want to change the image that populates automatically from your compute profile, from the Images list, select a different image to base the new host’s root volume on.
- Click Resolve in Provisioning templates to check the new host can identify the right provisioning templates to use.
- Click the Virtual Machine tab and confirm that these settings are populated with details from the host group and compute profile. Modify these settings to suit your needs.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save the host entry.
CLI procedure
Create the host with the
hammer host createcommand and include--provision-method image. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
Chapter 13. Provisioning cloud instances in Amazon EC2
Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides public cloud compute resources. Using Satellite, you can interact with Amazon EC2’s public API to create cloud instances and control their power management states. Use the procedures in this chapter to add a connection to an Amazon EC2 account and provision a cloud instance.
13.1. Prerequisites for Amazon EC2 provisioning
The requirements for Amazon EC2 provisioning include:
- A Capsule Server managing a network in your EC2 environment. Use a Virtual Private Cloud (VPC) to ensure a secure network between the hosts and Capsule Server.
- An Amazon Machine Image (AMI) for image-based provisioning.
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
13.2. Adding an Amazon EC2 connection to the Satellite Server
Use this procedure to add the Amazon EC2 connection in Satellite Server’s compute resources. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Prerequisites
-
An AWS EC2 user performing this procedure needs the
AmazonEC2FullAccesspermissions. You can attach these permissions from AWS.
Time settings and Amazon Web Services
Amazon Web Services uses time settings as part of the authentication process. Ensure that Satellite Server’s time is correctly synchronized. Ensure that an NTP service, such as ntpd or chronyd, is running properly on Satellite Server. Failure to provide the correct time to Amazon Web Services can lead to authentication failures.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and in the Compute Resources window, click Create Compute Resource.
- In the Name field, enter a name to identify the Amazon EC2 compute resource.
- From the Provider list, select EC2.
- In the Description field, enter information that helps distinguish the resource for future use.
- Optional: From the HTTP proxy list, select an HTTP proxy to connect to external API services. You must add HTTP proxies to Satellite before you can select a proxy from this list. For more information, see Section 13.3, “Using an HTTP proxy with compute resources”.
- In the Access Key and Secret Key fields, enter the access keys for your Amazon EC2 account. For more information, see Managing Access Keys for your AWS Account on the Amazon documentation website.
- Optional: Click Load Regions to populate the Regions list.
- From the Region list, select the Amazon EC2 region or data center to use.
- Click the Locations tab and ensure that the location you want to use is selected, or add a different location.
- Click the Organizations tab and ensure that the organization you want to use is selected, or add a different organization.
- Click Submit to save the Amazon EC2 connection.
- Select the new compute resource and then click the SSH keys tab, and click Download to save a copy of the SSH keys to use for SSH authentication. Until BZ1793138 is resolved, you can download a copy of the SSH keys only immediately after creating the Amazon EC2 compute resource. If you require SSH keys at a later stage, follow the procedure in Section 13.8, “Connecting to an Amazon EC2 instance using SSH”.
CLI procedure
Create the connection with the
hammer compute-resource createcommand. Use--userand--passwordoptions to add the access key and secret key respectively.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.3. Using an HTTP proxy with compute resources
In some cases, the EC2 compute resource that you use might require a specific HTTP proxy to communicate with Satellite. In Satellite, you can create an HTTP proxy and then assign the HTTP proxy to your EC2 compute resource.
However, if you configure an HTTP proxy for Satellite in Administer > Settings, and then add another HTTP proxy for your compute resource, the HTTP proxy that you define in Administer > Settings takes precedence.
Procedure
- In the Satellite web UI, navigate to Infrastructure > HTTP Proxies, and select New HTTP Proxy.
- In the Name field, enter a name for the HTTP proxy.
- In the URL field, enter the URL for the HTTP proxy, including the port number.
- Optional: Enter a username and password to authenticate to the HTTP proxy, if your HTTP proxy requires authentication.
- Click Test Connection to ensure that you can connect to the HTTP proxy from Satellite.
- Click the Locations tab and add a location.
- Click the Organization tab and add an organization.
- Click Submit.
13.4. Creating an image for Amazon EC2
You can create images for Amazon EC2 from within Satellite.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your Amazon EC2 provider.
Click Create Image.
- In the Name field, enter a meaningful and unique name for your EC2 image.
- From the Operating System list, select an operating system to associate with the image.
- From the Architecture list, select an architecture to associate with the image.
- In the Username field, enter the username needed to SSH into the machine.
- In the Image ID field, enter the image ID provided by Amazon or an operating system vendor.
- Optional: Select the User Data check box to enable support for user data input.
- Optional: Set an Iam Role for Fog to use when creating this image.
- Click Submit to save your changes to Satellite.
13.5. Adding Amazon EC2 images to Satellite Server
Amazon EC2 uses image-based provisioning to create hosts. You must add image details to your Satellite Server. This includes access details and image location.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and select an Amazon EC2 connection.
- Click the Images tab, and then click Create Image.
- In the Name field, enter a name to identify the image for future use.
- From the Operating System list, select the operating system that corresponds with the image you want to add.
- From the Architecture list, select the operating system’s architecture.
-
In the Username field, enter the SSH user name for image access. This is normally the
rootuser. - In the Password field, enter the SSH password for image access.
-
In the Image ID field, enter the Amazon Machine Image (AMI) ID for the image. This is usually in the following format:
ami-xxxxxxxx. -
Optional: Select the User Data checkbox if the images support user data input, such as
cloud-initdata. If you enable user data, the Finish scripts are automatically disabled. This also applies in reverse: if you enable the Finish scripts, this disables user data. - Optional: In the IAM role field, enter the Amazon security role used for creating the image.
- Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. Use the--uuidfield to store the full path of the image location on the Amazon EC2 server.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.6. Adding Amazon EC2 details to a compute profile
You can add hardware settings for instances on Amazon EC2 to a compute profile.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles and click the name of your profile, then click an EC2 connection.
- From the Flavor list, select the hardware profile on EC2 to use for the host.
- From the Image list, select the image to use for image-based provisioning.
- From the Availability zone list, select the target cluster to use within the chosen EC2 region.
- From the Subnet list, add the subnet for the EC2 instance. If you have a VPC for provisioning new hosts, use its subnet.
- From the Security Groups list, select the cloud-based access rules for ports and IP addresses to apply to the host.
-
From the Managed IP list, select either a
PublicIP or aPrivateIP. - Click Submit to save the compute profile.
CLI procedure
Set Amazon EC2 details to a compute profile:
hammer compute-profile values create --compute-resource "My_Laptop" \ --compute-profile "My_Compute_Profile" \ --compute-attributes "flavor_id=1,availability_zone= My_Zone,subnet_id=1,security_group_ids=1,managed_ip=public_ip"
# hammer compute-profile values create --compute-resource "My_Laptop" \ --compute-profile "My_Compute_Profile" \ --compute-attributes "flavor_id=1,availability_zone= My_Zone,subnet_id=1,security_group_ids=1,managed_ip=public_ip"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.7. Creating image-based hosts on Amazon EC2
The Amazon EC2 provisioning process creates hosts from existing images on the Amazon EC2 server. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the EC2 connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine-based settings.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. EC2 assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab and confirm that all fields are populated with values.
- Click the Virtual Machine tab and confirm that all fields are populated with values.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save your changes.
This new host entry triggers the Amazon EC2 server to create the instance, using the pre-existing image as a basis for the new volume.
CLI procedure
Create the host with the
hammer host createcommand and include--provision-method imageto use image-based provisioning.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
13.8. Connecting to an Amazon EC2 instance using SSH
You can connect remotely to an Amazon EC2 instance from Satellite Server using SSH. However, to connect to any Amazon Web Services EC2 instance that you provision through Red Hat Satellite, you must first access the private key that is associated with the compute resource in the Foreman database, and use this key for authentication.
Procedure
To locate the compute resource list, on your Satellite Server base system, enter the following command, and note the ID of the compute resource that you want to use:
hammer compute-resource list
# hammer compute-resource listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Connect to the Foreman database as the user
postgres:su - postgres -c psql foreman
# su - postgres -c psql foremanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Select the secret from
key_pairswherecompute_resource_id = 3:select secret from key_pairs where compute_resource_id = 3; secret
# select secret from key_pairs where compute_resource_id = 3; secretCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the key from after
-----BEGIN RSA PRIVATE KEY-----until-----END RSA PRIVATE KEY-----. Create a
.pemfile and paste your key into the file:vim Keyname.pem
# vim Keyname.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that you restrict access to the
.pemfile:chmod 600 Keyname.pem
# chmod 600 Keyname.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow To connect to the Amazon EC2 instance, enter the following command:
ssh -i Keyname.pem ec2-user@example.aws.com
ssh -i Keyname.pem ec2-user@example.aws.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.9. Configuring a finish template for an Amazon Web Service EC2 environment
You can use Red Hat Satellite finish templates during the provisioning of Red Hat Enterprise Linux instances in an Amazon EC2 environment.
If you want to use a Finish template with SSH, Satellite must reside within the EC2 environment and in the correct security group. Satellite currently performs SSH finish provisioning directly, not using Capsule Server. If Satellite Server does not reside within EC2, the EC2 virtual machine reports an internal IP rather than the necessary external IP with which it can be reached.
Procedure
- In the Satellite web UI, navigate to Hosts > Templates > Provisioning Templates.
-
In the Provisioning Templates page, enter
Kickstart default finishinto the search field and click Search. - On the Kickstart default finish template, select Clone.
- In the Name field, enter a unique name for the template.
In the template, prefix each command that requires root privileges with
sudo, except forsubscription-manager registerandyumcommands, or add the following line to run the entire template as the sudo user:sudo -s << EOS _Template_ _Body_ EOS
sudo -s << EOS _Template_ _Body_ EOSCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Click the Association tab, and associate the template with a Red Hat Enterprise Linux operating system that you want to use.
- Click the Locations tab, and add the the location where the host resides.
- Click the Organizations tab, and add the organization that the host belongs to.
- Make any additional customizations or changes that you require, then click Submit to save your template.
- In the Satellite web UI, navigate to Hosts > Operating systems and select the operating system that you want for your host.
- Click the Templates tab, and from the Finish Template list, select your finish template.
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- Click the Parameters tab and navigate to Host parameters.
In Host parameters, click Add Parameter two times to add two new parameter fields. Add the following parameters:
-
In the Name field, enter
activation_keys. In the corresponding Value field, enter your activation key. -
In the Name field, enter
remote_execution_ssh_user. In the corresponding Value field, enterec2-user.
-
In the Name field, enter
- Click Submit to save the changes.
13.10. Deleting a virtual machine on Amazon EC2
You can delete virtual machines running on Amazon EC2 from within Satellite.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your Amazon EC2 provider.
- On the Virtual Machines tab, click Delete from the Actions menu. This deletes the virtual machine from the Amazon EC2 compute resource while retaining any associated hosts within Satellite. If you want to delete an orphaned host, navigate to Hosts > All Hosts and delete the host manually.
Additional resources
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
13.11. More information about Amazon Web Services and Satellite
For information about how to locate Red Hat Gold Images on Amazon Web Services EC2, see How to Locate Red Hat Cloud Access Gold Images on AWS EC2.
For information about how to install and use the Amazon Web Service Client on Linux, see Install the AWS Command Line Interface on Linux in the Amazon Web Services documentation.
For information about importing and exporting virtual machines in Amazon Web Services, see VM Import/Export in the Amazon Web Services documentation.
Chapter 14. Provisioning cloud instances on Google Compute Engine
Satellite can interact with Google Compute Engine (GCE), including creating new virtual machines and controlling their power management states.
You can only use golden images supported by Red Hat with Satellite for creating GCE hosts.
Prerequisites
- Configure a domain and subnet on Satellite. For more information about networking requirements, see Chapter 3, Configuring networking.
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
- In your GCE project, configure a service account with the necessary IAM Compute role. For more information, see Compute Engine IAM roles in the GCE documentation.
-
In your GCE project-wise metadata, set the
enable-oslogintoFALSE. For more information, see Enabling or disabling OS Login in the GCE documentation. -
Optional: If you want to use Puppet with GCE hosts, navigate to Administer > Settings > Puppet and enable the
Use UUID for certificatessetting to configure Puppet to use consistent Puppet certificate IDs. -
Based on your needs, associate a
finishoruser_dataprovisioning template with the operating system you want to use. For more information, see Provisioning Templates in Provisioning hosts.
14.1. Adding a Google GCE connection to Satellite Server
Use this procedure to add Google Compute Engine (GCE) as a compute resource in Satellite. To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In Google GCE, generate a service account key in JSON format. For more information, see Create and manage service account keys in the GCE documentation.
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click Create Compute Resource.
- In the Name field, enter a name for the compute resource.
- From the Provider list, select Google.
- Optional: In the Description field, enter a description for the resource.
- In the JSON key field, click Choose File and locate your service account key for upload from your local machine.
- Click Load Zones to populate the list of zones from your GCE environment.
- From the Zone list, select the GCE zone to use.
- Click Submit.
CLI procedure
- In Google GCE, generate a service account key in JSON format. For more information, see Create and manage service account keys in the GCE documentation.
Copy the file from your local machine to Satellite Server:
scp My_GCE_Key.json root@satellite.example.com:/etc/foreman/My_GCE_Key.json
# scp My_GCE_Key.json root@satellite.example.com:/etc/foreman/My_GCE_Key.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Satellite Server, change the owner for your service account key to the
foremanuser:chown root:foreman /etc/foreman/My_GCE_Key.json
# chown root:foreman /etc/foreman/My_GCE_Key.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Satellite Server, configure permissions for your service account key to ensure that the file is readable:
chmod 0640 /etc/foreman/My_GCE_Key.json
# chmod 0640 /etc/foreman/My_GCE_Key.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow On Satellite Server, restore SELinux context for your service account key:
restorecon -vv /etc/foreman/My_GCE_Key.json
# restorecon -vv /etc/foreman/My_GCE_Key.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
hammer compute-resource createcommand to add a GCE compute resource to Satellite:hammer compute-resource create \ --key-path "/etc/foreman/My_GCE_Key.json" \ --name "My_GCE_Compute_Resource" \ --provider "gce" \ --zone "My_Zone"
# hammer compute-resource create \ --key-path "/etc/foreman/My_GCE_Key.json" \ --name "My_GCE_Compute_Resource" \ --provider "gce" \ --zone "My_Zone"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.2. Adding Google Compute Engine images to Satellite Server
To create hosts using image-based provisioning, you must add information about the image, such as access details and the image location, to your Satellite Server.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click the name of the Google Compute Engine connection.
- Click Create Image.
- In the Name field, enter a name for the image.
- From the Operating System list, select the base operating system of the image.
- From the Architecture list, select the operating system architecture.
-
In the Username field, enter the SSH user name for image access. Specify a user other than
root, because therootuser cannot connect to a GCE instance using SSH keys. The username must begin with a letter and consist of lowercase letters and numbers. - From the Image list, select an image from the Google Compute Engine compute resource.
-
Optional: Select the User Data checkbox if the image supports user data input, such as
cloud-initdata. - Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. With the--usernameoption, specify a user other thanroot, because therootuser cannot connect to a GCE instance using SSH keys. The username must begin with a letter and consist of lowercase letters and numbers.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.3. Adding Google GCE details to a compute profile
Use this procedure to add Google GCE hardware settings to a compute profile. When you create a host on Google GCE using this compute profile, these settings are automatically populated.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles.
- In the Compute Profiles window, click the name of an existing compute profile, or click Create Compute Profile, enter a Name, and click Submit.
- Click the name of the GCE compute resource.
- From the Machine Type list, select the machine type to use for provisioning.
- From the Image list, select the image to use for provisioning.
- From the Network list, select the Google GCE network to use for provisioning.
- Optional: Select the Associate Ephemeral External IP checkbox to assign a dynamic ephemeral IP address that Satellite uses to communicate with the host. This public IP address changes when you reboot the host. If you need a permanent IP address, reserve a static public IP address on Google GCE and attach it to the host.
- In the Size (GB) field, enter the size of the storage to create on the host.
- Click Submit to save the compute profile.
CLI procedure
Create a compute profile to use with the Google GCE compute resource:
hammer compute-profile create --name My_GCE_Compute_Profile
# hammer compute-profile create --name My_GCE_Compute_ProfileCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add GCE details to the compute profile:
hammer compute-profile values create \ --compute-attributes "machine_type=f1-micro,associate_external_ip=true,network=default" \ --compute-profile "My_GCE_Compute_Profile" \ --compute-resource "My_GCE_Compute_Resource" \ --volume "size_gb=20"
# hammer compute-profile values create \ --compute-attributes "machine_type=f1-micro,associate_external_ip=true,network=default" \ --compute-profile "My_GCE_Compute_Profile" \ --compute-resource "My_GCE_Compute_Resource" \ --volume "size_gb=20"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.4. Creating image-based hosts on Google Compute Engine
In Satellite, you can use Google Compute Engine provisioning to create hosts from an existing image. The new host entry triggers the Google Compute Engine server to create the instance using the pre-existing image as a basis for the new volume.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the Google Compute Engine connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine settings.
- From the Lifecycle Environment list, select the environment.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. Google Compute Engine assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- The Domain field is populated with the required domain.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and confirm that all fields automatically contain values.
- Click Resolve in Provisioning templates to check the new host can identify the right provisioning templates to use.
- Click the Virtual Machine tab and confirm that these settings are populated with details from the host group and compute profile. Modify these settings to suit your needs.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save the host entry.
CLI procedure
Create the host with the
hammer host createcommand and include--provision-method image. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
14.5. Deleting a VM on Google GCE
You can delete VMs running on Google GCE on your Satellite Server.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your Google GCE provider.
- On the Virtual Machines tab, click Delete from the Actions menu. This deletes the virtual machine from the Google GCE compute resource while retaining any associated hosts within Satellite. If you want to delete the orphaned host, navigate to Hosts > All Hosts and delete the host manually.
Additional resources
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
Chapter 15. Provisioning cloud instances on Microsoft Azure Resource Manager
Satellite can interact with Microsoft Azure Resource Manager, including creating new virtual machines and controlling their power management states. Only image-based provisioning is supported for creating Azure hosts. This includes provisioning by using Marketplace images, custom images, and shared image gallery.
For more information about Azure Resource Manager concepts, see Azure Resource Manager documentation.
Prerequisites
- You can use synchronized content repositories for Red Hat Enterprise Linux. For more information, see Syncing Repositories in Managing content.
- Provide an activation key for host registration. For more information, see Creating An Activation Key in Managing content.
- Ensure that you have the correct permissions to create an Azure Active Directory application. For more information, see Check Azure AD permissions in the Microsoft identity platform (Azure Active Directory for developers) documentation.
- You must create and configure an Azure Active Directory application and service principle to obtain Application or client ID, Directory or tenant ID, and Client Secret. For more information, see Use the portal to create an Azure AD application and service principal that can access resources in the Microsoft identity platform (Azure Active Directory for developers) documentation.
-
Optional: If you want to use Puppet with Azure hosts, navigate to Administer > Settings > Puppet and enable the
Use UUID for certificatessetting to configure Puppet to use consistent Puppet certificate IDs. -
Based on your needs, associate a
finishoruser_dataprovisioning template with the operating system you want to use. For more information about provisioning templates, see Provisioning Templates. - Optional: If you want the virtual machine to use a static private IP address, create a subnet in Satellite with the Network Address field matching the Azure subnet address.
- Before creating RHEL BYOS images, you must accept the image terms either in the Azure CLI or Portal so that the image can be used to create and manage virtual machines for your subscription.
15.1. Adding a Microsoft Azure Resource Manager connection to Satellite Server
Use this procedure to add Microsoft Azure as a compute resource in Satellite. Note that you must add a separate compute resource for each Microsoft Azure region that you want to use.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click Create Compute Resource.
- In the Name field, enter a name for the compute resource.
- From the Provider list, select Azure Resource Manager.
- Optional: In the Description field, enter a description for the resource.
By default, the Cloud is set to Public/Standard. Azure Government Cloud supports the following regions:
- US Government
- China
- Germany
- In the Client ID field, enter your Application or client ID.
- In the Client Secret field, enter your client secret.
- In the Subscription ID field, enter your subscription ID.
- In the Tenant ID field, enter your Directory or tenant ID.
- Click Load Regions. This tests if your connection to Azure Resource Manager is successful and loads the regions available in your subscription.
- From the Azure Region list, select the Azure region to use.
- Click Submit.
CLI procedure
Use
hammer compute-resource createto add an Azure compute resource to Satellite.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the value for the
--regionoption must be in lowercase and must not contain special characters.
If you are using Azure Government Cloud then you must pass in the --cloud parameter. The values for the cloud parameter are:
| Name of Azure Government Cloud | Value for hammer --cloud |
|---|---|
| US Government | azureusgovernment |
| China | azurechina |
| Germany | azuregermancloud |
15.2. Adding Microsoft Azure Resource Manager images to Satellite Server
To create hosts using image-based provisioning, you must add information about the image, such as access details and the image location, to your Satellite Server.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources and click the name of the Microsoft Azure Resource Manager connection.
- Click Create Image.
- In the Name field, enter a name for the image.
- From the Operating System list, select the base operating system of the image.
- From the Architecture list, select the operating system architecture.
-
In the Username field, enter the SSH user name for image access. You cannot use the
rootuser. - Optional: In the Password field, enter a password to authenticate with.
In the Azure Image Name field, enter an image name in the format
prefix://UUID.-
For a custom image, use the prefix
custom. For example, custom://image-name. -
For a shared gallery image, use the prefix
gallery. For example, gallery://Templates/image-name. For public and RHEL Bring Your Own Subscription (BYOS) images, use the prefix
marketplace. For example, marketplace://OpenLogicCentOS:7.5:latest.For more information, see Find Linux VM images in the Azure Marketplace with the Azure CLI.
-
For a custom image, use the prefix
-
Optional: Select the User Data checkbox if the image supports user data input, such as
cloud-initdata. - Click Submit to save the image details.
CLI procedure
Create the image with the
hammer compute-resource image createcommand. Note that the username that you enter for the image must be the same that you use when you create a host with this image. The--passwordoption is optional when creating an image. You cannot use therootuser.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
15.3. Adding Microsoft Azure Resource Manager details to a compute profile
Use this procedure to add Microsoft Azure hardware settings to a compute profile. When you create a host on Microsoft Azure using this compute profile, these settings are automatically populated.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Profiles.
- In the Compute Profiles window, click the name of an existing compute profile, or click Create Compute Profile, enter a Name, and click Submit.
- Click the name of the Azure compute resource.
- From the Resource group list, select the resource group to provision to.
- From the VM Size list, select a size of a virtual machine to provision.
- From the Platform list, select Linux.
- In the Username field, enter a user name to authenticate with. Note that the username that you enter for compute profile must be the same that you use when creating an image.
To authenticate the user, use one of the following options:
- To authenticate using a password, enter a password in the Password field.
- To authenticate using an SSH key, enter an SSH key in the SSH Key field.
- Optional: If you want the virtual machine to use a premium virtual machine disk, select the Premium OS Disk checkbox.
- From the OS Disk Caching list, select the disc caching setting.
- Optional: In the Custom Script Command field, enter commands to perform on the virtual machine when the virtual machine is provisioned.
-
Optional: If you want to run custom scripts when provisioning finishes, in the Comma separated file URIs field, enter comma-separated file URIs of scripts to use. The scripts must contain
sudoat the beginning because Red Hat Satellite downloads files to the/var/lib/waagent/custom-script/download/0/directory on the host and scripts require sudo privileges to be executed. Optional: You can add a NVIDIA Driver by selecting the NVIDIA driver / CUDA checkbox. For more information, refer to the following Microsoft Azure documentation:
Optional: If you want to create an additional volume on the VM, click the Add Volume button, enter the Size in GB and select the Data Disk Caching method.
- Note that the maximum number of these disks depends on the VM Size selected. For more information on Microsoft Azure VM storage requirements, see the Microsoft Azure documentation.
Click Add Interface.
ImportantThe maximum number of interfaces depends on the VM Size selected. For more information, see the Microsoft Azure documentation link above.
- From the Azure Subnet list, select the Azure subnet to provision to.
- From the Public IP list, select the public IP setting.
- Optional: If you want the virtual machine to use a static private IP, select the Static Private IP checkbox.
- Click Submit.
CLI procedure
Create a compute profile to use with the Azure Resource Manager compute resource:
hammer compute-profile create --name compute_profile_name
# hammer compute-profile create --name compute_profile_nameCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add Azure details to the compute profile. With the
usernamesetting, enter the SSH user name for image access. Note that the username that you enter for compute profile must be the same that you use when creating an image.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: If you want to run scripts on the virtual machine after provisioning, specify the following settings:
-
To enter the script directly, with the
script_commandsetting, enter a command to be executed on the provisioned virtual machine. -
To run a script from a URI, with the
script_urissetting, enter comma-separated file URIs of scripts to use. The scripts must containsudoat the beginning because Red Hat Satellite downloads files to the/var/lib/waagent/custom-script/download/0/directory on the host and therefore scripts require sudo privileges to be executed.
-
To enter the script directly, with the
15.4. Creating image-based hosts on Microsoft Azure Resource Manager
In Satellite, you can use Microsoft Azure Resource Manager provisioning to create hosts from an existing image. The new host entry triggers the Microsoft Azure Resource Manager server to create the instance using the pre-existing image as a basis for the new volume.
To use the CLI instead of the Satellite web UI, see the CLI procedure.
Procedure
- In the Satellite web UI, navigate to Hosts > Create Host.
- In the Name field, enter a name for the host.
- Optional: Click the Organization tab and change the organization context to match your requirement.
- Optional: Click the Location tab and change the location context to match your requirement.
- From the Host Group list, select a host group that you want to assign your host to. That host group will populate the form.
- From the Deploy on list, select the Microsoft Azure Resource Manager connection.
- From the Compute Profile list, select a profile to use to automatically populate virtual machine settings.
- From the Lifecycle Environment list, select the environment.
- Click the Interfaces tab, and on the interface of the host, click Edit.
Verify that the fields are populated with values. Note in particular:
- Satellite automatically assigns an IP address for the new host.
- Ensure that the MAC address field is blank. Microsoft Azure Resource Manager assigns a MAC address to the host during provisioning.
- The Name from the Host tab becomes the DNS name.
- The Azure Subnet field is populated with the required Azure subnet.
- Optional: If you want to use a static private IP address, from the IPv4 Subnet list select the Satellite subnet with the Network Address field matching the Azure subnet address. In the IPv4 Address field, enter an IPv4 address within the range of your Azure subnet.
- Ensure that Satellite automatically selects the Managed, Primary, and Provision options for the first interface on the host. If not, select them.
- Click OK to save. To add another interface, click Add Interface. You can select only one interface for Provision and Primary.
- Click the Operating System tab, and confirm that all fields automatically contain values.
- For Provisioning Method, ensure Image Based is selected.
- From the Image list, select the Azure Resource Manager image that you want to use for provisioning.
- In the Root Password field, enter the root password to authenticate with.
- Click Resolve in Provisioning templates to check the new host can identify the right provisioning templates to use.
- Click the Virtual Machine tab and confirm that these settings are populated with details from the host group and compute profile. Modify these settings to suit your needs.
-
On the Parameters tab, click Add parameter. Add a parameter named
kt_activation_keys, select the string type, and enter the name of the activation key as the value. The activation key has to belong to the same organization as your host. You can also enter a comma-separated list of multiple activation keys. - Click Submit to save the host entry.
CLI procedure
Create the host with the
hammer host createcommand and include--provision-method image. Replace the values in the following example with the appropriate values for your environment.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For more information about additional host creation parameters for this compute resource, enter the hammer host create --help command.
15.5. Deleting a VM on Microsoft Azure
You can delete VMs running on Microsoft Azure from within Satellite.
Procedure
- In the Satellite web UI, navigate to Infrastructure > Compute Resources.
- Select your Microsoft Azure provider.
- On the Virtual Machines tab, click Delete from the Actions menu. This deletes the virtual machine from the Microsoft Azure compute resource while retaining any associated hosts within Satellite. If you want to delete the orphaned host, navigate to Hosts > All Hosts and delete the host manually.
Additional resources
- You can configure Satellite to remove the associated virtual machine when you delete a host. For more information, see Section 2.22, “Removing a virtual machine upon host deletion”.
Appendix A. Initialization script for provisioning examples
If you have not followed the examples in Managing content, you can use the following initialization script to create an environment for provisioning examples.
Procedure
Create a script file (
content-init.sh) and include the following:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set executable permissions on the script:
chmod +x content-init.sh
# chmod +x content-init.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow Download a copy of your Red Hat Subscription Manifest from the Red Hat Customer Portal and run the script on the manifest:
./content-init.sh manifest_98f4290e-6c0b-4f37-ba79-3a3ec6e405ba.zip
# ./content-init.sh manifest_98f4290e-6c0b-4f37-ba79-3a3ec6e405ba.zipCopy to Clipboard Copied! Toggle word wrap Toggle overflow This imports the necessary Red Hat content for the provisioning examples in this guide.
Appendix B. Provisioning FIPS-compliant hosts
Satellite supports provisioning hosts that comply with the National Institute of Standards and Technology’s Security Requirements for Cryptographic Modules standard, reference number FIPS 140-2, referred to here as FIPS.
To enable the provisioning of hosts that are FIPS-compliant, complete the following tasks:
- Change the provisioning password hashing algorithm for the operating system
- Create a host group and set a host group parameter to enable FIPS
For more information, see Creating a Host Group in Managing hosts.
The provisioned hosts have the FIPS-compliant settings applied. To confirm that these settings are enabled, complete the steps in Section B.3, “Verifying FIPS mode is enabled”.
B.1. Changing the provisioning password hashing algorithm
To provision FIPS-compliant hosts, you must first set the password hashing algorithm that you use in provisioning to SHA256. This configuration setting must be applied for each operating system you want to deploy as FIPS-compliant.
Procedure
Identify the Operating System IDs:
hammer os list
# hammer os listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update each operating system’s password hash value.
hammer os update \ --password-hash SHA256 --title "My_Operating_System"
# hammer os update \ --password-hash SHA256 --title "My_Operating_System"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that you cannot use a comma-separated list of values.
B.2. Setting the FIPS-enabled parameter
To provision a FIPS-compliant host, you must create a host group and set the host group parameter fips_enabled to true. If this is not set to true, or is absent, the FIPS-specific changes do not apply to the system. You can set this parameter when you provision a host or for a host group.
To set this parameter when provisioning a host, append --parameters fips_enabled=true to the Hammer command.
hammer hostgroup set-parameter \ --hostgroup "My_Host_Group" \ --name fips_enabled \ --value "true"
# hammer hostgroup set-parameter \
--hostgroup "My_Host_Group" \
--name fips_enabled \
--value "true"
For more information, see the output of the command hammer hostgroup set-parameter --help.
B.3. Verifying FIPS mode is enabled
To verify these FIPS compliance changes have been successful, you must provision a host and check its configuration.
Procedure
-
Log in to the host as
rootor with an admin-level account. Enter the following command:
cat /proc/sys/crypto/fips_enabled
$ cat /proc/sys/crypto/fips_enabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow A value of
1confirms that FIPS mode is enabled.
Appendix C. Building cloud images for Red Hat Satellite
Use this section to build and register images to Red Hat Satellite.
You can use a preconfigured Red Hat Enterprise Linux KVM guest QCOW2 image:
These images contain cloud-init. To function properly, they must use ec2-compatible metadata services for provisioning an SSH key.
For the KVM guest images:
-
The
rootaccount in the image is disabled, butsudoaccess is granted to a special user namedcloud-user. -
There is no
rootpassword set for this image. Therootpassword is locked in/etc/shadowby placing!!in the second field.
If you want to create custom Red Hat Enterprise Linux images, see Composing a customized Red Hat Enterprise Linux 9 Image or Composing a customized Red Hat Enterprise Linux 8 Image.
C.1. Creating custom Red Hat Enterprise Linux images
Prerequisites
- Use a Linux host machine to create an image. In this example, we use a Red Hat Enterprise Linux 7 Workstation.
-
Use
virt-manageron your workstation to complete this procedure. If you create the image on a remote server, connect to the server from your workstation withvirt-manager. - A Red Hat Enterprise Linux 7 ISO file (see Red Hat Enterprise Linux 7.4 Binary DVD).
For more information about installing a Red Hat Enterprise Linux Workstation, see the Red Hat Enterprise Linux 7 Installation Guide.
Before you can create custom images, install the following packages:
Install
libvirt,qemu-kvm, and graphical tools:yum install virt-manager virt-viewer libvirt qemu-kvm
# yum install virt-manager virt-viewer libvirt qemu-kvmCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the following command line tools:
yum install virt-install libguestfs-tools-c
# yum install virt-install libguestfs-tools-cCopy to Clipboard Copied! Toggle word wrap Toggle overflow
In the following procedures, enter all commands with the [root@host]# prompt on the workstation that hosts the libvirt environment.
C.2. Supported clients in registration
Satellite supports the following operating systems and architectures for registration.
- Supported host operating systems
The hosts can use the following operating systems:
- Red Hat Enterprise Linux 9 and 8
- Red Hat Enterprise Linux 7 with the ELS Add-On
- Supported host architectures
The hosts can use the following architectures:
- AMD and Intel 64-bit architectures
- The 64-bit ARM architecture
- IBM Power Systems, Little Endian
- 64-bit IBM Z architectures
C.3. Configuring a host for registration
Configure your host for registration to Satellite Server or Capsule Server. You can use a configuration management tool to configure multiple hosts at once.
Prerequisites
- The host must be using a supported operating system. For more information, see Section C.2, “Supported clients in registration”.
- The system clock on your Satellite Server and any Capsule Servers must be synchronized across the network. If the system clock is not synchronized, SSL certificate verification might fail. For example, you can use the Chrony suite for timekeeping.
Procedure
Enable and start a time-synchronization tool on your host. The host must be synchronized with the same NTP server as Satellite Server and any Capsule Servers.
systemctl enable --now chronyd
# systemctl enable --now chronydCopy to Clipboard Copied! Toggle word wrap Toggle overflow Deploy the SSL CA file on your host so that the host can make a secured registration call.
- Find where Satellite stores the SSL CA file by navigating to Administer > Settings > Authentication and locating the value of the SSL CA file setting.
-
Transfer the SSL CA file to your host securely, for example by using
scp. - Login to your host by using SSH.
Copy the certificate to the truststore:
cp My_SSL_CA_file.pem /etc/pki/ca-trust/source/anchors
# cp My_SSL_CA_file.pem /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update the truststore:
update-ca-trust
# update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow
C.4. Registering a host
You can register a host by using registration templates and set up various integration features and host tools during the registration process.
Prerequisites
- Your Satellite account has the Register hosts role assigned or a role with equivalent permissions.
- You must have root privileges on the host that you want to register.
- You have configured the host for registration. For more information, see Section C.3, “Configuring a host for registration”.
- An activation key must be available for the host. For more information, see Managing Activation Keys in Managing content.
-
Optional: If you want to register hosts to Red Hat Insights, you must synchronize the
rhel-8-for-x86_64-baseos-rpmsandrhel-8-for-x86_64-appstream-rpmsrepositories and make them available in the activation key that you use. This is required to install theinsights-clientpackage on hosts. - Red Hat Satellite Client 6 repository for the operating system version of the host is synchronized on Satellite Server and enabled in the activation key you use. For more information, see Importing Content in Managing content. This repository is required for the remote execution pull client, Puppet agent, Tracer, and other tools.
If you want to use Capsule Servers instead of your Satellite Server, ensure that you have configured your Capsule Servers accordingly.
ImportantIt is essential to add your Capsule Server to the list of trusted proxies on Satellite Server!
For more information, see Configuring Capsule for Host Registration and Provisioning in Installing Capsule Server.
- If your Satellite Server or Capsule Server is behind an HTTP proxy, configure the Subscription Manager on your host to use the HTTP proxy for connection. For more information, see How to access Red Hat Subscription Manager (RHSM) through a firewall or proxy in the Red Hat Knowledgebase.
Procedure
- In the Satellite web UI, navigate to Hosts > Register Host.
- Enter the details for how you want the registered hosts to be configured.
- On the General tab, in the Activation Keys field, enter one or more activation keys to assign to hosts.
-
Click Generate to generate a
curlcommand. -
Run the
curlcommand asrooton the host that you want to register. After registration completes, any Ansible roles assigned to a host group you specified when configuring the registration template will run on the host.
The registration details that you can specify include the following:
- On the General tab, in the Capsule field, you can select the Capsule to register hosts through. A Capsule behind a load balancer takes precedence over a Capsule selected in the Satellite web UI as the content source of the host.
On the General tab, you can select the Insecure option to make the first call insecure. During this first call, the host downloads the CA file from Satellite. The host will use this CA file to connect to Satellite with all future calls making them secure.
Red Hat recommends that you avoid insecure calls.
If an attacker, located in the network between Satellite and a host, fetches the CA file from the first insecure call, the attacker will be able to access the content of the API calls to and from the registered host and the JSON Web Tokens (JWT). Therefore, if you have chosen to deploy SSH keys during registration, the attacker will be able to access the host using the SSH key.
- On the Advanced tab, in the Repositories field, you can list repositories to be added before the registration is performed. You do not have to specify repositories if you provide them in an activation key.
On the Advanced tab, in the Token lifetime (hours) field, you can change the validity duration of the JSON Web Token (JWT) that Satellite uses for authentication. The duration of this token defines how long the generated
curlcommand works.Note that Satellite applies the permissions of the user who generates the
curlcommand to authorization of hosts. If the user loses or gains additional permissions, the permissions of the JWT change too. Therefore, do not delete, block, or change permissions of the user during the token duration.The scope of the JWTs is limited to the registration endpoints only and cannot be used anywhere else.
CLI procedure
-
Use the
hammer host-registration generate-commandto generate thecurlcommand to register the host. -
On the host that you want to register, run the
curlcommand asroot.
For more information, see the Hammer CLI help with hammer host-registration generate-command --help.
Ansible procedure
-
Use the
redhat.satellite.registration_commandmodule.
For more information, see the Ansible module documentation with ansible-doc redhat.satellite.registration_command.
API procedure
-
Use the
POST /api/registration_commandsresource.
For more information, see the full API reference at https://satellite.example.com/apidoc/v2.html.
C.5. Installing and configuring Puppet agent manually
You can install and configure the Puppet agent on a host manually. A configured Puppet agent is required on the host for Puppet integration with your Satellite. For more information about Puppet, see Managing configurations by using Puppet integration.
Prerequisites
- Puppet must be enabled in your Satellite. For more information, see Enabling Puppet Integration with Satellite in Managing configurations by using Puppet integration.
- The host must have a Puppet environment assigned to it.
- Red Hat Satellite Client 6 repository for the operating system version of the host is synchronized on Satellite Server, available in the content view and the lifecycle environment of the host, and enabled for the host. For more information, see Changing the repository sets status for a host in Satellite in Managing content.
Procedure
-
Log in to the host as the
rootuser. Install the Puppet agent package.
On hosts running Red Hat Enterprise Linux 8 and above:
dnf install puppet-agent
# dnf install puppet-agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow On hosts running Red Hat Enterprise Linux 7 and below:
yum install puppet-agent
# yum install puppet-agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Add the Puppet agent to
PATHin your current shell using the following script:. /etc/profile.d/puppet-agent.sh
. /etc/profile.d/puppet-agent.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure the Puppet agent. Set the
environmentparameter to the name of the Puppet environment to which the host belongs:puppet config set server satellite.example.com --section agent puppet config set environment My_Puppet_Environment --section agent
# puppet config set server satellite.example.com --section agent # puppet config set environment My_Puppet_Environment --section agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start the Puppet agent service:
puppet resource service puppet ensure=running enable=true
# puppet resource service puppet ensure=running enable=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a certificate for the host:
puppet ssl bootstrap
# puppet ssl bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow - In the Satellite web UI, navigate to Infrastructure > Capsules.
- From the list in the Actions column for the required Capsule Server, select Certificates.
- Click Sign to the right of the required host to sign the SSL certificate for the Puppet agent.
On the host, run the Puppet agent again:
puppet ssl bootstrap
# puppet ssl bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
C.6. Completing the Red Hat Enterprise Linux 7 image
Procedure
Update the system:
yum update
# yum updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the
cloud-initpackages:yum install cloud-utils-growpart cloud-init
# yum install cloud-utils-growpart cloud-initCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the
/etc/cloud/cloud.cfgconfiguration file:vi /etc/cloud/cloud.cfg
# vi /etc/cloud/cloud.cfgCopy to Clipboard Copied! Toggle word wrap Toggle overflow Under the heading
cloud_init_modules, add:- resolv-conf
- resolv-confCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
resolv-confoption automatically configures theresolv.confwhen an instance boots for the first time. This file contains information related to the instance such asnameservers,domainand other options.Open the
/etc/sysconfig/networkfile:vi /etc/sysconfig/network
# vi /etc/sysconfig/networkCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the following line to avoid problems accessing the EC2 metadata service:
NOZEROCONF=yes
NOZEROCONF=yesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Un-register the virtual machine so that the resulting image does not contain the same subscription details for every instance cloned based on it:
subscription-manager repos --disable=* subscription-manager unregister
# subscription-manager repos --disable=* # subscription-manager unregisterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Power off the instance:
poweroff
# poweroffCopy to Clipboard Copied! Toggle word wrap Toggle overflow On your Red Hat Enterprise Linux Workstation, connect to the terminal as the root user and navigate to the
/var/lib/libvirt/images/directory:cd /var/lib/libvirt/images/
# cd /var/lib/libvirt/images/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reset and clean the image using the
virt-sysprepcommand so it can be used to create instances without issues:virt-sysprep -d rhel7
# virt-sysprep -d rhel7Copy to Clipboard Copied! Toggle word wrap Toggle overflow Reduce image size using the
virt-sparsifycommand. This command converts any free space within the disk image back to free space within the host:virt-sparsify --compress rhel7.qcow2 rhel7-cloud.qcow2
# virt-sparsify --compress rhel7.qcow2 rhel7-cloud.qcow2Copy to Clipboard Copied! Toggle word wrap Toggle overflow This creates a new
rhel7-cloud.qcow2file in the location where you enter the command.
C.7. Next steps
- Repeat the procedures for every image that you want to provision with Satellite.
- Move the image to the location where you want to store for future use.
Appendix D. Host parameter hierarchy
You can access host parameters when provisioning hosts. Hosts inherit their parameters from the following locations, in order of increasing precedence:
| Parameter Level | Set in Satellite web UI |
|---|---|
| Globally defined parameters | Configure > Global parameters |
| Organization-level parameters | Administer > Organizations |
| Location-level parameters | Administer > Locations |
| Domain-level parameters | Infrastructure > Domains |
| Subnet-level parameters | Infrastructure > Subnets |
| Operating system-level parameters | Hosts > Provisioning Setup > Operating Systems |
| Host group-level parameters | Configure > Host Groups |
| Host parameters | Hosts > All Hosts |
Appendix E. Permissions required to provision hosts
The following list provides an overview of the permissions a non-admin user requires to provision hosts.
| Resource name | Permissions | Additional details |
|---|---|---|
| Activation Keys | view_activation_keys | |
| Ansible role | view_ansible_roles | Required if Ansible is used. |
| Architecture | view_architectures | |
| Compute profile | view_compute_profiles | |
| Compute resource | view_compute_resources, create_compute_resources, destroy_compute_resources, power_compute_resources | Required to provision bare-metal hosts. |
| view_compute_resources_vms, create_compute_resources_vms, destroy_compute_resources_vms, power_compute_resources_vms | Required to provision virtual machines. | |
| Content Views | view_content_views | |
| Domain | view_domains | |
| Environment | view_environments | |
| Host | view_hosts, create_hosts, edit_hosts, destroy_hosts, build_hosts, power_hosts, play_roles_on_host | |
| view_discovered_hosts, submit_discovered_hosts, auto_provision_discovered_hosts, provision_discovered_hosts, edit_discovered_hosts, destroy_discovered_hosts | Required if the Discovery service is enabled. | |
| Hostgroup | view_hostgroups, create_hostgroups, edit_hostgroups, play_roles_on_hostgroup | |
| Image | view_images | |
| Lifecycle environment | view_lifecycle_environments | |
| Location | view_locations | |
| Medium | view_media | |
| Operatingsystem | view_operatingsystems | |
| Organization | view_organizations | |
| Parameter | view_params, create_params, edit_params, destroy_params | |
| Product and Repositories | view_products | |
| Provisioning template | view_provisioning_templates | |
| Ptable | view_ptables | |
| Capsule | view_smart_proxies, view_smart_proxies_puppetca | |
| view_openscap_proxies | Required if the OpenSCAP plugin is enabled. | |
| Subnet | view_subnets |