Chapter 6. Managing Security Compliance
Security compliance management is the ongoing process of defining security policies, auditing for compliance with those policies and resolving instances of non-compliance. Any non-compliance is managed according to the organization’s configuration management policies. Security policies range in scope from host-specific to industry-wide, therefore, flexibility in their definition is required.
6.1. Security Content Automation Protocol
Satellite 6 uses the Security Content Automation Protocol (SCAP) to define security configuration policies. For example, a security policy might specify that for hosts running Red Hat Enterprise Linux, login via SSH is not permitted for the root account. With Satellite 6 you can schedule compliance auditing and reporting on all hosts under management. For more information about SCAP, see the Red Hat Enterprise Linux 7 Security Guide.
6.1.1. SCAP Content
SCAP content is a datastream format containing the configuration and security baseline against which hosts are checked. Checklists are described in the extensible checklist configuration description format (XCCDF) and vulnerabilities in the open vulnerability and assessment language (OVAL). Checklist items, also known as rules express the desired configuration of a system item. For example, you may specify that no one can log in to a host over SSH using the root user account. Rules can be grouped into one or more profiles, allowing multiple profiles to share a rule. SCAP content consists of both rules and profiles.
You can either create SCAP content or obtain it from a vendor. Supported profiles are provided for Red Hat Enterprise Linux in the scap-security-guide package. The creation of SCAP content is outside the scope of this guide, but see the Red Hat Enterprise Linux 7 Security Guide for information on how to download, deploy, modify, and create your own content.
The default SCAP content provided with the OpenSCAP components of Satellite 6 depends on the version of Red Hat Enterprise Linux. On Red Hat Enterprise Linux 7, content for both Red Hat Enterprise Linux 6 and Red Hat Enterprise Linux 7 is installed.
6.1.2. XCCDF Profile
An XCCDF profile is a checklist against which a host or host group is evaluated. Profiles are created to verify compliance with an industry standard or custom standard.
The profiles provided with Satellite 6 are obtained from the OpenSCAP project.
6.1.2.1. Listing Available XCCDF Profiles
In the Satellite UI, list the available XCCD profiles.
Procedure
- Navigate to Hosts > SCAP contents.
6.2. Configuring SCAP Content
6.2.1. Importing OpenSCAP Puppet Modules
If you do not use Puppet to configure OpenSCAP auditing on hosts, you can skip this procedure.
To audit hosts with OpenSCAP, you must first import a Puppet environment. The Puppet environment contains the Puppet classes you must assign to each host to deploy the OpenSCAP configuration.
You must associate each host that you want to audit with the Puppet environment in the Satellite web UI.
Procedure
- In the Satellite web UI, navigate to Configure > Environments.
- Click Import environments from satellite.example.com.
Select the Puppet environment check box associated with the host you want to audit.
If no Puppet environment exists, select the production environment check box. The Puppet classes that you require for OpenSCAP are in the production environment by default.
- Click Update.
6.2.2. Loading the Default OpenSCAP Content
In the CLI, load the default OpenScap content.
Procedure
Use the
foreman-rakecommand:# foreman-rake foreman_openscap:bulk_upload:default
6.2.3. Extra SCAP Content
You can upload extra SCAP content into the Satellite Server, either content created by yourself or obtained elsewhere. SCAP content must be imported into the Satellite Server before being applied in a policy. For example, the scap-security-guide RPM package available in the Red Hat Enterprise Linux 7.2 repositories includes a profile for the Payment Card Industry Data Security Standard (PCI-DSS) version 3. You can upload this content into a Satellite Server even if it is not running Red Hat Enterprise Linux 7.2 as the content is not specific to an operating system version.
6.2.3.1. Uploading Extra SCAP Content
In the Satellite web UI, upload the extra SCAP content.
Procedure
- Navigate to Hosts > SCAP contents and click New SCAP Content.
Enter a title in the Title text box.
Example:
RHEL 7.2 SCAP Content.- Click Choose file, navigate to the location containing the SCAP content file and select Open.
- Click Submit.
If the SCAP content file is loaded successfully, a message similar to Successfully created RHEL 7.2 SCAP Content is shown and the list of SCAP Contents includes the new title.
6.3. Managing Compliance Policies
6.3.1. Compliance Policy
A scheduled audit, also known as a compliance policy, is a scheduled task that checks the specified hosts for compliance against an XCCDF profile. The schedule for scans is specified by the Satellite Server and the scans are performed on the host. When a scan completes, an Asset Reporting File (ARF) is generated in XML format and uploaded to the Satellite Server. You can see the results of the scan in the compliance policy dashboard. No changes are made to the scanned host by the compliance policy. The SCAP content includes several profiles with associated rules but policies are not included by default.
6.3.2. Creating a Compliance Policy
With Satellite 6, you can create a compliance policy to scan your content hosts to ensure that the hosts remain compliant to your security requirements.
You can use either Puppet or Ansible to deploy the compliance policy to your hosts. Note that Puppet runs by default every 30 minutes. If you assign a new policy, the next Puppet run synchronizes the policy to the host. However Ansible does not perform scheduled runs. To add a new policy, you must run Ansible role manually or using remote execution. For more information about remote execution, see Configuring and Setting up Remote Jobs in the Managing Hosts guide.
Prerequisites
Before you begin, you must decide whether you want to use a Puppet or Ansible deployment.
- For Puppet deployment, ensure that each host that you want to audit is associated with a Puppet environment. For more information, see Section 6.2.1, “Importing OpenSCAP Puppet Modules”.
-
For Ansible deployment, ensure that you import the
theforeman.foreman_scap_clientAnsible role. For more information about importing Ansible roles, see Getting Started with Ansible in Satellite in Configuring Satellite to use Ansible.
Procedure
- Navigate to Hosts > Policies, and select whether you want a manual, Ansible, or Puppet deployment.
- Enter a name for this policy, a description (optional), then click Next.
Select the SCAP Content and XCCDF Profile to be applied, then click Next.
Until BZ#1704582 is resolved, note that the
Default XCCDF Profilemight return an empty report.Specify the scheduled time when the policy is to be applied, then click Next.
Select Weekly, Monthly, or Custom from the Period list.
- If you select Weekly, also select the desired day of the week from the Weekday list.
- If you select Monthly, also specify the desired day of the month in the Day of month field.
If you select Custom, enter a valid Cron expression in the Cron line field.
The Custom option allows for greater flexibility in the policy’s schedule than either the Weekly or Monthly options.
- Select the locations to which the policy is to be applied, then click Next.
- Select the organizations to which the policy is to be applied, then click Next.
- Select the host groups to which the policy is to be applied, then click Submit.
When the Puppet agent runs on the hosts which belong to the selected host group, or hosts to which the policy has been applied, the OpenSCAP client will be installed and a Cron job added with the policy’s specified schedule. The SCAP Content tab provides the name of the SCAP content file which will be distributed to the directory /var/lib/openscap/content/ on all target hosts.
6.3.3. Viewing a Compliance Policy
You can preview the rules which will be applied by specific OpenSCAP content and profile combination. This is useful when planning policies.
In the Satellite web UI, view the compliance policy.
Procedure
- Navigate to Hosts > Policies.
- Click Show Guide.
6.3.4. Editing a Compliance Policy
In the Satellite web UI, edit the compliance policy.
Procedure
- Navigate to Hosts > Policies.
- From the drop-down list to the right of the policy’s name, select Edit.
- Edit the necessary attributes.
- Click Submit.
An edited policy is applied to the host when its Puppet agent next checks with the Satellite Server for updates. By default this occurs every 30 minutes.
6.3.5. Deleting a Compliance Policy
In the Satellite web UI, delete an existing policy.
- Navigate to Hosts > Policies.
- From the drop-down list to the right of the policy’s name, select Delete.
- Click OK in the confirmation message.
6.4. Tailoring Files
Tailoring Files allow existing OpenSCAP policies to be customized without forking or rewriting the policy. You can assign a Tailoring File to a policy when creating or updating a policy.
You can create a Tailoring File using the SCAP Workbench. For more information on using the SCAP Workbench tool, see Customizing SCAP Security Guide for your use-case.
6.4.1. Uploading a Tailoring File
In the Satellite web UI, upload a Tailoring file.
Procedure
- Navigate to Hosts > Compliance - Tailoring Files and click New Tailoring File.
- Enter a name in the Name text box.
- Click Choose File, navigate to the location containing the SCAP DataStream Tailoring File and select Open.
- Click Submit to upload the chosen Tailoring File.
6.4.2. Assigning a Tailoring File to a Policy
In the Satellite web UI, assign a Tailoring file to a policy.
Procedure
- Navigate to Hosts > Compliance - Policies.
- Click New Policy, or New Compliance Policy if there are existing Compliance Policies.
- Enter a name in the Name text box, and click Next.
- Select a Scap content from the dropdown menu.
- Select a XCCDF Profile from the dropdown menu.
- Select a Tailoring File from the dropdown menu.
Select a XCCDF Profile in Tailoring File from the dropdown menu.
It is important to select the XCCDF Profile because Tailoring Files are able to contain multiple XCCDF Profiles.
- Click Next.
- Select a Period from the dropdown menu.
- Select a Weekday from the dropdown menu, and click Next.
- Select a Location to move it to the Selected Items window, and click Next.
- Select an Organization to move it to the Selected Items window, and click Next.
- Select a Hostgroup to move it to the Selected Items window, and click Submit.
6.5. Configuring a host group for OpenSCAP
Use this procedure to configure all the OpenSCAP requirements for a host group.
OpenSCAP Setup Overview
You must complete the following tasks on Satellite Server to assign the necessary components for a host group:
- Enable OpenSCAP on Capsule. For more information, see Enabling OpenSCAP on External Capsules in the Installing Capsule Server guide.
- Assign an OpenSCAP Capsule.
- Assign a Puppet environment that contains the Puppet classes to deploy the OpenSCAP policies.
-
Assign the
foreman_scap_clientandforeman_scap_client::paramsPuppet classes. - Assign any compliance policies that you want to add.
For information about creating and administering hosts, see the Managing Hosts guide.
Procedure
- In the Satellite web UI, navigate to Configure > Host Groups, and either create a host group or click the host group that you want to configure for OpenSCAP reporting.
-
From the Puppet Environment list, select the Puppet environment that contains the
foreman_scap_clientandforeman_scap_client::paramsPuppet classes. - From the OpenSCAP Capsule list, select the Capsule with OpenSCAP enabled that you want to use.
-
Click the Puppet Classes tab, and add the
foreman_scap_clientandforeman_scap_client::paramsPuppet classes. - Click Submit to save your changes.
- Navigate to Hosts > Policies.
- Select the policy that you want to assign to the host group.
- Click the Host Groups tab.
- From the Host Groups list, select as many host groups as you want to assign to this policy.
- Click Submit to save your changes.
6.6. Configuring a host for OpenSCAP
Use this procedure to configure all the OpenSCAP requirements for a host.
OpenSCAP Setup Overview
You must complete the following tasks on Satellite Server to assign the necessary components for a host:
- Enable OpenSCAP on Capsule. For more information, see Enabling OpenSCAP on External Capsules in the Installing Capsule Server guide.
- Assign an OpenSCAP Capsule.
- Assign a Puppet environment that contains the Puppet classes to deploy the OpenSCAP policies.
-
Assign the
foreman_scap_clientandforeman_scap_client::paramsPuppet classes. - Assign any compliance policies that you want to add.
For information about creating and administering hosts, see the Managing Hosts guide.
Procedure
- In the Satellite web UI, navigate to Hosts > All Hosts, and select Edit on the host you want to configure for OpenSCAP reporting.
-
From the Puppet Environment list, select the Puppet environment that contains the
foreman_scap_clientandforeman_scap_client::paramsPuppet classes. - From the OpenSCAP Capsule list, select the Capsule with OpenSCAP enabled that you want to use.
-
Click the Puppet Classes tab, and add the
foreman_scap_clientandforeman_scap_client::paramsPuppet classes. - To add a compliance policy, navigate to one of the following locations:
- Navigate to Hosts > All Hosts.
- Select the host or hosts to which you want to add the policy.
- Click Select Action.
- Select Assign Compliance Policy from the list.
- In the Policy window, select the policy that you want from the list of available policies and click Submit.
6.7. Monitoring Compliance
Red Hat Satellite 6 enables centralized compliance monitoring and management. A compliance dashboard provides an overview of compliance of hosts and the ability to view details for each host within the scope of that policy. Compliance reports provide a detailed analysis of compliance of each host with the applicable policy. With this information, you can evaluate the risks presented by each host and manage the resources required to bring hosts into compliance.
Common objectives when monitoring compliance using SCAP include the following:
- Verifying policy compliance.
- Detecting changes in compliance.
6.7.1. Compliance Policy Dashboard
The compliance policy dashboard provides a statistical summary of compliance of hosts and the ability to view details for each host within the scope of that policy. For all hosts which were evaluated as non-compliant, the Failed statistic provides a useful metric for prioritizing compliance effort. The hosts detected as Never audited should also be a priority, since their status is unknown.
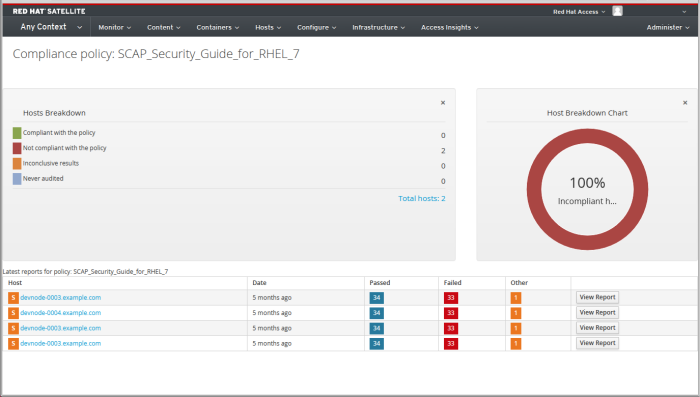
6.7.2. Viewing the Compliance Policy Dashboard
Use the Satellite web UI to verify policy compliance with the compliance policy dashboard.
Procedure
- In the Satellite web UI, navigate to Hosts > Policies.
Click the required policy name. The dashboard provides the following information:
- A ring chart illustrating a high-level view of compliance of hosts with the policy.
- A statistical breakdown of compliance of hosts with the policy, in a tabular format.
- Links to the latest policy report for each host.
6.7.3. Compliance Email Notifications
The Satellite Server sends an OpenSCAP Summary email to all users who subscribe to the Openscap policy summary email notifications. For more information on subscribing to email notifications, see Section 5.1.7, “Configuring Email Notifications”. Each time a policy is run, Satellite checks the results against the previous run, noting any changes between them. The email is sent according to the frequency requested by each subscriber, providing a summary of each policy and its most recent result.
An OpenSCAP Summary email message contains the following information:
- Details of the time period it covers.
- Totals for all hosts by status: changed, compliant, and noncompliant.
- A tabular breakdown of each host and the result of its latest policy, including totals of the rules that passed, failed, changed, or where results were unknown.
6.7.4. Compliance Report
A compliance report is the output of a policy run against a host. Each report includes the total number of rules passed or failed per policy. By default, reports are listed in descending date order.
In the Satellite web UI, navigate to Hosts > Reports to list all compliance reports.
A compliance report consists of the following areas:
- Introduction
- Evaluation Characteristics
- Compliance and Scoring
- Rule Overview
Evaluation Characteristics
The Evaluation Characteristics area provides details about an evaluation against a specific profile, including the host that was evaluated, the profile used in the evaluation, and when the evaluation started and finished. For reference, the IPv4, IPv6, and MAC addresses of the host are also listed.
| Name | Description | Example |
|---|---|---|
| Target machine | The fully-qualified domain name (FQDN) of the evaluated host. |
|
| Benchmark URL | The URL of the SCAP content against which the host was evaluated. |
|
| Benchmark ID | The identifier of the benchmark against which the host was evaluated. A benchmark is a set of profiles |
|
| Profile ID | The identifier of the profile against which the host was evaluated. |
|
| Started at | The date and time at which the evaluation started, in ISO 8601 format. |
|
| Finished at | The date and time at which the evaluation finished, in ISO 8601 format. |
|
| Performed by | The local account name under which the evaluation was performed on the host. |
|
Compliance and Scoring
The Compliance and Scoring area provides an overview of whether or not the host is in compliance with the profile rules, a breakdown of compliance failures by severity, and an overall compliance score as a percentage. If compliance with a rule was not checked, this is categorized in the Rule results field as Other.
Rule Overview
The Rule Overview area provides details about every rule and the compliance result, with the rules presented in a hierarchical layout.
Select or clear the check boxes to narrow the list of rules included in the compliance report. For example, if the focus of your review is any non-compliance, clear the pass and informational check boxes.
To search all rules, enter a criterion in the Search field. The search is dynamically applied as you type. The Search field only accepts a single plain-text search term and it is applied as a case-insensitive search. When you perform a search, only those rules whose descriptions match the search criterion will be listed. To remove the search filter, delete the search criterion.
For an explanation of each result, hover the cursor over the status shown in the Result column.
6.7.5. Examining Compliance Failure of Hosts
Use the Satellite web UI to determine why a host failed compliance on a rule.
Procedure
- In the Satellite web UI, navigate to Hosts > Reports to list all compliance reports.
- Click View Report in the row of the specific host to view the details of an individual report.
Click on the rule’s title to see further details:
- A description of the rule with instructions for bringing the host into compliance if available.
- The rationale for the rule.
- In some cases, a remediation script.
Do not implement any of the recommended remedial actions or scripts without first testing them in a non-production environment.
6.7.6. Searching Compliance Reports
Use the Compliance Reports search field to filter the list of available reports on any given subset of hosts.
Procedure
- To apply a filter, enter the search query in the Search field and click Search. The search query is case insensitive.
Search Use Cases
The following search query finds all compliance reports for which more than five rules failed:
failed > 5
The following search query finds all compliance reports created after January 1, YYYY, for hosts with host names that contain the
prod-group of characters:host ~ prod- AND date > "Jan 1, YYYY"The following search query finds all reports generated by the
rhel7_auditcompliance policy from an hour ago:"1 hour ago" AND compliance_policy = date = "1 hour ago" AND compliance_policy = rhel7_audit
The following search query finds reports that pass an XCCDF rule:
xccdf_rule_passed = xccdf_org.ssgproject.content_rule_firefox_preferences-auto-download_actions
The following search query finds reports that fail an XCCDF rule:
xccdf_rule_failed = xccdf_org.ssgproject.content_rule_firefox_preferences-auto-download_actions
The following search query finds reports that have a result different than fail or pass for an XCCDF rule:
xccdf_rule_othered = xccdf_org.ssgproject.content_rule_firefox_preferences-auto-download_actions
Additional Information
- To see a list of available search parameters, click the empty Search field.
-
You can create complex queries with the following logical operators:
and,notandhas. For more information about logical operators, see Section 5.4.4, “Supported Operators for Granular Search”. - You cannot use regular expressions in a search query. However, you can use multiple fields in a single search expression. For more information about all available search operators, see Section 5.4.4, “Supported Operators for Granular Search”.
- You can bookmark a search to reuse the same search query. For more information, see Section 15.3.1, “Creating Bookmarks”.
6.7.7. Deleting a Compliance Report
To delete a compliance report, complete the following steps:
- In the Satellite web UI, navigate to Hosts > Reports.
- In the Compliance Reports window, identify the policy that you want to delete and, on the right of the policy’s name, select Delete.
- Click OK.
6.7.8. Deleting Multiple Compliance Reports
You can delete multiple compliance policies simultaneously. However, in the Satellite web UI, compliance policies are paginated, so you must delete one page of reports at a time. If you want to delete all OpenSCAP reports, use the script in the Deleting OpenSCAP Reports section of the Red Hat Satellite API Guide.
- In the Satellite web UI, navigate to Hosts > Reports.
- In the Compliance Reports window, select the compliance reports that you want to delete.
- In the upper right of the list, select Delete reports.
- Repeat these steps for as many pages as you want to delete.
6.8. Specifications Supported by OpenSCAP
The following specifications are supported by OpenSCAP:
| Title | Description | Version |
|---|---|---|
| XCCDF | The Extensible Configuration Checklist Description Format | 1.2 |
| OVAL | Open Vulnerability and Assessment Language | 5.11 |
| - | Asset Identification | 1.1 |
| ARF | Asset Reporting Format | 1.1 |
| CCE | Common Configuration Enumeration | 5.0 |
| CPE | Common Platform Enumeration | 2.3 |
| CVE | Common Vulnerabilities and Exposures | - |
| CVSS | Common Vulnerability Scoring System | 2.0 |