14.3. Configuring an External LDAP Provider
14.3.1. Configuring an External LDAP Provider (Interactive Setup)
ovirt-engine-extension-aaa-ldap extension allows users to customize their external directory setup easily. The ovirt-engine-extension-aaa-ldap extension supports many different LDAP server types, and an interactive setup script is provided to assist you with the setup for most LDAP types.
Note
engine-manage-domains, used in previous versions of Red Hat Enterprise Virtualization is not supported after 3.6.
- You need to know the domain name of the DNS or the LDAP server. Round-robin and failover policies are also supported.
- To set up secure connection between the LDAP server and the Manager, ensure a PEM-encoded CA certificate has been prepared. See Section D.2, “Setting Up SSL or TLS Connections between the Manager and an LDAP Server” for more information.
- Unless anonymous search is supported, a user with permissions to browse all users and groups must be available on the directory server to be used as the search user. Note down the search user's distinguished name (DN). Do not use the administrative user for the directory server.
- Have at least one set of account name and password ready to perform search and login queries to the LDAP server.
Procedure 14.1. Configuring an External LDAP Provider
- On the Red Hat Enterprise Virtualization Manager, install the LDAP extension package:
yum install ovirt-engine-extension-aaa-ldap-setup
# yum install ovirt-engine-extension-aaa-ldap-setupCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run
ovirt-engine-extension-aaa-ldap-setupto start the interactive setup:ovirt-engine-extension-aaa-ldap-setup
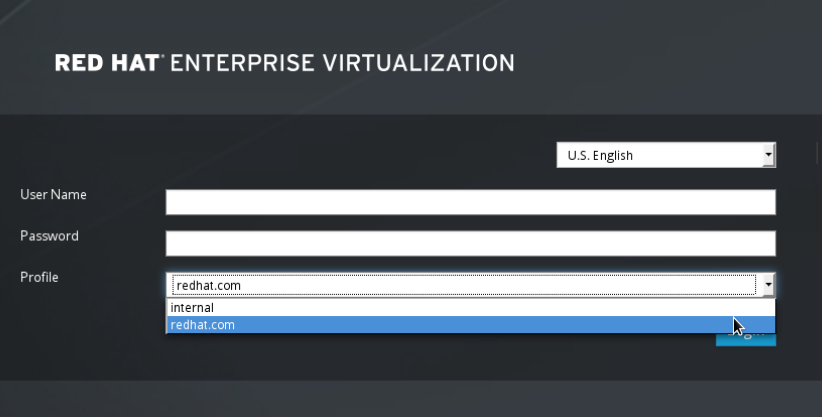
# ovirt-engine-extension-aaa-ldap-setupCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Specify a profile name. The profile name is visible to users on the login page. This example uses
redhat.com.Note
To rename the profile after the domain has been configured, edit theovirt.engine.aaa.authn.profile.nameattribute in the/etc/ovirt-engine/extensions.d/redhat.com-authn.propertiesfile. Restart the engine service for the changes to take effect.Please specify profile name that will be visible to users:redhat.com
Please specify profile name that will be visible to users:redhat.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Figure 14.1. The Administration Portal Login Page
Note
Users need to select the desired profile from the drop-down list when logging in for the first time. The information is then stored in browser cookies and preselected the next time the user logs in. - Select an LDAP type by entering the corresponding number. If you are not sure which schema your LDAP server is, select the standard schema of your LDAP server type. For Active Directory, follow the procedure at Section 14.3.2, “Attaching an Active Directory”.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Press Enter to accept the default and configure domain name resolution for your LDAP server name:
It is highly recommended to use DNS resolution for LDAP server. If for some reason you intend to use hosts or plain address disable DNS usage. Use DNS (Yes, No) [Yes]:
It is highly recommended to use DNS resolution for LDAP server. If for some reason you intend to use hosts or plain address disable DNS usage. Use DNS (Yes, No) [Yes]:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Select a DNS policy method by entering the corresponding number:
1 - Single server 2 - DNS domain LDAP SRV record 3 - Round-robin between multiple hosts 4 - Failover between multiple hosts Please select:
1 - Single server 2 - DNS domain LDAP SRV record 3 - Round-robin between multiple hosts 4 - Failover between multiple hosts Please select:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - For option 1, the DNS servers listed in
/etc/resolv.confis used to resolve the IP address. Ensure the/etc/resolv.conffile is updated with the correct DNS servers.Enter the fully qualified domain name (FQDN) or the IP address of the LDAP server. You can use thedigcommand with the SRV record to find out the domain name. An SRV record takes the following format: _service._protocol.domain name. For example:dig _ldap._tcp.redhat.com SRV. - For option 2, enter the domain name of the DNS server. A DNS search is performed to look up the SRV records to find out the domain name of the LDAP server.
- For option 3, enter a space-separated list of LDAP servers. Use either the FQDN or IP address of the servers. This policy provides load-balancing between the LDAP servers. Queries are distributed among all LDAP servers according to the round-robin algorithm.
- For option 4, enter a space-separated list of LDAP servers. Use either the FQDN or IP address of the servers. This policy defines the first LDAP server to be the default LDAP server to respond to queries. If the first server is not available, the query will go to the next LDAP server on the list.
- Select the secure connection method your LDAP server supports and specify the method to obtain a PEM-encoded CA certificate. The file option allows you to provide the full path to the certificate. The URL option allows you to specify a URL to the certificate. Use the inline option to paste the content of the certificate in the terminal. The system option allows you to specify the default location for all CA files. If the insecure mode is selected, the connection is still encrypted using TLS but certificate validation is skipped.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
LDAPS stands for Lightweight Directory Access Protocol Over Secure Socket Links. For SSL connections, select theldapsoption.For more information on creating a PEM-encoded CA certificate, see Section D.2, “Setting Up SSL or TLS Connections between the Manager and an LDAP Server”. - Enter the search user distinguished name (DN). The user must have permissions to browse all users and groups on the directory server. The search user must be specified in LDAP annotation. If anonymous search is allowed, press Enter without any input.
Enter search user DN (empty for anonymous): uid=user1,ou=Users,dc=test,dc=redhat,dc=com Enter search user password:
Enter search user DN (empty for anonymous): uid=user1,ou=Users,dc=test,dc=redhat,dc=com Enter search user password:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Test the search and login function to ensure the your LDAP server is connected to your Red Hat Enterprise Virtualization environment properly. For the login query, enter the account name and password. For the search query, select
Principalfor user accounts, and selectGroupfor group accounts. EnterYestoResolve Groupsif you want the group account information for the user account to be returned. SelectDoneto complete the setup. Three configuration files are created and displayed in the screen output.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the engine service. The profile you have created is now available on the Administration Portal and the User Portal login pages. To assign the user accounts on the LDAP server appropriate roles and permissions, for example to log in to the User Portal, see Section 14.7, “Administering User Tasks From the Administration Portal”.
service ovirt-engine restart
# service ovirt-engine restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Note
/usr/share/doc/ovirt-engine-extension-aaa-ldap-version.
14.3.2. Attaching an Active Directory
- You need to know the Active Directory forest name. The forest name is also known as the root domain name.
- You need to either add the DNS server that can resolve the Active Directory forest name to the
/etc/resolv.conffile on the Manager, or note down the Active Directory DNS servers and enter them when prompted by the interactive setup script. - To set up secure connection between the LDAP server and the Manager, ensure a PEM-encoded CA certificate has been prepared. See Section D.2, “Setting Up SSL or TLS Connections between the Manager and an LDAP Server” for more information.
- Unless anonymous search is supported, a user with permissions to browse all users and groups must be available on the Active Directory to be used as the search user. Note down the search user's distinguished name (DN). Do not use the administrative user for the Active Directory.
- Have at least one set of account name and password ready to perform search and login queries to the Active Directory.
Procedure 14.2. Configuring an External LDAP Provider
- On the Red Hat Enterprise Virtualization Manager, install the LDAP extension package:
yum install ovirt-engine-extension-aaa-ldap-setup
# yum install ovirt-engine-extension-aaa-ldap-setupCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Run
ovirt-engine-extension-aaa-ldap-setupto start the interactive setup:ovirt-engine-extension-aaa-ldap-setup
# ovirt-engine-extension-aaa-ldap-setupCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Specify a profile name. The profile name is visible to users on the login page. This example uses
redhat.com.Please specify profile name that will be visible to users:redhat.com
Please specify profile name that will be visible to users:redhat.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Figure 14.2. The Administration Portal Login Page
Note
Users need to select the desired profile from the drop-down list when logging in for the first time. The information is then stored in browser cookies and preselected the next time the user logs in. - Select an LDAP type by entering the corresponding number. The LDAP related questions after this step is different for different LDAP types.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Enter the Active Directory forest name. If the forest name is not resolvable by your Manager's DNS, the script prompts you to enter a space-separated list of Active Directory DNS server names.
Please enter Active Directory Forest name: ad-example.redhat.com [ INFO ] Resolving Global Catalog SRV record for ad-example.redhat.com [ INFO ] Resolving LDAP SRV record for ad-example.redhat.com
Please enter Active Directory Forest name: ad-example.redhat.com [ INFO ] Resolving Global Catalog SRV record for ad-example.redhat.com [ INFO ] Resolving LDAP SRV record for ad-example.redhat.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Select the secure connection method your LDAP server supports and specify the method to obtain a PEM-encoded CA certificate. The file option allows you to provide the full path to the certificate. The URL option allows you to specify a URL to the certificate. Use the inline option to paste the content of the certificate in the terminal. The system option allows you to specify the location for all CA files. The insecure option allows you to use startTLS in insecure mode.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note
LDAPS stands for Lightweight Directory Access Protocol Over Secure Socket Links. For SSL connections, select theldapsoption.For more information on creating a PEM-encoded CA certificate, see Section D.2, “Setting Up SSL or TLS Connections between the Manager and an LDAP Server”. - Enter the search user distinguished name (DN). The user must have permissions to browse all users and groups on the directory server. The search user must be of LDAP annotation. If anonymous search is allowed, press Enter without any input.
Enter search user DN (empty for anonymous): uid=user1,ou=Users,dc=test,dc=redhat,dc=com Enter search user password:
Enter search user DN (empty for anonymous): uid=user1,ou=Users,dc=test,dc=redhat,dc=com Enter search user password:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Test the search and login function to ensure your LDAP server is connected to your Red Hat Enterprise Virtualization environment properly. For the login query, enter the account name and password. For the search query, select
Principalfor user accounts, and selectGroupfor group accounts. EnterYestoResolve Groupsif you want the group account information for the user account to be returned. SelectDoneto complete the setup. Three configuration files are created and displayed in the screen output.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The profile you have created is now available on the Administration Portal and the User Portal login pages. To assign the user accounts on the LDAP server appropriate roles and permissions, for example to log in to the User Portal, see Section 14.7, “Administering User Tasks From the Administration Portal”.
Note
/usr/share/doc/ovirt-engine-extension-aaa-ldap-version.
14.3.3. Configuring an External LDAP Provider (Manual Method)
ovirt-engine-extension-aaa-ldap extension uses the LDAP protocol to access directory servers and is fully customizable. Kerberos authentication is not required unless you want to enable the single sign-on to the User Portal or the Administration Portal feature.
Procedure 14.3. Configuring an External LDAP Provider Manually
- On the Red Hat Enterprise Virtualization Manager, install the LDAP extension package:
yum install ovirt-engine-extension-aaa-ldap
# yum install ovirt-engine-extension-aaa-ldapCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the LDAP configuration template file into the
/etc/ovirt-enginedirectory. Template files are available for active directories (ad) and other directory types (simple). This example uses the simple configuration template.cp -r /usr/share/ovirt-engine-extension-aaa-ldap/examples/simple/. /etc/ovirt-engine
# cp -r /usr/share/ovirt-engine-extension-aaa-ldap/examples/simple/. /etc/ovirt-engineCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Rename the configuration files to match the profile name you want visible to users on the Administration Portal and the User Portal login pages:
mv /etc/ovirt-engine/aaa/profile1.properties /etc/ovirt-engine/aaa/example.properties mv /etc/ovirt-engine/extensions.d/profile1-authn.properties /etc/ovirt-engine/extensions.d/example-authn.properties mv /etc/ovirt-engine/extensions.d/profile1-authz.properties /etc/ovirt-engine/extensions.d/example-authz.properties
# mv /etc/ovirt-engine/aaa/profile1.properties /etc/ovirt-engine/aaa/example.properties # mv /etc/ovirt-engine/extensions.d/profile1-authn.properties /etc/ovirt-engine/extensions.d/example-authn.properties # mv /etc/ovirt-engine/extensions.d/profile1-authz.properties /etc/ovirt-engine/extensions.d/example-authz.propertiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Edit the LDAP property configuration file by uncommenting an LDAP server type and updating the domain and passwords fields:
vi /etc/ovirt-engine/aaa/example.properties
# vi /etc/ovirt-engine/aaa/example.propertiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example 14.1. Example profile: LDAP server section
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To use TLS or SSL protocol to interact with the LDAP server, obtain the root CA certificate for the LDAP server and use it to create a public keystore file. Uncomment the following lines and specify the full path to the public keystore file and the password to access the file.Note
For more information on creating a public keystore file, see Section D.2, “Setting Up SSL or TLS Connections between the Manager and an LDAP Server”.Example 14.2. Example profile: keystore section
# Create keystore, import certificate chain and uncomment # if using tls. pool.default.ssl.startTLS = true pool.default.ssl.truststore.file = /full/path/to/myrootca.jks pool.default.ssl.truststore.password = password
# Create keystore, import certificate chain and uncomment # if using tls. pool.default.ssl.startTLS = true pool.default.ssl.truststore.file = /full/path/to/myrootca.jks pool.default.ssl.truststore.password = passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Review the authentication configuration file. The profile name visible to users on the Administration Portal and the User Portal login pages is defined by
ovirt.engine.aaa.authn.profile.name. The configuration profile location must match the LDAP configuration file location. All fields can be left as default.vi /etc/ovirt-engine/extensions.d/example-authn.properties
# vi /etc/ovirt-engine/extensions.d/example-authn.propertiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example 14.3. Example authentication configuration file
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Review the authorization configuration file. The configuration profile location must match the LDAP configuration file location. All fields can be left as default.
vi /etc/ovirt-engine/extensions.d/example-authz.properties
# vi /etc/ovirt-engine/extensions.d/example-authz.propertiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example 14.4. Example authorization configuration file
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Ensure that the ownership and permissions of the configuration profile are appropriate:
chown ovirt:ovirt /etc/ovirt-engine/aaa/example.properties
# chown ovirt:ovirt /etc/ovirt-engine/aaa/example.propertiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow chmod 600 /etc/ovirt-engine/aaa/example.properties
# chmod 600 /etc/ovirt-engine/aaa/example.propertiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart the engine service:
service ovirt-engine restart
# service ovirt-engine restartCopy to Clipboard Copied! Toggle word wrap Toggle overflow - The example profile you have created is now available on the Administration Portal and the User Portal login pages. To give the user accounts on the LDAP server appropriate permissions, for example to log in to the User Portal, see the Red Hat Enterprise Virtualization Manager User Tasks section of the Red Hat Enterprise Virtualization Administration Guide.
Note
/usr/share/doc/ovirt-engine-extension-aaa-ldap-version.