Este contenido no está disponible en el idioma seleccionado.
6.6. Managing Password Synchronization
Synchronizing user entries is configured with the synchronization agreement. However, passwords in both Active Directory and Identity Management are not part of the normal user synchronization process. A separate client must be installed on the Active Directory servers to capture passwords as user accounts are created or passwords are changed, and then to forward that password information with the synchronized updates.
Note
The Password Synchronization client captures password changes and then synchronizes them between Active Directory and IdM. This means that it synchronizes new passwords or password updates.
Existing passwords, which are stored in a hashed form in both IdM and Active Directory, cannot be decrypted or synchronized when the Password Synchronization client is installed, so existing passwords are not synchronized. User passwords must be changed to initiate synchronization between the peer servers.
6.6.1. Setting up the Windows Server for Password Synchronization
Copiar enlaceEnlace copiado en el portapapeles!
Synchronizing passwords requires these things:
- Active Directory must be running in SSL.
Note
Install the Microsoft Certificate System in Enterprise Root Mode. Active Directory will then automatically enroll to retrieve its SSL server certificate. - The Password Synchronization Service must be installed on each Active Directory domain controller. To synchronize a password from Windows, the PassSync service requires access to the unencrypted password to synchronize it over a secure connection to IdM. Because users can change their passwords on every domain controller, the installation of the PassSync service on each domain controller is necessary.
- The password policy must be set similar on IdM and Active Directory side. When the synchronization destination receives an updated password, it was only validated to match the policy on the source. It is not re-validated on the synchronization destination.
To verify that the Active Directory password complexity policy is enabled, run on an Active Directory domain controller:
> dsquery * -scope base -attr pwdProperties
pwdProperties
1
> dsquery * -scope base -attr pwdProperties
pwdProperties
1
If the value of the attribute
pwdProperties is set to 1, the password complexity policy is enabled for the domain.
Note
If you are unsure if group policies define deviating password settings for Organizational Units (ou), ask your group policy administrator.
To enable the Active Directory password complexity setting for the whole domain:
- Run
gpmc.mscfrom the command line. - Select .
- Open
. - Right-click the entry and select .
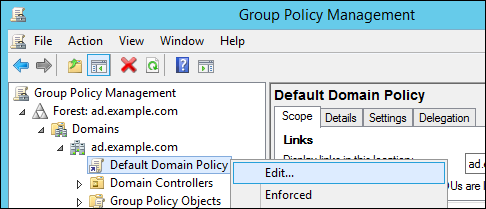
- The
Group Policy Management Editoropens automatically. - Open
. - Enable the
Password must meet complexity requirementsoption and save.
6.6.2. Setting up Password Synchronization
Copiar enlaceEnlace copiado en el portapapeles!
Install the Password Synchronization Service on every domain controller in the Active Directory domain in order to synchronize Windows passwords.
- Download the
RedHat-PassSync-*.msifile to the Active Directory domain controller:- Log in to the Customer Portal.
- Click Downloads at the top of the page.
- Select Red Hat Enterprise Linux from the product list.
- Select the most recent version of Red Hat Enterprise Linux 6 or Red Hat Enterprise Linux 7 and architecture.
- Download WinSync Installer for the architecture of the Active Directory domain controller by clicking the button.
- Double-click the
MSIfile to install it. - The Password Synchronrization Setup window appears. Hit Next to begin installing.
- Fill in the information to establish the connection to the IdM server.
- The IdM server connection information, including the host name and secure port number.
- The user name of the system user which Active Directory uses to connect to the IdM machine. This account is configured automatically when synchronization is configured on the IdM server. The default account is
uid=passsync,cn=sysaccounts,cn=etc,dc=example,dc=com. - The password set in the
--passsyncoption when the synchronization agreement was created. - The search base for the people subtree on the IdM server. The Active Directory server connects to the IdM server similar to an
ldapsearchor replication operation, so it has to know where in the IdM subtree to look for user accounts. The user subtree iscn=users,cn=accounts,dc=example,dc=com. - The certificate token is not used at this time, so that field should be left blank.
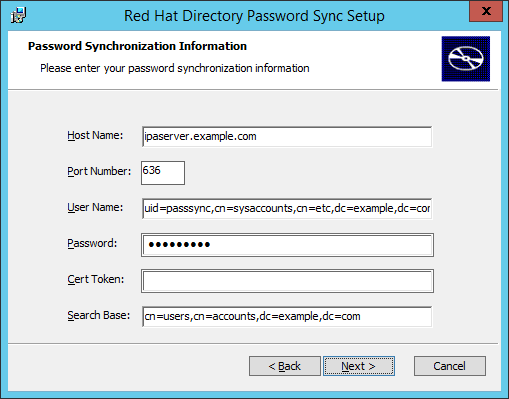 Hit , then to install Password Synchronization.
Hit , then to install Password Synchronization. - Import the IdM server's CA certificate into the PassSync certificate store.
- Download the IdM server's CA certificate from
http://ipa.example.com/ipa/config/ca.crt. - Copy the IdM CA certificate to the Active Directory server.
- Install the IdM CA certificate in the Password Synchronization database. For example:
cd "C:\Program Files\Red Hat Directory Password Synchronization" certutil.exe -d . -A -n "IPASERVER.EXAMPLE.COM IPA CA" -t CT,, -a -i ipaca.crt
cd "C:\Program Files\Red Hat Directory Password Synchronization" certutil.exe -d . -A -n "IPASERVER.EXAMPLE.COM IPA CA" -t CT,, -a -i ipaca.crtCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- Reboot the Windows machine to start Password Synchronization.
Note
The Windows machine must be rebooted. Without the rebooting,PasswordHook.dllis not enabled, and password synchronization will not function. - If passwords for existing accounts should be synchronized, reset the user passwords.
Note
The Password Synchronization client captures password changes and then synchronizes them between Active Directory and IdM. This means that it synchronizes new passwords or password updates.Existing passwords, which are stored in a hashed form in both IdM and Active Directory, cannot be decrypted or synchronized when the Password Synchronization client is installed, so existing passwords are not synchronized. User passwords must be changed to initiate synchronization between the peer servers.
The first attempt to synchronize passwords, which happened when the Password Synchronization application is installed, will always fail because of the SSL connection between the Directory Server and Active Directory synchronization peers. The tools to create the certificate and key databases is installed with the
.msi.
The password synchronization client cannot synchronize passwords for members of the IdM
admin group. This is an intended behavior to prevent, for example, password synchronization agents or low level user administrators to change passwords of top level administrators.
Note
Passwords are only validated on the synchronization source to match the password policies. To verify and enable the Active Directory password complexity policy, see Section 6.6.1, “Setting up the Windows Server for Password Synchronization”.