Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 3. RBAC mapping configuration
On OpenShift Container Platform (OCP), Cryostat uses a permission configuration that maps OCP resources to Cryostat-managed resources. The permission configuration provides Cryostat with a framework for authorizing a user to perform certain actions, such as creating a JFR recording, or viewing discovered targets.
The following table outlines definitions that represent Cryostat-managed resources:
| Resource | Description |
|---|---|
|
| SSL certificates that connect to Java Virtual Machine (JVM) applications with enabled encryption. |
|
| Stored credentials for target JVM applications. |
|
| Recordings created for JVM applications. |
|
| Report content generated from recordings. |
|
| Automated Rules that start recordings on matching targets when they become available to Cryostat, non-interactively. |
|
| Discovered JVM applications to monitor. |
|
| Event templates to configure recordings. |
The permission configuration defines lists of OCP resources that are equivalent to the previously listed resource definitions. API requests specify resource actions to translate a Cryostat-managed resource permissions into OCP resources. Cryostat checks each API request for this action and then processes the API request.
Cryostat assigns resource-verb pairs to each endpoint. These verbs are custom and specific to Cryostat. During permissions checks, Cryostat translates custom verbs into RBAC verbs.
You can implement the following verbs on these Cryostat-managed resources:
-
CREATE: create -
DELETE: delete -
READ: get -
UPDATE: patch
The following example shows a mapping configuration that links a Cryostat-managed resource to a list of Red Hat OpenShift resources:
TARGET=pods,services
To create an API request that outputs a list of discovered JVM targets, for example, from the Target JVM pane on the Recordings page, you must have READ permissions to view the discoverable TARGET. In the RBAC system, the READ permission provides access to read pods and services.
By default, Cryostat uses the following RBAC mapping configuration.
auth.properties:
TARGET=pods,services
RECORDING=pods,pods/exec,cryostats.operator.cryostat.io
CERTIFICATE=pods,cryostats.operator.cryostat.io
CREDENTIALS=pods,cryostats.operator.cryostat.io
The ConfigMap defines the mapping content. The previous example does not list all Cryostat-managed resources. If a Cryostat-managed resource is missing from the ConfigMap, Cryostat skips permission checks during the processing of an API request.
The Red Hat build of Cryostat Operator projects these settings from the provided ConfigMap API object into the Cryostat pod on Red Hat OpenShift. Your Cryostat pod can access these settings at any time to confirm what permissions of Cryostat functions a user can access. You can then define a ClusterRole in the custom resource (CR) that provides specific permissions to these mapped Red Hat OpenShift resources.
Example that shows a Cryostat CR with ConfigMap, ClusterRole, and filename fields defined in the spec field
apiVersion: operator.cryostat.io/v1beta1
kind: Cryostat
metadata:
name: cryostat-sample
spec:
authProperties:
configMapName: auth-properties
filename: auth.properties
clusterRoleName: oauth-cluster-role
Additional resources
- See, RBAC permissions (Installing Cryostat).
3.1. Configuring RBAC mappings
You can create a custom role with Cryostat-specific RBAC permissions and then bind this role to a user’s Red Hat OpenShift account. This feature is useful for when you want to set specific permissions for each user that operates within the same Cryostat namespace.
Prerequisites
- Logged in to the OpenShift Container Platform by using the Red Hat OpenShift web console.
- Created a Cryostat instance in your project. See Installing Cryostat on Red Hat OpenShift using an operator (Installing Cryostat).
Procedure
Define a custom permission mapping in a
ConfigMapobject.Example of a
ConfigMapcontaining the permission mappingapiVersion: v1 kind: ConfigMap metadata: name: auth-properties data: auth.properties: | TARGET=pods,deployments.apps RECORDING=pods,pods/exec CERTIFICATE=deployments.apps,pods,cryostats.operator.cryostat.io CREDENTIALS=cryostats.operator.cryostat.ioTo use custom permission mapping, a
ClusterRolemust exist and contain permissions for all Red Hat OpenShift objects listed in custom permission mapping.Example of a
ClusterRolethat contains the necessary rulesapiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: additional-oauth-client rules: - apiGroups: - operator.cryostat.io resources: - cryostats verbs: - create - patch - delete - get - apiGroups: - "" resources: - pods - pods/exec verbs: - create - patch - delete - get - apiGroups: - apps resources: - deployments verbs: - create - patch - delete - get
After you enter your credentials on the Red Hat OpenShift web console, the
OAuthserver uses your credentials and the specified scope to generate an API token.Provide the
authPropertiesspec in the Cryostat Custom Resource (CR) to reference theConfigMapthat holds the mapping content, andClusterRolethat defines RBAC access for those mapped Red Hat OpenShift resources.Example of a Cryostat CR with
authPropertiesthat define a custom permission mappingapiVersion: operator.cryostat.io/v1beta1 kind: Cryostat metadata: name: cryostat-sample spec: authProperties: configMapName: auth-properties filename: auth.properties clusterRoleName: oauth-cluster-role
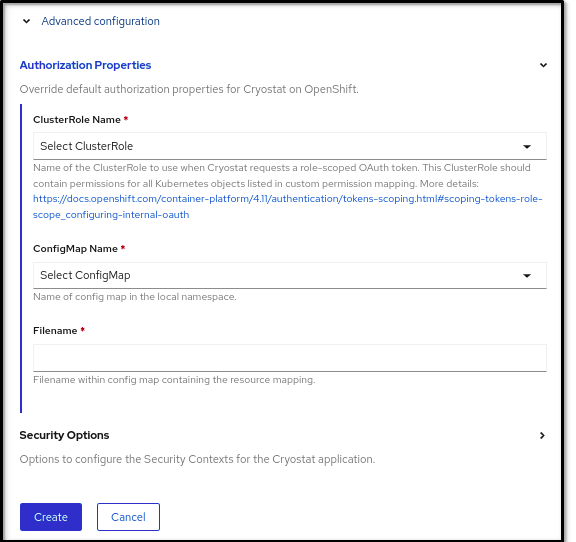
Alternatively, you can open your Red Hat OpenShift web console, create a Cryostat instance, and define
ClusterRole Name,ConfigMap Name, andFilenameproperties in theAuthorization Propertiesoption, which you can access in theAdvanced configurationsection.Figure 3.1. The Advanced configuration section on the OpenShift web console
Verification
- From the Installed Operators menu, select your Cryostat instance.
-
Click the link in the Application URL section to access the login screen. The
OAuthserver redirects you to an OpenShift Container Platform login page. -
Enter your credential details and then click Login. For the first time you log in through the
OAuthserver, an Authorize Access page opens on your web browser. - From the Requested Permissions option, confirm that the cluster role name matches the name that you specified in the Cryostat CR.
From the Authorize Access window, you can select the required checkboxes. For optimal Cryostat performance, select all checkboxes.
Figure 3.2. The Authorize Access window that lists three permissions
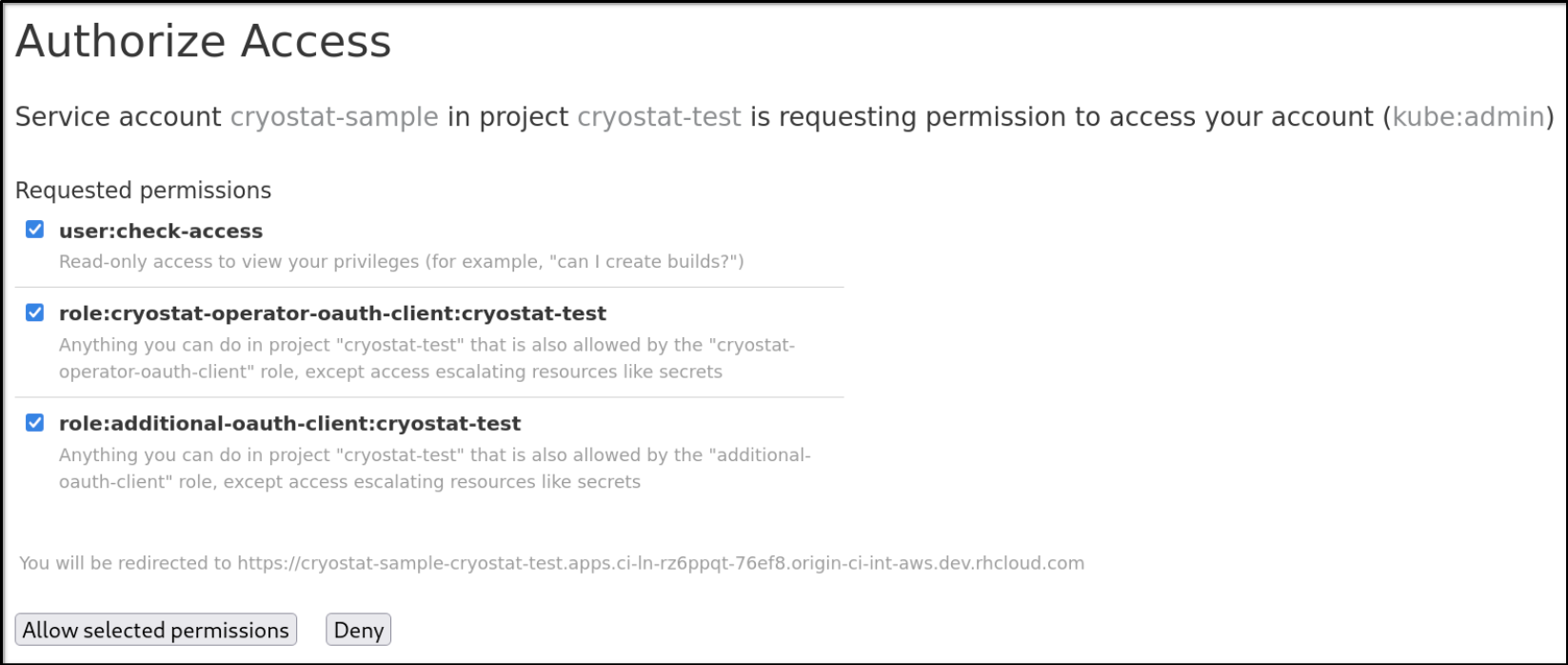
The Authorize Access window lists the following permissions:
- User:check-access, which is a permission check that the internal Cryostat application requests. Permission provides a user with read-only access to view their privileges.
-
role:cryostat-operator-oauth-client:<namespace>, which is a permission check that the internal Cryostat application requests. Replace <namespace> with the name of your project name or your namespace from your CLI. Permission provides a user with access to complete any operations that the
cryostat-operator-oauth-clientrole specifies, except access to escalate resources, such as secrets. -
role:<user-define-clusterrole-name>:<namespace>: The
clusterrolethat you defined in the Cryostat CR spec. Replace <namespace> with the name of your project name or your namespace from your CLI. Permission provides a user with access to complete any operations that theadditional-oauth-client rolespecifies, except escalating access to resources, such as secrets.
Choose one of the following options:
- Click Allow selected permissions if you want to accept the selected requested permissions.
Click Deny button if you want to reject all requested permission options.
Your web browser redirects you to the Cryostat web console, where you can monitor Java applications that are running in a Java Virtual Machine (JVM).
Additional resources
- See, Installing Cryostat on Red Hat OpenShift by using a Red Hat build of Cryostat Operator (Installing Cryostat).
Revised on 2023-12-12 18:49:07 UTC