Ce contenu n'est pas disponible dans la langue sélectionnée.
3.2. Configuring Fence Devices
Configuring fence devices consists of creating, updating, and deleting fence devices for the cluster. You must configure the fence devices in a cluster before you can configure fencing for the nodes in the cluster.
Creating a fence device consists of selecting a fence device type and entering parameters for that fence device (for example, name, IP address, login, and password). Updating a fence device consists of selecting an existing fence device and changing parameters for that fence device. Deleting a fence device consists of selecting an existing fence device and deleting it.
This section provides procedures for the following tasks:
- Creating fence devices — Refer to Section 3.2.1, “Creating a Fence Device”. Once you have created and named a fence device, you can configure the fence devices for each node in the cluster, as described in Section 3.3, “Configuring Fencing for Cluster Members”.
- Updating fence devices — Refer to Section 3.2.2, “Modifying a Fence Device”.
- Deleting fence devices — Refer to Section 3.2.3, “Deleting a Fence Device”.
From the cluster-specific page, you can configure fence devices for that cluster by clicking on along the top of the cluster display. This displays the fence devices for the cluster and displays the menu items for fence device configuration: and . This is the starting point of each procedure described in the following sections.
Note
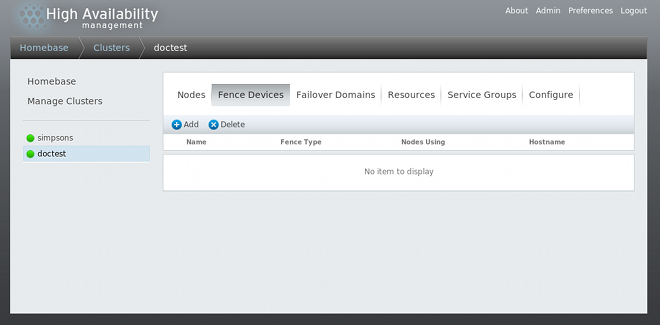
If this is an initial cluster configuration, no fence devices have been created, and therefore none are displayed.
Figure 3.1, “luci fence devices configuration page” shows the fence devices configuration screen before any fence devices have been created.
Figure 3.1. luci fence devices configuration page
3.2.1. Creating a Fence Device
Copier lienLien copié sur presse-papiers!
To create a fence device, follow these steps:
- From the configuration page, click . Clicking displays the Add Fence Device (Instance) dialog box. From this dialog box, select the type of fence device to configure.
- Specify the information in the Add Fence Device (Instance) dialog box according to the type of fence device. In some cases you will need to specify additional node-specific parameters for the fence device when you configure fencing for the individual nodes.
- Click .
After the fence device has been added, it appears on the configuration page.