Ce contenu n'est pas disponible dans la langue sélectionnée.
Chapter 3. Managing access to repositories
As a Red Hat Quay user, you can create your own repositories and make them accessible to other users that are part of your instance. Alternatively, you can create a specific Organization to allow access to repositories based on defined teams.
In both User and Organization repositories, you can allow access to those repositories by creating credentials associated with Robot Accounts. Robot Accounts make it easy for a variety of container clients, such as Docker or Podman, to access your repositories without requiring that the client have a Red Hat Quay user account.
3.1. Allowing access to user repositories
When you create a repository in a user namespace, you can add access to that repository to user accounts or through Robot Accounts.
3.1.1. Allowing user access to a user repository
Use the following procedure to allow access to a repository associated with a user account.
Procedure
- Log into Red Hat Quay with your user account.
- Select a repository under your user namespace that will be shared across multiple users.
- Select Settings in the navigation pane.
Type the name of the user to which you want to grant access to your repository. As you type, the name should appear. For example:
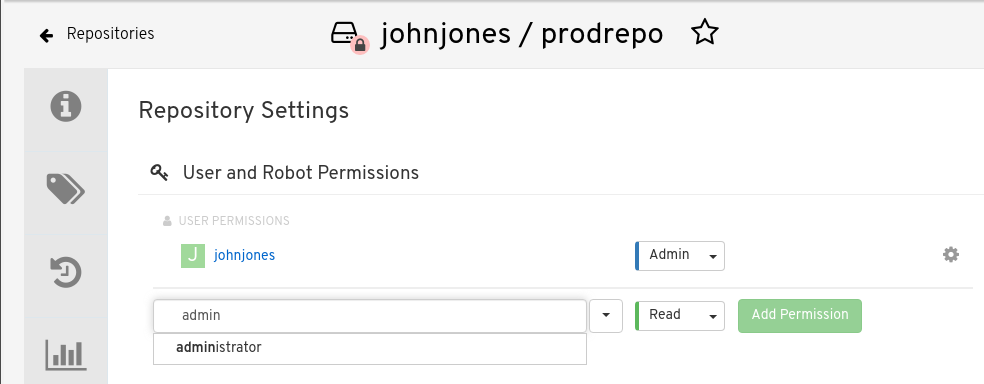
In the permissions box, select one of the following:
- Read. Allows the user to view and pull from the repository.
- Write. Allows the user to view the repository, pull images from the repository, or push images to the repository.
- Admin. Provides the user with all administrative settings to the repository, as well as all Read and Write permissions.
- Select the Add Permission button. The user now has the assigned permission.
- Optional. You can remove or change user permissions to the repository by selecting the Options icon, and then selecting Delete Permission.
3.1.2. Allowing robot access to a user repository
Robot Accounts are used to set up automated access to the repositories in your Red Hat Quay registry. They are similar to OpenShift Container Platform service accounts.
Setting up a Robot Account results in the following:
- Credentials are generated that are associated with the Robot Account.
- Repositories and images that the Robot Account can push and pull images from are identified.
- Generated credentials can be copied and pasted to use with different container clients, such as Docker, Podman, Kubernetes, Mesos, and so on, to access each defined repository.
Each Robot Account is limited to a single user namespace or Organization. For example, the Robot Account could provide access to all repositories for the user jsmith. However, it cannot provide access to repositories that are not in the user’s list of repositories.
Use the following procedure to set up a Robot Account that can allow access to your repositories.
Procedure
- On the Repositories landing page, click the name of a user.
- Click Robot Accounts on the navigation pane.
- Click Create Robot Account.
- Provide a name for your Robot Account.
- Optional. Provide a description for your Robot Account.
-
Click Create Robot Account. The name of your Robot Account becomes a combination of your username plus the name of the robot, for example,
jsmith+robot - Select the repositories that you want the Robot Account to be associated with.
Set the permissions of the Robot Account to one of the following:
- None. The Robot Account has no permission to the repository.
- Read. The Robot Account can view and pull from the repository.
- Write. The Robot Account can read (pull) from and write (push) to the repository.
- Admin. Full access to pull from, and push to, the repository, plus the ability to do administrative tasks associated with the repository.
- Click the Add permissions button to apply the settings.
- On the Robot Accounts page, select the Robot Account to see credential information for that robot.
Under the Robot Account option, copy the generated token for the robot by clicking Copy to Clipboard. To generate a new token, you can click Regenerate Token.
NoteRegenerating a token makes any previous tokens for this robot invalid.

Obtain the resulting credentials in the following ways:
- Kubernetes Secret: Select this to download credentials in the form of a Kubernetes pull secret yaml file.
-
rkt Configuration: Select this to download credentials for the rkt container runtime in the form of a
.jsonfile. -
Docker Login: Select this to copy a full
docker logincommand line that includes the credentials. -
Docker Configuration: Select this to download a file to use as a Docker
config.jsonfile, to permanently store the credentials on your client system. - Mesos Credentials: Select this to download a tarball that provides the credentials that can be identified in the URI field of a Mesos configuration file.
3.2. Organization repositories
After you have created an Organization, you can associate a set of repositories directly to that Organization. An Organization’s repository differs from a basic repository in that the Organization is intended to set up shared repositories through groups of users. In Red Hat Quay, groups of users can be either Teams, or sets of users with the same permissions, or individual users.
Other useful information about Organizations includes the following:
- You cannot have an Organization embedded within another Organization. To subdivide an Organization, you use teams.
Organizations cannot contain users directly. You must first add a team, and then add one or more users to each team.
NoteIndividual users can be added to specific repositories inside of an organization. Consequently, those users are not members of any team on the Repository Settings page. The Collaborators View on the Teams and Memberships page shows users who have direct access to specific repositories within the organization without needing to be part of that organization specifically.
- Teams can be set up in Organizations as just members who use the repositories and associated images, or as administrators with special privileges for managing the Organization.
3.2.1. Creating an Organization
Use the following procedure to create an Organization.
Procedure
- On the Repositories landing page, click Create New Organization.
- Under Organization Name, enter a name that is at least 2 characters long, and less than 225 characters long.
- Under Organization Email, enter an email that is different from your account’s email.
- Click Create Organization to finalize creation.
3.2.1.1. Creating another Organization by using the API
You can create another Organization by using the API. To do this, you must have created the first Organization by using the UI. You must also have generated an OAuth Access Token.
Use the following procedure to create another Organization by using the Red Hat Quay API endpoint.
Prerequisites
- You have already created at least one Organization by using the UI.
- You have generated an OAuth Access Token. For more information, see "Creating an OAuth Access Token".
Procedure
Create a file named
data.jsonby entering the following command:touch data.json
$ touch data.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the following content to the file, which will be the name of the new Organization:
{"name":"testorg1"}{"name":"testorg1"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to create the new Organization using the API endpoint, passing in your OAuth Access Token and Red Hat Quay registry endpoint:
curl -X POST -k -d @data.json -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" http://<quay-server.example.com>/api/v1/organization/
$ curl -X POST -k -d @data.json -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" http://<quay-server.example.com>/api/v1/organization/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
"Created"
"Created"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.2.2. Adding a team to an organization
When you create a team for your Organization you can select the team name, choose which repositories to make available to the team, and decide the level of access to the team.
Use the following procedure to create a team for your Organization.
Prerequisites
- You have created an organization.
Procedure
- On the Repositories landing page, select an Organization to add teams to.
- In the navigation pane, select Teams and Membership. By default, an owners team exists with Admin privileges for the user who created the Organization.
- Click Create New Team.
- Enter a name for your new team. Note that the team must start with a lowercase letter. It can also only use lowercase letters and numbers. Capital letters or special characters are not allowed.
- Click Create team.
- Click the name of your team to be redirected to the Team page. Here, you can add a description of the team, and add team members, like registered users, robots, or email addresses. For more information, see "Adding users to a team".
- Click the No repositories text to bring up a list of available repositories. Select the box of each repository you will provide the team access to.
Select the appropriate permissions that you want the team to have:
- None. Team members have no permission to the repository.
- Read. Team members can view and pull from the repository.
- Write. Team members can read (pull) from and write (push) to the repository.
- Admin. Full access to pull from, and push to, the repository, plus the ability to do administrative tasks associated with the repository.
- Click Add permissions to save the repository permissions for the team.
3.2.3. Setting a Team role
After you have added a team, you can set the role of that team within the Organization.
Prerequisites
- You have created a team.
Procedure
- On the Repository landing page, click the name of your Organization.
- In the navigation pane, click Teams and Membership.
Select the TEAM ROLE drop-down menu, as shown in the following figure:

For the selected team, choose one of the following roles:
- Member. Inherits all permissions set for the team.
- Creator. All member permissions, plus the ability to create new repositories.
- Admin. Full administrative access to the organization, including the ability to create teams, add members, and set permissions.
3.2.4. Adding users to a Team
With administrative privileges to an Organization, you can add users and robot accounts to a team. When you add a user, Red Hat Quay sends an email to that user. The user remains pending until they accept the invitation.
Use the following procedure to add users or robot accounts to a team.
Procedure
- On the Repository landing page, click the name of your Organization.
- In the navigation pane, click Teams and Membership.
- Select the team you want to add users or robot accounts to.
In the Team Members box, enter information for one of the following:
- A username from an account on the registry.
- The email address for a user account on the registry.
The name of a robot account. The name must be in the form of <organization_name>+<robot_name>.
NoteRobot Accounts are immediately added to the team. For user accounts, an invitation to join is mailed to the user. Until the user accepts that invitation, the user remains in the INVITED TO JOIN state. After the user accepts the email invitation to join the team, they move from the INVITED TO JOIN list to the MEMBERS list for the Organization.
3.3. Disabling robot accounts
Red Hat Quay administrators can manage robot accounts by disallowing users to create new robot accounts.
Robot accounts are mandatory for repository mirroring. Setting the ROBOTS_DISALLOW configuration field to true breaks mirroring configurations. Users mirroring repositories should not set ROBOTS_DISALLOW to true in their config.yaml file. This is a known issue and will be fixed in a future release of Red Hat Quay.
Use the following procedure to disable robot account creation.
Prerequisites
- You have created multiple robot accounts.
Procedure
Update your
config.yamlfield to add theROBOTS_DISALLOWvariable, for example:ROBOTS_DISALLOW: true
ROBOTS_DISALLOW: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart your Red Hat Quay deployment.
Verification: Creating a new robot account
- Navigate to your Red Hat Quay repository.
- Click the name of a repository.
- In the navigation pane, click Robot Accounts.
- Click Create Robot Account.
-
Enter a name for the robot account, for example,
<organization-name/username>+<robot-name>. -
Click Create robot account to confirm creation. The following message appears:
Cannot create robot account. Robot accounts have been disabled. Please contact your administrator.
Verification: Logging into a robot account
On the command-line interface (CLI), attempt to log in as one of the robot accounts by entering the following command:
podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following error message is returned:
Error: logging into "<quay-server.example.com>": invalid username/password
Error: logging into "<quay-server.example.com>": invalid username/passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can pass in the
log-level=debugflag to confirm that robot accounts have been deactivated:podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.
... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.Copy to Clipboard Copied! Toggle word wrap Toggle overflow