Questo contenuto non è disponibile nella lingua selezionata.
3.2. Setting up Certificate Profiles
In Certificate System, you can add, delete, and modify enrollment profiles:
- Using the PKI command-line interface
- Using the Java-based administration console
This section provides information on each method.
3.2.1. Managing Certificate Enrollment Profiles Using the PKI Command-line Interface
This section describes how to manage certificate profiles using the
pki utility. For further details, see the pki-ca-profile(1) man page.
Note
Using the raw format is recommended. For details on each attribute and field of the profile, see the section Creating and Editing Certificate Profiles Directly on the File System in Red Hat Certificate System Planning, Installation and Deployment Guide.
3.2.1.1. Enabling and Disabling a Certificate Profile
Before you can edit a certificate profile, you must disable it. After the modification is complete, you can re-enable the profile.
Note
Only CA agents can enable and disable certificate profiles.
For example, to disable the
caCMCECserverCert certificate profile:
# pki -c password -n caagent ca-profile-disable caCMCECserverCert
For example, to enable the
caCMCECserverCert certificate profile:
# pki -c password -n caagent ca-profile-enable caCMCECserverCert
3.2.1.2. Creating a Certificate Profile in Raw Format
To create a new profile in raw format:
# pki -c password -n caadmin ca-profile-add profile_name.cfg --raw
Note
In raw format, specify the new profile ID as follows:
profileId=profile_name
3.2.1.3. Editing a Certificate Profile in Raw Format
CA administrators can edit a certificate profile in raw format without manually downloading the configuration file.
For example, to edit the
caCMCECserverCert profile:
# pki -c password -n caadmin ca-profile-edit caCMCECserverCert
This command automatically downloads the profile configuration in raw format and opens it in the
VI editor. When you close the editor, the profile configuration is updated on the server.
You do not need to restart the CA after editing a profile.
Important
Before you can edit a profile, disable the profile. For details, see Section 3.2.1.1, “Enabling and Disabling a Certificate Profile”.
Example 3.2. Editing a Certificate Profile in RAW Format
For example, to edit the
caCMCserverCert profile to accept multiple user-supplied extensions:
- Disable the profile as a CA agent:
# pki -c password -n caagemt ca-profile-disable caCMCserverCert
- Edit the profile as a CA administrator:
- Download and open the profile in the
VIeditor:# pki -c password -n caadmin ca-profile-edit caCMCserverCert
- Update the configuration to accept the extensions. For details, see Example B.3, “Multiple User Supplied Extensions in CSR”.
- Enable the profile as a CA agent:
# pki -c password -n caagent ca-profile-enable caCMCserverCert
3.2.1.4. Deleting a Certificate Profile
To delete a certificate profile:
# pki -c password -n caadmin ca-profile-del profile_name
Important
Before you can delete a profile, disable the profile. For details, see Section 3.2.1.1, “Enabling and Disabling a Certificate Profile”.
3.2.2. Managing Certificate Enrollment Profiles Using the Java-based Administration Console
Important
pkiconsole is being deprecated.
3.2.2.1. Creating Certificate Profiles through the CA Console
For security reasons, the Certificate Systems enforces separation of roles whereby an existing certificate profile can only be edited by an administrator after it was allowed by an agent. To add a new certificate profile or modify an existing certificate profile, perform the following steps as the administrator:
- Log in to the Certificate System CA subsystem console.
pkiconsole https://server.example.com:8443/ca
- In the Configuration tab, select Certificate Manager, and then select Certificate Profiles.The Certificate Profile Instances Management tab, which lists configured certificate profiles, opens.
- To create a new certificate profile, click .In the Select Certificate Profile Plugin Implementation window, select the type of certificate for which the profile is being created.
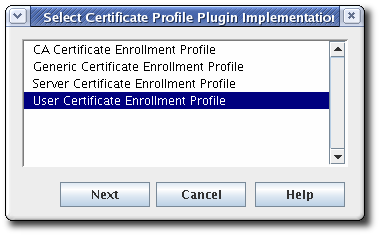
- Fill in the profile information in the Certificate Profile Instance Editor.
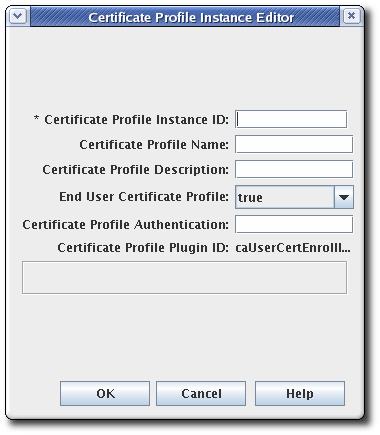
- Certificate Profile Instance ID. This is the ID used by the system to identify the profile.
- Certificate Profile Name. This is the user-friendly name for the profile.
- Certificate Profile Description.
- End User Certificate Profile. This sets whether the request must be made through the input form for the profile. This is usually set to
true. Setting this tofalseallows a signed request to be processed through the Certificate Manager's certificate profile framework, rather than through the input page for the certificate profile. - Certificate Profile Authentication. This sets the authentication method. An automated authentication is set by providing the instance ID for the authentication instance. If this field is blank, the authentication method is agent-approved enrollment; the request is submitted to the request queue of the agent services interface.Unless it is for a TMS subsystem, administrators must select one of the following authentication plug-ins:
CMCAuth: Use this plug-in when a CA agent must approve and submit the enrollment request.CMCUserSignedAuth: Use this plug-in to enable non-agent users to enroll own certificates.
- Click . The plug-in editor closes, and the new profile is listed in the profiles tab.
- Configure the policies, inputs, and outputs for the new profile. Select the new profile from the list, and click .
- Set up policies in the Policies tab of the Certificate Profile Rule Editor window. The Policies tab lists policies that are already set by default for the profile type.
- To add a policy, click .
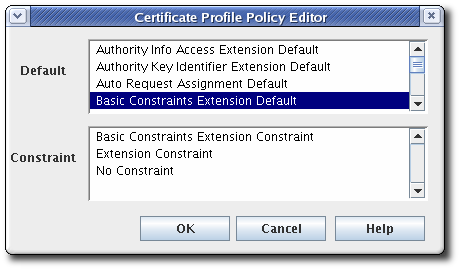
- Choose the default from the Default field, choose the constraints associated with that policy in the Constraints field, and click .

- Fill in the policy set ID. When issuing dual key pairs, separate policy sets define the policies associated with each certificate. Then fill in the certificate profile policy ID, a name or identifier for the certificate profile policy.
- Configure any parameters in the Defaults and Constraints tabs.
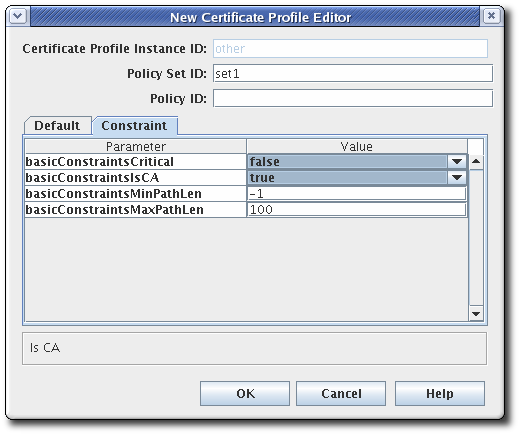 Defaults defines attributes that populate the certificate request, which in turn determines the content of the certificate. These can be extensions, validity periods, or other fields contained in the certificates. Constraints defines valid values for the defaults.See Section B.1, “Defaults Reference” and Section B.2, “Constraints Reference” for complete details for each default or constraint.
Defaults defines attributes that populate the certificate request, which in turn determines the content of the certificate. These can be extensions, validity periods, or other fields contained in the certificates. Constraints defines valid values for the defaults.See Section B.1, “Defaults Reference” and Section B.2, “Constraints Reference” for complete details for each default or constraint.
To modify an existing policy, select a policy, and click . Then edit the default and constraints for that policy.To delete a policy, select the policy, and click . - Set inputs in the Inputs tab of the Certificate Profile Rule Editor window. There can be more than one input type for a profile.
Note
Unless you configure the profile for a TMS subsystem, select onlycmcCertReqInputand delete other profiles by selecting them and clicking the button.- To add an input, click .
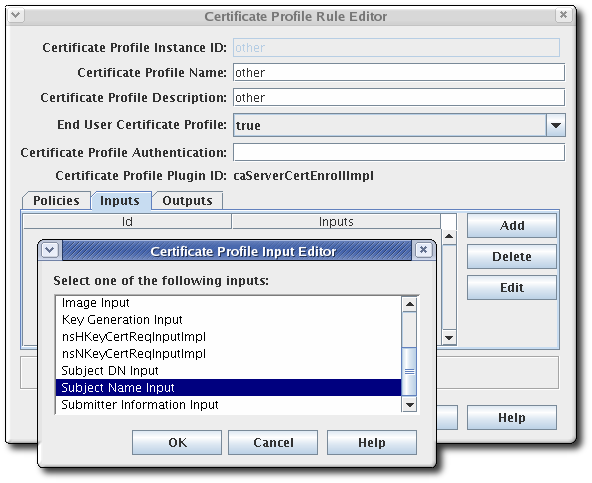
- Choose the input from the list, and click . See Section A.1, “Input Reference” for complete details of the default inputs.
- The New Certificate Profile Editor window opens. Set the input ID, and click .
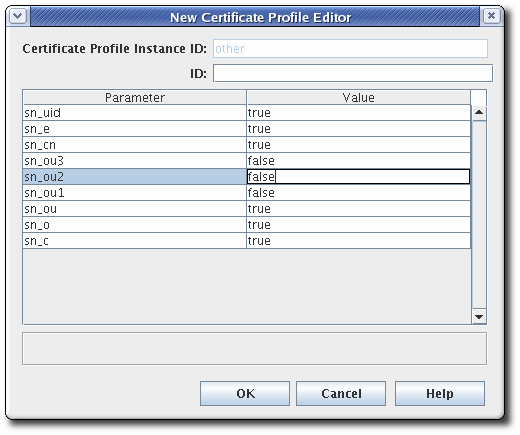
Inputs can be added and deleted. It is possible to select edit for an input, but since inputs have no parameters or other settings, there is nothing to configure.To delete an input, select the input, and click . - Set up outputs in the Outputs tab of the Certificate Profile Rule Editor window.Outputs must be set for any certificate profile that uses an automated authentication method; no output needs to be set for any certificate profile that uses agent-approved authentication. The Certificate Output type is set by default for all profiles and is added automatically to custom profiles.Unless you configure the profile for a TMS subsystem, select only
certOutput. Outputs can be added and deleted. It is possible to select edit for an output, but since outputs have no parameters or other settings, there is nothing to configure.
Outputs can be added and deleted. It is possible to select edit for an output, but since outputs have no parameters or other settings, there is nothing to configure.- To add an output, click .
- Choose the output from the list, and click .
- Give a name or identifier for the output, and click .This output will be listed in the output tab. You can edit it to provide values to the parameters in this output.
To delete an output, select the output from list, and click . - Restart the CA to apply the new profile.
systemctl restart pki-tomcatd-nuxwdog@instance_name.service
- After creating the profile as an administrator, a CA agent has to approve the profile in the agent services pages to enable the profile.
- Open the CA's services page.
https://server.example.com:8443/ca/services
- Click the Manage Certificate Profiles link. This page lists all of the certificate profiles that have been set up by an administrator, both active and inactive.
- Click the name of the certificate profile to approve.
- At the bottom of the page, click the button.

Note
If this profile will be used with a TPS, then the TPS must be configured to recognized the profile type. This is in 11.1.4. Managing Smart Card CA Profiles in Red Hat Certificate System's Planning, Installation, and Deployment Guide.
Authorization methods for the profiles can only be added to the profile using the command line, as described in the section Creating and Editing Certificate Profiles Directly on the File System in Red Hat Certificate System Planning, Installation and Deployment Guide.
3.2.2.2. Editing Certificate Profiles in the Console
To modify an existing certificate profile:
- Log into the agent services pages and disable the profile.Once a certificate profile is enabled by an agent, that certificate profile is marked enabled in the Certificate Profile Instance Management tab, and the certificate profile cannot be edited in any way through the console.
- Log in to the Certificate System CA subsystem console.
pkiconsole https://server.example.com:8443/ca
- In the Configuration tab, select Certificate Manager, and then select Certificate Profiles.
- Select the certificate profile, and click .
- The Certificate Profile Rule Editor window appears. Many any changes to the defaults, constraints, inputs, or outputs.
Note
The profile instance ID cannot be modified.If necessary, enlarge the window by pulling out one of the corners of the window. - Restart the CA to apply the changes.
- In the agent services page, re-enable the profile.
Note
Delete any certificate profiles that will not be approved by an agent. Any certificate profile that appears in the Certificate Profile Instance Management tab also appears in the agent services interface. If a profile has already been enabled, it must be disabled by the agent before it can be deleted from the profile list.
3.2.3. Listing Certificate Enrollment Profiles
The following pre-defined certificate profiles are ready to use and set up in this environment when the Certificate System CA is installed. These certificate profiles have been designed for the most common types of certificates, and they provide common defaults, constraints, authentication methods, inputs, and outputs.
To list the available profiles on the command line, use the
pki utility. For example:
# pki -c password -n caadmin ca-profile-find ------------------ 59 entries matched ------------------ Profile ID: caCMCserverCert Name: Server Certificate Enrollment using CMC Description: This certificate profile is for enrolling server certificates using CMC. Profile ID: caCMCECserverCert Name: Server Certificate wth ECC keys Enrollment using CMC Description: This certificate profile is for enrolling server certificates with ECC keys using CMC. Profile ID: caCMCECsubsystemCert Name: Subsystem Certificate Enrollment with ECC keys using CMC Description: This certificate profile is for enrolling subsystem certificates with ECC keys using CMC. Profile ID: caCMCsubsystemCert Name: Subsystem Certificate Enrollment using CMC Description: This certificate profile is for enrolling subsystem certificates using CMC. ... ----------------------------- Number of entries returned 20
For further details, see the pki-ca-profile(1) man page. Additional information can also be found at Red Hat Certificate System Planning, Installation, and Deployment Guide.
3.2.4. Displaying Details of a Certificate Enrollment Profile
For example, to display a specific certificate profile, such as
caECFullCMCUserSignedCert:
$ pki -c password -n caadmin ca-profile-show caECFullCMCUserSignedCert
-----------------------------------
Profile "caECFullCMCUserSignedCert"
-----------------------------------
Profile ID: caECFullCMCUserSignedCert
Name: User-Signed CMC-Authenticated User Certificate Enrollment
Description: This certificate profile is for enrolling user certificates with EC keys by using the CMC certificate request with non-agent user CMC authentication.
Name: Certificate Request Input
Class: cmcCertReqInputImpl
Attribute Name: cert_request
Attribute Description: Certificate Request
Attribute Syntax: cert_request
Name: Certificate Output
Class: certOutputImpl
Attribute Name: pretty_cert
Attribute Description: Certificate Pretty Print
Attribute Syntax: pretty_print
Attribute Name: b64_cert
Attribute Description: Certificate Base-64 Encoded
Attribute Syntax: pretty_print
For example, to display a specific certificate profile, such as
caECFullCMCUserSignedCert, in raw format:
$ pki -c password -n caadmin ca-profile-show caECFullCMCUserSignedCert --raw #Wed Jul 25 14:41:35 PDT 2018 auth.instance_id=CMCUserSignedAuth policyset.cmcUserCertSet.1.default.params.name= policyset.cmcUserCertSet.4.default.class_id=authorityKeyIdentifierExtDefaultImpl policyset.cmcUserCertSet.6.default.params.keyUsageKeyCertSign=false policyset.cmcUserCertSet.10.default.class_id=noDefaultImpl policyset.cmcUserCertSet.10.constraint.name=Renewal Grace Period Constraint output.o1.class_id=certOutputImpl ...
For further details, see the pki-ca-profile(1) man page.