Questo contenuto non è disponibile nella lingua selezionata.
27.4. Defining Role-Based Access Controls
Role-based access control grants a very different kind of authority to users compared to self-service and delegation access controls. Role-based access controls are fundamentally administrative, with the potential to add, delete, and significantly modify entries.
There are three parts to role-based access controls:
- The permission. The permission defines a specific operation or set of operations (write, add, or delete) and the target entries within the IdM LDAP directory to which those operations apply. Permissions are building blocks; they can be assigned to multiple privileges as needed.
- The privileges available to a role. A privilege is essentially a group of permissions. Permissions are not applied directly to a role. Permissions are added to a privilege so that the privilege creates a coherent and complete picture of a set of access control rules. For example, a permission can be created to add, edit, and delete automount locations. Then that permission can be combined with another permission relating to managing FTP services, and they can be used to create a single privilege that relates to managing filesystems.
- The role. This is the list of IdM users who are able to perform the actions defined in the privileges.
It is possible to create entirely new permissions, as well as to create new privileges based on existing permissions or new permissions.
27.4.1. Creating Roles
Copia collegamentoCollegamento copiato negli appunti!
27.4.1.1. Creating Roles in the Web UI
Copia collegamentoCollegamento copiato negli appunti!
- Open the IPA Server tab in the top menu, and select the Role Based Access Control subtab.
- Click the Add link at the top of the list of role-based ACIs.
- Enter the role name and a description.
- Click the button to save the new role and go to the configuration page.
- At the top of the Users tab, or in the Users Groups tab when adding groups, click the Add link.
- Select the users on the left and use the button to move them to the assigned box.
- Open the Privileges tab in the role configuration page.
- Click the Add link at the top of the list of privileges to add a new privilege.
- Select the privileges on the left and use the button to move them to the assigned box.
- Click the button to save.
27.4.1.2. Creating Roles in the Command Line
Copia collegamentoCollegamento copiato negli appunti!
- Add the new role:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the required privileges to the role:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Add the required groups to the role. In this case, we are adding only a single group,
useradmin, which already exists.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
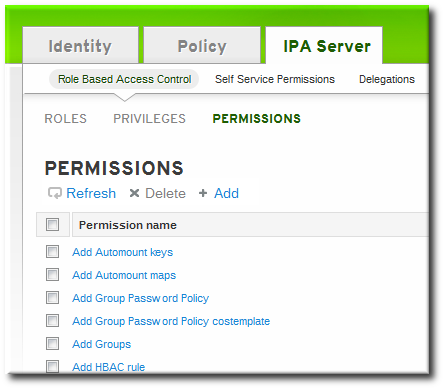
27.4.2. Creating New Permissions
Copia collegamentoCollegamento copiato negli appunti!
27.4.2.1. Creating New Permissions from the Web UI
Copia collegamentoCollegamento copiato negli appunti!
- Open the IPA Server tab in the top menu, and select the Role Based Access Control subtab.
- Select the Permissions task link.
- Click the Add link at the top of the list of permissions.
- Enter the name of the new permission.
- Select the checkboxes next to the allowed operations for this permission.
- Select the method to use to identify the target entries from the Target drop-down menu. There are four different methods:
- Type looks for an entry type like user, host, or service and then provides a list of all possible attributes for that entry type. The attributes which will be accessible through this ACI are selected from the list.
- Filter uses an LDAP filter to identify which entries the permission applies to.
- Subtree targets every entry beneath the specified subtree entry. All attributes within the matching entries can be modified.
- Target group specifies a user group, and all the user entries within that group are available through the ACI. All attributes within the matching entries can be modified.
- Fill in the required information to identify the target entries, depending on the selected type.
- For Filter, Subtree, and Target group targets, click the Add link to add attributes that are included in the permission. A single attribute is added at a time; to add multiple attributes, click the Add again to add another field.If no attributes are set for the permission then, by default, all attributes are excluded.
- Click the button to save the permission.
27.4.2.2. Creating New Permissions from the Command Line
Copia collegamentoCollegamento copiato negli appunti!
A new permission is added using the
permission-add command. All permissions require a list of attributes over which permission is granted (--attr), a list of allowed actions (--permissions), and the target entries for the ACI. There are four methods to identify the target entries:
- --type looks for an entry type like user, host, or service and then provides a list of all possible attributes for that entry type.
- --filter uses an LDAP filter to identify which entries the permission applies to.
- --subtree targets every entry beneath the specified subtree entry.
- --targetgroup specifies a user group, and all the user entries within that group are available through the ACI.
Example 27.1. Adding a Permission with a Filter
A filter can be any valid LDAP filter.
ipa permission-add "manage Windows groups" --filter="(!(objectclass=posixgroup))" --permissions=write --attrs=description
$ ipa permission-add "manage Windows groups" --filter="(!(objectclass=posixgroup))" --permissions=write --attrs=descriptionNote
The
permission-add command does not validate the given LDAP filter. Verify that the filter returns the expected results before configuring the permission.
Example 27.2. Adding a Permission for a Subtree
All a subtree filter requires is a DN within the directory. Since IdM uses a simplified, flat directory tree structure, this can be used to target some types of entries, like automount locations, which are containers or parent entries for other configuration.
ipa permission-add "manage automount locations" --subtree="ldap://ldap.example.com:389/cn=automount,dc=example,dc=com" --permissions=write --attrs=automountmapname,automountkey,automountInformation
$ ipa permission-add "manage automount locations" --subtree="ldap://ldap.example.com:389/cn=automount,dc=example,dc=com" --permissions=write --attrs=automountmapname,automountkey,automountInformationExample 27.3. Adding a Permission Based on Object Type
There seven object types that can be used to form a permission:
- user
- group
- host
- service
- hostgroup
- netgroup
- dnsrecord
Each type has its own set of allowed attributes, in a comma-separated list.
ipa permission-add "manage service" --permissions=all --type=service --attrs=krbprincipalkey,krbprincipalname,managedby
$ ipa permission-add "manage service" --permissions=all --type=service --attrs=krbprincipalkey,krbprincipalname,managedby
The attributes (
--attrs) must exist and be allowed attributes for the given object type, or the permission operation fails with schema syntax errors.
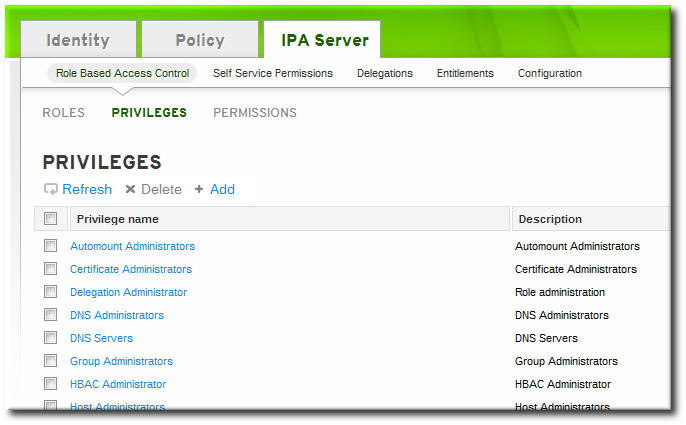
27.4.3. Creating New Privileges
Copia collegamentoCollegamento copiato negli appunti!
27.4.3.1. Creating New Privileges from the Web UI
Copia collegamentoCollegamento copiato negli appunti!
- Open the IPA Server tab in the top menu, and select the Role Based Access Control subtab.
- Select the Privileges task link.
- Click the Add link at the top of the list of privileges.
- Enter the name and a description of the privilege.
- Click the button to go to the privilege configuration page to add permissions.
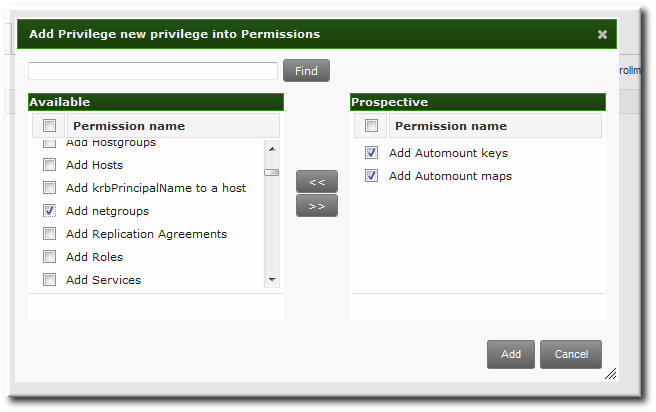
- Select the Permissions tab.
- Click the Add link at the top of the list of permissions to add permission to the privilege.
- Click the checkbox by the names of the permissions to add, and click the right arrows button, , to move the permissions to the selection box.
- Click the button.
27.4.3.2. Creating New Privileges from the Command Line
Copia collegamentoCollegamento copiato negli appunti!
Privilege entries are created using the
privilege-add command, and then permissions are added to the privilege group using the privilege-add-permission command.
- Create the privilege entry.
ipa privilege-add "managing filesystems" --desc="for filesystems"
$ ipa privilege-add "managing filesystems" --desc="for filesystems"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Assign the desired permissions. For example:
ipa privilege-add-permission "managing filesystems" --permissions="managing automount","managing ftp services"
$ ipa privilege-add-permission "managing filesystems" --permissions="managing automount","managing ftp services"Copy to Clipboard Copied! Toggle word wrap Toggle overflow