Questo contenuto non è disponibile nella lingua selezionata.
Chapter 7. Managing the validity of certificates in IdM
In Identity Management (IdM), you can manage the validity of both already existing certificates and certificates you want to issue in the future, but the methods are different.
7.1. Managing the validity of an existing certificate that was issued by IdM CA
In IdM, the following methods of viewing the expiry date of a certificate are available:
You can manage the validity of an already existing certificate that was issued by IdM CA in the following ways:
Renew a certificate by requesting a new certificate using either the original certificate signing request (CSR) or a new CSR generated from the private key. You can request a new certificate using the following utilities:
- certmonger
-
You can use
certmongerto request a service certificate. Before the certificate is due to expire,certmongerwill automatically renew the certificate, thereby ensuring a continuing validity of the service certificate. For details, see Obtaining an IdM certificate for a service using certmonger; - certutil
-
You can use
certutilto renew user, host, and service certificates. For details on requesting a user certificate, see Requesting a new user certificate and exporting it to the client; - openssl
-
You can use
opensslto renew user, host, and service certificates.
Revoke a certificate. For details, see:
Restore a certificate if it has been temporarily revoked. For details, see:
7.2. Managing the validity of future certificates issued by IdM CA
To manage the validity of future certificates issued by IdM CA, modify, import, or create a certificate profile. For details, see Creating and managing certificate profiles in Identity Management.
7.3. Viewing the expiry date of a certificate in IdM WebUI
You can use IdM WebUI to view the expiry date of all the certificates that have been issued by IdM CA.
Prerequisites
- Ensure that you have obtained the administrator’s credentials.
Procedure
-
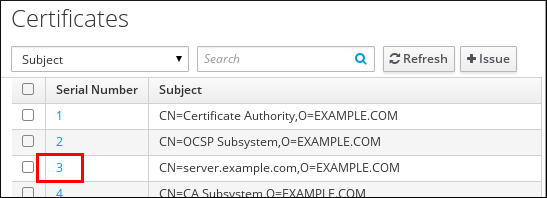
In the
Authenticationmenu, clickCertificates>Certificates. Click the serial number of the certificate to open the certificate information page.
Figure 7.1. List of Certificates
-
In the certificate information page, locate the
Expires Oninformation.
7.4. Viewing the expiry date of a certificate in the CLI
You can use the command line (CLI) to view the expiry date of a certificate.
Procedure
Use the
opensslutility to open the file in a human-readable format:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.5. Revoking certificates with the integrated IdM CAs
7.5.1. Certificate revocation reasons
A revoked certificate is invalid and cannot be used for authentication. All revocations are permanent, except for reason 6: Certificate Hold.
The default revocation reason is 0: unspecified.
| ID | Reason | Explanation |
|---|---|---|
| 0 | Unspecified | |
| 1 | Key Compromised | The key that issued the certificate is no longer trusted. Possible causes: lost token, improperly accessed file. |
| 2 | CA Compromised | The CA that issued the certificate is no longer trusted. |
| 3 | Affiliation Changed | Possible causes: * A person has left the company or moved to another department. * A host or service is being retired. |
| 4 | Superseded | A newer certificate has replaced the current certificate. |
| 5 | Cessation of Operation | The host or service is being decommissioned. |
| 6 | Certificate Hold | The certificate is temporarily revoked. You can restore the certificate later. |
| 8 | Remove from CRL | The certificate is not included in the certificate revocation list (CRL). |
| 9 | Privilege Withdrawn | The user, host, or service is no longer permitted to use the certificate. |
| 10 | Attribute Authority (AA) Compromise | The AA certificate is no longer trusted. |
7.5.2. Revoking certificates with the integrated IdM CAs using IdM WebUI
If you know you have lost the private key for your certificate, you must revoke the certificate to prevent its abuse. Complete this procedure to use the IdM WebUI to revoke a certificate issued by the IdM CA.
Procedure
-
Click
Authentication>Certificates>Certificates. Click the serial number of the certificate to open the certificate information page.
Figure 7.2. List of Certificates
-
In the certificate information page, click
. - Select the reason for revoking and click . See Certificate revocation reasons for details.
7.5.3. Revoking certificates with the integrated IdM CAs using IdM CLI
If you know you have lost the private key for your certificate, you must revoke the certificate to prevent its abuse. Complete this procedure to use the IdM CLI to revoke a certificate issued by the IdM CA.
Procedure
Use the
ipa cert-revokecommand, and specify:- the certificate serial number
- the ID number for the revocation reason; see Certificate revocation reasons for details
For example, to revoke the certificate with serial number 1032 because of reason 1: Key Compromised, enter:
ipa cert-revoke 1032 --revocation-reason=1
$ ipa cert-revoke 1032 --revocation-reason=1For details on requesting a new certificate, see the following documentation:
7.6. Restoring certificates with the integrated IdM CAs
If you have revoked a certificate because of reason 6: Certificate Hold, you can restore it again if the private key for the certificate has not been compromised. To restore a certificate, use one of the following procedures:
7.6.1. Restoring certificates with the integrated IdM CAs using IdM WebUI
Complete this procedure to use the IdM WebUI to restore an IdM certificate that has been revoked because of Reason 6: Certificate Hold.
Procedure
-
In the
Authenticationmenu, clickCertificates>Certificates. Click the serial number of the certificate to open the certificate information page.
Figure 7.3. List of Certificates
-
In the certificate information page, click
.
7.6.2. Restoring certificates with the integrated IdM CAs using IdM CLI
Complete this procedure to use the IdM CLI to restore an IdM certificate that has been revoked because of Reason 6: Certificate Hold.
Procedure
Use the
ipa cert-remove-holdcommand and specify the certificate serial number. For example:ipa cert-remove-hold 1032
$ ipa cert-remove-hold 1032Copy to Clipboard Copied! Toggle word wrap Toggle overflow