Questo contenuto non è disponibile nella lingua selezionata.
Chapter 4. Red Hat Quay Robot Account overview
Robot Accounts are used to set up automated access to the repositories in your Red Hat Quay. registry. They are similar to OpenShift Container Platform service accounts.
Setting up a Robot Account results in the following:
- Credentials are generated that are associated with the Robot Account.
- Repositories and images that the Robot Account can push and pull images from are identified.
- Generated credentials can be copied and pasted to use with different container clients, such as Docker, Podman, Kubernetes, Mesos, and so on, to access each defined repository.
Robot Accounts can help secure your Red Hat Quay registry by offering various security advantages, such as the following:
- Specifying repository access.
-
Granular permissions, such as
Read(pull) orWrite(push) access. They can also be equipped withAdminpermissions if warranted. - Designed for CI/CD pipelines, system integrations, and other automation tasks, helping avoid credential exposure in scripts, pipelines, or other environment variables.
- Robot Accounts use tokens instead of passwords, which provides the ability for an administrator to revoke the token in the event that it is compromised.
Each Robot Account is limited to a single user namespace or Organization. For example, the Robot Account could provide access to all repositories for the user quayadmin. However, it cannot provide access to repositories that are not in the user’s list of repositories.
Robot Accounts can be created using the Red Hat Quay UI, or through the CLI using the Red Hat Quay API. After creation, Red Hat Quay administrators can leverage more advanced features with Robot Accounts, such as keyless authentication.
4.1. Creating a robot account by using the UI
Use the following procedure to create a robot account using the v2 UI.
Procedure
- On the v2 UI, click Organizations.
-
Click the name of the organization that you will create the robot account for, for example,
test-org. -
Click the Robot accounts tab
Create robot account. -
In the Provide a name for your robot account box, enter a name, for example,
robot1. The name of your Robot Account becomes a combination of your username plus the name of the robot, for example,quayadmin+robot1 Optional. The following options are available if desired:
- Add the robot account to a team.
- Add the robot account to a repository.
- Adjust the robot account’s permissions.
On the Review and finish page, review the information you have provided, then click Review and finish. The following alert appears: Successfully created robot account with robot name: <organization_name> + <robot_name>.
Alternatively, if you tried to create a robot account with the same name as another robot account, you might receive the following error message: Error creating robot account.
- Optional. You can click Expand or Collapse to reveal descriptive information about the robot account.
-
Optional. You can change permissions of the robot account by clicking the kebab menu
Set repository permissions. The following message appears: Successfully updated repository permission. Optional. You can click the name of your robot account to obtain the following information:
- Robot Account: Select this obtain the robot account token. You can regenerate the token by clicking Regenerate token now.
- Kubernetes Secret: Select this to download credentials in the form of a Kubernetes pull secret YAML file.
-
Podman: Select this to copy a full
podman logincommand line that includes the credentials. -
Docker Configuration: Select this to copy a full
docker logincommand line that includes the credentials.
4.2. Creating a robot account by using the Red Hat Quay API
Use the following procedure to create a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to create a new robot account for an organization using the
PUT /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "orgname+robot-name", "created": "Fri, 10 May 2024 15:11:00 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to create a new robot account for the current user with the
PUT /api/v1/user/robots/{robot_shortname}endpoint:curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"
$ curl -X PUT -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/user/robots/<robot_name>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}{"name": "quayadmin+robot-name", "created": "Fri, 10 May 2024 15:24:57 -0000", "last_accessed": null, "description": "", "token": "<example_secret>", "unstructured_metadata": null}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3. Bulk managing robot account repository access
Use the following procedure to manage, in bulk, robot account repository access by using the Red Hat Quay v2 UI.
Prerequisites
- You have created a robot account.
- You have created multiple repositories under a single organization.
Procedure
- On the Red Hat Quay v2 UI landing page, click Organizations in the navigation pane.
- On the Organizations page, select the name of the organization that has multiple repositories. The number of repositories under a single organization can be found under the Repo Count column.
- On your organization’s page, click Robot accounts.
-
For the robot account that will be added to multiple repositories, click the kebab icon
Set repository permissions. On the Set repository permissions page, check the boxes of the repositories that the robot account will be added to. For example:
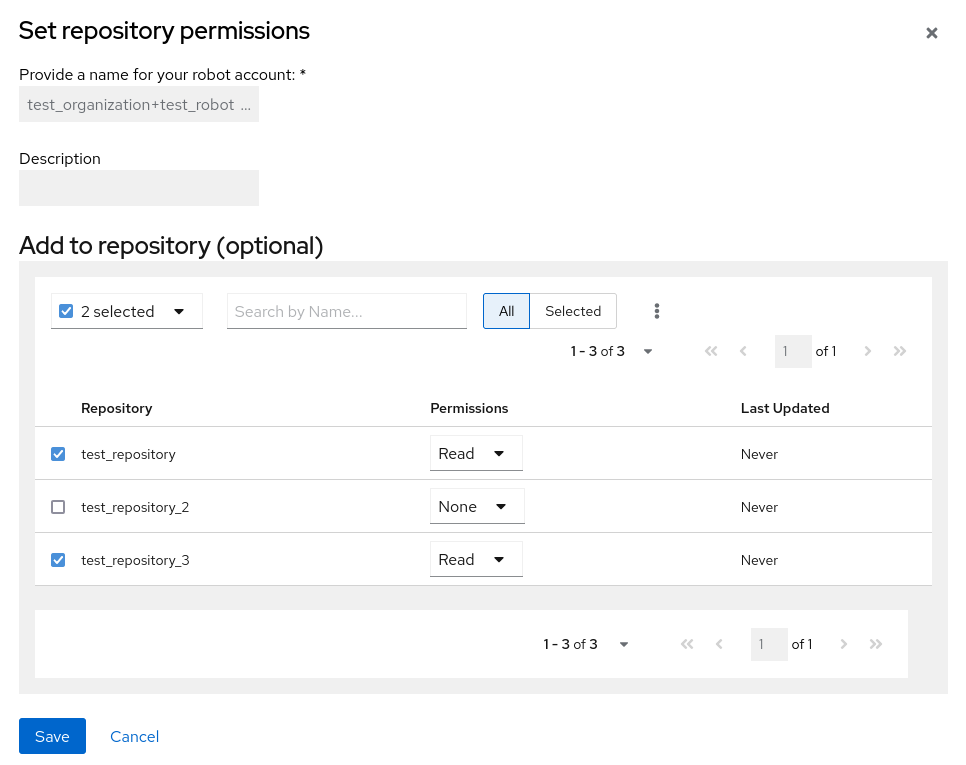
- Set the permissions for the robot account, for example, None, Read, Write, Admin.
- Click save. An alert that says Success alert: Successfully updated repository permission appears on the Set repository permissions page, confirming the changes.
-
Return to the Organizations
Robot accounts page. Now, the Repositories column of your robot account shows the number of repositories that the robot account has been added to.
4.4. Disabling robot accounts by using the UI
Red Hat Quay administrators can manage robot accounts by disallowing users to create new robot accounts.
Robot accounts are mandatory for repository mirroring. Setting the ROBOTS_DISALLOW configuration field to true breaks mirroring configurations. Users mirroring repositories should not set ROBOTS_DISALLOW to true in their config.yaml file. This is a known issue and will be fixed in a future release of Red Hat Quay.
Use the following procedure to disable robot account creation.
Prerequisites
- You have created multiple robot accounts.
Procedure
Update your
config.yamlfield to add theROBOTS_DISALLOWvariable, for example:ROBOTS_DISALLOW: true
ROBOTS_DISALLOW: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Restart your Red Hat Quay deployment.
Verification: Creating a new robot account
- Navigate to your Red Hat Quay repository.
- Click the name of a repository.
- In the navigation pane, click Robot Accounts.
- Click Create Robot Account.
-
Enter a name for the robot account, for example,
<organization-name/username>+<robot-name>. -
Click Create robot account to confirm creation. The following message appears:
Cannot create robot account. Robot accounts have been disabled. Please contact your administrator.
Verification: Logging into a robot account
On the command-line interface (CLI), attempt to log in as one of the robot accounts by entering the following command:
podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow The following error message is returned:
Error: logging into "<quay-server.example.com>": invalid username/password
Error: logging into "<quay-server.example.com>": invalid username/passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can pass in the
log-level=debugflag to confirm that robot accounts have been deactivated:podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>
$ podman login -u="<organization-name/username>+<robot-name>" -p="KETJ6VN0WT8YLLNXUJJ4454ZI6TZJ98NV41OE02PC2IQXVXRFQ1EJ36V12345678" --log-level=debug <quay-server.example.com>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.
... DEBU[0000] error logging into "quay-server.example.com": unable to retrieve auth token: invalid username/password: unauthorized: Robot accounts have been disabled. Please contact your administrator.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.5. Regenerating a robot account token by using the Red Hat Quay API
Use the following procedure to regenerate a robot account token using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to regenerate a robot account token for an organization using the
POST /api/v1/organization/{orgname}/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<orgname>/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "test-org+test", "created": "Fri, 10 May 2024 17:46:02 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to regenerate a robot account token for the current user with the
POST /api/v1/user/robots/{robot_shortname}/regenerateendpoint:curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"
$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>/regenerate"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}{"name": "quayadmin+test", "created": "Fri, 10 May 2024 14:12:11 -0000", "last_accessed": null, "description": "", "token": "<example_secret>"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.6. Deleting a robot account by using the UI
Use the following procedure to delete a robot account using the Red Hat Quay UI.
Procedure
- Log into your Red Hat Quay registry:
- Click the name of the Organization that has the robot account.
- Click Robot accounts.
- Check the box of the robot account to be deleted.
- Click the kebab menu.
- Click Delete.
-
Type
confirminto the textbox, then click Delete.
4.7. Deleting a robot account by using the Red Hat Quay API
Use the following procedure to delete a robot account using the Red Hat Quay API.
Prerequisites
- You have Created an OAuth access token.
Procedure
Enter the following command to delete a robot account for an organization using the
DELETE /api/v1/organization/{orgname}/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"
curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/organization/<organization_name>/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/organization/{orgname}/robotscommand to see if details are returned for the robot account:curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"
$ curl -X GET -H "Authorization: Bearer <bearer_token>" "https://<quay-server.example.com>/api/v1/organization/<organization_name>/robots"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"robots": []}{"robots": []}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enter the following command to delete a robot account for the current user with the
DELETE /api/v1/user/robots/{robot_shortname}endpoint:curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X DELETE \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow The CLI does not return information when deleting a robot account for the current user with the API. To confirm deletion, you can check the Red Hat Quay UI, or you can enter the following
GET /api/v1/user/robots/{robot_shortname}command to see if details are returned for the robot account:curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"
$ curl -X GET \ -H "Authorization: Bearer <bearer_token>" \ "<quay-server.example.com>/api/v1/user/robots/<robot_shortname>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"message":"Could not find robot with specified username"}{"message":"Could not find robot with specified username"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow