이 콘텐츠는 선택한 언어로 제공되지 않습니다.
7.5. Known Issues
Red Hat Certificate System 9.1 is affected by the following known issues:
Important
Note that this document only contains release notes for features which are not available in the base Red Hat Enterprise Linux 7.3 release. Some known issues in Red Hat Certificate System are in the pki-core, and those are documented in Red Hat Enterprise Linux 7.3 Release Notes.
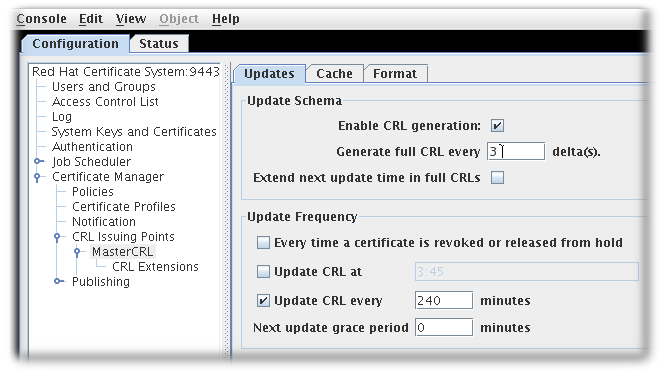
CRL cannot be configured in console to update after every revocation or release from hold unless grace period is set
Currently, the Certificate Revocation List (CRL) update cannot be configured solely based on certificate revocation events. When setting full and delta CRL schedules, the Update CRL every time a certificate is revoked or released from hold option also requires you to fill out the two grace period settings.
Thus, in order to select this option you need to first select the Update CRL every option and enter a number for the Next update grace period # minutes box.
Firefox can no longer enroll a signing and an archival certificate at the same time
The
caDualCert.cfg profile previously used the Mozilla cryptographic object to create two requests, one for a signing certificate and the other for an encryption certificate, with private key archival specified for the encryption certificate. Since Mozilla has removed the generateCRMFRequest() object, Red Hat Certificate System can no longer support this type of enrollment within the browser.
The following procedure specifies how to generate the same two certificates using the
pki command line interface (CLI) tools. It describes manual user signing and encryption certificates enrollment.
- Enroll for the signing-only certificate:
- Create the certificate signing request (CSR) using
certutil:certutil -R -k rsa -g 2048 -s "CN=John Smith,O=Example Corp,L=Mountain View,ST=California,C=US" -d ./ -a -o cert.cer
certutil -R -k rsa -g 2048 -s "CN=John Smith,O=Example Corp,L=Mountain View,ST=California,C=US" -d ./ -a -o cert.cerCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Send the request to the Certificate Authority (CA) using the
caSigningUserCertprofile:pki ca cert-request-submit --csr-file ./cert.cer --profile caSigningUserCert --subject "CN=John Smith,O=Example Corp,L=Mountain View,ST=California,C=US"
pki ca cert-request-submit --csr-file ./cert.cer --profile caSigningUserCert --subject "CN=John Smith,O=Example Corp,L=Mountain View,ST=California,C=US"Copy to Clipboard Copied! Toggle word wrap Toggle overflow - The final certificate can be retrieved using the standard end entity (EE) graphical user interface of the product:
- Enroll for the encryption-only certificate:
- Obtain the transport certificate from the Key Recovery Authority (KRA):
pki -C "" -U 'https://localhost:8443/ca' cert-show 0x07 --encoded --output transport.pem
pki -C "" -U 'https://localhost:8443/ca' cert-show 0x07 --encoded --output transport.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow - One can make sure that certificate
0x07is actually the transport certificate for the KRA by consulting the end entity interface of the product. If the certificate happens to have a different ID, use that one instead of0x07. - Use the
CRMFPopClientcommand to create the CSR for the encryption certificate that will have the private key archived to the KRA.Here we use thecaEncUserCertprofile to obtain this certificate:CRMFPopClient -d . -p password "secret123" -o csr -a rsa -l 2048 -n "UID=username" -f caEncUserCert -b transport.pem
CRMFPopClient -d . -p password "secret123" -o csr -a rsa -l 2048 -n "UID=username" -f caEncUserCert -b transport.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Get the enrollment template for the
caEncUserCertprofile:pki -v -C "secret123" -U https://localhost:8443/ca cert-request-profile-show caEncUserCert --output encuser.xml
pki -v -C "secret123" -U https://localhost:8443/ca cert-request-profile-show caEncUserCert --output encuser.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Sanitize the line endings in the
csrfile you just created:dos2unix csr
dos2unix csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Fill in the enrollment template as follows:
cert_request_type = crmf cert_request = <copied certificate request blob from the file csr> sn_cn = <your cn value>
cert_request_type = crmf cert_request = <copied certificate request blob from the file csr> sn_cn = <your cn value>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Submit the final request to the CA:
pki -v -C "secret123" -U https://localhost.localdomain:8443/ca cert-request-submit encuser.xml
pki -v -C "secret123" -U https://localhost.localdomain:8443/ca cert-request-submit encuser.xmlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The terminal should print out success or failure of the enrollment.
If the enrollment is successful, the agent can approve this request, issuing the certificate. Note that the approval will trigger an archival of the encryption key to the KRA.
The EE interface of the product can be used to obtain the new encryption certificate.
caUserCert profile request using Internet Explorer 10 results in an Invalid request error
Currently, when trying to submit request using
caUserCert profile using Internet Explorer 10 from Windows 7, the request results in the "Invalid request" error. The following procedure specifies how to work around this problem.
- Go to the Internet Options/Advanced/Security section and uncheck the TLS 1.2 box to connect to the SSL port.
- Go to the End Entity page which allows downloading and importing the CA certificate chain. Add the CA certificate to the Trusted CAs list.
- Go to Internet Options and enter the Security tab. Add the SSL url to the Trusted Sites list. Set the security slider to medium high or, alternatively, choose medium or below if trying to troubleshoot problems.
- Go to the Compatibility View Settings settings by clicking the Tools dropdown menu on the right and add the site to the list. Alternatively, enable the view for intranet sites or all sites.
- Go to the usual dual use profile enrollment page. The browser will probably issue a warning that a cryptographic operation is about to occur. Accept that by clickign OK. At this point the display should have a drop down list next to the key size list that contains the Communication Service Providers (CSPs). If this list is not empty, attempt an enrollment.
The console does not enable a separate ticking of the Update CRL every time a certificate is revoked or released from hold option
Currently, when setting full and delta CRL schedules, the Update CRL every time a certificate is revoked or released from hold option also requires you to fill out the two grace period settings. Thus, in order to select the Update CRL every time a certificate is revoked or released from hold option you need to first select the Update CRL every option and enter a number for the Next update grace period # minutes box.
Additional steps needed when uninstalling TPS
Due to a known issue, you must perform some additional steps when uninstalling the Token Processing System which were not necessary in earlier versions. See the
pkidestroy(8) man page for instructions.