이 콘텐츠는 선택한 언어로 제공되지 않습니다.
3.2. Supported Platforms
This section describes the different server platforms, hardware, tokens, and software supported by Red Hat Certificate System 9.5.
3.2.1. Server Support
링크 복사링크가 클립보드에 복사되었습니다!
Running the Certificate Authority (CA), Key Recovery Authority (KRA), Online Certificate Status Protocol (OCSP), Token Key Service (TKS), and Token Processing System (TPS) subsystems of Certificate System 9.5 is supported on Red Hat Enterprise Linux 7.7 and later. The supported Directory Server version is 10.4 and later.
Note
Certificate System 9.5 is supported running on a Red Hat Enterprise Linux virtual guest on a certified hypervisor. For details, see the Which hypervisors are certified to run Red Hat Enterprise Linux? solution article.
3.2.2. Client Support
링크 복사링크가 클립보드에 복사되었습니다!
The Enterprise Security Client (ESC) is supported on:
- Red Hat Enterprise Linux 7.
- The latest versions of Red Hat Enterprise Linux 5 and 6.Although these platforms do not support Red Hat Certificate System 9.5, those clients can be used with the Token Management System (TMS) system in Red Hat Certificate System 9.5.
3.2.3. Supported Web Browsers
링크 복사링크가 클립보드에 복사되었습니다!
Certificate System 9.5 supports the following browsers:
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 60 and later [a] | Firefox 60 and later [a] |
| Windows 7 | Firefox 60 and later [a] |
Firefox 60 and later
[a] |
[a]
This Firefox version no longer supports the crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
| ||
Note
The only fully-supported browser for the HTML-based instance configuration is Mozilla Firefox.
3.2.4. Supported Smart Cards
링크 복사링크가 클립보드에 복사되었습니다!
The Enterprise Security Client (ESC) supports Global Platform 2.01-compliant smart cards and JavaCard 2.1 or higher.
The Certificate System subsystems have been tested using the following tokens:
- Gemalto TOP IM FIPS CY2 64K token (SCP01)
- Giesecke & Devrient (G&D) SmartCafe Expert 7.0 (SCP03)
- SafeNet Assured Technologies SC-650 (SCP01)
The only card manager applet supported with Certificate System is the CoolKey applet, which is part of the pki-tps package in Red Hat Certificate System.
3.2.5. Supported Hardware Security Modules
링크 복사링크가 클립보드에 복사되었습니다!
The following table lists Hardware Security Modules (HSM) supported by Red Hat Certificate System:
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| Thales nCipher nShield Connect 6000 | 2.61.2 | CipherTools-linux64-dev-12.30.00 | CipherTools-linux64-dev-12.30.00 |
|
Gemalto SafeNet Luna SA 1700 / 7000 (limited)
(Limited support [a] )
| 6.24.0 | 6.2.0-15 | libcryptoki-6.2.x86_64 |
[a]
For details about supported features, see Section 3.2.5.1, “Gemalto SafeNet Luna SA 1700 / 7000 (limited)”.
| |||
3.2.5.1. Gemalto SafeNet Luna SA 1700 / 7000 (limited)
링크 복사링크가 클립보드에 복사되었습니다!
This section provides information on supported features when using the Gemalto SafeNet Luna SA 1700 / 7000 HSM.
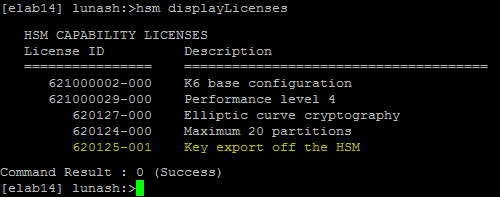
Gemalto SafeNet Luna SA only supports PKI private key extraction in its CKE - Key Export model, and only in non-FIPS mode. The Luna SA Cloning model and the CKE model in FIPS mode do not support PKI private key extraction. When the Luna SA CKE – Key Export Model is in FIPS mode, PKI private keys cannot be extracted.
- CL - Cloning Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: All asymmetric keys and objects are replicated when configured in an HA group
- Wrapping private (asymmetric) keys off the HSM: Not possible
Figure 3.1. Example of a Cloning Model
- CKE - Key Export Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Not possible
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: Not possible
- Wrapping private (asymmetric) keys off the HSM: Possible
Figure 3.2. Example of a Key Export Model