이 콘텐츠는 선택한 언어로 제공되지 않습니다.
Chapter 16. Configure Load Balancing-as-a-Service (LBaaS)
Load Balancing-as-a-Service (LBaaS) enables OpenStack Networking to distribute incoming requests evenly between designated instances. This step-by-step guide configures OpenStack Networking to use LBaaS with the Open vSwitch (OVS) plugin.
Introduced in Red Hat OpenStack Platform 5, Load Balancing-as-a-Service (LBaaS) enables OpenStack Networking to distribute incoming requests evenly between designated instances. This ensures the workload is shared predictably among instances, and allows more effective use of system resources. Incoming requests are distributed using one of these load balancing methods:
- Round robin - Rotates requests evenly between multiple instances.
- Source IP - Requests from a unique source IP address are consistently directed to the same instance.
- Least connections - Allocates requests to the instance with the least number of active connections.
Table 1: LBaaS features
| Feature | Description |
|---|---|
| Monitors | LBaaS provides availability monitoring with the ping, TCP, HTTP, and HTTPS GET methods. Monitors are implemented to determine whether pool members are available to handle requests. |
| Management | LBaaS is managed using a variety of tool sets. The REST API is available for programmatic administration and scripting. Users perform administrative management of load balancers through either the CLI (neutron) or the OpenStack dashboard. |
| Connection limits | Ingress traffic can be shaped with connection limits. This feature allows workload control and can also assist with mitigating DoS (Denial of Service) attacks. |
| Session persistence | LBaaS supports session persistence by ensuring incoming requests are routed to the same instance within a pool of multiple instances. LBaaS supports routing decisions based on cookies and source IP address. |
LBaaS is currently supported only with IPv4 addressing.
LBaaSv1 has been removed in Red Hat OpenStack Platform 10 (Newton), and replaced with LBaaSv2.
16.1. OpenStack Networking and LBaaS Topology
OpenStack Networking (neutron) services can be broadly classified into two categories.
1. - Neutron API server - This service runs the OpenStack Networking API server, which has the main responsibility of providing an API for end users and services to interact with OpenStack Networking. This server also has the responsibility of interacting with the underlying database to store and retrieve tenant network, router, and loadbalancer details, among others.
2. - Neutron Agents - These are the services that deliver various network functionality for OpenStack Networking.
- neutron-dhcp-agent - manages DHCP IP addressing for tenant private networks.
- neutron-l3-agent - facilitates layer 3 routing between tenant private networks, the external network, and others.
- neutron-lbaasv2-agent - provisions the LBaaS routers created by tenants.
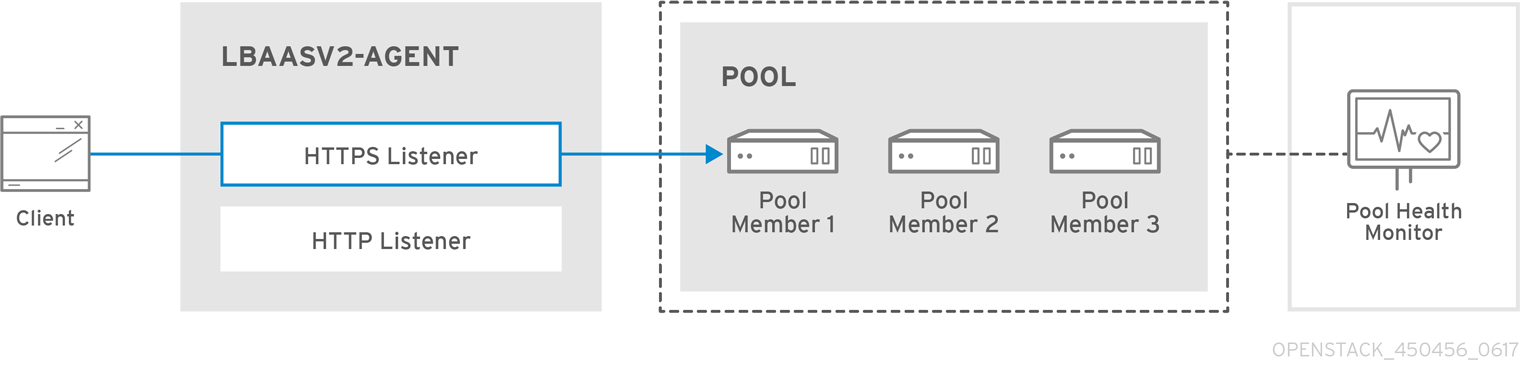
The following diagram describes the flow of HTTPS traffic through to a pool member:
16.1.1. Support Status of LBaaS
- LBaaS v1 API was deprecated in Red Hat OpenStack Platform 9 and removed in version 10.
- LBaaS v2 API was introduced in Red Hat OpenStack Platform 7, and is the only available LBaaS API as of version 10.
- LBaaS deployment is not currently supported in Red Hat OpenStack Platform director.
16.1.2. Service Placement
The OpenStack Networking services can either run together on the same physical server, or on separate dedicated servers.
Red Hat OpenStack Platform 10 added support for composable roles, allowing you to separate network services into a custom role. However, for simplicity, this guide assumes that a deployment uses the default controller role.
The server that runs API server is usually called the Controller node, whereas the server that runs the OpenStack Networking agents is called the Network node. An ideal production environment would separate these components to their own dedicated nodes for performance and scalability reasons, but a testing or PoC deployment might have them all running on the same node. This chapter covers both of these scenarios; the section under Controller node configuration need to be performed on the API server, whereas the section on Network node is performed on the server that runs the LBaaS agent.
If both the Controller and Network roles are on the same physical node, then the steps must be performed on that server.
16.2. Configure LBaaS
This procedure configures OpenStack Networking (neutron) to use LBaaS with the Open vSwitch (OVS) plugin.
Perform these steps on nodes running the neutron-server service:
On the Controller node (API Server):
Enable LBaaS:
yum install openstack-neutron-lbaas -y
# yum install openstack-neutron-lbaas -yCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the LBaaS tables to the neutron database:
neutron-db-manage --subproject neutron-lbaas --config-file /etc/neutron/neutron.conf --config-file /etc/neutron/plugins/ml2/ml2_conf.ini upgrade head
$ neutron-db-manage --subproject neutron-lbaas --config-file /etc/neutron/neutron.conf --config-file /etc/neutron/plugins/ml2/ml2_conf.ini upgrade headCopy to Clipboard Copied! Toggle word wrap Toggle overflow Change the service provider in
/etc/neutron/neutron_lbaas.conf. In the[service providers]section, comment out (#) all entries except for this entry:service_provider=LOADBALANCERV2:Haproxy:neutron_lbaas.drivers.haproxy.plugin_driver.HaproxyOnHostPluginDriver:default
service_provider=LOADBALANCERV2:Haproxy:neutron_lbaas.drivers.haproxy.plugin_driver.HaproxyOnHostPluginDriver:defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow In
/etc/neutron/neutron.conf, confirm that you have the LBaaS v2 plugin configured inservice_plugins:service_plugins=neutron_lbaas.services.loadbalancer.plugin.LoadBalancerPluginv2
service_plugins=neutron_lbaas.services.loadbalancer.plugin.LoadBalancerPluginv2Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also expect to see any other plugins you have previously added.
NoteIf you have
lbaasv1configured, replace it with the above setting forlbaasv2.In
/etc/neutron/lbaas_agent.ini, add the following to the[DEFAULT]section:ovs_use_veth = False interface_driver =neutron.agent.linux.interface.OVSInterfaceDriver
ovs_use_veth = False interface_driver =neutron.agent.linux.interface.OVSInterfaceDriverCopy to Clipboard Copied! Toggle word wrap Toggle overflow In
/etc/neutron/services_lbaas.conf, add the following to the[haproxy]section:user_group = haproxy
user_group = haproxyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Comment out any other
device driverentries.NoteIf the
l3-agentis in a failed mode, see thel3_agentlog files. You may need to edit/etc/neutron/neutron.confand comment out certain values in[DEFAULT], and uncomment the corresponding values inoslo_messaging_rabbit, as described in the log file.
Configure the LbaaS services, and review their status:
Stop the
lbaasv1services and startlbaasv2:systemctl disable neutron-lbaas-agent.service systemctl stop neutron-lbaas-agent.service systemctl mask neutron-lbaas-agent.service systemctl enable neutron-lbaasv2-agent.service systemctl start neutron-lbaasv2-agent.service
# systemctl disable neutron-lbaas-agent.service # systemctl stop neutron-lbaas-agent.service # systemctl mask neutron-lbaas-agent.service # systemctl enable neutron-lbaasv2-agent.service # systemctl start neutron-lbaasv2-agent.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Review the status of
lbaasv2:systemctl status neutron-lbaasv2-agent.service
# systemctl status neutron-lbaasv2-agent.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart
neutron-serverand check the status:systemctl restart neutron-server.service systemctl status neutron-server.service
# systemctl restart neutron-server.service # systemctl status neutron-server.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Check the
Loadbalancerv2agent:neutron agent-list
$ neutron agent-listCopy to Clipboard Copied! Toggle word wrap Toggle overflow