Este conteúdo não está disponível no idioma selecionado.
Chapter 24. Managing user groups using Ansible playbooks
This section introduces user group management using Ansible playbooks.
A user group is a set of users with common privileges, password policies, and other characteristics.
A user group in Identity Management (IdM) can include:
- IdM users
- other IdM user groups
- external users, which are users that exist outside of IdM
24.1. The different group types in IdM
IdM supports the following types of groups:
- POSIX groups (the default)
POSIX groups support Linux POSIX attributes for their members. Note that groups that interact with Active Directory cannot use POSIX attributes.
POSIX attributes identify users as separate entities. Examples of POSIX attributes relevant to users include
uidNumber, a user number (UID), andgidNumber, a group number (GID).- Non-POSIX groups
Non-POSIX groups do not support POSIX attributes. For example, these groups do not have a GID defined.
All members of this type of group must belong to the IdM domain.
- External groups
Use external groups to add group members that exist in an identity store outside of the IdM domain, such as:
- A local system
- An Active Directory domain
- A directory service
External groups do not support POSIX attributes. For example, these groups do not have a GID defined.
| Group name | Default group members |
|---|---|
|
| All IdM users |
|
|
Users with administrative privileges, including the default |
|
| This is a legacy group that no longer has any special privileges |
|
| Users with privileges to manage the Active Directory trusts |
When you add a user to a user group, the user gains the privileges and policies associated with the group. For example, to grant administrative privileges to a user, add the user to the admins group.
Do not delete the admins group. As admins is a pre-defined group required by IdM, this operation causes problems with certain commands.
In addition, IdM creates user private groups by default whenever a new user is created in IdM. For more information about private groups, see Adding users without a private group.
24.2. Direct and indirect group members
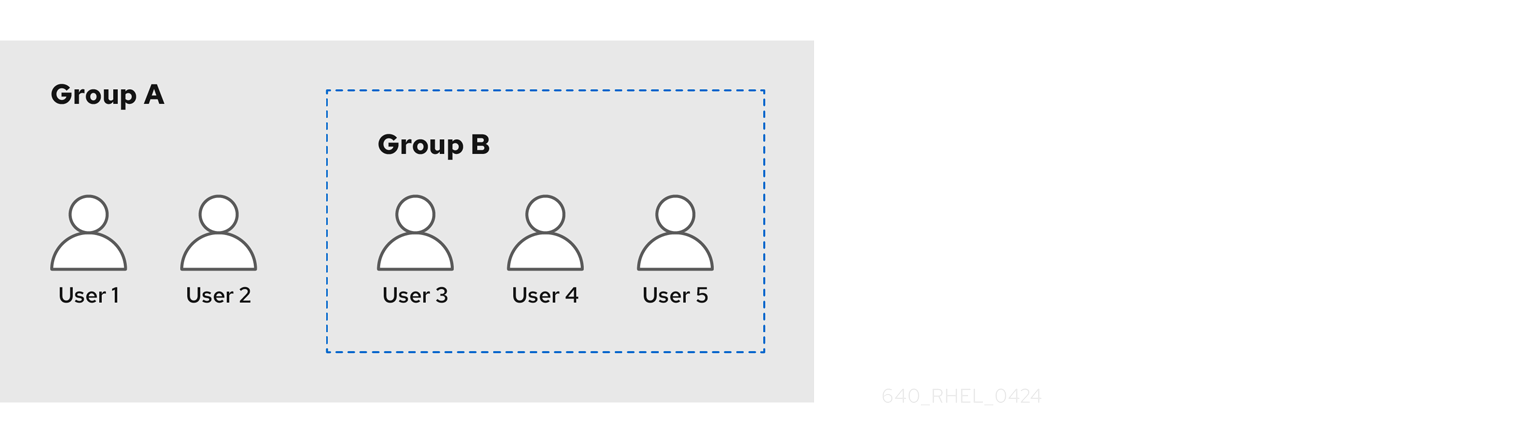
User group attributes in IdM apply to both direct and indirect members: when group B is a member of group A, all users in group B are considered indirect members of group A.
For example, in the following diagram:
- User 1 and User 2 are direct members of group A.
- User 3, User 4, and User 5 are indirect members of group A.
Figure 24.1. Direct and Indirect Group Membership
If you set a password policy for user group A, the policy also applies to all users in user group B.
24.3. Ensuring the presence of IdM groups and group members using Ansible playbooks
The following procedure describes ensuring the presence of IdM groups and group members - both users and user groups - using an Ansible playbook.
Prerequisites
- You know the IdM administrator password.
You have configured your Ansible control node to meet the following requirements:
- You are using Ansible version 2.13 or later.
-
You have installed the
ansible-freeipapackage. - The example assumes that in the ~/MyPlaybooks/ directory, you have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server.
-
The example assumes that the secret.yml Ansible vault stores your
ipaadmin_password.
-
The target node, that is the node on which the
ansible-freeipamodule is executed, is part of the IdM domain as an IdM client, server or replica. - The users you want to reference in your Ansible playbook exist in IdM. For details on ensuring the presence of users using Ansible, see Managing user accounts using Ansible playbooks.
Procedure
Create an inventory file, for example
inventory.file, and defineipaserverin it:[ipaserver] server.idm.example.com
[ipaserver] server.idm.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an Ansible playbook file with the necessary user and group information:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the playbook:
ansible-playbook --vault-password-file=password_file -v -i path_to_inventory_directory/inventory.file path_to_playbooks_directory/add-group-members.yml
$ ansible-playbook --vault-password-file=password_file -v -i path_to_inventory_directory/inventory.file path_to_playbooks_directory/add-group-members.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
You can verify if the ops group contains sysops and appops as direct members and idm_user as an indirect member by using the ipa group-show command:
Log into
ipaserveras administrator:ssh admin@server.idm.example.com
$ ssh admin@server.idm.example.com Password: [admin@server /]$Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display information about ops:
ipaserver]$ ipa group-show ops Group name: ops GID: 1234 Member groups: sysops, appops Indirect Member users: idm_user
ipaserver]$ ipa group-show ops Group name: ops GID: 1234 Member groups: sysops, appops Indirect Member users: idm_userCopy to Clipboard Copied! Toggle word wrap Toggle overflow The appops and sysops groups - the latter including the idm_user user - exist in IdM.
24.4. Using Ansible to add multiple IdM groups in a single task
You can use the ansible-freeipa ipagroup module to add, modify, and delete multiple Identity Management (IdM) user groups with a single Ansible task. For that, use the groups option of the ipagroup module.
Using the groups option, you can also specify multiple group variables that only apply to a particular group. Define this group by the name variable, which is the only mandatory variable for the groups option.
Complete this procedure to ensure the presence of the sysops and the appops groups in IdM in a single task. Define the sysops group as a nonposix group and the appops group as an external group.
Prerequisites
On the control node:
- You are using Ansible version 2.13 or later.
-
You have installed the
ansible-freeipapackage. - You have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server in the ~/MyPlaybooks/ directory.
- You are using RHEL 8.9 and later.
-
You have stored your
ipaadmin_passwordin the secret.yml Ansible vault.
Procedure
Create your Ansible playbook file add-nonposix-and-external-groups.yml with the following content:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the playbook:
ansible-playbook --vault-password-file=password_file -v -i <path_to_inventory_directory>/hosts <path_to_playbooks_directory>/add-nonposix-and-external-groups.yml
$ ansible-playbook --vault-password-file=password_file -v -i <path_to_inventory_directory>/hosts <path_to_playbooks_directory>/add-nonposix-and-external-groups.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
24.5. Using Ansible to enable AD users to administer IdM
You can use the ansible-freeipa idoverrideuser and group modules to create a user ID override for an Active Directory (AD) user from a trusted AD domain and give that user rights identical to those of an IdM user. The procedure uses the example of the Default Trust View ID view to which the ad_user@ad.example.com ID override of a user stored in AD is added in the first playbook task. In the next playbook task, the ad_user@ad.example.com ID override is added to the IdM admins group as a member. As a result, an AD administrator can administer IdM without having two different accounts and passwords.
Prerequisites
-
You know the IdM
adminpassword. - You have installed a trust with AD.
- The group to which you are adding the user ID override already exists in IdM.
-
You are using the 4.8.7 version of IdM or later. To view the version of IdM you have installed on your server, enter
ipa --version. You have configured your Ansible control node to meet the following requirements:
- You are using Ansible version 2.13 or later.
- You are using RHEL 8.10 or later.
-
You have installed the
ansible-freeipapackage. - The example assumes that in the ~/MyPlaybooks/ directory, you have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server.
-
The example assumes that the secret.yml Ansible vault stores your
ipaadmin_password.
- The AD forest is in trust with IdM. In the example, the name of the AD domain is ad.example.com and the fully-qualified domain name (FQDN) of the AD administrator is ad_user@ad.example.com.
-
The
ipaserverhost in the inventory file is configured as a trust controller or a trust agent. -
The target node, that is the node on which the
ansible-freeipamodule is executed, is part of the IdM domain as an IdM client, server or replica.
Procedure
Navigate to your ~/MyPlaybooks/ directory:
cd ~/MyPlaybooks/
$ cd ~/MyPlaybooks/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create an enable-ad-admin-to-administer-idm.yml playbook with a task to add the ad_user@ad.example.com user override to the Default Trust View:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the example:
- ad_user@ad.example.com is the user ID override of an AD user that is stored in the AD domain with which a trust has been established.
Use another playbook task in the same playbook to add the AD administrator user ID override to the
adminsgroup:Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the example:
-
adminsis the name of the IdM POSIX group to which you are adding the ad_user@ad.example.com ID override. Members of this group have full administrator privileges.
-
- Save the file.
Run the Ansible playbook. Specify the playbook file, the file storing the password protecting the secret.yml file, and the inventory file:
ansible-playbook --vault-password-file=password_file -v -i inventory enable-ad-admin-to-administer-idm.yml
$ ansible-playbook --vault-password-file=password_file -v -i inventory enable-ad-admin-to-administer-idm.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
24.6. Ensuring the presence of member managers in IdM user groups using Ansible playbooks
The following procedure describes ensuring the presence of IdM member managers - both users and user groups - using an Ansible playbook.
Prerequisites
On the control node:
- You are using Ansible version 2.13 or later.
-
You have installed the
ansible-freeipapackage. - The example assumes that in the ~/MyPlaybooks/ directory, you have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server.
-
The example assumes that the secret.yml Ansible vault stores your
ipaadmin_password.
-
The target node, that is the node on which the
ansible-freeipamodule is executed, is part of the IdM domain as an IdM client, server or replica. - You must have the name of the user or group you are adding as member managers and the name of the group you want them to manage.
Procedure
Create an inventory file, for example
inventory.file, and defineipaserverin it:[ipaserver] server.idm.example.com
[ipaserver] server.idm.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an Ansible playbook file with the necessary user and group member management information:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the playbook:
ansible-playbook --vault-password-file=password_file -v -i path_to_inventory_directory/inventory.file path_to_playbooks_directory/add-member-managers-user-groups.yml
$ ansible-playbook --vault-password-file=password_file -v -i path_to_inventory_directory/inventory.file path_to_playbooks_directory/add-member-managers-user-groups.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
You can verify if the group_a group contains test as a member manager and group_admins is a member manager of group_a by using the ipa group-show command:
Log into
ipaserveras administrator:ssh admin@server.idm.example.com
$ ssh admin@server.idm.example.com Password: [admin@server /]$Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display information about managergroup1:
ipaserver]$ ipa group-show group_a Group name: group_a GID: 1133400009 Membership managed by groups: group_admins Membership managed by users: test
ipaserver]$ ipa group-show group_a Group name: group_a GID: 1133400009 Membership managed by groups: group_admins Membership managed by users: testCopy to Clipboard Copied! Toggle word wrap Toggle overflow
24.7. Ensuring the absence of member managers in IdM user groups using Ansible playbooks
The following procedure describes ensuring the absence of IdM member managers - both users and user groups - using an Ansible playbook.
Prerequisites
On the control node:
- You are using Ansible version 2.13 or later.
-
You have installed the
ansible-freeipapackage. - The example assumes that in the ~/MyPlaybooks/ directory, you have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server.
-
The example assumes that the secret.yml Ansible vault stores your
ipaadmin_password.
-
The target node, that is the node on which the
ansible-freeipamodule is executed, is part of the IdM domain as an IdM client, server or replica. - You must have the name of the existing member manager user or group you are removing and the name of the group they are managing.
Procedure
Create an inventory file, for example
inventory.file, and defineipaserverin it:[ipaserver] server.idm.example.com
[ipaserver] server.idm.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an Ansible playbook file with the necessary user and group member management information:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the playbook:
ansible-playbook --vault-password-file=password_file -v -i path_to_inventory_directory/inventory.file path_to_playbooks_directory/ensure-member-managers-are-absent.yml
$ ansible-playbook --vault-password-file=password_file -v -i path_to_inventory_directory/inventory.file path_to_playbooks_directory/ensure-member-managers-are-absent.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Verification
You can verify if the group_a group does not contain test as a member manager and group_admins as a member manager of group_a by using the ipa group-show command:
Log into
ipaserveras administrator:ssh admin@server.idm.example.com
$ ssh admin@server.idm.example.com Password: [admin@server /]$Copy to Clipboard Copied! Toggle word wrap Toggle overflow Display information about group_a:
ipaserver]$ ipa group-show group_a Group name: group_a GID: 1133400009
ipaserver]$ ipa group-show group_a Group name: group_a GID: 1133400009Copy to Clipboard Copied! Toggle word wrap Toggle overflow