엣지 컴퓨팅
네트워크 엣지에서 OpenShift Container Platform 클러스터 구성 및 배포
초록
1장. 네트워크 맨 위 엣지의 과제
엣지 컴퓨팅은 지리적으로 대체된 위치에서 많은 사이트를 관리할 때 복잡한 문제를 안고 있습니다. ZTP( GitOps Zero Touch Provisioning)를 사용하여 네트워크의 맨 위에 있는 사이트를 프로비저닝하고 관리합니다.
1.1. 네트워크의 문제를 해결하여 엣지
현재 서비스 제공업체는 네트워크의 에지에 인프라를 배포하려고 합니다. 이는 상당한 과제를 안고 있습니다:
- 여러 에지 사이트의 배포를 병렬로 어떻게 처리합니까?
- 연결이 끊긴 환경에서 사이트를 배포해야 하는 경우 어떻게 됩니까?
- 대규모 클러스터의 라이프사이클을 어떻게 관리합니까?
GitOps ZTP(ZTP) 및 GitOps 는 베어 메탈 장비에 대한 선언적 사이트 정의 및 구성으로 대규모로 원격 에지 사이트를 프로비저닝할 수 있으므로 이러한 문제를 해결합니다. 템플릿 또는 오버레이 구성은 CNF 워크로드에 필요한 OpenShift Container Platform 기능을 설치합니다. 설치 및 업그레이드의 전체 라이프사이클은 GitOps ZTP 파이프라인을 통해 처리됩니다.
GitOps ZTP는 인프라 배포에 GitOps를 사용합니다. GitOps에서는 선언적 YAML 파일 및 Git 리포지토리에 저장된 기타 정의된 패턴을 사용합니다. RHACM(Red Hat Advanced Cluster Management)은 Git 리포지토리를 사용하여 인프라 배포를 지원합니다.
GitOps는 추적성, 역할 기반 액세스 제어(RBAC) 및 각 사이트의 원하는 상태에 대해 단일 정보 소스를 제공합니다. 확장성 문제는 Webhook를 통해 Git 방법론 및 이벤트 중심 작업을 통해 해결됩니다.
GitOps ZTP 파이프라인이 에지 노드에 제공하는 선언적 사이트 정의 및 구성 CR(사용자 정의 리소스)을 생성하여 GitOps ZTP 워크플로를 시작합니다.
다음 다이어그램은 GitOps ZTP가 far edge 프레임워크 내에서 작동하는 방법을 보여줍니다.
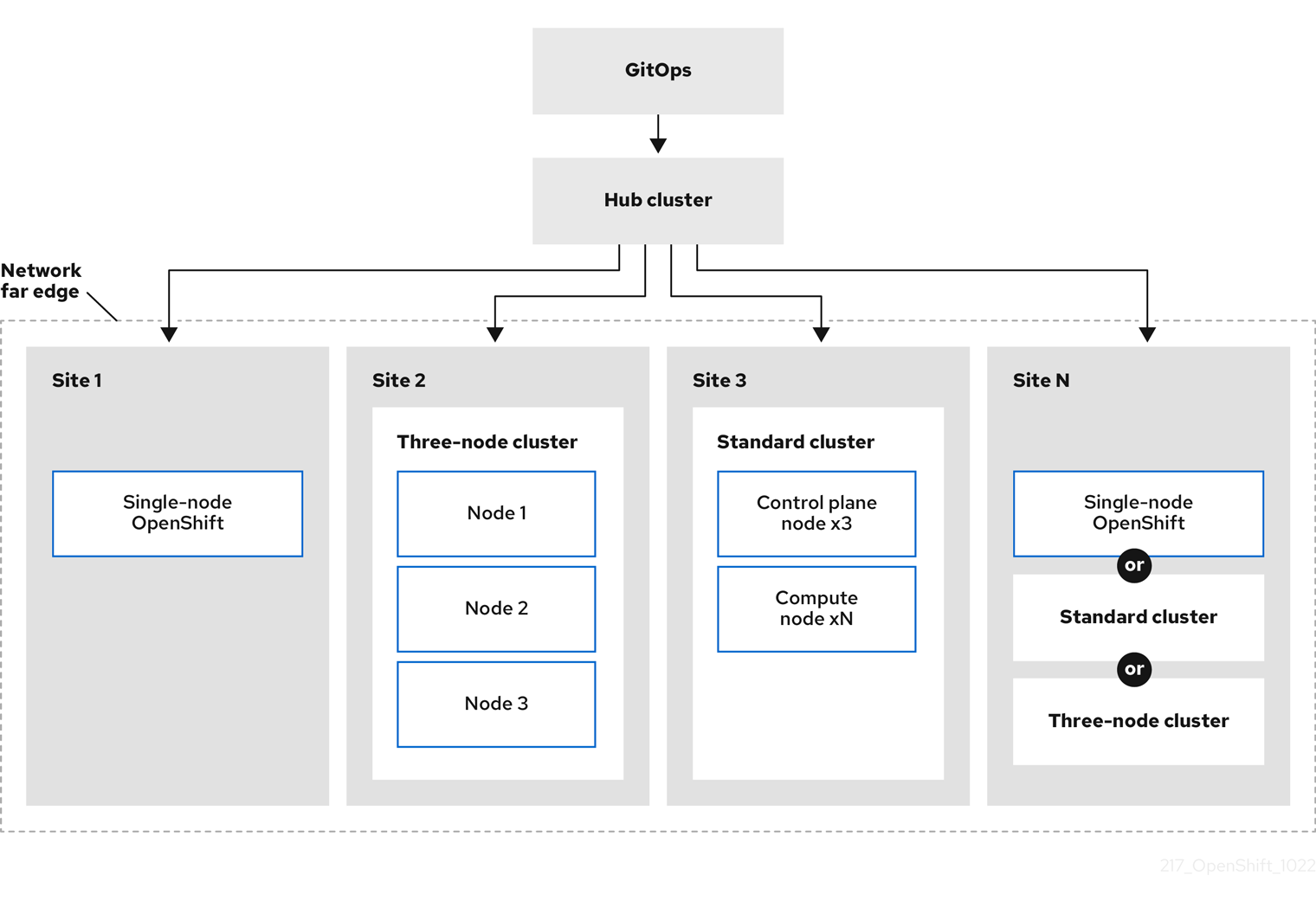
1.2. GitOps ZTP를 사용하여 네트워크 엣지에서 클러스터를 프로비저닝
RHACM(Red Hat Advanced Cluster Management)은 단일 허브 클러스터가 많은 spoke 클러스터를 관리하는 hub-and-spoke 아키텍처의 클러스터를 관리합니다. RHACM을 실행하는 Hub 클러스터는 GitOps ZTP(ZTP) 및 RHACM을 설치할 때 배포되는 지원 서비스를 사용하여 관리 클러스터를 프로비저닝하고 배포합니다.
지원 서비스는 단일 노드 클러스터, 3-노드 클러스터 또는 베어 메탈에서 실행되는 표준 클러스터에서 OpenShift Container Platform의 프로비저닝을 처리합니다.
OpenShift Container Platform으로 베어 메탈 호스트를 프로비저닝하고 유지 관리하기 위해 GitOps ZTP를 사용하는 방법에 대한 개괄적인 개요는 다음과 같습니다.
- RHACM을 실행하는 허브 클러스터는 OpenShift Container Platform 릴리스 이미지를 미러링하는 OpenShift 이미지 레지스트리를 관리합니다. RHACM은 OpenShift 이미지 레지스트리를 사용하여 관리 클러스터를 프로비저닝합니다.
- Git 리포지토리에 버전이 지정된 YAML 형식 인벤토리 파일에서 베어 메탈 호스트를 관리합니다.
- 호스트를 관리 클러스터로 프로비저닝할 준비를 하고 RHACM 및 지원 서비스를 사용하여 사이트에 베어 메탈 호스트를 설치합니다.
클러스터 설치 및 배포는 초기 설치 단계와 후속 구성 및 배포 단계가 포함된 2단계 프로세스입니다. 다음 다이어그램에서는 이 워크플로를 보여줍니다.

1.3. SiteConfig 리소스 및 RHACM을 사용하여 관리형 클러스터 설치
GitOps ZTP(ZTP)는 Git 리포지토리에서 site Config CR(사용자 정의 리소스)을 사용하여 OpenShift Container Platform 클러스터를 설치하는 프로세스를 관리합니다. SiteConfig CR에는 설치에 필요한 클러스터별 매개변수가 포함되어 있습니다. 사용자 정의 추가 매니페스트를 포함하여 설치 중에 선택한 구성 CR을 적용하는 옵션이 있습니다.
GitOps ZTP 플러그인은 siteConfig CR을 처리하여 허브 클러스터에서 CR 컬렉션을 생성합니다. 이렇게 하면 RHACM(Red Hat Advanced Cluster Management)에서 지원 서비스가 트리거되어 베어 메탈 호스트에 OpenShift Container Platform을 설치합니다. hub 클러스터에서 이러한 CR에서 설치 상태 및 오류 메시지를 찾을 수 있습니다.
단일 클러스터를 수동으로 프로비저닝하거나 GitOps ZTP를 사용하여 배치에서 프로비저닝할 수 있습니다.
- 단일 클러스터 프로비저닝
-
클러스터의 단일
SiteConfigCR 및 관련 설치 및 구성 CR을 생성하고 Hub 클러스터에 적용하여 클러스터 프로비저닝을 시작합니다. 이는 대규모에 배포하기 전에 CR을 테스트하는 좋은 방법입니다. - 여러 클러스터 프로비저닝
-
Git 리포지토리에서 site
Config 및 관련 CR을 정의하여 최대400개의 배치에 관리형 클러스터를 설치합니다. ArgoCD는 siteConfigCR을 사용하여 사이트를 배포합니다. RHACM 정책 생성기는 매니페스트를 생성하여 Hub 클러스터에 적용합니다. 그러면 클러스터 프로비저닝 프로세스가 시작됩니다.
1.4. 정책 및 PolicyGenTemplate 리소스를 사용하여 관리형 클러스터 구성
GitOps ZTP(Red Hat Advanced Cluster Management)는 정책 기반 거버넌스 접근 방식을 사용하여 구성을 적용하여 클러스터를 구성합니다.
정책 생성기 또는 PolicyGen 은 GitOps Operator의 플러그인으로, 간결한 템플릿에서 RHACM 정책을 생성할 수 있습니다. 이 툴은 여러 CR을 단일 정책으로 결합할 수 있으며, 플릿의 다양한 클러스터 하위 집합에 적용되는 여러 정책을 생성할 수 있습니다.
확장성을 유지하고 클러스터 전체에서 구성 관리의 복잡성을 줄이려면 가능한 한 많은 공통성을 갖춘 구성 CR을 사용하십시오.
- 가능한 경우 플릿 전체 공통 정책을 사용하여 구성 CR을 적용합니다.
- 다음 기본 설정은 그룹 정책에서 최대한 많은 나머지 구성을 관리할 클러스터의 논리 그룹을 생성하는 것입니다.
- 구성이 개별 사이트에 고유한 경우 허브 클러스터에서 RHACM 템플릿 작성을 사용하여 사이트별 데이터를 공통 또는 그룹 정책에 삽입합니다. 또는 사이트에 대한 개별 사이트 정책을 적용합니다.
다음 다이어그램은 클러스터 배포 구성 단계에서 정책 생성기가 GitOps 및 RHACM과 상호 작용하는 방법을 보여줍니다.
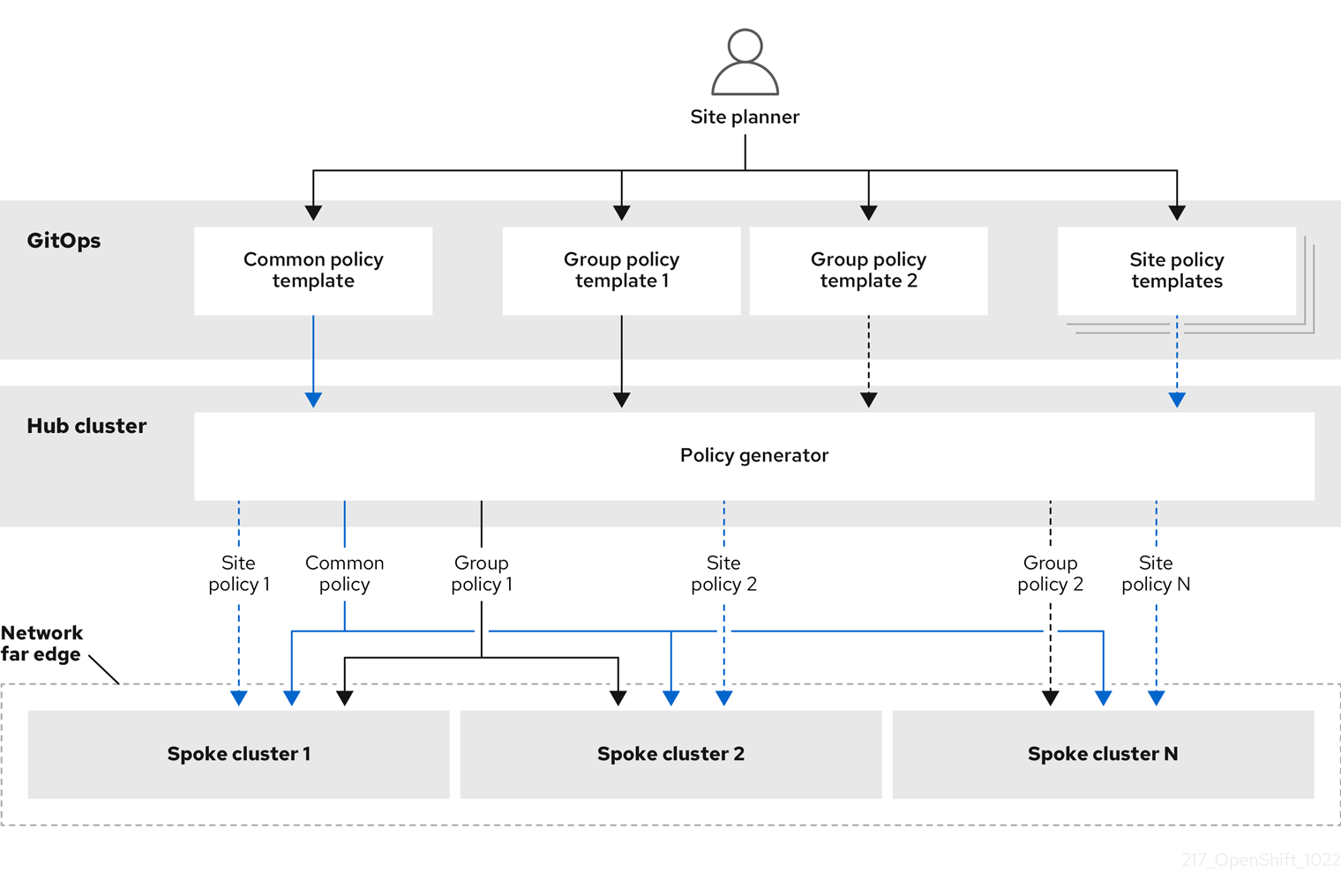
대규모 클러스터의 경우 해당 클러스터 구성에 높은 수준의 일관성이 있는 것이 일반적입니다.
다음과 같은 권장 정책 구조에서는 구성 CR을 결합하여 몇 가지 목표를 달성할 수 있습니다.
- 일반적인 구성을 한 번 설명하고 플릿에 적용됩니다.
- 유지 관리 및 관리되는 정책의 수를 최소화합니다.
- 클러스터 변형에 대한 일반적인 구성에서 유연성을 지원합니다.
| 정책 카테고리 | 설명 |
|---|---|
| 공통 |
공통 카테고리에 존재하는 정책은 플릿의 모든 클러스터에 적용됩니다. 공통 |
| 그룹 |
그룹 카테고리에 존재하는 정책은 플릿의 클러스터 그룹에 적용됩니다. 그룹 |
| 사이트 | 사이트 카테고리에 존재하는 정책은 특정 클러스터 사이트에 적용됩니다. 모든 클러스터는 고유한 정책을 유지 관리할 수 있습니다. |
2장. ZTP용 허브 클러스터 준비
연결이 끊긴 환경에서 RHACM을 사용하려면 필요한 Operator 이미지가 포함된 OpenShift Container Platform 릴리스 이미지 및 OLM(Operator Lifecycle Manager) 카탈로그를 미러링하는 미러 레지스트리를 생성합니다. OLM은 Operator 및 클러스터의 종속 항목을 관리, 설치 및 업그레이드합니다. 연결이 끊긴 미러 호스트를 사용하여 베어 메탈 호스트를 프로비저닝하는 데 사용되는 RHCOS ISO 및 RootFS 디스크 이미지를 제공할 수도 있습니다.
2.1. Telco RAN DU 4.15 검증 소프트웨어 구성 요소
Red Hat telco RAN DU 4.15 솔루션은 OpenShift Container Platform 관리 클러스터 및 허브 클러스터에 대해 다음과 같은 Red Hat 소프트웨어 제품을 사용하여 검증되었습니다.
| Component | 소프트웨어 버전 |
|---|---|
| 관리형 클러스터 버전 | 4.15 |
| Cluster Logging Operator | 5.8 |
| Local Storage Operator | 4.15 |
| PTP Operator | 4.15 |
| SRIOV Operator | 4.15 |
| Node Tuning Operator | 4.15 |
| Logging Operator | 4.15 |
| SRIOV-FEC Operator | 2.8 |
| Component | 소프트웨어 버전 |
|---|---|
| hub 클러스터 버전 | 4.15 |
| GitOps ZTP 플러그인 | 4.15 |
| Red Hat Advanced Cluster Management(RHACM) | 2.9, 2.10 |
| Red Hat OpenShift GitOps | 1.16 |
| 토폴로지 인식 라이프사이클 관리자(TALM) | 4.15 |
2.2. GitOps ZTP에 대한 권장 허브 클러스터 사양 및 관리 클러스터 제한
GitOps Zero Touch Provisioning (ZTP)을 사용하면 지리적으로 분산된 지역 및 네트워크에서 수천 개의 클러스터를 관리할 수 있습니다. Red Hat Performance 및 Scale 랩은 랩 환경에서 단일 RHACM(Red Hat Advanced Cluster Management) 허브 클러스터에서 DU 프로필이 감소하여 3500개의 가상 단일 노드 OpenShift 클러스터를 성공적으로 생성 및 관리합니다.
실제 상황에서 관리할 수 있는 클러스터 수에 대한 스케일링 제한은 hub 클러스터에 영향을 미치는 다양한 요인에 따라 달라집니다. 예를 들면 다음과 같습니다.
- hub 클러스터 리소스
- 사용 가능한 허브 클러스터 호스트 리소스(CPU, 메모리, 스토리지)는 허브 클러스터가 관리할 수 있는 클러스터 수를 결정하는 데 중요한 요소입니다. 허브 클러스터에 할당될수록 더 많은 관리 클러스터를 수용할 수 있습니다.
- hub 클러스터 스토리지
- 허브 클러스터 호스트 스토리지 IOPS 등급과 허브 클러스터 호스트가 NVMe 스토리지를 사용하는지 여부는 허브 클러스터 성능과 관리할 수 있는 클러스터 수에 영향을 미칠 수 있습니다.
- 네트워크 대역폭 및 대기 시간
- 허브 클러스터와 관리 클러스터 간의 대기 시간이 느리거나 대기 시간이 긴 네트워크 연결은 허브 클러스터가 여러 클러스터를 관리하는 방법에 영향을 미칠 수 있습니다.
- 관리형 클러스터 크기 및 복잡성
- 관리 클러스터의 크기와 복잡성은 허브 클러스터의 용량에도 영향을 미칩니다. 더 많은 노드, 네임스페이스 및 리소스가 있는 대규모 관리 클러스터에는 추가 처리 및 관리 리소스가 필요합니다. 마찬가지로 RAN DU 프로필 또는 다양한 워크로드와 같은 복잡한 구성이 있는 클러스터에는 허브 클러스터의 더 많은 리소스가 필요할 수 있습니다.
- 관리 정책 수
- 해당 정책에 바인딩된 관리 클러스터 수를 통해 확장되는 허브 클러스터에서 관리하는 정책 수는 관리할 수 있는 클러스터 수를 결정하는 중요한 요소입니다.
- 모니터링 및 관리 워크로드
- RHACM은 관리 클러스터를 지속적으로 모니터링하고 관리합니다. 허브 클러스터에서 실행되는 모니터링 및 관리 워크로드의 수와 복잡성은 용량에 영향을 미칠 수 있습니다. 집중적인 모니터링 또는 빈번한 조정 작업에는 추가 리소스가 필요할 수 있으므로 관리 가능한 클러스터 수를 제한할 수 있습니다.
- RHACM 버전 및 구성
- RHACM의 다른 버전에는 다양한 성능 특성과 리소스 요구 사항이 있을 수 있습니다. 또한 동시 조정 수 또는 상태 점검 빈도와 같은 RHACM의 구성 설정은 허브 클러스터의 관리 클러스터 용량에 영향을 미칠 수 있습니다.
다음 대표 구성 및 네트워크 사양을 사용하여 자체 Hub 클러스터 및 네트워크 사양을 개발합니다.
다음 지침은 내부 랩 벤치마크 테스트만 기반으로 하며 완전한 베어 메탈 호스트 사양을 나타내지 않습니다.
| 요구 사항 | 설명 |
|---|---|
| 서버 하드웨어 | 3개의 x Dell PowerEdge R650 랙 서버 |
| NVMe 하드 디스크 |
|
| SSD 하드 디스크 |
|
| 적용되는 DU 프로파일 정책 수 | 5 |
다음 네트워크 사양은 일반적인 실제 RAN 네트워크를 나타내며 테스트 중에 스케일 랩 환경에 적용되었습니다.
| 사양 | 설명 |
|---|---|
| Round-trip Time (RTT) 대기 시간 | 50 MS |
| 패킷 손실 | 0.02% 패킷 손실 |
| 네트워크 대역폭 제한 | 20Mbps |
2.3. 연결이 끊긴 환경에서 GitOps ZTP 설치
연결이 끊긴 환경의 허브 클러스터에서 RHACM(Red Hat Advanced Cluster Management), Red Hat OpenShift GitOps 및 Topology Aware Lifecycle Manager(TALM)를 사용하여 여러 관리 클러스터의 배포를 관리합니다.
사전 요구 사항
-
OpenShift Container Platform CLI(
oc)를 설치했습니다. -
cluster-admin권한이 있는 사용자로 로그인했습니다. 클러스터에서 사용할 연결이 끊긴 미러 레지스트리가 구성되어 있습니다.
참고생성하는 연결이 끊긴 미러 레지스트리에는 허브 클러스터에서 실행 중인 TALM 버전과 일치하는 TALM 백업 및 사전 캐시 이미지가 포함되어야 합니다. spoke 클러스터는 연결이 끊긴 미러 레지스트리에서 이러한 이미지를 확인할 수 있어야 합니다.
프로세스
- hub 클러스터에 RHACM을 설치합니다. 연결이 끊긴 환경에서 RHACM 설치를 참조하십시오.
- hub 클러스터에 GitOps 및 TALM을 설치합니다.
2.4. 연결이 끊긴 미러 호스트에 RHCOS ISO 및 RootFS 이미지 추가
RHACM(Red Hat Advanced Cluster Management)을 사용하여 연결이 끊긴 환경에 클러스터를 설치하기 전에 먼저 사용할 RHCOS(Red Hat Enterprise Linux CoreOS) 이미지를 호스팅해야 합니다. 연결이 끊긴 미러를 사용하여 RHCOS 이미지를 호스팅합니다.
사전 요구 사항
- 네트워크에서 RHCOS 이미지 리소스를 호스팅하도록 HTTP 서버를 배포하고 구성합니다. 사용자 컴퓨터에서 및 사용자가 생성한 시스템에서 HTTP 서버에 액세스할 수 있어야 합니다.
RHCOS 이미지는 OpenShift Container Platform 릴리스에 따라 변경되지 않을 수 있습니다. 설치하는 버전보다 작거나 같은 최신 버전의 이미지를 다운로드해야 합니다. 사용 가능한 경우 OpenShift Container Platform 버전과 일치하는 이미지 버전을 사용합니다. 호스트에 RHCOS를 설치하려면 ISO 및 RootFS 이미지가 필요합니다. 이 설치 유형에서는 RHCOS QCOW2 이미지가 지원되지 않습니다.
프로세스
- 미러 호스트에 로그인합니다.
mirror.openshift.com 에서 RHCOS ISO 및 RootFS 이미지를 가져옵니다. 예를 들면 다음과 같습니다.
필요한 이미지 이름 및 OpenShift Container Platform 버전을 환경 변수로 내보냅니다.
export ISO_IMAGE_NAME=<iso_image_name>
$ export ISO_IMAGE_NAME=<iso_image_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ROOTFS_IMAGE_NAME=<rootfs_image_name>
$ export ROOTFS_IMAGE_NAME=<rootfs_image_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow export OCP_VERSION=<ocp_version>
$ export OCP_VERSION=<ocp_version>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow 필요한 이미지를 다운로드합니다.
sudo wget https://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.15/${OCP_VERSION}/${ISO_IMAGE_NAME} -O /var/www/html/${ISO_IMAGE_NAME}$ sudo wget https://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.15/${OCP_VERSION}/${ISO_IMAGE_NAME} -O /var/www/html/${ISO_IMAGE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow sudo wget https://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.15/${OCP_VERSION}/${ROOTFS_IMAGE_NAME} -O /var/www/html/${ROOTFS_IMAGE_NAME}$ sudo wget https://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.15/${OCP_VERSION}/${ROOTFS_IMAGE_NAME} -O /var/www/html/${ROOTFS_IMAGE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
검증 단계
다음과 같이 이미지가 성공적으로 다운로드되고 연결이 끊긴 미러 호스트에서 제공되고 있는지 확인합니다.
wget http://$(hostname)/${ISO_IMAGE_NAME}$ wget http://$(hostname)/${ISO_IMAGE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Saving to: rhcos-4.15.1-x86_64-live.x86_64.iso rhcos-4.15.1-x86_64-live.x86_64.iso- 11%[====> ] 10.01M 4.71MB/s
Saving to: rhcos-4.15.1-x86_64-live.x86_64.iso rhcos-4.15.1-x86_64-live.x86_64.iso- 11%[====> ] 10.01M 4.71MB/sCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.5. 지원 서비스 활성화
RHACM(Red Hat Advanced Cluster Management)은 지원 서비스를 사용하여 OpenShift Container Platform 클러스터를 배포합니다. RHACM(Red Hat Advanced Cluster Management)에서 MultiClusterHub Operator를 활성화하면 Helped 서비스가 자동으로 배포됩니다. 그 후에는 모든 네임스페이스를 감시하고 AgentServiceConfig CR(사용자 정의 리소스)을 미러 레지스트리 HTTP 서버에서 호스팅되는 ISO 및 RootFS 이미지에 대한 참조로 업데이트하도록 Provisioning 리소스를 구성해야 합니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 허브 클러스터에 로그인했습니다. - MultiClusterHub가 활성화된 RHACM이 있어야 합니다.
프로세스
-
프로비저닝리소스를 활성화하여 모든 네임스페이스를 조사하고 연결이 끊긴 환경에 대한 미러를 구성합니다. 자세한 내용은 중앙 인프라 관리 서비스 활성화를 참조하십시오. 다음 명령을 실행하여
AgentServiceConfigCR을 업데이트합니다.oc edit AgentServiceConfig
$ oc edit AgentServiceConfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow CR의
items.spec.osImages필드에 다음 항목을 추가합니다.- cpuArchitecture: x86_64 openshiftVersion: "4.15" rootFSUrl: https://<host>/<path>/rhcos-live-rootfs.x86_64.img url: https://<host>/<path>/rhcos-live.x86_64.iso- cpuArchitecture: x86_64 openshiftVersion: "4.15" rootFSUrl: https://<host>/<path>/rhcos-live-rootfs.x86_64.img url: https://<host>/<path>/rhcos-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음과 같습니다.
- <host>
- 대상 미러 레지스트리 HTTP 서버의 FQDN(정규화된 도메인 이름)입니다.
- <path>
- 대상 미러 레지스트리의 이미지 경로입니다.
편집기를 저장하고 종료하여 변경 사항을 적용합니다.
2.6. 연결이 끊긴 미러 레지스트리를 사용하도록 허브 클러스터 구성
연결이 끊긴 환경에서 연결이 끊긴 미러 레지스트리를 사용하도록 허브 클러스터를 구성할 수 있습니다.
사전 요구 사항
- RHACM(Red Hat Advanced Cluster Management) 2.9가 설치된 연결이 끊긴 허브 클러스터 설치가 있어야 합니다.
-
HTTP 서버의
rootfs및iso이미지를 호스팅했습니다. OpenShift Container Platform 이미지 리포지토리 미러링에 대한 지침은 추가 리소스 섹션을 참조하십시오.
HTTP 서버에 대해 TLS를 활성화하면 루트 인증서가 클라이언트가 신뢰하는 기관에서 서명했는지 확인하고 OpenShift Container Platform 허브와 관리 클러스터와 HTTP 서버 간의 신뢰할 수 있는 인증서 체인을 확인해야 합니다. 신뢰할 수 없는 인증서로 구성된 서버를 사용하면 이미지가 이미지 생성 서비스로 다운로드되지 않습니다. 신뢰할 수 없는 HTTPS 서버 사용은 지원되지 않습니다.
프로세스
미러 레지스트리 구성이 포함된
ConfigMap을 생성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
ConfigMap네임스페이스는multicluster-engine으로 설정해야 합니다.- 2
- 미러 레지스트리를 생성할 때 사용되는 미러 레지스트리의 인증서입니다.
- 3
- 미러 레지스트리의 구성 파일입니다. 미러 레지스트리 구성은 검색 이미지의
/etc/containers/registries.conf파일에 미러 정보를 추가합니다. 미러 정보는 정보가 설치 프로그램에 전달될 때install-config.yaml파일의imageContentSources섹션에 저장됩니다. hub 클러스터에서 실행되는 지원 서비스 Pod는 구성된 미러 레지스트리에서 컨테이너 이미지를 가져옵니다. - 4
- 미러 레지스트리의 URL입니다. 미러 레지스트리를 구성할 때
oc adm release mirror명령을 실행하여imageContentSources섹션의 URL을 사용해야 합니다. 자세한 내용은 OpenShift Container Platform 이미지 저장소 미러링 섹션을 참조하십시오. - 5
registries.conf파일에 정의된 레지스트리는 레지스트리가 아닌 리포지터리로 범위를 지정해야 합니다. 이 예에서quay.io/example-repository및mirror1.registry.corp.com:5000/example-repository리포지토리의 범위는example-repository리포지토리로 지정됩니다.
이 업데이트는 다음과 같이
AgentServiceConfig사용자 정의 리소스에서mirrorRegistryRef를 업데이트합니다.출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
클러스터 설치 중에 유효한 NTP 서버가 필요합니다. 적절한 NTP 서버를 사용할 수 있고 연결이 끊긴 네트워크를 통해 설치된 클러스터에서 연결할 수 있는지 확인합니다.
2.7. 인증되지 않은 레지스트리를 사용하도록 허브 클러스터 구성
인증되지 않은 레지스트리를 사용하도록 허브 클러스터를 구성할 수 있습니다. 인증되지 않은 레지스트리는 이미지에 액세스하고 다운로드하는 데 인증이 필요하지 않습니다.
사전 요구 사항
- hub 클러스터를 설치 및 구성하고 hub 클러스터에 Red Hat Advanced Cluster Management(RHACM)를 설치 및 구성했습니다.
- OpenShift Container Platform CLI(oc)가 설치되어 있습니다.
-
cluster-admin권한이 있는 사용자로 로그인했습니다. - hub 클러스터에서 사용할 인증되지 않은 레지스트리를 구성했습니다.
프로세스
다음 명령을 실행하여
AgentServiceConfigCR(사용자 정의 리소스)을 업데이트합니다.oc edit AgentServiceConfig agent
$ oc edit AgentServiceConfig agentCopy to Clipboard Copied! Toggle word wrap Toggle overflow CR에
unauthenticatedRegistries필드를 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 인증되지 않은 레지스트리는
AgentServiceConfig리소스의spec.unauthenticatedRegistries에 나열됩니다. 이 목록의 레지스트리에는 spoke 클러스터 설치에 사용되는 풀 시크릿에 항목이 필요하지 않습니다.assisted-service는 설치에 사용되는 모든 이미지 레지스트리에 대한 인증 정보가 포함되어 있는지 확인하여 풀 시크릿을 검증합니다.
미러 레지스트리는 무시 목록에 자동으로 추가되며 spec.unauthenticatedRegistries 아래에 추가할 필요가 없습니다. ConfigMap 에서 PUBLIC_CONTAINER_REGISTRIES 환경 변수를 지정하면 지정된 값이 있는 기본값이 재정의됩니다. PUBLIC_CONTAINER_REGISTRIES 기본값은 quay.io 및 registry.svc.ci.openshift.org 입니다.
검증
다음 명령을 실행하여 hub 클러스터에서 새로 추가된 레지스트리에 액세스할 수 있는지 확인합니다.
hub 클러스터에 대한 디버그 쉘 프롬프트를 엽니다.
oc debug node/<node_name>
$ oc debug node/<node_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 인증되지 않은 레지스트리에 대한 액세스를 테스트합니다.
podman login -u kubeadmin -p $(oc whoami -t) <unauthenticated_registry>
sh-4.4# podman login -u kubeadmin -p $(oc whoami -t) <unauthenticated_registry>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음과 같습니다.
- <unauthenticated_registry>
-
새 레지스트리입니다(예:
unauthenticated-image-registry.openshift-image-registry.svc:5000).
출력 예
Login Succeeded!
Login Succeeded!Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.8. ArgoCD를 사용하여 허브 클러스터 구성
ZTP(ZTP)를 사용하여 각 사이트에 필요한 설치 및 정책 CR(사용자 정의 리소스)을 생성하는 ArgoCD 애플리케이션 세트를 사용하여 허브 클러스터를 구성할 수 있습니다.
RHACM(Red Hat Advanced Cluster Management)은 site Config CR을 사용하여 ArgoCD의 Day 1 관리형 클러스터 설치 CR을 생성합니다. 각 ArgoCD 애플리케이션은 최대 300개의 site Config CR을 관리할 수 있습니다.
사전 요구 사항
- RHACM(Red Hat Advanced Cluster Management) 및 Red Hat OpenShift GitOps가 설치된 OpenShift Container Platform 허브 클러스터가 있어야 합니다.
-
" GitOps ZTP 사이트 구성 리포지토리 준비" 섹션에 설명된 대로 GitOps ZTP 플러그인 컨테이너에서 참조 배포를 추출했습니다. 참조 배포를 추출하면 다음 절차에서 참조되는
out/argocd/deployment디렉터리가 생성됩니다.
프로세스
ArgoCD 파이프라인 구성을 준비합니다.
- 예제 디렉터리와 유사한 디렉터리 구조를 사용하여 Git 리포지토리를 생성합니다. 자세한 내용은 "GitOps ZTP 사이트 구성 저장소 준비"를 참조하세요.
ArgoCD UI를 사용하여 리포지토리에 대한 액세스를 구성합니다. 설정에서 다음을 구성합니다.
-
리포지토리 - 연결 정보를 추가합니다. URL은
.git로 끝나야 합니다(예:https://repo.example.com/repo.git및 인증 정보). - certificates - 필요한 경우 리포지토리의 공용 인증서를 추가합니다.
-
리포지토리 - 연결 정보를 추가합니다. URL은
Git 저장소에 따라 두 개의 ArgoCD 애플리케이션(
out/argocd/deployment/clusters-app.yaml및out/argocd/deployment/policies-app.yaml)을수정합니다.-
Git 리포지토리를 가리키도록 URL을 업데이트합니다. URL은
.git로 끝납니다(예:https://repo.example.com/repo.git). -
targetRevision은 모니터링할 Git 리포지토리 분기를 나타냅니다. -
path는 각각SiteConfig및PolicyGenTemplateCR의 경로를 지정합니다.
-
Git 리포지토리를 가리키도록 URL을 업데이트합니다. URL은
GitOps ZTP 플러그인을 설치하려면 허브 클러스터의 ArgoCD 인스턴스를 관련 MCCE(Multicluster engine) 서브스크립션 이미지로 패치합니다. 이전에 추출한 패치 파일을 사용자 환경의
out/argocd/deployment/디렉터리에 사용자 지정합니다.RHACM 버전과 일치하는
multicluster-operators-subscription이미지를 선택합니다.-
RHACM 2.8 및 2.9의 경우
registry.redhat.io/rhacm2/multicluster-operators-subscription-rhel8:v<rhacm_version> 이미지를 사용합니다. -
RHACM 2.10 이상의 경우
registry.redhat.io/rhacm2/multicluster-operators-subscription-rhel9:v<rhacm_version> 이미지를 사용합니다.
중요multicluster-operators-subscription이미지의 버전은 RHACM 버전과 일치해야 합니다. MCE 2.10 릴리스부터 RHEL 9는multicluster-operators-subscription이미지의 기본 이미지입니다.OpenShift Operator 라이프 사이클의 "Platform Aligned Operators" 표에서
[Expand for Operator list]를 클릭하여 OpenShift Container Platform에 대해 지원되는 전체 Operator 매트릭스를 확인합니다.-
RHACM 2.8 및 2.9의 경우
out/argocd/deployment/argocd-openshift-gitops-patch.json파일에 다음 구성을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow ArgoCD 인스턴스를 패치합니다. 다음 명령을 실행합니다.
oc patch argocd openshift-gitops \ -n openshift-gitops --type=merge \ --patch-file out/argocd/deployment/argocd-openshift-gitops-patch.json
$ oc patch argocd openshift-gitops \ -n openshift-gitops --type=merge \ --patch-file out/argocd/deployment/argocd-openshift-gitops-patch.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow
RHACM 2.7 이상에서는 다중 클러스터 엔진에서 기본적으로
cluster-proxy-addon기능을 활성화합니다. 다음 패치를 적용하여cluster-proxy-addon기능을 비활성화하고 이 애드온을 담당하는 관련 허브 클러스터 및 관리 Pod를 제거합니다. 다음 명령을 실행합니다.oc patch multiclusterengines.multicluster.openshift.io multiclusterengine --type=merge --patch-file out/argocd/deployment/disable-cluster-proxy-addon.json
$ oc patch multiclusterengines.multicluster.openshift.io multiclusterengine --type=merge --patch-file out/argocd/deployment/disable-cluster-proxy-addon.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 허브 클러스터에 파이프라인 구성을 적용합니다.
oc apply -k out/argocd/deployment
$ oc apply -k out/argocd/deploymentCopy to Clipboard Copied! Toggle word wrap Toggle overflow 선택 사항: 기존 ArgoCD 애플리케이션이 있는 경우 다음 명령을 실행하여
PrunePropagationPolicy=backECDSA 정책이애플리케이션리소스에 설정되어 있는지 확인합니다.oc -n openshift-gitops get applications.argoproj.io \ clusters -o jsonpath='{.spec.syncPolicy.syncOptions}' |jq$ oc -n openshift-gitops get applications.argoproj.io \ clusters -o jsonpath='{.spec.syncPolicy.syncOptions}' |jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 기존 정책의 출력 예
[ "CreateNamespace=true", "PrunePropagationPolicy=background", "RespectIgnoreDifferences=true" ]
[ "CreateNamespace=true", "PrunePropagationPolicy=background", "RespectIgnoreDifferences=true" ]Copy to Clipboard Copied! Toggle word wrap Toggle overflow spec.syncPolicy.syncOption필드에PrunePropagationPolicy매개변수가 포함되어 있지 않거나PrunePropagationPolicy가전경값으로 설정된 경우애플리케이션리소스에서 정책을백그라운드로 설정합니다. 다음 예제를 참조하십시오.kind: Application spec: syncPolicy: syncOptions: - PrunePropagationPolicy=backgroundkind: Application spec: syncPolicy: syncOptions: - PrunePropagationPolicy=backgroundCopy to Clipboard Copied! Toggle word wrap Toggle overflow
백그라운드삭제 정책을 설정하면ManagedClusterCR 및 모든 관련 리소스가 삭제됩니다.
2.9. GitOps ZTP 사이트 구성 리포지토리 준비
GitOps ZTP(ZTP) 파이프라인을 사용하려면 사이트 구성 데이터를 호스팅하기 위해 Git 리포지토리를 준비해야 합니다.
사전 요구 사항
- 필요한 설치 및 정책 CR(사용자 정의 리소스)을 생성하도록 Hub 클러스터 GitOps 애플리케이션을 구성했습니다.
- GitOps ZTP를 사용하여 관리 클러스터를 배포했습니다.
프로세스
SiteConfig및PolicyGenTemplateCR에 대한 별도의 경로를 사용하여 디렉터리 구조를 생성합니다.참고site
Config및PolicyGenTemplateCR을 별도의 디렉터리에 보관합니다.SiteConfig및PolicyGenTemplate디렉터리에는 둘 다 해당 디렉터리에 파일을 명시적으로 포함하는kustomization.yaml파일이 포함되어야 합니다.다음 명령을 사용하여
ztp-site-generate컨테이너 이미지에서argocd디렉터리를 내보냅니다.podman pull registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15
$ podman pull registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15Copy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p ./out
$ mkdir -p ./outCopy to Clipboard Copied! Toggle word wrap Toggle overflow podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 extract /home/ztp --tar | tar x -C ./out
$ podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 extract /home/ztp --tar | tar x -C ./outCopy to Clipboard Copied! Toggle word wrap Toggle overflow out디렉터리에 다음 하위 디렉터리가 포함되어 있는지 확인합니다.-
out/extra-manifest에는SiteConfig에서 추가 매니페스트configMap을 생성하는 데 사용하는 소스 CR 파일이 포함되어 있습니다. -
Out/source-crs에는PolicyGenTemplate이 RHACM(Red Hat Advanced Cluster Management) 정책을 생성하는 데 사용하는 소스 CR 파일이 포함되어 있습니다. -
out/argocd/deployment에는 이 절차의 다음 단계에서 사용할 허브 클러스터에 적용할 패치 및 YAML 파일이 포함되어 있습니다. -
out/argocd/example에는 권장 구성을 나타내는SiteConfig및PolicyGenTemplate파일의 예가 포함되어 있습니다.
-
-
out/source-crs폴더 및 콘텐츠를PolicyGentemplate디렉터리에 복사합니다. out/extra-manifests 디렉터리에는 RAN DU 클러스터에 대한 참조 매니페스트가 포함되어 있습니다.
out/extra-manifests디렉터리를 siteConfig폴더에 복사합니다. 이 디렉터리에는ztp-site-generate컨테이너의 CR만 포함되어야 합니다. 여기에 사용자 제공 CR을 추가하지 마십시오. 사용자 제공 CR을 사용하려면 해당 콘텐츠에 대한 다른 디렉터리를 생성해야 합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
디렉터리 구조와
kustomization.yaml파일을 커밋하고 Git 리포지토리로 내보냅니다. Git으로의 초기 내보내기에는kustomization.yaml파일이 포함되어야 합니다.
out/argocd/example 아래의 디렉터리 구조를 Git 리포지토리의 구조 및 콘텐츠에 대한 참조로 사용할 수 있습니다. 이러한 구조에는 단일 노드, 3-노드 및 표준 클러스터에 대한 SiteConfig 및 PolicyGenTemplate 참조 CR이 포함됩니다. 사용하지 않는 클러스터 유형에 대한 참조를 제거합니다.
모든 클러스터 유형의 경우 다음을 수행해야 합니다.
-
source-crs하위 디렉터리를policygentemplate디렉터리에 추가합니다. -
extra-manifests디렉터리를siteconfig디렉터리에 추가합니다.
다음 예제에서는 단일 노드 클러스터 네트워크에 대한 CR 세트를 설명합니다.
2.9.1. 버전 독립성을 위한 GitOps ZTP 사이트 구성 리포지토리 준비
GitOps ZTP를 사용하여 다른 버전의 OpenShift Container Platform을 실행하는 관리 클러스터의 소스 CR(사용자 정의 리소스)을 관리할 수 있습니다. 즉, hub 클러스터에서 실행되는 OpenShift Container Platform 버전은 관리 클러스터에서 실행되는 버전과 독립적일 수 있습니다.
프로세스
-
SiteConfig및PolicyGenTemplateCR에 대한 별도의 경로를 사용하여 디렉터리 구조를 생성합니다. PolicyGenTemplate디렉터리 내에서 사용할 각 OpenShift Container Platform 버전에 대한 디렉터리를 생성합니다. 각 버전에 다음 리소스를 생성합니다.-
해당 디렉터리에 파일을 명시적으로 포함하는
kustomization.yaml파일 ztp-site-generate컨테이너의 참조 CR 구성 파일을 포함하는source-crs디렉터리사용자 제공 CR을 사용하려면 이를 위해 별도의 디렉터리를 생성해야 합니다.
-
해당 디렉터리에 파일을 명시적으로 포함하는
/siteconfig디렉터리에서 사용할 각 OpenShift Container Platform 버전의 하위 디렉터리를 생성합니다. 각 버전에 대해 컨테이너에서 복사할 참조 CR을 참조하기 위해 하나 이상의 디렉터리를 생성합니다. 디렉터리 이름 지정 또는 참조 디렉터리 수에는 제한이 없습니다. 사용자 정의 매니페스트를 사용하려면 이를 위해 별도의 디렉터리를 생성해야 합니다.다음 예제에서는 다른 OpenShift Container Platform 버전에 대해 사용자 제공 매니페스트 및 CR을 사용하는 구조를 설명합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 최상위
kustomizationYAML 파일을 생성합니다. - 2 7
- 사용자 지정
/policygentemplates디렉터리 내에 버전별 디렉터리를 생성합니다. - 3 8
- 각 버전에 대한
kustomization.yaml파일을 생성합니다. - 4 9
ztp-site-generate컨테이너의 참조 CR을 포함하도록 각 버전의source-crs디렉터리를 생성합니다.- 5 10
- ZTP 컨테이너에서 추출된 정책 CR에 대한
reference-crs디렉터리를 생성합니다. - 6 11
- 선택 사항: 사용자 제공 CR에 대한 사용자
정의CR 디렉터리를 생성합니다. - 12 14
- 사용자 지정
/siteconfig디렉터리에 디렉터리를 생성하여ztp-site-generate컨테이너의 추가 매니페스트를 포함합니다. - 13 15
- 사용자 제공 매니페스트를 저장할 폴더를 생성합니다.
참고이전 예에서 사용자 지정
/siteconfig디렉터리의 각 버전 하위 디렉터리에는 컨테이너에서 복사한 참조 매니페스트가 포함된 두 개의 하위 디렉터리가 있으며, 다른 하나는 사용자가 제공하는 사용자 정의 매니페스트를 위한 것입니다. 해당 디렉터리에 할당된 이름은 예입니다. 사용자 제공 CR을 사용하는 경우SiteConfigCR의extraManifests.searchPaths아래에 나열된 마지막 디렉터리는 사용자 제공 CR이 포함된 디렉터리여야 합니다.생성한 디렉터리의 검색 경로를 포함하도록
SiteConfigCR을 편집합니다.extraManifests.searchPaths아래에 나열된 첫 번째 디렉터리는 참조 매니페스트가 포함된 디렉터리여야 합니다. 디렉터리가 나열되는 순서를 고려하십시오. 디렉터리에 이름이 같은 파일이 포함된 경우 최종 디렉터리의 파일이 우선합니다.siteConfig CR의 예
extraManifests: searchPaths: - extra-manifest/ - custom-manifest/extraManifests: searchPaths: - extra-manifest/1 - custom-manifest/2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow 최상위
kustomization.yaml파일을 편집하여 활성 상태인 OpenShift Container Platform 버전을 제어합니다. 다음은 최상위 수준의kustomization.yaml파일의 예입니다.resources: - version_4.13 #- version_4.14
resources: - version_4.131 #- version_4.142 Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3장. GitOps ZTP 업데이트
hub 클러스터, RHACM(Advanced Cluster Management) 및 관리형 OpenShift Container Platform 클러스터와 독립적으로ZTP(ZTP) 인프라를 업데이트할 수 있습니다.
새 버전이 출시되면 Red Hat OpenShift GitOps Operator를 업데이트할 수 있습니다. GitOps ZTP 플러그인을 업데이트할 때 참조 구성에서 업데이트된 파일을 검토하고 변경 사항이 요구 사항을 충족하는지 확인합니다.
3.1. GitOps ZTP 업데이트 프로세스 개요
이전 버전의 GitOps ZTP 인프라를 실행하는 완전히 작동하는 허브 클러스터에 대해 GitOps ZTP(ZTP)를 업데이트할 수 있습니다. 업데이트 프로세스는 관리 클러스터에 미치는 영향을 방지합니다.
권장 콘텐츠 추가를 포함하여 정책 설정을 변경하면 관리 클러스터에 롤아웃하고 조정되어야 하는 업데이트된 정책이 생성됩니다.
높은 수준에서 GitOps ZTP 인프라를 업데이트하기위한 전략은 다음과 같습니다.
-
기존 클러스터에
ztp-done라벨을 지정합니다. - ArgoCD 애플리케이션을 중지합니다.
- 새 GitOps ZTP 툴을 설치합니다.
- Git 리포지토리에서 필요한 콘텐츠 및 선택적 변경 사항을 업데이트합니다.
- 애플리케이션 구성을 업데이트하고 다시 시작합니다.
3.2. 업그레이드 준비
다음 절차에 따라ZTP(ZTP) 업그레이드를 위한 사이트를 준비합니다.
프로세스
- GitOps ZTP와 함께 사용하도록 Red Hat OpenShift GitOps를 구성하는 데 사용되는 사용자 정의 리소스(CR)가 있는 GitOps ZTP 컨테이너의 최신 버전을 가져옵니다.
다음 명령을 사용하여
argocd/deployment디렉터리를 추출합니다.mkdir -p ./update
$ mkdir -p ./updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 extract /home/ztp --tar | tar x -C ./update
$ podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 extract /home/ztp --tar | tar x -C ./updateCopy to Clipboard Copied! Toggle word wrap Toggle overflow /update디렉터리에는 다음 하위 디렉터리가 포함되어 있습니다.-
update/extra-manifest:SiteConfigCR에서 추가 매니페스트configMap을 생성하는 데 사용하는 소스 CR 파일이 포함되어 있습니다. -
update/source-crs:PolicyGenTemplateCR에서 RHACM(Red Hat Advanced Cluster Management) 정책을 생성하는 데 사용하는 소스 CR 파일이 포함되어 있습니다. -
update/argocd/deployment: 이 절차의 다음 단계에서 사용할 허브 클러스터에 적용할 패치 및 YAML 파일이 포함되어 있습니다. -
update/argocd/example: 권장 구성을 나타내는 example siteConfig및PolicyGenTemplate파일이 포함되어 있습니다.
-
애플리케이션 이름과 Git 리포지토리의 URL, 분기 및 경로를 반영하도록
cluster-app.yaml및policies-app.yaml파일을 업데이트합니다.업그레이드에 더 이상 사용되지 않는 정책이 생성되는 변경 사항이 포함된 경우 업그레이드를 수행하기 전에 더 이상 사용되지 않는 정책을 제거해야 합니다.
플릿 사이트 CR을 관리하는 /update 폴더 및 Git 리포지터리의 구성 및 배포 소스 CR 간 변경 사항을 diffe the changes between the configuration and deployment source CRs in the
/updatefolder and Git repo where you manage your fleet site CRs. 필요한 변경 사항을 적용하고 사이트 리포지토리에 내보냅니다.중요GitOps ZTP를 최신 버전으로 업데이트할 때
update/argocd/deployment디렉터리의 변경 사항을 사이트 리포지토리에 적용해야 합니다. 이전 버전의argocd/deployment/파일을 사용하지 마십시오.
3.3. 기존 클러스터에 레이블 지정
툴 업데이트로 기존 클러스터가 그대로 유지되도록 기존 관리 클러스터에 ztp-done 라벨을 지정합니다.
이 절차는 Topology Aware Lifecycle Manager (TALM)를 사용하여 프로비저닝되지 않은 클러스터를 업데이트하는 경우에만 적용됩니다. TALM으로 프로비저닝하는 클러스터는 자동으로 ztp-done 로 레이블이 지정됩니다.
프로세스
local-cluster!=true와 같이 GitOps ZTP(ZTP)와 함께 배포된 관리 클러스터를 나열하는 라벨 선택기를 찾습니다.oc get managedcluster -l 'local-cluster!=true'
$ oc get managedcluster -l 'local-cluster!=true'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 결과 목록에 GitOps ZTP와 함께 배포된 모든 관리 클러스터가 포함되어 있는지 확인한 다음 해당 선택기를 사용하여
ztp-done레이블을 추가합니다.oc label managedcluster -l 'local-cluster!=true' ztp-done=
$ oc label managedcluster -l 'local-cluster!=true' ztp-done=Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.4. 기존 GitOps ZTP 애플리케이션 중지
기존 애플리케이션을 제거하면 새 버전의 툴을 사용할 수 있을 때까지 Git 리포지토리의 기존 콘텐츠에 대한 변경 사항이 롤아웃되지 않습니다.
배포 디렉터리의 애플리케이션 파일을 사용합니다. 애플리케이션에 사용자 지정 이름을 사용한 경우 먼저 이러한 파일의 이름을 업데이트합니다.
프로세스
클러스터애플리케이션에서 캐스케이딩되지 않은 삭제를 수행하여 생성된 모든 리소스를 제자리에 남겨 둡니다.oc delete -f update/argocd/deployment/clusters-app.yaml
$ oc delete -f update/argocd/deployment/clusters-app.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 정책 애플리케이션에서 계단식 삭제를 수행하여 이전 정책을모두 제거합니다.oc patch -f policies-app.yaml -p '{"metadata": {"finalizers": ["resources-finalizer.argocd.argoproj.io"]}}' --type merge$ oc patch -f policies-app.yaml -p '{"metadata": {"finalizers": ["resources-finalizer.argocd.argoproj.io"]}}' --type mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc delete -f update/argocd/deployment/policies-app.yaml
$ oc delete -f update/argocd/deployment/policies-app.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.5. Git 리포지토리에 대한 필수 변경 사항
ztp-site-generate 컨테이너를 이전 버전의 ZTP(ZTP)에서 4.10 이상으로 업그레이드하는 경우 Git 리포지토리의 콘텐츠에 대한 추가 요구 사항이 있습니다. 리포지토리의 기존 콘텐츠는 이러한 변경 사항을 반영하도록 업데이트해야 합니다.
PolicyGenTemplate파일을 변경해야 합니다.모든
PolicyGenTemplate파일은ztp로 접두사가 지정된 네임스페이스에서 생성해야 합니다. 이렇게 하면 GitOps ZTP 애플리케이션이 RHSM(Red Hat Advanced Cluster Management)에서 내부적으로 정책을 관리하는 방식과 충돌하지 않고 GitOps ZTP에서 생성한 정책 CR을 관리할 수 있습니다.kustomization.yaml파일을 리포지토리에 추가합니다.모든
siteConfig및PolicyGenTemplateCR은 해당 디렉터리 트리 아래에kustomization.yaml파일에 포함되어야 합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고생성기섹션에 나열된 파일에는 siteConfig또는PolicyGenTemplateCR만 포함되어야 합니다. 기존 YAML 파일에 다른 CR(예:네임스페이스)이 포함된 경우 이러한 다른 CR을 별도의 파일로 가져와resources섹션에 나열해야 합니다.PolicyGenTemplatekustomization 파일에는resources섹션의generator섹션에 있는 모든PolicyGenTemplateYAML 파일과NamespaceCR이 포함되어야 합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow SiteConfigkustomization 파일에는생성기섹션의 모든SiteConfigYAML 파일과 리소스의 다른 CR이 포함되어야 합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow pre-sync.yaml및post-sync.yaml파일을 제거합니다.OpenShift Container Platform 4.10 이상에서는 더 이상
pre-sync.yaml및post-sync.yaml파일이 필요하지 않습니다.update/deployment/kustomization.yamlCR은 hub 클러스터에서 정책 배포를 관리합니다.참고SiteConfig및PolicyGenTemplate트리 아래에는pre-sync.yaml및post-sync.yaml파일 세트가 있습니다.권장 변경 사항 검토 및 통합
각 릴리스에는 배포된 클러스터에 적용된 구성에 권장되는 추가 변경 사항이 포함될 수 있습니다. 일반적으로 이러한 변경으로 인해 OpenShift 플랫폼, 추가 기능 또는 플랫폼 튜닝에서 CPU 사용이 줄어들게 됩니다.
네트워크의 클러스터 유형에 적용되는
사이트Config및PolicyGenTemplateCR을 확인합니다. 이러한 예제는 GitOps ZTP 컨테이너에서 추출된argocd/example디렉터리에서 확인할 수 있습니다.
3.6. 새 GitOps ZTP 애플리케이션 설치
추출된 argocd/deployment 디렉터리를 사용하여 애플리케이션이 사이트 Git 리포지토리를 가리키는지 확인한 후 배포 디렉터리의 전체 콘텐츠를 적용합니다. 디렉터리의 전체 콘텐츠를 적용하면 애플리케이션에 필요한 모든 리소스가 올바르게 구성됩니다.
프로세스
GitOps ZTP 플러그인을 설치하려면 허브 클러스터의 ArgoCD 인스턴스를 관련 MCCE(Multicluster engine) 서브스크립션 이미지로 패치합니다. 이전에 추출한 패치 파일을 사용자 환경의
out/argocd/deployment/디렉터리에 사용자 지정합니다.RHACM 버전과 일치하는
multicluster-operators-subscription이미지를 선택합니다.-
RHACM 2.8 및 2.9의 경우
registry.redhat.io/rhacm2/multicluster-operators-subscription-rhel8:v<rhacm_version> 이미지를 사용합니다. -
RHACM 2.10 이상의 경우
registry.redhat.io/rhacm2/multicluster-operators-subscription-rhel9:v<rhacm_version> 이미지를 사용합니다.
중요multicluster-operators-subscription이미지의 버전은 RHACM 버전과 일치해야 합니다. MCE 2.10 릴리스부터 RHEL 9는multicluster-operators-subscription이미지의 기본 이미지입니다.OpenShift Operator 라이프 사이클의 "Platform Aligned Operators" 표에서
[Expand for Operator list]를 클릭하여 OpenShift Container Platform에 대해 지원되는 전체 Operator 매트릭스를 확인합니다.-
RHACM 2.8 및 2.9의 경우
out/argocd/deployment/argocd-openshift-gitops-patch.json파일에 다음 구성을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow ArgoCD 인스턴스를 패치합니다. 다음 명령을 실행합니다.
oc patch argocd openshift-gitops \ -n openshift-gitops --type=merge \ --patch-file out/argocd/deployment/argocd-openshift-gitops-patch.json
$ oc patch argocd openshift-gitops \ -n openshift-gitops --type=merge \ --patch-file out/argocd/deployment/argocd-openshift-gitops-patch.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow
RHACM 2.7 이상에서는 다중 클러스터 엔진에서 기본적으로
cluster-proxy-addon기능을 활성화합니다. 다음 패치를 적용하여cluster-proxy-addon기능을 비활성화하고 이 애드온을 담당하는 관련 허브 클러스터 및 관리 Pod를 제거합니다. 다음 명령을 실행합니다.oc patch multiclusterengines.multicluster.openshift.io multiclusterengine --type=merge --patch-file out/argocd/deployment/disable-cluster-proxy-addon.json
$ oc patch multiclusterengines.multicluster.openshift.io multiclusterengine --type=merge --patch-file out/argocd/deployment/disable-cluster-proxy-addon.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 허브 클러스터에 파이프라인 구성을 적용합니다.
oc apply -k out/argocd/deployment
$ oc apply -k out/argocd/deploymentCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.7. GitOps ZTP 구성 변경 사항 롤아웃
권장 변경 사항 구현으로 인해 구성 변경이 업그레이드에 포함된 경우 업그레이드 프로세스에서 hub 클러스터에 정책 CR 세트를 Non-Compliant 상태로 만듭니다. GitOps ZTP(ZTP) 버전 4.10 및 이후 ztp-site-generate 컨테이너를 사용하면 이러한 정책은 정보 모드로 설정되고 사용자가 추가 단계없이 관리 클러스터로 푸시되지 않습니다. 이렇게 하면 변경 사항이 발생하는 시기(예: 유지 관리 기간 중) 및 동시에 업데이트되는 클러스터 수에 따라 클러스터에 잠재적으로 중단될 수 있습니다.
변경 사항을 롤아웃하려면 TALM 설명서에 자세히 설명된 대로 하나 이상의 ClusterGroupUpgrade CR을 생성합니다. CR에는 관리되는 클러스터에 푸시하려는 비준수 정책 목록과 업데이트에 포함되어야 하는 클러스터 목록 또는 선택기가 포함되어야 합니다.
4장. RHACM 및 siteConfig 리소스를 사용하여 관리형 클러스터 설치
지원 서비스 및 core-reduction 기술이 활성화된 GitOps 플러그인 정책 생성기를 사용하여 RHACM(Red Hat Advanced Cluster Management)을 사용하여 대규모로 OpenShift Container Platform 클러스터를 프로비저닝할 수 있습니다. GitOps ZTP(ZTP) 파이프라인은 클러스터 설치를 수행합니다. GitOps ZTP는 연결이 끊긴 환경에서 사용할 수 있습니다.
4.1. GitOps ZTP 및 토폴로지 인식 라이프사이클 관리자
GitOps ZTP(ZTP)는 Git에 저장된 매니페스트에서 설치 및 구성 CR을 생성합니다. 이러한 아티팩트는 RHACM(Red Hat Advanced Cluster Management), 지원 서비스, 토폴로지 Aware Lifecycle Manager(TALM)에서 CR을 사용하여 관리 클러스터를 설치하고 구성하는 중앙 집중식 허브 클러스터에 적용됩니다. GitOps ZTP 파이프라인의 구성 단계는 TALM을 사용하여 구성 CR의 애플리케이션을 클러스터에 오케스트레이션합니다. GitOps ZTP와 TALM 사이에는 몇 가지 주요 통합 지점이 있습니다.
- 정책 정보
-
기본적으로 GitOps ZTP는
inform이라는 수정 작업을 사용하여 모든 정책을 생성합니다. 이러한 정책을 사용하면 RHACM에서 정책과 관련된 클러스터의 규정 준수 상태를 보고하지만 원하는 구성은 적용되지 않습니다. GitOps ZTP 프로세스 중에 OpenShift를 설치한 후 생성된정보정책을 통해 TALM을 단계화하고 대상 관리 클러스터에 적용합니다. 이렇게 하면 구성이 관리 클러스터에 적용됩니다. 클러스터 라이프사이클의 GitOps ZTP 단계 외부에서는 해당 변경 사항을 영향을 받는 클러스터로 즉시 롤아웃할 위험이 없는 정책을 변경할 수 있습니다. TALM을 사용하여 수정되는 클러스터 세트와 타이밍을 제어할 수 있습니다. - ClusterGroupUpgrade CR 자동 생성
새로 배포된 클러스터의 초기 구성을 자동화하기 위해 TALM은 hub 클러스터에서 모든
ManagedClusterCR의 상태를 모니터링합니다. 새로 생성된ManagedClusterCR을 포함하여ztp-done레이블이 적용되지 않은ManagedClusterCR을 사용하면 TALM에서 다음과 같은 특성을 가진ClusterGroupUpgradeCR을 자동으로 생성합니다.-
ztp-install네임스페이스에서ClusterGroupUpgradeCR이 생성되고 활성화됩니다. -
ClusterGroupUpgradeCR의 이름은ManagedClusterCR과 동일합니다. -
클러스터 선택기에는 해당
ManagedClusterCR과 연결된 클러스터만 포함됩니다. -
관리 정책 세트에는
ClusterGroupUpgrade가 생성될 때 RHACM이 클러스터에 바인딩한 모든 정책이 포함됩니다. - 사전 캐싱은 비활성화되어 있습니다.
- 시간 초과가 4시간(240분)으로 설정됩니다.
활성화된
ClusterGroupUpgrade의 자동 생성을 통해 사용자 개입 없이도 초기 무차별 클러스터 배포를 진행할 수 있습니다. 또한ztp-done레이블이 없는ManagedCluster에 대한ClusterGroupUpgradeCR을 자동으로 생성하면 클러스터에 대한ClusterGroupUpgradeCR을 간단히 삭제하여 실패한 GitOps ZTP 설치를 다시 시작할 수 있습니다.-
- 웨이브
PolicyGenTemplateCR에서 생성된 각 정책에는ztp-deploy-ECDSA 주석이포함됩니다. 이 주석은 해당 정책에 포함된 각 CR에서 동일한 주석을 기반으로 합니다. 웨이브 주석은 자동 생성된ClusterGroupUpgradeCR의 정책을 정렬하는 데 사용됩니다. 웨이브 주석은 자동 생성된ClusterGroupUpgradeCR 이외의 용도로는 사용되지 않습니다.참고동일한 정책의 모든 CR에는
ztp-deploy-Cryostat 주석에 대해 동일한 설정이 있어야 합니다. 각 CR에 대한 이 주석의 기본값은PolicyGenTemplate에서 재정의할 수 있습니다. 소스 CR의 웨이브 주석은 정책파 주석을 결정하고 설정하는 데 사용됩니다. 이 주석은 런타임 시 생성된 정책에 포함된 각 빌드된 CR에서 제거됩니다.TALM은 웨이브 주석에 의해 지정된 순서로 구성 정책을 적용합니다. TALM은 다음 정책으로 이동하기 전에 각 정책이 준수될 때까지 기다립니다. 각 CR의 웨이브 주석이 클러스터에 적용되려면 해당 CR의 사전 요구 사항을 고려해야 합니다. 예를 들어 Operator의 구성과 동시에 Operator를 설치해야 합니다. 마찬가지로 Operator 서브스크립션 이전 또는 동시에 Operator의
CatalogSource를 설치해야 합니다. 각 CR의 기본 웨이브 값은 이러한 사전 요구 사항을 고려합니다.참고여러 CR과 정책은 동일한 웨이브 번호를 공유할 수 있습니다. 정책을 줄이면 배포가 빨라지고 CPU 사용량을 줄일 수 있습니다. 많은 CR을 비교적 적은 파도로 그룹화하는 것이 좋습니다.
각 소스 CR의 기본 웨이브 값을 확인하려면
ztp-site-generate컨테이너 이미지에서 추출된out/source-crs디렉터리에 대해 다음 명령을 실행합니다.grep -r "ztp-deploy-wave" out/source-crs
$ grep -r "ztp-deploy-wave" out/source-crsCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 단계 레이블
ClusterGroupUpgradeCR이 자동으로 생성되고 GitOps ZTP 프로세스의 시작 및 종료 시 라벨을 사용하여ManagedClusterCR에 주석을 달 수 있는 지시문이 포함됩니다.GitOps ZTP 구성 후 설치가 시작되면
ManagedCluster에ztp-running레이블이 적용됩니다. 모든 정책이 클러스터에 수정되어 완전히 준수되면 이러한 지시문으로 인해 TALM에서ztp-running레이블을 제거하고ztp-done레이블을 적용합니다.informDuValidator정책을 사용하는 배포의 경우 클러스터가 애플리케이션 배포를 완전히 준비할 때ztp-done레이블이 적용됩니다. 여기에는 GitOps ZTP가 적용된 구성 CR의 모든 조정 및 결과 영향이 포함됩니다.ztp-done레이블은 TALM의 자동ClusterGroupUpgradeCR 생성에 영향을 미칩니다. 클러스터의 초기 GitOps ZTP 설치 후에는 이 라벨을 조작하지 마십시오.- 연결된 CR
-
자동으로 생성된
ClusterGroupUpgradeCR에는 파생된ManagedCluster로 설정된 owner 참조가 있습니다. 이 참조를 사용하면ManagedClusterCR을 삭제하면 지원되는 리소스와 함께ClusterGroupUpgrade인스턴스가 삭제됩니다.
4.2. GitOps ZTP를 사용하여 관리형 클러스터 배포 개요
RHACM(Red Hat Advanced Cluster Management)은 GitOps ZTP(ZTP)를 사용하여 단일 노드 OpenShift Container Platform 클러스터, 3노드 클러스터 및 표준 클러스터를 배포합니다. Git 리포지토리에서 사이트 구성 데이터를 OpenShift Container Platform CR(사용자 정의 리소스)으로 관리합니다. GitOps ZTP는 선언적 GitOps 접근 방식을 사용하여 한 번 개발하고 모델을 배포하여 관리 클러스터를 배포합니다.
클러스터 배포에는 다음이 포함됩니다.
- 빈 서버에 호스트 운영 체제(RHCOS) 설치
- OpenShift Container Platform 배포
- 클러스터 정책 및 사이트 서브스크립션 생성
- 서버 운영 체제에 필요한 네트워크 구성 만들기
- 프로파일 Operator 배포 및 성능 프로필, PTP 및 SR-IOV와 같은 필요한 소프트웨어 관련 구성 수행
4.2.1. 관리 사이트 설치 프로세스 개요
허브 클러스터에 관리 사이트 CR(사용자 정의 리소스)을 적용한 후 다음 작업이 자동으로 수행됩니다.
- 검색 이미지 ISO 파일이 생성되어 대상 호스트에서 부팅됩니다.
- 대상 호스트에서 ISO 파일이 성공적으로 부팅되면 호스트 하드웨어 정보를 RHACM에 보고합니다.
- 모든 호스트가 검색되면 OpenShift Container Platform이 설치됩니다.
-
OpenShift Container Platform 설치가 완료되면 허브가 대상 클러스터에
klusterlet서비스를 설치합니다. - 요청된 애드온 서비스가 대상 클러스터에 설치되어 있습니다.
hub 클러스터에서 관리 클러스터의 Agent CR이 생성되면 Discovery 이미지 ISO 프로세스가 완료됩니다.
대상 베어 메탈 호스트는 vDU 애플리케이션 워크로드에 대해 권장 단일 노드 OpenShift 클러스터 구성에 나열된 네트워킹, 펌웨어 및 하드웨어 요구 사항을 충족해야 합니다.
4.3. 관리형 베어 메탈 호스트 시크릿 생성
관리 베어 메탈 호스트에 필요한 Secret CR(사용자 정의 리소스)을 hub 클러스터에 추가합니다. BMC(Baseboard Management Controller)에 액세스하려면 GitOps ZTP(ZTP) 파이프라인의 시크릿과 지원되는 설치 프로그램 서비스에서 레지스트리에서 클러스터 설치 이미지를 가져오는 시크릿이 필요합니다.
보안은 site Config CR에서 이름으로 참조됩니다. 네임스페이스는 site Config 네임스페이스와 일치해야 합니다.
프로세스
OpenShift 및 모든 추가 기능 클러스터 Operator 설치에 필요한 호스트 BMC(Baseboard Management Controller)에 대한 인증 정보와 풀 시크릿을 포함하는 YAML 시크릿 파일을 생성합니다.
-
클러스터를 설치하는 데 사용하는
kustomization.yaml파일에example-sno-secret.yaml에 상대 경로를 추가합니다.
4.4. GitOps ZTP를 사용하여 설치를 위한 Discovery ISO 커널 인수 구성
GitOps ZTP(ZTP) 워크플로는 관리형 베어 메탈 호스트에서 OpenShift Container Platform 설치 프로세스의 일부로 Discovery ISO를 사용합니다. InfraEnv 리소스를 편집하여 Discovery ISO에 대한 커널 인수를 지정할 수 있습니다. 이는 특정 환경 요구 사항이 있는 클러스터 설치에 유용합니다. 예를 들어 클러스터의 정적 네트워킹을 용이하게 하거나 설치 중에 루트 파일 시스템을 다운로드하기 전에 DHCP 주소를 수신하도록 Discovery ISO에 rd.net.timeout.carrier 커널 인수를 구성합니다.
OpenShift Container Platform 4.15에서는 커널 인수만 추가할 수 있습니다. 커널 인수를 교체하거나 삭제할 수 없습니다.
사전 요구 사항
- OpenShift CLI(oc)가 설치되어 있습니다.
- cluster-admin 권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
InfraEnvCR을 생성하고spec.kernelArguments사양을 편집하여 커널 인수를 구성합니다.다음 YAML을
InfraEnv-example.yaml파일에 저장합니다.참고이 예제의
InfraEnvCR은 siteConfigCR의 값에 따라 채워진{{ .Cluster.ClusterName }}과 같은 템플릿 구문을 사용합니다.SiteConfigCR은 배포 중에 이러한 템플릿의 값을 자동으로 채웁니다. 템플릿을 수동으로 편집하지 마십시오.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
InfraEnv-example.yamlCR을 siteConfigCR이 있는 Git 리포지토리의 동일한 위치에 커밋하고 변경 사항을 내보냅니다. 다음 예제에서는 샘플 Git 리포지토리 구조를 보여줍니다.~/example-ztp/install └── site-install ├── siteconfig-example.yaml ├── InfraEnv-example.yaml ...~/example-ztp/install └── site-install ├── siteconfig-example.yaml ├── InfraEnv-example.yaml ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow SiteConfigCR에서spec.clusters.crTemplates사양을 편집하여 Git 리포지토리의InfraEnv-example.yamlCR을 참조합니다.clusters: crTemplates: InfraEnv: "InfraEnv-example.yaml"clusters: crTemplates: InfraEnv: "InfraEnv-example.yaml"Copy to Clipboard Copied! Toggle word wrap Toggle overflow SiteConfigCR을 커밋하고 푸시하여 클러스터를 배포할 준비가 되면 빌드 파이프라인은 Git 리포지토리의 사용자 지정InfraEnv-exampleCR을 사용하여 사용자 지정 커널 인수를 포함하여 인프라 환경을 구성합니다.
검증
커널 인수가 적용되었는지 확인하려면 검색 이미지에서 OpenShift Container Platform을 설치할 준비가 되었는지 확인한 후 설치 프로세스가 시작되기 전에 대상 호스트에 SSH를 수행할 수 있습니다. 이때 /proc/cmdline 파일에서 Discovery ISO의 커널 인수를 볼 수 있습니다.
대상 호스트를 사용하여 SSH 세션을 시작합니다.
ssh -i /path/to/privatekey core@<host_name>
$ ssh -i /path/to/privatekey core@<host_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 시스템의 커널 인수를 확인합니다.
cat /proc/cmdline
$ cat /proc/cmdlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.5. SiteConfig 및 GitOps ZTP를 사용하여 관리형 클러스터 배포
다음 절차에 따라 SiteConfig CR(사용자 정의 리소스) 및 관련 파일을 생성하고 ZTP( GitOps Zero Touch Provisioning) 클러스터 배포를 시작합니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다. - 필요한 설치 및 정책 CR을 생성하도록 허브 클러스터를 구성했습니다.
사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성하셨습니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 ArgoCD 애플리케이션의 소스 리포지토리로 구성해야 합니다. 자세한 내용은 " GitOps ZTP 사이트 구성 리포지토리 준비"를 참조하십시오.
참고소스 리포지토리를 생성할 때
ztp-site-generate컨테이너에서 추출한argocd/deployment/argocd-openshift-gitops-patch.jsonpatch-file을 사용하여 ArgoCD 애플리케이션을 패치하는지 확인합니다. " ArgoCD를 사용하여 허브 클러스터 구성"을 참조하십시오.관리 클러스터 프로비저닝을 준비하려면 각 베어 메탈 호스트에 대해 다음이 필요합니다.
- 네트워크 연결
- 네트워크에는 DNS가 필요합니다. 허브 클러스터에서 관리 클러스터 호스트에 연결할 수 있어야 합니다. hub 클러스터와 관리 클러스터 호스트 간에 계층 3 연결이 있는지 확인합니다.
- BMC(Baseboard Management Controller) 세부 정보
-
GitOps ZTP는 BMC 사용자 이름과 암호 세부 정보를 사용하여 클러스터 설치 중에 BMC에 연결합니다. GitOps ZTP 플러그인은 사이트 Git 리포지토리의 site
ConfigCR을 기반으로 Hub 클러스터에서ManagedClusterCR을 관리합니다. 각 호스트에 대해 수동으로 개별BMCSecretCR을 생성합니다.
프로세스
hub 클러스터에 필요한 관리 클러스터 시크릿을 생성합니다. 이러한 리소스는 클러스터 이름과 일치하는 이름이 있는 네임스페이스에 있어야 합니다. 예를 들어
out/argocd/example/siteconfig/example-sno.yaml에서 클러스터 이름과 네임스페이스는example-sno입니다.다음 명령을 실행하여 클러스터 네임스페이스를 내보냅니다.
export CLUSTERNS=example-sno
$ export CLUSTERNS=example-snoCopy to Clipboard Copied! Toggle word wrap Toggle overflow 네임스페이스를 생성합니다.
oc create namespace $CLUSTERNS
$ oc create namespace $CLUSTERNSCopy to Clipboard Copied! Toggle word wrap Toggle overflow
관리 클러스터에 대한 풀 시크릿 및 BMC
SecretCR을 생성합니다. 풀 시크릿에는 OpenShift Container Platform 및 필요한 모든 Operator를 설치하는 데 필요한 모든 인증 정보가 포함되어야 합니다. 자세한 내용은 "관리된 베어 메탈 호스트 시크릿 생성"을 참조하십시오.참고보안은 site
ConfigCR(사용자 정의 리소스)에서 이름으로 참조됩니다. 네임스페이스는 siteConfig 네임스페이스와일치해야 합니다.Git 리포지토리의 로컬 복제본에 클러스터의 site
ConfigCR을 생성합니다.out/argocd/example/siteconfig/폴더에서 CR에 적합한 예제를 선택합니다. 폴더에는 단일 노드, 3-노드 및 표준 클러스터에 대한 예제 파일이 포함되어 있습니다.-
example-sno.yaml -
예:-3node.yaml -
example-standard.yaml
-
예제 파일의 클러스터 및 호스트 세부 정보를 원하는 클러스터 유형과 일치하도록 변경합니다. 예를 들면 다음과 같습니다.
단일 노드 OpenShift SiteConfig CR의 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고BMC 주소 지정에 대한 자세한 내용은 "추가 리소스" 섹션을 참조하십시오.
installConfigOverrides및ignitionConfigOverride필드는 쉽게 읽을 수 있도록 확장됩니다.-
외부/argocd/extra-manifest에서기본 extra-manifestMachineConfigCR 세트를 검사할 수 있습니다. 설치 시 클러스터에 자동으로 적용됩니다. 선택 사항: 프로비저닝된 클러스터에서 추가 설치 시간 매니페스트를 프로비저닝하려면 Git 리포지토리에 디렉터리를 생성하고 (예:
sno-extra-manifest/) 사용자 정의 매니페스트 CR을 이 디렉터리에 추가합니다.SiteConfig.yaml이extraManifestPath필드의 이 디렉터리를 참조하는 경우 이 참조 디렉터리의 모든 CR이 기본 추가 매니페스트 세트에 추가됩니다.crun OCI 컨테이너 런타임 활성화최적의 클러스터 성능을 위해서는 단일 노드 OpenShift에서 마스터 및 작업자 노드에 대해 crun, 추가 작업자 노드가 있는 단일 노드 OpenShift, 3-노드 OpenShift 및 표준 클러스터를 활성화합니다.
클러스터를 재부팅하지 않도록
ContainerRuntimeConfigCR에서 0일 추가 설치 시간 매니페스트로 crun을 활성화합니다.enable-crun-master.yaml및enable-crun-worker.yamlCR 파일은ztp-site-generate컨테이너에서 추출할 수 있는out/source-crs/optional-extra-manifest/폴더에 있습니다. 자세한 내용은 " GitOps ZTP 파이프라인의 추가 설치 매니페스트 사용자 지정"을 참조하십시오.
-
out/argocd/example/siteconfig/과 유사하게kustomization.yamlgenerators섹션의 kustomization.yaml 파일에SiteConfigCR을 추가합니다. Git 리포지토리에서
SiteConfigCR 및 관련kustomization.yaml변경 사항을 커밋하고 변경 사항을 내보냅니다.ArgoCD 파이프라인은 변경 사항을 감지하고 관리 클러스터 배포를 시작합니다.
검증
노드가 배포된 후 사용자 정의 역할 및 라벨이 적용되는지 확인합니다.
oc describe node example-node.example.com
$ oc describe node example-node.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
출력 예
- 1
- 사용자 정의 레이블이 노드에 적용됩니다.
4.5.1. 단일 노드 OpenShift SiteConfig CR 설치 참조
| siteConfig CR 필드 | 설명 |
|---|---|
|
|
참고
|
|
|
|
|
|
사이트의 모든 클러스터에 대해 hub 클러스터에서 사용 가능한 이미지 세트를 구성합니다. hub 클러스터에서 지원되는 버전 목록을 보려면 |
|
|
클러스터 설치 전에 선택적 구성 요소를 활성화하거나 비활성화하려면 중요
예제 |
|
|
개별 클러스터를 배포하는 데 사용되는 클러스터 이미지 세트를 지정합니다. 정의된 경우 사이트 수준에서 |
|
|
사용자가 정의한 |
|
|
선택 사항: |
|
|
단일 노드 배포의 경우 단일 호스트를 정의합니다. 3-노드 배포의 경우 세 개의 호스트를 정의합니다. 표준 배포의 경우 역할이 있는 세 개의 호스트( |
|
| 관리 클러스터에서 노드의 사용자 지정 역할을 지정합니다. 추가 역할은 사용자만 OpenShift Container Platform 구성 요소에서 사용하지 않습니다. 사용자 지정 역할을 추가하면 해당 역할의 특정 구성을 참조하는 사용자 지정 머신 구성 풀과 연결할 수 있습니다. 설치 중에 사용자 정의 레이블 또는 역할을 추가하면 배포 프로세스가 더 효과적이며 설치가 완료된 후 추가 재부팅이 필요하지 않습니다. |
|
|
선택 사항: 디스크를 완전히 삭제하지 않고 값의 주석을 |
|
| 호스트에 액세스하는 데 사용하는 BMC 주소입니다. 모든 클러스터 유형에 적용됩니다. GitOps ZTP는 Redfish 또는 IPMI 프로토콜을 사용하여 iPXE 및 가상 미디어 부팅을 지원합니다. iPXE 부팅을 사용하려면 RHACM 2.8 이상을 사용해야 합니다. BMC 주소 지정에 대한 자세한 내용은 "추가 리소스" 섹션을 참조하십시오. |
|
| 호스트에 액세스하는 데 사용하는 BMC 주소입니다. 모든 클러스터 유형에 적용됩니다. GitOps ZTP는 Redfish 또는 IPMI 프로토콜을 사용하여 iPXE 및 가상 미디어 부팅을 지원합니다. iPXE 부팅을 사용하려면 RHACM 2.8 이상을 사용해야 합니다. BMC 주소 지정에 대한 자세한 내용은 "추가 리소스" 섹션을 참조하십시오. 참고 지금까지 엣지 Telco 사용 사례에서는 GitOps ZTP에서 사용할 수 있도록 가상 미디어만 지원됩니다. |
|
|
호스트 BMC 인증 정보를 사용하여 별도로 생성하는 |
|
|
호스트의 부팅 모드를 |
|
|
배포 장치를 지정합니다. 재부팅 시 안정적인 식별자를 사용하는 것이 좋습니다. 예를 들어 |
|
| 선택 사항: 이 필드를 사용하여 영구 스토리지의 파티션을 할당합니다. 디스크 ID와 크기를 특정 하드웨어에 조정합니다. |
|
| 노드의 네트워크 설정을 구성합니다. |
|
| 호스트의 IPv6 주소를 구성합니다. 고정 IP 주소가 있는 단일 노드 OpenShift 클러스터의 경우 노드별 API 및 Ingress IP가 동일해야 합니다. |
4.6. 관리형 클러스터 설치 진행 상황 모니터링
ArgoCD 파이프라인은 site Config CR을 사용하여 클러스터 구성 CR을 생성하고 Hub 클러스터와 동기화합니다. ArgoCD 대시보드에서 동기화의 진행 상황을 모니터링할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
동기화가 완료되면 설치는 일반적으로 다음과 같이 진행됩니다.
Assisted Service Operator는 클러스터에 OpenShift Container Platform을 설치합니다. 다음 명령을 실행하여 RHACM 대시보드 또는 명령줄에서 클러스터 설치 진행 상황을 모니터링할 수 있습니다.
클러스터 이름을 내보냅니다.
export CLUSTER=<clusterName>
$ export CLUSTER=<clusterName>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터의
AgentClusterInstallCR을 쿼리합니다.oc get agentclusterinstall -n $CLUSTER $CLUSTER -o jsonpath='{.status.conditions[?(@.type=="Completed")]}' | jq$ oc get agentclusterinstall -n $CLUSTER $CLUSTER -o jsonpath='{.status.conditions[?(@.type=="Completed")]}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 클러스터의 설치 이벤트를 가져옵니다.
curl -sk $(oc get agentclusterinstall -n $CLUSTER $CLUSTER -o jsonpath='{.status.debugInfo.eventsURL}') | jq '.[-2,-1]'$ curl -sk $(oc get agentclusterinstall -n $CLUSTER $CLUSTER -o jsonpath='{.status.debugInfo.eventsURL}') | jq '.[-2,-1]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.7. 설치 CR을 검증하여 GitOps ZTP 문제 해결
ArgoCD 파이프라인은 site Config 및 PolicyGenTemplate CR(사용자 정의 리소스)을 사용하여 클러스터 구성 CR 및 RHACM(Red Hat Advanced Cluster Management) 정책을 생성합니다. 이 프로세스 중에 발생할 수 있는 문제를 해결하려면 다음 단계를 사용하십시오.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
다음 명령을 사용하여 설치 CR이 생성되었는지 확인합니다.
oc get AgentClusterInstall -n <cluster_name>
$ oc get AgentClusterInstall -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 오브젝트가 반환되지 않은 경우 다음 단계를 사용하여
SiteConfig파일에서 설치 CR로 ArgoCD 파이프라인 흐름의 문제를 해결합니다.hub 클러스터의
SiteConfigCR을 사용하여ManagedClusterCR이 생성되었는지 확인합니다.oc get managedcluster
$ oc get managedclusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow ManagedCluster가 없는 경우클러스터애플리케이션이 Git 리포지토리의 파일을 hub 클러스터와 동기화하지 않았는지 확인합니다.oc get applications.argoproj.io -n openshift-gitops clusters -o yaml
$ oc get applications.argoproj.io -n openshift-gitops clusters -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터의 오류 로그를 식별하려면
status.operationState.syncResult.resources필드를 검사합니다. 예를 들어, siteConfig CR의않은 값이 할당되면 다음과 유사한 오류가 생성됩니다.extraManifestPath에 유효하지Copy to Clipboard Copied! Toggle word wrap Toggle overflow 자세한 site
Config 오류를보려면 다음 단계를 완료하십시오.- Argo CD 대시보드에서 Argo CD가 동기화하려는 SiteConfig 리소스를 클릭합니다.
DESIRED MANIFEST 탭을 확인하여
siteConfigError필드를 찾습니다.siteConfigError: >- Error: could not build the entire SiteConfig defined by /tmp/kust-plugin-config-1081291903: stat sno-extra-manifest: no such file or directory
siteConfigError: >- Error: could not build the entire SiteConfig defined by /tmp/kust-plugin-config-1081291903: stat sno-extra-manifest: no such file or directoryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Status.Sync필드를 확인합니다. 로그 오류가 있는 경우Status.Sync필드에 알 수없는오류가 표시될 수 있습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.8. Supermicro 서버에서 GitOps ZTP 가상 미디어 부팅 문제 해결
Supermicro X11 서버는 https 프로토콜을 사용하여 이미지를 제공하는 경우 가상 미디어 설치를 지원하지 않습니다. 결과적으로 이 환경의 단일 노드 OpenShift 배포가 대상 노드에서 부팅되지 않습니다. 이 문제를 방지하려면 hub 클러스터에 로그인하고 프로비저닝 리소스에서 TLS(Transport Layer Security)를 비활성화합니다. 이렇게 하면 이미지 주소가 https 스키마를 사용하더라도 TLS로 이미지가 제공되지 않습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
다음 명령을 실행하여
프로비저닝리소스에서 TLS를 비활성화합니다.oc patch provisioning provisioning-configuration --type merge -p '{"spec":{"disableVirtualMediaTLS": true}}'$ oc patch provisioning provisioning-configuration --type merge -p '{"spec":{"disableVirtualMediaTLS": true}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 단일 노드 OpenShift 클러스터를 배포하려면 단계를 계속합니다.
4.9. GitOps ZTP 파이프라인에서 관리되는 클러스터 사이트 제거
GitOps ZTP(ZTP) 파이프라인에서 관리 사이트 및 관련 설치 및 구성 정책 CR을 제거할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
-
kustomization.yaml파일에서 관련SiteConfig및PolicyGenTemplate파일을 제거하여 사이트 및 관련 CR을 제거합니다. SiteConfig애플리케이션에 다음syncOptions필드를 추가합니다.kind: Application spec: syncPolicy: syncOptions: - PrunePropagationPolicy=backgroundkind: Application spec: syncPolicy: syncOptions: - PrunePropagationPolicy=backgroundCopy to Clipboard Copied! Toggle word wrap Toggle overflow GitOps ZTP 파이프라인을 다시 실행하면 생성된 CR이 제거됩니다.
-
선택 사항: 사이트를 영구적으로 제거하려면 Git 리포지토리에서 site
Config및 사이트별PolicyGenTemplate파일을 제거해야 합니다. -
선택 사항: 예를 들어 사이트를 재배포할 때 사이트를 일시적으로 제거하려면 site
Config 및 사이트별PolicyGenTemplateCR을 Git 리포지토리에 남겨 둘 수 있습니다.
4.10. GitOps ZTP 파이프라인에서 더 이상 사용되지 않는 콘텐츠 제거
PolicyGenTemplate 구성을 변경하면 더 이상 사용되지 않는 정책이 생성되는 경우(예: 정책 이름 변경) 다음 절차를 사용하여 더 이상 사용되지 않는 정책을 제거합니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
-
Git 리포지토리에서 영향을 받는
PolicyGenTemplate파일을 제거하고 원격 리포지토리를 커밋하고 내보냅니다. - 변경 사항이 애플리케이션을 통해 동기화되고 영향을 받는 정책이 허브 클러스터에서 제거될 때까지 기다립니다.
업데이트된
PolicyGenTemplate파일을 Git 리포지토리에 다시 추가한 다음 원격 리포지토리를 커밋하고 내보냅니다.참고Git 리포지토리에서 GitOps Zero Touch Provisioning(ZTP) 정책을 제거하면 허브 클러스터에서도 해당 정책을 제거해도 관리 클러스터의 구성에 영향을 미치지 않습니다. 해당 정책에서 관리하는 정책 및 CR은 관리 클러스터에 남아 있습니다.
선택 사항: 대신 더 이상 사용되지 않는 정책을 생성하는
PolicyGenTemplateCR을 변경한 후 hub 클러스터에서 이러한 정책을 수동으로 제거할 수 있습니다. Governance 탭을 사용하거나 다음 명령을 실행하여 RHACM 콘솔에서 정책을 삭제할 수 있습니다.oc delete policy -n <namespace> <policy_name>
$ oc delete policy -n <namespace> <policy_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11. GitOps ZTP 파이프라인 종료
ArgoCD 파이프라인 및 생성된 모든 ZTP(ZTP) 아티팩트를 제거할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
- hub 클러스터의 RHACM(Red Hat Advanced Cluster Management)에서 모든 클러스터를 분리합니다.
다음 명령을 사용하여
배포디렉터리에서kustomization.yaml파일을 삭제합니다.oc delete -k out/argocd/deployment
$ oc delete -k out/argocd/deploymentCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 변경 사항을 커밋하고 사이트 리포지토리로 내보냅니다.
5장. 정책 및 PolicyGenTemplate 리소스를 사용하여 관리형 클러스터 구성
적용된 정책 CR(사용자 정의 리소스)은 사용자가 프로비저닝하는 관리 클러스터를 구성합니다. RHACM(Red Hat Advanced Cluster Management)에서 PolicyGenTemplate CR을 사용하여 적용된 정책 CR을 생성하는 방법을 사용자 지정할 수 있습니다.
5.1. PolicyGenTemplate CRD 정보
PolicyGenTemplate CRD(사용자 정의 리소스 정의)는 PolicyGen 정책 생성기에 클러스터 구성에 포함할 사용자 정의 리소스(CR), CR을 생성된 정책에 결합하는 방법, 해당 CR의 항목을 오버레이 콘텐츠로 업데이트해야 함을 알려줍니다.
다음 예제에서는 ztp-site-generate 참조 컨테이너에서 추출된 PolicyGenTemplate CR(common-du-ranGen.yaml)을 보여줍니다. common-du-ranGen.yaml 파일은 두 개의 RHACM(Red Hat Advanced Cluster Management) 정책을 정의합니다. 경찰은 CR에서 policyName 의 각 고유 값에 대해 하나씩 구성 CR 컬렉션을 관리합니다. common-du-ranGen.yaml 은 bindingRules 섹션에 나열된 레이블을 기반으로 정책을 클러스터에 바인딩하는 단일 배치 바인딩 및 배치 규칙을 생성합니다.
예: PolicyGenTemplate CR - common-du-ranGen.yaml
- 1
Common: "true"는 이 레이블이 있는 모든 클러스터에 정책을 적용합니다.- 2
sourceFiles아래에 나열된 파일은 설치된 클러스터에 대한 Operator 정책을 생성합니다.- 3
OperatorHub.yaml은 연결이 끊긴 레지스트리에 대한 OperatorHub를 구성합니다.- 4
DefaultCatsrc.yaml은 연결이 끊긴 레지스트리의 카탈로그 소스를 구성합니다.- 5
PolicyName: "config-policy"는 Operator 서브스크립션을 구성합니다.OperatorHubCR은 기본값을 비활성화하고 이 CR은 연결이 끊긴 레지스트리를 가리키는CatalogSourceCR로redhat-operators를 대체합니다.
PolicyGenTemplate CR은 포함된 CR 수를 사용하여 구성할 수 있습니다. hub 클러스터에 다음 예제 CR을 적용하여 단일 CR을 포함하는 정책을 생성합니다.
소스 파일 PtpConfigSlave.yaml 을 예로 사용하여 파일은 PtpConfig CR을 정의합니다. PtpConfigSlave 예제에 대해 생성된 정책의 이름은 group-du-sno-config-policy 입니다. 생성된 group-du-sno-config-policy 에 정의된 PtpConfig CR의 이름은 du-ptp-slave 입니다. PtpConfigSlave.yaml 에 정의된 사양 은 소스 파일에 정의된 다른 사양 항목과 함께 du-ptp-slave 아래에 배치됩니다.
다음 예제에서는 group-du-sno-config-policy CR을 보여줍니다.
5.2. PolicyGenTemplate CR을 사용자 정의할 때 권장 사항
사이트 구성 PolicyGenTemplate CR(사용자 정의 리소스)을 사용자 정의할 때 다음과 같은 모범 사례를 고려하십시오.
-
필요한 만큼의 정책을 사용하십시오. 정책을 더 적게 사용하려면 더 적은 리소스가 필요합니다. 각 추가 정책은 허브 클러스터 및 배포된 관리 클러스터에 대한 오버헤드를 생성합니다. CR은
PolicyGenTemplateCR의policyName필드를 기반으로 정책에 결합됩니다.policyName에 동일한 값이 있는 동일한PolicyGenTemplate의 CR은 단일 정책으로 관리됩니다. -
연결이 끊긴 환경에서는 모든 Operator가 포함된 단일 인덱스로 레지스트리를 구성하여 모든 Operator에 대해 단일 카탈로그 소스를 사용합니다. 관리 클러스터의 각 추가
CatalogSourceCR은 CPU 사용량을 늘립니다. -
MachineConfigCR은 설치 중에 적용되도록SiteConfigCR에서extraManifests로 포함되어야 합니다. 이를 통해 클러스터가 애플리케이션을 배포할 준비가 될 때까지 걸리는 전체 시간을 줄일 수 있습니다. -
PolicyGenTemplates는 원하는 버전을 명시적으로 식별하도록 channel 필드를 재정의해야 합니다. 이렇게 하면 업그레이드 중에 소스 CR의 변경이 생성된 서브스크립션을 업데이트하지 않습니다.
허브 클러스터에서 많은 수의 음성 클러스터를 관리할 때 정책 수를 최소화하여 리소스 소비를 줄입니다.
여러 구성 CR을 단일 또는 제한된 정책으로 그룹화하는 것이 허브 클러스터의 전체 정책 수를 줄이는 한 가지 방법입니다. 사이트 구성을 관리하기 위한 공통, 그룹 및 사이트 계층 구조를 사용하는 경우 사이트별 구성을 단일 정책으로 결합하는 것이 특히 중요합니다.
5.3. RAN 배포를 위한 PolicyGenTemplate CR
PBT( PolicyGenTemplate ) 사용자 정의 리소스(CR)를 사용하여ZTP( GitOps Zero Touch Provisioning) 파이프라인을 사용하여 클러스터에 적용되는 구성을 사용자 지정합니다. PGT CR을 사용하면 클러스터의 구성 CR 세트를 관리하는 하나 이상의 정책을 생성할 수 있습니다. PGT는 관리되는 CR 세트를 식별하고, 정책에 번들로 연결하며, 해당 CR을 래핑하는 정책을 구축하고, 라벨 바인딩 규칙을 사용하여 정책을 클러스터와 연결합니다.
GitOps ZTP 컨테이너에서 얻은 참조 구성은 클러스터가 RAN(Radio Access Network) 분산 단위(DU) 애플리케이션의 엄격한 성능 및 리소스 사용률 제약 조건을 지원할 수 있도록 중요한 기능 및 노드 튜닝 설정 세트를 제공하도록 설계되었습니다. 기준 구성의 변경 사항 또는 누락은 기능 가용성, 성능 및 리소스 사용률에 영향을 미칠 수 있습니다. 참조 PolicyGenTemplate CR을 기준으로 사용하여 특정 사이트 요구 사항에 맞는 구성 파일의 계층 구조를 생성합니다.
RAN DU 클러스터 구성에 정의된 기본 PolicyGenTemplate CR은 GitOps ZTP ztp-site-generate 컨테이너에서 추출할 수 있습니다. 자세한 내용은 " GitOps ZTP 사이트 구성 리포지토리 준비"를 참조하십시오.
PolicyGenTemplate CR은 ./out/argocd/example/policygentemplates 폴더에서 확인할 수 있습니다. 참조 아키텍처에는 공통, 그룹 및 사이트별 구성 CR이 있습니다. 각 PolicyGenTemplate CR은 ./out/source-crs 폴더에 있는 다른 CR을 나타냅니다.
RAN 클러스터 구성과 관련된 PolicyGenTemplate CR은 다음과 같습니다. 단일 노드, 3-노드 컴팩트 및 표준 클러스터 구성의 차이점을 고려하여 PolicyGenTemplate CR 그룹에 변형이 제공됩니다. 마찬가지로 단일 노드 클러스터 및 다중 노드(콤팩트 또는 표준) 클러스터에 대해 사이트별 구성 변형이 제공됩니다. 배포와 관련된 그룹 및 사이트별 구성 변형을 사용합니다.
| PolicyGenTemplate CR | 설명 |
|---|---|
|
| 다중 노드 클러스터에 적용되는 CR 세트를 포함합니다. 이러한 CR은 RAN 설치에 일반적인 SR-IOV 기능을 구성합니다. |
|
| 단일 노드 OpenShift 클러스터에 적용되는 CR 세트를 포함합니다. 이러한 CR은 RAN 설치에 일반적인 SR-IOV 기능을 구성합니다. |
|
| 모든 클러스터에 적용되는 공통 RAN CR 세트를 포함합니다. 이러한 CR은 RAN 및 기본 클러스터 튜닝에 일반적인 클러스터 기능을 제공하는 Operator 세트에 서브스크립션합니다. |
|
| 3-노드 클러스터에 대한 RAN 정책만 포함합니다. |
|
| 단일 노드 클러스터에 대한 RAN 정책만 포함합니다. |
|
| 표준 세 개의 컨트롤 플레인 클러스터에 대한 RAN 정책을 포함합니다. |
|
|
3-노드 클러스터에 필요한 다양한 정책을 생성하는 데 사용되는 |
|
|
표준 클러스터에 필요한 다양한 정책을 생성하는 데 사용되는 |
|
|
단일 노드 OpenShift 클러스터에 필요한 다양한 정책을 생성하는 데 사용되는 |
5.4. PolicyGenTemplate CR을 사용하여 관리 클러스터 사용자 정의
다음 절차에 따라 ZTP(ZTP) 파이프라인을 사용하여 프로비저닝하는 관리 클러스터에 적용할 수 있는 정책을 사용자 지정할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다. - 필요한 설치 및 정책 CR을 생성하도록 허브 클러스터를 구성했습니다.
- 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성하셨습니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 Argo CD 애플리케이션의 소스 리포지토리로 정의해야 합니다.
프로세스
사이트별 구성 CR에 대한
PolicyGenTemplateCR을 생성합니다.-
out/argocd/example/policygentemplates폴더에서 CR에 대한 적절한 예를 선택합니다(예:example-sno-site.yaml또는example-multinode-site.yaml). 예제 파일의
bindingRules필드를 siteConfigCR에 포함된 사이트별 레이블과 일치하도록 변경합니다. 예제SiteConfig파일에서 사이트별 레이블은sites: example-sno입니다.참고PolicyGenTemplatebindingRules필드에 정의된 라벨이 관련 관리 클러스터 siteConfigCR에 정의된 라벨에 해당하는지 확인합니다.- 예제 파일의 콘텐츠를 원하는 구성과 일치하도록 변경합니다.
-
선택 사항: 전체 클러스터에 적용되는 일반적인 구성 CR에 대한
PolicyGenTemplateCR을 생성합니다.-
out/argocd/example/policygentemplates폴더에서 CR에 대한 적절한 예를 선택합니다(예:common-ranGen.yaml). - 예제 파일의 콘텐츠를 원하는 구성과 일치하도록 변경합니다.
-
선택 사항: 플릿의 특정 클러스터 그룹에 적용되는 모든 그룹 구성 CR에 대해
PolicyGenTemplateCR을 생성합니다.overlaid 사양 파일의 내용이 원하는 최종 상태와 일치하는지 확인합니다. 참조로 out/source-crs 디렉터리에는 PolicyGenTemplate 템플릿에서 포함할 수 있는 source-crs의 전체 목록이 포함되어 있습니다.
참고클러스터의 특정 요구 사항에 따라 클러스터 유형당 단일 그룹 정책이 필요할 수 있습니다. 특히 예제 그룹 정책에는 각각 동일한 하드웨어 구성으로 구성된 클러스터 집합에서만 공유할 수 있는 단일 PerformancePolicy.yaml 파일이 있습니다.
-
out/argocd/example/policygentemplates폴더에서 CR에 대한 적절한 예를 선택합니다(예:group-du-sno-ranGen.yaml). - 예제 파일의 콘텐츠를 원하는 구성과 일치하도록 변경합니다.
-
-
선택 사항: 배포된 클러스터의 GitOps ZTP 설치 및 구성이 완료되면 정책
PolicyGenTemplateCR을 생성합니다. 자세한 내용은 "검토 확인 정보 정책 생성"을 참조하십시오. example
out/argocd/example/policygentemplates/ns.yaml파일과 유사한 YAML 파일에서 모든 정책 네임스페이스를 정의합니다.중요PolicyGenTemplateCR과 동일한 파일에NamespaceCR을 포함하지 마십시오.-
out/argocd/example/policygentemplates/에 표시된 예제와 유사하게kustomization.yamlPolicyGenTemplateCR 및NamespaceCR을 generators 섹션의 kustomization.yaml 파일에 추가합니다. Git 리포지토리에서
PolicyGenTemplateCR,NamespaceCR 및 관련kustomization.yaml파일을 커밋하고 변경 사항을 내보냅니다.ArgoCD 파이프라인은 변경 사항을 감지하고 관리 클러스터 배포를 시작합니다. 변경 사항을
SiteConfigCR 및PolicyGenTemplateCR에 동시에 푸시할 수 있습니다.
5.5. 관리형 클러스터 정책 배포 진행 상황 모니터링
ArgoCD 파이프라인은 Git의 PolicyGenTemplate CR을 사용하여 RHACM 정책을 생성한 다음 hub 클러스터에 동기화합니다. 지원 서비스가 관리형 클러스터에 OpenShift Container Platform을 설치한 후 관리 클러스터 정책 동기화의 진행 상황을 모니터링할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
Topology Aware Lifecycle Manager(TALM)는 클러스터에 바인딩된 구성 정책을 적용합니다.
클러스터 설치가 완료되고 클러스터가
Ready가 되면ran.openshift.io/ztp-deploy-ECDHE 주석에의해 정의된 정렬된 정책 목록과 함께 이 클러스터에 해당하는ClusterGroupUpgradeCR이 TALM에 의해 자동으로 생성됩니다. 클러스터의 정책은ClusterGroupUpgradeCR에 나열된 순서대로 적용됩니다.다음 명령을 사용하여 구성 정책 조정의 고급 진행 상황을 모니터링할 수 있습니다.
export CLUSTER=<clusterName>
$ export CLUSTER=<clusterName>Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc get clustergroupupgrades -n ztp-install $CLUSTER -o jsonpath='{.status.conditions[-1:]}' | jq$ oc get clustergroupupgrades -n ztp-install $CLUSTER -o jsonpath='{.status.conditions[-1:]}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow RHACM 대시보드 또는 명령줄을 사용하여 자세한 클러스터 정책 규정 준수 상태를 모니터링할 수 있습니다.
oc를 사용하여 정책 규정 준수를 확인하려면 다음 명령을 실행합니다.oc get policies -n $CLUSTER
$ oc get policies -n $CLUSTERCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow RHACM 웹 콘솔에서 정책 상태를 확인하려면 다음 작업을 수행합니다.
- Governance → policies 찾기를 클릭합니다.
- 클러스터 정책을 클릭하여 상태를 확인합니다.
모든 클러스터 정책이 준수되면 클러스터의 GitOps ZTP 설치 및 구성이 완료됩니다. ztp-done 레이블이 클러스터에 추가되었습니다.
참조 구성에서 준수되는 최종 정책은 *-du-validator-policy 정책에 정의된 정책입니다. 클러스터 준수 시 이 정책은 모든 클러스터 구성, Operator 설치 및 Operator 구성이 완료되었는지 확인합니다.
5.6. 구성 정책 CR 생성 검증
정책 CR(사용자 정의 리소스)은 해당 리소스가 생성된 PolicyGenTemplate 과 동일한 네임스페이스에 생성됩니다. 동일한 문제 해결 흐름은 다음 명령을 사용하여 표시된 것처럼 ztp-common,ztp-group 또는 ztp-site 기반 여부에 관계없이 PolicyGenTemplate 에서 생성된 모든 정책 CR에 적용됩니다.
export NS=<namespace>
$ export NS=<namespace>oc get policy -n $NS
$ oc get policy -n $NS정책 래핑된 CR의 예상 세트가 표시되어야 합니다.
정책 동기화에 실패한 경우 다음 문제 해결 단계를 사용하십시오.
프로세스
정책에 대한 자세한 정보를 표시하려면 다음 명령을 실행합니다.
oc describe -n openshift-gitops application policies
$ oc describe -n openshift-gitops application policiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Status: Conditions:를 확인하여 오류 로그를 표시합니다. 예를 들어 잘못된sourceFile CryostatfileName:을 설정하면 다음과 같은 오류가 생성됩니다.Status: Conditions: Last Transition Time: 2021-11-26T17:21:39Z Message: rpc error: code = Unknown desc = `kustomize build /tmp/https___git.com/ran-sites/policies/ --enable-alpha-plugins` failed exit status 1: 2021/11/26 17:21:40 Error could not find test.yaml under source-crs/: no such file or directory Error: failure in plugin configured via /tmp/kust-plugin-config-52463179; exit status 1: exit status 1 Type: ComparisonErrorStatus: Conditions: Last Transition Time: 2021-11-26T17:21:39Z Message: rpc error: code = Unknown desc = `kustomize build /tmp/https___git.com/ran-sites/policies/ --enable-alpha-plugins` failed exit status 1: 2021/11/26 17:21:40 Error could not find test.yaml under source-crs/: no such file or directory Error: failure in plugin configured via /tmp/kust-plugin-config-52463179; exit status 1: exit status 1 Type: ComparisonErrorCopy to Clipboard Copied! Toggle word wrap Toggle overflow 상태 확인: 동기화:.Status: Conditions:에 로그 오류가 있는 경우Status: Sync:showsUnknownorError:Copy to Clipboard Copied! Toggle word wrap Toggle overflow RHACM(Red Hat Advanced Cluster Management)에서
ManagedCluster오브젝트에 정책이 적용되는 것을 인식하면 정책 CR 오브젝트가 클러스터 네임스페이스에 적용됩니다. 정책이 클러스터 네임스페이스에 복사되었는지 확인합니다.oc get policy -n $CLUSTER
$ oc get policy -n $CLUSTERCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow RHACM은 적용 가능한 모든 정책을 클러스터 네임스페이스에 복사합니다. 복사된 정책 이름의 형식은 <
policyGenTemplate.Namespace>.<policyGenTemplate.Name>-<policyName>입니다.클러스터 네임스페이스에 복사되지 않은 모든 정책의 배치 규칙을 확인합니다. 해당 정책에 대한
PlacementRule의matchSelector는ManagedCluster오브젝트의 라벨과 일치해야 합니다.oc get placementrule -n $NS
$ oc get placementrule -n $NSCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 누락된 정책, 공통, 그룹 또는 사이트에 적절한
PlacementRule이름을 확인합니다.oc get placementrule -n $NS <placementRuleName> -o yaml
$ oc get placementrule -n $NS <placementRuleName> -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow - status-decisions에는 클러스터 이름이 포함되어야 합니다.
-
사양에 있는
matchSelector의 키-값 쌍은 관리 클러스터의 라벨과 일치해야 합니다.
다음 명령을 사용하여
ManagedCluster오브젝트에서 라벨을 확인합니다.oc get ManagedCluster $CLUSTER -o jsonpath='{.metadata.labels}' | jq$ oc get ManagedCluster $CLUSTER -o jsonpath='{.metadata.labels}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 호환되는 정책을 확인합니다.
oc get policy -n $CLUSTER
$ oc get policy -n $CLUSTERCopy to Clipboard Copied! Toggle word wrap Toggle overflow 네임스페이스
,OperatorGroup및서브스크립션정책이 호환되지만 Operator 구성 정책이 적용되지 않은 경우 Operator가 관리 클러스터에 설치되지 않을 수 있습니다. 이로 인해 CRD가 아직 spoke에 적용되지 않았기 때문에 Operator 구성 정책이 적용되지 않습니다.
5.7. 정책 조정 다시 시작
예를 들어 ClusterGroupUpgrade CR(사용자 정의 리소스)이 시간 초과된 경우 예기치 않은 규정 준수 문제가 발생하면 정책 조정을 다시 시작할 수 있습니다.
프로세스
ClusterGroupUpgradeCR은 관리 클러스터가Ready가 된 후 토폴로지 Aware Lifecycle Manager를 통해ztp-install네임스페이스에 생성됩니다.export CLUSTER=<clusterName>
$ export CLUSTER=<clusterName>Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc get clustergroupupgrades -n ztp-install $CLUSTER
$ oc get clustergroupupgrades -n ztp-install $CLUSTERCopy to Clipboard Copied! Toggle word wrap Toggle overflow 예기치 않은 문제가 있고 정책이 구성된 시간 내에 불만이 발생하지 않는 경우(기본값은 4시간)
ClusterGroupUpgradeCR의 상태에UpgradeTimedOut이 표시됩니다.oc get clustergroupupgrades -n ztp-install $CLUSTER -o jsonpath='{.status.conditions[?(@.type=="Ready")]}'$ oc get clustergroupupgrades -n ztp-install $CLUSTER -o jsonpath='{.status.conditions[?(@.type=="Ready")]}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow UpgradeTimedOut상태의ClusterGroupUpgradeCR은 시간마다 정책 조정을 자동으로 다시 시작합니다. 정책을 변경한 경우 기존ClusterGroupUpgradeCR을 삭제하여 즉시 재시도를 시작할 수 있습니다. 이렇게 하면 새ClusterGroupUpgradeCR의 자동 생성이 트리거되고 즉시 정책 조정이 시작됩니다.oc delete clustergroupupgrades -n ztp-install $CLUSTER
$ oc delete clustergroupupgrades -n ztp-install $CLUSTERCopy to Clipboard Copied! Toggle word wrap Toggle overflow
ClusterGroupUpgrade CR이 UpgradeCompleted 상태로 완료되고 관리 클러스터에 ztp-done 레이블이 적용된 경우 PolicyGenTemplate 을 사용하여 추가 구성을 변경할 수 있습니다. 기존 ClusterGroupUpgrade CR을 삭제하면 TALM에서 새 CR이 생성되지 않습니다.
이 시점에서 GitOps ZTP는 클러스터와의 상호 작용을 완료했으며 추가 상호 작용을 업데이트 및 정책 수정을 위해 생성된 새 ClusterGroupUpgrade CR로 처리해야 합니다.
5.8. 정책을 사용하여 적용된 관리 클러스터 CR 변경
정책을 통해 관리 클러스터에 배포된 CR(사용자 정의 리소스)에서 콘텐츠를 제거할 수 있습니다.
기본적으로 CR에서 생성된 모든 Policy CR에는 Policy GenTemplatecomplianceType 필드가 musthave 로 설정되어 있습니다. 관리 클러스터의 CR에 지정된 콘텐츠가 모두 있으므로 제거된 콘텐츠가 없는 musthave 정책은 계속 호환됩니다. 이 구성을 사용하면 CR에서 콘텐츠를 제거할 때 TALM은 정책에서 콘텐츠를 제거하지만 콘텐츠는 관리 클러스터의 CR에서 제거되지 않습니다.
mustonlyhave 에 complianceType 필드를 사용하면 정책에서 클러스터의 CR이 정책에 지정된 내용과 정확히 일치하도록 합니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다. - RHACM을 실행하는 허브 클러스터에서 관리 클러스터를 배포했습니다.
- hub 클러스터에 Topology Aware Lifecycle Manager를 설치했습니다.
프로세스
영향을 받는 CR에서 더 이상 필요하지 않은 콘텐츠를 제거합니다. 이 예에서는
disableDrain: false행이SriovOperatorConfigCR에서 제거되었습니다.CR 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 영향을 받는 정책의
complianceType을group-du-sno-ranGen.yaml파일에서mustonlyhave로 변경합니다.YAML의 예
# ... - fileName: SriovOperatorConfig.yaml policyName: "config-policy" complianceType: mustonlyhave # ...
# ... - fileName: SriovOperatorConfig.yaml policyName: "config-policy" complianceType: mustonlyhave # ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow ClusterGroupUpdatesCR을 생성하고 CR 변경 사항을 받아야 하는 클러스터를 지정합니다.ClusterGroupUpdates CR의 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
ClusterGroupUpgradeCR을 생성합니다.oc create -f cgu-remove.yaml
$ oc create -f cgu-remove.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 적절한 유지 관리 기간 동안 변경 사항을 적용할 준비가 되면 다음 명령을 실행하여
spec.enable필드의 값을true로 변경합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-remove \ --patch '{"spec":{"enable":true}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-remove \ --patch '{"spec":{"enable":true}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
다음 명령을 실행하여 정책의 상태를 확인합니다.
oc get <kind> <changed_cr_name>
$ oc get <kind> <changed_cr_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME REMEDIATION ACTION COMPLIANCE STATE AGE default cgu-ztp-group.group-du-sno-config-policy enforce 17m default ztp-group.group-du-sno-config-policy inform NonCompliant 15h
NAMESPACE NAME REMEDIATION ACTION COMPLIANCE STATE AGE default cgu-ztp-group.group-du-sno-config-policy enforce 17m default ztp-group.group-du-sno-config-policy inform NonCompliant 15hCopy to Clipboard Copied! Toggle word wrap Toggle overflow 정책의
COMPLIANCE STATE가Compliant인 경우 CR이 업데이트되고 원하지 않는 콘텐츠가 제거됨을 의미합니다.관리 클러스터에서 다음 명령을 실행하여 정책이 대상 클러스터에서 제거되었는지 확인합니다.
oc get <kind> <changed_cr_name>
$ oc get <kind> <changed_cr_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 결과가 없는 경우 관리 클러스터에서 CR이 제거됩니다.
5.9. GitOps ZTP 설치에 대해 수행됨 표시
GitOps ZTP(ZTP)는 클러스터의 GitOps ZTP 설치 상태를 확인하는 프로세스를 단순화합니다. GitOps ZTP 상태는 클러스터 설치, 클러스터 구성 및 GitOps ZTP의 세 단계로 이동합니다.
- 클러스터 설치 단계
-
클러스터 설치 단계는 ManagedCluster CR의
ManagedClusterJoined및ManagedClusterAvailableManagedClusterCR에 이러한 조건이 없거나 조건이False로 설정되어 있는 경우 클러스터는 여전히 설치 단계에 있습니다. 설치에 대한 자세한 내용은AgentClusterInstall및ClusterDeploymentCR에서 확인할 수 있습니다. 자세한 내용은 "Troubleshooting GitOps ZTP"를 참조하십시오. - 클러스터 구성 단계
-
클러스터 구성 단계는 클러스터의
ManagedClusterCR을 적용한ztp 실행라벨에 의해 표시됩니다. - GitOps ZTP 완료
GitOps ZTP 완료 단계에서 클러스터 설치 및 구성이 완료됩니다. 이는
ztp-running레이블을 제거하고ztp-done레이블을ManagedClusterCR에 추가하여 표시됩니다.ztp-done레이블은 구성이 적용되었으며 기준 DU 구성이 클러스터 튜닝을 완료했음을 보여줍니다.GitOps ZTP done 상태로의 전환은 RHACM(Red Hat Advanced Cluster Management) 검증 검증 정보 정책의 준수 상태에서 조건부입니다. 이 정책은 완료된 설치에 대한 기존 기준을 캡처하고 관리 클러스터의 GitOps ZTP 프로비저닝이 완료된 경우에만 규정 준수 상태로 이동하는지 확인합니다.
검증기 정보 정책은 클러스터 구성이 완전히 적용되고 Operator가 초기화를 완료하도록 합니다. 정책은 다음을 확인합니다.
-
대상
MachineConfigPool에는 예상되는 항목이 포함되어 있으며 업데이트가 완료되었습니다. 모든 노드를 사용할 수 있으며 성능이 저하되지 않습니다. -
SR-IOV Operator는
syncStatus: Succeeded가 있는 하나 이상의SriovNetworkNodeState에 표시된 대로 초기화를 완료했습니다. - PTP Operator 데몬 세트가 있습니다.
-
대상
6장. ZTP를 사용하여 단일 노드 OpenShift 클러스터 수동 설치
RHACM(Red Hat Advanced Cluster Management) 및 지원 서비스를 사용하여 관리형 단일 노드 OpenShift 클러스터를 배포할 수 있습니다.
여러 개의 관리 클러스터를 생성하는 경우 ZTP를 사용하여 멀리 엣지 사이트 배포에 설명된 site Config 방법을 사용하십시오.
대상 베어 메탈 호스트는 vDU 애플리케이션 워크로드에 대한 권장 클러스터 구성에 나열된 네트워킹, 펌웨어 및 하드웨어 요구 사항을 충족해야 합니다.
6.1. 수동으로 GitOps ZTP 설치 및 구성 CR 생성
ztp-site-generate 컨테이너의 생성기 진입점을 사용하여 SiteConfig 및 PolicyGenTemplate CR을 기반으로 클러스터에 대한 사이트 설치 및 구성 CR(사용자 정의 리소스)을 생성합니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
프로세스
다음 명령을 실행하여 출력 폴더를 생성합니다.
mkdir -p ./out
$ mkdir -p ./outCopy to Clipboard Copied! Toggle word wrap Toggle overflow ztp-site-generate컨테이너 이미지에서argocd디렉터리를 내보냅니다.podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 extract /home/ztp --tar | tar x -C ./out
$ podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 extract /home/ztp --tar | tar x -C ./outCopy to Clipboard Copied! Toggle word wrap Toggle overflow ./out디렉터리에는out/argocd/example/폴더에PolicyGenTemplate및SiteConfigCR이 있습니다.출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 사이트 설치 CR의 출력 폴더를 생성합니다.
mkdir -p ./site-install
$ mkdir -p ./site-installCopy to Clipboard Copied! Toggle word wrap Toggle overflow 설치할 클러스터 유형에 대한
SiteConfigCR 예제를 수정합니다.example-sno.yaml을site-1-sno.yaml에 복사하고 설치할 사이트 및 베어 메탈 호스트의 세부 정보와 일치하도록 CR을 수정합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고ztp-site-generate컨테이너의out/extra-manifest디렉터리에서 참조 CR 구성 파일을 추출하면extraManifests.searchPaths를 사용하여 해당 파일이 포함된 git 디렉터리의 경로를 포함할 수 있습니다. 그러면 GitOps ZTP 파이프라인에서 클러스터 설치 중에 해당 CR 파일을 적용할 수 있습니다.searchPaths디렉터리를 구성하면 GitOps ZTP 파이프라인에서 사이트를 설치하는 동안ztp-site-generate컨테이너에서 매니페스트를 가져오지 않습니다.다음 명령을 실행하여 수정된
SiteConfigCRsite-1-sno.yaml을 처리하여 0일 설치 CR을 생성합니다.podman run -it --rm -v `pwd`/out/argocd/example/siteconfig:/resources:Z -v `pwd`/site-install:/output:Z,U registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 generator install site-1-sno.yaml /output
$ podman run -it --rm -v `pwd`/out/argocd/example/siteconfig:/resources:Z -v `pwd`/site-install:/output:Z,U registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 generator install site-1-sno.yaml /outputCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 선택 사항:
-E옵션으로 참조SiteConfigCR을 처리하여 특정 클러스터 유형에 대한 Day 0MachineConfig설치 CR만 생성합니다. 예를 들어 다음 명령을 실행합니다.MachineConfigCR의 출력 폴더를 생성합니다.mkdir -p ./site-machineconfig
$ mkdir -p ./site-machineconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow MachineConfig설치 CR을 생성합니다.podman run -it --rm -v `pwd`/out/argocd/example/siteconfig:/resources:Z -v `pwd`/site-machineconfig:/output:Z,U registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 generator install -E site-1-sno.yaml /output
$ podman run -it --rm -v `pwd`/out/argocd/example/siteconfig:/resources:Z -v `pwd`/site-machineconfig:/output:Z,U registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 generator install -E site-1-sno.yaml /outputCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
site-machineconfig └── site-1-sno ├── site-1-sno_machineconfig_02-master-workload-partitioning.yaml ├── site-1-sno_machineconfig_predefined-extra-manifests-master.yaml └── site-1-sno_machineconfig_predefined-extra-manifests-worker.yamlsite-machineconfig └── site-1-sno ├── site-1-sno_machineconfig_02-master-workload-partitioning.yaml ├── site-1-sno_machineconfig_predefined-extra-manifests-master.yaml └── site-1-sno_machineconfig_predefined-extra-manifests-worker.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
이전 단계의
PolicyGenTemplateCR 참조를 사용하여 Day 2 구성 CR을 생성하고 내보냅니다. 다음 명령을 실행합니다.Day 2 CR의 출력 폴더를 생성합니다.
mkdir -p ./ref
$ mkdir -p ./refCopy to Clipboard Copied! Toggle word wrap Toggle overflow Day 2 구성 CR을 생성하고 내보냅니다.
podman run -it --rm -v `pwd`/out/argocd/example/policygentemplates:/resources:Z -v `pwd`/ref:/output:Z,U registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 generator config -N . /output
$ podman run -it --rm -v `pwd`/out/argocd/example/policygentemplates:/resources:Z -v `pwd`/ref:/output:Z,U registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15 generator config -N . /outputCopy to Clipboard Copied! Toggle word wrap Toggle overflow 이 명령은 단일 노드 OpenShift, 3-노드 클러스터,
./ref폴더에 표준 클러스터를 위한 예제 그룹 및 사이트별PolicyGenTemplateCR을 생성합니다.출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- 생성된 CR을 클러스터를 설치하는 데 사용하는 CR의 기반으로 사용합니다. "단일 관리 클러스터 설치"에 설명된 대로 hub 클러스터에 설치 CR을 적용합니다. 클러스터 설치가 완료된 후 구성 CR을 클러스터에 적용할 수 있습니다.
검증
노드가 배포된 후 사용자 정의 역할 및 라벨이 적용되는지 확인합니다.
oc describe node example-node.example.com
$ oc describe node example-node.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
출력 예
- 1
- 사용자 정의 레이블이 노드에 적용됩니다.
6.2. 관리형 베어 메탈 호스트 시크릿 생성
관리 베어 메탈 호스트에 필요한 Secret CR(사용자 정의 리소스)을 hub 클러스터에 추가합니다. BMC(Baseboard Management Controller)에 액세스하려면 GitOps ZTP(ZTP) 파이프라인의 시크릿과 지원되는 설치 프로그램 서비스에서 레지스트리에서 클러스터 설치 이미지를 가져오는 시크릿이 필요합니다.
보안은 site Config CR에서 이름으로 참조됩니다. 네임스페이스는 site Config 네임스페이스와 일치해야 합니다.
프로세스
OpenShift 및 모든 추가 기능 클러스터 Operator 설치에 필요한 호스트 BMC(Baseboard Management Controller)에 대한 인증 정보와 풀 시크릿을 포함하는 YAML 시크릿 파일을 생성합니다.
-
클러스터를 설치하는 데 사용하는
kustomization.yaml파일에example-sno-secret.yaml에 상대 경로를 추가합니다.
6.3. GitOps ZTP를 사용하여 수동 설치를 위한 Discovery ISO 커널 인수 구성
GitOps ZTP(ZTP) 워크플로는 관리형 베어 메탈 호스트에서 OpenShift Container Platform 설치 프로세스의 일부로 Discovery ISO를 사용합니다. InfraEnv 리소스를 편집하여 Discovery ISO에 대한 커널 인수를 지정할 수 있습니다. 이는 특정 환경 요구 사항이 있는 클러스터 설치에 유용합니다. 예를 들어 클러스터의 정적 네트워킹을 용이하게 하거나 설치 중에 루트 파일 시스템을 다운로드하기 전에 DHCP 주소를 수신하도록 Discovery ISO에 rd.net.timeout.carrier 커널 인수를 구성합니다.
OpenShift Container Platform 4.15에서는 커널 인수만 추가할 수 있습니다. 커널 인수를 교체하거나 삭제할 수 없습니다.
사전 요구 사항
- OpenShift CLI(oc)가 설치되어 있습니다.
- cluster-admin 권한이 있는 사용자로 hub 클러스터에 로그인했습니다.
- 설치 및 구성 사용자 정의 리소스(CR)를 수동으로 생성했습니다.
프로세스
-
InfraEnvCR에서spec.kernelArguments사양을 편집하여 커널 인수를 구성합니다.
SiteConfig CR은 InfraEnv 리소스를 day-0 설치 CR의 일부로 생성합니다.
검증
커널 인수가 적용되었는지 확인하려면 검색 이미지에서 OpenShift Container Platform을 설치할 준비가 되었는지 확인한 후 설치 프로세스가 시작되기 전에 대상 호스트에 SSH를 수행할 수 있습니다. 이때 /proc/cmdline 파일에서 Discovery ISO의 커널 인수를 볼 수 있습니다.
대상 호스트를 사용하여 SSH 세션을 시작합니다.
ssh -i /path/to/privatekey core@<host_name>
$ ssh -i /path/to/privatekey core@<host_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 시스템의 커널 인수를 확인합니다.
cat /proc/cmdline
$ cat /proc/cmdlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.4. 단일 관리형 클러스터 설치
지원 서비스 및 RHACM(Red Hat Advanced Cluster Management)을 사용하여 단일 관리형 클러스터를 수동으로 배포할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 허브 클러스터에 로그인했습니다. -
BMC(Baseboard Management Controller)
Secret및 image pull-secretSecret사용자 정의 리소스(CR)를 생성했습니다. 자세한 내용은 "관리된 베어 메탈 호스트 시크릿 생성"을 참조하십시오. - 대상 베어 메탈 호스트는 관리 클러스터의 네트워킹 및 하드웨어 요구 사항을 충족합니다.
프로세스
배포할 각 특정 클러스터 버전에 대한
ClusterImageSet을 만듭니다(예:clusterImageSet-4.15.yaml).ClusterImageSet의 형식은 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow clusterImageSetCR을 적용합니다.oc apply -f clusterImageSet-4.15.yaml
$ oc apply -f clusterImageSet-4.15.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow cluster-namespace.yaml파일에NamespaceCR을 생성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
네임스페이스CR을 적용합니다.oc apply -f cluster-namespace.yaml
$ oc apply -f cluster-namespace.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow ztp-site-generate컨테이너에서 추출하고 요구 사항을 충족하도록 사용자 지정된 생성된 day-0 CR을 적용합니다.oc apply -R ./site-install/site-sno-1
$ oc apply -R ./site-install/site-sno-1Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5. 관리 클러스터 설치 상태 모니터링
클러스터 상태를 확인하여 클러스터 프로비저닝에 성공했는지 확인합니다.
사전 요구 사항
-
모든 사용자 지정 리소스가 구성 및 프로비저닝되었으며
Agent사용자 지정 리소스는 관리 클러스터의 허브에 생성됩니다.
프로세스
관리 클러스터의 상태를 확인합니다.
oc get managedcluster
$ oc get managedclusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow true는 관리 클러스터가 준비되었음을 나타냅니다.에이전트 상태를 확인합니다.
oc get agent -n <cluster_name>
$ oc get agent -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow describe명령을 사용하여 에이전트의 상태에 대한 심층적인 설명을 제공합니다. 알 수 있는 상태에는BackendError,InputError,ValidationsFailing,InstallationFailed,AgentIConnected 가포함됩니다. 이러한 상태는Agent및AgentClusterInstall사용자 정의 리소스와 관련이 있습니다.oc describe agent -n <cluster_name>
$ oc describe agent -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 클러스터 프로비저닝 상태를 확인합니다.
oc get agentclusterinstall -n <cluster_name>
$ oc get agentclusterinstall -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow describe명령을 사용하여 클러스터 프로비저닝 상태에 대한 심층적인 설명을 제공합니다.oc describe agentclusterinstall -n <cluster_name>
$ oc describe agentclusterinstall -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터의 애드온 서비스의 상태를 확인합니다.
oc get managedclusteraddon -n <cluster_name>
$ oc get managedclusteraddon -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터에 대한
kubeconfig파일의 인증 정보를 검색합니다.oc get secret -n <cluster_name> <cluster_name>-admin-kubeconfig -o jsonpath={.data.kubeconfig} | base64 -d > <directory>/<cluster_name>-kubeconfig$ oc get secret -n <cluster_name> <cluster_name>-admin-kubeconfig -o jsonpath={.data.kubeconfig} | base64 -d > <directory>/<cluster_name>-kubeconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.6. 관리 클러스터 문제 해결
관리 클러스터에서 발생할 수 있는 설치 문제를 진단하려면 다음 절차를 사용하십시오.
프로세스
관리 클러스터의 상태를 확인합니다.
oc get managedcluster
$ oc get managedclusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE SNO-cluster true True True 2d19h
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE SNO-cluster true True True 2d19hCopy to Clipboard Copied! Toggle word wrap Toggle overflow AVAILABLE열의 상태가True이면 관리 클러스터가 허브에 의해 관리되고 있습니다.AVAILABLE열의 상태가Unknown인 경우 관리 클러스터는 허브에 의해 관리되지 않습니다. 자세한 정보를 얻으려면 다음 단계를 계속 확인하십시오.AgentClusterInstall설치 상태를 확인합니다.oc get clusterdeployment -n <cluster_name>
$ oc get clusterdeployment -n <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME PLATFORM REGION CLUSTERTYPE INSTALLED INFRAID VERSION POWERSTATE AGE Sno0026 agent-baremetal false Initialized 2d14h
NAME PLATFORM REGION CLUSTERTYPE INSTALLED INFRAID VERSION POWERSTATE AGE Sno0026 agent-baremetal false Initialized 2d14hCopy to Clipboard Copied! Toggle word wrap Toggle overflow INSTALLED열의 상태가false이면 설치에 실패했습니다.설치에 실패한 경우 다음 명령을 입력하여
AgentClusterInstall리소스의 상태를 검토합니다.oc describe agentclusterinstall -n <cluster_name> <cluster_name>
$ oc describe agentclusterinstall -n <cluster_name> <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 오류를 해결하고 클러스터를 재설정합니다.
클러스터의 관리 클러스터 리소스를 제거합니다.
oc delete managedcluster <cluster_name>
$ oc delete managedcluster <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 클러스터의 네임스페이스를 제거합니다.
oc delete namespace <cluster_name>
$ oc delete namespace <cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 이렇게 하면 이 클러스터에 대해 생성된 네임스페이스 범위 사용자 정의 리소스가 모두 삭제됩니다. 계속하기 전에
ManagedClusterCR 삭제가 완료될 때까지 기다려야 합니다.- 관리 클러스터에 대한 사용자 정의 리소스를 다시 생성합니다.
6.7. RHACM 생성 클러스터 설치 CR 참조
RHACM(Red Hat Advanced Cluster Management)은 각 사이트에 site Config CR을 사용하여 생성하는 특정 설치 사용자 정의 리소스(CR) 세트가 있는 단일 노드 클러스터, 3-노드 클러스터 및 표준 클러스터에 OpenShift Container Platform 배포를 지원합니다.
관리되는 모든 클러스터에는 자체 네임스페이스가 있으며 ManagedCluster 및 ClusterImageSet 을 제외한 모든 설치 CR은 해당 네임스페이스에 있습니다. ManagedCluster 및 ClusterImageSet 은 네임스페이스 범위가 아닌 클러스터 범위입니다. 네임스페이스 및 CR 이름은 클러스터 이름과 일치합니다.
다음 표에는 구성된 SiteConfig CR을 사용하여 클러스터를 설치할 때 RHACM 지원 서비스에서 자동으로 적용하는 설치 CR이 나열되어 있습니다.
| CR | 설명 | 사용법 |
|---|---|---|
|
| 대상 베어 메탈 호스트의 BMC(Baseboard Management Controller)에 대한 연결 정보를 포함합니다. | Redfish 프로토콜을 사용하여 대상 서버에서 검색 이미지를 로드하고 시작할 BMC에 대한 액세스를 제공합니다. |
|
| 대상 베어 메탈 호스트에 OpenShift Container Platform을 설치하기 위한 정보가 포함되어 있습니다. |
|
|
|
네트워킹 및 컨트롤 플레인 노드 수와 같은 관리형 클러스터 구성의 세부 정보를 지정합니다. 설치가 완료되면 클러스터 | 관리되는 클러스터 구성 정보를 지정하고 클러스터를 설치하는 동안 상태를 제공합니다. |
|
|
사용할 |
|
|
|
| 관리 클러스터의 Kube API 서버의 고정 IP 주소를 설정합니다. |
|
| 대상 베어 메탈 호스트에 대한 하드웨어 정보를 포함합니다. | 대상 시스템의 검색 이미지가 부팅될 때 허브에서 자동으로 생성됩니다. |
|
| 허브에서 클러스터를 관리하는 경우 이를 가져오고 알고 있어야 합니다. 이 Kubernetes 오브젝트는 해당 인터페이스를 제공합니다. | 허브는 이 리소스를 사용하여 관리 클러스터의 상태를 관리하고 표시합니다. |
|
|
|
|
|
|
허브에 존재하는 |
|
|
|
|
|
|
| 리포지토리 및 이미지 이름과 같은 OpenShift Container Platform 이미지 정보가 포함되어 있습니다. | OpenShift Container Platform 이미지를 제공하기 위해 리소스에 전달됩니다. |
7장. vDU 애플리케이션 워크로드에 권장되는 단일 노드 OpenShift 클러스터 구성
다음 참조 정보를 사용하여 클러스터에 가상 분산 단위(vDU) 애플리케이션을 배포하는 데 필요한 단일 노드 OpenShift 구성을 파악합니다. 구성에는 고성능 워크로드를 위한 클러스터 최적화, 워크로드 파티셔닝 활성화, 설치 후 필요한 재부팅 횟수 최소화가 포함됩니다.
7.1. OpenShift Container Platform에서 짧은 대기 시간 애플리케이션 실행
OpenShift Container Platform을 사용하면 여러 기술 및 특수 하드웨어 장치를 사용하여 COTS(Commer off-the-shelf) 하드웨어에서 실행되는 애플리케이션에 대해 대기 시간이 짧은 처리를 수행할 수 있습니다.
- RHCOS의 실시간 커널
- 높은 수준의 프로세스 결정으로 워크로드가 처리되도록 합니다.
- CPU 격리
- CPU 스케줄링 지연을 방지하고 CPU 용량을 일관되게 사용할 수 있도록 합니다.
- NUMA 인식 토폴로지 관리
- 메모리 및 대규모 페이지를 CPU 및 PCI 장치와 조정하여 보장된 컨테이너 메모리 및 대규모 페이지를 NUMA(Non-Uniform Memory Access) 노드에 고정합니다. 모든 QoS(Quality of Service) 클래스에 대한 Pod 리소스는 동일한 NUMA 노드에 남아 있습니다. 이렇게 하면 대기 시간이 줄어들고 노드의 성능이 향상됩니다.
- 대규모 페이지 메모리 관리
- 대규모 페이지 크기를 사용하면 페이지 테이블에 액세스하는 데 필요한 시스템 리소스의 양을 줄임으로써 시스템 성능이 향상됩니다.
- PTP를 사용한 정확한 타이밍 동기화
- 네트워크의 노드 간 동기화를 통해 마이크로초 이하의 정확도를 사용할 수 있습니다.
7.2. vDU 애플리케이션 워크로드에 대한 권장 클러스터 호스트 요구 사항
vDU 애플리케이션 워크로드를 실행하려면 OpenShift Container Platform 서비스 및 프로덕션 워크로드를 실행하기에 충분한 리소스가 있는 베어 메탈 호스트가 필요합니다.
| 프로필 | vCPU | 메모리 | 스토리지 |
|---|---|---|---|
| 최소 | 4에서 8 vCPU | 32GB RAM | 120GB |
하나의 vCPU는 하나의 물리적 코어와 동일합니다. 그러나 동시 멀티스레딩(SMT) 또는 Hyper-Threading을 활성화하면 다음 공식을 사용하여 하나의 물리적 코어를 나타내는 vCPU 수를 계산합니다.
- (threads per core × cores) × sockets = vCPUs
가상 미디어를 사용하여 부팅할 때 서버에 BMC(Baseboard Management Controller)가 있어야 합니다.
7.3. 짧은 대기 시간과 고성능을 위해 호스트 펌웨어 구성
호스트를 프로비저닝하기 전에 베어 메탈 호스트에 펌웨어를 구성해야 합니다. 펌웨어 구성은 특정 하드웨어 및 설치의 특정 요구 사항에 따라 다릅니다.
프로세스
-
UEFI/BIOS 부팅 모드를
UEFI로 설정합니다. - 호스트 부팅 순서에서 먼저 하드 드라이브를 설정합니다.
하드웨어에 대한 특정 펌웨어 구성을 적용합니다. 다음 표에서는 Intel FlexRAN 4G 및 5G 베이스band CryostatY 참조 설계를 기반으로 하는 Intel Xeon Skylake 또는 Intel Cascade Lake 서버의 대표적인 펌웨어 구성에 대해 설명합니다.
중요정확한 펌웨어 구성은 특정 하드웨어 및 네트워크 요구 사항에 따라 다릅니다. 다음 샘플 구성은 예시적인 목적으로만 사용됩니다.
Expand 표 7.2. Intel Xeon Skylake 또는 Cascade Lake 서버의 펌웨어 구성 샘플 펌웨어 설정 설정 CPU 전원 및 성능 정책
성능
코어 빈도 확장 해제
비활성화됨
성능 P-limit
비활성화됨
향상된 Intel SpeedStep ® Tech
활성화됨
Intel Configurable TDP
활성화됨
구성 가능한 TDP 수준
수준 2
Intel® Turbo Boost Technology
활성화됨
에너지 효율성:
비활성화됨
하드웨어 P-States
비활성화됨
패키지 C-State
C0/C1 상태
C1E
비활성화됨
프로세서 C6
비활성화됨
호스트의 펌웨어에서 글로벌 SR-IOV 및 VT-d 설정을 활성화합니다. 이러한 설정은 베어 메탈 환경과 관련이 있습니다.
7.4. 관리되는 클러스터 네트워크에 대한 연결 사전 요구 사항
GitOps ZTP(ZTP) 파이프라인을 사용하여 관리 클러스터를 설치하고 프로비저닝하려면 관리 클러스터 호스트가 다음 네트워킹 사전 요구 사항을 충족해야 합니다.
- hub 클러스터의 GitOps ZTP 컨테이너와 대상 베어 메탈 호스트의 BMC(Baseboard Management Controller) 간에 양방향 연결이 있어야 합니다.
관리 클러스터는 허브 호스트 이름 및
*.apps호스트 이름의 API 호스트 이름을 확인하고 연결할 수 있어야 합니다. 다음은 hub 및*.apps호스트 이름의 API 호스트 이름의 예입니다.-
api.hub-cluster.internal.domain.com -
console-openshift-console.apps.hub-cluster.internal.domain.com
-
허브 클러스터는 관리형 클러스터의 API 및
*.apps호스트 이름을 확인하고 연결할 수 있어야 합니다. 다음은 관리 클러스터의 API 호스트 이름과*.apps호스트 이름의 예입니다.-
api.sno-managed-cluster-1.internal.domain.com -
console-openshift-console.apps.sno-managed-cluster-1.internal.domain.com
-
7.5. GitOps ZTP를 사용하여 단일 노드 OpenShift에서 워크로드 파티셔닝
워크로드 파티셔닝은 예약된 수의 호스트 CPU에서 실행되도록 OpenShift Container Platform 서비스, 클러스터 관리 워크로드 및 인프라 Pod를 구성합니다.
GitOps ZTP(ZTP)를 사용하여 워크로드 파티셔닝을 구성하려면 클러스터를 설치하는 데 사용하는 SiteConfig CR(사용자 정의 리소스)에서 cpu CryostatingMode 필드를 구성하고 호스트에 분리 및 예약된 CPU를 구성하는 PerformanceProfile CR을 적용합니다.
SiteConfig CR을 구성하면 클러스터 설치 시 워크로드 파티셔닝을 활성화하고 PerformanceProfile CR을 적용하면 예약 및 분리된 세트에 대한 CPU의 특정 할당이 구성됩니다. 이 두 단계는 클러스터 프로비저닝 중에 서로 다른 지점에서 수행됩니다.
SiteConfig CR에서 cpu CryostatingMode 필드를 사용하여 워크로드 파티셔닝을 구성하는 것은 OpenShift Container Platform 4.13의 기술 프리뷰 기능입니다.
또는 SiteConfig 사용자 정의 리소스(CR)의 cpuset 필드와 PolicyGenTemplate CR 그룹의 reserved 필드를 사용하여 클러스터 관리 CPU 리소스를 지정할 수 있습니다. GitOps ZTP 파이프라인은 이러한 값을 사용하여 워크로드 파티셔닝 MachineConfig CR(cpuset) 및 단일 노드 OpenShift 클러스터를 구성하는 PerformanceProfile CR(reserved)의 필수 필드를 채웁니다. 이 방법은 OpenShift Container Platform 4.14의 일반 가용성 기능입니다.
워크로드 파티셔닝 구성은 OpenShift Container Platform 인프라 Pod를 예약된 CPU 세트에 고정합니다. systemd, CRI-O 및 kubelet과 같은 플랫폼 서비스는 예약된 CPU 세트에서 실행됩니다. 격리된 CPU 세트는 컨테이너 워크로드에 독점적으로 할당됩니다. CPU를 격리하면 동일한 노드에서 실행되는 다른 애플리케이션의 경합 없이 워크로드가 지정된 CPU에 대한 액세스를 보장할 수 있습니다. 분리되지 않은 모든 CPU를 예약해야 합니다.
예약 및 분리된 CPU 세트가 서로 겹치지 않도록 합니다.
7.6. 권장되는 클러스터 설치 매니페스트
ZTP 파이프라인은 클러스터 설치 중에 다음 사용자 정의 리소스(CR)를 적용합니다. 이러한 구성 CR을 사용하면 클러스터가 vDU 애플리케이션을 실행하는 데 필요한 기능 및 성능 요구 사항을 충족할 수 있습니다.
클러스터 배포에 GitOps ZTP 플러그인 및 SiteConfig CR을 사용하는 경우 다음 MachineConfig CR이 기본적으로 포함됩니다.
SiteConfig 추가Manifests 필터를 사용하여 기본적으로 포함된 CR을 변경합니다. 자세한 내용은 SiteConfig CR을 사용한 고급 관리 클러스터 구성 을 참조하십시오.
7.6.1. 워크로드 파티셔닝
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 워크로드 파티셔닝이 필요합니다. 이렇게 하면 플랫폼 서비스를 실행할 수 있는 코어가 제한되고 애플리케이션 페이로드의 CPU 코어를 최대화할 수 있습니다.
워크로드 파티셔닝은 클러스터 설치 중에만 활성화할 수 있습니다. 워크로드 파티션 설치 후 비활성화할 수 없습니다. 그러나 PerformanceProfile CR을 통해 분리된 세트 및 예약된 세트에 할당된 CPU 세트를 변경할 수 있습니다. CPU 설정을 변경하면 노드가 재부팅됩니다.
워크로드 파티셔닝을 활성화하기 위해 cpu CryostatingMode 를 사용하여 전환할 때 클러스터를 프로비저닝하는 데 사용하는 /extra-manifest 폴더에서 워크로드 파티션 MachineConfig CR을 제거합니다.
워크로드 파티셔닝에 권장되는 site Config CR 구성
- 1
cpu CryostatingMode필드를AllNodes로 설정하여 클러스터의 모든 노드에 대한 워크로드 파티셔닝을 구성합니다.
검증
애플리케이션 및 클러스터 시스템 CPU 고정이 올바른지 확인합니다. 다음 명령을 실행합니다.
관리 클러스터에 대한 원격 쉘 프롬프트를 엽니다.
oc debug node/example-sno-1
$ oc debug node/example-sno-1Copy to Clipboard Copied! Toggle word wrap Toggle overflow OpenShift 인프라 애플리케이션 CPU 고정이 올바른지 확인합니다.
pgrep ovn | while read i; do taskset -cp $i; done
sh-4.4# pgrep ovn | while read i; do taskset -cp $i; doneCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 시스템 애플리케이션 CPU 고정이 올바른지 확인합니다.
pgrep systemd | while read i; do taskset -cp $i; done
sh-4.4# pgrep systemd | while read i; do taskset -cp $i; doneCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
pid 1's current affinity list: 0-1,52-53 pid 938's current affinity list: 0-1,52-53 pid 962's current affinity list: 0-1,52-53 pid 1197's current affinity list: 0-1,52-53
pid 1's current affinity list: 0-1,52-53 pid 938's current affinity list: 0-1,52-53 pid 962's current affinity list: 0-1,52-53 pid 1197's current affinity list: 0-1,52-53Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.6.2. 플랫폼 관리 공간 감소
플랫폼의 전체 관리 공간을 줄이기 위해 MachineConfig CR(사용자 정의 리소스)을 호스트 운영 체제와 별도로 새 네임스페이스에 모든 Kubernetes별 마운트 지점을 배치해야 합니다. 다음 base64로 인코딩된 예제 MachineConfig CR은 이 구성을 보여줍니다.
권장 컨테이너 마운트 네임스페이스 구성 (01-container-mount-ns-and-kubelet-conf-master.yaml)
7.6.3. SCTP
SCTP(스트림 제어 전송 프로토콜)는 RAN 애플리케이션에서 사용되는 주요 프로토콜입니다. 이 MachineConfig 오브젝트는 노드에 SCTP 커널 모듈을 추가하여 이 프로토콜을 활성화합니다.
권장 컨트롤 플레인 노드 SCTP 구성 (03-sctp-machine-config-master.yaml)
권장 작업자 노드 SCTP 구성 (03-sctp-machine-config-worker.yaml)
7.6.4. rcu_normal 설정
다음 MachineConfig CR은 시스템 시작이 완료된 후 rcu_normal 를 1로 설정하도록 구성합니다. 이로 인해 vDU 애플리케이션의 커널 대기 시간이 향상됩니다.
노드가 시작된 후 rcu_expedited 를 비활성화하는 권장 설정 (08-set-rcu-normal-master.yaml)
7.6.5. kdump를 사용한 자동 커널 크래시 덤프
kdump 는 커널이 충돌할 때 커널 크래시 덤프를 생성하는 Linux 커널 기능입니다. kdump 는 다음 MachineConfig CR을 사용하여 활성화됩니다.
컨트롤 플레인 kdump 로그에서 원래 드라이버를 제거하려면 MachineConfig CR을 권장함 (05-kdump-config-master.yaml)
권장 컨트롤 플레인 노드 kdump 구성 (06-kdump-master.yaml)
작업자 노드 kdump 로그에서 원래 드라이버를 제거하려면 MachineConfig CR을 권장함 (05-kdump-config-worker.yaml)
권장 kdump 작업자 노드 구성 (06-kdump-worker.yaml)
7.6.6. 자동 CRI-O 캐시 초기화 비활성화
제어되지 않은 호스트 종료 또는 클러스터 재부팅 후 CRI-O는 전체 CRI-O 캐시를 자동으로 삭제하여 노드가 재부팅될 때 레지스트리에서 모든 이미지를 가져옵니다. 이로 인해 복구 시간이 너무 느려지거나 복구 실패가 발생할 수 있습니다. GitOps ZTP로 설치하는 단일 노드 OpenShift 클러스터에서 이러한 문제가 발생하지 않도록 하려면 클러스터 설치 중에 CRI-O 삭제 캐시 기능을 비활성화합니다.
컨트롤 플레인 노드에서 CRI-O 캐시 초기화를 비활성화하려면 권장되는 MachineConfig CR (99-crio-disable-wipe-master.yaml)
작업자 노드에서 CRI-O 캐시 초기화를 비활성화하려면 MachineConfig CR을 권장함 (99-crio-disable-wipe-worker.yaml)
7.6.7. crun을 기본 컨테이너 런타임으로 구성
다음 ContainerRuntimeConfig CR(사용자 정의 리소스)은 crun을 컨트롤 플레인 및 작업자 노드의 기본 OCI 컨테이너 런타임으로 구성합니다. crun 컨테이너 런타임은 빠르고 가벼우며 메모리 공간이 적습니다.
최적의 성능을 위해 단일 노드 OpenShift, 3-노드 OpenShift 및 표준 클러스터에서 컨트롤 플레인 및 작업자 노드에 대해 crun을 활성화합니다. CR을 적용할 때 클러스터 재부팅을 방지하려면 변경 사항을 GitOps ZTP 추가 날짜 0 설치 시간 매니페스트로 적용합니다.
컨트롤 플레인 노드에 권장되는 ContainerRuntimeConfig CR (enable-crun-master.yaml)
작업자 노드에 권장되는 ContainerRuntimeConfig CR (enable-crun-worker.yaml)
7.7. 설치 후 클러스터 구성 권장
클러스터 설치가 완료되면 ZTP 파이프라인에서 DU 워크로드를 실행하는 데 필요한 다음 사용자 정의 리소스(CR)를 적용합니다.
GitOps ZTP v4.10 및 이전 버전에서는 MachineConfig CR을 사용하여 UEFI 보안 부팅을 구성합니다. GitOps ZTP v4.11 이상에서는 더 이상 필요하지 않습니다. v4.11에서는 클러스터를 설치하는 데 사용하는 site Config CR에서 spec.clusters.nodes.bootMode 필드를 업데이트하여 단일 노드 OpenShift 클러스터에 대해 UEFI 보안 부팅을 구성합니다. 자세한 내용은 site Config 및 GitOps ZTP를 사용하여 관리되는 클러스터 배포를 참조하십시오.
7.7.1. Operator
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 다음 Operator를 설치해야 합니다.
- Local Storage Operator
- Logging Operator
- PTP Operator
- SR-IOV 네트워크 Operator
또한 사용자 정의 CatalogSource CR을 구성하고 기본 OperatorHub 구성을 비활성화하고 설치하는 클러스터에서 액세스할 수 있는 ImageContentSourcePolicy 미러 레지스트리를 구성해야 합니다.
권장 스토리지 Operator 네임스페이스 및 Operator group 구성 (StorageNS.yaml,StorageOperGroup.yaml)
권장되는 Cluster Logging Operator 네임스페이스 및 Operator group 구성 (ClusterLogNS.yaml,ClusterLogOperGroup.yaml)
권장되는 PTP Operator 네임스페이스 및 Operator 그룹 구성(PtpSubscriptionNS.yaml,PtpSubscriptionOperGroup.yaml)
권장되는 SR-IOV Operator 네임스페이스 및 Operator 그룹 구성(SriovSubscriptionNS.yaml,SriovSubscriptionOperGroup.yaml)
권장되는 CatalogSource 구성 (DefaultCatsrc.yaml)
권장되는 ImageContentSourcePolicy 구성 (DisconnectedICSP.yaml)
권장되는 OperatorHub 구성 (OperatorHub.yaml)
7.7.2. Operator 서브스크립션
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 다음과 같은 Subscription CR이 필요합니다. 서브스크립션은 다음 Operator를 다운로드할 위치를 제공합니다.
- Local Storage Operator
- Logging Operator
- PTP Operator
- SR-IOV 네트워크 Operator
- SRIOV-FEC Operator
Operator 서브스크립션마다 Operator를 가져올 채널을 지정합니다. 권장 채널은 안정적입니다.
수동 또는 자동 업데이트를 지정할 수 있습니다. 자동 모드에서 Operator는 레지스트리에서 사용 가능하게 되면 채널의 최신 버전으로 자동으로 업데이트됩니다. 수동 모드에서는 새 Operator 버전이 명시적으로 승인되는 경우에만 설치됩니다.
서브스크립션에 수동 모드를 사용합니다. 이를 통해 예약된 유지 관리 창에 맞게 Operator 업데이트의 타이밍을 제어할 수 있습니다.
권장 Local Storage Operator 서브스크립션 (StorageSubscription.yaml)
권장되는 SR-IOV Operator 서브스크립션 (SriovSubscription.yaml)
권장되는 PTP Operator 서브스크립션(PtpSubscription.yaml)
권장 Cluster Logging Operator 서브스크립션 (ClusterLogSubscription.yaml)
7.7.3. 클러스터 로깅 및 로그 전달
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 디버깅을 위해 로깅 및 로그 전달이 필요합니다. 다음 ClusterLogging 및 ClusterLogForwarder CR(사용자 정의 리소스)이 필요합니다.
권장되는 클러스터 로깅 구성 (ClusterLogging.yaml)
권장되는 로그 전달 구성 (ClusterLogForwarder.yaml)
spec.outputs.url 필드를 로그가 전달되는 Kafka 서버의 URL로 설정합니다.
7.7.4. 성능 프로필
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 실시간 호스트 기능 및 서비스를 사용하기 위해 Node Tuning Operator 성능 프로필이 필요합니다.
이전 버전의 OpenShift Container Platform에서는 Performance Addon Operator를 사용하여 OpenShift 애플리케이션에 대해 짧은 대기 시간 성능을 달성하기 위해 자동 튜닝을 구현했습니다. OpenShift Container Platform 4.11 이상에서 이 기능은 Node Tuning Operator의 일부입니다.
다음 예제 PerformanceProfile CR은 필요한 단일 노드 OpenShift 클러스터 구성을 보여줍니다.
권장 성능 프로파일 구성 (PerformanceProfile.yaml)
| PerformanceProfile CR 필드 | 설명 |
|---|---|
|
|
|
|
|
|
|
| 분리된 CPU를 설정합니다. 모든 Hyper-Threading 쌍이 일치하는지 확인합니다. 중요 예약 및 격리된 CPU 풀은 겹치지 않아야 하며 함께 사용 가능한 모든 코어에 걸쳐 있어야 합니다. 에 대해 고려하지 않은 CPU 코어로 인해 시스템에서 정의되지 않은 동작이 발생합니다. |
|
| 예약된 CPU를 설정합니다. 워크로드 파티셔닝이 활성화되면 시스템 프로세스, 커널 스레드 및 시스템 컨테이너 스레드가 이러한 CPU로 제한됩니다. 분리되지 않은 모든 CPU를 예약해야 합니다. |
|
|
|
|
|
실시간 커널을 사용하려면 |
|
|
|
7.7.5. 클러스터 시간 동기화 구성
컨트롤 플레인 또는 작업자 노드에 대한 일회성 시스템 시간 동기화 작업을 실행합니다.
컨트롤 플레인 노드에 대해 한 번의 시간 동기화 (99-sync-time-once-master.yaml)
작업자 노드에 대해 한 번의 시간 동기화 (99-sync-time-once-worker.yaml)
7.7.6. PTP
단일 노드 OpenShift 클러스터는 네트워크 시간 동기화에 PTP(Precision Time Protocol)를 사용합니다. 다음 예제 PtpConfig CR은 일반 클럭, 경계 클럭 및 마스터 클록에 필요한 PTP 구성을 보여줍니다. 적용하는 정확한 구성은 노드 하드웨어 및 특정 사용 사례에 따라 다릅니다.
권장되는 PTP 일반 클럭 구성(PtpConfigSlave.yaml)
권장 경계 클럭 구성 (PtpConfigBoundary.yaml)
Recommended PTP Westport Channel e810 grandmaster clock configuration (PtpConfigGmWpc.yaml)
다음 선택적 PtpOperatorConfig CR은 노드에 대한 PTP 이벤트 보고를 구성합니다.
권장되는 PTP 이벤트 구성(PtpOperatorConfigForEvent.yaml)
7.7.7. 확장된 Tuned 프로파일
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 고성능 워크로드에 필요한 추가 성능 튜닝 구성이 필요합니다. 다음 예제 Tuned CR은 Tuned 프로필을 확장합니다.
권장되는 확장 Tuned 프로파일 구성 (TunedPerformancePatch.yaml)
| tuned CR 필드 | 설명 |
|---|---|
|
|
|
7.7.8. SR-IOV
SR-IOV(Single Root I/O Virtualization)는 일반적으로 프론트haul 및 midhaul 네트워크를 활성화하는 데 사용됩니다. 다음 YAML 예제에서는 단일 노드 OpenShift 클러스터에 대해 SR-IOV를 구성합니다.
SriovNetwork CR의 구성은 특정 네트워크 및 인프라 요구 사항에 따라 다릅니다.
권장되는 SriovOperatorConfig CR 구성 (SriovOperatorConfig.yaml)
| SriovOperatorConfig CR 필드 | 설명 |
|---|---|
|
|
예를 들면 다음과 같습니다. |
|
|
|
권장되는 SriovNetwork 구성 (SriovNetwork.yaml)
| SriovNetwork CR 필드 | 설명 |
|---|---|
|
|
midhaul 네트워크의 VLAN을 사용하여 |
권장되는 SriovNetworkNodePolicy CR 구성 (SriovNetworkNodePolicy.yaml)
| SriovNetworkNodePolicy CR field | 설명 |
|---|---|
|
|
|
|
| fronthaul 네트워크에 연결된 인터페이스를 지정합니다. |
|
| fronthaul 네트워크의 VF 수를 지정합니다. |
|
| 물리적 기능의 정확한 이름은 하드웨어와 일치해야 합니다. |
권장되는 SR-IOV 커널 구성 (07-sriov-related-kernel-args-master.yaml)
7.7.9. Console Operator
클러스터 기능 기능을 사용하여 Console Operator가 설치되지 않도록 합니다. 노드를 중앙 집중식으로 관리하면 필요하지 않습니다. Operator를 제거하면 애플리케이션 워크로드에 대한 추가 공간 및 용량이 제공됩니다.
관리 클러스터를 설치하는 동안 Console Operator를 비활성화하려면 siteConfig CR(사용자 정의 리소스)의 spec.clusters.0.install 필드에 다음을 설정합니다.
Config Overrides
installConfigOverrides: "{\"capabilities\":{\"baselineCapabilitySet\": \"None\" }}"
installConfigOverrides: "{\"capabilities\":{\"baselineCapabilitySet\": \"None\" }}"7.7.10. Alertmanager
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 OpenShift Container Platform 모니터링 구성 요소에서 사용하는 CPU 리소스가 감소해야 합니다. 다음 ConfigMap CR(사용자 정의 리소스)은 Alertmanager를 비활성화합니다.
권장 클러스터 모니터링 구성(ReduceMonitoringFootprint.yaml)
7.7.11. Operator Lifecycle Manager
분산 단위 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 CPU 리소스에 대한 일관된 액세스 권한이 필요합니다. OLM(Operator Lifecycle Manager)은 정기적으로 Operator에서 성능 데이터를 수집하여 CPU 사용률이 증가합니다. 다음 ConfigMap CR(사용자 정의 리소스)은 OLM의 Operator 성능 데이터 수집을 비활성화합니다.
권장되는 클러스터 OLM 구성(ReduceOLMFootprint.yaml)
7.7.12. LVM 스토리지
LVM(Logical Volume Manager) 스토리지를 사용하여 단일 노드 OpenShift 클러스터에서 로컬 스토리지를 동적으로 프로비저닝할 수 있습니다.
단일 노드 OpenShift에 권장되는 스토리지 솔루션은 Local Storage Operator입니다. 또는 LVM 스토리지를 사용할 수 있지만 추가 CPU 리소스를 할당해야 합니다.
다음 YAML 예제에서는 OpenShift Container Platform 애플리케이션에서 사용할 수 있도록 노드의 스토리지를 구성합니다.
권장되는 LVMCluster 구성(StorageLVMCluster.yaml)
| LVMCluster CR 필드 | 설명 |
|---|---|
|
| LVM 스토리지에 사용되는 디스크를 구성합니다. 디스크를 지정하지 않으면 LVM 스토리지에서 지정된 씬 풀에서 사용되지 않는 모든 디스크를 사용합니다. |
7.7.13. 네트워크 진단
DU 워크로드를 실행하는 단일 노드 OpenShift 클러스터에는 이러한 Pod에서 생성한 추가 로드를 줄이기 위해 Pod 간 네트워크 연결 검사가 덜 필요합니다. 다음 CR(사용자 정의 리소스)에서는 이러한 검사를 비활성화합니다.
권장되는 네트워크 진단 구성 (DisableSnoNetworkDiag.yaml)
8장. vDU 애플리케이션 워크로드에 대한 단일 노드 OpenShift 클러스터 튜닝 검증
vDU(가상 분산 단위) 애플리케이션을 배포하려면 클러스터 호스트 펌웨어 및 기타 다양한 클러스터 구성 설정을 튜닝하고 구성해야 합니다. 다음 정보를 사용하여 vDU 워크로드를 지원하는 클러스터 구성을 검증합니다.
8.1. vDU 클러스터 호스트의 권장 펌웨어 구성
다음 표를 기반으로 OpenShift Container Platform 4.15에서 실행되는 vDU 애플리케이션의 클러스터 호스트 펌웨어를 구성합니다.
다음 표는 vDU 클러스터 호스트 펌웨어 구성에 대한 일반적인 권장 사항입니다. 정확한 펌웨어 설정은 요구 사항과 특정 하드웨어 플랫폼에 따라 달라집니다. 펌웨어의 자동 설정은 제로 터치 프로비저닝 파이프라인에 의해 처리되지 않습니다.
| 펌웨어 설정 | 설정 | 설명 |
|---|---|---|
| HyperTransport (HT) | 활성화됨 | HT(HyperTransport) 버스는 AMD에서 개발한 버스 기술입니다. HT는 호스트 메모리의 구성 요소와 다른 시스템 주변 장치 간의 고속 링크를 제공합니다. |
| UEFI | 활성화됨 | vDU 호스트에 대해 UEFI에서 부팅을 활성화합니다. |
| CPU 전원 및 성능 정책 | 성능 | CPU 전원 및 성능 정책을 설정하여 에너지 효율성에 대한 성능을 위해 시스템을 최적화합니다. |
| 코어 빈도 확장 해제 | 비활성화됨 | Uncore Frequency Scaling을 비활성화하여 CPU의 코어가 아닌 부분 및 빈도가 독립적으로 설정되지 않도록 합니다. |
| Uncore frequency | 최대 | 캐시 및 메모리 컨트롤러와 같은 CPU의 코어가 아닌 부분을 최대 작업 빈도로 설정합니다. |
| 성능 P-limit | 비활성화됨 | 프로세서의 Uncore 빈도 조정을 방지하려면 성능 P 제한을 비활성화합니다. |
| Enhanced Intel® SpeedStep Tech | 활성화됨 | 향상된 Intel SpeedStep을 활성화하여 시스템의 프로세서 마운드 및 코어 빈도를 동적으로 조정하여 호스트의 전력 소비 및 열 생산량을 줄일 수 있습니다. |
| Intel® Turbo Boost Technology | 활성화됨 | Intel 기반 CPU용 Cryostat Boost Technology를 사용하면 전력, 현재 및 온도 사양 제한 미만으로 작동하는 경우 프로세서 코어가 정격된 작동 빈도보다 빠르게 실행될 수 있습니다. |
| Intel Configurable TDP | 활성화됨 | CPU에 대해 TDP(rmal Design Power)를 활성화합니다. |
| 구성 가능한 TDP 수준 | 수준 2 | TDP 수준은 특정 성능 평가에 필요한 CPU 전력 소비를 설정합니다. TDP 수준 2는 전력 소비로 CPU를 가장 안정적인 성능 수준으로 설정합니다. |
| 에너지 효율성: | 비활성화됨 | 프로세서는 에너지 효율성 기반 정책을 사용하지 못하도록 energy Efficient Cryostat를 비활성화합니다. |
| 하드웨어 P-States | 활성화 또는 비활성화 |
OS가 제어하는 P-States를 활성화하여 전원 저장 구성을 허용합니다. |
| 패키지 C-State | C0/C1 상태 | C0 또는 C1 상태를 사용하여 프로세서를 완전히 활성 상태(C0)로 설정하거나 소프트웨어(C1)에서 실행되는 CPU 내부 시계를 중지합니다. |
| C1E | 비활성화됨 | CPU Enhanced Halt(C1E)는 Intel 칩의 전원 저장 기능입니다. C1E를 비활성화하면 비활성 상태에서 운영 체제가 CPU에 halt 명령을 보내지 않습니다. |
| 프로세서 C6 | 비활성화됨 | C6 전원은 유휴 CPU 코어 및 캐시를 자동으로 비활성화하는 CPU 기능입니다. C6을 비활성화하면 시스템 성능이 향상됩니다. |
| 하위 NUMA | 비활성화됨 | 하위 NUMA 클러스터링은 프로세서 코어, 캐시 및 메모리를 여러 NUMA 도메인으로 나눕니다. 이 옵션을 비활성화하면 대기 시간에 민감한 워크로드의 성능이 향상될 수 있습니다. |
호스트의 펌웨어에서 글로벌 SR-IOV 및 VT-d 설정을 활성화합니다. 이러한 설정은 베어 메탈 환경과 관련이 있습니다.
C-states 및 OS가 제어하는 P-States 를 모두 활성화하여 Pod 전원 관리를 허용합니다.
8.2. vDU 애플리케이션을 실행하기 위한 권장 클러스터 구성
vDU(가상 분산 장치) 애플리케이션을 실행하는 클러스터에는 고도로 조정되고 최적화된 구성이 필요합니다. 다음 정보는 OpenShift Container Platform 4.15 클러스터에서 vDU 워크로드를 지원하는 데 필요한 다양한 요소를 설명합니다.
8.2.1. 단일 노드 OpenShift 클러스터에 권장되는 클러스터 MachineConfig CR
ztp-site-generate 컨테이너에서 추출한 MachineConfig CR(사용자 정의 리소스)이 클러스터에 적용되었는지 확인합니다. CR은 추출된 out/source-crs/extra-manifest/ 폴더에서 확인할 수 있습니다.
ztp-site-generate 컨테이너의 다음 MachineConfig CR은 클러스터 호스트를 구성합니다.
| MachineConfig CR | 설명 |
|---|---|
|
| 컨테이너 마운트 네임스페이스 및 kubelet 구성을 구성합니다. |
|
|
SCTP 커널 모듈을 로드합니다. 이러한 |
|
| 클러스터에 대한 kdump 크래시 보고를 구성합니다. |
|
| 클러스터에서 SR-IOV 커널 인수를 구성합니다. |
|
|
클러스터가 재부팅된 후 |
|
| 클러스터 재부팅 후 자동 CRI-O 캐시 초기화를 비활성화합니다. |
|
| Chrony 서비스에서 시스템 클럭의 일회성 검사 및 조정을 구성합니다. |
|
|
|
|
| 클러스터 설치 중에 cgroup v1을 활성화하고 RHACM 클러스터 정책을 생성할 때 사용합니다. |
OpenShift Container Platform 4.14 이상에서는 SiteConfig CR의 cpu CryostatingMode 필드를 사용하여 워크로드 파티셔닝을 구성합니다.
8.2.2. 권장되는 클러스터 Operator
다음 Operator는 가상화된 vDU(Distributed Unit) 애플리케이션을 실행하는 클러스터에 필요하며 기본 참조 구성의 일부입니다.
- NTO(Node Tuning Operator) 이전에 Performance Addon Operator와 함께 제공된 NTO 패키지 기능은 이제 NTO의 일부입니다.
- PTP Operator
- SR-IOV 네트워크 Operator
- Red Hat OpenShift Logging Operator
- Local Storage Operator
8.2.3. 권장되는 클러스터 커널 구성
항상 클러스터에서 지원되는 최신 실시간 커널 버전을 사용합니다. 클러스터에 다음 구성을 적용해야 합니다.
다음
additionalKernelArgs가 클러스터 성능 프로필에 설정되어 있는지 확인합니다.spec: additionalKernelArgs: - "rcupdate.rcu_normal_after_boot=0" - "efi=runtime" - "module_blacklist=irdma"
spec: additionalKernelArgs: - "rcupdate.rcu_normal_after_boot=0" - "efi=runtime" - "module_blacklist=irdma"Copy to Clipboard Copied! Toggle word wrap Toggle overflow TunedCR의performance-patch프로필이 관련PerformanceProfileCR의격리된CPU 세트와 일치하는 올바른 CPU 격리 세트를 구성하는지 확인합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.4. 실시간 커널 버전 확인
항상 OpenShift Container Platform 클러스터에서 최신 버전의 실시간 커널을 사용하십시오. 클러스터에서 사용 중인 커널 버전을 잘 모를 경우 현재 실시간 커널 버전을 릴리스 버전과 다음 절차와 비교할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 로그인합니다. -
podman을 설치했습니다.
프로세스
다음 명령을 실행하여 클러스터 버전을 가져옵니다.
OCP_VERSION=$(oc get clusterversion version -o jsonpath='{.status.desired.version}{"\n"}')$ OCP_VERSION=$(oc get clusterversion version -o jsonpath='{.status.desired.version}{"\n"}')Copy to Clipboard Copied! Toggle word wrap Toggle overflow 릴리스 이미지 SHA 번호를 가져옵니다.
DTK_IMAGE=$(oc adm release info --image-for=driver-toolkit quay.io/openshift-release-dev/ocp-release:$OCP_VERSION-x86_64)
$ DTK_IMAGE=$(oc adm release info --image-for=driver-toolkit quay.io/openshift-release-dev/ocp-release:$OCP_VERSION-x86_64)Copy to Clipboard Copied! Toggle word wrap Toggle overflow 릴리스 이미지 컨테이너를 실행하고 클러스터의 현재 릴리스와 함께 패키지된 커널 버전을 추출합니다.
podman run --rm $DTK_IMAGE rpm -qa | grep 'kernel-rt-core-' | sed 's#kernel-rt-core-##'
$ podman run --rm $DTK_IMAGE rpm -qa | grep 'kernel-rt-core-' | sed 's#kernel-rt-core-##'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
4.18.0-305.49.1.rt7.121.el8_4.x86_64
4.18.0-305.49.1.rt7.121.el8_4.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow 이는 릴리스와 함께 제공되는 기본 실시간 커널 버전입니다.
참고실시간 커널은 커널 버전의
.rt문자열로 표시됩니다.
검증
클러스터의 현재 릴리스에 대해 나열된 커널 버전이 클러스터에서 실행 중인 실제 실시간 커널과 일치하는지 확인합니다. 다음 명령을 실행하여 실행 중인 실시간 커널 버전을 확인합니다.
클러스터 노드에 대한 원격 쉘 연결을 엽니다.
oc debug node/<node_name>
$ oc debug node/<node_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 실시간 커널 버전을 확인합니다.
uname -r
sh-4.4# uname -rCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
4.18.0-305.49.1.rt7.121.el8_4.x86_64
4.18.0-305.49.1.rt7.121.el8_4.x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.3. 권장 클러스터 구성이 적용되었는지 확인
클러스터가 올바른 구성을 실행하고 있는지 확인할 수 있습니다. 다음 절차에서는 OpenShift Container Platform 4.15 클러스터에서 DU 애플리케이션을 배포하는 데 필요한 다양한 구성을 확인하는 방법을 설명합니다.
사전 요구 사항
- 클러스터를 배포하고 vDU 워크로드에 맞게 조정했습니다.
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 로그인했습니다.
프로세스
기본 OperatorHub 소스가 비활성화되어 있는지 확인합니다. 다음 명령을 실행합니다.
oc get operatorhub cluster -o yaml
$ oc get operatorhub cluster -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
spec: disableAllDefaultSources: truespec: disableAllDefaultSources: trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 모든 필요한
CatalogSource리소스에 워크로드 파티셔닝(PreferredDuringScheduling)에 대한 주석이 있는지 확인합니다.oc get catalogsource -A -o jsonpath='{range .items[*]}{.metadata.name}{" -- "}{.metadata.annotations.target\.workload\.openshift\.io/management}{"\n"}{end}'$ oc get catalogsource -A -o jsonpath='{range .items[*]}{.metadata.name}{" -- "}{.metadata.annotations.target\.workload\.openshift\.io/management}{"\n"}{end}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
certified-operators -- {"effect": "PreferredDuringScheduling"} community-operators -- {"effect": "PreferredDuringScheduling"} ran-operators redhat-marketplace -- {"effect": "PreferredDuringScheduling"} redhat-operators -- {"effect": "PreferredDuringScheduling"}certified-operators -- {"effect": "PreferredDuringScheduling"} community-operators -- {"effect": "PreferredDuringScheduling"} ran-operators1 redhat-marketplace -- {"effect": "PreferredDuringScheduling"} redhat-operators -- {"effect": "PreferredDuringScheduling"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 주석이 없는
CatalogSource리소스도 반환됩니다. 이 예에서ran-operatorsCatalogSource리소스에는 주석이 추가되지 않으며PreferredDuringScheduling주석이 없습니다.
참고올바르게 구성된 vDU 클러스터에는 주석이 지정된 단일 카탈로그 소스만 나열됩니다.
워크로드 파티셔닝을 위해 해당하는 모든 OpenShift Container Platform Operator 네임스페이스에 주석이 추가되었는지 확인합니다. 여기에는 코어 OpenShift Container Platform과 함께 설치된 모든 Operator 및 참조 DU 튜닝 구성에 포함된 추가 Operator 세트가 포함됩니다. 다음 명령을 실행합니다.
oc get namespaces -A -o jsonpath='{range .items[*]}{.metadata.name}{" -- "}{.metadata.annotations.workload\.openshift\.io/allowed}{"\n"}{end}'$ oc get namespaces -A -o jsonpath='{range .items[*]}{.metadata.name}{" -- "}{.metadata.annotations.workload\.openshift\.io/allowed}{"\n"}{end}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
default -- openshift-apiserver -- management openshift-apiserver-operator -- management openshift-authentication -- management openshift-authentication-operator -- management
default -- openshift-apiserver -- management openshift-apiserver-operator -- management openshift-authentication -- management openshift-authentication-operator -- managementCopy to Clipboard Copied! Toggle word wrap Toggle overflow 중요추가 Operator는 워크로드 파티셔닝을 위해 주석을 달 수 없습니다. 이전 명령의 출력에서
--separator 오른쪽에 값을 지정하지 않고 추가 Operator를 나열해야 합니다.ClusterLogging구성이 올바른지 확인합니다. 다음 명령을 실행합니다.적절한 입력 및 출력 로그가 구성되어 있는지 확인합니다.
oc get -n openshift-logging ClusterLogForwarder instance -o yaml
$ oc get -n openshift-logging ClusterLogForwarder instance -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 큐레이션 일정이 애플리케이션에 적합한지 확인합니다.
oc get -n openshift-logging clusterloggings.logging.openshift.io instance -o yaml
$ oc get -n openshift-logging clusterloggings.logging.openshift.io instance -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
다음 명령을 실행하여 웹 콘솔이 비활성화(
managementState: Removed)인지 확인합니다.oc get consoles.operator.openshift.io cluster -o jsonpath="{ .spec.managementState }"$ oc get consoles.operator.openshift.io cluster -o jsonpath="{ .spec.managementState }"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Removed
RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 클러스터 노드에서
chronyd가 비활성화되어 있는지 확인합니다.oc debug node/<node_name>
$ oc debug node/<node_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 노드에서
chronyd의 상태를 확인합니다.chroot /host
sh-4.4# chroot /hostCopy to Clipboard Copied! Toggle word wrap Toggle overflow systemctl status chronyd
sh-4.4# systemctl status chronydCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
● chronyd.service - NTP client/server Loaded: loaded (/usr/lib/systemd/system/chronyd.service; disabled; vendor preset: enabled) Active: inactive (dead) Docs: man:chronyd(8) man:chrony.conf(5)● chronyd.service - NTP client/server Loaded: loaded (/usr/lib/systemd/system/chronyd.service; disabled; vendor preset: enabled) Active: inactive (dead) Docs: man:chronyd(8) man:chrony.conf(5)Copy to Clipboard Copied! Toggle word wrap Toggle overflow linuxptp-daemon컨테이너 및 PTP 관리 클라이언트(pmc) 툴에 대한 원격 쉘 연결을 사용하여 PTP 인터페이스가 기본 클록에 성공적으로 동기화되었는지 확인합니다.다음 명령을 실행하여
linuxptp-daemonPod의 이름으로$PTP_POD_NAME변수를 설정합니다.PTP_POD_NAME=$(oc get pods -n openshift-ptp -l app=linuxptp-daemon -o name)
$ PTP_POD_NAME=$(oc get pods -n openshift-ptp -l app=linuxptp-daemon -o name)Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 PTP 장치의 동기화 상태를 확인합니다.
oc -n openshift-ptp rsh -c linuxptp-daemon-container ${PTP_POD_NAME} pmc -u -f /var/run/ptp4l.0.config -b 0 'GET PORT_DATA_SET'$ oc -n openshift-ptp rsh -c linuxptp-daemon-container ${PTP_POD_NAME} pmc -u -f /var/run/ptp4l.0.config -b 0 'GET PORT_DATA_SET'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음
pmc명령을 실행하여 PTP 클럭 상태를 확인합니다.oc -n openshift-ptp rsh -c linuxptp-daemon-container ${PTP_POD_NAME} pmc -u -f /var/run/ptp4l.0.config -b 0 'GET TIME_STATUS_NP'$ oc -n openshift-ptp rsh -c linuxptp-daemon-container ${PTP_POD_NAME} pmc -u -f /var/run/ptp4l.0.config -b 0 'GET TIME_STATUS_NP'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow /var/run/ptp4l.0.config의 값에 해당하는 예상마스터 오프셋값이linuxptp-daemon-container로그에 있는지 확인합니다.oc logs $PTP_POD_NAME -n openshift-ptp -c linuxptp-daemon-container
$ oc logs $PTP_POD_NAME -n openshift-ptp -c linuxptp-daemon-containerCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
phc2sys[56020.341]: [ptp4l.1.config] CLOCK_REALTIME phc offset -1731092 s2 freq -1546242 delay 497 ptp4l[56020.390]: [ptp4l.1.config] master offset -2 s2 freq -5863 path delay 541 ptp4l[56020.390]: [ptp4l.0.config] master offset -8 s2 freq -10699 path delay 533
phc2sys[56020.341]: [ptp4l.1.config] CLOCK_REALTIME phc offset -1731092 s2 freq -1546242 delay 497 ptp4l[56020.390]: [ptp4l.1.config] master offset -2 s2 freq -5863 path delay 541 ptp4l[56020.390]: [ptp4l.0.config] master offset -8 s2 freq -10699 path delay 533Copy to Clipboard Copied! Toggle word wrap Toggle overflow
다음 명령을 실행하여 SR-IOV 구성이 올바른지 확인합니다.
SriovOperatorConfig리소스의disableDrain값이true로 설정되어 있는지 확인합니다.oc get sriovoperatorconfig -n openshift-sriov-network-operator default -o jsonpath="{.spec.disableDrain}{'\n'}"$ oc get sriovoperatorconfig -n openshift-sriov-network-operator default -o jsonpath="{.spec.disableDrain}{'\n'}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
true
trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
SriovNetworkNodeState동기화 상태가Succeeded인지 확인합니다.oc get SriovNetworkNodeStates -n openshift-sriov-network-operator -o jsonpath="{.items[*].status.syncStatus}{'\n'}"$ oc get SriovNetworkNodeStates -n openshift-sriov-network-operator -o jsonpath="{.items[*].status.syncStatus}{'\n'}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Succeeded
SucceededCopy to Clipboard Copied! Toggle word wrap Toggle overflow SR-IOV용으로 구성된 각 인터페이스에서
Vfs(가상 기능)의 예상 수와 구성이 있고.status.interfaces필드에 올바른지 확인합니다. 예를 들면 다음과 같습니다.oc get SriovNetworkNodeStates -n openshift-sriov-network-operator -o yaml
$ oc get SriovNetworkNodeStates -n openshift-sriov-network-operator -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
클러스터 성능 프로필이 올바른지 확인합니다.
cpu및hugepages섹션은 하드웨어 구성에 따라 다릅니다. 다음 명령을 실행합니다.oc get PerformanceProfile openshift-node-performance-profile -o yaml
$ oc get PerformanceProfile openshift-node-performance-profile -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고CPU 설정은 서버에서 사용 가능한 코어 수에 따라 다르며 워크로드 파티셔닝 설정과 일치해야 합니다.
hugepages구성은 서버와 애플리케이션에 따라 다릅니다.다음 명령을 실행하여
PerformanceProfile이 클러스터에 성공적으로 적용되었는지 확인합니다.oc get performanceprofile openshift-node-performance-profile -o jsonpath="{range .status.conditions[*]}{ @.type }{' -- '}{@.status}{'\n'}{end}"$ oc get performanceprofile openshift-node-performance-profile -o jsonpath="{range .status.conditions[*]}{ @.type }{' -- '}{@.status}{'\n'}{end}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Available -- True Upgradeable -- True Progressing -- False Degraded -- False
Available -- True Upgradeable -- True Progressing -- False Degraded -- FalseCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
Tuned성능 패치 설정을 확인합니다.oc get tuneds.tuned.openshift.io -n openshift-cluster-node-tuning-operator performance-patch -o yaml
$ oc get tuneds.tuned.openshift.io -n openshift-cluster-node-tuning-operator performance-patch -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
cmdline=nohz_full=의 cpu 목록은 하드웨어 구성에 따라 다릅니다.
다음 명령을 실행하여 클러스터 네트워킹 진단이 비활성화되었는지 확인합니다.
oc get networks.operator.openshift.io cluster -o jsonpath='{.spec.disableNetworkDiagnostics}'$ oc get networks.operator.openshift.io cluster -o jsonpath='{.spec.disableNetworkDiagnostics}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
true
trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Kubelet하우스키핑 간격이 느린 속도로 조정되었는지 확인합니다. 이는containerMountNS머신 구성에 설정됩니다. 다음 명령을 실행합니다.oc describe machineconfig container-mount-namespace-and-kubelet-conf-master | grep OPENSHIFT_MAX_HOUSEKEEPING_INTERVAL_DURATION
$ oc describe machineconfig container-mount-namespace-and-kubelet-conf-master | grep OPENSHIFT_MAX_HOUSEKEEPING_INTERVAL_DURATIONCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Environment="OPENSHIFT_MAX_HOUSEKEEPING_INTERVAL_DURATION=60s"
Environment="OPENSHIFT_MAX_HOUSEKEEPING_INTERVAL_DURATION=60s"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 Grafana 및
alertManagerMain이 비활성화되어 Prometheus 보존 기간이 24h로 설정되어 있는지 확인합니다.oc get configmap cluster-monitoring-config -n openshift-monitoring -o jsonpath="{ .data.config\.yaml }"$ oc get configmap cluster-monitoring-config -n openshift-monitoring -o jsonpath="{ .data.config\.yaml }"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 Grafana 및
alertManagerMain경로가 클러스터에 없는지 확인합니다.oc get route -n openshift-monitoring alertmanager-main
$ oc get route -n openshift-monitoring alertmanager-mainCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc get route -n openshift-monitoring grafana
$ oc get route -n openshift-monitoring grafanaCopy to Clipboard Copied! Toggle word wrap Toggle overflow 두 쿼리 모두
서버 오류(NotFound)메시지를 반환해야 합니다.
다음 명령을 실행하여
PerformanceProfile,Tunedperformance-patch, 워크로드 파티셔닝 및 커널 명령줄 인수에 대해예약된CPU가 최소 4개 이상 있는지 확인합니다.oc get performanceprofile -o jsonpath="{ .items[0].spec.cpu.reserved }"$ oc get performanceprofile -o jsonpath="{ .items[0].spec.cpu.reserved }"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
0-3
0-3Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고워크로드 요구 사항에 따라 추가 예약된 CPU를 할당해야 할 수 있습니다.
9장. SiteConfig 리소스를 사용한 고급 관리 클러스터 구성
SiteConfig CR(사용자 정의 리소스)을 사용하여 설치 시 관리 클러스터에 사용자 정의 기능 및 구성을 배포할 수 있습니다.
9.1. GitOps ZTP 파이프라인에서 추가 설치 매니페스트 사용자 정의
GitOps ZTP(ZTP) 파이프라인의 설치 단계에 포함할 추가 매니페스트 세트를 정의할 수 있습니다. 이러한 매니페스트는 site Config CR (사용자 정의 리소스)에 연결되며 설치 중에 클러스터에 적용됩니다. 설치 시 MachineConfig CR을 포함하면 설치 프로세스의 효율성이 향상됩니다.
사전 요구 사항
- 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성합니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 Argo CD 애플리케이션의 소스 리포지토리로 정의해야 합니다.
프로세스
- GitOps ZTP 파이프라인에서 클러스터 설치를 사용자 정의하는 데 사용하는 추가 매니페스트 CR 세트를 생성합니다.
사용자 지정
/siteconfig디렉터리에서 추가 매니페스트를 위한 하위 디렉터리/custom-manifest를 생성합니다. 다음 예제에서는/custom-manifest폴더가 있는 샘플/siteconfig를 보여줍니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고전체에서 사용되는 하위 디렉터리 이름
/custom-manifest및/extra-manifest는 예제 이름 전용입니다. 이러한 이름을 사용할 필요는 없으며 이러한 하위 디렉터리의 이름을 지정하는 방법에 대한 제한은 없습니다. 이 예에서/extra-manifest는ztp-site-generate컨테이너에서/extra-manifest의 콘텐츠를 저장하는 Git 하위 디렉터리를 나타냅니다.-
사용자 정의 매니페스트 CR을
siteconfig/custom-manifest디렉터리에 추가합니다. SiteConfigCR에서extraManifests.searchPaths필드에 디렉터리 이름을 입력합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
SiteConfig,/extra-manifestCR 및/custom-manifestCR을 저장하고 사이트 구성 리포지터리로 푸시합니다.
클러스터 프로비저닝 중에 GitOps ZTP 파이프라인은 /custom-manifest 디렉터리의 CR을 extra-manifest /에 저장된 추가 매니페스트 세트에 추가합니다.
4.14 버전의 extraManifestPath 에는 사용 중단 경고가 적용됩니다.
extraManifestPath 는 계속 지원되지만 extraManifests.searchPaths 를 사용하는 것이 좋습니다. SiteConfig 파일에 extraManifests.searchPaths 를 정의하는 경우 GitOps ZTP 파이프라인은 사이트 설치 중에 ztp-site-generate 컨테이너에서 매니페스트를 가져오지 않습니다.
Siteconfig CR에서 extraManifestPath 및 extraManifests.searchPaths 를 모두 정의하는 경우 extraManifests.searchPaths 에 정의된 설정이 우선합니다.
ztp-site-generate 컨테이너에서 /extra-manifest 의 내용을 추출하여 GIT 리포지토리로 내보내는 것이 좋습니다.
9.2. siteConfig 필터를 사용하여 사용자 정의 리소스 필터링
필터를 사용하면 GitOps ZTP(ZTP) 파이프라인의 설치 단계에서 사용할 다른 CR을 포함하거나 제외하도록 SiteConfig CR(사용자 정의 리소스)을 쉽게 사용자 지정할 수 있습니다.
SiteConfig CR의 include 또는 exclude 기본값 을 포함하거나 제외하려는 특정 추가Manifest RAN CR 목록과 함께 지정할 수 있습니다. include Default를 포함 으로 설정하면 GitOps ZTP 파이프라인이 설치 중에 /source-crs/extra-manifest 의 모든 파일을 적용합니다. exclude 로 inclusionDefault 를 설정하면 그 반대입니다.
기본적으로 포함된 /source-crs/extra-manifest 폴더에서 개별 CR을 제외할 수 있습니다. 다음 예제에서는 설치 시 /source-crs/extra-manifest/03-sctp-machine-config-worker.yaml CR을 제외하도록 사용자 정의 단일 노드 OpenShift SiteConfig CR을 구성합니다.
일부 추가 필터링 시나리오도 설명되어 있습니다.
사전 요구 사항
- 필요한 설치 및 정책 CR을 생성하도록 허브 클러스터를 구성했습니다.
- 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성하셨습니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 Argo CD 애플리케이션의 소스 리포지토리로 정의해야 합니다.
프로세스
GitOps ZTP 파이프라인이
03-sctp-machine-config-worker.yamlCR 파일을 적용하지 못하도록 siteConfigCR에 다음 YAML을 적용합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow GitOps ZTP 파이프라인은 설치 중에
03-sctp-machine-config-worker.yamlCR을 건너뜁니다./source-crs/extra-manifest의 다른 모든 CR이 적용됩니다.SiteConfigCR을 저장하고 사이트 구성 리포지토리로 변경 사항을 내보냅니다.GitOps ZTP 파이프라인은 site
Config 필터 명령에 따라 적용되는 CR을모니터링하고 조정합니다.선택 사항: GitOps ZTP 파이프라인이 클러스터 설치 중에 모든
/source-crs/extra-manifestCR을 적용하지 않도록 하려면 siteConfigCR에서 다음 YAML을 적용합니다.- clusterName: "site1-sno-du" extraManifests: filter: inclusionDefault: exclude- clusterName: "site1-sno-du" extraManifests: filter: inclusionDefault: excludeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 선택 사항:
/source-crs/extra-manifestRAN CR을 모두 제외하고 설치 중에 사용자 지정 CR 파일을 포함하려면 사용자 정의SiteConfigCR을 편집하여 사용자 정의 매니페스트 폴더 및포함파일을 설정합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 예제에서는 사용자 지정 폴더 구조를 보여줍니다.
siteconfig ├── site1-sno-du.yaml └── user-custom-manifest └── custom-sctp-machine-config-worker.yamlsiteconfig ├── site1-sno-du.yaml └── user-custom-manifest └── custom-sctp-machine-config-worker.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3. SiteConfig CR을 사용하여 노드 삭제
SiteConfig CR(사용자 정의 리소스)을 사용하면 노드를 삭제하고 다시 프로비저닝할 수 있습니다. 이 방법은 노드를 수동으로 삭제하는 것보다 효율적입니다.
사전 요구 사항
- 필요한 설치 및 정책 CR을 생성하도록 허브 클러스터를 구성했습니다.
- 사용자 지정 사이트 구성 데이터를 관리할 수 있는 Git 리포지토리를 생성했습니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 Argo CD 애플리케이션의 소스 리포지토리로 정의해야 합니다.
프로세스
bmac.agent-install.openshift.io/remove-agent-and-node-on-delete=true주석을 포함하도록SiteConfigCR을 업데이트하고 변경 사항을 Git 리포지토리로 내보냅니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
BareMetalHost오브젝트에 주석이 추가되었는지 확인합니다.oc get bmh -n <managed-cluster-namespace> <bmh-object> -ojsonpath='{.metadata}' | jq -r '.annotations["bmac.agent-install.openshift.io/remove-agent-and-node-on-delete"]'oc get bmh -n <managed-cluster-namespace> <bmh-object> -ojsonpath='{.metadata}' | jq -r '.annotations["bmac.agent-install.openshift.io/remove-agent-and-node-on-delete"]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
true
trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow crSuppression.BareMetalHost주석을 포함하도록SiteConfigCR을 업데이트하여BareMetalHostCR 생성을 비활성화합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
변경 사항을 Git 리포지토리로 푸시하고 프로비저닝 해제가 시작될 때까지 기다립니다.
BareMetalHostCR의 상태는프로비저닝 해제로 변경되어야 합니다.BareMetalHost가 프로비저닝 해제가 완료될 때까지 기다린 후 완전히 삭제됩니다.
검증
다음 명령을 실행하여 작업자 노드의
BareMetalHost및AgentCR이 hub 클러스터에서 삭제되었는지 확인합니다.oc get bmh -n <cluster-ns>
$ oc get bmh -n <cluster-ns>Copy to Clipboard Copied! Toggle word wrap Toggle overflow oc get agent -n <cluster-ns>
$ oc get agent -n <cluster-ns>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 노드 레코드가 spoke 클러스터에서 삭제되었는지 확인합니다.
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow 참고시크릿을 사용하여 작업하는 경우 ArgoCD에는 삭제 후 다시 동기화를 완료하기 위해 시크릿이 필요하므로 시크릿을 너무 빨리 삭제하면 문제가 발생할 수 있습니다. 현재 ArgoCD 동기화가 완료되면 노드 정리 후에만 보안을 삭제합니다.
다음 단계
노드를 다시 프로비저닝하려면 이전에 SiteConfig 에 추가된 변경 사항을 삭제하고, 변경 사항을 Git 리포지토리로 푸시하고 동기화가 완료될 때까지 기다립니다. 이렇게 하면 작업자 노드의 BareMetalHost CR이 다시 생성되고 노드를 다시 설치합니다.
10장. PolicyGenTemplate 리소스를 사용한 고급 관리 클러스터 구성
PolicyGenTemplate CR을 사용하여 관리 클러스터에 사용자 지정 기능을 배포할 수 있습니다.
10.1. 클러스터에 추가 변경 사항 배포
기본 GitOps ZTP(ZTP) 파이프라인 구성 외부에서 클러스터 구성을 변경해야 하는 경우 다음 세 가지 옵션이 있습니다.
- GitOps ZTP 파이프라인이 완료된 후 추가 구성을 적용합니다.
- GitOps ZTP 파이프라인 배포가 완료되면 배포된 클러스터가 애플리케이션 워크로드에 대해 준비됩니다. 이 시점에서 추가 Operator를 설치하고 요구 사항과 관련된 구성을 적용할 수 있습니다. 추가 구성이 플랫폼 성능 또는 할당된 CPU 예산에 부정적인 영향을 미치지 않도록 합니다.
- GitOps ZTP 라이브러리에 콘텐츠 추가
- GitOps ZTP 파이프라인을 사용하여 배포하는 기본 소스 CR(사용자 정의 리소스)은 필요에 따라 사용자 정의 콘텐츠를 사용하여 보강할 수 있습니다.
- 클러스터 설치에 대한 추가 매니페스트 생성
- 추가 매니페스트는 설치 중에 적용되며 설치 프로세스를 보다 효율적으로 만듭니다.
추가 소스 CR을 제공하거나 기존 소스 CR을 수정하면 OpenShift Container Platform의 성능 또는 CPU 프로필에 큰 영향을 미칠 수 있습니다.
10.2. PolicyGenTemplate CR을 사용하여 소스 CR 콘텐츠를 재정의
PolicyGenTemplate CR(사용자 정의 리소스)을 사용하면 ztp-site-generate 컨테이너의 GitOps 플러그인과 함께 제공된 기본 소스 CR 상단에 추가 구성 세부 정보를 오버레이할 수 있습니다. PolicyGenTemplate CR은 기본 CR에 대한 논리 병합 또는 패치로 생각할 수 있습니다. PolicyGenTemplate CR을 사용하여 기본 CR의 단일 필드를 업데이트하거나 기본 CR의 전체 콘텐츠를 오버레이합니다. 값을 업데이트하고 기본 CR에 없는 필드를 삽입할 수 있습니다.
다음 예제 절차에서는 group-du-sno-ranGen.yaml 파일의 PolicyGenTemplate CR을 기반으로 한 참조 구성에 대해 생성된 PerformanceProfile CR의 필드를 업데이트하는 방법을 설명합니다. 요구 사항에 따라 PolicyGenTemplate 의 다른 부분을 수정하는 기준으로 절차를 사용하십시오.
사전 요구 사항
- 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성합니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 Argo CD의 소스 리포지토리로 정의해야 합니다.
프로세스
기존 콘텐츠의 기본 소스 CR을 검토합니다. ZTP(ZTP) 컨테이너에서 해당 CR을 추출하여 참조
PolicyGenTemplateCR에 나열된 소스 CR을 검토할 수 있습니다./out폴더를 생성합니다.mkdir -p ./out
$ mkdir -p ./outCopy to Clipboard Copied! Toggle word wrap Toggle overflow 소스 CR을 추출합니다.
podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15.1 extract /home/ztp --tar | tar x -C ./out
$ podman run --log-driver=none --rm registry.redhat.io/openshift4/ztp-site-generate-rhel8:v4.15.1 extract /home/ztp --tar | tar x -C ./outCopy to Clipboard Copied! Toggle word wrap Toggle overflow
./out/source-crs/PerformanceProfile.yaml에서 기준PerformanceProfileCR을 검토합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고$…이 포함된 소스 CR의 모든 필드는PolicyGenTemplateCR에 제공되지 않는 경우 생성된 CR에서 제거됩니다.group-du-sno-ranGen.yaml참조 파일에서PerformanceProfile의PolicyGenTemplate항목을 업데이트합니다. 다음 예제PolicyGenTemplateCR 스탠자는 적절한 CPU 사양을 제공하고hugepages구성을 설정하며globallyDisableIrqLoadBalancing을 false로 설정하는 새 필드를 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP argo CD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
출력 예
GitOps ZTP 애플리케이션은 생성된 PerformanceProfile CR을 포함하는 RHACM 정책을 생성합니다. 해당 CR의 내용은 PolicyGenTemplate 의 PerformanceProfile 항목의 메타데이터 및 사양 콘텐츠를 소스 CR에 병합하여 파생됩니다. 결과 CR에는 다음과 같은 내용이 있습니다.
ztp-site-generate 컨테이너에서 추출한 /source-crs 폴더에서 $ 구문은 구문에 의해 함축된 템플릿 대체에 사용되지 않습니다. 대신 policyGen 툴에 문자열의 $ 접두사가 표시되고 관련 PolicyGenTemplate CR에서 해당 필드의 값을 지정하지 않으면 해당 필드가 출력 CR에서 완전히 생략됩니다.
이에 대한 예외는 PolicyGenTemplate CR에서 mcp 값으로 대체되는 /source-crs YAML 파일의 $mcp 변수입니다. 예를 들어 example/policygentemplates/group-du-standard-ranGen.yaml 에서 mcp 의 값은 worker 입니다.
spec:
bindingRules:
group-du-standard: ""
mcp: "worker"
spec:
bindingRules:
group-du-standard: ""
mcp: "worker"
policyGen 툴은 출력 CR에서 $mcp 의 인스턴스를 worker 로 바꿉니다.
10.3. GitOps ZTP 파이프라인에 사용자 정의 콘텐츠 추가
다음 절차에 따라 GitOps ZTP 파이프라인에 새 콘텐츠를 추가합니다.
프로세스
-
PolicyGenTemplateCR(사용자 정의 리소스)에 대한kustomization.yaml파일이 포함된 디렉터리에source-crs라는 하위 디렉터리를 생성합니다. 다음 예와 같이 사용자 제공 CR을
source-crs하위 디렉터리에 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
source-crs하위 디렉터리는kustomization.yaml파일과 동일한 디렉터리에 있어야 합니다.
source-crs/custom-crs및source-crs/elasticsearch디렉터리에 추가한 콘텐츠에 대한 참조를 포함하도록 필요한PolicyGenTemplateCR을 업데이트합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP Argo CD 정책 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다. 변경된
PolicyGenTemplate을 포함하도록ClusterGroupUpgradeCR을 업데이트하고cgu-test.yaml로 저장합니다. 다음 예제는 생성된cgu-test.yaml파일을 보여줍니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 업데이트된
ClusterGroupUpgradeCR을 적용합니다.oc apply -f cgu-test.yaml
$ oc apply -f cgu-test.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
다음 명령을 실행하여 업데이트가 성공했는지 확인합니다.
oc get cgu -A
$ oc get cgu -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME AGE STATE DETAILS ztp-clusters custom-source-cr 6s InProgress Remediating non-compliant policies ztp-install cluster1 19h Completed All clusters are compliant with all the managed policies
NAMESPACE NAME AGE STATE DETAILS ztp-clusters custom-source-cr 6s InProgress Remediating non-compliant policies ztp-install cluster1 19h Completed All clusters are compliant with all the managed policiesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.4. PolicyGenTemplate CR에 대한 정책 준수 평가 시간 초과 구성
hub 클러스터에 설치된 RHACM(Red Hat Advanced Cluster Management)을 사용하여 관리 클러스터가 적용된 정책을 준수하는지 여부를 모니터링하고 보고합니다. RHACM은 정책 템플릿을 사용하여 사전 정의된 정책 컨트롤러 및 정책을 적용합니다. 정책 컨트롤러는 Kubernetes CRD(사용자 정의 리소스 정의) 인스턴스입니다.
PolicyGenTemplate CR(사용자 정의 리소스)을 사용하여 기본 정책 평가 간격을 덮어쓸 수 있습니다. RHACM이 적용된 클러스터 정책을 다시 평가하기 전에 ConfigurationPolicy CR이 정책 준수 또는 비준수 상태에 있을 수 있는 기간을 정의하는 기간을 구성합니다.
GitOps ZTP(ZTP) 정책 생성기는 사전 정의된 정책 평가 간격을 사용하여 ConfigurationPolicy CR 정책을 생성합니다. 비준수 상태의 기본값은 10초입니다. 규정 준수 상태의 기본값은 10분입니다. 평가 간격을 비활성화하려면 값을 never 로 설정합니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 허브 클러스터에 로그인했습니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다.
프로세스
PolicyGenTemplateCR의 모든 정책에 대한 평가 간격을 구성하려면spec필드에evaluationInterval를 추가한 다음 적절한준수및비준수값을 설정합니다. 예를 들면 다음과 같습니다.spec: evaluationInterval: compliant: 30m noncompliant: 20sspec: evaluationInterval: compliant: 30m noncompliant: 20sCopy to Clipboard Copied! Toggle word wrap Toggle overflow PolicyGenTemplateCR에서spec.sourceFiles오브젝트의 평가 간격을 구성하려면sourceFiles필드에evaluationInterval을 추가합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Git 리포지토리에서
PolicyGenTemplateCR 파일을 커밋하고 변경 사항을 내보냅니다.
검증
관리형 spoke 클러스터 정책이 예상 간격으로 모니터링되는지 확인합니다.
-
관리 클러스터에서
cluster-admin권한이 있는 사용자로 로그인합니다. open-cluster-management-agent-addon네임스페이스에서 실행 중인 Pod를 가져옵니다. 다음 명령을 실행합니다.oc get pods -n open-cluster-management-agent-addon
$ oc get pods -n open-cluster-management-agent-addonCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME READY STATUS RESTARTS AGE config-policy-controller-858b894c68-v4xdb 1/1 Running 22 (5d8h ago) 10d
NAME READY STATUS RESTARTS AGE config-policy-controller-858b894c68-v4xdb 1/1 Running 22 (5d8h ago) 10dCopy to Clipboard Copied! Toggle word wrap Toggle overflow config-policy-controllerPod에 대한 로그에서 적용된 정책이 예상 간격으로 평가되고 있는지 확인합니다.oc logs -n open-cluster-management-agent-addon config-policy-controller-858b894c68-v4xdb
$ oc logs -n open-cluster-management-agent-addon config-policy-controller-858b894c68-v4xdbCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
2022-05-10T15:10:25.280Z info configuration-policy-controller controllers/configurationpolicy_controller.go:166 Skipping the policy evaluation due to the policy not reaching the evaluation interval {"policy": "compute-1-config-policy-config"} 2022-05-10T15:10:25.280Z info configuration-policy-controller controllers/configurationpolicy_controller.go:166 Skipping the policy evaluation due to the policy not reaching the evaluation interval {"policy": "compute-1-common-compute-1-catalog-policy-config"}2022-05-10T15:10:25.280Z info configuration-policy-controller controllers/configurationpolicy_controller.go:166 Skipping the policy evaluation due to the policy not reaching the evaluation interval {"policy": "compute-1-config-policy-config"} 2022-05-10T15:10:25.280Z info configuration-policy-controller controllers/configurationpolicy_controller.go:166 Skipping the policy evaluation due to the policy not reaching the evaluation interval {"policy": "compute-1-common-compute-1-catalog-policy-config"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.5. 검증기 정보 정책을 사용하여 GitOps ZTP 클러스터 배포 완료 신호 전송
GitOps ZTP(ZTP) 설치 및 배포된 클러스터의 구성이 완료된 경우 신호를 알리는 검증기 정보를 생성합니다. 이 정책은 단일 노드 OpenShift 클러스터, 3-노드 클러스터 및 표준 클러스터의 배포에 사용할 수 있습니다.
프로세스
소스 파일
validatorCRs/informDuValidator.yaml을 포함하는 독립 실행형PolicyGenTemplateCR(사용자 정의 리소스)을 생성합니다. 각 클러스터 유형에 대해 하나의 독립 실행형PolicyGenTemplateCR만 있으면 됩니다. 예를 들어 이 CR은 단일 노드 OpenShift 클러스터에 대한 검증기 정보 정책을 적용합니다.single-node 클러스터 검증기 정보 정책 CR의 예 (group-du-sno-validator-ranGen.yaml)
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
PolicyGenTemplates오브젝트의 이름입니다. 이 이름은 요청된네임스페이스에생성된placementBinding,placementRule및정책의일부로 사용됩니다.- 2
- 이 값은
PolicyGenTemplates그룹에 사용된네임스페이스와 일치해야 합니다. - 3
bindingRules에 정의된group-du-*레이블은 siteConfig 파일에있어야 합니다.- 4
bindingExcludedRules에 정의된 레이블은'ztp-done:'이어야 합니다.ztp-done레이블은 토폴로지 Aware Lifecycle Manager와의 조정에 사용됩니다.- 5
MCP는 소스 파일validatorCRs/informDuValidator.yaml에 사용되는MachineConfigPool오브젝트를 정의합니다. 단일 노드와 3-노드 클러스터 배포의 경우master이고 표준 클러스터 배포의 경우worker여야 합니다.- 6
- 선택 사항: 기본값은
inform입니다. - 7
- 이 값은 생성된 RHACM 정책의 이름으로 사용됩니다. 단일 노드 예에 대해 생성된 검증 검증 정책은
group-du-sno-validator-du-policy입니다.
-
Git 리포지토리에서
PolicyGenTemplateCR 파일을 커밋하고 변경 사항을 내보냅니다.
10.6. PolicyGenTemplates CR을 사용하여 전원 상태 구성
대기 시간이 짧고 고성능 에지 배포를 위해 C-state 및 P-state를 비활성화하거나 제한해야 합니다. 이 구성을 사용하면 CPU가 일정한 빈도로 실행되며 일반적으로 최대 turbo 빈도입니다. 이렇게 하면 CPU가 항상 최대 속도로 실행되므로 높은 성능과 대기 시간이 단축됩니다. 이로 인해 워크로드에 대한 최적의 대기 시간이 발생합니다. 그러나 이는 또한 가장 높은 전력 소비를 초래하며, 이는 모든 워크로드에 필요하지 않을 수 있습니다.
워크로드는 높은 성능 및 낮은 대기 시간을 위해 C-state 및 P-state 설정을 비활성화해야 하는 중요한 워크로드로 분류할 수 있지만 중요하지 않은 워크로드는 C-state 및 P-state 설정을 사용하여 일부 대기 시간 및 성능을 저하시킵니다. ZTP(ZTP)를 사용하여 다음 세 가지 전원 상태를 구성할 수 있습니다.
- 고성능 모드는 가장 높은 전력 소비에서 매우 낮은 대기 시간을 제공합니다.
- 성능 모드는 비교적 높은 전력 소비로 짧은 대기 시간을 제공합니다.
- 전력 절감은 대기 시간이 증가하여 전력 소비를 줄일 수 있습니다.
기본 구성은 대기 시간이 짧은 성능 모드입니다.
PolicyGenTemplate CR(사용자 정의 리소스)을 사용하면 ztp-site-generate 컨테이너의 GitOps 플러그인과 함께 제공된 기본 소스 CR에 추가 구성 세부 정보를 오버레이할 수 있습니다.
group-du-sno-ranGen.yaml 의 PolicyGenTemplate CR을 기반으로 생성된 PerformanceProfile CR의 workloadHints 필드를 업데이트하여 전원 상태를 구성합니다.
다음과 같은 일반적인 사전 요구 사항은 세 가지 전원 상태를 모두 구성하는 데 적용됩니다.
사전 요구 사항
- 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 Argo CD의 소스 리포지토리로 정의해야 합니다.
- " GitOps ZTP 사이트 구성 리포지토리 준비"에 설명된 절차를 수행했습니다.
10.6.1. PolicyGenTemplate CR을 사용하여 성능 모드 구성
이 예제에 따라 group-du-sno-ranGen.yaml 의 PolicyGenTemplate CR을 기반으로 생성된 PerformanceProfile CR의 workloadHints 필드를 업데이트하여 성능 모드를 설정합니다.
성능 모드는 비교적 높은 전력 소비로 짧은 대기 시간을 제공합니다.
사전 요구 사항
- "낮은 대기 시간과 고성능을 위해 호스트 펌웨어 구성"의 지침에 따라 성능 관련 설정으로 BIOS를 구성했습니다.
프로세스
다음과 같이
out/argocd/example/policygentemplates에서group-du-sno-ranGen.yaml참조 파일에서PerformanceProfile의PolicyGenTemplate항목을 업데이트합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP Argo CD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
10.6.2. PolicyGenTemplate CR을 사용하여 고성능 모드 구성
다음 예제에서는 group-du-sno-ranGen.yaml 의 PolicyGenTemplate CR을 기반으로 생성된 PerformanceProfile CR의 workloadHints 필드를 업데이트하여 고성능 모드를 설정합니다.
고성능 모드는 가장 높은 전력 소비에서 매우 짧은 대기 시간을 제공합니다.
사전 요구 사항
- "낮은 대기 시간과 고성능을 위해 호스트 펌웨어 구성"의 지침에 따라 성능 관련 설정으로 BIOS를 구성했습니다.
프로세스
다음과 같이
out/argocd/example/policygentemplates에서group-du-sno-ranGen.yaml참조 파일에서PerformanceProfile의PolicyGenTemplate항목을 업데이트합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP Argo CD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
10.6.3. PolicyGenTemplate CR을 사용하여 전원 저장 모드 구성
다음 예제에서는 group-du-sno-ranGen.yaml 의 PolicyGenTemplate CR을 기반으로 생성된 PerformanceProfile CR의 workloadHints 필드를 업데이트하여 전원 저장 모드를 설정합니다.
절전 모드는 대기 시간이 증가하여 전력 소비를 줄입니다.
사전 요구 사항
- BIOS에서 C-states 및 OS 제어 P-states를 활성화했습니다.
프로세스
다음과 같이
out/argocd/example/policygentemplates에서group-du-sno-ranGen.yaml참조 파일에서PerformanceProfile의PolicyGenTemplate항목을 업데이트합니다. 추가 커널 인수 오브젝트를 통해 전원 저장 모드에 대한 CPU governor를 구성하는 것이 좋습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 그러나
schedutilgovernor를 사용하는 것이 좋습니다. 그러나 사용 가능한 다른 governor에는온디맨드및전원 세이프가 포함됩니다.
-
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP Argo CD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
검증
다음 명령을 사용하여 식별된 노드 목록에서 배포된 클러스터에서 작업자 노드를 선택합니다.
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 노드에 로그인합니다.
oc debug node/<node-name>
$ oc debug node/<node-name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow &
lt;node-name>을 전원 상태를 확인할 노드의 이름으로 바꿉니다.디버그 쉘 내에서
/host를 root 디렉터리로 설정합니다. 디버그 Pod는 Pod 내의/host에 호스트의 루트 파일 시스템을 마운트합니다. root 디렉토리를/host로 변경하면 다음 예와 같이 호스트의 실행 경로에 포함된 바이너리를 실행할 수 있습니다.chroot /host
# chroot /hostCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 적용된 전원 상태를 확인합니다.
cat /proc/cmdline
# cat /proc/cmdlineCopy to Clipboard Copied! Toggle word wrap Toggle overflow
예상 출력
-
절전 모드의 경우
intel_pstate=passive입니다.
10.6.4. 전원 비용 절감 극대화
최대 CPU 빈도를 제한하면 최대 전력 절감이 권장됩니다. 최대 CPU 빈도를 제한하지 않고 중요하지 않은 워크로드 CPU에서 C 상태를 활성화하면 중요한 CPU의 빈도를 높임으로써 전력 절감이 거의 발생하지 않습니다.
sysfs 플러그인 필드를 업데이트하여 전력 절감을 극대화하고 참조 구성에 대한 TunedPerformancePatch CR의 max_perf_pct 에 대한 적절한 값을 설정합니다. group-du-sno-ranGen.yaml 을 기반으로 하는 이 예제에서는 최대 CPU 빈도를 제한하는 절차를 설명합니다.
사전 요구 사항
- " PolicyGenTemplate CR 사용으로 전원 절약 모드"에 설명된 대로 전원 절감 모드를 구성했습니다.
프로세스
group-du-sno-ranGen.yaml참조 파일에서TunedPerformancePatch의PolicyGenTemplate항목을out/argocd/example/policygentemplates에서 업데이트합니다. 전원 절감을 극대화하려면 다음 예와 같이max_perf_pct를 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
max_perf_pct는cpufreq드라이버가 지원되는 최대 CPU 빈도의 백분율로 설정할 수 있는 최대 빈도를 제어합니다. 이 값은 모든 CPU에 적용됩니다./sys/devices/system/cpu/cpu0/cpufreq/cpuinfo_max_freq에서 지원되는 최대 빈도를 확인할 수 있습니다. 시작점으로 모든 CPU를 모든코어frequency로 제한하는 백분율로 사용할 수 있습니다.모든 코어의frequency는 코어가 완전히 비어 있을 때 모든 코어가 실행되는 빈도입니다.
참고전력 절감을 극대화하려면 더 낮은 가치를 설정하십시오.
max_perf_pct에 대한 더 낮은 값을 설정하면 최대 CPU 빈도가 제한되므로 전력 소비가 줄어들지만 잠재적으로 성능에 영향을 미칠 수 있습니다. 다양한 값을 실험하고 시스템의 성능 및 전력 소비를 모니터링하여 사용 사례에 가장 적합한 설정을 찾습니다.-
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP Argo CD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
10.7. PolicyGenTemplate CR을 사용하여 LVM 스토리지 구성
ZTP(ZTP)를 사용하여 배포하는 관리형 클러스터에 대해 LVM(Logical Volume Manager) 스토리지를 구성할 수 있습니다.
HTTP 전송과 함께 PTP 이벤트 또는 베어 메탈 하드웨어 이벤트를 사용할 때 LVM 스토리지를 사용하여 이벤트 서브스크립션을 유지합니다.
분산 단위로 로컬 볼륨을 사용하는 영구 스토리지에 Local Storage Operator를 사용합니다.
사전 요구 사항
-
OpenShift CLI(
oc)를 설치합니다. -
cluster-admin권한이 있는 사용자로 로그인합니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성합니다.
프로세스
새 관리 클러스터에 대해 LVM 스토리지를 구성하려면
common-ranGen.yaml파일의spec.sourceFiles에 다음 YAML을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고스토리지 LVMO 서브스크립션은 더 이상 사용되지 않습니다. 향후 OpenShift Container Platform 릴리스에서는 스토리지 LVMO 서브스크립션을 사용할 수 없습니다. 대신 Storage LVMS 서브스크립션을 사용해야 합니다.
OpenShift Container Platform 4.15에서는 LVMO 서브스크립션 대신 스토리지 LVMS 서브스크립션을 사용할 수 있습니다. LVMS 서브스크립션에는
common-ranGen.yaml파일의 수동 덮어쓰기가 필요하지 않습니다. 스토리지 LVMS 서브스크립션을 사용하려면common-ranGen.yaml파일의spec.sourceFiles에 다음 YAML을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 특정 그룹 또는 개별 사이트 구성 파일의
spec.sourceFiles에LVMClusterCR을 추가합니다. 예를 들어group-du-sno-ranGen.yaml파일에서 다음을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 이 예제 구성은 OpenShift Container Platform이 설치된 디스크를 제외하고 사용 가능한 모든 장치가 포함된 볼륨 그룹( Cryostat1)을 생성합니다.
thin-pool 논리 볼륨도 생성됩니다.
- 기타 필요한 변경 사항 및 파일을 사용자 지정 사이트 리포지토리와 병합합니다.
-
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 사이트 구성 리포지토리로 변경 사항을 내보내 GitOps ZTP를 사용하여 새 사이트에 LVM 스토리지를 배포합니다.
10.8. PolicyGenTemplate CR을 사용하여 PTP 이벤트 구성
GitOps ZTP 파이프라인을 사용하여 HTTP 또는 AMQP 전송을 사용하는 PTP 이벤트를 구성할 수 있습니다.
HTTP 전송은 PTP 및 베어 메탈 이벤트의 기본 전송입니다. 가능한 경우 PTP 및 베어 메탈 이벤트에 AMQP 대신 HTTP 전송을 사용합니다. AMQ Interconnect는 2024년 6월 30일부터 EOL입니다. AMQ Interconnect의 ELS(Extended Life Cycle Support)는 2029년 11월 29일에 종료됩니다. 자세한 내용은 Red Hat AMQ Interconnect 지원 상태를 참조하십시오.
10.8.1. HTTP 전송을 사용하는 PTP 이벤트 구성
ZTP(ZTP) 파이프라인으로 배포하는 관리형 클러스터에서 HTTP 전송을 사용하는 PTP 이벤트를 구성할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 로그인했습니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다.
프로세스
요구 사항에 따라
group-du-3node-ranGen.yaml,group-du-sno-ranGen.yaml또는group-du-standard-ranGen.yaml파일에 다음PolicyGenTemplate변경 사항을 적용합니다..sourceFiles에서 전송 호스트를 구성하는PtpOperatorConfigCR 파일을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고OpenShift Container Platform 4.13 이상에서는 PTP 이벤트와 함께 HTTP 전송을 사용할 때
PtpOperatorConfig리소스에서transportHost필드를 설정할 필요가 없습니다.PTP 클럭 유형 및 인터페이스에 대해
linuxptp및phc2sys를 구성합니다. 예를 들어 다음 스탠자를.sourceFiles에 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 요구 사항에 따라
PtpConfigMaster.yaml또는PtpConfigSlave.yaml일 수 있습니다.group-du-sno-ranGen.yaml또는group-du-3node-ranGen.yaml을 기반으로 하는 구성의 경우PtpConfigSlave.yaml을 사용합니다. - 2
- 장치별 인터페이스 이름입니다.
- 3
- PTP 빠른 이벤트를 활성화하려면
.spec.sourceFiles.spec.profile의ptp4lOpts에--summary_interval -4값을 추가해야 합니다. - 4
- 필수
phc2sysOpts값.-m은 메시지를stdout에 출력합니다.linuxptp-daemonDaemonSet은 로그를 구문 분석하고 Prometheus 지표를 생성합니다. - 5
- 선택 사항:
ptpClockThreshold스탠자가 없으면ptpClockThreshold필드에 기본값이 사용됩니다. 스탠자는 기본ptpClockThreshold값을 표시합니다.ptpClockThreshold값은 PTP 이벤트가 트리거되기 전에 PTP 마스터 클록의 연결이 해제된 후의 시간을 구성합니다.holdOverTimeout은 PTP 마스터 클록의 연결이 끊어지면 PTP 클럭 이벤트 상태가 FreeRUN으로 변경되기 전의 시간(초)입니다.maxOffsetThreshold및minOffsetThreshold설정은CLOCK_REALTIME(phc2sys) 또는 master 오프셋(ptp4l)의 값과 비교하는 오프셋 값을 나노초로 구성합니다.ptp4l또는phc2sys오프셋 값이 이 범위를 벗어나는 경우 PTP 클럭 상태가 FreeRUN으로설정됩니다. 오프셋 값이 이 범위 내에 있으면 PTP 클럭 상태가LOCKED로 설정됩니다.
- 기타 필요한 변경 사항 및 파일을 사용자 지정 사이트 리포지토리와 병합합니다.
- GitOps ZTP를 사용하여 새 사이트에 PTP 빠른 이벤트를 배포하려면 사이트 구성 리포지토리로 변경 사항을 푸시합니다.
10.8.2. AMQP 전송을 사용하는 PTP 이벤트 구성
ZTP(ZTP) 파이프라인으로 배포하는 관리 클러스터에서 AMQP 전송을 사용하는 PTP 이벤트를 구성할 수 있습니다.
HTTP 전송은 PTP 및 베어 메탈 이벤트의 기본 전송입니다. 가능한 경우 PTP 및 베어 메탈 이벤트에 AMQP 대신 HTTP 전송을 사용합니다. AMQ Interconnect는 2024년 6월 30일부터 EOL입니다. AMQ Interconnect의 ELS(Extended Life Cycle Support)는 2029년 11월 29일에 종료됩니다. 자세한 내용은 Red Hat AMQ Interconnect 지원 상태를 참조하십시오.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 로그인했습니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다.
프로세스
common-ranGen.yaml파일의.spec.sourceFiles에 다음 YAML을 추가하여 AMQP Operator를 구성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 요구 사항에 따라
group-du-3node-ranGen.yaml,group-du-sno-ranGen.yaml또는group-du-standard-ranGen.yaml파일에 다음PolicyGenTemplate변경 사항을 적용합니다..sourceFiles에서 AMQ 전송 호스트를config-policy에 구성하는PtpOperatorConfigCR 파일을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow PTP 클럭 유형 및 인터페이스에 대해
linuxptp및phc2sys를 구성합니다. 예를 들어 다음 스탠자를.sourceFiles에 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 요구 사항에 따라
PtpConfigMaster.yaml또는PtpConfigSlave.yaml일 수 있습니다.group-du-sno-ranGen.yaml또는group-du-3node-ranGen.yaml을 기반으로 하는 구성의 경우PtpConfigSlave.yaml을 사용합니다. - 2
- 장치별 인터페이스 이름입니다.
- 3
- PTP 빠른 이벤트를 활성화하려면
.spec.sourceFiles.spec.profile의ptp4lOpts에--summary_interval -4값을 추가해야 합니다. - 4
- 필수
phc2sysOpts값.-m은 메시지를stdout에 출력합니다.linuxptp-daemonDaemonSet은 로그를 구문 분석하고 Prometheus 지표를 생성합니다. - 5
- 선택 사항:
ptpClockThreshold스탠자가 없으면ptpClockThreshold필드에 기본값이 사용됩니다. 스탠자는 기본ptpClockThreshold값을 표시합니다.ptpClockThreshold값은 PTP 이벤트가 트리거되기 전에 PTP 마스터 클록의 연결이 해제된 후의 시간을 구성합니다.holdOverTimeout은 PTP 마스터 클록의 연결이 끊어지면 PTP 클럭 이벤트 상태가 FreeRUN으로 변경되기 전의 시간(초)입니다.maxOffsetThreshold및minOffsetThreshold설정은CLOCK_REALTIME(phc2sys) 또는 master 오프셋(ptp4l)의 값과 비교하는 오프셋 값을 나노초로 구성합니다.ptp4l또는phc2sys오프셋 값이 이 범위를 벗어나는 경우 PTP 클럭 상태가 FreeRUN으로설정됩니다. 오프셋 값이 이 범위 내에 있으면 PTP 클럭 상태가LOCKED로 설정됩니다.
특정 사이트 YAML 파일에 다음
PolicyGenTemplate변경 사항을 적용합니다(예:example-sno-site.yaml)..sourceFiles에서 AMQ 라우터를config-policy에 구성하는InterconnectCR 파일을 추가합니다.- fileName: AmqInstance.yaml policyName: "config-policy"
- fileName: AmqInstance.yaml policyName: "config-policy"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- 기타 필요한 변경 사항 및 파일을 사용자 지정 사이트 리포지토리와 병합합니다.
- GitOps ZTP를 사용하여 새 사이트에 PTP 빠른 이벤트를 배포하려면 사이트 구성 리포지토리로 변경 사항을 푸시합니다.
10.9. PolicyGenTemplate CR을 사용하여 베어 메탈 이벤트 구성
GitOps ZTP 파이프라인을 사용하여 HTTP 또는 AMQP 전송을 사용하는 베어 메탈 이벤트를 구성할 수 있습니다.
HTTP 전송은 PTP 및 베어 메탈 이벤트의 기본 전송입니다. 가능한 경우 PTP 및 베어 메탈 이벤트에 AMQP 대신 HTTP 전송을 사용합니다. AMQ Interconnect는 2024년 6월 30일부터 EOL입니다. AMQ Interconnect의 ELS(Extended Life Cycle Support)는 2029년 11월 29일에 종료됩니다. 자세한 내용은 Red Hat AMQ Interconnect 지원 상태를 참조하십시오.
10.9.1. HTTP 전송을 사용하는 베어 메탈 이벤트 구성
ZTP(ZTP) 파이프라인으로 배포하는 관리형 클러스터에서 HTTP 전송을 사용하는 베어 메탈 이벤트를 구성할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 로그인했습니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다.
프로세스
common-ranGen.yaml파일의spec.sourceFiles에 다음 YAML을 추가하여 Bare Metal Event Relay Operator를 구성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 특정 그룹 구성 파일의
spec.sourceFiles에HardwareEventCR을 추가합니다(예:group-du-sno-ranGen.yaml파일).Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 각 BMC(Baseboard Management Controller)에는 단일
HardwareEventCR만 필요합니다.
참고OpenShift Container Platform 4.13 이상에서는 베어 메탈 이벤트와 함께 HTTP 전송을 사용할 때
HardwareEventCR(사용자 정의 리소스)에서transportHost필드를 설정할 필요가 없습니다.- 기타 필요한 변경 사항 및 파일을 사용자 지정 사이트 리포지토리와 병합합니다.
- 변경 사항을 사이트 구성 리포지토리로 내보내 GitOps ZTP가 있는 새 사이트에 베어 메탈 이벤트를 배포합니다.
다음 명령을 실행하여 Redfish 보안을 생성합니다.
oc -n openshift-bare-metal-events create secret generic redfish-basic-auth \ --from-literal=username=<bmc_username> --from-literal=password=<bmc_password> \ --from-literal=hostaddr="<bmc_host_ip_addr>"
$ oc -n openshift-bare-metal-events create secret generic redfish-basic-auth \ --from-literal=username=<bmc_username> --from-literal=password=<bmc_password> \ --from-literal=hostaddr="<bmc_host_ip_addr>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.9.2. AMQP 전송을 사용하는 베어 메탈 이벤트 구성
ZTP(ZTP) 파이프라인으로 배포하는 관리 클러스터에서 AMQP 전송을 사용하는 베어 메탈 이벤트를 구성할 수 있습니다.
HTTP 전송은 PTP 및 베어 메탈 이벤트의 기본 전송입니다. 가능한 경우 PTP 및 베어 메탈 이벤트에 AMQP 대신 HTTP 전송을 사용합니다. AMQ Interconnect는 2024년 6월 30일부터 EOL입니다. AMQ Interconnect의 ELS(Extended Life Cycle Support)는 2029년 11월 29일에 종료됩니다. 자세한 내용은 Red Hat AMQ Interconnect 지원 상태를 참조하십시오.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 로그인했습니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다.
프로세스
AMQ Interconnect Operator 및 Bare Metal Event Relay Operator를 구성하려면
common-ranGen.yaml파일의spec.sourceFiles에 다음 YAML을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 사이트 구성 파일의
.spec.sourceFiles에InterconnectCR을 추가합니다(예:example-sno-site.yaml파일).- fileName: AmqInstance.yaml policyName: "config-policy"
- fileName: AmqInstance.yaml policyName: "config-policy"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 특정 그룹 구성 파일의
spec.sourceFiles에HardwareEventCR을 추가합니다(예:group-du-sno-ranGen.yaml파일).Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
transportHostURL은 기존 AMQ Interconnect CR이름과네임스페이스로 구성됩니다. 예를 들어transportHost: "amqp://amq-router.amq-router.svc.cluster.local"에서 AMQ 상호 연결이름과네임스페이스는 모두amq-router로 설정됩니다.
참고각 BMC(Baseboard Management Controller)에는 단일
HardwareEvent리소스만 필요합니다.-
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 사이트 구성 리포지토리로 변경 사항을 푸시하여 GitOps ZTP를 사용하여 베어 메탈 이벤트 모니터링을 새 사이트에 배포합니다. 다음 명령을 실행하여 Redfish 보안을 생성합니다.
oc -n openshift-bare-metal-events create secret generic redfish-basic-auth \ --from-literal=username=<bmc_username> --from-literal=password=<bmc_password> \ --from-literal=hostaddr="<bmc_host_ip_addr>"
$ oc -n openshift-bare-metal-events create secret generic redfish-basic-auth \ --from-literal=username=<bmc_username> --from-literal=password=<bmc_password> \ --from-literal=hostaddr="<bmc_host_ip_addr>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.10. 이미지 로컬 캐싱을 위해 Image Registry Operator 구성
OpenShift Container Platform은 로컬 레지스트리를 사용하여 이미지 캐싱을 관리합니다. 에지 컴퓨팅 사용 사례에서 클러스터는 중앙 집중식 이미지 레지스트리와 통신할 때 대역폭 제한의 영향을 받는 경우가 많기 때문에 이미지 다운로드 시간이 길어질 수 있습니다.
초기 배포 시에는 다운로드 시간이 길어지는 것은 불가피합니다. 시간이 지남에 따라 CRI-O에서 예기치 않은 종료의 경우 /var/lib/containers/storage 디렉터리를 지울 위험이 있습니다. 긴 이미지 다운로드 시간을 해결하기 위해ZTP( GitOps Zero Touch Provisioning)를 사용하여 원격 관리 클러스터에 로컬 이미지 레지스트리를 생성할 수 있습니다. 이는 클러스터가 네트워크의 맨 에지에 배포되는 에지 컴퓨팅 시나리오에서 유용합니다.
GitOps ZTP를 사용하여 로컬 이미지 레지스트리를 설정하려면 원격 관리 클러스터를 설치하는 데 사용하는 SiteConfig CR에서 디스크 파티션을 구성해야 합니다. 설치 후 PolicyGenTemplate CR을 사용하여 로컬 이미지 레지스트리를 구성합니다. 그런 다음 GitOps ZTP 파이프라인은 PV(영구 볼륨) 및 PVC(영구 볼륨 클레임) CR을 생성하고 imageregistry 구성을 패치합니다.
로컬 이미지 레지스트리는 사용자 애플리케이션 이미지에만 사용할 수 있으며 OpenShift Container Platform 또는 Operator Lifecycle Manager Operator 이미지에는 사용할 수 없습니다.
10.10.1. siteConfig를 사용하여 디스크 파티션 구성
SiteConfig CR 및 GitOps ZTP(ZTP)를 사용하여 관리 클러스터에 대한 디스크 파티션을 구성합니다. SiteConfig CR의 디스크 파티션 세부 정보는 기본 디스크와 일치해야 합니다.
설치 시 이 절차를 완료해야 합니다.
사전 요구 사항
- Butane을 설치합니다.
프로세스
다음 예제 YAML 파일을 사용하여
storage.bu파일을 생성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
storage.bu를 Ignition 파일로 변환합니다.butane storage.bu
$ butane storage.buCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
{"ignition":{"version":"3.2.0"},"storage":{"disks":[{"device":"/dev/disk/by-path/pci-0000:01:00.0-scsi-0:2:0:0","partitions":[{"label":"var-lib-containers","sizeMiB":0,"startMiB":250000}],"wipeTable":false}],"filesystems":[{"device":"/dev/disk/by-partlabel/var-lib-containers","format":"xfs","mountOptions":["defaults","prjquota"],"path":"/var/lib/containers","wipeFilesystem":true}]},"systemd":{"units":[{"contents":"# # Generated by Butane\n[Unit]\nRequires=systemd-fsck@dev-disk-by\\x2dpartlabel-var\\x2dlib\\x2dcontainers.service\nAfter=systemd-fsck@dev-disk-by\\x2dpartlabel-var\\x2dlib\\x2dcontainers.service\n\n[Mount]\nWhere=/var/lib/containers\nWhat=/dev/disk/by-partlabel/var-lib-containers\nType=xfs\nOptions=defaults,prjquota\n\n[Install]\nRequiredBy=local-fs.target","enabled":true,"name":"var-lib-containers.mount"}]}}{"ignition":{"version":"3.2.0"},"storage":{"disks":[{"device":"/dev/disk/by-path/pci-0000:01:00.0-scsi-0:2:0:0","partitions":[{"label":"var-lib-containers","sizeMiB":0,"startMiB":250000}],"wipeTable":false}],"filesystems":[{"device":"/dev/disk/by-partlabel/var-lib-containers","format":"xfs","mountOptions":["defaults","prjquota"],"path":"/var/lib/containers","wipeFilesystem":true}]},"systemd":{"units":[{"contents":"# # Generated by Butane\n[Unit]\nRequires=systemd-fsck@dev-disk-by\\x2dpartlabel-var\\x2dlib\\x2dcontainers.service\nAfter=systemd-fsck@dev-disk-by\\x2dpartlabel-var\\x2dlib\\x2dcontainers.service\n\n[Mount]\nWhere=/var/lib/containers\nWhat=/dev/disk/by-partlabel/var-lib-containers\nType=xfs\nOptions=defaults,prjquota\n\n[Install]\nRequiredBy=local-fs.target","enabled":true,"name":"var-lib-containers.mount"}]}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow - JSON Pretty Print 와 같은 도구를 사용하여 출력을 JSON 형식으로 변환합니다.
출력을
SiteConfigCR의.spec.clusters.nodes.ignitionConfigOverride필드에 복사합니다.예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고.spec.clusters.nodes.ignitionConfigOverride필드가 없는 경우 생성합니다.
검증
설치 중 또는 설치 후 hub 클러스터에서
BareMetalHost오브젝트가 다음 명령을 실행하여 주석을 표시하는지 확인합니다.oc get bmh -n my-sno-ns my-sno -ojson | jq '.metadata.annotations["bmac.agent-install.openshift.io/ignition-config-overrides"]
$ oc get bmh -n my-sno-ns my-sno -ojson | jq '.metadata.annotations["bmac.agent-install.openshift.io/ignition-config-overrides"]Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
"{\"ignition\":{\"version\":\"3.2.0\"},\"storage\":{\"disks\":[{\"device\":\"/dev/disk/by-id/wwn-0x6b07b250ebb9d0002a33509f24af1f62\",\"partitions\":[{\"label\":\"var-lib-containers\",\"sizeMiB\":0,\"startMiB\":250000}],\"wipeTable\":false}],\"filesystems\":[{\"device\":\"/dev/disk/by-partlabel/var-lib-containers\",\"format\":\"xfs\",\"mountOptions\":[\"defaults\",\"prjquota\"],\"path\":\"/var/lib/containers\",\"wipeFilesystem\":true}]},\"systemd\":{\"units\":[{\"contents\":\"# Generated by Butane\\n[Unit]\\nRequires=systemd-fsck@dev-disk-by\\\\x2dpartlabel-var\\\\x2dlib\\\\x2dcontainers.service\\nAfter=systemd-fsck@dev-disk-by\\\\x2dpartlabel-var\\\\x2dlib\\\\x2dcontainers.service\\n\\n[Mount]\\nWhere=/var/lib/containers\\nWhat=/dev/disk/by-partlabel/var-lib-containers\\nType=xfs\\nOptions=defaults,prjquota\\n\\n[Install]\\nRequiredBy=local-fs.target\",\"enabled\":true,\"name\":\"var-lib-containers.mount\"}]}}""{\"ignition\":{\"version\":\"3.2.0\"},\"storage\":{\"disks\":[{\"device\":\"/dev/disk/by-id/wwn-0x6b07b250ebb9d0002a33509f24af1f62\",\"partitions\":[{\"label\":\"var-lib-containers\",\"sizeMiB\":0,\"startMiB\":250000}],\"wipeTable\":false}],\"filesystems\":[{\"device\":\"/dev/disk/by-partlabel/var-lib-containers\",\"format\":\"xfs\",\"mountOptions\":[\"defaults\",\"prjquota\"],\"path\":\"/var/lib/containers\",\"wipeFilesystem\":true}]},\"systemd\":{\"units\":[{\"contents\":\"# Generated by Butane\\n[Unit]\\nRequires=systemd-fsck@dev-disk-by\\\\x2dpartlabel-var\\\\x2dlib\\\\x2dcontainers.service\\nAfter=systemd-fsck@dev-disk-by\\\\x2dpartlabel-var\\\\x2dlib\\\\x2dcontainers.service\\n\\n[Mount]\\nWhere=/var/lib/containers\\nWhat=/dev/disk/by-partlabel/var-lib-containers\\nType=xfs\\nOptions=defaults,prjquota\\n\\n[Install]\\nRequiredBy=local-fs.target\",\"enabled\":true,\"name\":\"var-lib-containers.mount\"}]}}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 설치 후 단일 노드 OpenShift 디스크 상태를 확인합니다.
다음 명령을 실행하여 단일 노드 OpenShift 노드에서 디버그 세션에 들어갑니다.
이 단계는
<node_name>-debug라는 디버그 Pod를 인스턴스화합니다.oc debug node/my-sno-node
$ oc debug node/my-sno-nodeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 디버그 쉘 내에서
/host를 root 디렉터리로 설정합니다.디버그 Pod는 Pod 내의
/host에 호스트의 루트 파일 시스템을 마운트합니다. root 디렉토리를/host로 변경하면 호스트의 실행 경로에 포함된 바이너리를 실행할 수 있습니다.chroot /host
# chroot /hostCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 사용 가능한 모든 블록 장치에 대한 정보를 나열합니다.
lsblk
# lsblkCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 파일 시스템 디스크 공간 사용량에 대한 정보를 표시합니다.
df -h
# df -hCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.10.2. PolicyGenTemplate CR을 사용하여 이미지 레지스트리 구성
PGT( PolicyGenTemplate ) CR을 사용하여 이미지 레지스트리를 구성하고 imageregistry 구성을 패치하는 데 필요한 CR을 적용합니다.
사전 요구 사항
- 관리 클러스터에 디스크 파티션을 구성했습니다.
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 허브 클러스터에 로그인했습니다. - GitOps ZTP(ZTP)와 함께 사용할 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다.
프로세스
적절한
PolicyGenTemplateCR에서 스토리지 클래스, 영구 볼륨 클레임, 영구 볼륨 및 이미지 레지스트리 구성을 구성합니다. 예를 들어 개별 사이트를 구성하려면example-sno-site.yaml파일에 다음 YAML을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 중요complianceType: mustonlyhavefor the- fileName: ImageRegistryConfig.yaml설정을 설정하지 마십시오. 이로 인해 레지스트리 Pod 배포가 실패할 수 있습니다.-
Git에서
PolicyGenTemplate변경 사항을 커밋한 다음 GitOps ZTP ArgoCD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
검증
다음 단계를 사용하여 관리 클러스터의 로컬 이미지 레지스트리의 오류를 해결합니다.
관리 클러스터에 로그인하는 동안 레지스트리에 성공적으로 로그인했는지 확인합니다. 다음 명령을 실행합니다.
관리 클러스터 이름을 내보냅니다.
cluster=<managed_cluster_name>
$ cluster=<managed_cluster_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터
kubeconfig세부 정보를 가져옵니다.oc get secret -n $cluster $cluster-admin-password -o jsonpath='{.data.password}' | base64 -d > kubeadmin-password-$cluster$ oc get secret -n $cluster $cluster-admin-password -o jsonpath='{.data.password}' | base64 -d > kubeadmin-password-$clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow 클러스터
kubeconfig를 다운로드하여 내보냅니다.oc get secret -n $cluster $cluster-admin-kubeconfig -o jsonpath='{.data.kubeconfig}' | base64 -d > kubeconfig-$cluster && export KUBECONFIG=./kubeconfig-$cluster$ oc get secret -n $cluster $cluster-admin-kubeconfig -o jsonpath='{.data.kubeconfig}' | base64 -d > kubeconfig-$cluster && export KUBECONFIG=./kubeconfig-$clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 관리 클러스터에서 이미지 레지스트리에 대한 액세스를 확인합니다. " registry 액세스"를 참조하십시오.
imageregistry.operator.openshift.io그룹 인스턴스의ConfigCRD가 오류를 보고하지 않는지 확인합니다. 관리 클러스터에 로그인하는 동안 다음 명령을 실행합니다.oc get image.config.openshift.io cluster -o yaml
$ oc get image.config.openshift.io cluster -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터의
PersistentVolumeClaim이 데이터로 채워져 있는지 확인합니다. 관리 클러스터에 로그인하는 동안 다음 명령을 실행합니다.oc get pv image-registry-sc
$ oc get pv image-registry-scCopy to Clipboard Copied! Toggle word wrap Toggle overflow registry*포드가 실행 중이고openshift-image-registry네임스페이스에 있는지 확인합니다.oc get pods -n openshift-image-registry | grep registry*
$ oc get pods -n openshift-image-registry | grep registry*Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
cluster-image-registry-operator-68f5c9c589-42cfg 1/1 Running 0 8d image-registry-5f8987879-6nx6h 1/1 Running 0 8d
cluster-image-registry-operator-68f5c9c589-42cfg 1/1 Running 0 8d image-registry-5f8987879-6nx6h 1/1 Running 0 8dCopy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터의 디스크 파티션이 올바른지 확인합니다.
관리 클러스터에 대한 디버그 쉘을 엽니다.
oc debug node/sno-1.example.com
$ oc debug node/sno-1.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow lsblk를 실행하여 호스트 디스크 파티션을 확인합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
/var/imageregistry는 디스크가 올바르게 분할되었음을 나타냅니다.
10.11. PolicyGenTemplate CR에서 허브 템플릿 사용
토폴로지 Aware Lifecycle Manager는 GitOps ZTP(ZTP)와 함께 사용되는 구성 정책에서 partial Red Hat Advanced Cluster Management(RHACM) 허브 클러스터 템플릿 기능을 지원합니다.
Hub-side 클러스터 템플릿을 사용하면 대상 클러스터에 동적으로 사용자 지정할 수 있는 구성 정책을 정의할 수 있습니다. 이렇게 하면 similiar 구성이 있지만 값이 다른 많은 클러스터에 대해 별도의 정책을 만들 필요가 줄어듭니다.
정책 템플릿은 정책이 정의된 네임스페이스와 동일한 네임스페이스로 제한됩니다. 즉, 정책이 생성되는 동일한 네임스페이스의 hub 템플릿에서 참조되는 오브젝트를 생성해야 합니다.
다음과 같은 지원되는 허브 템플릿 함수는 TALM을 사용하여 GitOps ZTP에서 사용할 수 있습니다.
fromConfigmap은 이름이 지정된ConfigMap리소스에 제공된 데이터 키 값을 반환합니다.참고ConfigMapCR에는 1MiB 크기 제한이 있습니다.ConfigMapCR의 유효 크기는last-applied-configuration주석으로 추가로 제한됩니다.last-applied-configuration제한을 방지하려면 템플릿ConfigMap에 다음 주석을 추가합니다.argocd.argoproj.io/sync-options: Replace=true
argocd.argoproj.io/sync-options: Replace=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
base64enc는 입력 문자열의 base64 인코딩 값을 반환합니다. -
base64dec은 base64로 인코딩된 입력 문자열의 디코딩된 값을 반환합니다. -
들여쓰기는 추가된 들여쓰기 공백을 사용하여 입력 문자열을 반환합니다. -
autoindent는 상위 템플릿에 사용된 간격에 따라 추가 들여쓰기가 포함된 입력 문자열을 반환합니다. -
ToInt입력 값의 정수 값을 캐스팅하고 반환합니다. -
toBool입력 문자열을 부울 값으로 변환하고 부울을 반환합니다.
GitOps ZTP에서 다양한 오픈 소스 커뮤니티 기능 도 사용할 수 있습니다.
10.11.1. hub 템플릿 예
다음 코드 예제는 유효한 허브 템플릿입니다. 이러한 각 템플릿은 기본 네임스페이스에 test-config 라는 이름으로 ConfigMap CR의 값을 반환합니다.
common-key키를 사용하여 값을 반환합니다.{{hub fromConfigMap "default" "test-config" "common-key" hub}}{{hub fromConfigMap "default" "test-config" "common-key" hub}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow .ManagedClusterName필드의 연결된 값과-name문자열을 사용하여 문자열을 반환합니다.{{hub fromConfigMap "default" "test-config" (printf "%s-name" .ManagedClusterName) hub}}{{hub fromConfigMap "default" "test-config" (printf "%s-name" .ManagedClusterName) hub}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow .ManagedClusterName필드의 연결된 값 및 문자열-name:에서 부울 값을 캐스팅하고 반환합니다.{{hub fromConfigMap "default" "test-config" (printf "%s-name" .ManagedClusterName) | toBool hub}}{{hub fromConfigMap "default" "test-config" (printf "%s-name" .ManagedClusterName) | toBool hub}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow .ManagedClusterName필드의 연결된 값 및 문자열-name:에서 정수 값을 캐스팅하고 반환합니다.{{hub (printf "%s-name" .ManagedClusterName) | fromConfigMap "default" "test-config" | toInt hub}}{{hub (printf "%s-name" .ManagedClusterName) | fromConfigMap "default" "test-config" | toInt hub}}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.11.2. 허브 템플릿을 사용하여 PolicyGenTemplate CR에서 그룹 및 사이트 구성 지정
hub 템플릿을 사용하여 관리 클러스터에 적용되는 생성된 정책의 그룹 및 사이트 값을 채우는 방식으로 ConfigMap CR을 사용하여 클러스터의 구성을 관리할 수 있습니다. PGT( PolicyGenTemplate ) CR에서 허브 템플릿을 사용하면 각 사이트에 대해 PolicyGenTemplate CR을 생성할 필요가 없습니다.
사용 사례에 따라 다양한 범주의 플릿으로 클러스터를 그룹화할 수 있습니다(예: 하드웨어 유형 또는 리전). 각 클러스터에는 클러스터가 있는 그룹 또는 그룹에 해당하는 레이블이 있어야 합니다. 다른 ConfigMap CR에서 각 그룹의 구성 값을 관리하는 경우 hub 템플릿을 사용하여 그룹의 모든 클러스터에 변경 사항을 적용하려면 하나의 그룹 PolicyGenTemplate CR만 있으면 됩니다.
다음 예제에서는 3개의 ConfigMap CR과 하나의 그룹 PolicyGenTemplate CR을 사용하여 사이트 구성과 그룹 구성을 하드웨어 유형 및 리전별로 그룹화한 클러스터에 적용하는 방법을 보여줍니다.
fromConfigmap 함수를 사용하면 템플릿 리소스 데이터 키 필드에만 Cryostat 변수를 사용할 수 있습니다. name 및 namespace 필드에는 사용할 수 없습니다.
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 허브 클러스터에 로그인했습니다. - 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성했습니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 GitOps ZTP ArgoCD 애플리케이션의 소스 리포지토리로 정의해야 합니다.
프로세스
그룹 및 사이트 구성이 포함된 세 개의
ConfigMapCR을 생성합니다.하드웨어별 구성을 유지하기 위해
group-hardware-types-configmap이라는ConfigMapCR을 생성합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
ConfigMap이 크기가 1MiB를 초과하는 경우에만argocd.argoproj.io/sync-options주석이 필요합니다.
지역 구성을 유지하기 위해
group-zones-configmap이라는ConfigMapCR을 생성합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 사이트별 구성을 유지하기 위해
site-data-configmap이라는ConfigMapCR을 생성합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
참고각
ConfigMapCR은 그룹PolicyGenTemplateCR에서 생성할 정책과 동일한 네임스페이스에 있어야 합니다.-
Git에서
ConfigMapCR을 커밋한 다음 Argo CD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다. 하드웨어 유형 및 리전 레이블을 클러스터에 적용합니다. 다음 명령은
du-sno-1-zone-1이라는 단일 클러스터에 적용되며, 선택한 레이블은"hardware-type": "hardware-type-1"및"group-du-sno-zone": "zone-1"입니다.oc patch managedclusters.cluster.open-cluster-management.io/du-sno-1-zone-1 --type merge -p '{"metadata":{"labels":{"hardware-type": "hardware-type-1", "group-du-sno-zone": "zone-1"}}}'$ oc patch managedclusters.cluster.open-cluster-management.io/du-sno-1-zone-1 --type merge -p '{"metadata":{"labels":{"hardware-type": "hardware-type-1", "group-du-sno-zone": "zone-1"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow hub 템플릿을 사용하여
ConfigMap오브젝트에서 필요한 데이터를 가져오는 그룹PolicyGenTemplateCR을 생성합니다. 이 예제PolicyGenTemplateCR은spec.bindingRules아래에 나열된 라벨과 일치하는 클러스터에 대해 로깅, VLAN ID, NIC 및 성능 프로필을 구성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고사이트별 구성 값을 검색하려면
.ManagedClusterName필드를 사용합니다. 이는 대상 관리 클러스터의 이름으로 설정된 템플릿 컨텍스트 값입니다.그룹별 구성을 검색하려면
.ManagedClusterLabels필드를 사용합니다. 이는 관리 클러스터 레이블의 값으로 설정된 템플릿 컨텍스트 값입니다.Git에서 사이트
PolicyGenTemplateCR을 커밋하고 ArgoCD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.참고참조된
ConfigMapCR에 대한 후속 변경 사항은 적용된 정책과 자동으로 동기화되지 않습니다. 새ConfigMap변경 사항을 수동으로 동기화하여 기존PolicyGenTemplateCR을 업데이트해야 합니다. "기존 PolicyGenTemplate CR에 새 ConfigMap 변경 동기화"를 참조하십시오.여러 클러스터에 동일한
PolicyGenTemplateCR을 사용할 수 있습니다. 구성이 변경되면 각 클러스터에 대한 구성을 보유하는ConfigMap오브젝트와 관리 클러스터의 레이블을 유지하는 유일한 수정 사항이 있습니다.
10.11.3. 기존 PolicyGenTemplate CR에 새 ConfigMap 변경 사항 동기화
사전 요구 사항
-
OpenShift CLI(
oc)가 설치되어 있습니다. -
cluster-admin권한이 있는 사용자로 허브 클러스터에 로그인했습니다. -
hub 클러스터 템플릿을 사용하여
ConfigMapCR에서 정보를 가져오는PolicyGenTemplateCR을 생성했습니다.
프로세스
-
ConfigMapCR의 콘텐츠를 업데이트하고 hub 클러스터의 변경 사항을 적용합니다. 업데이트된
ConfigMapCR의 콘텐츠를 배포된 정책에 동기화하려면 다음 중 하나를 수행하십시오.옵션 1: 기존 정책을 삭제합니다. rgocd는
PolicyGenTemplateCR을 사용하여 삭제된 정책을 즉시 다시 생성합니다. 예를 들어 다음 명령을 실행합니다.oc delete policy <policy_name> -n <policy_namespace>
$ oc delete policy <policy_name> -n <policy_namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 옵션 2:
ConfigMap을 업데이트할 때마다 다른 값을 사용하여정책에 특수 주석 정책.open-cluster-management.io/trigger-update를 적용합니다. 예를 들면 다음과 같습니다.oc annotate policy <policy_name> -n <policy_namespace> policy.open-cluster-management.io/trigger-update="1"
$ oc annotate policy <policy_name> -n <policy_namespace> policy.open-cluster-management.io/trigger-update="1"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고변경 사항을 적용하려면 업데이트된 정책을 적용해야 합니다. 자세한 내용은 재처리를 위한 특수 주석을 참조하십시오.
선택 사항: 존재하는 경우 정책이 포함된
ClusterGroupUpdateCR을 삭제합니다. 예를 들면 다음과 같습니다.oc delete clustergroupupgrade <cgu_name> -n <cgu_namespace>
$ oc delete clustergroupupgrade <cgu_name> -n <cgu_namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트된
ConfigMap변경 사항에 적용할 정책이 포함된 새ClusterGroupUpdateCR을 생성합니다. 예를 들어cgr-example.yaml파일에 다음 YAML을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트된 정책을 적용합니다.
oc apply -f cgr-example.yaml
$ oc apply -f cgr-example.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11장. 토폴로지 Aware Lifecycle Manager를 사용하여 관리형 클러스터 업데이트
Topology Aware Lifecycle Manager(TALM)를 사용하여 여러 클러스터의 소프트웨어 라이프사이클을 관리할 수 있습니다. TALM은 RHACM(Red Hat Advanced Cluster Management) 정책을 사용하여 대상 클러스터에서 변경 사항을 수행합니다.
11.1. 토폴로지 Aware Lifecycle Manager 구성 정보
Topology Aware Lifecycle Manager(TALM)는 하나 이상의 OpenShift Container Platform 클러스터에 대한 RHACM(Red Hat Advanced Cluster Management) 정책 배포를 관리합니다. 대규모 클러스터 네트워크에서 TALM을 사용하면 제한된 배치로 클러스터에 정책을 단계적으로 롤아웃할 수 있습니다. 이를 통해 업데이트 시 가능한 서비스 중단을 최소화할 수 있습니다. TALM을 사용하면 다음 작업을 제어할 수 있습니다.
- 업데이트의 타이밍
- RHACM 관리 클러스터 수
- 정책을 적용할 관리 클러스터의 하위 세트
- 클러스터의 업데이트 순서
- 클러스터에 적용되는 정책 세트
- 클러스터에 대한 정책 업데이트 순서
- 카나리아 클러스터 할당
단일 노드 OpenShift의 경우 Topology Aware Lifecycle Manager(TALM)는 다음과 같은 기능을 제공합니다.
- 업그레이드하기 전에 배포 백업 생성
- 대역폭이 제한된 클러스터의 이미지 사전 캐싱
TALM은 OpenShift Container Platform y-stream 및 z-stream 업데이트의 오케스트레이션과 y-stream 및 z-streams에 대한 Day-two 작업을 지원합니다.
11.2. 토폴로지 Aware Lifecycle Manager와 함께 사용되는 관리형 정책 정보
TALM( Topology Aware Lifecycle Manager)은 클러스터 업데이트에 RHACM 정책을 사용합니다.
TALM을 사용하여 remediationAction 필드가 알리는 모든 정책 CR의 롤아웃을 관리할 수 있습니다. 지원되는 사용 사례는 다음과 같습니다.
- 정책 CR 수동 사용자 생성
-
PolicyGenTemplateCRD(사용자 정의 리소스 정의)에서 자동으로 생성된 정책
Operator 서브스크립션을 수동 승인으로 업데이트하는 정책의 경우 TALM은 업데이트된 Operator 설치를 승인하는 추가 기능을 제공합니다.
관리 정책에 대한 자세한 내용은 RHACM 설명서의 정책 개요 를 참조하십시오.
PolicyGenTemplate CRD에 대한 자세한 내용은 "policy 및 PolicyGenTemplate 리소스를 사용하여 관리 클러스터 구성"의 " PolicyGenTemplate CRD 설명" 섹션을 참조하십시오.
11.3. 웹 콘솔을 사용하여 토폴로지 Aware Lifecycle Manager 설치
OpenShift Container Platform 웹 콘솔을 사용하여 토폴로지 Aware Lifecycle Manager를 설치할 수 있습니다.
사전 요구 사항
- 최신 버전의 RHACM Operator를 설치합니다.
- 연결이 끊긴 regitry를 사용하여 허브 클러스터를 설정합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다.
프로세스
- OpenShift Container Platform 웹 콘솔에서 Operator → OperatorHub로 이동합니다.
- 사용 가능한 Operator 목록에서 토폴로지 Aware Lifecycle Manager 를 검색한 다음 설치를 클릭합니다.
- 기본 설치 모드 ["기본"] 및 설치된 네임스페이스("openshift-operators")를 계속 선택하여 Operator가 올바르게 설치되었는지 확인합니다.
- 설치를 클릭합니다.
검증
설치에 성공했는지 확인하려면 다음을 수행하십시오.
- Operator → 설치된 Operator 페이지로 이동합니다.
-
Operator가
모든 네임스페이스네임스페이스에 설치되어 있고 해당 상태가Succeeded인지 확인합니다.
Operator가 성공적으로 설치되지 않은 경우 다음을 수행하십시오.
-
Operator → 설치된 Operator 페이지로 이동하여
Status열에 오류 또는 실패가 있는지 점검합니다. -
워크로드 → Pod 페이지로 이동하여 문제를 보고하는
cluster-group-upgrades-controller-managerPod에서 컨테이너의 로그를 확인합니다.
11.4. CLI를 사용하여 토폴로지 인식 라이프사이클 관리자 설치
OpenShift CLI(oc)를 사용하여 Topology Aware Lifecycle Manager(TALM)를 설치할 수 있습니다.
사전 요구 사항
-
OpenShift CLI(
oc)를 설치합니다. - 최신 버전의 RHACM Operator를 설치합니다.
- 연결이 끊긴 레지스트리를 사용하여 허브 클러스터를 설정합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다.
프로세스
서브스크립션CR을 생성합니다.SubscriptionCR을 정의하고 YAML 파일을 저장합니다(예:talm-subscription.yaml):Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
서브스크립션CR을 생성합니다.oc create -f talm-subscription.yaml
$ oc create -f talm-subscription.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
CSV 리소스를 검사하여 설치에 성공했는지 확인합니다.
oc get csv -n openshift-operators
$ oc get csv -n openshift-operatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME DISPLAY VERSION REPLACES PHASE topology-aware-lifecycle-manager.4.15.x Topology Aware Lifecycle Manager 4.15.x Succeeded
NAME DISPLAY VERSION REPLACES PHASE topology-aware-lifecycle-manager.4.15.x Topology Aware Lifecycle Manager 4.15.x SucceededCopy to Clipboard Copied! Toggle word wrap Toggle overflow TALM이 실행 중인지 확인합니다.
oc get deploy -n openshift-operators
$ oc get deploy -n openshift-operatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME READY UP-TO-DATE AVAILABLE AGE openshift-operators cluster-group-upgrades-controller-manager 1/1 1 1 14s
NAMESPACE NAME READY UP-TO-DATE AVAILABLE AGE openshift-operators cluster-group-upgrades-controller-manager 1/1 1 1 14sCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.5. ClusterGroupUpgrade CR 정보
Topology Aware Lifecycle Manager(TALM)는 클러스터 그룹의 ClusterGroupUpgrade CR에서 수정 계획을 빌드합니다. ClusterGroupUpgrade CR에서 다음 사양을 정의할 수 있습니다.
- 그룹의 클러스터
-
ClusterGroupUpgradeCR 차단 - 적용 가능한 관리 정책 목록
- 동시 업데이트 수
- 적용 가능한 카나리아 업데이트
- 업데이트 전후에 수행할 작업
- 업데이트 타이밍
ClusterGroupUpgrade CR의 enable 필드를 사용하여 업데이트 시작 시간을 제어할 수 있습니다. 예를 들어 스케줄링된 유지 관리 기간이 4시간인 경우 enable 필드가 false 로 설정된 ClusterGroupUpgrade CR을 준비할 수 있습니다.
spec.remediationStrategy.timeout 설정을 다음과 같이 구성하여 시간 제한을 설정할 수 있습니다.
spec
remediationStrategy:
maxConcurrency: 1
timeout: 240
spec
remediationStrategy:
maxConcurrency: 1
timeout: 240
batchTimeoutAction 을 사용하여 클러스터에 대한 업데이트가 실패하면 어떤 일이 발생하는지 확인할 수 있습니다. 실패한 클러스터를 계속 건너뛰고 다른 클러스터를 계속 업그레이드하거나 모든 클러스터의 정책 수정을 중지하도록 중단할 수 있습니다. 시간 초과가 경과하면 TALM은 모든 적용 정책을 제거하여 클러스터에 대한 추가 업데이트가 없는지 확인합니다.
변경 사항을 적용하려면 enabled 필드를 true 로 설정합니다.
자세한 내용은 "관리된 클러스터에 업데이트 정책 적용" 섹션을 참조하십시오.
TALM은 지정된 클러스터에 대한 정책 수정을 통해 작동하므로 ClusterGroupUpgrade CR은 여러 조건에 대해 true 또는 false 상태를 보고할 수 있습니다.
TALM이 클러스터 업데이트를 완료한 후 동일한 ClusterGroupUpgrade CR 제어 하에서 클러스터가 다시 업데이트되지 않습니다. 다음과 같은 경우 새 ClusterGroupUpgrade CR을 생성해야 합니다.
- 클러스터를 다시 업데이트해야 하는 경우
-
클러스터가 업데이트 후 알림 정책과
호환되지않는 경우
11.5.1. 클러스터 선택
TALM은 수정 계획을 빌드하고 다음 필드를 기반으로 클러스터를 선택합니다.
-
clusterLabelSelector필드는 업데이트할 클러스터의 레이블을 지정합니다.k8s.io/apimachinery/pkg/apis/meta/v1의 표준 라벨 선택기 목록으로 구성됩니다. 목록의 각 선택기는 레이블 값 쌍 또는 레이블 표현식을 사용합니다. 각 선택기의 일치 항목은clusterSelector필드 및 cluster 필드의 일치 항목과 함께 최종클러스터목록에 추가됩니다. -
cluster필드는 업데이트할 클러스터 목록을 지정합니다. -
canaries필드는 카나리아 업데이트를 위한 클러스터를 지정합니다. -
maxConcurrency필드는 배치에서 업데이트할 클러스터 수를 지정합니다. -
actions필드는 TALM이 업데이트 프로세스를 시작할 때 수행하는beforeEnable작업과 TALM이 각 클러스터에 대한 정책 수정을 완료할 때 수행하는afterCompletion작업을 지정합니다.
clusters , clusterLabelSelector , clusterSelector 필드를 함께 사용하면 클러스터의 결합된 목록을 만들 수 있습니다.
수정 계획은 canaries 필드에 나열된 클러스터로 시작합니다. 각 카나리아 클러스터는 단일 클러스터 배치를 형성합니다.
enabled 필드 가 false로 설정된 샘플 ClusterGroupUpgrade CR
- 1
- 각 클러스터에 대한 정책 수정을 완료할 때 TALM이 수행하는 작업을 지정합니다.
- 2
- 업데이트 프로세스를 시작할 때 TALM이 수행하는 작업을 지정합니다.
- 3
- 업데이트할 클러스터 목록을 정의합니다.
- 4
enable필드는false로 설정됩니다.- 5
- 수정할 사용자 정의 정책 집합을 나열합니다.
- 6
- 클러스터 업데이트의 세부 사항을 정의합니다.
- 7
- 카나리아 업데이트를 위한 클러스터를 정의합니다.
- 8
- 일괄 처리의 최대 동시 업데이트 수를 정의합니다. 수정 배치 수는 카나리아 클러스터 수와 카나리아 클러스터를 제외하고
maxConcurrency값으로 나눈 클러스터 수입니다. 이미 모든 관리 정책과 호환되는 클러스터는 수정 계획에서 제외됩니다. - 9
- 클러스터 선택을 위한 매개변수를 표시합니다.
- 10
- 일괄 처리가 시간 초과되는 경우 발생하는 작업을 제어합니다. 가능한 값은
abort또는continue입니다. 지정되지 않은 경우 기본값은계속됩니다. - 11
- 업데이트 상태에 대한 정보를 표시합니다.
- 12
ClustersSelected조건은 선택한 모든 클러스터가 유효한 것으로 표시됩니다.- 13
검증됨조건은 선택한 모든 클러스터가 검증되었음을 보여줍니다.
카나리아 클러스터를 업데이트하는 동안 오류가 발생하면 업데이트 프로세스가 중지됩니다.
수정 계획이 성공적으로 생성되면 enable 필드를 true 로 설정하고 TALM이 지정된 관리 정책으로 호환되지 않는 클러스터를 업데이트하기 시작할 수 있습니다.
ClusterGroupUpgrade CR의 enable 필드가 false 로 설정된 경우에만 spec 필드를 변경할 수 있습니다.
11.5.2. 검증
TALM은 지정된 모든 관리 정책이 사용 가능하고 올바른지 확인하고 검증 조건을 사용하여 다음과 같이 상태 및 이유를 보고합니다.
true검증이 완료되었습니다.
false정책이 없거나 유효하지 않거나 잘못된 플랫폼 이미지가 지정되었습니다.
11.5.3. 사전 캐싱
클러스터는 컨테이너 이미지 레지스트리에 액세스하기 위한 대역폭이 제한될 수 있으므로 업데이트가 완료되기 전에 시간 초과가 발생할 수 있습니다. 단일 노드 OpenShift 클러스터에서는 사전 캐싱을 사용하여 이 문제를 방지할 수 있습니다. preCaching 필드가 true 로 설정된 ClusterGroupUpgrade CR을 생성할 때 컨테이너 이미지 사전 캐싱이 시작됩니다. TALM은 사용 가능한 디스크 공간을 예상 OpenShift Container Platform 이미지 크기와 비교하여 충분한 공간이 있는지 확인합니다. 클러스터에 공간이 충분하지 않으면 TALM은 해당 클러스터의 사전 캐싱을 취소하고 정책을 수정하지 않습니다.
TALM은 PrecacheSpecValid 조건을 사용하여 다음과 같이 상태 정보를 보고합니다.
true사전 캐싱 사양은 유효하고 일관되게 유지됩니다.
false사전 캐싱 사양은 불완전합니다.
TALM은 PrecachingSucceeded 조건을 사용하여 다음과 같이 상태 정보를 보고합니다.
trueTALM은 사전 캐싱 프로세스를 완료했습니다. 클러스터에 대한 사전 캐싱이 실패하면 해당 클러스터에 대한 업데이트가 실패하지만 다른 모든 클러스터를 진행합니다. 클러스터에 대해 사전 캐싱이 실패한 경우 메시지가 표시됩니다.
false하나 이상의 클러스터에 대해 아직 진행 중이거나 모든 클러스터에서 실패했습니다.
자세한 내용은 "컨테이너 이미지 사전 캐시 기능 사용" 섹션을 참조하십시오.
11.5.4. 백업 생성
단일 노드 OpenShift의 경우 TALM은 업데이트 전에 배포 백업을 생성할 수 있습니다. 업데이트가 실패하면 이전 버전을 복구하고 애플리케이션을 다시 프로비저닝하지 않고도 클러스터를 작동 상태로 복원할 수 있습니다. 백업 기능을 사용하려면 먼저 backup 필드가 true 로 설정된 ClusterGroupUpgrade CR을 생성합니다. 백업 내용이 최신 상태인지 확인하기 위해 ClusterGroupUpgrade CR의 enable 필드를 true 로 설정할 때까지 백업이 수행되지 않습니다.
TALM은 BackupSucceeded 조건을 사용하여 다음과 같이 상태 및 이유를 보고합니다.
true모든 클러스터 또는 백업 실행이 완료되었지만 하나 이상의 클러스터에 대해 백업이 완료되었습니다. 클러스터에 대한 백업이 실패하면 해당 클러스터에 대한 업데이트가 실패하지만 다른 모든 클러스터를 진행합니다.
false하나 이상의 클러스터에 대한 백업이 진행 중이거나 모든 클러스터에 실패했습니다.
자세한 내용은 "업그레이드 전에 클러스터 리소스의 백업 생성" 섹션을 참조하십시오.
11.5.5. 클러스터 업데이트
TALM은 수정 계획에 따라 정책을 적용합니다. 현재 배치의 모든 클러스터가 모든 관리 정책을 준수한 직후 후속 배치에 대한 정책을 강제 적용합니다. 배치 시간이 초과되면 TALM은 다음 일괄 처리로 이동합니다. 배치의 시간 초과 값은 수정 계획의 배치 수로 나눈 spec.timeout 필드입니다.
TALM은 Progressing 조건을 사용하여 다음과 같이 상태 및 이유를 보고합니다.
trueTALM은 준수하지 않는 정책을 수정하고 있습니다.
false업데이트가 진행 중이 아닙니다. 가능한 이유는 다음과 같습니다.
- 모든 클러스터는 모든 관리 정책을 준수합니다.
- 정책 수정이 너무 오래 걸리기 때문에 업데이트가 시간 초과되었습니다.
- 차단 CR이 시스템에서 누락되었거나 아직 완료되지 않았습니다.
-
ClusterGroupUpgradeCR이 활성화되지 않습니다. - 백업은 아직 진행 중입니다.
관리되는 정책은 ClusterGroupUpgrade CR의 managedPolicies 필드에 나열된 순서에 적용됩니다. 한 번에 지정된 클러스터에 하나의 관리 정책이 적용됩니다. 클러스터가 현재 정책을 준수하면 다음 관리 정책이 적용됩니다.
Progressing 상태의 샘플 ClusterGroupUpgrade CR
- 1
진행중 필드에 TALM이 정책을 수정하는 중입니다.
11.5.6. 업데이트 상태
TALM은 Succeeded 조건을 사용하여 다음과 같이 상태 및 이유를 보고합니다.
true모든 클러스터는 지정된 관리 정책을 준수합니다.
false수정에 사용할 수 있는 클러스터가 없으므로 정책 수정이 실패했거나 다음과 같은 이유 중 하나에 정책 수정을 수행하는 데 시간이 너무 오래 걸리기 때문입니다.
- 현재 배치에는 카나리아 업데이트가 포함되어 있으며 일괄 처리의 클러스터는 배치 시간 초과 내의 모든 관리 정책을 준수하지는 않습니다.
-
클러스터는
remediationStrategy필드에 지정된타임아웃값 내의 관리 정책을 준수하지 않았습니다.
Succeeded 상태의 샘플 ClusterGroupUpgrade CR
timedout 상태의 샘플 ClusterGroupUpgrade CR
11.5.7. Blocking ClusterGroupUpgrade CRs
ClusterGroupUpgrade CR을 여러 개 생성하고 애플리케이션 순서를 제어할 수 있습니다.
예를 들어 CR A의 시작을 차단하는 ClusterGroupUpgrade CR C를 생성하는 경우 ClusterGroupUpgrade ClusterGroupUpgrade CR C의 상태가 UpgradeComplete 가 될 때까지 ClusterGroupUpgrade CR A를 시작할 수 없습니다.
하나의 ClusterGroupUpgrade CR에는 차단 CR이 여러 개 있을 수 있습니다. 이 경우 현재 CR의 업그레이드가 시작되기 전에 차단 CR을 모두 완료해야 합니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- 하나 이상의 관리 클러스터를 프로비저닝합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - hub 클러스터에 RHACM 정책을 생성합니다.
프로세스
ClusterGroupUpgradeCR의 내용을cgu-a.yaml,cgu-b.yaml및cgu-c.yaml파일에 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- blocking CR을 정의합니다.
cgu-a업데이트는cgu-c가 완료될 때까지 시작할 수 없습니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
cgu-b업데이트는cgu-a가 완료될 때까지 시작할 수 없습니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
cgu-c업데이트에는 차단 CR이 없습니다.enable필드가true로 설정된 경우 TALM은cgu-c업데이트를 시작합니다.
각 관련 CR에 대해 다음 명령을 실행하여
ClusterGroupUpgradeCR을 생성합니다.oc apply -f <name>.yaml
$ oc apply -f <name>.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 각 관련 CR에 대해 다음 명령을 실행하여 업데이트 프로세스를 시작합니다.
oc --namespace=default patch clustergroupupgrade.ran.openshift.io/<name> \ --type merge -p '{"spec":{"enable":true}}'$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/<name> \ --type merge -p '{"spec":{"enable":true}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 예제에서는
enable필드가true로 설정된ClusterGroupUpgradeCR을 보여줍니다.CR 차단이 있는
cgu-a의 예Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 차단 CR 목록을 표시합니다.
CR 차단이 있는
cgu-b의 예Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 차단 CR 목록을 표시합니다.
CR 차단이 있는
cgu-c의 예Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
cgu-c업데이트에는 차단 CR이 없습니다.
11.6. 관리 클러스터에서 정책 업데이트
TALM( Topology Aware Lifecycle Manager)은 ClusterGroupUpgrade CR에 지정된 클러스터에 대한 정보 정책 세트를 수정합니다. TALM은 관리 RHACM 정책의 사본을 적용하여 정보 정책을 해결합니다. 복사된 각 정책에는 고유한 RHACM 배치 규칙과 RHACM 배치 바인딩이 있습니다.
TALM은 현재 배치의 각 클러스터를 적용 가능한 관리 정책에 해당하는 배치 규칙에 추가합니다. 클러스터가 이미 정책과 호환되는 경우 TALM은 규정 준수 클러스터에 해당 정책 적용을 건너뜁니다. 그런 다음 TALM은 호환되지 않는 클러스터에 다음 정책을 적용하기 위해 계속 이동합니다. TALM이 배치의 업데이트를 완료하면 복사된 정책과 연결된 배치 규칙에서 모든 클러스터가 제거됩니다. 그런 다음 다음 배치의 업데이트가 시작됩니다.
spoke 클러스터에서 RHACM에 호환되는 상태를 보고하지 않으면 허브 클러스터의 관리 정책에 TALM에 필요한 상태 정보가 누락될 수 있습니다. TALM은 다음과 같은 방법으로 이러한 사례를 처리합니다.
-
정책의
status.compliant필드가 없는 경우 TALM은 정책을 무시하고 로그 항목을 추가합니다. 그런 다음 TALM은 정책의status.status필드를 계속 확인합니다. -
정책의
status.status가 없으면 TALM에서 오류가 발생합니다. -
정책의
status.status필드에 클러스터의 규정 준수 상태가 없는 경우 TALM은 해당 클러스터가 해당 정책과 호환되지 않는 것으로 간주합니다.
ClusterGroupUpgrade CR의 batchTimeoutAction 에 따라 클러스터에 대한 업그레이드가 실패하는 경우 발생하는 상황이 결정됩니다. 실패한 클러스터를 계속 건너뛰고 다른 클러스터를 계속 업그레이드하거나 모든 클러스터의 정책 수정을 중지하려면 중단을 지정할 수 있습니다. 시간 초과가 경과하면 TALM은 모든 적용 정책을 제거하여 클러스터에 대한 추가 업데이트가 없는지 확인합니다.
업그레이드 정책의 예
RHACM 정책에 대한 자세한 내용은 정책 개요 를 참조하십시오.
11.6.1. TALM을 사용하여 설치하는 관리형 클러스터에 대한 Operator 서브스크립션 구성
Operator의 Subscription CR(사용자 정의 리소스)에 status.state.AtLatestKnown 필드가 포함된 경우에만 TALM( topology Aware Lifecycle Manager)은 Operator에 대한 설치 계획을 승인할 수 있습니다.
프로세스
status.state.AtLatestKnown필드를 Operator의SubscriptionCR에 추가합니다.서브스크립션 CR의 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
status.state: AtLatestKnown필드는 Operator 카탈로그에서 사용 가능한 최신 Operator 버전에 사용됩니다.
참고레지스트리에서 새 버전의 Operator를 사용할 수 있으면 연결된 정책이 호환되지 않습니다.
-
ClusterGroupUpgradeCR이 있는 관리 클러스터에 변경된서브스크립션정책을 적용합니다.
11.6.2. 관리 클러스터에 업데이트 정책 적용
정책을 적용하여 관리 클러스터를 업데이트할 수 있습니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- 하나 이상의 관리 클러스터를 프로비저닝합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - hub 클러스터에 RHACM 정책을 생성합니다.
프로세스
ClusterGroupUpgradeCR의 내용을cgu-1.yaml파일에 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
ClusterGroupUpgradeCR을 생성합니다.oc create -f cgu-1.yaml
$ oc create -f cgu-1.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 Hub 클러스터에서
ClusterGroupUpgradeCR이 생성되었는지 확인합니다.oc get cgu --all-namespaces
$ oc get cgu --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME AGE STATE DETAILS default cgu-1 8m55 NotEnabled Not Enabled
NAMESPACE NAME AGE STATE DETAILS default cgu-1 8m55 NotEnabled Not EnabledCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 업데이트 상태를 확인합니다.
oc get cgu -n default cgu-1 -ojsonpath='{.status}' | jq$ oc get cgu -n default cgu-1 -ojsonpath='{.status}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
ClusterGroupUpgradeCR의spec.enable필드는false로 설정됩니다.
다음 명령을 실행하여 정책의 상태를 확인합니다.
oc get policies -A
$ oc get policies -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 클러스터에 현재 적용된 정책의
spec.remediationAction필드는적용하도록 설정되어 있습니다. 업데이트 중에ClusterGroupUpgradeCR의 알림 모드에서 관리되는정책은알림 모드로 유지됩니다.
다음 명령을 실행하여
spec.enable필드의 값을true로 변경합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-1 \ --patch '{"spec":{"enable":true}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-1 \ --patch '{"spec":{"enable":true}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
다음 명령을 실행하여 업데이트 상태를 다시 확인합니다.
oc get cgu -n default cgu-1 -ojsonpath='{.status}' | jq$ oc get cgu -n default cgu-1 -ojsonpath='{.status}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 현재 배치의 업데이트 진행 상황을 반영합니다. 이 명령을 다시 실행하여 진행 상황에 대한 업데이트된 정보를 수신합니다.
정책에 Operator 서브스크립션이 포함된 경우 단일 노드 클러스터에서 직접 설치 진행 상황을 확인할 수 있습니다.
다음 명령을 실행하여 설치 진행 상황을 확인할 단일 노드 클러스터의
KUBECONFIG파일을 내보냅니다.export KUBECONFIG=<cluster_kubeconfig_absolute_path>
$ export KUBECONFIG=<cluster_kubeconfig_absolute_path>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 단일 노드 클러스터에 있는 모든 서브스크립션을 확인하고 다음 명령을 실행하여
ClusterGroupUpgradeCR을 통해 설치하려는 정책에서 해당 서브스크립션을 찾습니다.oc get subs -A | grep -i <subscription_name>
$ oc get subs -A | grep -i <subscription_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow cluster-logging정책의 출력 예NAMESPACE NAME PACKAGE SOURCE CHANNEL openshift-logging cluster-logging cluster-logging redhat-operators stable
NAMESPACE NAME PACKAGE SOURCE CHANNEL openshift-logging cluster-logging cluster-logging redhat-operators stableCopy to Clipboard Copied! Toggle word wrap Toggle overflow
관리 정책 중 하나에
ClusterVersionCR이 포함된 경우 spoke 클러스터에 대해 다음 명령을 실행하여 현재 일괄 처리에서 플랫폼 업데이트 상태를 확인합니다.oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version 4.4.15.5 True True 43s Working towards 4.4.15.7: 71 of 735 done (9% complete)
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version 4.4.15.5 True True 43s Working towards 4.4.15.7: 71 of 735 done (9% complete)Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 Operator 서브스크립션을 확인합니다.
oc get subs -n <operator-namespace> <operator-subscription> -ojsonpath="{.status}"$ oc get subs -n <operator-namespace> <operator-subscription> -ojsonpath="{.status}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 원하는 서브스크립션과 연결된 단일 노드 클러스터에 있는 설치 계획을 확인합니다.
oc get installplan -n <subscription_namespace>
$ oc get installplan -n <subscription_namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow cluster-loggingOperator의 출력 예NAMESPACE NAME CSV APPROVAL APPROVED openshift-logging install-6khtw cluster-logging.5.3.3-4 Manual true
NAMESPACE NAME CSV APPROVAL APPROVED openshift-logging install-6khtw cluster-logging.5.3.3-4 Manual true1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 설치 계획의
승인필드가Manual로 설정되고 TALM에서 설치 계획을 승인한 후승인필드가false에서true로 변경됩니다.
참고TALM이 서브스크립션이 포함된 정책을 수정하면 해당 서브스크립션에 연결된 모든 설치 계획을 자동으로 승인합니다. Operator를 최신 알려진 버전으로 가져오기 위해 여러 설치 계획이 필요한 경우 TALM은 여러 설치 계획을 승인하여 하나 이상의 중간 버전을 통해 최종 버전으로 업그레이드할 수 있습니다.
다음 명령을 실행하여
ClusterGroupUpgrade가Succeeded단계에 도달한 정책의 Operator의 클러스터 서비스 버전이 있는지 확인합니다.oc get csv -n <operator_namespace>
$ oc get csv -n <operator_namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow OpenShift Logging Operator의 출력 예
NAME DISPLAY VERSION REPLACES PHASE cluster-logging.5.4.2 Red Hat OpenShift Logging 5.4.2 Succeeded
NAME DISPLAY VERSION REPLACES PHASE cluster-logging.5.4.2 Red Hat OpenShift Logging 5.4.2 SucceededCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.7. 업그레이드하기 전에 클러스터 리소스의 백업 생성
단일 노드 OpenShift의 경우 TALM(토폴로지 Aware Lifecycle Manager)은 업그레이드하기 전에 배포 백업을 생성할 수 있습니다. 업그레이드에 실패하면 이전 버전을 복구하고 애플리케이션을 다시 프로비저닝하지 않고도 클러스터를 작동 상태로 복원할 수 있습니다.
백업 기능을 사용하려면 먼저 backup 필드가 true 로 설정된 ClusterGroupUpgrade CR을 생성합니다. 백업 내용이 최신 상태인지 확인하기 위해 ClusterGroupUpgrade CR의 enable 필드를 true 로 설정할 때까지 백업이 수행되지 않습니다.
TALM은 BackupSucceeded 조건을 사용하여 다음과 같이 상태 및 이유를 보고합니다.
true모든 클러스터 또는 백업 실행이 완료되었지만 하나 이상의 클러스터에 대해 백업이 완료되었습니다. 클러스터에 대한 백업이 실패하면 해당 클러스터를 업데이트하지 않습니다.
false하나 이상의 클러스터에 대한 백업이 진행 중이거나 모든 클러스터에 실패했습니다. spoke 클러스터에서 실행되는 백업 프로세스는 다음과 같은 상태를 가질 수 있습니다.
PreparingToStart첫 번째 조정 단계는 진행 중입니다. TALM은 업그레이드 실패 시 생성된 모든 spoke 백업 네임스페이스 및 허브 뷰 리소스를 삭제합니다.
Starting백업 사전 요구 사항 및 백업 작업이 생성 중입니다.
활성백업이 진행 중입니다.
succeeded백업에 성공했습니다.
BackupTimeout아티팩트 백업은 부분적으로 수행됩니다.
UnrecoverableError백업이 0이 아닌 종료 코드로 종료되었습니다.
클러스터 백업에 실패하고 BackupTimeout 또는 UnrecoverableError 상태를 입력하면 클러스터 업데이트가 해당 클러스터를 진행하지 않습니다. 다른 클러스터의 업데이트는 영향을 받지 않으며 계속됩니다.
11.7.1. 백업을 사용하여 ClusterGroupUpgrade CR 생성
단일 노드 OpenShift 클러스터에서 업그레이드하기 전에 배포 백업을 생성할 수 있습니다. 업그레이드에 실패하면 Topology Aware Lifecycle Manager(TALM)에서 생성한 upgrade-recovery.sh 스크립트를 사용하여 시스템을 사전 업그레이드 상태로 되돌릴 수 있습니다. 백업은 다음 항목으로 구성됩니다.
- 클러스터 백업
-
etcd및 정적 pod 매니페스트의 스냅샷입니다. - 콘텐츠 백업
-
폴더의 백업(예:
/etc,/usr/local,/var/lib/kubelet). - 변경된 파일 백업
-
변경된
machine-config에서 관리하는 모든 파일입니다. - Deployment
-
고정된
ostree배포입니다. - 이미지(선택 사항)
- 사용 중인 컨테이너 이미지입니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- 하나 이상의 관리 클러스터를 프로비저닝합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - RHACM(Red Hat Advanced Cluster Management)을 설치합니다.
복구 파티션을 만드는 것이 좋습니다. 다음은 50GB의 복구 파티션에 대한 SiteConfig CR(사용자 정의 리소스)의 예입니다.
프로세스
clustergroupupgrades-group-du.yaml파일에서backup및enable필드를true로 설정하여ClusterGroupUpgradeCR의 내용을 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트를 시작하려면 다음 명령을 실행하여
ClusterGroupUpgradeCR을 적용합니다.oc apply -f clustergroupupgrades-group-du.yaml
$ oc apply -f clustergroupupgrades-group-du.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
다음 명령을 실행하여 hub 클러스터에서 업그레이드 상태를 확인합니다.
oc get cgu -n ztp-group-du-sno du-upgrade-4918 -o jsonpath='{.status}'$ oc get cgu -n ztp-group-du-sno du-upgrade-4918 -o jsonpath='{.status}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.7.2. 업그레이드 실패 후 클러스터 복구
클러스터 업그레이드가 실패하면 클러스터에 수동으로 로그인하고 백업을 사용하여 클러스터를 업그레이드 전 상태로 되돌릴 수 있습니다. 두 단계가 있습니다.
- rollback
- 시도한 업그레이드에 플랫폼 OS 배포 변경 사항이 포함된 경우 복구 스크립트를 실행하기 전에 이전 버전으로 롤백해야 합니다.
롤백은 TALM 및 단일 노드 OpenShift에서 업그레이드하는 경우에만 사용할 수 있습니다. 이 프로세스는 다른 업그레이드 유형의 롤백에는 적용되지 않습니다.
- 복구
- 복구는 컨테이너를 종료하고 백업 파티션의 파일을 사용하여 컨테이너를 다시 시작하고 클러스터를 복원합니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- 하나 이상의 관리 클러스터를 프로비저닝합니다.
- RHACM(Red Hat Advanced Cluster Management)을 설치합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - 백업용으로 구성된 업그레이드를 실행합니다.
프로세스
다음 명령을 실행하여 이전에 생성한
ClusterGroupUpgradeCR(사용자 정의 리소스)을 삭제합니다.oc delete cgu/du-upgrade-4918 -n ztp-group-du-sno
$ oc delete cgu/du-upgrade-4918 -n ztp-group-du-snoCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 복구할 클러스터에 로그인합니다.
다음 명령을 실행하여 플랫폼 OS 배포의 상태를 확인합니다.
ostree admin status
$ ostree admin statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
ostree admin status * rhcos c038a8f08458bbed83a77ece033ad3c55597e3f64edad66ea12fda18cbdceaf9.0 Version: 49.84.202202230006-0 Pinned: yes origin refspec: c038a8f08458bbed83a77ece033ad3c55597e3f64edad66ea12fda18cbdceaf9[root@lab-test-spoke2-node-0 core]# ostree admin status * rhcos c038a8f08458bbed83a77ece033ad3c55597e3f64edad66ea12fda18cbdceaf9.0 Version: 49.84.202202230006-0 Pinned: yes1 origin refspec: c038a8f08458bbed83a77ece033ad3c55597e3f64edad66ea12fda18cbdceaf9Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 현재 배포가 고정되어 있습니다. 플랫폼 OS 배포 롤백은 필요하지 않습니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 플랫폼 OS 배포의 롤백을 트리거하려면 다음 명령을 실행합니다.
rpm-ostree rollback -r
$ rpm-ostree rollback -rCopy to Clipboard Copied! Toggle word wrap Toggle overflow 복구의 첫 번째 단계는 컨테이너를 종료하고 백업 파티션에서 대상 디렉터리로 파일을 복원합니다. 복구를 시작하려면 다음 명령을 실행합니다.
/var/recovery/upgrade-recovery.sh
$ /var/recovery/upgrade-recovery.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow 메시지가 표시되면 다음 명령을 실행하여 클러스터를 재부팅합니다.
systemctl reboot
$ systemctl rebootCopy to Clipboard Copied! Toggle word wrap Toggle overflow 재부팅 후 다음 명령을 실행하여 복구를 다시 시작합니다.
/var/recovery/upgrade-recovery.sh --resume
$ /var/recovery/upgrade-recovery.sh --resumeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
복구 유틸리티가 실패하면 --restart 옵션을 사용하여 다시 시도할 수 있습니다.
/var/recovery/upgrade-recovery.sh --restart
$ /var/recovery/upgrade-recovery.sh --restart검증
복구 상태를 확인하려면 다음 명령을 실행합니다.
oc get clusterversion,nodes,clusteroperator
$ oc get clusterversion,nodes,clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.8. 컨테이너 이미지 사전 캐시 기능 사용
단일 노드 OpenShift 클러스터는 컨테이너 이미지 레지스트리에 액세스하기 위해 대역폭이 제한될 수 있으므로 업데이트가 완료되기 전에 시간 초과가 발생할 수 있습니다.
업데이트 시간은 TALM에 의해 설정되지 않습니다. 수동 애플리케이션 또는 외부 자동화를 통해 업데이트 시작 시 ClusterGroupUpgrade CR을 적용할 수 있습니다.
ClusterGroupUpgrade CR에서 preCaching 필드가 true 로 설정된 경우 컨테이너 이미지 사전 캐싱이 시작됩니다.
TALM은 PrecacheSpecValid 조건을 사용하여 다음과 같이 상태 정보를 보고합니다.
true사전 캐싱 사양은 유효하고 일관되게 유지됩니다.
false사전 캐싱 사양은 불완전합니다.
TALM은 PrecachingSucceeded 조건을 사용하여 다음과 같이 상태 정보를 보고합니다.
trueTALM은 사전 캐싱 프로세스를 완료했습니다. 클러스터에 대한 사전 캐싱이 실패하면 해당 클러스터에 대한 업데이트가 실패하지만 다른 모든 클러스터를 진행합니다. 클러스터에 대해 사전 캐싱이 실패한 경우 메시지가 표시됩니다.
false하나 이상의 클러스터에 대해 아직 진행 중이거나 모든 클러스터에서 실패했습니다.
성공적인 사전 캐싱 프로세스 후 정책 수정을 시작할 수 있습니다. 수정 작업은 enable 필드가 true 로 설정된 경우 시작됩니다. 클러스터에 사전 캐싱 오류가 발생하면 해당 클러스터에 대한 업그레이드가 실패합니다. 업그레이드 프로세스는 사전 캐시가 성공한 다른 모든 클러스터에서 계속됩니다.
사전 캐싱 프로세스는 다음과 같은 상태에 있을 수 있습니다.
NotStarted이는
ClusterGroupUpgradeCR의 첫 번째 조정 패스에서 모든 클러스터가 자동으로 할당됩니다. 이 상태에서 TALM은 이전에 불완전한 업데이트에서 남아 있는 spoke 클러스터의 모든 사전 캐싱 네임스페이스 및 허브 뷰 리소스를 삭제합니다. 그런 다음 TALM은PrecachePreparing상태에서 삭제를 확인하기 위해 spoke pre-caching 네임스페이스에 대한 새ManagedClusterView리소스를 생성합니다.PreparingToStart이전 불완전한 업데이트의 나머지 리소스를 정리하는 작업이 진행 중입니다.
Starting작업 사전 캐싱 사전 요구 사항 및 작업이 생성됩니다.
활성작업은 "활성" 상태입니다.
succeededpre-cache 작업이 성공했습니다.
PrecacheTimeout아티팩트 사전 캐싱은 부분적으로 수행됩니다.
UnrecoverableError작업이 0이 아닌 종료 코드로 종료됩니다.
11.8.1. 컨테이너 이미지 사전 캐시 필터 사용
사전 캐시 기능은 일반적으로 업데이트에 필요한 클러스터보다 많은 이미지를 다운로드합니다. 클러스터에 다운로드되는 사전 캐시 이미지를 제어할 수 있습니다. 이렇게 하면 다운로드 시간이 줄어들고 대역폭과 스토리지를 절약할 수 있습니다.
다음 명령을 사용하여 다운로드할 모든 이미지 목록을 확인할 수 있습니다.
oc adm release info <ocp-version>
$ oc adm release info <ocp-version>
다음 ConfigMap 예제에서는 excludePrecachePatterns 필드를 사용하여 이미지를 제외하는 방법을 보여줍니다.
- 1
- TALM은 여기에 나열된 패턴이 포함된 이름이 있는 모든 이미지를 제외합니다.
11.8.2. 사전 캐싱을 사용하여 ClusterGroupUpgrade CR 생성
단일 노드 OpenShift의 경우 사전 캐시 기능을 사용하면 업데이트가 시작되기 전에 필요한 컨테이너 이미지를 spoke 클러스터에 표시할 수 있습니다.
사전 캐싱의 경우 TALM은 ClusterGroupUpgrade CR의 spec.remediationStrategy.timeout 값을 사용합니다. 사전 캐싱 작업이 완료될 수 있도록 충분한 시간을 허용하는 시간 초과 값을 설정해야 합니다. 사전 캐싱이 완료된 후 ClusterGroupUpgrade CR을 활성화하면 시간 초과 값을 업데이트에 적합한 기간으로 변경할 수 있습니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- 하나 이상의 관리 클러스터를 프로비저닝합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다.
프로세스
clustergroupupgrades-group-du.yaml파일에서preCaching필드를true로 설정하여ClusterGroupUpgradeCR의 내용을 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
preCaching필드는true로 설정되어 업데이트를 시작하기 전에 TALM에서 컨테이너 이미지를 가져올 수 있습니다.
사전 캐싱을 시작하려면 다음 명령을 실행하여
ClusterGroupUpgradeCR을 적용합니다.oc apply -f clustergroupupgrades-group-du.yaml
$ oc apply -f clustergroupupgrades-group-du.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
다음 명령을 실행하여 Hub 클러스터에
ClusterGroupUpgradeCR이 있는지 확인합니다.oc get cgu -A
$ oc get cgu -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME AGE STATE DETAILS ztp-group-du-sno du-upgrade-4918 10s InProgress Precaching is required and not done
NAMESPACE NAME AGE STATE DETAILS ztp-group-du-sno du-upgrade-4918 10s InProgress Precaching is required and not done1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- CR이 생성됩니다.
다음 명령을 실행하여 사전 캐싱 작업의 상태를 확인합니다.
oc get cgu -n ztp-group-du-sno du-upgrade-4918 -o jsonpath='{.status}'$ oc get cgu -n ztp-group-du-sno du-upgrade-4918 -o jsonpath='{.status}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 식별된 클러스터 목록을 표시합니다.
spoke 클러스터에서 다음 명령을 실행하여 사전 캐싱 작업의 상태를 확인합니다.
oc get jobs,pods -n openshift-talo-pre-cache
$ oc get jobs,pods -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME COMPLETIONS DURATION AGE job.batch/pre-cache 0/1 3m10s 3m10s NAME READY STATUS RESTARTS AGE pod/pre-cache--1-9bmlr 1/1 Running 0 3m10s
NAME COMPLETIONS DURATION AGE job.batch/pre-cache 0/1 3m10s 3m10s NAME READY STATUS RESTARTS AGE pod/pre-cache--1-9bmlr 1/1 Running 0 3m10sCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
ClusterGroupUpgradeCR의 상태를 확인합니다.oc get cgu -n ztp-group-du-sno du-upgrade-4918 -o jsonpath='{.status}'$ oc get cgu -n ztp-group-du-sno du-upgrade-4918 -o jsonpath='{.status}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 사전 캐시 작업이 수행됩니다.
11.9. 토폴로지 인식 라이프사이클 관리자 문제 해결
Topology Aware Lifecycle Manager (TALM)는 RHACM 정책을 수정하는 OpenShift Container Platform Operator입니다. 문제가 발생하면 oc adm must-gather 명령을 사용하여 세부 정보 및 로그를 수집하고 문제를 디버깅하는 단계를 수행합니다.
관련 항목에 대한 자세한 내용은 다음 설명서를 참조하십시오.
- Red Hat Advanced Cluster Management for Kubernetes 2.4 지원 매트릭스
- Red Hat Advanced Cluster Management 문제 해결
- "Troubleshooting Operator 문제" 섹션
11.9.1. 일반 문제 해결
다음 질문을 검토하여 문제의 원인을 확인할 수 있습니다.
적용 중인 구성이 지원됩니까?
- RHACM 및 OpenShift Container Platform 버전이 호환됩니까?
- TALM 및 RHACM 버전이 호환됩니까?
다음 중 문제를 유발하는 구성 요소는 무엇입니까?
ClusterGroupUpgrade 구성이 작동하는지 확인하려면 다음을 수행할 수 있습니다.
-
spec.enable필드가false로 설정된ClusterGroupUpgradeCR을 생성합니다. - 상태가 업데이트될 때까지 기다린 후 문제 해결 질문을 진행합니다.
-
모든 항목이 예상대로 표시되면
ClusterGroupUpgradeCR에서spec.enable필드를true로 설정합니다.
ClusterUpgradeGroup CR에서 spec.enable 필드를 true 로 설정한 후에는 업데이트 절차가 시작되고 CR의 spec 필드를 더 이상 편집할 수 없습니다.
11.9.2. ClusterUpgradeGroup CR을 수정할 수 없음
- 문제
-
업데이트를 활성화한 후에는
ClusterUpgradeGroupCR을 편집할 수 없습니다. - 해결
다음 단계를 수행하여 절차를 다시 시작합니다.
다음 명령을 실행하여 이전
ClusterGroupUpgradeCR을 제거합니다.oc delete cgu -n <ClusterGroupUpgradeCR_namespace> <ClusterGroupUpgradeCR_name>
$ oc delete cgu -n <ClusterGroupUpgradeCR_namespace> <ClusterGroupUpgradeCR_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터 및 정책의 기존 문제를 확인하고 수정합니다.
- 모든 클러스터가 관리 클러스터이고 사용 가능한지 확인합니다.
-
모든 정책이 존재하고
spec.remediationAction필드가 설정되어 있는지확인합니다.
올바른 구성으로 새
ClusterGroupUpgradeCR을 생성합니다.oc apply -f <ClusterGroupUpgradeCR_YAML>
$ oc apply -f <ClusterGroupUpgradeCR_YAML>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.9.3. 관리형 정책
시스템에서 관리되는 정책 확인
- 문제
- 시스템에 올바른 관리 정책이 있는지 확인하려고 합니다.
- 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -ojsonpath='{.spec.managedPolicies}'$ oc get cgu lab-upgrade -ojsonpath='{.spec.managedPolicies}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
["group-du-sno-validator-du-validator-policy", "policy2-common-nto-sub-policy", "policy3-common-ptp-sub-policy"]
["group-du-sno-validator-du-validator-policy", "policy2-common-nto-sub-policy", "policy3-common-ptp-sub-policy"]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
수정 모드 확인
- 문제
-
관리되는 정책의
사양에서remediationAction필드가inform으로 설정되어 있는지 확인하고 싶습니다. - 해결
다음 명령을 실행합니다.
oc get policies --all-namespaces
$ oc get policies --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME REMEDIATION ACTION COMPLIANCE STATE AGE default policy1-common-cluster-version-policy inform NonCompliant 5d21h default policy2-common-nto-sub-policy inform Compliant 5d21h default policy3-common-ptp-sub-policy inform NonCompliant 5d21h default policy4-common-sriov-sub-policy inform NonCompliant 5d21h
NAMESPACE NAME REMEDIATION ACTION COMPLIANCE STATE AGE default policy1-common-cluster-version-policy inform NonCompliant 5d21h default policy2-common-nto-sub-policy inform Compliant 5d21h default policy3-common-ptp-sub-policy inform NonCompliant 5d21h default policy4-common-sriov-sub-policy inform NonCompliant 5d21hCopy to Clipboard Copied! Toggle word wrap Toggle overflow
정책 규정 준수 상태 확인
- 문제
- 정책의 규정 준수 상태를 확인하려고 합니다.
- 해결
다음 명령을 실행합니다.
oc get policies --all-namespaces
$ oc get policies --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME REMEDIATION ACTION COMPLIANCE STATE AGE default policy1-common-cluster-version-policy inform NonCompliant 5d21h default policy2-common-nto-sub-policy inform Compliant 5d21h default policy3-common-ptp-sub-policy inform NonCompliant 5d21h default policy4-common-sriov-sub-policy inform NonCompliant 5d21h
NAMESPACE NAME REMEDIATION ACTION COMPLIANCE STATE AGE default policy1-common-cluster-version-policy inform NonCompliant 5d21h default policy2-common-nto-sub-policy inform Compliant 5d21h default policy3-common-ptp-sub-policy inform NonCompliant 5d21h default policy4-common-sriov-sub-policy inform NonCompliant 5d21hCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.9.4. 클러스터
관리 클러스터가 있는지 확인
- 문제
-
ClusterGroupUpgradeCR의 클러스터가 관리 클러스터인지 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get managedclusters
$ oc get managedclustersCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE local-cluster true https://api.hub.example.com:6443 True Unknown 13d spoke1 true https://api.spoke1.example.com:6443 True True 13d spoke3 true https://api.spoke3.example.com:6443 True True 27h
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE local-cluster true https://api.hub.example.com:6443 True Unknown 13d spoke1 true https://api.spoke1.example.com:6443 True True 13d spoke3 true https://api.spoke3.example.com:6443 True True 27hCopy to Clipboard Copied! Toggle word wrap Toggle overflow 또는 TALM 관리자 로그를 확인합니다.
다음 명령을 실행하여 TALM 관리자의 이름을 가져옵니다.
oc get pod -n openshift-operators
$ oc get pod -n openshift-operatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME READY STATUS RESTARTS AGE cluster-group-upgrades-controller-manager-75bcc7484d-8k8xp 2/2 Running 0 45m
NAME READY STATUS RESTARTS AGE cluster-group-upgrades-controller-manager-75bcc7484d-8k8xp 2/2 Running 0 45mCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 TALM 관리자 로그를 확인합니다.
oc logs -n openshift-operators \ cluster-group-upgrades-controller-manager-75bcc7484d-8k8xp -c manager
$ oc logs -n openshift-operators \ cluster-group-upgrades-controller-manager-75bcc7484d-8k8xp -c managerCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
ERROR controller-runtime.manager.controller.clustergroupupgrade Reconciler error {"reconciler group": "ran.openshift.io", "reconciler kind": "ClusterGroupUpgrade", "name": "lab-upgrade", "namespace": "default", "error": "Cluster spoke5555 is not a ManagedCluster"} sigs.k8s.io/controller-runtime/pkg/internal/controller.(*Controller).processNextWorkItemERROR controller-runtime.manager.controller.clustergroupupgrade Reconciler error {"reconciler group": "ran.openshift.io", "reconciler kind": "ClusterGroupUpgrade", "name": "lab-upgrade", "namespace": "default", "error": "Cluster spoke5555 is not a ManagedCluster"}1 sigs.k8s.io/controller-runtime/pkg/internal/controller.(*Controller).processNextWorkItemCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 오류 메시지는 클러스터가 관리 클러스터가 아님을 나타냅니다.
관리 클러스터를 사용할 수 있는지 확인
- 문제
-
ClusterGroupUpgradeCR에 지정된 관리 클러스터를 사용할 수 있는지 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get managedclusters
$ oc get managedclustersCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE local-cluster true https://api.hub.testlab.com:6443 True Unknown 13d spoke1 true https://api.spoke1.testlab.com:6443 True True 13d spoke3 true https://api.spoke3.testlab.com:6443 True True 27h
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE local-cluster true https://api.hub.testlab.com:6443 True Unknown 13d spoke1 true https://api.spoke1.testlab.com:6443 True True 13d1 spoke3 true https://api.spoke3.testlab.com:6443 True True 27h2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow
clusterLabelSelector 확인
- 문제
-
ClusterGroupUpgradeCR에 지정된clusterLabelSelector필드가 관리 클러스터 중 하나와 일치하는지 확인해야 합니다. - 해결
다음 명령을 실행합니다.
oc get managedcluster --selector=upgrade=true
$ oc get managedcluster --selector=upgrade=true1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 업데이트하려는 클러스터의 레이블은
upgrade:true입니다.
출력 예
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE spoke1 true https://api.spoke1.testlab.com:6443 True True 13d spoke3 true https://api.spoke3.testlab.com:6443 True True 27h
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE spoke1 true https://api.spoke1.testlab.com:6443 True True 13d spoke3 true https://api.spoke3.testlab.com:6443 True True 27hCopy to Clipboard Copied! Toggle word wrap Toggle overflow
카나리아 클러스터가 있는지 확인
- 문제
카나리아 클러스터가 클러스터 목록에 있는지 확인하려고 합니다.
ClusterGroupUpgradeCR의 예Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -ojsonpath='{.spec.clusters}'$ oc get cgu lab-upgrade -ojsonpath='{.spec.clusters}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
["spoke1", "spoke3"]
["spoke1", "spoke3"]Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 카나리아 클러스터가
clusterLabelSelector라벨과 일치하는 클러스터 목록에 있는지 확인합니다.oc get managedcluster --selector=upgrade=true
$ oc get managedcluster --selector=upgrade=trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE spoke1 true https://api.spoke1.testlab.com:6443 True True 13d spoke3 true https://api.spoke3.testlab.com:6443 True True 27h
NAME HUB ACCEPTED MANAGED CLUSTER URLS JOINED AVAILABLE AGE spoke1 true https://api.spoke1.testlab.com:6443 True True 13d spoke3 true https://api.spoke3.testlab.com:6443 True True 27hCopy to Clipboard Copied! Toggle word wrap Toggle overflow
클러스터는 spec.clusters 에 존재할 수 있으며 spec.clusterLabelSelector 라벨과 일치할 수도 있습니다.
spoke 클러스터에서 사전 캐싱 상태 확인
spoke 클러스터에서 다음 명령을 실행하여 사전 캐싱 상태를 확인합니다.
oc get jobs,pods -n openshift-talo-pre-cache
$ oc get jobs,pods -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.9.5. 수정 전략
ClusterGroupUpgrade CR에 remediationStrategy가 있는지 확인
- 문제
-
remediationStrategy가ClusterGroupUpgradeCR에 있는지 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -ojsonpath='{.spec.remediationStrategy}'$ oc get cgu lab-upgrade -ojsonpath='{.spec.remediationStrategy}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
{"maxConcurrency":2, "timeout":240}{"maxConcurrency":2, "timeout":240}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
ClusterGroupUpgrade CR에 maxConcurrency가 지정되었는지 확인
- 문제
-
maxConcurrency가ClusterGroupUpgradeCR에 지정되어 있는지 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -ojsonpath='{.spec.remediationStrategy.maxConcurrency}'$ oc get cgu lab-upgrade -ojsonpath='{.spec.remediationStrategy.maxConcurrency}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
2
2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.9.6. 토폴로지 인식 라이프사이클 관리자
ClusterGroupUpgrade CR에서 조건 메시지 및 상태 확인
- 문제
-
ClusterGroupUpgradeCR에서status.conditions필드의 값을 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -ojsonpath='{.status.conditions}'$ oc get cgu lab-upgrade -ojsonpath='{.status.conditions}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
{"lastTransitionTime":"2022-02-17T22:25:28Z", "message":"Missing managed policies:[policyList]", "reason":"NotAllManagedPoliciesExist", "status":"False", "type":"Validated"}{"lastTransitionTime":"2022-02-17T22:25:28Z", "message":"Missing managed policies:[policyList]", "reason":"NotAllManagedPoliciesExist", "status":"False", "type":"Validated"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
복사된 해당 정책 확인
- 문제
-
status.managedPoliciesForUpgrade의 모든 정책에status.copiedPolicies.copiedPolicies의 해당 정책이 있는지 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -oyaml
$ oc get cgu lab-upgrade -oyamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
status.remediationPlan이 계산되었는지 확인
- 문제
-
status.remediationPlan이 계산되었는지 확인하려고 합니다. - 해결
다음 명령을 실행합니다.
oc get cgu lab-upgrade -ojsonpath='{.status.remediationPlan}'$ oc get cgu lab-upgrade -ojsonpath='{.status.remediationPlan}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
[["spoke2", "spoke3"]]
[["spoke2", "spoke3"]]Copy to Clipboard Copied! Toggle word wrap Toggle overflow
TALM 관리자 컨테이너의 오류
- 문제
- TALM의 manager 컨테이너의 로그를 확인하려고 합니다.
- 해결
다음 명령을 실행합니다.
oc logs -n openshift-operators \ cluster-group-upgrades-controller-manager-75bcc7484d-8k8xp -c manager
$ oc logs -n openshift-operators \ cluster-group-upgrades-controller-manager-75bcc7484d-8k8xp -c managerCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
ERROR controller-runtime.manager.controller.clustergroupupgrade Reconciler error {"reconciler group": "ran.openshift.io", "reconciler kind": "ClusterGroupUpgrade", "name": "lab-upgrade", "namespace": "default", "error": "Cluster spoke5555 is not a ManagedCluster"} sigs.k8s.io/controller-runtime/pkg/internal/controller.(*Controller).processNextWorkItemERROR controller-runtime.manager.controller.clustergroupupgrade Reconciler error {"reconciler group": "ran.openshift.io", "reconciler kind": "ClusterGroupUpgrade", "name": "lab-upgrade", "namespace": "default", "error": "Cluster spoke5555 is not a ManagedCluster"}1 sigs.k8s.io/controller-runtime/pkg/internal/controller.(*Controller).processNextWorkItemCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 오류를 표시합니다.
ClusterGroupUpgrade CR이 완료된 후 일부 정책을 준수하지 않는 클러스터
- 문제
TALM이 사용하는 정책 준수 상태는 모든 클러스터에 대해 수정이 아직 완전히 업데이트되지 않았는지 여부를 결정하는 데 사용합니다. 그 이유는 다음과 같습니다.
- 정책을 만들거나 업데이트한 후 CGU가 너무 빨리 실행되었습니다.
-
정책을 수정하면
ClusterGroupUpgradeCR의 후속 정책 준수에 영향을 미칩니다.
- 해결
-
동일한 사양으로 새
ClusterGroupUpdateCR을 생성하고 적용합니다.
GitOps ZTP 워크플로의 자동 생성된 ClusterGroupUpgrade CR에는 관리 정책이 없습니다.
- 문제
-
클러스터가
Ready가 될 때 관리 클러스터에 대한 정책이 없는 경우 정책이 자동으로 생성되지 않은ClusterGroupUpgradeCR이 있습니다.ClusterGroupUpgradeCR이 완료되면 관리 클러스터에ztp-done이라는 레이블이 지정됩니다.SiteConfig리소스를 푸시한 후 필요한 시간 내에PolicyGenTemplateCR이 Git 리포지토리로 푸시되지 않은 경우 클러스터가Ready상태가 되면 대상 클러스터에 정책을 사용할 수 없을 수 있습니다. - 해결
-
적용할 정책을 hub 클러스터에서 사용할 수 있는지 확인한 다음 필요한 정책을 사용하여
ClusterGroupUpgradeCR을 생성합니다.
ClusterGroupUpgrade CR을 수동으로 생성하거나 자동 생성을 다시 트리거할 수 있습니다. ClusterGroupUpgrade CR의 자동 생성을 트리거하려면 클러스터에서 ztp-done 레이블을 제거하고 zip-install 네임스페이스에서 이전에 생성된 비어 있는 ClusterGroupUpgrade CR을 삭제합니다.
사전 캐싱 실패
- 문제
다음 이유 중 하나로 인해 사전 캐싱이 실패할 수 있습니다.
- 노드에 사용 가능한 공간이 충분하지 않습니다.
- 연결이 끊긴 환경의 경우 사전 캐시 이미지가 올바르게 미러링되지 않았습니다.
- Pod를 생성할 때 문제가 발생했습니다.
- 해결
공간이 부족하여 사전 캐싱이 실패했는지 확인하려면 노드에서 사전 캐싱 Pod의 로그를 확인합니다.
다음 명령을 사용하여 Pod 이름을 찾습니다.
oc get pods -n openshift-talo-pre-cache
$ oc get pods -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 사용하여 로그에서 오류가 충분하지 않은 공간과 관련이 있는지 확인합니다.
oc logs -n openshift-talo-pre-cache <pod name>
$ oc logs -n openshift-talo-pre-cache <pod name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
로그가 없는 경우 다음 명령을 사용하여 Pod 상태를 확인합니다.
oc describe pod -n openshift-talo-pre-cache <pod name>
$ oc describe pod -n openshift-talo-pre-cache <pod name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Pod가 없는 경우 작업 상태를 확인하여 다음 명령을 사용하여 Pod를 생성할 수 없는 이유를 확인합니다.
oc describe job -n openshift-talo-pre-cache pre-cache
$ oc describe job -n openshift-talo-pre-cache pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12장. 토폴로지 Aware Lifecycle Manager를 사용하여 연결이 끊긴 환경에서 관리형 클러스터 업데이트
Topology Aware Lifecycle Manager (TALM)를 사용하여 OpenShift Container Platform 관리 클러스터의 소프트웨어 라이프사이클을 관리할 수 있습니다. TALM은 RHACM(Red Hat Advanced Cluster Management) 정책을 사용하여 대상 클러스터에서 변경 사항을 수행합니다.
12.1. 연결이 끊긴 환경에서 클러스터 업데이트
ZTP(ZTP) 및 Topology Aware Lifecycle Manager(TALM)를 사용하여 배포한 관리형 클러스터 및 Operator를 업그레이드할 수 있습니다.
12.1.1. 환경 설정
TALM은 플랫폼과 Operator 업데이트를 모두 수행할 수 있습니다.
TALM을 사용하여 연결이 끊긴 클러스터를 업데이트하기 전에 미러 레지스트리에서 업데이트하려는 플랫폼 이미지와 Operator 이미지를 모두 미러링해야 합니다. 이미지를 미러링하려면 다음 단계를 완료합니다.
플랫폼 업데이트의 경우 다음 단계를 수행해야 합니다.
원하는 OpenShift Container Platform 이미지 저장소를 미러링합니다. 추가 리소스에 연결된 "OpenShift Container Platform 이미지 저장소 미러링" 절차에 따라 원하는 플랫폼 이미지가 미러링되었는지 확인합니다.
imageContentSources섹션의 내용을imageContentSources.yaml파일에 저장합니다.출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 미러링된 플랫폼 이미지의 이미지 서명을 저장합니다. 플랫폼 업데이트를 위해
PolicyGenTemplateCR에 이미지 서명을 추가해야 합니다. 이미지 서명을 가져오려면 다음 단계를 수행합니다.다음 명령을 실행하여 원하는 OpenShift Container Platform 태그를 지정합니다.
OCP_RELEASE_NUMBER=<release_version>
$ OCP_RELEASE_NUMBER=<release_version>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 클러스터의 아키텍처를 지정합니다.
ARCHITECTURE=<cluster_architecture>
$ ARCHITECTURE=<cluster_architecture>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
x86_64,aarch64,s390x또는ppc64le과 같은 클러스터의 아키텍처를 지정합니다.
다음 명령을 실행하여 Quay에서 릴리스 이미지 다이제스트를 가져옵니다.
DIGEST="$(oc adm release info quay.io/openshift-release-dev/ocp-release:${OCP_RELEASE_NUMBER}-${ARCHITECTURE} | sed -n 's/Pull From: .*@//p')"$ DIGEST="$(oc adm release info quay.io/openshift-release-dev/ocp-release:${OCP_RELEASE_NUMBER}-${ARCHITECTURE} | sed -n 's/Pull From: .*@//p')"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 다이제스트 알고리즘을 설정합니다.
DIGEST_ALGO="${DIGEST%%:*}"$ DIGEST_ALGO="${DIGEST%%:*}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 다이제스트 서명을 설정합니다.
DIGEST_ENCODED="${DIGEST#*:}"$ DIGEST_ENCODED="${DIGEST#*:}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 mirror.openshift.com 웹 사이트에서 이미지 서명을 가져옵니다.
SIGNATURE_BASE64=$(curl -s "https://mirror.openshift.com/pub/openshift-v4/signatures/openshift/release/${DIGEST_ALGO}=${DIGEST_ENCODED}/signature-1" | base64 -w0 && echo)$ SIGNATURE_BASE64=$(curl -s "https://mirror.openshift.com/pub/openshift-v4/signatures/openshift/release/${DIGEST_ALGO}=${DIGEST_ENCODED}/signature-1" | base64 -w0 && echo)Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
checksum-<OCP_RELEASE_NUMBER>.yaml파일에 이미지 서명을 저장합니다.cat >checksum-${OCP_RELEASE_NUMBER}.yaml <<EOF$ cat >checksum-${OCP_RELEASE_NUMBER}.yaml <<EOFCopy to Clipboard Copied! Toggle word wrap Toggle overflow ${DIGEST_ALGO}-${DIGEST_ENCODED}: ${SIGNATURE_BASE64} EOF${DIGEST_ALGO}-${DIGEST_ENCODED}: ${SIGNATURE_BASE64} EOFCopy to Clipboard Copied! Toggle word wrap Toggle overflow
업데이트 그래프를 준비합니다. 업데이트 그래프를 준비할 수 있는 두 가지 옵션이 있습니다.
OpenShift 업데이트 서비스를 사용합니다.
hub 클러스터에 그래프를 설정하는 방법에 대한 자세한 내용은 OpenShift Update Service용 Operator 배포 및 그래프 데이터 init 컨테이너 빌드를 참조하십시오.
업스트림 그래프의 로컬 사본을 만듭니다. 관리 클러스터에 액세스할 수 있는 연결이 끊긴 환경의
http또는https서버에서 업데이트 그래프를 호스팅합니다. 업데이트 그래프를 다운로드하려면 다음 명령을 사용하십시오.curl -s https://api.openshift.com/api/upgrades_info/v1/graph?channel=stable-4.15 -o ~/upgrade-graph_stable-4.15
$ curl -s https://api.openshift.com/api/upgrades_info/v1/graph?channel=stable-4.15 -o ~/upgrade-graph_stable-4.15Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Operator를 업데이트하려면 다음 작업을 수행해야 합니다.
- Operator 카탈로그를 미러링합니다. "연결이 끊긴 클러스터에 사용하기 위해 Operator 카탈로그 미러링" 섹션의 절차에 따라 원하는 Operator 이미지가 미러링되었는지 확인합니다.
12.1.2. 플랫폼 업데이트 수행
TALM으로 플랫폼 업데이트를 수행할 수 있습니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- GitOps Zero Touch Provisioning (ZTP)을 최신 버전으로 업데이트합니다.
- GitOps ZTP를 사용하여 하나 이상의 관리 클러스터를 프로비저닝합니다.
- 원하는 이미지 저장소를 미러링합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - hub 클러스터에 RHACM 정책을 생성합니다.
프로세스
플랫폼 업데이트에 대한
PolicyGenTemplateCR을 생성합니다.PolicyGenTemplateCR의 다음 내용을du-upgrade.yaml파일에 저장합니다.플랫폼 업데이트를 위한
PolicyGenTemplate예Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
ConfigMapCR에는 업데이트할 원하는 릴리스 이미지의 서명이 포함되어 있습니다.- 2
- 원하는 OpenShift Container Platform 릴리스의 이미지 서명을 표시합니다. "환경 설정" 섹션의 절차에 따라 저장한
checksum-${OCP_RELEASE_NUMBER}.yaml파일에서 서명을 가져옵니다. - 3
- 원하는 OpenShift Container Platform 이미지가 포함된 미러 저장소를 표시합니다. "환경 설정" 섹션의 절차를 따를 때 저장한
imageContentSources.yaml파일에서 미러를 가져옵니다. - 4
- 업데이트를 트리거할
ClusterVersionCR을 표시합니다.채널,업스트림및desiredVersion필드는 모두 이미지 사전 캐싱에 필요합니다.
PolicyGenTemplateCR은 다음 두 가지 정책을 생성합니다.-
du-upgrade-platform-prep정책은 플랫폼 업데이트에 대한 준비 작업을 수행합니다. 원하는 릴리스 이미지 서명에 대한ConfigMapCR을 생성하고 미러링된 릴리스 이미지 저장소의 이미지 콘텐츠 소스를 생성하고, 원하는 업데이트 채널 및 연결이 끊긴 환경에서 관리 클러스터에서 연결할 수 있는 업데이트 그래프로 클러스터 버전을 업데이트합니다. -
du-upgrade-platform-upgrade정책은 플랫폼 업그레이드를 수행하는 데 사용됩니다.
PolicyGenTemplateCR의 GitOps ZTP Git 리포지토리에 있는kustomization.yaml파일에du-upgrade.yaml파일 내용을 추가하고 Git 리포지토리로 변경 사항을 내보냅니다.rgocd는 Git 리포지토리에서 변경 사항을 가져와서 hub 클러스터에 정책을 생성합니다.
다음 명령을 실행하여 생성된 정책을 확인합니다.
oc get policies -A | grep platform-upgrade
$ oc get policies -A | grep platform-upgradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
spec.enable필드가false로 설정된 상태에서 플랫폼 업데이트에 대한ClusterGroupUpdateCR을 생성합니다.du-upgrade-platform-upgrade-prep 및 du-upgrade-platform-upgrade정책 및 대상 클러스터를 다음 예와 같이cgu-platform-upgrade.yml파일에 사용하여 플랫폼 업데이트ClusterGroupUpdateCR의 콘텐츠를 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 Hub 클러스터에
ClusterGroupUpdateCR을 적용합니다.oc apply -f cgu-platform-upgrade.yml
$ oc apply -f cgu-platform-upgrade.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
선택 사항: 플랫폼 업데이트의 이미지를 사전 캐시합니다.
다음 명령을 실행하여
ClusterGroupUpdateCR에서 사전 캐싱을 활성화합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-platform-upgrade \ --patch '{"spec":{"preCaching": true}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-platform-upgrade \ --patch '{"spec":{"preCaching": true}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트 프로세스를 모니터링하고 사전 캐싱이 완료될 때까지 기다립니다. hub 클러스터에서 다음 명령을 실행하여 사전 캐싱 상태를 확인합니다.
oc get cgu cgu-platform-upgrade -o jsonpath='{.status.precaching.status}'$ oc get cgu cgu-platform-upgrade -o jsonpath='{.status.precaching.status}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
플랫폼 업데이트를 시작합니다.
다음 명령을 실행하여
cgu-platform-upgrade정책을 활성화하고 사전 캐싱을 비활성화합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-platform-upgrade \ --patch '{"spec":{"enable":true, "preCaching": false}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-platform-upgrade \ --patch '{"spec":{"enable":true, "preCaching": false}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 프로세스를 모니터링합니다. 완료되면 다음 명령을 실행하여 정책을 준수하는지 확인합니다.
oc get policies --all-namespaces
$ oc get policies --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.1.3. Operator 업데이트 수행
TALM을 사용하여 Operator 업데이트를 수행할 수 있습니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- GitOps Zero Touch Provisioning (ZTP)을 최신 버전으로 업데이트합니다.
- GitOps ZTP를 사용하여 하나 이상의 관리 클러스터를 프로비저닝합니다.
- 번들 이미지에서 참조하는 원하는 인덱스 이미지, 번들 이미지 및 모든 Operator 이미지를 미러링합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - hub 클러스터에 RHACM 정책을 생성합니다.
프로세스
Operator 업데이트의
PolicyGenTemplateCR을 업데이트합니다.du-upgrade.yamlPolicyGenTemplateCR을 업데이트합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 인덱스 이미지 URL에는 원하는 Operator 이미지가 포함되어 있습니다. 인덱스 이미지가 항상 동일한 이미지 이름 및 태그로 푸시되는 경우 이 변경이 필요하지 않습니다.
- 2
- OLM(Operator Lifecycle Manager)에서
registryPoll.interval필드를 사용하여 새 Operator 버전의 인덱스 이미지를 폴링하는 빈도를 설정합니다. 이 변경 사항은 y-stream 및 z-stream Operator 업데이트를 위해 새 인덱스 이미지 태그가 항상 푸시되는 경우 필요하지 않습니다.registryPoll.interval필드는 업데이트를 신속하게 처리하기 위해 더 짧은 간격으로 설정할 수 있지만 더 짧은 간격은 계산 부하를 늘리십시오. 이 문제를 대응하려면 업데이트가 완료되면registryPoll.interval을 기본값으로 복원할 수 있습니다. - 3
- 카탈로그 연결의 마지막으로 관찰된 상태입니다.
READY값을 사용하면CatalogSource정책이 준비되어 인덱스 Pod를 가져와 실행 중임을 나타냅니다. 이렇게 하면 TALM이 최신 정책 준수 상태를 기반으로 Operator를 업그레이드합니다.
이번 업데이트에서는 원하는 Operator 이미지가 포함된 새 인덱스 이미지로
redhat-operators-disconnected카탈로그 소스를 업데이트하기 위해 하나의 정책인du-upgrade-operator-catsrc-policy를 생성합니다.참고Operator에 이미지 사전 캐싱을 사용하고
redhat-operators-disconnected이외의 다른 카탈로그 소스의 Operator가 있는 경우 다음 작업을 수행해야 합니다.- 다른 카탈로그 소스에 대해 새 인덱스 이미지 또는 레지스트리 폴링 간격 업데이트를 사용하여 별도의 카탈로그 소스 정책을 준비합니다.
- 다른 카탈로그 소스의 Operator에 대해 별도의 서브스크립션 정책을 준비합니다.
예를 들어 원하는 SRIOV-FEC Operator는
certified-operators카탈로그 소스에서 사용할 수 있습니다. 카탈로그 소스 및 Operator 서브스크립션을 업데이트하려면 다음 내용을 추가하여du-upgrade-fec-catsrc-policy및du-upgrade-subscriptions-fec-policy: 두 가지 정책을 생성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Common
PolicyGenTemplateCR이 있는 경우 지정된 서브스크립션 채널을 제거합니다. GitOps ZTP 이미지의 기본 서브스크립션 채널은 업데이트에 사용됩니다.참고GitOps ZTP 4.15를 통해 적용되는 Operator의 기본 채널은
performance-addon-operator를 제외하고안정적입니다. OpenShift Container Platform 4.11부터performance-addon-operator기능이node-tuning-operator로 이동되었습니다. 4.10 릴리스의 경우 PAO의 기본 채널은v4.10입니다. 공통PolicyGenTemplateCR에서 기본 채널을 지정할 수도 있습니다.PolicyGenTemplateCR 업데이트를 GitOps ZTP Git 리포지토리로 내보냅니다.rgocd는 Git 리포지토리에서 변경 사항을 가져와서 hub 클러스터에 정책을 생성합니다.
다음 명령을 실행하여 생성된 정책을 확인합니다.
oc get policies -A | grep -E "catsrc-policy|subscription"
$ oc get policies -A | grep -E "catsrc-policy|subscription"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Operator 업데이트를 시작하기 전에 필요한 카탈로그 소스 업데이트를 적용합니다.
카탈로그 소스 정책 및 대상 관리 클러스터를
cgu-operator-upgrade-prep파일에 사용하여 operator-upgrade-prep라는ClusterGroupUpgradeCR의 콘텐츠를 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 허브 클러스터에 정책을 적용합니다.
oc apply -f cgu-operator-upgrade-prep.yml
$ oc apply -f cgu-operator-upgrade-prep.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트 프로세스를 모니터링합니다. 완료되면 다음 명령을 실행하여 정책을 준수하는지 확인합니다.
oc get policies -A | grep -E "catsrc-policy"
$ oc get policies -A | grep -E "catsrc-policy"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
spec.enable필드를false로 설정하여 Operator 업데이트에 대한ClusterGroupUpgradeCR을 생성합니다.다음 예와 같이 Operator 업데이트
ClusterGroupUpgradeCR의 콘텐츠를du-upgrade-operator-catsrc-policy정책 및 공통PolicyGenTemplate에서 생성한 서브스크립션 정책과 대상 클러스터에서cgu-operator-upgrade.yml파일에 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 참고하나의
ClusterGroupUpgradeCR은ClusterGroupUpgradeCR에 포함된 하나의 카탈로그 소스에서 서브스크립션 정책에 정의된 Operator의 이미지만 사전 캐시할 수 있습니다. SRIOV-FEC Operator의 예와 같이 원하는 Operator가 다양한 카탈로그 소스의 경우 SRIOV-FEC Operator 이미지에 대한du-upgrade-fec-catsrc-policy및du-upgrade-subscriptions-fec-policy정책을 사용하여 다른ClusterGroupUpgradeCR을 생성해야 합니다.다음 명령을 실행하여 hub 클러스터에
ClusterGroupUpgradeCR을 적용합니다.oc apply -f cgu-operator-upgrade.yml
$ oc apply -f cgu-operator-upgrade.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
선택 사항: Operator 업데이트의 이미지를 사전 캐시합니다.
이미지 사전 캐싱을 시작하기 전에 다음 명령을 실행하여 서브스크립션 정책이 이 시점에서
NonCompliant인지 확인합니다.oc get policy common-subscriptions-policy -n <policy_namespace>
$ oc get policy common-subscriptions-policy -n <policy_namespace>Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME REMEDIATION ACTION COMPLIANCE STATE AGE common-subscriptions-policy inform NonCompliant 27d
NAME REMEDIATION ACTION COMPLIANCE STATE AGE common-subscriptions-policy inform NonCompliant 27dCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
ClusterGroupUpgradeCR에서 pre-caching을 활성화합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-operator-upgrade \ --patch '{"spec":{"preCaching": true}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-operator-upgrade \ --patch '{"spec":{"preCaching": true}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 프로세스를 모니터링하고 사전 캐싱이 완료될 때까지 기다립니다. 관리 클러스터에서 다음 명령을 실행하여 사전 캐싱 상태를 확인합니다.
oc get cgu cgu-operator-upgrade -o jsonpath='{.status.precaching.status}'$ oc get cgu cgu-operator-upgrade -o jsonpath='{.status.precaching.status}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 업데이트를 시작하기 전에 사전 캐싱이 완료되었는지 확인합니다.
oc get cgu -n default cgu-operator-upgrade -ojsonpath='{.status.conditions}' | jq$ oc get cgu -n default cgu-operator-upgrade -ojsonpath='{.status.conditions}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Operator 업데이트를 시작합니다.
cgu-operator-upgradeClusterGroupUpgradeCR을 활성화하고 다음 명령을 실행하여 Operator 업데이트를 시작하도록 사전 캐싱을 비활성화합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-operator-upgrade \ --patch '{"spec":{"enable":true, "preCaching": false}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-operator-upgrade \ --patch '{"spec":{"enable":true, "preCaching": false}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 프로세스를 모니터링합니다. 완료되면 다음 명령을 실행하여 정책을 준수하는지 확인합니다.
oc get policies --all-namespaces
$ oc get policies --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.1.3.1. 최신 정책 준수 상태로 인해 누락된 Operator 업데이트 문제 해결
일부 시나리오에서는 TALM( Topology Aware Lifecycle Manager)에서 최신 정책 준수 상태로 인해 Operator 업데이트가 누락될 수 있습니다.
카탈로그 소스 업데이트 후 OLM(Operator Lifecycle Manager)에서 서브스크립션 상태를 업데이트하는 데 시간이 걸립니다. TALM에서 수정이 필요한지 여부를 결정하는 동안 서브스크립션 정책의 상태가 계속 준수로 표시될 수 있습니다. 결과적으로 서브스크립션 정책에 지정된 Operator가 업그레이드되지 않습니다.
이 시나리오를 방지하려면 PolicyGenTemplate 에 다른 카탈로그 소스 구성을 추가하고 업데이트가 필요한 Operator의 서브스크립션에 이 구성을 지정합니다.
프로세스
PolicyGenTemplate리소스에 카탈로그 소스 구성을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트가 필요한 Operator의 새 구성을 가리키도록
Subscription리소스를 업데이트합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
PolicyGenTemplate리소스에 정의된 추가 카탈로그 소스 구성의 이름을 입력합니다.
12.1.4. 플랫폼 및 Operator 업데이트를 함께 수행
플랫폼 및 Operator 업데이트를 동시에 수행할 수 있습니다.
사전 요구 사항
- TALM(토폴로지 Aware Lifecycle Manager)을 설치합니다.
- GitOps Zero Touch Provisioning (ZTP)을 최신 버전으로 업데이트합니다.
- GitOps ZTP를 사용하여 하나 이상의 관리 클러스터를 프로비저닝합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다. - hub 클러스터에 RHACM 정책을 생성합니다.
프로세스
-
"플랫폼 업데이트 수행" 및 "Operator 업데이트 수행" 섹션에 설명된 단계에 따라 업데이트에 대한
PolicyGenTemplateCR을 생성합니다. 플랫폼 및 Operator 업데이트에 대한 prep 작업을 적용합니다.
플랫폼 업데이트 준비 작업, 카탈로그 소스 업데이트 및 대상 클러스터에 대한 정책을 사용하여
ClusterGroupUpgradeCR의 콘텐츠를cgu-platform-operator-upgrade-prep.yml파일에 저장합니다. 예를 들면 다음과 같습니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
cgu-platform-operator-upgrade-prep.yml파일을 hub 클러스터에 적용합니다.oc apply -f cgu-platform-operator-upgrade-prep.yml
$ oc apply -f cgu-platform-operator-upgrade-prep.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 프로세스를 모니터링합니다. 완료되면 다음 명령을 실행하여 정책을 준수하는지 확인합니다.
oc get policies --all-namespaces
$ oc get policies --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
플랫폼에 대한
ClusterGroupUpdateCR을 생성하고spec.enable필드를false로 설정하여 Operator를 업데이트합니다.다음 예와 같이 플랫폼 및 Operator의 콘텐츠를 정책 및 대상 클러스터를 사용하여
cgu-platform-operator-upgrade.yml파일에 저장합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여
cgu-platform-operator-upgrade.yml파일을 hub 클러스터에 적용합니다.oc apply -f cgu-platform-operator-upgrade.yml
$ oc apply -f cgu-platform-operator-upgrade.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
선택 사항: 플랫폼 및 Operator 업데이트의 이미지를 사전 캐시합니다.
다음 명령을 실행하여
ClusterGroupUpgradeCR에서 pre-caching을 활성화합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-du-upgrade \ --patch '{"spec":{"preCaching": true}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-du-upgrade \ --patch '{"spec":{"preCaching": true}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 업데이트 프로세스를 모니터링하고 사전 캐싱이 완료될 때까지 기다립니다. 관리 클러스터에서 다음 명령을 실행하여 사전 캐싱 상태를 확인합니다.
oc get jobs,pods -n openshift-talm-pre-cache
$ oc get jobs,pods -n openshift-talm-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 업데이트를 시작하기 전에 사전 캐싱이 완료되었는지 확인합니다.
oc get cgu cgu-du-upgrade -ojsonpath='{.status.conditions}'$ oc get cgu cgu-du-upgrade -ojsonpath='{.status.conditions}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
플랫폼 및 Operator 업데이트를 시작합니다.
다음 명령을 실행하여
cgu-du-upgradeClusterGroupUpgradeCR을 활성화하여 플랫폼 및 Operator 업데이트를 시작합니다.oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-du-upgrade \ --patch '{"spec":{"enable":true, "preCaching": false}}' --type=merge$ oc --namespace=default patch clustergroupupgrade.ran.openshift.io/cgu-du-upgrade \ --patch '{"spec":{"enable":true, "preCaching": false}}' --type=mergeCopy to Clipboard Copied! Toggle word wrap Toggle overflow 프로세스를 모니터링합니다. 완료되면 다음 명령을 실행하여 정책을 준수하는지 확인합니다.
oc get policies --all-namespaces
$ oc get policies --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow 참고플랫폼 및 Operator 업데이트의 CR은 설정을
spec.enable: true로 구성하여 처음부터 생성할 수 있습니다. 이 경우 업데이트는 사전 캐싱이 완료된 직후 시작되어 CR을 수동으로 활성화할 필요가 없습니다.사전 캐싱과 업데이트 모두 정책, 배치 바인딩, 배치 규칙, 관리 클러스터 작업 및 관리 클러스터 뷰와 같은 추가 리소스를 생성하여 절차를 완료하는 데 도움이 됩니다.
afterCompletion.deleteObjects필드를true로 설정하면 업데이트가 완료된 후 이러한 리소스가 모두 삭제됩니다.
12.1.5. 배포된 클러스터에서 Performance Addon Operator 서브스크립션 제거
이전 버전의 OpenShift Container Platform에서 Performance Addon Operator는 애플리케이션에 대한 짧은 대기 시간 성능 튜닝을 제공합니다. OpenShift Container Platform 4.11 이상에서 이러한 기능은 Node Tuning Operator의 일부입니다.
OpenShift Container Platform 4.11 이상을 실행하는 클러스터에 Performance Addon Operator를 설치하지 마십시오. OpenShift Container Platform 4.11 이상으로 업그레이드하면 Node Tuning Operator가 Performance Addon Operator를 자동으로 제거합니다.
Operator를 다시 설치하지 않도록 Performance Addon Operator 서브스크립션을 생성하는 정책을 제거해야 합니다.
참조 DU 프로필에는 PolicyGenTemplate CR common-ranGen.yaml 의 Performance Addon Operator가 포함되어 있습니다. 배포된 관리 클러스터에서 서브스크립션을 제거하려면 common-ranGen.yaml 을 업데이트해야 합니다.
OpenShift Container Platform 4.11 이상에 Performance Addon Operator 4.10.3-5 이상을 설치하는 경우 Performance Addon Operator는 클러스터 버전을 감지하고 Node Tuning Operator 함수를 방해하지 않도록 자동으로 hibernates를 탐지합니다. 그러나 최상의 성능을 보장하기 위해 OpenShift Container Platform 4.11 클러스터에서 Performance Addon Operator를 제거하십시오.
사전 요구 사항
- 사용자 지정 사이트 구성 데이터를 관리하는 Git 리포지토리를 생성합니다. 리포지토리는 hub 클러스터에서 액세스할 수 있어야 하며 ArgoCD의 소스 리포지토리로 정의해야 합니다.
- OpenShift Container Platform 4.11 이상으로 업데이트합니다.
-
cluster-admin권한이 있는 사용자로 로그인합니다.
프로세스
common-ranGen.yaml파일에서 Performance Addon Operator 네임스페이스, Operator group 및 서브스크립션에 대해complianceType을mustnothave로 변경합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
사용자 정의 사이트 리포지토리와 변경 사항을 병합하고 ArgoCD 애플리케이션이 변경 사항을 허브 클러스터에 동기화할 때까지 기다립니다.
common-subscriptions-policy정책의 상태는 비준수. - 토폴로지 Aware Lifecycle Manager를 사용하여 대상 클러스터에 변경 사항을 적용합니다. 구성 변경 사항 롤아웃에 대한 자세한 내용은 "추가 리소스" 섹션을 참조하십시오.
프로세스를 모니터링합니다. 대상 클러스터의
common-subscriptions-policy정책이Compliant인 경우 Performance Addon Operator가 클러스터에서 제거되었습니다. 다음 명령을 실행하여common-subscriptions-policy의 상태를 가져옵니다.oc get policy -n ztp-common common-subscriptions-policy
$ oc get policy -n ztp-common common-subscriptions-policyCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
common-ranGen.yaml파일의.spec.sourceFiles에서 Performance Addon Operator 네임스페이스, Operator group 및 서브스크립션 CR을 삭제합니다. - 사용자 정의 사이트 리포지토리와 변경 사항을 병합하고 ArgoCD 애플리케이션이 변경 사항을 허브 클러스터에 동기화할 때까지 기다립니다. 정책은 그대로 유지됩니다.
12.1.6. 단일 노드 OpenShift 클러스터에서 TALM을 사용하여 사용자 지정 이미지 미리 캐싱
애플리케이션을 업그레이드하기 전에 단일 노드 OpenShift 클러스터에서 애플리케이션별 워크로드 이미지를 사전 캐시할 수 있습니다.
다음 CR(사용자 정의 리소스)을 사용하여 사전 캐싱 작업에 대한 구성 옵션을 지정할 수 있습니다.
-
PreCachingConfigCR -
ClusterGroupUpgradeCR
PreCachingConfig CR의 모든 필드는 선택 사항입니다.
PreCachingConfig CR의 예
- 1
- 기본적으로 TALM은 관리 클러스터 정책에서
platformImage,operatorsIndexes및operatorsPackagesAndChannels필드를 자동으로 채웁니다. 이러한 필드의 기본 TALM 파생 값을 재정의하는 값을 지정할 수 있습니다. - 2
- 클러스터에서 필요한 최소 디스크 공간을 지정합니다. 지정되지 않은 경우 TALM은 OpenShift Container Platform 이미지의 기본값을 정의합니다. 디스크 공간 필드에는 정수 값과 스토리지 유닛이 포함되어야 합니다. 예:
40GiB,200MB,1TiB. - 3
- 일치하는 이미지 이름에 따라 사전 캐싱에서 제외할 이미지를 지정합니다.
- 4
- 사전 캐시할 추가 이미지 목록을 지정합니다.
PreCachingConfig CR 참조가 있는 ClusterGroupUpgrade CR의 예
12.1.6.1. 사전 캐싱을 위한 사용자 정의 리소스 생성
ClusterGroupUpgrade CR 전에 PreCachingConfig CR을 생성해야 합니다.
사전 캐시하려는 추가 이미지 목록을 사용하여
PreCachingConfigCR을 생성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow preCaching필드를true로 설정하여ClusterGroupUpgradeCR을 생성하고 이전 단계에서 생성한PreCachingConfigCR을 지정합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 주의클러스터에 이미지를 설치한 후에는 변경하거나 삭제할 수 없습니다.
이미지를 사전 캐싱하려면 다음 명령을 실행하여
ClusterGroupUpgradeCR을 적용합니다.oc apply -f cgu.yaml
$ oc apply -f cgu.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
TALM은 ClusterGroupUpgrade CR을 확인합니다.
이 시점에서 TALM 사전 캐싱 워크플로우를 계속 사용할 수 있습니다.
모든 사이트는 동시에 사전 캐시됩니다.
검증
다음 명령을 실행하여
ClusterUpgradeGroupCR이 적용되는 hub 클러스터에서 사전 캐싱 상태를 확인합니다.oc get cgu <cgu_name> -n <cgu_namespace> -oyaml
$ oc get cgu <cgu_name> -n <cgu_namespace> -oyamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 정책이 있는지 확인하여 사전 캐싱 구성의 유효성을 검사합니다.
ClusterGroupUpgrade및PreCachingConfigCR의 유효한 구성으로 인해 다음과 같은 상태가 발생합니다.유효한 CR의 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 잘못된 PreCachingConfig CR의 예
Type: "PrecacheSpecValid" Status: False, Reason: "PrecacheSpecIncomplete" Message: "Precaching spec is incomplete: failed to get PreCachingConfig resource due to PreCachingConfig.ran.openshift.io "<pre-caching_cr_name>" not found"
Type: "PrecacheSpecValid" Status: False, Reason: "PrecacheSpecIncomplete" Message: "Precaching spec is incomplete: failed to get PreCachingConfig resource due to PreCachingConfig.ran.openshift.io "<pre-caching_cr_name>" not found"Copy to Clipboard Copied! Toggle word wrap Toggle overflow 관리 클러스터에서 다음 명령을 실행하여 사전 캐싱 작업을 찾을 수 있습니다.
oc get jobs -n openshift-talo-pre-cache
$ oc get jobs -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 진행 중인 사전 캐싱 작업 예
NAME COMPLETIONS DURATION AGE pre-cache 0/1 1s 1s
NAME COMPLETIONS DURATION AGE pre-cache 0/1 1s 1sCopy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 사전 캐싱 작업에 대해 생성된 Pod의 상태를 확인할 수 있습니다.
oc describe pod pre-cache -n openshift-talo-pre-cache
$ oc describe pod pre-cache -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 진행 중인 사전 캐싱 작업 예
Type Reason Age From Message Normal SuccesfulCreate 19s job-controller Created pod: pre-cache-abcd1
Type Reason Age From Message Normal SuccesfulCreate 19s job-controller Created pod: pre-cache-abcd1Copy to Clipboard Copied! Toggle word wrap Toggle overflow 다음 명령을 실행하여 작업 상태에 대한 실시간 업데이트를 가져올 수 있습니다.
oc logs -f pre-cache-abcd1 -n openshift-talo-pre-cache
$ oc logs -f pre-cache-abcd1 -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 사전 캐시 작업이 성공적으로 완료되었는지 확인하려면 다음 명령을 실행합니다.
oc describe pod pre-cache -n openshift-talo-pre-cache
$ oc describe pod pre-cache -n openshift-talo-pre-cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow 완료된 사전 캐시 작업의 예
Type Reason Age From Message Normal SuccesfulCreate 5m19s job-controller Created pod: pre-cache-abcd1 Normal Completed 19s job-controller Job completed
Type Reason Age From Message Normal SuccesfulCreate 5m19s job-controller Created pod: pre-cache-abcd1 Normal Completed 19s job-controller Job completedCopy to Clipboard Copied! Toggle word wrap Toggle overflow 단일 노드 OpenShift에서 이미지가 성공적으로 사전 캐시되었는지 확인하려면 다음을 수행하십시오.
디버그 모드에서 노드로 들어갑니다.
oc debug node/cnfdf00.example.lab
$ oc debug node/cnfdf00.example.labCopy to Clipboard Copied! Toggle word wrap Toggle overflow root를
호스트로변경 :chroot /host/
$ chroot /host/Copy to Clipboard Copied! Toggle word wrap Toggle overflow 원하는 이미지를 검색합니다.
sudo podman images | grep <operator_name>
$ sudo podman images | grep <operator_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.2. GitOps ZTP의 자동 생성 ClusterGroupUpgrade CR 정보
TALM에는 hub 클러스터에서 ManagedCluster CR의 Ready 상태를 모니터링하고 GitOps Zero Touch Provisioning (ZTP)에 대한 ClusterGroupUpgrade CR을 생성하는 ManagedClusterForCGU 라는 컨트롤러가 있습니다.
ztp-done 레이블이 적용되지 않은 Ready 상태의 관리형 클러스터의 경우 ManagedClusterForCGU 컨트롤러는 GitOps ZTP 프로세스 중에 생성되는 관련 RHACM 정책을 사용하여 ztp-install 네임스페이스에 ClusterGroupUpgrade CR을 자동으로 생성합니다. 그런 다음 TALM은 자동 생성된 ClusterGroupUpgrade CR에 나열된 구성 정책 세트를 수정하여 구성 CR을 관리 클러스터로 푸시합니다.
클러스터가 Ready 상태가 되는 시점에 관리 클러스터에 대한 정책이 없는 경우 정책이 생성되지 않은 ClusterGroupUpgrade CR이 생성됩니다. ClusterGroupUpgrade 가 완료되면 관리형 클러스터는 ztp-done 로 레이블이 지정됩니다. 해당 관리 클러스터에 적용하려는 정책이 있는 경우 2일 차 작업으로 ClusterGroupUpgrade 를 수동으로 생성합니다.
GitOps ZTP의 자동 생성 ClusterGroupUpgrade CR의 예
13장. GitOps ZTP를 사용하여 단일 노드 OpenShift 클러스터 확장
ZTP(ZTP)를 사용하여 단일 노드 OpenShift 클러스터를 확장할 수 있습니다. 단일 노드 OpenShift 클러스터에 작업자 노드를 추가하면 원래 단일 노드 OpenShift 클러스터는 컨트롤 플레인 노드 역할을 유지합니다. 작업자 노드를 추가하는 경우 기존 단일 노드 OpenShift 클러스터에 대한 다운타임이 필요하지 않습니다.
단일 노드 OpenShift 클러스터에 추가할 수 있는 작업자 노드 수에 지정된 제한이 없지만 추가 작업자 노드의 컨트롤 플레인 노드에서 예약된 CPU 할당을 다시 평가해야 합니다.
작업자 노드에 워크로드 파티셔닝이 필요한 경우 노드를 설치하기 전에 허브 클러스터에서 관리형 클러스터 정책을 배포하고 수정해야 합니다. 이렇게 하면 GitOps ZTP 워크플로우가 MachineConfig ignition 파일을 작업자 노드에 적용하기 전에 워크로드 파티셔닝 MachineConfig 오브젝트가 렌더링되고 작업자 머신 구성 풀과 연결됩니다.
먼저 정책을 수정한 다음 작업자 노드를 설치하는 것이 좋습니다. 작업자 노드를 설치한 후 워크로드 파티셔닝 매니페스트를 생성하는 경우 노드를 수동으로 드레이닝하고 데몬 세트에서 관리하는 모든 Pod를 삭제해야 합니다. 관리 데몬 세트에서 새 Pod를 생성하면 새 Pod에 워크로드 파티션 프로세스가 수행됩니다.
GitOps ZTP를 사용하여 단일 노드 OpenShift 클러스터에 작업자 노드를 추가하는 것은 기술 프리뷰 기능 전용입니다. 기술 프리뷰 기능은 Red Hat 프로덕션 서비스 수준 계약(SLA)에서 지원되지 않으며 기능적으로 완전하지 않을 수 있습니다. 따라서 프로덕션 환경에서 사용하는 것은 권장하지 않습니다. 이러한 기능을 사용하면 향후 제품 기능을 조기에 이용할 수 있어 개발 과정에서 고객이 기능을 테스트하고 피드백을 제공할 수 있습니다.
Red Hat 기술 프리뷰 기능의 지원 범위에 대한 자세한 내용은 기술 프리뷰 기능 지원 범위를 참조하십시오.
13.1. 작업자 노드에 프로필 적용
DU 프로필을 사용하여 추가 작업자 노드를 구성할 수 있습니다.
ZTP(ZTP) 공통, 그룹 및 사이트별 PolicyGenTemplate 리소스를 사용하여 작업자 노드 클러스터에 DU(RAN 분산 단위) 프로필을 적용할 수 있습니다. ArgoCD 정책 애플리케이션에 연결된 GitOps ZTP 파이프라인에는 ztp-site-generate 컨테이너를 추출할 때 out/argocd/example/policygentemplates 폴더에서 찾을 수 있는 다음 CR이 포함되어 있습니다.
-
common-ranGen.yaml -
group-du-sno-ranGen.yaml -
example-sno-site.yaml -
ns.yaml -
kustomization.yaml
작업자 노드에서 DU 프로필을 구성하는 것은 업그레이드로 간주됩니다. 업그레이드 흐름을 시작하려면 기존 정책을 업데이트하거나 추가 정책을 생성해야 합니다. 그런 다음 클러스터 그룹의 정책을 조정하려면 ClusterGroupUpgrade CR을 생성해야 합니다.
13.2. (선택 사항) PTP 및 SR-IOV 데몬 선택기 호환성 활성화
ZTP(ZTP) 플러그인 버전 4.11 이상을 사용하여 DU 프로필을 배포한 경우 master 로 표시된 노드에만 데몬을 배치하도록 PTP 및 SR-IOV Operator를 구성할 수 있습니다. 이 구성으로 인해 PTP 및 SR-IOV 데몬이 작업자 노드에서 작동하지 않습니다. 시스템에 PTP 및 SR-IOV 데몬 노드 선택기가 잘못 구성된 경우 작업자 DU 프로필 구성을 진행하기 전에 데몬을 변경해야 합니다.
프로세스
spoke 클러스터 중 하나에서 PTP Operator의 데몬 노드 선택기 설정을 확인합니다.
oc get ptpoperatorconfig/default -n openshift-ptp -ojsonpath='{.spec}' | jq$ oc get ptpoperatorconfig/default -n openshift-ptp -ojsonpath='{.spec}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow PTP Operator의 출력 예
{"daemonNodeSelector":{"node-role.kubernetes.io/master":""}}{"daemonNodeSelector":{"node-role.kubernetes.io/master":""}}1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 노드 선택기를
master로 설정하면 변경 사항이 필요한 GitOps ZTP 플러그인 버전과 함께 spoke가 배포되었습니다.
spoke 클러스터 중 하나에서 SR-IOV Operator의 데몬 노드 선택기 설정을 확인합니다.
oc get sriovoperatorconfig/default -n \ openshift-sriov-network-operator -ojsonpath='{.spec}' | jq$ oc get sriovoperatorconfig/default -n \ openshift-sriov-network-operator -ojsonpath='{.spec}' | jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow SR-IOV Operator의 출력 예
{"configDaemonNodeSelector":{"node-role.kubernetes.io/worker":""},"disableDrain":false,"enableInjector":true,"enableOperatorWebhook":true}{"configDaemonNodeSelector":{"node-role.kubernetes.io/worker":""},"disableDrain":false,"enableInjector":true,"enableOperatorWebhook":true}1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- 노드 선택기를
master로 설정하면 변경 사항이 필요한 GitOps ZTP 플러그인 버전과 함께 spoke가 배포되었습니다.
그룹 정책에서 다음
complianceType및spec항목을 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 중요daemonNodeSelector필드를 변경하면 임시 PTP 동기화 손실 및 SR-IOV 연결이 손실됩니다.- Git의 변경 사항을 커밋한 다음 GitOps ZTP ArgoCD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
13.3. PTP 및 SR-IOV 노드 선택기 호환성
PTP 구성 리소스 및 SR-IOV 네트워크 노드 정책은 node-role.kubernetes.io/master: "" 를 노드 선택기로 사용합니다. 추가 작업자 노드에 컨트롤 플레인 노드와 동일한 NIC 구성이 있는 경우 컨트롤 플레인 노드를 구성하는 데 사용되는 정책을 작업자 노드에 재사용할 수 있습니다. 그러나 "node-role.kubernetes.io/worker" 레이블과 같이 두 노드 유형을 모두 선택하도록 노드 선택기를 변경해야 합니다.
13.4. PolicyGenTemplate CR을 사용하여 작업자 노드 정책을 작업자 노드에 적용
작업자 노드에 대한 정책을 생성할 수 있습니다.
프로세스
다음 정책 템플릿을 생성합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 일반
MachineConfigCR은 작업자 노드에서 워크로드 파티셔닝을 구성하는 데 사용됩니다.crio및kubelet구성 파일의 콘텐츠를 생성할 수 있습니다.-
ArgoCD 정책 애플리케이션에서 모니터링하는 Git 리포지토리에 생성된
정책템플릿을 추가합니다. -
kustomization.yaml파일에 정책을 추가합니다. - Git의 변경 사항을 커밋한 다음 GitOps ZTP ArgoCD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
spoke 클러스터에 대한 새 정책을 수정하려면 TALM 사용자 정의 리소스를 생성합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.5. GitOps ZTP를 사용하여 단일 노드 OpenShift 클러스터에 작업자 노드 추가
기존 단일 노드 OpenShift 클러스터에 하나 이상의 작업자 노드를 추가하여 클러스터에서 사용 가능한 CPU 리소스를 늘릴 수 있습니다.
사전 요구 사항
- OpenShift Container Platform 4.11 이상 베어 메탈 허브 클러스터에서 RHACM 2.6 이상을 설치하고 구성
- 허브 클러스터에 토폴로지 Aware Lifecycle Manager 설치
- hub 클러스터에 Red Hat OpenShift GitOps 설치
-
GitOps ZTP
ztp-site-generate컨테이너 이미지 버전 4.12 이상 사용 - GitOps ZTP를 사용하여 관리형 단일 노드 OpenShift 클러스터 배포
- RHACM 설명서에 설명된 대로 중앙 인프라 관리 구성
-
내부 API 끝점
api-int.<cluster_name>.<base_domain>을 확인하도록 클러스터를 제공하는 DNS를 구성합니다.
프로세스
example-sno.yamlSiteConfig매니페스트를 사용하여 클러스터를 배포한 경우 새 작업자 노드를spec.clusters['example-sno'].nodes목록에 추가합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow SiteConfig파일의spec.nodes섹션에 있는bmcCredentialsName필드에서 참조하는 새 호스트의 BMC 인증 시크릿을 생성합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Git의 변경 사항을 커밋한 다음 GitOps ZTP ArgoCD 애플리케이션에서 모니터링하는 Git 리포지토리로 내보냅니다.
ArgoCD
클러스터애플리케이션이 동기화되면 GitOps ZTP 플러그인에서 생성한 허브 클러스터에 두 개의 새 매니페스트가 표시됩니다.-
BareMetalHost NMStateConfig중요작업자 노드에 대해
cpuset필드를 구성해서는 안 됩니다. 노드 설치가 완료된 후 작업자 노드의 워크로드 파티셔닝이 관리 정책을 통해 추가됩니다.
-
검증
설치 프로세스를 여러 가지 방법으로 모니터링할 수 있습니다.
다음 명령을 실행하여 사전 프로비저닝 이미지가 생성되었는지 확인합니다.
oc get ppimg -n example-sno
$ oc get ppimg -n example-snoCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAMESPACE NAME READY REASON example-sno example-sno True ImageCreated example-sno example-node2 True ImageCreated
NAMESPACE NAME READY REASON example-sno example-sno True ImageCreated example-sno example-node2 True ImageCreatedCopy to Clipboard Copied! Toggle word wrap Toggle overflow 베어 메탈 호스트의 상태를 확인합니다.
oc get bmh -n example-sno
$ oc get bmh -n example-snoCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME STATE CONSUMER ONLINE ERROR AGE example-sno provisioned true 69m example-node2 provisioning true 4m50s
NAME STATE CONSUMER ONLINE ERROR AGE example-sno provisioned true 69m example-node2 provisioning true 4m50s1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
프로비저닝상태는 설치 미디어에서 부팅하는 노드가 진행 중임을 나타냅니다.
설치 프로세스를 지속적으로 모니터링합니다.
다음 명령을 실행하여 에이전트 설치 프로세스를 확인합니다.
oc get agent -n example-sno --watch
$ oc get agent -n example-sno --watchCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 작업자 노드 설치가 완료되면 작업자 노드 인증서가 자동으로 승인됩니다. 이 시점에서 작업자는
ManagedClusterInfo상태에 나타납니다. 다음 명령을 실행하여 상태를 확인합니다.oc get managedclusterinfo/example-sno -n example-sno -o \ jsonpath='{range .status.nodeList[*]}{.name}{"\t"}{.conditions}{"\t"}{.labels}{"\n"}{end}'$ oc get managedclusterinfo/example-sno -n example-sno -o \ jsonpath='{range .status.nodeList[*]}{.name}{"\t"}{.conditions}{"\t"}{.labels}{"\n"}{end}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
example-sno [{"status":"True","type":"Ready"}] {"node-role.kubernetes.io/master":"","node-role.kubernetes.io/worker":""} example-node2 [{"status":"True","type":"Ready"}] {"node-role.kubernetes.io/worker":""}example-sno [{"status":"True","type":"Ready"}] {"node-role.kubernetes.io/master":"","node-role.kubernetes.io/worker":""} example-node2 [{"status":"True","type":"Ready"}] {"node-role.kubernetes.io/worker":""}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14장. 단일 노드 OpenShift 배포를 위한 이미지 사전 캐싱
ZTP( GitOps Zero Touch Provisioning) 솔루션을 사용하여 다수의 클러스터를 배포하는 제한된 대역폭이 있는 환경에서는 OpenShift Container Platform을 부트스트랩 및 설치하는 데 필요한 모든 이미지를 다운로드하지 않도록 해야 합니다. 원격 단일 노드 OpenShift 사이트의 제한된 대역폭으로 인해 배포 시간이 길어질 수 있습니다. factory-precaching-cli 툴을 사용하면 ZTP 프로비저닝을 위해 원격 사이트에 제공하기 전에 서버를 사전 단계적으로 제공할 수 있습니다.
factory-precaching-cli 툴은 다음을 수행합니다.
- 부팅에 최소 ISO에 필요한 RHCOS rootfs 이미지를 다운로드합니다.
-
데이터로레이블이 지정된 설치 디스크에서 파티션을 생성합니다. - xfs로 디스크를 포맷합니다.
- 디스크 끝에 GUID 파티션 테이블(GPT) 데이터 파티션을 만듭니다. 여기서 도구에서 파티션 크기를 구성할 수 있습니다.
- OpenShift Container Platform을 설치하는 데 필요한 컨테이너 이미지를 복사합니다.
- OpenShift Container Platform을 설치하기 위해 ZTP에 필요한 컨테이너 이미지를 복사합니다.
- 선택 사항: Day-2 Operator를 파티션에 복사합니다.
factory-precaching-cli 툴은 기술 프리뷰 기능 전용입니다. 기술 프리뷰 기능은 Red Hat 프로덕션 서비스 수준 계약(SLA)에서 지원되지 않으며 기능적으로 완전하지 않을 수 있습니다. 따라서 프로덕션 환경에서 사용하는 것은 권장하지 않습니다. 이러한 기능을 사용하면 향후 제품 기능을 조기에 이용할 수 있어 개발 과정에서 고객이 기능을 테스트하고 피드백을 제공할 수 있습니다.
Red Hat 기술 프리뷰 기능의 지원 범위에 대한 자세한 내용은 기술 프리뷰 기능 지원 범위를 참조하십시오.
14.1. factory-precaching-cli 툴 가져오기
factory-precaching-cli 툴 Go 바이너리는 {rds-first} 툴 컨테이너 이미지에서 공개적으로 사용할 수 있습니다. 컨테이너 이미지의 factory-precaching-cli 툴 Go 바이너리는 podman 을 사용하여 RHCOS 라이브 이미지를 실행하는 서버에서 실행됩니다. 연결이 끊긴 환경에서 작업 중이거나 프라이빗 레지스트리가 있는 경우 이미지를 서버에 다운로드할 수 있도록 이미지를 복사해야 합니다.
프로세스
다음 명령을 실행하여 factory-precaching-cli 툴 이미지를 가져옵니다.
podman pull quay.io/openshift-kni/telco-ran-tools:latest
# podman pull quay.io/openshift-kni/telco-ran-tools:latestCopy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
도구를 사용할 수 있는지 확인하려면 factory-precaching-cli 도구 Go 바이너리의 현재 버전을 쿼리합니다.
podman run quay.io/openshift-kni/telco-ran-tools:latest -- factory-precaching-cli -v
# podman run quay.io/openshift-kni/telco-ran-tools:latest -- factory-precaching-cli -vCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
factory-precaching-cli version 20221018.120852+main.feecf17
factory-precaching-cli version 20221018.120852+main.feecf17Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.2. 라이브 운영 체제 이미지에서 부팅
factory-precaching-cli 툴을 사용하여 하나의 디스크만 사용 가능하고 외부 디스크 드라이브를 서버에 연결할 수 없는 서버를 부팅할 수 있습니다.
RHCOS는 RHCOS 이미지로 디스크를 쓸 때 디스크를 사용하지 않아야 합니다.
서버 하드웨어에 따라 다음 방법 중 하나를 사용하여 RHCOS 라이브 ISO를 빈 서버에 마운트할 수 있습니다.
- Dell 서버에서 Dell RACADM 툴 사용.
- HP 서버에서 HPONCFG 툴 사용.
- Redfish BMC API 사용.
마운트 절차를 자동화하는 것이 좋습니다. 절차를 자동화하려면 필요한 이미지를 가져와서 로컬 HTTP 서버에서 호스팅해야 합니다.
사전 요구 사항
- 호스트의 전원을 켭니다.
- 호스트에 대한 네트워크 연결이 있습니다.
이 예제 절차에서는 Redfish BMC API를 사용하여 RHCOS 라이브 ISO를 마운트합니다.
RHCOS 라이브 ISO를 마운트합니다.
가상 미디어 상태를 확인합니다.
curl --globoff -H "Content-Type: application/json" -H \ "Accept: application/json" -k -X GET --user ${username_password} \ https://$BMC_ADDRESS/redfish/v1/Managers/Self/VirtualMedia/1 | python -m json.tool$ curl --globoff -H "Content-Type: application/json" -H \ "Accept: application/json" -k -X GET --user ${username_password} \ https://$BMC_ADDRESS/redfish/v1/Managers/Self/VirtualMedia/1 | python -m json.toolCopy to Clipboard Copied! Toggle word wrap Toggle overflow ISO 파일을 가상 미디어로 마운트합니다.
curl --globoff -L -w "%{http_code} %{url_effective}\\n" -ku ${username_password} -H "Content-Type: application/json" -H "Accept: application/json" -d '{"Image": "http://[$HTTPd_IP]/RHCOS-live.iso"}' -X POST https://$BMC_ADDRESS/redfish/v1/Managers/Self/VirtualMedia/1/Actions/VirtualMedia.InsertMedia$ curl --globoff -L -w "%{http_code} %{url_effective}\\n" -ku ${username_password} -H "Content-Type: application/json" -H "Accept: application/json" -d '{"Image": "http://[$HTTPd_IP]/RHCOS-live.iso"}' -X POST https://$BMC_ADDRESS/redfish/v1/Managers/Self/VirtualMedia/1/Actions/VirtualMedia.InsertMediaCopy to Clipboard Copied! Toggle word wrap Toggle overflow 가상 미디어에서 한 번 부팅되도록 부팅 순서를 설정합니다.
curl --globoff -L -w "%{http_code} %{url_effective}\\n" -ku ${username_password} -H "Content-Type: application/json" -H "Accept: application/json" -d '{"Boot":{ "BootSourceOverrideEnabled": "Once", "BootSourceOverrideTarget": "Cd", "BootSourceOverrideMode": "UEFI"}}' -X PATCH https://$BMC_ADDRESS/redfish/v1/Systems/Self$ curl --globoff -L -w "%{http_code} %{url_effective}\\n" -ku ${username_password} -H "Content-Type: application/json" -H "Accept: application/json" -d '{"Boot":{ "BootSourceOverrideEnabled": "Once", "BootSourceOverrideTarget": "Cd", "BootSourceOverrideMode": "UEFI"}}' -X PATCH https://$BMC_ADDRESS/redfish/v1/Systems/SelfCopy to Clipboard Copied! Toggle word wrap Toggle overflow
- 재부팅하고 서버가 가상 미디어에서 부팅 중인지 확인합니다.
14.3. 디스크 파티셔닝
전체 사전 캐싱 프로세스를 실행하려면 라이브 ISO에서 부팅하고 컨테이너 이미지에서 factory-precaching-cli 툴을 사용하여 필요한 모든 아티팩트를 파티션 및 사전 캐시해야 합니다.
프로비저닝 중에 운영 체제(RHCOS)가 장치에 기록될 때 디스크를 사용하지 않아야 하므로 라이브 ISO 또는 RHCOS 라이브 ISO가 필요합니다. 이 절차를 통해 단일 디스크 서버도 활성화할 수 있습니다.
사전 요구 사항
- 분할되지 않은 디스크가 있습니다.
-
quay.io/openshift-kni/telco-ran-tools:latest이미지에 액세스할 수 있습니다. - OpenShift Container Platform을 설치하고 필요한 이미지를 사전 캐시할 수 있는 충분한 스토리지가 있습니다.
프로세스
디스크가 지워졌는지 확인합니다.
lsblk
# lsblkCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT loop0 7:0 0 93.8G 0 loop /run/ephemeral loop1 7:1 0 897.3M 1 loop /sysroot sr0 11:0 1 999M 0 rom /run/media/iso nvme0n1 259:1 0 1.5T 0 disk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT loop0 7:0 0 93.8G 0 loop /run/ephemeral loop1 7:1 0 897.3M 1 loop /sysroot sr0 11:0 1 999M 0 rom /run/media/iso nvme0n1 259:1 0 1.5T 0 diskCopy to Clipboard Copied! Toggle word wrap Toggle overflow 장치에서 파일 시스템, RAID 또는 파티션 테이블 서명을 지웁니다.
wipefs -a /dev/nvme0n1
# wipefs -a /dev/nvme0n1Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
/dev/nvme0n1: 8 bytes were erased at offset 0x00000200 (gpt): 45 46 49 20 50 41 52 54 /dev/nvme0n1: 8 bytes were erased at offset 0x1749a955e00 (gpt): 45 46 49 20 50 41 52 54 /dev/nvme0n1: 2 bytes were erased at offset 0x000001fe (PMBR): 55 aa
/dev/nvme0n1: 8 bytes were erased at offset 0x00000200 (gpt): 45 46 49 20 50 41 52 54 /dev/nvme0n1: 8 bytes were erased at offset 0x1749a955e00 (gpt): 45 46 49 20 50 41 52 54 /dev/nvme0n1: 2 bytes were erased at offset 0x000001fe (PMBR): 55 aaCopy to Clipboard Copied! Toggle word wrap Toggle overflow
아티팩트를 미리 캐싱하기 위해 장치의 파티션 번호 1을 사용하므로 디스크가 비어 있지 않으면 도구가 실패합니다.
14.3.1. 파티션 생성
장치가 준비되면 단일 파티션과 GPT 파티션 테이블을 만듭니다. 파티션은 자동으로 데이터로 레이블이 지정되어 장치 끝에 생성됩니다. 그렇지 않으면 coreos-installer 로 파티션을 덮어씁니다.
coreos-installer 를 사용하려면 장치 끝에 파티션을 생성하고 데이터로 레이블이 지정되어야 합니다. RHCOS 이미지를 디스크에 쓸 때 파티션을 저장하려면 두 요구 사항이 모두 필요합니다.
사전 요구 사항
-
호스트 장치의 포맷으로 인해 컨테이너가
privileged로 실행되어야 합니다. -
컨테이너 내에서 프로세스를 실행할 수 있도록
/dev폴더를 마운트해야 합니다.
프로세스
다음 예에서 파티션 크기는 Day 2 Operator의 DU 프로파일을 사전 캐싱할 수 있기 때문에 250GiB입니다.
컨테이너를 권한으로
실행하고디스크를 분할합니다.podman run -v /dev:/dev --privileged \ --rm quay.io/openshift-kni/telco-ran-tools:latest -- \ factory-precaching-cli partition \ -d /dev/nvme0n1 \ -s 250
# podman run -v /dev:/dev --privileged \ --rm quay.io/openshift-kni/telco-ran-tools:latest -- \ factory-precaching-cli partition \1 -d /dev/nvme0n1 \2 -s 2503 Copy to Clipboard Copied! Toggle word wrap Toggle overflow 스토리지 정보를 확인합니다.
lsblk
# lsblkCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
다음 요구 사항이 충족되었는지 확인해야 합니다.
- 장치에 GPT 파티션 테이블이 있습니다.
- 파티션은 장치의 최신 섹터를 사용합니다.
-
파티션이
데이터로 올바르게 레이블이 지정되었습니다.
디스크 상태를 쿼리하여 디스크가 예상대로 분할되었는지 확인합니다.
gdisk -l /dev/nvme0n1
# gdisk -l /dev/nvme0n1출력 예
14.3.2. 파티션 마운트
디스크가 올바르게 분할되었는지 확인한 후 장치를 /mnt 에 마운트할 수 있습니다.
GitOps ZTP 준비 중에 해당 마운트 지점이 사용되므로 장치를 /mnt 에 마운트하는 것이 좋습니다.
파티션이
xfs로 포맷되었는지 확인합니다.lsblk -f /dev/nvme0n1
# lsblk -f /dev/nvme0n1Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
NAME FSTYPE LABEL UUID MOUNTPOINT nvme0n1 └─nvme0n1p1 xfs 1bee8ea4-d6cf-4339-b690-a76594794071
NAME FSTYPE LABEL UUID MOUNTPOINT nvme0n1 └─nvme0n1p1 xfs 1bee8ea4-d6cf-4339-b690-a76594794071Copy to Clipboard Copied! Toggle word wrap Toggle overflow 파티션을 마운트합니다.
mount /dev/nvme0n1p1 /mnt/
# mount /dev/nvme0n1p1 /mnt/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
파티션이 마운트되었는지 확인합니다.
lsblk
# lsblkCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- RHCOS의
/mnt폴더가/var/mnt에 대한 링크이므로 마운트 지점은/var/mnt입니다.
14.4. 이미지 다운로드
factory-precaching-cli 툴을 사용하면 다음 이미지를 분할된 서버에 다운로드할 수 있습니다.
- OpenShift Container Platform 이미지
- 5G RAN 사이트의 DU(Distributed Unit) 프로필에 포함된 Operator 이미지
- 연결이 끊긴 레지스트리의 Operator 이미지
사용 가능한 Operator 이미지 목록은 OpenShift Container Platform 릴리스마다 다를 수 있습니다.
14.4.1. 병렬 작업자로 다운로드
factory-precaching-cli 툴은 병렬 작업자를 사용하여 여러 이미지를 동시에 다운로드합니다. --parallel 또는 -p 옵션을 사용하여 작업자 수를 구성할 수 있습니다. 기본 수는 서버에 사용 가능한 CPU의 80%로 설정됩니다.
로그인 쉘은 CPU의 서브 세트로 제한될 수 있으므로 컨테이너에서 사용할 수 있는 CPU가 줄어듭니다. 이 제한을 제거하려면 명령 앞에 taskset 0xffffff 를 붙일 수 있습니다. 예를 들면 다음과 같습니다.
taskset 0xffffffff podman run --rm quay.io/openshift-kni/telco-ran-tools:latest factory-precaching-cli download --help
# taskset 0xffffffff podman run --rm quay.io/openshift-kni/telco-ran-tools:latest factory-precaching-cli download --help14.4.2. OpenShift Container Platform 이미지 다운로드 준비
OpenShift Container Platform 컨테이너 이미지를 다운로드하려면 다중 클러스터 엔진 버전을 알아야 합니다. --du-profile 플래그를 사용하는 경우 단일 노드 OpenShift를 프로비저닝할 허브 클러스터에서 실행 중인 RHACM(Red Hat Advanced Cluster Management) 버전도 지정해야 합니다.
사전 요구 사항
- RHACM 및 다중 클러스터 엔진 Operator가 설치되어 있어야 합니다.
- 스토리지 장치를 분할했습니다.
- 분할된 장치에 이미지를 위한 충분한 공간이 있습니다.
- 베어 메탈 서버를 인터넷에 연결했습니다.
- 유효한 풀 시크릿이 있습니다.
프로세스
hub 클러스터에서 다음 명령을 실행하여 RHACM 버전과 다중 클러스터 엔진 버전을 확인합니다.
oc get csv -A | grep -i advanced-cluster-management
$ oc get csv -A | grep -i advanced-cluster-managementCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
open-cluster-management advanced-cluster-management.v2.6.3 Advanced Cluster Management for Kubernetes 2.6.3 advanced-cluster-management.v2.6.3 Succeeded
open-cluster-management advanced-cluster-management.v2.6.3 Advanced Cluster Management for Kubernetes 2.6.3 advanced-cluster-management.v2.6.3 SucceededCopy to Clipboard Copied! Toggle word wrap Toggle overflow oc get csv -A | grep -i multicluster-engine
$ oc get csv -A | grep -i multicluster-engineCopy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
multicluster-engine cluster-group-upgrades-operator.v0.0.3 cluster-group-upgrades-operator 0.0.3 Pending multicluster-engine multicluster-engine.v2.1.4 multicluster engine for Kubernetes 2.1.4 multicluster-engine.v2.0.3 Succeeded multicluster-engine openshift-gitops-operator.v1.5.7 Red Hat OpenShift GitOps 1.5.7 openshift-gitops-operator.v1.5.6-0.1664915551.p Succeeded multicluster-engine openshift-pipelines-operator-rh.v1.6.4 Red Hat OpenShift Pipelines 1.6.4 openshift-pipelines-operator-rh.v1.6.3 Succeeded
multicluster-engine cluster-group-upgrades-operator.v0.0.3 cluster-group-upgrades-operator 0.0.3 Pending multicluster-engine multicluster-engine.v2.1.4 multicluster engine for Kubernetes 2.1.4 multicluster-engine.v2.0.3 Succeeded multicluster-engine openshift-gitops-operator.v1.5.7 Red Hat OpenShift GitOps 1.5.7 openshift-gitops-operator.v1.5.6-0.1664915551.p Succeeded multicluster-engine openshift-pipelines-operator-rh.v1.6.4 Red Hat OpenShift Pipelines 1.6.4 openshift-pipelines-operator-rh.v1.6.3 SucceededCopy to Clipboard Copied! Toggle word wrap Toggle overflow 컨테이너 레지스트리에 액세스하려면 설치할 서버에 유효한 풀 시크릿을 복사합니다.
.docker폴더를 생성합니다.mkdir /root/.docker
$ mkdir /root/.dockerCopy to Clipboard Copied! Toggle word wrap Toggle overflow config.json파일의 유효한 가져오기를 이전에 생성된.docker/폴더에 복사합니다.cp config.json /root/.docker/config.json
$ cp config.json /root/.docker/config.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
/root/.docker/config.json은podman이 레지스트리의 로그인 인증 정보를 확인하는 기본 경로입니다.
다른 레지스트리를 사용하여 필요한 아티팩트를 가져오는 경우 적절한 풀 시크릿을 복사해야 합니다. 로컬 레지스트리에서 TLS를 사용하는 경우 레지스트리의 인증서도 포함해야 합니다.
14.4.3. OpenShift Container Platform 이미지 다운로드
factory-precaching-cli 툴을 사용하면 특정 OpenShift Container Platform 릴리스를 프로비저닝하는 데 필요한 모든 컨테이너 이미지를 사전 캐시할 수 있습니다.
프로세스
다음 명령을 실행하여 릴리스를 사전 캐시합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
검증
모든 이미지가 서버의 대상 폴더에 압축되었는지 확인합니다.
ls -l /mnt
$ ls -l /mnt1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
/mnt폴더의 이미지를 사전 캐시하는 것이 좋습니다.
출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.4.4. Operator 이미지 다운로드
5G radio Access Network (RAN) Distributed Unit (DU) 클러스터 구성에서 사용되는 pre-cache Day-2 Operator도 사용할 수 있습니다. Day-2 Operator는 설치된 OpenShift Container Platform 버전을 사용합니다.
--acm-version 및 --mce-version 플래그를 사용하여 RHACM 허브 및 다중 클러스터 엔진 Operator 버전을 포함해야 합니다. 따라서 factory-precaching-cli 툴이 RHACM 및 다중 클러스터 엔진 Operator에 적합한 컨테이너 이미지를 사전 캐시할 수 있습니다.
프로세스
Operator 이미지를 사전 캐시합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 출력 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.4.5. 연결이 끊긴 환경에서 사용자 정의 이미지 사전 캐싱
--generate-imageset 인수는 ImageSetConfiguration CR(사용자 정의 리소스)이 생성된 후 factory-precaching-cli 툴을 중지합니다. 이를 통해 이미지를 다운로드하기 전에 ImageSetConfiguration CR을 사용자 지정할 수 있습니다. CR을 사용자 지정한 후 --skip-imageset 인수를 사용하여 ImageSetConfiguration CR에 지정한 이미지를 다운로드할 수 있습니다.
다음과 같은 방법으로 ImageSetConfiguration CR을 사용자 지정할 수 있습니다.
- Operator 및 추가 이미지 추가
- Operator 및 추가 이미지 제거
- Operator 및 카탈로그 소스를 로컬 또는 연결이 끊긴 레지스트리로 변경
프로세스
이미지를 사전 캐시합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- factory-precaching-cli 툴의 다운로드 기능을 지정합니다.
- 2
- OpenShift Container Platform 릴리스 버전을 정의합니다.
- 3
- RHACM 버전을 정의합니다.
- 4
- 다중 클러스터 엔진 버전을 정의합니다.
- 5
- 디스크에서 이미지를 다운로드할 폴더를 정의합니다.
- 6
- 선택 사항: 추가 이미지를 저장하는 리포지토리를 정의합니다. 이러한 이미지는 디스크에서 다운로드되고 미리 캐시됩니다.
- 7
- DU 구성에 포함된 Operator를 사전 캐싱합니다.
- 8
--generate-imageset인수는 CR을 사용자 지정할 수 있는ImageSetConfigurationCR만 생성합니다.
출력 예
Generated /mnt/imageset.yaml
Generated /mnt/imageset.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImageSetConfiguration CR의 예
Copy to Clipboard Copied! Toggle word wrap Toggle overflow CR에서 카탈로그 리소스를 사용자 지정합니다.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow 로컬 또는 연결이 끊긴 레지스트리를 사용하여 이미지를 다운로드하는 경우 먼저 콘텐츠를 가져오려는 레지스트리에 대한 인증서를 추가해야 합니다.
오류를 방지하려면 레지스트리 인증서를 서버에 복사합니다.
cp /tmp/eko4-ca.crt /etc/pki/ca-trust/source/anchors/.
# cp /tmp/eko4-ca.crt /etc/pki/ca-trust/source/anchors/.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 그런 다음 인증서 신뢰 저장소를 업데이트합니다.
update-ca-trust
# update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow host
/etc/pki폴더를 factory-cli 이미지에 마운트합니다.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- factory-precaching-cli 툴의 다운로드 기능을 지정합니다.
- 2
- OpenShift Container Platform 릴리스 버전을 정의합니다.
- 3
- RHACM 버전을 정의합니다.
- 4
- 다중 클러스터 엔진 버전을 정의합니다.
- 5
- 디스크에서 이미지를 다운로드할 폴더를 정의합니다.
- 6
- 선택 사항: 추가 이미지를 저장하는 리포지토리를 정의합니다. 이러한 이미지는 디스크에서 다운로드되고 미리 캐시됩니다.
- 7
- DU 구성에 포함된 Operator를 사전 캐싱합니다.
- 8
--skip-imageset인수를 사용하면 사용자 지정된ImageSetConfigurationCR에 지정한 이미지를 다운로드할 수 있습니다.
새
imageSetConfigurationCR을 생성하지 않고 이미지를 다운로드합니다.podman run -v /mnt:/mnt -v /root/.docker:/root/.docker --privileged --rm quay.io/openshift-kni/telco-ran-tools:latest -- factory-precaching-cli download -r 4.15.0 \ --acm-version 2.6.3 --mce-version 2.1.4 -f /mnt \ --img quay.io/custom/repository \ --du-profile -s \ --skip-imageset
# podman run -v /mnt:/mnt -v /root/.docker:/root/.docker --privileged --rm quay.io/openshift-kni/telco-ran-tools:latest -- factory-precaching-cli download -r 4.15.0 \ --acm-version 2.6.3 --mce-version 2.1.4 -f /mnt \ --img quay.io/custom/repository \ --du-profile -s \ --skip-imagesetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
14.5. GitOps ZTP의 이미지 사전 캐싱
SiteConfig 매니페스트는 OpenShift 클러스터를 설치 및 구성하는 방법을 정의합니다. ZTP( GitOps Zero Touch Provisioning) 프로비저닝 워크플로우에서 factory-precaching-cli 툴에는 site Config 매니페스트에 다음과 같은 추가 필드가 필요합니다.
-
clusters.ignitionConfigOverride -
nodes.installerArgs -
nodes.ignitionConfigOverride
추가 필드가 있는 siteConfig의 예
14.5.1. cluster.ignitionConfigOverride 필드 이해
clusters.ignitionConfigOverride 필드는 GitOps ZTP 검색 단계에서 Ignition 형식으로 구성을 추가합니다. 구성에는 가상 미디어에 마운트된 ISO의 systemd 서비스가 포함됩니다. 이렇게 하면 스크립트는 검색 RHCOS 라이브 ISO의 일부이며 지원 설치 관리자(AI) 이미지를 로드하는 데 사용할 수 있습니다.
systemd서비스-
systemd서비스는var-mnt.mount및precache-images.services입니다.precache-images.service는var-mnt.mount단위의/var/mnt에 마운트할 디스크 파티션에 따라 다릅니다. 서비스는extract-ai.sh라는 스크립트를 호출합니다. extract-ai.sh-
extract-ai.sh스크립트는 디스크 파티션의 필수 이미지를 추출하고 로컬 컨테이너 스토리지로 로드합니다. 스크립트가 성공적으로 완료되면 이미지를 로컬에서 사용할 수 있습니다. agent-fix-bz1964591-
agent-fix-bz1964591스크립트는 AI 문제에 대한 해결 방법입니다. AI가 이미지를 제거하지 못하도록 하여agent.service가 레지스트리에서 이미지를 다시 가져올 수 있도록agent-fix-bz1964591스크립트에서 요청된 컨테이너 이미지가 존재하는지 확인합니다.
14.5.2. nodes.installerArgs 필드 이해
nodes.installerArgs 필드를 사용하면 coreos-installer 유틸리티에서 RHCOS 라이브 ISO를 디스크에 쓰는 방법을 구성할 수 있습니다. 데이터 파티션에 저장된 아티팩트가 OpenShift Container Platform 설치 단계에서 필요하므로 레이블이 지정된 디스크 파티션을 데이터로 저장하려면 지정해야 합니다.
추가 매개변수는 라이브 RHCOS를 디스크에 쓰는 coreos-installer 유틸리티로 직접 전달됩니다. 다음 재부팅 시 운영 체제가 디스크에서 시작됩니다.
coreos-installer 유틸리티에 여러 옵션을 전달할 수 있습니다.
14.5.3. nodes.ignitionConfigOverride 필드 이해
cluster .ignitionConfigOverride 와 마찬가지로 nodes.ignitionConfigOverride 필드를 사용하면 Ignition 형식의 구성을 coreos-installer 유틸리티에 추가할 수 있지만 OpenShift Container Platform 설치 단계에서 구성을 추가할 수 있습니다. RHCOS가 디스크에 기록되면 GitOps ZTP 검색 ISO에 포함된 추가 구성을 더 이상 사용할 수 없습니다. 검색 단계에서 추가 구성이 라이브 OS의 메모리에 저장됩니다.
이 단계에서는 추출 및 로드된 컨테이너 이미지의 수가 검색 단계보다 큽니다. OpenShift Container Platform 릴리스 및 Day-2 Operator 설치 여부에 따라 설치 시간이 다를 수 있습니다.
설치 단계에서 var-mnt.mount 및 precache-ocp.services systemd 서비스가 사용됩니다.
precache-ocp.serviceprecache-ocp.service는var-mnt.mount단위의/var/mnt에 마운트할 디스크 파티션에 따라 다릅니다.precache-ocp.service서비스는extract-ocp.sh라는 스크립트를 호출합니다.중요OpenShift Container Platform 설치 전에 모든 이미지를 추출하려면
machine-config-daemon-pull.service및nodeip-configuration.service서비스를 실행하기 전에precache-ocp.service를 실행해야 합니다.extract-ocp.sh-
extract-ocp.sh스크립트는 디스크 파티션의 필수 이미지를 추출하고 로컬 컨테이너 스토리지로 로드합니다. 스크립트가 성공적으로 완료되면 이미지를 로컬에서 사용할 수 있습니다.
Argo CD가 모니터링되는 Git 리포지터리에 site Config 및 PolicyGenTemplates CR(사용자 정의 리소스)을 업로드할 때 허브 클러스터와 CR을 동기화하여 GitOps ZTP 워크플로를 시작할 수 있습니다.
14.6. 문제 해결
14.6.1. 렌더링된 카탈로그가 유효하지 않음
로컬 또는 연결이 끊긴 레지스트리를 사용하여 이미지를 다운로드하는 경우 렌더링된 카탈로그가 유효하지 않은 오류가 표시될 수 있습니다. 즉, 콘텐츠를 가져오려는 새 레지스트리의 인증서가 누락되어 있습니다.
factory-precaching-cli 툴 이미지는 UBI RHEL 이미지를 기반으로 합니다. 인증서 경로와 위치는 RHCOS에서 동일합니다.
오류 예
프로세스
레지스트리 인증서를 서버에 복사합니다.
cp /tmp/eko4-ca.crt /etc/pki/ca-trust/source/anchors/.
# cp /tmp/eko4-ca.crt /etc/pki/ca-trust/source/anchors/.Copy to Clipboard Copied! Toggle word wrap Toggle overflow 인증서 신뢰 저장소를 업데이트합니다.
update-ca-trust
# update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow host
/etc/pki폴더를 factory-cli 이미지에 마운트합니다.podman run -v /mnt:/mnt -v /root/.docker:/root/.docker -v /etc/pki:/etc/pki --privileged -it --rm quay.io/openshift-kni/telco-ran-tools:latest -- \ factory-precaching-cli download -r 4.15.0 --acm-version 2.5.4 \ --mce-version 2.0.4 -f /mnt \--img quay.io/custom/repository --du-profile -s --skip-imageset
# podman run -v /mnt:/mnt -v /root/.docker:/root/.docker -v /etc/pki:/etc/pki --privileged -it --rm quay.io/openshift-kni/telco-ran-tools:latest -- \ factory-precaching-cli download -r 4.15.0 --acm-version 2.5.4 \ --mce-version 2.0.4 -f /mnt \--img quay.io/custom/repository --du-profile -s --skip-imagesetCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Legal Notice
Copyright © Red Hat
OpenShift documentation is licensed under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0).
Modified versions must remove all Red Hat trademarks.
Portions adapted from https://github.com/kubernetes-incubator/service-catalog/ with modifications by Red Hat.
Red Hat, Red Hat Enterprise Linux, the Red Hat logo, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries.
Linux® is the registered trademark of Linus Torvalds in the United States and other countries.
Java® is a registered trademark of Oracle and/or its affiliates.
XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries.
MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries.
Node.js® is an official trademark of the OpenJS Foundation.
The OpenStack® Word Mark and OpenStack logo are either registered trademarks/service marks or trademarks/service marks of the OpenStack Foundation, in the United States and other countries and are used with the OpenStack Foundation’s permission. We are not affiliated with, endorsed or sponsored by the OpenStack Foundation, or the OpenStack community.
All other trademarks are the property of their respective owners.