This documentation is for a release that is no longer maintained
See documentation for the latest supported version 3 or the latest supported version 4.Installing
Installing and configuring OpenShift Container Platform clusters
Abstract
Chapter 1. Mirroring images for a disconnected installation
You can use the procedures in this section to ensure your clusters only use container images that satisfy your organizational controls on external content. Before you install a cluster on infrastructure that you provision in a restricted network, you must mirror the required container images into that environment. To mirror container images, you must have a registry for mirroring.
You must have access to the internet to obtain the necessary container images. In this procedure, you place your mirror registry on a mirror host that has access to both your network and the Internet. If you do not have access to a mirror host, use the Mirroring an Operator catalog procedure to copy images to a device you can move across network boundaries with.
1.1. Prerequisites
You must have a container image registry that supports Docker v2-2 in the location that will host the OpenShift Container Platform cluster, such as one of the following registries:
If you have an entitlement to Red Hat Quay, see the documentation on deploying Red Hat Quay for proof-of-concept purposes or by using the Quay Operator. If you need additional assistance selecting and installing a registry, contact your sales representative or Red Hat support.
- If you do not already have an existing solution for a container image registry, subscribers of OpenShift Container Platform are provided a mirror registry for Red Hat OpenShift. The mirror registry for Red Hat OpenShift is included with your subscription and is a small-scale container registry that can be used to mirror the required container images of OpenShift Container Platform in disconnected installations.
1.2. About the mirror registry
You can mirror the images that are required for OpenShift Container Platform installation and subsequent product updates to a container mirror registry such as Red Hat Quay, JFrog Artifactory, Sonatype Nexus Repository, or Harbor. If you do not have access to a large-scale container registry, you can use the mirror registry for Red Hat OpenShift, a small-scale container registry included with OpenShift Container Platform subscriptions.
You can use any container registry that supports Docker v2-2, such as Red Hat Quay, the mirror registry for Red Hat OpenShift, Artifactory, Sonatype Nexus Repository, or Harbor. Regardless of your chosen registry, the procedure to mirror content from Red Hat hosted sites on the internet to an isolated image registry is the same. After you mirror the content, you configure each cluster to retrieve this content from your mirror registry.
The internal registry of the OpenShift Container Platform cluster cannot be used as the target registry because it does not support pushing without a tag, which is required during the mirroring process.
If choosing a container registry that is not the mirror registry for Red Hat OpenShift, it must be reachable by every machine in the clusters that you provision. If the registry is unreachable, installation, updating, or normal operations such as workload relocation might fail. For that reason, you must run mirror registries in a highly available way, and the mirror registries must at least match the production availability of your OpenShift Container Platform clusters.
When you populate your mirror registry with OpenShift Container Platform images, you can follow two scenarios. If you have a host that can access both the internet and your mirror registry, but not your cluster nodes, you can directly mirror the content from that machine. This process is referred to as connected mirroring. If you have no such host, you must mirror the images to a file system and then bring that host or removable media into your restricted environment. This process is referred to as disconnected mirroring.
For mirrored registries, to view the source of pulled images, you must review the Trying to access log entry in the CRI-O logs. Other methods to view the image pull source, such as using the crictl images command on a node, show the non-mirrored image name, even though the image is pulled from the mirrored location.
Red Hat does not test third party registries with OpenShift Container Platform.
Additional information
For information on viewing the CRI-O logs to view the image source, see Viewing the image pull source.
1.3. Preparing your mirror host
Before you perform the mirror procedure, you must prepare the host to retrieve content and push it to the remote location.
1.3.1. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
1.3.1.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>1.3.1.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>1.3.1.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>1.4. Configuring credentials that allow images to be mirrored
Create a container image registry credentials file that allows mirroring images from Red Hat to your mirror.
Do not use this image registry credentials file as the pull secret when you install a cluster. If you provide this file when you install cluster, all of the machines in the cluster will have write access to your mirror registry.
This process requires that you have write access to a container image registry on the mirror registry and adds the credentials to a registry pull secret.
Prerequisites
- You configured a mirror registry to use in your restricted network.
- You identified an image repository location on your mirror registry to mirror images into.
- You provisioned a mirror registry account that allows images to be uploaded to that image repository.
Procedure
Complete the following steps on the installation host:
-
Download your
registry.redhat.iopull secret from the Red Hat OpenShift Cluster Manager and save it to a.jsonfile. Generate the base64-encoded user name and password or token for your mirror registry:
echo -n '<user_name>:<password>' | base64 -w0
$ echo -n '<user_name>:<password>' | base64 -w01 BGVtbYk3ZHAtqXs=Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<user_name>and<password>, specify the user name and password that you configured for your registry.
Make a copy of your pull secret in JSON format:
cat ./pull-secret.text | jq . > <path>/<pull_secret_file_in_json>
$ cat ./pull-secret.text | jq . > <path>/<pull_secret_file_in_json>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path to the folder to store the pull secret in and a name for the JSON file that you create.
The contents of the file resemble the following example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the new file and add a section that describes your registry to it:
"auths": { "<mirror_registry>": { "auth": "<credentials>", "email": "you@example.com" },"auths": { "<mirror_registry>": {1 "auth": "<credentials>",2 "email": "you@example.com" },Copy to Clipboard Copied! Toggle word wrap Toggle overflow The file resembles the following example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
1.5. Mirror registry for Red Hat OpenShift
The mirror registry for Red Hat OpenShift is a small and streamlined container registry that you can use as a target for mirroring the required container images of OpenShift Container Platform for disconnected installations.
If you already have a container image registry, such as Red Hat Quay, you can skip these steps and go straight to Mirroring the OpenShift Container Platform image repository.
Prerequisites
- An OpenShift Container Platform subscription.
- Red Hat Enterprise Linux (RHEL) 8 with Podman 3.3 and OpenSSL installed.
- Fully qualified domain name for the Red Hat Quay service, which must resolve through a DNS server.
-
Passwordless
sudoaccess on the target host. - Key-based SSH connectivity on the target host. SSH keys are automatically generated for local installs. For remote hosts, you must generate your own SSH keys.
- 2 or more vCPUs.
- 8 GB of RAM.
About 6.8 GB for OpenShift Container Platform 4.6 Release images, or about 696 GB for OpenShift Container Platform 4.6 Release images and OpenShift Container Platform 4.6 Red Hat Operator images. Up to 1 TB per stream or more is suggested.
ImportantThese requirements are based on local testing results with only Release images and Operator images tested. Storage requirements can vary based on your organization’s needs. Some users might require more space, for example, when they mirror multiple z-streams. You can use standard Red Hat Quay functionality to remove unnecessary images and free up space.
1.5.1. Mirror registry for Red Hat OpenShift introduction
For disconnected deployments of OpenShift Container Platform, a container registry is required to carry out the installation of the clusters. To run a production-grade registry service on such a cluster, you must create a separate registry deployment to install the first cluster. The mirror registry for Red Hat OpenShift addresses this need and is included in every OpenShift subscription. It is available for download on the OpenShift console Downloads page.
The mirror registry for Red Hat OpenShift allows users to install a small-scale version of Red Hat Quay and its required components using the mirror-registry command line interface (CLI) tool. The mirror registry for Red Hat OpenShift is deployed automatically with pre-configured local storage and a local database. It also includes auto-generated user credentials and access permissions with a single set of inputs and no additional configuration choices to get started.
The mirror registry for Red Hat OpenShift provides a pre-determined network configuration and reports deployed component credentials and access URLs upon success. A limited set of optional configuration inputs like fully qualified domain name (FQDN) services, superuser name and password, and custom TLS certificates are also provided. This provides users with a container registry so that they can easily create an offline mirror of all OpenShift Container Platform release content when running OpenShift Container Platform in restricted network environments.
The mirror registry for Red Hat OpenShift is limited to hosting images that are required to install a disconnected OpenShift Container Platform cluster, such as Release images or Red Hat Operator images. It uses local storage on your Red Hat Enterprise Linux (RHEL) machine, and storage supported by RHEL is supported by the mirror registry for Red Hat OpenShift. Content built by customers should not be hosted by the mirror registry for Red Hat OpenShift.
Unlike Red Hat Quay, the mirror registry for Red Hat OpenShift is not a highly-available registry and only local file system storage is supported. Using the mirror registry for Red Hat OpenShift with more than one cluster is discouraged, because multiple clusters can create a single point of failure when updating your cluster fleet. It is advised to leverage the mirror registry for Red Hat OpenShift to install a cluster that can host a production-grade, highly-available registry such as Red Hat Quay, which can serve OpenShift Container Platform content to other clusters.
Use of the mirror registry for Red Hat OpenShift is optional if another container registry is already available in the install environment.
1.5.2. Mirroring on a local host with mirror registry for Red Hat OpenShift
This procedure explains how to install the mirror registry for Red Hat OpenShift on a local host using the mirror-registry installer tool. By doing so, users can create a local host registry running on port 443 for the purpose of storing a mirror of OpenShift Container Platform images.
Installing the mirror registry for Red Hat OpenShift using the mirror-registry CLI tool makes several changes to your machine. After installation, a /etc/quay-install directory is created, which has installation files, local storage, and the configuration bundle. Trusted SSH keys are generated in case the deployment target is the local host, and systemd files on the host machine are set up to ensure that container runtimes are persistent. Additionally, an initial user named init is created with an automatically generated password. All access credentials are printed at the end of the install routine.
Procedure
-
Download the
mirror-registry.tar.gzpackage for the latest version of the mirror registry for Red Hat OpenShift found on the OpenShift console Downloads page. Install the mirror registry for Red Hat OpenShift on your local host with your current user account by using the
mirror-registrytool. For a full list of available flags, see "mirror registry for Red Hat OpenShift flags".sudo ./mirror-registry install \ --quayHostname <host_example_com> \ --quayRoot <example_directory_name>
$ sudo ./mirror-registry install \ --quayHostname <host_example_com> \ --quayRoot <example_directory_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the user name and password generated during installation to log into the registry by running the following command:
podman login --authfile pull-secret.txt \ -u init \ -p <password> \ <host_example_com>:8443> \ --tls-verify=false
$ podman login --authfile pull-secret.txt \ -u init \ -p <password> \ <host_example_com>:8443> \ --tls-verify=false1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- You can avoid running
--tls-verify=falseby configuring your system to trust the generated rootCA certificates. See "Using SSL to protect connections to Red Hat Quay" and "Configuring the system to trust the certificate authority" for more information.
NoteYou can also log in by accessing the UI at
https://<host.example.com>:8443after installation.You can mirror OpenShift Container Platform images after logging in. Depending on your needs, see either the "Mirroring the OpenShift Container Platform image repository" or the "Mirroring an Operator catalog" sections of this document.
NoteIf there are issues with images stored by the mirror registry for Red Hat OpenShift due to storage layer problems, you can remirror the OpenShift Container Platform images, or reinstall mirror registry on more stable storage.
1.5.3. Mirroring on a remote host with mirror registry for Red Hat OpenShift
This procedure explains how to install the mirror registry for Red Hat OpenShift on a remote host using the mirror-registry tool. By doing so, users can create a registry to hold a mirror of OpenShift Container Platform images.
Installing the mirror registry for Red Hat OpenShift using the mirror-registry CLI tool makes several changes to your machine. After installation, a /etc/quay-install directory is created, which has installation files, local storage, and the configuration bundle. Trusted SSH keys are generated in case the deployment target is the local host, and systemd files on the host machine are set up to ensure that container runtimes are persistent. Additionally, an initial user named init is created with an automatically generated password. All access credentials are printed at the end of the install routine.
Procedure
-
Download the
mirror-registry.tar.gzpackage for the latest version of the mirror registry for Red Hat OpenShift found on the OpenShift console Downloads page. Install the mirror registry for Red Hat OpenShift on your local host with your current user account by using the
mirror-registrytool. For a full list of available flags, see "mirror registry for Red Hat OpenShift flags".Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the user name and password generated during installation to log into the mirror registry by running the following command:
podman login --authfile pull-secret.txt \ -u init \ -p <password> \ <host_example_com>:8443> \ --tls-verify=false
$ podman login --authfile pull-secret.txt \ -u init \ -p <password> \ <host_example_com>:8443> \ --tls-verify=false1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- You can avoid running
--tls-verify=falseby configuring your system to trust the generated rootCA certificates. See "Using SSL to protect connections to Red Hat Quay" and "Configuring the system to trust the certificate authority" for more information.
NoteYou can also log in by accessing the UI at
https://<host.example.com>:8443after installation.You can mirror OpenShift Container Platform images after logging in. Depending on your needs, see either the "Mirroring the OpenShift Container Platform image repository" or the "Mirroring an Operator catalog" sections of this document.
NoteIf there are issues with images stored by the mirror registry for Red Hat OpenShift due to storage layer problems, you can remirror the OpenShift Container Platform images, or reinstall mirror registry on more stable storage.
1.6. Upgrading the mirror registry for Red Hat OpenShift
You can upgrade the mirror registry for Red Hat OpenShift from your local host by running the following command:
sudo ./mirror-registry upgrade
$ sudo ./mirror-registry upgradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Note-
Users who upgrade the mirror registry for Red Hat OpenShift with the
./mirror-registry upgradeflag must include the same credentials used when creating their mirror registry. For example, if you installed the mirror registry for Red Hat OpenShift with--quayHostname <host_example_com>and--quayRoot <example_directory_name>, you must include that string to properly upgrade the mirror registry.
-
Users who upgrade the mirror registry for Red Hat OpenShift with the
1.6.1. Uninstalling the mirror registry for Red Hat OpenShift
You can uninstall the mirror registry for Red Hat OpenShift from your local host by running the following command:
sudo ./mirror-registry uninstall -v \ --quayRoot <example_directory_name>
$ sudo ./mirror-registry uninstall -v \ --quayRoot <example_directory_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note-
Deleting the mirror registry for Red Hat OpenShift will prompt the user before deletion. You can use
--autoApproveto skip this prompt. -
Users who install the mirror registry for Red Hat OpenShift with the
--quayRootflag must include the--quayRootflag when uninstalling. For example, if you installed the mirror registry for Red Hat OpenShift with--quayRoot example_directory_name, you must include that string to properly uninstall the mirror registry.
-
Deleting the mirror registry for Red Hat OpenShift will prompt the user before deletion. You can use
1.6.2. Mirror registry for Red Hat OpenShift flags
The following flags are available for the mirror registry for Red Hat OpenShift:
| Flags | Description |
|---|---|
|
|
A boolean value that disables interactive prompts. If set to |
|
| The password of the init user created during Quay installation. Must be at least eight characters and contain no whitespace. |
|
|
Shows the username of the initial user. Defaults to |
|
|
The fully-qualified domain name of the mirror registry that clients will use to contact the registry. Equivalent to |
|
|
The directory where container image layer and configuration data is saved, including |
|
|
The path of your SSH identity key. Defaults to |
|
|
The path to the SSL/TLS public key / certificate. Defaults to |
|
|
Skips the check for the certificate hostname against the |
|
|
The path to the SSL/TLS private key used for HTTPS communication. Defaults to |
|
|
The hostname of the target you want to install Quay to. Defaults to |
|
|
The user on the target host which will be used for SSH. Defaults to |
|
| Shows debug logs and Ansible playbook outputs. |
|
| Shows the version for the mirror registry for Red Hat OpenShift. |
-
--quayHostnamemust be modified if the public DNS name of your system is different from the local hostname. -
--sslCheckSkipis used in cases when the mirror registry is set behind a proxy and the exposed hostname is different from the internal Quay hostname. It can also be used when users do not want the certificates to be validated against the provided Quay hostname during installation.
1.7. Mirroring the OpenShift Container Platform image repository
Mirror the OpenShift Container Platform image repository to your registry to use during cluster installation or upgrade.
Prerequisites
- Your mirror host has access to the Internet.
- You configured a mirror registry to use in your restricted network and can access the certificate and credentials that you configured.
- You downloaded the pull secret from the Red Hat OpenShift Cluster Manager and modified it to include authentication to your mirror repository.
If you use self-signed certificates that do not set a Subject Alternative Name, you must precede the
occommands in this procedure withGODEBUG=x509ignoreCN=0. If you do not set this variable, theoccommands will fail with the following error:x509: certificate relies on legacy Common Name field, use SANs or temporarily enable Common Name matching with GODEBUG=x509ignoreCN=0
x509: certificate relies on legacy Common Name field, use SANs or temporarily enable Common Name matching with GODEBUG=x509ignoreCN=0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Procedure
Complete the following steps on the mirror host:
- Review the OpenShift Container Platform downloads page to determine the version of OpenShift Container Platform that you want to install and determine the corresponding tag on the Repository Tags page.
Set the required environment variables:
Export the release version:
OCP_RELEASE=<release_version>
$ OCP_RELEASE=<release_version>Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<release_version>, specify the tag that corresponds to the version of OpenShift Container Platform to install, such as4.5.4.Export the local registry name and host port:
LOCAL_REGISTRY='<local_registry_host_name>:<local_registry_host_port>'
$ LOCAL_REGISTRY='<local_registry_host_name>:<local_registry_host_port>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<local_registry_host_name>, specify the registry domain name for your mirror repository, and for<local_registry_host_port>, specify the port that it serves content on.Export the local repository name:
LOCAL_REPOSITORY='<local_repository_name>'
$ LOCAL_REPOSITORY='<local_repository_name>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<local_repository_name>, specify the name of the repository to create in your registry, such asocp4/openshift4.Export the name of the repository to mirror:
PRODUCT_REPO='openshift-release-dev'
$ PRODUCT_REPO='openshift-release-dev'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For a production release, you must specify
openshift-release-dev.Export the path to your registry pull secret:
LOCAL_SECRET_JSON='<path_to_pull_secret>'
$ LOCAL_SECRET_JSON='<path_to_pull_secret>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<path_to_pull_secret>, specify the absolute path to and file name of the pull secret for your mirror registry that you created.Export the release mirror:
RELEASE_NAME="ocp-release"
$ RELEASE_NAME="ocp-release"Copy to Clipboard Copied! Toggle word wrap Toggle overflow For a production release, you must specify
ocp-release.Export the type of architecture for your server, such as
x86_64.:ARCHITECTURE=<server_architecture>
$ ARCHITECTURE=<server_architecture>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the path to the directory to host the mirrored images:
REMOVABLE_MEDIA_PATH=<path>
$ REMOVABLE_MEDIA_PATH=<path>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the full path, including the initial forward slash (/) character.
Mirror the version images to the mirror registry:
If your mirror host does not have internet access, take the following actions:
- Connect the removable media to a system that is connected to the internet.
Review the images and configuration manifests to mirror:
oc adm release mirror -a ${LOCAL_SECRET_JSON} \ --from=quay.io/${PRODUCT_REPO}/${RELEASE_NAME}:${OCP_RELEASE}-${ARCHITECTURE} \ --to=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY} \ --to-release-image=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}-${ARCHITECTURE} --dry-run$ oc adm release mirror -a ${LOCAL_SECRET_JSON} \ --from=quay.io/${PRODUCT_REPO}/${RELEASE_NAME}:${OCP_RELEASE}-${ARCHITECTURE} \ --to=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY} \ --to-release-image=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}-${ARCHITECTURE} --dry-runCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Record the entire
imageContentSourcessection from the output of the previous command. The information about your mirrors is unique to your mirrored repository, and you must add theimageContentSourcessection to theinstall-config.yamlfile during installation. Mirror the images to a directory on the removable media:
oc adm release mirror -a ${LOCAL_SECRET_JSON} --to-dir=${REMOVABLE_MEDIA_PATH}/mirror quay.io/${PRODUCT_REPO}/${RELEASE_NAME}:${OCP_RELEASE}-${ARCHITECTURE}$ oc adm release mirror -a ${LOCAL_SECRET_JSON} --to-dir=${REMOVABLE_MEDIA_PATH}/mirror quay.io/${PRODUCT_REPO}/${RELEASE_NAME}:${OCP_RELEASE}-${ARCHITECTURE}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Take the media to the restricted network environment and upload the images to the local container registry.
oc image mirror -a ${LOCAL_SECRET_JSON} --from-dir=${REMOVABLE_MEDIA_PATH}/mirror "file://openshift/release:${OCP_RELEASE}*" ${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}$ oc image mirror -a ${LOCAL_SECRET_JSON} --from-dir=${REMOVABLE_MEDIA_PATH}/mirror "file://openshift/release:${OCP_RELEASE}*" ${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
REMOVABLE_MEDIA_PATH, you must use the same path that you specified when you mirrored the images.
If the local container registry is connected to the mirror host, take the following actions:
Directly push the release images to the local registry by using following command:
oc adm release mirror -a ${LOCAL_SECRET_JSON} \ --from=quay.io/${PRODUCT_REPO}/${RELEASE_NAME}:${OCP_RELEASE}-${ARCHITECTURE} \ --to=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY} \ --to-release-image=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}-${ARCHITECTURE}$ oc adm release mirror -a ${LOCAL_SECRET_JSON} \ --from=quay.io/${PRODUCT_REPO}/${RELEASE_NAME}:${OCP_RELEASE}-${ARCHITECTURE} \ --to=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY} \ --to-release-image=${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}-${ARCHITECTURE}Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command pulls the release information as a digest, and its output includes the
imageContentSourcesdata that you require when you install your cluster.Record the entire
imageContentSourcessection from the output of the previous command. The information about your mirrors is unique to your mirrored repository, and you must add theimageContentSourcessection to theinstall-config.yamlfile during installation.NoteThe image name gets patched to Quay.io during the mirroring process, and the podman images will show Quay.io in the registry on the bootstrap virtual machine.
To create the installation program that is based on the content that you mirrored, extract it and pin it to the release:
If your mirror host does not have Internet access, run the following command:
oc adm release extract -a ${LOCAL_SECRET_JSON} --command=openshift-install "${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}"$ oc adm release extract -a ${LOCAL_SECRET_JSON} --command=openshift-install "${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the local container registry is connected to the mirror host, run the following command:
oc adm release extract -a ${LOCAL_SECRET_JSON} --command=openshift-install "${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}-${ARCHITECTURE}"$ oc adm release extract -a ${LOCAL_SECRET_JSON} --command=openshift-install "${LOCAL_REGISTRY}/${LOCAL_REPOSITORY}:${OCP_RELEASE}-${ARCHITECTURE}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To ensure that you use the correct images for the version of OpenShift Container Platform that you selected, you must extract the installation program from the mirrored content.
You must perform this step on a machine with an active Internet connection.
If you are in a disconnected environment, use the --image flag as part of must-gather and point to the payload image.
1.8. The Cluster Samples Operator in a disconnected environment
In a disconnected environment, you must take additional steps after you install a cluster to configure the Cluster Samples Operator.
1.9. Next steps
- Mirror the OperatorHub images for the Operators that you want to install in your cluster.
- Install a cluster on infrastructure that you provision in your restricted network, such as on VMware vSphere, bare metal, or Amazon Web Services.
Chapter 2. Installing on AWS
2.1. Configuring an AWS account
Before you can install OpenShift Container Platform, you must configure an Amazon Web Services (AWS) account.
2.1.1. Configuring Route 53
To install OpenShift Container Platform, the Amazon Web Services (AWS) account you use must have a dedicated public hosted zone in your Route 53 service. This zone must be authoritative for the domain. The Route 53 service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through AWS or another source.
NoteIf you purchase a new domain through AWS, it takes time for the relevant DNS changes to propagate. For more information about purchasing domains through AWS, see Registering Domain Names Using Amazon Route 53 in the AWS documentation.
- If you are using an existing domain and registrar, migrate its DNS to AWS. See Making Amazon Route 53 the DNS Service for an Existing Domain in the AWS documentation.
Create a public hosted zone for your domain or subdomain. See Creating a Public Hosted Zone in the AWS documentation.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.- Extract the new authoritative name servers from the hosted zone records. See Getting the Name Servers for a Public Hosted Zone in the AWS documentation.
- Update the registrar records for the AWS Route 53 name servers that your domain uses. For example, if you registered your domain to a Route 53 service in a different accounts, see the following topic in the AWS documentation: Adding or Changing Name Servers or Glue Records.
- If you are using a subdomain, add its delegation records to the parent domain. This gives Amazon Route 53 responsibility for the subdomain. Follow the delegation procedure outlined by the DNS provider of the parent domain. See Creating a subdomain that uses Amazon Route 53 as the DNS service without migrating the parent domain in the AWS documentation for an example high level procedure.
2.1.1.1. Ingress Operator endpoint configuration for AWS Route 53
If you install in either Amazon Web Services (AWS) GovCloud (US) US-West or US-East region, the Ingress Operator uses us-gov-west-1 region for Route53 and tagging API clients.
The Ingress Operator uses https://tagging.us-gov-west-1.amazonaws.com as the tagging API endpoint if a tagging custom endpoint is configured that includes the string 'us-gov-east-1'.
For more information on AWS GovCloud (US) endpoints, see the Service Endpoints in the AWS documentation about GovCloud (US).
Private, disconnected installations are not supported for AWS GovCloud when you install in the us-gov-east-1 region.
Example Route 53 configuration
- 1
- Route 53 defaults to
https://route53.us-gov.amazonaws.comfor both AWS GovCloud (US) regions. - 2
- Only the US-West region has endpoints for tagging. Omit this parameter if your cluster is in another region.
2.1.2. AWS account limits
The OpenShift Container Platform cluster uses a number of Amazon Web Services (AWS) components, and the default Service Limits affect your ability to install OpenShift Container Platform clusters. If you use certain cluster configurations, deploy your cluster in certain AWS regions, or run multiple clusters from your account, you might need to request additional resources for your AWS account.
The following table summarizes the AWS components whose limits can impact your ability to install and run OpenShift Container Platform clusters.
| Component | Number of clusters available by default | Default AWS limit | Description |
|---|---|---|---|
| Instance Limits | Varies | Varies | By default, each cluster creates the following instances:
These instance type counts are within a new account’s default limit. To deploy more worker nodes, enable autoscaling, deploy large workloads, or use a different instance type, review your account limits to ensure that your cluster can deploy the machines that you need.
In most regions, the bootstrap and worker machines uses an |
| Elastic IPs (EIPs) | 0 to 1 | 5 EIPs per account | To provision the cluster in a highly available configuration, the installation program creates a public and private subnet for each availability zone within a region. Each private subnet requires a NAT Gateway, and each NAT gateway requires a separate elastic IP. Review the AWS region map to determine how many availability zones are in each region. To take advantage of the default high availability, install the cluster in a region with at least three availability zones. To install a cluster in a region with more than five availability zones, you must increase the EIP limit. Important
To use the |
| Virtual Private Clouds (VPCs) | 5 | 5 VPCs per region | Each cluster creates its own VPC. |
| Elastic Load Balancing (ELB/NLB) | 3 | 20 per region |
By default, each cluster creates internal and external network load balancers for the master API server and a single classic elastic load balancer for the router. Deploying more Kubernetes |
| NAT Gateways | 5 | 5 per availability zone | The cluster deploys one NAT gateway in each availability zone. |
| Elastic Network Interfaces (ENIs) | At least 12 | 350 per region |
The default installation creates 21 ENIs and an ENI for each availability zone in your region. For example, the Additional ENIs are created for additional machines and elastic load balancers that are created by cluster usage and deployed workloads. |
| VPC Gateway | 20 | 20 per account | Each cluster creates a single VPC Gateway for S3 access. |
| S3 buckets | 99 | 100 buckets per account | Because the installation process creates a temporary bucket and the registry component in each cluster creates a bucket, you can create only 99 OpenShift Container Platform clusters per AWS account. |
| Security Groups | 250 | 2,500 per account | Each cluster creates 10 distinct security groups. |
2.1.3. Required AWS permissions
Your IAM user must have the permission tag:GetResources in the region us-east-1 to delete the base cluster resources. As part of the AWS API requirement, the OpenShift Container Platform installation program performs various actions in this region.
When you attach the AdministratorAccess policy to the IAM user that you create in Amazon Web Services (AWS), you grant that user all of the required permissions. To deploy all components of an OpenShift Container Platform cluster, the IAM user requires the following permissions:
Example 2.1. Required EC2 permissions for installation
-
tag:TagResources -
tag:UntagResources -
ec2:AllocateAddress -
ec2:AssociateAddress -
ec2:AuthorizeSecurityGroupEgress -
ec2:AuthorizeSecurityGroupIngress -
ec2:CopyImage -
ec2:CreateNetworkInterface -
ec2:AttachNetworkInterface -
ec2:CreateSecurityGroup -
ec2:CreateTags -
ec2:CreateVolume -
ec2:DeleteSecurityGroup -
ec2:DeleteSnapshot -
ec2:DeleteTags -
ec2:DeregisterImage -
ec2:DescribeAccountAttributes -
ec2:DescribeAddresses -
ec2:DescribeAvailabilityZones -
ec2:DescribeDhcpOptions -
ec2:DescribeImages -
ec2:DescribeInstanceAttribute -
ec2:DescribeInstanceCreditSpecifications -
ec2:DescribeInstances -
ec2:DescribeInternetGateways -
ec2:DescribeKeyPairs -
ec2:DescribeNatGateways -
ec2:DescribeNetworkAcls -
ec2:DescribeNetworkInterfaces -
ec2:DescribePrefixLists -
ec2:DescribeRegions -
ec2:DescribeRouteTables -
ec2:DescribeSecurityGroups -
ec2:DescribeSubnets -
ec2:DescribeTags -
ec2:DescribeVolumes -
ec2:DescribeVpcAttribute -
ec2:DescribeVpcClassicLink -
ec2:DescribeVpcClassicLinkDnsSupport -
ec2:DescribeVpcEndpoints -
ec2:DescribeVpcs -
ec2:GetEbsDefaultKmsKeyId -
ec2:ModifyInstanceAttribute -
ec2:ModifyNetworkInterfaceAttribute -
ec2:ReleaseAddress -
ec2:RevokeSecurityGroupEgress -
ec2:RevokeSecurityGroupIngress -
ec2:RunInstances -
ec2:TerminateInstances
Example 2.2. Required permissions for creating network resources during installation
-
ec2:AssociateDhcpOptions -
ec2:AssociateRouteTable -
ec2:AttachInternetGateway -
ec2:CreateDhcpOptions -
ec2:CreateInternetGateway -
ec2:CreateNatGateway -
ec2:CreateRoute -
ec2:CreateRouteTable -
ec2:CreateSubnet -
ec2:CreateVpc -
ec2:CreateVpcEndpoint -
ec2:ModifySubnetAttribute -
ec2:ModifyVpcAttribute
If you use an existing VPC, your account does not require these permissions for creating network resources.
Example 2.3. Required Elastic Load Balancing permissions (ELB) for installation
-
elasticloadbalancing:AddTags -
elasticloadbalancing:ApplySecurityGroupsToLoadBalancer -
elasticloadbalancing:AttachLoadBalancerToSubnets -
elasticloadbalancing:ConfigureHealthCheck -
elasticloadbalancing:CreateLoadBalancer -
elasticloadbalancing:CreateLoadBalancerListeners -
elasticloadbalancing:DeleteLoadBalancer -
elasticloadbalancing:DeregisterInstancesFromLoadBalancer -
elasticloadbalancing:DescribeInstanceHealth -
elasticloadbalancing:DescribeLoadBalancerAttributes -
elasticloadbalancing:DescribeLoadBalancers -
elasticloadbalancing:DescribeTags -
elasticloadbalancing:ModifyLoadBalancerAttributes -
elasticloadbalancing:RegisterInstancesWithLoadBalancer -
elasticloadbalancing:SetLoadBalancerPoliciesOfListener
Example 2.4. Required Elastic Load Balancing permissions (ELBv2) for installation
-
elasticloadbalancing:AddTags -
elasticloadbalancing:CreateListener -
elasticloadbalancing:CreateLoadBalancer -
elasticloadbalancing:CreateTargetGroup -
elasticloadbalancing:DeleteLoadBalancer -
elasticloadbalancing:DeregisterTargets -
elasticloadbalancing:DescribeListeners -
elasticloadbalancing:DescribeLoadBalancerAttributes -
elasticloadbalancing:DescribeLoadBalancers -
elasticloadbalancing:DescribeTargetGroupAttributes -
elasticloadbalancing:DescribeTargetHealth -
elasticloadbalancing:ModifyLoadBalancerAttributes -
elasticloadbalancing:ModifyTargetGroup -
elasticloadbalancing:ModifyTargetGroupAttributes -
elasticloadbalancing:RegisterTargets
Example 2.5. Required IAM permissions for installation
-
iam:AddRoleToInstanceProfile -
iam:CreateInstanceProfile -
iam:CreateRole -
iam:DeleteInstanceProfile -
iam:DeleteRole -
iam:DeleteRolePolicy -
iam:GetInstanceProfile -
iam:GetRole -
iam:GetRolePolicy -
iam:GetUser -
iam:ListInstanceProfilesForRole -
iam:ListRoles -
iam:ListUsers -
iam:PassRole -
iam:PutRolePolicy -
iam:RemoveRoleFromInstanceProfile -
iam:SimulatePrincipalPolicy -
iam:TagRole
If you have not created an elastic load balancer (ELB) in your AWS account, the IAM user also requires the iam:CreateServiceLinkedRole permission.
Example 2.6. Required Route 53 permissions for installation
-
route53:ChangeResourceRecordSets -
route53:ChangeTagsForResource -
route53:CreateHostedZone -
route53:DeleteHostedZone -
route53:GetChange -
route53:GetHostedZone -
route53:ListHostedZones -
route53:ListHostedZonesByName -
route53:ListResourceRecordSets -
route53:ListTagsForResource -
route53:UpdateHostedZoneComment
Example 2.7. Required S3 permissions for installation
-
s3:CreateBucket -
s3:DeleteBucket -
s3:GetAccelerateConfiguration -
s3:GetBucketAcl -
s3:GetBucketCors -
s3:GetBucketLocation -
s3:GetBucketLogging -
s3:GetBucketObjectLockConfiguration -
s3:GetBucketReplication -
s3:GetBucketRequestPayment -
s3:GetBucketTagging -
s3:GetBucketVersioning -
s3:GetBucketWebsite -
s3:GetEncryptionConfiguration -
s3:GetLifecycleConfiguration -
s3:GetReplicationConfiguration -
s3:ListBucket -
s3:PutBucketAcl -
s3:PutBucketTagging -
s3:PutEncryptionConfiguration
Example 2.8. S3 permissions that cluster Operators require
-
s3:DeleteObject -
s3:GetObject -
s3:GetObjectAcl -
s3:GetObjectTagging -
s3:GetObjectVersion -
s3:PutObject -
s3:PutObjectAcl -
s3:PutObjectTagging
Example 2.9. Required permissions to delete base cluster resources
-
autoscaling:DescribeAutoScalingGroups -
ec2:DeleteNetworkInterface -
ec2:DeleteVolume -
elasticloadbalancing:DeleteTargetGroup -
elasticloadbalancing:DescribeTargetGroups -
iam:DeleteAccessKey -
iam:DeleteUser -
iam:ListAttachedRolePolicies -
iam:ListInstanceProfiles -
iam:ListRolePolicies -
iam:ListUserPolicies -
s3:DeleteObject -
s3:ListBucketVersions -
tag:GetResources
Example 2.10. Required permissions to delete network resources
-
ec2:DeleteDhcpOptions -
ec2:DeleteInternetGateway -
ec2:DeleteNatGateway -
ec2:DeleteRoute -
ec2:DeleteRouteTable -
ec2:DeleteSubnet -
ec2:DeleteVpc -
ec2:DeleteVpcEndpoints -
ec2:DetachInternetGateway -
ec2:DisassociateRouteTable -
ec2:ReplaceRouteTableAssociation
If you use an existing VPC, your account does not require these permissions to delete network resources.
Example 2.11. Additional IAM and S3 permissions that are required to create manifests
-
iam:DeleteAccessKey -
iam:DeleteUser -
iam:DeleteUserPolicy -
iam:GetUserPolicy -
iam:ListAccessKeys -
iam:PutUserPolicy -
iam:TagUser -
iam:GetUserPolicy -
iam:ListAccessKeys -
s3:PutBucketPublicAccessBlock -
s3:GetBucketPublicAccessBlock -
s3:PutLifecycleConfiguration -
s3:HeadBucket -
s3:ListBucketMultipartUploads -
s3:AbortMultipartUpload
If you are managing your cloud provider credentials with mint mode, the IAM user also requires the iam:CreateAccessKey and iam:CreateUser permissions.
Example 2.12. Optional permission for quota checks for installation
-
servicequotas:ListAWSDefaultServiceQuotas
2.1.4. Creating an IAM user
Each Amazon Web Services (AWS) account contains a root user account that is based on the email address you used to create the account. This is a highly-privileged account, and it is recommended to use it for only initial account and billing configuration, creating an initial set of users, and securing the account.
Before you install OpenShift Container Platform, create a secondary IAM administrative user. As you complete the Creating an IAM User in Your AWS Account procedure in the AWS documentation, set the following options:
Procedure
-
Specify the IAM user name and select
Programmatic access. Attach the
AdministratorAccesspolicy to ensure that the account has sufficient permission to create the cluster. This policy provides the cluster with the ability to grant credentials to each OpenShift Container Platform component. The cluster grants the components only the credentials that they require.NoteWhile it is possible to create a policy that grants the all of the required AWS permissions and attach it to the user, this is not the preferred option. The cluster will not have the ability to grant additional credentials to individual components, so the same credentials are used by all components.
- Optional: Add metadata to the user by attaching tags.
-
Confirm that the user name that you specified is granted the
AdministratorAccesspolicy. Record the access key ID and secret access key values. You must use these values when you configure your local machine to run the installation program.
ImportantYou cannot use a temporary session token that you generated while using a multi-factor authentication device to authenticate to AWS when you deploy a cluster. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use key-based, long-lived credentials.
2.1.5. Supported AWS regions
You can deploy an OpenShift Container Platform cluster to the following public regions:
Your IAM user must have the permission tag:GetResources in the region us-east-1 to delete the base cluster resources. As part of the AWS API requirement, the OpenShift Container Platform installation program performs various actions in this region.
-
af-south-1(Cape Town) -
ap-east-1(Hong Kong) -
ap-northeast-1(Tokyo) -
ap-northeast-2(Seoul) -
ap-northeast-3(Osaka) -
ap-south-1(Mumbai) -
ap-southeast-1(Singapore) -
ap-southeast-2(Sydney) -
ca-central-1(Central) -
eu-central-1(Frankfurt) -
eu-north-1(Stockholm) -
eu-south-1(Milan) -
eu-west-1(Ireland) -
eu-west-2(London) -
eu-west-3(Paris) -
me-south-1(Bahrain) -
sa-east-1(São Paulo) -
us-east-1(N. Virginia) -
us-east-2(Ohio) -
us-west-1(N. California) -
us-west-2(Oregon)
The following AWS GovCloud regions are supported:
-
us-gov-west-1 -
us-gov-east-1
2.1.6. Next steps
Install an OpenShift Container Platform cluster:
- Quickly install a cluster with default options on installer-provisioned infrastructure
- Install a cluster with cloud customizations on installer-provisioned infrastructure
- Install a cluster with network customizations on installer-provisioned infrastructure
- Installing a cluster on user-provisioned infrastructure in AWS by using CloudFormation templates
2.2. Manually creating IAM for AWS
In environments where the cloud identity and access management (IAM) APIs are not reachable, or the administrator prefers not to store an administrator-level credential secret in the cluster kube-system namespace, you can put the Cloud Credential Operator (CCO) into manual mode before you install the cluster.
2.2.1. Alternatives to storing administrator-level secrets in the kube-system project
The Cloud Credential Operator (CCO) manages cloud provider credentials as Kubernetes custom resource definitions (CRDs). You can configure the CCO to suit the security requirements of your organization by setting different values for the credentialsMode parameter in the install-config.yaml file.
If you prefer not to store an administrator-level credential secret in the cluster kube-system project, you can choose one of the following options when installing OpenShift Container Platform:
Manage cloud credentials manually:
You can set the
credentialsModeparameter for the CCO toManualto manage cloud credentials manually. Using manual mode allows each cluster component to have only the permissions it requires, without storing an administrator-level credential in the cluster. You can also use this mode if your environment does not have connectivity to the cloud provider public IAM endpoint. However, you must manually reconcile permissions with new release images for every upgrade. You must also manually supply credentials for every component that requests them.Remove the administrator-level credential secret after installing OpenShift Container Platform with mint mode:
If you are using the CCO with the
credentialsModeparameter set toMint, you can remove or rotate the administrator-level credential after installing OpenShift Container Platform. Mint mode is the default configuration for the CCO. This option requires the presence of the administrator-level credential during an installation. The administrator-level credential is used during the installation to mint other credentials with some permissions granted. The original credential secret is not stored in the cluster permanently.
Prior to a non z-stream upgrade, you must reinstate the credential secret with the administrator-level credential. If the credential is not present, the upgrade might be blocked.
2.2.2. Manually create IAM
The Cloud Credential Operator (CCO) can be put into manual mode prior to installation in environments where the cloud identity and access management (IAM) APIs are not reachable, or the administrator prefers not to store an administrator-level credential secret in the cluster kube-system namespace.
Procedure
Change to the directory that contains the installation program and create the
install-config.yamlfile:openshift-install create install-config --dir <installation_directory>
$ openshift-install create install-config --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
install-config.yamlconfiguration file so that it contains thecredentialsModeparameter set toManual.Example
install-config.yamlconfiguration fileCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- This line is added to set the
credentialsModeparameter toManual.
To generate the manifests, run the following command from the directory that contains the installation program:
openshift-install create manifests --dir <installation_directory>
$ openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
Remove the
admincredential secret created using your local cloud credentials. This removal prevents youradmincredential from being stored in the cluster:rm mycluster/openshift/99_cloud-creds-secret.yaml
$ rm mycluster/openshift/99_cloud-creds-secret.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the directory that contains the installation program, obtain details of the OpenShift Container Platform release image that your
openshift-installbinary is built to use:openshift-install version
$ openshift-install versionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
release image quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64
release image quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Locate all
CredentialsRequestobjects in this release image that target the cloud you are deploying on:oc adm release extract quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64 --credentials-requests --cloud=aws
$ oc adm release extract quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64 --credentials-requests --cloud=awsCopy to Clipboard Copied! Toggle word wrap Toggle overflow This displays the details for each request.
Sample
CredentialsRequestobjectCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Create YAML files for secrets in the
openshift-installmanifests directory that you generated previously. The secrets must be stored using the namespace and secret name defined in thespec.secretReffor eachcredentialsRequest. The format for the secret data varies for each cloud provider. From the directory that contains the installation program, proceed with your cluster creation:
openshift-install create cluster --dir <installation_directory>
$ openshift-install create cluster --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantBefore upgrading a cluster that uses manually maintained credentials, you must ensure that the CCO is in an upgradeable state. For details, see the Upgrading clusters with manually maintained credentials section of the installation content for your cloud provider.
2.2.3. Admin credentials root secret format
Each cloud provider uses a credentials root secret in the kube-system namespace by convention, which is then used to satisfy all credentials requests and create their respective secrets. This is done either by minting new credentials, with mint mode, or by copying the credentials root secret, with passthrough mode.
The format for the secret varies by cloud, and is also used for each CredentialsRequest secret.
Amazon Web Services (AWS) secret format
2.2.4. Upgrading clusters with manually maintained credentials
If credentials are added in a future release, the Cloud Credential Operator (CCO) upgradable status for a cluster with manually maintained credentials changes to false. For minor release, for example, from 4.5 to 4.6, this status prevents you from upgrading until you have addressed any updated permissions. For z-stream releases, for example, from 4.5.10 to 4.5.11, the upgrade is not blocked, but the credentials must still be updated for the new release.
Use the Administrator perspective of the web console to determine if the CCO is upgradeable.
- Navigate to Administration → Cluster Settings.
- To view the CCO status details, click cloud-credential in the Cluster Operators list.
-
If the Upgradeable status in the Conditions section is False, examine the
credentialsRequestsfor the new release and update the manually maintained credentials on your cluster to match before upgrading.
In addition to creating new credentials for the release image that you are upgrading to, you must review the required permissions for existing credentials and accommodate any new permissions requirements for existing components in the new release. The CCO cannot detect these mismatches and will not set upgradable to false in this case.
The Manually creating IAM section of the installation content for your cloud provider explains how to obtain and use the credentials required for your cloud.
2.2.5. Mint mode
Mint mode is the default and recommended Cloud Credential Operator (CCO) credentials mode for OpenShift Container Platform. In this mode, the CCO uses the provided administrator-level cloud credential to run the cluster. Mint mode is supported for AWS, GCP, and Azure.
In mint mode, the admin credential is stored in the kube-system namespace and then used by the CCO to process the CredentialsRequest objects in the cluster and create users for each with specific permissions.
The benefits of mint mode include:
- Each cluster component has only the permissions it requires
- Automatic, on-going reconciliation for cloud credentials, including additional credentials or permissions that might be required for upgrades
One drawback is that mint mode requires admin credential storage in a cluster kube-system secret.
2.2.6. Mint Mode with removal or rotation of the admin credential
Currently, this mode is only supported on AWS.
In this mode, a user installs OpenShift Container Platform with an admin credential just like the normal mint mode. However, this mode removes the admin credential secret from the cluster post-installation.
The administrator can have the Cloud Credential Operator make its own request for a read-only credential that allows it to verify if all CredentialsRequest objects have their required permissions, thus the admin credential is not required unless something needs to be changed. After the associated credential is removed, it can be destroyed on the underlying cloud, if desired.
Prior to upgrade, the admin credential should be restored. In the future, upgrade might be blocked if the credential is not present.
The admin credential is not stored in the cluster permanently.
This mode still requires the admin credential in the cluster for brief periods of time. It also requires manually re-instating the secret with admin credentials for each upgrade.
2.2.7. Next steps
Install an OpenShift Container Platform cluster:
- Installing a cluster quickly on AWS with default options on installer-provisioned infrastructure
- Install a cluster with cloud customizations on installer-provisioned infrastructure
- Install a cluster with network customizations on installer-provisioned infrastructure
- Installing a cluster on user-provisioned infrastructure in AWS by using CloudFormation templates
2.3. Installing a cluster quickly on AWS
In OpenShift Container Platform version 4.6, you can install a cluster on Amazon Web Services (AWS) that uses the default configuration options.
2.3.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
Configure an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use key-based, long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.3.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.3.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.3.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.3.5. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Provide values at the prompts:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select aws as the platform to target.
If you do not have an Amazon Web Services (AWS) profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
NoteThe AWS access key ID and secret access key are stored in
~/.aws/credentialsin the home directory of the current user on the installation host. You are prompted for the credentials by the installation program if the credentials for the exported profile are not present in the file. Any credentials that you provide to the installation program are stored in the file.- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
Optional: Remove or disable the
AdministratorAccesspolicy from the IAM account that you used to install the cluster.NoteThe elevated permissions provided by the
AdministratorAccesspolicy are required only during installation.
2.3.6. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.3.6.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.3.6.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.3.6.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.3.7. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.3.8. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.3.9. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.3.10. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.4. Installing a cluster on AWS with customizations
In OpenShift Container Platform version 4.6, you can install a customized cluster on infrastructure that the installation program provisions on Amazon Web Services (AWS). To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
2.4.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
Configure an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.4.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.4.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.4.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.4.5. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Amazon Web Services (AWS).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select AWS as the platform to target.
- If you do not have an Amazon Web Services (AWS) profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
2.4.5.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
2.4.5.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
2.4.5.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
2.4.5.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
2.4.5.1.4. Optional AWS configuration parameters
Optional AWS configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The AWS AMI used to boot compute machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Input/Output Operations Per Second (IOPS) that is reserved for the root volume. |
Integer, for example |
|
| The size in GiB of the root volume. |
Integer, for example |
|
| The type of the root volume. |
Valid AWS EBS volume type, such as |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of worker nodes with a specific KMS key. | Valid key ID or the key ARN. |
|
| The EC2 instance type for the compute machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the compute machine pool. If you provide your own VPC, you must provide a subnet in that availability zone. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates compute resources in. |
Any valid AWS region, such as |
|
| The AWS AMI used to boot control plane machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of control plane nodes with a specific KMS key. | Valid key ID and the key ARN. |
|
| The EC2 instance type for the control plane machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the control plane machine pool. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates control plane resources in. |
Valid AWS region, such as |
|
| The AWS AMI used to boot all machines for the cluster. If set, the AMI must belong to the same region as the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The AWS service endpoint name. Custom endpoints are only required for cases where alternative AWS endpoints, like FIPS, must be used. Custom API endpoints can be specified for EC2, S3, IAM, Elastic Load Balancing, Tagging, Route 53, and STS AWS services. | Valid AWS service endpoint name. |
|
|
The AWS service endpoint URL. The URL must use the | Valid AWS service endpoint URL. |
|
| A map of keys and values that the installation program adds as tags to all resources that it creates. |
Any valid YAML map, such as key value pairs in the |
|
|
If you provide the VPC instead of allowing the installation program to create the VPC for you, specify the subnet for the cluster to use. The subnet must be part of the same | Valid subnet IDs. |
2.4.5.2. Sample customized install-config.yaml file for AWS
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 11 16
- Required. The installation program prompts you for this value.
- 2
- Optional: Add this parameter to force the Cloud Credential Operator (CCO) to use the specified mode, instead of having the CCO dynamically try to determine the capabilities of the credentials. For details about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
- 3 7
- If you do not provide these parameters and values, the installation program provides the default value.
- 4
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 5 8
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger instance types, such as
m4.2xlargeorm5.2xlarge, for your machines if you disable simultaneous multithreading. - 6 9
- To configure faster storage for etcd, especially for larger clusters, set the storage type as
io1and setiopsto2000. - 12
- The ID of the AMI used to boot machines for the cluster. If set, the AMI must belong to the same region as the cluster.
- 13
- The AWS service endpoints. Custom endpoints are required when installing to an unknown AWS region. The endpoint URL must use the
httpsprotocol and the host must trust the certificate. - 14
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 15
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
2.4.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.4.6. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: Remove or disable the
AdministratorAccesspolicy from the IAM account that you used to install the cluster.NoteThe elevated permissions provided by the
AdministratorAccesspolicy are required only during installation.
2.4.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.4.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.4.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.4.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.4.8. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.4.9. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.4.10. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.4.11. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.5. Installing a cluster on AWS with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster on Amazon Web Services (AWS) with customized network configuration options. By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing MTU and VXLAN configurations.
You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
2.5.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
Configure an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use key-based, long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.5.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.5.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.5.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.5.5. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
2.5.6. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Amazon Web Services (AWS).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select AWS as the platform to target.
- If you do not have an Amazon Web Services (AWS) profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
2.5.6.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
2.5.6.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
2.5.6.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
2.5.6.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
2.5.6.1.4. Optional AWS configuration parameters
Optional AWS configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The AWS AMI used to boot compute machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Input/Output Operations Per Second (IOPS) that is reserved for the root volume. |
Integer, for example |
|
| The size in GiB of the root volume. |
Integer, for example |
|
| The type of the root volume. |
Valid AWS EBS volume type, such as |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of worker nodes with a specific KMS key. | Valid key ID or the key ARN. |
|
| The EC2 instance type for the compute machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the compute machine pool. If you provide your own VPC, you must provide a subnet in that availability zone. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates compute resources in. |
Any valid AWS region, such as |
|
| The AWS AMI used to boot control plane machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of control plane nodes with a specific KMS key. | Valid key ID and the key ARN. |
|
| The EC2 instance type for the control plane machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the control plane machine pool. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates control plane resources in. |
Valid AWS region, such as |
|
| The AWS AMI used to boot all machines for the cluster. If set, the AMI must belong to the same region as the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The AWS service endpoint name. Custom endpoints are only required for cases where alternative AWS endpoints, like FIPS, must be used. Custom API endpoints can be specified for EC2, S3, IAM, Elastic Load Balancing, Tagging, Route 53, and STS AWS services. | Valid AWS service endpoint name. |
|
|
The AWS service endpoint URL. The URL must use the | Valid AWS service endpoint URL. |
|
| A map of keys and values that the installation program adds as tags to all resources that it creates. |
Any valid YAML map, such as key value pairs in the |
|
|
If you provide the VPC instead of allowing the installation program to create the VPC for you, specify the subnet for the cluster to use. The subnet must be part of the same | Valid subnet IDs. |
2.5.6.2. Sample customized install-config.yaml file for AWS
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 12 17
- Required. The installation program prompts you for this value.
- 2
- Optional: Add this parameter to force the Cloud Credential Operator (CCO) to use the specified mode, instead of having the CCO dynamically try to determine the capabilities of the credentials. For details about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
- 3 7 11
- If you do not provide these parameters and values, the installation program provides the default value.
- 4
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 5 8
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger instance types, such as
m4.2xlargeorm5.2xlarge, for your machines if you disable simultaneous multithreading. - 6 9
- To configure faster storage for etcd, especially for larger clusters, set the storage type as
io1and setiopsto2000. - 13
- The ID of the AMI used to boot machines for the cluster. If set, the AMI must belong to the same region as the cluster.
- 14
- The AWS service endpoints. Custom endpoints are required when installing to an unknown AWS region. The endpoint URL must use the
httpsprotocol and the host must trust the certificate. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
2.5.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.5.7. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
2.5.7.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
2.5.8. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
For more information on using a Network Load Balancer (NLB) on AWS, see Configuring Ingress cluster traffic on AWS using a Network Load Balancer.
2.5.9. Configuring an Ingress Controller Network Load Balancer on a new AWS cluster
You can create an Ingress Controller backed by an AWS Network Load Balancer (NLB) on a new cluster.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Create an Ingress Controller backed by an AWS NLB on a new cluster.
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the name of the directory that contains theinstall-config.yamlfile for your cluster.
Create a file that is named
cluster-ingress-default-ingresscontroller.yamlin the<installation_directory>/manifests/directory:touch <installation_directory>/manifests/cluster-ingress-default-ingresscontroller.yaml
$ touch <installation_directory>/manifests/cluster-ingress-default-ingresscontroller.yaml1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name that contains themanifests/directory for your cluster.
After creating the file, several network configuration files are in the
manifests/directory, as shown:ls <installation_directory>/manifests/cluster-ingress-default-ingresscontroller.yaml
$ ls <installation_directory>/manifests/cluster-ingress-default-ingresscontroller.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
cluster-ingress-default-ingresscontroller.yaml
cluster-ingress-default-ingresscontroller.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the
cluster-ingress-default-ingresscontroller.yamlfile in an editor and enter a CR that describes the Operator configuration you want:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-ingress-default-ingresscontroller.yamlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-ingress-default-ingresscontroller.yamlfile. The installation program deletes themanifests/directory when creating the cluster.
2.5.10. Configuring hybrid networking with OVN-Kubernetes
You can configure your cluster to use hybrid networking with OVN-Kubernetes. This allows a hybrid cluster that supports different node networking configurations. For example, this is necessary to run both Linux and Windows nodes in a cluster.
You must configure hybrid networking with OVN-Kubernetes during the installation of your cluster. You cannot switch to hybrid networking after the installation process.
Prerequisites
-
You defined
OVNKubernetesfor thenetworking.networkTypeparameter in theinstall-config.yamlfile. See the installation documentation for configuring OpenShift Container Platform network customizations on your chosen cloud provider for more information.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and configure OVN-Kubernetes with hybrid networking, such as in the following example:Specify a hybrid networking configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the CIDR configuration used for nodes on the additional overlay network. The
hybridClusterNetworkCIDR cannot overlap with theclusterNetworkCIDR. - 2
- Specify a custom VXLAN port for the additional overlay network. This is required for running Windows nodes in a cluster installed on vSphere, and must not be configured for any other cloud provider. The custom port can be any open port excluding the default
4789port. For more information on this requirement, see the Microsoft documentation on Pod-to-pod connectivity between hosts is broken.
-
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
For more information on using Linux and Windows nodes in the same cluster, see Understanding Windows container workloads.
2.5.11. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: Remove or disable the
AdministratorAccesspolicy from the IAM account that you used to install the cluster.NoteThe elevated permissions provided by the
AdministratorAccesspolicy are required only during installation.
2.5.12. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.5.12.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.5.12.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.5.12.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.5.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.5.14. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.5.15. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.5.16. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.6. Installing a cluster on AWS in a restricted network
In OpenShift Container Platform version 4.6, you can install a cluster on Amazon Web Services (AWS) in a restricted network by creating an internal mirror of the installation release content on an existing Amazon Virtual Private Cloud (VPC).
2.6.1. Prerequisites
You mirrored the images for a disconnected installation to your registry and obtained the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
You have an existing VPC in AWS. When installing to a restricted network using installer-provisioned infrastructure, you cannot use the installer-provisioned VPC. You must use a user-provisioned VPC that satisfies one of the following requirements:
- Contains the mirror registry.
- Has firewall rules or a peering connection to access the mirror registry hosted elsewhere.
- You reviewed details about the OpenShift Container Platform installation and update processes.
You configured an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use key-based, long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer (Linux, macOS, or Unix) in the AWS documentation.
If you use a firewall and plan to use the Telemetry service, you configured the firewall to allow the sites that your cluster requires access to.
NoteIf you are configuring a proxy, be sure to also review this site list.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.6.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
2.6.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
2.6.3. About using a custom VPC
In OpenShift Container Platform 4.6, you can deploy a cluster into existing subnets in an existing Amazon Virtual Private Cloud (VPC) in Amazon Web Services (AWS). By deploying OpenShift Container Platform into an existing AWS VPC, you might be able to avoid limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. If you cannot obtain the infrastructure creation permissions that are required to create the VPC yourself, use this installation option.
Because the installation program cannot know what other components are also in your existing subnets, it cannot choose subnet CIDRs and so forth on your behalf. You must configure networking for the subnets that you install your cluster to yourself.
2.6.3.1. Requirements for using your VPC
The installation program no longer creates the following components:
- Internet gateways
- NAT gateways
- Subnets
- Route tables
- VPCs
- VPC DHCP options
- VPC endpoints
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VPC, you must correctly configure it and its subnets for the installation program and the cluster to use. See Amazon VPC console wizard configurations and Work with VPCs and subnets in the AWS documentation for more information on creating and managing an AWS VPC.
The installation program cannot:
- Subdivide network ranges for the cluster to use.
- Set route tables for the subnets.
- Set VPC options like DHCP.
You must complete these tasks before you install the cluster. See VPC networking components and Route tables for your VPC for more information on configuring networking in an AWS VPC.
Your VPC must meet the following characteristics:
The VPC must not use the
kubernetes.io/cluster/.*: ownedtag.The installation program modifies your subnets to add the
kubernetes.io/cluster/.*: sharedtag, so your subnets must have at least one free tag slot available for it. See Tag Restrictions in the AWS documentation to confirm that the installation program can add a tag to each subnet that you specify.You must enable the
enableDnsSupportandenableDnsHostnamesattributes in your VPC, so that the cluster can use the Route 53 zones that are attached to the VPC to resolve cluster’s internal DNS records. See DNS Support in Your VPC in the AWS documentation.If you prefer to use your own Route 53 hosted private zone, you must associate the existing hosted zone with your VPC prior to installing a cluster. You can define your hosted zone using the
platform.aws.hostedZonefield in theinstall-config.yamlfile.- If you use a cluster with public access, you must create a public and a private subnet for each availability zone that your cluster uses. Each availability zone can contain no more than one public and one private subnet.
If you are working in a disconnected environment, you are unable to reach the public IP addresses for EC2 and ELB endpoints. To resolve this, you must create a VPC endpoint and attach it to the subnet that the clusters are using. The endpoints should be named as follows:
-
ec2.<region>.amazonaws.com -
elasticloadbalancing.<region>.amazonaws.com -
s3.<region>.amazonaws.com
Required VPC components
You must provide a suitable VPC and subnets that allow communication to your machines.
| Component | AWS type | Description | |
|---|---|---|---|
| VPC |
| You must provide a public VPC for the cluster to use. The VPC uses an endpoint that references the route tables for each subnet to improve communication with the registry that is hosted in S3. | |
| Public subnets |
| Your VPC must have public subnets for between 1 and 3 availability zones and associate them with appropriate Ingress rules. | |
| Internet gateway |
| You must have a public Internet gateway, with public routes, attached to the VPC. In the provided templates, each public subnet has a NAT gateway with an EIP address. These NAT gateways allow cluster resources, like private subnet instances, to reach the Internet and are not required for some restricted network or proxy scenarios. | |
| Network access control |
| You must allow the VPC to access the following ports: | |
| Port | Reason | ||
|
| Inbound HTTP traffic | ||
|
| Inbound HTTPS traffic | ||
|
| Inbound SSH traffic | ||
|
| Inbound ephemeral traffic | ||
|
| Outbound ephemeral traffic | ||
| Private subnets |
| Your VPC can have private subnets. The provided CloudFormation templates can create private subnets for between 1 and 3 availability zones. If you use private subnets, you must provide appropriate routes and tables for them. | |
2.6.3.2. VPC validation
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the subnets that you specify exist.
- You provide private subnets.
- The subnet CIDRs belong to the machine CIDR that you specified.
- You provide subnets for each availability zone. Each availability zone contains no more than one public and one private subnet. If you use a private cluster, provide only a private subnet for each availability zone. Otherwise, provide exactly one public and private subnet for each availability zone.
- You provide a public subnet for each private subnet availability zone. Machines are not provisioned in availability zones that you do not provide private subnets for.
If you destroy a cluster that uses an existing VPC, the VPC is not deleted. When you remove the OpenShift Container Platform cluster from a VPC, the kubernetes.io/cluster/.*: shared tag is removed from the subnets that it used.
2.6.3.3. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resource in your clouds than others. For example, you might be able to create application-specific items, like instances, buckets, and load balancers, but not networking-related components such as VPCs, subnets, or ingress rules.
The AWS credentials that you use when you create your cluster do not need the networking permissions that are required to make VPCs and core networking components within the VPC, such as subnets, routing tables, Internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as ELBs, security groups, S3 buckets, and nodes.
2.6.3.4. Isolation between clusters
If you deploy OpenShift Container Platform to an existing network, the isolation of cluster services is reduced in the following ways:
- You can install multiple OpenShift Container Platform clusters in the same VPC.
- ICMP ingress is allowed from the entire network.
- TCP 22 ingress (SSH) is allowed to the entire network.
- Control plane TCP 6443 ingress (Kubernetes API) is allowed to the entire network.
- Control plane TCP 22623 ingress (MCS) is allowed to the entire network.
2.6.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.6.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.6.6. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Amazon Web Services (AWS).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
Have the
imageContentSourcesvalues that were generated during mirror registry creation. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select AWS as the platform to target.
- If you do not have an Amazon Web Services (AWS) profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<mirror_host_name>, specify the registry domain name that you specified in the certificate for your mirror registry, and for<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.
Define the subnets for the VPC to install the cluster in:
subnets: - subnet-1 - subnet-2 - subnet-3
subnets: - subnet-1 - subnet-2 - subnet-3Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the image content resources, which look like this excerpt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To complete these values, use the
imageContentSourcesthat you recorded during mirror registry creation.
-
Make any other modifications to the
install-config.yamlfile that you require. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
2.6.6.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
2.6.6.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
2.6.6.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
2.6.6.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
2.6.6.1.4. Optional AWS configuration parameters
Optional AWS configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The AWS AMI used to boot compute machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Input/Output Operations Per Second (IOPS) that is reserved for the root volume. |
Integer, for example |
|
| The size in GiB of the root volume. |
Integer, for example |
|
| The type of the root volume. |
Valid AWS EBS volume type, such as |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of worker nodes with a specific KMS key. | Valid key ID or the key ARN. |
|
| The EC2 instance type for the compute machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the compute machine pool. If you provide your own VPC, you must provide a subnet in that availability zone. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates compute resources in. |
Any valid AWS region, such as |
|
| The AWS AMI used to boot control plane machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of control plane nodes with a specific KMS key. | Valid key ID and the key ARN. |
|
| The EC2 instance type for the control plane machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the control plane machine pool. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates control plane resources in. |
Valid AWS region, such as |
|
| The AWS AMI used to boot all machines for the cluster. If set, the AMI must belong to the same region as the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The AWS service endpoint name. Custom endpoints are only required for cases where alternative AWS endpoints, like FIPS, must be used. Custom API endpoints can be specified for EC2, S3, IAM, Elastic Load Balancing, Tagging, Route 53, and STS AWS services. | Valid AWS service endpoint name. |
|
|
The AWS service endpoint URL. The URL must use the | Valid AWS service endpoint URL. |
|
| A map of keys and values that the installation program adds as tags to all resources that it creates. |
Any valid YAML map, such as key value pairs in the |
|
|
If you provide the VPC instead of allowing the installation program to create the VPC for you, specify the subnet for the cluster to use. The subnet must be part of the same | Valid subnet IDs. |
2.6.6.2. Sample customized install-config.yaml file for AWS
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 11
- Required. The installation program prompts you for this value.
- 2
- Optional: Add this parameter to force the Cloud Credential Operator (CCO) to use the specified mode, instead of having the CCO dynamically try to determine the capabilities of the credentials. For details about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
- 3 7
- If you do not provide these parameters and values, the installation program provides the default value.
- 4
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 5 8
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger instance types, such as
m4.2xlargeorm5.2xlarge, for your machines if you disable simultaneous multithreading. - 6 9
- To configure faster storage for etcd, especially for larger clusters, set the storage type as
io1and setiopsto2000. - 12
- If you provide your own VPC, specify subnets for each availability zone that your cluster uses.
- 13
- The ID of the AMI used to boot machines for the cluster. If set, the AMI must belong to the same region as the cluster.
- 14
- The AWS service endpoints. Custom endpoints are required when installing to an unknown AWS region. The endpoint URL must use the
httpsprotocol and the host must trust the certificate. - 15
- The ID of your existing Route 53 private hosted zone. Providing an existing hosted zone requires that you supply your own VPC and the hosted zone is already associated with the VPC prior to installing your cluster. If undefined, the installation program creates a new hosted zone.
- 16
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 17
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 18
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 19
- Provide the contents of the certificate file that you used for your mirror registry.
- 20
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
2.6.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.6.7. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: Remove or disable the
AdministratorAccesspolicy from the IAM account that you used to install the cluster.NoteThe elevated permissions provided by the
AdministratorAccesspolicy are required only during installation.
2.6.8. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.6.8.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.6.8.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.6.8.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.6.9. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.6.10. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
2.6.11. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.6.12. Next steps
- Validate an installation.
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
2.7. Installing a cluster on AWS into an existing VPC
In OpenShift Container Platform version 4.6, you can install a cluster into an existing Amazon Virtual Private Cloud (VPC) on Amazon Web Services (AWS). The installation program provisions the rest of the required infrastructure, which you can further customize. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
2.7.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
Configure an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.7.2. About using a custom VPC
In OpenShift Container Platform 4.6, you can deploy a cluster into existing subnets in an existing Amazon Virtual Private Cloud (VPC) in Amazon Web Services (AWS). By deploying OpenShift Container Platform into an existing AWS VPC, you might be able to avoid limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. If you cannot obtain the infrastructure creation permissions that are required to create the VPC yourself, use this installation option.
Because the installation program cannot know what other components are also in your existing subnets, it cannot choose subnet CIDRs and so forth on your behalf. You must configure networking for the subnets that you install your cluster to yourself.
2.7.2.1. Requirements for using your VPC
The installation program no longer creates the following components:
- Internet gateways
- NAT gateways
- Subnets
- Route tables
- VPCs
- VPC DHCP options
- VPC endpoints
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VPC, you must correctly configure it and its subnets for the installation program and the cluster to use. See Amazon VPC console wizard configurations and Work with VPCs and subnets in the AWS documentation for more information on creating and managing an AWS VPC.
The installation program cannot:
- Subdivide network ranges for the cluster to use.
- Set route tables for the subnets.
- Set VPC options like DHCP.
You must complete these tasks before you install the cluster. See VPC networking components and Route tables for your VPC for more information on configuring networking in an AWS VPC.
Your VPC must meet the following characteristics:
Create a public and private subnet for each availability zone that your cluster uses. Each availability zone can contain no more than one public and one private subnet. For an example of this type of configuration, see VPC with public and private subnets (NAT) in the AWS documentation.
Record each subnet ID. Completing the installation requires that you enter these values in the
platformsection of theinstall-config.yamlfile. See Finding a subnet ID in the AWS documentation.-
The VPC’s CIDR block must contain the
Networking.MachineCIDRrange, which is the IP address pool for cluster machines. The subnet CIDR blocks must belong to the machine CIDR that you specify. The VPC must have a public internet gateway attached to it. For each availability zone:
- The public subnet requires a route to the internet gateway.
- The public subnet requires a NAT gateway with an EIP address.
- The private subnet requires a route to the NAT gateway in public subnet.
The VPC must not use the
kubernetes.io/cluster/.*: ownedtag.The installation program modifies your subnets to add the
kubernetes.io/cluster/.*: sharedtag, so your subnets must have at least one free tag slot available for it. See Tag Restrictions in the AWS documentation to confirm that the installation program can add a tag to each subnet that you specify.You must enable the
enableDnsSupportandenableDnsHostnamesattributes in your VPC, so that the cluster can use the Route 53 zones that are attached to the VPC to resolve cluster’s internal DNS records. See DNS Support in Your VPC in the AWS documentation.If you prefer to use your own Route 53 hosted private zone, you must associate the existing hosted zone with your VPC prior to installing a cluster. You can define your hosted zone using the
platform.aws.hostedZonefield in theinstall-config.yamlfile.
If you are working in a disconnected environment, you are unable to reach the public IP addresses for EC2 and ELB endpoints. To resolve this, you must create a VPC endpoint and attach it to the subnet that the clusters are using. The endpoints should be named as follows:
-
ec2.<region>.amazonaws.com -
elasticloadbalancing.<region>.amazonaws.com -
s3.<region>.amazonaws.com
Required VPC components
You must provide a suitable VPC and subnets that allow communication to your machines.
| Component | AWS type | Description | |
|---|---|---|---|
| VPC |
| You must provide a public VPC for the cluster to use. The VPC uses an endpoint that references the route tables for each subnet to improve communication with the registry that is hosted in S3. | |
| Public subnets |
| Your VPC must have public subnets for between 1 and 3 availability zones and associate them with appropriate Ingress rules. | |
| Internet gateway |
| You must have a public Internet gateway, with public routes, attached to the VPC. In the provided templates, each public subnet has a NAT gateway with an EIP address. These NAT gateways allow cluster resources, like private subnet instances, to reach the Internet and are not required for some restricted network or proxy scenarios. | |
| Network access control |
| You must allow the VPC to access the following ports: | |
| Port | Reason | ||
|
| Inbound HTTP traffic | ||
|
| Inbound HTTPS traffic | ||
|
| Inbound SSH traffic | ||
|
| Inbound ephemeral traffic | ||
|
| Outbound ephemeral traffic | ||
| Private subnets |
| Your VPC can have private subnets. The provided CloudFormation templates can create private subnets for between 1 and 3 availability zones. If you use private subnets, you must provide appropriate routes and tables for them. | |
2.7.2.2. VPC validation
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the subnets that you specify exist.
- You provide private subnets.
- The subnet CIDRs belong to the machine CIDR that you specified.
- You provide subnets for each availability zone. Each availability zone contains no more than one public and one private subnet. If you use a private cluster, provide only a private subnet for each availability zone. Otherwise, provide exactly one public and private subnet for each availability zone.
- You provide a public subnet for each private subnet availability zone. Machines are not provisioned in availability zones that you do not provide private subnets for.
If you destroy a cluster that uses an existing VPC, the VPC is not deleted. When you remove the OpenShift Container Platform cluster from a VPC, the kubernetes.io/cluster/.*: shared tag is removed from the subnets that it used.
2.7.2.3. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resource in your clouds than others. For example, you might be able to create application-specific items, like instances, buckets, and load balancers, but not networking-related components such as VPCs, subnets, or ingress rules.
The AWS credentials that you use when you create your cluster do not need the networking permissions that are required to make VPCs and core networking components within the VPC, such as subnets, routing tables, Internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as ELBs, security groups, S3 buckets, and nodes.
2.7.2.4. Isolation between clusters
If you deploy OpenShift Container Platform to an existing network, the isolation of cluster services is reduced in the following ways:
- You can install multiple OpenShift Container Platform clusters in the same VPC.
- ICMP ingress is allowed from the entire network.
- TCP 22 ingress (SSH) is allowed to the entire network.
- Control plane TCP 6443 ingress (Kubernetes API) is allowed to the entire network.
- Control plane TCP 22623 ingress (MCS) is allowed to the entire network.
2.7.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.7.4. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.7.5. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.7.6. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Amazon Web Services (AWS).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select AWS as the platform to target.
- If you do not have an Amazon Web Services (AWS) profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
2.7.6.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
2.7.6.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
2.7.6.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
2.7.6.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
2.7.6.1.4. Optional AWS configuration parameters
Optional AWS configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The AWS AMI used to boot compute machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Input/Output Operations Per Second (IOPS) that is reserved for the root volume. |
Integer, for example |
|
| The size in GiB of the root volume. |
Integer, for example |
|
| The type of the root volume. |
Valid AWS EBS volume type, such as |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of worker nodes with a specific KMS key. | Valid key ID or the key ARN. |
|
| The EC2 instance type for the compute machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the compute machine pool. If you provide your own VPC, you must provide a subnet in that availability zone. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates compute resources in. |
Any valid AWS region, such as |
|
| The AWS AMI used to boot control plane machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of control plane nodes with a specific KMS key. | Valid key ID and the key ARN. |
|
| The EC2 instance type for the control plane machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the control plane machine pool. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates control plane resources in. |
Valid AWS region, such as |
|
| The AWS AMI used to boot all machines for the cluster. If set, the AMI must belong to the same region as the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The AWS service endpoint name. Custom endpoints are only required for cases where alternative AWS endpoints, like FIPS, must be used. Custom API endpoints can be specified for EC2, S3, IAM, Elastic Load Balancing, Tagging, Route 53, and STS AWS services. | Valid AWS service endpoint name. |
|
|
The AWS service endpoint URL. The URL must use the | Valid AWS service endpoint URL. |
|
| A map of keys and values that the installation program adds as tags to all resources that it creates. |
Any valid YAML map, such as key value pairs in the |
|
|
If you provide the VPC instead of allowing the installation program to create the VPC for you, specify the subnet for the cluster to use. The subnet must be part of the same | Valid subnet IDs. |
2.7.6.2. Sample customized install-config.yaml file for AWS
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 11 18
- Required. The installation program prompts you for this value.
- 2
- Optional: Add this parameter to force the Cloud Credential Operator (CCO) to use the specified mode, instead of having the CCO dynamically try to determine the capabilities of the credentials. For details about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
- 3 7
- If you do not provide these parameters and values, the installation program provides the default value.
- 4
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 5 8
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger instance types, such as
m4.2xlargeorm5.2xlarge, for your machines if you disable simultaneous multithreading. - 6 9
- To configure faster storage for etcd, especially for larger clusters, set the storage type as
io1and setiopsto2000. - 12
- If you provide your own VPC, specify subnets for each availability zone that your cluster uses.
- 13
- The ID of the AMI used to boot machines for the cluster. If set, the AMI must belong to the same region as the cluster.
- 14
- The AWS service endpoints. Custom endpoints are required when installing to an unknown AWS region. The endpoint URL must use the
httpsprotocol and the host must trust the certificate. - 15
- The ID of your existing Route 53 private hosted zone. Providing an existing hosted zone requires that you supply your own VPC and the hosted zone is already associated with the VPC prior to installing your cluster. If undefined, the installation program creates a new hosted zone.
- 16
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 17
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
2.7.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.7.7. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: Remove or disable the
AdministratorAccesspolicy from the IAM account that you used to install the cluster.NoteThe elevated permissions provided by the
AdministratorAccesspolicy are required only during installation.
2.7.8. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.7.8.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.7.8.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.7.8.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.7.9. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.7.10. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.7.11. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.7.12. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.8. Installing a private cluster on AWS
In OpenShift Container Platform version 4.6, you can install a private cluster into an existing VPC on Amazon Web Services (AWS). The installation program provisions the rest of the required infrastructure, which you can further customize. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
2.8.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
Configure an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.8.2. Private clusters
You can deploy a private OpenShift Container Platform cluster that does not expose external endpoints. Private clusters are accessible from only an internal network and are not visible to the Internet.
By default, OpenShift Container Platform is provisioned to use publicly-accessible DNS and endpoints. A private cluster sets the DNS, Ingress Controller, and API server to private when you deploy your cluster. This means that the cluster resources are only accessible from your internal network and are not visible to the internet.
To deploy a private cluster, you must use existing networking that meets your requirements. Your cluster resources might be shared between other clusters on the network.
Additionally, you must deploy a private cluster from a machine that has access the API services for the cloud you provision to, the hosts on the network that you provision, and to the internet to obtain installation media. You can use any machine that meets these access requirements and follows your company’s guidelines. For example, this machine can be a bastion host on your cloud network or a machine that has access to the network through a VPN.
2.8.2.1. Private clusters in AWS
To create a private cluster on Amazon Web Services (AWS), you must provide an existing private VPC and subnets to host the cluster. The installation program must also be able to resolve the DNS records that the cluster requires. The installation program configures the Ingress Operator and API server for access from only the private network.
The cluster still requires access to Internet to access the AWS APIs.
The following items are not required or created when you install a private cluster:
- Public subnets
- Public load balancers, which support public ingress
-
A public Route 53 zone that matches the
baseDomainfor the cluster
The installation program does use the baseDomain that you specify to create a private Route 53 zone and the required records for the cluster. The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.
2.8.2.1.1. Limitations
The ability to add public functionality to a private cluster is limited.
- You cannot make the Kubernetes API endpoints public after installation without taking additional actions, including creating public subnets in the VPC for each availability zone in use, creating a public load balancer, and configuring the control plane security groups to allow traffic from Internet on 6443 (Kubernetes API port).
-
If you use a public Service type load balancer, you must tag a public subnet in each availability zone with
kubernetes.io/cluster/<cluster-infra-id>: sharedso that AWS can use them to create public load balancers.
2.8.3. About using a custom VPC
In OpenShift Container Platform 4.6, you can deploy a cluster into existing subnets in an existing Amazon Virtual Private Cloud (VPC) in Amazon Web Services (AWS). By deploying OpenShift Container Platform into an existing AWS VPC, you might be able to avoid limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. If you cannot obtain the infrastructure creation permissions that are required to create the VPC yourself, use this installation option.
Because the installation program cannot know what other components are also in your existing subnets, it cannot choose subnet CIDRs and so forth on your behalf. You must configure networking for the subnets that you install your cluster to yourself.
2.8.3.1. Requirements for using your VPC
The installation program no longer creates the following components:
- Internet gateways
- NAT gateways
- Subnets
- Route tables
- VPCs
- VPC DHCP options
- VPC endpoints
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VPC, you must correctly configure it and its subnets for the installation program and the cluster to use. See Amazon VPC console wizard configurations and Work with VPCs and subnets in the AWS documentation for more information on creating and managing an AWS VPC.
The installation program cannot:
- Subdivide network ranges for the cluster to use.
- Set route tables for the subnets.
- Set VPC options like DHCP.
You must complete these tasks before you install the cluster. See VPC networking components and Route tables for your VPC for more information on configuring networking in an AWS VPC.
Your VPC must meet the following characteristics:
The VPC must not use the
kubernetes.io/cluster/.*: ownedtag.The installation program modifies your subnets to add the
kubernetes.io/cluster/.*: sharedtag, so your subnets must have at least one free tag slot available for it. See Tag Restrictions in the AWS documentation to confirm that the installation program can add a tag to each subnet that you specify.You must enable the
enableDnsSupportandenableDnsHostnamesattributes in your VPC, so that the cluster can use the Route 53 zones that are attached to the VPC to resolve cluster’s internal DNS records. See DNS Support in Your VPC in the AWS documentation.If you prefer to use your own Route 53 hosted private zone, you must associate the existing hosted zone with your VPC prior to installing a cluster. You can define your hosted zone using the
platform.aws.hostedZonefield in theinstall-config.yamlfile.- If you use a cluster with public access, you must create a public and a private subnet for each availability zone that your cluster uses. Each availability zone can contain no more than one public and one private subnet.
If you are working in a disconnected environment, you are unable to reach the public IP addresses for EC2 and ELB endpoints. To resolve this, you must create a VPC endpoint and attach it to the subnet that the clusters are using. The endpoints should be named as follows:
-
ec2.<region>.amazonaws.com -
elasticloadbalancing.<region>.amazonaws.com -
s3.<region>.amazonaws.com
Required VPC components
You must provide a suitable VPC and subnets that allow communication to your machines.
| Component | AWS type | Description | |
|---|---|---|---|
| VPC |
| You must provide a public VPC for the cluster to use. The VPC uses an endpoint that references the route tables for each subnet to improve communication with the registry that is hosted in S3. | |
| Public subnets |
| Your VPC must have public subnets for between 1 and 3 availability zones and associate them with appropriate Ingress rules. | |
| Internet gateway |
| You must have a public Internet gateway, with public routes, attached to the VPC. In the provided templates, each public subnet has a NAT gateway with an EIP address. These NAT gateways allow cluster resources, like private subnet instances, to reach the Internet and are not required for some restricted network or proxy scenarios. | |
| Network access control |
| You must allow the VPC to access the following ports: | |
| Port | Reason | ||
|
| Inbound HTTP traffic | ||
|
| Inbound HTTPS traffic | ||
|
| Inbound SSH traffic | ||
|
| Inbound ephemeral traffic | ||
|
| Outbound ephemeral traffic | ||
| Private subnets |
| Your VPC can have private subnets. The provided CloudFormation templates can create private subnets for between 1 and 3 availability zones. If you use private subnets, you must provide appropriate routes and tables for them. | |
2.8.3.2. VPC validation
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the subnets that you specify exist.
- You provide private subnets.
- The subnet CIDRs belong to the machine CIDR that you specified.
- You provide subnets for each availability zone. Each availability zone contains no more than one public and one private subnet. If you use a private cluster, provide only a private subnet for each availability zone. Otherwise, provide exactly one public and private subnet for each availability zone.
- You provide a public subnet for each private subnet availability zone. Machines are not provisioned in availability zones that you do not provide private subnets for.
If you destroy a cluster that uses an existing VPC, the VPC is not deleted. When you remove the OpenShift Container Platform cluster from a VPC, the kubernetes.io/cluster/.*: shared tag is removed from the subnets that it used.
2.8.3.3. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resource in your clouds than others. For example, you might be able to create application-specific items, like instances, buckets, and load balancers, but not networking-related components such as VPCs, subnets, or ingress rules.
The AWS credentials that you use when you create your cluster do not need the networking permissions that are required to make VPCs and core networking components within the VPC, such as subnets, routing tables, Internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as ELBs, security groups, S3 buckets, and nodes.
2.8.3.4. Isolation between clusters
If you deploy OpenShift Container Platform to an existing network, the isolation of cluster services is reduced in the following ways:
- You can install multiple OpenShift Container Platform clusters in the same VPC.
- ICMP ingress is allowed from the entire network.
- TCP 22 ingress (SSH) is allowed to the entire network.
- Control plane TCP 6443 ingress (Kubernetes API) is allowed to the entire network.
- Control plane TCP 22623 ingress (MCS) is allowed to the entire network.
2.8.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.8.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.8.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.8.7. Manually creating the installation configuration file
For installations of a private OpenShift Container Platform cluster that are only accessible from an internal network and are not visible to the Internet, you must manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
2.8.7.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
2.8.7.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
2.8.7.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
2.8.7.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
2.8.7.1.4. Optional AWS configuration parameters
Optional AWS configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The AWS AMI used to boot compute machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Input/Output Operations Per Second (IOPS) that is reserved for the root volume. |
Integer, for example |
|
| The size in GiB of the root volume. |
Integer, for example |
|
| The type of the root volume. |
Valid AWS EBS volume type, such as |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of worker nodes with a specific KMS key. | Valid key ID or the key ARN. |
|
| The EC2 instance type for the compute machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the compute machine pool. If you provide your own VPC, you must provide a subnet in that availability zone. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates compute resources in. |
Any valid AWS region, such as |
|
| The AWS AMI used to boot control plane machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of control plane nodes with a specific KMS key. | Valid key ID and the key ARN. |
|
| The EC2 instance type for the control plane machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the control plane machine pool. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates control plane resources in. |
Valid AWS region, such as |
|
| The AWS AMI used to boot all machines for the cluster. If set, the AMI must belong to the same region as the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The AWS service endpoint name. Custom endpoints are only required for cases where alternative AWS endpoints, like FIPS, must be used. Custom API endpoints can be specified for EC2, S3, IAM, Elastic Load Balancing, Tagging, Route 53, and STS AWS services. | Valid AWS service endpoint name. |
|
|
The AWS service endpoint URL. The URL must use the | Valid AWS service endpoint URL. |
|
| A map of keys and values that the installation program adds as tags to all resources that it creates. |
Any valid YAML map, such as key value pairs in the |
|
|
If you provide the VPC instead of allowing the installation program to create the VPC for you, specify the subnet for the cluster to use. The subnet must be part of the same | Valid subnet IDs. |
2.8.7.2. Sample customized install-config.yaml file for AWS
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 11 19
- Required. The installation program prompts you for this value.
- 2
- Optional: Add this parameter to force the Cloud Credential Operator (CCO) to use the specified mode, instead of having the CCO dynamically try to determine the capabilities of the credentials. For details about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
- 3 7
- If you do not provide these parameters and values, the installation program provides the default value.
- 4
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 5 8
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger instance types, such as
m4.2xlargeorm5.2xlarge, for your machines if you disable simultaneous multithreading. - 6 9
- To configure faster storage for etcd, especially for larger clusters, set the storage type as
io1and setiopsto2000. - 12
- If you provide your own VPC, specify subnets for each availability zone that your cluster uses.
- 13
- The ID of the AMI used to boot machines for the cluster. If set, the AMI must belong to the same region as the cluster.
- 14
- The AWS service endpoints. Custom endpoints are required when installing to an unknown AWS region. The endpoint URL must use the
httpsprotocol and the host must trust the certificate. - 15
- The ID of your existing Route 53 private hosted zone. Providing an existing hosted zone requires that you supply your own VPC and the hosted zone is already associated with the VPC prior to installing your cluster. If undefined, the installation program creates a new hosted zone.
- 16
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 17
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 18
- How to publish the user-facing endpoints of your cluster. Set
publishtoInternalto deploy a private cluster, which cannot be accessed from the Internet. The default value isExternal.
2.8.7.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.8.8. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
2.8.9. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.8.9.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.8.9.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.8.9.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.8.10. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.8.11. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.8.12. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.8.13. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.9. Installing a cluster on AWS into a government region
In OpenShift Container Platform version 4.6, you can install a cluster on Amazon Web Services (AWS) into a government region. To configure the government region, modify parameters in the install-config.yaml file before you install the cluster.
2.9.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
Configure an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.9.2. AWS government regions
OpenShift Container Platform supports deploying a cluster to AWS GovCloud (US) regions. AWS GovCloud is specifically designed for US government agencies at the federal, state, and local level, as well as contractors, educational institutions, and other US customers that must run sensitive workloads in the cloud.
These regions do not have published Red Hat Enterprise Linux CoreOS (RHCOS) Amazon Machine Images (AMI) to select, so you must upload a custom AMI that belongs to that region.
The following AWS GovCloud partitions are supported:
-
us-gov-west-1 -
us-gov-east-1
The AWS GovCloud region and custom AMI must be manually configured in the install-config.yaml file since RHCOS AMIs are not provided by Red Hat for those regions.
2.9.3. Private clusters
You can deploy a private OpenShift Container Platform cluster that does not expose external endpoints. Private clusters are accessible from only an internal network and are not visible to the Internet.
Public zones are not supported in Route 53 in AWS GovCloud. Therefore, clusters must be private if they are deployed to an AWS government region.
By default, OpenShift Container Platform is provisioned to use publicly-accessible DNS and endpoints. A private cluster sets the DNS, Ingress Controller, and API server to private when you deploy your cluster. This means that the cluster resources are only accessible from your internal network and are not visible to the internet.
To deploy a private cluster, you must use existing networking that meets your requirements. Your cluster resources might be shared between other clusters on the network.
Additionally, you must deploy a private cluster from a machine that has access the API services for the cloud you provision to, the hosts on the network that you provision, and to the internet to obtain installation media. You can use any machine that meets these access requirements and follows your company’s guidelines. For example, this machine can be a bastion host on your cloud network or a machine that has access to the network through a VPN.
2.9.3.1. Private clusters in AWS
To create a private cluster on Amazon Web Services (AWS), you must provide an existing private VPC and subnets to host the cluster. The installation program must also be able to resolve the DNS records that the cluster requires. The installation program configures the Ingress Operator and API server for access from only the private network.
The cluster still requires access to Internet to access the AWS APIs.
The following items are not required or created when you install a private cluster:
- Public subnets
- Public load balancers, which support public ingress
-
A public Route 53 zone that matches the
baseDomainfor the cluster
The installation program does use the baseDomain that you specify to create a private Route 53 zone and the required records for the cluster. The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.
2.9.3.1.1. Limitations
The ability to add public functionality to a private cluster is limited.
- You cannot make the Kubernetes API endpoints public after installation without taking additional actions, including creating public subnets in the VPC for each availability zone in use, creating a public load balancer, and configuring the control plane security groups to allow traffic from Internet on 6443 (Kubernetes API port).
-
If you use a public Service type load balancer, you must tag a public subnet in each availability zone with
kubernetes.io/cluster/<cluster-infra-id>: sharedso that AWS can use them to create public load balancers.
2.9.4. About using a custom VPC
In OpenShift Container Platform 4.6, you can deploy a cluster into existing subnets in an existing Amazon Virtual Private Cloud (VPC) in Amazon Web Services (AWS). By deploying OpenShift Container Platform into an existing AWS VPC, you might be able to avoid limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. If you cannot obtain the infrastructure creation permissions that are required to create the VPC yourself, use this installation option.
Because the installation program cannot know what other components are also in your existing subnets, it cannot choose subnet CIDRs and so forth on your behalf. You must configure networking for the subnets that you install your cluster to yourself.
2.9.4.1. Requirements for using your VPC
The installation program no longer creates the following components:
- Internet gateways
- NAT gateways
- Subnets
- Route tables
- VPCs
- VPC DHCP options
- VPC endpoints
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VPC, you must correctly configure it and its subnets for the installation program and the cluster to use. See Amazon VPC console wizard configurations and Work with VPCs and subnets in the AWS documentation for more information on creating and managing an AWS VPC.
The installation program cannot:
- Subdivide network ranges for the cluster to use.
- Set route tables for the subnets.
- Set VPC options like DHCP.
You must complete these tasks before you install the cluster. See VPC networking components and Route tables for your VPC for more information on configuring networking in an AWS VPC.
Your VPC must meet the following characteristics:
The VPC must not use the
kubernetes.io/cluster/.*: ownedtag.The installation program modifies your subnets to add the
kubernetes.io/cluster/.*: sharedtag, so your subnets must have at least one free tag slot available for it. See Tag Restrictions in the AWS documentation to confirm that the installation program can add a tag to each subnet that you specify.You must enable the
enableDnsSupportandenableDnsHostnamesattributes in your VPC, so that the cluster can use the Route 53 zones that are attached to the VPC to resolve cluster’s internal DNS records. See DNS Support in Your VPC in the AWS documentation.If you prefer to use your own Route 53 hosted private zone, you must associate the existing hosted zone with your VPC prior to installing a cluster. You can define your hosted zone using the
platform.aws.hostedZonefield in theinstall-config.yamlfile.- If you use a cluster with public access, you must create a public and a private subnet for each availability zone that your cluster uses. Each availability zone can contain no more than one public and one private subnet.
If you are working in a disconnected environment, you are unable to reach the public IP addresses for EC2 and ELB endpoints. To resolve this, you must create a VPC endpoint and attach it to the subnet that the clusters are using. The endpoints should be named as follows:
-
ec2.<region>.amazonaws.com -
elasticloadbalancing.<region>.amazonaws.com -
s3.<region>.amazonaws.com
Required VPC components
You must provide a suitable VPC and subnets that allow communication to your machines.
| Component | AWS type | Description | |
|---|---|---|---|
| VPC |
| You must provide a public VPC for the cluster to use. The VPC uses an endpoint that references the route tables for each subnet to improve communication with the registry that is hosted in S3. | |
| Public subnets |
| Your VPC must have public subnets for between 1 and 3 availability zones and associate them with appropriate Ingress rules. | |
| Internet gateway |
| You must have a public Internet gateway, with public routes, attached to the VPC. In the provided templates, each public subnet has a NAT gateway with an EIP address. These NAT gateways allow cluster resources, like private subnet instances, to reach the Internet and are not required for some restricted network or proxy scenarios. | |
| Network access control |
| You must allow the VPC to access the following ports: | |
| Port | Reason | ||
|
| Inbound HTTP traffic | ||
|
| Inbound HTTPS traffic | ||
|
| Inbound SSH traffic | ||
|
| Inbound ephemeral traffic | ||
|
| Outbound ephemeral traffic | ||
| Private subnets |
| Your VPC can have private subnets. The provided CloudFormation templates can create private subnets for between 1 and 3 availability zones. If you use private subnets, you must provide appropriate routes and tables for them. | |
2.9.4.2. VPC validation
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the subnets that you specify exist.
- You provide private subnets.
- The subnet CIDRs belong to the machine CIDR that you specified.
- You provide subnets for each availability zone. Each availability zone contains no more than one public and one private subnet. If you use a private cluster, provide only a private subnet for each availability zone. Otherwise, provide exactly one public and private subnet for each availability zone.
- You provide a public subnet for each private subnet availability zone. Machines are not provisioned in availability zones that you do not provide private subnets for.
If you destroy a cluster that uses an existing VPC, the VPC is not deleted. When you remove the OpenShift Container Platform cluster from a VPC, the kubernetes.io/cluster/.*: shared tag is removed from the subnets that it used.
2.9.4.3. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resource in your clouds than others. For example, you might be able to create application-specific items, like instances, buckets, and load balancers, but not networking-related components such as VPCs, subnets, or ingress rules.
The AWS credentials that you use when you create your cluster do not need the networking permissions that are required to make VPCs and core networking components within the VPC, such as subnets, routing tables, Internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as ELBs, security groups, S3 buckets, and nodes.
2.9.4.4. Isolation between clusters
If you deploy OpenShift Container Platform to an existing network, the isolation of cluster services is reduced in the following ways:
- You can install multiple OpenShift Container Platform clusters in the same VPC.
- ICMP ingress is allowed from the entire network.
- TCP 22 ingress (SSH) is allowed to the entire network.
- Control plane TCP 6443 ingress (Kubernetes API) is allowed to the entire network.
- Control plane TCP 22623 ingress (MCS) is allowed to the entire network.
2.9.5. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.9.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
2.9.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.9.8. Manually creating the installation configuration file
When installing OpenShift Container Platform on Amazon Web Services (AWS) into a region requiring a custom Red Hat Enterprise Linux CoreOS (RHCOS) AMI, you must manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
2.9.8.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
2.9.8.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
2.9.8.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
2.9.8.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
2.9.8.1.4. Optional AWS configuration parameters
Optional AWS configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The AWS AMI used to boot compute machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Input/Output Operations Per Second (IOPS) that is reserved for the root volume. |
Integer, for example |
|
| The size in GiB of the root volume. |
Integer, for example |
|
| The type of the root volume. |
Valid AWS EBS volume type, such as |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of worker nodes with a specific KMS key. | Valid key ID or the key ARN. |
|
| The EC2 instance type for the compute machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the compute machine pool. If you provide your own VPC, you must provide a subnet in that availability zone. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates compute resources in. |
Any valid AWS region, such as |
|
| The AWS AMI used to boot control plane machines for the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The Amazon Resource Name (key ARN) of a KMS key. This is required to encrypt OS volumes of control plane nodes with a specific KMS key. | Valid key ID and the key ARN. |
|
| The EC2 instance type for the control plane machines. |
Valid AWS instance type, such as |
|
| The availability zones where the installation program creates machines for the control plane machine pool. |
A list of valid AWS availability zones, such as |
|
| The AWS region that the installation program creates control plane resources in. |
Valid AWS region, such as |
|
| The AWS AMI used to boot all machines for the cluster. If set, the AMI must belong to the same region as the cluster. This is required for regions that require a custom RHCOS AMI. | Any published or custom RHCOS AMI that belongs to the set AWS region. |
|
| The AWS service endpoint name. Custom endpoints are only required for cases where alternative AWS endpoints, like FIPS, must be used. Custom API endpoints can be specified for EC2, S3, IAM, Elastic Load Balancing, Tagging, Route 53, and STS AWS services. | Valid AWS service endpoint name. |
|
|
The AWS service endpoint URL. The URL must use the | Valid AWS service endpoint URL. |
|
| A map of keys and values that the installation program adds as tags to all resources that it creates. |
Any valid YAML map, such as key value pairs in the |
|
|
If you provide the VPC instead of allowing the installation program to create the VPC for you, specify the subnet for the cluster to use. The subnet must be part of the same | Valid subnet IDs. |
2.9.8.2. Sample customized install-config.yaml file for AWS
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 18
- Required.
- 2
- Optional: Add this parameter to force the Cloud Credential Operator (CCO) to use the specified mode, instead of having the CCO dynamically try to determine the capabilities of the credentials. For details about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
- 3 7
- If you do not provide these parameters and values, the installation program provides the default value.
- 4
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 5 8
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger instance types, such as
m4.2xlargeorm5.2xlarge, for your machines if you disable simultaneous multithreading. - 6 9
- To configure faster storage for etcd, especially for larger clusters, set the storage type as
io1and setiopsto2000. - 11
- If you provide your own VPC, specify subnets for each availability zone that your cluster uses.
- 12
- The ID of the AMI used to boot machines for the cluster. If set, the AMI must belong to the same region as the cluster.
- 13
- The AWS service endpoints. Custom endpoints are required when installing to an unknown AWS region. The endpoint URL must use the
httpsprotocol and the host must trust the certificate. - 14
- The ID of your existing Route 53 private hosted zone. Providing an existing hosted zone requires that you supply your own VPC and the hosted zone is already associated with the VPC prior to installing your cluster. If undefined, the installation program creates a new hosted zone.
- 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 17
- How to publish the user-facing endpoints of your cluster. Set
publishtoInternalto deploy a private cluster, which cannot be accessed from the Internet. The default value isExternal. - 19
- The custom CA certificate. This is required when deploying to the AWS C2S Secret Region because the AWS API requires a custom CA trust bundle.
2.9.8.3. AWS regions without a published RHCOS AMI
You can deploy an OpenShift Container Platform cluster to Amazon Web Services (AWS) regions without native support for a Red Hat Enterprise Linux CoreOS (RHCOS) Amazon Machine Image (AMI) or the AWS software development kit (SDK). If a published AMI is not available for an AWS region, you can upload a custom AMI prior to installing the cluster. This is required if you are deploying your cluster to an AWS government region.
If you are deploying to a non-government region that does not have a published RHCOS AMI, and you do not specify a custom AMI, the installation program copies the us-east-1 AMI to the user account automatically. Then the installation program creates the control plane machines with encrypted EBS volumes using the default or user-specified Key Management Service (KMS) key. This allows the AMI to follow the same process workflow as published RHCOS AMIs.
A region without native support for an RHCOS AMI is not available to select from the terminal during cluster creation because it is not published. However, you can install to this region by configuring the custom AMI in the install-config.yaml file.
2.9.8.4. Uploading a custom RHCOS AMI in AWS
If you are deploying to a custom Amazon Web Services (AWS) region, you must upload a custom Red Hat Enterprise Linux CoreOS (RHCOS) Amazon Machine Image (AMI) that belongs to that region.
Prerequisites
- You configured an AWS account.
- You created an Amazon S3 bucket with the required IAM service role.
- You uploaded your RHCOS VMDK file to Amazon S3. The RHCOS VMDK file must be the highest version that is less than or equal to the OpenShift Container Platform version you are installing.
- You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer.
Procedure
Export your AWS profile as an environment variable:
export AWS_PROFILE=<aws_profile>
$ export AWS_PROFILE=<aws_profile>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The AWS profile name that holds your AWS credentials, like
govcloud.
Export the region to associate with your custom AMI as an environment variable:
export AWS_DEFAULT_REGION=<aws_region>
$ export AWS_DEFAULT_REGION=<aws_region>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The AWS region, like
us-gov-east-1.
Export the version of RHCOS you uploaded to Amazon S3 as an environment variable:
export RHCOS_VERSION=<version>
$ export RHCOS_VERSION=<version>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The RHCOS VMDK version, like
4.6.0.
Export the Amazon S3 bucket name as an environment variable:
export VMIMPORT_BUCKET_NAME=<s3_bucket_name>
$ export VMIMPORT_BUCKET_NAME=<s3_bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
containers.jsonfile and define your RHCOS VMDK file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Import the RHCOS disk as an Amazon EBS snapshot:
aws ec2 import-snapshot --region ${AWS_DEFAULT_REGION} \ --description "<description>" \ --disk-container "file://<file_path>/containers.json"$ aws ec2 import-snapshot --region ${AWS_DEFAULT_REGION} \ --description "<description>" \1 --disk-container "file://<file_path>/containers.json"2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check the status of the image import:
watch -n 5 aws ec2 describe-import-snapshot-tasks --region ${AWS_DEFAULT_REGION}$ watch -n 5 aws ec2 describe-import-snapshot-tasks --region ${AWS_DEFAULT_REGION}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy the
SnapshotIdto register the image.Create a custom RHCOS AMI from the RHCOS snapshot:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To learn more about these APIs, see the AWS documentation for importing snapshots and creating EBS-backed AMIs.
2.9.8.5. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.9.9. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: Remove or disable the
AdministratorAccesspolicy from the IAM account that you used to install the cluster.NoteThe elevated permissions provided by the
AdministratorAccesspolicy are required only during installation.
2.9.10. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.9.10.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.9.10.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.9.10.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.9.11. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.9.12. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.9.13. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.9.14. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.10. Installing a cluster on user-provisioned infrastructure in AWS by using CloudFormation templates
In OpenShift Container Platform version 4.6, you can install a cluster on Amazon Web Services (AWS) that uses infrastructure that you provide.
One way to create this infrastructure is to use the provided CloudFormation templates. You can modify the templates to customize your infrastructure or use the information that they contain to create AWS objects according to your company’s policies.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the cloud provider and the installation process of OpenShift Container Platform. Several CloudFormation templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods; the templates are just an example.
2.10.1. Prerequisites
- You reviewed details about the OpenShift Container Platform installation and update processes.
You configured an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use key-based, long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer (Linux, macOS, or Unix) in the AWS documentation.
If you use a firewall, you configured it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.10.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.10.3. Required AWS infrastructure components
To install OpenShift Container Platform on user-provisioned infrastructure in Amazon Web Services (AWS), you must manually create both the machines and their supporting infrastructure.
For more information about the integration testing for different platforms, see the OpenShift Container Platform 4.x Tested Integrations page.
By using the provided CloudFormation templates, you can create stacks of AWS resources that represent the following components:
- An AWS Virtual Private Cloud (VPC)
- Networking and load balancing components
- Security groups and roles
- An OpenShift Container Platform bootstrap node
- OpenShift Container Platform control plane nodes
- An OpenShift Container Platform compute node
Alternatively, you can manually create the components or you can reuse existing infrastructure that meets the cluster requirements. Review the CloudFormation templates for more details about how the components interrelate.
2.10.3.1. Cluster machines
You need AWS::EC2::Instance objects for the following machines:
- A bootstrap machine. This machine is required during installation, but you can remove it after your cluster deploys.
- Three control plane machines. The control plane machines are not governed by a machine set.
- Compute machines. You must create at least two compute machines, which are also known as worker machines, during installation. These machines are not governed by a machine set.
You can use the following instance types for the cluster machines with the provided CloudFormation templates.
If m4 instance types are not available in your region, such as with eu-west-3, use m5 types instead.
| Instance type | Bootstrap | Control plane | Compute |
|---|---|---|---|
|
| x | ||
|
| x | ||
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | ||
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | ||
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x |
You might be able to use other instance types that meet the specifications of these instance types.
2.10.3.2. Other infrastructure components
- A VPC
- DNS entries
- Load balancers (classic or network) and listeners
- A public and a private Route 53 zone
- Security groups
- IAM roles
- S3 buckets
If you are working in a disconnected environment or use a proxy, you cannot reach the public IP addresses for EC2 and ELB endpoints. To reach these endpoints, you must create a VPC endpoint and attach it to the subnet that the clusters are using. Create the following endpoints:
-
ec2.<region>.amazonaws.com -
elasticloadbalancing.<region>.amazonaws.com -
s3.<region>.amazonaws.com
Required VPC components
You must provide a suitable VPC and subnets that allow communication to your machines.
| Component | AWS type | Description | |
|---|---|---|---|
| VPC |
| You must provide a public VPC for the cluster to use. The VPC uses an endpoint that references the route tables for each subnet to improve communication with the registry that is hosted in S3. | |
| Public subnets |
| Your VPC must have public subnets for between 1 and 3 availability zones and associate them with appropriate Ingress rules. | |
| Internet gateway |
| You must have a public Internet gateway, with public routes, attached to the VPC. In the provided templates, each public subnet has a NAT gateway with an EIP address. These NAT gateways allow cluster resources, like private subnet instances, to reach the Internet and are not required for some restricted network or proxy scenarios. | |
| Network access control |
| You must allow the VPC to access the following ports: | |
| Port | Reason | ||
|
| Inbound HTTP traffic | ||
|
| Inbound HTTPS traffic | ||
|
| Inbound SSH traffic | ||
|
| Inbound ephemeral traffic | ||
|
| Outbound ephemeral traffic | ||
| Private subnets |
| Your VPC can have private subnets. The provided CloudFormation templates can create private subnets for between 1 and 3 availability zones. If you use private subnets, you must provide appropriate routes and tables for them. | |
Required DNS and load balancing components
Your DNS and load balancer configuration needs to use a public hosted zone and can use a private hosted zone similar to the one that the installation program uses if it provisions the cluster’s infrastructure. You must create a DNS entry that resolves to your load balancer. An entry for api.<cluster_name>.<domain> must point to the external load balancer, and an entry for api-int.<cluster_name>.<domain> must point to the internal load balancer.
The cluster also requires load balancers and listeners for port 6443, which are required for the Kubernetes API and its extensions, and port 22623, which are required for the Ignition config files for new machines. The targets will be the control plane nodes (also known as the master nodes). Port 6443 must be accessible to both clients external to the cluster and nodes within the cluster. Port 22623 must be accessible to nodes within the cluster.
| Component | AWS type | Description |
|---|---|---|
| DNS |
| The hosted zone for your internal DNS. |
| etcd record sets |
| The registration records for etcd for your control plane machines. |
| Public load balancer |
| The load balancer for your public subnets. |
| External API server record |
| Alias records for the external API server. |
| External listener |
| A listener on port 6443 for the external load balancer. |
| External target group |
| The target group for the external load balancer. |
| Private load balancer |
| The load balancer for your private subnets. |
| Internal API server record |
| Alias records for the internal API server. |
| Internal listener |
| A listener on port 22623 for the internal load balancer. |
| Internal target group |
| The target group for the internal load balancer. |
| Internal listener |
| A listener on port 6443 for the internal load balancer. |
| Internal target group |
| The target group for the internal load balancer. |
Security groups
The control plane and worker machines require access to the following ports:
| Group | Type | IP Protocol | Port range |
|---|---|---|---|
|
|
|
|
|
|
|
| ||
|
|
| ||
|
|
| ||
|
|
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
Control plane Ingress
The control plane machines require the following Ingress groups. Each Ingress group is a AWS::EC2::SecurityGroupIngress resource.
| Ingress group | Description | IP protocol | Port range |
|---|---|---|---|
|
| etcd |
|
|
|
| Vxlan packets |
|
|
|
| Vxlan packets |
|
|
|
| Internal cluster communication and Kubernetes proxy metrics |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes kubelet, scheduler and controller manager |
|
|
|
| Kubernetes kubelet, scheduler and controller manager |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Geneve packets |
|
|
|
| Geneve packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec ESP packets |
|
|
|
| IPsec ESP packets |
|
|
|
| Internal cluster communication |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
Worker Ingress
The worker machines require the following Ingress groups. Each Ingress group is a AWS::EC2::SecurityGroupIngress resource.
| Ingress group | Description | IP protocol | Port range |
|---|---|---|---|
|
| Vxlan packets |
|
|
|
| Vxlan packets |
|
|
|
| Internal cluster communication |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes kubelet, scheduler, and controller manager |
|
|
|
| Kubernetes kubelet, scheduler, and controller manager |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Geneve packets |
|
|
|
| Geneve packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec ESP packets |
|
|
|
| IPsec ESP packets |
|
|
|
| Internal cluster communication |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
Roles and instance profiles
You must grant the machines permissions in AWS. The provided CloudFormation templates grant the machines Allow permissions for the following AWS::IAM::Role objects and provide a AWS::IAM::InstanceProfile for each set of roles. If you do not use the templates, you can grant the machines the following broad permissions or the following individual permissions.
| Role | Effect | Action | Resource |
|---|---|---|---|
| Master |
|
|
|
|
|
|
| |
|
|
|
| |
|
|
|
| |
| Worker |
|
|
|
| Bootstrap |
|
|
|
|
|
|
| |
|
|
|
|
2.10.3.3. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
2.10.3.4. Required AWS permissions
Your IAM user must have the permission tag:GetResources in the region us-east-1 to delete the base cluster resources. As part of the AWS API requirement, the OpenShift Container Platform installation program performs various actions in this region.
When you attach the AdministratorAccess policy to the IAM user that you create in Amazon Web Services (AWS), you grant that user all of the required permissions. To deploy all components of an OpenShift Container Platform cluster, the IAM user requires the following permissions:
Example 2.13. Required EC2 permissions for installation
-
tag:TagResources -
tag:UntagResources -
ec2:AllocateAddress -
ec2:AssociateAddress -
ec2:AuthorizeSecurityGroupEgress -
ec2:AuthorizeSecurityGroupIngress -
ec2:CopyImage -
ec2:CreateNetworkInterface -
ec2:AttachNetworkInterface -
ec2:CreateSecurityGroup -
ec2:CreateTags -
ec2:CreateVolume -
ec2:DeleteSecurityGroup -
ec2:DeleteSnapshot -
ec2:DeleteTags -
ec2:DeregisterImage -
ec2:DescribeAccountAttributes -
ec2:DescribeAddresses -
ec2:DescribeAvailabilityZones -
ec2:DescribeDhcpOptions -
ec2:DescribeImages -
ec2:DescribeInstanceAttribute -
ec2:DescribeInstanceCreditSpecifications -
ec2:DescribeInstances -
ec2:DescribeInternetGateways -
ec2:DescribeKeyPairs -
ec2:DescribeNatGateways -
ec2:DescribeNetworkAcls -
ec2:DescribeNetworkInterfaces -
ec2:DescribePrefixLists -
ec2:DescribeRegions -
ec2:DescribeRouteTables -
ec2:DescribeSecurityGroups -
ec2:DescribeSubnets -
ec2:DescribeTags -
ec2:DescribeVolumes -
ec2:DescribeVpcAttribute -
ec2:DescribeVpcClassicLink -
ec2:DescribeVpcClassicLinkDnsSupport -
ec2:DescribeVpcEndpoints -
ec2:DescribeVpcs -
ec2:GetEbsDefaultKmsKeyId -
ec2:ModifyInstanceAttribute -
ec2:ModifyNetworkInterfaceAttribute -
ec2:ReleaseAddress -
ec2:RevokeSecurityGroupEgress -
ec2:RevokeSecurityGroupIngress -
ec2:RunInstances -
ec2:TerminateInstances
Example 2.14. Required permissions for creating network resources during installation
-
ec2:AssociateDhcpOptions -
ec2:AssociateRouteTable -
ec2:AttachInternetGateway -
ec2:CreateDhcpOptions -
ec2:CreateInternetGateway -
ec2:CreateNatGateway -
ec2:CreateRoute -
ec2:CreateRouteTable -
ec2:CreateSubnet -
ec2:CreateVpc -
ec2:CreateVpcEndpoint -
ec2:ModifySubnetAttribute -
ec2:ModifyVpcAttribute
If you use an existing VPC, your account does not require these permissions for creating network resources.
Example 2.15. Required Elastic Load Balancing permissions (ELB) for installation
-
elasticloadbalancing:AddTags -
elasticloadbalancing:ApplySecurityGroupsToLoadBalancer -
elasticloadbalancing:AttachLoadBalancerToSubnets -
elasticloadbalancing:ConfigureHealthCheck -
elasticloadbalancing:CreateLoadBalancer -
elasticloadbalancing:CreateLoadBalancerListeners -
elasticloadbalancing:DeleteLoadBalancer -
elasticloadbalancing:DeregisterInstancesFromLoadBalancer -
elasticloadbalancing:DescribeInstanceHealth -
elasticloadbalancing:DescribeLoadBalancerAttributes -
elasticloadbalancing:DescribeLoadBalancers -
elasticloadbalancing:DescribeTags -
elasticloadbalancing:ModifyLoadBalancerAttributes -
elasticloadbalancing:RegisterInstancesWithLoadBalancer -
elasticloadbalancing:SetLoadBalancerPoliciesOfListener
Example 2.16. Required Elastic Load Balancing permissions (ELBv2) for installation
-
elasticloadbalancing:AddTags -
elasticloadbalancing:CreateListener -
elasticloadbalancing:CreateLoadBalancer -
elasticloadbalancing:CreateTargetGroup -
elasticloadbalancing:DeleteLoadBalancer -
elasticloadbalancing:DeregisterTargets -
elasticloadbalancing:DescribeListeners -
elasticloadbalancing:DescribeLoadBalancerAttributes -
elasticloadbalancing:DescribeLoadBalancers -
elasticloadbalancing:DescribeTargetGroupAttributes -
elasticloadbalancing:DescribeTargetHealth -
elasticloadbalancing:ModifyLoadBalancerAttributes -
elasticloadbalancing:ModifyTargetGroup -
elasticloadbalancing:ModifyTargetGroupAttributes -
elasticloadbalancing:RegisterTargets
Example 2.17. Required IAM permissions for installation
-
iam:AddRoleToInstanceProfile -
iam:CreateInstanceProfile -
iam:CreateRole -
iam:DeleteInstanceProfile -
iam:DeleteRole -
iam:DeleteRolePolicy -
iam:GetInstanceProfile -
iam:GetRole -
iam:GetRolePolicy -
iam:GetUser -
iam:ListInstanceProfilesForRole -
iam:ListRoles -
iam:ListUsers -
iam:PassRole -
iam:PutRolePolicy -
iam:RemoveRoleFromInstanceProfile -
iam:SimulatePrincipalPolicy -
iam:TagRole
If you have not created an elastic load balancer (ELB) in your AWS account, the IAM user also requires the iam:CreateServiceLinkedRole permission.
Example 2.18. Required Route 53 permissions for installation
-
route53:ChangeResourceRecordSets -
route53:ChangeTagsForResource -
route53:CreateHostedZone -
route53:DeleteHostedZone -
route53:GetChange -
route53:GetHostedZone -
route53:ListHostedZones -
route53:ListHostedZonesByName -
route53:ListResourceRecordSets -
route53:ListTagsForResource -
route53:UpdateHostedZoneComment
Example 2.19. Required S3 permissions for installation
-
s3:CreateBucket -
s3:DeleteBucket -
s3:GetAccelerateConfiguration -
s3:GetBucketAcl -
s3:GetBucketCors -
s3:GetBucketLocation -
s3:GetBucketLogging -
s3:GetBucketObjectLockConfiguration -
s3:GetBucketReplication -
s3:GetBucketRequestPayment -
s3:GetBucketTagging -
s3:GetBucketVersioning -
s3:GetBucketWebsite -
s3:GetEncryptionConfiguration -
s3:GetLifecycleConfiguration -
s3:GetReplicationConfiguration -
s3:ListBucket -
s3:PutBucketAcl -
s3:PutBucketTagging -
s3:PutEncryptionConfiguration
Example 2.20. S3 permissions that cluster Operators require
-
s3:DeleteObject -
s3:GetObject -
s3:GetObjectAcl -
s3:GetObjectTagging -
s3:GetObjectVersion -
s3:PutObject -
s3:PutObjectAcl -
s3:PutObjectTagging
Example 2.21. Required permissions to delete base cluster resources
-
autoscaling:DescribeAutoScalingGroups -
ec2:DeleteNetworkInterface -
ec2:DeleteVolume -
elasticloadbalancing:DeleteTargetGroup -
elasticloadbalancing:DescribeTargetGroups -
iam:DeleteAccessKey -
iam:DeleteUser -
iam:ListAttachedRolePolicies -
iam:ListInstanceProfiles -
iam:ListRolePolicies -
iam:ListUserPolicies -
s3:DeleteObject -
s3:ListBucketVersions -
tag:GetResources
Example 2.22. Required permissions to delete network resources
-
ec2:DeleteDhcpOptions -
ec2:DeleteInternetGateway -
ec2:DeleteNatGateway -
ec2:DeleteRoute -
ec2:DeleteRouteTable -
ec2:DeleteSubnet -
ec2:DeleteVpc -
ec2:DeleteVpcEndpoints -
ec2:DetachInternetGateway -
ec2:DisassociateRouteTable -
ec2:ReplaceRouteTableAssociation
If you use an existing VPC, your account does not require these permissions to delete network resources.
Example 2.23. Additional IAM and S3 permissions that are required to create manifests
-
iam:DeleteAccessKey -
iam:DeleteUser -
iam:DeleteUserPolicy -
iam:GetUserPolicy -
iam:ListAccessKeys -
iam:PutUserPolicy -
iam:TagUser -
iam:GetUserPolicy -
iam:ListAccessKeys -
s3:PutBucketPublicAccessBlock -
s3:GetBucketPublicAccessBlock -
s3:PutLifecycleConfiguration -
s3:HeadBucket -
s3:ListBucketMultipartUploads -
s3:AbortMultipartUpload
If you are managing your cloud provider credentials with mint mode, the IAM user also requires the iam:CreateAccessKey and iam:CreateUser permissions.
Example 2.24. Optional permission for quota checks for installation
-
servicequotas:ListAWSDefaultServiceQuotas
2.10.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
2.10.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
2.10.6. Creating the installation files for AWS
To install OpenShift Container Platform on Amazon Web Services (AWS) using user-provisioned infrastructure, you must generate the files that the installation program needs to deploy your cluster and modify them so that the cluster creates only the machines that it will use. You generate and customize the install-config.yaml file, Kubernetes manifests, and Ignition config files. You also have the option to first set up a separate var partition during the preparation phases of installation.
2.10.6.1. Optional: Creating a separate /var partition
It is recommended that disk partitioning for OpenShift Container Platform be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
If you follow the steps to create a separate /var partition in this procedure, it is not necessary to create the Kubernetes manifest and Ignition config files again as described later in this section.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:openshift-install create manifests --dir $HOME/clusterconfig
$ openshift-install create manifests --dir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshift
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Confirm that the installation program created manifests in the
clusterconfig/openshiftdirectory:ls $HOME/clusterconfig/openshift/
$ ls $HOME/clusterconfig/openshift/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 MiB (Mebibytes) is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
2.10.6.2. Creating the installation configuration file
Generate and customize the installation configuration file that the installation program needs to deploy your cluster.
Prerequisites
- You obtained the OpenShift Container Platform installation program for user-provisioned infrastructure and the pull secret for your cluster.
-
You checked that you are deploying your cluster to a region with an accompanying Red Hat Enterprise Linux CoreOS (RHCOS) AMI published by Red Hat. If you are deploying to a region that requires a custom AMI, such as an AWS GovCloud region, you must create the
install-config.yamlfile manually.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select aws as the platform to target.
If you do not have an AWS profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
NoteThe AWS access key ID and secret access key are stored in
~/.aws/credentialsin the home directory of the current user on the installation host. You are prompted for the credentials by the installation program if the credentials for the exported profile are not present in the file. Any credentials that you provide to the installation program are stored in the file.- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Optional: Back up the
install-config.yamlfile.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
2.10.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.10.6.4. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow By removing these files, you prevent the cluster from automatically generating control plane machines.
Remove the Kubernetes manifest files that define the worker machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage the worker machines yourself, you do not need to initialize these machines.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
Optional: If you do not want the Ingress Operator to create DNS records on your behalf, remove the
privateZoneandpublicZonesections from the<installation_directory>/manifests/cluster-dns-02-config.ymlDNS configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you do so, you must add ingress DNS records manually in a later step.
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.10.7. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in Amazon Web Services (AWS). The infrastructure name is also used to locate the appropriate AWS resources during an OpenShift Container Platform installation. The provided CloudFormation templates contain references to this infrastructure name, so you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
2.10.8. Creating a VPC in AWS
You must create a Virtual Private Cloud (VPC) in Amazon Web Services (AWS) for your OpenShift Container Platform cluster to use. You can customize the VPC to meet your requirements, including VPN and route tables.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources that represent the VPC.
If you do not use the provided CloudFormation template to create your AWS infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
Procedure
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the template from the CloudFormation template for the VPC section of this topic and save it as a YAML file on your computer. This template describes the VPC that your cluster requires.
Launch the CloudFormation template to create a stack of AWS resources that represent the VPC:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-vpc. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-vpc/dbedae40-2fd3-11eb-820e-12a48460849f
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-vpc/dbedae40-2fd3-11eb-820e-12a48460849fCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:VpcIdThe ID of your VPC.
PublicSubnetIdsThe IDs of the new public subnets.
PrivateSubnetIdsThe IDs of the new private subnets.
2.10.8.1. CloudFormation template for the VPC
You can use the following CloudFormation template to deploy the VPC that you need for your OpenShift Container Platform cluster.
Example 2.25. CloudFormation template for the VPC
2.10.9. Creating networking and load balancing components in AWS
You must configure networking and classic or network load balancing in Amazon Web Services (AWS) that your OpenShift Container Platform cluster can use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources. The stack represents the networking and load balancing components that your OpenShift Container Platform cluster requires. The template also creates a hosted zone and subnet tags.
You can run the template multiple times within a single Virtual Private Cloud (VPC).
If you do not use the provided CloudFormation template to create your AWS infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
Procedure
Obtain the hosted zone ID for the Route 53 base domain that you specified in the
install-config.yamlfile for your cluster. You can obtain details about your hosted zone by running the following command:aws route53 list-hosted-zones-by-name --dns-name <route53_domain>
$ aws route53 list-hosted-zones-by-name --dns-name <route53_domain>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For the
<route53_domain>, specify the Route 53 base domain that you used when you generated theinstall-config.yamlfile for the cluster.
Example output
mycluster.example.com. False 100 HOSTEDZONES 65F8F38E-2268-B835-E15C-AB55336FCBFA /hostedzone/Z21IXYZABCZ2A4 mycluster.example.com. 10
mycluster.example.com. False 100 HOSTEDZONES 65F8F38E-2268-B835-E15C-AB55336FCBFA /hostedzone/Z21IXYZABCZ2A4 mycluster.example.com. 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the example output, the hosted zone ID is
Z21IXYZABCZ2A4.Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A short, representative cluster name to use for hostnames, etc.
- 2
- Specify the cluster name that you used when you generated the
install-config.yamlfile for the cluster. - 3
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 4
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 5
- The Route 53 public zone ID to register the targets with.
- 6
- Specify the Route 53 public zone ID, which as a format similar to
Z21IXYZABCZ2A4. You can obtain this value from the AWS console. - 7
- The Route 53 zone to register the targets with.
- 8
- Specify the Route 53 base domain that you used when you generated the
install-config.yamlfile for the cluster. Do not include the trailing period (.) that is displayed in the AWS console. - 9
- The public subnets that you created for your VPC.
- 10
- Specify the
PublicSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 11
- The private subnets that you created for your VPC.
- 12
- Specify the
PrivateSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 13
- The VPC that you created for the cluster.
- 14
- Specify the
VpcIdvalue from the output of the CloudFormation template for the VPC.
Copy the template from the CloudFormation template for the network and load balancers section of this topic and save it as a YAML file on your computer. This template describes the networking and load balancing objects that your cluster requires.
ImportantIf you are deploying your cluster to an AWS government region, you must update the
InternalApiServerRecordin the CloudFormation template to useCNAMErecords. Records of typeALIASare not supported for AWS government regions.Launch the CloudFormation template to create a stack of AWS resources that provide the networking and load balancing components:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 --capabilities CAPABILITY_NAMED_IAM4 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-dns. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.- 4
- You must explicitly declare the
CAPABILITY_NAMED_IAMcapability because the provided template creates someAWS::IAM::Roleresources.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-dns/cd3e5de0-2fd4-11eb-5cf0-12be5c33a183
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-dns/cd3e5de0-2fd4-11eb-5cf0-12be5c33a183Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:PrivateHostedZoneIdHosted zone ID for the private DNS.
ExternalApiLoadBalancerNameFull name of the external API load balancer.
InternalApiLoadBalancerNameFull name of the internal API load balancer.
ApiServerDnsNameFull hostname of the API server.
RegisterNlbIpTargetsLambdaLambda ARN useful to help register/deregister IP targets for these load balancers.
ExternalApiTargetGroupArnARN of external API target group.
InternalApiTargetGroupArnARN of internal API target group.
InternalServiceTargetGroupArnARN of internal service target group.
2.10.9.1. CloudFormation template for the network and load balancers
You can use the following CloudFormation template to deploy the networking objects and load balancers that you need for your OpenShift Container Platform cluster.
Example 2.26. CloudFormation template for the network and load balancers
If you are deploying your cluster to an AWS government region, you must update the InternalApiServerRecord to use CNAME records. Records of type ALIAS are not supported for AWS government regions. For example:
Type: CNAME TTL: 10 ResourceRecords: - !GetAtt IntApiElb.DNSName
Type: CNAME
TTL: 10
ResourceRecords:
- !GetAtt IntApiElb.DNSName2.10.10. Creating security group and roles in AWS
You must create security groups and roles in Amazon Web Services (AWS) for your OpenShift Container Platform cluster to use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources. The stack represents the security groups and roles that your OpenShift Container Platform cluster requires.
If you do not use the provided CloudFormation template to create your AWS infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
Procedure
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- The CIDR block for the VPC.
- 4
- Specify the CIDR block parameter that you used for the VPC that you defined in the form
x.x.x.x/16-24. - 5
- The private subnets that you created for your VPC.
- 6
- Specify the
PrivateSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 7
- The VPC that you created for the cluster.
- 8
- Specify the
VpcIdvalue from the output of the CloudFormation template for the VPC.
- Copy the template from the CloudFormation template for security objects section of this topic and save it as a YAML file on your computer. This template describes the security groups and roles that your cluster requires.
Launch the CloudFormation template to create a stack of AWS resources that represent the security groups and roles:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 --capabilities CAPABILITY_NAMED_IAM4 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-sec. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.- 4
- You must explicitly declare the
CAPABILITY_NAMED_IAMcapability because the provided template creates someAWS::IAM::RoleandAWS::IAM::InstanceProfileresources.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-sec/03bd4210-2ed7-11eb-6d7a-13fc0b61e9db
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-sec/03bd4210-2ed7-11eb-6d7a-13fc0b61e9dbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:MasterSecurityGroupIdMaster Security Group ID
WorkerSecurityGroupIdWorker Security Group ID
MasterInstanceProfileMaster IAM Instance Profile
WorkerInstanceProfileWorker IAM Instance Profile
2.10.10.1. CloudFormation template for security objects
You can use the following CloudFormation template to deploy the security objects that you need for your OpenShift Container Platform cluster.
Example 2.27. CloudFormation template for security objects
2.10.11. RHCOS AMIs for the AWS infrastructure
Red Hat provides Red Hat Enterprise Linux CoreOS (RHCOS) AMIs valid for the various Amazon Web Services (AWS) zones you can specify for your OpenShift Container Platform nodes.
You can also install to regions that do not have a RHCOS AMI published by importing your own AMI.
| AWS zone | AWS AMI |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2.10.11.1. AWS regions without a published RHCOS AMI
You can deploy an OpenShift Container Platform cluster to Amazon Web Services (AWS) regions without native support for a Red Hat Enterprise Linux CoreOS (RHCOS) Amazon Machine Image (AMI) or the AWS software development kit (SDK). If a published AMI is not available for an AWS region, you can upload a custom AMI prior to installing the cluster. This is required if you are deploying your cluster to an AWS government region.
If you are deploying to a non-government region that does not have a published RHCOS AMI, and you do not specify a custom AMI, the installation program copies the us-east-1 AMI to the user account automatically. Then the installation program creates the control plane machines with encrypted EBS volumes using the default or user-specified Key Management Service (KMS) key. This allows the AMI to follow the same process workflow as published RHCOS AMIs.
A region without native support for an RHCOS AMI is not available to select from the terminal during cluster creation because it is not published. However, you can install to this region by configuring the custom AMI in the install-config.yaml file.
2.10.11.2. Uploading a custom RHCOS AMI in AWS
If you are deploying to a custom Amazon Web Services (AWS) region, you must upload a custom Red Hat Enterprise Linux CoreOS (RHCOS) Amazon Machine Image (AMI) that belongs to that region.
Prerequisites
- You configured an AWS account.
- You created an Amazon S3 bucket with the required IAM service role.
- You uploaded your RHCOS VMDK file to Amazon S3. The RHCOS VMDK file must be the highest version that is less than or equal to the OpenShift Container Platform version you are installing.
- You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer.
Procedure
Export your AWS profile as an environment variable:
export AWS_PROFILE=<aws_profile>
$ export AWS_PROFILE=<aws_profile>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The AWS profile name that holds your AWS credentials, like
govcloud.
Export the region to associate with your custom AMI as an environment variable:
export AWS_DEFAULT_REGION=<aws_region>
$ export AWS_DEFAULT_REGION=<aws_region>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The AWS region, like
us-gov-east-1.
Export the version of RHCOS you uploaded to Amazon S3 as an environment variable:
export RHCOS_VERSION=<version>
$ export RHCOS_VERSION=<version>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The RHCOS VMDK version, like
4.6.0.
Export the Amazon S3 bucket name as an environment variable:
export VMIMPORT_BUCKET_NAME=<s3_bucket_name>
$ export VMIMPORT_BUCKET_NAME=<s3_bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
containers.jsonfile and define your RHCOS VMDK file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Import the RHCOS disk as an Amazon EBS snapshot:
aws ec2 import-snapshot --region ${AWS_DEFAULT_REGION} \ --description "<description>" \ --disk-container "file://<file_path>/containers.json"$ aws ec2 import-snapshot --region ${AWS_DEFAULT_REGION} \ --description "<description>" \1 --disk-container "file://<file_path>/containers.json"2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check the status of the image import:
watch -n 5 aws ec2 describe-import-snapshot-tasks --region ${AWS_DEFAULT_REGION}$ watch -n 5 aws ec2 describe-import-snapshot-tasks --region ${AWS_DEFAULT_REGION}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy the
SnapshotIdto register the image.Create a custom RHCOS AMI from the RHCOS snapshot:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To learn more about these APIs, see the AWS documentation for importing snapshots and creating EBS-backed AMIs.
2.10.12. Creating the bootstrap node in AWS
You must create the bootstrap node in Amazon Web Services (AWS) to use during OpenShift Container Platform cluster initialization.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources. The stack represents the bootstrap node that your OpenShift Container Platform installation requires.
If you do not use the provided CloudFormation template to create your bootstrap node, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
Procedure
Provide a location to serve the
bootstrap.ignIgnition config file to your cluster. This file is located in your installation directory. One way to do this is to create an S3 bucket in your cluster’s region and upload the Ignition config file to it.ImportantThe provided CloudFormation Template assumes that the Ignition config files for your cluster are served from an S3 bucket. If you choose to serve the files from another location, you must modify the templates.
ImportantIf you are deploying to a region that has endpoints that differ from the AWS SDK, or you are providing your own custom endpoints, you must use a presigned URL for your S3 bucket instead of the
s3://schema.NoteThe bootstrap Ignition config file does contain secrets, like X.509 keys. The following steps provide basic security for the S3 bucket. To provide additional security, you can enable an S3 bucket policy to allow only certain users, such as the OpenShift IAM user, to access objects that the bucket contains. You can avoid S3 entirely and serve your bootstrap Ignition config file from any address that the bootstrap machine can reach.
Create the bucket:
aws s3 mb s3://<cluster-name>-infra
$ aws s3 mb s3://<cluster-name>-infra1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<cluster-name>-infrais the bucket name. When creating theinstall-config.yamlfile, replace<cluster-name>with the name specified for the cluster.
Upload the
bootstrap.ignIgnition config file to the bucket:aws s3 cp <installation_directory>/bootstrap.ign s3://<cluster-name>-infra/bootstrap.ign
$ aws s3 cp <installation_directory>/bootstrap.ign s3://<cluster-name>-infra/bootstrap.ign1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify that the file uploaded:
aws s3 ls s3://<cluster-name>-infra/
$ aws s3 ls s3://<cluster-name>-infra/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
2019-04-03 16:15:16 314878 bootstrap.ign
2019-04-03 16:15:16 314878 bootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- Current Red Hat Enterprise Linux CoreOS (RHCOS) AMI to use for the bootstrap node.
- 4
- Specify a valid
AWS::EC2::Image::Idvalue. - 5
- CIDR block to allow SSH access to the bootstrap node.
- 6
- Specify a CIDR block in the format
x.x.x.x/16-24. - 7
- The public subnet that is associated with your VPC to launch the bootstrap node into.
- 8
- Specify the
PublicSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 9
- The master security group ID (for registering temporary rules)
- 10
- Specify the
MasterSecurityGroupIdvalue from the output of the CloudFormation template for the security group and roles. - 11
- The VPC created resources will belong to.
- 12
- Specify the
VpcIdvalue from the output of the CloudFormation template for the VPC. - 13
- Location to fetch bootstrap Ignition config file from.
- 14
- Specify the S3 bucket and file name in the form
s3://<bucket_name>/bootstrap.ign. - 15
- Whether or not to register a network load balancer (NLB).
- 16
- Specify
yesorno. If you specifyyes, you must provide a Lambda Amazon Resource Name (ARN) value. - 17
- The ARN for NLB IP target registration lambda group.
- 18
- Specify the
RegisterNlbIpTargetsLambdavalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 19
- The ARN for external API load balancer target group.
- 20
- Specify the
ExternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 21
- The ARN for internal API load balancer target group.
- 22
- Specify the
InternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 23
- The ARN for internal service load balancer target group.
- 24
- Specify the
InternalServiceTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region.
- Copy the template from the CloudFormation template for the bootstrap machine section of this topic and save it as a YAML file on your computer. This template describes the bootstrap machine that your cluster requires.
Launch the CloudFormation template to create a stack of AWS resources that represent the bootstrap node:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 --capabilities CAPABILITY_NAMED_IAM4 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-bootstrap. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.- 4
- You must explicitly declare the
CAPABILITY_NAMED_IAMcapability because the provided template creates someAWS::IAM::RoleandAWS::IAM::InstanceProfileresources.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-bootstrap/12944486-2add-11eb-9dee-12dace8e3a83
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-bootstrap/12944486-2add-11eb-9dee-12dace8e3a83Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:BootstrapInstanceIdThe bootstrap Instance ID.
BootstrapPublicIpThe bootstrap node public IP address.
BootstrapPrivateIpThe bootstrap node private IP address.
2.10.12.1. CloudFormation template for the bootstrap machine
You can use the following CloudFormation template to deploy the bootstrap machine that you need for your OpenShift Container Platform cluster.
Example 2.28. CloudFormation template for the bootstrap machine
2.10.13. Creating the control plane machines in AWS
You must create the control plane machines in Amazon Web Services (AWS) that your cluster will use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources that represent the control plane nodes.
The CloudFormation template creates a stack that represents three control plane nodes.
If you do not use the provided CloudFormation template to create your control plane nodes, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
- You created the bootstrap machine.
Procedure
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- CurrentRed Hat Enterprise Linux CoreOS (RHCOS) AMI to use for the control plane machines.
- 4
- Specify an
AWS::EC2::Image::Idvalue. - 5
- Whether or not to perform DNS etcd registration.
- 6
- Specify
yesorno. If you specifyyes, you must provide hosted zone information. - 7
- The Route 53 private zone ID to register the etcd targets with.
- 8
- Specify the
PrivateHostedZoneIdvalue from the output of the CloudFormation template for DNS and load balancing. - 9
- The Route 53 zone to register the targets with.
- 10
- Specify
<cluster_name>.<domain_name>where<domain_name>is the Route 53 base domain that you used when you generatedinstall-config.yamlfile for the cluster. Do not include the trailing period (.) that is displayed in the AWS console. - 11 13 15
- A subnet, preferably private, to launch the control plane machines on.
- 12 14 16
- Specify a subnet from the
PrivateSubnetsvalue from the output of the CloudFormation template for DNS and load balancing. - 17
- The master security group ID to associate with control plane nodes (also known as the master nodes).
- 18
- Specify the
MasterSecurityGroupIdvalue from the output of the CloudFormation template for the security group and roles. - 19
- The location to fetch control plane Ignition config file from.
- 20
- Specify the generated Ignition config file location,
https://api-int.<cluster_name>.<domain_name>:22623/config/master. - 21
- The base64 encoded certificate authority string to use.
- 22
- Specify the value from the
master.ignfile that is in the installation directory. This value is the long string with the formatdata:text/plain;charset=utf-8;base64,ABC…xYz==. - 23
- The IAM profile to associate with control plane nodes.
- 24
- Specify the
MasterInstanceProfileparameter value from the output of the CloudFormation template for the security group and roles. - 25
- The type of AWS instance to use for the control plane machines.
- 26
- Allowed values:
-
m4.xlarge -
m4.2xlarge -
m4.4xlarge -
m4.8xlarge -
m4.10xlarge -
m4.16xlarge -
m5.xlarge -
m5.2xlarge -
m5.4xlarge -
m5.8xlarge -
m5.10xlarge -
m5.16xlarge -
m6i.xlarge -
c4.2xlarge -
c4.4xlarge -
c4.8xlarge -
r4.xlarge -
r4.2xlarge -
r4.4xlarge -
r4.8xlarge r4.16xlargeImportantIf
m4instance types are not available in your region, such as witheu-west-3, specify anm5type, such asm5.xlarge, instead.
-
- 27
- Whether or not to register a network load balancer (NLB).
- 28
- Specify
yesorno. If you specifyyes, you must provide a Lambda Amazon Resource Name (ARN) value. - 29
- The ARN for NLB IP target registration lambda group.
- 30
- Specify the
RegisterNlbIpTargetsLambdavalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 31
- The ARN for external API load balancer target group.
- 32
- Specify the
ExternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 33
- The ARN for internal API load balancer target group.
- 34
- Specify the
InternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 35
- The ARN for internal service load balancer target group.
- 36
- Specify the
InternalServiceTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region.
- Copy the template from the CloudFormation template for control plane machines section of this topic and save it as a YAML file on your computer. This template describes the control plane machines that your cluster requires.
-
If you specified an
m5instance type as the value forMasterInstanceType, add that instance type to theMasterInstanceType.AllowedValuesparameter in the CloudFormation template. Launch the CloudFormation template to create a stack of AWS resources that represent the control plane nodes:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-control-plane. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-control-plane/21c7e2b0-2ee2-11eb-c6f6-0aa34627df4b
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-control-plane/21c7e2b0-2ee2-11eb-c6f6-0aa34627df4bCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe CloudFormation template creates a stack that represents three control plane nodes.
Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.10.13.1. CloudFormation template for control plane machines
You can use the following CloudFormation template to deploy the control plane machines that you need for your OpenShift Container Platform cluster.
Example 2.29. CloudFormation template for control plane machines
2.10.14. Creating the worker nodes in AWS
You can create worker nodes in Amazon Web Services (AWS) for your cluster to use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources that represent a worker node.
The CloudFormation template creates a stack that represents one worker node. You must create a stack for each worker node.
If you do not use the provided CloudFormation template to create your worker nodes, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
- You created the bootstrap machine.
- You created the control plane machines.
Procedure
Create a JSON file that contains the parameter values that the CloudFormation template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- Current Red Hat Enterprise Linux CoreOS (RHCOS) AMI to use for the worker nodes.
- 4
- Specify an
AWS::EC2::Image::Idvalue. - 5
- A subnet, preferably private, to launch the worker nodes on.
- 6
- Specify a subnet from the
PrivateSubnetsvalue from the output of the CloudFormation template for DNS and load balancing. - 7
- The worker security group ID to associate with worker nodes.
- 8
- Specify the
WorkerSecurityGroupIdvalue from the output of the CloudFormation template for the security group and roles. - 9
- The location to fetch bootstrap Ignition config file from.
- 10
- Specify the generated Ignition config location,
https://api-int.<cluster_name>.<domain_name>:22623/config/worker. - 11
- Base64 encoded certificate authority string to use.
- 12
- Specify the value from the
worker.ignfile that is in the installation directory. This value is the long string with the formatdata:text/plain;charset=utf-8;base64,ABC…xYz==. - 13
- The IAM profile to associate with worker nodes.
- 14
- Specify the
WorkerInstanceProfileparameter value from the output of the CloudFormation template for the security group and roles. - 15
- The type of AWS instance to use for the control plane machines.
- 16
- Allowed values:
-
m4.large -
m4.xlarge -
m4.2xlarge -
m4.4xlarge -
m4.8xlarge -
m4.10xlarge -
m4.16xlarge -
m5.large -
m5.xlarge -
m5.2xlarge -
m5.4xlarge -
m5.8xlarge -
m5.10xlarge -
m5.16xlarge -
m6i.xlarge -
c4.2xlarge -
c4.4xlarge -
c4.8xlarge -
r4.large -
r4.xlarge -
r4.2xlarge -
r4.4xlarge -
r4.8xlarge r4.16xlargeImportantIf
m4instance types are not available in your region, such as witheu-west-3, usem5types instead.
-
- Copy the template from the CloudFormation template for worker machines section of this topic and save it as a YAML file on your computer. This template describes the networking objects and load balancers that your cluster requires.
-
If you specified an
m5instance type as the value forWorkerInstanceType, add that instance type to theWorkerInstanceType.AllowedValuesparameter in the CloudFormation template. Launch the CloudFormation template to create a stack of AWS resources that represent a worker node:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml \2 --parameters file://<parameters>.json3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-worker-1. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-worker-1/729ee301-1c2a-11eb-348f-sd9888c65b59
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-worker-1/729ee301-1c2a-11eb-348f-sd9888c65b59Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe CloudFormation template creates a stack that represents one worker node.
Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Continue to create worker stacks until you have created enough worker machines for your cluster. You can create additional worker stacks by referencing the same template and parameter files and specifying a different stack name.
ImportantYou must create at least two worker machines, so you must create at least two stacks that use this CloudFormation template.
2.10.14.1. CloudFormation template for worker machines
You can use the following CloudFormation template to deploy the worker machines that you need for your OpenShift Container Platform cluster.
Example 2.30. CloudFormation template for worker machines
2.10.15. Initializing the bootstrap sequence on AWS with user-provisioned infrastructure
After you create all of the required infrastructure in Amazon Web Services (AWS), you can start the bootstrap sequence that initializes the OpenShift Container Platform control plane.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
- You created the bootstrap machine.
- You created the control plane machines.
- You created the worker nodes.
Procedure
Change to the directory that contains the installation program and start the bootstrap process that initializes the OpenShift Container Platform control plane:
./openshift-install wait-for bootstrap-complete --dir <installation_directory> \ --log-level=info$ ./openshift-install wait-for bootstrap-complete --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 20m0s for the Kubernetes API at https://api.mycluster.example.com:6443... INFO API v1.19.0+9f84db3 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources INFO Time elapsed: 1s
INFO Waiting up to 20m0s for the Kubernetes API at https://api.mycluster.example.com:6443... INFO API v1.19.0+9f84db3 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources INFO Time elapsed: 1sCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the command exits without a
FATALwarning, your OpenShift Container Platform control plane has initialized.NoteAfter the control plane initializes, it sets up the compute nodes and installs additional services in the form of Operators.
2.10.16. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
2.10.16.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.10.16.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>2.10.16.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>2.10.17. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.10.18. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
2.10.19. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
2.10.19.1. Image registry storage configuration
Amazon Web Services provides default storage, which means the Image Registry Operator is available after installation. However, if the Registry Operator cannot create an S3 bucket and automatically configure storage, you must manually configure registry storage.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
You can configure registry storage for user-provisioned infrastructure in AWS to deploy OpenShift Container Platform to hidden regions. See Configuring the registry for AWS user-provisioned infrastructure for more information.
2.10.19.1.1. Configuring registry storage for AWS with user-provisioned infrastructure
During installation, your cloud credentials are sufficient to create an Amazon S3 bucket and the Registry Operator will automatically configure storage.
If the Registry Operator cannot create an S3 bucket and automatically configure storage, you can create an S3 bucket and configure storage with the following procedure.
Prerequisites
- You have a cluster on AWS with user-provisioned infrastructure.
For Amazon S3 storage, the secret is expected to contain two keys:
-
REGISTRY_STORAGE_S3_ACCESSKEY -
REGISTRY_STORAGE_S3_SECRETKEY
-
Procedure
Use the following procedure if the Registry Operator cannot create an S3 bucket and automatically configure storage.
- Set up a Bucket Lifecycle Policy to abort incomplete multipart uploads that are one day old.
Fill in the storage configuration in
configs.imageregistry.operator.openshift.io/cluster:oc edit configs.imageregistry.operator.openshift.io/cluster
$ oc edit configs.imageregistry.operator.openshift.io/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example configuration
storage: s3: bucket: <bucket-name> region: <region-name>storage: s3: bucket: <bucket-name> region: <region-name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To secure your registry images in AWS, block public access to the S3 bucket.
2.10.19.1.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
2.10.20. Deleting the bootstrap resources
After you complete the initial Operator configuration for the cluster, remove the bootstrap resources from Amazon Web Services (AWS).
Prerequisites
- You completed the initial Operator configuration for your cluster.
Procedure
Delete the bootstrap resources. If you used the CloudFormation template, delete its stack:
Delete the stack by using the AWS CLI:
aws cloudformation delete-stack --stack-name <name>
$ aws cloudformation delete-stack --stack-name <name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name of your bootstrap stack.
- Delete the stack by using the AWS CloudFormation console.
2.10.21. Creating the Ingress DNS Records
If you removed the DNS Zone configuration, manually create DNS records that point to the Ingress load balancer. You can create either a wildcard record or specific records. While the following procedure uses A records, you can use other record types that you require, such as CNAME or alias.
Prerequisites
- You deployed an OpenShift Container Platform cluster on Amazon Web Services (AWS) that uses infrastructure that you provisioned.
-
You installed the OpenShift CLI (
oc). -
You installed the
jqpackage. - You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer (Linux, macOS, or Unix).
Procedure
Determine the routes to create.
-
To create a wildcard record, use
*.apps.<cluster_name>.<domain_name>, where<cluster_name>is your cluster name, and<domain_name>is the Route 53 base domain for your OpenShift Container Platform cluster. To create specific records, you must create a record for each route that your cluster uses, as shown in the output of the following command:
oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routes$ oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
To create a wildcard record, use
Retrieve the Ingress Operator load balancer status and note the value of the external IP address that it uses, which is shown in the
EXTERNAL-IPcolumn:oc -n openshift-ingress get service router-default
$ oc -n openshift-ingress get service router-defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.62.215 ab3...28.us-east-2.elb.amazonaws.com 80:31499/TCP,443:30693/TCP 5m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.62.215 ab3...28.us-east-2.elb.amazonaws.com 80:31499/TCP,443:30693/TCP 5mCopy to Clipboard Copied! Toggle word wrap Toggle overflow Locate the hosted zone ID for the load balancer:
aws elb describe-load-balancers | jq -r '.LoadBalancerDescriptions[] | select(.DNSName == "<external_ip>").CanonicalHostedZoneNameID'
$ aws elb describe-load-balancers | jq -r '.LoadBalancerDescriptions[] | select(.DNSName == "<external_ip>").CanonicalHostedZoneNameID'1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<external_ip>, specify the value of the external IP address of the Ingress Operator load balancer that you obtained.
Example output
Z3AADJGX6KTTL2
Z3AADJGX6KTTL2Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of this command is the load balancer hosted zone ID.
Obtain the public hosted zone ID for your cluster’s domain:
aws route53 list-hosted-zones-by-name \ --dns-name "<domain_name>" \ --query 'HostedZones[? Config.PrivateZone != `true` && Name == `<domain_name>.`].Id'$ aws route53 list-hosted-zones-by-name \ --dns-name "<domain_name>" \1 --query 'HostedZones[? Config.PrivateZone != `true` && Name == `<domain_name>.`].Id'2 --output textCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
/hostedzone/Z3URY6TWQ91KVV
/hostedzone/Z3URY6TWQ91KVVCopy to Clipboard Copied! Toggle word wrap Toggle overflow The public hosted zone ID for your domain is shown in the command output. In this example, it is
Z3URY6TWQ91KVV.Add the alias records to your private zone:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<private_hosted_zone_id>, specify the value from the output of the CloudFormation template for DNS and load balancing. - 2
- For
<cluster_domain>, specify the domain or subdomain that you use with your OpenShift Container Platform cluster. - 3
- For
<hosted_zone_id>, specify the public hosted zone ID for the load balancer that you obtained. - 4
- For
<external_ip>, specify the value of the external IP address of the Ingress Operator load balancer. Ensure that you include the trailing period (.) in this parameter value.
Add the records to your public zone:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<public_hosted_zone_id>, specify the public hosted zone for your domain. - 2
- For
<cluster_domain>, specify the domain or subdomain that you use with your OpenShift Container Platform cluster. - 3
- For
<hosted_zone_id>, specify the public hosted zone ID for the load balancer that you obtained. - 4
- For
<external_ip>, specify the value of the external IP address of the Ingress Operator load balancer. Ensure that you include the trailing period (.) in this parameter value.
2.10.22. Completing an AWS installation on user-provisioned infrastructure
After you start the OpenShift Container Platform installation on Amazon Web Service (AWS) user-provisioned infrastructure, monitor the deployment to completion.
Prerequisites
- You removed the bootstrap node for an OpenShift Container Platform cluster on user-provisioned AWS infrastructure.
-
You installed the
ocCLI.
Procedure
From the directory that contains the installation program, complete the cluster installation:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
2.10.23. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.10.24. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.10.26. Next steps
- Validating an installation.
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.11. Installing a cluster on AWS in a restricted network with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on Amazon Web Services (AWS) using infrastructure that you provide and an internal mirror of the installation release content.
While you can install an OpenShift Container Platform cluster by using mirrored installation release content, your cluster still requires Internet access to use the AWS APIs.
One way to create this infrastructure is to use the provided CloudFormation templates. You can modify the templates to customize your infrastructure or use the information that they contain to create AWS objects according to your company’s policies.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the cloud provider and the installation process of OpenShift Container Platform. Several CloudFormation templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods; the templates are just an example.
2.11.1. Prerequisites
You created a mirror registry on your mirror host and obtained the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
- You reviewed details about the OpenShift Container Platform installation and update processes.
You configured an AWS account to host the cluster.
ImportantIf you have an AWS profile stored on your computer, it must not use a temporary session token that you generated while using a multi-factor authentication device. The cluster continues to use your current AWS credentials to create AWS resources for the entire life of the cluster, so you must use key-based, long-lived credentials. To generate appropriate keys, see Managing Access Keys for IAM Users in the AWS documentation. You can supply the keys when you run the installation program.
- You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer (Linux, macOS, or Unix) in the AWS documentation.
If you use a firewall and plan to use the Telemetry service, you configured the firewall to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
2.11.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
2.11.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
2.11.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
2.11.4. Required AWS infrastructure components
To install OpenShift Container Platform on user-provisioned infrastructure in Amazon Web Services (AWS), you must manually create both the machines and their supporting infrastructure.
For more information about the integration testing for different platforms, see the OpenShift Container Platform 4.x Tested Integrations page.
By using the provided CloudFormation templates, you can create stacks of AWS resources that represent the following components:
- An AWS Virtual Private Cloud (VPC)
- Networking and load balancing components
- Security groups and roles
- An OpenShift Container Platform bootstrap node
- OpenShift Container Platform control plane nodes
- An OpenShift Container Platform compute node
Alternatively, you can manually create the components or you can reuse existing infrastructure that meets the cluster requirements. Review the CloudFormation templates for more details about how the components interrelate.
2.11.4.1. Cluster machines
You need AWS::EC2::Instance objects for the following machines:
- A bootstrap machine. This machine is required during installation, but you can remove it after your cluster deploys.
- Three control plane machines. The control plane machines are not governed by a machine set.
- Compute machines. You must create at least two compute machines, which are also known as worker machines, during installation. These machines are not governed by a machine set.
You can use the following instance types for the cluster machines with the provided CloudFormation templates.
If m4 instance types are not available in your region, such as with eu-west-3, use m5 types instead.
| Instance type | Bootstrap | Control plane | Compute |
|---|---|---|---|
|
| x | ||
|
| x | ||
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | ||
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | ||
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x | |
|
| x | x |
You might be able to use other instance types that meet the specifications of these instance types.
2.11.4.2. Other infrastructure components
- A VPC
- DNS entries
- Load balancers (classic or network) and listeners
- A public and a private Route 53 zone
- Security groups
- IAM roles
- S3 buckets
If you are working in a disconnected environment or use a proxy, you cannot reach the public IP addresses for EC2 and ELB endpoints. To reach these endpoints, you must create a VPC endpoint and attach it to the subnet that the clusters are using. Create the following endpoints:
-
ec2.<region>.amazonaws.com -
elasticloadbalancing.<region>.amazonaws.com -
s3.<region>.amazonaws.com
Required VPC components
You must provide a suitable VPC and subnets that allow communication to your machines.
| Component | AWS type | Description | |
|---|---|---|---|
| VPC |
| You must provide a public VPC for the cluster to use. The VPC uses an endpoint that references the route tables for each subnet to improve communication with the registry that is hosted in S3. | |
| Public subnets |
| Your VPC must have public subnets for between 1 and 3 availability zones and associate them with appropriate Ingress rules. | |
| Internet gateway |
| You must have a public Internet gateway, with public routes, attached to the VPC. In the provided templates, each public subnet has a NAT gateway with an EIP address. These NAT gateways allow cluster resources, like private subnet instances, to reach the Internet and are not required for some restricted network or proxy scenarios. | |
| Network access control |
| You must allow the VPC to access the following ports: | |
| Port | Reason | ||
|
| Inbound HTTP traffic | ||
|
| Inbound HTTPS traffic | ||
|
| Inbound SSH traffic | ||
|
| Inbound ephemeral traffic | ||
|
| Outbound ephemeral traffic | ||
| Private subnets |
| Your VPC can have private subnets. The provided CloudFormation templates can create private subnets for between 1 and 3 availability zones. If you use private subnets, you must provide appropriate routes and tables for them. | |
Required DNS and load balancing components
Your DNS and load balancer configuration needs to use a public hosted zone and can use a private hosted zone similar to the one that the installation program uses if it provisions the cluster’s infrastructure. You must create a DNS entry that resolves to your load balancer. An entry for api.<cluster_name>.<domain> must point to the external load balancer, and an entry for api-int.<cluster_name>.<domain> must point to the internal load balancer.
The cluster also requires load balancers and listeners for port 6443, which are required for the Kubernetes API and its extensions, and port 22623, which are required for the Ignition config files for new machines. The targets will be the control plane nodes (also known as the master nodes). Port 6443 must be accessible to both clients external to the cluster and nodes within the cluster. Port 22623 must be accessible to nodes within the cluster.
| Component | AWS type | Description |
|---|---|---|
| DNS |
| The hosted zone for your internal DNS. |
| etcd record sets |
| The registration records for etcd for your control plane machines. |
| Public load balancer |
| The load balancer for your public subnets. |
| External API server record |
| Alias records for the external API server. |
| External listener |
| A listener on port 6443 for the external load balancer. |
| External target group |
| The target group for the external load balancer. |
| Private load balancer |
| The load balancer for your private subnets. |
| Internal API server record |
| Alias records for the internal API server. |
| Internal listener |
| A listener on port 22623 for the internal load balancer. |
| Internal target group |
| The target group for the internal load balancer. |
| Internal listener |
| A listener on port 6443 for the internal load balancer. |
| Internal target group |
| The target group for the internal load balancer. |
Security groups
The control plane and worker machines require access to the following ports:
| Group | Type | IP Protocol | Port range |
|---|---|---|---|
|
|
|
|
|
|
|
| ||
|
|
| ||
|
|
| ||
|
|
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
Control plane Ingress
The control plane machines require the following Ingress groups. Each Ingress group is a AWS::EC2::SecurityGroupIngress resource.
| Ingress group | Description | IP protocol | Port range |
|---|---|---|---|
|
| etcd |
|
|
|
| Vxlan packets |
|
|
|
| Vxlan packets |
|
|
|
| Internal cluster communication and Kubernetes proxy metrics |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes kubelet, scheduler and controller manager |
|
|
|
| Kubernetes kubelet, scheduler and controller manager |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Geneve packets |
|
|
|
| Geneve packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec ESP packets |
|
|
|
| IPsec ESP packets |
|
|
|
| Internal cluster communication |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
Worker Ingress
The worker machines require the following Ingress groups. Each Ingress group is a AWS::EC2::SecurityGroupIngress resource.
| Ingress group | Description | IP protocol | Port range |
|---|---|---|---|
|
| Vxlan packets |
|
|
|
| Vxlan packets |
|
|
|
| Internal cluster communication |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes kubelet, scheduler, and controller manager |
|
|
|
| Kubernetes kubelet, scheduler, and controller manager |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Geneve packets |
|
|
|
| Geneve packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec IKE packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec NAT-T packets |
|
|
|
| IPsec ESP packets |
|
|
|
| IPsec ESP packets |
|
|
|
| Internal cluster communication |
|
|
|
| Internal cluster communication |
|
|
|
| Kubernetes Ingress services |
|
|
|
| Kubernetes Ingress services |
|
|
Roles and instance profiles
You must grant the machines permissions in AWS. The provided CloudFormation templates grant the machines Allow permissions for the following AWS::IAM::Role objects and provide a AWS::IAM::InstanceProfile for each set of roles. If you do not use the templates, you can grant the machines the following broad permissions or the following individual permissions.
| Role | Effect | Action | Resource |
|---|---|---|---|
| Master |
|
|
|
|
|
|
| |
|
|
|
| |
|
|
|
| |
| Worker |
|
|
|
| Bootstrap |
|
|
|
|
|
|
| |
|
|
|
|
2.11.4.3. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
2.11.4.4. Required AWS permissions
Your IAM user must have the permission tag:GetResources in the region us-east-1 to delete the base cluster resources. As part of the AWS API requirement, the OpenShift Container Platform installation program performs various actions in this region.
When you attach the AdministratorAccess policy to the IAM user that you create in Amazon Web Services (AWS), you grant that user all of the required permissions. To deploy all components of an OpenShift Container Platform cluster, the IAM user requires the following permissions:
Example 2.31. Required EC2 permissions for installation
-
tag:TagResources -
tag:UntagResources -
ec2:AllocateAddress -
ec2:AssociateAddress -
ec2:AuthorizeSecurityGroupEgress -
ec2:AuthorizeSecurityGroupIngress -
ec2:CopyImage -
ec2:CreateNetworkInterface -
ec2:AttachNetworkInterface -
ec2:CreateSecurityGroup -
ec2:CreateTags -
ec2:CreateVolume -
ec2:DeleteSecurityGroup -
ec2:DeleteSnapshot -
ec2:DeleteTags -
ec2:DeregisterImage -
ec2:DescribeAccountAttributes -
ec2:DescribeAddresses -
ec2:DescribeAvailabilityZones -
ec2:DescribeDhcpOptions -
ec2:DescribeImages -
ec2:DescribeInstanceAttribute -
ec2:DescribeInstanceCreditSpecifications -
ec2:DescribeInstances -
ec2:DescribeInternetGateways -
ec2:DescribeKeyPairs -
ec2:DescribeNatGateways -
ec2:DescribeNetworkAcls -
ec2:DescribeNetworkInterfaces -
ec2:DescribePrefixLists -
ec2:DescribeRegions -
ec2:DescribeRouteTables -
ec2:DescribeSecurityGroups -
ec2:DescribeSubnets -
ec2:DescribeTags -
ec2:DescribeVolumes -
ec2:DescribeVpcAttribute -
ec2:DescribeVpcClassicLink -
ec2:DescribeVpcClassicLinkDnsSupport -
ec2:DescribeVpcEndpoints -
ec2:DescribeVpcs -
ec2:GetEbsDefaultKmsKeyId -
ec2:ModifyInstanceAttribute -
ec2:ModifyNetworkInterfaceAttribute -
ec2:ReleaseAddress -
ec2:RevokeSecurityGroupEgress -
ec2:RevokeSecurityGroupIngress -
ec2:RunInstances -
ec2:TerminateInstances
Example 2.32. Required permissions for creating network resources during installation
-
ec2:AssociateDhcpOptions -
ec2:AssociateRouteTable -
ec2:AttachInternetGateway -
ec2:CreateDhcpOptions -
ec2:CreateInternetGateway -
ec2:CreateNatGateway -
ec2:CreateRoute -
ec2:CreateRouteTable -
ec2:CreateSubnet -
ec2:CreateVpc -
ec2:CreateVpcEndpoint -
ec2:ModifySubnetAttribute -
ec2:ModifyVpcAttribute
If you use an existing VPC, your account does not require these permissions for creating network resources.
Example 2.33. Required Elastic Load Balancing permissions (ELB) for installation
-
elasticloadbalancing:AddTags -
elasticloadbalancing:ApplySecurityGroupsToLoadBalancer -
elasticloadbalancing:AttachLoadBalancerToSubnets -
elasticloadbalancing:ConfigureHealthCheck -
elasticloadbalancing:CreateLoadBalancer -
elasticloadbalancing:CreateLoadBalancerListeners -
elasticloadbalancing:DeleteLoadBalancer -
elasticloadbalancing:DeregisterInstancesFromLoadBalancer -
elasticloadbalancing:DescribeInstanceHealth -
elasticloadbalancing:DescribeLoadBalancerAttributes -
elasticloadbalancing:DescribeLoadBalancers -
elasticloadbalancing:DescribeTags -
elasticloadbalancing:ModifyLoadBalancerAttributes -
elasticloadbalancing:RegisterInstancesWithLoadBalancer -
elasticloadbalancing:SetLoadBalancerPoliciesOfListener
Example 2.34. Required Elastic Load Balancing permissions (ELBv2) for installation
-
elasticloadbalancing:AddTags -
elasticloadbalancing:CreateListener -
elasticloadbalancing:CreateLoadBalancer -
elasticloadbalancing:CreateTargetGroup -
elasticloadbalancing:DeleteLoadBalancer -
elasticloadbalancing:DeregisterTargets -
elasticloadbalancing:DescribeListeners -
elasticloadbalancing:DescribeLoadBalancerAttributes -
elasticloadbalancing:DescribeLoadBalancers -
elasticloadbalancing:DescribeTargetGroupAttributes -
elasticloadbalancing:DescribeTargetHealth -
elasticloadbalancing:ModifyLoadBalancerAttributes -
elasticloadbalancing:ModifyTargetGroup -
elasticloadbalancing:ModifyTargetGroupAttributes -
elasticloadbalancing:RegisterTargets
Example 2.35. Required IAM permissions for installation
-
iam:AddRoleToInstanceProfile -
iam:CreateInstanceProfile -
iam:CreateRole -
iam:DeleteInstanceProfile -
iam:DeleteRole -
iam:DeleteRolePolicy -
iam:GetInstanceProfile -
iam:GetRole -
iam:GetRolePolicy -
iam:GetUser -
iam:ListInstanceProfilesForRole -
iam:ListRoles -
iam:ListUsers -
iam:PassRole -
iam:PutRolePolicy -
iam:RemoveRoleFromInstanceProfile -
iam:SimulatePrincipalPolicy -
iam:TagRole
If you have not created an elastic load balancer (ELB) in your AWS account, the IAM user also requires the iam:CreateServiceLinkedRole permission.
Example 2.36. Required Route 53 permissions for installation
-
route53:ChangeResourceRecordSets -
route53:ChangeTagsForResource -
route53:CreateHostedZone -
route53:DeleteHostedZone -
route53:GetChange -
route53:GetHostedZone -
route53:ListHostedZones -
route53:ListHostedZonesByName -
route53:ListResourceRecordSets -
route53:ListTagsForResource -
route53:UpdateHostedZoneComment
Example 2.37. Required S3 permissions for installation
-
s3:CreateBucket -
s3:DeleteBucket -
s3:GetAccelerateConfiguration -
s3:GetBucketAcl -
s3:GetBucketCors -
s3:GetBucketLocation -
s3:GetBucketLogging -
s3:GetBucketObjectLockConfiguration -
s3:GetBucketReplication -
s3:GetBucketRequestPayment -
s3:GetBucketTagging -
s3:GetBucketVersioning -
s3:GetBucketWebsite -
s3:GetEncryptionConfiguration -
s3:GetLifecycleConfiguration -
s3:GetReplicationConfiguration -
s3:ListBucket -
s3:PutBucketAcl -
s3:PutBucketTagging -
s3:PutEncryptionConfiguration
Example 2.38. S3 permissions that cluster Operators require
-
s3:DeleteObject -
s3:GetObject -
s3:GetObjectAcl -
s3:GetObjectTagging -
s3:GetObjectVersion -
s3:PutObject -
s3:PutObjectAcl -
s3:PutObjectTagging
Example 2.39. Required permissions to delete base cluster resources
-
autoscaling:DescribeAutoScalingGroups -
ec2:DeleteNetworkInterface -
ec2:DeleteVolume -
elasticloadbalancing:DeleteTargetGroup -
elasticloadbalancing:DescribeTargetGroups -
iam:DeleteAccessKey -
iam:DeleteUser -
iam:ListAttachedRolePolicies -
iam:ListInstanceProfiles -
iam:ListRolePolicies -
iam:ListUserPolicies -
s3:DeleteObject -
s3:ListBucketVersions -
tag:GetResources
Example 2.40. Required permissions to delete network resources
-
ec2:DeleteDhcpOptions -
ec2:DeleteInternetGateway -
ec2:DeleteNatGateway -
ec2:DeleteRoute -
ec2:DeleteRouteTable -
ec2:DeleteSubnet -
ec2:DeleteVpc -
ec2:DeleteVpcEndpoints -
ec2:DetachInternetGateway -
ec2:DisassociateRouteTable -
ec2:ReplaceRouteTableAssociation
If you use an existing VPC, your account does not require these permissions to delete network resources.
Example 2.41. Additional IAM and S3 permissions that are required to create manifests
-
iam:DeleteAccessKey -
iam:DeleteUser -
iam:DeleteUserPolicy -
iam:GetUserPolicy -
iam:ListAccessKeys -
iam:PutUserPolicy -
iam:TagUser -
iam:GetUserPolicy -
iam:ListAccessKeys -
s3:PutBucketPublicAccessBlock -
s3:GetBucketPublicAccessBlock -
s3:PutLifecycleConfiguration -
s3:HeadBucket -
s3:ListBucketMultipartUploads -
s3:AbortMultipartUpload
If you are managing your cloud provider credentials with mint mode, the IAM user also requires the iam:CreateAccessKey and iam:CreateUser permissions.
Example 2.42. Optional permission for quota checks for installation
-
servicequotas:ListAWSDefaultServiceQuotas
2.11.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
2.11.6. Creating the installation files for AWS
To install OpenShift Container Platform on Amazon Web Services (AWS) using user-provisioned infrastructure, you must generate the files that the installation program needs to deploy your cluster and modify them so that the cluster creates only the machines that it will use. You generate and customize the install-config.yaml file, Kubernetes manifests, and Ignition config files. You also have the option to first set up a separate var partition during the preparation phases of installation.
2.11.6.1. Optional: Creating a separate /var partition
It is recommended that disk partitioning for OpenShift Container Platform be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
If you follow the steps to create a separate /var partition in this procedure, it is not necessary to create the Kubernetes manifest and Ignition config files again as described later in this section.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:openshift-install create manifests --dir $HOME/clusterconfig
$ openshift-install create manifests --dir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshift
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Confirm that the installation program created manifests in the
clusterconfig/openshiftdirectory:ls $HOME/clusterconfig/openshift/
$ ls $HOME/clusterconfig/openshift/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 MiB (Mebibytes) is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
2.11.6.2. Creating the installation configuration file
Generate and customize the installation configuration file that the installation program needs to deploy your cluster.
Prerequisites
- You obtained the OpenShift Container Platform installation program for user-provisioned infrastructure and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
You checked that you are deploying your cluster to a region with an accompanying Red Hat Enterprise Linux CoreOS (RHCOS) AMI published by Red Hat. If you are deploying to a region that requires a custom AMI, such as an AWS GovCloud region, you must create the
install-config.yamlfile manually.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select aws as the platform to target.
If you do not have an AWS profile stored on your computer, enter the AWS access key ID and secret access key for the user that you configured to run the installation program.
NoteThe AWS access key ID and secret access key are stored in
~/.aws/credentialsin the home directory of the current user on the installation host. You are prompted for the credentials by the installation program if the credentials for the exported profile are not present in the file. Any credentials that you provide to the installation program are stored in the file.- Select the AWS region to deploy the cluster to.
- Select the base domain for the Route 53 service that you configured for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<local_registry>": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<local_registry>": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value. The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the image content resources:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use the
imageContentSourcessection from the output of the command to mirror the repository or the values that you used when you mirrored the content from the media that you brought into your restricted network.Optional: Set the publishing strategy to
Internal:publish: Internal
publish: InternalCopy to Clipboard Copied! Toggle word wrap Toggle overflow By setting this option, you create an internal Ingress Controller and a private load balancer.
Optional: Back up the
install-config.yamlfile.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
2.11.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).-
If your cluster is on AWS, you added the
ec2.<region>.amazonaws.com,elasticloadbalancing.<region>.amazonaws.com, ands3.<region>.amazonaws.comendpoints to your VPC endpoint. These endpoints are required to complete requests from the nodes to the AWS EC2 API. Because the proxy works on the container level, not the node level, you must route these requests to the AWS EC2 API through the AWS private network. Adding the public IP address of the EC2 API to your allowlist in your proxy server is not sufficient.
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
2.11.6.4. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program. For a restricted network installation, these files are on your mirror host.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow By removing these files, you prevent the cluster from automatically generating control plane machines.
Remove the Kubernetes manifest files that define the worker machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage the worker machines yourself, you do not need to initialize these machines.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
Optional: If you do not want the Ingress Operator to create DNS records on your behalf, remove the
privateZoneandpublicZonesections from the<installation_directory>/manifests/cluster-dns-02-config.ymlDNS configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you do so, you must add ingress DNS records manually in a later step.
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.11.7. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in Amazon Web Services (AWS). The infrastructure name is also used to locate the appropriate AWS resources during an OpenShift Container Platform installation. The provided CloudFormation templates contain references to this infrastructure name, so you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
2.11.8. Creating a VPC in AWS
You must create a Virtual Private Cloud (VPC) in Amazon Web Services (AWS) for your OpenShift Container Platform cluster to use. You can customize the VPC to meet your requirements, including VPN and route tables.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources that represent the VPC.
If you do not use the provided CloudFormation template to create your AWS infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
Procedure
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Copy the template from the CloudFormation template for the VPC section of this topic and save it as a YAML file on your computer. This template describes the VPC that your cluster requires.
Launch the CloudFormation template to create a stack of AWS resources that represent the VPC:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-vpc. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-vpc/dbedae40-2fd3-11eb-820e-12a48460849f
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-vpc/dbedae40-2fd3-11eb-820e-12a48460849fCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:VpcIdThe ID of your VPC.
PublicSubnetIdsThe IDs of the new public subnets.
PrivateSubnetIdsThe IDs of the new private subnets.
2.11.8.1. CloudFormation template for the VPC
You can use the following CloudFormation template to deploy the VPC that you need for your OpenShift Container Platform cluster.
Example 2.43. CloudFormation template for the VPC
2.11.9. Creating networking and load balancing components in AWS
You must configure networking and classic or network load balancing in Amazon Web Services (AWS) that your OpenShift Container Platform cluster can use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources. The stack represents the networking and load balancing components that your OpenShift Container Platform cluster requires. The template also creates a hosted zone and subnet tags.
You can run the template multiple times within a single Virtual Private Cloud (VPC).
If you do not use the provided CloudFormation template to create your AWS infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
Procedure
Obtain the hosted zone ID for the Route 53 base domain that you specified in the
install-config.yamlfile for your cluster. You can obtain details about your hosted zone by running the following command:aws route53 list-hosted-zones-by-name --dns-name <route53_domain>
$ aws route53 list-hosted-zones-by-name --dns-name <route53_domain>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For the
<route53_domain>, specify the Route 53 base domain that you used when you generated theinstall-config.yamlfile for the cluster.
Example output
mycluster.example.com. False 100 HOSTEDZONES 65F8F38E-2268-B835-E15C-AB55336FCBFA /hostedzone/Z21IXYZABCZ2A4 mycluster.example.com. 10
mycluster.example.com. False 100 HOSTEDZONES 65F8F38E-2268-B835-E15C-AB55336FCBFA /hostedzone/Z21IXYZABCZ2A4 mycluster.example.com. 10Copy to Clipboard Copied! Toggle word wrap Toggle overflow In the example output, the hosted zone ID is
Z21IXYZABCZ2A4.Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A short, representative cluster name to use for hostnames, etc.
- 2
- Specify the cluster name that you used when you generated the
install-config.yamlfile for the cluster. - 3
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 4
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 5
- The Route 53 public zone ID to register the targets with.
- 6
- Specify the Route 53 public zone ID, which as a format similar to
Z21IXYZABCZ2A4. You can obtain this value from the AWS console. - 7
- The Route 53 zone to register the targets with.
- 8
- Specify the Route 53 base domain that you used when you generated the
install-config.yamlfile for the cluster. Do not include the trailing period (.) that is displayed in the AWS console. - 9
- The public subnets that you created for your VPC.
- 10
- Specify the
PublicSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 11
- The private subnets that you created for your VPC.
- 12
- Specify the
PrivateSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 13
- The VPC that you created for the cluster.
- 14
- Specify the
VpcIdvalue from the output of the CloudFormation template for the VPC.
Copy the template from the CloudFormation template for the network and load balancers section of this topic and save it as a YAML file on your computer. This template describes the networking and load balancing objects that your cluster requires.
ImportantIf you are deploying your cluster to an AWS government region, you must update the
InternalApiServerRecordin the CloudFormation template to useCNAMErecords. Records of typeALIASare not supported for AWS government regions.Launch the CloudFormation template to create a stack of AWS resources that provide the networking and load balancing components:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 --capabilities CAPABILITY_NAMED_IAM4 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-dns. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.- 4
- You must explicitly declare the
CAPABILITY_NAMED_IAMcapability because the provided template creates someAWS::IAM::Roleresources.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-dns/cd3e5de0-2fd4-11eb-5cf0-12be5c33a183
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-dns/cd3e5de0-2fd4-11eb-5cf0-12be5c33a183Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:PrivateHostedZoneIdHosted zone ID for the private DNS.
ExternalApiLoadBalancerNameFull name of the external API load balancer.
InternalApiLoadBalancerNameFull name of the internal API load balancer.
ApiServerDnsNameFull hostname of the API server.
RegisterNlbIpTargetsLambdaLambda ARN useful to help register/deregister IP targets for these load balancers.
ExternalApiTargetGroupArnARN of external API target group.
InternalApiTargetGroupArnARN of internal API target group.
InternalServiceTargetGroupArnARN of internal service target group.
2.11.9.1. CloudFormation template for the network and load balancers
You can use the following CloudFormation template to deploy the networking objects and load balancers that you need for your OpenShift Container Platform cluster.
Example 2.44. CloudFormation template for the network and load balancers
If you are deploying your cluster to an AWS government region, you must update the InternalApiServerRecord to use CNAME records. Records of type ALIAS are not supported for AWS government regions. For example:
Type: CNAME TTL: 10 ResourceRecords: - !GetAtt IntApiElb.DNSName
Type: CNAME
TTL: 10
ResourceRecords:
- !GetAtt IntApiElb.DNSName2.11.10. Creating security group and roles in AWS
You must create security groups and roles in Amazon Web Services (AWS) for your OpenShift Container Platform cluster to use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources. The stack represents the security groups and roles that your OpenShift Container Platform cluster requires.
If you do not use the provided CloudFormation template to create your AWS infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
Procedure
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- The CIDR block for the VPC.
- 4
- Specify the CIDR block parameter that you used for the VPC that you defined in the form
x.x.x.x/16-24. - 5
- The private subnets that you created for your VPC.
- 6
- Specify the
PrivateSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 7
- The VPC that you created for the cluster.
- 8
- Specify the
VpcIdvalue from the output of the CloudFormation template for the VPC.
- Copy the template from the CloudFormation template for security objects section of this topic and save it as a YAML file on your computer. This template describes the security groups and roles that your cluster requires.
Launch the CloudFormation template to create a stack of AWS resources that represent the security groups and roles:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 --capabilities CAPABILITY_NAMED_IAM4 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-sec. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.- 4
- You must explicitly declare the
CAPABILITY_NAMED_IAMcapability because the provided template creates someAWS::IAM::RoleandAWS::IAM::InstanceProfileresources.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-sec/03bd4210-2ed7-11eb-6d7a-13fc0b61e9db
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-sec/03bd4210-2ed7-11eb-6d7a-13fc0b61e9dbCopy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:MasterSecurityGroupIdMaster Security Group ID
WorkerSecurityGroupIdWorker Security Group ID
MasterInstanceProfileMaster IAM Instance Profile
WorkerInstanceProfileWorker IAM Instance Profile
2.11.10.1. CloudFormation template for security objects
You can use the following CloudFormation template to deploy the security objects that you need for your OpenShift Container Platform cluster.
Example 2.45. CloudFormation template for security objects
2.11.11. RHCOS AMIs for the AWS infrastructure
Red Hat provides Red Hat Enterprise Linux CoreOS (RHCOS) AMIs valid for the various Amazon Web Services (AWS) zones you can specify for your OpenShift Container Platform nodes.
You can also install to regions that do not have a RHCOS AMI published by importing your own AMI.
| AWS zone | AWS AMI |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2.11.12. Creating the bootstrap node in AWS
You must create the bootstrap node in Amazon Web Services (AWS) to use during OpenShift Container Platform cluster initialization.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources. The stack represents the bootstrap node that your OpenShift Container Platform installation requires.
If you do not use the provided CloudFormation template to create your bootstrap node, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
Procedure
Provide a location to serve the
bootstrap.ignIgnition config file to your cluster. This file is located in your installation directory. One way to do this is to create an S3 bucket in your cluster’s region and upload the Ignition config file to it.ImportantThe provided CloudFormation Template assumes that the Ignition config files for your cluster are served from an S3 bucket. If you choose to serve the files from another location, you must modify the templates.
ImportantIf you are deploying to a region that has endpoints that differ from the AWS SDK, or you are providing your own custom endpoints, you must use a presigned URL for your S3 bucket instead of the
s3://schema.NoteThe bootstrap Ignition config file does contain secrets, like X.509 keys. The following steps provide basic security for the S3 bucket. To provide additional security, you can enable an S3 bucket policy to allow only certain users, such as the OpenShift IAM user, to access objects that the bucket contains. You can avoid S3 entirely and serve your bootstrap Ignition config file from any address that the bootstrap machine can reach.
Create the bucket:
aws s3 mb s3://<cluster-name>-infra
$ aws s3 mb s3://<cluster-name>-infra1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<cluster-name>-infrais the bucket name. When creating theinstall-config.yamlfile, replace<cluster-name>with the name specified for the cluster.
Upload the
bootstrap.ignIgnition config file to the bucket:aws s3 cp <installation_directory>/bootstrap.ign s3://<cluster-name>-infra/bootstrap.ign
$ aws s3 cp <installation_directory>/bootstrap.ign s3://<cluster-name>-infra/bootstrap.ign1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify that the file uploaded:
aws s3 ls s3://<cluster-name>-infra/
$ aws s3 ls s3://<cluster-name>-infra/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
2019-04-03 16:15:16 314878 bootstrap.ign
2019-04-03 16:15:16 314878 bootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- Current Red Hat Enterprise Linux CoreOS (RHCOS) AMI to use for the bootstrap node.
- 4
- Specify a valid
AWS::EC2::Image::Idvalue. - 5
- CIDR block to allow SSH access to the bootstrap node.
- 6
- Specify a CIDR block in the format
x.x.x.x/16-24. - 7
- The public subnet that is associated with your VPC to launch the bootstrap node into.
- 8
- Specify the
PublicSubnetIdsvalue from the output of the CloudFormation template for the VPC. - 9
- The master security group ID (for registering temporary rules)
- 10
- Specify the
MasterSecurityGroupIdvalue from the output of the CloudFormation template for the security group and roles. - 11
- The VPC created resources will belong to.
- 12
- Specify the
VpcIdvalue from the output of the CloudFormation template for the VPC. - 13
- Location to fetch bootstrap Ignition config file from.
- 14
- Specify the S3 bucket and file name in the form
s3://<bucket_name>/bootstrap.ign. - 15
- Whether or not to register a network load balancer (NLB).
- 16
- Specify
yesorno. If you specifyyes, you must provide a Lambda Amazon Resource Name (ARN) value. - 17
- The ARN for NLB IP target registration lambda group.
- 18
- Specify the
RegisterNlbIpTargetsLambdavalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 19
- The ARN for external API load balancer target group.
- 20
- Specify the
ExternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 21
- The ARN for internal API load balancer target group.
- 22
- Specify the
InternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 23
- The ARN for internal service load balancer target group.
- 24
- Specify the
InternalServiceTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region.
- Copy the template from the CloudFormation template for the bootstrap machine section of this topic and save it as a YAML file on your computer. This template describes the bootstrap machine that your cluster requires.
Launch the CloudFormation template to create a stack of AWS resources that represent the bootstrap node:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 --capabilities CAPABILITY_NAMED_IAM4 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-bootstrap. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.- 4
- You must explicitly declare the
CAPABILITY_NAMED_IAMcapability because the provided template creates someAWS::IAM::RoleandAWS::IAM::InstanceProfileresources.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-bootstrap/12944486-2add-11eb-9dee-12dace8e3a83
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-bootstrap/12944486-2add-11eb-9dee-12dace8e3a83Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow After the
StackStatusdisplaysCREATE_COMPLETE, the output displays values for the following parameters. You must provide these parameter values to the other CloudFormation templates that you run to create your cluster:BootstrapInstanceIdThe bootstrap Instance ID.
BootstrapPublicIpThe bootstrap node public IP address.
BootstrapPrivateIpThe bootstrap node private IP address.
2.11.12.1. CloudFormation template for the bootstrap machine
You can use the following CloudFormation template to deploy the bootstrap machine that you need for your OpenShift Container Platform cluster.
Example 2.46. CloudFormation template for the bootstrap machine
2.11.13. Creating the control plane machines in AWS
You must create the control plane machines in Amazon Web Services (AWS) that your cluster will use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources that represent the control plane nodes.
The CloudFormation template creates a stack that represents three control plane nodes.
If you do not use the provided CloudFormation template to create your control plane nodes, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
- You created the bootstrap machine.
Procedure
Create a JSON file that contains the parameter values that the template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- CurrentRed Hat Enterprise Linux CoreOS (RHCOS) AMI to use for the control plane machines.
- 4
- Specify an
AWS::EC2::Image::Idvalue. - 5
- Whether or not to perform DNS etcd registration.
- 6
- Specify
yesorno. If you specifyyes, you must provide hosted zone information. - 7
- The Route 53 private zone ID to register the etcd targets with.
- 8
- Specify the
PrivateHostedZoneIdvalue from the output of the CloudFormation template for DNS and load balancing. - 9
- The Route 53 zone to register the targets with.
- 10
- Specify
<cluster_name>.<domain_name>where<domain_name>is the Route 53 base domain that you used when you generatedinstall-config.yamlfile for the cluster. Do not include the trailing period (.) that is displayed in the AWS console. - 11 13 15
- A subnet, preferably private, to launch the control plane machines on.
- 12 14 16
- Specify a subnet from the
PrivateSubnetsvalue from the output of the CloudFormation template for DNS and load balancing. - 17
- The master security group ID to associate with control plane nodes (also known as the master nodes).
- 18
- Specify the
MasterSecurityGroupIdvalue from the output of the CloudFormation template for the security group and roles. - 19
- The location to fetch control plane Ignition config file from.
- 20
- Specify the generated Ignition config file location,
https://api-int.<cluster_name>.<domain_name>:22623/config/master. - 21
- The base64 encoded certificate authority string to use.
- 22
- Specify the value from the
master.ignfile that is in the installation directory. This value is the long string with the formatdata:text/plain;charset=utf-8;base64,ABC…xYz==. - 23
- The IAM profile to associate with control plane nodes.
- 24
- Specify the
MasterInstanceProfileparameter value from the output of the CloudFormation template for the security group and roles. - 25
- The type of AWS instance to use for the control plane machines.
- 26
- Allowed values:
-
m4.xlarge -
m4.2xlarge -
m4.4xlarge -
m4.8xlarge -
m4.10xlarge -
m4.16xlarge -
m5.xlarge -
m5.2xlarge -
m5.4xlarge -
m5.8xlarge -
m5.10xlarge -
m5.16xlarge -
m6i.xlarge -
c4.2xlarge -
c4.4xlarge -
c4.8xlarge -
r4.xlarge -
r4.2xlarge -
r4.4xlarge -
r4.8xlarge r4.16xlargeImportantIf
m4instance types are not available in your region, such as witheu-west-3, specify anm5type, such asm5.xlarge, instead.
-
- 27
- Whether or not to register a network load balancer (NLB).
- 28
- Specify
yesorno. If you specifyyes, you must provide a Lambda Amazon Resource Name (ARN) value. - 29
- The ARN for NLB IP target registration lambda group.
- 30
- Specify the
RegisterNlbIpTargetsLambdavalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 31
- The ARN for external API load balancer target group.
- 32
- Specify the
ExternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 33
- The ARN for internal API load balancer target group.
- 34
- Specify the
InternalApiTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region. - 35
- The ARN for internal service load balancer target group.
- 36
- Specify the
InternalServiceTargetGroupArnvalue from the output of the CloudFormation template for DNS and load balancing. Usearn:aws-us-govif deploying the cluster to an AWS GovCloud region.
- Copy the template from the CloudFormation template for control plane machines section of this topic and save it as a YAML file on your computer. This template describes the control plane machines that your cluster requires.
-
If you specified an
m5instance type as the value forMasterInstanceType, add that instance type to theMasterInstanceType.AllowedValuesparameter in the CloudFormation template. Launch the CloudFormation template to create a stack of AWS resources that represent the control plane nodes:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml2 --parameters file://<parameters>.json3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-control-plane. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-control-plane/21c7e2b0-2ee2-11eb-c6f6-0aa34627df4b
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-control-plane/21c7e2b0-2ee2-11eb-c6f6-0aa34627df4bCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe CloudFormation template creates a stack that represents three control plane nodes.
Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
2.11.13.1. CloudFormation template for control plane machines
You can use the following CloudFormation template to deploy the control plane machines that you need for your OpenShift Container Platform cluster.
Example 2.47. CloudFormation template for control plane machines
2.11.14. Creating the worker nodes in AWS
You can create worker nodes in Amazon Web Services (AWS) for your cluster to use.
You can use the provided CloudFormation template and a custom parameter file to create a stack of AWS resources that represent a worker node.
The CloudFormation template creates a stack that represents one worker node. You must create a stack for each worker node.
If you do not use the provided CloudFormation template to create your worker nodes, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
- You created the bootstrap machine.
- You created the control plane machines.
Procedure
Create a JSON file that contains the parameter values that the CloudFormation template requires:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The name for your cluster infrastructure that is encoded in your Ignition config files for the cluster.
- 2
- Specify the infrastructure name that you extracted from the Ignition config file metadata, which has the format
<cluster-name>-<random-string>. - 3
- Current Red Hat Enterprise Linux CoreOS (RHCOS) AMI to use for the worker nodes.
- 4
- Specify an
AWS::EC2::Image::Idvalue. - 5
- A subnet, preferably private, to launch the worker nodes on.
- 6
- Specify a subnet from the
PrivateSubnetsvalue from the output of the CloudFormation template for DNS and load balancing. - 7
- The worker security group ID to associate with worker nodes.
- 8
- Specify the
WorkerSecurityGroupIdvalue from the output of the CloudFormation template for the security group and roles. - 9
- The location to fetch bootstrap Ignition config file from.
- 10
- Specify the generated Ignition config location,
https://api-int.<cluster_name>.<domain_name>:22623/config/worker. - 11
- Base64 encoded certificate authority string to use.
- 12
- Specify the value from the
worker.ignfile that is in the installation directory. This value is the long string with the formatdata:text/plain;charset=utf-8;base64,ABC…xYz==. - 13
- The IAM profile to associate with worker nodes.
- 14
- Specify the
WorkerInstanceProfileparameter value from the output of the CloudFormation template for the security group and roles. - 15
- The type of AWS instance to use for the control plane machines.
- 16
- Allowed values:
-
m4.large -
m4.xlarge -
m4.2xlarge -
m4.4xlarge -
m4.8xlarge -
m4.10xlarge -
m4.16xlarge -
m5.large -
m5.xlarge -
m5.2xlarge -
m5.4xlarge -
m5.8xlarge -
m5.10xlarge -
m5.16xlarge -
m6i.xlarge -
c4.2xlarge -
c4.4xlarge -
c4.8xlarge -
r4.large -
r4.xlarge -
r4.2xlarge -
r4.4xlarge -
r4.8xlarge r4.16xlargeImportantIf
m4instance types are not available in your region, such as witheu-west-3, usem5types instead.
-
- Copy the template from the CloudFormation template for worker machines section of this topic and save it as a YAML file on your computer. This template describes the networking objects and load balancers that your cluster requires.
-
If you specified an
m5instance type as the value forWorkerInstanceType, add that instance type to theWorkerInstanceType.AllowedValuesparameter in the CloudFormation template. Launch the CloudFormation template to create a stack of AWS resources that represent a worker node:
ImportantYou must enter the command on a single line.
aws cloudformation create-stack --stack-name <name>
$ aws cloudformation create-stack --stack-name <name>1 --template-body file://<template>.yaml \2 --parameters file://<parameters>.json3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name for the CloudFormation stack, such ascluster-worker-1. You need the name of this stack if you remove the cluster.- 2
<template>is the relative path to and name of the CloudFormation template YAML file that you saved.- 3
<parameters>is the relative path to and name of the CloudFormation parameters JSON file.
Example output
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-worker-1/729ee301-1c2a-11eb-348f-sd9888c65b59
arn:aws:cloudformation:us-east-1:269333783861:stack/cluster-worker-1/729ee301-1c2a-11eb-348f-sd9888c65b59Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe CloudFormation template creates a stack that represents one worker node.
Confirm that the template components exist:
aws cloudformation describe-stacks --stack-name <name>
$ aws cloudformation describe-stacks --stack-name <name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Continue to create worker stacks until you have created enough worker machines for your cluster. You can create additional worker stacks by referencing the same template and parameter files and specifying a different stack name.
ImportantYou must create at least two worker machines, so you must create at least two stacks that use this CloudFormation template.
2.11.14.1. CloudFormation template for worker machines
You can use the following CloudFormation template to deploy the worker machines that you need for your OpenShift Container Platform cluster.
Example 2.48. CloudFormation template for worker machines
2.11.15. Initializing the bootstrap sequence on AWS with user-provisioned infrastructure
After you create all of the required infrastructure in Amazon Web Services (AWS), you can start the bootstrap sequence that initializes the OpenShift Container Platform control plane.
Prerequisites
- You configured an AWS account.
-
You added your AWS keys and region to your local AWS profile by running
aws configure. - You generated the Ignition config files for your cluster.
- You created and configured a VPC and associated subnets in AWS.
- You created and configured DNS, load balancers, and listeners in AWS.
- You created the security groups and roles required for your cluster in AWS.
- You created the bootstrap machine.
- You created the control plane machines.
- You created the worker nodes.
Procedure
Change to the directory that contains the installation program and start the bootstrap process that initializes the OpenShift Container Platform control plane:
./openshift-install wait-for bootstrap-complete --dir <installation_directory> \ --log-level=info$ ./openshift-install wait-for bootstrap-complete --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 20m0s for the Kubernetes API at https://api.mycluster.example.com:6443... INFO API v1.19.0+9f84db3 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources INFO Time elapsed: 1s
INFO Waiting up to 20m0s for the Kubernetes API at https://api.mycluster.example.com:6443... INFO API v1.19.0+9f84db3 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources INFO Time elapsed: 1sCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the command exits without a
FATALwarning, your OpenShift Container Platform control plane has initialized.NoteAfter the control plane initializes, it sets up the compute nodes and installs additional services in the form of Operators.
2.11.16. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
2.11.17. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
2.11.18. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
2.11.18.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
2.11.18.2. Image registry storage configuration
Amazon Web Services provides default storage, which means the Image Registry Operator is available after installation. However, if the Registry Operator cannot create an S3 bucket and automatically configure storage, you must manually configure registry storage.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
2.11.18.2.1. Configuring registry storage for AWS with user-provisioned infrastructure
During installation, your cloud credentials are sufficient to create an Amazon S3 bucket and the Registry Operator will automatically configure storage.
If the Registry Operator cannot create an S3 bucket and automatically configure storage, you can create an S3 bucket and configure storage with the following procedure.
Prerequisites
- You have a cluster on AWS with user-provisioned infrastructure.
For Amazon S3 storage, the secret is expected to contain two keys:
-
REGISTRY_STORAGE_S3_ACCESSKEY -
REGISTRY_STORAGE_S3_SECRETKEY
-
Procedure
Use the following procedure if the Registry Operator cannot create an S3 bucket and automatically configure storage.
- Set up a Bucket Lifecycle Policy to abort incomplete multipart uploads that are one day old.
Fill in the storage configuration in
configs.imageregistry.operator.openshift.io/cluster:oc edit configs.imageregistry.operator.openshift.io/cluster
$ oc edit configs.imageregistry.operator.openshift.io/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example configuration
storage: s3: bucket: <bucket-name> region: <region-name>storage: s3: bucket: <bucket-name> region: <region-name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To secure your registry images in AWS, block public access to the S3 bucket.
2.11.18.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
2.11.19. Deleting the bootstrap resources
After you complete the initial Operator configuration for the cluster, remove the bootstrap resources from Amazon Web Services (AWS).
Prerequisites
- You completed the initial Operator configuration for your cluster.
Procedure
Delete the bootstrap resources. If you used the CloudFormation template, delete its stack:
Delete the stack by using the AWS CLI:
aws cloudformation delete-stack --stack-name <name>
$ aws cloudformation delete-stack --stack-name <name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<name>is the name of your bootstrap stack.
- Delete the stack by using the AWS CloudFormation console.
2.11.20. Creating the Ingress DNS Records
If you removed the DNS Zone configuration, manually create DNS records that point to the Ingress load balancer. You can create either a wildcard record or specific records. While the following procedure uses A records, you can use other record types that you require, such as CNAME or alias.
Prerequisites
- You deployed an OpenShift Container Platform cluster on Amazon Web Services (AWS) that uses infrastructure that you provisioned.
-
You installed the OpenShift CLI (
oc). -
You installed the
jqpackage. - You downloaded the AWS CLI and installed it on your computer. See Install the AWS CLI Using the Bundled Installer (Linux, macOS, or Unix).
Procedure
Determine the routes to create.
-
To create a wildcard record, use
*.apps.<cluster_name>.<domain_name>, where<cluster_name>is your cluster name, and<domain_name>is the Route 53 base domain for your OpenShift Container Platform cluster. To create specific records, you must create a record for each route that your cluster uses, as shown in the output of the following command:
oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routes$ oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
To create a wildcard record, use
Retrieve the Ingress Operator load balancer status and note the value of the external IP address that it uses, which is shown in the
EXTERNAL-IPcolumn:oc -n openshift-ingress get service router-default
$ oc -n openshift-ingress get service router-defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.62.215 ab3...28.us-east-2.elb.amazonaws.com 80:31499/TCP,443:30693/TCP 5m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.62.215 ab3...28.us-east-2.elb.amazonaws.com 80:31499/TCP,443:30693/TCP 5mCopy to Clipboard Copied! Toggle word wrap Toggle overflow Locate the hosted zone ID for the load balancer:
aws elb describe-load-balancers | jq -r '.LoadBalancerDescriptions[] | select(.DNSName == "<external_ip>").CanonicalHostedZoneNameID'
$ aws elb describe-load-balancers | jq -r '.LoadBalancerDescriptions[] | select(.DNSName == "<external_ip>").CanonicalHostedZoneNameID'1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<external_ip>, specify the value of the external IP address of the Ingress Operator load balancer that you obtained.
Example output
Z3AADJGX6KTTL2
Z3AADJGX6KTTL2Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output of this command is the load balancer hosted zone ID.
Obtain the public hosted zone ID for your cluster’s domain:
aws route53 list-hosted-zones-by-name \ --dns-name "<domain_name>" \ --query 'HostedZones[? Config.PrivateZone != `true` && Name == `<domain_name>.`].Id'$ aws route53 list-hosted-zones-by-name \ --dns-name "<domain_name>" \1 --query 'HostedZones[? Config.PrivateZone != `true` && Name == `<domain_name>.`].Id'2 --output textCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
/hostedzone/Z3URY6TWQ91KVV
/hostedzone/Z3URY6TWQ91KVVCopy to Clipboard Copied! Toggle word wrap Toggle overflow The public hosted zone ID for your domain is shown in the command output. In this example, it is
Z3URY6TWQ91KVV.Add the alias records to your private zone:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<private_hosted_zone_id>, specify the value from the output of the CloudFormation template for DNS and load balancing. - 2
- For
<cluster_domain>, specify the domain or subdomain that you use with your OpenShift Container Platform cluster. - 3
- For
<hosted_zone_id>, specify the public hosted zone ID for the load balancer that you obtained. - 4
- For
<external_ip>, specify the value of the external IP address of the Ingress Operator load balancer. Ensure that you include the trailing period (.) in this parameter value.
Add the records to your public zone:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<public_hosted_zone_id>, specify the public hosted zone for your domain. - 2
- For
<cluster_domain>, specify the domain or subdomain that you use with your OpenShift Container Platform cluster. - 3
- For
<hosted_zone_id>, specify the public hosted zone ID for the load balancer that you obtained. - 4
- For
<external_ip>, specify the value of the external IP address of the Ingress Operator load balancer. Ensure that you include the trailing period (.) in this parameter value.
2.11.21. Completing an AWS installation on user-provisioned infrastructure
After you start the OpenShift Container Platform installation on Amazon Web Service (AWS) user-provisioned infrastructure, monitor the deployment to completion.
Prerequisites
- You removed the bootstrap node for an OpenShift Container Platform cluster on user-provisioned AWS infrastructure.
-
You installed the
ocCLI.
Procedure
From the directory that contains the installation program, complete the cluster installation:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
- Register your cluster on the Cluster registration page.
2.11.22. Logging in to the cluster by using the web console
The kubeadmin user exists by default after an OpenShift Container Platform installation. You can log in to your cluster as the kubeadmin user by using the OpenShift Container Platform web console.
Prerequisites
- You have access to the installation host.
- You completed a cluster installation and all cluster Operators are available.
Procedure
Obtain the password for the
kubeadminuser from thekubeadmin-passwordfile on the installation host:cat <installation_directory>/auth/kubeadmin-password
$ cat <installation_directory>/auth/kubeadmin-passwordCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the
kubeadminpassword from the<installation_directory>/.openshift_install.loglog file on the installation host.List the OpenShift Container Platform web console route:
oc get routes -n openshift-console | grep 'console-openshift'
$ oc get routes -n openshift-console | grep 'console-openshift'Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteAlternatively, you can obtain the OpenShift Container Platform route from the
<installation_directory>/.openshift_install.loglog file on the installation host.Example output
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect None
console console-openshift-console.apps.<cluster_name>.<base_domain> console https reencrypt/Redirect NoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Navigate to the route detailed in the output of the preceding command in a web browser and log in as the
kubeadminuser.
2.11.23. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
2.11.25. Next steps
- Validate an installation.
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
- If necessary, you can remove cloud provider credentials.
2.12. Uninstalling a cluster on AWS
You can remove a cluster that you deployed to Amazon Web Services (AWS).
2.12.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
Chapter 3. Installing on Azure
3.1. Configuring an Azure account
Before you can install OpenShift Container Platform, you must configure a Microsoft Azure account.
All Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
3.1.1. Azure account limits
The OpenShift Container Platform cluster uses a number of Microsoft Azure components, and the default Azure subscription and service limits, quotas, and constraints affect your ability to install OpenShift Container Platform clusters.
Default limits vary by offer category types, such as Free Trial and Pay-As-You-Go, and by series, such as Dv2, F, and G. For example, the default for Enterprise Agreement subscriptions is 350 cores.
Check the limits for your subscription type and if necessary, increase quota limits for your account before you install a default cluster on Azure.
The following table summarizes the Azure components whose limits can impact your ability to install and run OpenShift Container Platform clusters.
| Component | Number of components required by default | Default Azure limit | Description | ||||||
|---|---|---|---|---|---|---|---|---|---|
| vCPU | 40 | 20 per region | A default cluster requires 40 vCPUs, so you must increase the account limit. By default, each cluster creates the following instances:
Because the bootstrap machine uses To deploy more worker nodes, enable autoscaling, deploy large workloads, or use a different instance type, you must further increase the vCPU limit for your account to ensure that your cluster can deploy the machines that you require. By default, the installation program distributes control plane and compute machines across all availability zones within a region. To ensure high availability for your cluster, select a region with at least three availability zones. If your region contains fewer than three availability zones, the installation program places more than one control plane machine in the available zones. | ||||||
| OS Disk | 7 |
VM OS disk must be able to sustain a minimum throughput of 5000 IOPS / 200MBps. This throughput can be provided by having a minimum of 1 TiB Premium SSD (P30). In Azure, disk performance is directly dependent on SSD disk sizes, so to achieve the throughput supported by
Host caching must be set to | |||||||
| VNet | 1 | 1000 per region | Each default cluster requires one Virtual Network (VNet), which contains two subnets. | ||||||
| Network interfaces | 6 | 65,536 per region | Each default cluster requires six network interfaces. If you create more machines or your deployed workloads create load balancers, your cluster uses more network interfaces. | ||||||
| Network security groups | 2 | 5000 | Each default cluster Each cluster creates network security groups for each subnet in the VNet. The default cluster creates network security groups for the control plane and for the compute node subnets:
| ||||||
| Network load balancers | 3 | 1000 per region | Each cluster creates the following load balancers:
If your applications create more Kubernetes | ||||||
| Public IP addresses | 3 | Each of the two public load balancers uses a public IP address. The bootstrap machine also uses a public IP address so that you can SSH into the machine to troubleshoot issues during installation. The IP address for the bootstrap node is used only during installation. | |||||||
| Private IP addresses | 7 | The internal load balancer, each of the three control plane machines, and each of the three worker machines each use a private IP address. | |||||||
| Spot VM vCPUs (optional) | 0 If you configure spot VMs, your cluster must have two spot VM vCPUs for every compute node. | 20 per region | This is an optional component. To use spot VMs, you must increase the Azure default limit to at least twice the number of compute nodes in your cluster. Note Using spot VMs for control plane nodes is not recommended. |
3.1.2. Configuring a public DNS zone in Azure
To install OpenShift Container Platform, the Microsoft Azure account you use must have a dedicated public hosted DNS zone in your account. This zone must be authoritative for the domain. This service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through Azure or another source.
NoteFor more information about purchasing domains through Azure, see Buy a custom domain name for Azure App Service in the Azure documentation.
- If you are using an existing domain and registrar, migrate its DNS to Azure. See Migrate an active DNS name to Azure App Service in the Azure documentation.
Configure DNS for your domain. Follow the steps in the Tutorial: Host your domain in Azure DNS in the Azure documentation to create a public hosted zone for your domain or subdomain, extract the new authoritative name servers, and update the registrar records for the name servers that your domain uses.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.- If you use a subdomain, follow your company’s procedures to add its delegation records to the parent domain.
3.1.3. Increasing Azure account limits
To increase an account limit, file a support request on the Azure portal.
You can increase only one type of quota per support request.
Procedure
- From the Azure portal, click Help + support in the lower left corner.
Click New support request and then select the required values:
- From the Issue type list, select Service and subscription limits (quotas).
- From the Subscription list, select the subscription to modify.
- From the Quota type list, select the quota to increase. For example, select Compute-VM (cores-vCPUs) subscription limit increases to increase the number of vCPUs, which is required to install a cluster.
- Click Next: Solutions.
On the Problem Details page, provide the required information for your quota increase:
- Click Provide details and provide the required details in the Quota details window.
- In the SUPPORT METHOD and CONTACT INFO sections, provide the issue severity and your contact details.
- Click Next: Review + create and then click Create.
3.1.4. Required Azure roles
OpenShift Container Platform needs a service principal so it can manage Microsoft Azure resources. Before you can create a service principal, your Azure account subscription must have the following roles:
-
User Access Administrator -
Owner
To set roles on the Azure portal, see the Manage access to Azure resources using RBAC and the Azure portal in the Azure documentation.
3.1.5. Creating a service principal
Because OpenShift Container Platform and its installation program must create Microsoft Azure resources through Azure Resource Manager, you must create a service principal to represent it.
Prerequisites
- Install or update the Azure CLI.
-
Install the
jqpackage. - Your Azure account has the required roles for the subscription that you use.
Procedure
Log in to the Azure CLI:
az login
$ az loginCopy to Clipboard Copied! Toggle word wrap Toggle overflow Log in to Azure in the web console by using your credentials.
If your Azure account uses subscriptions, ensure that you are using the right subscription.
View the list of available accounts and record the
tenantIdvalue for the subscription you want to use for your cluster:az account list --refresh
$ az account list --refreshCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View your active account details and confirm that the
tenantIdvalue matches the subscription you want to use:az account show
$ az account showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Ensure that the value of the
tenantIdparameter is the UUID of the correct subscription.
If you are not using the right subscription, change the active subscription:
az account set -s <id>
$ az account set -s <id>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Substitute the value of the
idfor the subscription that you want to use for<id>.
If you changed the active subscription, display your account information again:
az account show
$ az account showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
Record the values of the
tenantIdandidparameters from the previous output. You need these values during OpenShift Container Platform installation. Create the service principal for your account:
az ad sp create-for-rbac --role Contributor --name <service_principal>
$ az ad sp create-for-rbac --role Contributor --name <service_principal>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<service_principal>with the name to assign to the service principal.
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Record the values of the
appIdandpasswordparameters from the previous output. You need these values during OpenShift Container Platform installation. Grant additional permissions to the service principal.
-
You must always add the
ContributorandUser Access Administratorroles to the app registration service principal so the cluster can assign credentials for its components. -
To operate the Cloud Credential Operator (CCO) in mint mode, the app registration service principal also requires the
Azure Active Directory Graph/Application.ReadWrite.OwnedByAPI permission. - To operate the CCO in passthrough mode, the app registration service principal does not require additional API permissions.
For more information about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
To assign the
User Access Administratorrole, run the following command:az role assignment create --role "User Access Administrator" \ --assignee-object-id $(az ad sp list --filter "appId eq '<appId>'" \ | jq '.[0].id' -r)$ az role assignment create --role "User Access Administrator" \ --assignee-object-id $(az ad sp list --filter "appId eq '<appId>'" \ | jq '.[0].id' -r)1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<appId>with theappIdparameter value for your service principal.
To assign the
Azure Active Directory Graphpermission, run the following command:az ad app permission add --id <appId> \ --api 00000002-0000-0000-c000-000000000000 \ --api-permissions 824c81eb-e3f8-4ee6-8f6d-de7f50d565b7=Role$ az ad app permission add --id <appId> \1 --api 00000002-0000-0000-c000-000000000000 \ --api-permissions 824c81eb-e3f8-4ee6-8f6d-de7f50d565b7=RoleCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<appId>with theappIdparameter value for your service principal.
Example output
Invoking "az ad app permission grant --id 46d33abc-b8a3-46d8-8c84-f0fd58177435 --api 00000002-0000-0000-c000-000000000000" is needed to make the change effective
Invoking "az ad app permission grant --id 46d33abc-b8a3-46d8-8c84-f0fd58177435 --api 00000002-0000-0000-c000-000000000000" is needed to make the change effectiveCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about the specific permissions that you grant with this command, see the GUID Table for Windows Azure Active Directory Permissions.
Approve the permissions request. If your account does not have the Azure Active Directory tenant administrator role, follow the guidelines for your organization to request that the tenant administrator approve your permissions request.
az ad app permission grant --id <appId> \ --api 00000002-0000-0000-c000-000000000000$ az ad app permission grant --id <appId> \1 --api 00000002-0000-0000-c000-000000000000Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<appId>with theappIdparameter value for your service principal.
-
You must always add the
3.1.6. Supported Azure regions
The installation program dynamically generates the list of available Microsoft Azure regions based on your subscription. The following Azure regions were tested and validated in OpenShift Container Platform version 4.6.1:
Supported Azure public regions
-
australiacentral(Australia Central) -
australiaeast(Australia East) -
australiasoutheast(Australia South East) -
brazilsouth(Brazil South) -
canadacentral(Canada Central) -
canadaeast(Canada East) -
centralindia(Central India) -
centralus(Central US) -
eastasia(East Asia) -
eastus(East US) -
eastus2(East US 2) -
francecentral(France Central) -
germanywestcentral(Germany West Central) -
japaneast(Japan East) -
japanwest(Japan West) -
koreacentral(Korea Central) -
koreasouth(Korea South) -
northcentralus(North Central US) -
northeurope(North Europe) -
norwayeast(Norway East) -
southafricanorth(South Africa North) -
southcentralus(South Central US) -
southeastasia(Southeast Asia) -
southindia(South India) -
switzerlandnorth(Switzerland North) -
uaenorth(UAE North) -
uksouth(UK South) -
ukwest(UK West) -
westcentralus(West Central US) -
westeurope(West Europe) -
westindia(West India) -
westus(West US) -
westus2(West US 2)
Supported Azure Government regions
Support for the following Microsoft Azure Government (MAG) regions was added in OpenShift Container Platform version 4.6:
-
usgovtexas(US Gov Texas) -
usgovvirginia(US Gov Virginia)
You can reference all available MAG regions in the Azure documentation. Other provided MAG regions are expected to work with OpenShift Container Platform, but have not been tested.
3.1.7. Next steps
- Install an OpenShift Container Platform cluster on Azure. You can install a customized cluster or quickly install a cluster with default options.
3.2. Manually creating IAM for Azure
In environments where the cloud identity and access management (IAM) APIs are not reachable, or the administrator prefers not to store an administrator-level credential secret in the cluster kube-system namespace, you can put the Cloud Credential Operator (CCO) into manual mode before you install the cluster.
3.2.1. Alternatives to storing administrator-level secrets in the kube-system project
The Cloud Credential Operator (CCO) manages cloud provider credentials as Kubernetes custom resource definitions (CRDs). You can configure the CCO to suit the security requirements of your organization by setting different values for the credentialsMode parameter in the install-config.yaml file.
If you prefer not to store an administrator-level credential secret in the cluster kube-system project, you can set the credentialsMode parameter for the CCO to Manual when installing OpenShift Container Platform and manage your cloud credentials manually.
Using manual mode allows each cluster component to have only the permissions it requires, without storing an administrator-level credential in the cluster. You can also use this mode if your environment does not have connectivity to the cloud provider public IAM endpoint. However, you must manually reconcile permissions with new release images for every upgrade. You must also manually supply credentials for every component that requests them.
3.2.2. Manually create IAM
The Cloud Credential Operator (CCO) can be put into manual mode prior to installation in environments where the cloud identity and access management (IAM) APIs are not reachable, or the administrator prefers not to store an administrator-level credential secret in the cluster kube-system namespace.
Procedure
To generate the manifests, run the following command from the directory that contains the installation program:
openshift-install create manifests --dir <installation_directory>
$ openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
Insert a config map into the manifests directory so that the Cloud Credential Operator is placed in manual mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the
admincredential secret created using your local cloud credentials. This removal prevents youradmincredential from being stored in the cluster:rm mycluster/openshift/99_cloud-creds-secret.yaml
$ rm mycluster/openshift/99_cloud-creds-secret.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the directory that contains the installation program, obtain details of the OpenShift Container Platform release image that your
openshift-installbinary is built to use:openshift-install version
$ openshift-install versionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
release image quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64
release image quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Locate all
CredentialsRequestobjects in this release image that target the cloud you are deploying on:oc adm release extract quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64 --credentials-requests --cloud=azure
$ oc adm release extract quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64 --credentials-requests --cloud=azureCopy to Clipboard Copied! Toggle word wrap Toggle overflow This displays the details for each request.
Sample
CredentialsRequestobjectCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Create YAML files for secrets in the
openshift-installmanifests directory that you generated previously. The secrets must be stored using the namespace and secret name defined in thespec.secretReffor eachcredentialsRequest. The format for the secret data varies for each cloud provider. From the directory that contains the installation program, proceed with your cluster creation:
openshift-install create cluster --dir <installation_directory>
$ openshift-install create cluster --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantBefore upgrading a cluster that uses manually maintained credentials, you must ensure that the CCO is in an upgradeable state. For details, see the Upgrading clusters with manually maintained credentials section of the installation content for your cloud provider.
3.2.3. Admin credentials root secret format
Each cloud provider uses a credentials root secret in the kube-system namespace by convention, which is then used to satisfy all credentials requests and create their respective secrets. This is done either by minting new credentials, with mint mode, or by copying the credentials root secret, with passthrough mode.
The format for the secret varies by cloud, and is also used for each CredentialsRequest secret.
Microsoft Azure secret format
On Microsoft Azure, the credentials secret format includes two properties that must contain the cluster’s infrastructure ID, generated randomly for each cluster installation. This value can be found after running create manifests:
cat .openshift_install_state.json | jq '."*installconfig.ClusterID".InfraID' -r
$ cat .openshift_install_state.json | jq '."*installconfig.ClusterID".InfraID' -rExample output
mycluster-2mpcn
mycluster-2mpcnThis value would be used in the secret data as follows:
azure_resource_prefix: mycluster-2mpcn azure_resourcegroup: mycluster-2mpcn-rg
azure_resource_prefix: mycluster-2mpcn
azure_resourcegroup: mycluster-2mpcn-rg3.2.4. Upgrading clusters with manually maintained credentials
If credentials are added in a future release, the Cloud Credential Operator (CCO) upgradable status for a cluster with manually maintained credentials changes to false. For minor release, for example, from 4.5 to 4.6, this status prevents you from upgrading until you have addressed any updated permissions. For z-stream releases, for example, from 4.5.10 to 4.5.11, the upgrade is not blocked, but the credentials must still be updated for the new release.
Use the Administrator perspective of the web console to determine if the CCO is upgradeable.
- Navigate to Administration → Cluster Settings.
- To view the CCO status details, click cloud-credential in the Cluster Operators list.
-
If the Upgradeable status in the Conditions section is False, examine the
credentialsRequestsfor the new release and update the manually maintained credentials on your cluster to match before upgrading.
In addition to creating new credentials for the release image that you are upgrading to, you must review the required permissions for existing credentials and accommodate any new permissions requirements for existing components in the new release. The CCO cannot detect these mismatches and will not set upgradable to false in this case.
The Manually creating IAM section of the installation content for your cloud provider explains how to obtain and use the credentials required for your cloud.
3.2.5. Mint mode
Mint mode is the default and recommended Cloud Credential Operator (CCO) credentials mode for OpenShift Container Platform. In this mode, the CCO uses the provided administrator-level cloud credential to run the cluster. Mint mode is supported for AWS, GCP, and Azure.
In mint mode, the admin credential is stored in the kube-system namespace and then used by the CCO to process the CredentialsRequest objects in the cluster and create users for each with specific permissions.
The benefits of mint mode include:
- Each cluster component has only the permissions it requires
- Automatic, on-going reconciliation for cloud credentials, including additional credentials or permissions that might be required for upgrades
One drawback is that mint mode requires admin credential storage in a cluster kube-system secret.
3.2.6. Next steps
Install an OpenShift Container Platform cluster:
- Installing a cluster quickly on Azure with default options on installer-provisioned infrastructure
- Install a cluster with cloud customizations on installer-provisioned infrastructure
- Install a cluster with network customizations on installer-provisioned infrastructure
3.3. Installing a cluster quickly on Azure
In OpenShift Container Platform version 4.6, you can install a cluster on Microsoft Azure that uses the default configuration options.
3.3.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster and determine the tested and validated region to deploy the cluster to.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
3.3.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.3.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
3.3.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.3.5. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Provide values at the prompts:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select azure as the platform to target.
If you do not have a Microsoft Azure profile stored on your computer, specify the following Azure parameter values for your subscription and service principal:
-
azure subscription id: The subscription ID to use for the cluster. Specify the
idvalue in your account output. -
azure tenant id: The tenant ID. Specify the
tenantIdvalue in your account output. -
azure service principal client id: The value of the
appIdparameter for the service principal. -
azure service principal client secret: The value of the
passwordparameter for the service principal.
-
azure subscription id: The subscription ID to use for the cluster. Specify the
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the Azure DNS Zone that you created for your cluster.
Enter a descriptive name for your cluster.
ImportantAll Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
3.3.6. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.3.6.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.3.6.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.3.6.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.3.7. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.3.8. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.3.9. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
3.4. Installing a cluster on Azure with customizations
In OpenShift Container Platform version 4.6, you can install a customized cluster on infrastructure that the installation program provisions on Microsoft Azure. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
3.4.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster and determine the tested and validated region to deploy the cluster to.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
3.4.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.4.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
3.4.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.4.5. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Microsoft Azure.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select azure as the platform to target.
If you do not have a Microsoft Azure profile stored on your computer, specify the following Azure parameter values for your subscription and service principal:
-
azure subscription id: The subscription ID to use for the cluster. Specify the
idvalue in your account output. -
azure tenant id: The tenant ID. Specify the
tenantIdvalue in your account output. -
azure service principal client id: The value of the
appIdparameter for the service principal. -
azure service principal client secret: The value of the
passwordparameter for the service principal.
-
azure subscription id: The subscription ID to use for the cluster. Specify the
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the Azure DNS Zone that you created for your cluster.
Enter a descriptive name for your cluster.
ImportantAll Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
3.4.5.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
3.4.5.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
3.4.5.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
3.4.5.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
3.4.5.1.4. Additional Azure configuration parameters
Additional Azure configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The name of the resource group that contains the DNS zone for your base domain. |
String, for example |
|
| The outbound routing strategy used to connect your cluster to the internet. If you are using user-defined routing, you must have pre-existing networking available where the outbound routing has already been configured prior to installing a cluster. The installation program is not responsible for configuring user-defined routing. |
|
|
| The name of the Azure region that hosts your cluster. |
Any valid region name, such as |
|
| List of availability zones to place machines in. For high availability, specify at least two zones. |
List of zones, for example |
|
|
The name of the resource group that contains the existing VNet that you want to deploy your cluster to. This name cannot be the same as the | String. |
|
| The name of the existing VNet that you want to deploy your cluster to. | String. |
|
| The name of the existing subnet in your VNet that you want to deploy your control plane machines to. |
Valid CIDR, for example |
|
| The name of the existing subnet in your VNet that you want to deploy your compute machines to. |
Valid CIDR, for example |
|
|
The name of the Azure cloud environment that is used to configure the Azure SDK with the appropriate Azure API endpoints. If empty, the default value |
Any valid cloud environment, such as |
You cannot customize Azure Availability Zones or Use tags to organize your Azure resources with an Azure cluster.
3.4.5.2. Sample customized install-config.yaml file for Azure
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 12 14
- Required. The installation program prompts you for this value.
- 2 6
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 7
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger virtual machine types, such as
Standard_D8s_v3, for your machines if you disable simultaneous multithreading. - 5 8
- You can specify the size of the disk to use in GB. Minimum recommendation for control plane nodes (also known as the master nodes) is 1024 GB.
- 9
- Specify a list of zones to deploy your machines to. For high availability, specify at least two zones.
- 11
- Specify the name of the resource group that contains the DNS zone for your base domain.
- 13
- Specify the name of an already existing resource group to install your cluster to. If undefined, a new resource group is created for the cluster.
- 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
3.4.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
3.4.6. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
3.4.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.4.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.4.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.4.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.4.8. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.4.9. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.4.10. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
3.5. Installing a cluster on Azure with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster with a customized network configuration on infrastructure that the installation program provisions on Microsoft Azure. By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing MTU and VXLAN configurations.
You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
3.5.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster and determine the tested and validated region to deploy the cluster to.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
3.5.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.5.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
3.5.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.5.5. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Microsoft Azure.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select azure as the platform to target.
If you do not have a Microsoft Azure profile stored on your computer, specify the following Azure parameter values for your subscription and service principal:
-
azure subscription id: The subscription ID to use for the cluster. Specify the
idvalue in your account output. -
azure tenant id: The tenant ID. Specify the
tenantIdvalue in your account output. -
azure service principal client id: The value of the
appIdparameter for the service principal. -
azure service principal client secret: The value of the
passwordparameter for the service principal.
-
azure subscription id: The subscription ID to use for the cluster. Specify the
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the Azure DNS Zone that you created for your cluster.
Enter a descriptive name for your cluster.
ImportantAll Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
3.5.5.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
3.5.5.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
3.5.5.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
3.5.5.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
3.5.5.1.4. Additional Azure configuration parameters
Additional Azure configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The name of the resource group that contains the DNS zone for your base domain. |
String, for example |
|
| The outbound routing strategy used to connect your cluster to the internet. If you are using user-defined routing, you must have pre-existing networking available where the outbound routing has already been configured prior to installing a cluster. The installation program is not responsible for configuring user-defined routing. |
|
|
| The name of the Azure region that hosts your cluster. |
Any valid region name, such as |
|
| List of availability zones to place machines in. For high availability, specify at least two zones. |
List of zones, for example |
|
|
The name of the resource group that contains the existing VNet that you want to deploy your cluster to. This name cannot be the same as the | String. |
|
| The name of the existing VNet that you want to deploy your cluster to. | String. |
|
| The name of the existing subnet in your VNet that you want to deploy your control plane machines to. |
Valid CIDR, for example |
|
| The name of the existing subnet in your VNet that you want to deploy your compute machines to. |
Valid CIDR, for example |
|
|
The name of the Azure cloud environment that is used to configure the Azure SDK with the appropriate Azure API endpoints. If empty, the default value |
Any valid cloud environment, such as |
You cannot customize Azure Availability Zones or Use tags to organize your Azure resources with an Azure cluster.
3.5.5.2. Sample customized install-config.yaml file for Azure
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 13 15
- Required. The installation program prompts you for this value.
- 2 6 11
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 7
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger virtual machine types, such as
Standard_D8s_v3, for your machines if you disable simultaneous multithreading. - 5 8
- You can specify the size of the disk to use in GB. Minimum recommendation for control plane nodes (also known as the master nodes) is 1024 GB.
- 9
- Specify a list of zones to deploy your machines to. For high availability, specify at least two zones.
- 12
- Specify the name of the resource group that contains the DNS zone for your base domain.
- 14
- Specify the name of an already existing resource group to install your cluster to. If undefined, a new resource group is created for the cluster.
- 16
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 17
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
3.5.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
3.5.6. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
3.5.7. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
3.5.8. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
3.5.8.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
3.5.9. Configuring hybrid networking with OVN-Kubernetes
You can configure your cluster to use hybrid networking with OVN-Kubernetes. This allows a hybrid cluster that supports different node networking configurations. For example, this is necessary to run both Linux and Windows nodes in a cluster.
You must configure hybrid networking with OVN-Kubernetes during the installation of your cluster. You cannot switch to hybrid networking after the installation process.
Prerequisites
-
You defined
OVNKubernetesfor thenetworking.networkTypeparameter in theinstall-config.yamlfile. See the installation documentation for configuring OpenShift Container Platform network customizations on your chosen cloud provider for more information.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and configure OVN-Kubernetes with hybrid networking, such as in the following example:Specify a hybrid networking configuration
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the CIDR configuration used for nodes on the additional overlay network. The
hybridClusterNetworkCIDR cannot overlap with theclusterNetworkCIDR. - 2
- Specify a custom VXLAN port for the additional overlay network. This is required for running Windows nodes in a cluster installed on vSphere, and must not be configured for any other cloud provider. The custom port can be any open port excluding the default
4789port. For more information on this requirement, see the Microsoft documentation on Pod-to-pod connectivity between hosts is broken.
-
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
For more information on using Linux and Windows nodes in the same cluster, see Understanding Windows container workloads.
3.5.10. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
3.5.11. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.5.11.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.5.11.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.5.11.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.5.12. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.5.13. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.5.14. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
3.6. Installing a cluster on Azure into an existing VNet
In OpenShift Container Platform version 4.6, you can install a cluster into an existing Azure Virtual Network (VNet) on Microsoft Azure. The installation program provisions the rest of the required infrastructure, which you can further customize. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
3.6.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster and determine the tested and validated region to deploy the cluster to.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
3.6.2. About reusing a VNet for your OpenShift Container Platform cluster
In OpenShift Container Platform 4.6, you can deploy a cluster into an existing Azure Virtual Network (VNet) in Microsoft Azure. If you do, you must also use existing subnets within the VNet and routing rules.
By deploying OpenShift Container Platform into an existing Azure VNet, you might be able to avoid service limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. This is a good option to use if you cannot obtain the infrastructure creation permissions that are required to create the VNet.
3.6.2.1. Requirements for using your VNet
When you deploy a cluster by using an existing VNet, you must perform additional network configuration before you install the cluster. In installer-provisioned infrastructure clusters, the installer usually creates the following components, but it does not create them when you install into an existing VNet:
- Subnets
- Route tables
- VNets
- Network Security Groups
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VNet, you must correctly configure it and its subnets for the installation program and the cluster to use. The installation program cannot subdivide network ranges for the cluster to use, set route tables for the subnets, or set VNet options like DHCP, so you must do so before you install the cluster.
The cluster must be able to access the resource group that contains the existing VNet and subnets. While all of the resources that the cluster creates are placed in a separate resource group that it creates, some network resources are used from a separate group. Some cluster Operators must be able to access resources in both resource groups. For example, the Machine API controller attaches NICS for the virtual machines that it creates to subnets from the networking resource group.
Your VNet must meet the following characteristics:
-
The VNet’s CIDR block must contain the
Networking.MachineCIDRrange, which is the IP address pool for cluster machines. - The VNet and its subnets must belong to the same resource group, and the subnets must be configured to use Azure-assigned DHCP IP addresses instead of static IP addresses.
You must provide two subnets within your VNet, one for the control plane machines and one for the compute machines. Because Azure distributes machines in different availability zones within the region that you specify, your cluster will have high availability by default.
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the specified subnets exist.
- There are two private subnets, one for the control plane machines and one for the compute machines.
- The subnet CIDRs belong to the machine CIDR that you specified. Machines are not provisioned in availability zones that you do not provide private subnets for. If required, the installation program creates public load balancers that manage the control plane and worker nodes, and Azure allocates a public IP address to them.
If you destroy a cluster that uses an existing VNet, the VNet is not deleted.
3.6.2.1.1. Network security group requirements
The network security groups for the subnets that host the compute and control plane machines require specific access to ensure that the cluster communication is correct. You must create rules to allow access to the required cluster communication ports.
The network security group rules must be in place before you install the cluster. If you attempt to install a cluster without the required access, the installation program cannot reach the Azure APIs, and installation fails.
| Port | Description | Control plane | Compute |
|---|---|---|---|
|
| Allows HTTP traffic | x | |
|
| Allows HTTPS traffic | x | |
|
| Allows communication to the control plane machines | x | |
|
| Allows communication to the machine config server | x |
Since cluster components do not modify the user-provided network security groups, which the Kubernetes controllers update, a pseudo-network security group is created for the Kubernetes controller to modify without impacting the rest of the environment.
3.6.2.2. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resources in your clouds than others. For example, you might be able to create application-specific items, like instances, storage, and load balancers, but not networking-related components such as VNets, subnet, or ingress rules.
The Azure credentials that you use when you create your cluster do not need the networking permissions that are required to make VNets and core networking components within the VNet, such as subnets, routing tables, internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as load balancers, security groups, storage accounts, and nodes.
3.6.2.3. Isolation between clusters
Because the cluster is unable to modify network security groups in an existing subnet, there is no way to isolate clusters from each other on the VNet.
3.6.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.6.4. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
3.6.5. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.6.6. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Microsoft Azure.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select azure as the platform to target.
If you do not have a Microsoft Azure profile stored on your computer, specify the following Azure parameter values for your subscription and service principal:
-
azure subscription id: The subscription ID to use for the cluster. Specify the
idvalue in your account output. -
azure tenant id: The tenant ID. Specify the
tenantIdvalue in your account output. -
azure service principal client id: The value of the
appIdparameter for the service principal. -
azure service principal client secret: The value of the
passwordparameter for the service principal.
-
azure subscription id: The subscription ID to use for the cluster. Specify the
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the Azure DNS Zone that you created for your cluster.
Enter a descriptive name for your cluster.
ImportantAll Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
3.6.6.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
3.6.6.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
3.6.6.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
3.6.6.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
3.6.6.1.4. Additional Azure configuration parameters
Additional Azure configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The name of the resource group that contains the DNS zone for your base domain. |
String, for example |
|
| The outbound routing strategy used to connect your cluster to the internet. If you are using user-defined routing, you must have pre-existing networking available where the outbound routing has already been configured prior to installing a cluster. The installation program is not responsible for configuring user-defined routing. |
|
|
| The name of the Azure region that hosts your cluster. |
Any valid region name, such as |
|
| List of availability zones to place machines in. For high availability, specify at least two zones. |
List of zones, for example |
|
|
The name of the resource group that contains the existing VNet that you want to deploy your cluster to. This name cannot be the same as the | String. |
|
| The name of the existing VNet that you want to deploy your cluster to. | String. |
|
| The name of the existing subnet in your VNet that you want to deploy your control plane machines to. |
Valid CIDR, for example |
|
| The name of the existing subnet in your VNet that you want to deploy your compute machines to. |
Valid CIDR, for example |
|
|
The name of the Azure cloud environment that is used to configure the Azure SDK with the appropriate Azure API endpoints. If empty, the default value |
Any valid cloud environment, such as |
You cannot customize Azure Availability Zones or Use tags to organize your Azure resources with an Azure cluster.
3.6.6.2. Sample customized install-config.yaml file for Azure
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 12 18
- Required. The installation program prompts you for this value.
- 2 6
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 7
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger virtual machine types, such as
Standard_D8s_v3, for your machines if you disable simultaneous multithreading. - 5 8
- You can specify the size of the disk to use in GB. Minimum recommendation for control plane nodes (also known as the master nodes) is 1024 GB.
- 9
- Specify a list of zones to deploy your machines to. For high availability, specify at least two zones.
- 11
- Specify the name of the resource group that contains the DNS zone for your base domain.
- 13
- Specify the name of an already existing resource group to install your cluster to. If undefined, a new resource group is created for the cluster.
- 14
- If you use an existing VNet, specify the name of the resource group that contains it.
- 15
- If you use an existing VNet, specify its name.
- 16
- If you use an existing VNet, specify the name of the subnet to host the control plane machines.
- 17
- If you use an existing VNet, specify the name of the subnet to host the compute machines.
- 19
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 20
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
3.6.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
3.6.7. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
3.6.8. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.6.8.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.6.8.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.6.8.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.6.9. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.6.10. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.6.11. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
3.7. Installing a private cluster on Azure
In OpenShift Container Platform version 4.6, you can install a private cluster into an existing Azure Virtual Network (VNet) on Microsoft Azure. The installation program provisions the rest of the required infrastructure, which you can further customize. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
3.7.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster and determine the tested and validated region to deploy the cluster to.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
3.7.2. Private clusters
You can deploy a private OpenShift Container Platform cluster that does not expose external endpoints. Private clusters are accessible from only an internal network and are not visible to the Internet.
By default, OpenShift Container Platform is provisioned to use publicly-accessible DNS and endpoints. A private cluster sets the DNS, Ingress Controller, and API server to private when you deploy your cluster. This means that the cluster resources are only accessible from your internal network and are not visible to the internet.
To deploy a private cluster, you must use existing networking that meets your requirements. Your cluster resources might be shared between other clusters on the network.
Additionally, you must deploy a private cluster from a machine that has access the API services for the cloud you provision to, the hosts on the network that you provision, and to the internet to obtain installation media. You can use any machine that meets these access requirements and follows your company’s guidelines. For example, this machine can be a bastion host on your cloud network or a machine that has access to the network through a VPN.
3.7.2.1. Private clusters in Azure
To create a private cluster on Microsoft Azure, you must provide an existing private VNet and subnets to host the cluster. The installation program must also be able to resolve the DNS records that the cluster requires. The installation program configures the Ingress Operator and API server for only internal traffic.
Depending how your network connects to the private VNET, you might need to use a DNS forwarder in order to resolve the cluster’s private DNS records. The cluster’s machines use 168.63.129.16 internally for DNS resolution. For more information, see What is Azure Private DNS? and What is IP address 168.63.129.16? in the Azure documentation.
The cluster still requires access to Internet to access the Azure APIs.
The following items are not required or created when you install a private cluster:
-
A
BaseDomainResourceGroup, since the cluster does not create public records - Public IP addresses
- Public DNS records
Public endpoints
The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.
The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.7.2.1.1. Limitations
Private clusters on Azure are subject to only the limitations that are associated with the use of an existing VNet.
3.7.2.2. User-defined outbound routing
In OpenShift Container Platform, you can choose your own outbound routing for a cluster to connect to the Internet. This allows you to skip the creation of public IP addresses and the public load balancer.
You can configure user-defined routing by modifying parameters in the install-config.yaml file before installing your cluster. A pre-existing VNet is required to use outbound routing when installing a cluster; the installation program is not responsible for configuring this.
When configuring a cluster to use user-defined routing, the installation program does not create the following resources:
- Outbound rules for access to the Internet.
- Public IPs for the public load balancer.
- Kubernetes Service object to add the cluster machines to the public load balancer for outbound requests.
You must ensure the following items are available before setting user-defined routing:
- Egress to the Internet is possible to pull container images, unless using an internal registry mirror.
- The cluster can access Azure APIs.
- Various allowlist endpoints are configured. You can reference these endpoints in the Configuring your firewall section.
There are several pre-existing networking setups that are supported for Internet access using user-defined routing.
Private cluster with network address translation
You can use Azure VNET network address translation (NAT) to provide outbound Internet access for the subnets in your cluster. You can reference Create a NAT gateway using Azure CLI in the Azure documentation for configuration instructions.
When using a VNet setup with Azure NAT and user-defined routing configured, you can create a private cluster with no public endpoints.
Private cluster with Azure Firewall
You can use Azure Firewall to provide outbound routing for the VNet used to install the cluster. You can learn more about providing user-defined routing with Azure Firewall in the Azure documentation.
When using a VNet setup with Azure Firewall and user-defined routing configured, you can create a private cluster with no public endpoints.
Private cluster with a proxy configuration
You can use a proxy with user-defined routing to allow egress to the Internet. You must ensure that cluster Operators do not access Azure APIs using a proxy; Operators must have access to Azure APIs outside of the proxy.
When using the default route table for subnets, with 0.0.0.0/0 populated automatically by Azure, all Azure API requests are routed over Azure’s internal network even though the IP addresses are public. As long as the Network Security Group rules allow egress to Azure API endpoints, proxies with user-defined routing configured allow you to create private clusters with no public endpoints.
Private cluster with no Internet access
You can install a private network that restricts all access to the internet, except the Azure API. This is accomplished by mirroring the release image registry locally. Your cluster must have access to the following:
- An internal registry mirror that allows for pulling container images
- Access to Azure APIs
With these requirements available, you can use user-defined routing to create private clusters with no public endpoints.
3.7.3. About reusing a VNet for your OpenShift Container Platform cluster
In OpenShift Container Platform 4.6, you can deploy a cluster into an existing Azure Virtual Network (VNet) in Microsoft Azure. If you do, you must also use existing subnets within the VNet and routing rules.
By deploying OpenShift Container Platform into an existing Azure VNet, you might be able to avoid service limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. This is a good option to use if you cannot obtain the infrastructure creation permissions that are required to create the VNet.
3.7.3.1. Requirements for using your VNet
When you deploy a cluster by using an existing VNet, you must perform additional network configuration before you install the cluster. In installer-provisioned infrastructure clusters, the installer usually creates the following components, but it does not create them when you install into an existing VNet:
- Subnets
- Route tables
- VNets
- Network Security Groups
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VNet, you must correctly configure it and its subnets for the installation program and the cluster to use. The installation program cannot subdivide network ranges for the cluster to use, set route tables for the subnets, or set VNet options like DHCP, so you must do so before you install the cluster.
The cluster must be able to access the resource group that contains the existing VNet and subnets. While all of the resources that the cluster creates are placed in a separate resource group that it creates, some network resources are used from a separate group. Some cluster Operators must be able to access resources in both resource groups. For example, the Machine API controller attaches NICS for the virtual machines that it creates to subnets from the networking resource group.
Your VNet must meet the following characteristics:
-
The VNet’s CIDR block must contain the
Networking.MachineCIDRrange, which is the IP address pool for cluster machines. - The VNet and its subnets must belong to the same resource group, and the subnets must be configured to use Azure-assigned DHCP IP addresses instead of static IP addresses.
You must provide two subnets within your VNet, one for the control plane machines and one for the compute machines. Because Azure distributes machines in different availability zones within the region that you specify, your cluster will have high availability by default.
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the specified subnets exist.
- There are two private subnets, one for the control plane machines and one for the compute machines.
- The subnet CIDRs belong to the machine CIDR that you specified. Machines are not provisioned in availability zones that you do not provide private subnets for.
If you destroy a cluster that uses an existing VNet, the VNet is not deleted.
3.7.3.1.1. Network security group requirements
The network security groups for the subnets that host the compute and control plane machines require specific access to ensure that the cluster communication is correct. You must create rules to allow access to the required cluster communication ports.
The network security group rules must be in place before you install the cluster. If you attempt to install a cluster without the required access, the installation program cannot reach the Azure APIs, and installation fails.
| Port | Description | Control plane | Compute |
|---|---|---|---|
|
| Allows HTTP traffic | x | |
|
| Allows HTTPS traffic | x | |
|
| Allows communication to the control plane machines | x | |
|
| Allows communication to the machine config server | x |
Since cluster components do not modify the user-provided network security groups, which the Kubernetes controllers update, a pseudo-network security group is created for the Kubernetes controller to modify without impacting the rest of the environment.
3.7.3.2. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resources in your clouds than others. For example, you might be able to create application-specific items, like instances, storage, and load balancers, but not networking-related components such as VNets, subnet, or ingress rules.
The Azure credentials that you use when you create your cluster do not need the networking permissions that are required to make VNets and core networking components within the VNet, such as subnets, routing tables, internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as load balancers, security groups, storage accounts, and nodes.
3.7.3.3. Isolation between clusters
Because the cluster is unable to modify network security groups in an existing subnet, there is no way to isolate clusters from each other on the VNet.
3.7.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.7.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
3.7.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.7.7. Manually creating the installation configuration file
For installations of a private OpenShift Container Platform cluster that are only accessible from an internal network and are not visible to the Internet, you must manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
3.7.7.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
3.7.7.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
3.7.7.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
3.7.7.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
3.7.7.1.4. Additional Azure configuration parameters
Additional Azure configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The name of the resource group that contains the DNS zone for your base domain. |
String, for example |
|
| The outbound routing strategy used to connect your cluster to the internet. If you are using user-defined routing, you must have pre-existing networking available where the outbound routing has already been configured prior to installing a cluster. The installation program is not responsible for configuring user-defined routing. |
|
|
| The name of the Azure region that hosts your cluster. |
Any valid region name, such as |
|
| List of availability zones to place machines in. For high availability, specify at least two zones. |
List of zones, for example |
|
|
The name of the resource group that contains the existing VNet that you want to deploy your cluster to. This name cannot be the same as the | String. |
|
| The name of the existing VNet that you want to deploy your cluster to. | String. |
|
| The name of the existing subnet in your VNet that you want to deploy your control plane machines to. |
Valid CIDR, for example |
|
| The name of the existing subnet in your VNet that you want to deploy your compute machines to. |
Valid CIDR, for example |
|
|
The name of the Azure cloud environment that is used to configure the Azure SDK with the appropriate Azure API endpoints. If empty, the default value |
Any valid cloud environment, such as |
You cannot customize Azure Availability Zones or Use tags to organize your Azure resources with an Azure cluster.
3.7.7.2. Sample customized install-config.yaml file for Azure
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 12 19
- Required. The installation program prompts you for this value.
- 2 6
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 7
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger virtual machine types, such as
Standard_D8s_v3, for your machines if you disable simultaneous multithreading. - 5 8
- You can specify the size of the disk to use in GB. Minimum recommendation for control plane nodes (also known as the master nodes) is 1024 GB.
- 9
- Specify a list of zones to deploy your machines to. For high availability, specify at least two zones.
- 11
- Specify the name of the resource group that contains the DNS zone for your base domain.
- 13
- Specify the name of an already existing resource group to install your cluster to. If undefined, a new resource group is created for the cluster.
- 14
- If you use an existing VNet, specify the name of the resource group that contains it.
- 15
- If you use an existing VNet, specify its name.
- 16
- If you use an existing VNet, specify the name of the subnet to host the control plane machines.
- 17
- If you use an existing VNet, specify the name of the subnet to host the compute machines.
- 18
- You can customize your own outbound routing. Configuring user-defined routing prevents exposing external endpoints in your cluster. User-defined routing for egress requires deploying your cluster to an existing VNet.
- 20
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 21
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 22
- How to publish the user-facing endpoints of your cluster. Set
publishtoInternalto deploy a private cluster, which cannot be accessed from the Internet. The default value isExternal.
3.7.7.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
3.7.8. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
3.7.9. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.7.9.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.7.9.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.7.9.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.7.10. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.7.11. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.7.12. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
3.8. Installing a cluster on Azure into a government region
In OpenShift Container Platform version 4.6, you can install a cluster on Microsoft Azure into a government region. To configure the government region, you modify parameters in the install-config.yaml file before you install the cluster.
3.8.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster and determine the tested and validated government region to deploy the cluster to.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
3.8.2. Azure government regions
OpenShift Container Platform supports deploying a cluster to Microsoft Azure Government (MAG) regions. MAG is specifically designed for US government agencies at the federal, state, and local level, as well as contractors, educational institutions, and other US customers that must run sensitive workloads on Azure. MAG is composed of government-only data center regions, all granted an Impact Level 5 Provisional Authorization.
Installing to a MAG region requires manually configuring the Azure Government dedicated cloud instance and region in the install-config.yaml file. You must also update your service principal to reference the appropriate government environment.
The Azure government region cannot be selected using the guided terminal prompts from the installation program. You must define the region manually in the install-config.yaml file. Remember to also set the dedicated cloud instance, like AzureUSGovernmentCloud, based on the region specified.
3.8.3. Private clusters
You can deploy a private OpenShift Container Platform cluster that does not expose external endpoints. Private clusters are accessible from only an internal network and are not visible to the Internet.
By default, OpenShift Container Platform is provisioned to use publicly-accessible DNS and endpoints. A private cluster sets the DNS, Ingress Controller, and API server to private when you deploy your cluster. This means that the cluster resources are only accessible from your internal network and are not visible to the internet.
To deploy a private cluster, you must use existing networking that meets your requirements. Your cluster resources might be shared between other clusters on the network.
Additionally, you must deploy a private cluster from a machine that has access the API services for the cloud you provision to, the hosts on the network that you provision, and to the internet to obtain installation media. You can use any machine that meets these access requirements and follows your company’s guidelines. For example, this machine can be a bastion host on your cloud network or a machine that has access to the network through a VPN.
3.8.3.1. Private clusters in Azure
To create a private cluster on Microsoft Azure, you must provide an existing private VNet and subnets to host the cluster. The installation program must also be able to resolve the DNS records that the cluster requires. The installation program configures the Ingress Operator and API server for only internal traffic.
Depending how your network connects to the private VNET, you might need to use a DNS forwarder in order to resolve the cluster’s private DNS records. The cluster’s machines use 168.63.129.16 internally for DNS resolution. For more information, see What is Azure Private DNS? and What is IP address 168.63.129.16? in the Azure documentation.
The cluster still requires access to Internet to access the Azure APIs.
The following items are not required or created when you install a private cluster:
-
A
BaseDomainResourceGroup, since the cluster does not create public records - Public IP addresses
- Public DNS records
Public endpoints
The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.
The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.8.3.1.1. Limitations
Private clusters on Azure are subject to only the limitations that are associated with the use of an existing VNet.
3.8.3.2. User-defined outbound routing
In OpenShift Container Platform, you can choose your own outbound routing for a cluster to connect to the Internet. This allows you to skip the creation of public IP addresses and the public load balancer.
You can configure user-defined routing by modifying parameters in the install-config.yaml file before installing your cluster. A pre-existing VNet is required to use outbound routing when installing a cluster; the installation program is not responsible for configuring this.
When configuring a cluster to use user-defined routing, the installation program does not create the following resources:
- Outbound rules for access to the Internet.
- Public IPs for the public load balancer.
- Kubernetes Service object to add the cluster machines to the public load balancer for outbound requests.
You must ensure the following items are available before setting user-defined routing:
- Egress to the Internet is possible to pull container images, unless using an internal registry mirror.
- The cluster can access Azure APIs.
- Various allowlist endpoints are configured. You can reference these endpoints in the Configuring your firewall section.
There are several pre-existing networking setups that are supported for Internet access using user-defined routing.
Private cluster with network address translation
You can use Azure VNET network address translation (NAT) to provide outbound Internet access for the subnets in your cluster. You can reference Create a NAT gateway using Azure CLI in the Azure documentation for configuration instructions.
When using a VNet setup with Azure NAT and user-defined routing configured, you can create a private cluster with no public endpoints.
Private cluster with Azure Firewall
You can use Azure Firewall to provide outbound routing for the VNet used to install the cluster. You can learn more about providing user-defined routing with Azure Firewall in the Azure documentation.
When using a VNet setup with Azure Firewall and user-defined routing configured, you can create a private cluster with no public endpoints.
Private cluster with a proxy configuration
You can use a proxy with user-defined routing to allow egress to the Internet. You must ensure that cluster Operators do not access Azure APIs using a proxy; Operators must have access to Azure APIs outside of the proxy.
When using the default route table for subnets, with 0.0.0.0/0 populated automatically by Azure, all Azure API requests are routed over Azure’s internal network even though the IP addresses are public. As long as the Network Security Group rules allow egress to Azure API endpoints, proxies with user-defined routing configured allow you to create private clusters with no public endpoints.
Private cluster with no Internet access
You can install a private network that restricts all access to the internet, except the Azure API. This is accomplished by mirroring the release image registry locally. Your cluster must have access to the following:
- An internal registry mirror that allows for pulling container images
- Access to Azure APIs
With these requirements available, you can use user-defined routing to create private clusters with no public endpoints.
3.8.4. About reusing a VNet for your OpenShift Container Platform cluster
In OpenShift Container Platform 4.6, you can deploy a cluster into an existing Azure Virtual Network (VNet) in Microsoft Azure. If you do, you must also use existing subnets within the VNet and routing rules.
By deploying OpenShift Container Platform into an existing Azure VNet, you might be able to avoid service limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. This is a good option to use if you cannot obtain the infrastructure creation permissions that are required to create the VNet.
3.8.4.1. Requirements for using your VNet
When you deploy a cluster by using an existing VNet, you must perform additional network configuration before you install the cluster. In installer-provisioned infrastructure clusters, the installer usually creates the following components, but it does not create them when you install into an existing VNet:
- Subnets
- Route tables
- VNets
- Network Security Groups
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
If you use a custom VNet, you must correctly configure it and its subnets for the installation program and the cluster to use. The installation program cannot subdivide network ranges for the cluster to use, set route tables for the subnets, or set VNet options like DHCP, so you must do so before you install the cluster.
The cluster must be able to access the resource group that contains the existing VNet and subnets. While all of the resources that the cluster creates are placed in a separate resource group that it creates, some network resources are used from a separate group. Some cluster Operators must be able to access resources in both resource groups. For example, the Machine API controller attaches NICS for the virtual machines that it creates to subnets from the networking resource group.
Your VNet must meet the following characteristics:
-
The VNet’s CIDR block must contain the
Networking.MachineCIDRrange, which is the IP address pool for cluster machines. - The VNet and its subnets must belong to the same resource group, and the subnets must be configured to use Azure-assigned DHCP IP addresses instead of static IP addresses.
You must provide two subnets within your VNet, one for the control plane machines and one for the compute machines. Because Azure distributes machines in different availability zones within the region that you specify, your cluster will have high availability by default.
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the specified subnets exist.
- There are two private subnets, one for the control plane machines and one for the compute machines.
- The subnet CIDRs belong to the machine CIDR that you specified. Machines are not provisioned in availability zones that you do not provide private subnets for. If required, the installation program creates public load balancers that manage the control plane and worker nodes, and Azure allocates a public IP address to them.
If you destroy a cluster that uses an existing VNet, the VNet is not deleted.
3.8.4.1.1. Network security group requirements
The network security groups for the subnets that host the compute and control plane machines require specific access to ensure that the cluster communication is correct. You must create rules to allow access to the required cluster communication ports.
The network security group rules must be in place before you install the cluster. If you attempt to install a cluster without the required access, the installation program cannot reach the Azure APIs, and installation fails.
| Port | Description | Control plane | Compute |
|---|---|---|---|
|
| Allows HTTP traffic | x | |
|
| Allows HTTPS traffic | x | |
|
| Allows communication to the control plane machines | x | |
|
| Allows communication to the machine config server | x |
Since cluster components do not modify the user-provided network security groups, which the Kubernetes controllers update, a pseudo-network security group is created for the Kubernetes controller to modify without impacting the rest of the environment.
3.8.4.2. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resources in your clouds than others. For example, you might be able to create application-specific items, like instances, storage, and load balancers, but not networking-related components such as VNets, subnet, or ingress rules.
The Azure credentials that you use when you create your cluster do not need the networking permissions that are required to make VNets and core networking components within the VNet, such as subnets, routing tables, internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as load balancers, security groups, storage accounts, and nodes.
3.8.4.3. Isolation between clusters
Because the cluster is unable to modify network security groups in an existing subnet, there is no way to isolate clusters from each other on the VNet.
3.8.5. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.8.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
3.8.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.8.8. Manually creating the installation configuration file
When installing OpenShift Container Platform on Microsoft Azure into a government region, you must manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
3.8.8.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
3.8.8.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
3.8.8.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
3.8.8.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
3.8.8.1.4. Additional Azure configuration parameters
Additional Azure configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The Azure disk size for the VM. |
Integer that represents the size of the disk in GB. The default is |
|
| Defines the type of disk. |
|
|
| The name of the resource group that contains the DNS zone for your base domain. |
String, for example |
|
| The outbound routing strategy used to connect your cluster to the internet. If you are using user-defined routing, you must have pre-existing networking available where the outbound routing has already been configured prior to installing a cluster. The installation program is not responsible for configuring user-defined routing. |
|
|
| The name of the Azure region that hosts your cluster. |
Any valid region name, such as |
|
| List of availability zones to place machines in. For high availability, specify at least two zones. |
List of zones, for example |
|
|
The name of the resource group that contains the existing VNet that you want to deploy your cluster to. This name cannot be the same as the | String. |
|
| The name of the existing VNet that you want to deploy your cluster to. | String. |
|
| The name of the existing subnet in your VNet that you want to deploy your control plane machines to. |
Valid CIDR, for example |
|
| The name of the existing subnet in your VNet that you want to deploy your compute machines to. |
Valid CIDR, for example |
|
|
The name of the Azure cloud environment that is used to configure the Azure SDK with the appropriate Azure API endpoints. If empty, the default value |
Any valid cloud environment, such as |
You cannot customize Azure Availability Zones or Use tags to organize your Azure resources with an Azure cluster.
3.8.8.2. Sample customized install-config.yaml file for Azure
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 10 19
- Required.
- 2 6
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 7
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger virtual machine types, such as
Standard_D8s_v3, for your machines if you disable simultaneous multithreading. - 5 8
- You can specify the size of the disk to use in GB. Minimum recommendation for control plane nodes (also known as the master nodes) is 1024 GB.
- 9
- Specify a list of zones to deploy your machines to. For high availability, specify at least two zones.
- 11
- Specify the name of the resource group that contains the DNS zone for your base domain.
- 12
- Specify the name of an already existing resource group to install your cluster to. If undefined, a new resource group is created for the cluster.
- 13
- If you use an existing VNet, specify the name of the resource group that contains it.
- 14
- If you use an existing VNet, specify its name.
- 15
- If you use an existing VNet, specify the name of the subnet to host the control plane machines.
- 16
- If you use an existing VNet, specify the name of the subnet to host the compute machines.
- 17
- You can customize your own outbound routing. Configuring user-defined routing prevents exposing external endpoints in your cluster. User-defined routing for egress requires deploying your cluster to an existing VNet.
- 18
- Specify the name of the Azure cloud environment to deploy your cluster to. Set
AzureUSGovernmentCloudto deploy to a Microsoft Azure Government (MAG) region. The default value isAzurePublicCloud. - 20
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 21
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 22
- How to publish the user-facing endpoints of your cluster. Set
publishtoInternalto deploy a private cluster, which cannot be accessed from the Internet. The default value isExternal.
3.8.8.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
3.8.9. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
3.8.10. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.8.10.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.8.10.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.8.10.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.8.11. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.8.12. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.8.13. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
3.9. Installing a cluster on Azure using ARM templates
In OpenShift Container Platform version 4.6, you can install a cluster on Microsoft Azure by using infrastructure that you provide.
Several Azure Resource Manager (ARM) templates are provided to assist in completing these steps or to help model your own.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the cloud provider and the installation process of OpenShift Container Platform. Several ARM templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods; the templates are just an example.
3.9.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure an Azure account to host the cluster.
-
Download the Azure CLI and install it on your computer. See Install the Azure CLI in the Azure documentation. The documentation below was last tested using version
2.2.0of the Azure CLI. Azure CLI commands might perform differently based on the version you use. - If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
NoteBe sure to also review this site list if you are configuring a proxy.
3.9.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
3.9.3. Configuring your Azure project
Before you can install OpenShift Container Platform, you must configure an Azure project to host it.
All Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
3.9.3.1. Azure account limits
The OpenShift Container Platform cluster uses a number of Microsoft Azure components, and the default Azure subscription and service limits, quotas, and constraints affect your ability to install OpenShift Container Platform clusters.
Default limits vary by offer category types, such as Free Trial and Pay-As-You-Go, and by series, such as Dv2, F, and G. For example, the default for Enterprise Agreement subscriptions is 350 cores.
Check the limits for your subscription type and if necessary, increase quota limits for your account before you install a default cluster on Azure.
The following table summarizes the Azure components whose limits can impact your ability to install and run OpenShift Container Platform clusters.
| Component | Number of components required by default | Default Azure limit | Description | ||||||
|---|---|---|---|---|---|---|---|---|---|
| vCPU | 40 | 20 per region | A default cluster requires 40 vCPUs, so you must increase the account limit. By default, each cluster creates the following instances:
Because the bootstrap machine uses To deploy more worker nodes, enable autoscaling, deploy large workloads, or use a different instance type, you must further increase the vCPU limit for your account to ensure that your cluster can deploy the machines that you require. By default, the installation program distributes control plane and compute machines across all availability zones within a region. To ensure high availability for your cluster, select a region with at least three availability zones. If your region contains fewer than three availability zones, the installation program places more than one control plane machine in the available zones. | ||||||
| OS Disk | 7 |
VM OS disk must be able to sustain a minimum throughput of 5000 IOPS / 200MBps. This throughput can be provided by having a minimum of 1 TiB Premium SSD (P30). In Azure, disk performance is directly dependent on SSD disk sizes, so to achieve the throughput supported by
Host caching must be set to | |||||||
| VNet | 1 | 1000 per region | Each default cluster requires one Virtual Network (VNet), which contains two subnets. | ||||||
| Network interfaces | 6 | 65,536 per region | Each default cluster requires six network interfaces. If you create more machines or your deployed workloads create load balancers, your cluster uses more network interfaces. | ||||||
| Network security groups | 2 | 5000 | Each default cluster Each cluster creates network security groups for each subnet in the VNet. The default cluster creates network security groups for the control plane and for the compute node subnets:
| ||||||
| Network load balancers | 3 | 1000 per region | Each cluster creates the following load balancers:
If your applications create more Kubernetes | ||||||
| Public IP addresses | 3 | Each of the two public load balancers uses a public IP address. The bootstrap machine also uses a public IP address so that you can SSH into the machine to troubleshoot issues during installation. The IP address for the bootstrap node is used only during installation. | |||||||
| Private IP addresses | 7 | The internal load balancer, each of the three control plane machines, and each of the three worker machines each use a private IP address. | |||||||
| Spot VM vCPUs (optional) | 0 If you configure spot VMs, your cluster must have two spot VM vCPUs for every compute node. | 20 per region | This is an optional component. To use spot VMs, you must increase the Azure default limit to at least twice the number of compute nodes in your cluster. Note Using spot VMs for control plane nodes is not recommended. |
3.9.3.2. Configuring a public DNS zone in Azure
To install OpenShift Container Platform, the Microsoft Azure account you use must have a dedicated public hosted DNS zone in your account. This zone must be authoritative for the domain. This service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through Azure or another source.
NoteFor more information about purchasing domains through Azure, see Buy a custom domain name for Azure App Service in the Azure documentation.
- If you are using an existing domain and registrar, migrate its DNS to Azure. See Migrate an active DNS name to Azure App Service in the Azure documentation.
Configure DNS for your domain. Follow the steps in the Tutorial: Host your domain in Azure DNS in the Azure documentation to create a public hosted zone for your domain or subdomain, extract the new authoritative name servers, and update the registrar records for the name servers that your domain uses.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.- If you use a subdomain, follow your company’s procedures to add its delegation records to the parent domain.
You can view Azure’s DNS solution by visiting this example for creating DNS zones.
3.9.3.3. Increasing Azure account limits
To increase an account limit, file a support request on the Azure portal.
You can increase only one type of quota per support request.
Procedure
- From the Azure portal, click Help + support in the lower left corner.
Click New support request and then select the required values:
- From the Issue type list, select Service and subscription limits (quotas).
- From the Subscription list, select the subscription to modify.
- From the Quota type list, select the quota to increase. For example, select Compute-VM (cores-vCPUs) subscription limit increases to increase the number of vCPUs, which is required to install a cluster.
- Click Next: Solutions.
On the Problem Details page, provide the required information for your quota increase:
- Click Provide details and provide the required details in the Quota details window.
- In the SUPPORT METHOD and CONTACT INFO sections, provide the issue severity and your contact details.
- Click Next: Review + create and then click Create.
3.9.3.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
3.9.3.5. Required Azure roles
OpenShift Container Platform needs a service principal so it can manage Microsoft Azure resources. Before you can create a service principal, your Azure account subscription must have the following roles:
-
User Access Administrator -
Owner
To set roles on the Azure portal, see the Manage access to Azure resources using RBAC and the Azure portal in the Azure documentation.
3.9.3.6. Creating a service principal
Because OpenShift Container Platform and its installation program must create Microsoft Azure resources through Azure Resource Manager, you must create a service principal to represent it.
Prerequisites
- Install or update the Azure CLI.
-
Install the
jqpackage. - Your Azure account has the required roles for the subscription that you use.
Procedure
Log in to the Azure CLI:
az login
$ az loginCopy to Clipboard Copied! Toggle word wrap Toggle overflow Log in to Azure in the web console by using your credentials.
If your Azure account uses subscriptions, ensure that you are using the right subscription.
View the list of available accounts and record the
tenantIdvalue for the subscription you want to use for your cluster:az account list --refresh
$ az account list --refreshCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View your active account details and confirm that the
tenantIdvalue matches the subscription you want to use:az account show
$ az account showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Ensure that the value of the
tenantIdparameter is the UUID of the correct subscription.
If you are not using the right subscription, change the active subscription:
az account set -s <id>
$ az account set -s <id>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Substitute the value of the
idfor the subscription that you want to use for<id>.
If you changed the active subscription, display your account information again:
az account show
$ az account showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
-
Record the values of the
tenantIdandidparameters from the previous output. You need these values during OpenShift Container Platform installation. Create the service principal for your account:
az ad sp create-for-rbac --role Contributor --name <service_principal>
$ az ad sp create-for-rbac --role Contributor --name <service_principal>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<service_principal>with the name to assign to the service principal.
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Record the values of the
appIdandpasswordparameters from the previous output. You need these values during OpenShift Container Platform installation. Grant additional permissions to the service principal.
-
You must always add the
ContributorandUser Access Administratorroles to the app registration service principal so the cluster can assign credentials for its components. -
To operate the Cloud Credential Operator (CCO) in mint mode, the app registration service principal also requires the
Azure Active Directory Graph/Application.ReadWrite.OwnedByAPI permission. - To operate the CCO in passthrough mode, the app registration service principal does not require additional API permissions.
For more information about CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content.
To assign the
User Access Administratorrole, run the following command:az role assignment create --role "User Access Administrator" \ --assignee-object-id $(az ad sp list --filter "appId eq '<appId>'" \ | jq '.[0].id' -r)$ az role assignment create --role "User Access Administrator" \ --assignee-object-id $(az ad sp list --filter "appId eq '<appId>'" \ | jq '.[0].id' -r)1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<appId>with theappIdparameter value for your service principal.
To assign the
Azure Active Directory Graphpermission, run the following command:az ad app permission add --id <appId> \ --api 00000002-0000-0000-c000-000000000000 \ --api-permissions 824c81eb-e3f8-4ee6-8f6d-de7f50d565b7=Role$ az ad app permission add --id <appId> \1 --api 00000002-0000-0000-c000-000000000000 \ --api-permissions 824c81eb-e3f8-4ee6-8f6d-de7f50d565b7=RoleCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<appId>with theappIdparameter value for your service principal.
Example output
Invoking "az ad app permission grant --id 46d33abc-b8a3-46d8-8c84-f0fd58177435 --api 00000002-0000-0000-c000-000000000000" is needed to make the change effective
Invoking "az ad app permission grant --id 46d33abc-b8a3-46d8-8c84-f0fd58177435 --api 00000002-0000-0000-c000-000000000000" is needed to make the change effectiveCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information about the specific permissions that you grant with this command, see the GUID Table for Windows Azure Active Directory Permissions.
Approve the permissions request. If your account does not have the Azure Active Directory tenant administrator role, follow the guidelines for your organization to request that the tenant administrator approve your permissions request.
az ad app permission grant --id <appId> \ --api 00000002-0000-0000-c000-000000000000$ az ad app permission grant --id <appId> \1 --api 00000002-0000-0000-c000-000000000000Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<appId>with theappIdparameter value for your service principal.
-
You must always add the
3.9.3.7. Supported Azure regions
The installation program dynamically generates the list of available Microsoft Azure regions based on your subscription. The following Azure regions were tested and validated in OpenShift Container Platform version 4.6.1:
Supported Azure public regions
-
australiacentral(Australia Central) -
australiaeast(Australia East) -
australiasoutheast(Australia South East) -
brazilsouth(Brazil South) -
canadacentral(Canada Central) -
canadaeast(Canada East) -
centralindia(Central India) -
centralus(Central US) -
eastasia(East Asia) -
eastus(East US) -
eastus2(East US 2) -
francecentral(France Central) -
germanywestcentral(Germany West Central) -
japaneast(Japan East) -
japanwest(Japan West) -
koreacentral(Korea Central) -
koreasouth(Korea South) -
northcentralus(North Central US) -
northeurope(North Europe) -
norwayeast(Norway East) -
southafricanorth(South Africa North) -
southcentralus(South Central US) -
southeastasia(Southeast Asia) -
southindia(South India) -
switzerlandnorth(Switzerland North) -
uaenorth(UAE North) -
uksouth(UK South) -
ukwest(UK West) -
westcentralus(West Central US) -
westeurope(West Europe) -
westindia(West India) -
westus(West US) -
westus2(West US 2)
Supported Azure Government regions
Support for the following Microsoft Azure Government (MAG) regions was added in OpenShift Container Platform version 4.6:
-
usgovtexas(US Gov Texas) -
usgovvirginia(US Gov Virginia)
You can reference all available MAG regions in the Azure documentation. Other provided MAG regions are expected to work with OpenShift Container Platform, but have not been tested.
3.9.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
3.9.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
3.9.6. Creating the installation files for Azure
To install OpenShift Container Platform on Microsoft Azure using user-provisioned infrastructure, you must generate the files that the installation program needs to deploy your cluster and modify them so that the cluster creates only the machines that it will use. You generate and customize the install-config.yaml file, Kubernetes manifests, and Ignition config files. You also have the option to first set up a separate var partition during the preparation phases of installation.
3.9.6.1. Optional: Creating a separate /var partition
It is recommended that disk partitioning for OpenShift Container Platform be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
If you follow the steps to create a separate /var partition in this procedure, it is not necessary to create the Kubernetes manifest and Ignition config files again as described later in this section.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:openshift-install create manifests --dir $HOME/clusterconfig
$ openshift-install create manifests --dir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshift
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Confirm that the installation program created manifests in the
clusterconfig/openshiftdirectory:ls $HOME/clusterconfig/openshift/
$ ls $HOME/clusterconfig/openshift/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 MiB (Mebibytes) is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
3.9.6.2. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Microsoft Azure.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select azure as the platform to target.
If you do not have a Microsoft Azure profile stored on your computer, specify the following Azure parameter values for your subscription and service principal:
-
azure subscription id: The subscription ID to use for the cluster. Specify the
idvalue in your account output. -
azure tenant id: The tenant ID. Specify the
tenantIdvalue in your account output. -
azure service principal client id: The value of the
appIdparameter for the service principal. -
azure service principal client secret: The value of the
passwordparameter for the service principal.
-
azure subscription id: The subscription ID to use for the cluster. Specify the
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the Azure DNS Zone that you created for your cluster.
Enter a descriptive name for your cluster.
ImportantAll Azure resources that are available through public endpoints are subject to resource name restrictions, and you cannot create resources that use certain terms. For a list of terms that Azure restricts, see Resolve reserved resource name errors in the Azure documentation.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Optional: If you do not want the cluster to provision compute machines, empty the compute pool by editing the resulting
install-config.yamlfile to setreplicasto0for thecomputepool:compute: - hyperthreading: Enabled name: worker platform: {} replicas: 0compute: - hyperthreading: Enabled name: worker platform: {} replicas: 01 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Set to
0.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
3.9.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
3.9.6.4. Exporting common variables for ARM templates
You must export a common set of variables that are used with the provided Azure Resource Manager (ARM) templates used to assist in completing a user-provided infrastructure install on Microsoft Azure.
Specific ARM templates can also require additional exported variables, which are detailed in their related procedures.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Export common variables found in the
install-config.yamlto be used by the provided ARM templates:export CLUSTER_NAME=<cluster_name> export AZURE_REGION=<azure_region> export SSH_KEY=<ssh_key> export BASE_DOMAIN=<base_domain> export BASE_DOMAIN_RESOURCE_GROUP=<base_domain_resource_group>
$ export CLUSTER_NAME=<cluster_name>1 $ export AZURE_REGION=<azure_region>2 $ export SSH_KEY=<ssh_key>3 $ export BASE_DOMAIN=<base_domain>4 $ export BASE_DOMAIN_RESOURCE_GROUP=<base_domain_resource_group>5 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The value of the
.metadata.nameattribute from theinstall-config.yamlfile. - 2
- The region to deploy the cluster into, for example
centralus. This is the value of the.platform.azure.regionattribute from theinstall-config.yamlfile. - 3
- The SSH RSA public key file as a string. You must enclose the SSH key in quotes since it contains spaces. This is the value of the
.sshKeyattribute from theinstall-config.yamlfile. - 4
- The base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster. This is the value of the
.baseDomainattribute from theinstall-config.yamlfile. - 5
- The resource group where the public DNS zone exists. This is the value of the
.platform.azure.baseDomainResourceGroupNameattribute from theinstall-config.yamlfile.
For example:
export CLUSTER_NAME=test-cluster export AZURE_REGION=centralus export SSH_KEY="ssh-rsa xxx/xxx/xxx= user@email.com" export BASE_DOMAIN=example.com export BASE_DOMAIN_RESOURCE_GROUP=ocp-cluster
$ export CLUSTER_NAME=test-cluster $ export AZURE_REGION=centralus $ export SSH_KEY="ssh-rsa xxx/xxx/xxx= user@email.com" $ export BASE_DOMAIN=example.com $ export BASE_DOMAIN_RESOURCE_GROUP=ocp-clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Export the kubeadmin credentials:
export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
3.9.6.5. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow By removing these files, you prevent the cluster from automatically generating control plane machines.
Remove the Kubernetes manifest files that define the worker machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage the worker machines yourself, you do not need to initialize these machines.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
Optional: If you do not want the Ingress Operator to create DNS records on your behalf, remove the
privateZoneandpublicZonesections from the<installation_directory>/manifests/cluster-dns-02-config.ymlDNS configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you do so, you must add ingress DNS records manually in a later step.
When configuring Azure on user-provisioned infrastructure, you must export some common variables defined in the manifest files to use later in the Azure Resource Manager (ARM) templates:
Export the infrastructure ID by using the following command:
export INFRA_ID=<infra_id>
$ export INFRA_ID=<infra_id>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The OpenShift Container Platform cluster has been assigned an identifier (
INFRA_ID) in the form of<cluster_name>-<random_string>. This will be used as the base name for most resources created using the provided ARM templates. This is the value of the.status.infrastructureNameattribute from themanifests/cluster-infrastructure-02-config.ymlfile.
Export the resource group by using the following command:
export RESOURCE_GROUP=<resource_group>
$ export RESOURCE_GROUP=<resource_group>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- All resources created in this Azure deployment exists as part of a resource group. The resource group name is also based on the
INFRA_ID, in the form of<cluster_name>-<random_string>-rg. This is the value of the.status.platformStatus.azure.resourceGroupNameattribute from themanifests/cluster-infrastructure-02-config.ymlfile.
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.7. Creating the Azure resource group and identity
You must create a Microsoft Azure resource group and an identity for that resource group. These are both used during the installation of your OpenShift Container Platform cluster on Azure.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
Procedure
Create the resource group in a supported Azure region:
az group create --name ${RESOURCE_GROUP} --location ${AZURE_REGION}$ az group create --name ${RESOURCE_GROUP} --location ${AZURE_REGION}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create an Azure identity for the resource group:
az identity create -g ${RESOURCE_GROUP} -n ${INFRA_ID}-identity$ az identity create -g ${RESOURCE_GROUP} -n ${INFRA_ID}-identityCopy to Clipboard Copied! Toggle word wrap Toggle overflow This is used to grant the required access to Operators in your cluster. For example, this allows the Ingress Operator to create a public IP and its load balancer. You must assign the Azure identity to a role.
Grant the Contributor role to the Azure identity:
Export the following variables required by the Azure role assignment:
export PRINCIPAL_ID=`az identity show -g ${RESOURCE_GROUP} -n ${INFRA_ID}-identity --query principalId --out tsv`$ export PRINCIPAL_ID=`az identity show -g ${RESOURCE_GROUP} -n ${INFRA_ID}-identity --query principalId --out tsv`Copy to Clipboard Copied! Toggle word wrap Toggle overflow export RESOURCE_GROUP_ID=`az group show -g ${RESOURCE_GROUP} --query id --out tsv`$ export RESOURCE_GROUP_ID=`az group show -g ${RESOURCE_GROUP} --query id --out tsv`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Assign the Contributor role to the identity:
az role assignment create --assignee "${PRINCIPAL_ID}" --role 'Contributor' --scope "${RESOURCE_GROUP_ID}"$ az role assignment create --assignee "${PRINCIPAL_ID}" --role 'Contributor' --scope "${RESOURCE_GROUP_ID}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.8. Uploading the RHCOS cluster image and bootstrap Ignition config file
The Azure client does not support deployments based on files existing locally; therefore, you must copy and store the RHCOS virtual hard disk (VHD) cluster image and bootstrap Ignition config file in a storage container so they are accessible during deployment.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
Procedure
Create an Azure storage account to store the VHD cluster image:
az storage account create -g ${RESOURCE_GROUP} --location ${AZURE_REGION} --name ${CLUSTER_NAME}sa --kind Storage --sku Standard_LRS$ az storage account create -g ${RESOURCE_GROUP} --location ${AZURE_REGION} --name ${CLUSTER_NAME}sa --kind Storage --sku Standard_LRSCopy to Clipboard Copied! Toggle word wrap Toggle overflow WarningThe Azure storage account name must be between 3 and 24 characters in length and use numbers and lower-case letters only. If your
CLUSTER_NAMEvariable does not follow these restrictions, you must manually define the Azure storage account name. For more information on Azure storage account name restrictions, see Resolve errors for storage account names in the Azure documentation.Export the storage account key as an environment variable:
export ACCOUNT_KEY=`az storage account keys list -g ${RESOURCE_GROUP} --account-name ${CLUSTER_NAME}sa --query "[0].value" -o tsv`$ export ACCOUNT_KEY=`az storage account keys list -g ${RESOURCE_GROUP} --account-name ${CLUSTER_NAME}sa --query "[0].value" -o tsv`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Choose the RHCOS version to use and export the URL of its VHD to an environment variable:
export VHD_URL=`curl -s https://raw.githubusercontent.com/openshift/installer/release-4.6/data/data/rhcos.json | jq -r .azure.url`
$ export VHD_URL=`curl -s https://raw.githubusercontent.com/openshift/installer/release-4.6/data/data/rhcos.json | jq -r .azure.url`Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must specify an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
Copy the chosen VHD to a blob:
az storage container create --name vhd --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY}$ az storage container create --name vhd --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY}Copy to Clipboard Copied! Toggle word wrap Toggle overflow az storage blob copy start --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} --destination-blob "rhcos.vhd" --destination-container vhd --source-uri "${VHD_URL}"$ az storage blob copy start --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} --destination-blob "rhcos.vhd" --destination-container vhd --source-uri "${VHD_URL}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow To track the progress of the VHD copy task, run this script:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a blob storage container and upload the generated
bootstrap.ignfile:az storage container create --name files --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} --public-access blob$ az storage container create --name files --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} --public-access blobCopy to Clipboard Copied! Toggle word wrap Toggle overflow az storage blob upload --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} -c "files" -f "<installation_directory>/bootstrap.ign" -n "bootstrap.ign"$ az storage blob upload --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} -c "files" -f "<installation_directory>/bootstrap.ign" -n "bootstrap.ign"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.9. Example for creating DNS zones
DNS records are required for clusters that use user-provisioned infrastructure. You should choose the DNS strategy that fits your scenario.
For this example, Azure’s DNS solution is used, so you will create a new public DNS zone for external (internet) visibility and a private DNS zone for internal cluster resolution.
The public DNS zone is not required to exist in the same resource group as the cluster deployment and might already exist in your organization for the desired base domain. If that is the case, you can skip creating the public DNS zone; be sure the installation config you generated earlier reflects that scenario.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
Procedure
Create the new public DNS zone in the resource group exported in the
BASE_DOMAIN_RESOURCE_GROUPenvironment variable:az network dns zone create -g ${BASE_DOMAIN_RESOURCE_GROUP} -n ${CLUSTER_NAME}.${BASE_DOMAIN}$ az network dns zone create -g ${BASE_DOMAIN_RESOURCE_GROUP} -n ${CLUSTER_NAME}.${BASE_DOMAIN}Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can skip this step if you are using a public DNS zone that already exists.
Create the private DNS zone in the same resource group as the rest of this deployment:
az network private-dns zone create -g ${RESOURCE_GROUP} -n ${CLUSTER_NAME}.${BASE_DOMAIN}$ az network private-dns zone create -g ${RESOURCE_GROUP} -n ${CLUSTER_NAME}.${BASE_DOMAIN}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
You can learn more about configuring a public DNS zone in Azure by visiting that section.
3.9.10. Creating a VNet in Azure
You must create a virtual network (VNet) in Microsoft Azure for your OpenShift Container Platform cluster to use. You can customize the VNet to meet your requirements. One way to create the VNet is to modify the provided Azure Resource Manager (ARM) template.
If you do not use the provided ARM template to create your Azure infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
Procedure
-
Copy the template from the ARM template for the VNet section of this topic and save it as
01_vnet.jsonin your cluster’s installation directory. This template describes the VNet that your cluster requires. Create the deployment by using the
azCLI:az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/01_vnet.json" \ --parameters baseName="${INFRA_ID}"$ az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/01_vnet.json" \ --parameters baseName="${INFRA_ID}"1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The base name to be used in resource names; this is usually the cluster’s infrastructure ID.
Link the VNet template to the private DNS zone:
az network private-dns link vnet create -g ${RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n ${INFRA_ID}-network-link -v "${INFRA_ID}-vnet" -e false$ az network private-dns link vnet create -g ${RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n ${INFRA_ID}-network-link -v "${INFRA_ID}-vnet" -e falseCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.10.1. ARM template for the VNet
You can use the following Azure Resource Manager (ARM) template to deploy the VNet that you need for your OpenShift Container Platform cluster:
Example 3.1. 01_vnet.json ARM template
3.9.11. Deploying the RHCOS cluster image for the Azure infrastructure
You must use a valid Red Hat Enterprise Linux CoreOS (RHCOS) image for Microsoft Azure for your OpenShift Container Platform nodes.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
- Store the RHCOS virtual hard disk (VHD) cluster image in an Azure storage container.
- Store the bootstrap Ignition config file in an Azure storage container.
Procedure
-
Copy the template from the ARM template for image storage section of this topic and save it as
02_storage.jsonin your cluster’s installation directory. This template describes the image storage that your cluster requires. Export the RHCOS VHD blob URL as a variable:
export VHD_BLOB_URL=`az storage blob url --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} -c vhd -n "rhcos.vhd" -o tsv`$ export VHD_BLOB_URL=`az storage blob url --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} -c vhd -n "rhcos.vhd" -o tsv`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Deploy the cluster image:
az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/02_storage.json" \ --parameters vhdBlobURL="${VHD_BLOB_URL}" \ --parameters baseName="${INFRA_ID}"$ az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/02_storage.json" \ --parameters vhdBlobURL="${VHD_BLOB_URL}" \1 --parameters baseName="${INFRA_ID}"2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.11.1. ARM template for image storage
You can use the following Azure Resource Manager (ARM) template to deploy the stored Red Hat Enterprise Linux CoreOS (RHCOS) image that you need for your OpenShift Container Platform cluster:
Example 3.2. 02_storage.json ARM template
3.9.12. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 3.32. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 3.33. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
3.9.13. Creating networking and load balancing components in Azure
You must configure networking and load balancing in Microsoft Azure for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Azure Resource Manager (ARM) template.
If you do not use the provided ARM template to create your Azure infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
- Create and configure a VNet and associated subnets in Azure.
Procedure
-
Copy the template from the ARM template for the network and load balancers section of this topic and save it as
03_infra.jsonin your cluster’s installation directory. This template describes the networking and load balancing objects that your cluster requires. Create the deployment by using the
azCLI:az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/03_infra.json" \ --parameters privateDNSZoneName="${CLUSTER_NAME}.${BASE_DOMAIN}" \ --parameters baseName="${INFRA_ID}"$ az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/03_infra.json" \ --parameters privateDNSZoneName="${CLUSTER_NAME}.${BASE_DOMAIN}" \1 --parameters baseName="${INFRA_ID}"2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create an
apiDNS record in the public zone for the API public load balancer. The${BASE_DOMAIN_RESOURCE_GROUP}variable must point to the resource group where the public DNS zone exists.Export the following variable:
export PUBLIC_IP=`az network public-ip list -g ${RESOURCE_GROUP} --query "[?name=='${INFRA_ID}-master-pip'] | [0].ipAddress" -o tsv`$ export PUBLIC_IP=`az network public-ip list -g ${RESOURCE_GROUP} --query "[?name=='${INFRA_ID}-master-pip'] | [0].ipAddress" -o tsv`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the DNS record in a new public zone:
az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n api -a ${PUBLIC_IP} --ttl 60$ az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n api -a ${PUBLIC_IP} --ttl 60Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you are adding the cluster to an existing public zone, you can create the DNS record in it instead:
az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${BASE_DOMAIN} -n api.${CLUSTER_NAME} -a ${PUBLIC_IP} --ttl 60$ az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${BASE_DOMAIN} -n api.${CLUSTER_NAME} -a ${PUBLIC_IP} --ttl 60Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.13.1. ARM template for the network and load balancers
You can use the following Azure Resource Manager (ARM) template to deploy the networking objects and load balancers that you need for your OpenShift Container Platform cluster:
Example 3.3. 03_infra.json ARM template
3.9.14. Creating the bootstrap machine in Azure
You must create the bootstrap machine in Microsoft Azure to use during OpenShift Container Platform cluster initialization. One way to create this machine is to modify the provided Azure Resource Manager (ARM) template.
If you do not use the provided ARM template to create your bootstrap machine, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
- Create and configure a VNet and associated subnets in Azure.
- Create and configure networking and load balancers in Azure.
- Create control plane and compute roles.
Procedure
-
Copy the template from the ARM template for the bootstrap machine section of this topic and save it as
04_bootstrap.jsonin your cluster’s installation directory. This template describes the bootstrap machine that your cluster requires. Export the following variables required by the bootstrap machine deployment:
export BOOTSTRAP_URL=`az storage blob url --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} -c "files" -n "bootstrap.ign" -o tsv` export BOOTSTRAP_IGNITION=`jq -rcnM --arg v "3.1.0" --arg url ${BOOTSTRAP_URL} '{ignition:{version:$v,config:{replace:{source:$url}}}}' | base64 | tr -d '\n'`$ export BOOTSTRAP_URL=`az storage blob url --account-name ${CLUSTER_NAME}sa --account-key ${ACCOUNT_KEY} -c "files" -n "bootstrap.ign" -o tsv` $ export BOOTSTRAP_IGNITION=`jq -rcnM --arg v "3.1.0" --arg url ${BOOTSTRAP_URL} '{ignition:{version:$v,config:{replace:{source:$url}}}}' | base64 | tr -d '\n'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
azCLI:az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/04_bootstrap.json" \ --parameters bootstrapIgnition="${BOOTSTRAP_IGNITION}" \ --parameters sshKeyData="${SSH_KEY}" \ --parameters baseName="${INFRA_ID}"$ az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/04_bootstrap.json" \ --parameters bootstrapIgnition="${BOOTSTRAP_IGNITION}" \1 --parameters sshKeyData="${SSH_KEY}" \2 --parameters baseName="${INFRA_ID}"3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.14.1. ARM template for the bootstrap machine
You can use the following Azure Resource Manager (ARM) template to deploy the bootstrap machine that you need for your OpenShift Container Platform cluster:
Example 3.4. 04_bootstrap.json ARM template
3.9.15. Creating the control plane machines in Azure
You must create the control plane machines in Microsoft Azure for your cluster to use. One way to create these machines is to modify the provided Azure Resource Manager (ARM) template.
If you do not use the provided ARM template to create your control plane machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
- Create and configure a VNet and associated subnets in Azure.
- Create and configure networking and load balancers in Azure.
- Create control plane and compute roles.
- Create the bootstrap machine.
Procedure
-
Copy the template from the ARM template for control plane machines section of this topic and save it as
05_masters.jsonin your cluster’s installation directory. This template describes the control plane machines that your cluster requires. Export the following variable needed by the control plane machine deployment:
export MASTER_IGNITION=`cat <installation_directory>/master.ign | base64 | tr -d '\n'`
$ export MASTER_IGNITION=`cat <installation_directory>/master.ign | base64 | tr -d '\n'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
azCLI:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The Ignition content for the control plane nodes (also known as the master nodes).
- 2
- The SSH RSA public key file as a string.
- 3
- The name of the private DNS zone to which the control plane nodes are attached.
- 4
- The base name to be used in resource names; this is usually the cluster’s infrastructure ID.
3.9.15.1. ARM template for control plane machines
You can use the following Azure Resource Manager (ARM) template to deploy the control plane machines that you need for your OpenShift Container Platform cluster:
Example 3.5. 05_masters.json ARM template
3.9.16. Wait for bootstrap completion and remove bootstrap resources in Azure
After you create all of the required infrastructure in Microsoft Azure, wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
- Create and configure a VNet and associated subnets in Azure.
- Create and configure networking and load balancers in Azure.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
Change to the directory that contains the installation program and run the following command:
./openshift-install wait-for bootstrap-complete --dir <installation_directory> \ --log-level info$ ./openshift-install wait-for bootstrap-complete --dir <installation_directory> \1 --log-level info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command exits without a
FATALwarning, your production control plane has initialized.Delete the bootstrap resources:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.17. Creating additional worker machines in Azure
You can create worker machines in Microsoft Azure for your cluster to use by launching individual instances discretely or by automated processes outside the cluster, such as auto scaling groups. You can also take advantage of the built-in cluster scaling mechanisms and the machine API in OpenShift Container Platform.
In this example, you manually launch one instance by using the Azure Resource Manager (ARM) template. Additional instances can be launched by including additional resources of type 06_workers.json in the file.
If you do not use the provided ARM template to create your worker machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure an Azure account.
- Generate the Ignition config files for your cluster.
- Create and configure a VNet and associated subnets in Azure.
- Create and configure networking and load balancers in Azure.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
-
Copy the template from the ARM template for worker machines section of this topic and save it as
06_workers.jsonin your cluster’s installation directory. This template describes the worker machines that your cluster requires. Export the following variable needed by the worker machine deployment:
export WORKER_IGNITION=`cat <installation_directory>/worker.ign | base64 | tr -d '\n'`
$ export WORKER_IGNITION=`cat <installation_directory>/worker.ign | base64 | tr -d '\n'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
azCLI:az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/06_workers.json" \ --parameters workerIgnition="${WORKER_IGNITION}" \ --parameters sshKeyData="${SSH_KEY}" \ --parameters baseName="${INFRA_ID}"$ az deployment group create -g ${RESOURCE_GROUP} \ --template-file "<installation_directory>/06_workers.json" \ --parameters workerIgnition="${WORKER_IGNITION}" \1 --parameters sshKeyData="${SSH_KEY}" \2 --parameters baseName="${INFRA_ID}"3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.17.1. ARM template for worker machines
You can use the following Azure Resource Manager (ARM) template to deploy the worker machines that you need for your OpenShift Container Platform cluster:
Example 3.6. 06_workers.json ARM template
3.9.18. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
3.9.18.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.9.18.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>3.9.18.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>3.9.19. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
3.9.20. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
3.9.21. Adding the Ingress DNS records
If you removed the DNS Zone configuration when creating Kubernetes manifests and generating Ignition configs, you must manually create DNS records that point at the Ingress load balancer. You can create either a wildcard *.apps.{baseDomain}. or specific records. You can use A, CNAME, and other records per your requirements.
Prerequisites
- You deployed an OpenShift Container Platform cluster on Microsoft Azure by using infrastructure that you provisioned.
-
Install the OpenShift CLI (
oc). -
Install the
jqpackage. - Install or update the Azure CLI.
Procedure
Confirm the Ingress router has created a load balancer and populated the
EXTERNAL-IPfield:oc -n openshift-ingress get service router-default
$ oc -n openshift-ingress get service router-defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.20.10 35.130.120.110 80:32288/TCP,443:31215/TCP 20
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.20.10 35.130.120.110 80:32288/TCP,443:31215/TCP 20Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the Ingress router IP as a variable:
export PUBLIC_IP_ROUTER=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`$ export PUBLIC_IP_ROUTER=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add a
*.appsrecord to the public DNS zone.If you are adding this cluster to a new public zone, run:
az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n *.apps -a ${PUBLIC_IP_ROUTER} --ttl 300$ az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n *.apps -a ${PUBLIC_IP_ROUTER} --ttl 300Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you are adding this cluster to an already existing public zone, run:
az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${BASE_DOMAIN} -n *.apps.${CLUSTER_NAME} -a ${PUBLIC_IP_ROUTER} --ttl 300$ az network dns record-set a add-record -g ${BASE_DOMAIN_RESOURCE_GROUP} -z ${BASE_DOMAIN} -n *.apps.${CLUSTER_NAME} -a ${PUBLIC_IP_ROUTER} --ttl 300Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Add a
*.appsrecord to the private DNS zone:Create a
*.appsrecord by using the following command:az network private-dns record-set a create -g ${RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n *.apps --ttl 300$ az network private-dns record-set a create -g ${RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n *.apps --ttl 300Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
*.appsrecord to the private DNS zone by using the following command:az network private-dns record-set a add-record -g ${RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n *.apps -a ${PUBLIC_IP_ROUTER}$ az network private-dns record-set a add-record -g ${RESOURCE_GROUP} -z ${CLUSTER_NAME}.${BASE_DOMAIN} -n *.apps -a ${PUBLIC_IP_ROUTER}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If you prefer to add explicit domains instead of using a wildcard, you can create entries for each of the cluster’s current routes:
oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routes
$ oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routesExample output
3.9.22. Completing an Azure installation on user-provisioned infrastructure
After you start the OpenShift Container Platform installation on Microsoft Azure user-provisioned infrastructure, you can monitor the cluster events until the cluster is ready.
Prerequisites
- Deploy the bootstrap machine for an OpenShift Container Platform cluster on user-provisioned Azure infrastructure.
-
Install the
ocCLI and log in.
Procedure
Complete the cluster installation:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
3.9.23. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
3.10. Uninstalling a cluster on Azure
You can remove a cluster that you deployed to Microsoft Azure.
3.10.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
Chapter 4. Installing on GCP
4.1. Configuring a GCP project
Before you can install OpenShift Container Platform, you must configure a Google Cloud Platform (GCP) project to host it.
4.1.1. Creating a GCP project
To install OpenShift Container Platform, you must create a project in your Google Cloud Platform (GCP) account to host the cluster.
Procedure
Create a project to host your OpenShift Container Platform cluster. See Creating and Managing Projects in the GCP documentation.
ImportantYour GCP project must use the Premium Network Service Tier if you are using installer-provisioned infrastructure. The Standard Network Service Tier is not supported for clusters installed using the installation program. The installation program configures internal load balancing for the
api-int.<cluster_name>.<base_domain>URL; the Premium Tier is required for internal load balancing.
4.1.2. Enabling API services in GCP
Your Google Cloud Platform (GCP) project requires access to several API services to complete OpenShift Container Platform installation.
Prerequisites
- You created a project to host your cluster.
Procedure
Enable the following required API services in the project that hosts your cluster. See Enabling services in the GCP documentation.
Expand Table 4.1. Required API services API service Console service name Compute Engine API
compute.googleapis.comGoogle Cloud APIs
cloudapis.googleapis.comCloud Resource Manager API
cloudresourcemanager.googleapis.comGoogle DNS API
dns.googleapis.comIAM Service Account Credentials API
iamcredentials.googleapis.comIdentity and Access Management (IAM) API
iam.googleapis.comService Management API
servicemanagement.googleapis.comService Usage API
serviceusage.googleapis.comGoogle Cloud Storage JSON API
storage-api.googleapis.comCloud Storage
storage-component.googleapis.com
4.1.3. Configuring DNS for GCP
To install OpenShift Container Platform, the Google Cloud Platform (GCP) account you use must have a dedicated public hosted zone in the same project that you host the OpenShift Container Platform cluster. This zone must be authoritative for the domain. The DNS service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through GCP or another source.
NoteIf you purchase a new domain, it can take time for the relevant DNS changes to propagate. For more information about purchasing domains through Google, see Google Domains.
Create a public hosted zone for your domain or subdomain in your GCP project. See Creating public zones in the GCP documentation.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.Extract the new authoritative name servers from the hosted zone records. See Look up your Cloud DNS name servers in the GCP documentation.
You typically have four name servers.
- Update the registrar records for the name servers that your domain uses. For example, if you registered your domain to Google Domains, see the following topic in the Google Domains Help: How to switch to custom name servers.
- If you migrated your root domain to Google Cloud DNS, migrate your DNS records. See Migrating to Cloud DNS in the GCP documentation.
- If you use a subdomain, follow your company’s procedures to add its delegation records to the parent domain. This process might include a request to your company’s IT department or the division that controls the root domain and DNS services for your company.
4.1.4. GCP account limits
The OpenShift Container Platform cluster uses a number of Google Cloud Platform (GCP) components, but the default Quotas do not affect your ability to install a default OpenShift Container Platform cluster.
A default cluster, which contains three compute and three control plane machines, uses the following resources. Note that some resources are required only during the bootstrap process and are removed after the cluster deploys.
| Service | Component | Location | Total resources required | Resources removed after bootstrap |
|---|---|---|---|---|
| Service account | IAM | Global | 5 | 0 |
| Firewall rules | Compute | Global | 11 | 1 |
| Forwarding rules | Compute | Global | 2 | 0 |
| In-use global IP addresses | Compute | Global | 4 | 1 |
| Health checks | Compute | Global | 3 | 0 |
| Images | Compute | Global | 1 | 0 |
| Networks | Compute | Global | 2 | 0 |
| Static IP addresses | Compute | Region | 4 | 1 |
| Routers | Compute | Global | 1 | 0 |
| Routes | Compute | Global | 2 | 0 |
| Subnetworks | Compute | Global | 2 | 0 |
| Target pools | Compute | Global | 3 | 0 |
| CPUs | Compute | Region | 28 | 4 |
| Persistent disk SSD (GB) | Compute | Region | 896 | 128 |
If any of the quotas are insufficient during installation, the installation program displays an error that states both which quota was exceeded and the region.
Be sure to consider your actual cluster size, planned cluster growth, and any usage from other clusters that are associated with your account. The CPU, static IP addresses, and persistent disk SSD (storage) quotas are the ones that are most likely to be insufficient.
If you plan to deploy your cluster in one of the following regions, you will exceed the maximum storage quota and are likely to exceed the CPU quota limit:
-
asia-east2 -
asia-northeast2 -
asia-south1 -
australia-southeast1 -
europe-north1 -
europe-west2 -
europe-west3 -
europe-west6 -
northamerica-northeast1 -
southamerica-east1 -
us-west2
You can increase resource quotas from the GCP console, but you might need to file a support ticket. Be sure to plan your cluster size early so that you can allow time to resolve the support ticket before you install your OpenShift Container Platform cluster.
4.1.5. Creating a service account in GCP
OpenShift Container Platform requires a Google Cloud Platform (GCP) service account that provides authentication and authorization to access data in the Google APIs. If you do not have an existing IAM service account that contains the required roles in your project, you must create one.
Prerequisites
- You created a project to host your cluster.
Procedure
- Create a service account in the project that you use to host your OpenShift Container Platform cluster. See Creating a service account in the GCP documentation.
Grant the service account the appropriate permissions. You can either grant the individual permissions that follow or assign the
Ownerrole to it. See Granting roles to a service account for specific resources.NoteWhile making the service account an owner of the project is the easiest way to gain the required permissions, it means that service account has complete control over the project. You must determine if the risk that comes from offering that power is acceptable.
Create the service account key in JSON format. See Creating service account keys in the GCP documentation.
The service account key is required to create a cluster.
4.1.5.1. Required GCP permissions
When you attach the Owner role to the service account that you create, you grant that service account all permissions, including those that are required to install OpenShift Container Platform. To deploy an OpenShift Container Platform cluster, the service account requires the following permissions. If you deploy your cluster into an existing VPC, the service account does not require certain networking permissions, which are noted in the following lists:
Required roles for the installation program
- Compute Admin
- Security Admin
- Service Account Admin
- Service Account User
- Storage Admin
Required roles for creating network resources during installation
- DNS Administrator
Optional roles
For the cluster to create new limited credentials for its Operators, add the following role:
- Service Account Key Admin
The roles are applied to the service accounts that the control plane and compute machines use:
| Account | Roles |
|---|---|
| Control Plane |
|
|
| |
|
| |
|
| |
|
| |
| Compute |
|
|
|
4.1.6. Supported GCP regions
You can deploy an OpenShift Container Platform cluster to the following Google Cloud Platform (GCP) regions:
-
asia-east1(Changhua County, Taiwan) -
asia-east2(Hong Kong) -
asia-northeast1(Tokyo, Japan) -
asia-northeast2(Osaka, Japan) -
asia-northeast3(Seoul, South Korea) -
asia-south1(Mumbai, India) -
asia-southeast1(Jurong West, Singapore) -
asia-southeast2(Jakarta, Indonesia) -
australia-southeast1(Sydney, Australia) -
europe-north1(Hamina, Finland) -
europe-west1(St. Ghislain, Belgium) -
europe-west2(London, England, UK) -
europe-west3(Frankfurt, Germany) -
europe-west4(Eemshaven, Netherlands) -
europe-west6(Zürich, Switzerland) -
northamerica-northeast1(Montréal, Québec, Canada) -
southamerica-east1(São Paulo, Brazil) -
us-central1(Council Bluffs, Iowa, USA) -
us-east1(Moncks Corner, South Carolina, USA) -
us-east4(Ashburn, Northern Virginia, USA) -
us-west1(The Dalles, Oregon, USA) -
us-west2(Los Angeles, California, USA) -
us-west3(Salt Lake City, Utah, USA) -
us-west4(Las Vegas, Nevada, USA)
4.1.7. Next steps
- Install an OpenShift Container Platform cluster on GCP. You can install a customized cluster or quickly install a cluster with default options.
4.2. Manually creating IAM for GCP
In environments where the cloud identity and access management (IAM) APIs are not reachable, or the administrator prefers not to store an administrator-level credential secret in the cluster kube-system namespace, you can put the Cloud Credential Operator (CCO) into manual mode before you install the cluster.
4.2.1. Alternatives to storing administrator-level secrets in the kube-system project
The Cloud Credential Operator (CCO) manages cloud provider credentials as Kubernetes custom resource definitions (CRDs). You can configure the CCO to suit the security requirements of your organization by setting different values for the credentialsMode parameter in the install-config.yaml file.
If you prefer not to store an administrator-level credential secret in the cluster kube-system project, you can set the credentialsMode parameter for the CCO to Manual when installing OpenShift Container Platform and manage your cloud credentials manually.
Using manual mode allows each cluster component to have only the permissions it requires, without storing an administrator-level credential in the cluster. You can also use this mode if your environment does not have connectivity to the cloud provider public IAM endpoint. However, you must manually reconcile permissions with new release images for every upgrade. You must also manually supply credentials for every component that requests them.
For a detailed description of all available CCO credential modes and their supported platforms, see the Cloud Credential Operator reference.
4.2.2. Manually create IAM
The Cloud Credential Operator (CCO) can be put into manual mode prior to installation in environments where the cloud identity and access management (IAM) APIs are not reachable, or the administrator prefers not to store an administrator-level credential secret in the cluster kube-system namespace.
Procedure
To generate the manifests, run the following command from the directory that contains the installation program:
openshift-install create manifests --dir <installation_directory>
$ openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
Insert a config map into the manifests directory so that the Cloud Credential Operator is placed in manual mode:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the
admincredential secret created using your local cloud credentials. This removal prevents youradmincredential from being stored in the cluster:rm mycluster/openshift/99_cloud-creds-secret.yaml
$ rm mycluster/openshift/99_cloud-creds-secret.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the directory that contains the installation program, obtain details of the OpenShift Container Platform release image that your
openshift-installbinary is built to use:openshift-install version
$ openshift-install versionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
release image quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64
release image quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Locate all
CredentialsRequestobjects in this release image that target the cloud you are deploying on:oc adm release extract quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64 --credentials-requests --cloud=gcp
$ oc adm release extract quay.io/openshift-release-dev/ocp-release:4.y.z-x86_64 --credentials-requests --cloud=gcpCopy to Clipboard Copied! Toggle word wrap Toggle overflow This displays the details for each request.
Sample
CredentialsRequestobjectCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Create YAML files for secrets in the
openshift-installmanifests directory that you generated previously. The secrets must be stored using the namespace and secret name defined in thespec.secretReffor eachcredentialsRequest. The format for the secret data varies for each cloud provider. From the directory that contains the installation program, proceed with your cluster creation:
openshift-install create cluster --dir <installation_directory>
$ openshift-install create cluster --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantBefore upgrading a cluster that uses manually maintained credentials, you must ensure that the CCO is in an upgradeable state. For details, see the Upgrading clusters with manually maintained credentials section of the installation content for your cloud provider.
4.2.3. Admin credentials root secret format
Each cloud provider uses a credentials root secret in the kube-system namespace by convention, which is then used to satisfy all credentials requests and create their respective secrets. This is done either by minting new credentials, with mint mode, or by copying the credentials root secret, with passthrough mode.
The format for the secret varies by cloud, and is also used for each CredentialsRequest secret.
Google Cloud Platform (GCP) secret format
4.2.4. Upgrading clusters with manually maintained credentials
If credentials are added in a future release, the Cloud Credential Operator (CCO) upgradable status for a cluster with manually maintained credentials changes to false. For minor release, for example, from 4.5 to 4.6, this status prevents you from upgrading until you have addressed any updated permissions. For z-stream releases, for example, from 4.5.10 to 4.5.11, the upgrade is not blocked, but the credentials must still be updated for the new release.
Use the Administrator perspective of the web console to determine if the CCO is upgradeable.
- Navigate to Administration → Cluster Settings.
- To view the CCO status details, click cloud-credential in the Cluster Operators list.
-
If the Upgradeable status in the Conditions section is False, examine the
credentialsRequestsfor the new release and update the manually maintained credentials on your cluster to match before upgrading.
In addition to creating new credentials for the release image that you are upgrading to, you must review the required permissions for existing credentials and accommodate any new permissions requirements for existing components in the new release. The CCO cannot detect these mismatches and will not set upgradable to false in this case.
The Manually creating IAM section of the installation content for your cloud provider explains how to obtain and use the credentials required for your cloud.
4.2.5. Mint mode
Mint mode is the default and recommended Cloud Credential Operator (CCO) credentials mode for OpenShift Container Platform. In this mode, the CCO uses the provided administrator-level cloud credential to run the cluster. Mint mode is supported for AWS, GCP, and Azure.
In mint mode, the admin credential is stored in the kube-system namespace and then used by the CCO to process the CredentialsRequest objects in the cluster and create users for each with specific permissions.
The benefits of mint mode include:
- Each cluster component has only the permissions it requires
- Automatic, on-going reconciliation for cloud credentials, including additional credentials or permissions that might be required for upgrades
One drawback is that mint mode requires admin credential storage in a cluster kube-system secret.
4.2.6. Mint Mode with removal or rotation of the admin credential
Currently, this mode is only supported on AWS.
In this mode, a user installs OpenShift Container Platform with an admin credential just like the normal mint mode. However, this mode removes the admin credential secret from the cluster post-installation.
The administrator can have the Cloud Credential Operator make its own request for a read-only credential that allows it to verify if all CredentialsRequest objects have their required permissions, thus the admin credential is not required unless something needs to be changed. After the associated credential is removed, it can be destroyed on the underlying cloud, if desired.
Prior to upgrade, the admin credential should be restored. In the future, upgrade might be blocked if the credential is not present.
The admin credential is not stored in the cluster permanently.
This mode still requires the admin credential in the cluster for brief periods of time. It also requires manually re-instating the secret with admin credentials for each upgrade.
4.2.7. Next steps
Install an OpenShift Container Platform cluster:
- Installing a cluster quickly on GCP with default options on installer-provisioned infrastructure
- Install a cluster with cloud customizations on installer-provisioned infrastructure
- Install a cluster with network customizations on installer-provisioned infrastructure
4.3. Installing a cluster quickly on GCP
In OpenShift Container Platform version 4.6, you can install a cluster on Google Cloud Platform (GCP) that uses the default configuration options.
4.3.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure a GCP account to host the cluster.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.3.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.3.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Set the
GOOGLE_APPLICATION_CREDENTIALSenvironment variable to the full path to your service account private key file.export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"
$ export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the credentials were applied.
gcloud auth list
$ gcloud auth listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
4.3.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
4.3.5. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Remove any existing GCP credentials that do not use the service account key for the GCP account that you configured for your cluster and that are stored in the following locations:
-
The
GOOGLE_CREDENTIALS,GOOGLE_CLOUD_KEYFILE_JSON, orGCLOUD_KEYFILE_JSONenvironment variables -
The
~/.gcp/osServiceAccount.jsonfile -
The
gcloud clidefault credentials
-
The
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Provide values at the prompts:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster. If you provide a name that is longer than 6 characters, only the first 6 characters will be used in the infrastructure ID that is generated from the cluster name.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
Optional: You can reduce the number of permissions for the service account that you used to install the cluster.
-
If you assigned the
Ownerrole to your service account, you can remove that role and replace it with theViewerrole. -
If you included the
Service Account Key Adminrole, you can remove it.
-
If you assigned the
4.3.6. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.3.6.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.3.6.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.3.6.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.3.7. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.3.8. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.3.9. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.4. Installing a cluster on GCP with customizations
In OpenShift Container Platform version 4.6, you can install a customized cluster on infrastructure that the installation program provisions on Google Cloud Platform (GCP). To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
4.4.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure a GCP account to host the cluster.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.4.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.4.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Set the
GOOGLE_APPLICATION_CREDENTIALSenvironment variable to the full path to your service account private key file.export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"
$ export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the credentials were applied.
gcloud auth list
$ gcloud auth listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
4.4.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
4.4.5. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Google Cloud Platform (GCP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
4.4.5.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
4.4.5.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
4.4.5.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
4.4.5.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
4.4.5.1.4. Additional Google Cloud Platform (GCP) configuration parameters
Additional GCP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The name of the existing VPC that you want to deploy your cluster to. | String. |
|
| The name of the GCP region that hosts your cluster. |
Any valid region name, such as |
|
| The GCP machine type. | The GCP machine type. |
|
| The availability zones where the installation program creates machines for the specified MachinePool. |
A list of valid GCP availability zones, such as |
|
| The name of the existing subnet in your VPC that you want to deploy your control plane machines to. | The subnet name. |
|
| The name of the existing subnet in your VPC that you want to deploy your compute machines to. | The subnet name. |
|
| A list of license URLs that must be applied to the compute images. Important
The | Any license available with the license API, such as the license to enable nested virtualization. You cannot use this parameter with a mechanism that generates pre-built images. Using a license URL forces the installer to copy the source image before use. |
|
| The size of the disk in gigabytes (GB). | Any size between 16 GB and 65536 GB. |
|
| The type of disk. |
Either the default |
4.4.5.2. Sample customized install-config.yaml file for GCP
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 8 9 10 11
- Required. The installation program prompts you for this value.
- 2 5
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 6
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4 7
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger machine types, such as
n1-standard-8, for your machines if you disable simultaneous multithreading. - 12
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 13
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
4.4.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.4.6. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Remove any existing GCP credentials that do not use the service account key for the GCP account that you configured for your cluster and that are stored in the following locations:
-
The
GOOGLE_CREDENTIALS,GOOGLE_CLOUD_KEYFILE_JSON, orGCLOUD_KEYFILE_JSONenvironment variables -
The
~/.gcp/osServiceAccount.jsonfile -
The
gcloud clidefault credentials
-
The
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: You can reduce the number of permissions for the service account that you used to install the cluster.
-
If you assigned the
Ownerrole to your service account, you can remove that role and replace it with theViewerrole. -
If you included the
Service Account Key Adminrole, you can remove it.
-
If you assigned the
4.4.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.4.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.4.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.4.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.4.8. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.4.9. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.4.10. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.5. Installing a cluster on GCP with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster with a customized network configuration on infrastructure that the installation program provisions on Google Cloud Platform (GCP). By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing MTU and VXLAN configurations. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
4.5.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure a GCP account to host the cluster.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.5.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.5.3. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Set the
GOOGLE_APPLICATION_CREDENTIALSenvironment variable to the full path to your service account private key file.export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"
$ export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the credentials were applied.
gcloud auth list
$ gcloud auth listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
4.5.4. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
4.5.5. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Google Cloud Platform (GCP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
4.5.5.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
4.5.5.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
4.5.5.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
4.5.5.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
4.5.5.1.4. Additional Google Cloud Platform (GCP) configuration parameters
Additional GCP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The name of the existing VPC that you want to deploy your cluster to. | String. |
|
| The name of the GCP region that hosts your cluster. |
Any valid region name, such as |
|
| The GCP machine type. | The GCP machine type. |
|
| The availability zones where the installation program creates machines for the specified MachinePool. |
A list of valid GCP availability zones, such as |
|
| The name of the existing subnet in your VPC that you want to deploy your control plane machines to. | The subnet name. |
|
| The name of the existing subnet in your VPC that you want to deploy your compute machines to. | The subnet name. |
|
| A list of license URLs that must be applied to the compute images. Important
The | Any license available with the license API, such as the license to enable nested virtualization. You cannot use this parameter with a mechanism that generates pre-built images. Using a license URL forces the installer to copy the source image before use. |
|
| The size of the disk in gigabytes (GB). | Any size between 16 GB and 65536 GB. |
|
| The type of disk. |
Either the default |
4.5.5.2. Sample customized install-config.yaml file for GCP
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 8 10 11 12
- Required. The installation program prompts you for this value.
- 2 5 9
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 6
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4 7
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger machine types, such as
n1-standard-8, for your machines if you disable simultaneous multithreading. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
4.5.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.5.6. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
4.5.7. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
4.5.8. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
4.5.8.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
4.5.9. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
4.5.10. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.5.10.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.5.10.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.5.10.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.5.11. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.5.12. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.5.13. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.6. Installing a cluster on GCP in a restricted network
In OpenShift Container Platform 4.6, you can install a cluster on Google Cloud Platform (GCP) in a restricted network by creating an internal mirror of the installation release content on an existing Google Virtual Private Cloud (VPC).
You can install an OpenShift Container Platform cluster by using mirrored installation release content, but your cluster will require internet access to use the GCP APIs.
4.6.1. Prerequisites
You mirrored the images for a disconnected installation to your registry and obtained the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
You have an existing VPC in GCP. While installing a cluster in a restricted network that uses installer-provisioned infrastructure, you cannot use the installer-provisioned VPC. You must use a user-provisioned VPC that satisfies one of the following requirements:
- Contains the mirror registry
- Has firewall rules or a peering connection to access the mirror registry hosted elsewhere
- You reviewed details about the OpenShift Container Platform installation and update processes.
-
If you use a firewall, you must configure it to allow the sites that your cluster requires access to. While you might need to grant access to more sites, you must grant access to
*.googleapis.comandaccounts.google.com. - If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.6.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
4.6.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
4.6.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.6.4. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Set the
GOOGLE_APPLICATION_CREDENTIALSenvironment variable to the full path to your service account private key file.export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"
$ export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the credentials were applied.
gcloud auth list
$ gcloud auth listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
4.6.5. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Google Cloud Platform (GCP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
Have the
imageContentSourcesvalues that were generated during mirror registry creation. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<mirror_host_name>, specify the registry domain name that you specified in the certificate for your mirror registry, and for<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.
Define the network and subnets for the VPC to install the cluster in under the parent
platform.gcpfield:network: <existing_vpc> controlPlaneSubnet: <control_plane_subnet> computeSubnet: <compute_subnet>
network: <existing_vpc> controlPlaneSubnet: <control_plane_subnet> computeSubnet: <compute_subnet>Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
platform.gcp.network, specify the name for the existing Google VPC. Forplatform.gcp.controlPlaneSubnetandplatform.gcp.computeSubnet, specify the existing subnets to deploy the control plane machines and compute machines, respectively.Add the image content resources, which look like this excerpt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To complete these values, use the
imageContentSourcesthat you recorded during mirror registry creation.
-
Make any other modifications to the
install-config.yamlfile that you require. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
4.6.5.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
4.6.5.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
4.6.5.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
4.6.5.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
4.6.5.1.4. Additional Google Cloud Platform (GCP) configuration parameters
Additional GCP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The name of the existing VPC that you want to deploy your cluster to. | String. |
|
| The name of the GCP region that hosts your cluster. |
Any valid region name, such as |
|
| The GCP machine type. | The GCP machine type. |
|
| The availability zones where the installation program creates machines for the specified MachinePool. |
A list of valid GCP availability zones, such as |
|
| The name of the existing subnet in your VPC that you want to deploy your control plane machines to. | The subnet name. |
|
| The name of the existing subnet in your VPC that you want to deploy your compute machines to. | The subnet name. |
|
| A list of license URLs that must be applied to the compute images. Important
The | Any license available with the license API, such as the license to enable nested virtualization. You cannot use this parameter with a mechanism that generates pre-built images. Using a license URL forces the installer to copy the source image before use. |
|
| The size of the disk in gigabytes (GB). | Any size between 16 GB and 65536 GB. |
|
| The type of disk. |
Either the default |
4.6.5.2. Sample customized install-config.yaml file for GCP
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 8 9 10
- Required. The installation program prompts you for this value.
- 2 5
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 6
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4 7
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger machine types, such as
n1-standard-8, for your machines if you disable simultaneous multithreading. - 11
- Specify the name of an existing VPC.
- 12
- Specify the name of the existing subnet to deploy the control plane machines to. The subnet must belong to the VPC that you specified.
- 13
- Specify the name of the existing subnet to deploy the compute machines to. The subnet must belong to the VPC that you specified.
- 14
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For example,registry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 17
- Provide the contents of the certificate file that you used for your mirror registry.
- 18
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
4.6.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.6.6. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Remove any existing GCP credentials that do not use the service account key for the GCP account that you configured for your cluster and that are stored in the following locations:
-
The
GOOGLE_CREDENTIALS,GOOGLE_CLOUD_KEYFILE_JSON, orGCLOUD_KEYFILE_JSONenvironment variables -
The
~/.gcp/osServiceAccount.jsonfile -
The
gcloud clidefault credentials
-
The
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: You can reduce the number of permissions for the service account that you used to install the cluster.
-
If you assigned the
Ownerrole to your service account, you can remove that role and replace it with theViewerrole. -
If you included the
Service Account Key Adminrole, you can remove it.
-
If you assigned the
4.6.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.6.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.6.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.6.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.6.8. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.6.9. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
4.6.10. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.6.11. Next steps
- Validate an installation.
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
4.7. Installing a cluster on GCP into an existing VPC
In OpenShift Container Platform version 4.6, you can install a cluster into an existing Virtual Private Cloud (VPC) on Google Cloud Platform (GCP). The installation program provisions the rest of the required infrastructure, which you can further customize. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
4.7.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure a GCP account to host the cluster.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.7.2. About using a custom VPC
In OpenShift Container Platform 4.6, you can deploy a cluster into existing subnets in an existing Virtual Private Cloud (VPC) in Google Cloud Platform (GCP). By deploying OpenShift Container Platform into an existing GCP VPC, you might be able to avoid limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. If you cannot obtain the infrastructure creation permissions that are required to create the VPC yourself, use this installation option. You must configure networking for the subnets.
4.7.2.1. Requirements for using your VPC
The union of the VPC CIDR block and the machine network CIDR must be non-empty. The subnets must be within the machine network.
The installation program does not create the following components:
- NAT gateways
- Subnets
- Route tables
- VPC network
The installation program requires that you use the cloud-provided DNS server. Using a custom DNS server is not supported and causes the installation to fail.
4.7.2.2. VPC validation
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the subnets that you specify exist.
- You provide one subnet for control-plane machines and one subnet for compute machines.
- The subnet’s CIDRs belong to the machine CIDR that you specified.
4.7.2.3. Division of permissions
Some individuals can create different resource in your clouds than others. For example, you might be able to create application-specific items, like instances, buckets, and load balancers, but not networking-related components such as VPCs, subnets, or ingress rules.
4.7.2.4. Isolation between clusters
If you deploy OpenShift Container Platform to an existing network, the isolation of cluster services is reduced in the following ways:
- You can install multiple OpenShift Container Platform clusters in the same VPC.
- ICMP ingress is allowed to the entire network.
- TCP 22 ingress (SSH) is allowed to the entire network.
- Control plane TCP 6443 ingress (Kubernetes API) is allowed to the entire network.
- Control plane TCP 22623 ingress (MCS) is allowed to the entire network.
4.7.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.7.4. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Set the
GOOGLE_APPLICATION_CREDENTIALSenvironment variable to the full path to your service account private key file.export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"
$ export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the credentials were applied.
gcloud auth list
$ gcloud auth listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
4.7.5. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
4.7.6. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Google Cloud Platform (GCP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
4.7.6.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
4.7.6.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
4.7.6.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
4.7.6.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
4.7.6.1.4. Additional Google Cloud Platform (GCP) configuration parameters
Additional GCP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The name of the existing VPC that you want to deploy your cluster to. | String. |
|
| The name of the GCP region that hosts your cluster. |
Any valid region name, such as |
|
| The GCP machine type. | The GCP machine type. |
|
| The availability zones where the installation program creates machines for the specified MachinePool. |
A list of valid GCP availability zones, such as |
|
| The name of the existing subnet in your VPC that you want to deploy your control plane machines to. | The subnet name. |
|
| The name of the existing subnet in your VPC that you want to deploy your compute machines to. | The subnet name. |
|
| A list of license URLs that must be applied to the compute images. Important
The | Any license available with the license API, such as the license to enable nested virtualization. You cannot use this parameter with a mechanism that generates pre-built images. Using a license URL forces the installer to copy the source image before use. |
|
| The size of the disk in gigabytes (GB). | Any size between 16 GB and 65536 GB. |
|
| The type of disk. |
Either the default |
4.7.6.2. Sample customized install-config.yaml file for GCP
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 8 9 10 14
- Required. The installation program prompts you for this value.
- 2 5
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 6
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4 7
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger machine types, such as
n1-standard-8, for your machines if you disable simultaneous multithreading. - 11
- Specify the name of an existing VPC.
- 12
- Specify the name of the existing subnet to deploy the control plane machines to. The subnet must belong to the VPC that you specified.
- 13
- Specify the name of the existing subnet to deploy the compute machines to. The subnet must belong to the VPC that you specified.
- 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
4.7.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.7.7. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Remove any existing GCP credentials that do not use the service account key for the GCP account that you configured for your cluster and that are stored in the following locations:
-
The
GOOGLE_CREDENTIALS,GOOGLE_CLOUD_KEYFILE_JSON, orGCLOUD_KEYFILE_JSONenvironment variables -
The
~/.gcp/osServiceAccount.jsonfile -
The
gcloud clidefault credentials
-
The
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
Optional: You can reduce the number of permissions for the service account that you used to install the cluster.
-
If you assigned the
Ownerrole to your service account, you can remove that role and replace it with theViewerrole. -
If you included the
Service Account Key Adminrole, you can remove it.
-
If you assigned the
4.7.8. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.7.8.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.7.8.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.7.8.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.7.9. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.7.10. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.7.11. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.8. Installing a private cluster on GCP
In OpenShift Container Platform version 4.6, you can install a private cluster into an existing VPC on Google Cloud Platform (GCP). The installation program provisions the rest of the required infrastructure, which you can further customize. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
4.8.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Configure a GCP account to host the cluster.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
- If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.8.2. Private clusters
You can deploy a private OpenShift Container Platform cluster that does not expose external endpoints. Private clusters are accessible from only an internal network and are not visible to the Internet.
By default, OpenShift Container Platform is provisioned to use publicly-accessible DNS and endpoints. A private cluster sets the DNS, Ingress Controller, and API server to private when you deploy your cluster. This means that the cluster resources are only accessible from your internal network and are not visible to the internet.
To deploy a private cluster, you must use existing networking that meets your requirements. Your cluster resources might be shared between other clusters on the network.
Additionally, you must deploy a private cluster from a machine that has access the API services for the cloud you provision to, the hosts on the network that you provision, and to the internet to obtain installation media. You can use any machine that meets these access requirements and follows your company’s guidelines. For example, this machine can be a bastion host on your cloud network or a machine that has access to the network through a VPN.
4.8.2.1. Private clusters in GCP
To create a private cluster on Google Cloud Platform (GCP), you must provide an existing private VPC and subnets to host the cluster. The installation program must also be able to resolve the DNS records that the cluster requires. The installation program configures the Ingress Operator and API server for only internal traffic.
The cluster still requires access to Internet to access the GCP APIs.
The following items are not required or created when you install a private cluster:
- Public subnets
- Public network load balancers, which support public ingress
-
A public DNS zone that matches the
baseDomainfor the cluster
The installation program does use the baseDomain that you specify to create a private DNS zone and the required records for the cluster. The cluster is configured so that the Operators do not create public records for the cluster and all cluster machines are placed in the private subnets that you specify.
Because it is not possible to limit access to external load balancers based on source tags, the private cluster uses only internal load balancers to allow access to internal instances.
The internal load balancer relies on instance groups rather than the target pools that the network load balancers use. The installation program creates instance groups for each zone, even if there is no instance in that group.
- The cluster IP address is internal only.
- One forwarding rule manages both the Kubernetes API and machine config server ports.
- The backend service is comprised of each zone’s instance group and, while it exists, the bootstrap instance group.
- The firewall uses a single rule that is based on only internal source ranges.
4.8.2.1.1. Limitations
No health check for the Machine config server, /healthz, runs because of a difference in load balancer functionality. Two internal load balancers cannot share a single IP address, but two network load balancers can share a single external IP address. Instead, the health of an instance is determined entirely by the /readyz check on port 6443.
4.8.3. About using a custom VPC
In OpenShift Container Platform 4.6, you can deploy a cluster into an existing VPC in Google Cloud Platform (GCP). If you do, you must also use existing subnets within the VPC and routing rules.
By deploying OpenShift Container Platform into an existing GCP VPC, you might be able to avoid limit constraints in new accounts or more easily abide by the operational constraints that your company’s guidelines set. This is a good option to use if you cannot obtain the infrastructure creation permissions that are required to create the VPC yourself.
4.8.3.1. Requirements for using your VPC
The installation program will no longer create the following components:
- VPC
- Subnets
- Cloud router
- Cloud NAT
- NAT IP addresses
If you use a custom VPC, you must correctly configure it and its subnets for the installation program and the cluster to use. The installation program cannot subdivide network ranges for the cluster to use, set route tables for the subnets, or set VPC options like DHCP, so you must do so before you install the cluster.
Your VPC and subnets must meet the following characteristics:
- The VPC must be in the same GCP project that you deploy the OpenShift Container Platform cluster to.
- To allow access to the Internet from the control plane and compute machines, you must configure cloud NAT on the subnets to allow egress to it. These machines do not have a public address. Even if you do not require access to the Internet, you must allow egress to the VPC network to obtain the installation program and images. Because multiple cloud NATs cannot be configured on the shared subnets, the installation program cannot configure it.
To ensure that the subnets that you provide are suitable, the installation program confirms the following data:
- All the subnets that you specify exist and belong to the VPC that you specified.
- The subnet CIDRs belong to the machine CIDR.
- You must provide a subnet to deploy the cluster control plane and compute machines to. You can use the same subnet for both machine types.
If you destroy a cluster that uses an existing VPC, the VPC is not deleted.
4.8.3.2. Division of permissions
Starting with OpenShift Container Platform 4.3, you do not need all of the permissions that are required for an installation program-provisioned infrastructure cluster to deploy a cluster. This change mimics the division of permissions that you might have at your company: some individuals can create different resources in your clouds than others. For example, you might be able to create application-specific items, like instances, buckets, and load balancers, but not networking-related components such as VPCs, subnets, or Ingress rules.
The GCP credentials that you use when you create your cluster do not need the networking permissions that are required to make VPCs and core networking components within the VPC, such as subnets, routing tables, internet gateways, NAT, and VPN. You still need permission to make the application resources that the machines within the cluster require, such as load balancers, security groups, storage, and nodes.
4.8.3.3. Isolation between clusters
If you deploy OpenShift Container Platform to an existing network, the isolation of cluster services is preserved by firewall rules that reference the machines in your cluster by the cluster’s infrastructure ID. Only traffic within the cluster is allowed.
If you deploy multiple clusters to the same VPC, the following components might share access between clusters:
- The API, which is globally available with an external publishing strategy or available throughout the network in an internal publishing strategy
- Debugging tools, such as ports on VM instances that are open to the machine CIDR for SSH and ICMP access
4.8.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.8.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Set the
GOOGLE_APPLICATION_CREDENTIALSenvironment variable to the full path to your service account private key file.export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"
$ export GOOGLE_APPLICATION_CREDENTIALS="<your_service_account_file>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the credentials were applied.
gcloud auth list
$ gcloud auth listCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
4.8.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
4.8.7. Manually creating the installation configuration file
For installations of a private OpenShift Container Platform cluster that are only accessible from an internal network and are not visible to the Internet, you must manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
4.8.7.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
4.8.7.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
4.8.7.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
4.8.7.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
|
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
4.8.7.1.4. Additional Google Cloud Platform (GCP) configuration parameters
Additional GCP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The name of the existing VPC that you want to deploy your cluster to. | String. |
|
| The name of the GCP region that hosts your cluster. |
Any valid region name, such as |
|
| The GCP machine type. | The GCP machine type. |
|
| The availability zones where the installation program creates machines for the specified MachinePool. |
A list of valid GCP availability zones, such as |
|
| The name of the existing subnet in your VPC that you want to deploy your control plane machines to. | The subnet name. |
|
| The name of the existing subnet in your VPC that you want to deploy your compute machines to. | The subnet name. |
|
| A list of license URLs that must be applied to the compute images. Important
The | Any license available with the license API, such as the license to enable nested virtualization. You cannot use this parameter with a mechanism that generates pre-built images. Using a license URL forces the installer to copy the source image before use. |
|
| The size of the disk in gigabytes (GB). | Any size between 16 GB and 65536 GB. |
|
| The type of disk. |
Either the default |
4.8.7.2. Sample customized install-config.yaml file for GCP
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
This sample YAML file is provided for reference only. You must obtain your install-config.yaml file by using the installation program and modify it.
- 1 8 9 10 14
- Required. The installation program prompts you for this value.
- 2 5
- If you do not provide these parameters and values, the installation program provides the default value.
- 3 6
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 4 7
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Use larger machine types, such as
n1-standard-8, for your machines if you disable simultaneous multithreading. - 11
- Specify the name of an existing VPC.
- 12
- Specify the name of the existing subnet to deploy the control plane machines to. The subnet must belong to the VPC that you specified.
- 13
- Specify the name of the existing subnet to deploy the compute machines to. The subnet must belong to the VPC that you specified.
- 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- You can optionally provide the
sshKeyvalue that you use to access the machines in your cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 17
- How to publish the user-facing endpoints of your cluster. Set
publishtoInternalto deploy a private cluster, which cannot be accessed from the Internet. The default value isExternal.
4.8.7.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.8.8. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
4.8.9. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.8.9.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.8.9.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.8.9.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.8.10. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.8.11. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.8.12. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.9. Installing a cluster on user-provisioned infrastructure in GCP by using Deployment Manager templates
In OpenShift Container Platform version 4.6, you can install a cluster on Google Cloud Platform (GCP) that uses infrastructure that you provide.
The steps for performing a user-provided infrastructure install are outlined here. Several Deployment Manager templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the cloud provider and the installation process of OpenShift Container Platform. Several Deployment Manager templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods; the templates are just an example.
4.9.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
NoteBe sure to also review this site list if you are configuring a proxy.
4.9.2. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
4.9.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.9.4. Configuring your GCP project
Before you can install OpenShift Container Platform, you must configure a Google Cloud Platform (GCP) project to host it.
4.9.4.1. Creating a GCP project
To install OpenShift Container Platform, you must create a project in your Google Cloud Platform (GCP) account to host the cluster.
Procedure
Create a project to host your OpenShift Container Platform cluster. See Creating and Managing Projects in the GCP documentation.
ImportantYour GCP project must use the Premium Network Service Tier if you are using installer-provisioned infrastructure. The Standard Network Service Tier is not supported for clusters installed using the installation program. The installation program configures internal load balancing for the
api-int.<cluster_name>.<base_domain>URL; the Premium Tier is required for internal load balancing.
4.9.4.2. Enabling API services in GCP
Your Google Cloud Platform (GCP) project requires access to several API services to complete OpenShift Container Platform installation.
Prerequisites
- You created a project to host your cluster.
Procedure
Enable the following required API services in the project that hosts your cluster. See Enabling services in the GCP documentation.
Expand Table 4.29. Required API services API service Console service name Cloud Deployment Manager V2 API
deploymentmanager.googleapis.comCompute Engine API
compute.googleapis.comGoogle Cloud APIs
cloudapis.googleapis.comCloud Resource Manager API
cloudresourcemanager.googleapis.comGoogle DNS API
dns.googleapis.comIAM Service Account Credentials API
iamcredentials.googleapis.comIdentity and Access Management (IAM) API
iam.googleapis.comService Management API
servicemanagement.googleapis.comService Usage API
serviceusage.googleapis.comGoogle Cloud Storage JSON API
storage-api.googleapis.comCloud Storage
storage-component.googleapis.com
4.9.4.3. Configuring DNS for GCP
To install OpenShift Container Platform, the Google Cloud Platform (GCP) account you use must have a dedicated public hosted zone in the same project that you host the OpenShift Container Platform cluster. This zone must be authoritative for the domain. The DNS service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through GCP or another source.
NoteIf you purchase a new domain, it can take time for the relevant DNS changes to propagate. For more information about purchasing domains through Google, see Google Domains.
Create a public hosted zone for your domain or subdomain in your GCP project. See Creating public zones in the GCP documentation.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.Extract the new authoritative name servers from the hosted zone records. See Look up your Cloud DNS name servers in the GCP documentation.
You typically have four name servers.
- Update the registrar records for the name servers that your domain uses. For example, if you registered your domain to Google Domains, see the following topic in the Google Domains Help: How to switch to custom name servers.
- If you migrated your root domain to Google Cloud DNS, migrate your DNS records. See Migrating to Cloud DNS in the GCP documentation.
- If you use a subdomain, follow your company’s procedures to add its delegation records to the parent domain. This process might include a request to your company’s IT department or the division that controls the root domain and DNS services for your company.
4.9.4.4. GCP account limits
The OpenShift Container Platform cluster uses a number of Google Cloud Platform (GCP) components, but the default Quotas do not affect your ability to install a default OpenShift Container Platform cluster.
A default cluster, which contains three compute and three control plane machines, uses the following resources. Note that some resources are required only during the bootstrap process and are removed after the cluster deploys.
| Service | Component | Location | Total resources required | Resources removed after bootstrap |
|---|---|---|---|---|
| Service account | IAM | Global | 5 | 0 |
| Firewall rules | Networking | Global | 11 | 1 |
| Forwarding rules | Compute | Global | 2 | 0 |
| Health checks | Compute | Global | 2 | 0 |
| Images | Compute | Global | 1 | 0 |
| Networks | Networking | Global | 1 | 0 |
| Routers | Networking | Global | 1 | 0 |
| Routes | Networking | Global | 2 | 0 |
| Subnetworks | Compute | Global | 2 | 0 |
| Target pools | Networking | Global | 2 | 0 |
If any of the quotas are insufficient during installation, the installation program displays an error that states both which quota was exceeded and the region.
Be sure to consider your actual cluster size, planned cluster growth, and any usage from other clusters that are associated with your account. The CPU, static IP addresses, and persistent disk SSD (storage) quotas are the ones that are most likely to be insufficient.
If you plan to deploy your cluster in one of the following regions, you will exceed the maximum storage quota and are likely to exceed the CPU quota limit:
-
asia-east2 -
asia-northeast2 -
asia-south1 -
australia-southeast1 -
europe-north1 -
europe-west2 -
europe-west3 -
europe-west6 -
northamerica-northeast1 -
southamerica-east1 -
us-west2
You can increase resource quotas from the GCP console, but you might need to file a support ticket. Be sure to plan your cluster size early so that you can allow time to resolve the support ticket before you install your OpenShift Container Platform cluster.
4.9.4.5. Creating a service account in GCP
OpenShift Container Platform requires a Google Cloud Platform (GCP) service account that provides authentication and authorization to access data in the Google APIs. If you do not have an existing IAM service account that contains the required roles in your project, you must create one.
Prerequisites
- You created a project to host your cluster.
Procedure
- Create a service account in the project that you use to host your OpenShift Container Platform cluster. See Creating a service account in the GCP documentation.
Grant the service account the appropriate permissions. You can either grant the individual permissions that follow or assign the
Ownerrole to it. See Granting roles to a service account for specific resources.NoteWhile making the service account an owner of the project is the easiest way to gain the required permissions, it means that service account has complete control over the project. You must determine if the risk that comes from offering that power is acceptable.
Create the service account key in JSON format. See Creating service account keys in the GCP documentation.
The service account key is required to create a cluster.
4.9.4.5.1. Required GCP permissions
When you attach the Owner role to the service account that you create, you grant that service account all permissions, including those that are required to install OpenShift Container Platform. To deploy an OpenShift Container Platform cluster, the service account requires the following permissions. If you deploy your cluster into an existing VPC, the service account does not require certain networking permissions, which are noted in the following lists:
Required roles for the installation program
- Compute Admin
- Security Admin
- Service Account Admin
- Service Account User
- Storage Admin
Required roles for creating network resources during installation
- DNS Administrator
Required roles for user-provisioned GCP infrastructure
- Deployment Manager Editor
- Service Account Key Admin
Optional roles
For the cluster to create new limited credentials for its Operators, add the following role:
- Service Account Key Admin
The roles are applied to the service accounts that the control plane and compute machines use:
| Account | Roles |
|---|---|
| Control Plane |
|
|
| |
|
| |
|
| |
|
| |
| Compute |
|
|
|
4.9.4.6. Supported GCP regions
You can deploy an OpenShift Container Platform cluster to the following Google Cloud Platform (GCP) regions:
-
asia-east1(Changhua County, Taiwan) -
asia-east2(Hong Kong) -
asia-northeast1(Tokyo, Japan) -
asia-northeast2(Osaka, Japan) -
asia-northeast3(Seoul, South Korea) -
asia-south1(Mumbai, India) -
asia-southeast1(Jurong West, Singapore) -
asia-southeast2(Jakarta, Indonesia) -
australia-southeast1(Sydney, Australia) -
europe-north1(Hamina, Finland) -
europe-west1(St. Ghislain, Belgium) -
europe-west2(London, England, UK) -
europe-west3(Frankfurt, Germany) -
europe-west4(Eemshaven, Netherlands) -
europe-west6(Zürich, Switzerland) -
northamerica-northeast1(Montréal, Québec, Canada) -
southamerica-east1(São Paulo, Brazil) -
us-central1(Council Bluffs, Iowa, USA) -
us-east1(Moncks Corner, South Carolina, USA) -
us-east4(Ashburn, Northern Virginia, USA) -
us-west1(The Dalles, Oregon, USA) -
us-west2(Los Angeles, California, USA) -
us-west3(Salt Lake City, Utah, USA) -
us-west4(Las Vegas, Nevada, USA)
4.9.4.7. Installing and configuring CLI tools for GCP
To install OpenShift Container Platform on Google Cloud Platform (GCP) using user-provisioned infrastructure, you must install and configure the CLI tools for GCP.
Prerequisites
- You created a project to host your cluster.
- You created a service account and granted it the required permissions.
Procedure
Install the following binaries in
$PATH:-
gcloud -
gsutil
See Install the latest Cloud SDK version in the GCP documentation.
-
Authenticate using the
gcloudtool with your configured service account.See Authorizing with a service account in the GCP documentation.
4.9.5. Creating the installation files for GCP
To install OpenShift Container Platform on Google Cloud Platform (GCP) using user-provisioned infrastructure, you must generate the files that the installation program needs to deploy your cluster and modify them so that the cluster creates only the machines that it will use. You generate and customize the install-config.yaml file, Kubernetes manifests, and Ignition config files. You also have the option to first set up a separate var partition during the preparation phases of installation.
4.9.5.1. Optional: Creating a separate /var partition
It is recommended that disk partitioning for OpenShift Container Platform be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
If you follow the steps to create a separate /var partition in this procedure, it is not necessary to create the Kubernetes manifest and Ignition config files again as described later in this section.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:openshift-install create manifests --dir $HOME/clusterconfig
$ openshift-install create manifests --dir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshift
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Confirm that the installation program created manifests in the
clusterconfig/openshiftdirectory:ls $HOME/clusterconfig/openshift/
$ ls $HOME/clusterconfig/openshift/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 MiB (Mebibytes) is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
4.9.5.2. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Google Cloud Platform (GCP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Optional: If you do not want the cluster to provision compute machines, empty the compute pool by editing the resulting
install-config.yamlfile to setreplicasto0for thecomputepool:compute: - hyperthreading: Enabled name: worker platform: {} replicas: 0compute: - hyperthreading: Enabled name: worker platform: {} replicas: 01 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Set to
0.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
4.9.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.9.5.4. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow By removing these files, you prevent the cluster from automatically generating control plane machines.
Optional: If you do not want the cluster to provision compute machines, remove the Kubernetes manifest files that define the worker machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage the worker machines yourself, you do not need to initialize these machines.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
Optional: If you do not want the Ingress Operator to create DNS records on your behalf, remove the
privateZoneandpublicZonesections from the<installation_directory>/manifests/cluster-dns-02-config.ymlDNS configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you do so, you must add ingress DNS records manually in a later step.
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.6. Exporting common variables
4.9.6.1. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in Google Cloud Platform (GCP). The infrastructure name is also used to locate the appropriate GCP resources during an OpenShift Container Platform installation. The provided Deployment Manager templates contain references to this infrastructure name, so you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
4.9.6.2. Exporting common variables for Deployment Manager templates
You must export a common set of variables that are used with the provided Deployment Manager templates used to assist in completing a user-provided infrastructure install on Google Cloud Platform (GCP).
Specific Deployment Manager templates can also require additional exported variables, which are detailed in their related procedures.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
- Generate the Ignition config files for your cluster.
-
Install the
jqpackage.
Procedure
Export the following common variables to be used by the provided Deployment Manager templates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
4.9.7. Creating a VPC in GCP
You must create a VPC in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. You can customize the VPC to meet your requirements. One way to create the VPC is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
Procedure
-
Copy the template from the Deployment Manager template for the VPC section of this topic and save it as
01_vpc.pyon your computer. This template describes the VPC that your cluster requires. Create a
01_vpc.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
regionis the region to deploy the cluster into, for exampleus-central1.- 3
master_subnet_cidris the CIDR for the master subnet, for example10.0.0.0/19.- 4
worker_subnet_cidris the CIDR for the worker subnet, for example10.0.32.0/19.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-vpc --config 01_vpc.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-vpc --config 01_vpc.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.7.1. Deployment Manager template for the VPC
You can use the following Deployment Manager template to deploy the VPC that you need for your OpenShift Container Platform cluster:
Example 4.1. 01_vpc.py Deployment Manager template
4.9.8. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 4.35. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 4.36. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
4.9.9. Creating load balancers in GCP
You must configure load balancers in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for the internal load balancer section of this topic and save it as
02_lb_int.pyon your computer. This template describes the internal load balancing objects that your cluster requires. -
For an external cluster, also copy the template from the Deployment Manager template for the external load balancer section of this topic and save it as
02_lb_ext.pyon your computer. This template describes the external load balancing objects that your cluster requires. Export the variables that the deployment template uses:
Export the cluster network location:
export CLUSTER_NETWORK=(`gcloud compute networks describe ${INFRA_ID}-network --format json | jq -r .selfLink`)$ export CLUSTER_NETWORK=(`gcloud compute networks describe ${INFRA_ID}-network --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the control plane subnet location:
export CONTROL_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-master-subnet --region=${REGION} --format json | jq -r .selfLink`)$ export CONTROL_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-master-subnet --region=${REGION} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the three zones that the cluster uses:
export ZONE_0=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[0] | cut -d "/" -f9`)$ export ZONE_0=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[0] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ZONE_1=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[1] | cut -d "/" -f9`)$ export ZONE_1=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[1] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ZONE_2=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[2] | cut -d "/" -f9`)$ export ZONE_2=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[2] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
02_infra.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1 2
- Required only when deploying an external cluster.
- 3
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 4
regionis the region to deploy the cluster into, for exampleus-central1.- 5
control_subnetis the URI to the control subnet.- 6
zonesare the zones to deploy the control plane instances into, likeus-east1-b,us-east1-c, andus-east1-d.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-infra --config 02_infra.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-infra --config 02_infra.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Export the cluster IP address:
export CLUSTER_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-ip --region=${REGION} --format json | jq -r .address`)$ export CLUSTER_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-ip --region=${REGION} --format json | jq -r .address`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also export the cluster public IP address:
export CLUSTER_PUBLIC_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-public-ip --region=${REGION} --format json | jq -r .address`)$ export CLUSTER_PUBLIC_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-public-ip --region=${REGION} --format json | jq -r .address`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.9.1. Deployment Manager template for the external load balancer
You can use the following Deployment Manager template to deploy the external load balancer that you need for your OpenShift Container Platform cluster:
Example 4.2. 02_lb_ext.py Deployment Manager template
4.9.9.2. Deployment Manager template for the internal load balancer
You can use the following Deployment Manager template to deploy the internal load balancer that you need for your OpenShift Container Platform cluster:
Example 4.3. 02_lb_int.py Deployment Manager template
You will need this template in addition to the 02_lb_ext.py template when you create an external cluster.
4.9.10. Creating a private DNS zone in GCP
You must configure a private DNS zone in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create this component is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for the private DNS section of this topic and save it as
02_dns.pyon your computer. This template describes the private DNS objects that your cluster requires. Create a
02_dns.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-dns --config 02_dns.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-dns --config 02_dns.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not create DNS entries due to limitations of Deployment Manager, so you must create them manually:
Add the internal DNS entries:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction add ${CLUSTER_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction add ${CLUSTER_IP} --name api-int.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction add ${CLUSTER_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction add ${CLUSTER_IP} --name api-int.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also add the external DNS entries:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction add ${CLUSTER_PUBLIC_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction add ${CLUSTER_PUBLIC_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.10.1. Deployment Manager template for the private DNS
You can use the following Deployment Manager template to deploy the private DNS that you need for your OpenShift Container Platform cluster:
Example 4.4. 02_dns.py Deployment Manager template
4.9.11. Creating firewall rules in GCP
You must create firewall rules in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for firewall rules section of this topic and save it as
03_firewall.pyon your computer. This template describes the security groups that your cluster requires. Create a
03_firewall.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
allowed_external_cidris the CIDR range that can access the cluster API and SSH to the bootstrap host. For an internal cluster, set this value to${NETWORK_CIDR}.- 2
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 3
cluster_networkis theselfLinkURL to the cluster network.- 4
network_cidris the CIDR of the VPC network, for example10.0.0.0/16.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-firewall --config 03_firewall.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-firewall --config 03_firewall.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.11.1. Deployment Manager template for firewall rules
You can use the following Deployment Manager template to deploy the firewall rues that you need for your OpenShift Container Platform cluster:
Example 4.5. 03_firewall.py Deployment Manager template
4.9.13. Creating the RHCOS cluster image for the GCP infrastructure
You must use a valid Red Hat Enterprise Linux CoreOS (RHCOS) image for Google Cloud Platform (GCP) for your OpenShift Container Platform nodes.
Procedure
Obtain the RHCOS image from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The file name contains the OpenShift Container Platform version number in the format
rhcos-<version>-<arch>-gcp.<arch>.tar.gz.Create the Google storage bucket:
gsutil mb gs://<bucket_name>
$ gsutil mb gs://<bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Upload the RHCOS image to the Google storage bucket:
gsutil cp <downloaded_image_file_path>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz gs://<bucket_name>
$ gsutil cp <downloaded_image_file_path>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz gs://<bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the uploaded RHCOS image location as a variable:
export IMAGE_SOURCE="gs://<bucket_name>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz"
$ export IMAGE_SOURCE="gs://<bucket_name>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the cluster image:
gcloud compute images create "${INFRA_ID}-rhcos-image" \ --source-uri="${IMAGE_SOURCE}"$ gcloud compute images create "${INFRA_ID}-rhcos-image" \ --source-uri="${IMAGE_SOURCE}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.14. Creating the bootstrap machine in GCP
You must create the bootstrap machine in Google Cloud Platform (GCP) to use during OpenShift Container Platform cluster initialization. One way to create this machine is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your bootstrap machine, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Ensure pyOpenSSL is installed.
Procedure
-
Copy the template from the Deployment Manager template for the bootstrap machine section of this topic and save it as
04_bootstrap.pyon your computer. This template describes the bootstrap machine that your cluster requires. Export the location of the Red Hat Enterprise Linux CoreOS (RHCOS) image that the installation program requires:
export CLUSTER_IMAGE=(`gcloud compute images describe ${INFRA_ID}-rhcos-image --format json | jq -r .selfLink`)$ export CLUSTER_IMAGE=(`gcloud compute images describe ${INFRA_ID}-rhcos-image --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a bucket and upload the
bootstrap.ignfile:gsutil mb gs://${INFRA_ID}-bootstrap-ignition gsutil cp <installation_directory>/bootstrap.ign gs://${INFRA_ID}-bootstrap-ignition/$ gsutil mb gs://${INFRA_ID}-bootstrap-ignition $ gsutil cp <installation_directory>/bootstrap.ign gs://${INFRA_ID}-bootstrap-ignition/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a signed URL for the bootstrap instance to use to access the Ignition config. Export the URL from the output as a variable:
export BOOTSTRAP_IGN=`gsutil signurl -d 1h service-account-key.json gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign | grep "^gs:" | awk '{print $5}'`$ export BOOTSTRAP_IGN=`gsutil signurl -d 1h service-account-key.json gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign | grep "^gs:" | awk '{print $5}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
04_bootstrap.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
regionis the region to deploy the cluster into, for exampleus-central1.- 3
zoneis the zone to deploy the bootstrap instance into, for exampleus-central1-b.- 4
cluster_networkis theselfLinkURL to the cluster network.- 5
control_subnetis theselfLinkURL to the control subnet.- 6
imageis theselfLinkURL to the RHCOS image.- 7
machine_typeis the machine type of the instance, for examplen1-standard-4.- 8
root_volume_sizeis the boot disk size for the bootstrap machine.- 9
bootstrap_ignis the URL output when creating a signed URL.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-bootstrap --config 04_bootstrap.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-bootstrap --config 04_bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not manage load balancer membership due to limitations of Deployment Manager, so you must add the bootstrap machine manually.
Add the bootstrap instance to the internal load balancer instance group:
gcloud compute instance-groups unmanaged add-instances \ ${INFRA_ID}-bootstrap-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-bootstrap$ gcloud compute instance-groups unmanaged add-instances \ ${INFRA_ID}-bootstrap-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the bootstrap instance group to the internal load balancer backend service:
gcloud compute backend-services add-backend \ ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0}$ gcloud compute backend-services add-backend \ ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.14.1. Deployment Manager template for the bootstrap machine
You can use the following Deployment Manager template to deploy the bootstrap machine that you need for your OpenShift Container Platform cluster:
Example 4.7. 04_bootstrap.py Deployment Manager template
4.9.15. Creating the control plane machines in GCP
You must create the control plane machines in Google Cloud Platform (GCP) for your cluster to use. One way to create these machines is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your control plane machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
Procedure
-
Copy the template from the Deployment Manager template for control plane machines section of this topic and save it as
05_control_plane.pyon your computer. This template describes the control plane machines that your cluster requires. Export the following variable required by the resource definition:
export MASTER_IGNITION=`cat <installation_directory>/master.ign`
$ export MASTER_IGNITION=`cat <installation_directory>/master.ign`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
05_control_plane.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
zonesare the zones to deploy the control plane instances into, for exampleus-central1-a,us-central1-b, andus-central1-c.- 3
control_subnetis theselfLinkURL to the control subnet.- 4
imageis theselfLinkURL to the RHCOS image.- 5
machine_typeis the machine type of the instance, for examplen1-standard-4.- 6
service_account_emailis the email address for the master service account that you created.- 7
ignitionis the contents of themaster.ignfile.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-control-plane --config 05_control_plane.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-control-plane --config 05_control_plane.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not manage load balancer membership due to limitations of Deployment Manager, so you must add the control plane machines manually.
Run the following commands to add the control plane machines to the appropriate instance groups:
gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_0}-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-master-0 gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_1}-instance-group --zone=${ZONE_1} --instances=${INFRA_ID}-master-1 gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_2}-instance-group --zone=${ZONE_2} --instances=${INFRA_ID}-master-2$ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_0}-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-master-0 $ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_1}-instance-group --zone=${ZONE_1} --instances=${INFRA_ID}-master-1 $ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_2}-instance-group --zone=${ZONE_2} --instances=${INFRA_ID}-master-2Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, you must also run the following commands to add the control plane machines to the target pools:
gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_0}" --instances=${INFRA_ID}-master-0 gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_1}" --instances=${INFRA_ID}-master-1 gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_2}" --instances=${INFRA_ID}-master-2$ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_0}" --instances=${INFRA_ID}-master-0 $ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_1}" --instances=${INFRA_ID}-master-1 $ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_2}" --instances=${INFRA_ID}-master-2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.15.1. Deployment Manager template for control plane machines
You can use the following Deployment Manager template to deploy the control plane machines that you need for your OpenShift Container Platform cluster:
Example 4.8. 05_control_plane.py Deployment Manager template
4.9.16. Wait for bootstrap completion and remove bootstrap resources in GCP
After you create all of the required infrastructure in Google Cloud Platform (GCP), wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
Change to the directory that contains the installation program and run the following command:
./openshift-install wait-for bootstrap-complete --dir <installation_directory> \ --log-level info$ ./openshift-install wait-for bootstrap-complete --dir <installation_directory> \1 --log-level info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command exits without a
FATALwarning, your production control plane has initialized.Delete the bootstrap resources:
gcloud compute backend-services remove-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0} gsutil rm gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign gsutil rb gs://${INFRA_ID}-bootstrap-ignition gcloud deployment-manager deployments delete ${INFRA_ID}-bootstrap$ gcloud compute backend-services remove-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0} $ gsutil rm gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign $ gsutil rb gs://${INFRA_ID}-bootstrap-ignition $ gcloud deployment-manager deployments delete ${INFRA_ID}-bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.17. Creating additional worker machines in GCP
You can create worker machines in Google Cloud Platform (GCP) for your cluster to use by launching individual instances discretely or by automated processes outside the cluster, such as auto scaling groups. You can also take advantage of the built-in cluster scaling mechanisms and the machine API in OpenShift Container Platform.
In this example, you manually launch one instance by using the Deployment Manager template. Additional instances can be launched by including additional resources of type 06_worker.py in the file.
If you do not use the provided Deployment Manager template to create your worker machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
-
Copy the template from the Deployment Manager template for worker machines section of this topic and save it as
06_worker.pyon your computer. This template describes the worker machines that your cluster requires. Export the variables that the resource definition uses.
Export the subnet that hosts the compute machines:
export COMPUTE_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-worker-subnet --region=${REGION} --format json | jq -r .selfLink`)$ export COMPUTE_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-worker-subnet --region=${REGION} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the email address for your service account:
export WORKER_SERVICE_ACCOUNT=(`gcloud iam service-accounts list --filter "email~^${INFRA_ID}-w@${PROJECT_NAME}." --format json | jq -r '.[0].email'`)$ export WORKER_SERVICE_ACCOUNT=(`gcloud iam service-accounts list --filter "email~^${INFRA_ID}-w@${PROJECT_NAME}." --format json | jq -r '.[0].email'`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the location of the compute machine Ignition config file:
export WORKER_IGNITION=`cat <installation_directory>/worker.ign`
$ export WORKER_IGNITION=`cat <installation_directory>/worker.ign`Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
06_worker.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
nameis the name of the worker machine, for exampleworker-0.- 2 9
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 3 10
zoneis the zone to deploy the worker machine into, for exampleus-central1-a.- 4 11
compute_subnetis theselfLinkURL to the compute subnet.- 5 12
imageis theselfLinkURL to the RHCOS image.- 6 13
machine_typeis the machine type of the instance, for examplen1-standard-4.- 7 14
service_account_emailis the email address for the worker service account that you created.- 8 15
ignitionis the contents of theworker.ignfile.
-
Optional: If you want to launch additional instances, include additional resources of type
06_worker.pyin your06_worker.yamlresource definition file. Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-worker --config 06_worker.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-worker --config 06_worker.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.17.1. Deployment Manager template for worker machines
You can use the following Deployment Manager template to deploy the worker machines that you need for your OpenShift Container Platform cluster:
Example 4.9. 06_worker.py Deployment Manager template
4.9.18. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.9.18.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.9.18.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.9.18.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.9.19. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.20. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
4.9.21. Optional: Adding the ingress DNS records
If you removed the DNS zone configuration when creating Kubernetes manifests and generating Ignition configs, you must manually create DNS records that point at the ingress load balancer. You can create either a wildcard *.apps.{baseDomain}. or specific records. You can use A, CNAME, and other records per your requirements.
Prerequisites
- Configure a GCP account.
- Remove the DNS Zone configuration when creating Kubernetes manifests and generating Ignition configs.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
- Create the worker machines.
Procedure
Wait for the Ingress router to create a load balancer and populate the
EXTERNAL-IPfield:oc -n openshift-ingress get service router-default
$ oc -n openshift-ingress get service router-defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.18.154 35.233.157.184 80:32288/TCP,443:31215/TCP 98
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.18.154 35.233.157.184 80:32288/TCP,443:31215/TCP 98Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the A record to your zones:
To use A records:
Export the variable for the router IP address:
export ROUTER_IP=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`$ export ROUTER_IP=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the A record to the private zones:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also add the A record to the public zones:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To add explicit domains instead of using a wildcard, create entries for each of the cluster’s current routes:
oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routes$ oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.9.22. Completing a GCP installation on user-provisioned infrastructure
After you start the OpenShift Container Platform installation on Google Cloud Platform (GCP) user-provisioned infrastructure, you can monitor the cluster events until the cluster is ready.
Prerequisites
- Deploy the bootstrap machine for an OpenShift Container Platform cluster on user-provisioned GCP infrastructure.
-
Install the
ocCLI and log in.
Procedure
Complete the cluster installation:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Observe the running state of your cluster.
Run the following command to view the current cluster version and status:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version False True 24m Working towards 4.5.4: 99% complete
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version False True 24m Working towards 4.5.4: 99% completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to view the Operators managed on the control plane by the Cluster Version Operator (CVO):
oc get clusteroperators
$ oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to view your cluster pods:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
When the current cluster version is
AVAILABLE, the installation is complete.
4.9.23. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.9.24. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.10. Installing a cluster into a shared VPC on GCP using Deployment Manager templates
In OpenShift Container Platform version 4.6, you can install a cluster into a shared Virtual Private Cloud (VPC) on Google Cloud Platform (GCP) that uses infrastructure that you provide. In this context, a cluster installed into a shared VPC is a cluster that is configured to use a VPC from a project different from where the cluster is being deployed.
A shared VPC enables an organization to connect resources from multiple projects to a common VPC network. You can communicate within the organization securely and efficiently by using internal IPs from that network. For more information about shared VPC, see Shared VPC overview in the GCP documentation.
The steps for performing a user-provided infrastructure installation into a shared VPC are outlined here. Several Deployment Manager templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the cloud provider and the installation process of OpenShift Container Platform. Several Deployment Manager templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods; the templates are just an example.
4.10.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
NoteBe sure to also review this site list if you are configuring a proxy.
4.10.2. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
4.10.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.10.4. Configuring the GCP project that hosts your cluster
Before you can install OpenShift Container Platform, you must configure a Google Cloud Platform (GCP) project to host it.
4.10.4.1. Creating a GCP project
To install OpenShift Container Platform, you must create a project in your Google Cloud Platform (GCP) account to host the cluster.
Procedure
Create a project to host your OpenShift Container Platform cluster. See Creating and Managing Projects in the GCP documentation.
ImportantYour GCP project must use the Premium Network Service Tier if you are using installer-provisioned infrastructure. The Standard Network Service Tier is not supported for clusters installed using the installation program. The installation program configures internal load balancing for the
api-int.<cluster_name>.<base_domain>URL; the Premium Tier is required for internal load balancing.
4.10.4.2. Enabling API services in GCP
Your Google Cloud Platform (GCP) project requires access to several API services to complete OpenShift Container Platform installation.
Prerequisites
- You created a project to host your cluster.
Procedure
Enable the following required API services in the project that hosts your cluster. See Enabling services in the GCP documentation.
Expand Table 4.37. Required API services API service Console service name Cloud Deployment Manager V2 API
deploymentmanager.googleapis.comCompute Engine API
compute.googleapis.comGoogle Cloud APIs
cloudapis.googleapis.comCloud Resource Manager API
cloudresourcemanager.googleapis.comGoogle DNS API
dns.googleapis.comIAM Service Account Credentials API
iamcredentials.googleapis.comIdentity and Access Management (IAM) API
iam.googleapis.comService Management API
servicemanagement.googleapis.comService Usage API
serviceusage.googleapis.comGoogle Cloud Storage JSON API
storage-api.googleapis.comCloud Storage
storage-component.googleapis.com
4.10.4.3. GCP account limits
The OpenShift Container Platform cluster uses a number of Google Cloud Platform (GCP) components, but the default Quotas do not affect your ability to install a default OpenShift Container Platform cluster.
A default cluster, which contains three compute and three control plane machines, uses the following resources. Note that some resources are required only during the bootstrap process and are removed after the cluster deploys.
| Service | Component | Location | Total resources required | Resources removed after bootstrap |
|---|---|---|---|---|
| Service account | IAM | Global | 5 | 0 |
| Firewall rules | Networking | Global | 11 | 1 |
| Forwarding rules | Compute | Global | 2 | 0 |
| Health checks | Compute | Global | 2 | 0 |
| Images | Compute | Global | 1 | 0 |
| Networks | Networking | Global | 1 | 0 |
| Routers | Networking | Global | 1 | 0 |
| Routes | Networking | Global | 2 | 0 |
| Subnetworks | Compute | Global | 2 | 0 |
| Target pools | Networking | Global | 2 | 0 |
If any of the quotas are insufficient during installation, the installation program displays an error that states both which quota was exceeded and the region.
Be sure to consider your actual cluster size, planned cluster growth, and any usage from other clusters that are associated with your account. The CPU, static IP addresses, and persistent disk SSD (storage) quotas are the ones that are most likely to be insufficient.
If you plan to deploy your cluster in one of the following regions, you will exceed the maximum storage quota and are likely to exceed the CPU quota limit:
-
asia-east2 -
asia-northeast2 -
asia-south1 -
australia-southeast1 -
europe-north1 -
europe-west2 -
europe-west3 -
europe-west6 -
northamerica-northeast1 -
southamerica-east1 -
us-west2
You can increase resource quotas from the GCP console, but you might need to file a support ticket. Be sure to plan your cluster size early so that you can allow time to resolve the support ticket before you install your OpenShift Container Platform cluster.
4.10.4.4. Creating a service account in GCP
OpenShift Container Platform requires a Google Cloud Platform (GCP) service account that provides authentication and authorization to access data in the Google APIs. If you do not have an existing IAM service account that contains the required roles in your project, you must create one.
Prerequisites
- You created a project to host your cluster.
Procedure
- Create a service account in the project that you use to host your OpenShift Container Platform cluster. See Creating a service account in the GCP documentation.
Grant the service account the appropriate permissions. You can either grant the individual permissions that follow or assign the
Ownerrole to it. See Granting roles to a service account for specific resources.NoteWhile making the service account an owner of the project is the easiest way to gain the required permissions, it means that service account has complete control over the project. You must determine if the risk that comes from offering that power is acceptable.
Create the service account key in JSON format. See Creating service account keys in the GCP documentation.
The service account key is required to create a cluster.
4.10.4.4.1. Required GCP permissions
When you attach the Owner role to the service account that you create, you grant that service account all permissions, including those that are required to install OpenShift Container Platform. To deploy an OpenShift Container Platform cluster, the service account requires the following permissions. If you deploy your cluster into an existing VPC, the service account does not require certain networking permissions, which are noted in the following lists:
Required roles for the installation program
- Compute Admin
- Security Admin
- Service Account Admin
- Service Account User
- Storage Admin
Required roles for creating network resources during installation
- DNS Administrator
Required roles for user-provisioned GCP infrastructure
- Deployment Manager Editor
- Service Account Key Admin
Optional roles
For the cluster to create new limited credentials for its Operators, add the following role:
- Service Account Key Admin
The roles are applied to the service accounts that the control plane and compute machines use:
| Account | Roles |
|---|---|
| Control Plane |
|
|
| |
|
| |
|
| |
|
| |
| Compute |
|
|
|
4.10.4.5. Supported GCP regions
You can deploy an OpenShift Container Platform cluster to the following Google Cloud Platform (GCP) regions:
-
asia-east1(Changhua County, Taiwan) -
asia-east2(Hong Kong) -
asia-northeast1(Tokyo, Japan) -
asia-northeast2(Osaka, Japan) -
asia-northeast3(Seoul, South Korea) -
asia-south1(Mumbai, India) -
asia-southeast1(Jurong West, Singapore) -
asia-southeast2(Jakarta, Indonesia) -
australia-southeast1(Sydney, Australia) -
europe-north1(Hamina, Finland) -
europe-west1(St. Ghislain, Belgium) -
europe-west2(London, England, UK) -
europe-west3(Frankfurt, Germany) -
europe-west4(Eemshaven, Netherlands) -
europe-west6(Zürich, Switzerland) -
northamerica-northeast1(Montréal, Québec, Canada) -
southamerica-east1(São Paulo, Brazil) -
us-central1(Council Bluffs, Iowa, USA) -
us-east1(Moncks Corner, South Carolina, USA) -
us-east4(Ashburn, Northern Virginia, USA) -
us-west1(The Dalles, Oregon, USA) -
us-west2(Los Angeles, California, USA) -
us-west3(Salt Lake City, Utah, USA) -
us-west4(Las Vegas, Nevada, USA)
4.10.4.6. Installing and configuring CLI tools for GCP
To install OpenShift Container Platform on Google Cloud Platform (GCP) using user-provisioned infrastructure, you must install and configure the CLI tools for GCP.
Prerequisites
- You created a project to host your cluster.
- You created a service account and granted it the required permissions.
Procedure
Install the following binaries in
$PATH:-
gcloud -
gsutil
See Install the latest Cloud SDK version in the GCP documentation.
-
Authenticate using the
gcloudtool with your configured service account.See Authorizing with a service account in the GCP documentation.
4.10.5. Configuring the GCP project that hosts your shared VPC network
If you use a shared Virtual Private Cloud (VPC) to host your OpenShift Container Platform cluster in Google Cloud Platform (GCP), you must configure the project that hosts it.
If you already have a project that hosts the shared VPC network, review this section to ensure that the project meets all of the requirements to install an OpenShift Container Platform cluster.
Procedure
- Create a project to host the shared VPC for your OpenShift Container Platform cluster. See Creating and Managing Projects in the GCP documentation.
- Create a service account in the project that hosts your shared VPC. See Creating a service account in the GCP documentation.
Grant the service account the appropriate permissions. You can either grant the individual permissions that follow or assign the
Ownerrole to it. See Granting roles to a service account for specific resources.NoteWhile making the service account an owner of the project is the easiest way to gain the required permissions, it means that service account has complete control over the project. You must determine if the risk that comes from offering that power is acceptable.
The service account for the project that hosts the shared VPC network requires the following roles:
- Compute Network User
- Compute Security Admin
- Deployment Manager Editor
- DNS Administrator
- Security Admin
- Network Management Admin
4.10.5.1. Configuring DNS for GCP
To install OpenShift Container Platform, the Google Cloud Platform (GCP) account you use must have a dedicated public hosted zone in the project that hosts the shared VPC that you install the cluster into. This zone must be authoritative for the domain. The DNS service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through GCP or another source.
NoteIf you purchase a new domain, it can take time for the relevant DNS changes to propagate. For more information about purchasing domains through Google, see Google Domains.
Create a public hosted zone for your domain or subdomain in your GCP project. See Creating public zones in the GCP documentation.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.Extract the new authoritative name servers from the hosted zone records. See Look up your Cloud DNS name servers in the GCP documentation.
You typically have four name servers.
- Update the registrar records for the name servers that your domain uses. For example, if you registered your domain to Google Domains, see the following topic in the Google Domains Help: How to switch to custom name servers.
- If you migrated your root domain to Google Cloud DNS, migrate your DNS records. See Migrating to Cloud DNS in the GCP documentation.
- If you use a subdomain, follow your company’s procedures to add its delegation records to the parent domain. This process might include a request to your company’s IT department or the division that controls the root domain and DNS services for your company.
4.10.5.2. Creating a VPC in GCP
You must create a VPC in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. You can customize the VPC to meet your requirements. One way to create the VPC is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
Procedure
-
Copy the template from the Deployment Manager template for the VPC section of this topic and save it as
01_vpc.pyon your computer. This template describes the VPC that your cluster requires. Export the following variables required by the resource definition:
Export the control plane CIDR:
export MASTER_SUBNET_CIDR='10.0.0.0/19'
$ export MASTER_SUBNET_CIDR='10.0.0.0/19'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the compute CIDR:
export WORKER_SUBNET_CIDR='10.0.32.0/19'
$ export WORKER_SUBNET_CIDR='10.0.32.0/19'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the region to deploy the VPC network and cluster to:
export REGION='<region>'
$ export REGION='<region>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Export the variable for the ID of the project that hosts the shared VPC:
export HOST_PROJECT=<host_project>
$ export HOST_PROJECT=<host_project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the variable for the email of the service account that belongs to host project:
export HOST_PROJECT_ACCOUNT=<host_service_account_email>
$ export HOST_PROJECT_ACCOUNT=<host_service_account_email>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
01_vpc.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create <vpc_deployment_name> --config 01_vpc.yaml --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}$ gcloud deployment-manager deployments create <vpc_deployment_name> --config 01_vpc.yaml --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<vpc_deployment_name>, specify the name of the VPC to deploy.
Export the VPC variable that other components require:
Export the name of the host project network:
export HOST_PROJECT_NETWORK=<vpc_network>
$ export HOST_PROJECT_NETWORK=<vpc_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the name of the host project control plane subnet:
export HOST_PROJECT_CONTROL_SUBNET=<control_plane_subnet>
$ export HOST_PROJECT_CONTROL_SUBNET=<control_plane_subnet>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the name of the host project compute subnet:
export HOST_PROJECT_COMPUTE_SUBNET=<compute_subnet>
$ export HOST_PROJECT_COMPUTE_SUBNET=<compute_subnet>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Set up the shared VPC. See Setting up Shared VPC in the GCP documentation.
4.10.5.2.1. Deployment Manager template for the VPC
You can use the following Deployment Manager template to deploy the VPC that you need for your OpenShift Container Platform cluster:
Example 4.10. 01_vpc.py Deployment Manager template
4.10.6. Creating the installation files for GCP
To install OpenShift Container Platform on Google Cloud Platform (GCP) using user-provisioned infrastructure, you must generate the files that the installation program needs to deploy your cluster and modify them so that the cluster creates only the machines that it will use. You generate and customize the install-config.yaml file, Kubernetes manifests, and Ignition config files. You also have the option to first set up a separate var partition during the preparation phases of installation.
4.10.6.1. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
4.10.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.10.6.4. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow By removing these files, you prevent the cluster from automatically generating control plane machines.
Remove the Kubernetes manifest files that define the worker machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage the worker machines yourself, you do not need to initialize these machines.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
Remove the
privateZonesections from the<installation_directory>/manifests/cluster-dns-02-config.ymlDNS configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Remove this section completely.
Configure the cloud provider for your VPC.
-
Open the
<installation_directory>/manifests/cloud-provider-config.yamlfile. -
Add the
network-project-idparameter and set its value to the ID of project that hosts the shared VPC network. -
Add the
network-nameparameter and set its value to the name of the shared VPC network that hosts the OpenShift Container Platform cluster. -
Replace the value of the
subnetwork-nameparameter with the value of the shared VPC subnet that hosts your compute machines.
The contents of the
<installation_directory>/manifests/cloud-provider-config.yamlresemble the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Open the
If you deploy a cluster that is not on a private network, open the
<installation_directory>/manifests/cluster-ingress-default-ingresscontroller.yamlfile and replace the value of thescopeparameter withExternal. The contents of the file resemble the following example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.7. Exporting common variables
4.10.7.1. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in Google Cloud Platform (GCP). The infrastructure name is also used to locate the appropriate GCP resources during an OpenShift Container Platform installation. The provided Deployment Manager templates contain references to this infrastructure name, so you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
4.10.7.2. Exporting common variables for Deployment Manager templates
You must export a common set of variables that are used with the provided Deployment Manager templates used to assist in completing a user-provided infrastructure install on Google Cloud Platform (GCP).
Specific Deployment Manager templates can also require additional exported variables, which are detailed in their related procedures.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
- Generate the Ignition config files for your cluster.
-
Install the
jqpackage.
Procedure
- Export the following common variables to be used by the provided Deployment Manager templates:
4.10.8. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 4.43. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 4.44. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
4.10.9. Creating load balancers in GCP
You must configure load balancers in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for the internal load balancer section of this topic and save it as
02_lb_int.pyon your computer. This template describes the internal load balancing objects that your cluster requires. -
For an external cluster, also copy the template from the Deployment Manager template for the external load balancer section of this topic and save it as
02_lb_ext.pyon your computer. This template describes the external load balancing objects that your cluster requires. Export the variables that the deployment template uses:
Export the cluster network location:
export CLUSTER_NETWORK=(`gcloud compute networks describe ${HOST_PROJECT_NETWORK} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} --format json | jq -r .selfLink`)$ export CLUSTER_NETWORK=(`gcloud compute networks describe ${HOST_PROJECT_NETWORK} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the control plane subnet location:
export CONTROL_SUBNET=(`gcloud compute networks subnets describe ${HOST_PROJECT_CONTROL_SUBNET} --region=${REGION} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} --format json | jq -r .selfLink`)$ export CONTROL_SUBNET=(`gcloud compute networks subnets describe ${HOST_PROJECT_CONTROL_SUBNET} --region=${REGION} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the three zones that the cluster uses:
export ZONE_0=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[0] | cut -d "/" -f9`)$ export ZONE_0=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[0] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ZONE_1=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[1] | cut -d "/" -f9`)$ export ZONE_1=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[1] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ZONE_2=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[2] | cut -d "/" -f9`)$ export ZONE_2=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[2] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
02_infra.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1 2
- Required only when deploying an external cluster.
- 3
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 4
regionis the region to deploy the cluster into, for exampleus-central1.- 5
control_subnetis the URI to the control subnet.- 6
zonesare the zones to deploy the control plane instances into, likeus-east1-b,us-east1-c, andus-east1-d.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-infra --config 02_infra.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-infra --config 02_infra.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Export the cluster IP address:
export CLUSTER_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-ip --region=${REGION} --format json | jq -r .address`)$ export CLUSTER_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-ip --region=${REGION} --format json | jq -r .address`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also export the cluster public IP address:
export CLUSTER_PUBLIC_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-public-ip --region=${REGION} --format json | jq -r .address`)$ export CLUSTER_PUBLIC_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-public-ip --region=${REGION} --format json | jq -r .address`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.9.1. Deployment Manager template for the external load balancer
You can use the following Deployment Manager template to deploy the external load balancer that you need for your OpenShift Container Platform cluster:
Example 4.11. 02_lb_ext.py Deployment Manager template
4.10.9.2. Deployment Manager template for the internal load balancer
You can use the following Deployment Manager template to deploy the internal load balancer that you need for your OpenShift Container Platform cluster:
Example 4.12. 02_lb_int.py Deployment Manager template
You will need this template in addition to the 02_lb_ext.py template when you create an external cluster.
4.10.10. Creating a private DNS zone in GCP
You must configure a private DNS zone in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create this component is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for the private DNS section of this topic and save it as
02_dns.pyon your computer. This template describes the private DNS objects that your cluster requires. Create a
02_dns.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-dns --config 02_dns.yaml --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}$ gcloud deployment-manager deployments create ${INFRA_ID}-dns --config 02_dns.yaml --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}Copy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not create DNS entries due to limitations of Deployment Manager, so you must create them manually:
Add the internal DNS entries:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction add ${CLUSTER_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction add ${CLUSTER_IP} --name api-int.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction add ${CLUSTER_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction add ${CLUSTER_IP} --name api-int.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also add the external DNS entries:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud --account=${HOST_PROJECT_ACCOUNT} --project=${HOST_PROJECT} dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} gcloud --account=${HOST_PROJECT_ACCOUNT} --project=${HOST_PROJECT} dns record-sets transaction add ${CLUSTER_PUBLIC_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${BASE_DOMAIN_ZONE_NAME} gcloud --account=${HOST_PROJECT_ACCOUNT} --project=${HOST_PROJECT} dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud --account=${HOST_PROJECT_ACCOUNT} --project=${HOST_PROJECT} dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud --account=${HOST_PROJECT_ACCOUNT} --project=${HOST_PROJECT} dns record-sets transaction add ${CLUSTER_PUBLIC_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud --account=${HOST_PROJECT_ACCOUNT} --project=${HOST_PROJECT} dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.10.1. Deployment Manager template for the private DNS
You can use the following Deployment Manager template to deploy the private DNS that you need for your OpenShift Container Platform cluster:
Example 4.13. 02_dns.py Deployment Manager template
4.10.11. Creating firewall rules in GCP
You must create firewall rules in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for firewall rules section of this topic and save it as
03_firewall.pyon your computer. This template describes the security groups that your cluster requires. Create a
03_firewall.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
allowed_external_cidris the CIDR range that can access the cluster API and SSH to the bootstrap host. For an internal cluster, set this value to${NETWORK_CIDR}.- 2
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 3
cluster_networkis theselfLinkURL to the cluster network.- 4
network_cidris the CIDR of the VPC network, for example10.0.0.0/16.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-firewall --config 03_firewall.yaml --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}$ gcloud deployment-manager deployments create ${INFRA_ID}-firewall --config 03_firewall.yaml --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.11.1. Deployment Manager template for firewall rules
You can use the following Deployment Manager template to deploy the firewall rues that you need for your OpenShift Container Platform cluster:
Example 4.14. 03_firewall.py Deployment Manager template
4.10.13. Creating the RHCOS cluster image for the GCP infrastructure
You must use a valid Red Hat Enterprise Linux CoreOS (RHCOS) image for Google Cloud Platform (GCP) for your OpenShift Container Platform nodes.
Procedure
Obtain the RHCOS image from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The file name contains the OpenShift Container Platform version number in the format
rhcos-<version>-<arch>-gcp.<arch>.tar.gz.Create the Google storage bucket:
gsutil mb gs://<bucket_name>
$ gsutil mb gs://<bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Upload the RHCOS image to the Google storage bucket:
gsutil cp <downloaded_image_file_path>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz gs://<bucket_name>
$ gsutil cp <downloaded_image_file_path>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz gs://<bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the uploaded RHCOS image location as a variable:
export IMAGE_SOURCE="gs://<bucket_name>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz"
$ export IMAGE_SOURCE="gs://<bucket_name>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the cluster image:
gcloud compute images create "${INFRA_ID}-rhcos-image" \ --source-uri="${IMAGE_SOURCE}"$ gcloud compute images create "${INFRA_ID}-rhcos-image" \ --source-uri="${IMAGE_SOURCE}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.14. Creating the bootstrap machine in GCP
You must create the bootstrap machine in Google Cloud Platform (GCP) to use during OpenShift Container Platform cluster initialization. One way to create this machine is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your bootstrap machine, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Ensure pyOpenSSL is installed.
Procedure
-
Copy the template from the Deployment Manager template for the bootstrap machine section of this topic and save it as
04_bootstrap.pyon your computer. This template describes the bootstrap machine that your cluster requires. Export the location of the Red Hat Enterprise Linux CoreOS (RHCOS) image that the installation program requires:
export CLUSTER_IMAGE=(`gcloud compute images describe ${INFRA_ID}-rhcos-image --format json | jq -r .selfLink`)$ export CLUSTER_IMAGE=(`gcloud compute images describe ${INFRA_ID}-rhcos-image --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a bucket and upload the
bootstrap.ignfile:gsutil mb gs://${INFRA_ID}-bootstrap-ignition gsutil cp <installation_directory>/bootstrap.ign gs://${INFRA_ID}-bootstrap-ignition/$ gsutil mb gs://${INFRA_ID}-bootstrap-ignition $ gsutil cp <installation_directory>/bootstrap.ign gs://${INFRA_ID}-bootstrap-ignition/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a signed URL for the bootstrap instance to use to access the Ignition config. Export the URL from the output as a variable:
export BOOTSTRAP_IGN=`gsutil signurl -d 1h service-account-key.json gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign | grep "^gs:" | awk '{print $5}'`$ export BOOTSTRAP_IGN=`gsutil signurl -d 1h service-account-key.json gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign | grep "^gs:" | awk '{print $5}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
04_bootstrap.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
regionis the region to deploy the cluster into, for exampleus-central1.- 3
zoneis the zone to deploy the bootstrap instance into, for exampleus-central1-b.- 4
cluster_networkis theselfLinkURL to the cluster network.- 5
control_subnetis theselfLinkURL to the control subnet.- 6
imageis theselfLinkURL to the RHCOS image.- 7
machine_typeis the machine type of the instance, for examplen1-standard-4.- 8
root_volume_sizeis the boot disk size for the bootstrap machine.- 9
bootstrap_ignis the URL output when creating a signed URL.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-bootstrap --config 04_bootstrap.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-bootstrap --config 04_bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the bootstrap instance to the internal load balancer instance group:
gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-bootstrap-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-bootstrap$ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-bootstrap-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the bootstrap instance group to the internal load balancer backend service:
gcloud compute backend-services add-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0}$ gcloud compute backend-services add-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.14.1. Deployment Manager template for the bootstrap machine
You can use the following Deployment Manager template to deploy the bootstrap machine that you need for your OpenShift Container Platform cluster:
Example 4.16. 04_bootstrap.py Deployment Manager template
4.10.15. Creating the control plane machines in GCP
You must create the control plane machines in Google Cloud Platform (GCP) for your cluster to use. One way to create these machines is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your control plane machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
Procedure
-
Copy the template from the Deployment Manager template for control plane machines section of this topic and save it as
05_control_plane.pyon your computer. This template describes the control plane machines that your cluster requires. Export the following variable required by the resource definition:
export MASTER_IGNITION=`cat <installation_directory>/master.ign`
$ export MASTER_IGNITION=`cat <installation_directory>/master.ign`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
05_control_plane.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
zonesare the zones to deploy the control plane instances into, for exampleus-central1-a,us-central1-b, andus-central1-c.- 3
control_subnetis theselfLinkURL to the control subnet.- 4
imageis theselfLinkURL to the RHCOS image.- 5
machine_typeis the machine type of the instance, for examplen1-standard-4.- 6
service_account_emailis the email address for the master service account that you created.- 7
ignitionis the contents of themaster.ignfile.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-control-plane --config 05_control_plane.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-control-plane --config 05_control_plane.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not manage load balancer membership due to limitations of Deployment Manager, so you must add the control plane machines manually.
Run the following commands to add the control plane machines to the appropriate instance groups:
gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_0}-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-master-0 gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_1}-instance-group --zone=${ZONE_1} --instances=${INFRA_ID}-master-1 gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_2}-instance-group --zone=${ZONE_2} --instances=${INFRA_ID}-master-2$ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_0}-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-master-0 $ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_1}-instance-group --zone=${ZONE_1} --instances=${INFRA_ID}-master-1 $ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_2}-instance-group --zone=${ZONE_2} --instances=${INFRA_ID}-master-2Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, you must also run the following commands to add the control plane machines to the target pools:
gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_0}" --instances=${INFRA_ID}-master-0 gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_1}" --instances=${INFRA_ID}-master-1 gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_2}" --instances=${INFRA_ID}-master-2$ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_0}" --instances=${INFRA_ID}-master-0 $ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_1}" --instances=${INFRA_ID}-master-1 $ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_2}" --instances=${INFRA_ID}-master-2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.15.1. Deployment Manager template for control plane machines
You can use the following Deployment Manager template to deploy the control plane machines that you need for your OpenShift Container Platform cluster:
Example 4.17. 05_control_plane.py Deployment Manager template
4.10.16. Wait for bootstrap completion and remove bootstrap resources in GCP
After you create all of the required infrastructure in Google Cloud Platform (GCP), wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
Change to the directory that contains the installation program and run the following command:
./openshift-install wait-for bootstrap-complete --dir <installation_directory> \ --log-level info$ ./openshift-install wait-for bootstrap-complete --dir <installation_directory> \1 --log-level info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command exits without a
FATALwarning, your production control plane has initialized.Delete the bootstrap resources:
gcloud compute backend-services remove-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0} gsutil rm gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign gsutil rb gs://${INFRA_ID}-bootstrap-ignition gcloud deployment-manager deployments delete ${INFRA_ID}-bootstrap$ gcloud compute backend-services remove-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0} $ gsutil rm gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign $ gsutil rb gs://${INFRA_ID}-bootstrap-ignition $ gcloud deployment-manager deployments delete ${INFRA_ID}-bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.17. Creating additional worker machines in GCP
You can create worker machines in Google Cloud Platform (GCP) for your cluster to use by launching individual instances discretely or by automated processes outside the cluster, such as auto scaling groups. You can also take advantage of the built-in cluster scaling mechanisms and the machine API in OpenShift Container Platform.
In this example, you manually launch one instance by using the Deployment Manager template. Additional instances can be launched by including additional resources of type 06_worker.py in the file.
If you do not use the provided Deployment Manager template to create your worker machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
-
Copy the template from the Deployment Manager template for worker machines section of this topic and save it as
06_worker.pyon your computer. This template describes the worker machines that your cluster requires. Export the variables that the resource definition uses.
Export the subnet that hosts the compute machines:
export COMPUTE_SUBNET=(`gcloud compute networks subnets describe ${HOST_PROJECT_COMPUTE_SUBNET} --region=${REGION} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} --format json | jq -r .selfLink`)$ export COMPUTE_SUBNET=(`gcloud compute networks subnets describe ${HOST_PROJECT_COMPUTE_SUBNET} --region=${REGION} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the email address for your service account:
export WORKER_SERVICE_ACCOUNT=(`gcloud iam service-accounts list --filter "email~^${INFRA_ID}-w@${PROJECT_NAME}." --format json | jq -r '.[0].email'`)$ export WORKER_SERVICE_ACCOUNT=(`gcloud iam service-accounts list --filter "email~^${INFRA_ID}-w@${PROJECT_NAME}." --format json | jq -r '.[0].email'`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the location of the compute machine Ignition config file:
export WORKER_IGNITION=`cat <installation_directory>/worker.ign`
$ export WORKER_IGNITION=`cat <installation_directory>/worker.ign`Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
06_worker.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
nameis the name of the worker machine, for exampleworker-0.- 2 9
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 3 10
zoneis the zone to deploy the worker machine into, for exampleus-central1-a.- 4 11
compute_subnetis theselfLinkURL to the compute subnet.- 5 12
imageis theselfLinkURL to the RHCOS image.- 6 13
machine_typeis the machine type of the instance, for examplen1-standard-4.- 7 14
service_account_emailis the email address for the worker service account that you created.- 8 15
ignitionis the contents of theworker.ignfile.
-
Optional: If you want to launch additional instances, include additional resources of type
06_worker.pyin your06_worker.yamlresource definition file. Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-worker --config 06_worker.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-worker --config 06_worker.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.17.1. Deployment Manager template for worker machines
You can use the following Deployment Manager template to deploy the worker machines that you need for your OpenShift Container Platform cluster:
Example 4.18. 06_worker.py Deployment Manager template
4.10.18. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
4.10.18.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.10.18.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>4.10.18.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>4.10.19. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.20. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
4.10.21. Adding the ingress DNS records
DNS zone configuration is removed when creating Kubernetes manifests and generating Ignition configs. You must manually create DNS records that point at the ingress load balancer. You can create either a wildcard *.apps.{baseDomain}. or specific records. You can use A, CNAME, and other records per your requirements.
Prerequisites
- Configure a GCP account.
- Remove the DNS Zone configuration when creating Kubernetes manifests and generating Ignition configs.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
- Create the worker machines.
Procedure
Wait for the Ingress router to create a load balancer and populate the
EXTERNAL-IPfield:oc -n openshift-ingress get service router-default
$ oc -n openshift-ingress get service router-defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.18.154 35.233.157.184 80:32288/TCP,443:31215/TCP 98
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.18.154 35.233.157.184 80:32288/TCP,443:31215/TCP 98Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the A record to your zones:
To use A records:
Export the variable for the router IP address:
export ROUTER_IP=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`$ export ROUTER_IP=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the A record to the private zones:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also add the A record to the public zones:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${BASE_DOMAIN_ZONE_NAME} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${BASE_DOMAIN_ZONE_NAME} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT} $ gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME} --project ${HOST_PROJECT} --account ${HOST_PROJECT_ACCOUNT}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To add explicit domains instead of using a wildcard, create entries for each of the cluster’s current routes:
oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routes$ oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.10.22. Adding ingress firewall rules
The cluster requires several firewall rules. If you do not use a shared VPC, these rules are created by the ingress controller via the GCP cloud provider. When you use a shared VPC, you can either create cluster-wide firewall rules for all services now or create each rule based on events, when the cluster requests access. By creating each rule when the cluster requests access, you know exactly which firewall rules are required. By creating cluster-wide firewall rules, you can apply the same rule set across multiple clusters.
If you choose to create each rule based on events, you must create firewall rules after you provision the cluster and during the life of the cluster when the console notifies you that rules are missing. Events that are similar to the following event are displayed, and you must add the firewall rules that are required:
oc get events -n openshift-ingress --field-selector="reason=LoadBalancerManualChange"
$ oc get events -n openshift-ingress --field-selector="reason=LoadBalancerManualChange"Example output
Firewall change required by security admin: `gcloud compute firewall-rules create k8s-fw-a26e631036a3f46cba28f8df67266d55 --network example-network --description "{\"kubernetes.io/service-name\":\"openshift-ingress/router-default\", \"kubernetes.io/service-ip\":\"35.237.236.234\"}\" --allow tcp:443,tcp:80 --source-ranges 0.0.0.0/0 --target-tags exampl-fqzq7-master,exampl-fqzq7-worker --project example-project`
Firewall change required by security admin: `gcloud compute firewall-rules create k8s-fw-a26e631036a3f46cba28f8df67266d55 --network example-network --description "{\"kubernetes.io/service-name\":\"openshift-ingress/router-default\", \"kubernetes.io/service-ip\":\"35.237.236.234\"}\" --allow tcp:443,tcp:80 --source-ranges 0.0.0.0/0 --target-tags exampl-fqzq7-master,exampl-fqzq7-worker --project example-project`If you encounter issues when creating these rule-based events, you can configure the cluster-wide firewall rules while your cluster is running.
4.10.23. Completing a GCP installation on user-provisioned infrastructure
After you start the OpenShift Container Platform installation on Google Cloud Platform (GCP) user-provisioned infrastructure, you can monitor the cluster events until the cluster is ready.
Prerequisites
- Deploy the bootstrap machine for an OpenShift Container Platform cluster on user-provisioned GCP infrastructure.
-
Install the
ocCLI and log in.
Procedure
Complete the cluster installation:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Observe the running state of your cluster.
Run the following command to view the current cluster version and status:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version False True 24m Working towards 4.5.4: 99% complete
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version False True 24m Working towards 4.5.4: 99% completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to view the Operators managed on the control plane by the Cluster Version Operator (CVO):
oc get clusteroperators
$ oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to view your cluster pods:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
When the current cluster version is
AVAILABLE, the installation is complete.
4.10.24. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.10.25. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
4.11. Installing a cluster on GCP in a restricted network with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on Google Cloud Platform (GCP) that uses infrastructure that you provide and an internal mirror of the installation release content.
While you can install an OpenShift Container Platform cluster by using mirrored installation release content, your cluster still requires internet access to use the GCP APIs.
The steps for performing a user-provided infrastructure install are outlined here. Several Deployment Manager templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the cloud provider and the installation process of OpenShift Container Platform. Several Deployment Manager templates are provided to assist in completing these steps or to help model your own. You are also free to create the required resources through other methods; the templates are just an example.
4.11.1. Prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
- Review details about the OpenShift Container Platform installation and update processes.
-
If you use a firewall, you must configure it to allow the sites that your cluster requires access to. While you might need to grant access to more sites, you must grant access to
*.googleapis.comandaccounts.google.com. - If you do not allow the system to manage identity and access management (IAM), then a cluster administrator can manually create and maintain IAM credentials. Manual mode can also be used in environments where the cloud IAM APIs are not reachable.
4.11.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
4.11.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
4.11.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
4.11.4. Configuring your GCP project
Before you can install OpenShift Container Platform, you must configure a Google Cloud Platform (GCP) project to host it.
4.11.4.1. Creating a GCP project
To install OpenShift Container Platform, you must create a project in your Google Cloud Platform (GCP) account to host the cluster.
Procedure
Create a project to host your OpenShift Container Platform cluster. See Creating and Managing Projects in the GCP documentation.
ImportantYour GCP project must use the Premium Network Service Tier if you are using installer-provisioned infrastructure. The Standard Network Service Tier is not supported for clusters installed using the installation program. The installation program configures internal load balancing for the
api-int.<cluster_name>.<base_domain>URL; the Premium Tier is required for internal load balancing.
4.11.4.2. Enabling API services in GCP
Your Google Cloud Platform (GCP) project requires access to several API services to complete OpenShift Container Platform installation.
Prerequisites
- You created a project to host your cluster.
Procedure
Enable the following required API services in the project that hosts your cluster. See Enabling services in the GCP documentation.
Expand Table 4.45. Required API services API service Console service name Compute Engine API
compute.googleapis.comGoogle Cloud APIs
cloudapis.googleapis.comCloud Resource Manager API
cloudresourcemanager.googleapis.comGoogle DNS API
dns.googleapis.comIAM Service Account Credentials API
iamcredentials.googleapis.comIdentity and Access Management (IAM) API
iam.googleapis.comService Management API
servicemanagement.googleapis.comService Usage API
serviceusage.googleapis.comGoogle Cloud Storage JSON API
storage-api.googleapis.comCloud Storage
storage-component.googleapis.com
4.11.4.3. Configuring DNS for GCP
To install OpenShift Container Platform, the Google Cloud Platform (GCP) account you use must have a dedicated public hosted zone in the same project that you host the OpenShift Container Platform cluster. This zone must be authoritative for the domain. The DNS service provides cluster DNS resolution and name lookup for external connections to the cluster.
Procedure
Identify your domain, or subdomain, and registrar. You can transfer an existing domain and registrar or obtain a new one through GCP or another source.
NoteIf you purchase a new domain, it can take time for the relevant DNS changes to propagate. For more information about purchasing domains through Google, see Google Domains.
Create a public hosted zone for your domain or subdomain in your GCP project. See Creating public zones in the GCP documentation.
Use an appropriate root domain, such as
openshiftcorp.com, or subdomain, such asclusters.openshiftcorp.com.Extract the new authoritative name servers from the hosted zone records. See Look up your Cloud DNS name servers in the GCP documentation.
You typically have four name servers.
- Update the registrar records for the name servers that your domain uses. For example, if you registered your domain to Google Domains, see the following topic in the Google Domains Help: How to switch to custom name servers.
- If you migrated your root domain to Google Cloud DNS, migrate your DNS records. See Migrating to Cloud DNS in the GCP documentation.
- If you use a subdomain, follow your company’s procedures to add its delegation records to the parent domain. This process might include a request to your company’s IT department or the division that controls the root domain and DNS services for your company.
4.11.4.4. GCP account limits
The OpenShift Container Platform cluster uses a number of Google Cloud Platform (GCP) components, but the default Quotas do not affect your ability to install a default OpenShift Container Platform cluster.
A default cluster, which contains three compute and three control plane machines, uses the following resources. Note that some resources are required only during the bootstrap process and are removed after the cluster deploys.
| Service | Component | Location | Total resources required | Resources removed after bootstrap |
|---|---|---|---|---|
| Service account | IAM | Global | 5 | 0 |
| Firewall rules | Networking | Global | 11 | 1 |
| Forwarding rules | Compute | Global | 2 | 0 |
| Health checks | Compute | Global | 2 | 0 |
| Images | Compute | Global | 1 | 0 |
| Networks | Networking | Global | 1 | 0 |
| Routers | Networking | Global | 1 | 0 |
| Routes | Networking | Global | 2 | 0 |
| Subnetworks | Compute | Global | 2 | 0 |
| Target pools | Networking | Global | 2 | 0 |
If any of the quotas are insufficient during installation, the installation program displays an error that states both which quota was exceeded and the region.
Be sure to consider your actual cluster size, planned cluster growth, and any usage from other clusters that are associated with your account. The CPU, static IP addresses, and persistent disk SSD (storage) quotas are the ones that are most likely to be insufficient.
If you plan to deploy your cluster in one of the following regions, you will exceed the maximum storage quota and are likely to exceed the CPU quota limit:
-
asia-east2 -
asia-northeast2 -
asia-south1 -
australia-southeast1 -
europe-north1 -
europe-west2 -
europe-west3 -
europe-west6 -
northamerica-northeast1 -
southamerica-east1 -
us-west2
You can increase resource quotas from the GCP console, but you might need to file a support ticket. Be sure to plan your cluster size early so that you can allow time to resolve the support ticket before you install your OpenShift Container Platform cluster.
4.11.4.5. Creating a service account in GCP
OpenShift Container Platform requires a Google Cloud Platform (GCP) service account that provides authentication and authorization to access data in the Google APIs. If you do not have an existing IAM service account that contains the required roles in your project, you must create one.
Prerequisites
- You created a project to host your cluster.
Procedure
- Create a service account in the project that you use to host your OpenShift Container Platform cluster. See Creating a service account in the GCP documentation.
Grant the service account the appropriate permissions. You can either grant the individual permissions that follow or assign the
Ownerrole to it. See Granting roles to a service account for specific resources.NoteWhile making the service account an owner of the project is the easiest way to gain the required permissions, it means that service account has complete control over the project. You must determine if the risk that comes from offering that power is acceptable.
Create the service account key in JSON format. See Creating service account keys in the GCP documentation.
The service account key is required to create a cluster.
4.11.4.5.1. Required GCP permissions
When you attach the Owner role to the service account that you create, you grant that service account all permissions, including those that are required to install OpenShift Container Platform. To deploy an OpenShift Container Platform cluster, the service account requires the following permissions. If you deploy your cluster into an existing VPC, the service account does not require certain networking permissions, which are noted in the following lists:
Required roles for the installation program
- Compute Admin
- Security Admin
- Service Account Admin
- Service Account User
- Storage Admin
Required roles for creating network resources during installation
- DNS Administrator
Required roles for user-provisioned GCP infrastructure
- Deployment Manager Editor
- Service Account Key Admin
Optional roles
For the cluster to create new limited credentials for its Operators, add the following role:
- Service Account Key Admin
The roles are applied to the service accounts that the control plane and compute machines use:
| Account | Roles |
|---|---|
| Control Plane |
|
|
| |
|
| |
|
| |
|
| |
| Compute |
|
|
|
4.11.4.6. Supported GCP regions
You can deploy an OpenShift Container Platform cluster to the following Google Cloud Platform (GCP) regions:
-
asia-east1(Changhua County, Taiwan) -
asia-east2(Hong Kong) -
asia-northeast1(Tokyo, Japan) -
asia-northeast2(Osaka, Japan) -
asia-northeast3(Seoul, South Korea) -
asia-south1(Mumbai, India) -
asia-southeast1(Jurong West, Singapore) -
asia-southeast2(Jakarta, Indonesia) -
australia-southeast1(Sydney, Australia) -
europe-north1(Hamina, Finland) -
europe-west1(St. Ghislain, Belgium) -
europe-west2(London, England, UK) -
europe-west3(Frankfurt, Germany) -
europe-west4(Eemshaven, Netherlands) -
europe-west6(Zürich, Switzerland) -
northamerica-northeast1(Montréal, Québec, Canada) -
southamerica-east1(São Paulo, Brazil) -
us-central1(Council Bluffs, Iowa, USA) -
us-east1(Moncks Corner, South Carolina, USA) -
us-east4(Ashburn, Northern Virginia, USA) -
us-west1(The Dalles, Oregon, USA) -
us-west2(Los Angeles, California, USA) -
us-west3(Salt Lake City, Utah, USA) -
us-west4(Las Vegas, Nevada, USA)
4.11.4.7. Installing and configuring CLI tools for GCP
To install OpenShift Container Platform on Google Cloud Platform (GCP) using user-provisioned infrastructure, you must install and configure the CLI tools for GCP.
Prerequisites
- You created a project to host your cluster.
- You created a service account and granted it the required permissions.
Procedure
Install the following binaries in
$PATH:-
gcloud -
gsutil
See Install the latest Cloud SDK version in the GCP documentation.
-
Authenticate using the
gcloudtool with your configured service account.See Authorizing with a service account in the GCP documentation.
4.11.5. Creating the installation files for GCP
To install OpenShift Container Platform on Google Cloud Platform (GCP) using user-provisioned infrastructure, you must generate the files that the installation program needs to deploy your cluster and modify them so that the cluster creates only the machines that it will use. You generate and customize the install-config.yaml file, Kubernetes manifests, and Ignition config files. You also have the option to first set up a separate var partition during the preparation phases of installation.
4.11.5.1. Optional: Creating a separate /var partition
It is recommended that disk partitioning for OpenShift Container Platform be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
If you follow the steps to create a separate /var partition in this procedure, it is not necessary to create the Kubernetes manifest and Ignition config files again as described later in this section.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:openshift-install create manifests --dir $HOME/clusterconfig
$ openshift-install create manifests --dir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshift
? SSH Public Key ... INFO Credentials loaded from the "myprofile" profile in file "/home/myuser/.aws/credentials" INFO Consuming Install Config from target directory INFO Manifests created in: $HOME/clusterconfig/manifests and $HOME/clusterconfig/openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: Confirm that the installation program created manifests in the
clusterconfig/openshiftdirectory:ls $HOME/clusterconfig/openshift/
$ ls $HOME/clusterconfig/openshift/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...
99_kubeadmin-password-secret.yaml 99_openshift-cluster-api_master-machines-0.yaml 99_openshift-cluster-api_master-machines-1.yaml 99_openshift-cluster-api_master-machines-2.yaml ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 MiB (Mebibytes) is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
4.11.5.2. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Google Cloud Platform (GCP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
Have the
imageContentSourcesvalues that were generated during mirror registry creation. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select gcp as the platform to target.
- If you have not configured the service account key for your GCP account on your computer, you must obtain it from GCP and paste the contents of the file or enter the absolute path to the file.
- Select the project ID to provision the cluster in. The default value is specified by the service account that you configured.
- Select the region to deploy the cluster to.
- Select the base domain to deploy the cluster to. The base domain corresponds to the public DNS zone that you created for your cluster.
- Enter a descriptive name for your cluster.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<mirror_host_name>, specify the registry domain name that you specified in the certificate for your mirror registry, and for<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.
Define the network and subnets for the VPC to install the cluster in under the parent
platform.gcpfield:network: <existing_vpc> controlPlaneSubnet: <control_plane_subnet> computeSubnet: <compute_subnet>
network: <existing_vpc> controlPlaneSubnet: <control_plane_subnet> computeSubnet: <compute_subnet>Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
platform.gcp.network, specify the name for the existing Google VPC. Forplatform.gcp.controlPlaneSubnetandplatform.gcp.computeSubnet, specify the existing subnets to deploy the control plane machines and compute machines, respectively.Add the image content resources, which look like this excerpt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To complete these values, use the
imageContentSourcesthat you recorded during mirror registry creation.
-
Make any other modifications to the
install-config.yamlfile that you require. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
4.11.5.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
4.11.5.4. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program. For a restricted network installation, these files are on your mirror host.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_master-machines-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow By removing these files, you prevent the cluster from automatically generating control plane machines.
Optional: If you do not want the cluster to provision compute machines, remove the Kubernetes manifest files that define the worker machines:
rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f <installation_directory>/openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage the worker machines yourself, you do not need to initialize these machines.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
Optional: If you do not want the Ingress Operator to create DNS records on your behalf, remove the
privateZoneandpublicZonesections from the<installation_directory>/manifests/cluster-dns-02-config.ymlDNS configuration file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you do so, you must add ingress DNS records manually in a later step.
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.6. Exporting common variables
4.11.6.1. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in Google Cloud Platform (GCP). The infrastructure name is also used to locate the appropriate GCP resources during an OpenShift Container Platform installation. The provided Deployment Manager templates contain references to this infrastructure name, so you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
4.11.6.2. Exporting common variables for Deployment Manager templates
You must export a common set of variables that are used with the provided Deployment Manager templates used to assist in completing a user-provided infrastructure install on Google Cloud Platform (GCP).
Specific Deployment Manager templates can also require additional exported variables, which are detailed in their related procedures.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
- Generate the Ignition config files for your cluster.
-
Install the
jqpackage.
Procedure
Export the following common variables to be used by the provided Deployment Manager templates:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
4.11.7. Creating a VPC in GCP
You must create a VPC in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. You can customize the VPC to meet your requirements. One way to create the VPC is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
Procedure
-
Copy the template from the Deployment Manager template for the VPC section of this topic and save it as
01_vpc.pyon your computer. This template describes the VPC that your cluster requires. Create a
01_vpc.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
regionis the region to deploy the cluster into, for exampleus-central1.- 3
master_subnet_cidris the CIDR for the master subnet, for example10.0.0.0/19.- 4
worker_subnet_cidris the CIDR for the worker subnet, for example10.0.32.0/19.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-vpc --config 01_vpc.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-vpc --config 01_vpc.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.7.1. Deployment Manager template for the VPC
You can use the following Deployment Manager template to deploy the VPC that you need for your OpenShift Container Platform cluster:
Example 4.19. 01_vpc.py Deployment Manager template
4.11.8. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 4.51. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 4.52. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
4.11.9. Creating load balancers in GCP
You must configure load balancers in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for the internal load balancer section of this topic and save it as
02_lb_int.pyon your computer. This template describes the internal load balancing objects that your cluster requires. -
For an external cluster, also copy the template from the Deployment Manager template for the external load balancer section of this topic and save it as
02_lb_ext.pyon your computer. This template describes the external load balancing objects that your cluster requires. Export the variables that the deployment template uses:
Export the cluster network location:
export CLUSTER_NETWORK=(`gcloud compute networks describe ${INFRA_ID}-network --format json | jq -r .selfLink`)$ export CLUSTER_NETWORK=(`gcloud compute networks describe ${INFRA_ID}-network --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the control plane subnet location:
export CONTROL_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-master-subnet --region=${REGION} --format json | jq -r .selfLink`)$ export CONTROL_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-master-subnet --region=${REGION} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the three zones that the cluster uses:
export ZONE_0=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[0] | cut -d "/" -f9`)$ export ZONE_0=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[0] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ZONE_1=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[1] | cut -d "/" -f9`)$ export ZONE_1=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[1] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow export ZONE_2=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[2] | cut -d "/" -f9`)$ export ZONE_2=(`gcloud compute regions describe ${REGION} --format=json | jq -r .zones[2] | cut -d "/" -f9`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
02_infra.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1 2
- Required only when deploying an external cluster.
- 3
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 4
regionis the region to deploy the cluster into, for exampleus-central1.- 5
control_subnetis the URI to the control subnet.- 6
zonesare the zones to deploy the control plane instances into, likeus-east1-b,us-east1-c, andus-east1-d.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-infra --config 02_infra.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-infra --config 02_infra.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Export the cluster IP address:
export CLUSTER_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-ip --region=${REGION} --format json | jq -r .address`)$ export CLUSTER_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-ip --region=${REGION} --format json | jq -r .address`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also export the cluster public IP address:
export CLUSTER_PUBLIC_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-public-ip --region=${REGION} --format json | jq -r .address`)$ export CLUSTER_PUBLIC_IP=(`gcloud compute addresses describe ${INFRA_ID}-cluster-public-ip --region=${REGION} --format json | jq -r .address`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.9.1. Deployment Manager template for the external load balancer
You can use the following Deployment Manager template to deploy the external load balancer that you need for your OpenShift Container Platform cluster:
Example 4.20. 02_lb_ext.py Deployment Manager template
4.11.9.2. Deployment Manager template for the internal load balancer
You can use the following Deployment Manager template to deploy the internal load balancer that you need for your OpenShift Container Platform cluster:
Example 4.21. 02_lb_int.py Deployment Manager template
You will need this template in addition to the 02_lb_ext.py template when you create an external cluster.
4.11.10. Creating a private DNS zone in GCP
You must configure a private DNS zone in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create this component is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for the private DNS section of this topic and save it as
02_dns.pyon your computer. This template describes the private DNS objects that your cluster requires. Create a
02_dns.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-dns --config 02_dns.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-dns --config 02_dns.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not create DNS entries due to limitations of Deployment Manager, so you must create them manually:
Add the internal DNS entries:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction add ${CLUSTER_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction add ${CLUSTER_IP} --name api-int.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction add ${CLUSTER_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction add ${CLUSTER_IP} --name api-int.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also add the external DNS entries:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction add ${CLUSTER_PUBLIC_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction add ${CLUSTER_PUBLIC_IP} --name api.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 60 --type A --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.10.1. Deployment Manager template for the private DNS
You can use the following Deployment Manager template to deploy the private DNS that you need for your OpenShift Container Platform cluster:
Example 4.22. 02_dns.py Deployment Manager template
4.11.11. Creating firewall rules in GCP
You must create firewall rules in Google Cloud Platform (GCP) for your OpenShift Container Platform cluster to use. One way to create these components is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your GCP infrastructure, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
Procedure
-
Copy the template from the Deployment Manager template for firewall rules section of this topic and save it as
03_firewall.pyon your computer. This template describes the security groups that your cluster requires. Create a
03_firewall.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
allowed_external_cidris the CIDR range that can access the cluster API and SSH to the bootstrap host. For an internal cluster, set this value to${NETWORK_CIDR}.- 2
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 3
cluster_networkis theselfLinkURL to the cluster network.- 4
network_cidris the CIDR of the VPC network, for example10.0.0.0/16.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-firewall --config 03_firewall.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-firewall --config 03_firewall.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.11.1. Deployment Manager template for firewall rules
You can use the following Deployment Manager template to deploy the firewall rues that you need for your OpenShift Container Platform cluster:
Example 4.23. 03_firewall.py Deployment Manager template
4.11.13. Creating the RHCOS cluster image for the GCP infrastructure
You must use a valid Red Hat Enterprise Linux CoreOS (RHCOS) image for Google Cloud Platform (GCP) for your OpenShift Container Platform nodes.
Procedure
Obtain the RHCOS image from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The file name contains the OpenShift Container Platform version number in the format
rhcos-<version>-<arch>-gcp.<arch>.tar.gz.Create the Google storage bucket:
gsutil mb gs://<bucket_name>
$ gsutil mb gs://<bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Upload the RHCOS image to the Google storage bucket:
gsutil cp <downloaded_image_file_path>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz gs://<bucket_name>
$ gsutil cp <downloaded_image_file_path>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz gs://<bucket_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the uploaded RHCOS image location as a variable:
export IMAGE_SOURCE="gs://<bucket_name>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz"
$ export IMAGE_SOURCE="gs://<bucket_name>/rhcos-<version>-x86_64-gcp.x86_64.tar.gz"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the cluster image:
gcloud compute images create "${INFRA_ID}-rhcos-image" \ --source-uri="${IMAGE_SOURCE}"$ gcloud compute images create "${INFRA_ID}-rhcos-image" \ --source-uri="${IMAGE_SOURCE}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.14. Creating the bootstrap machine in GCP
You must create the bootstrap machine in Google Cloud Platform (GCP) to use during OpenShift Container Platform cluster initialization. One way to create this machine is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your bootstrap machine, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Ensure pyOpenSSL is installed.
Procedure
-
Copy the template from the Deployment Manager template for the bootstrap machine section of this topic and save it as
04_bootstrap.pyon your computer. This template describes the bootstrap machine that your cluster requires. Export the location of the Red Hat Enterprise Linux CoreOS (RHCOS) image that the installation program requires:
export CLUSTER_IMAGE=(`gcloud compute images describe ${INFRA_ID}-rhcos-image --format json | jq -r .selfLink`)$ export CLUSTER_IMAGE=(`gcloud compute images describe ${INFRA_ID}-rhcos-image --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a bucket and upload the
bootstrap.ignfile:gsutil mb gs://${INFRA_ID}-bootstrap-ignition gsutil cp <installation_directory>/bootstrap.ign gs://${INFRA_ID}-bootstrap-ignition/$ gsutil mb gs://${INFRA_ID}-bootstrap-ignition $ gsutil cp <installation_directory>/bootstrap.ign gs://${INFRA_ID}-bootstrap-ignition/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a signed URL for the bootstrap instance to use to access the Ignition config. Export the URL from the output as a variable:
export BOOTSTRAP_IGN=`gsutil signurl -d 1h service-account-key.json gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign | grep "^gs:" | awk '{print $5}'`$ export BOOTSTRAP_IGN=`gsutil signurl -d 1h service-account-key.json gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign | grep "^gs:" | awk '{print $5}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
04_bootstrap.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
regionis the region to deploy the cluster into, for exampleus-central1.- 3
zoneis the zone to deploy the bootstrap instance into, for exampleus-central1-b.- 4
cluster_networkis theselfLinkURL to the cluster network.- 5
control_subnetis theselfLinkURL to the control subnet.- 6
imageis theselfLinkURL to the RHCOS image.- 7
machine_typeis the machine type of the instance, for examplen1-standard-4.- 8
root_volume_sizeis the boot disk size for the bootstrap machine.- 9
bootstrap_ignis the URL output when creating a signed URL.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-bootstrap --config 04_bootstrap.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-bootstrap --config 04_bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not manage load balancer membership due to limitations of Deployment Manager, so you must add the bootstrap machine manually.
Add the bootstrap instance to the internal load balancer instance group:
gcloud compute instance-groups unmanaged add-instances \ ${INFRA_ID}-bootstrap-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-bootstrap$ gcloud compute instance-groups unmanaged add-instances \ ${INFRA_ID}-bootstrap-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the bootstrap instance group to the internal load balancer backend service:
gcloud compute backend-services add-backend \ ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0}$ gcloud compute backend-services add-backend \ ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.14.1. Deployment Manager template for the bootstrap machine
You can use the following Deployment Manager template to deploy the bootstrap machine that you need for your OpenShift Container Platform cluster:
Example 4.25. 04_bootstrap.py Deployment Manager template
4.11.15. Creating the control plane machines in GCP
You must create the control plane machines in Google Cloud Platform (GCP) for your cluster to use. One way to create these machines is to modify the provided Deployment Manager template.
If you do not use the provided Deployment Manager template to create your control plane machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
Procedure
-
Copy the template from the Deployment Manager template for control plane machines section of this topic and save it as
05_control_plane.pyon your computer. This template describes the control plane machines that your cluster requires. Export the following variable required by the resource definition:
export MASTER_IGNITION=`cat <installation_directory>/master.ign`
$ export MASTER_IGNITION=`cat <installation_directory>/master.ign`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
05_control_plane.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 2
zonesare the zones to deploy the control plane instances into, for exampleus-central1-a,us-central1-b, andus-central1-c.- 3
control_subnetis theselfLinkURL to the control subnet.- 4
imageis theselfLinkURL to the RHCOS image.- 5
machine_typeis the machine type of the instance, for examplen1-standard-4.- 6
service_account_emailis the email address for the master service account that you created.- 7
ignitionis the contents of themaster.ignfile.
Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-control-plane --config 05_control_plane.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-control-plane --config 05_control_plane.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow The templates do not manage load balancer membership due to limitations of Deployment Manager, so you must add the control plane machines manually.
Run the following commands to add the control plane machines to the appropriate instance groups:
gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_0}-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-master-0 gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_1}-instance-group --zone=${ZONE_1} --instances=${INFRA_ID}-master-1 gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_2}-instance-group --zone=${ZONE_2} --instances=${INFRA_ID}-master-2$ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_0}-instance-group --zone=${ZONE_0} --instances=${INFRA_ID}-master-0 $ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_1}-instance-group --zone=${ZONE_1} --instances=${INFRA_ID}-master-1 $ gcloud compute instance-groups unmanaged add-instances ${INFRA_ID}-master-${ZONE_2}-instance-group --zone=${ZONE_2} --instances=${INFRA_ID}-master-2Copy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, you must also run the following commands to add the control plane machines to the target pools:
gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_0}" --instances=${INFRA_ID}-master-0 gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_1}" --instances=${INFRA_ID}-master-1 gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_2}" --instances=${INFRA_ID}-master-2$ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_0}" --instances=${INFRA_ID}-master-0 $ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_1}" --instances=${INFRA_ID}-master-1 $ gcloud compute target-pools add-instances ${INFRA_ID}-api-target-pool --instances-zone="${ZONE_2}" --instances=${INFRA_ID}-master-2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.15.1. Deployment Manager template for control plane machines
You can use the following Deployment Manager template to deploy the control plane machines that you need for your OpenShift Container Platform cluster:
Example 4.26. 05_control_plane.py Deployment Manager template
4.11.16. Wait for bootstrap completion and remove bootstrap resources in GCP
After you create all of the required infrastructure in Google Cloud Platform (GCP), wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
Change to the directory that contains the installation program and run the following command:
./openshift-install wait-for bootstrap-complete --dir <installation_directory> \ --log-level info$ ./openshift-install wait-for bootstrap-complete --dir <installation_directory> \1 --log-level info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the command exits without a
FATALwarning, your production control plane has initialized.Delete the bootstrap resources:
gcloud compute backend-services remove-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0} gsutil rm gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign gsutil rb gs://${INFRA_ID}-bootstrap-ignition gcloud deployment-manager deployments delete ${INFRA_ID}-bootstrap$ gcloud compute backend-services remove-backend ${INFRA_ID}-api-internal-backend-service --region=${REGION} --instance-group=${INFRA_ID}-bootstrap-instance-group --instance-group-zone=${ZONE_0} $ gsutil rm gs://${INFRA_ID}-bootstrap-ignition/bootstrap.ign $ gsutil rb gs://${INFRA_ID}-bootstrap-ignition $ gcloud deployment-manager deployments delete ${INFRA_ID}-bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.17. Creating additional worker machines in GCP
You can create worker machines in Google Cloud Platform (GCP) for your cluster to use by launching individual instances discretely or by automated processes outside the cluster, such as auto scaling groups. You can also take advantage of the built-in cluster scaling mechanisms and the machine API in OpenShift Container Platform.
In this example, you manually launch one instance by using the Deployment Manager template. Additional instances can be launched by including additional resources of type 06_worker.py in the file.
If you do not use the provided Deployment Manager template to create your worker machines, you must review the provided information and manually create the infrastructure. If your cluster does not initialize correctly, you might have to contact Red Hat support with your installation logs.
Prerequisites
- Configure a GCP account.
- Generate the Ignition config files for your cluster.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
Procedure
-
Copy the template from the Deployment Manager template for worker machines section of this topic and save it as
06_worker.pyon your computer. This template describes the worker machines that your cluster requires. Export the variables that the resource definition uses.
Export the subnet that hosts the compute machines:
export COMPUTE_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-worker-subnet --region=${REGION} --format json | jq -r .selfLink`)$ export COMPUTE_SUBNET=(`gcloud compute networks subnets describe ${INFRA_ID}-worker-subnet --region=${REGION} --format json | jq -r .selfLink`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the email address for your service account:
export WORKER_SERVICE_ACCOUNT=(`gcloud iam service-accounts list --filter "email~^${INFRA_ID}-w@${PROJECT_NAME}." --format json | jq -r '.[0].email'`)$ export WORKER_SERVICE_ACCOUNT=(`gcloud iam service-accounts list --filter "email~^${INFRA_ID}-w@${PROJECT_NAME}." --format json | jq -r '.[0].email'`)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the location of the compute machine Ignition config file:
export WORKER_IGNITION=`cat <installation_directory>/worker.ign`
$ export WORKER_IGNITION=`cat <installation_directory>/worker.ign`Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create a
06_worker.yamlresource definition file:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
nameis the name of the worker machine, for exampleworker-0.- 2 9
infra_idis theINFRA_IDinfrastructure name from the extraction step.- 3 10
zoneis the zone to deploy the worker machine into, for exampleus-central1-a.- 4 11
compute_subnetis theselfLinkURL to the compute subnet.- 5 12
imageis theselfLinkURL to the RHCOS image.- 6 13
machine_typeis the machine type of the instance, for examplen1-standard-4.- 7 14
service_account_emailis the email address for the worker service account that you created.- 8 15
ignitionis the contents of theworker.ignfile.
-
Optional: If you want to launch additional instances, include additional resources of type
06_worker.pyin your06_worker.yamlresource definition file. Create the deployment by using the
gcloudCLI:gcloud deployment-manager deployments create ${INFRA_ID}-worker --config 06_worker.yaml$ gcloud deployment-manager deployments create ${INFRA_ID}-worker --config 06_worker.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.17.1. Deployment Manager template for worker machines
You can use the following Deployment Manager template to deploy the worker machines that you need for your OpenShift Container Platform cluster:
Example 4.27. 06_worker.py Deployment Manager template
4.11.18. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.19. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
4.11.20. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
4.11.21. Optional: Adding the ingress DNS records
If you removed the DNS zone configuration when creating Kubernetes manifests and generating Ignition configs, you must manually create DNS records that point at the ingress load balancer. You can create either a wildcard *.apps.{baseDomain}. or specific records. You can use A, CNAME, and other records per your requirements.
Prerequisites
- Configure a GCP account.
- Remove the DNS Zone configuration when creating Kubernetes manifests and generating Ignition configs.
- Create and configure a VPC and associated subnets in GCP.
- Create and configure networking and load balancers in GCP.
- Create control plane and compute roles.
- Create the bootstrap machine.
- Create the control plane machines.
- Create the worker machines.
Procedure
Wait for the Ingress router to create a load balancer and populate the
EXTERNAL-IPfield:oc -n openshift-ingress get service router-default
$ oc -n openshift-ingress get service router-defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.18.154 35.233.157.184 80:32288/TCP,443:31215/TCP 98
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE router-default LoadBalancer 172.30.18.154 35.233.157.184 80:32288/TCP,443:31215/TCP 98Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the A record to your zones:
To use A records:
Export the variable for the router IP address:
export ROUTER_IP=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`$ export ROUTER_IP=`oc -n openshift-ingress get service router-default --no-headers | awk '{print $4}'`Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the A record to the private zones:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${INFRA_ID}-private-zone gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zone$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${INFRA_ID}-private-zone $ gcloud dns record-sets transaction execute --zone ${INFRA_ID}-private-zoneCopy to Clipboard Copied! Toggle word wrap Toggle overflow For an external cluster, also add the A record to the public zones:
if [ -f transaction.yaml ]; then rm transaction.yaml; fi gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${BASE_DOMAIN_ZONE_NAME} gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}$ if [ -f transaction.yaml ]; then rm transaction.yaml; fi $ gcloud dns record-sets transaction start --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction add ${ROUTER_IP} --name \*.apps.${CLUSTER_NAME}.${BASE_DOMAIN}. --ttl 300 --type A --zone ${BASE_DOMAIN_ZONE_NAME} $ gcloud dns record-sets transaction execute --zone ${BASE_DOMAIN_ZONE_NAME}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To add explicit domains instead of using a wildcard, create entries for each of the cluster’s current routes:
oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routes$ oc get --all-namespaces -o jsonpath='{range .items[*]}{range .status.ingress[*]}{.host}{"\n"}{end}{end}' routesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
4.11.22. Completing a GCP installation on user-provisioned infrastructure
After you start the OpenShift Container Platform installation on Google Cloud Platform (GCP) user-provisioned infrastructure, you can monitor the cluster events until the cluster is ready.
Prerequisites
- Deploy the bootstrap machine for an OpenShift Container Platform cluster on user-provisioned GCP infrastructure.
-
Install the
ocCLI and log in.
Procedure
Complete the cluster installation:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Observe the running state of your cluster.
Run the following command to view the current cluster version and status:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version False True 24m Working towards 4.5.4: 99% complete
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version False True 24m Working towards 4.5.4: 99% completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to view the Operators managed on the control plane by the Cluster Version Operator (CVO):
oc get clusteroperators
$ oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to view your cluster pods:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
When the current cluster version is
AVAILABLE, the installation is complete.
4.11.23. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
4.11.24. Next steps
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
4.12. Uninstalling a cluster on GCP
You can remove a cluster that you deployed to Google Cloud Platform (GCP).
4.12.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access. For example, some Google Cloud resources require IAM permissions in shared VPC host projects, or there might be unused health checks that must be deleted.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
Chapter 5. Installing on bare metal
5.1. Installing a cluster on bare metal
In OpenShift Container Platform version 4.6, you can install a cluster on bare metal infrastructure that you provision.
While you might be able to follow this procedure to deploy a cluster on virtualized or cloud environments, you must be aware of additional considerations for non-bare metal platforms. Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you attempt to install an OpenShift Container Platform cluster in such an environment.
5.1.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
5.1.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
5.1.3. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
5.1.3.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines. If you are running a three-node cluster, running zero compute machines is supported. Running one compute machine is not supported.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
5.1.3.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
5.1.3.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | CPU [1] | RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One CPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = CPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
5.1.3.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
5.1.4. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
5.1.4.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 5.5. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 5.6. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
5.1.4.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 5.1. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 5.2. Sample DNS zone database for reverse records
5.1.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
5.1.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
5.1.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
5.1.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>5.1.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>5.1.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>5.1.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
5.1.8.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
5.1.8.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
5.1.8.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
5.1.8.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
5.1.8.2. Sample install-config.yaml file for bare metal
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for your platform. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- The pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
5.1.8.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
For bare metal installations, if you do not assign node IP addresses from the range that is specified in the networking.machineNetwork[].cidr field in the install-config.yaml file, you must include them in the proxy.noProxy field.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
5.1.9. Configuring a three-node cluster
You can optionally install and run three-node clusters in OpenShift Container Platform with no workers. This provides smaller, more resource efficient clusters for cluster administrators and developers to use for development, production, and testing.
Procedure
Edit the
install-config.yamlfile to set the number of compute replicas, which are also known as worker replicas, to0, as shown in the followingcomputestanza:compute: - name: worker platform: {} replicas: 0compute: - name: worker platform: {} replicas: 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.1.10. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
If you are installing a three-node cluster, skip the following step to allow the control plane nodes to be schedulable.
+
When you configure control plane nodes from the default unschedulable to schedulable, additional subscriptions are required. This is because control plane nodes then become worker nodes.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Additional resources
- See Recovering from expired control plane certificates for more information about recovering kubelet certificates.
5.1.11. Installing RHCOS and starting the OpenShift Container Platform bootstrap process
To install OpenShift Container Platform on bare metal infrastructure that you provision, you must install Red Hat Enterprise Linux CoreOS (RHCOS) on the machines. When you install RHCOS, you must provide the Ignition config file that was generated by the OpenShift Container Platform installation program for the type of machine you are installing. If you have configured suitable networking, DNS, and load balancing infrastructure, the OpenShift Container Platform bootstrap process begins automatically after the RHCOS machines have rebooted.
To install RHCOS on the machines, follow either the steps to use an ISO image or network PXE booting.
The compute node deployment steps included in this installation document are RHCOS-specific. If you choose instead to deploy RHEL-based compute nodes, you take responsibility for all operating system life cycle management and maintenance, including performing system updates, applying patches, and completing all other required tasks. Use of RHEL 7 compute machines is deprecated and planned for removal in a future release of OpenShift Container Platform 4.
You can configure RHCOS during ISO and PXE installations by using the following methods:
-
Kernel arguments: You can use kernel arguments to provide installation-specific information. For example, you can specify the locations of the RHCOS installation files that you uploaded to your HTTP server and the location of the Ignition config file for the type of node you are installing. For a PXE installation, you can use the
APPENDparameter to pass the arguments to the kernel of the live installer. For an ISO installation, you can interrupt the live installation boot process to add the kernel arguments. In both installation cases, you can use specialcoreos.inst.*arguments to direct the live installer, as well as standard installation boot arguments for turning standard kernel services on or off. -
Ignition configs: OpenShift Container Platform Ignition config files (
*.ign) are specific to the type of node you are installing. You pass the location of a bootstrap, control plane, or compute node Ignition config file during the RHCOS installation so that it takes effect on first boot. In special cases, you can create a separate, limited Ignition config to pass to the live system. That Ignition config could do a certain set of tasks, such as reporting success to a provisioning system after completing installation. This special Ignition config is consumed by thecoreos-installerto be applied on first boot of the installed system. Do not provide the standard control plane and compute node Ignition configs to the live ISO directly. -
coreos-installer: You can boot the live ISO installer to a shell prompt, which allows you to prepare the permanent system in a variety of ways before first boot. In particular, you can run thecoreos-installercommand to identify various artifacts to include, work with disk partitions, and set up networking. In some cases, you can configure features on the live system and copy them to the installed system.
Whether to use an ISO or PXE install depends on your situation. A PXE install requires an available DHCP service and more preparation, but can make the installation process more automated. An ISO install is a more manual process and can be inconvenient if you are setting up more than a few machines.
As of OpenShift Container Platform 4.6, the RHCOS ISO and other installation artifacts provide support for installation on disks with 4K sectors.
5.1.11.1. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines using an ISO image
Before you install a cluster on infrastructure that you provision, you must create RHCOS machines for it to use. You can use an ISO image to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Have access to an HTTP server that can be accessed from your computer, and from the machines that you create.
Procedure
Upload the control plane, compute, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS images that are required for your preferred method of installing operating system instances from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available. Use only ISO images for this procedure. RHCOS qcow2 images are not supported for this installation type.
ISO file names resemble the following example:
rhcos-<version>-live.<architecture>.isoUse the ISO to start the RHCOS installation. Use one of the following installation options:
- Burn the ISO image to a disk and boot it directly.
- Use ISO redirection via a LOM interface.
-
Boot the ISO image. You can interrupt the installation boot process to add kernel arguments. However, for this ISO procedure you should use the
coreos-installercommand instead of adding kernel arguments. If you run the live installer without options or interruption, the installer boots up to a shell prompt on the live system, ready for you to install RHCOS to disk. -
Review the Advanced RHCOS installation reference section for different ways of configuring features, such as networking and disk partitions, before running the
coreos-installer. Run the
coreos-installercommand. At a minimum, you must identify the Ignition config file location for your node type, and the location of the disk you are installing to. Here is an example:sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sda$ sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After RHCOS installs, the system reboots. During the system reboot, it applies the Ignition config file that you specified.
Continue to create the other machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
5.1.11.2. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines by PXE or iPXE booting
Before you install a cluster that uses manually-provisioned RHCOS nodes, such as bare metal, you must create RHCOS machines for it to use. You can use PXE or iPXE booting to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Configure suitable PXE or iPXE infrastructure.
- Have access to an HTTP server that you can access from your computer.
Procedure
Upload the master, worker, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantYou can add or change configuration settings in your Ignition configs before saving them to your HTTP server. If you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS
kernel,initramfsandrootfsfiles from the RHCOS image mirror page.ImportantThe RHCOS artifacts might not change with every release of OpenShift Container Platform. You must download artifacts with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate
kernel,initramfs, androotfsartifacts described below for this procedure. RHCOS qcow2 images are not supported for this installation type.The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:rhcos-<version>-live-kernel-<architecture> -
initramfs:rhcos-<version>-live-initramfs.<architecture>.img -
rootfs:rhcos-<version>-live-rootfs.<architecture>.img
-
Upload the additional files that are required for your booting method:
-
For traditional PXE, upload the
kernelandinitramfsfiles to your TFTP server and therootfsfile to your HTTP server. For iPXE, upload the
kernel,initramfs, androotfsfiles to your HTTP server.ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
-
For traditional PXE, upload the
- Configure the network boot infrastructure so that the machines boot from their local disks after RHCOS is installed on them.
Configure PXE or iPXE installation for the RHCOS images.
Modify one of the following example menu entries for your environment and verify that the image and Ignition files are properly accessible:
For PXE:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the location of the live
kernelfile that you uploaded to your HTTP server. The URL must be HTTP, TFTP, or FTP; HTTPS and NFS are not supported. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
initrdparameter value is the location of theinitramfsfile, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. You can also add more kernel arguments to theAPPENDline to configure networking or other boot options.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to theAPPENDline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.For iPXE:
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img boot
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign1 2 initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img3 bootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
kernelparameter value is the location of thekernelfile, theinitrd=mainargument is needed for booting on UEFI systems, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify the location of the
initramfsfile that you uploaded to your HTTP server.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to thekernelline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.
If you use PXE UEFI, perform the following actions:
Provide the
shimx64.efiandgrubx64.efiEFI binaries and thegrub.cfgfile that are required for booting the system.Extract the necessary EFI binaries by mounting the RHCOS ISO to your host and then mounting the
images/efiboot.imgfile to your host:mkdir -p /mnt/iso
$ mkdir -p /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p /mnt/efiboot
$ mkdir -p /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop rhcos-installer.x86_64.iso /mnt/iso
$ mount -o loop rhcos-installer.x86_64.iso /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efiboot
$ mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the
efiboot.imgmount point, copy theEFI/redhat/shimx64.efiandEFI/redhat/grubx64.efifiles to your TFTP server:cp /mnt/efiboot/EFI/redhat/shimx64.efi .
$ cp /mnt/efiboot/EFI/redhat/shimx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp /mnt/efiboot/EFI/redhat/grubx64.efi .
$ cp /mnt/efiboot/EFI/redhat/grubx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/efiboot
$ umount /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/iso
$ umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the
EFI/redhat/grub.cfgfile that is included in the RHCOS ISO to your TFTP server.
Edit the
grub.cfgfile to include arguments similar to the following:menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
rhcos-<version>-live-kernel-<architecture>-
Specifies the
kernelfile that you uploaded to your TFTP server. http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img- Specifies the location of the live rootfs image that you uploaded to your HTTP server.
http://<HTTP_server>/bootstrap.ign- Specifies the location of the bootstrap Ignition config file that you uploaded to your HTTP server.
rhcos-<version>-live-initramfs.<architecture>.img-
Specifies the location of the
initramfsfile that you uploaded to your TFTP server.
NoteFor more information on how to configure a PXE server for UEFI boot, see the Red Hat Knowledgebase article: How to configure/setup a PXE server for UEFI boot for Red Hat Enterprise Linux?.
Continue to create the machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
5.1.11.3. Advanced Red Hat Enterprise Linux CoreOS (RHCOS) installation configuration
A key benefit for manually provisioning the Red Hat Enterprise Linux CoreOS (RHCOS) nodes for OpenShift Container Platform is to be able to do configuration that is not available through default OpenShift Container Platform installation methods. This section describes some of the configurations that you can do using techniques that include:
- Passing kernel arguments to the live installer
-
Running
coreos-installermanually from the live system - Embedding Ignition configs in an ISO
The advanced configuration topics for manual Red Hat Enterprise Linux CoreOS (RHCOS) installations detailed in this section relate to disk partitioning, networking, and using Ignition configs in different ways.
5.1.11.3.1. Using advanced networking options for PXE and ISO installations
Networking for OpenShift Container Platform nodes uses DHCP by default to gather all necessary configuration settings. To set up static IP addresses or configure special settings, such as bonding, you can do one of the following:
- Pass special kernel parameters when you boot the live installer.
- Use a machine config to copy networking files to the installed system.
- Configure networking from a live installer shell prompt, then copy those settings to the installed system so that they take effect when the installed system first boots.
To configure a PXE or iPXE installation, use one of the following options:
- See the "Advanced RHCOS installation reference" tables.
- Use a machine config to copy networking files to the installed system.
To configure an ISO installation, use the following procedure.
Procedure
- Boot the ISO installer.
-
From the live system shell prompt, configure networking for the live system using available RHEL tools, such as
nmcliornmtui. Run the
coreos-installercommand to install the system, adding the--copy-networkoption to copy networking configuration. For example:coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sda$ coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe
--copy-networkoption only copies networking configuration found under/etc/NetworkManager/system-connections. In particular, it does not copy the system hostname.- Reboot into the installed system.
5.1.11.3.2. Disk partitioning
The disk partitions are created on OpenShift Container Platform cluster nodes during the Red Hat Enterprise Linux CoreOS (RHCOS) installation. Each RHCOS node of a particular architecture uses the same partition layout, unless the default partitioning configuration is overridden. During the RHCOS installation, the size of the root file system is increased to use the remaining available space on the target device.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
5.1.11.3.2.1. Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the ISO or PXE manual installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
5.1.11.3.2.2. Retaining existing partitions
For an ISO installation, you can add options to the coreos-installer command line that causes the installer to maintain one or more existing partitions. For a PXE installation, you can APPEND coreos.inst.* options to preserve partitions.
Saved partitions might be partitions from an existing OpenShift Container Platform system that has data partitions that you want to keep. Here are a few tips:
- If you save existing partitions, and those partitions do not leave enough space for RHCOS, installation will fail without damaging the saved partitions.
- Identify the disk partitions you want to keep either by partition label or by number.
For an ISO installation
This example preserves any partition in which the partition label begins with data (data*):
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
The following example illustrates running the coreos-installer in a way that preserves the sixth (6) partition on the disk:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sdaThis example preserves partitions 5 and higher:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
--save-partindex 5- /dev/sda
In the previous examples where partition saving is used, coreos-installer recreates the partition immediately.
For a PXE installation
This APPEND option preserves any partition in which the partition label begins with 'data' ('data*'):
coreos.inst.save_partlabel=data*
coreos.inst.save_partlabel=data*
This APPEND option preserves partitions 5 and higher:
coreos.inst.save_partindex=5-
coreos.inst.save_partindex=5-
This APPEND option preserves partition 6:
coreos.inst.save_partindex=6
coreos.inst.save_partindex=65.1.11.3.3. Identifying Ignition configs
When doing an RHCOS manual installation, there are two types of Ignition configs that you can provide, with different reasons for providing each one:
Permanent install Ignition config: Every manual RHCOS installation needs to pass one of the Ignition config files generated by
openshift-installer, such asbootstrap.ign,master.ignandworker.ign, to carry out the installation.ImportantIt is not recommended to modify these files.
For PXE installations, you pass the Ignition configs on the
APPENDline using thecoreos.inst.ignition_url=option. For ISO installations, after the ISO boots to the shell prompt, you identify the Ignition config on thecoreos-installercommand line with the--ignition-url=option. In both cases, only HTTP and HTTPS protocols are supported.Live install Ignition config: This type must be created manually and should be avoided if possible, as it is not supported by Red Hat. With this method, the Ignition config passes to the live install medium, runs immediately upon booting, and performs setup tasks before and/or after the RHCOS system installs to disk. This method should only be used for performing tasks that must be performed once and not applied again later, such as with advanced partitioning that cannot be done using a machine config.
For PXE or ISO boots, you can create the Ignition config and
APPENDtheignition.config.url=option to identify the location of the Ignition config. You also need to appendignition.firstboot ignition.platform.id=metalor theignition.config.urloption will be ignored.
5.1.11.3.3.1. Embedding an Ignition config in the RHCOS ISO
You can embed a live install Ignition config directly in an RHCOS ISO image. When the ISO image is booted, the embedded config will be applied automatically.
Procedure
-
Download the
coreos-installerbinary from the following image mirror page: https://mirror.openshift.com/pub/openshift-v4/clients/coreos-installer/latest/. Retrieve the RHCOS ISO image and the Ignition config file, and copy them into an accessible directory, such as
/mnt:cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ chmod 644 /mnt/rhcos-<version>-live.x86_64.iso
# cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ # chmod 644 /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to embed the Ignition config into the ISO:
./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.iso# ./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now use that ISO to install RHCOS using the specified live install Ignition config.
ImportantUsing
coreos-installer iso ignition embedto embed a file generated byopenshift-installer, such asbootstrap.ign,master.ignandworker.ign, is unsupported and not recommended.To show the contents of the embedded Ignition config and direct it into a file, run:
./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ign
# ./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow diff -s bootstrap.ign mybootstrap.ign
# diff -s bootstrap.ign mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Files bootstrap.ign and mybootstrap.ign are identical
Files bootstrap.ign and mybootstrap.ign are identicalCopy to Clipboard Copied! Toggle word wrap Toggle overflow To remove the Ignition config and return the ISO to its pristine state so you can reuse it, run:
./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.iso
# ./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now embed another Ignition config into the ISO or use the ISO in its pristine state.
5.1.11.3.4. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
coreos.inst boot options for ISO or PXE install
While you can pass most standard installation boot arguments to the live installer, there are several arguments that are specific to the RHCOS live installer.
- For ISO, these options can be added by interrupting the RHCOS installer.
-
For PXE or iPXE, these options must be added to the
APPENDline before starting the PXE kernel. You cannot interrupt a live PXE install.
The following table shows the RHCOS live installer boot options for ISO and PXE installs.
| Argument | Description |
|---|---|
|
|
Required. The block device on the system to install to. It is recommended to use the full path, such as |
|
| Optional: The URL of the Ignition config to embed into the installed system. If no URL is specified, no Ignition config is embedded. |
|
| Optional: Comma-separated labels of partitions to preserve during the install. Glob-style wildcards are permitted. The specified partitions do not need to exist. |
|
|
Optional: Comma-separated indexes of partitions to preserve during the install. Ranges |
|
|
Optional: Permits the OS image that is specified by |
|
| Optional: Download and install the specified RHCOS image.
|
|
| Optional: The system will not reboot after installing. Once the install finishes, you will receive a prompt that allows you to inspect what is happening during installation. This argument should not be used in production environments and is intended for debugging purposes only. |
|
|
Optional: The Ignition platform ID of the platform the RHCOS image is being installed on. Default is |
|
|
Optional: The URL of the Ignition config for the live boot. For example, this can be used to customize how |
coreos-installer options for ISO install
You can also install RHCOS by invoking the coreos-installer command directly from the command line. The kernel arguments in the previous table provide a shortcut for automatically invoking coreos-installer at boot time, but you can pass similar arguments directly to coreos-installer when running it from a shell prompt.
The following table shows the options and subcommands you can pass to the coreos-installer command from a shell prompt during a live install.
| Command-line options | |
| Option | Description |
|
| Specify the image URL manually. |
|
| Specify a local image file manually. |
|
| Embed an Ignition config from a file. |
|
| Embed an Ignition config from a URL. |
|
|
Digest |
|
| Override the Ignition platform ID. |
|
| Append the default kernel argument. |
|
| Delete the default kernel argument. |
|
| Copy the network configuration from the install environment. Important
The |
|
|
For use with |
|
| Save partitions with this label glob. |
|
| Save partitions with this number or range. |
|
| Force offline installation. |
|
| Skip signature verification. |
|
| Allow Ignition URL without HTTPS or hash. |
|
|
Target CPU architecture. Default is |
|
| Do not clear partition table on error. |
|
| Print help information. |
| Command-line argument | |
| Argument | Description |
|
| The destination device. |
| coreos-installer embedded Ignition commands | |
| Command | Description |
|
| Embed an Ignition config in an ISO image. |
|
| Show the embedded Ignition config from an ISO image. |
|
| Remove the embedded Ignition config from an ISO image. |
| coreos-installer ISO Ignition options | |
| Option | Description |
|
| Overwrite an existing Ignition config. |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
| coreos-installer PXE Ignition commands | |
| Command | Description |
| Note that not all of these options are accepted by all subcommands. | |
|
| Wrap an Ignition config in an image. |
|
| Show the wrapped Ignition config in an image. |
|
|
Show the wrapped Ignition config in an |
| coreos-installer PXE Ignition options | |
| Option | Description |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
5.1.12. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
5.1.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.1.14. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
5.1.15. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
5.1.15.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
5.1.15.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
5.1.15.2.1. Configuring registry storage for bare metal and other manual installations
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster that uses manually-provisioned Red Hat Enterprise Linux CoreOS (RHCOS) nodes, such as bare metal.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.1.15.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
5.1.15.2.3. Configuring block registry storage
To allow the image registry to use block storage types during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with the image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only one (1) replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
- Edit the registry configuration so that it references the correct PVC.
5.1.16. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
5.1.17. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
5.1.18. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
5.2. Installing a cluster on bare metal with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster on bare metal infrastructure that you provision with customized network configuration options. By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing MTU and VXLAN configurations.
You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
5.2.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- If you use a firewall, you must configure it to access Red Hat Insights.
5.2.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
5.2.3. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
5.2.3.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines. If you are running a three-node cluster, running zero compute machines is supported. Running one compute machine is not supported.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
5.2.3.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
5.2.3.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | CPU [1] | RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One CPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = CPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
5.2.3.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
5.2.4. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
5.2.4.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 5.17. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 5.18. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
5.2.4.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 5.3. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 5.4. Sample DNS zone database for reverse records
5.2.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
5.2.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
5.2.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
5.2.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>5.2.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>5.2.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>5.2.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
5.2.8.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
5.2.8.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
5.2.8.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
5.2.8.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
5.2.8.2. Sample install-config.yaml file for bare metal
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for your platform. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- The pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
5.2.9. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
5.2.10. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it. - Create the Ignition config files for your cluster.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
5.2.11. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
5.2.11.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
5.2.12. Creating the Ignition config files
Because you must manually start the cluster machines, you must generate the Ignition config files that the cluster needs to make its machines.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Obtain the Ignition config files:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantIf you created an
install-config.yamlfile, specify the directory that contains it. Otherwise, specify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.2.13. Installing RHCOS and starting the OpenShift Container Platform bootstrap process
To install OpenShift Container Platform on bare metal infrastructure that you provision, you must install Red Hat Enterprise Linux CoreOS (RHCOS) on the machines. When you install RHCOS, you must provide the Ignition config file that was generated by the OpenShift Container Platform installation program for the type of machine you are installing. If you have configured suitable networking, DNS, and load balancing infrastructure, the OpenShift Container Platform bootstrap process begins automatically after the RHCOS machines have rebooted.
To install RHCOS on the machines, follow either the steps to use an ISO image or network PXE booting.
The compute node deployment steps included in this installation document are RHCOS-specific. If you choose instead to deploy RHEL-based compute nodes, you take responsibility for all operating system life cycle management and maintenance, including performing system updates, applying patches, and completing all other required tasks. Use of RHEL 7 compute machines is deprecated and planned for removal in a future release of OpenShift Container Platform 4.
You can configure RHCOS during ISO and PXE installations by using the following methods:
-
Kernel arguments: You can use kernel arguments to provide installation-specific information. For example, you can specify the locations of the RHCOS installation files that you uploaded to your HTTP server and the location of the Ignition config file for the type of node you are installing. For a PXE installation, you can use the
APPENDparameter to pass the arguments to the kernel of the live installer. For an ISO installation, you can interrupt the live installation boot process to add the kernel arguments. In both installation cases, you can use specialcoreos.inst.*arguments to direct the live installer, as well as standard installation boot arguments for turning standard kernel services on or off. -
Ignition configs: OpenShift Container Platform Ignition config files (
*.ign) are specific to the type of node you are installing. You pass the location of a bootstrap, control plane, or compute node Ignition config file during the RHCOS installation so that it takes effect on first boot. In special cases, you can create a separate, limited Ignition config to pass to the live system. That Ignition config could do a certain set of tasks, such as reporting success to a provisioning system after completing installation. This special Ignition config is consumed by thecoreos-installerto be applied on first boot of the installed system. Do not provide the standard control plane and compute node Ignition configs to the live ISO directly. -
coreos-installer: You can boot the live ISO installer to a shell prompt, which allows you to prepare the permanent system in a variety of ways before first boot. In particular, you can run thecoreos-installercommand to identify various artifacts to include, work with disk partitions, and set up networking. In some cases, you can configure features on the live system and copy them to the installed system.
Whether to use an ISO or PXE install depends on your situation. A PXE install requires an available DHCP service and more preparation, but can make the installation process more automated. An ISO install is a more manual process and can be inconvenient if you are setting up more than a few machines.
As of OpenShift Container Platform 4.6, the RHCOS ISO and other installation artifacts provide support for installation on disks with 4K sectors.
5.2.13.1. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines using an ISO image
Before you install a cluster on infrastructure that you provision, you must create RHCOS machines for it to use. You can use an ISO image to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Have access to an HTTP server that can be accessed from your computer, and from the machines that you create.
Procedure
Upload the control plane, compute, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS images that are required for your preferred method of installing operating system instances from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available. Use only ISO images for this procedure. RHCOS qcow2 images are not supported for this installation type.
ISO file names resemble the following example:
rhcos-<version>-live.<architecture>.isoUse the ISO to start the RHCOS installation. Use one of the following installation options:
- Burn the ISO image to a disk and boot it directly.
- Use ISO redirection via a LOM interface.
-
Boot the ISO image. You can interrupt the installation boot process to add kernel arguments. However, for this ISO procedure you should use the
coreos-installercommand instead of adding kernel arguments. If you run the live installer without options or interruption, the installer boots up to a shell prompt on the live system, ready for you to install RHCOS to disk. -
Review the Advanced RHCOS installation reference section for different ways of configuring features, such as networking and disk partitions, before running the
coreos-installer. Run the
coreos-installercommand. At a minimum, you must identify the Ignition config file location for your node type, and the location of the disk you are installing to. Here is an example:sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sda$ sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After RHCOS installs, the system reboots. During the system reboot, it applies the Ignition config file that you specified.
Continue to create the other machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
5.2.13.2. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines by PXE or iPXE booting
Before you install a cluster that uses manually-provisioned RHCOS nodes, such as bare metal, you must create RHCOS machines for it to use. You can use PXE or iPXE booting to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Configure suitable PXE or iPXE infrastructure.
- Have access to an HTTP server that you can access from your computer.
Procedure
Upload the master, worker, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantYou can add or change configuration settings in your Ignition configs before saving them to your HTTP server. If you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS
kernel,initramfsandrootfsfiles from the RHCOS image mirror page.ImportantThe RHCOS artifacts might not change with every release of OpenShift Container Platform. You must download artifacts with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate
kernel,initramfs, androotfsartifacts described below for this procedure. RHCOS qcow2 images are not supported for this installation type.The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:rhcos-<version>-live-kernel-<architecture> -
initramfs:rhcos-<version>-live-initramfs.<architecture>.img -
rootfs:rhcos-<version>-live-rootfs.<architecture>.img
-
Upload the additional files that are required for your booting method:
-
For traditional PXE, upload the
kernelandinitramfsfiles to your TFTP server and therootfsfile to your HTTP server. For iPXE, upload the
kernel,initramfs, androotfsfiles to your HTTP server.ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
-
For traditional PXE, upload the
- Configure the network boot infrastructure so that the machines boot from their local disks after RHCOS is installed on them.
Configure PXE or iPXE installation for the RHCOS images.
Modify one of the following example menu entries for your environment and verify that the image and Ignition files are properly accessible:
For PXE:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the location of the live
kernelfile that you uploaded to your HTTP server. The URL must be HTTP, TFTP, or FTP; HTTPS and NFS are not supported. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
initrdparameter value is the location of theinitramfsfile, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. You can also add more kernel arguments to theAPPENDline to configure networking or other boot options.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to theAPPENDline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.For iPXE:
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img boot
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign1 2 initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img3 bootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
kernelparameter value is the location of thekernelfile, theinitrd=mainargument is needed for booting on UEFI systems, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify the location of the
initramfsfile that you uploaded to your HTTP server.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to thekernelline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.
If you use PXE UEFI, perform the following actions:
Provide the
shimx64.efiandgrubx64.efiEFI binaries and thegrub.cfgfile that are required for booting the system.Extract the necessary EFI binaries by mounting the RHCOS ISO to your host and then mounting the
images/efiboot.imgfile to your host:mkdir -p /mnt/iso
$ mkdir -p /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p /mnt/efiboot
$ mkdir -p /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop rhcos-installer.x86_64.iso /mnt/iso
$ mount -o loop rhcos-installer.x86_64.iso /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efiboot
$ mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the
efiboot.imgmount point, copy theEFI/redhat/shimx64.efiandEFI/redhat/grubx64.efifiles to your TFTP server:cp /mnt/efiboot/EFI/redhat/shimx64.efi .
$ cp /mnt/efiboot/EFI/redhat/shimx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp /mnt/efiboot/EFI/redhat/grubx64.efi .
$ cp /mnt/efiboot/EFI/redhat/grubx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/efiboot
$ umount /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/iso
$ umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the
EFI/redhat/grub.cfgfile that is included in the RHCOS ISO to your TFTP server.
Edit the
grub.cfgfile to include arguments similar to the following:menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
rhcos-<version>-live-kernel-<architecture>-
Specifies the
kernelfile that you uploaded to your TFTP server. http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img- Specifies the location of the live rootfs image that you uploaded to your HTTP server.
http://<HTTP_server>/bootstrap.ign- Specifies the location of the bootstrap Ignition config file that you uploaded to your HTTP server.
rhcos-<version>-live-initramfs.<architecture>.img-
Specifies the location of the
initramfsfile that you uploaded to your TFTP server.
NoteFor more information on how to configure a PXE server for UEFI boot, see the Red Hat Knowledgebase article: How to configure/setup a PXE server for UEFI boot for Red Hat Enterprise Linux?.
Continue to create the machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
5.2.13.3. Advanced Red Hat Enterprise Linux CoreOS (RHCOS) installation configuration
A key benefit for manually provisioning the Red Hat Enterprise Linux CoreOS (RHCOS) nodes for OpenShift Container Platform is to be able to do configuration that is not available through default OpenShift Container Platform installation methods. This section describes some of the configurations that you can do using techniques that include:
- Passing kernel arguments to the live installer
-
Running
coreos-installermanually from the live system - Embedding Ignition configs in an ISO
The advanced configuration topics for manual Red Hat Enterprise Linux CoreOS (RHCOS) installations detailed in this section relate to disk partitioning, networking, and using Ignition configs in different ways.
5.2.13.3.1. Using advanced networking options for PXE and ISO installations
Networking for OpenShift Container Platform nodes uses DHCP by default to gather all necessary configuration settings. To set up static IP addresses or configure special settings, such as bonding, you can do one of the following:
- Pass special kernel parameters when you boot the live installer.
- Use a machine config to copy networking files to the installed system.
- Configure networking from a live installer shell prompt, then copy those settings to the installed system so that they take effect when the installed system first boots.
To configure a PXE or iPXE installation, use one of the following options:
- See the "Advanced RHCOS installation reference" tables.
- Use a machine config to copy networking files to the installed system.
To configure an ISO installation, use the following procedure.
Procedure
- Boot the ISO installer.
-
From the live system shell prompt, configure networking for the live system using available RHEL tools, such as
nmcliornmtui. Run the
coreos-installercommand to install the system, adding the--copy-networkoption to copy networking configuration. For example:coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sda$ coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe
--copy-networkoption only copies networking configuration found under/etc/NetworkManager/system-connections. In particular, it does not copy the system hostname.- Reboot into the installed system.
5.2.13.3.2. Disk partitioning
The disk partitions are created on OpenShift Container Platform cluster nodes during the Red Hat Enterprise Linux CoreOS (RHCOS) installation. Each RHCOS node of a particular architecture uses the same partition layout, unless the default partitioning configuration is overridden. During the RHCOS installation, the size of the root file system is increased to use the remaining available space on the target device.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
5.2.13.3.2.1. Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the ISO or PXE manual installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
5.2.13.3.2.2. Retaining existing partitions
For an ISO installation, you can add options to the coreos-installer command line that causes the installer to maintain one or more existing partitions. For a PXE installation, you can APPEND coreos.inst.* options to preserve partitions.
Saved partitions might be partitions from an existing OpenShift Container Platform system that has data partitions that you want to keep. Here are a few tips:
- If you save existing partitions, and those partitions do not leave enough space for RHCOS, installation will fail without damaging the saved partitions.
- Identify the disk partitions you want to keep either by partition label or by number.
For an ISO installation
This example preserves any partition in which the partition label begins with data (data*):
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
The following example illustrates running the coreos-installer in a way that preserves the sixth (6) partition on the disk:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sdaThis example preserves partitions 5 and higher:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
--save-partindex 5- /dev/sda
In the previous examples where partition saving is used, coreos-installer recreates the partition immediately.
For a PXE installation
This APPEND option preserves any partition in which the partition label begins with 'data' ('data*'):
coreos.inst.save_partlabel=data*
coreos.inst.save_partlabel=data*
This APPEND option preserves partitions 5 and higher:
coreos.inst.save_partindex=5-
coreos.inst.save_partindex=5-
This APPEND option preserves partition 6:
coreos.inst.save_partindex=6
coreos.inst.save_partindex=65.2.13.3.3. Identifying Ignition configs
When doing an RHCOS manual installation, there are two types of Ignition configs that you can provide, with different reasons for providing each one:
Permanent install Ignition config: Every manual RHCOS installation needs to pass one of the Ignition config files generated by
openshift-installer, such asbootstrap.ign,master.ignandworker.ign, to carry out the installation.ImportantIt is not recommended to modify these files.
For PXE installations, you pass the Ignition configs on the
APPENDline using thecoreos.inst.ignition_url=option. For ISO installations, after the ISO boots to the shell prompt, you identify the Ignition config on thecoreos-installercommand line with the--ignition-url=option. In both cases, only HTTP and HTTPS protocols are supported.Live install Ignition config: This type must be created manually and should be avoided if possible, as it is not supported by Red Hat. With this method, the Ignition config passes to the live install medium, runs immediately upon booting, and performs setup tasks before and/or after the RHCOS system installs to disk. This method should only be used for performing tasks that must be performed once and not applied again later, such as with advanced partitioning that cannot be done using a machine config.
For PXE or ISO boots, you can create the Ignition config and
APPENDtheignition.config.url=option to identify the location of the Ignition config. You also need to appendignition.firstboot ignition.platform.id=metalor theignition.config.urloption will be ignored.
5.2.13.3.3.1. Embedding an Ignition config in the RHCOS ISO
You can embed a live install Ignition config directly in an RHCOS ISO image. When the ISO image is booted, the embedded config will be applied automatically.
Procedure
-
Download the
coreos-installerbinary from the following image mirror page: https://mirror.openshift.com/pub/openshift-v4/clients/coreos-installer/latest/. Retrieve the RHCOS ISO image and the Ignition config file, and copy them into an accessible directory, such as
/mnt:cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ chmod 644 /mnt/rhcos-<version>-live.x86_64.iso
# cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ # chmod 644 /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to embed the Ignition config into the ISO:
./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.iso# ./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now use that ISO to install RHCOS using the specified live install Ignition config.
ImportantUsing
coreos-installer iso ignition embedto embed a file generated byopenshift-installer, such asbootstrap.ign,master.ignandworker.ign, is unsupported and not recommended.To show the contents of the embedded Ignition config and direct it into a file, run:
./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ign
# ./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow diff -s bootstrap.ign mybootstrap.ign
# diff -s bootstrap.ign mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Files bootstrap.ign and mybootstrap.ign are identical
Files bootstrap.ign and mybootstrap.ign are identicalCopy to Clipboard Copied! Toggle word wrap Toggle overflow To remove the Ignition config and return the ISO to its pristine state so you can reuse it, run:
./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.iso
# ./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now embed another Ignition config into the ISO or use the ISO in its pristine state.
5.2.13.3.4. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
coreos.inst boot options for ISO or PXE install
While you can pass most standard installation boot arguments to the live installer, there are several arguments that are specific to the RHCOS live installer.
- For ISO, these options can be added by interrupting the RHCOS installer.
-
For PXE or iPXE, these options must be added to the
APPENDline before starting the PXE kernel. You cannot interrupt a live PXE install.
The following table shows the RHCOS live installer boot options for ISO and PXE installs.
| Argument | Description |
|---|---|
|
|
Required. The block device on the system to install to. It is recommended to use the full path, such as |
|
| Optional: The URL of the Ignition config to embed into the installed system. If no URL is specified, no Ignition config is embedded. |
|
| Optional: Comma-separated labels of partitions to preserve during the install. Glob-style wildcards are permitted. The specified partitions do not need to exist. |
|
|
Optional: Comma-separated indexes of partitions to preserve during the install. Ranges |
|
|
Optional: Permits the OS image that is specified by |
|
| Optional: Download and install the specified RHCOS image.
|
|
| Optional: The system will not reboot after installing. Once the install finishes, you will receive a prompt that allows you to inspect what is happening during installation. This argument should not be used in production environments and is intended for debugging purposes only. |
|
|
Optional: The Ignition platform ID of the platform the RHCOS image is being installed on. Default is |
|
|
Optional: The URL of the Ignition config for the live boot. For example, this can be used to customize how |
coreos-installer options for ISO install
You can also install RHCOS by invoking the coreos-installer command directly from the command line. The kernel arguments in the previous table provide a shortcut for automatically invoking coreos-installer at boot time, but you can pass similar arguments directly to coreos-installer when running it from a shell prompt.
The following table shows the options and subcommands you can pass to the coreos-installer command from a shell prompt during a live install.
| Command-line options | |
| Option | Description |
|
| Specify the image URL manually. |
|
| Specify a local image file manually. |
|
| Embed an Ignition config from a file. |
|
| Embed an Ignition config from a URL. |
|
|
Digest |
|
| Override the Ignition platform ID. |
|
| Append the default kernel argument. |
|
| Delete the default kernel argument. |
|
| Copy the network configuration from the install environment. Important
The |
|
|
For use with |
|
| Save partitions with this label glob. |
|
| Save partitions with this number or range. |
|
| Force offline installation. |
|
| Skip signature verification. |
|
| Allow Ignition URL without HTTPS or hash. |
|
|
Target CPU architecture. Default is |
|
| Do not clear partition table on error. |
|
| Print help information. |
| Command-line argument | |
| Argument | Description |
|
| The destination device. |
| coreos-installer embedded Ignition commands | |
| Command | Description |
|
| Embed an Ignition config in an ISO image. |
|
| Show the embedded Ignition config from an ISO image. |
|
| Remove the embedded Ignition config from an ISO image. |
| coreos-installer ISO Ignition options | |
| Option | Description |
|
| Overwrite an existing Ignition config. |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
| coreos-installer PXE Ignition commands | |
| Command | Description |
| Note that not all of these options are accepted by all subcommands. | |
|
| Wrap an Ignition config in an image. |
|
| Show the wrapped Ignition config in an image. |
|
|
Show the wrapped Ignition config in an |
| coreos-installer PXE Ignition options | |
| Option | Description |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
5.2.14. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
5.2.15. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.2.16. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
5.2.17. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
5.2.17.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
5.2.17.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
5.2.17.3. Configuring block registry storage
To allow the image registry to use block storage types during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with the image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only one (1) replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
- Edit the registry configuration so that it references the correct PVC.
5.2.18. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
5.2.19. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
5.2.20. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
5.3. Installing a cluster on bare metal in a restricted network
In OpenShift Container Platform version 4.6, you can install a cluster on bare metal infrastructure that you provision in a restricted network.
While you might be able to follow this procedure to deploy a cluster on virtualized or cloud environments, you must be aware of additional considerations for non-bare metal platforms. Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you attempt to install an OpenShift Container Platform cluster in such an environment.
5.3.1. Prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
- Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide ReadWriteMany access modes.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
5.3.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
5.3.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
5.3.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
5.3.4. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
5.3.4.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines. If you are running a three-node cluster, running zero compute machines is supported. Running one compute machine is not supported.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
5.3.4.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
5.3.4.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | CPU [1] | RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One CPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = CPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
5.3.4.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
5.3.5. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
5.3.5.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 5.34. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 5.35. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers. :!restricted:
5.3.5.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 5.5. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 5.6. Sample DNS zone database for reverse records
5.3.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
5.3.7. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
-
Obtain the
imageContentSourcessection from the output of the command to mirror the repository. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.-
Unless you use a registry that RHCOS trusts by default, such as
docker.io, you must provide the contents of the certificate for your mirror repository in theadditionalTrustBundlesection. In most cases, you must provide the certificate for your mirror. -
You must include the
imageContentSourcessection from the output of the command to mirror the repository.
-
Unless you use a registry that RHCOS trusts by default, such as
Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
5.3.7.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
5.3.7.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
5.3.7.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
5.3.7.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
5.3.7.2. Sample install-config.yaml file for bare metal
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for your platform. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 16
- Provide the contents of the certificate file that you used for your mirror registry.
- 17
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
5.3.7.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
For bare metal installations, if you do not assign node IP addresses from the range that is specified in the networking.machineNetwork[].cidr field in the install-config.yaml file, you must include them in the proxy.noProxy field.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
5.3.8. Configuring a three-node cluster
You can optionally install and run three-node clusters in OpenShift Container Platform with no workers. This provides smaller, more resource efficient clusters for cluster administrators and developers to use for development, production, and testing.
Procedure
Edit the
install-config.yamlfile to set the number of compute replicas, which are also known as worker replicas, to0, as shown in the followingcomputestanza:compute: - name: worker platform: {} replicas: 0compute: - name: worker platform: {} replicas: 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3.9. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program. For a restricted network installation, these files are on your mirror host.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
If you are installing a three-node cluster, skip the following step to allow the control plane nodes to be schedulable.
+
When you configure control plane nodes from the default unschedulable to schedulable, additional subscriptions are required. This is because control plane nodes then become worker nodes.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3.10. Configuring chrony time service
You must set the time server and related settings used by the chrony time service (chronyd) by modifying the contents of the chrony.conf file and passing those contents to your nodes as a machine config.
Procedure
Create the contents of the
chrony.conffile and encode it as base64. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify any valid, reachable time source, such as the one provided by your DHCP server.
Example output
ICAgIHNlcnZlciBjbG9jay5yZWRoYXQuY29tIGlidXJzdAogICAgZHJpZnRmaWxlIC92YXIvbGli L2Nocm9ueS9kcmlmdAogICAgbWFrZXN0ZXAgMS4wIDMKICAgIHJ0Y3N5bmMKICAgIGxvZ2RpciAv dmFyL2xvZy9jaHJvbnkK
ICAgIHNlcnZlciBjbG9jay5yZWRoYXQuY29tIGlidXJzdAogICAgZHJpZnRmaWxlIC92YXIvbGli L2Nocm9ueS9kcmlmdAogICAgbWFrZXN0ZXAgMS4wIDMKICAgIHJ0Y3N5bmMKICAgIGxvZ2RpciAv dmFyL2xvZy9jaHJvbnkKCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
MachineConfigobject file, replacing the base64 string with the one you just created. This example adds the file tomasternodes. You can change it toworkeror make an additional MachineConfig for theworkerrole. Create MachineConfig files for each type of machine that your cluster uses:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify an octal value mode for the
modefield in the machine config file. After creating the file and applying the changes, themodeis converted to a decimal value. You can check the YAML file with the commandoc get mc <mc-name> -o yaml.
- Make a backup copy of the configuration files.
Apply the configurations in one of two ways:
-
If the cluster is not up yet, after you generate manifest files, add this file to the
<installation_directory>/openshiftdirectory, and then continue to create the cluster. If the cluster is already running, apply the file:
oc apply -f ./99-masters-chrony-configuration.yaml
$ oc apply -f ./99-masters-chrony-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
If the cluster is not up yet, after you generate manifest files, add this file to the
5.3.11. Installing RHCOS and starting the OpenShift Container Platform bootstrap process
To install OpenShift Container Platform on bare metal infrastructure that you provision, you must install Red Hat Enterprise Linux CoreOS (RHCOS) on the machines. When you install RHCOS, you must provide the Ignition config file that was generated by the OpenShift Container Platform installation program for the type of machine you are installing. If you have configured suitable networking, DNS, and load balancing infrastructure, the OpenShift Container Platform bootstrap process begins automatically after the RHCOS machines have rebooted.
To install RHCOS on the machines, follow either the steps to use an ISO image or network PXE booting.
The compute node deployment steps included in this installation document are RHCOS-specific. If you choose instead to deploy RHEL-based compute nodes, you take responsibility for all operating system life cycle management and maintenance, including performing system updates, applying patches, and completing all other required tasks. Use of RHEL 7 compute machines is deprecated and planned for removal in a future release of OpenShift Container Platform 4.
You can configure RHCOS during ISO and PXE installations by using the following methods:
-
Kernel arguments: You can use kernel arguments to provide installation-specific information. For example, you can specify the locations of the RHCOS installation files that you uploaded to your HTTP server and the location of the Ignition config file for the type of node you are installing. For a PXE installation, you can use the
APPENDparameter to pass the arguments to the kernel of the live installer. For an ISO installation, you can interrupt the live installation boot process to add the kernel arguments. In both installation cases, you can use specialcoreos.inst.*arguments to direct the live installer, as well as standard installation boot arguments for turning standard kernel services on or off. -
Ignition configs: OpenShift Container Platform Ignition config files (
*.ign) are specific to the type of node you are installing. You pass the location of a bootstrap, control plane, or compute node Ignition config file during the RHCOS installation so that it takes effect on first boot. In special cases, you can create a separate, limited Ignition config to pass to the live system. That Ignition config could do a certain set of tasks, such as reporting success to a provisioning system after completing installation. This special Ignition config is consumed by thecoreos-installerto be applied on first boot of the installed system. Do not provide the standard control plane and compute node Ignition configs to the live ISO directly. -
coreos-installer: You can boot the live ISO installer to a shell prompt, which allows you to prepare the permanent system in a variety of ways before first boot. In particular, you can run thecoreos-installercommand to identify various artifacts to include, work with disk partitions, and set up networking. In some cases, you can configure features on the live system and copy them to the installed system.
Whether to use an ISO or PXE install depends on your situation. A PXE install requires an available DHCP service and more preparation, but can make the installation process more automated. An ISO install is a more manual process and can be inconvenient if you are setting up more than a few machines.
As of OpenShift Container Platform 4.6, the RHCOS ISO and other installation artifacts provide support for installation on disks with 4K sectors.
5.3.11.1. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines using an ISO image
Before you install a cluster on infrastructure that you provision, you must create RHCOS machines for it to use. You can use an ISO image to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Have access to an HTTP server that can be accessed from your computer, and from the machines that you create.
Procedure
Upload the control plane, compute, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS images that are required for your preferred method of installing operating system instances from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available. Use only ISO images for this procedure. RHCOS qcow2 images are not supported for this installation type.
ISO file names resemble the following example:
rhcos-<version>-live.<architecture>.isoUse the ISO to start the RHCOS installation. Use one of the following installation options:
- Burn the ISO image to a disk and boot it directly.
- Use ISO redirection via a LOM interface.
-
Boot the ISO image. You can interrupt the installation boot process to add kernel arguments. However, for this ISO procedure you should use the
coreos-installercommand instead of adding kernel arguments. If you run the live installer without options or interruption, the installer boots up to a shell prompt on the live system, ready for you to install RHCOS to disk. -
Review the Advanced RHCOS installation reference section for different ways of configuring features, such as networking and disk partitions, before running the
coreos-installer. Run the
coreos-installercommand. At a minimum, you must identify the Ignition config file location for your node type, and the location of the disk you are installing to. Here is an example:sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sda$ sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After RHCOS installs, the system reboots. During the system reboot, it applies the Ignition config file that you specified.
Continue to create the other machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
5.3.11.2. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines by PXE or iPXE booting
Before you install a cluster that uses manually-provisioned RHCOS nodes, such as bare metal, you must create RHCOS machines for it to use. You can use PXE or iPXE booting to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Configure suitable PXE or iPXE infrastructure.
- Have access to an HTTP server that you can access from your computer.
Procedure
Upload the master, worker, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantYou can add or change configuration settings in your Ignition configs before saving them to your HTTP server. If you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS
kernel,initramfsandrootfsfiles from the RHCOS image mirror page.ImportantThe RHCOS artifacts might not change with every release of OpenShift Container Platform. You must download artifacts with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate
kernel,initramfs, androotfsartifacts described below for this procedure. RHCOS qcow2 images are not supported for this installation type.The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:rhcos-<version>-live-kernel-<architecture> -
initramfs:rhcos-<version>-live-initramfs.<architecture>.img -
rootfs:rhcos-<version>-live-rootfs.<architecture>.img
-
Upload the additional files that are required for your booting method:
-
For traditional PXE, upload the
kernelandinitramfsfiles to your TFTP server and therootfsfile to your HTTP server. For iPXE, upload the
kernel,initramfs, androotfsfiles to your HTTP server.ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
-
For traditional PXE, upload the
- Configure the network boot infrastructure so that the machines boot from their local disks after RHCOS is installed on them.
Configure PXE or iPXE installation for the RHCOS images.
Modify one of the following example menu entries for your environment and verify that the image and Ignition files are properly accessible:
For PXE:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the location of the live
kernelfile that you uploaded to your HTTP server. The URL must be HTTP, TFTP, or FTP; HTTPS and NFS are not supported. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
initrdparameter value is the location of theinitramfsfile, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. You can also add more kernel arguments to theAPPENDline to configure networking or other boot options.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to theAPPENDline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.For iPXE:
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img boot
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign1 2 initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img3 bootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
kernelparameter value is the location of thekernelfile, theinitrd=mainargument is needed for booting on UEFI systems, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify the location of the
initramfsfile that you uploaded to your HTTP server.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to thekernelline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.
If you use PXE UEFI, perform the following actions:
Provide the
shimx64.efiandgrubx64.efiEFI binaries and thegrub.cfgfile that are required for booting the system.Extract the necessary EFI binaries by mounting the RHCOS ISO to your host and then mounting the
images/efiboot.imgfile to your host:mkdir -p /mnt/iso
$ mkdir -p /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p /mnt/efiboot
$ mkdir -p /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop rhcos-installer.x86_64.iso /mnt/iso
$ mount -o loop rhcos-installer.x86_64.iso /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efiboot
$ mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the
efiboot.imgmount point, copy theEFI/redhat/shimx64.efiandEFI/redhat/grubx64.efifiles to your TFTP server:cp /mnt/efiboot/EFI/redhat/shimx64.efi .
$ cp /mnt/efiboot/EFI/redhat/shimx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp /mnt/efiboot/EFI/redhat/grubx64.efi .
$ cp /mnt/efiboot/EFI/redhat/grubx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/efiboot
$ umount /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/iso
$ umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the
EFI/redhat/grub.cfgfile that is included in the RHCOS ISO to your TFTP server.
Edit the
grub.cfgfile to include arguments similar to the following:menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
rhcos-<version>-live-kernel-<architecture>-
Specifies the
kernelfile that you uploaded to your TFTP server. http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img- Specifies the location of the live rootfs image that you uploaded to your HTTP server.
http://<HTTP_server>/bootstrap.ign- Specifies the location of the bootstrap Ignition config file that you uploaded to your HTTP server.
rhcos-<version>-live-initramfs.<architecture>.img-
Specifies the location of the
initramfsfile that you uploaded to your TFTP server.
NoteFor more information on how to configure a PXE server for UEFI boot, see the Red Hat Knowledgebase article: How to configure/setup a PXE server for UEFI boot for Red Hat Enterprise Linux?.
Continue to create the machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
5.3.11.3. Advanced Red Hat Enterprise Linux CoreOS (RHCOS) installation configuration
A key benefit for manually provisioning the Red Hat Enterprise Linux CoreOS (RHCOS) nodes for OpenShift Container Platform is to be able to do configuration that is not available through default OpenShift Container Platform installation methods. This section describes some of the configurations that you can do using techniques that include:
- Passing kernel arguments to the live installer
-
Running
coreos-installermanually from the live system - Embedding Ignition configs in an ISO
The advanced configuration topics for manual Red Hat Enterprise Linux CoreOS (RHCOS) installations detailed in this section relate to disk partitioning, networking, and using Ignition configs in different ways.
5.3.11.3.1. Using advanced networking options for PXE and ISO installations
Networking for OpenShift Container Platform nodes uses DHCP by default to gather all necessary configuration settings. To set up static IP addresses or configure special settings, such as bonding, you can do one of the following:
- Pass special kernel parameters when you boot the live installer.
- Use a machine config to copy networking files to the installed system.
- Configure networking from a live installer shell prompt, then copy those settings to the installed system so that they take effect when the installed system first boots.
To configure a PXE or iPXE installation, use one of the following options:
- See the "Advanced RHCOS installation reference" tables.
- Use a machine config to copy networking files to the installed system.
To configure an ISO installation, use the following procedure.
Procedure
- Boot the ISO installer.
-
From the live system shell prompt, configure networking for the live system using available RHEL tools, such as
nmcliornmtui. Run the
coreos-installercommand to install the system, adding the--copy-networkoption to copy networking configuration. For example:coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sda$ coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe
--copy-networkoption only copies networking configuration found under/etc/NetworkManager/system-connections. In particular, it does not copy the system hostname.- Reboot into the installed system.
5.3.11.3.2. Disk partitioning
The disk partitions are created on OpenShift Container Platform cluster nodes during the Red Hat Enterprise Linux CoreOS (RHCOS) installation. Each RHCOS node of a particular architecture uses the same partition layout, unless the default partitioning configuration is overridden. During the RHCOS installation, the size of the root file system is increased to use the remaining available space on the target device.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
5.3.11.3.2.1. Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the ISO or PXE manual installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
5.3.11.3.2.2. Retaining existing partitions
For an ISO installation, you can add options to the coreos-installer command line that causes the installer to maintain one or more existing partitions. For a PXE installation, you can APPEND coreos.inst.* options to preserve partitions.
Saved partitions might be partitions from an existing OpenShift Container Platform system that has data partitions that you want to keep. Here are a few tips:
- If you save existing partitions, and those partitions do not leave enough space for RHCOS, installation will fail without damaging the saved partitions.
- Identify the disk partitions you want to keep either by partition label or by number.
For an ISO installation
This example preserves any partition in which the partition label begins with data (data*):
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
The following example illustrates running the coreos-installer in a way that preserves the sixth (6) partition on the disk:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sdaThis example preserves partitions 5 and higher:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
--save-partindex 5- /dev/sda
In the previous examples where partition saving is used, coreos-installer recreates the partition immediately.
For a PXE installation
This APPEND option preserves any partition in which the partition label begins with 'data' ('data*'):
coreos.inst.save_partlabel=data*
coreos.inst.save_partlabel=data*
This APPEND option preserves partitions 5 and higher:
coreos.inst.save_partindex=5-
coreos.inst.save_partindex=5-
This APPEND option preserves partition 6:
coreos.inst.save_partindex=6
coreos.inst.save_partindex=65.3.11.3.3. Identifying Ignition configs
When doing an RHCOS manual installation, there are two types of Ignition configs that you can provide, with different reasons for providing each one:
Permanent install Ignition config: Every manual RHCOS installation needs to pass one of the Ignition config files generated by
openshift-installer, such asbootstrap.ign,master.ignandworker.ign, to carry out the installation.ImportantIt is not recommended to modify these files.
For PXE installations, you pass the Ignition configs on the
APPENDline using thecoreos.inst.ignition_url=option. For ISO installations, after the ISO boots to the shell prompt, you identify the Ignition config on thecoreos-installercommand line with the--ignition-url=option. In both cases, only HTTP and HTTPS protocols are supported.Live install Ignition config: This type must be created manually and should be avoided if possible, as it is not supported by Red Hat. With this method, the Ignition config passes to the live install medium, runs immediately upon booting, and performs setup tasks before and/or after the RHCOS system installs to disk. This method should only be used for performing tasks that must be performed once and not applied again later, such as with advanced partitioning that cannot be done using a machine config.
For PXE or ISO boots, you can create the Ignition config and
APPENDtheignition.config.url=option to identify the location of the Ignition config. You also need to appendignition.firstboot ignition.platform.id=metalor theignition.config.urloption will be ignored.
5.3.11.3.3.1. Embedding an Ignition config in the RHCOS ISO
You can embed a live install Ignition config directly in an RHCOS ISO image. When the ISO image is booted, the embedded config will be applied automatically.
Procedure
-
Download the
coreos-installerbinary from the following image mirror page: https://mirror.openshift.com/pub/openshift-v4/clients/coreos-installer/latest/. Retrieve the RHCOS ISO image and the Ignition config file, and copy them into an accessible directory, such as
/mnt:cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ chmod 644 /mnt/rhcos-<version>-live.x86_64.iso
# cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ # chmod 644 /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to embed the Ignition config into the ISO:
./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.iso# ./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now use that ISO to install RHCOS using the specified live install Ignition config.
ImportantUsing
coreos-installer iso ignition embedto embed a file generated byopenshift-installer, such asbootstrap.ign,master.ignandworker.ign, is unsupported and not recommended.To show the contents of the embedded Ignition config and direct it into a file, run:
./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ign
# ./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow diff -s bootstrap.ign mybootstrap.ign
# diff -s bootstrap.ign mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Files bootstrap.ign and mybootstrap.ign are identical
Files bootstrap.ign and mybootstrap.ign are identicalCopy to Clipboard Copied! Toggle word wrap Toggle overflow To remove the Ignition config and return the ISO to its pristine state so you can reuse it, run:
./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.iso
# ./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now embed another Ignition config into the ISO or use the ISO in its pristine state.
5.3.11.3.4. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
coreos.inst boot options for ISO or PXE install
While you can pass most standard installation boot arguments to the live installer, there are several arguments that are specific to the RHCOS live installer.
- For ISO, these options can be added by interrupting the RHCOS installer.
-
For PXE or iPXE, these options must be added to the
APPENDline before starting the PXE kernel. You cannot interrupt a live PXE install.
The following table shows the RHCOS live installer boot options for ISO and PXE installs.
| Argument | Description |
|---|---|
|
|
Required. The block device on the system to install to. It is recommended to use the full path, such as |
|
| Optional: The URL of the Ignition config to embed into the installed system. If no URL is specified, no Ignition config is embedded. |
|
| Optional: Comma-separated labels of partitions to preserve during the install. Glob-style wildcards are permitted. The specified partitions do not need to exist. |
|
|
Optional: Comma-separated indexes of partitions to preserve during the install. Ranges |
|
|
Optional: Permits the OS image that is specified by |
|
| Optional: Download and install the specified RHCOS image.
|
|
| Optional: The system will not reboot after installing. Once the install finishes, you will receive a prompt that allows you to inspect what is happening during installation. This argument should not be used in production environments and is intended for debugging purposes only. |
|
|
Optional: The Ignition platform ID of the platform the RHCOS image is being installed on. Default is |
|
|
Optional: The URL of the Ignition config for the live boot. For example, this can be used to customize how |
coreos-installer options for ISO install
You can also install RHCOS by invoking the coreos-installer command directly from the command line. The kernel arguments in the previous table provide a shortcut for automatically invoking coreos-installer at boot time, but you can pass similar arguments directly to coreos-installer when running it from a shell prompt.
The following table shows the options and subcommands you can pass to the coreos-installer command from a shell prompt during a live install.
| Command-line options | |
| Option | Description |
|
| Specify the image URL manually. |
|
| Specify a local image file manually. |
|
| Embed an Ignition config from a file. |
|
| Embed an Ignition config from a URL. |
|
|
Digest |
|
| Override the Ignition platform ID. |
|
| Append the default kernel argument. |
|
| Delete the default kernel argument. |
|
| Copy the network configuration from the install environment. Important
The |
|
|
For use with |
|
| Save partitions with this label glob. |
|
| Save partitions with this number or range. |
|
| Force offline installation. |
|
| Skip signature verification. |
|
| Allow Ignition URL without HTTPS or hash. |
|
|
Target CPU architecture. Default is |
|
| Do not clear partition table on error. |
|
| Print help information. |
| Command-line argument | |
| Argument | Description |
|
| The destination device. |
| coreos-installer embedded Ignition commands | |
| Command | Description |
|
| Embed an Ignition config in an ISO image. |
|
| Show the embedded Ignition config from an ISO image. |
|
| Remove the embedded Ignition config from an ISO image. |
| coreos-installer ISO Ignition options | |
| Option | Description |
|
| Overwrite an existing Ignition config. |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
| coreos-installer PXE Ignition commands | |
| Command | Description |
| Note that not all of these options are accepted by all subcommands. | |
|
| Wrap an Ignition config in an image. |
|
| Show the wrapped Ignition config in an image. |
|
|
Show the wrapped Ignition config in an |
| coreos-installer PXE Ignition options | |
| Option | Description |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
5.3.12. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
5.3.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3.14. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
5.3.15. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
5.3.15.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
5.3.15.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
5.3.15.2.1. Changing the image registry’s management state
To start the image registry, you must change the Image Registry Operator configuration’s managementState from Removed to Managed.
Procedure
Change
managementStateImage Registry Operator configuration fromRemovedtoManaged. For example:oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"managementState":"Managed"}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"managementState":"Managed"}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3.15.2.2. Configuring registry storage for bare metal and other manual installations
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster that uses manually-provisioned Red Hat Enterprise Linux CoreOS (RHCOS) nodes, such as bare metal.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
5.3.15.2.3. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
5.3.15.2.4. Configuring block registry storage
To allow the image registry to use block storage types during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with the image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only one (1) replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
- Edit the registry configuration so that it references the correct PVC.
5.3.16. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
- Register your cluster on the Cluster registration page.
5.3.17. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
5.3.18. Next steps
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
Chapter 6. Deploying installer-provisioned clusters on bare metal
6.1. Overview
Installer-provisioned installation provides support for installing OpenShift Container Platform on bare metal nodes. This guide provides a methodology to achieving a successful installation.
During installer-provisioned installation on bare metal, the installer on the bare metal node labeled as provisioner creates a bootstrap VM. The role of the bootstrap VM is to assist in the process of deploying an OpenShift Container Platform cluster. The bootstrap VM connects to the baremetal network and to the provisioning network, if present, via the network bridges.
When the installation of OpenShift Container Platform control plane nodes is complete and fully operational, the installer destroys the bootstrap VM automatically and moves the virtual IP addresses (VIPs) to the appropriate nodes accordingly. The API VIP moves to the control plane nodes and the Ingress VIP moves to the worker nodes.
6.2. Prerequisites
Installer-provisioned installation of OpenShift Container Platform requires:
- One provisioner node with Red Hat Enterprise Linux (RHEL) 8.x installed.
- Three control plane nodes.
- Baseboard Management Controller (BMC) access to each node.
At least one network:
- One required routable network
- One optional network for provisioning nodes; and,
- One optional management network.
Before starting an installer-provisioned installation of OpenShift Container Platform, ensure the hardware environment meets the following requirements.
6.2.1. Node requirements
Installer-provisioned installation involves a number of hardware node requirements:
-
CPU architecture: All nodes must use
x86_64CPU architecture. - Similar nodes: Red Hat recommends nodes have an identical configuration per role. That is, Red Hat recommends nodes be the same brand and model with the same CPU, memory, and storage configuration.
-
Baseboard Management Controller: The
provisionernode must be able to access the baseboard management controller (BMC) of each OpenShift Container Platform cluster node. You may use IPMI, RedFish, or a proprietary protocol. -
Latest generation: Nodes must be of the most recent generation. Because the installer-provisioned installation relies on BMC protocols, the hardware must support IPMI cipher suite 17. Additionally, RHEL 8 ships with the most recent drivers for RAID controllers. Ensure that the nodes are recent enough to support RHEL 8 for the
provisionernode and RHCOS 8 for the control plane and worker nodes. - Registry node: Optional: If setting up a disconnected mirrored registry, it is recommended the registry reside in its own node.
-
Provisioner node: Installer-provisioned installation requires one
provisionernode. - Control plane: Installer-provisioned installation requires three control plane nodes for high availability.
- Worker nodes: While not required, a typical production cluster has one or more worker nodes. Smaller clusters are more resource efficient for administrators and developers during development and testing.
-
Network interfaces: Each node must have at least one network interface for the routable
baremetalnetwork. Each node must have one network interface for aprovisioningnetwork when using theprovisioningnetwork for deployment. Using theprovisioningnetwork is the default configuration. Network interface naming must be consistent across control plane nodes for the provisioning network. For example, if a control plane node uses theeth0NIC for the provisioning network, the other control plane nodes must use it as well. -
Unified Extensible Firmware Interface (UEFI): Installer-provisioned installation requires UEFI boot on all OpenShift Container Platform nodes when using IPv6 addressing on the
provisioningnetwork. In addition, UEFI Device PXE Settings must be set to use the IPv6 protocol on theprovisioningnetwork NIC, but omitting theprovisioningnetwork removes this requirement.
6.2.2. Network requirements
Installer-provisioned installation of OpenShift Container Platform involves several network requirements by default. First, installer-provisioned installation involves a non-routable provisioning network for provisioning the operating system on each bare metal node and a routable baremetal network. Since installer-provisioned installation deploys ironic-dnsmasq, the networks should have no other DHCP servers running on the same broadcast domain. Network administrators must reserve IP addresses for each node in the OpenShift Container Platform cluster.
Network Time Protocol (NTP)
It is recommended that each OpenShift Container Platform node in the cluster have access to a Network Time Protocol (NTP) server that is discoverable using DHCP. While installation without an NTP server is possible, asynchronous server clocks can cause errors. Using an NTP server can prevent this issue.
Configuring NICs
OpenShift Container Platform deploys with two networks:
-
provisioning: Theprovisioningnetwork is an optional non-routable network used for provisioning the underlying operating system on each node that is a part of the OpenShift Container Platform cluster. When deploying using theprovisioningnetwork, the first NIC on each node, such aseth0oreno1, must interface with theprovisioningnetwork. -
baremetal: Thebaremetalnetwork is a routable network. When deploying using theprovisioningnetwork, the second NIC on each node, such aseth1oreno2, must interface with thebaremetalnetwork. When deploying without aprovisioningnetwork, you can use any NIC on each node to interface with thebaremetalnetwork.
Each NIC should be on a separate VLAN corresponding to the appropriate network.
Configuring the DNS server
Clients access the OpenShift Container Platform cluster nodes over the baremetal network. A network administrator must configure a subdomain or subzone where the canonical name extension is the cluster name.
<cluster-name>.<domain-name>
<cluster-name>.<domain-name>For example:
test-cluster.example.com
test-cluster.example.comReserving IP addresses for nodes with the DHCP server
For the baremetal network, a network administrator must reserve a number of IP addresses, including:
Two virtual IP addresses.
- One IP address for the API endpoint
- One IP address for the wildcard Ingress endpoint
- One IP address for the provisioner node.
- One IP address for each control plane (master) node.
- One IP address for each worker node, if applicable.
The following table provides an exemplary embodiment of fully-qualified domain names. The API and Nameserver addresses begin with canonical name extensions. The hostnames of the control plane and worker nodes are exemplary, so you can use any host naming convention you prefer.
| Usage | Hostname | IP |
|---|---|---|
| API | api.<cluster-name>.<domain> | <ip> |
| Ingress LB (apps) | *.apps.<cluster-name>.<domain> | <ip> |
| Provisioner node | provisioner.<cluster-name>.<domain> | <ip> |
| Master-0 | openshift-master-0.<cluster-name>.<domain> | <ip> |
| Master-1 | openshift-master-1.<cluster-name>-.<domain> | <ip> |
| Master-2 | openshift-master-2.<cluster-name>.<domain> | <ip> |
| Worker-0 | openshift-worker-0.<cluster-name>.<domain> | <ip> |
| Worker-1 | openshift-worker-1.<cluster-name>.<domain> | <ip> |
| Worker-n | openshift-worker-n.<cluster-name>.<domain> | <ip> |
Additional requirements with no provisioning network
All installer-provisioned installations require a baremetal network. The baremetal network is a routable network used for external network access to the outside world. In addition to the IP address supplied to the OpenShift Container Platform cluster node, installations without a provisioning network require the following:
-
Setting an available IP address from the
baremetalnetwork to thebootstrapProvisioningIPconfiguration setting within theinstall-config.yamlconfiguration file. -
Setting an available IP address from the
baremetalnetwork to theprovisioningHostIPconfiguration setting within theinstall-config.yamlconfiguration file. - Deploying the OpenShift Container Platform cluster using RedFish Virtual Media/iDRAC Virtual Media.
Configuring additional IP addresses for bootstrapProvisioningIP and provisioningHostIP is not required when using a provisioning network.
Port access for the out-of-band management IP address
The out-of-band management IP address is on a separate network from the node. To ensure that the out-of-band management can communicate with the baremetal node during installation, the out-of-band management IP address address must be granted access to the TCP 6180 port.
6.2.3. Configuring nodes
Configuring nodes when using the provisioning network
Each node in the cluster requires the following configuration for proper installation.
A mismatch between nodes will cause an installation failure.
While the cluster nodes can contain more than two NICs, the installation process only focuses on the first two NICs:
| NIC | Network | VLAN |
| NIC1 |
| <provisioning-vlan> |
| NIC2 |
| <baremetal-vlan> |
NIC1 is a non-routable network (provisioning) that is only used for the installation of the OpenShift Container Platform cluster.
The Red Hat Enterprise Linux (RHEL) 8.x installation process on the provisioner node might vary. To install Red Hat Enterprise Linux (RHEL) 8.x using a local Satellite server or a PXE server, PXE-enable NIC2.
| PXE | Boot order |
|
NIC1 PXE-enabled | 1 |
|
NIC2 | 2 |
Ensure PXE is disabled on all other NICs.
Configure the control plane and worker nodes as follows:
| PXE | Boot order |
| NIC1 PXE-enabled (provisioning network) | 1 |
Configuring nodes without the provisioning network
The installation process requires one NIC:
| NIC | Network | VLAN |
| NICx |
| <baremetal-vlan> |
NICx is a routable network (baremetal) that is used for the installation of the OpenShift Container Platform cluster, and routable to the Internet.
6.2.4. Out-of-band management
Nodes will typically have an additional NIC used by the Baseboard Management Controllers (BMCs). These BMCs must be accessible from the provisioner node.
Each node must be accessible via out-of-band management. When using an out-of-band management network, the provisioner node requires access to the out-of-band management network for a successful OpenShift Container Platform 4 installation.
The out-of-band management setup is out of scope for this document. We recommend setting up a separate management network for out-of-band management. However, using the provisioning network or the baremetal network are valid options.
6.2.5. Required data for installation
Prior to the installation of the OpenShift Container Platform cluster, gather the following information from all cluster nodes:
Out-of-band management IP
Examples
- Dell (iDRAC) IP
- HP (iLO) IP
When using the provisioning network
-
NIC1 (
provisioning) MAC address -
NIC2 (
baremetal) MAC address
When omitting the provisioning network
-
NICx (
baremetal) MAC address
6.2.6. Validation checklist for nodes
When using the provisioning network
-
❏ NIC1 VLAN is configured for the
provisioningnetwork. -
❏ NIC2 VLAN is configured for the
baremetalnetwork. - ❏ NIC1 is PXE-enabled on the provisioner, control plane (master), and worker nodes.
- ❏ PXE has been disabled on all other NICs.
- ❏ Control plane and worker nodes are configured.
- ❏ All nodes accessible via out-of-band management.
- ❏ A separate management network has been created. (optional)
- ❏ Required data for installation.
When omitting the provisioning network
-
❏ NICx VLAN is configured for the
baremetalnetwork. - ❏ Control plane and worker nodes are configured.
- ❏ All nodes accessible via out-of-band management.
- ❏ A separate management network has been created. (optional)
- ❏ Required data for installation.
6.3. Setting up the environment for an OpenShift installation
6.3.1. Installing RHEL on the provisioner node
With the networking configuration complete, the next step is to install RHEL 8.x on the provisioner node. The installer uses the provisioner node as the orchestrator while installing the OpenShift Container Platform cluster. For the purposes of this document, installing RHEL on the provisioner node is out of scope. However, options include but are not limited to using a RHEL Satellite server, PXE, or installation media.
6.3.2. Preparing the provisioner node for OpenShift Container Platform installation
Perform the following steps to prepare the environment.
Procedure
-
Log in to the provisioner node via
ssh. Create a non-root user (
kni) and provide that user withsudoprivileges.useradd kni passwd kni echo "kni ALL=(root) NOPASSWD:ALL" | tee -a /etc/sudoers.d/kni chmod 0440 /etc/sudoers.d/kni
# useradd kni # passwd kni # echo "kni ALL=(root) NOPASSWD:ALL" | tee -a /etc/sudoers.d/kni # chmod 0440 /etc/sudoers.d/kniCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an
sshkey for the new user.su - kni -c "ssh-keygen -t ed25519 -f /home/kni/.ssh/id_rsa -N ''"
# su - kni -c "ssh-keygen -t ed25519 -f /home/kni/.ssh/id_rsa -N ''"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Log in as the new user on the provisioner node.
su - kni
# su - kni $Copy to Clipboard Copied! Toggle word wrap Toggle overflow Use Red Hat Subscription Manager to register the provisioner node:
sudo subscription-manager register --username=<user> --password=<pass> --auto-attach sudo subscription-manager repos --enable=rhel-8-for-x86_64-appstream-rpms --enable=rhel-8-for-x86_64-baseos-rpms
$ sudo subscription-manager register --username=<user> --password=<pass> --auto-attach $ sudo subscription-manager repos --enable=rhel-8-for-x86_64-appstream-rpms --enable=rhel-8-for-x86_64-baseos-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteFor more information about Red Hat Subscription Manager, see Using and Configuring Red Hat Subscription Manager.
Install the following packages.
sudo dnf install -y libvirt qemu-kvm mkisofs python3-devel jq ipmitool
$ sudo dnf install -y libvirt qemu-kvm mkisofs python3-devel jq ipmitoolCopy to Clipboard Copied! Toggle word wrap Toggle overflow Modify the user to add the
libvirtgroup to the newly created user.sudo usermod --append --groups libvirt <user>
$ sudo usermod --append --groups libvirt <user>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Restart
firewalldand enable thehttpservice.sudo systemctl start firewalld sudo firewall-cmd --zone=public --add-service=http --permanent sudo firewall-cmd --reload
$ sudo systemctl start firewalld $ sudo firewall-cmd --zone=public --add-service=http --permanent $ sudo firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Start and enable the
libvirtdservice.sudo systemctl enable libvirtd --now
$ sudo systemctl enable libvirtd --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
defaultstorage pool and start it.sudo virsh pool-define-as --name default --type dir --target /var/lib/libvirt/images sudo virsh pool-start default sudo virsh pool-autostart default
$ sudo virsh pool-define-as --name default --type dir --target /var/lib/libvirt/images $ sudo virsh pool-start default $ sudo virsh pool-autostart defaultCopy to Clipboard Copied! Toggle word wrap Toggle overflow Configure networking.
NoteThis step can also be run from the web console.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe
sshconnection might disconnect after executing this step.The IPv6 address can be any address as long as it is not routable via the
baremetalnetwork.Ensure that UEFI is enabled and UEFI PXE settings are set to the IPv6 protocol when using IPv6 addressing.
Configure the IPv4 address on the
provisioningnetwork connection.nmcli connection modify provisioning ipv4.addresses 172.22.0.254/24 ipv4.method manual
$ nmcli connection modify provisioning ipv4.addresses 172.22.0.254/24 ipv4.method manualCopy to Clipboard Copied! Toggle word wrap Toggle overflow sshback into theprovisionernode (if required).ssh kni@provisioner.<cluster-name>.<domain>
# ssh kni@provisioner.<cluster-name>.<domain>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify the connection bridges have been properly created.
sudo nmcli con show
$ sudo nmcli con showCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
pull-secret.txtfile.vim pull-secret.txt
$ vim pull-secret.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow In a web browser, navigate to Install OpenShift on Bare Metal with installer-provisioned infrastructure, and scroll down to the Downloads section. Click Copy pull secret. Paste the contents into the
pull-secret.txtfile and save the contents in thekniuser’s home directory.
6.3.3. Retrieving the OpenShift Container Platform installer
Use the latest-4.x version of the installer to deploy the latest generally available version of OpenShift Container Platform:
export VERSION=latest-4.6
$ export VERSION=latest-4.6
export RELEASE_IMAGE=$(curl -s https://mirror.openshift.com/pub/openshift-v4/clients/ocp/$VERSION/release.txt | grep 'Pull From: quay.io' | awk -F ' ' '{print $3}')6.3.4. Extracting the OpenShift Container Platform installer
After retrieving the installer, the next step is to extract it.
Procedure
Set the environment variables:
export cmd=openshift-baremetal-install export pullsecret_file=~/pull-secret.txt export extract_dir=$(pwd)
$ export cmd=openshift-baremetal-install $ export pullsecret_file=~/pull-secret.txt $ export extract_dir=$(pwd)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the
ocbinary:curl -s https://mirror.openshift.com/pub/openshift-v4/clients/ocp/$VERSION/openshift-client-linux.tar.gz | tar zxvf - oc
$ curl -s https://mirror.openshift.com/pub/openshift-v4/clients/ocp/$VERSION/openshift-client-linux.tar.gz | tar zxvf - ocCopy to Clipboard Copied! Toggle word wrap Toggle overflow Extract the installer:
sudo cp oc /usr/local/bin oc adm release extract --registry-config "${pullsecret_file}" --command=$cmd --to "${extract_dir}" ${RELEASE_IMAGE} sudo cp openshift-baremetal-install /usr/local/bin$ sudo cp oc /usr/local/bin $ oc adm release extract --registry-config "${pullsecret_file}" --command=$cmd --to "${extract_dir}" ${RELEASE_IMAGE} $ sudo cp openshift-baremetal-install /usr/local/binCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.5. Creating an RHCOS images cache (optional)
To employ image caching, you must download two images: the Red Hat Enterprise Linux CoreOS (RHCOS) image used by the bootstrap VM and the RHCOS image used by the installer to provision the different nodes. Image caching is optional, but especially useful when running the installer on a network with limited bandwidth.
If you are running the installer on a network with limited bandwidth and the RHCOS images download takes more than 15 to 20 minutes, the installer will timeout. Caching images on a web server will help in such scenarios.
Use the following steps to install a container that contains the images.
Install
podman.sudo dnf install -y podman
$ sudo dnf install -y podmanCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open firewall port
8080to be used for RHCOS image caching.sudo firewall-cmd --add-port=8080/tcp --zone=public --permanent
$ sudo firewall-cmd --add-port=8080/tcp --zone=public --permanentCopy to Clipboard Copied! Toggle word wrap Toggle overflow sudo firewall-cmd --reload
$ sudo firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create a directory to store the
bootstraposimageandclusterosimage.mkdir /home/kni/rhcos_image_cache
$ mkdir /home/kni/rhcos_image_cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the appropriate SELinux context for the newly created directory.
sudo semanage fcontext -a -t httpd_sys_content_t "/home/kni/rhcos_image_cache(/.*)?" sudo restorecon -Rv rhcos_image_cache/
$ sudo semanage fcontext -a -t httpd_sys_content_t "/home/kni/rhcos_image_cache(/.*)?" $ sudo restorecon -Rv rhcos_image_cache/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the commit ID from the installer. The ID determines which images the installer needs to download.
export COMMIT_ID=$(/usr/local/bin/openshift-baremetal-install version | grep '^built from commit' | awk '{print $4}')$ export COMMIT_ID=$(/usr/local/bin/openshift-baremetal-install version | grep '^built from commit' | awk '{print $4}')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the URI for the RHCOS image that the installer will deploy on the nodes.
export RHCOS_OPENSTACK_URI=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq .images.openstack.path | sed 's/"//g')
$ export RHCOS_OPENSTACK_URI=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq .images.openstack.path | sed 's/"//g')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the URI for the RHCOS image that the installer will deploy on the bootstrap VM.
export RHCOS_QEMU_URI=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq .images.qemu.path | sed 's/"//g')
$ export RHCOS_QEMU_URI=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq .images.qemu.path | sed 's/"//g')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the path where the images are published.
export RHCOS_PATH=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq .baseURI | sed 's/"//g')
$ export RHCOS_PATH=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq .baseURI | sed 's/"//g')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the SHA hash for the RHCOS image that will be deployed on the bootstrap VM.
export RHCOS_QEMU_SHA_UNCOMPRESSED=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq -r '.images.qemu["uncompressed-sha256"]')
$ export RHCOS_QEMU_SHA_UNCOMPRESSED=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq -r '.images.qemu["uncompressed-sha256"]')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the SHA hash for the RHCOS image that will be deployed on the nodes.
export RHCOS_OPENSTACK_SHA_COMPRESSED=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq -r '.images.openstack.sha256')
$ export RHCOS_OPENSTACK_SHA_COMPRESSED=$(curl -s -S https://raw.githubusercontent.com/openshift/installer/$COMMIT_ID/data/data/rhcos.json | jq -r '.images.openstack.sha256')Copy to Clipboard Copied! Toggle word wrap Toggle overflow Download the images and place them in the
/home/kni/rhcos_image_cachedirectory.curl -L ${RHCOS_PATH}${RHCOS_QEMU_URI} -o /home/kni/rhcos_image_cache/${RHCOS_QEMU_URI} curl -L ${RHCOS_PATH}${RHCOS_OPENSTACK_URI} -o /home/kni/rhcos_image_cache/${RHCOS_OPENSTACK_URI}$ curl -L ${RHCOS_PATH}${RHCOS_QEMU_URI} -o /home/kni/rhcos_image_cache/${RHCOS_QEMU_URI} $ curl -L ${RHCOS_PATH}${RHCOS_OPENSTACK_URI} -o /home/kni/rhcos_image_cache/${RHCOS_OPENSTACK_URI}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm SELinux type is of
httpd_sys_content_tfor the newly created files.ls -Z /home/kni/rhcos_image_cache
$ ls -Z /home/kni/rhcos_image_cacheCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the pod.
podman run -d --name rhcos_image_cache \ -v /home/kni/rhcos_image_cache:/var/www/html \ -p 8080:8080/tcp \ quay.io/centos7/httpd-24-centos7:latest
$ podman run -d --name rhcos_image_cache \ -v /home/kni/rhcos_image_cache:/var/www/html \ -p 8080:8080/tcp \ quay.io/centos7/httpd-24-centos7:latestCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.6. Configuration files
6.3.6.1. Configuring the install-config.yaml file
The install-config.yaml file requires some additional details. Most of the information is teaching the installer and the resulting cluster enough about the available hardware so that it is able to fully manage it.
Configure
install-config.yaml. Change the appropriate variables to match the environment, includingpullSecretandsshKey.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a directory to store cluster configs.
mkdir ~/clusterconfigs cp install-config.yaml ~/clusterconfigs
$ mkdir ~/clusterconfigs $ cp install-config.yaml ~/clusterconfigsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure all bare metal nodes are powered off prior to installing the OpenShift Container Platform cluster.
ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power off
$ ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power offCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove old bootstrap resources if any are left over from a previous deployment attempt.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.6.2. Setting proxy settings within the install-config.yaml file (optional)
To deploy an OpenShift Container Platform cluster using a proxy, make the following changes to the install-config.yaml file.
The following is an example of noProxy with values.
noProxy: .example.com,172.22.0.0/24,10.10.0.0/24
noProxy: .example.com,172.22.0.0/24,10.10.0.0/24With a proxy enabled, set the appropriate values of the proxy in the corresponding key/value pair.
Key considerations:
-
If the proxy does not have an HTTPS proxy, change the value of
httpsProxyfromhttps://tohttp://. -
If using a provisioning network, include it in the
noProxysetting, otherwise the installer will fail. -
Set all of the proxy settings as environment variables within the provisioner node. For example,
HTTP_PROXY,HTTPS_PROXY, andNO_PROXY.
When provisioning with IPv6, you cannot define a CIDR address block in the noProxy settings. You must define each address separately.
6.3.6.3. Modifying the install-config.yaml file for no provisioning network (optional)
To deploy an OpenShift Container Platform cluster without a provisioning network, make the following changes to the install-config.yaml file.
Requires providing two IP addresses from the baremetal network for the provisioningHostIP and bootstrapProvisioningIP configuration settings, and removing the provisioningBridge and provisioningNetworkCIDR configuration settings.
6.3.6.4. Additional install-config parameters
See the following tables for the required parameters, the hosts parameter, and the bmc parameter for the install-config.yaml file.
| Parameters | Default | Description |
|---|---|---|
|
|
The domain name for the cluster. For example, | |
|
|
The | |
|
|
The | |
metadata:
name:
|
The name to be given to the OpenShift Container Platform cluster. For example, | |
networking:
machineCIDR:
|
The public CIDR (Classless Inter-Domain Routing) of the external network. For example, | |
compute: - name: worker | The OpenShift Container Platform cluster requires a name be provided for worker (or compute) nodes even if there are zero nodes. | |
compute:
replicas: 2
| Replicas sets the number of worker (or compute) nodes in the OpenShift Container Platform cluster. | |
controlPlane:
name: master
| The OpenShift Container Platform cluster requires a name for control plane (master) nodes. | |
controlPlane:
replicas: 3
| Replicas sets the number of control plane (master) nodes included as part of the OpenShift Container Platform cluster. | |
|
| The name of the network interface on control plane nodes connected to the provisioning network. | |
|
| The default configuration used for machine pools without a platform configuration. | |
|
|
| The VIP to use for internal API communication. This setting must either be provided or pre-configured in the DNS so that the default name resolves correctly. |
|
|
|
|
|
|
| The VIP to use for ingress traffic. |
| Parameters | Default | Description |
|---|---|---|
|
|
|
Defines the IP range for nodes on the |
|
|
|
The CIDR for the network to use for provisioning. This option is required when not using the default address range on the |
|
|
The third IP address of the |
The IP address within the cluster where the provisioning services run. Defaults to the third IP address of the |
|
|
The second IP address of the |
The IP on the bootstrap VM where the provisioning services run while the installer is deploying the control plane (master) nodes. Defaults to the second IP of the
When using no |
|
|
|
The name of the |
|
|
|
The name of the |
|
| The default configuration used for machine pools without a platform configuration. | |
|
|
A URL to override the default operating system image for the bootstrap node. The URL must contain a SHA-256 hash of the image. For example: | |
|
|
A URL to override the default operating system for cluster nodes. The URL must include a SHA-256 hash of the image. For example, | |
|
|
Set this parameter to
Set this parameter to | |
|
|
Set this parameter to an available IP address on the | |
|
| Set this parameter to the appropriate HTTP proxy used within your environment. | |
|
| Set this parameter to the appropriate HTTPS proxy used within your environment. | |
|
| Set this parameter to the appropriate list of exclusions for proxy usage within your environment. |
Hosts
The hosts parameter is a list of separate bare metal assets used to build the cluster.
| Name | Default | Description |
|
|
The name of the | |
|
|
The role of the bare metal node. Either | |
|
| Connection details for the baseboard management controller. See the BMC addressing section for additional details. | |
|
|
The MAC address of the NIC the host will use to boot on the |
6.3.6.5. BMC addressing
The address field for each bmc entry is a URL for connecting to the OpenShift Container Platform cluster nodes, including the type of controller in the URL scheme and its location on the network.
IPMI
IPMI hosts use ipmi://<out-of-band-ip>:<port> and defaults to port 623 if not specified. The following example demonstrates an IPMI configuration within the install-config.yaml file.
RedFish for HPE
To enable RedFish, use redfish:// or redfish+http:// to disable TLS. The installer requires both the hostname or the IP address and the path to the system ID. The following example demonstrates a RedFish configuration within the install-config.yaml file.
While it is recommended to have a certificate of authority for the out-of-band management addresses, you must include disableCertificateVerification: True in the bmc configuration if using self-signed certificates. The following example demonstrates a RedFish configuration using the disableCertificateVerification: True configuration parameter within the install-config.yaml file.
RedFish for Dell
To enable RedFish, use redfish:// or redfish+http:// to disable TLS. The installer requires both the hostname or the IP address and the path to the system ID. The following example demonstrates a RedFish configuration within the install-config.yaml file.
While it is recommended to have a certificate of authority for the out-of-band management addresses, you must include disableCertificateVerification: True in the bmc configuration if using self-signed certificates. The following example demonstrates a RedFish configuration using the disableCertificateVerification: True configuration parameter within the install-config.yaml file.
Currently RedFish is only supported on Dell with iDRAC firmware version 4.20.20.20 or higher for installer-provisioned installations of OpenShift Container Platform on bare metal deployments.
RedFish Virtual Media for HPE
To enable RedFish Virtual Media for HPE servers, use redfish-virtualmedia:// in the address setting. The following example demonstrates using RedFish Virtual Media within the install-config.yaml file.
RedFish Virtual Media for Dell
For RedFish Virtual Media on Dell servers, use idrac-virtualmedia:// in the address setting.
RedFish Virtual Media on Dell servers has a known issue in OpenShift Container Platform 4.6. The 4.6.1 point release will resolve the issue.
The following example demonstrates using iDRAC Virtual Media within the install-config.yaml file.
idrac-virtualmedia requires iDRAC firmware version 4.20.20.20 or higher.
Ensure the OpenShift Container Platform cluster nodes have AutoAttach Enabled through the iDRAC console. The menu path is: Configuration→Virtual Media→Attach Mode→AutoAttach.
6.3.6.6. Root device hints
The rootDeviceHints parameter enables the installer to provision the Red Hat Enterprise Linux CoreOS (RHCOS) image to a particular device. The installer examines the devices in the order it discovers them, and compares the discovered values with the hint values. The installer uses the first discovered device that matches the hint value. The configuration can combine multiple hints, but a device must match all hints for the installer to select it.
| Subfield | Description |
|---|---|
|
|
A string containing a Linux device name like |
|
|
A string containing a SCSI bus address like |
|
| A string containing a vendor-specific device identifier. The hint can be a substring of the actual value. |
|
| A string containing the name of the vendor or manufacturer of the device. The hint can be a sub-string of the actual value. |
|
| A string containing the device serial number. The hint must match the actual value exactly. |
|
| An integer representing the minimum size of the device in gigabytes. |
|
| A string containing the unique storage identifier. The hint must match the actual value exactly. |
|
| A string containing the unique storage identifier with the vendor extension appended. The hint must match the actual value exactly. |
|
| A string containing the unique vendor storage identifier. The hint must match the actual value exactly. |
|
| A boolean indicating whether the device should be a rotating disk (true) or not (false). |
Example usage
6.3.6.7. Creating the OpenShift Container Platform manifests
Create the OpenShift Container Platform manifests.
./openshift-baremetal-install --dir ~/clusterconfigs create manifests
$ ./openshift-baremetal-install --dir ~/clusterconfigs create manifestsCopy to Clipboard Copied! Toggle word wrap Toggle overflow INFO Consuming Install Config from target directory WARNING Making control-plane schedulable by setting MastersSchedulable to true for Scheduler cluster settings WARNING Discarding the OpenShift Manifest that was provided in the target directory because its dependencies are dirty and it needs to be regenerated
INFO Consuming Install Config from target directory WARNING Making control-plane schedulable by setting MastersSchedulable to true for Scheduler cluster settings WARNING Discarding the OpenShift Manifest that was provided in the target directory because its dependencies are dirty and it needs to be regeneratedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.7. Creating a disconnected registry (optional)
In some cases, you might want to install an OpenShift KNI cluster using a local copy of the installation registry. This could be for enhancing network efficiency because the cluster nodes are on a network that does not have access to the internet.
A local, or mirrored, copy of the registry requires the following:
- A certificate for the registry node. This can be a self-signed certificate.
- A webserver - this will be served by a container on a system.
- An updated pull secret that contains the certificate and local repository information.
Creating a disconnected registry on a registry node is optional. The subsequent sections indicate that they are optional since they are steps you need to execute only when creating a disconnected registry on a registry node. You should execute all of the subsequent sub-sections labeled "(optional)" when creating a disconnected registry on a registry node.
6.3.7.1. Preparing the registry node to host the mirrored registry (optional)
Make the following changes to the registry node.
Procedure
Open the firewall port on the registry node.
sudo firewall-cmd --add-port=5000/tcp --zone=libvirt --permanent sudo firewall-cmd --add-port=5000/tcp --zone=public --permanent sudo firewall-cmd --reload
$ sudo firewall-cmd --add-port=5000/tcp --zone=libvirt --permanent $ sudo firewall-cmd --add-port=5000/tcp --zone=public --permanent $ sudo firewall-cmd --reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the required packages for the registry node.
sudo yum -y install python3 podman httpd httpd-tools jq
$ sudo yum -y install python3 podman httpd httpd-tools jqCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the directory structure where the repository information will be held.
sudo mkdir -p /opt/registry/{auth,certs,data}$ sudo mkdir -p /opt/registry/{auth,certs,data}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.7.2. Generating the self-signed certificate (optional)
Generate a self-signed certificate for the registry node and put it in the /opt/registry/certs directory.
Procedure
Adjust the certificate information as appropriate.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteWhen replacing
<Country Name>, ensure that it only contains two letters. For example,US.Update the registry node’s
ca-trustwith the new certificate.sudo cp /opt/registry/certs/domain.crt /etc/pki/ca-trust/source/anchors/ sudo update-ca-trust extract
$ sudo cp /opt/registry/certs/domain.crt /etc/pki/ca-trust/source/anchors/ $ sudo update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.7.3. Creating the registry podman container (optional)
The registry container uses the /opt/registry directory for certificates, authentication files, and to store its data files.
The registry container uses httpd and needs an htpasswd file for authentication.
Procedure
Create an
htpasswdfile in/opt/registry/authfor the container to use.htpasswd -bBc /opt/registry/auth/htpasswd <user> <passwd>
$ htpasswd -bBc /opt/registry/auth/htpasswd <user> <passwd>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<user>with the user name and<passwd>with the password.Create and start the registry container.
Copy to Clipboard Copied! Toggle word wrap Toggle overflow podman start ocpdiscon-registry
$ podman start ocpdiscon-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.7.4. Copy and update the pull-secret (optional)
Copy the pull secret file from the provisioner node to the registry node and modify it to include the authentication information for the new registry node.
Procedure
Copy the
pull-secret.txtfile.scp kni@provisioner:/home/kni/pull-secret.txt pull-secret.txt
$ scp kni@provisioner:/home/kni/pull-secret.txt pull-secret.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update the
host_fqdnenvironment variable with the fully qualified domain name of the registry node.host_fqdn=$( hostname --long )
$ host_fqdn=$( hostname --long )Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the
b64authenvironment variable with the base64 encoding of thehttpcredentials used to create thehtpasswdfile.b64auth=$( echo -n '<username>:<passwd>' | openssl base64 )
$ b64auth=$( echo -n '<username>:<passwd>' | openssl base64 )Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<username>with the user name and<passwd>with the password.Set the
AUTHSTRINGenvironment variable to use thebase64authorization string. The$USERvariable is an environment variable containing the name of the current user.AUTHSTRING="{\"$host_fqdn:5000\": {\"auth\": \"$b64auth\",\"email\": \"$USER@redhat.com\"}}"$ AUTHSTRING="{\"$host_fqdn:5000\": {\"auth\": \"$b64auth\",\"email\": \"$USER@redhat.com\"}}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the
pull-secret.txtfile.jq ".auths += $AUTHSTRING" < pull-secret.txt > pull-secret-update.txt
$ jq ".auths += $AUTHSTRING" < pull-secret.txt > pull-secret-update.txtCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.7.5. Mirroring the repository (optional)
Procedure
Copy the
ocbinary from the provisioner node to the registry node.sudo scp kni@provisioner:/usr/local/bin/oc /usr/local/bin
$ sudo scp kni@provisioner:/usr/local/bin/oc /usr/local/binCopy to Clipboard Copied! Toggle word wrap Toggle overflow Set the required environment variables.
Set the release version:
VERSION=<release_version>
$ VERSION=<release_version>Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<release_version>, specify the tag that corresponds to the version of OpenShift Container Platform to install, such as4.6.Set the local registry name and host port:
LOCAL_REG='<local_registry_host_name>:<local_registry_host_port>'
$ LOCAL_REG='<local_registry_host_name>:<local_registry_host_port>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<local_registry_host_name>, specify the registry domain name for your mirror repository, and for<local_registry_host_port>, specify the port that it serves content on.Set the local repository name:
LOCAL_REPO='<local_repository_name>'
$ LOCAL_REPO='<local_repository_name>'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<local_repository_name>, specify the name of the repository to create in your registry, such asocp4/openshift4.
Mirror the remote install images to the local repository.
/usr/local/bin/oc adm release mirror \ -a pull-secret-update.txt \ --from=$UPSTREAM_REPO \ --to-release-image=$LOCAL_REG/$LOCAL_REPO:${VERSION} \ --to=$LOCAL_REG/$LOCAL_REPO$ /usr/local/bin/oc adm release mirror \ -a pull-secret-update.txt \ --from=$UPSTREAM_REPO \ --to-release-image=$LOCAL_REG/$LOCAL_REPO:${VERSION} \ --to=$LOCAL_REG/$LOCAL_REPOCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.7.6. Modify the install-config.yaml file to use the disconnected registry (optional)
On the provisioner node, the install-config.yaml file should use the newly created pull-secret from the pull-secret-update.txt file. The install-config.yaml file must also contain the disconnected registry node’s certificate and registry information.
Procedure
Add the disconnected registry node’s certificate to the
install-config.yamlfile. The certificate should follow the"additionalTrustBundle: |"line and be properly indented, usually by two spaces.echo "additionalTrustBundle: |" >> install-config.yaml sed -e 's/^/ /' /opt/registry/certs/domain.crt >> install-config.yaml
$ echo "additionalTrustBundle: |" >> install-config.yaml $ sed -e 's/^/ /' /opt/registry/certs/domain.crt >> install-config.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the mirror information for the registry to the
install-config.yamlfile.Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteReplace
registry.example.comwith the registry’s fully qualified domain name.
6.3.8. Deploying routers on worker nodes
During installation, the installer deploys router pods on worker nodes. By default, the installer installs two router pods. If the initial cluster has only one worker node, or if a deployed cluster requires additional routers to handle external traffic loads destined for services within the OpenShift Container Platform cluster, you can create a yaml file to set an appropriate number of router replicas.
By default, the installer deploys two routers. If the cluster has at least two worker nodes, you can skip this section. For more information on the Ingress Operator see: Ingress Operator in OpenShift Container Platform.
If the cluster has no worker nodes, the installer deploys the two routers on the control plane nodes by default. If the cluster has no worker nodes, you can skip this section.
Procedure
Create a
router-replicas.yamlfile.Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteReplace
<num-of-router-pods>with an appropriate value. If working with just one worker node, setreplicas:to1. If working with more than 3 worker nodes, you can increasereplicas:from the default value2as appropriate.Save and copy the
router-replicas.yamlfile to theclusterconfigs/openshiftdirectory.cp ~/router-replicas.yaml clusterconfigs/openshift/99_router-replicas.yaml
cp ~/router-replicas.yaml clusterconfigs/openshift/99_router-replicas.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.3.9. Validation checklist for installation
- ❏ OpenShift Container Platform installer has been retrieved.
- ❏ OpenShift Container Platform installer has been extracted.
-
❏ Required parameters for the
install-config.yamlhave been configured. -
❏ The
hostsparameter for theinstall-config.yamlhas been configured. -
❏ The
bmcparameter for theinstall-config.yamlhas been configured. -
❏ Conventions for the values configured in the
bmcaddressfield have been applied. - ❏ Created a disconnected registry (optional).
- ❏ (optional) Validate disconnected registry settings if in use.
- ❏ (optional) Deployed routers on worker nodes.
6.3.10. Deploying the cluster via the OpenShift Container Platform installer
Run the OpenShift Container Platform installer:
./openshift-baremetal-install --dir ~/clusterconfigs --log-level debug create cluster
$ ./openshift-baremetal-install --dir ~/clusterconfigs --log-level debug create cluster6.3.11. Following the installation
During the deployment process, you can check the installation’s overall status by issuing the tail command to the .openshift_install.log log file in the install directory folder.
tail -f /path/to/install-dir/.openshift_install.log
$ tail -f /path/to/install-dir/.openshift_install.log6.3.12. Preparing to reinstall a cluster on bare metal
Before you reinstall a cluster on bare metal, you must perform cleanup operations.
Procedure
- Remove or reformat the disks for the bootstrap, control plane (also known as master) node, and worker nodes. If you are working in a hypervisor environment, you must add any disks you removed.
Delete the artifacts that the previous installation generated:
cd ; /bin/rm -rf auth/ bootstrap.ign master.ign worker.ign metadata.json \ .openshift_install.log .openshift_install_state.json
$ cd ; /bin/rm -rf auth/ bootstrap.ign master.ign worker.ign metadata.json \ .openshift_install.log .openshift_install_state.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Generate new manifests and Ignition config files. See “Creating the Kubernetes manifest and Ignition config files" for more information.
- Upload the new bootstrap, control plane, and compute node Ignition config files that the installation program created to your HTTP server. This will overwrite the previous Ignition files.
6.4. Expanding the cluster
After deploying an installer-provisioned OpenShift Container Platform cluster, you can use the following procedures to expand the number of worker nodes. Ensure that each prospective worker node meets the prerequisites.
6.4.1. Preparing the bare metal node
Preparing the bare metal node requires executing the following procedure from the provisioner node.
Procedure
Get the
ocbinary, if needed. It should already exist on the provisioner node.curl -s https://mirror.openshift.com/pub/openshift-v4/clients/ocp-dev-preview/$VERSION/openshift-client-linux.tar.gz | tar zxvf - oc
$ curl -s https://mirror.openshift.com/pub/openshift-v4/clients/ocp-dev-preview/$VERSION/openshift-client-linux.tar.gz | tar zxvf - ocCopy to Clipboard Copied! Toggle word wrap Toggle overflow sudo cp oc /usr/local/bin
$ sudo cp oc /usr/local/binCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the
ipmitool.sudo dnf install -y OpenIPMI ipmitool
$ sudo dnf install -y OpenIPMI ipmitoolCopy to Clipboard Copied! Toggle word wrap Toggle overflow Power off the bare metal node and ensure it is off.
ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power off
$ ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power offCopy to Clipboard Copied! Toggle word wrap Toggle overflow Where
<management-server-ip>is the IP address of the bare metal node’s base board management controller.ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power status
$ ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power statusCopy to Clipboard Copied! Toggle word wrap Toggle overflow Chassis Power is off
Chassis Power is offCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retrieve the username and password of the bare metal node’s baseboard management controller. Then, create
base64strings from the username and password. In the following example, the username isrootand the password iscalvin.echo -ne "root" | base64
$ echo -ne "root" | base64Copy to Clipboard Copied! Toggle word wrap Toggle overflow echo -ne "calvin" | base64
$ echo -ne "calvin" | base64Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a configuration file for the bare metal node.
vim bmh.yaml
$ vim bmh.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<num>for the worker number of bare metal node in twonamefields andcredentialsNamefield. Replace<base64-of-uid>with thebase64string of the username. Replace<base64-of-pwd>with thebase64string of the password. Replace<NIC1-mac-address>with the MAC address of the bare metal node’s first NIC. Replace<bmc-ip>with the IP address of the bare metal node’s baseboard management controller.Create the bare metal node.
oc -n openshift-machine-api create -f bmh.yaml
$ oc -n openshift-machine-api create -f bmh.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow secret/openshift-worker-<num>-bmc-secret created baremetalhost.metal3.io/openshift-worker-<num> created
secret/openshift-worker-<num>-bmc-secret created baremetalhost.metal3.io/openshift-worker-<num> createdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Where
<num>will be the worker number.Power up and inspect the bare metal node.
oc -n openshift-machine-api get bmh openshift-worker-<num>
$ oc -n openshift-machine-api get bmh openshift-worker-<num>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Where
<num>is the worker node number.NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK ready ipmi://<out-of-band-ip> unknown true
NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK ready ipmi://<out-of-band-ip> unknown trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.4.2. Provisioning the bare metal node
Provisioning the bare metal node requires executing the following procedure from the provisioner node.
Procedure
Ensure the
PROVISIONING STATUSisreadybefore provisioning the bare metal node.oc -n openshift-machine-api get bmh openshift-worker-<num>
$ oc -n openshift-machine-api get bmh openshift-worker-<num>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Where
<num>is the worker node number.NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK ready ipmi://<out-of-band-ip> unknown true
NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK ready ipmi://<out-of-band-ip> unknown trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Get a count of the number of worker nodes.
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the machine set.
oc get machinesets -n openshift-machine-api
$ oc get machinesets -n openshift-machine-apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow NAME DESIRED CURRENT READY AVAILABLE AGE ... openshift-worker-0.example.com 1 1 1 1 55m openshift-worker-1.example.com 1 1 1 1 55m
NAME DESIRED CURRENT READY AVAILABLE AGE ... openshift-worker-0.example.com 1 1 1 1 55m openshift-worker-1.example.com 1 1 1 1 55mCopy to Clipboard Copied! Toggle word wrap Toggle overflow Increase the number of worker nodes by one.
oc scale --replicas=<num> machineset <machineset> -n openshift-machine-api
$ oc scale --replicas=<num> machineset <machineset> -n openshift-machine-apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<num>with the new number of worker nodes. Replace<machineset>with the name of the machine set from the previous step.Check the status of the bare metal node.
oc -n openshift-machine-api get bmh openshift-worker-<num>
$ oc -n openshift-machine-api get bmh openshift-worker-<num>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Where
<num>is the worker node number. The status changes fromreadytoprovisioning.NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK provisioning openshift-worker-<num>-65tjz ipmi://<out-of-band-ip> unknown true
NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK provisioning openshift-worker-<num>-65tjz ipmi://<out-of-band-ip> unknown trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
provisioningstatus remains until the OpenShift Container Platform cluster provisions the node. This can take 30 minutes or more. Once complete, the status will change toprovisioned.NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK provisioned openshift-worker-<num>-65tjz ipmi://<out-of-band-ip> unknown true
NAME STATUS PROVISIONING STATUS CONSUMER BMC HARDWARE PROFILE ONLINE ERROR openshift-worker-<num> OK provisioned openshift-worker-<num>-65tjz ipmi://<out-of-band-ip> unknown trueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Once provisioned, ensure the bare metal node is ready.
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can also check the kubelet.
ssh openshift-worker-<num>
$ ssh openshift-worker-<num>Copy to Clipboard Copied! Toggle word wrap Toggle overflow [kni@openshift-worker-<num>]$ journalctl -fu kubelet
[kni@openshift-worker-<num>]$ journalctl -fu kubeletCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5. Troubleshooting
6.5.1. Troubleshooting the installer workflow
Prior to troubleshooting the installation environment, it is critical to understand the overall flow of the installer-provisioned installation on bare metal. The diagrams below provide a troubleshooting flow with a step-by-step breakdown for the environment.
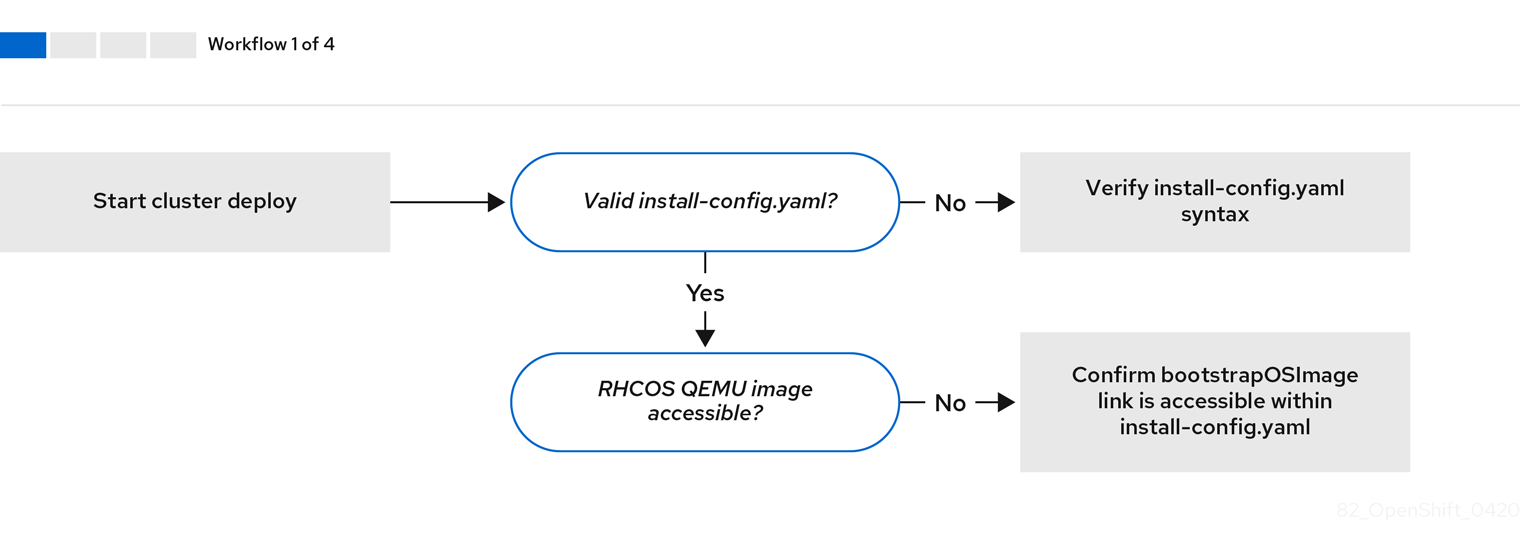
Workflow 1 of 4 illustrates a troubleshooting workflow when the install-config.yaml file has errors or the Red Hat Enterprise Linux CoreOS (RHCOS) images are inaccessible. Troubleshooting suggestions can be found at Troubleshooting install-config.yaml.
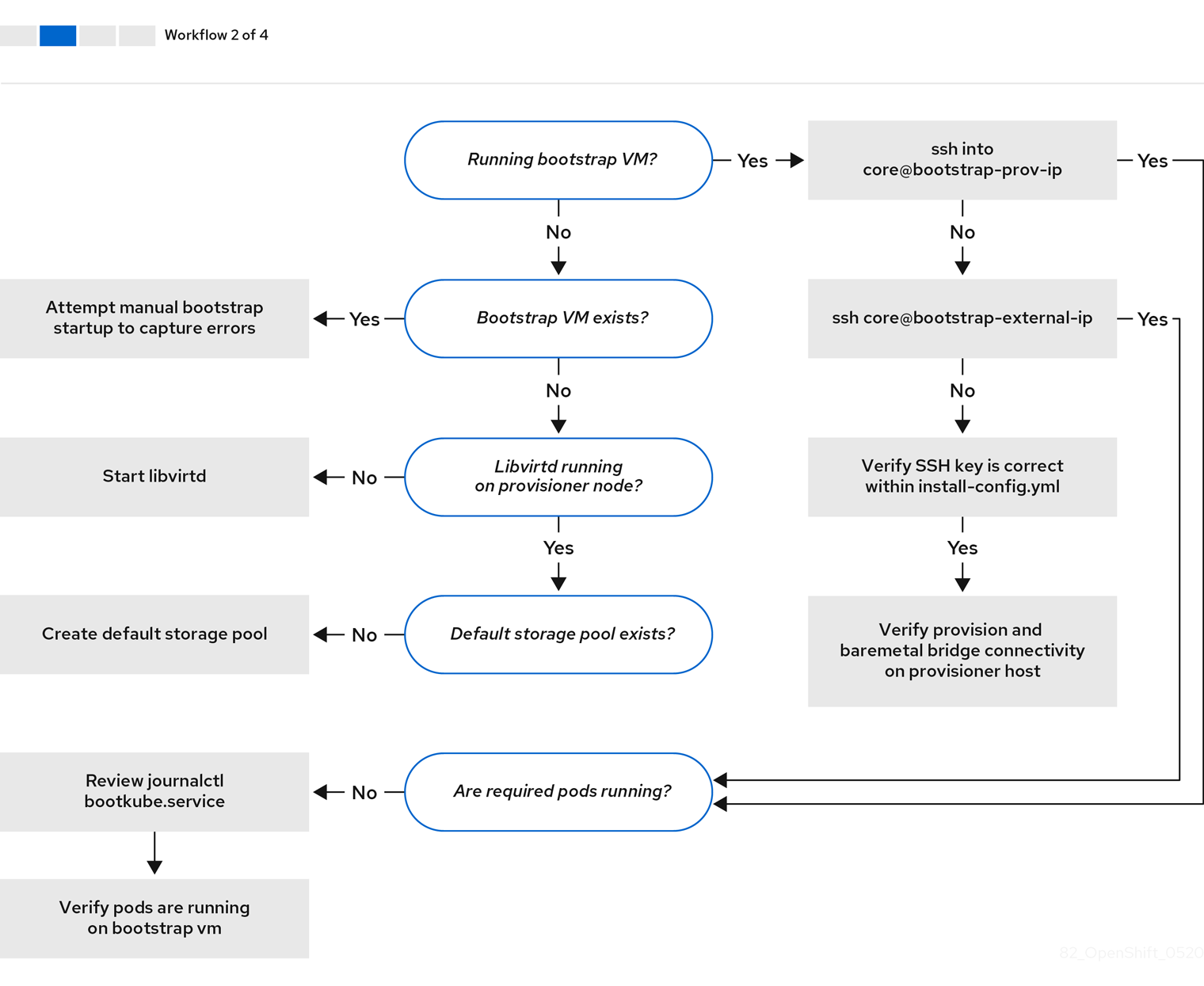
Workflow 2 of 4 illustrates a troubleshooting workflow for bootstrap VM issues, bootstrap VMs that cannot boot up the cluster nodes, and inspecting logs. When installing a OpenShift Container Platform cluster without the provisioning network, this workflow does not apply.
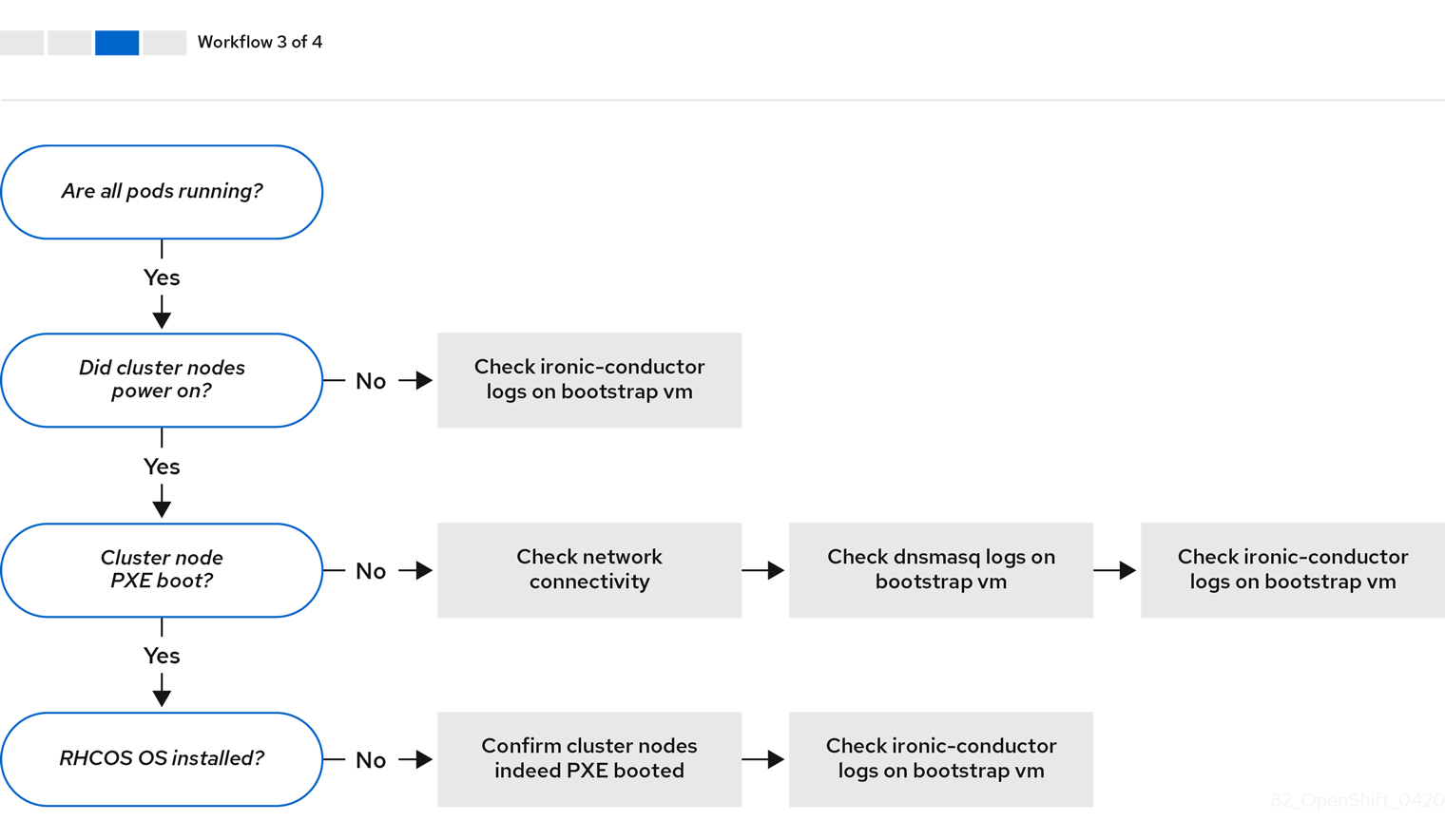
Workflow 3 of 4 illustrates a troubleshooting workflow for cluster nodes that will not PXE boot.

Workflow 4 of 4 illustrates a troubleshooting workflow from a non-accessible API to a validated installation.
6.5.2. Troubleshooting install-config.yaml
The install-config.yaml configuration file represents all of the nodes that are part of the OpenShift Container Platform cluster. The file contains the necessary options consisting of but not limited to apiVersion, baseDomain, imageContentSources and virtual IP addresses. If errors occur early in the deployment of the OpenShift Container Platform cluster, the errors are likely in the install-config.yaml configuration file.
Procedure
- Use the guidelines in YAML-tips.
- Verify the YAML syntax is correct using syntax-check.
Verify the Red Hat Enterprise Linux CoreOS (RHCOS) QEMU images are properly defined and accessible via the URL provided in the
install-config.yaml. For example:curl -s -o /dev/null -I -w "%{http_code}\n" http://webserver.example.com:8080/rhcos-44.81.202004250133-0-qemu.x86_64.qcow2.gz?sha256=7d884b46ee54fe87bbc3893bf2aa99af3b2d31f2e19ab5529c60636fbd0f1ce7$ curl -s -o /dev/null -I -w "%{http_code}\n" http://webserver.example.com:8080/rhcos-44.81.202004250133-0-qemu.x86_64.qcow2.gz?sha256=7d884b46ee54fe87bbc3893bf2aa99af3b2d31f2e19ab5529c60636fbd0f1ce7Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the output is
200, there is a valid response from the webserver storing the bootstrap VM image.
6.5.3. Bootstrap VM issues
The OpenShift Container Platform installer spawns a bootstrap node virtual machine, which handles provisioning the OpenShift Container Platform cluster nodes.
Procedure
About 10 to 15 minutes after triggering the installer, check to ensure the bootstrap VM is operational using the
virshcommand:sudo virsh list
$ sudo virsh listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Id Name State -------------------------------------------- 12 openshift-xf6fq-bootstrap running
Id Name State -------------------------------------------- 12 openshift-xf6fq-bootstrap runningCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe name of the bootstrap VM is always the cluster name followed by a random set of characters and ending in the word "bootstrap."
If the bootstrap VM is not running after 10-15 minutes, troubleshoot why it is not running. Possible issues include:
Verify
libvirtdis running on the system:systemctl status libvirtd
$ systemctl status libvirtdCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the bootstrap VM is operational, log in to it.
Use the
virsh consolecommand to find the IP address of the bootstrap VM:sudo virsh console example.com
$ sudo virsh console example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantWhen deploying a OpenShift Container Platform cluster without the
provisioningnetwork, you must use a public IP address and not a private IP address like172.22.0.2.Once you obtain the IP address, log in to the bootstrap VM using the
sshcommand:NoteIn the console output of the previous step, you can use the IPv6 IP address provided by
ens3or the IPv4 IP provided byens4.ssh core@172.22.0.2
$ ssh core@172.22.0.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If you are not successful logging in to the bootstrap VM, you have likely encountered one of the following scenarios:
-
You cannot reach the
172.22.0.0/24network. Verify network connectivity on the provisioner host specifically around theprovisioningnetwork bridge. This will not be the issue if you are not using theprovisioningnetwork. -
You cannot reach the bootstrap VM via the public network. When attempting to SSH via
baremetalnetwork, verify connectivity on theprovisionerhost specifically around thebaremetalnetwork bridge. -
You encountered
Permission denied (publickey,password,keyboard-interactive). When attempting to access the bootstrap VM, aPermission deniederror might occur. Verify that the SSH key for the user attempting to log into the VM is set within theinstall-config.yamlfile.
6.5.3.1. Bootstrap VM cannot boot up the cluster nodes
During the deployment, it is possible for the bootstrap VM to fail to boot the cluster nodes, which prevents the VM from provisioning the nodes with the RHCOS image. This scenario can arise due to:
-
A problem with the
install-config.yamlfile. - Issues with out-of-band network access via the baremetal network.
To verify the issue, there are three containers related to ironic:
-
ironic-api -
ironic-conductor -
ironic-inspector
Procedure
Log in to the bootstrap VM:
ssh core@172.22.0.2
$ ssh core@172.22.0.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow To check the container logs, execute the following:
sudo podman logs -f <container-name>
[core@localhost ~]$ sudo podman logs -f <container-name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<container-name>with one ofironic-api,ironic-conductor, orironic-inspector. If you encounter an issue where the control plane nodes are not booting up via PXE, check theironic-conductorpod. Theironic-conductorpod contains the most detail about the attempt to boot the cluster nodes, because it attempts to log in to the node over IPMI.
Potential reason
The cluster nodes might be in the ON state when deployment started.
Solution
Power off the OpenShift Container Platform cluster nodes before you begin the installation over IPMI:
ipmitool -I lanplus -U root -P <password> -H <out-of-band-ip> power off
$ ipmitool -I lanplus -U root -P <password> -H <out-of-band-ip> power off6.5.3.2. Inspecting logs
When experiencing issues downloading or accessing the RHCOS images, first verify that the URL is correct in the install-config.yaml configuration file.
Example of internal webserver hosting RHCOS images
bootstrapOSImage: http://<ip:port>/rhcos-43.81.202001142154.0-qemu.x86_64.qcow2.gz?sha256=9d999f55ff1d44f7ed7c106508e5deecd04dc3c06095d34d36bf1cd127837e0c clusterOSImage: http://<ip:port>/rhcos-43.81.202001142154.0-openstack.x86_64.qcow2.gz?sha256=a1bda656fa0892f7b936fdc6b6a6086bddaed5dafacedcd7a1e811abb78fe3b0
bootstrapOSImage: http://<ip:port>/rhcos-43.81.202001142154.0-qemu.x86_64.qcow2.gz?sha256=9d999f55ff1d44f7ed7c106508e5deecd04dc3c06095d34d36bf1cd127837e0c
clusterOSImage: http://<ip:port>/rhcos-43.81.202001142154.0-openstack.x86_64.qcow2.gz?sha256=a1bda656fa0892f7b936fdc6b6a6086bddaed5dafacedcd7a1e811abb78fe3b0
The ipa-downloader and coreos-downloader containers download resources from a webserver or the external quay.io registry, whichever the install-config.yaml configuration file specifies. Verify the following two containers are up and running and inspect their logs as needed:
-
ipa-downloader -
coreos-downloader
Procedure
Log in to the bootstrap VM:
ssh core@172.22.0.2
$ ssh core@172.22.0.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check the status of the
ipa-downloaderandcoreos-downloadercontainers within the bootstrap VM:sudo podman logs -f ipa-downloader
[core@localhost ~]$ sudo podman logs -f ipa-downloaderCopy to Clipboard Copied! Toggle word wrap Toggle overflow sudo podman logs -f coreos-downloader
[core@localhost ~]$ sudo podman logs -f coreos-downloaderCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the bootstrap VM cannot access the URL to the images, use the
curlcommand to verify that the VM can access the images.To inspect the
bootkubelogs that indicate if all the containers launched during the deployment phase, execute the following:journalctl -xe
[core@localhost ~]$ journalctl -xeCopy to Clipboard Copied! Toggle word wrap Toggle overflow journalctl -b -f -u bootkube.service
[core@localhost ~]$ journalctl -b -f -u bootkube.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify all the pods, including
dnsmasq,mariadb,httpd, andironic, are running:sudo podman ps
[core@localhost ~]$ sudo podman psCopy to Clipboard Copied! Toggle word wrap Toggle overflow If there are issues with the pods, check the logs of the containers with issues. To check the log of the
ironic-api, execute the following:sudo podman logs <ironic-api>
[core@localhost ~]$ sudo podman logs <ironic-api>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.4. Cluster nodes will not PXE boot
When OpenShift Container Platform cluster nodes will not PXE boot, execute the following checks on the cluster nodes that will not PXE boot. This procedure does not apply when installing a OpenShift Container Platform cluster without the provisioning network.
Procedure
-
Check the network connectivity to the
provisioningnetwork. -
Ensure PXE is enabled on the NIC for the
provisioningnetwork and PXE is disabled for all other NICs. Verify that the
install-config.yamlconfiguration file has the proper hardware profile and boot MAC address for the NIC connected to theprovisioningnetwork. For example:control plane node settings
bootMACAddress: 24:6E:96:1B:96:90 # MAC of bootable provisioning NIC hardwareProfile: default #control plane node settings
bootMACAddress: 24:6E:96:1B:96:90 # MAC of bootable provisioning NIC hardwareProfile: default #control plane node settingsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Worker node settings
bootMACAddress: 24:6E:96:1B:96:90 # MAC of bootable provisioning NIC hardwareProfile: unknown #worker node settings
bootMACAddress: 24:6E:96:1B:96:90 # MAC of bootable provisioning NIC hardwareProfile: unknown #worker node settingsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.5. The API is not accessible
When the cluster is running and clients cannot access the API, domain name resolution issues might impede access to the API.
Procedure
Hostname Resolution: Check the cluster nodes to ensure they have a fully qualified domain name, and not just
localhost.localdomain. For example:hostname
$ hostnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow If a hostname is not set, set the correct hostname. For example:
hostnamectl set-hostname <hostname>
$ hostnamectl set-hostname <hostname>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Incorrect Name Resolution: Ensure that each node has the correct name resolution in the DNS server using
digandnslookup. For example:dig api.<cluster-name>.example.com
$ dig api.<cluster-name>.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output in the foregoing example indicates that the appropriate IP address for the
api.<cluster-name>.example.comVIP is10.19.13.86. This IP address should reside on thebaremetalnetwork.
6.5.6. Cleaning up previous installations
In the event of a previous failed deployment, remove the artifacts from the failed attempt before attempting to deploy OpenShift Container Platform again.
Procedure
Power off all bare metal nodes prior to installing the OpenShift Container Platform cluster:
ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power off
$ ipmitool -I lanplus -U <user> -P <password> -H <management-server-ip> power offCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove all old bootstrap resources if any are left over from a previous deployment attempt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the following from the
clusterconfigsdirectory to prevent Terraform from failing:rm -rf ~/clusterconfigs/auth ~/clusterconfigs/terraform* ~/clusterconfigs/tls ~/clusterconfigs/metadata.json
$ rm -rf ~/clusterconfigs/auth ~/clusterconfigs/terraform* ~/clusterconfigs/tls ~/clusterconfigs/metadata.jsonCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.7. Issues with creating the registry
When creating a disconnected registry, you might encounter a "User Not Authorized" error when attempting to mirror the registry. This error might occur if you fail to append the new authentication to the existing pull-secret.txt file.
Procedure
Check to ensure authentication is successful:
/usr/local/bin/oc adm release mirror \ -a pull-secret-update.json
$ /usr/local/bin/oc adm release mirror \ -a pull-secret-update.json --from=$UPSTREAM_REPO \ --to-release-image=$LOCAL_REG/$LOCAL_REPO:${VERSION} \ --to=$LOCAL_REG/$LOCAL_REPOCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteExample output of the variables used to mirror the install images:
UPSTREAM_REPO=${RELEASE_IMAGE} LOCAL_REG=<registry_FQDN>:<registry_port> LOCAL_REPO='ocp4/openshift4'UPSTREAM_REPO=${RELEASE_IMAGE} LOCAL_REG=<registry_FQDN>:<registry_port> LOCAL_REPO='ocp4/openshift4'Copy to Clipboard Copied! Toggle word wrap Toggle overflow The values of
RELEASE_IMAGEandVERSIONwere set during the Retrieving OpenShift Installer step of the Setting up the environment for an OpenShift installation section.After mirroring the registry, confirm that you can access it in your disconnected environment:
curl -k -u <user>:<password> https://registry.example.com:<registry-port>/v2/_catalog
$ curl -k -u <user>:<password> https://registry.example.com:<registry-port>/v2/_catalog {"repositories":["<Repo-Name>"]}Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.8. Miscellaneous issues
6.5.8.1. Addressing the runtime network not ready error
After the deployment of a cluster you might receive the following error:
`runtime network not ready: NetworkReady=false reason:NetworkPluginNotReady message:Network plugin returns error: Missing CNI default network`
`runtime network not ready: NetworkReady=false reason:NetworkPluginNotReady message:Network plugin returns error: Missing CNI default network`
The Cluster Network Operator is responsible for deploying the networking components in response to a special object created by the installer. It runs very early in the installation process, after the control plane (master) nodes have come up, but before the bootstrap control plane has been torn down. It can be indicative of more subtle installer issues, such as long delays in bringing up control plane (master) nodes or issues with apiserver communication.
Procedure
Inspect the pods in the
openshift-network-operatornamespace:oc get all -n openshift-network-operator
$ oc get all -n openshift-network-operatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow NAME READY STATUS RESTARTS AGE pod/network-operator-69dfd7b577-bg89v 0/1 ContainerCreating 0 149m
NAME READY STATUS RESTARTS AGE pod/network-operator-69dfd7b577-bg89v 0/1 ContainerCreating 0 149mCopy to Clipboard Copied! Toggle word wrap Toggle overflow On the
provisionernode, determine that the network configuration exists:kubectl get network.config.openshift.io cluster -oyaml
$ kubectl get network.config.openshift.io cluster -oyamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow If it does not exist, the installer did not create it. To determine why the installer did not create it, execute the following:
openshift-install create manifests
$ openshift-install create manifestsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Check that the
network-operatoris running:kubectl -n openshift-network-operator get pods
$ kubectl -n openshift-network-operator get podsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Retrieve the logs:
kubectl -n openshift-network-operator logs -l "name=network-operator"
$ kubectl -n openshift-network-operator logs -l "name=network-operator"Copy to Clipboard Copied! Toggle word wrap Toggle overflow On high availability clusters with three or more control plane (master) nodes, the Operator will perform leader election and all other Operators will sleep. For additional details, see Troubleshooting.
6.5.8.2. Cluster nodes not getting the correct IPv6 address over DHCP
If the cluster nodes are not getting the correct IPv6 address over DHCP, check the following:
- Ensure the reserved IPv6 addresses reside outside the DHCP range.
In the IP address reservation on the DHCP server, ensure the reservation specifies the correct DHCP Unique Identifier (DUID). For example:
This is a dnsmasq dhcp reservation, 'id:00:03:00:01' is the client id and '18:db:f2:8c:d5:9f' is the MAC Address for the NIC
# This is a dnsmasq dhcp reservation, 'id:00:03:00:01' is the client id and '18:db:f2:8c:d5:9f' is the MAC Address for the NIC id:00:03:00:01:18:db:f2:8c:d5:9f,openshift-master-1,[2620:52:0:1302::6]Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Ensure that route announcements are working.
- Ensure that the DHCP server is listening on the required interfaces serving the IP address ranges.
6.5.8.3. Cluster nodes not getting the correct hostname over DHCP
During IPv6 deployment, cluster nodes must get their hostname over DHCP. Sometimes the NetworkManager does not assign the hostname immediately. A control plane (master) node might report an error such as:
Failed Units: 2 NetworkManager-wait-online.service nodeip-configuration.service
Failed Units: 2
NetworkManager-wait-online.service
nodeip-configuration.service
This error indicates that the cluster node likely booted without first receiving a hostname from the DHCP server, which causes kubelet to boot with a localhost.localdomain hostname. To address the error, force the node to renew the hostname.
Procedure
Retrieve the
hostname:hostname
[core@master-X ~]$ hostnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the hostname is
localhost, proceed with the following steps.NoteWhere
Xis the control plane node (also known as the master node) number.Force the cluster node to renew the DHCP lease:
sudo nmcli con up "<bare-metal-nic>"
[core@master-X ~]$ sudo nmcli con up "<bare-metal-nic>"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Replace
<bare-metal-nic>with the wired connection corresponding to thebaremetalnetwork.Check
hostnameagain:hostname
[core@master-X ~]$ hostnameCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the hostname is still
localhost.localdomain, restartNetworkManager:sudo systemctl restart NetworkManager
[core@master-X ~]$ sudo systemctl restart NetworkManagerCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
If the hostname is still
localhost.localdomain, wait a few minutes and check again. If the hostname remainslocalhost.localdomain, repeat the previous steps. Restart the
nodeip-configurationservice:sudo systemctl restart nodeip-configuration.service
[core@master-X ~]$ sudo systemctl restart nodeip-configuration.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow This service will reconfigure the
kubeletservice with the correct hostname references.Reload the unit files definition since the kubelet changed in the previous step:
sudo systemctl daemon-reload
[core@master-X ~]$ sudo systemctl daemon-reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
kubeletservice:sudo systemctl restart kubelet.service
[core@master-X ~]$ sudo systemctl restart kubelet.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure
kubeletbooted with the correct hostname:sudo journalctl -fu kubelet.service
[core@master-X ~]$ sudo journalctl -fu kubelet.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
If the cluster node is not getting the correct hostname over DHCP after the cluster is up and running, such as during a reboot, the cluster will have a pending csr. Do not approve a csr, or other issues might arise.
Addressing a csr
Get CSRs on the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Verify if a pending
csrcontainsSubject Name: localhost.localdomain:oc get csr <pending_csr> -o jsonpath='{.spec.request}' | base64 --decode | openssl req -noout -text$ oc get csr <pending_csr> -o jsonpath='{.spec.request}' | base64 --decode | openssl req -noout -textCopy to Clipboard Copied! Toggle word wrap Toggle overflow Remove any
csrthat containsSubject Name: localhost.localdomain:oc delete csr <wrong_csr>
$ oc delete csr <wrong_csr>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.8.4. Routes do not reach endpoints
During the installation process, it is possible to encounter a Virtual Router Redundancy Protocol (VRRP) conflict. This conflict might occur if a previously used OpenShift Container Platform node that was once part of a cluster deployment using a specific cluster name is still running but not part of the current OpenShift Container Platform cluster deployment using that same cluster name. For example, a cluster was deployed using the cluster name openshift, deploying three control plane (master) nodes and three worker nodes. Later, a separate install uses the same cluster name openshift, but this redeployment only installed three control plane (master) nodes, leaving the three worker nodes from a previous deployment in an ON state. This might cause a Virtual Router Identifier (VRID) conflict and a VRRP conflict.
Get the route:
oc get route oauth-openshift
$ oc get route oauth-openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow Check the service endpoint:
oc get svc oauth-openshift
$ oc get svc oauth-openshiftCopy to Clipboard Copied! Toggle word wrap Toggle overflow NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE oauth-openshift ClusterIP 172.30.19.162 <none> 443/TCP 59m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE oauth-openshift ClusterIP 172.30.19.162 <none> 443/TCP 59mCopy to Clipboard Copied! Toggle word wrap Toggle overflow Attempt to reach the service from a control plane (master) node:
curl -k https://172.30.19.162
[core@master0 ~]$ curl -k https://172.30.19.162Copy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow Identify the
authentication-operatorerrors from theprovisionernode:oc logs deployment/authentication-operator -n openshift-authentication-operator
$ oc logs deployment/authentication-operator -n openshift-authentication-operatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow Event(v1.ObjectReference{Kind:"Deployment", Namespace:"openshift-authentication-operator", Name:"authentication-operator", UID:"225c5bd5-b368-439b-9155-5fd3c0459d98", APIVersion:"apps/v1", ResourceVersion:"", FieldPath:""}): type: 'Normal' reason: 'OperatorStatusChanged' Status for clusteroperator/authentication changed: Degraded message changed from "IngressStateEndpointsDegraded: All 2 endpoints for oauth-server are reporting"Event(v1.ObjectReference{Kind:"Deployment", Namespace:"openshift-authentication-operator", Name:"authentication-operator", UID:"225c5bd5-b368-439b-9155-5fd3c0459d98", APIVersion:"apps/v1", ResourceVersion:"", FieldPath:""}): type: 'Normal' reason: 'OperatorStatusChanged' Status for clusteroperator/authentication changed: Degraded message changed from "IngressStateEndpointsDegraded: All 2 endpoints for oauth-server are reporting"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Solution
- Ensure that the cluster name for every deployment is unique, ensuring no conflict.
- Turn off all the rogue nodes which are not part of the cluster deployment that are using the same cluster name. Otherwise, the authentication pod of the OpenShift Container Platform cluster might never start successfully.
6.5.8.5. Failed Ignition during Firstboot
During the Firstboot, the Ignition configuration may fail.
Procedure
Connect to the node where the Ignition configuration failed:
Failed Units: 1 machine-config-daemon-firstboot.service
Failed Units: 1 machine-config-daemon-firstboot.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Restart the
machine-config-daemon-firstbootservice:sudo systemctl restart machine-config-daemon-firstboot.service
[core@worker-X ~]$ sudo systemctl restart machine-config-daemon-firstboot.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow
6.5.8.6. NTP out of sync
The deployment of OpenShift Container Platform clusters depends on NTP synchronized clocks among the cluster nodes. Without synchronized clocks, the deployment may fail due to clock drift if the time difference is greater than two seconds.
Procedure
Check for differences in the
AGEof the cluster nodes. For example:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow NAME STATUS ROLES AGE VERSION master-0.cloud.example.com Ready master 145m v1.16.2 master-1.cloud.example.com Ready master 135m v1.16.2 master-2.cloud.example.com Ready master 145m v1.16.2 worker-2.cloud.example.com Ready worker 100m v1.16.2
NAME STATUS ROLES AGE VERSION master-0.cloud.example.com Ready master 145m v1.16.2 master-1.cloud.example.com Ready master 135m v1.16.2 master-2.cloud.example.com Ready master 145m v1.16.2 worker-2.cloud.example.com Ready worker 100m v1.16.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check for inconsistent timing delays due to clock drift. For example:
oc get bmh -n openshift-machine-api
$ oc get bmh -n openshift-machine-apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow master-1 error registering master-1 ipmi://<out-of-band-ip>
master-1 error registering master-1 ipmi://<out-of-band-ip>Copy to Clipboard Copied! Toggle word wrap Toggle overflow sudo timedatectl
$ sudo timedatectlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Addressing clock drift in existing clusters
Create a
chrony.conffile and encode it asbase64string. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<NTP-server>with the IP address of the NTP server. Copy the output.
[text-in-base-64]
[text-in-base-64]Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject, replacing thebase64string with the[text-in-base-64]string generated in the output of the previous step. The following example adds the file to the control plane (master) nodes. You can modify the file for worker nodes or make an additional machine config for the worker role.Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
[text-in-base-64]with the base64 string.
Make a backup copy of the configuration file. For example:
cp 99_masters-chrony-configuration.yaml 99_masters-chrony-configuration.yaml.backup
$ cp 99_masters-chrony-configuration.yaml 99_masters-chrony-configuration.yaml.backupCopy to Clipboard Copied! Toggle word wrap Toggle overflow Apply the configuration file:
oc apply -f ./masters-chrony-configuration.yaml
$ oc apply -f ./masters-chrony-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure the
System clock synchronizedvalue is yes:sudo timedatectl
$ sudo timedatectlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Copy to Clipboard Copied! Toggle word wrap Toggle overflow To setup clock synchronization prior to deployment, generate the manifest files and add this file to the
openshiftdirectory. For example:cp chrony-masters.yaml ~/clusterconfigs/openshift/99_masters-chrony-configuration.yaml
$ cp chrony-masters.yaml ~/clusterconfigs/openshift/99_masters-chrony-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, continue to create the cluster.
6.5.9. Reviewing the installation
After installation, ensure the installer deployed the nodes and pods successfully.
Procedure
When the OpenShift Container Platform cluster nodes are installed appropriately, the following
Readystate is seen within theSTATUScolumn:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow NAME STATUS ROLES AGE VERSION master-0.example.com Ready master,worker 4h v1.16.2 master-1.example.com Ready master,worker 4h v1.16.2 master-2.example.com Ready master,worker 4h v1.16.2
NAME STATUS ROLES AGE VERSION master-0.example.com Ready master,worker 4h v1.16.2 master-1.example.com Ready master,worker 4h v1.16.2 master-2.example.com Ready master,worker 4h v1.16.2Copy to Clipboard Copied! Toggle word wrap Toggle overflow Confirm the installer deployed all pods successfully. The following command removes any pods that are still running or have completed as part of the output.
oc get pods --all-namespaces | grep -iv running | grep -iv complete
$ oc get pods --all-namespaces | grep -iv running | grep -iv completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Chapter 7. Installing on IBM Z and LinuxONE
7.1. Installing a cluster on IBM Z and LinuxONE
In OpenShift Container Platform version 4.6, you can install a cluster on IBM Z or LinuxONE infrastructure that you provision.
While this document refers only to IBM Z, all information in it also applies to LinuxONE.
Additional considerations exist for non-bare metal platforms. Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you install an OpenShift Container Platform cluster.
7.1.1. Prerequisites
- Before you begin the installation process, you must clean the installation directory. This ensures that the required installation files are created and updated during the installation process.
-
Provision persistent storage using NFS for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
- If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
Be sure to also review this site list if you are configuring a proxy.
7.1.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
7.1.3. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
7.1.3.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To improve high availability of your cluster, distribute the control plane machines over different z/VM instances on at least two physical machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
7.1.3.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. The machines are configured with static IP addresses. No DHCP server is required. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server.
7.1.3.3. IBM Z network connectivity requirements
To install on IBM Z under z/VM, you require a single z/VM virtual NIC in layer 2 mode. You also need:
- A direct-attached OSA or RoCE network adapter
- A z/VM VSwitch set up. For a preferred setup, use OSA link aggregation.
7.1.3.4. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | N/A |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | N/A |
| Compute | RHCOS | 2 | 8 GB | 100 GB | N/A |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
7.1.3.5. Minimum IBM Z system environment
You can install OpenShift Container Platform version 4.6 on the following IBM hardware:
- IBM z15 (all models), IBM z14 (all models), IBM z13, and IBM z13s
- LinuxONE, any version
Hardware requirements
- The equivalent of 6 IFLs, which are SMT2 enabled, for each cluster.
-
At least one network connection to both connect to the
LoadBalancerservice and to serve data for traffic outside the cluster.
You can use dedicated or shared IFLs to assign sufficient compute resources. Resource sharing is one of the key strengths of IBM Z. However, you must adjust capacity correctly on each hypervisor layer and ensure sufficient resources for every OpenShift Container Platform cluster.
Since the overall performance of the cluster can be impacted, the LPARs that are used to setup the OpenShift Container Platform clusters must provide sufficient compute capacity. In this context, LPAR weight management, entitlements, and CPU shares on the hypervisor level play an important role.
Operating system requirements
- One instance of z/VM 7.1 or later
On your z/VM instance, set up:
- 3 guest virtual machines for OpenShift Container Platform control plane machines
- 2 guest virtual machines for OpenShift Container Platform compute machines
- 1 guest virtual machine for the temporary OpenShift Container Platform bootstrap machine
IBM Z network connectivity requirements
To install on IBM Z under z/VM, you require a single z/VM virtual NIC in layer 2 mode. You also need:
- A direct-attached OSA or RoCE network adapter
- A z/VM VSwitch set up. For a preferred setup, use OSA link aggregation.
Disk storage for the z/VM guest virtual machines
- FICON attached disk storage (DASDs). These can be z/VM minidisks, fullpack minidisks, or dedicated DASDs, all of which must be formatted as CDL, which is the default. To reach the minimum required DASD size for Red Hat Enterprise Linux CoreOS (RHCOS) installations, you need extended address volumes (EAV). If available, use HyperPAV to ensure optimal performance.
- FCP attached disk storage
Storage / Main Memory
- 16 GB for OpenShift Container Platform control plane machines
- 8 GB for OpenShift Container Platform compute machines
- 16 GB for the temporary OpenShift Container Platform bootstrap machine
7.1.3.6. Preferred IBM Z system environment
Hardware requirements
- 3 LPARS that each have the equivalent of 6 IFLs, which are SMT2 enabled, for each cluster.
-
Two network connections to connect to both connect to the
LoadBalancerservice and to serve data for traffic outside the cluster. - HiperSockets, which are attached to a node either directly as a device or by bridging with one z/VM VSWITCH to be transparent to the z/VM guest. To directly connect HiperSockets to a node, you must set up a gateway to the external network via a RHEL 8 guest to bridge to the HiperSockets network.
Operating system requirements
- 2 or 3 instances of z/VM 7.1 or later for high availability
On your z/VM instances, set up:
- 3 guest virtual machines for OpenShift Container Platform control plane machines, one per z/VM instance.
- At least 6 guest virtual machines for OpenShift Container Platform compute machines, distributed across the z/VM instances.
- 1 guest virtual machine for the temporary OpenShift Container Platform bootstrap machine.
-
To ensure the availability of integral components in an overcommitted environment, increase the priority of the control plane by using the CP command
SET SHARE. Do the same for infrastructure nodes, if they exist. See SET SHARE in IBM Documentation.
IBM Z network connectivity requirements
To install on IBM Z under z/VM, you require a single z/VM virtual NIC in layer 2 mode. You also need:
- A direct-attached OSA or RoCE network adapter
- A z/VM VSwitch set up. For a preferred setup, use OSA link aggregation.
Disk storage for the z/VM guest virtual machines
- FICON attached disk storage (DASDs). These can be z/VM minidisks, fullpack minidisks, or dedicated DASDs, all of which must be formatted as CDL, which is the default. To reach the minimum required DASD size for Red Hat Enterprise Linux CoreOS (RHCOS) installations, you need extended address volumes (EAV). If available, use HyperPAV and High Performance FICON (zHPF) to ensure optimal performance.
- FCP attached disk storage
Storage / Main Memory
- 16 GB for OpenShift Container Platform control plane machines
- 8 GB for OpenShift Container Platform compute machines
- 16 GB for the temporary OpenShift Container Platform bootstrap machine
7.1.3.7. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
7.1.4. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Set up static IP addresses.
- Set up an FTP server.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
7.1.4.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require an FTP server in order to establish a network connection to download their Ignition config files.
Ensure that the machines have persistent IP addresses and host names.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 7.5. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 7.6. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
7.1.4.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 7.1. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 7.2. Sample DNS zone database for reverse records
7.1.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
Do not skip this procedure in production environments where disaster recovery and debugging is required.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
7.1.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on your provisioning machine.
Prerequisites
- You have a machine that runs Linux, for example Red Hat Enterprise Linux 8, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
7.1.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
7.1.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>7.1.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>7.1.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>7.1.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
7.1.8.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
7.1.8.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
7.1.8.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap.
If you specify multiple IP kernel arguments, the | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
7.1.8.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
7.1.8.2. Sample install-config.yaml file for IBM Z
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for IBM Z infrastructure. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- The pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
7.1.9. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
7.1.10. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.1.11. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines
Before you install a cluster on IBM Z infrastructure that you provision, you must install RHCOS on z/VM guest virtual machines for the cluster to use. Complete the following steps to create the machines.
Prerequisites
- An FTP server running on your provisioning machine that is accessible to the machines you create.
Procedure
- Log in to Linux on your provisioning machine.
Obtain the Red Hat Enterprise Linux CoreOS (RHCOS) kernel, initramfs, and rootfs files from the RHCOS image mirror.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate kernel, initramfs, and rootfs artifacts described in the following procedure.
The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:
rhcos-<version>-live-kernel-<architecture> -
initramfs:
rhcos-<version>-live-initramfs.<architecture>.img rootfs:
rhcos-<version>-live-rootfs.<architecture>.imgNoteThe rootfs image is the same for FCP and DASD.
-
kernel:
Create parameter files. The following parameters are specific for a particular virtual machine:
-
For
coreos.inst.install_dev=, specifydasdafor a DASD installation, orsdafor FCP. Note that FCP requireszfcp.allow_lun_scan=0. -
For
rd.dasd=, specifys the DASD where RHCOS is to be installed. -
rd.zfcp=<adapter>,<wwpn>,<lun>specifies the FCP disk to install RHCOS on. For
ip=, specify the following seven entries:- The IP address for the machine.
- An empty string.
- The gateway.
- The netmask.
-
The machine host and domain name in the form
hostname.domainname. Omit this value to let RHCOS decide. - The network interface name. Omit this value to let RHCOS decide.
- If you use static IP addresses, an empty string.
-
For
coreos.inst.ignition_url=, specify the Ignition file for the machine role. Usebootstrap.ign,master.ign, orworker.ign. Only HTTP and HTTPS protocols are supported. -
For
coreos.live.rootfs_url=, specify the matching rootfs artifact for the kernel and initramfs you are booting. Only HTTP and HTTPS protocols are supported. All other parameters can stay as they are.
Example parameter file,
bootstrap-0.parm, for the bootstrap machine:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Write all options in the parameter file as a single line and make sure you have no newline characters.
-
For
- Transfer the initramfs, kernel, parameter files, and RHCOS images to z/VM, for example with FTP. For details about how to transfer the files with FTP and boot from the virtual reader, see Installing under Z/VM.
Punch the files to the virtual reader of the z/VM guest virtual machine that is to become your bootstrap node.
See PUNCH in IBM Documentation.
TipYou can use the CP PUNCH command or, if you use Linux, the vmur command to transfer files between two z/VM guest virtual machines.
- Log in to CMS on the bootstrap machine.
IPL the bootstrap machine from the reader:
ipl c
$ ipl cCopy to Clipboard Copied! Toggle word wrap Toggle overflow See IPL in IBM Documentation.
- Repeat this procedure for the other machines in the cluster.
7.1.11.1. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
7.1.12. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
7.1.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.1.14. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-mddf5 20m system:node:master-01.example.com Approved,Issued csr-z5rln 16m system:node:worker-21.example.com Approved,Issued
NAME AGE REQUESTOR CONDITION csr-mddf5 20m system:node:master-01.example.com Approved,Issued csr-z5rln 16m system:node:worker-21.example.com Approved,IssuedCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
7.1.15. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
7.1.15.1. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
7.1.15.1.1. Configuring registry storage for IBM Z
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on IBM Z.
Persistent storage provisioned for your cluster.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.1.15.1.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
7.1.16. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
7.1.17. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
7.1.18. Collecting debugging information
You can gather debugging information that might help you to troubleshoot and debug certain issues with an OpenShift Container Platform installation on IBM Z.
Prerequisites
-
The
ocCLI tool installed.
Procedure
Log in to the cluster:
oc login
$ oc loginCopy to Clipboard Copied! Toggle word wrap Toggle overflow On the node you want to gather hardware information about, start a debugging container:
oc debug node/<nodename>
$ oc debug node/<nodename>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Change to the /host file system and start
toolbox:chroot /host toolbox
$ chroot /host $ toolboxCopy to Clipboard Copied! Toggle word wrap Toggle overflow Collect the
dbginfodata:dbginfo.sh
$ dbginfo.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
You can then retrieve the data, for example, using
scp.
7.1.19. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
7.2. Installing a cluster on IBM Z and LinuxONE in a restricted network
In OpenShift Container Platform version 4.6, you can install a cluster on IBM Z and LinuxONE infrastructure that you provision in a restricted network.
While this document refers to only IBM Z, all information in it also applies to LinuxONE.
Additional considerations exist for non-bare metal platforms. Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you install an OpenShift Container Platform cluster.
Prerequisites
-
Create a mirror registry for installation in a restricted network and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform. Before you begin the installation process, you must move or remove any existing installation files. This ensures that the required installation files are created and updated during the installation process.
ImportantEnsure that installation steps are done from a machine with access to the installation media.
-
Provision persistent storage using NFS for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
7.2.1. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
7.2.1.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
7.2.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
7.2.3. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
7.2.3.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To improve high availability of your cluster, distribute the control plane machines over different z/VM instances on at least two physical machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
7.2.3.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. The machines are configured with static IP addresses. No DHCP server is required. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server.
7.2.3.3. IBM Z network connectivity requirements
To install on IBM Z under z/VM, you require a single z/VM virtual NIC in layer 2 mode. You also need:
- A direct-attached OSA or RoCE network adapter
- A z/VM VSwitch set up. For a preferred setup, use OSA link aggregation.
7.2.3.4. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | N/A |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | N/A |
| Compute | RHCOS | 2 | 8 GB | 100 GB | N/A |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
7.2.3.5. Minimum IBM Z system environment
You can install OpenShift Container Platform version 4.6 on the following IBM hardware:
- IBM z15 (all models), IBM z14 (all models), IBM z13, and IBM z13s
- LinuxONE, any version
Hardware requirements
- The equivalent of 6 IFLs, which are SMT2 enabled, for each cluster.
-
At least one network connection to both connect to the
LoadBalancerservice and to serve data for traffic outside the cluster.
You can use dedicated or shared IFLs to assign sufficient compute resources. Resource sharing is one of the key strengths of IBM Z. However, you must adjust capacity correctly on each hypervisor layer and ensure sufficient resources for every OpenShift Container Platform cluster.
Since the overall performance of the cluster can be impacted, the LPARs that are used to setup the OpenShift Container Platform clusters must provide sufficient compute capacity. In this context, LPAR weight management, entitlements, and CPU shares on the hypervisor level play an important role.
Operating system requirements
- One instance of z/VM 7.1 or later
On your z/VM instance, set up:
- 3 guest virtual machines for OpenShift Container Platform control plane machines
- 2 guest virtual machines for OpenShift Container Platform compute machines
- 1 guest virtual machine for the temporary OpenShift Container Platform bootstrap machine
IBM Z network connectivity requirements
To install on IBM Z under z/VM, you require a single z/VM virtual NIC in layer 2 mode. You also need:
- A direct-attached OSA or RoCE network adapter
- A z/VM VSwitch set up. For a preferred setup, use OSA link aggregation.
Disk storage for the z/VM guest virtual machines
- FICON attached disk storage (DASDs). These can be z/VM minidisks, fullpack minidisks, or dedicated DASDs, all of which must be formatted as CDL, which is the default. To reach the minimum required DASD size for Red Hat Enterprise Linux CoreOS (RHCOS) installations, you need extended address volumes (EAV). If available, use HyperPAV to ensure optimal performance.
- FCP attached disk storage
Storage / Main Memory
- 16 GB for OpenShift Container Platform control plane machines
- 8 GB for OpenShift Container Platform compute machines
- 16 GB for the temporary OpenShift Container Platform bootstrap machine
7.2.3.6. Preferred IBM Z system environment
Hardware requirements
- 3 LPARS that each have the equivalent of 6 IFLs, which are SMT2 enabled, for each cluster.
-
Two network connections to connect to both connect to the
LoadBalancerservice and to serve data for traffic outside the cluster. - HiperSockets, which are attached to a node either directly as a device or by bridging with one z/VM VSWITCH to be transparent to the z/VM guest. To directly connect HiperSockets to a node, you must set up a gateway to the external network via a RHEL 8 guest to bridge to the HiperSockets network.
Operating system requirements
- 2 or 3 instances of z/VM 7.1 or later for high availability
On your z/VM instances, set up:
- 3 guest virtual machines for OpenShift Container Platform control plane machines, one per z/VM instance.
- At least 6 guest virtual machines for OpenShift Container Platform compute machines, distributed across the z/VM instances.
- 1 guest virtual machine for the temporary OpenShift Container Platform bootstrap machine.
-
To ensure the availability of integral components in an overcommitted environment, increase the priority of the control plane by using the CP command
SET SHARE. Do the same for infrastructure nodes, if they exist. See SET SHARE in IBM Documentation.
IBM Z network connectivity requirements
To install on IBM Z under z/VM, you require a single z/VM virtual NIC in layer 2 mode. You also need:
- A direct-attached OSA or RoCE network adapter
- A z/VM VSwitch set up. For a preferred setup, use OSA link aggregation.
Disk storage for the z/VM guest virtual machines
- FICON attached disk storage (DASDs). These can be z/VM minidisks, fullpack minidisks, or dedicated DASDs, all of which must be formatted as CDL, which is the default. To reach the minimum required DASD size for Red Hat Enterprise Linux CoreOS (RHCOS) installations, you need extended address volumes (EAV). If available, use HyperPAV and High Performance FICON (zHPF) to ensure optimal performance.
- FCP attached disk storage
Storage / Main Memory
- 16 GB for OpenShift Container Platform control plane machines
- 8 GB for OpenShift Container Platform compute machines
- 16 GB for the temporary OpenShift Container Platform bootstrap machine
7.2.3.7. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
7.2.4. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
7.2.4.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 7.15. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 7.16. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers. :!restricted:
7.2.4.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 7.3. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 7.4. Sample DNS zone database for reverse records
7.2.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
Do not skip this procedure in production environments where disaster recovery and debugging is required.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
7.2.6. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
-
Obtain the
imageContentSourcessection from the output of the command to mirror the repository. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.-
Unless you use a registry that RHCOS trusts by default, such as
docker.io, you must provide the contents of the certificate for your mirror repository in theadditionalTrustBundlesection. In most cases, you must provide the certificate for your mirror. -
You must include the
imageContentSourcessection from the output of the command to mirror the repository.
-
Unless you use a registry that RHCOS trusts by default, such as
Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
7.2.6.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
7.2.6.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
7.2.6.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap.
If you specify multiple IP kernel arguments, the | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
7.2.6.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
7.2.6.2. Sample install-config.yaml file for IBM Z
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for IBM Z infrastructure. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 16
- Add the
additionalTrustBundleparameter and value. The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry. - 17
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
7.2.6.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
7.2.7. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
7.2.8. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines
Before you install a cluster on IBM Z infrastructure that you provision, you must install RHCOS on z/VM guest virtual machines for the cluster to use. Complete the following steps to create the machines.
Prerequisites
- An FTP server running on your provisioning machine that is accessible to the machines you create.
Procedure
- Log in to Linux on your provisioning machine.
Obtain the Red Hat Enterprise Linux CoreOS (RHCOS) kernel, initramfs, and rootfs files from the RHCOS image mirror.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate kernel, initramfs, and rootfs artifacts described in the following procedure.
The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:
rhcos-<version>-live-kernel-<architecture> -
initramfs:
rhcos-<version>-live-initramfs.<architecture>.img rootfs:
rhcos-<version>-live-rootfs.<architecture>.imgNoteThe rootfs image is the same for FCP and DASD.
-
kernel:
Create parameter files. The following parameters are specific for a particular virtual machine:
-
For
coreos.inst.install_dev=, specifydasdafor a DASD installation, orsdafor FCP. Note that FCP requireszfcp.allow_lun_scan=0. -
For
rd.dasd=, specifys the DASD where RHCOS is to be installed. -
rd.zfcp=<adapter>,<wwpn>,<lun>specifies the FCP disk to install RHCOS on. For
ip=, specify the following seven entries:- The IP address for the machine.
- An empty string.
- The gateway.
- The netmask.
-
The machine host and domain name in the form
hostname.domainname. Omit this value to let RHCOS decide. - The network interface name. Omit this value to let RHCOS decide.
- If you use static IP addresses, an empty string.
-
For
coreos.inst.ignition_url=, specify the Ignition file for the machine role. Usebootstrap.ign,master.ign, orworker.ign. Only HTTP and HTTPS protocols are supported. -
For
coreos.live.rootfs_url=, specify the matching rootfs artifact for the kernel and initramfs you are booting. Only HTTP and HTTPS protocols are supported. All other parameters can stay as they are.
Example parameter file,
bootstrap-0.parm, for the bootstrap machine:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Write all options in the parameter file as a single line and make sure you have no newline characters.
-
For
- Transfer the initramfs, kernel, parameter files, and RHCOS images to z/VM, for example with FTP. For details about how to transfer the files with FTP and boot from the virtual reader, see Installing under Z/VM.
Punch the files to the virtual reader of the z/VM guest virtual machine that is to become your bootstrap node.
See PUNCH in IBM Documentation.
TipYou can use the CP PUNCH command or, if you use Linux, the vmur command to transfer files between two z/VM guest virtual machines.
- Log in to CMS on the bootstrap machine.
IPL the bootstrap machine from the reader:
ipl c
$ ipl cCopy to Clipboard Copied! Toggle word wrap Toggle overflow See IPL in IBM Documentation.
- Repeat this procedure for the other machines in the cluster.
7.2.8.1. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
7.2.9. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
7.2.10. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.2.11. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
7.2.12. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
7.2.12.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
7.2.12.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
7.2.12.2.1. Configuring registry storage for IBM Z
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on IBM Z.
Persistent storage provisioned for your cluster.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
7.2.12.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
7.2.13. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
- Register your cluster on the Cluster registration page.
7.2.14. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
7.2.15. Collecting debugging information
You can gather debugging information that might help you to troubleshoot and debug certain issues with an OpenShift Container Platform installation on IBM Z.
Prerequisites
-
The
ocCLI tool installed.
Procedure
Log in to the cluster:
oc login
$ oc loginCopy to Clipboard Copied! Toggle word wrap Toggle overflow On the node you want to gather hardware information about, start a debugging container:
oc debug node/<nodename>
$ oc debug node/<nodename>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Change to the /host file system and start
toolbox:chroot /host toolbox
$ chroot /host $ toolboxCopy to Clipboard Copied! Toggle word wrap Toggle overflow Collect the
dbginfodata:dbginfo.sh
$ dbginfo.shCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
You can then retrieve the data, for example, using
scp.
7.2.16. Next steps
- Customize your cluster.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
Chapter 8. Installing on IBM Power Systems
8.1. Installing a cluster on IBM Power Systems
In OpenShift Container Platform version 4.6, you can install a cluster on IBM Power Systems infrastructure that you provision.
Additional considerations exist for non-bare metal platforms. Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you install an OpenShift Container Platform cluster.
Prerequisites
- Before you begin the installation process, you must clean the installation directory. This ensures that the required installation files are created and updated during the installation process.
-
Provision persistent storage using NFS for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
8.1.1. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
8.1.2. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
8.1.2.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
8.1.2.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
8.1.2.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 2 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 2 | 16 GB | 100 GB | 300 |
| Compute | RHCOS | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
8.1.2.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
8.1.3. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
8.1.3.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 8.5. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 8.6. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
8.1.3.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 8.1. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 8.2. Sample DNS zone database for reverse records
8.1.4. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
8.1.5. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
8.1.6. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
8.1.6.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>8.1.6.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>8.1.6.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>8.1.7. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
8.1.7.1. Sample install-config.yaml file for IBM Power Systems
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for IBM Power Systems infrastructure. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- The pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
8.1.7.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
8.1.8. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.9. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines
Before you install a cluster on IBM Power Systems infrastructure that you provision, you must create RHCOS machines for it to use. Follow either the steps to use an ISO image or network PXE booting to create the machines.
8.1.9.1. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines using an ISO image
Before you install a cluster on IBM Power Systems infrastructure that you provision, you must create RHCOS machines for it to use. You can use an ISO image to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Have access to an HTTP server that can be accessed from your computer, and from the machines that you create.
Procedure
Upload the control plane, compute, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS images that are required for your preferred method of installing operating system instances from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available. Use only ISO images for this procedure. RHCOS qcow2 images are not supported for this installation type.
ISO file names resemble the following example:
rhcos-<version>-live.<architecture>.isoUse the ISO to start the RHCOS installation. Use one of the following installation options:
- Burn the ISO image to a disk and boot it directly.
- Use ISO redirection via a LOM interface.
-
Boot the ISO image. You can interrupt the installation boot process to add kernel arguments. However, for this ISO procedure you should use the
coreos-installercommand instead of adding kernel arguments. If you run the live installer without options or interruption, the installer boots up to a shell prompt on the live system, ready for you to install RHCOS to disk. -
Review the Advanced RHCOS installation reference section for different ways of configuring features, such as networking and disk partitions, before running the
coreos-installer. Run the
coreos-installercommand. At a minimum, you must identify the Ignition config file location for your node type, and the location of the disk you are installing to. Here is an example:sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sda$ sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After RHCOS installs, the system reboots. During the system reboot, it applies the Ignition config file that you specified.
Continue to create the other machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
8.1.9.1.1. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
8.1.9.2. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines by PXE or iPXE booting
Before you install a cluster that uses manually-provisioned RHCOS nodes, such as bare metal, you must create RHCOS machines for it to use. You can use PXE or iPXE booting to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Configure suitable PXE or iPXE infrastructure.
- Have access to an HTTP server that you can access from your computer.
Procedure
Upload the master, worker, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantYou can add or change configuration settings in your Ignition configs before saving them to your HTTP server. If you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS
kernel,initramfsandrootfsfiles from the RHCOS image mirror page.ImportantThe RHCOS artifacts might not change with every release of OpenShift Container Platform. You must download artifacts with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate
kernel,initramfs, androotfsartifacts described below for this procedure. RHCOS qcow2 images are not supported for this installation type.The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:rhcos-<version>-live-kernel-<architecture> -
initramfs:rhcos-<version>-live-initramfs.<architecture>.img -
rootfs:rhcos-<version>-live-rootfs.<architecture>.img
-
Upload the additional files that are required for your booting method:
-
For traditional PXE, upload the
kernelandinitramfsfiles to your TFTP server and therootfsfile to your HTTP server. For iPXE, upload the
kernel,initramfs, androotfsfiles to your HTTP server.ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
-
For traditional PXE, upload the
- Configure the network boot infrastructure so that the machines boot from their local disks after RHCOS is installed on them.
Configure PXE or iPXE installation for the RHCOS images.
Modify one of the following example menu entries for your environment and verify that the image and Ignition files are properly accessible:
For PXE:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the location of the live
kernelfile that you uploaded to your HTTP server. The URL must be HTTP, TFTP, or FTP; HTTPS and NFS are not supported. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
initrdparameter value is the location of theinitramfsfile, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. You can also add more kernel arguments to theAPPENDline to configure networking or other boot options.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to theAPPENDline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.For iPXE:
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img boot
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign1 2 initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img3 bootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
kernelparameter value is the location of thekernelfile, theinitrd=mainargument is needed for booting on UEFI systems, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify the location of the
initramfsfile that you uploaded to your HTTP server.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to thekernelline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.
If you use PXE UEFI, perform the following actions:
Provide the
shimx64.efiandgrubx64.efiEFI binaries and thegrub.cfgfile that are required for booting the system.Extract the necessary EFI binaries by mounting the RHCOS ISO to your host and then mounting the
images/efiboot.imgfile to your host:mkdir -p /mnt/iso
$ mkdir -p /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p /mnt/efiboot
$ mkdir -p /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop rhcos-installer.x86_64.iso /mnt/iso
$ mount -o loop rhcos-installer.x86_64.iso /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efiboot
$ mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the
efiboot.imgmount point, copy theEFI/redhat/shimx64.efiandEFI/redhat/grubx64.efifiles to your TFTP server:cp /mnt/efiboot/EFI/redhat/shimx64.efi .
$ cp /mnt/efiboot/EFI/redhat/shimx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp /mnt/efiboot/EFI/redhat/grubx64.efi .
$ cp /mnt/efiboot/EFI/redhat/grubx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/efiboot
$ umount /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/iso
$ umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the
EFI/redhat/grub.cfgfile that is included in the RHCOS ISO to your TFTP server.
Edit the
grub.cfgfile to include arguments similar to the following:menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
rhcos-<version>-live-kernel-<architecture>-
Specifies the
kernelfile that you uploaded to your TFTP server. http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img- Specifies the location of the live rootfs image that you uploaded to your HTTP server.
http://<HTTP_server>/bootstrap.ign- Specifies the location of the bootstrap Ignition config file that you uploaded to your HTTP server.
rhcos-<version>-live-initramfs.<architecture>.img-
Specifies the location of the
initramfsfile that you uploaded to your TFTP server.
NoteFor more information on how to configure a PXE server for UEFI boot, see the Red Hat Knowledgebase article: How to configure/setup a PXE server for UEFI boot for Red Hat Enterprise Linux?.
Continue to create the machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
8.1.10. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
8.1.11. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.12. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
8.1.13. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
8.1.13.1. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
8.1.13.1.1. Configuring registry storage for IBM Power Systems
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on IBM Power Systems.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.1.13.1.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
8.1.14. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
8.1.15. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
8.1.16. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
8.2. Installing a cluster on IBM Power Systems in a restricted network
In OpenShift Container Platform version 4.6, you can install a cluster on IBM Power Systems infrastructure that you provision in a restricted network.
Additional considerations exist for non-bare metal platforms. Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you install an OpenShift Container Platform cluster.
Prerequisites
-
Create a mirror registry for installation in a restricted network and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform. Before you begin the installation process, you must move or remove any existing installation files. This ensures that the required installation files are created and updated during the installation process.
ImportantEnsure that installation steps are performed on a machine with access to the installation media.
-
Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
8.2.1. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
8.2.1.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
8.2.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
8.2.3. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
8.2.3.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
8.2.3.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
8.2.3.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 2 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 2 | 16 GB | 100 GB | 300 |
| Compute | RHCOS | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
8.2.3.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
8.2.4. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
8.2.4.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 8.12. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 8.13. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers. :!restricted:
8.2.4.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 8.3. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 8.4. Sample DNS zone database for reverse records
8.2.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
8.2.6. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
-
Obtain the
imageContentSourcessection from the output of the command to mirror the repository. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.-
Unless you use a registry that RHCOS trusts by default, such as
docker.io, you must provide the contents of the certificate for your mirror repository in theadditionalTrustBundlesection. In most cases, you must provide the certificate for your mirror. -
You must include the
imageContentSourcessection from the output of the command to mirror the repository.
-
Unless you use a registry that RHCOS trusts by default, such as
Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
8.2.6.1. Sample install-config.yaml file for IBM Power Systems
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for IBM Power Systems infrastructure. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 16
- Provide the contents of the certificate file that you used for your mirror registry.
- 17
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
8.2.6.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
8.2.7. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program. For a restricted network installation, these files are on your mirror host.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.8. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines
Before you install a cluster on IBM Power Systems infrastructure that you provision, you must create RHCOS machines for it to use. Follow either the steps to use an ISO image or network PXE booting to create the machines.
8.2.8.1. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines using an ISO image
Before you install a cluster on IBM Power Systems infrastructure that you provision, you must create RHCOS machines for it to use. You can use an ISO image to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Have access to an HTTP server that can be accessed from your computer, and from the machines that you create.
Procedure
Upload the control plane, compute, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS images that are required for your preferred method of installing operating system instances from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available. Use only ISO images for this procedure. RHCOS qcow2 images are not supported for this installation type.
ISO file names resemble the following example:
rhcos-<version>-live.<architecture>.isoUse the ISO to start the RHCOS installation. Use one of the following installation options:
- Burn the ISO image to a disk and boot it directly.
- Use ISO redirection via a LOM interface.
-
Boot the ISO image. You can interrupt the installation boot process to add kernel arguments. However, for this ISO procedure you should use the
coreos-installercommand instead of adding kernel arguments. If you run the live installer without options or interruption, the installer boots up to a shell prompt on the live system, ready for you to install RHCOS to disk. -
Review the Advanced RHCOS installation reference section for different ways of configuring features, such as networking and disk partitions, before running the
coreos-installer. Run the
coreos-installercommand. At a minimum, you must identify the Ignition config file location for your node type, and the location of the disk you are installing to. Here is an example:sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sda$ sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After RHCOS installs, the system reboots. During the system reboot, it applies the Ignition config file that you specified.
Continue to create the other machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
8.2.8.1.1. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
8.2.8.2. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines by PXE or iPXE booting
Before you install a cluster that uses manually-provisioned RHCOS nodes, such as bare metal, you must create RHCOS machines for it to use. You can use PXE or iPXE booting to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Configure suitable PXE or iPXE infrastructure.
- Have access to an HTTP server that you can access from your computer.
Procedure
Upload the master, worker, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantYou can add or change configuration settings in your Ignition configs before saving them to your HTTP server. If you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS
kernel,initramfsandrootfsfiles from the RHCOS image mirror page.ImportantThe RHCOS artifacts might not change with every release of OpenShift Container Platform. You must download artifacts with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate
kernel,initramfs, androotfsartifacts described below for this procedure. RHCOS qcow2 images are not supported for this installation type.The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:rhcos-<version>-live-kernel-<architecture> -
initramfs:rhcos-<version>-live-initramfs.<architecture>.img -
rootfs:rhcos-<version>-live-rootfs.<architecture>.img
-
Upload the additional files that are required for your booting method:
-
For traditional PXE, upload the
kernelandinitramfsfiles to your TFTP server and therootfsfile to your HTTP server. For iPXE, upload the
kernel,initramfs, androotfsfiles to your HTTP server.ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
-
For traditional PXE, upload the
- Configure the network boot infrastructure so that the machines boot from their local disks after RHCOS is installed on them.
Configure PXE or iPXE installation for the RHCOS images.
Modify one of the following example menu entries for your environment and verify that the image and Ignition files are properly accessible:
For PXE:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the location of the live
kernelfile that you uploaded to your HTTP server. The URL must be HTTP, TFTP, or FTP; HTTPS and NFS are not supported. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
initrdparameter value is the location of theinitramfsfile, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. You can also add more kernel arguments to theAPPENDline to configure networking or other boot options.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to theAPPENDline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.For iPXE:
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img boot
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign1 2 initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img3 bootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
kernelparameter value is the location of thekernelfile, theinitrd=mainargument is needed for booting on UEFI systems, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify the location of the
initramfsfile that you uploaded to your HTTP server.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to thekernelline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.
If you use PXE UEFI, perform the following actions:
Provide the
shimx64.efiandgrubx64.efiEFI binaries and thegrub.cfgfile that are required for booting the system.Extract the necessary EFI binaries by mounting the RHCOS ISO to your host and then mounting the
images/efiboot.imgfile to your host:mkdir -p /mnt/iso
$ mkdir -p /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p /mnt/efiboot
$ mkdir -p /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop rhcos-installer.x86_64.iso /mnt/iso
$ mount -o loop rhcos-installer.x86_64.iso /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efiboot
$ mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the
efiboot.imgmount point, copy theEFI/redhat/shimx64.efiandEFI/redhat/grubx64.efifiles to your TFTP server:cp /mnt/efiboot/EFI/redhat/shimx64.efi .
$ cp /mnt/efiboot/EFI/redhat/shimx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp /mnt/efiboot/EFI/redhat/grubx64.efi .
$ cp /mnt/efiboot/EFI/redhat/grubx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/efiboot
$ umount /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/iso
$ umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the
EFI/redhat/grub.cfgfile that is included in the RHCOS ISO to your TFTP server.
Edit the
grub.cfgfile to include arguments similar to the following:menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
rhcos-<version>-live-kernel-<architecture>-
Specifies the
kernelfile that you uploaded to your TFTP server. http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img- Specifies the location of the live rootfs image that you uploaded to your HTTP server.
http://<HTTP_server>/bootstrap.ign- Specifies the location of the bootstrap Ignition config file that you uploaded to your HTTP server.
rhcos-<version>-live-initramfs.<architecture>.img-
Specifies the location of the
initramfsfile that you uploaded to your TFTP server.
NoteFor more information on how to configure a PXE server for UEFI boot, see the Red Hat Knowledgebase article: How to configure/setup a PXE server for UEFI boot for Red Hat Enterprise Linux?.
Continue to create the machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
8.2.9. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
8.2.10. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.11. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
8.2.12. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
8.2.12.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
8.2.12.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
8.2.12.2.1. Changing the image registry’s management state
To start the image registry, you must change the Image Registry Operator configuration’s managementState from Removed to Managed.
Procedure
Change
managementStateImage Registry Operator configuration fromRemovedtoManaged. For example:oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"managementState":"Managed"}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"managementState":"Managed"}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.12.2.2. Configuring registry storage for IBM Power Systems
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on IBM Power Systems.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
8.2.12.2.3. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
8.2.13. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
8.2.14. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
8.2.15. Next steps
- Customize your cluster.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
Chapter 9. Installing on OpenStack
9.1. Installing a cluster on OpenStack with customizations
In OpenShift Container Platform version 4.6, you can install a customized cluster on Red Hat OpenStack Platform (RHOSP). To customize the installation, modify parameters in the install-config.yaml before you install the cluster.
9.1.1. Prerequisites
Review details about the OpenShift Container Platform installation and update processes.
- Verify that OpenShift Container Platform 4.6 is compatible with your RHOSP version in the Available platforms section. You can also compare platform support across different versions by viewing the OpenShift Container Platform on RHOSP support matrix.
- Verify that your network configuration does not rely on a provider network. Provider networks are not supported.
- Have a storage service installed in RHOSP, like block storage (Cinder) or object storage (Swift). Object storage is the recommended storage technology for OpenShift Container Platform registry cluster deployment. For more information, see Optimizing storage.
- Have metadata service enabled in RHOSP
9.1.2. Resource guidelines for installing OpenShift Container Platform on RHOSP
To support an OpenShift Container Platform installation, your Red Hat OpenStack Platform (RHOSP) quota must meet the following requirements:
| Resource | Value |
|---|---|
| Floating IP addresses | 3 |
| Ports | 15 |
| Routers | 1 |
| Subnets | 1 |
| RAM | 112 GB |
| vCPUs | 28 |
| Volume storage | 275 GB |
| Instances | 7 |
| Security groups | 3 |
| Security group rules | 60 |
A cluster might function with fewer than recommended resources, but its performance is not guaranteed.
If RHOSP object storage (Swift) is available and operated by a user account with the swiftoperator role, it is used as the default backend for the OpenShift Container Platform image registry. In this case, the volume storage requirement is 175 GB. Swift space requirements vary depending on the size of the image registry.
By default, your security group and security group rule quotas might be low. If you encounter problems, run openstack quota set --secgroups 3 --secgroup-rules 60 <project> as an administrator to increase them.
An OpenShift Container Platform deployment comprises control plane machines, compute machines, and a bootstrap machine.
9.1.2.1. Control plane machines
By default, the OpenShift Container Platform installation process creates three control plane machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.1.2.2. Compute machines
By default, the OpenShift Container Platform installation process creates three compute machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 8 GB memory, 2 vCPUs, and 100 GB storage space
Compute machines host the applications that you run on OpenShift Container Platform; aim to run as many as you can.
9.1.2.3. Bootstrap machine
During installation, a bootstrap machine is temporarily provisioned to stand up the control plane. After the production control plane is ready, the bootstrap machine is deprovisioned.
The bootstrap machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.1.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
9.1.4. Enabling Swift on RHOSP
Swift is operated by a user account with the swiftoperator role. Add the role to an account before you run the installation program.
If the Red Hat OpenStack Platform (RHOSP) object storage service, commonly known as Swift, is available, OpenShift Container Platform uses it as the image registry storage. If it is unavailable, the installation program relies on the RHOSP block storage service, commonly known as Cinder.
If Swift is present and you want to use it, you must enable access to it. If it is not present, or if you do not want to use it, skip this section.
Prerequisites
- You have a RHOSP administrator account on the target environment.
- The Swift service is installed.
-
On Ceph RGW, the
account in urloption is enabled.
Procedure
To enable Swift on RHOSP:
As an administrator in the RHOSP CLI, add the
swiftoperatorrole to the account that will access Swift:openstack role add --user <user> --project <project> swiftoperator
$ openstack role add --user <user> --project <project> swiftoperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Your RHOSP deployment can now use Swift for the image registry.
9.1.5. Verifying external network access
The OpenShift Container Platform installation process requires external network access. You must provide an external network value to it, or deployment fails. Before you begin the process, verify that a network with the external router type exists in Red Hat OpenStack Platform (RHOSP).
Prerequisites
Procedure
Using the RHOSP CLI, verify the name and ID of the 'External' network:
openstack network list --long -c ID -c Name -c "Router Type"
$ openstack network list --long -c ID -c Name -c "Router Type"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+Copy to Clipboard Copied! Toggle word wrap Toggle overflow
A network with an external router type appears in the network list. If at least one does not, see Creating a default floating IP network and Creating a default provider network.
If the external network’s CIDR range overlaps one of the default network ranges, you must change the matching network ranges in the install-config.yaml file before you start the installation process.
The default network ranges are:
| Network | Range |
|---|---|
|
| 10.0.0.0/16 |
|
| 172.30.0.0/16 |
|
| 10.128.0.0/14 |
If the installation program finds multiple networks with the same name, it sets one of them at random. To avoid this behavior, create unique names for resources in RHOSP.
If the Neutron trunk service plug-in is enabled, a trunk port is created by default. For more information, see Neutron trunk port.
9.1.6. Defining parameters for the installation program
The OpenShift Container Platform installation program relies on a file that is called clouds.yaml. The file describes Red Hat OpenStack Platform (RHOSP) configuration parameters, including the project name, log in information, and authorization service URLs.
Procedure
Create the
clouds.yamlfile:If your RHOSP distribution includes the Horizon web UI, generate a
clouds.yamlfile in it.ImportantRemember to add a password to the
authfield. You can also keep secrets in a separate file fromclouds.yaml.If your RHOSP distribution does not include the Horizon web UI, or you do not want to use Horizon, create the file yourself. For detailed information about
clouds.yaml, see Config files in the RHOSP documentation.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If your RHOSP installation uses self-signed certificate authority (CA) certificates for endpoint authentication:
- Copy the certificate authority file to your machine.
Add the machine to the certificate authority trust bundle:
sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/
$ sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the trust bundle:
sudo update-ca-trust extract
$ sudo update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
cacertskey to theclouds.yamlfile. The value must be an absolute, non-root-accessible path to the CA certificate:clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"Copy to Clipboard Copied! Toggle word wrap Toggle overflow TipAfter you run the installer with a custom CA certificate, you can update the certificate by editing the value of the
ca-cert.pemkey in thecloud-provider-configkeymap. On a command line, run:oc edit configmap -n openshift-config cloud-provider-config
$ oc edit configmap -n openshift-config cloud-provider-configCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Place the
clouds.yamlfile in one of the following locations:-
The value of the
OS_CLIENT_CONFIG_FILEenvironment variable - The current directory
-
A Unix-specific user configuration directory, for example
~/.config/openstack/clouds.yaml A Unix-specific site configuration directory, for example
/etc/openstack/clouds.yamlThe installation program searches for
clouds.yamlin that order.
-
The value of the
9.1.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
9.1.8. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Red Hat OpenStack Platform (RHOSP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select openstack as the platform to target.
- Specify the Red Hat OpenStack Platform (RHOSP) external network name to use for installing the cluster.
- Specify the floating IP address to use for external access to the OpenShift API.
- Specify a RHOSP flavor with at least 16 GB RAM to use for control plane nodes and 8 GB RAM for compute nodes.
- Select the base domain to deploy the cluster to. All DNS records will be sub-domains of this base and will also include the cluster name.
- Enter a name for your cluster. The name must be 14 or fewer characters long.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
9.1.8.1. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
9.1.9. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
9.1.9.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
9.1.9.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
9.1.9.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
9.1.9.4. Additional Red Hat OpenStack Platform (RHOSP) configuration parameters
Additional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| For compute machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For compute machines, the root volume’s type. |
String, for example |
|
| For control plane machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For control plane machines, the root volume’s type. |
String, for example |
|
|
The name of the RHOSP cloud to use from the list of clouds in the |
String, for example |
|
| The RHOSP external network name to be used for installation. |
String, for example |
|
| The RHOSP flavor to use for control plane and compute machines. |
String, for example |
9.1.9.5. Optional RHOSP configuration parameters
Optional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Additional networks that are associated with compute machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with compute machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| Additional networks that are associated with control plane machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with control plane machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. | An HTTP or HTTPS URL, optionally with an SHA-256 checksum.
For example, |
|
| The default machine pool platform configuration. |
|
|
|
An existing floating IP address to associate with the Ingress port. To use this property, you must also define the |
An IP address, for example |
|
|
An existing floating IP address to associate with the API load balancer. To use this property, you must also define the |
An IP address, for example |
|
| IP addresses for external DNS servers that cluster instances use for DNS resolution. |
A list of IP addresses as strings. For example, |
|
| The UUID of a RHOSP subnet that the cluster’s nodes use. Nodes and virtual IP (VIP) ports are created on this subnet.
The first item in If you deploy to a custom subnet, you cannot specify an external DNS server to the OpenShift Container Platform installer. Instead, add DNS to the subnet in RHOSP. |
A UUID as a string. For example, |
9.1.9.6. Custom subnets in RHOSP deployments
Optionally, you can deploy a cluster on a Red Hat OpenStack Platform (RHOSP) subnet of your choice. The subnet’s GUID is passed as the value of platform.openstack.machinesSubnet in the install-config.yaml file.
This subnet is used as the cluster’s primary subnet; nodes and ports are created on it.
Before you run the OpenShift Container Platform installer with a custom subnet, verify that:
- The target network and subnet are available.
- DHCP is enabled on the target subnet.
- You can provide installer credentials that have permission to create ports on the target network.
- If your network configuration requires a router, it is created in RHOSP. Some configurations rely on routers for floating IP address translation.
- Your network configuration does not rely on a provider network. Provider networks are not supported.
By default, the API VIP takes x.x.x.5 and the Ingress VIP takes x.x.x.7 from your network’s CIDR block. To override these default values, set values for platform.openstack.apiVIP and platform.openstack.ingressVIP that are outside of the DHCP allocation pool.
9.1.9.7. Sample customized install-config.yaml file for RHOSP
This sample install-config.yaml demonstrates all of the possible Red Hat OpenStack Platform (RHOSP) customization options.
This sample file is provided for reference only. You must obtain your install-config.yaml file by using the installation program.
9.1.10. Setting compute machine affinity
Optionally, you can set the affinity policy for compute machines during installation. The installer does not select an affinity policy for compute machines by default.
You can also create machine sets that use particular RHOSP server groups after installation.
Control plane machines are created with a soft-anti-affinity policy.
You can learn more about RHOSP instance scheduling and placement in the RHOSP documentation.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Using the RHOSP command-line interface, create a server group for your compute machines. For example:
openstack \ --os-compute-api-version=2.15 \ server group create \ --policy anti-affinity \ my-openshift-worker-group$ openstack \ --os-compute-api-version=2.15 \ server group create \ --policy anti-affinity \ my-openshift-worker-groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information, see the
server group createcommand documentation.Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir=<installation_directory>
$ ./openshift-install create manifests --dir=<installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
installation_directory-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
-
Open
manifests/99_openshift-cluster-api_worker-machineset-0.yaml, theMachineSetdefinition file. Add the property
serverGroupIDto the definition beneath thespec.template.spec.providerSpec.valueproperty. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Add the UUID of your server group here.
-
Optional: Back up the
manifests/99_openshift-cluster-api_worker-machineset-0.yamlfile. The installation program deletes themanifests/directory when creating the cluster.
When you install the cluster, the installer uses the MachineSet definition that you modified to create compute machines within your RHOSP server group.
9.1.11. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
9.1.12. Enabling access to the environment
At deployment, all OpenShift Container Platform machines are created in a Red Hat OpenStack Platform (RHOSP)-tenant network. Therefore, they are not accessible directly in most RHOSP deployments.
You can configure OpenShift Container Platform API and application access by using floating IP addresses (FIPs) during installation. You can also complete an installation without configuring FIPs, but the installer will not configure a way to reach the API or applications externally.
9.1.12.1. Enabling access with floating IP addresses
Create floating IP (FIP) addresses for external access to the OpenShift Container Platform API and cluster applications.
Procedure
Using the Red Hat OpenStack Platform (RHOSP) CLI, create the API FIP:
openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the Red Hat OpenStack Platform (RHOSP) CLI, create the apps, or Ingress, FIP:
openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add records that follow these patterns to your DNS server for the API and Ingress FIPs:
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you do not control the DNS server, you can access the cluster by adding the cluster domain names such as the following to your
/etc/hostsfile:-
<api_floating_ip> api.<cluster_name>.<base_domain> -
<application_floating_ip> grafana-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> prometheus-k8s-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> oauth-openshift.apps.<cluster_name>.<base_domain> -
<application_floating_ip> console-openshift-console.apps.<cluster_name>.<base_domain> -
application_floating_ip integrated-oauth-server-openshift-authentication.apps.<cluster_name>.<base_domain>
The cluster domain names in the
/etc/hostsfile grant access to the web console and the monitoring interface of your cluster locally. You can also use thekubectloroc. You can access the user applications by using the additional entries pointing to the <application_floating_ip>. This action makes the API and applications accessible to only you, which is not suitable for production deployment, but does allow installation for development and testing.-
Add the FIPs to the
install-config.yamlfile as the values of the following parameters:-
platform.openstack.ingressFloatingIP -
platform.openstack.lbFloatingIP
-
If you use these values, you must also enter an external network as the value of the platform.openstack.externalNetwork parameter in the install-config.yaml file.
You can make OpenShift Container Platform resources available outside of the cluster by assigning a floating IP address and updating your firewall configuration.
9.1.12.2. Completing installation without floating IP addresses
You can install OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) without providing floating IP addresses.
In the install-config.yaml file, do not define the following parameters:
-
platform.openstack.ingressFloatingIP -
platform.openstack.lbFloatingIP
If you cannot provide an external network, you can also leave platform.openstack.externalNetwork blank. If you do not provide a value for platform.openstack.externalNetwork, a router is not created for you, and, without additional action, the installer will fail to retrieve an image from Glance. You must configure external connectivity on your own.
If you run the installer from a system that cannot reach the cluster API due to a lack of floating IP addresses or name resolution, installation fails. To prevent installation failure in these cases, you can use a proxy network or run the installer from a system that is on the same network as your machines.
You can enable name resolution by creating DNS records for the API and Ingress ports. For example:
api.<cluster_name>.<base_domain>. IN A <api_port_IP> *.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
api.<cluster_name>.<base_domain>. IN A <api_port_IP>
*.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
If you do not control the DNS server, you can add the record to your /etc/hosts file. This action makes the API accessible to only you, which is not suitable for production deployment but does allow installation for development and testing.
9.1.13. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
9.1.14. Verifying cluster status
You can verify your OpenShift Container Platform cluster’s status during or after installation.
Procedure
In the cluster environment, export the administrator’s kubeconfig file:
export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
The
kubeconfigfile contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server.View the control plane and compute machines created after a deployment:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your cluster’s version:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your Operators' status:
oc get clusteroperator
$ oc get clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow View all running pods in the cluster:
oc get pods -A
$ oc get pods -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.1.15. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.1.16. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
9.1.17. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If you need to enable external access to node ports, configure ingress cluster traffic by using a node port.
- If you did not configure RHOSP to accept application traffic over floating IP addresses, configure RHOSP access with floating IP addresses.
9.2. Installing a cluster on OpenStack with Kuryr
In OpenShift Container Platform version 4.6, you can install a customized cluster on Red Hat OpenStack Platform (RHOSP) that uses Kuryr SDN. To customize the installation, modify parameters in the install-config.yaml before you install the cluster.
9.2.1. Prerequisites
Review details about the OpenShift Container Platform installation and update processes.
- Verify that OpenShift Container Platform 4.6 is compatible with your RHOSP version in the Available platforms section. You can also compare platform support across different versions by viewing the OpenShift Container Platform on RHOSP support matrix.
- Verify that your network configuration does not rely on a provider network. Provider networks are not supported.
- Have a storage service installed in RHOSP, like block storage (Cinder) or object storage (Swift). Object storage is the recommended storage technology for OpenShift Container Platform registry cluster deployment. For more information, see Optimizing storage.
9.2.2. About Kuryr SDN
Kuryr is a container network interface (CNI) plug-in solution that uses the Neutron and Octavia Red Hat OpenStack Platform (RHOSP) services to provide networking for pods and Services.
Kuryr and OpenShift Container Platform integration is primarily designed for OpenShift Container Platform clusters running on RHOSP VMs. Kuryr improves the network performance by plugging OpenShift Container Platform pods into RHOSP SDN. In addition, it provides interconnectivity between pods and RHOSP virtual instances.
Kuryr components are installed as pods in OpenShift Container Platform using the openshift-kuryr namespace:
-
kuryr-controller- a single service instance installed on amasternode. This is modeled in OpenShift Container Platform as aDeploymentobject. -
kuryr-cni- a container installing and configuring Kuryr as a CNI driver on each OpenShift Container Platform node. This is modeled in OpenShift Container Platform as aDaemonSetobject.
The Kuryr controller watches the OpenShift Container Platform API server for pod, service, and namespace create, update, and delete events. It maps the OpenShift Container Platform API calls to corresponding objects in Neutron and Octavia. This means that every network solution that implements the Neutron trunk port functionality can be used to back OpenShift Container Platform via Kuryr. This includes open source solutions such as Open vSwitch (OVS) and Open Virtual Network (OVN) as well as Neutron-compatible commercial SDNs.
Kuryr is recommended for OpenShift Container Platform deployments on encapsulated RHOSP tenant networks to avoid double encapsulation, such as running an encapsulated OpenShift Container Platform SDN over an RHOSP network.
If you use provider networks or tenant VLANs, you do not need to use Kuryr to avoid double encapsulation. The performance benefit is negligible. Depending on your configuration, though, using Kuryr to avoid having two overlays might still be beneficial.
Kuryr is not recommended in deployments where all of the following criteria are true:
- The RHOSP version is less than 16.
- The deployment uses UDP services, or a large number of TCP services on few hypervisors.
or
-
The
ovn-octaviaOctavia driver is disabled. - The deployment uses a large number of TCP services on few hypervisors.
9.2.3. Resource guidelines for installing OpenShift Container Platform on RHOSP with Kuryr
When using Kuryr SDN, the pods, services, namespaces, and network policies are using resources from the RHOSP quota; this increases the minimum requirements. Kuryr also has some additional requirements on top of what a default install requires.
Use the following quota to satisfy a default cluster’s minimum requirements:
| Resource | Value |
|---|---|
| Floating IP addresses | 3 - plus the expected number of Services of LoadBalancer type |
| Ports | 1500 - 1 needed per Pod |
| Routers | 1 |
| Subnets | 250 - 1 needed per Namespace/Project |
| Networks | 250 - 1 needed per Namespace/Project |
| RAM | 112 GB |
| vCPUs | 28 |
| Volume storage | 275 GB |
| Instances | 7 |
| Security groups | 250 - 1 needed per Service and per NetworkPolicy |
| Security group rules | 1000 |
| Load balancers | 100 - 1 needed per Service |
| Load balancer listeners | 500 - 1 needed per Service-exposed port |
| Load balancer pools | 500 - 1 needed per Service-exposed port |
A cluster might function with fewer than recommended resources, but its performance is not guaranteed.
If RHOSP object storage (Swift) is available and operated by a user account with the swiftoperator role, it is used as the default backend for the OpenShift Container Platform image registry. In this case, the volume storage requirement is 175 GB. Swift space requirements vary depending on the size of the image registry.
If you are using Red Hat OpenStack Platform (RHOSP) version 16 with the Amphora driver rather than the OVN Octavia driver, security groups are associated with service accounts instead of user projects.
Take the following notes into consideration when setting resources:
- The number of ports that are required is larger than the number of pods. Kuryr uses ports pools to have pre-created ports ready to be used by pods and speed up the pods' booting time.
-
Each network policy is mapped into an RHOSP security group, and depending on the
NetworkPolicyspec, one or more rules are added to the security group. Each service is mapped to an RHOSP load balancer. Consider this requirement when estimating the number of security groups required for the quota.
If you are using RHOSP version 15 or earlier, or the
ovn-octavia driver, each load balancer has a security group with the user project.The quota does not account for load balancer resources (such as VM resources), but you must consider these resources when you decide the RHOSP deployment’s size. The default installation will have more than 50 load balancers; the clusters must be able to accommodate them.
If you are using RHOSP version 16 with the OVN Octavia driver enabled, only one load balancer VM is generated; services are load balanced through OVN flows.
An OpenShift Container Platform deployment comprises control plane machines, compute machines, and a bootstrap machine.
To enable Kuryr SDN, your environment must meet the following requirements:
- Run RHOSP 13+.
- Have Overcloud with Octavia.
- Use Neutron Trunk ports extension.
-
Use
openvswitchfirewall driver if ML2/OVS Neutron driver is used instead ofovs-hybrid.
9.2.3.1. Increasing quota
When using Kuryr SDN, you must increase quotas to satisfy the Red Hat OpenStack Platform (RHOSP) resources used by pods, services, namespaces, and network policies.
Procedure
Increase the quotas for a project by running the following command:
sudo openstack quota set --secgroups 250 --secgroup-rules 1000 --ports 1500 --subnets 250 --networks 250 <project>
$ sudo openstack quota set --secgroups 250 --secgroup-rules 1000 --ports 1500 --subnets 250 --networks 250 <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2.3.2. Configuring Neutron
Kuryr CNI leverages the Neutron Trunks extension to plug containers into the Red Hat OpenStack Platform (RHOSP) SDN, so you must use the trunks extension for Kuryr to properly work.
In addition, if you leverage the default ML2/OVS Neutron driver, the firewall must be set to openvswitch instead of ovs_hybrid so that security groups are enforced on trunk subports and Kuryr can properly handle network policies.
9.2.3.3. Configuring Octavia
Kuryr SDN uses Red Hat OpenStack Platform (RHOSP)'s Octavia LBaaS to implement OpenShift Container Platform services. Thus, you must install and configure Octavia components in RHOSP to use Kuryr SDN.
To enable Octavia, you must include the Octavia service during the installation of the RHOSP Overcloud, or upgrade the Octavia service if the Overcloud already exists. The following steps for enabling Octavia apply to both a clean install of the Overcloud or an Overcloud update.
The following steps only capture the key pieces required during the deployment of RHOSP when dealing with Octavia. It is also important to note that registry methods vary.
This example uses the local registry method.
Procedure
If you are using the local registry, create a template to upload the images to the registry. For example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the
local_registry_images.yamlfile contains the Octavia images. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe Octavia container versions vary depending upon the specific RHOSP release installed.
Pull the container images from
registry.redhat.ioto the Undercloud node:(undercloud) $ sudo openstack overcloud container image upload \ --config-file /home/stack/local_registry_images.yaml \ --verbose
(undercloud) $ sudo openstack overcloud container image upload \ --config-file /home/stack/local_registry_images.yaml \ --verboseCopy to Clipboard Copied! Toggle word wrap Toggle overflow This may take some time depending on the speed of your network and Undercloud disk.
Since an Octavia load balancer is used to access the OpenShift Container Platform API, you must increase their listeners' default timeouts for the connections. The default timeout is 50 seconds. Increase the timeout to 20 minutes by passing the following file to the Overcloud deploy command:
(undercloud) $ cat octavia_timeouts.yaml parameter_defaults: OctaviaTimeoutClientData: 1200000 OctaviaTimeoutMemberData: 1200000
(undercloud) $ cat octavia_timeouts.yaml parameter_defaults: OctaviaTimeoutClientData: 1200000 OctaviaTimeoutMemberData: 1200000Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThis is not needed for RHOSP 13.0.13+.
Install or update your Overcloud environment with Octavia:
openstack overcloud deploy --templates \ -e /usr/share/openstack-tripleo-heat-templates/environments/services-docker/octavia.yaml \ -e octavia_timeouts.yaml
$ openstack overcloud deploy --templates \ -e /usr/share/openstack-tripleo-heat-templates/environments/services-docker/octavia.yaml \ -e octavia_timeouts.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThis command only includes the files associated with Octavia; it varies based on your specific installation of RHOSP. See the RHOSP documentation for further information. For more information on customizing your Octavia installation, see installation of Octavia using Director.
NoteWhen leveraging Kuryr SDN, the Overcloud installation requires the Neutron
trunkextension. This is available by default on director deployments. Use theopenvswitchfirewall instead of the defaultovs-hybridwhen the Neutron backend is ML2/OVS. There is no need for modifications if the backend is ML2/OVN.In RHOSP versions earlier than 13.0.13, add the project ID to the
octavia.confconfiguration file after you create the project.To enforce network policies across services, like when traffic goes through the Octavia load balancer, you must ensure Octavia creates the Amphora VM security groups on the user project.
This change ensures that required load balancer security groups belong to that project, and that they can be updated to enforce services isolation.
NoteThis task is unnecessary in RHOSP version 13.0.13 or later.
Octavia implements a new ACL API that restricts access to the load balancers VIP.
Get the project ID
openstack project show <project>
$ openstack project show <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the project ID to
octavia.conffor the controllers.Source the
stackrcfile:source stackrc # Undercloud credentials
$ source stackrc # Undercloud credentialsCopy to Clipboard Copied! Toggle word wrap Toggle overflow List the Overcloud controllers:
openstack server list
$ openstack server listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow SSH into the controller(s).
ssh heat-admin@192.168.24.8
$ ssh heat-admin@192.168.24.8Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
octavia.conffile to add the project into the list of projects where Amphora security groups are on the user’s account.List of project IDs that are allowed to have Load balancer security groups belonging to them.
# List of project IDs that are allowed to have Load balancer security groups # belonging to them. amp_secgroup_allowed_projects = PROJECT_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Restart the Octavia worker so the new configuration loads.
controller-0$ sudo docker restart octavia_worker
controller-0$ sudo docker restart octavia_workerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Depending on your RHOSP environment, Octavia might not support UDP listeners. If you use Kuryr SDN on RHOSP version 13.0.13 or earlier, UDP services are not supported. RHOSP version 16 or later support UDP.
9.2.3.3.1. The Octavia OVN Driver
Octavia supports multiple provider drivers through the Octavia API.
To see all available Octavia provider drivers, on a command line, enter:
openstack loadbalancer provider list
$ openstack loadbalancer provider listExample output
Beginning with RHOSP version 16, the Octavia OVN provider driver (ovn) is supported on OpenShift Container Platform on RHOSP deployments.
ovn is an integration driver for the load balancing that Octavia and OVN provide. It supports basic load balancing capabilities, and is based on OpenFlow rules. The driver is automatically enabled in Octavia by Director on deployments that use OVN Neutron ML2.
The Amphora provider driver is the default driver. If ovn is enabled, however, Kuryr uses it.
If Kuryr uses ovn instead of Amphora, it offers the following benefits:
- Decreased resource requirements. Kuryr does not require a load balancer VM for each service.
- Reduced network latency.
- Increased service creation speed by using OpenFlow rules instead of a VM for each service.
- Distributed load balancing actions across all nodes instead of centralized on Amphora VMs.
You can configure your cluster to use the Octavia OVN driver after your RHOSP cloud is upgraded from version 13 to version 16.
9.2.3.4. Known limitations of installing with Kuryr
Using OpenShift Container Platform with Kuryr SDN has several known limitations.
RHOSP general limitations
OpenShift Container Platform with Kuryr SDN does not support Service objects with type NodePort.
If the machines subnet is not connected to a router, or if the subnet is connected, but the router has no external gateway set, Kuryr cannot create floating IPs for Service objects with type LoadBalancer.
-
Configuring the
sessionAffinity=ClientIPproperty onServiceobjects does not have an effect. Kuryr does not support this setting.
RHOSP version limitations
Using OpenShift Container Platform with Kuryr SDN has several limitations that depend on the RHOSP version.
RHOSP versions before 16 use the default Octavia load balancer driver (Amphora). This driver requires that one Amphora load balancer VM is deployed per OpenShift Container Platform service. Creating too many services can cause you to run out of resources.
Deployments of later versions of RHOSP that have the OVN Octavia driver disabled also use the Amphora driver. They are subject to the same resource concerns as earlier versions of RHOSP.
- Octavia RHOSP versions before 13.0.13 do not support UDP listeners. Therefore, OpenShift Container Platform UDP services are not supported.
- Octavia RHOSP versions before 13.0.13 cannot listen to multiple protocols on the same port. Services that expose the same port to different protocols, like TCP and UDP, are not supported.
- Kuryr SDN does not support automatic unidling by a service.
RHOSP environment limitations
There are limitations when using Kuryr SDN that depend on your deployment environment.
Because of Octavia’s lack of support for the UDP protocol and multiple listeners, if the RHOSP version is earlier than 13.0.13, Kuryr forces pods to use TCP for DNS resolution.
In Go versions 1.12 and earlier, applications that are compiled with CGO support disabled use UDP only. In this case, the native Go resolver does not recognize the use-vc option in resolv.conf, which controls whether TCP is forced for DNS resolution. As a result, UDP is still used for DNS resolution, which fails.
To ensure that TCP forcing is allowed, compile applications either with the environment variable CGO_ENABLED set to 1, i.e. CGO_ENABLED=1, or ensure that the variable is absent.
In Go versions 1.13 and later, TCP is used automatically if DNS resolution using UDP fails.
musl-based containers, including Alpine-based containers, do not support the use-vc option.
RHOSP upgrade limitations
As a result of the RHOSP upgrade process, the Octavia API might be changed, and upgrades to the Amphora images that are used for load balancers might be required.
You can address API changes on an individual basis.
If the Amphora image is upgraded, the RHOSP operator can handle existing load balancer VMs in two ways:
- Upgrade each VM by triggering a load balancer failover.
- Leave responsibility for upgrading the VMs to users.
If the operator takes the first option, there might be short downtimes during failovers.
If the operator takes the second option, the existing load balancers will not support upgraded Octavia API features, like UDP listeners. In this case, users must recreate their Services to use these features.
If OpenShift Container Platform detects a new Octavia version that supports UDP load balancing, it recreates the DNS service automatically. The service recreation ensures that the service default supports UDP load balancing.
The recreation causes the DNS service approximately one minute of downtime.
9.2.3.5. Control plane machines
By default, the OpenShift Container Platform installation process creates three control plane machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.2.3.6. Compute machines
By default, the OpenShift Container Platform installation process creates three compute machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 8 GB memory, 2 vCPUs, and 100 GB storage space
Compute machines host the applications that you run on OpenShift Container Platform; aim to run as many as you can.
9.2.3.7. Bootstrap machine
During installation, a bootstrap machine is temporarily provisioned to stand up the control plane. After the production control plane is ready, the bootstrap machine is deprovisioned.
The bootstrap machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.2.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
9.2.5. Enabling Swift on RHOSP
Swift is operated by a user account with the swiftoperator role. Add the role to an account before you run the installation program.
If the Red Hat OpenStack Platform (RHOSP) object storage service, commonly known as Swift, is available, OpenShift Container Platform uses it as the image registry storage. If it is unavailable, the installation program relies on the RHOSP block storage service, commonly known as Cinder.
If Swift is present and you want to use it, you must enable access to it. If it is not present, or if you do not want to use it, skip this section.
Prerequisites
- You have a RHOSP administrator account on the target environment.
- The Swift service is installed.
-
On Ceph RGW, the
account in urloption is enabled.
Procedure
To enable Swift on RHOSP:
As an administrator in the RHOSP CLI, add the
swiftoperatorrole to the account that will access Swift:openstack role add --user <user> --project <project> swiftoperator
$ openstack role add --user <user> --project <project> swiftoperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Your RHOSP deployment can now use Swift for the image registry.
9.2.6. Verifying external network access
The OpenShift Container Platform installation process requires external network access. You must provide an external network value to it, or deployment fails. Before you begin the process, verify that a network with the external router type exists in Red Hat OpenStack Platform (RHOSP).
Prerequisites
Procedure
Using the RHOSP CLI, verify the name and ID of the 'External' network:
openstack network list --long -c ID -c Name -c "Router Type"
$ openstack network list --long -c ID -c Name -c "Router Type"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+Copy to Clipboard Copied! Toggle word wrap Toggle overflow
A network with an external router type appears in the network list. If at least one does not, see Creating a default floating IP network and Creating a default provider network.
If the external network’s CIDR range overlaps one of the default network ranges, you must change the matching network ranges in the install-config.yaml file before you start the installation process.
The default network ranges are:
| Network | Range |
|---|---|
|
| 10.0.0.0/16 |
|
| 172.30.0.0/16 |
|
| 10.128.0.0/14 |
If the installation program finds multiple networks with the same name, it sets one of them at random. To avoid this behavior, create unique names for resources in RHOSP.
If the Neutron trunk service plug-in is enabled, a trunk port is created by default. For more information, see Neutron trunk port.
9.2.7. Defining parameters for the installation program
The OpenShift Container Platform installation program relies on a file that is called clouds.yaml. The file describes Red Hat OpenStack Platform (RHOSP) configuration parameters, including the project name, log in information, and authorization service URLs.
Procedure
Create the
clouds.yamlfile:If your RHOSP distribution includes the Horizon web UI, generate a
clouds.yamlfile in it.ImportantRemember to add a password to the
authfield. You can also keep secrets in a separate file fromclouds.yaml.If your RHOSP distribution does not include the Horizon web UI, or you do not want to use Horizon, create the file yourself. For detailed information about
clouds.yaml, see Config files in the RHOSP documentation.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If your RHOSP installation uses self-signed certificate authority (CA) certificates for endpoint authentication:
- Copy the certificate authority file to your machine.
Add the machine to the certificate authority trust bundle:
sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/
$ sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the trust bundle:
sudo update-ca-trust extract
$ sudo update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
cacertskey to theclouds.yamlfile. The value must be an absolute, non-root-accessible path to the CA certificate:clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"Copy to Clipboard Copied! Toggle word wrap Toggle overflow TipAfter you run the installer with a custom CA certificate, you can update the certificate by editing the value of the
ca-cert.pemkey in thecloud-provider-configkeymap. On a command line, run:oc edit configmap -n openshift-config cloud-provider-config
$ oc edit configmap -n openshift-config cloud-provider-configCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Place the
clouds.yamlfile in one of the following locations:-
The value of the
OS_CLIENT_CONFIG_FILEenvironment variable - The current directory
-
A Unix-specific user configuration directory, for example
~/.config/openstack/clouds.yaml A Unix-specific site configuration directory, for example
/etc/openstack/clouds.yamlThe installation program searches for
clouds.yamlin that order.
-
The value of the
9.2.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
9.2.9. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Red Hat OpenStack Platform (RHOSP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select openstack as the platform to target.
- Specify the Red Hat OpenStack Platform (RHOSP) external network name to use for installing the cluster.
- Specify the floating IP address to use for external access to the OpenShift API.
- Specify a RHOSP flavor with at least 16 GB RAM to use for control plane nodes and 8 GB RAM for compute nodes.
- Select the base domain to deploy the cluster to. All DNS records will be sub-domains of this base and will also include the cluster name.
- Enter a name for your cluster. The name must be 14 or fewer characters long.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
9.2.9.1. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
9.2.10. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
9.2.10.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
9.2.10.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
9.2.10.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
9.2.10.4. Additional Red Hat OpenStack Platform (RHOSP) configuration parameters
Additional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| For compute machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For compute machines, the root volume’s type. |
String, for example |
|
| For control plane machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For control plane machines, the root volume’s type. |
String, for example |
|
|
The name of the RHOSP cloud to use from the list of clouds in the |
String, for example |
|
| The RHOSP external network name to be used for installation. |
String, for example |
|
| The RHOSP flavor to use for control plane and compute machines. |
String, for example |
9.2.10.5. Optional RHOSP configuration parameters
Optional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Additional networks that are associated with compute machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with compute machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| Additional networks that are associated with control plane machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with control plane machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. | An HTTP or HTTPS URL, optionally with an SHA-256 checksum.
For example, |
|
| The default machine pool platform configuration. |
|
|
|
An existing floating IP address to associate with the Ingress port. To use this property, you must also define the |
An IP address, for example |
|
|
An existing floating IP address to associate with the API load balancer. To use this property, you must also define the |
An IP address, for example |
|
| IP addresses for external DNS servers that cluster instances use for DNS resolution. |
A list of IP addresses as strings. For example, |
|
| The UUID of a RHOSP subnet that the cluster’s nodes use. Nodes and virtual IP (VIP) ports are created on this subnet.
The first item in If you deploy to a custom subnet, you cannot specify an external DNS server to the OpenShift Container Platform installer. Instead, add DNS to the subnet in RHOSP. |
A UUID as a string. For example, |
9.2.10.6. Custom subnets in RHOSP deployments
Optionally, you can deploy a cluster on a Red Hat OpenStack Platform (RHOSP) subnet of your choice. The subnet’s GUID is passed as the value of platform.openstack.machinesSubnet in the install-config.yaml file.
This subnet is used as the cluster’s primary subnet; nodes and ports are created on it.
Before you run the OpenShift Container Platform installer with a custom subnet, verify that:
- The target network and subnet are available.
- DHCP is enabled on the target subnet.
- You can provide installer credentials that have permission to create ports on the target network.
- If your network configuration requires a router, it is created in RHOSP. Some configurations rely on routers for floating IP address translation.
- Your network configuration does not rely on a provider network. Provider networks are not supported.
By default, the API VIP takes x.x.x.5 and the Ingress VIP takes x.x.x.7 from your network’s CIDR block. To override these default values, set values for platform.openstack.apiVIP and platform.openstack.ingressVIP that are outside of the DHCP allocation pool.
9.2.10.7. Sample customized install-config.yaml file for RHOSP with Kuryr
To deploy with Kuryr SDN instead of the default OpenShift SDN, you must modify the install-config.yaml file to include Kuryr as the desired networking.networkType and proceed with the default OpenShift Container Platform SDN installation steps. This sample install-config.yaml demonstrates all of the possible Red Hat OpenStack Platform (RHOSP) customization options.
This sample file is provided for reference only. You must obtain your install-config.yaml file by using the installation program.
- 1
- The Amphora Octavia driver creates two ports per load balancer. As a result, the service subnet that the installer creates is twice the size of the CIDR that is specified as the value of the
serviceNetworkproperty. The larger range is required to prevent IP address conflicts. - 2 3
- Both
trunkSupportandoctaviaSupportare automatically discovered by the installer, so there is no need to set them. But if your environment does not meet both requirements, Kuryr SDN will not properly work. Trunks are needed to connect the pods to the RHOSP network and Octavia is required to create the OpenShift Container Platform services.
9.2.10.8. Kuryr ports pools
A Kuryr ports pool maintains a number of ports on standby for pod creation.
Keeping ports on standby minimizes pod creation time. Without ports pools, Kuryr must explicitly request port creation or deletion whenever a pod is created or deleted.
The Neutron ports that Kuryr uses are created in subnets that are tied to namespaces. These pod ports are also added as subports to the primary port of OpenShift Container Platform cluster nodes.
Because Kuryr keeps each namespace in a separate subnet, a separate ports pool is maintained for each namespace-worker pair.
Prior to installing a cluster, you can set the following parameters in the cluster-network-03-config.yml manifest file to configure ports pool behavior:
-
The
enablePortPoolsPrepopulationparameter controls pool prepopulation, which forces Kuryr to add ports to the pool when it is created, such as when a new host is added, or a new namespace is created. The default value isfalse. -
The
poolMinPortsparameter is the minimum number of free ports that are kept in the pool. The default value is1. The
poolMaxPortsparameter is the maximum number of free ports that are kept in the pool. A value of0disables that upper bound. This is the default setting.If your OpenStack port quota is low, or you have a limited number of IP addresses on the pod network, consider setting this option to ensure that unneeded ports are deleted.
-
The
poolBatchPortsparameter defines the maximum number of Neutron ports that can be created at once. The default value is3.
9.2.10.9. Adjusting Kuryr ports pools during installation
During installation, you can configure how Kuryr manages Red Hat OpenStack Platform (RHOSP) Neutron ports to control the speed and efficiency of pod creation.
Prerequisites
-
Create and modify the
install-config.yamlfile.
Procedure
From a command line, create the manifest files:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the name of the directory that contains theinstall-config.yamlfile for your cluster.
Create a file that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:touch <installation_directory>/manifests/cluster-network-03-config.yml
$ touch <installation_directory>/manifests/cluster-network-03-config.yml1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name that contains themanifests/directory for your cluster.
After creating the file, several network configuration files are in the
manifests/directory, as shown:ls <installation_directory>/manifests/cluster-network-*
$ ls <installation_directory>/manifests/cluster-network-*Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
cluster-network-01-crd.yml cluster-network-02-config.yml cluster-network-03-config.yml
cluster-network-01-crd.yml cluster-network-02-config.yml cluster-network-03-config.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the
cluster-network-03-config.ymlfile in an editor, and enter a custom resource (CR) that describes the Cluster Network Operator configuration that you want:oc edit networks.operator.openshift.io cluster
$ oc edit networks.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the settings to meet your requirements. The following file is provided as an example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Set the value of
enablePortPoolsPrepopulationtotrueto make Kuryr create new Neutron ports after a namespace is created or a new node is added to the cluster. This setting raises the Neutron ports quota but can reduce the time that is required to spawn pods. The default value isfalse. - 2
- Kuryr creates new ports for a pool if the number of free ports in that pool is lower than the value of
poolMinPorts. The default value is1. - 3
poolBatchPortscontrols the number of new ports that are created if the number of free ports is lower than the value ofpoolMinPorts. The default value is3.- 4
- If the number of free ports in a pool is higher than the value of
poolMaxPorts, Kuryr deletes them until the number matches that value. Setting this value to0disables this upper bound, preventing pools from shrinking. The default value is0. - 5
- The
openStackServiceNetworkparameter defines the CIDR range of the network from which IP addresses are allocated to RHOSP Octavia’s LoadBalancers.
If this parameter is used with the Amphora driver, Octavia takes two IP addresses from this network for each load balancer: one for OpenShift and the other for VRRP connections. Because these IP addresses are managed by OpenShift Container Platform and Neutron respectively, they must come from different pools. Therefore, the value of
openStackServiceNetworkmust be at least twice the size of the value ofserviceNetwork, and the value ofserviceNetworkmust overlap entirely with the range that is defined byopenStackServiceNetwork.The CNO verifies that VRRP IP addresses that are taken from the range that is defined by this parameter do not overlap with the range that is defined by the
serviceNetworkparameter.If this parameter is not set, the CNO uses an expanded value of
serviceNetworkthat is determined by decrementing the prefix size by 1.-
Save the
cluster-network-03-config.ymlfile, and exit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory while creating the cluster.
9.2.11. Setting compute machine affinity
Optionally, you can set the affinity policy for compute machines during installation. The installer does not select an affinity policy for compute machines by default.
You can also create machine sets that use particular RHOSP server groups after installation.
Control plane machines are created with a soft-anti-affinity policy.
You can learn more about RHOSP instance scheduling and placement in the RHOSP documentation.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Using the RHOSP command-line interface, create a server group for your compute machines. For example:
openstack \ --os-compute-api-version=2.15 \ server group create \ --policy anti-affinity \ my-openshift-worker-group$ openstack \ --os-compute-api-version=2.15 \ server group create \ --policy anti-affinity \ my-openshift-worker-groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information, see the
server group createcommand documentation.Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir=<installation_directory>
$ ./openshift-install create manifests --dir=<installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
installation_directory-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
-
Open
manifests/99_openshift-cluster-api_worker-machineset-0.yaml, theMachineSetdefinition file. Add the property
serverGroupIDto the definition beneath thespec.template.spec.providerSpec.valueproperty. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Add the UUID of your server group here.
-
Optional: Back up the
manifests/99_openshift-cluster-api_worker-machineset-0.yamlfile. The installation program deletes themanifests/directory when creating the cluster.
When you install the cluster, the installer uses the MachineSet definition that you modified to create compute machines within your RHOSP server group.
9.2.12. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
9.2.13. Enabling access to the environment
At deployment, all OpenShift Container Platform machines are created in a Red Hat OpenStack Platform (RHOSP)-tenant network. Therefore, they are not accessible directly in most RHOSP deployments.
You can configure OpenShift Container Platform API and application access by using floating IP addresses (FIPs) during installation. You can also complete an installation without configuring FIPs, but the installer will not configure a way to reach the API or applications externally.
9.2.13.1. Enabling access with floating IP addresses
Create floating IP (FIP) addresses for external access to the OpenShift Container Platform API and cluster applications.
Procedure
Using the Red Hat OpenStack Platform (RHOSP) CLI, create the API FIP:
openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the Red Hat OpenStack Platform (RHOSP) CLI, create the apps, or Ingress, FIP:
openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add records that follow these patterns to your DNS server for the API and Ingress FIPs:
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you do not control the DNS server, you can access the cluster by adding the cluster domain names such as the following to your
/etc/hostsfile:-
<api_floating_ip> api.<cluster_name>.<base_domain> -
<application_floating_ip> grafana-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> prometheus-k8s-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> oauth-openshift.apps.<cluster_name>.<base_domain> -
<application_floating_ip> console-openshift-console.apps.<cluster_name>.<base_domain> -
application_floating_ip integrated-oauth-server-openshift-authentication.apps.<cluster_name>.<base_domain>
The cluster domain names in the
/etc/hostsfile grant access to the web console and the monitoring interface of your cluster locally. You can also use thekubectloroc. You can access the user applications by using the additional entries pointing to the <application_floating_ip>. This action makes the API and applications accessible to only you, which is not suitable for production deployment, but does allow installation for development and testing.-
Add the FIPs to the
install-config.yamlfile as the values of the following parameters:-
platform.openstack.ingressFloatingIP -
platform.openstack.lbFloatingIP
-
If you use these values, you must also enter an external network as the value of the platform.openstack.externalNetwork parameter in the install-config.yaml file.
You can make OpenShift Container Platform resources available outside of the cluster by assigning a floating IP address and updating your firewall configuration.
9.2.13.2. Completing installation without floating IP addresses
You can install OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) without providing floating IP addresses.
In the install-config.yaml file, do not define the following parameters:
-
platform.openstack.ingressFloatingIP -
platform.openstack.lbFloatingIP
If you cannot provide an external network, you can also leave platform.openstack.externalNetwork blank. If you do not provide a value for platform.openstack.externalNetwork, a router is not created for you, and, without additional action, the installer will fail to retrieve an image from Glance. You must configure external connectivity on your own.
If you run the installer from a system that cannot reach the cluster API due to a lack of floating IP addresses or name resolution, installation fails. To prevent installation failure in these cases, you can use a proxy network or run the installer from a system that is on the same network as your machines.
You can enable name resolution by creating DNS records for the API and Ingress ports. For example:
api.<cluster_name>.<base_domain>. IN A <api_port_IP> *.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
api.<cluster_name>.<base_domain>. IN A <api_port_IP>
*.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
If you do not control the DNS server, you can add the record to your /etc/hosts file. This action makes the API accessible to only you, which is not suitable for production deployment but does allow installation for development and testing.
9.2.14. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
9.2.15. Verifying cluster status
You can verify your OpenShift Container Platform cluster’s status during or after installation.
Procedure
In the cluster environment, export the administrator’s kubeconfig file:
export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
The
kubeconfigfile contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server.View the control plane and compute machines created after a deployment:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your cluster’s version:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your Operators' status:
oc get clusteroperator
$ oc get clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow View all running pods in the cluster:
oc get pods -A
$ oc get pods -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2.16. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.2.17. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
9.2.18. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If you need to enable external access to node ports, configure ingress cluster traffic by using a node port.
- If you did not configure RHOSP to accept application traffic over floating IP addresses, configure RHOSP access with floating IP addresses.
9.3. Installing a cluster on OpenStack on your own infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on Red Hat OpenStack Platform (RHOSP) that runs on user-provisioned infrastructure.
Using your own infrastructure allows you to integrate your cluster with existing infrastructure and modifications. The process requires more labor on your part than installer-provisioned installations, because you must create all RHOSP resources, like Nova servers, Neutron ports, and security groups. However, Red Hat provides Ansible playbooks to help you in the deployment process.
9.3.1. Prerequisites
Review details about the OpenShift Container Platform installation and update processes.
- Verify that OpenShift Container Platform 4.6 is compatible with your RHOSP version in the Available platforms section. You can also compare platform support across different versions by viewing the OpenShift Container Platform on RHOSP support matrix.
- Verify that your network configuration does not rely on a provider network. Provider networks are not supported.
- Have an RHOSP account where you want to install OpenShift Container Platform.
On the machine from which you run the installation program, have:
- A single directory in which you can keep the files you create during the installation process
- Python 3
9.3.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
9.3.3. Resource guidelines for installing OpenShift Container Platform on RHOSP
To support an OpenShift Container Platform installation, your Red Hat OpenStack Platform (RHOSP) quota must meet the following requirements:
| Resource | Value |
|---|---|
| Floating IP addresses | 3 |
| Ports | 15 |
| Routers | 1 |
| Subnets | 1 |
| RAM | 112 GB |
| vCPUs | 28 |
| Volume storage | 275 GB |
| Instances | 7 |
| Security groups | 3 |
| Security group rules | 60 |
A cluster might function with fewer than recommended resources, but its performance is not guaranteed.
If RHOSP object storage (Swift) is available and operated by a user account with the swiftoperator role, it is used as the default backend for the OpenShift Container Platform image registry. In this case, the volume storage requirement is 175 GB. Swift space requirements vary depending on the size of the image registry.
By default, your security group and security group rule quotas might be low. If you encounter problems, run openstack quota set --secgroups 3 --secgroup-rules 60 <project> as an administrator to increase them.
An OpenShift Container Platform deployment comprises control plane machines, compute machines, and a bootstrap machine.
9.3.3.1. Control plane machines
By default, the OpenShift Container Platform installation process creates three control plane machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.3.3.2. Compute machines
By default, the OpenShift Container Platform installation process creates three compute machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 8 GB memory, 2 vCPUs, and 100 GB storage space
Compute machines host the applications that you run on OpenShift Container Platform; aim to run as many as you can.
9.3.3.3. Bootstrap machine
During installation, a bootstrap machine is temporarily provisioned to stand up the control plane. After the production control plane is ready, the bootstrap machine is deprovisioned.
The bootstrap machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.3.4. Downloading playbook dependencies
The Ansible playbooks that simplify the installation process on user-provisioned infrastructure require several Python modules. On the machine where you will run the installer, add the modules' repositories and then download them.
These instructions assume that you are using Red Hat Enterprise Linux (RHEL) 8.
Prerequisites
- Python 3 is installed on your machine.
Procedure
On a command line, add the repositories:
Register with Red Hat Subscription Manager:
sudo subscription-manager register # If not done already
$ sudo subscription-manager register # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Pull the latest subscription data:
sudo subscription-manager attach --pool=$YOUR_POOLID # If not done already
$ sudo subscription-manager attach --pool=$YOUR_POOLID # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Disable the current repositories:
sudo subscription-manager repos --disable=* # If not done already
$ sudo subscription-manager repos --disable=* # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the required repositories:
sudo subscription-manager repos \ --enable=rhel-8-for-x86_64-baseos-rpms \ --enable=openstack-16-tools-for-rhel-8-x86_64-rpms \ --enable=ansible-2.9-for-rhel-8-x86_64-rpms \ --enable=rhel-8-for-x86_64-appstream-rpms
$ sudo subscription-manager repos \ --enable=rhel-8-for-x86_64-baseos-rpms \ --enable=openstack-16-tools-for-rhel-8-x86_64-rpms \ --enable=ansible-2.9-for-rhel-8-x86_64-rpms \ --enable=rhel-8-for-x86_64-appstream-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Install the modules:
sudo yum install python3-openstackclient ansible python3-openstacksdk python3-netaddr
$ sudo yum install python3-openstackclient ansible python3-openstacksdk python3-netaddrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that the
pythoncommand points topython3:sudo alternatives --set python /usr/bin/python3
$ sudo alternatives --set python /usr/bin/python3Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3.5. Downloading the installation playbooks
Download Ansible playbooks that you can use to install OpenShift Container Platform on your own Red Hat OpenStack Platform (RHOSP) infrastructure.
Prerequisites
- The curl command-line tool is available on your machine.
Procedure
To download the playbooks to your working directory, run the following script from a command line:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The playbooks are downloaded to your machine.
During the installation process, you can modify the playbooks to configure your deployment.
Retain all playbooks for the life of your cluster. You must have the playbooks to remove your OpenShift Container Platform cluster from RHOSP.
You must match any edits you make in the bootstrap.yaml, compute-nodes.yaml, control-plane.yaml, network.yaml, and security-groups.yaml files to the corresponding playbooks that are prefixed with down-. For example, edits to the bootstrap.yaml file must be reflected in the down-bootstrap.yaml file, too. If you do not edit both files, the supported cluster removal process will fail.
9.3.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
9.3.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
9.3.8. Creating the Red Hat Enterprise Linux CoreOS (RHCOS) image
The OpenShift Container Platform installation program requires that a Red Hat Enterprise Linux CoreOS (RHCOS) image be present in the Red Hat OpenStack Platform (RHOSP) cluster. Retrieve the latest RHCOS image, then upload it using the RHOSP CLI.
Prerequisites
- The RHOSP CLI is installed.
Procedure
- Log in to the Red Hat Customer Portal’s Product Downloads page.
Under Version, select the most recent release of OpenShift Container Platform 4.6 for Red Hat Enterprise Linux (RHEL) 8.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available.
- Download the Red Hat Enterprise Linux CoreOS (RHCOS) - OpenStack Image (QCOW).
Decompress the image.
NoteYou must decompress the RHOSP image before the cluster can use it. The name of the downloaded file might not contain a compression extension, like
.gzor.tgz. To find out if or how the file is compressed, in a command line, enter:file <name_of_downloaded_file>
$ file <name_of_downloaded_file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow From the image that you downloaded, create an image that is named
rhcosin your cluster by using the RHOSP CLI:openstack image create --container-format=bare --disk-format=qcow2 --file rhcos-${RHCOS_VERSION}-openstack.qcow2 rhcos$ openstack image create --container-format=bare --disk-format=qcow2 --file rhcos-${RHCOS_VERSION}-openstack.qcow2 rhcosCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantDepending on your RHOSP environment, you might be able to upload the image in either
.rawor.qcow2formats. If you use Ceph, you must use the.rawformat.WarningIf the installation program finds multiple images with the same name, it chooses one of them at random. To avoid this behavior, create unique names for resources in RHOSP.
After you upload the image to RHOSP, it is usable in the installation process.
9.3.9. Verifying external network access
The OpenShift Container Platform installation process requires external network access. You must provide an external network value to it, or deployment fails. Before you begin the process, verify that a network with the external router type exists in Red Hat OpenStack Platform (RHOSP).
Prerequisites
Procedure
Using the RHOSP CLI, verify the name and ID of the 'External' network:
openstack network list --long -c ID -c Name -c "Router Type"
$ openstack network list --long -c ID -c Name -c "Router Type"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+Copy to Clipboard Copied! Toggle word wrap Toggle overflow
A network with an external router type appears in the network list. If at least one does not, see Creating a default floating IP network and Creating a default provider network.
If the Neutron trunk service plug-in is enabled, a trunk port is created by default. For more information, see Neutron trunk port.
9.3.10. Enabling access to the environment
At deployment, all OpenShift Container Platform machines are created in a Red Hat OpenStack Platform (RHOSP)-tenant network. Therefore, they are not accessible directly in most RHOSP deployments.
You can configure OpenShift Container Platform API and application access by using floating IP addresses (FIPs) during installation. You can also complete an installation without configuring FIPs, but the installer will not configure a way to reach the API or applications externally.
9.3.10.1. Enabling access with floating IP addresses
Create floating IP (FIP) addresses for external access to the OpenShift Container Platform API, cluster applications, and the bootstrap process.
Procedure
Using the Red Hat OpenStack Platform (RHOSP) CLI, create the API FIP:
openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the Red Hat OpenStack Platform (RHOSP) CLI, create the apps, or Ingress, FIP:
openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow By using the Red Hat OpenStack Platform (RHOSP) CLI, create the bootstrap FIP:
openstack floating ip create --description "bootstrap machine" <external_network>
$ openstack floating ip create --description "bootstrap machine" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add records that follow these patterns to your DNS server for the API and Ingress FIPs:
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you do not control the DNS server, you can access the cluster by adding the cluster domain names such as the following to your
/etc/hostsfile:-
<api_floating_ip> api.<cluster_name>.<base_domain> -
<application_floating_ip> grafana-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> prometheus-k8s-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> oauth-openshift.apps.<cluster_name>.<base_domain> -
<application_floating_ip> console-openshift-console.apps.<cluster_name>.<base_domain> -
application_floating_ip integrated-oauth-server-openshift-authentication.apps.<cluster_name>.<base_domain>
The cluster domain names in the
/etc/hostsfile grant access to the web console and the monitoring interface of your cluster locally. You can also use thekubectloroc. You can access the user applications by using the additional entries pointing to the <application_floating_ip>. This action makes the API and applications accessible to only you, which is not suitable for production deployment, but does allow installation for development and testing.-
Add the FIPs to the
inventory.yamlfile as the values of the following variables:-
os_api_fip -
os_bootstrap_fip -
os_ingress_fip
-
If you use these values, you must also enter an external network as the value of the os_external_network variable in the inventory.yaml file.
You can make OpenShift Container Platform resources available outside of the cluster by assigning a floating IP address and updating your firewall configuration.
9.3.10.2. Completing installation without floating IP addresses
You can install OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) without providing floating IP addresses.
In the inventory.yaml file, do not define the following variables:
-
os_api_fip -
os_bootstrap_fip -
os_ingress_fip
If you cannot provide an external network, you can also leave os_external_network blank. If you do not provide a value for os_external_network, a router is not created for you, and, without additional action, the installer will fail to retrieve an image from Glance. Later in the installation process, when you create network resources, you must configure external connectivity on your own.
If you run the installer with the wait-for command from a system that cannot reach the cluster API due to a lack of floating IP addresses or name resolution, installation fails. To prevent installation failure in these cases, you can use a proxy network or run the installer from a system that is on the same network as your machines.
You can enable name resolution by creating DNS records for the API and Ingress ports. For example:
api.<cluster_name>.<base_domain>. IN A <api_port_IP> *.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
api.<cluster_name>.<base_domain>. IN A <api_port_IP>
*.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
If you do not control the DNS server, you can add the record to your /etc/hosts file. This action makes the API accessible to only you, which is not suitable for production deployment but does allow installation for development and testing.
9.3.11. Defining parameters for the installation program
The OpenShift Container Platform installation program relies on a file that is called clouds.yaml. The file describes Red Hat OpenStack Platform (RHOSP) configuration parameters, including the project name, log in information, and authorization service URLs.
Procedure
Create the
clouds.yamlfile:If your RHOSP distribution includes the Horizon web UI, generate a
clouds.yamlfile in it.ImportantRemember to add a password to the
authfield. You can also keep secrets in a separate file fromclouds.yaml.If your RHOSP distribution does not include the Horizon web UI, or you do not want to use Horizon, create the file yourself. For detailed information about
clouds.yaml, see Config files in the RHOSP documentation.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If your RHOSP installation uses self-signed certificate authority (CA) certificates for endpoint authentication:
- Copy the certificate authority file to your machine.
Add the machine to the certificate authority trust bundle:
sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/
$ sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the trust bundle:
sudo update-ca-trust extract
$ sudo update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
cacertskey to theclouds.yamlfile. The value must be an absolute, non-root-accessible path to the CA certificate:clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"Copy to Clipboard Copied! Toggle word wrap Toggle overflow TipAfter you run the installer with a custom CA certificate, you can update the certificate by editing the value of the
ca-cert.pemkey in thecloud-provider-configkeymap. On a command line, run:oc edit configmap -n openshift-config cloud-provider-config
$ oc edit configmap -n openshift-config cloud-provider-configCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Place the
clouds.yamlfile in one of the following locations:-
The value of the
OS_CLIENT_CONFIG_FILEenvironment variable - The current directory
-
A Unix-specific user configuration directory, for example
~/.config/openstack/clouds.yaml A Unix-specific site configuration directory, for example
/etc/openstack/clouds.yamlThe installation program searches for
clouds.yamlin that order.
-
The value of the
9.3.12. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Red Hat OpenStack Platform (RHOSP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select openstack as the platform to target.
- Specify the Red Hat OpenStack Platform (RHOSP) external network name to use for installing the cluster.
- Specify the floating IP address to use for external access to the OpenShift API.
- Specify a RHOSP flavor with at least 16 GB RAM to use for control plane nodes and 8 GB RAM for compute nodes.
- Select the base domain to deploy the cluster to. All DNS records will be sub-domains of this base and will also include the cluster name.
- Enter a name for your cluster. The name must be 14 or fewer characters long.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
You now have the file install-config.yaml in the directory that you specified.
9.3.13. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
9.3.13.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
9.3.13.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
9.3.13.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
9.3.13.4. Additional Red Hat OpenStack Platform (RHOSP) configuration parameters
Additional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| For compute machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For compute machines, the root volume’s type. |
String, for example |
|
| For control plane machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For control plane machines, the root volume’s type. |
String, for example |
|
|
The name of the RHOSP cloud to use from the list of clouds in the |
String, for example |
|
| The RHOSP external network name to be used for installation. |
String, for example |
|
| The RHOSP flavor to use for control plane and compute machines. |
String, for example |
9.3.13.5. Optional RHOSP configuration parameters
Optional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Additional networks that are associated with compute machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with compute machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| Additional networks that are associated with control plane machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with control plane machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. | An HTTP or HTTPS URL, optionally with an SHA-256 checksum.
For example, |
|
| The default machine pool platform configuration. |
|
|
|
An existing floating IP address to associate with the Ingress port. To use this property, you must also define the |
An IP address, for example |
|
|
An existing floating IP address to associate with the API load balancer. To use this property, you must also define the |
An IP address, for example |
|
| IP addresses for external DNS servers that cluster instances use for DNS resolution. |
A list of IP addresses as strings. For example, |
|
| The UUID of a RHOSP subnet that the cluster’s nodes use. Nodes and virtual IP (VIP) ports are created on this subnet.
The first item in If you deploy to a custom subnet, you cannot specify an external DNS server to the OpenShift Container Platform installer. Instead, add DNS to the subnet in RHOSP. |
A UUID as a string. For example, |
9.3.13.6. Custom subnets in RHOSP deployments
Optionally, you can deploy a cluster on a Red Hat OpenStack Platform (RHOSP) subnet of your choice. The subnet’s GUID is passed as the value of platform.openstack.machinesSubnet in the install-config.yaml file.
This subnet is used as the cluster’s primary subnet; nodes and ports are created on it.
Before you run the OpenShift Container Platform installer with a custom subnet, verify that:
- The target network and subnet are available.
- DHCP is enabled on the target subnet.
- You can provide installer credentials that have permission to create ports on the target network.
- If your network configuration requires a router, it is created in RHOSP. Some configurations rely on routers for floating IP address translation.
- Your network configuration does not rely on a provider network. Provider networks are not supported.
By default, the API VIP takes x.x.x.5 and the Ingress VIP takes x.x.x.7 from your network’s CIDR block. To override these default values, set values for platform.openstack.apiVIP and platform.openstack.ingressVIP that are outside of the DHCP allocation pool.
9.3.13.7. Sample customized install-config.yaml file for RHOSP
This sample install-config.yaml demonstrates all of the possible Red Hat OpenStack Platform (RHOSP) customization options.
This sample file is provided for reference only. You must obtain your install-config.yaml file by using the installation program.
9.3.13.8. Setting a custom subnet for machines
The IP range that the installation program uses by default might not match the Neutron subnet that you create when you install OpenShift Container Platform. If necessary, update the CIDR value for new machines by editing the installation configuration file.
Prerequisites
-
You have the
install-config.yamlfile that was generated by the OpenShift Container Platform installation program.
Procedure
-
On a command line, browse to the directory that contains
install-config.yaml. From that directory, either run a script to edit the
install-config.yamlfile or update the file manually:To set the value by using a script, run:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Insert a value that matches your intended Neutron subnet, e.g.
192.0.2.0/24.
-
To set the value manually, open the file and set the value of
networking.machineCIDRto something that matches your intended Neutron subnet.
9.3.13.9. Emptying compute machine pools
To proceed with an installation that uses your own infrastructure, set the number of compute machines in the installation configuration file to zero. Later, you create these machines manually.
Prerequisites
-
You have the
install-config.yamlfile that was generated by the OpenShift Container Platform installation program.
Procedure
-
On a command line, browse to the directory that contains
install-config.yaml. From that directory, either run a script to edit the
install-config.yamlfile or update the file manually:To set the value by using a script, run:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
To set the value manually, open the file and set the value of
compute.<first entry>.replicasto0.
9.3.14. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines and compute machine sets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the machine set files to create compute machines by using the machine API, but you must update references to them to match your environment.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the metadata file’s
infraIDkey as an environment variable:export INFRA_ID=$(jq -r .infraID metadata.json)
$ export INFRA_ID=$(jq -r .infraID metadata.json)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Extract the infraID key from metadata.json and use it as a prefix for all of the RHOSP resources that you create. By doing so, you avoid name conflicts when making multiple deployments in the same project.
9.3.15. Preparing the bootstrap Ignition files
The OpenShift Container Platform installation process relies on bootstrap machines that are created from a bootstrap Ignition configuration file.
Edit the file and upload it. Then, create a secondary bootstrap Ignition configuration file that Red Hat OpenStack Platform (RHOSP) uses to download the primary file.
Prerequisites
-
You have the bootstrap Ignition file that the installer program generates,
bootstrap.ign. The infrastructure ID from the installer’s metadata file is set as an environment variable (
$INFRA_ID).- If the variable is not set, see Creating the Kubernetes manifest and Ignition config files.
You have an HTTP(S)-accessible way to store the bootstrap Ignition file.
- The documented procedure uses the RHOSP image service (Glance), but you can also use the RHOSP storage service (Swift), Amazon S3, an internal HTTP server, or an ad hoc Nova server.
Procedure
Run the following Python script. The script modifies the bootstrap Ignition file to set the hostname and, if available, CA certificate file when it runs:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the RHOSP CLI, create an image that uses the bootstrap Ignition file:
openstack image create --disk-format=raw --container-format=bare --file bootstrap.ign <image_name>
$ openstack image create --disk-format=raw --container-format=bare --file bootstrap.ign <image_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the image’s details:
openstack image show <image_name>
$ openstack image show <image_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Make a note of the
filevalue; it follows the patternv2/images/<image_ID>/file.NoteVerify that the image you created is active.
Retrieve the image service’s public address:
openstack catalog show image
$ openstack catalog show imageCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Combine the public address with the image
filevalue and save the result as the storage location. The location follows the pattern<image_service_public_URL>/v2/images/<image_ID>/file. Generate an auth token and save the token ID:
openstack token issue -c id -f value
$ openstack token issue -c id -f valueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Insert the following content into a file called
$INFRA_ID-bootstrap-ignition.jsonand edit the placeholders to match your own values:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace the value of
ignition.config.merge.sourcewith the bootstrap Ignition file storage URL. - 2
- Set
nameinhttpHeadersto"X-Auth-Token". - 3
- Set
valueinhttpHeadersto your token’s ID. - 4
- If the bootstrap Ignition file server uses a self-signed certificate, include the base64-encoded certificate.
- Save the secondary Ignition config file.
The bootstrap Ignition data will be passed to RHOSP during installation.
The bootstrap Ignition file contains sensitive information, like clouds.yaml credentials. Ensure that you store it in a secure place, and delete it after you complete the installation process.
9.3.16. Creating control plane Ignition config files on RHOSP
Installing OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) on your own infrastructure requires control plane Ignition config files. You must create multiple config files.
As with the bootstrap Ignition configuration, you must explicitly define a hostname for each control plane machine.
Prerequisites
The infrastructure ID from the installation program’s metadata file is set as an environment variable (
$INFRA_ID).- If the variable is not set, see "Creating the Kubernetes manifest and Ignition config files."
Procedure
On a command line, run the following Python script:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You now have three control plane Ignition files:
<INFRA_ID>-master-0-ignition.json,<INFRA_ID>-master-1-ignition.json, and<INFRA_ID>-master-2-ignition.json.
9.3.17. Creating network resources on RHOSP
Create the network resources that an OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) installation on your own infrastructure requires. To save time, run supplied Ansible playbooks that generate security groups, networks, subnets, routers, and ports.
Prerequisites
- Python 3 is installed on your machine.
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
Procedure
Optional: Add an external network value to the
inventory.yamlplaybook:Example external network value in the
inventory.yamlAnsible playbookCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you did not provide a value for
os_external_networkin theinventory.yamlfile, you must ensure that VMs can access Glance and an external connection yourself.Optional: Add external network and floating IP (FIP) address values to the
inventory.yamlplaybook:Example FIP values in the
inventory.yamlAnsible playbookCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you do not define values for
os_api_fipandos_ingress_fip, you must perform post-installation network configuration.If you do not define a value for
os_bootstrap_fip, the installer cannot download debugging information from failed installations.See "Enabling access to the environment" for more information.
On a command line, create security groups by running the
security-groups.yamlplaybook:ansible-playbook -i inventory.yaml security-groups.yaml
$ ansible-playbook -i inventory.yaml security-groups.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow On a command line, create a network, subnet, and router by running the
network.yamlplaybook:ansible-playbook -i inventory.yaml network.yaml
$ ansible-playbook -i inventory.yaml network.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: If you want to control the default resolvers that Nova servers use, run the RHOSP CLI command:
openstack subnet set --dns-nameserver <server_1> --dns-nameserver <server_2> "$INFRA_ID-nodes"
$ openstack subnet set --dns-nameserver <server_1> --dns-nameserver <server_2> "$INFRA_ID-nodes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3.18. Creating the bootstrap machine on RHOSP
Create a bootstrap machine and give it the network access it needs to run on Red Hat OpenStack Platform (RHOSP). Red Hat provides an Ansible playbook that you run to simplify this process.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The
inventory.yaml,common.yaml, andbootstrap.yamlAnsible playbooks are in a common directory. -
The
metadata.jsonfile that the installation program created is in the same directory as the Ansible playbooks.
Procedure
- On a command line, change the working directory to the location of the playbooks.
On a command line, run the
bootstrap.yamlplaybook:ansible-playbook -i inventory.yaml bootstrap.yaml
$ ansible-playbook -i inventory.yaml bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow After the bootstrap server is active, view the logs to verify that the Ignition files were received:
openstack console log show "$INFRA_ID-bootstrap"
$ openstack console log show "$INFRA_ID-bootstrap"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3.19. Creating the control plane machines on RHOSP
Create three control plane machines by using the Ignition config files that you generated. Red Hat provides an Ansible playbook that you run to simplify this process.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The infrastructure ID from the installation program’s metadata file is set as an environment variable (
$INFRA_ID). -
The
inventory.yaml,common.yaml, andcontrol-plane.yamlAnsible playbooks are in a common directory. - You have the three Ignition files that were created in "Creating control plane Ignition config files."
Procedure
- On a command line, change the working directory to the location of the playbooks.
- If the control plane Ignition config files aren’t already in your working directory, copy them into it.
On a command line, run the
control-plane.yamlplaybook:ansible-playbook -i inventory.yaml control-plane.yaml
$ ansible-playbook -i inventory.yaml control-plane.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to monitor the bootstrapping process:
openshift-install wait-for bootstrap-complete
$ openshift-install wait-for bootstrap-completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow You will see messages that confirm that the control plane machines are running and have joined the cluster:
INFO API v1.14.6+f9b5405 up INFO Waiting up to 30m0s for bootstrapping to complete... ... INFO It is now safe to remove the bootstrap resources
INFO API v1.14.6+f9b5405 up INFO Waiting up to 30m0s for bootstrapping to complete... ... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3.20. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.3.21. Deleting bootstrap resources from RHOSP
Delete the bootstrap resources that you no longer need.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The
inventory.yaml,common.yaml, anddown-bootstrap.yamlAnsible playbooks are in a common directory. The control plane machines are running.
- If you do not know the status of the machines, see "Verifying cluster status."
Procedure
- On a command line, change the working directory to the location of the playbooks.
On a command line, run the
down-bootstrap.yamlplaybook:ansible-playbook -i inventory.yaml down-bootstrap.yaml
$ ansible-playbook -i inventory.yaml down-bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The bootstrap port, server, and floating IP address are deleted.
If you did not disable the bootstrap Ignition file URL earlier, do so now.
9.3.22. Creating compute machines on RHOSP
After standing up the control plane, create compute machines. Red Hat provides an Ansible playbook that you run to simplify this process.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The
inventory.yaml,common.yaml, andcompute-nodes.yamlAnsible playbooks are in a common directory. -
The
metadata.jsonfile that the installation program created is in the same directory as the Ansible playbooks. - The control plane is active.
Procedure
- On a command line, change the working directory to the location of the playbooks.
On a command line, run the playbook:
ansible-playbook -i inventory.yaml compute-nodes.yaml
$ ansible-playbook -i inventory.yaml compute-nodes.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Approve the certificate signing requests for the machines.
9.3.23. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
9.3.24. Verifying a successful installation
Verify that the OpenShift Container Platform installation is complete.
Prerequisites
-
You have the installation program (
openshift-install)
Procedure
On a command line, enter:
openshift-install --log-level debug wait-for install-complete
$ openshift-install --log-level debug wait-for install-completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The program outputs the console URL, as well as the administrator’s login information.
9.3.25. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
9.3.26. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If you need to enable external access to node ports, configure ingress cluster traffic by using a node port.
- If you did not configure RHOSP to accept application traffic over floating IP addresses, configure RHOSP access with floating IP addresses.
9.4. Installing a cluster on OpenStack with Kuryr on your own infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on Red Hat OpenStack Platform (RHOSP) that runs on user-provisioned infrastructure.
Using your own infrastructure allows you to integrate your cluster with existing infrastructure and modifications. The process requires more labor on your part than installer-provisioned installations, because you must create all RHOSP resources, like Nova servers, Neutron ports, and security groups. However, Red Hat provides Ansible playbooks to help you in the deployment process.
9.4.1. Prerequisites
Review details about the OpenShift Container Platform installation and update processes.
- Verify that OpenShift Container Platform 4.6 is compatible with your RHOSP version in the Available platforms section. You can also compare platform support across different versions by viewing the OpenShift Container Platform on RHOSP support matrix.
- Verify that your network configuration does not rely on a provider network. Provider networks are not supported.
- Have an RHOSP account where you want to install OpenShift Container Platform.
On the machine from which you run the installation program, have:
- A single directory in which you can keep the files you create during the installation process
- Python 3
9.4.2. About Kuryr SDN
Kuryr is a container network interface (CNI) plug-in solution that uses the Neutron and Octavia Red Hat OpenStack Platform (RHOSP) services to provide networking for pods and Services.
Kuryr and OpenShift Container Platform integration is primarily designed for OpenShift Container Platform clusters running on RHOSP VMs. Kuryr improves the network performance by plugging OpenShift Container Platform pods into RHOSP SDN. In addition, it provides interconnectivity between pods and RHOSP virtual instances.
Kuryr components are installed as pods in OpenShift Container Platform using the openshift-kuryr namespace:
-
kuryr-controller- a single service instance installed on amasternode. This is modeled in OpenShift Container Platform as aDeploymentobject. -
kuryr-cni- a container installing and configuring Kuryr as a CNI driver on each OpenShift Container Platform node. This is modeled in OpenShift Container Platform as aDaemonSetobject.
The Kuryr controller watches the OpenShift Container Platform API server for pod, service, and namespace create, update, and delete events. It maps the OpenShift Container Platform API calls to corresponding objects in Neutron and Octavia. This means that every network solution that implements the Neutron trunk port functionality can be used to back OpenShift Container Platform via Kuryr. This includes open source solutions such as Open vSwitch (OVS) and Open Virtual Network (OVN) as well as Neutron-compatible commercial SDNs.
Kuryr is recommended for OpenShift Container Platform deployments on encapsulated RHOSP tenant networks to avoid double encapsulation, such as running an encapsulated OpenShift Container Platform SDN over an RHOSP network.
If you use provider networks or tenant VLANs, you do not need to use Kuryr to avoid double encapsulation. The performance benefit is negligible. Depending on your configuration, though, using Kuryr to avoid having two overlays might still be beneficial.
Kuryr is not recommended in deployments where all of the following criteria are true:
- The RHOSP version is less than 16.
- The deployment uses UDP services, or a large number of TCP services on few hypervisors.
or
-
The
ovn-octaviaOctavia driver is disabled. - The deployment uses a large number of TCP services on few hypervisors.
9.4.3. Resource guidelines for installing OpenShift Container Platform on RHOSP with Kuryr
When using Kuryr SDN, the pods, services, namespaces, and network policies are using resources from the RHOSP quota; this increases the minimum requirements. Kuryr also has some additional requirements on top of what a default install requires.
Use the following quota to satisfy a default cluster’s minimum requirements:
| Resource | Value |
|---|---|
| Floating IP addresses | 3 - plus the expected number of Services of LoadBalancer type |
| Ports | 1500 - 1 needed per Pod |
| Routers | 1 |
| Subnets | 250 - 1 needed per Namespace/Project |
| Networks | 250 - 1 needed per Namespace/Project |
| RAM | 112 GB |
| vCPUs | 28 |
| Volume storage | 275 GB |
| Instances | 7 |
| Security groups | 250 - 1 needed per Service and per NetworkPolicy |
| Security group rules | 1000 |
| Load balancers | 100 - 1 needed per Service |
| Load balancer listeners | 500 - 1 needed per Service-exposed port |
| Load balancer pools | 500 - 1 needed per Service-exposed port |
A cluster might function with fewer than recommended resources, but its performance is not guaranteed.
If RHOSP object storage (Swift) is available and operated by a user account with the swiftoperator role, it is used as the default backend for the OpenShift Container Platform image registry. In this case, the volume storage requirement is 175 GB. Swift space requirements vary depending on the size of the image registry.
If you are using Red Hat OpenStack Platform (RHOSP) version 16 with the Amphora driver rather than the OVN Octavia driver, security groups are associated with service accounts instead of user projects.
Take the following notes into consideration when setting resources:
- The number of ports that are required is larger than the number of pods. Kuryr uses ports pools to have pre-created ports ready to be used by pods and speed up the pods' booting time.
-
Each network policy is mapped into an RHOSP security group, and depending on the
NetworkPolicyspec, one or more rules are added to the security group. Each service is mapped to an RHOSP load balancer. Consider this requirement when estimating the number of security groups required for the quota.
If you are using RHOSP version 15 or earlier, or the
ovn-octavia driver, each load balancer has a security group with the user project.The quota does not account for load balancer resources (such as VM resources), but you must consider these resources when you decide the RHOSP deployment’s size. The default installation will have more than 50 load balancers; the clusters must be able to accommodate them.
If you are using RHOSP version 16 with the OVN Octavia driver enabled, only one load balancer VM is generated; services are load balanced through OVN flows.
An OpenShift Container Platform deployment comprises control plane machines, compute machines, and a bootstrap machine.
To enable Kuryr SDN, your environment must meet the following requirements:
- Run RHOSP 13+.
- Have Overcloud with Octavia.
- Use Neutron Trunk ports extension.
-
Use
openvswitchfirewall driver if ML2/OVS Neutron driver is used instead ofovs-hybrid.
9.4.3.1. Increasing quota
When using Kuryr SDN, you must increase quotas to satisfy the Red Hat OpenStack Platform (RHOSP) resources used by pods, services, namespaces, and network policies.
Procedure
Increase the quotas for a project by running the following command:
sudo openstack quota set --secgroups 250 --secgroup-rules 1000 --ports 1500 --subnets 250 --networks 250 <project>
$ sudo openstack quota set --secgroups 250 --secgroup-rules 1000 --ports 1500 --subnets 250 --networks 250 <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.3.2. Configuring Neutron
Kuryr CNI leverages the Neutron Trunks extension to plug containers into the Red Hat OpenStack Platform (RHOSP) SDN, so you must use the trunks extension for Kuryr to properly work.
In addition, if you leverage the default ML2/OVS Neutron driver, the firewall must be set to openvswitch instead of ovs_hybrid so that security groups are enforced on trunk subports and Kuryr can properly handle network policies.
9.4.3.3. Configuring Octavia
Kuryr SDN uses Red Hat OpenStack Platform (RHOSP)'s Octavia LBaaS to implement OpenShift Container Platform services. Thus, you must install and configure Octavia components in RHOSP to use Kuryr SDN.
To enable Octavia, you must include the Octavia service during the installation of the RHOSP Overcloud, or upgrade the Octavia service if the Overcloud already exists. The following steps for enabling Octavia apply to both a clean install of the Overcloud or an Overcloud update.
The following steps only capture the key pieces required during the deployment of RHOSP when dealing with Octavia. It is also important to note that registry methods vary.
This example uses the local registry method.
Procedure
If you are using the local registry, create a template to upload the images to the registry. For example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Verify that the
local_registry_images.yamlfile contains the Octavia images. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe Octavia container versions vary depending upon the specific RHOSP release installed.
Pull the container images from
registry.redhat.ioto the Undercloud node:(undercloud) $ sudo openstack overcloud container image upload \ --config-file /home/stack/local_registry_images.yaml \ --verbose
(undercloud) $ sudo openstack overcloud container image upload \ --config-file /home/stack/local_registry_images.yaml \ --verboseCopy to Clipboard Copied! Toggle word wrap Toggle overflow This may take some time depending on the speed of your network and Undercloud disk.
Since an Octavia load balancer is used to access the OpenShift Container Platform API, you must increase their listeners' default timeouts for the connections. The default timeout is 50 seconds. Increase the timeout to 20 minutes by passing the following file to the Overcloud deploy command:
(undercloud) $ cat octavia_timeouts.yaml parameter_defaults: OctaviaTimeoutClientData: 1200000 OctaviaTimeoutMemberData: 1200000
(undercloud) $ cat octavia_timeouts.yaml parameter_defaults: OctaviaTimeoutClientData: 1200000 OctaviaTimeoutMemberData: 1200000Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThis is not needed for RHOSP 13.0.13+.
Install or update your Overcloud environment with Octavia:
openstack overcloud deploy --templates \ -e /usr/share/openstack-tripleo-heat-templates/environments/services-docker/octavia.yaml \ -e octavia_timeouts.yaml
$ openstack overcloud deploy --templates \ -e /usr/share/openstack-tripleo-heat-templates/environments/services-docker/octavia.yaml \ -e octavia_timeouts.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThis command only includes the files associated with Octavia; it varies based on your specific installation of RHOSP. See the RHOSP documentation for further information. For more information on customizing your Octavia installation, see installation of Octavia using Director.
NoteWhen leveraging Kuryr SDN, the Overcloud installation requires the Neutron
trunkextension. This is available by default on director deployments. Use theopenvswitchfirewall instead of the defaultovs-hybridwhen the Neutron backend is ML2/OVS. There is no need for modifications if the backend is ML2/OVN.In RHOSP versions earlier than 13.0.13, add the project ID to the
octavia.confconfiguration file after you create the project.To enforce network policies across services, like when traffic goes through the Octavia load balancer, you must ensure Octavia creates the Amphora VM security groups on the user project.
This change ensures that required load balancer security groups belong to that project, and that they can be updated to enforce services isolation.
NoteThis task is unnecessary in RHOSP version 13.0.13 or later.
Octavia implements a new ACL API that restricts access to the load balancers VIP.
Get the project ID
openstack project show <project>
$ openstack project show <project>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the project ID to
octavia.conffor the controllers.Source the
stackrcfile:source stackrc # Undercloud credentials
$ source stackrc # Undercloud credentialsCopy to Clipboard Copied! Toggle word wrap Toggle overflow List the Overcloud controllers:
openstack server list
$ openstack server listCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow SSH into the controller(s).
ssh heat-admin@192.168.24.8
$ ssh heat-admin@192.168.24.8Copy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
octavia.conffile to add the project into the list of projects where Amphora security groups are on the user’s account.List of project IDs that are allowed to have Load balancer security groups belonging to them.
# List of project IDs that are allowed to have Load balancer security groups # belonging to them. amp_secgroup_allowed_projects = PROJECT_IDCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Restart the Octavia worker so the new configuration loads.
controller-0$ sudo docker restart octavia_worker
controller-0$ sudo docker restart octavia_workerCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Depending on your RHOSP environment, Octavia might not support UDP listeners. If you use Kuryr SDN on RHOSP version 13.0.13 or earlier, UDP services are not supported. RHOSP version 16 or later support UDP.
9.4.3.3.1. The Octavia OVN Driver
Octavia supports multiple provider drivers through the Octavia API.
To see all available Octavia provider drivers, on a command line, enter:
openstack loadbalancer provider list
$ openstack loadbalancer provider listExample output
Beginning with RHOSP version 16, the Octavia OVN provider driver (ovn) is supported on OpenShift Container Platform on RHOSP deployments.
ovn is an integration driver for the load balancing that Octavia and OVN provide. It supports basic load balancing capabilities, and is based on OpenFlow rules. The driver is automatically enabled in Octavia by Director on deployments that use OVN Neutron ML2.
The Amphora provider driver is the default driver. If ovn is enabled, however, Kuryr uses it.
If Kuryr uses ovn instead of Amphora, it offers the following benefits:
- Decreased resource requirements. Kuryr does not require a load balancer VM for each service.
- Reduced network latency.
- Increased service creation speed by using OpenFlow rules instead of a VM for each service.
- Distributed load balancing actions across all nodes instead of centralized on Amphora VMs.
9.4.3.4. Known limitations of installing with Kuryr
Using OpenShift Container Platform with Kuryr SDN has several known limitations.
RHOSP general limitations
OpenShift Container Platform with Kuryr SDN does not support Service objects with type NodePort.
If the machines subnet is not connected to a router, or if the subnet is connected, but the router has no external gateway set, Kuryr cannot create floating IPs for Service objects with type LoadBalancer.
-
Configuring the
sessionAffinity=ClientIPproperty onServiceobjects does not have an effect. Kuryr does not support this setting.
RHOSP version limitations
Using OpenShift Container Platform with Kuryr SDN has several limitations that depend on the RHOSP version.
RHOSP versions before 16 use the default Octavia load balancer driver (Amphora). This driver requires that one Amphora load balancer VM is deployed per OpenShift Container Platform service. Creating too many services can cause you to run out of resources.
Deployments of later versions of RHOSP that have the OVN Octavia driver disabled also use the Amphora driver. They are subject to the same resource concerns as earlier versions of RHOSP.
- Octavia RHOSP versions before 13.0.13 do not support UDP listeners. Therefore, OpenShift Container Platform UDP services are not supported.
- Octavia RHOSP versions before 13.0.13 cannot listen to multiple protocols on the same port. Services that expose the same port to different protocols, like TCP and UDP, are not supported.
- Kuryr SDN does not support automatic unidling by a service.
RHOSP environment limitations
There are limitations when using Kuryr SDN that depend on your deployment environment.
Because of Octavia’s lack of support for the UDP protocol and multiple listeners, if the RHOSP version is earlier than 13.0.13, Kuryr forces pods to use TCP for DNS resolution.
In Go versions 1.12 and earlier, applications that are compiled with CGO support disabled use UDP only. In this case, the native Go resolver does not recognize the use-vc option in resolv.conf, which controls whether TCP is forced for DNS resolution. As a result, UDP is still used for DNS resolution, which fails.
To ensure that TCP forcing is allowed, compile applications either with the environment variable CGO_ENABLED set to 1, i.e. CGO_ENABLED=1, or ensure that the variable is absent.
In Go versions 1.13 and later, TCP is used automatically if DNS resolution using UDP fails.
musl-based containers, including Alpine-based containers, do not support the use-vc option.
RHOSP upgrade limitations
As a result of the RHOSP upgrade process, the Octavia API might be changed, and upgrades to the Amphora images that are used for load balancers might be required.
You can address API changes on an individual basis.
If the Amphora image is upgraded, the RHOSP operator can handle existing load balancer VMs in two ways:
- Upgrade each VM by triggering a load balancer failover.
- Leave responsibility for upgrading the VMs to users.
If the operator takes the first option, there might be short downtimes during failovers.
If the operator takes the second option, the existing load balancers will not support upgraded Octavia API features, like UDP listeners. In this case, users must recreate their Services to use these features.
If OpenShift Container Platform detects a new Octavia version that supports UDP load balancing, it recreates the DNS service automatically. The service recreation ensures that the service default supports UDP load balancing.
The recreation causes the DNS service approximately one minute of downtime.
9.4.3.5. Control plane machines
By default, the OpenShift Container Platform installation process creates three control plane machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.4.3.6. Compute machines
By default, the OpenShift Container Platform installation process creates three compute machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 8 GB memory, 2 vCPUs, and 100 GB storage space
Compute machines host the applications that you run on OpenShift Container Platform; aim to run as many as you can.
9.4.3.7. Bootstrap machine
During installation, a bootstrap machine is temporarily provisioned to stand up the control plane. After the production control plane is ready, the bootstrap machine is deprovisioned.
The bootstrap machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.4.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
9.4.5. Downloading playbook dependencies
The Ansible playbooks that simplify the installation process on user-provisioned infrastructure require several Python modules. On the machine where you will run the installer, add the modules' repositories and then download them.
These instructions assume that you are using Red Hat Enterprise Linux (RHEL) 8.
Prerequisites
- Python 3 is installed on your machine.
Procedure
On a command line, add the repositories:
Register with Red Hat Subscription Manager:
sudo subscription-manager register # If not done already
$ sudo subscription-manager register # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Pull the latest subscription data:
sudo subscription-manager attach --pool=$YOUR_POOLID # If not done already
$ sudo subscription-manager attach --pool=$YOUR_POOLID # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Disable the current repositories:
sudo subscription-manager repos --disable=* # If not done already
$ sudo subscription-manager repos --disable=* # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the required repositories:
sudo subscription-manager repos \ --enable=rhel-8-for-x86_64-baseos-rpms \ --enable=openstack-16-tools-for-rhel-8-x86_64-rpms \ --enable=ansible-2.9-for-rhel-8-x86_64-rpms \ --enable=rhel-8-for-x86_64-appstream-rpms
$ sudo subscription-manager repos \ --enable=rhel-8-for-x86_64-baseos-rpms \ --enable=openstack-16-tools-for-rhel-8-x86_64-rpms \ --enable=ansible-2.9-for-rhel-8-x86_64-rpms \ --enable=rhel-8-for-x86_64-appstream-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Install the modules:
sudo yum install python3-openstackclient ansible python3-openstacksdk python3-netaddr
$ sudo yum install python3-openstackclient ansible python3-openstacksdk python3-netaddrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that the
pythoncommand points topython3:sudo alternatives --set python /usr/bin/python3
$ sudo alternatives --set python /usr/bin/python3Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.6. Downloading the installation playbooks
Download Ansible playbooks that you can use to install OpenShift Container Platform on your own Red Hat OpenStack Platform (RHOSP) infrastructure.
Prerequisites
- The curl command-line tool is available on your machine.
Procedure
To download the playbooks to your working directory, run the following script from a command line:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
The playbooks are downloaded to your machine.
During the installation process, you can modify the playbooks to configure your deployment.
Retain all playbooks for the life of your cluster. You must have the playbooks to remove your OpenShift Container Platform cluster from RHOSP.
You must match any edits you make in the bootstrap.yaml, compute-nodes.yaml, control-plane.yaml, network.yaml, and security-groups.yaml files to the corresponding playbooks that are prefixed with down-. For example, edits to the bootstrap.yaml file must be reflected in the down-bootstrap.yaml file, too. If you do not edit both files, the supported cluster removal process will fail.
9.4.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
9.4.8. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
9.4.9. Creating the Red Hat Enterprise Linux CoreOS (RHCOS) image
The OpenShift Container Platform installation program requires that a Red Hat Enterprise Linux CoreOS (RHCOS) image be present in the Red Hat OpenStack Platform (RHOSP) cluster. Retrieve the latest RHCOS image, then upload it using the RHOSP CLI.
Prerequisites
- The RHOSP CLI is installed.
Procedure
- Log in to the Red Hat Customer Portal’s Product Downloads page.
Under Version, select the most recent release of OpenShift Container Platform 4.6 for Red Hat Enterprise Linux (RHEL) 8.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available.
- Download the Red Hat Enterprise Linux CoreOS (RHCOS) - OpenStack Image (QCOW).
Decompress the image.
NoteYou must decompress the RHOSP image before the cluster can use it. The name of the downloaded file might not contain a compression extension, like
.gzor.tgz. To find out if or how the file is compressed, in a command line, enter:file <name_of_downloaded_file>
$ file <name_of_downloaded_file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow From the image that you downloaded, create an image that is named
rhcosin your cluster by using the RHOSP CLI:openstack image create --container-format=bare --disk-format=qcow2 --file rhcos-${RHCOS_VERSION}-openstack.qcow2 rhcos$ openstack image create --container-format=bare --disk-format=qcow2 --file rhcos-${RHCOS_VERSION}-openstack.qcow2 rhcosCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantDepending on your RHOSP environment, you might be able to upload the image in either
.rawor.qcow2formats. If you use Ceph, you must use the.rawformat.WarningIf the installation program finds multiple images with the same name, it chooses one of them at random. To avoid this behavior, create unique names for resources in RHOSP.
After you upload the image to RHOSP, it is usable in the installation process.
9.4.10. Verifying external network access
The OpenShift Container Platform installation process requires external network access. You must provide an external network value to it, or deployment fails. Before you begin the process, verify that a network with the external router type exists in Red Hat OpenStack Platform (RHOSP).
Prerequisites
Procedure
Using the RHOSP CLI, verify the name and ID of the 'External' network:
openstack network list --long -c ID -c Name -c "Router Type"
$ openstack network list --long -c ID -c Name -c "Router Type"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+
+--------------------------------------+----------------+-------------+ | ID | Name | Router Type | +--------------------------------------+----------------+-------------+ | 148a8023-62a7-4672-b018-003462f8d7dc | public_network | External | +--------------------------------------+----------------+-------------+Copy to Clipboard Copied! Toggle word wrap Toggle overflow
A network with an external router type appears in the network list. If at least one does not, see Creating a default floating IP network and Creating a default provider network.
If the Neutron trunk service plug-in is enabled, a trunk port is created by default. For more information, see Neutron trunk port.
9.4.11. Enabling access to the environment
At deployment, all OpenShift Container Platform machines are created in a Red Hat OpenStack Platform (RHOSP)-tenant network. Therefore, they are not accessible directly in most RHOSP deployments.
You can configure OpenShift Container Platform API and application access by using floating IP addresses (FIPs) during installation. You can also complete an installation without configuring FIPs, but the installer will not configure a way to reach the API or applications externally.
9.4.11.1. Enabling access with floating IP addresses
Create floating IP (FIP) addresses for external access to the OpenShift Container Platform API, cluster applications, and the bootstrap process.
Procedure
Using the Red Hat OpenStack Platform (RHOSP) CLI, create the API FIP:
openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the Red Hat OpenStack Platform (RHOSP) CLI, create the apps, or Ingress, FIP:
openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow By using the Red Hat OpenStack Platform (RHOSP) CLI, create the bootstrap FIP:
openstack floating ip create --description "bootstrap machine" <external_network>
$ openstack floating ip create --description "bootstrap machine" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add records that follow these patterns to your DNS server for the API and Ingress FIPs:
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you do not control the DNS server, you can access the cluster by adding the cluster domain names such as the following to your
/etc/hostsfile:-
<api_floating_ip> api.<cluster_name>.<base_domain> -
<application_floating_ip> grafana-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> prometheus-k8s-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> oauth-openshift.apps.<cluster_name>.<base_domain> -
<application_floating_ip> console-openshift-console.apps.<cluster_name>.<base_domain> -
application_floating_ip integrated-oauth-server-openshift-authentication.apps.<cluster_name>.<base_domain>
The cluster domain names in the
/etc/hostsfile grant access to the web console and the monitoring interface of your cluster locally. You can also use thekubectloroc. You can access the user applications by using the additional entries pointing to the <application_floating_ip>. This action makes the API and applications accessible to only you, which is not suitable for production deployment, but does allow installation for development and testing.-
Add the FIPs to the
inventory.yamlfile as the values of the following variables:-
os_api_fip -
os_bootstrap_fip -
os_ingress_fip
-
If you use these values, you must also enter an external network as the value of the os_external_network variable in the inventory.yaml file.
You can make OpenShift Container Platform resources available outside of the cluster by assigning a floating IP address and updating your firewall configuration.
9.4.11.2. Completing installation without floating IP addresses
You can install OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) without providing floating IP addresses.
In the inventory.yaml file, do not define the following variables:
-
os_api_fip -
os_bootstrap_fip -
os_ingress_fip
If you cannot provide an external network, you can also leave os_external_network blank. If you do not provide a value for os_external_network, a router is not created for you, and, without additional action, the installer will fail to retrieve an image from Glance. Later in the installation process, when you create network resources, you must configure external connectivity on your own.
If you run the installer with the wait-for command from a system that cannot reach the cluster API due to a lack of floating IP addresses or name resolution, installation fails. To prevent installation failure in these cases, you can use a proxy network or run the installer from a system that is on the same network as your machines.
You can enable name resolution by creating DNS records for the API and Ingress ports. For example:
api.<cluster_name>.<base_domain>. IN A <api_port_IP> *.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
api.<cluster_name>.<base_domain>. IN A <api_port_IP>
*.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
If you do not control the DNS server, you can add the record to your /etc/hosts file. This action makes the API accessible to only you, which is not suitable for production deployment but does allow installation for development and testing.
9.4.12. Defining parameters for the installation program
The OpenShift Container Platform installation program relies on a file that is called clouds.yaml. The file describes Red Hat OpenStack Platform (RHOSP) configuration parameters, including the project name, log in information, and authorization service URLs.
Procedure
Create the
clouds.yamlfile:If your RHOSP distribution includes the Horizon web UI, generate a
clouds.yamlfile in it.ImportantRemember to add a password to the
authfield. You can also keep secrets in a separate file fromclouds.yaml.If your RHOSP distribution does not include the Horizon web UI, or you do not want to use Horizon, create the file yourself. For detailed information about
clouds.yaml, see Config files in the RHOSP documentation.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If your RHOSP installation uses self-signed certificate authority (CA) certificates for endpoint authentication:
- Copy the certificate authority file to your machine.
Add the machine to the certificate authority trust bundle:
sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/
$ sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the trust bundle:
sudo update-ca-trust extract
$ sudo update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
cacertskey to theclouds.yamlfile. The value must be an absolute, non-root-accessible path to the CA certificate:clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"Copy to Clipboard Copied! Toggle word wrap Toggle overflow TipAfter you run the installer with a custom CA certificate, you can update the certificate by editing the value of the
ca-cert.pemkey in thecloud-provider-configkeymap. On a command line, run:oc edit configmap -n openshift-config cloud-provider-config
$ oc edit configmap -n openshift-config cloud-provider-configCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Place the
clouds.yamlfile in one of the following locations:-
The value of the
OS_CLIENT_CONFIG_FILEenvironment variable - The current directory
-
A Unix-specific user configuration directory, for example
~/.config/openstack/clouds.yaml A Unix-specific site configuration directory, for example
/etc/openstack/clouds.yamlThe installation program searches for
clouds.yamlin that order.
-
The value of the
9.4.13. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Red Hat OpenStack Platform (RHOSP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select openstack as the platform to target.
- Specify the Red Hat OpenStack Platform (RHOSP) external network name to use for installing the cluster.
- Specify the floating IP address to use for external access to the OpenShift API.
- Specify a RHOSP flavor with at least 16 GB RAM to use for control plane nodes and 8 GB RAM for compute nodes.
- Select the base domain to deploy the cluster to. All DNS records will be sub-domains of this base and will also include the cluster name.
- Enter a name for your cluster. The name must be 14 or fewer characters long.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
You now have the file install-config.yaml in the directory that you specified.
9.4.14. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
9.4.14.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
9.4.14.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
9.4.14.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
9.4.14.4. Additional Red Hat OpenStack Platform (RHOSP) configuration parameters
Additional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| For compute machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For compute machines, the root volume’s type. |
String, for example |
|
| For control plane machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For control plane machines, the root volume’s type. |
String, for example |
|
|
The name of the RHOSP cloud to use from the list of clouds in the |
String, for example |
|
| The RHOSP external network name to be used for installation. |
String, for example |
|
| The RHOSP flavor to use for control plane and compute machines. |
String, for example |
9.4.14.5. Optional RHOSP configuration parameters
Optional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Additional networks that are associated with compute machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with compute machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| Additional networks that are associated with control plane machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with control plane machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. | An HTTP or HTTPS URL, optionally with an SHA-256 checksum.
For example, |
|
| The default machine pool platform configuration. |
|
|
|
An existing floating IP address to associate with the Ingress port. To use this property, you must also define the |
An IP address, for example |
|
|
An existing floating IP address to associate with the API load balancer. To use this property, you must also define the |
An IP address, for example |
|
| IP addresses for external DNS servers that cluster instances use for DNS resolution. |
A list of IP addresses as strings. For example, |
|
| The UUID of a RHOSP subnet that the cluster’s nodes use. Nodes and virtual IP (VIP) ports are created on this subnet.
The first item in If you deploy to a custom subnet, you cannot specify an external DNS server to the OpenShift Container Platform installer. Instead, add DNS to the subnet in RHOSP. |
A UUID as a string. For example, |
9.4.14.6. Custom subnets in RHOSP deployments
Optionally, you can deploy a cluster on a Red Hat OpenStack Platform (RHOSP) subnet of your choice. The subnet’s GUID is passed as the value of platform.openstack.machinesSubnet in the install-config.yaml file.
This subnet is used as the cluster’s primary subnet; nodes and ports are created on it.
Before you run the OpenShift Container Platform installer with a custom subnet, verify that:
- The target network and subnet are available.
- DHCP is enabled on the target subnet.
- You can provide installer credentials that have permission to create ports on the target network.
- If your network configuration requires a router, it is created in RHOSP. Some configurations rely on routers for floating IP address translation.
- Your network configuration does not rely on a provider network. Provider networks are not supported.
By default, the API VIP takes x.x.x.5 and the Ingress VIP takes x.x.x.7 from your network’s CIDR block. To override these default values, set values for platform.openstack.apiVIP and platform.openstack.ingressVIP that are outside of the DHCP allocation pool.
9.4.14.7. Sample customized install-config.yaml file for RHOSP with Kuryr
To deploy with Kuryr SDN instead of the default OpenShift SDN, you must modify the install-config.yaml file to include Kuryr as the desired networking.networkType and proceed with the default OpenShift Container Platform SDN installation steps. This sample install-config.yaml demonstrates all of the possible Red Hat OpenStack Platform (RHOSP) customization options.
This sample file is provided for reference only. You must obtain your install-config.yaml file by using the installation program.
- 1
- The Amphora Octavia driver creates two ports per load balancer. As a result, the service subnet that the installer creates is twice the size of the CIDR that is specified as the value of the
serviceNetworkproperty. The larger range is required to prevent IP address conflicts. - 2 3
- Both
trunkSupportandoctaviaSupportare automatically discovered by the installer, so there is no need to set them. But if your environment does not meet both requirements, Kuryr SDN will not properly work. Trunks are needed to connect the pods to the RHOSP network and Octavia is required to create the OpenShift Container Platform services.
9.4.14.8. Kuryr ports pools
A Kuryr ports pool maintains a number of ports on standby for pod creation.
Keeping ports on standby minimizes pod creation time. Without ports pools, Kuryr must explicitly request port creation or deletion whenever a pod is created or deleted.
The Neutron ports that Kuryr uses are created in subnets that are tied to namespaces. These pod ports are also added as subports to the primary port of OpenShift Container Platform cluster nodes.
Because Kuryr keeps each namespace in a separate subnet, a separate ports pool is maintained for each namespace-worker pair.
Prior to installing a cluster, you can set the following parameters in the cluster-network-03-config.yml manifest file to configure ports pool behavior:
-
The
enablePortPoolsPrepopulationparameter controls pool prepopulation, which forces Kuryr to add ports to the pool when it is created, such as when a new host is added, or a new namespace is created. The default value isfalse. -
The
poolMinPortsparameter is the minimum number of free ports that are kept in the pool. The default value is1. The
poolMaxPortsparameter is the maximum number of free ports that are kept in the pool. A value of0disables that upper bound. This is the default setting.If your OpenStack port quota is low, or you have a limited number of IP addresses on the pod network, consider setting this option to ensure that unneeded ports are deleted.
-
The
poolBatchPortsparameter defines the maximum number of Neutron ports that can be created at once. The default value is3.
9.4.14.9. Adjusting Kuryr ports pools during installation
During installation, you can configure how Kuryr manages Red Hat OpenStack Platform (RHOSP) Neutron ports to control the speed and efficiency of pod creation.
Prerequisites
-
Create and modify the
install-config.yamlfile.
Procedure
From a command line, create the manifest files:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the name of the directory that contains theinstall-config.yamlfile for your cluster.
Create a file that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:touch <installation_directory>/manifests/cluster-network-03-config.yml
$ touch <installation_directory>/manifests/cluster-network-03-config.yml1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name that contains themanifests/directory for your cluster.
After creating the file, several network configuration files are in the
manifests/directory, as shown:ls <installation_directory>/manifests/cluster-network-*
$ ls <installation_directory>/manifests/cluster-network-*Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
cluster-network-01-crd.yml cluster-network-02-config.yml cluster-network-03-config.yml
cluster-network-01-crd.yml cluster-network-02-config.yml cluster-network-03-config.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Open the
cluster-network-03-config.ymlfile in an editor, and enter a custom resource (CR) that describes the Cluster Network Operator configuration that you want:oc edit networks.operator.openshift.io cluster
$ oc edit networks.operator.openshift.io clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the settings to meet your requirements. The following file is provided as an example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Set the value of
enablePortPoolsPrepopulationtotrueto make Kuryr create new Neutron ports after a namespace is created or a new node is added to the cluster. This setting raises the Neutron ports quota but can reduce the time that is required to spawn pods. The default value isfalse. - 2
- Kuryr creates new ports for a pool if the number of free ports in that pool is lower than the value of
poolMinPorts. The default value is1. - 3
poolBatchPortscontrols the number of new ports that are created if the number of free ports is lower than the value ofpoolMinPorts. The default value is3.- 4
- If the number of free ports in a pool is higher than the value of
poolMaxPorts, Kuryr deletes them until the number matches that value. Setting this value to0disables this upper bound, preventing pools from shrinking. The default value is0. - 5
- The
openStackServiceNetworkparameter defines the CIDR range of the network from which IP addresses are allocated to RHOSP Octavia’s LoadBalancers.
If this parameter is used with the Amphora driver, Octavia takes two IP addresses from this network for each load balancer: one for OpenShift and the other for VRRP connections. Because these IP addresses are managed by OpenShift Container Platform and Neutron respectively, they must come from different pools. Therefore, the value of
openStackServiceNetworkmust be at least twice the size of the value ofserviceNetwork, and the value ofserviceNetworkmust overlap entirely with the range that is defined byopenStackServiceNetwork.The CNO verifies that VRRP IP addresses that are taken from the range that is defined by this parameter do not overlap with the range that is defined by the
serviceNetworkparameter.If this parameter is not set, the CNO uses an expanded value of
serviceNetworkthat is determined by decrementing the prefix size by 1.-
Save the
cluster-network-03-config.ymlfile, and exit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory while creating the cluster.
9.4.14.10. Setting a custom subnet for machines
The IP range that the installation program uses by default might not match the Neutron subnet that you create when you install OpenShift Container Platform. If necessary, update the CIDR value for new machines by editing the installation configuration file.
Prerequisites
-
You have the
install-config.yamlfile that was generated by the OpenShift Container Platform installation program.
Procedure
-
On a command line, browse to the directory that contains
install-config.yaml. From that directory, either run a script to edit the
install-config.yamlfile or update the file manually:To set the value by using a script, run:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Insert a value that matches your intended Neutron subnet, e.g.
192.0.2.0/24.
-
To set the value manually, open the file and set the value of
networking.machineCIDRto something that matches your intended Neutron subnet.
9.4.14.11. Emptying compute machine pools
To proceed with an installation that uses your own infrastructure, set the number of compute machines in the installation configuration file to zero. Later, you create these machines manually.
Prerequisites
-
You have the
install-config.yamlfile that was generated by the OpenShift Container Platform installation program.
Procedure
-
On a command line, browse to the directory that contains
install-config.yaml. From that directory, either run a script to edit the
install-config.yamlfile or update the file manually:To set the value by using a script, run:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
To set the value manually, open the file and set the value of
compute.<first entry>.replicasto0.
9.4.14.12. Modifying the network type
By default, the installation program selects the OpenShiftSDN network type. To use Kuryr instead, change the value in the installation configuration file that the program generated.
Prerequisites
-
You have the file
install-config.yamlthat was generated by the OpenShift Container Platform installation program
Procedure
-
In a command prompt, browse to the directory that contains
install-config.yaml. From that directory, either run a script to edit the
install-config.yamlfile or update the file manually:To set the value by using a script, run:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
To set the value manually, open the file and set
networking.networkTypeto"Kuryr".
9.4.15. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines and compute machine sets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the machine set files to create compute machines by using the machine API, but you must update references to them to match your environment.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Export the metadata file’s
infraIDkey as an environment variable:export INFRA_ID=$(jq -r .infraID metadata.json)
$ export INFRA_ID=$(jq -r .infraID metadata.json)Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Extract the infraID key from metadata.json and use it as a prefix for all of the RHOSP resources that you create. By doing so, you avoid name conflicts when making multiple deployments in the same project.
9.4.16. Preparing the bootstrap Ignition files
The OpenShift Container Platform installation process relies on bootstrap machines that are created from a bootstrap Ignition configuration file.
Edit the file and upload it. Then, create a secondary bootstrap Ignition configuration file that Red Hat OpenStack Platform (RHOSP) uses to download the primary file.
Prerequisites
-
You have the bootstrap Ignition file that the installer program generates,
bootstrap.ign. The infrastructure ID from the installer’s metadata file is set as an environment variable (
$INFRA_ID).- If the variable is not set, see Creating the Kubernetes manifest and Ignition config files.
You have an HTTP(S)-accessible way to store the bootstrap Ignition file.
- The documented procedure uses the RHOSP image service (Glance), but you can also use the RHOSP storage service (Swift), Amazon S3, an internal HTTP server, or an ad hoc Nova server.
Procedure
Run the following Python script. The script modifies the bootstrap Ignition file to set the hostname and, if available, CA certificate file when it runs:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the RHOSP CLI, create an image that uses the bootstrap Ignition file:
openstack image create --disk-format=raw --container-format=bare --file bootstrap.ign <image_name>
$ openstack image create --disk-format=raw --container-format=bare --file bootstrap.ign <image_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Get the image’s details:
openstack image show <image_name>
$ openstack image show <image_name>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Make a note of the
filevalue; it follows the patternv2/images/<image_ID>/file.NoteVerify that the image you created is active.
Retrieve the image service’s public address:
openstack catalog show image
$ openstack catalog show imageCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Combine the public address with the image
filevalue and save the result as the storage location. The location follows the pattern<image_service_public_URL>/v2/images/<image_ID>/file. Generate an auth token and save the token ID:
openstack token issue -c id -f value
$ openstack token issue -c id -f valueCopy to Clipboard Copied! Toggle word wrap Toggle overflow Insert the following content into a file called
$INFRA_ID-bootstrap-ignition.jsonand edit the placeholders to match your own values:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace the value of
ignition.config.merge.sourcewith the bootstrap Ignition file storage URL. - 2
- Set
nameinhttpHeadersto"X-Auth-Token". - 3
- Set
valueinhttpHeadersto your token’s ID. - 4
- If the bootstrap Ignition file server uses a self-signed certificate, include the base64-encoded certificate.
- Save the secondary Ignition config file.
The bootstrap Ignition data will be passed to RHOSP during installation.
The bootstrap Ignition file contains sensitive information, like clouds.yaml credentials. Ensure that you store it in a secure place, and delete it after you complete the installation process.
9.4.17. Creating control plane Ignition config files on RHOSP
Installing OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) on your own infrastructure requires control plane Ignition config files. You must create multiple config files.
As with the bootstrap Ignition configuration, you must explicitly define a hostname for each control plane machine.
Prerequisites
The infrastructure ID from the installation program’s metadata file is set as an environment variable (
$INFRA_ID).- If the variable is not set, see "Creating the Kubernetes manifest and Ignition config files."
Procedure
On a command line, run the following Python script:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You now have three control plane Ignition files:
<INFRA_ID>-master-0-ignition.json,<INFRA_ID>-master-1-ignition.json, and<INFRA_ID>-master-2-ignition.json.
9.4.18. Creating network resources on RHOSP
Create the network resources that an OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) installation on your own infrastructure requires. To save time, run supplied Ansible playbooks that generate security groups, networks, subnets, routers, and ports.
Prerequisites
- Python 3 is installed on your machine.
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
Procedure
Optional: Add an external network value to the
inventory.yamlplaybook:Example external network value in the
inventory.yamlAnsible playbookCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you did not provide a value for
os_external_networkin theinventory.yamlfile, you must ensure that VMs can access Glance and an external connection yourself.Optional: Add external network and floating IP (FIP) address values to the
inventory.yamlplaybook:Example FIP values in the
inventory.yamlAnsible playbookCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you do not define values for
os_api_fipandos_ingress_fip, you must perform post-installation network configuration.If you do not define a value for
os_bootstrap_fip, the installer cannot download debugging information from failed installations.See "Enabling access to the environment" for more information.
On a command line, create security groups by running the
security-groups.yamlplaybook:ansible-playbook -i inventory.yaml security-groups.yaml
$ ansible-playbook -i inventory.yaml security-groups.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow On a command line, create a network, subnet, and router by running the
network.yamlplaybook:ansible-playbook -i inventory.yaml network.yaml
$ ansible-playbook -i inventory.yaml network.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Optional: If you want to control the default resolvers that Nova servers use, run the RHOSP CLI command:
openstack subnet set --dns-nameserver <server_1> --dns-nameserver <server_2> "$INFRA_ID-nodes"
$ openstack subnet set --dns-nameserver <server_1> --dns-nameserver <server_2> "$INFRA_ID-nodes"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.19. Creating the bootstrap machine on RHOSP
Create a bootstrap machine and give it the network access it needs to run on Red Hat OpenStack Platform (RHOSP). Red Hat provides an Ansible playbook that you run to simplify this process.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The
inventory.yaml,common.yaml, andbootstrap.yamlAnsible playbooks are in a common directory. -
The
metadata.jsonfile that the installation program created is in the same directory as the Ansible playbooks.
Procedure
- On a command line, change the working directory to the location of the playbooks.
On a command line, run the
bootstrap.yamlplaybook:ansible-playbook -i inventory.yaml bootstrap.yaml
$ ansible-playbook -i inventory.yaml bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow After the bootstrap server is active, view the logs to verify that the Ignition files were received:
openstack console log show "$INFRA_ID-bootstrap"
$ openstack console log show "$INFRA_ID-bootstrap"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.20. Creating the control plane machines on RHOSP
Create three control plane machines by using the Ignition config files that you generated. Red Hat provides an Ansible playbook that you run to simplify this process.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The infrastructure ID from the installation program’s metadata file is set as an environment variable (
$INFRA_ID). -
The
inventory.yaml,common.yaml, andcontrol-plane.yamlAnsible playbooks are in a common directory. - You have the three Ignition files that were created in "Creating control plane Ignition config files."
Procedure
- On a command line, change the working directory to the location of the playbooks.
- If the control plane Ignition config files aren’t already in your working directory, copy them into it.
On a command line, run the
control-plane.yamlplaybook:ansible-playbook -i inventory.yaml control-plane.yaml
$ ansible-playbook -i inventory.yaml control-plane.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to monitor the bootstrapping process:
openshift-install wait-for bootstrap-complete
$ openshift-install wait-for bootstrap-completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow You will see messages that confirm that the control plane machines are running and have joined the cluster:
INFO API v1.14.6+f9b5405 up INFO Waiting up to 30m0s for bootstrapping to complete... ... INFO It is now safe to remove the bootstrap resources
INFO API v1.14.6+f9b5405 up INFO Waiting up to 30m0s for bootstrapping to complete... ... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.21. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.4.22. Deleting bootstrap resources from RHOSP
Delete the bootstrap resources that you no longer need.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The
inventory.yaml,common.yaml, anddown-bootstrap.yamlAnsible playbooks are in a common directory. The control plane machines are running.
- If you do not know the status of the machines, see "Verifying cluster status."
Procedure
- On a command line, change the working directory to the location of the playbooks.
On a command line, run the
down-bootstrap.yamlplaybook:ansible-playbook -i inventory.yaml down-bootstrap.yaml
$ ansible-playbook -i inventory.yaml down-bootstrap.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The bootstrap port, server, and floating IP address are deleted.
If you did not disable the bootstrap Ignition file URL earlier, do so now.
9.4.23. Creating compute machines on RHOSP
After standing up the control plane, create compute machines. Red Hat provides an Ansible playbook that you run to simplify this process.
Prerequisites
- You downloaded the modules in "Downloading playbook dependencies."
- You downloaded the playbooks in "Downloading the installation playbooks."
-
The
inventory.yaml,common.yaml, andcompute-nodes.yamlAnsible playbooks are in a common directory. -
The
metadata.jsonfile that the installation program created is in the same directory as the Ansible playbooks. - The control plane is active.
Procedure
- On a command line, change the working directory to the location of the playbooks.
On a command line, run the playbook:
ansible-playbook -i inventory.yaml compute-nodes.yaml
$ ansible-playbook -i inventory.yaml compute-nodes.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Approve the certificate signing requests for the machines.
9.4.24. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
9.4.25. Verifying a successful installation
Verify that the OpenShift Container Platform installation is complete.
Prerequisites
-
You have the installation program (
openshift-install)
Procedure
On a command line, enter:
openshift-install --log-level debug wait-for install-complete
$ openshift-install --log-level debug wait-for install-completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow
The program outputs the console URL, as well as the administrator’s login information.
9.4.26. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
9.4.27. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- If you need to enable external access to node ports, configure ingress cluster traffic by using a node port.
- If you did not configure RHOSP to accept application traffic over floating IP addresses, configure RHOSP access with floating IP addresses.
9.5. Installing a cluster on OpenStack in a restricted network
In OpenShift Container Platform 4.6, you can install a cluster on Red Hat OpenStack Platform (RHOSP) in a restricted network by creating an internal mirror of the installation release content.
Installing in a restricted network is supported only for installer-provisioned installations.
Prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
Review details about the OpenShift Container Platform installation and update processes.
- Verify that OpenShift Container Platform 4.6 is compatible with your RHOSP version by consulting the architecture documentation’s list of available platforms. You can also compare platform support across different versions by viewing the OpenShift Container Platform on RHOSP support matrix.
- Verify that your network configuration does not rely on a provider network. Provider networks are not supported.
- Have the metadata service enabled in RHOSP.
9.5.1. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
9.5.1.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
9.5.2. Resource guidelines for installing OpenShift Container Platform on RHOSP
To support an OpenShift Container Platform installation, your Red Hat OpenStack Platform (RHOSP) quota must meet the following requirements:
| Resource | Value |
|---|---|
| Floating IP addresses | 3 |
| Ports | 15 |
| Routers | 1 |
| Subnets | 1 |
| RAM | 112 GB |
| vCPUs | 28 |
| Volume storage | 275 GB |
| Instances | 7 |
| Security groups | 3 |
| Security group rules | 60 |
A cluster might function with fewer than recommended resources, but its performance is not guaranteed.
If RHOSP object storage (Swift) is available and operated by a user account with the swiftoperator role, it is used as the default backend for the OpenShift Container Platform image registry. In this case, the volume storage requirement is 175 GB. Swift space requirements vary depending on the size of the image registry.
By default, your security group and security group rule quotas might be low. If you encounter problems, run openstack quota set --secgroups 3 --secgroup-rules 60 <project> as an administrator to increase them.
An OpenShift Container Platform deployment comprises control plane machines, compute machines, and a bootstrap machine.
9.5.2.1. Control plane machines
By default, the OpenShift Container Platform installation process creates three control plane machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.5.2.2. Compute machines
By default, the OpenShift Container Platform installation process creates three compute machines.
Each machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 8 GB memory, 2 vCPUs, and 100 GB storage space
Compute machines host the applications that you run on OpenShift Container Platform; aim to run as many as you can.
9.5.2.3. Bootstrap machine
During installation, a bootstrap machine is temporarily provisioned to stand up the control plane. After the production control plane is ready, the bootstrap machine is deprovisioned.
The bootstrap machine requires:
- An instance from the RHOSP quota
- A port from the RHOSP quota
- A flavor with at least 16 GB memory, 4 vCPUs, and 100 GB storage space
9.5.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
9.5.4. Enabling Swift on RHOSP
Swift is operated by a user account with the swiftoperator role. Add the role to an account before you run the installation program.
If the Red Hat OpenStack Platform (RHOSP) object storage service, commonly known as Swift, is available, OpenShift Container Platform uses it as the image registry storage. If it is unavailable, the installation program relies on the RHOSP block storage service, commonly known as Cinder.
If Swift is present and you want to use it, you must enable access to it. If it is not present, or if you do not want to use it, skip this section.
Prerequisites
- You have a RHOSP administrator account on the target environment.
- The Swift service is installed.
-
On Ceph RGW, the
account in urloption is enabled.
Procedure
To enable Swift on RHOSP:
As an administrator in the RHOSP CLI, add the
swiftoperatorrole to the account that will access Swift:openstack role add --user <user> --project <project> swiftoperator
$ openstack role add --user <user> --project <project> swiftoperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Your RHOSP deployment can now use Swift for the image registry.
9.5.5. Defining parameters for the installation program
The OpenShift Container Platform installation program relies on a file that is called clouds.yaml. The file describes Red Hat OpenStack Platform (RHOSP) configuration parameters, including the project name, log in information, and authorization service URLs.
Procedure
Create the
clouds.yamlfile:If your RHOSP distribution includes the Horizon web UI, generate a
clouds.yamlfile in it.ImportantRemember to add a password to the
authfield. You can also keep secrets in a separate file fromclouds.yaml.If your RHOSP distribution does not include the Horizon web UI, or you do not want to use Horizon, create the file yourself. For detailed information about
clouds.yaml, see Config files in the RHOSP documentation.Copy to Clipboard Copied! Toggle word wrap Toggle overflow
If your RHOSP installation uses self-signed certificate authority (CA) certificates for endpoint authentication:
- Copy the certificate authority file to your machine.
Add the machine to the certificate authority trust bundle:
sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/
$ sudo cp ca.crt.pem /etc/pki/ca-trust/source/anchors/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Update the trust bundle:
sudo update-ca-trust extract
$ sudo update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the
cacertskey to theclouds.yamlfile. The value must be an absolute, non-root-accessible path to the CA certificate:clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"clouds: shiftstack: ... cacert: "/etc/pki/ca-trust/source/anchors/ca.crt.pem"Copy to Clipboard Copied! Toggle word wrap Toggle overflow TipAfter you run the installer with a custom CA certificate, you can update the certificate by editing the value of the
ca-cert.pemkey in thecloud-provider-configkeymap. On a command line, run:oc edit configmap -n openshift-config cloud-provider-config
$ oc edit configmap -n openshift-config cloud-provider-configCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Place the
clouds.yamlfile in one of the following locations:-
The value of the
OS_CLIENT_CONFIG_FILEenvironment variable - The current directory
-
A Unix-specific user configuration directory, for example
~/.config/openstack/clouds.yaml A Unix-specific site configuration directory, for example
/etc/openstack/clouds.yamlThe installation program searches for
clouds.yamlin that order.
-
The value of the
9.5.6. Creating the RHCOS image for restricted network installations
Download the Red Hat Enterprise Linux CoreOS (RHCOS) image to install OpenShift Container Platform on a restricted network Red Hat OpenStack Platform (RHOSP) environment.
Prerequisites
- Obtain the OpenShift Container Platform installation program. For a restricted network installation, the program is on your mirror registry host.
Procedure
- Log in to the Red Hat Customer Portal’s Product Downloads page.
Under Version, select the most recent release of OpenShift Container Platform 4.6 for RHEL 8.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available.
- Download the Red Hat Enterprise Linux CoreOS (RHCOS) - OpenStack Image (QCOW) image.
Decompress the image.
NoteYou must decompress the image before the cluster can use it. The name of the downloaded file might not contain a compression extension, like
.gzor.tgz. To find out if or how the file is compressed, in a command line, enter:file <name_of_downloaded_file>
$ file <name_of_downloaded_file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Upload the image that you decompressed to a location that is accessible from the bastion server, like Glance. For example:
openstack image create --file rhcos-44.81.202003110027-0-openstack.x86_64.qcow2 --disk-format qcow2 rhcos-${RHCOS_VERSION}$ openstack image create --file rhcos-44.81.202003110027-0-openstack.x86_64.qcow2 --disk-format qcow2 rhcos-${RHCOS_VERSION}Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantDepending on your RHOSP environment, you might be able to upload the image in either
.rawor.qcow2formats. If you use Ceph, you must use the.rawformat.WarningIf the installation program finds multiple images with the same name, it chooses one of them at random. To avoid this behavior, create unique names for resources in RHOSP.
The image is now available for a restricted installation. Note the image name or location for use in OpenShift Container Platform deployment.
9.5.7. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Red Hat OpenStack Platform (RHOSP).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
Have the
imageContentSourcesvalues that were generated during mirror registry creation. - Obtain the contents of the certificate for your mirror registry.
- Retrieve a Red Hat Enterprise Linux CoreOS (RHCOS) image and upload it to an accessible location.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select openstack as the platform to target.
- Specify the Red Hat OpenStack Platform (RHOSP) external network name to use for installing the cluster.
- Specify the floating IP address to use for external access to the OpenShift API.
- Specify a RHOSP flavor with at least 16 GB RAM to use for control plane nodes and 8 GB RAM for compute nodes.
- Select the base domain to deploy the cluster to. All DNS records will be sub-domains of this base and will also include the cluster name.
- Enter a name for your cluster. The name must be 14 or fewer characters long.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
In the
install-config.yamlfile, set the value ofplatform.openstack.clusterOSImageto the image location or name. For example:platform: openstack: clusterOSImage: http://mirror.example.com/images/rhcos-43.81.201912131630.0-openstack.x86_64.qcow2.gz?sha256=ffebbd68e8a1f2a245ca19522c16c86f67f9ac8e4e0c1f0a812b068b16f7265dplatform: openstack: clusterOSImage: http://mirror.example.com/images/rhcos-43.81.201912131630.0-openstack.x86_64.qcow2.gz?sha256=ffebbd68e8a1f2a245ca19522c16c86f67f9ac8e4e0c1f0a812b068b16f7265dCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<mirror_host_name>, specify the registry domain name that you specified in the certificate for your mirror registry, and for<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.
Add the image content resources, which look like this excerpt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To complete these values, use the
imageContentSourcesthat you recorded during mirror registry creation.
-
Make any other modifications to the
install-config.yamlfile that you require. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
9.5.7.1. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
9.5.7.2. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
9.5.7.2.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
9.5.7.2.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
9.5.7.2.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
9.5.7.2.4. Additional Red Hat OpenStack Platform (RHOSP) configuration parameters
Additional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| For compute machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For compute machines, the root volume’s type. |
String, for example |
|
| For control plane machines, the size in gigabytes of the root volume. If you do not set this value, machines use ephemeral storage. |
Integer, for example |
|
| For control plane machines, the root volume’s type. |
String, for example |
|
|
The name of the RHOSP cloud to use from the list of clouds in the |
String, for example |
|
| The RHOSP external network name to be used for installation. |
String, for example |
|
| The RHOSP flavor to use for control plane and compute machines. |
String, for example |
9.5.7.2.5. Optional RHOSP configuration parameters
Optional RHOSP configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Additional networks that are associated with compute machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with compute machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| Additional networks that are associated with control plane machines. Allowed address pairs are not created for additional networks. |
A list of one or more UUIDs as strings. For example, |
|
| Additional security groups that are associated with control plane machines. |
A list of one or more UUIDs as strings. For example, |
|
| RHOSP Compute (Nova) availability zones (AZs) to install machines on. If this parameter is not set, the installer relies on the default settings for Nova that the RHOSP administrator configured. On clusters that use Kuryr, RHOSP Octavia does not support availability zones. Load balancers and, if you are using the Amphora provider driver, OpenShift Container Platform services that rely on Amphora VMs, are not created according to the value of this property. |
A list of strings. For example, |
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. | An HTTP or HTTPS URL, optionally with an SHA-256 checksum.
For example, |
|
| The default machine pool platform configuration. |
|
|
|
An existing floating IP address to associate with the Ingress port. To use this property, you must also define the |
An IP address, for example |
|
|
An existing floating IP address to associate with the API load balancer. To use this property, you must also define the |
An IP address, for example |
|
| IP addresses for external DNS servers that cluster instances use for DNS resolution. |
A list of IP addresses as strings. For example, |
|
| The UUID of a RHOSP subnet that the cluster’s nodes use. Nodes and virtual IP (VIP) ports are created on this subnet.
The first item in If you deploy to a custom subnet, you cannot specify an external DNS server to the OpenShift Container Platform installer. Instead, add DNS to the subnet in RHOSP. |
A UUID as a string. For example, |
9.5.7.3. Sample customized install-config.yaml file for restricted OpenStack installations
This sample install-config.yaml demonstrates all of the possible Red Hat OpenStack Platform (RHOSP) customization options.
This sample file is provided for reference only. You must obtain your install-config.yaml file by using the installation program.
9.5.8. Setting compute machine affinity
Optionally, you can set the affinity policy for compute machines during installation. The installer does not select an affinity policy for compute machines by default.
You can also create machine sets that use particular RHOSP server groups after installation.
Control plane machines are created with a soft-anti-affinity policy.
You can learn more about RHOSP instance scheduling and placement in the RHOSP documentation.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Using the RHOSP command-line interface, create a server group for your compute machines. For example:
openstack \ --os-compute-api-version=2.15 \ server group create \ --policy anti-affinity \ my-openshift-worker-group$ openstack \ --os-compute-api-version=2.15 \ server group create \ --policy anti-affinity \ my-openshift-worker-groupCopy to Clipboard Copied! Toggle word wrap Toggle overflow For more information, see the
server group createcommand documentation.Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir=<installation_directory>
$ ./openshift-install create manifests --dir=<installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
installation_directory-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
-
Open
manifests/99_openshift-cluster-api_worker-machineset-0.yaml, theMachineSetdefinition file. Add the property
serverGroupIDto the definition beneath thespec.template.spec.providerSpec.valueproperty. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Add the UUID of your server group here.
-
Optional: Back up the
manifests/99_openshift-cluster-api_worker-machineset-0.yamlfile. The installation program deletes themanifests/directory when creating the cluster.
When you install the cluster, the installer uses the MachineSet definition that you modified to create compute machines within your RHOSP server group.
9.5.9. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
9.5.10. Enabling access to the environment
At deployment, all OpenShift Container Platform machines are created in a Red Hat OpenStack Platform (RHOSP)-tenant network. Therefore, they are not accessible directly in most RHOSP deployments.
You can configure OpenShift Container Platform API and application access by using floating IP addresses (FIPs) during installation. You can also complete an installation without configuring FIPs, but the installer will not configure a way to reach the API or applications externally.
9.5.10.1. Enabling access with floating IP addresses
Create floating IP (FIP) addresses for external access to the OpenShift Container Platform API and cluster applications.
Procedure
Using the Red Hat OpenStack Platform (RHOSP) CLI, create the API FIP:
openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "API <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Using the Red Hat OpenStack Platform (RHOSP) CLI, create the apps, or Ingress, FIP:
openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>
$ openstack floating ip create --description "Ingress <cluster_name>.<base_domain>" <external_network>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add records that follow these patterns to your DNS server for the API and Ingress FIPs:
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>
api.<cluster_name>.<base_domain>. IN A <API_FIP> *.apps.<cluster_name>.<base_domain>. IN A <apps_FIP>Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you do not control the DNS server, you can access the cluster by adding the cluster domain names such as the following to your
/etc/hostsfile:-
<api_floating_ip> api.<cluster_name>.<base_domain> -
<application_floating_ip> grafana-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> prometheus-k8s-openshift-monitoring.apps.<cluster_name>.<base_domain> -
<application_floating_ip> oauth-openshift.apps.<cluster_name>.<base_domain> -
<application_floating_ip> console-openshift-console.apps.<cluster_name>.<base_domain> -
application_floating_ip integrated-oauth-server-openshift-authentication.apps.<cluster_name>.<base_domain>
The cluster domain names in the
/etc/hostsfile grant access to the web console and the monitoring interface of your cluster locally. You can also use thekubectloroc. You can access the user applications by using the additional entries pointing to the <application_floating_ip>. This action makes the API and applications accessible to only you, which is not suitable for production deployment, but does allow installation for development and testing.-
Add the FIPs to the
install-config.yamlfile as the values of the following parameters:-
platform.openstack.ingressFloatingIP -
platform.openstack.lbFloatingIP
-
If you use these values, you must also enter an external network as the value of the platform.openstack.externalNetwork parameter in the install-config.yaml file.
You can make OpenShift Container Platform resources available outside of the cluster by assigning a floating IP address and updating your firewall configuration.
9.5.10.2. Completing installation without floating IP addresses
You can install OpenShift Container Platform on Red Hat OpenStack Platform (RHOSP) without providing floating IP addresses.
In the install-config.yaml file, do not define the following parameters:
-
platform.openstack.ingressFloatingIP -
platform.openstack.lbFloatingIP
If you cannot provide an external network, you can also leave platform.openstack.externalNetwork blank. If you do not provide a value for platform.openstack.externalNetwork, a router is not created for you, and, without additional action, the installer will fail to retrieve an image from Glance. You must configure external connectivity on your own.
If you run the installer from a system that cannot reach the cluster API due to a lack of floating IP addresses or name resolution, installation fails. To prevent installation failure in these cases, you can use a proxy network or run the installer from a system that is on the same network as your machines.
You can enable name resolution by creating DNS records for the API and Ingress ports. For example:
api.<cluster_name>.<base_domain>. IN A <api_port_IP> *.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
api.<cluster_name>.<base_domain>. IN A <api_port_IP>
*.apps.<cluster_name>.<base_domain>. IN A <ingress_port_IP>
If you do not control the DNS server, you can add the record to your /etc/hosts file. This action makes the API accessible to only you, which is not suitable for production deployment but does allow installation for development and testing.
9.5.11. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
9.5.12. Verifying cluster status
You can verify your OpenShift Container Platform cluster’s status during or after installation.
Procedure
In the cluster environment, export the administrator’s kubeconfig file:
export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
The
kubeconfigfile contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server.View the control plane and compute machines created after a deployment:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your cluster’s version:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your Operators' status:
oc get clusteroperator
$ oc get clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow View all running pods in the cluster:
oc get pods -A
$ oc get pods -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.5.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
9.5.14. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
9.5.15. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
9.5.16. Next steps
- Customize your cluster.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If you did not configure RHOSP to accept application traffic over floating IP addresses, configure RHOSP access with floating IP addresses.
9.6. Uninstalling a cluster on OpenStack
You can remove a cluster that you deployed to Red Hat OpenStack Platform (RHOSP).
9.6.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
9.7. Uninstalling a cluster on RHOSP from your own infrastructure
You can remove a cluster that you deployed to Red Hat OpenStack Platform (RHOSP) on user-provisioned infrastructure.
9.7.1. Downloading playbook dependencies
The Ansible playbooks that simplify the removal process on user-provisioned infrastructure require several Python modules. On the machine where you will run the process, add the modules' repositories and then download them.
These instructions assume that you are using Red Hat Enterprise Linux (RHEL) 8.
Prerequisites
- Python 3 is installed on your machine.
Procedure
On a command line, add the repositories:
Register with Red Hat Subscription Manager:
sudo subscription-manager register # If not done already
$ sudo subscription-manager register # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Pull the latest subscription data:
sudo subscription-manager attach --pool=$YOUR_POOLID # If not done already
$ sudo subscription-manager attach --pool=$YOUR_POOLID # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Disable the current repositories:
sudo subscription-manager repos --disable=* # If not done already
$ sudo subscription-manager repos --disable=* # If not done alreadyCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the required repositories:
sudo subscription-manager repos \ --enable=rhel-8-for-x86_64-baseos-rpms \ --enable=openstack-16-tools-for-rhel-8-x86_64-rpms \ --enable=ansible-2.9-for-rhel-8-x86_64-rpms \ --enable=rhel-8-for-x86_64-appstream-rpms
$ sudo subscription-manager repos \ --enable=rhel-8-for-x86_64-baseos-rpms \ --enable=openstack-16-tools-for-rhel-8-x86_64-rpms \ --enable=ansible-2.9-for-rhel-8-x86_64-rpms \ --enable=rhel-8-for-x86_64-appstream-rpmsCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Install the modules:
sudo yum install python3-openstackclient ansible python3-openstacksdk
$ sudo yum install python3-openstackclient ansible python3-openstacksdkCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that the
pythoncommand points topython3:sudo alternatives --set python /usr/bin/python3
$ sudo alternatives --set python /usr/bin/python3Copy to Clipboard Copied! Toggle word wrap Toggle overflow
9.7.2. Removing a cluster from RHOSP that uses your own infrastructure
You can remove an OpenShift Container Platform cluster on Red Hat OpenStack Platform (RHOSP) that uses your own infrastructure. To complete the removal process quickly, run several Ansible playbooks.
Prerequisites
- Python 3 is installed on your machine.
- You downloaded the modules in "Downloading playbook dependencies."
- You have the playbooks that you used to install the cluster.
-
You modified the playbooks that are prefixed with
down-to reflect any changes that you made to their corresponding installation playbooks. For example, changes to thebootstrap.yamlfile are reflected in thedown-bootstrap.yamlfile. - All of the playbooks are in a common directory.
Procedure
On a command line, run the playbooks that you downloaded:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Remove any DNS record changes you made for the OpenShift Container Platform installation.
OpenShift Container Platform is removed from your infrastructure.
Chapter 10. Installing on RHV
10.1. Installing a cluster quickly on RHV
You can quickly install a default, non-customized, OpenShift Container Platform cluster on a Red Hat Virtualization (RHV) cluster, similar to the one shown in the following diagram.
The installation program uses installer-provisioned infrastructure to automate creating and deploying the cluster.
To install a default cluster, you prepare the environment, run the installation program and answer its prompts. Then, the installation program creates the OpenShift Container Platform cluster.
For an alternative to installing a default cluster, see Installing a cluster with customizations.
This installation program is available for Linux and macOS only.
10.1.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- You have a supported combination of versions in the Support Matrix for OpenShift Container Platform on Red Hat Virtualization (RHV).
- If you use a firewall, configure it to allow the sites that your cluster requires access to.
10.1.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
10.1.3. Requirements for the RHV environment
To install and run an OpenShift Container Platform cluster, the RHV environment must meet the following requirements.
Not meeting these requirements can cause the installation or process to fail. Additionally, not meeting these requirements can cause the OpenShift Container Platform cluster to fail days or weeks after installation.
The following requirements for CPU, memory, and storage resources are based on default values multiplied by the default number of virtual machines the installation program creates. These resources must be available in addition to what the RHV environment uses for non-OpenShift Container Platform operations.
By default, the installation program creates seven virtual machines during the installation process. First, it creates a bootstrap virtual machine to provide temporary services and a control plane while it creates the rest of the OpenShift Container Platform cluster. When the installation program finishes creating the cluster, deleting the bootstrap machine frees up its resources.
If you increase the number of virtual machines in the RHV environment, you must increase the resources accordingly.
Requirements
- The RHV environment has one data center whose state is Up.
- The RHV data center contains an RHV cluster.
The RHV cluster has the following resources exclusively for the OpenShift Container Platform cluster:
- Minimum 28 vCPUs: four for each of the seven virtual machines created during installation.
112 GiB RAM or more, including:
- 16 GiB or more for the bootstrap machine, which provides the temporary control plane.
- 16 GiB or more for each of the three control plane machines which provide the control plane.
- 16 GiB or more for each of the three compute machines, which run the application workloads.
- The RHV storage domain must meet these etcd backend performance requirements.
- In production environments, each virtual machine must have 120 GiB or more. Therefore, the storage domain must provide 840 GiB or more for the default OpenShift Container Platform cluster. In resource-constrained or non-production environments, each virtual machine must have 32 GiB or more, so the storage domain must have 230 GiB or more for the default OpenShift Container Platform cluster.
- To download images from the Red Hat Ecosystem Catalog during installation and update procedures, the RHV cluster must have access to an internet connection. The Telemetry service also needs an internet connection to simplify the subscription and entitlement process.
- The RHV cluster must have a virtual network with access to the REST API on the RHV Manager. Ensure that DHCP is enabled on this network, because the VMs that the installer creates obtain their IP address by using DHCP.
A user account and group with the following least privileges for installing and managing an OpenShift Container Platform cluster on the target RHV cluster:
-
DiskOperator -
DiskCreator -
UserTemplateBasedVm -
TemplateOwner -
TemplateCreator -
ClusterAdminon the target cluster
-
Apply the principle of least privilege: Avoid using an administrator account with SuperUser privileges on RHV during the installation process. The installation program saves the credentials you provide to a temporary ovirt-config.yaml file that might be compromised.
10.1.4. Verifying the requirements for the RHV environment
Verify that the RHV environment meets the requirements to install and run an OpenShift Container Platform cluster. Not meeting these requirements can cause failures.
These requirements are based on the default resources the installation program uses to create control plane and compute machines. These resources include vCPUs, memory, and storage. If you change these resources or increase the number of OpenShift Container Platform machines, adjust these requirements accordingly.
Procedure
Check the RHV version.
- In the RHV Administration Portal, click the ? help icon in the upper-right corner and select About.
- In the window that opens, make a note of the RHV Software Version.
- Confirm that version 4.6 of OpenShift Container Platform and the version of RHV you noted are one of the supported combinations in the Support Matrix for OpenShift Container Platform on RHV.
Inspect the data center, cluster, and storage.
- In the RHV Administration Portal, click Compute → Data Centers.
- Confirm that the data center where you plan to install OpenShift Container Platform is accessible.
- Click the name of that data center.
- In the data center details, on the Storage tab, confirm the storage domain where you plan to install OpenShift Container Platform is Active.
- Record the Domain Name for use later on.
- Confirm Free Space has at least 230 GiB.
- Confirm that the storage domain meets these etcd backend performance requirements, which you can measure by using the fio performance benchmarking tool.
- In the data center details, click the Clusters tab.
- Find the RHV cluster where you plan to install OpenShift Container Platform. Record the cluster name for use later on.
Inspect the RHV host resources.
- In the RHV Administration Portal, click Compute > Clusters.
- Click the cluster where you plan to install OpenShift Container Platform.
- In the cluster details, click the Hosts tab.
- Inspect the hosts and confirm they have a combined total of at least 28 Logical CPU Cores available exclusively for the OpenShift Container Platform cluster.
- Record the number of available Logical CPU Cores for use later on.
- Confirm that these CPU cores are distributed so that each of the seven virtual machines created during installation can have four cores.
Confirm that, all together, the hosts have 112 GiB of Max free Memory for scheduling new virtual machines distributed to meet the requirements for each of the following OpenShift Container Platform machines:
- 16 GiB required for the bootstrap machine
- 16 GiB required for each of the three control plane machines
- 16 GiB for each of the three compute machines
- Record the amount of Max free Memory for scheduling new virtual machines for use later on.
Verify that the virtual network for installing OpenShift Container Platform has access to the RHV Manager’s REST API. From a virtual machine on this network, use curl to reach the RHV Manager’s REST API:
curl -k -u <username>@<profile>:<password> \ https://<engine-fqdn>/ovirt-engine/api
$ curl -k -u <username>@<profile>:<password> \1 https://<engine-fqdn>/ovirt-engine/api2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<username>, specify the user name of an RHV account with privileges to create and manage an OpenShift Container Platform cluster on RHV. For<profile>, specify the login profile, which you can get by going to the RHV Administration Portal login page and reviewing the Profile dropdown list. For<password>, specify the password for that user name. - 2
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV environment.
For example:
curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/api
$ curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.1.5. Preparing the network environment on RHV
Configure two static IP addresses for the OpenShift Container Platform cluster and create DNS entries using these addresses.
Procedure
Reserve two static IP addresses
- On the network where you plan to install OpenShift Container Platform, identify two static IP addresses that are outside the DHCP lease pool.
Connect to a host on this network and verify that each of the IP addresses is not in use. For example, use Address Resolution Protocol (ARP) to check that none of the IP addresses have entries:
arp 10.35.1.19
$ arp 10.35.1.19Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
10.35.1.19 (10.35.1.19) -- no entry
10.35.1.19 (10.35.1.19) -- no entryCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reserve two static IP addresses following the standard practices for your network environment.
- Record these IP addresses for future reference.
Create DNS entries for the OpenShift Container Platform REST API and apps domain names using this format:
api.<cluster-name>.<base-domain> <ip-address> *.apps.<cluster-name>.<base-domain> <ip-address>
api.<cluster-name>.<base-domain> <ip-address>1 *.apps.<cluster-name>.<base-domain> <ip-address>2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example:
api.my-cluster.virtlab.example.com 10.35.1.19 *.apps.my-cluster.virtlab.example.com 10.35.1.20
api.my-cluster.virtlab.example.com 10.35.1.19 *.apps.my-cluster.virtlab.example.com 10.35.1.20Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.1.6. Setting up the CA certificate for RHV
Download the CA certificate from the Red Hat Virtualization (RHV) Manager and set it up on the installation machine.
You can download the certificate from a webpage on the RHV Manager or by using a curl command.
Later, you provide the certificate to the installation program.
Procedure
Use either of these two methods to download the CA certificate:
-
Go to the Manager’s webpage,
https://<engine-fqdn>/ovirt-engine/. Then, under Downloads, click the CA Certificate link. Run the following command:
curl -k 'https://<engine-fqdn>/ovirt-engine/services/pki-resource?resource=ca-certificate&format=X509-PEM-CA' -o /tmp/ca.pem
$ curl -k 'https://<engine-fqdn>/ovirt-engine/services/pki-resource?resource=ca-certificate&format=X509-PEM-CA' -o /tmp/ca.pem1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV Manager, such asrhv-env.virtlab.example.com.
-
Go to the Manager’s webpage,
Configure the CA file to grant rootless user access to the Manager. Set the CA file permissions to have an octal value of
0644(symbolic value:-rw-r—r--):sudo chmod 0644 /tmp/ca.pem
$ sudo chmod 0644 /tmp/ca.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow For Linux, copy the CA certificate to the directory for server certificates. Use
-pto preserve the permissions:sudo cp -p /tmp/ca.pem /etc/pki/ca-trust/source/anchors/ca.pem
$ sudo cp -p /tmp/ca.pem /etc/pki/ca-trust/source/anchors/ca.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the certificate to the certificate manager for your operating system:
- For macOS, double-click the certificate file and use the Keychain Access utility to add the file to the System keychain.
For Linux, update the CA trust:
sudo update-ca-trust
$ sudo update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you use your own certificate authority, make sure the system trusts it.
10.1.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
10.1.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
10.1.9. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
-
Open the
ovirt-imageioport to the Manager from the machine running the installer. By default, the port is54322. - Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Respond to the installation program prompts.
Optional: For
SSH Public Key, select a password-less public key, such as~/.ssh/id_rsa.pub. This key authenticates connections with the new OpenShift Container Platform cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, select an SSH key that your
ssh-agentprocess uses.-
For
Platform, selectovirt. For
Engine FQDN[:PORT], enter the fully qualified domain name (FQDN) of the RHV environment.For example:
rhv-env.virtlab.example.com:443
rhv-env.virtlab.example.com:443Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
The installer automatically generates a CA certificate. For
Would you like to use the above certificate to connect to the Manager?, answeryorN. If you answerN, you must install OpenShift Container Platform in insecure mode. For
Engine username, enter the user name and profile of the RHV administrator using this format:<username>@<profile>
<username>@<profile>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<username>, specify the user name of an RHV administrator. For<profile>, specify the login profile, which you can get by going to the RHV Administration Portal login page and reviewing the Profile dropdown list. For example:admin@internal.
-
For
Engine password, enter the RHV admin password. -
For
Cluster, select the RHV cluster for installing OpenShift Container Platform. -
For
Storage domain, select the storage domain for installing OpenShift Container Platform. -
For
Network, select a virtual network that has access to the RHV Manager REST API. -
For
Internal API Virtual IP, enter the static IP address you set aside for the cluster’s REST API. -
For
Ingress virtual IP, enter the static IP address you reserved for the wildcard apps domain. -
For
Base Domain, enter the base domain of the OpenShift Container Platform cluster. If this cluster is exposed to the outside world, this must be a valid domain recognized by DNS infrastructure. For example, enter:virtlab.example.com -
For
Cluster Name, enter the name of the cluster. For example,my-cluster. Use cluster name from the externally registered/resolvable DNS entries you created for the OpenShift Container Platform REST API and apps domain names. The installation program also gives this name to the cluster in the RHV environment. -
For
Pull Secret, copy the pull secret from thepull-secret.txtfile you downloaded earlier and paste it here. You can also get a copy of the same pull secret from the Red Hat OpenShift Cluster Manager.
NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
You have completed the steps required to install the cluster. The remaining steps show you how to verify the cluster and troubleshoot the installation.
10.1.10. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
10.1.10.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>10.1.10.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>10.1.10.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>To learn more, see Getting started with the OpenShift CLI.
10.1.11. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.1.12. Verifying cluster status
You can verify your OpenShift Container Platform cluster’s status during or after installation.
Procedure
In the cluster environment, export the administrator’s kubeconfig file:
export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
The
kubeconfigfile contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server.View the control plane and compute machines created after a deployment:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your cluster’s version:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your Operators' status:
oc get clusteroperator
$ oc get clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow View all running pods in the cluster:
oc get pods -A
$ oc get pods -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting
If the installation fails, the installation program times out and displays an error message. To learn more, see Troubleshooting installation issues.
10.1.13. Accessing the OpenShift Container Platform web console on RHV
After the OpenShift Container Platform cluster initializes, you can log in to the OpenShift Container Platform web console.
Procedure
- Optional: In the Red Hat Virtualization (RHV) Administration Portal, open Compute → Cluster.
- Verify that the installation program creates the virtual machines.
- Return to the command line where the installation program is running. When the installation program finishes, it displays the user name and temporary password for logging into the OpenShift Container Platform web console.
In a browser, open the URL of the OpenShift Container Platform web console. The URL uses this format:
console-openshift-console.apps.<clustername>.<basedomain>
console-openshift-console.apps.<clustername>.<basedomain>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<clustername>.<basedomain>, specify the cluster name and base domain.
For example:
console-openshift-console.apps.my-cluster.virtlab.example.com
console-openshift-console.apps.my-cluster.virtlab.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.1.14. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
10.1.15. Troubleshooting common issues with installing on Red Hat Virtualization (RHV)
Here are some common issues you might encounter, along with proposed causes and solutions.
10.1.15.1. CPU load increases and nodes go into a Not Ready state
-
Symptom: CPU load increases significantly and nodes start going into a
Not Readystate. - Cause: The storage domain latency might be too high, especially for control plane nodes (also known as the master nodes).
Solution:
Make the nodes ready again by restarting the kubelet service:
systemctl restart kubelet
$ systemctl restart kubeletCopy to Clipboard Copied! Toggle word wrap Toggle overflow Inspect the OpenShift Container Platform metrics service, which automatically gathers and reports on some valuable data such as the etcd disk sync duration. If the cluster is operational, use this data to help determine whether storage latency or throughput is the root issue. If so, consider using a storage resource that has lower latency and higher throughput.
To get raw metrics, enter the following command as kubeadmin or user with cluster-admin privileges:
oc get --insecure-skip-tls-verify --server=https://localhost:<port> --raw=/metrics
$ oc get --insecure-skip-tls-verify --server=https://localhost:<port> --raw=/metricsCopy to Clipboard Copied! Toggle word wrap Toggle overflow To learn more, see Exploring Application Endpoints for the purposes of Debugging with OpenShift 4.x
10.1.15.2. Trouble connecting the OpenShift Container Platform cluster API
Symptom: The installation program completes but the OpenShift Container Platform cluster API is not available. The bootstrap virtual machine remains up after the bootstrap process is complete. When you enter the following command, the response will time out.
oc login -u kubeadmin -p *** <apiurl>
$ oc login -u kubeadmin -p *** <apiurl>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Cause: The bootstrap VM was not deleted by the installation program and has not released the cluster’s API IP address.
Solution: Use the
wait-forsubcommand to be notified when the bootstrap process is complete:./openshift-install wait-for bootstrap-complete
$ ./openshift-install wait-for bootstrap-completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow When the bootstrap process is complete, delete the bootstrap virtual machine:
./openshift-install destroy bootstrap
$ ./openshift-install destroy bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.1.16. Post-installation tasks
After the OpenShift Container Platform cluster initializes, you can perform the following tasks.
- Optional: After deployment, add or replace SSH keys using the Machine Config Operator (MCO) in OpenShift Container Platform.
-
Optional: Remove the
kubeadminuser. Instead, use the authentication provider to create a user with cluster-admin privileges.
10.2. Installing a cluster on RHV with customizations
You can customize and install an OpenShift Container Platform cluster on Red Hat Virtualization (RHV), similar to the one shown in the following diagram.
The installation program uses installer-provisioned infrastructure to automate creating and deploying the cluster.
To install a customized cluster, you prepare the environment and perform the following steps:
-
Create an installation configuration file, the
install-config.yamlfile, by running the installation program and answering its prompts. -
Inspect and modify parameters in the
install-config.yamlfile. -
Make a working copy of the
install-config.yamlfile. -
Run the installation program with a copy of the
install-config.yamlfile.
Then, the installation program creates the OpenShift Container Platform cluster.
For an alternative to installing a customized cluster, see Installing a default cluster.
This installation program is available for Linux and macOS only.
10.2.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- You have a supported combination of versions in the Support Matrix for OpenShift Container Platform on Red Hat Virtualization (RHV).
- If you use a firewall, configure it to allow the sites that your cluster requires access to.
10.2.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
10.2.3. Requirements for the RHV environment
To install and run an OpenShift Container Platform cluster, the RHV environment must meet the following requirements.
Not meeting these requirements can cause the installation or process to fail. Additionally, not meeting these requirements can cause the OpenShift Container Platform cluster to fail days or weeks after installation.
The following requirements for CPU, memory, and storage resources are based on default values multiplied by the default number of virtual machines the installation program creates. These resources must be available in addition to what the RHV environment uses for non-OpenShift Container Platform operations.
By default, the installation program creates seven virtual machines during the installation process. First, it creates a bootstrap virtual machine to provide temporary services and a control plane while it creates the rest of the OpenShift Container Platform cluster. When the installation program finishes creating the cluster, deleting the bootstrap machine frees up its resources.
If you increase the number of virtual machines in the RHV environment, you must increase the resources accordingly.
Requirements
- The RHV environment has one data center whose state is Up.
- The RHV data center contains an RHV cluster.
The RHV cluster has the following resources exclusively for the OpenShift Container Platform cluster:
- Minimum 28 vCPUs: four for each of the seven virtual machines created during installation.
112 GiB RAM or more, including:
- 16 GiB or more for the bootstrap machine, which provides the temporary control plane.
- 16 GiB or more for each of the three control plane machines which provide the control plane.
- 16 GiB or more for each of the three compute machines, which run the application workloads.
- The RHV storage domain must meet these etcd backend performance requirements.
- In production environments, each virtual machine must have 120 GiB or more. Therefore, the storage domain must provide 840 GiB or more for the default OpenShift Container Platform cluster. In resource-constrained or non-production environments, each virtual machine must have 32 GiB or more, so the storage domain must have 230 GiB or more for the default OpenShift Container Platform cluster.
- To download images from the Red Hat Ecosystem Catalog during installation and update procedures, the RHV cluster must have access to an internet connection. The Telemetry service also needs an internet connection to simplify the subscription and entitlement process.
- The RHV cluster must have a virtual network with access to the REST API on the RHV Manager. Ensure that DHCP is enabled on this network, because the VMs that the installer creates obtain their IP address by using DHCP.
A user account and group with the following least privileges for installing and managing an OpenShift Container Platform cluster on the target RHV cluster:
-
DiskOperator -
DiskCreator -
UserTemplateBasedVm -
TemplateOwner -
TemplateCreator -
ClusterAdminon the target cluster
-
Apply the principle of least privilege: Avoid using an administrator account with SuperUser privileges on RHV during the installation process. The installation program saves the credentials you provide to a temporary ovirt-config.yaml file that might be compromised.
10.2.4. Verifying the requirements for the RHV environment
Verify that the RHV environment meets the requirements to install and run an OpenShift Container Platform cluster. Not meeting these requirements can cause failures.
These requirements are based on the default resources the installation program uses to create control plane and compute machines. These resources include vCPUs, memory, and storage. If you change these resources or increase the number of OpenShift Container Platform machines, adjust these requirements accordingly.
Procedure
Check the RHV version.
- In the RHV Administration Portal, click the ? help icon in the upper-right corner and select About.
- In the window that opens, make a note of the RHV Software Version.
- Confirm that version 4.6 of OpenShift Container Platform and the version of RHV you noted are one of the supported combinations in the Support Matrix for OpenShift Container Platform on RHV.
Inspect the data center, cluster, and storage.
- In the RHV Administration Portal, click Compute → Data Centers.
- Confirm that the data center where you plan to install OpenShift Container Platform is accessible.
- Click the name of that data center.
- In the data center details, on the Storage tab, confirm the storage domain where you plan to install OpenShift Container Platform is Active.
- Record the Domain Name for use later on.
- Confirm Free Space has at least 230 GiB.
- Confirm that the storage domain meets these etcd backend performance requirements, which you can measure by using the fio performance benchmarking tool.
- In the data center details, click the Clusters tab.
- Find the RHV cluster where you plan to install OpenShift Container Platform. Record the cluster name for use later on.
Inspect the RHV host resources.
- In the RHV Administration Portal, click Compute > Clusters.
- Click the cluster where you plan to install OpenShift Container Platform.
- In the cluster details, click the Hosts tab.
- Inspect the hosts and confirm they have a combined total of at least 28 Logical CPU Cores available exclusively for the OpenShift Container Platform cluster.
- Record the number of available Logical CPU Cores for use later on.
- Confirm that these CPU cores are distributed so that each of the seven virtual machines created during installation can have four cores.
Confirm that, all together, the hosts have 112 GiB of Max free Memory for scheduling new virtual machines distributed to meet the requirements for each of the following OpenShift Container Platform machines:
- 16 GiB required for the bootstrap machine
- 16 GiB required for each of the three control plane machines
- 16 GiB for each of the three compute machines
- Record the amount of Max free Memory for scheduling new virtual machines for use later on.
Verify that the virtual network for installing OpenShift Container Platform has access to the RHV Manager’s REST API. From a virtual machine on this network, use curl to reach the RHV Manager’s REST API:
curl -k -u <username>@<profile>:<password> \ https://<engine-fqdn>/ovirt-engine/api
$ curl -k -u <username>@<profile>:<password> \1 https://<engine-fqdn>/ovirt-engine/api2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<username>, specify the user name of an RHV account with privileges to create and manage an OpenShift Container Platform cluster on RHV. For<profile>, specify the login profile, which you can get by going to the RHV Administration Portal login page and reviewing the Profile dropdown list. For<password>, specify the password for that user name. - 2
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV environment.
For example:
curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/api
$ curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.2.5. Preparing the network environment on RHV
Configure two static IP addresses for the OpenShift Container Platform cluster and create DNS entries using these addresses.
Procedure
Reserve two static IP addresses
- On the network where you plan to install OpenShift Container Platform, identify two static IP addresses that are outside the DHCP lease pool.
Connect to a host on this network and verify that each of the IP addresses is not in use. For example, use Address Resolution Protocol (ARP) to check that none of the IP addresses have entries:
arp 10.35.1.19
$ arp 10.35.1.19Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
10.35.1.19 (10.35.1.19) -- no entry
10.35.1.19 (10.35.1.19) -- no entryCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Reserve two static IP addresses following the standard practices for your network environment.
- Record these IP addresses for future reference.
Create DNS entries for the OpenShift Container Platform REST API and apps domain names using this format:
api.<cluster-name>.<base-domain> <ip-address> *.apps.<cluster-name>.<base-domain> <ip-address>
api.<cluster-name>.<base-domain> <ip-address>1 *.apps.<cluster-name>.<base-domain> <ip-address>2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow For example:
api.my-cluster.virtlab.example.com 10.35.1.19 *.apps.my-cluster.virtlab.example.com 10.35.1.20
api.my-cluster.virtlab.example.com 10.35.1.19 *.apps.my-cluster.virtlab.example.com 10.35.1.20Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.2.6. Setting up the CA certificate for RHV
Download the CA certificate from the Red Hat Virtualization (RHV) Manager and set it up on the installation machine.
You can download the certificate from a webpage on the RHV Manager or by using a curl command.
Later, you provide the certificate to the installation program.
Procedure
Use either of these two methods to download the CA certificate:
-
Go to the Manager’s webpage,
https://<engine-fqdn>/ovirt-engine/. Then, under Downloads, click the CA Certificate link. Run the following command:
curl -k 'https://<engine-fqdn>/ovirt-engine/services/pki-resource?resource=ca-certificate&format=X509-PEM-CA' -o /tmp/ca.pem
$ curl -k 'https://<engine-fqdn>/ovirt-engine/services/pki-resource?resource=ca-certificate&format=X509-PEM-CA' -o /tmp/ca.pem1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV Manager, such asrhv-env.virtlab.example.com.
-
Go to the Manager’s webpage,
Configure the CA file to grant rootless user access to the Manager. Set the CA file permissions to have an octal value of
0644(symbolic value:-rw-r—r--):sudo chmod 0644 /tmp/ca.pem
$ sudo chmod 0644 /tmp/ca.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow For Linux, copy the CA certificate to the directory for server certificates. Use
-pto preserve the permissions:sudo cp -p /tmp/ca.pem /etc/pki/ca-trust/source/anchors/ca.pem
$ sudo cp -p /tmp/ca.pem /etc/pki/ca-trust/source/anchors/ca.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the certificate to the certificate manager for your operating system:
- For macOS, double-click the certificate file and use the Keychain Access utility to add the file to the System keychain.
For Linux, update the CA trust:
sudo update-ca-trust
$ sudo update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you use your own certificate authority, make sure the system trusts it.
10.2.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
10.2.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
10.2.9. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on Red Hat Virtualization (RHV).
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Respond to the installation program prompts.
For
SSH Public Key, select a password-less public key, such as~/.ssh/id_rsa.pub. This key authenticates connections with the new OpenShift Container Platform cluster.NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, select an SSH key that your
ssh-agentprocess uses.-
For
Platform, selectovirt. For
Enter oVirt’s API endpoint URL, enter the URL of the RHV API using this format:https://<engine-fqdn>/ovirt-engine/api
https://<engine-fqdn>/ovirt-engine/api1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV environment.
For example:
curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/api
$ curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
For
Is the oVirt CA trusted locally?, enterYessince you have already set up a CA certificate. Otherwise, enterNo. -
For
oVirt’s CA bundle, if you enteredYesfor the preceding question, copy the certificate content from/etc/pki/ca-trust/source/anchors/ca.pemand paste it here. Then, pressEntertwice. Otherwise, if you enteredNofor the preceding question, this question does not appear. For
oVirt engine username, enter the user name and profile of the RHV administrator using this format:<username>@<profile>
<username>@<profile>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<username>, specify the user name of an RHV administrator. For<profile>, specify the login profile, which you can get by going to the RHV Administration Portal login page and reviewing the Profile dropdown list. Together, the user name and profile should look similar to this example:
ocpadmin@internal
ocpadmin@internalCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
For
oVirt engine password, enter the RHV admin password. -
For
oVirt cluster, select the cluster for installing OpenShift Container Platform. -
For
oVirt storage domain, select the storage domain for installing OpenShift Container Platform. -
For
oVirt network, select a virtual network that has access to the Manager REST API. -
For
Internal API Virtual IP, enter the static IP address you set aside for the cluster’s REST API. -
For
Ingress virtual IP, enter the static IP address you reserved for the wildcard apps domain. -
For
Base Domain, enter the base domain of the OpenShift Container Platform cluster. If this cluster is exposed to the outside world, this must be a valid domain recognized by DNS infrastructure. For example, enter:virtlab.example.com -
For
Cluster Name, enter the name of the cluster. For example,my-cluster. Use cluster name from the externally registered/resolvable DNS entries you created for the OpenShift Container Platform REST API and apps domain names. The installation program also gives this name to the cluster in the RHV environment. -
For
Pull Secret, copy the pull secret from thepull-secret.txtfile you downloaded earlier and paste it here. You can also get a copy of the same pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
10.2.9.1. Example install-config.yaml files for Red Hat Virtualization (RHV)
You can customize the OpenShift Container Platform cluster the installation program creates by changing the parameters and parameter values in the install-config.yaml file.
The following example is specific to installing OpenShift Container Platform on RHV.
This file is located in the <installation_directory> you specified when you ran the following command.
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>-
These example files are provided for reference only. You must obtain your
install-config.yamlfile by using the installation program. -
Changing the
install-config.yamlfile can increase the resources your cluster requires. Verify that your RHV environment has those additional resources. Otherwise, the installation or cluster will fail.
Example: This is the default install-config.yaml file
Example: A minimal install-config.yaml file
Example: Custom machine pools in an install-config.yaml file
10.2.9.2. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
10.2.9.2.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters, hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
10.2.9.2.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
10.2.9.2.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
10.2.9.2.4. Additional Red Hat Virtualization (RHV) configuration parameters
Additional RHV configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Required. The Cluster where the VMs will be created. |
String. For example: |
|
| Required. The Storage Domain ID where the VM disks will be created. |
String. For example: |
|
| Required. The network name where the VM nics will be created. |
String. For example: |
|
| Required. The vNIC profile ID of the VM network interfaces. This can be inferred if the cluster network has a single profile. |
String. For example: |
|
| Required. An IP address on the machine network that will be assigned to the API virtual IP (VIP). You can access the OpenShift API at this endpoint. |
String. Example: |
|
| Required. An IP address on the machine network that will be assigned to the Ingress virtual IP (VIP). |
String. Example: |
10.2.9.2.5. Additional RHV parameters for machine pools
Additional RHV configuration parameters for machine pools are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| Optional. Defines the CPU of the VM. | Object |
|
|
Required if you use | Integer |
|
|
Required if you use | Integer |
|
| Optional. Memory of the VM in MiB. | Integer |
|
|
Optional. An instance type UUID, such as | String of UUID |
|
| Optional. Defines the first and bootable disk of the VM. | String |
|
|
Required if you use | Number |
|
|
Optional. The VM workload type, such as | String |
You can replace <machine-pool> with controlPlane or compute.
10.2.10. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
-
Open the
ovirt-imageioport to the Manager from the machine running the installer. By default, the port is54322. - Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
You have completed the steps required to install the cluster. The remaining steps show you how to verify the cluster and troubleshoot the installation.
10.2.11. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
10.2.11.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>10.2.11.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>10.2.11.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>10.2.12. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
To learn more, see Getting started with the OpenShift CLI.
10.2.13. Verifying cluster status
You can verify your OpenShift Container Platform cluster’s status during or after installation.
Procedure
In the cluster environment, export the administrator’s kubeconfig file:
export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
The
kubeconfigfile contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server.View the control plane and compute machines created after a deployment:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your cluster’s version:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your Operators' status:
oc get clusteroperator
$ oc get clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow View all running pods in the cluster:
oc get pods -A
$ oc get pods -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow
Troubleshooting
If the installation fails, the installation program times out and displays an error message. To learn more, see Troubleshooting installation issues.
10.2.14. Accessing the OpenShift Container Platform web console on RHV
After the OpenShift Container Platform cluster initializes, you can log in to the OpenShift Container Platform web console.
Procedure
- Optional: In the Red Hat Virtualization (RHV) Administration Portal, open Compute → Cluster.
- Verify that the installation program creates the virtual machines.
- Return to the command line where the installation program is running. When the installation program finishes, it displays the user name and temporary password for logging into the OpenShift Container Platform web console.
In a browser, open the URL of the OpenShift Container Platform web console. The URL uses this format:
console-openshift-console.apps.<clustername>.<basedomain>
console-openshift-console.apps.<clustername>.<basedomain>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<clustername>.<basedomain>, specify the cluster name and base domain.
For example:
console-openshift-console.apps.my-cluster.virtlab.example.com
console-openshift-console.apps.my-cluster.virtlab.example.comCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.2.15. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
10.2.16. Troubleshooting common issues with installing on Red Hat Virtualization (RHV)
Here are some common issues you might encounter, along with proposed causes and solutions.
10.2.16.1. CPU load increases and nodes go into a Not Ready state
-
Symptom: CPU load increases significantly and nodes start going into a
Not Readystate. - Cause: The storage domain latency might be too high, especially for control plane nodes (also known as the master nodes).
Solution:
Make the nodes ready again by restarting the kubelet service:
systemctl restart kubelet
$ systemctl restart kubeletCopy to Clipboard Copied! Toggle word wrap Toggle overflow Inspect the OpenShift Container Platform metrics service, which automatically gathers and reports on some valuable data such as the etcd disk sync duration. If the cluster is operational, use this data to help determine whether storage latency or throughput is the root issue. If so, consider using a storage resource that has lower latency and higher throughput.
To get raw metrics, enter the following command as kubeadmin or user with cluster-admin privileges:
oc get --insecure-skip-tls-verify --server=https://localhost:<port> --raw=/metrics
$ oc get --insecure-skip-tls-verify --server=https://localhost:<port> --raw=/metricsCopy to Clipboard Copied! Toggle word wrap Toggle overflow To learn more, see Exploring Application Endpoints for the purposes of Debugging with OpenShift 4.x
10.2.16.2. Trouble connecting the OpenShift Container Platform cluster API
Symptom: The installation program completes but the OpenShift Container Platform cluster API is not available. The bootstrap virtual machine remains up after the bootstrap process is complete. When you enter the following command, the response will time out.
oc login -u kubeadmin -p *** <apiurl>
$ oc login -u kubeadmin -p *** <apiurl>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Cause: The bootstrap VM was not deleted by the installation program and has not released the cluster’s API IP address.
Solution: Use the
wait-forsubcommand to be notified when the bootstrap process is complete:./openshift-install wait-for bootstrap-complete
$ ./openshift-install wait-for bootstrap-completeCopy to Clipboard Copied! Toggle word wrap Toggle overflow When the bootstrap process is complete, delete the bootstrap virtual machine:
./openshift-install destroy bootstrap
$ ./openshift-install destroy bootstrapCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.2.17. Post-installation tasks
After the OpenShift Container Platform cluster initializes, you can perform the following tasks.
- Optional: After deployment, add or replace SSH keys using the Machine Config Operator (MCO) in OpenShift Container Platform.
-
Optional: Remove the
kubeadminuser. Instead, use the authentication provider to create a user with cluster-admin privileges.
10.2.18. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
10.3. Installing a cluster on RHV with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a customized OpenShift Container Platform cluster on Red Hat Virtualization (RHV) and other infrastructure that you provide. The OpenShift Container Platform documentation uses the term user-provisioned infrastructure to refer to this infrastructure type.
The following diagram shows an example of a potential OpenShift Container Platform cluster running on a RHV cluster.
The RHV hosts run virtual machines that contain both control plane and compute pods. One of the hosts also runs a Manager virtual machine and a bootstrap virtual machine that contains a temporary control plane pod.]
10.3.1. Prerequisites
The following items are required to install an OpenShift Container Platform cluster on a RHV environment.
- You have a supported combination of versions in the Support Matrix for OpenShift Container Platform on Red Hat Virtualization (RHV).
- You are familiar with the OpenShift Container Platform installation and update processes.
10.3.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
10.3.3. Requirements for the RHV environment
To install and run an OpenShift Container Platform cluster, the RHV environment must meet the following requirements.
Not meeting these requirements can cause the installation or process to fail. Additionally, not meeting these requirements can cause the OpenShift Container Platform cluster to fail days or weeks after installation.
The following requirements for CPU, memory, and storage resources are based on default values multiplied by the default number of virtual machines the installation program creates. These resources must be available in addition to what the RHV environment uses for non-OpenShift Container Platform operations.
By default, the installation program creates seven virtual machines during the installation process. First, it creates a bootstrap virtual machine to provide temporary services and a control plane while it creates the rest of the OpenShift Container Platform cluster. When the installation program finishes creating the cluster, deleting the bootstrap machine frees up its resources.
If you increase the number of virtual machines in the RHV environment, you must increase the resources accordingly.
Requirements
- The RHV environment has one data center whose state is Up.
- The RHV data center contains an RHV cluster.
The RHV cluster has the following resources exclusively for the OpenShift Container Platform cluster:
- Minimum 28 vCPUs: four for each of the seven virtual machines created during installation.
112 GiB RAM or more, including:
- 16 GiB or more for the bootstrap machine, which provides the temporary control plane.
- 16 GiB or more for each of the three control plane machines which provide the control plane.
- 16 GiB or more for each of the three compute machines, which run the application workloads.
- The RHV storage domain must meet these etcd backend performance requirements.
- In production environments, each virtual machine must have 120 GiB or more. Therefore, the storage domain must provide 840 GiB or more for the default OpenShift Container Platform cluster. In resource-constrained or non-production environments, each virtual machine must have 32 GiB or more, so the storage domain must have 230 GiB or more for the default OpenShift Container Platform cluster.
- To download images from the Red Hat Ecosystem Catalog during installation and update procedures, the RHV cluster must have access to an internet connection. The Telemetry service also needs an internet connection to simplify the subscription and entitlement process.
- The RHV cluster must have a virtual network with access to the REST API on the RHV Manager. Ensure that DHCP is enabled on this network, because the VMs that the installer creates obtain their IP address by using DHCP.
A user account and group with the following least privileges for installing and managing an OpenShift Container Platform cluster on the target RHV cluster:
-
DiskOperator -
DiskCreator -
UserTemplateBasedVm -
TemplateOwner -
TemplateCreator -
ClusterAdminon the target cluster
-
Apply the principle of least privilege: Avoid using an administrator account with SuperUser privileges on RHV during the installation process. The installation program saves the credentials you provide to a temporary ovirt-config.yaml file that might be compromised.
10.3.4. Verifying the requirements for the RHV environment
Verify that the RHV environment meets the requirements to install and run an OpenShift Container Platform cluster. Not meeting these requirements can cause failures.
These requirements are based on the default resources the installation program uses to create control plane and compute machines. These resources include vCPUs, memory, and storage. If you change these resources or increase the number of OpenShift Container Platform machines, adjust these requirements accordingly.
Procedure
Check the RHV version.
- In the RHV Administration Portal, click the ? help icon in the upper-right corner and select About.
- In the window that opens, make a note of the RHV Software Version.
- Confirm that version 4.6 of OpenShift Container Platform and the version of RHV you noted are one of the supported combinations in the Support Matrix for OpenShift Container Platform on RHV.
Inspect the data center, cluster, and storage.
- In the RHV Administration Portal, click Compute → Data Centers.
- Confirm that the data center where you plan to install OpenShift Container Platform is accessible.
- Click the name of that data center.
- In the data center details, on the Storage tab, confirm the storage domain where you plan to install OpenShift Container Platform is Active.
- Record the Domain Name for use later on.
- Confirm Free Space has at least 230 GiB.
- Confirm that the storage domain meets these etcd backend performance requirements, which you can measure by using the fio performance benchmarking tool.
- In the data center details, click the Clusters tab.
- Find the RHV cluster where you plan to install OpenShift Container Platform. Record the cluster name for use later on.
Inspect the RHV host resources.
- In the RHV Administration Portal, click Compute > Clusters.
- Click the cluster where you plan to install OpenShift Container Platform.
- In the cluster details, click the Hosts tab.
- Inspect the hosts and confirm they have a combined total of at least 28 Logical CPU Cores available exclusively for the OpenShift Container Platform cluster.
- Record the number of available Logical CPU Cores for use later on.
- Confirm that these CPU cores are distributed so that each of the seven virtual machines created during installation can have four cores.
Confirm that, all together, the hosts have 112 GiB of Max free Memory for scheduling new virtual machines distributed to meet the requirements for each of the following OpenShift Container Platform machines:
- 16 GiB required for the bootstrap machine
- 16 GiB required for each of the three control plane machines
- 16 GiB for each of the three compute machines
- Record the amount of Max free Memory for scheduling new virtual machines for use later on.
Verify that the virtual network for installing OpenShift Container Platform has access to the RHV Manager’s REST API. From a virtual machine on this network, use curl to reach the RHV Manager’s REST API:
curl -k -u <username>@<profile>:<password> \ https://<engine-fqdn>/ovirt-engine/api
$ curl -k -u <username>@<profile>:<password> \1 https://<engine-fqdn>/ovirt-engine/api2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<username>, specify the user name of an RHV account with privileges to create and manage an OpenShift Container Platform cluster on RHV. For<profile>, specify the login profile, which you can get by going to the RHV Administration Portal login page and reviewing the Profile dropdown list. For<password>, specify the password for that user name. - 2
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV environment.
For example:
curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/api
$ curl -k -u ocpadmin@internal:pw123 \ https://rhv-env.virtlab.example.com/ovirt-engine/apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.5. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
Firewall
Configure your firewall so your cluster has access to required sites.
See also:
Load balancers
Configure one or preferably two layer-4 load balancers:
-
Provide load balancing for ports
6443and22623on the control plane and bootstrap machines. Port6443provides access to the Kubernetes API server and must be reachable both internally and externally. Port22623must be accessible to nodes within the cluster. -
Provide load balancing for port
443and80for machines that run the Ingress router, which are usually compute nodes in the default configuration. Both ports must be accessible from within and outside the cluster.
DNS
Configure infrastructure-provided DNS to allow the correct resolution of the main components and services. If you use only one load balancer, these DNS records can point to the same IP address.
-
Create DNS records for
api.<cluster_name>.<base_domain>(internal and external resolution) andapi-int.<cluster_name>.<base_domain>(internal resolution) that point to the load balancer for the control plane machines. -
Create a DNS record for
*.apps.<cluster_name>.<base_domain>that points to the load balancer for the Ingress router. For example, ports443and80of the compute machines.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 10.9. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 10.10. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
10.3.6. Setting up the installation machine
To run the binary openshift-install installation program and Ansible scripts, set up the RHV Manager or an Red Hat Enterprise Linux (RHEL) computer with network access to the RHV environment and the REST API on the Manager.
Procedure
Update or install Python3 and Ansible. For example:
dnf update python3 ansible
# dnf update python3 ansibleCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Install the
python3-ovirt-engine-sdk4package to get the Python Software Development Kit. Install the
ovirt.image-templateAnsible role. On the RHV Manager and other Red Hat Enterprise Linux (RHEL) machines, this role is distributed as theovirt-ansible-image-templatepackage. For example, enter:dnf install ovirt-ansible-image-template
# dnf install ovirt-ansible-image-templateCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the
ovirt.vm-infraAnsible role. On the RHV Manager and other RHEL machines, this role is distributed as theovirt-ansible-vm-infrapackage.dnf install ovirt-ansible-vm-infra
# dnf install ovirt-ansible-vm-infraCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an environment variable and assign an absolute or relative path to it. For example, enter:
export ASSETS_DIR=./wrk
$ export ASSETS_DIR=./wrkCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe installation program uses this variable to create a directory where it saves important installation-related files. Later, the installation process reuses this variable to locate those asset files. Avoid deleting this assets directory; it is required for uninstalling the cluster.
10.3.7. Setting up the CA certificate for RHV
Download the CA certificate from the Red Hat Virtualization (RHV) Manager and set it up on the installation machine.
You can download the certificate from a webpage on the RHV Manager or by using a curl command.
Later, you provide the certificate to the installation program.
Procedure
Use either of these two methods to download the CA certificate:
-
Go to the Manager’s webpage,
https://<engine-fqdn>/ovirt-engine/. Then, under Downloads, click the CA Certificate link. Run the following command:
curl -k 'https://<engine-fqdn>/ovirt-engine/services/pki-resource?resource=ca-certificate&format=X509-PEM-CA' -o /tmp/ca.pem
$ curl -k 'https://<engine-fqdn>/ovirt-engine/services/pki-resource?resource=ca-certificate&format=X509-PEM-CA' -o /tmp/ca.pem1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<engine-fqdn>, specify the fully qualified domain name of the RHV Manager, such asrhv-env.virtlab.example.com.
-
Go to the Manager’s webpage,
Configure the CA file to grant rootless user access to the Manager. Set the CA file permissions to have an octal value of
0644(symbolic value:-rw-r—r--):sudo chmod 0644 /tmp/ca.pem
$ sudo chmod 0644 /tmp/ca.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow For Linux, copy the CA certificate to the directory for server certificates. Use
-pto preserve the permissions:sudo cp -p /tmp/ca.pem /etc/pki/ca-trust/source/anchors/ca.pem
$ sudo cp -p /tmp/ca.pem /etc/pki/ca-trust/source/anchors/ca.pemCopy to Clipboard Copied! Toggle word wrap Toggle overflow Add the certificate to the certificate manager for your operating system:
- For macOS, double-click the certificate file and use the Keychain Access utility to add the file to the System keychain.
For Linux, update the CA trust:
sudo update-ca-trust
$ sudo update-ca-trustCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf you use your own certificate authority, make sure the system trusts it.
10.3.8. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
10.3.9. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
10.3.10. Downloading the Ansible playbooks
Download the Ansible playbooks for installing OpenShift Container Platform version 4.6 on RHV.
Procedure
On your installation machine, run the following commands:
mkdir playbooks
$ mkdir playbooksCopy to Clipboard Copied! Toggle word wrap Toggle overflow cd playbooks
$ cd playbooksCopy to Clipboard Copied! Toggle word wrap Toggle overflow curl -s -L -X GET https://api.github.com/repos/openshift/installer/contents/upi/ovirt?ref=release-4.6 |
$ curl -s -L -X GET https://api.github.com/repos/openshift/installer/contents/upi/ovirt?ref=release-4.6 | grep 'download_url.*\.yml' | awk '{ print $2 }' | sed -r 's/("|",)//g' | xargs -n 1 curl -OCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
-
After you download these Ansible playbooks, you must also create the environment variable for the assets directory and customize the
inventory.ymlfile before you create an installation configuration file by running the installation program.
10.3.11. The inventory.yml file
You use the inventory.yml file to define and create elements of the OpenShift Container Platform cluster you are installing. This includes elements such as the Red Hat Enterprise Linux CoreOS (RHCOS) image, virtual machine templates, bootstrap machine, control plane nodes, and worker nodes. You also use inventory.yml to destroy the cluster.
The following inventory.yml example shows you the parameters and their default values. The quantities and numbers in these default values meet the requirements for running a production OpenShift Container Platform cluster in a RHV environment.
Example inventory.yml file
Enter values for parameters whose descriptions begin with "Enter." Otherwise, you can use the default value or replace it with a new value.
General section
-
ovirt_cluster: Enter the name of an existing RHV cluster in which to install the OpenShift Container Platform cluster. -
ocp.assets_dir: The path of a directory theopenshift-installinstallation program creates to store the files that it generates. -
ocp.ovirt_config_path: The path of theovirt-config.yamlfile the installation program generates, for example,./wrk/install-config.yaml. This file contains the credentials required to interact with the REST API of the Manager.
Red Hat Enterprise Linux CoreOS (RHCOS) section
-
image_url: Enter the URL of the RHCOS image you specified for download. -
local_cmp_image_path: The path of a local download directory for the compressed RHCOS image. -
local_image_path: The path of a local directory for the extracted RHCOS image.
Profiles section
This section consists of two profiles:
-
control_plane: The profile of the bootstrap and control plane nodes. -
compute: The profile of workers nodes in the compute plane.
These profiles have the following parameters. The default values of the parameters meet the minimum requirements for running a production cluster. You can increase or customize these values to meet your workload requirements.
-
cluster: The value gets the cluster name fromovirt_clusterin the General Section. -
memory: The amount of memory, in GB, for the virtual machine. -
sockets: The number of sockets for the virtual machine. -
cores: The number of cores for the virtual machine. -
template: The name of the virtual machine template. If plan to install multiple clusters, and these clusters use templates that contain different specifications, prepend the template name with the ID of the cluster. -
operating_system: The type of guest operating system in the virtual machine. With oVirt/RHV version 4.4, this value must berhcos_x64so the value ofIgnition scriptcan be passed to the VM. type: Enterserveras the type of the virtual machine.ImportantYou must change the value of the
typeparameter fromhigh_performancetoserver.-
disks: The disk specifications. Thecontrol_planeandcomputenodes can have different storage domains. -
size: The minimum disk size. -
name: Enter the name of a disk connected to the target cluster in RHV. -
interface: Enter the interface type of the disk you specified. -
storage_domain: Enter the storage domain of the disk you specified. -
nics: Enter thenameandnetworkthe virtual machines use. You can also specify the virtual network interface profile. By default, NICs obtain their MAC addresses from the oVirt/RHV MAC pool.
Virtual machines section
This final section, vms, defines the virtual machines you plan to create and deploy in the cluster. By default, it provides the minimum number of control plane and worker nodes for a production environment.
vms contains three required elements:
-
name: The name of the virtual machine. In this case,metadata.infraIDprepends the virtual machine name with the infrastructure ID from themetadata.ymlfile. -
ocp_type: The role of the virtual machine in the OCP cluster. Possible values arebootstrap,master,worker. profile: The name of the profile from which each virtual machine inherits specifications. Possible values in this example arecontrol_planeorcompute.You can override the value a virtual machine inherits from its profile. To do this, you add the name of the profile attribute to the virtual machine in
inventory.ymland assign it an overriding value. To see an example of this, examine thename: "{{ metadata.infraID }}-bootstrap"virtual machine in the precedinginventory.ymlexample: It has atypeattribute whose value,server, overrides the value of thetypeattribute this virtual machine would otherwise inherit from thecontrol_planeprofile.
Metadata variables
For virtual machines, metadata.infraID prepends the name of the virtual machine with the infrastructure ID from the metadata.json file you create when you build the Ignition files.
The playbooks use the following code to read infraID from the specific file located in the ocp.assets_dir.
10.3.12. Specifying the RHCOS image settings
Update the Red Hat Enterprise Linux CoreOS (RHCOS) image settings of the inventory.yml file. Later, when you run this file one of the playbooks, it downloads a compressed Red Hat Enterprise Linux CoreOS (RHCOS) image from the image_url URL to the local_cmp_image_path directory. The playbook then uncompresses the image to the local_image_path directory and uses it to create oVirt/RHV templates.
Procedure
- Locate the RHCOS image download page for the version of OpenShift Container Platform you are installing, such as Index of /pub/openshift-v4/dependencies/rhcos/latest/latest.
-
From that download page, copy the URL of an OpenStack
qcow2image, such ashttps://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.6/latest/rhcos-openstack.x86_64.qcow2.gz. Edit the
inventory.ymlplaybook you downloaded earlier. In it, paste the URL as the value forimage_url. For example:rhcos: "https://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.6/latest/rhcos-openstack.x86_64.qcow2.gz"
rhcos: "https://mirror.openshift.com/pub/openshift-v4/dependencies/rhcos/4.6/latest/rhcos-openstack.x86_64.qcow2.gz"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.13. Creating the install config file
You create an installation configuration file by running the installation program, openshift-install, and responding to its prompts with information you specified or gathered earlier.
When you finish responding to the prompts, the installation program creates an initial version of the install-config.yaml file in the assets directory you specified earlier, for example, ./wrk/install-config.yaml
The installation program also creates a file, $HOME/.ovirt/ovirt-config.yaml, that contains all the connection parameters that are required to reach the Manager and use its REST API.
NOTE: The installation process does not use values you supply for some parameters, such as Internal API virtual IP and Ingress virtual IP, because you have already configured them in your infrastructure DNS.
It also uses the values you supply for parameters in inventory.yml, like the ones for oVirt cluster, oVirt storage, and oVirt network. And uses a script to remove or replace these same values from install-config.yaml with the previously mentioned virtual IPs.
Procedure
Run the installation program:
openshift-install create install-config --dir $ASSETS_DIR
$ openshift-install create install-config --dir $ASSETS_DIRCopy to Clipboard Copied! Toggle word wrap Toggle overflow Respond to the installation program’s prompts with information about your system.
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
For Internal API virtual IP and Ingress virtual IP, supply the IP addresses you specified when you configured the DNS service.
Together, the values you enter for the oVirt cluster and Base Domain prompts form the FQDN portion of URLs for the REST API and any applications you create, such as https://api.ocp4.example.org:6443/ and https://console-openshift-console.apps.ocp4.example.org.
You can get the pull secret from the Red Hat OpenShift Cluster Manager.
10.3.14. Customizing install-config.yaml
Here, you use three Python scripts to override some of the installation program’s default behaviors:
- By default, the installation program uses the machine API to create nodes. To override this default behavior, you set the number of compute nodes to zero replicas. Later, you use Ansible playbooks to create the compute nodes.
- By default, the installation program sets the IP range of the machine network for nodes. To override this default behavior, you set the IP range to match your infrastructure.
-
By default, the installation program sets the platform to
ovirt. However, installing a cluster on user-provisioned infrastructure is more similar to installing a cluster on bare metal. Therefore, you delete the ovirt platform section frominstall-config.yamland change the platform tonone. Instead, you useinventory.ymlto specify all of the required settings.
These snippets work with Python 3 and Python 2.
Procedure
Set the number of compute nodes to zero replicas:
python3 -c 'import os, yaml
$ python3 -c 'import os, yaml path = "%s/install-config.yaml" % os.environ["ASSETS_DIR"] conf = yaml.safe_load(open(path)) conf["compute"][0]["replicas"] = 0 open(path, "w").write(yaml.dump(conf, default_flow_style=False))'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the IP range of the machine network. For example, to set the range to
172.16.0.0/16, enter:python3 -c 'import os, yaml
$ python3 -c 'import os, yaml path = "%s/install-config.yaml" % os.environ["ASSETS_DIR"] conf = yaml.safe_load(open(path)) conf["networking"]["machineNetwork"][0]["cidr"] = "172.16.0.0/16" open(path, "w").write(yaml.dump(conf, default_flow_style=False))'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Remove the
ovirtsection and change the platform tonone:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.15. Generate manifest files
Use the installation program to generate a set of manifest files in the assets directory.
The command to generate the manifest files displays a warning message before it consumes the install-config.yaml file.
If you plan to reuse the install-config.yaml file, create a backup copy of it before you back it up before you generate the manifest files.
Procedure
Optional: Create a backup copy of the
install-config.yamlfile:cp install-config.yaml install-config.yaml.backup
$ cp install-config.yaml install-config.yaml.backupCopy to Clipboard Copied! Toggle word wrap Toggle overflow Generate a set of manifests in your assets directory:
openshift-install create manifests --dir $ASSETS_DIR
$ openshift-install create manifests --dir $ASSETS_DIRCopy to Clipboard Copied! Toggle word wrap Toggle overflow This command displays the following messages.
Example output
INFO Consuming Install Config from target directory WARNING Making control-plane schedulable by setting MastersSchedulable to true for Scheduler cluster settings
INFO Consuming Install Config from target directory WARNING Making control-plane schedulable by setting MastersSchedulable to true for Scheduler cluster settingsCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command generates the following manifest files:
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Next steps
- Make control plane nodes non-schedulable.
10.3.16. Making control-plane nodes non-schedulable
Because you are manually creating and deploying the control plane machines, you must configure a manifest file to make the control plane nodes non-schedulable.
Procedure
To make the control plane nodes non-schedulable, enter:
python3 -c 'import os, yaml
$ python3 -c 'import os, yaml path = "%s/manifests/cluster-scheduler-02-config.yml" % os.environ["ASSETS_DIR"] data = yaml.safe_load(open(path)) data["spec"]["mastersSchedulable"] = False open(path, "w").write(yaml.dump(data, default_flow_style=False))'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.17. Building the Ignition files
To build the Ignition files from the manifest files you just generated and modified, you run the installation program. This action creates a Red Hat Enterprise Linux CoreOS (RHCOS) machine, initramfs, which fetches the Ignition files and performs the configurations needed to create a node.
In addition to the Ignition files, the installation program generates the following:
-
An
authdirectory that contains the admin credentials for connecting to the cluster with theocandkubectlutilities. -
A
metadata.jsonfile that contains information such as the OpenShift Container Platform cluster name, cluster ID, and infrastructure ID for the current installation.
The Ansible playbooks for this installation process use the value of infraID as a prefix for the virtual machines they create. This prevents naming conflicts when there are multiple installations in the same oVirt/RHV cluster.
Certificates in Ignition configuration files expire after 24 hours. Complete the cluster installation and keep the cluster running in a non-degraded state for 24 hours so that the first certificate rotation can finish.
Procedure
To build the Ignition files, enter:
openshift-install create ignition-configs --dir $ASSETS_DIR
$ openshift-install create ignition-configs --dir $ASSETS_DIRCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.18. Creating templates and virtual machines
After confirming the variables in the inventory.yml, you run the first Ansible provisioning playbook, create-templates-and-vms.yml.
This playbook uses the connection parameters for the RHV Manager from $HOME/.ovirt/ovirt-config.yaml and reads metadata.json in the assets directory.
If a local Red Hat Enterprise Linux CoreOS (RHCOS) image is not already present, the playbook downloads one from the URL you specified for image_url in inventory.yml. It extracts the image and uploads it to RHV to create templates.
The playbook creates a template based on the control_plane and compute profiles in the inventory.yml file. If these profiles have different names, it creates two templates.
When the playbook finishes, the virtual machines it creates are stopped. You can get information from them to help configure other infrastructure elements. For example, you can get the virtual machines' MAC addresses to configure DHCP to assign permanent IP addresses to the virtual machines.
Procedure
-
In
inventory.yml, under thecontrol_planeandcomputevariables, change both instances oftype: high_performancetotype: server. Optional: If you plan to perform multiple installations to the same cluster, create different templates for each OCP installation. In the
inventory.ymlfile, prepend the value oftemplatewithinfraID. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create the templates and virtual machines:
ansible-playbook -i inventory.yml create-templates-and-vms.yml
$ ansible-playbook -i inventory.yml create-templates-and-vms.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.19. Creating the bootstrap machine
You create a bootstrap machine by running the bootstrap.yml playbook. This playbook starts the bootstrap virtual machine, and passes it the bootstrap.ign Ignition file from the assets directory. The bootstrap node configures itself so it can serve Ignition files to the control plane nodes.
To monitor the bootstrap process, you use the console in the RHV Administration Portal or connect to the virtual machine by using SSH.
Procedure
Create the bootstrap machine:
ansible-playbook -i inventory.yml bootstrap.yml
$ ansible-playbook -i inventory.yml bootstrap.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Connect to the bootstrap machine using a console in the Administration Portal or SSH. Replace
<bootstrap_ip>with the bootstrap node IP address. To use SSH, enter:ssh core@<boostrap.ip>
$ ssh core@<boostrap.ip>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Collect
bootkube.servicejournald unit logs for the release image service from the bootstrap node:journalctl -b -f -u release-image.service -u bootkube.service
[core@ocp4-lk6b4-bootstrap ~]$ journalctl -b -f -u release-image.service -u bootkube.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe
bootkube.servicelog on the bootstrap node outputs etcdconnection refusederrors, indicating that the bootstrap server is unable to connect to etcd on control plane nodes (also known as the master nodes). After etcd has started on each control plane node and the nodes have joined the cluster, the errors should stop.
10.3.20. Creating the control plane nodes
You create the control plane nodes by running the masters.yml playbook. This playbook passes the master.ign Ignition file to each of the virtual machines. The Ignition file contains a directive for the control plane node to get the Ignition from a URL such as https://api-int.ocp4.example.org:22623/config/master. The port number in this URL is managed by the load balancer, and is accessible only inside the cluster.
Procedure
Create the control plane nodes:
ansible-playbook -i inventory.yml masters.yml
$ ansible-playbook -i inventory.yml masters.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow While the playbook creates your control plane, monitor the bootstrapping process:
openshift-install wait-for bootstrap-complete --dir $ASSETS_DIR
$ openshift-install wait-for bootstrap-complete --dir $ASSETS_DIRCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO API v1.18.3+b74c5ed up INFO Waiting up to 40m0s for bootstrapping to complete...
INFO API v1.18.3+b74c5ed up INFO Waiting up to 40m0s for bootstrapping to complete...Copy to Clipboard Copied! Toggle word wrap Toggle overflow When all the pods on the control plane nodes and etcd are up and running, the installation program displays the following output.
Example output
INFO It is now safe to remove the bootstrap resources
INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.21. Verifying cluster status
You can verify your OpenShift Container Platform cluster’s status during or after installation.
Procedure
In the cluster environment, export the administrator’s kubeconfig file:
export KUBECONFIG=$ASSETS_DIR/auth/kubeconfig
$ export KUBECONFIG=$ASSETS_DIR/auth/kubeconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow The
kubeconfigfile contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server.View the control plane and compute machines created after a deployment:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your cluster’s version:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow View your Operators' status:
oc get clusteroperator
$ oc get clusteroperatorCopy to Clipboard Copied! Toggle word wrap Toggle overflow View all running pods in the cluster:
oc get pods -A
$ oc get pods -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow
10.3.22. Removing the bootstrap machine
After the wait-for command shows that the bootstrap process is complete, you must remove the bootstrap virtual machine to free up compute, memory, and storage resources. Also, remove settings for the bootstrap machine from the load balancer directives.
Procedure
To remove the bootstrap machine from the cluster, enter:
ansible-playbook -i inventory.yml retire-bootstrap.yml
$ ansible-playbook -i inventory.yml retire-bootstrap.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Remove settings for the bootstrap machine from the load balancer directives.
10.3.23. Creating the worker nodes and completing the installation
Creating worker nodes is similar to creating control plane nodes. However, worker nodes workers do not automatically join the cluster. To add them to the cluster, you review and approve the workers' pending CSRs (Certificate Signing Requests).
After approving the first requests, you continue approving CSR until all of the worker nodes are approved. When you complete this process, the worker nodes become Ready and can have pods scheduled to run on them.
Finally, monitor the command line to see when the installation process completes.
Procedure
Create the worker nodes:
ansible-playbook -i inventory.yml workers.yml
$ ansible-playbook -i inventory.yml workers.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow To list all of the CSRs, enter:
oc get csr -A
$ oc get csr -ACopy to Clipboard Copied! Toggle word wrap Toggle overflow Eventually, this command displays one CSR per node. For example:
Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To filter the list and see only pending CSRs, enter:
watch "oc get csr -A | grep pending -i"
$ watch "oc get csr -A | grep pending -i"Copy to Clipboard Copied! Toggle word wrap Toggle overflow This command refreshes the output every two seconds and displays only pending CSRs. For example:
Example output
Every 2.0s: oc get csr -A | grep pending -i csr-m724n 10m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-wcbrf 11m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending
Every 2.0s: oc get csr -A | grep pending -i csr-m724n 10m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-wcbrf 11m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper PendingCopy to Clipboard Copied! Toggle word wrap Toggle overflow Inspect each pending request. For example:
Example output
oc describe csr csr-m724n
$ oc describe csr csr-m724nCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the CSR information is correct, approve the request:
oc adm certificate approve csr-m724n
$ oc adm certificate approve csr-m724nCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait for the installation process to finish:
openshift-install wait-for install-complete --dir $ASSETS_DIR --log-level debug
$ openshift-install wait-for install-complete --dir $ASSETS_DIR --log-level debugCopy to Clipboard Copied! Toggle word wrap Toggle overflow When the installation completes, the command line displays the URL of the OpenShift Container Platform web console and the administrator user name and password.
10.3.24. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
10.4. Uninstalling a cluster on RHV
You can remove an OpenShift Container Platform cluster from Red Hat Virtualization (RHV).
10.4.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
10.4.2. Removing a cluster that uses user-provisioned infrastructure
When you are finished using the cluster, you can remove a cluster that uses user-provisioned infrastructure from your cloud.
Prerequisites
-
Have the original playbook files, assets directory and files, and
$ASSETS_DIRenvironment variable that you used to you install the cluster. Typically, you can achieve this by using the same computer you used when you installed the cluster.
Procedure
To remove the cluster, enter:
ansible-playbook -i inventory.yml \ retire-bootstrap.yml \ retire-masters.yml \ retire-workers.yml$ ansible-playbook -i inventory.yml \ retire-bootstrap.yml \ retire-masters.yml \ retire-workers.ymlCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Remove any configurations you added to DNS, load balancers, and any other infrastructure for this cluster.
Chapter 11. Installing on vSphere
11.1. Installing a cluster on vSphere
In OpenShift Container Platform version 4.6, you can install a cluster on your VMware vSphere instance by using installer-provisioned infrastructure.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
11.1.1. Prerequisites
-
Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
- The OpenShift Container Platform installer requires access to port 443 on the vCenter and ESXi hosts. You verified that port 443 is accessible.
- If you use a firewall, you confirmed with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
11.1.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.1.3. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.1.4. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
11.1.5. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 11.1. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 11.2. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
11.1.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
11.1.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
11.1.8. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.1.9. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Provide values at the prompts:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
Select the default vCenter datastore to use.
NoteDatastore and cluster names cannot exceed 60 characters; therefore, ensure the combined string length does not exceed the 60 character limit.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
NoteDatastore and cluster names cannot exceed 60 characters; therefore, ensure the combined string length does not exceed the 60 character limit.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
+ When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.+ .Example output
+
The cluster access and credential information also outputs to <installation_directory>/.openshift_install.log when an installation succeeds.
+
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
+
You must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
11.1.10. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
11.1.10.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.1.10.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>11.1.10.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.1.11. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.1.12. Creating registry storage
After you install the cluster, you must create storage for the registry Operator.
11.1.12.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
11.1.12.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.1.12.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.1.12.2.2. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
11.1.13. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
11.1.14. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.1.15. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
11.2. Installing a cluster on vSphere with customizations
In OpenShift Container Platform version 4.6, you can install a cluster on your VMware vSphere instance by using installer-provisioned infrastructure. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
11.2.1. Prerequisites
-
Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
- The OpenShift Container Platform installer requires access to port 443 on the vCenter and ESXi hosts. You verified that port 443 is accessible.
- If you use a firewall, you confirmed with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
11.2.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.2.3. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.2.4. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
11.2.5. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 11.3. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 11.4. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
11.2.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
11.2.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
11.2.8. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.2.9. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on VMware vSphere.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
- Select the default vCenter datastore to use.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
- Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
11.2.9.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
11.2.9.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters and hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
11.2.9.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
11.2.9.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
11.2.9.1.4. Additional VMware vSphere configuration parameters
Additional VMware vSphere configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The fully-qualified hostname or IP address of the vCenter server. | String |
|
| The user name to use to connect to the vCenter instance with. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere. | String |
|
| The password for the vCenter user name. | String |
|
| The name of the datacenter to use in the vCenter instance. | String |
|
| The name of the default datastore to use for provisioning volumes. | String |
|
| Optional. The absolute path of an existing folder where the installation program creates the virtual machines. If you do not provide this value, the installation program creates a folder that is named with the infrastructure ID in the datacenter virtual machine folder. |
String, for example, |
|
| The network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured. | String |
|
| The vCenter cluster to install the OpenShift Container Platform cluster in. | String |
|
| The virtual IP (VIP) address that you configured for control plane API access. |
An IP address, for example |
|
| The virtual IP (VIP) address that you configured for cluster ingress. |
An IP address, for example |
11.2.9.1.5. Optional VMware vSphere machine pool configuration parameters
Optional VMware vSphere machine pool configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. |
An HTTP or HTTPS URL, optionally with a SHA-256 checksum. For example, |
|
| The size of the disk in gigabytes. | Integer |
|
| The total number of virtual processor cores to assign a virtual machine. | Integer |
|
|
The number of cores per socket in a virtual machine. The number of virtual sockets on the virtual machine is | Integer |
|
| The size of a virtual machine’s memory in megabytes. | Integer |
11.2.9.2. Sample install-config.yaml file for an installer-provisioned VMware vSphere cluster
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4 7
- Optional: Provide additional configuration for the machine pool parameters for the compute and control plane machines.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The vSphere cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
11.2.9.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
11.2.10. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the location of your customized./install-config.yamlfile. - 2
- To view different installation details, specify
warn,debug, orerrorinstead ofinfo.When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.
+
The cluster access and credential information also outputs to <installation_directory>/.openshift_install.log when an installation succeeds.
+
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
+
You must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
11.2.11. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
11.2.11.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.2.11.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>11.2.11.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.2.12. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.2.13. Creating registry storage
After you install the cluster, you must create storage for the registry Operator.
11.2.13.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
11.2.13.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.2.13.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.2.13.2.2. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
11.2.14. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
11.2.15. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.2.16. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
11.3. Installing a cluster on vSphere with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster on your VMware vSphere instance by using installer-provisioned infrastructure with customized network configuration options. By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing MTU and VXLAN configurations. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster.
You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
11.3.1. Prerequisites
-
Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
- The OpenShift Container Platform installer requires access to port 443 on the vCenter and ESXi hosts. You verified that port 443 is accessible.
- If you use a firewall, confirm with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
11.3.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.3.3. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.3.4. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
11.3.5. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 11.5. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 11.6. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
11.3.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
11.3.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
11.3.8. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.3.9. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on VMware vSphere.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
- Select the default vCenter datastore to use.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
- Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
11.3.9.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
11.3.9.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters and hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
11.3.9.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
11.3.9.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
11.3.9.1.4. Additional VMware vSphere configuration parameters
Additional VMware vSphere configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The fully-qualified hostname or IP address of the vCenter server. | String |
|
| The user name to use to connect to the vCenter instance with. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere. | String |
|
| The password for the vCenter user name. | String |
|
| The name of the datacenter to use in the vCenter instance. | String |
|
| The name of the default datastore to use for provisioning volumes. | String |
|
| Optional. The absolute path of an existing folder where the installation program creates the virtual machines. If you do not provide this value, the installation program creates a folder that is named with the infrastructure ID in the datacenter virtual machine folder. |
String, for example, |
|
| The network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured. | String |
|
| The vCenter cluster to install the OpenShift Container Platform cluster in. | String |
|
| The virtual IP (VIP) address that you configured for control plane API access. |
An IP address, for example |
|
| The virtual IP (VIP) address that you configured for cluster ingress. |
An IP address, for example |
11.3.9.1.5. Optional VMware vSphere machine pool configuration parameters
Optional VMware vSphere machine pool configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. |
An HTTP or HTTPS URL, optionally with a SHA-256 checksum. For example, |
|
| The size of the disk in gigabytes. | Integer |
|
| The total number of virtual processor cores to assign a virtual machine. | Integer |
|
|
The number of cores per socket in a virtual machine. The number of virtual sockets on the virtual machine is | Integer |
|
| The size of a virtual machine’s memory in megabytes. | Integer |
11.3.9.2. Sample install-config.yaml file for an installer-provisioned VMware vSphere cluster
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4 7
- Optional: Provide additional configuration for the machine pool parameters for the compute and control plane machines.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The vSphere cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
11.3.9.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
11.3.10. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
11.3.11. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
11.3.12. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
11.3.12.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
11.3.13. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the location of your customized./install-config.yamlfile. - 2
- To view different installation details, specify
warn,debug, orerrorinstead ofinfo.When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.
+
The cluster access and credential information also outputs to <installation_directory>/.openshift_install.log when an installation succeeds.
+
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
+
You must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
11.3.14. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
11.3.14.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.3.14.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>11.3.14.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.3.15. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.3.16. Creating registry storage
After you install the cluster, you must create storage for the registry Operator.
11.3.16.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
11.3.16.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.3.16.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.3.16.2.2. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
11.3.17. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
11.3.18. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.3.19. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
11.4. Installing a cluster on vSphere with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere infrastructure that you provision.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the vSphere platform and the installation process of OpenShift Container Platform. Use the user-provisioned infrastructure installation instructions as a guide; you are free to create the required resources through other methods.
11.4.1. Prerequisites
-
Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
- Completing the installation requires that you upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA on vSphere hosts. The machine from which you complete this process requires access to port 443 on the vCenter and ESXi hosts. You verified that port 443 is accessible.
- If you use a firewall, you confirmed with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
11.4.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.4.3. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.4.4. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
11.4.4.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
All virtual machines must reside in the same datastore and in the same folder as the installer.
11.4.4.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
11.4.4.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
11.4.4.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
11.4.5. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
11.4.5.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 11.36. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 11.37. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
Ethernet adaptor hardware address requirements
When provisioning VMs for the cluster, the ethernet interfaces configured for each VM must use a MAC address from the VMware Organizationally Unique Identifier (OUI) allocation ranges:
-
00:05:69:00:00:00to00:05:69:FF:FF:FF -
00:0c:29:00:00:00to00:0c:29:FF:FF:FF -
00:1c:14:00:00:00to00:1c:14:FF:FF:FF -
00:50:56:00:00:00to00:50:56:FF:FF:FF
If a MAC address outside the VMware OUI is used, the cluster installation will not succeed.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
11.4.5.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 11.7. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 11.8. Sample DNS zone database for reverse records
11.4.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
11.4.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
11.4.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
11.4.8.1. Sample install-config.yaml file for VMware vSphere
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but the compute section is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Although both sections currently define a single machine pool, it is possible that future versions of OpenShift Container Platform will support defining multiple compute pools during installation. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The fully-qualified hostname or IP address of the vCenter server.
- 10
- The name of the user for accessing the server. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere.
- 11
- The password associated with the vSphere user.
- 12
- The vSphere datacenter.
- 13
- The default vSphere datastore to use.
- 14
- Optional: For installer-provisioned infrastructure, the absolute path of an existing folder where the installation program creates the virtual machines, for example,
/<datacenter_name>/vm/<folder_name>/<subfolder_name>. If you do not provide this value, the installation program creates a top-level folder in the datacenter virtual machine folder that is named with the infrastructure ID. If you are providing the infrastructure for the cluster, omit this parameter. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- The pull secret that you obtained from OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 17
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).
11.4.8.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
11.4.9. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines and compute machine sets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the machine set files to create compute machines by using the machine API, but you must update references to them to match your environment.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.4.10. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in VMware vSphere. If you plan to use the cluster identifier as the name of your virtual machine folder, you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
11.4.11. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
Before you install a cluster that contains user-provisioned infrastructure on VMware vSphere, you must create RHCOS machines on vSphere hosts for it to use.
Prerequisites
- You have obtained the Ignition config files for your cluster.
- You have access to an HTTP server that you can access from your computer and that the machines that you create can access.
- You have created a vSphere cluster.
Procedure
-
Upload the bootstrap Ignition config file, which is named
<installation_directory>/bootstrap.ign, that the installation program created to your HTTP server. Note the URL of this file. Save the following secondary Ignition config file for your bootstrap node to your computer as
<installation_directory>/merge-bootstrap.ign:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the URL of the bootstrap Ignition config file that you hosted.
When you create the virtual machine (VM) for the bootstrap machine, you use this Ignition config file.
Locate the following Ignition config files that the installation program created:
-
<installation_directory>/master.ign -
<installation_directory>/worker.ign -
<installation_directory>/merge-bootstrap.ign
-
Convert the Ignition config files to Base64 encoding. Later in this procedure, you must add these files to the extra configuration parameter
guestinfo.ignition.config.datain your VM.For example, if you use a Linux operating system, you can use the
base64command to encode the files.base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64
$ base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64
$ base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64
$ base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS OVA image. Images are available from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The filename contains the OpenShift Container Platform version number in the format
rhcos-vmware.<architecture>.ova.In the vSphere Client, create a folder in your datacenter to store your VMs.
- Click the VMs and Templates view.
- Right-click the name of your datacenter.
- Click New Folder → New VM and Template Folder.
-
In the window that is displayed, enter the folder name. If you did not specify an existing folder in the
install-config.yamlfile, then create a folder with the same name as the infrastructure ID. You use this folder name so vCenter dynamically provisions storage in the appropriate location for its Workspace configuration.
In the vSphere Client, create a template for the OVA image and then clone the template as needed.
NoteIn the following steps, you create a template and then clone the template for all of your cluster machines. You then provide the location for the Ignition config file for that cloned machine type when you provision the VMs.
- From the Hosts and Clusters tab, right-click your cluster name and select Deploy OVF Template.
- On the Select an OVF tab, specify the name of the RHCOS OVA file that you downloaded.
-
On the Select a name and folder tab, set a Virtual machine name for your template, such as
Template-RHCOS. Click the name of your vSphere cluster and select the folder you created in the previous step. - On the Select a compute resource tab, click the name of your vSphere cluster.
On the Select storage tab, configure the storage options for your VM.
- Select Thin Provision or Thick Provision, based on your storage preferences.
-
Select the datastore that you specified in your
install-config.yamlfile.
- On the Select network tab, specify the network that you configured for the cluster, if available.
When creating the OVF template, do not specify values on the Customize template tab or configure the template any further.
ImportantDo not start the original VM template. The VM template must remain off and must be cloned for new RHCOS machines. Starting the VM template configures the VM template as a VM on the platform, which prevents it from being used as a template that machine sets can apply configurations to.
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
control-plane-0orcompute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
On the Select a compute resource tab, select the name of a host in your datacenter.
For a bootstrap machine, specify the URL of the bootstrap Ignition config file that you hosted.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
Optional: Override default DHCP networking in vSphere. To enable static IP networking:
Set your static IP configuration:
export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"
$ export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example command
export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"
$ export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
guestinfo.afterburn.initrd.network-kargsproperty before booting a VM from an OVA in vSphere:govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"$ govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: In the event of cluster performance issues, from the Latency Sensitivity list, select High. Ensure that your VM’s CPU and memory reservation have the following values:
- Memory reservation value must be equal to its configured memory size.
- CPU reservation value must be at least the number of low latency virtual CPUs multiplied by the measured physical CPU speed.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Locate the base-64 encoded files that you created previously in this procedure, and paste the contents of the base64-encoded Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type.
- Complete the configuration and power on the VM.
Create the rest of the machines for your cluster by following the preceding steps for each machine.
ImportantYou must create the bootstrap and control plane machines at this time. Because some pods are deployed on compute machines by default, also create at least two compute machines before you install the cluster.
11.4.12. Creating more Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
You can create more compute machines for your cluster that uses user-provisioned infrastructure on VMware vSphere.
Prerequisites
- Obtain the base64-encoded Ignition file for your compute machines.
- You have access to the vSphere template that you created for your cluster.
Procedure
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template’s name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
compute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
- On the Select a compute resource tab, select the name of a host in your datacenter.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
- From the Latency Sensitivity list, select High.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Paste the contents of the base64-encoded compute Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type. Also, make sure to select the correct network under Add network adapter if there are multiple networks available.
- Complete the configuration and power on the VM.
- Continue to create more compute machines for your cluster.
11.4.13. Disk partitioning
In most cases, data partitions are originally created by installing RHCOS, rather than by installing another operating system. In such cases, the OpenShift Container Platform installer should be allowed to configure your disk partitions.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the vSphere installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
11.4.14. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
11.4.14.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.4.14.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>11.4.14.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.4.15. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
11.4.16. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.4.17. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
11.4.18. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
11.4.18.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
11.4.18.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.4.18.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.4.18.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
11.4.18.2.3. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
11.4.19. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
You can add extra compute machines after the cluster installation is completed by following Adding compute machines to vSphere.
11.4.20. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
11.4.21. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.4.22. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
11.5. Installing a cluster on vSphere with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere infrastructure that you provision with customized network configuration options. By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing MTU and VXLAN configurations.
You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the vSphere platform and the installation process of OpenShift Container Platform. Use the user-provisioned infrastructure installation instructions as a guide; you are free to create the required resources through other methods.
11.5.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
- Completing the installation requires that you upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA on vSphere hosts. The machine from which you complete this process requires access to port 443 on the vCenter and ESXi hosts. Verify that port 443 is accessible.
- If you use a firewall, you confirmed with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
- If you use a firewall, you must configure it to access Red Hat Insights.
11.5.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.5.3. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.5.4. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
11.5.4.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
All virtual machines must reside in the same datastore and in the same folder as the installer.
11.5.4.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
11.5.4.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
11.5.4.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
11.5.5. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
11.5.5.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 11.44. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 11.45. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
Ethernet adaptor hardware address requirements
When provisioning VMs for the cluster, the ethernet interfaces configured for each VM must use a MAC address from the VMware Organizationally Unique Identifier (OUI) allocation ranges:
-
00:05:69:00:00:00to00:05:69:FF:FF:FF -
00:0c:29:00:00:00to00:0c:29:FF:FF:FF -
00:1c:14:00:00:00to00:1c:14:FF:FF:FF -
00:50:56:00:00:00to00:50:56:FF:FF:FF
If a MAC address outside the VMware OUI is used, the cluster installation will not succeed.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
11.5.5.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 11.9. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 11.10. Sample DNS zone database for reverse records
11.5.6. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
11.5.7. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
11.5.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
11.5.8.1. Sample install-config.yaml file for VMware vSphere
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but the compute section is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Although both sections currently define a single machine pool, it is possible that future versions of OpenShift Container Platform will support defining multiple compute pools during installation. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The fully-qualified hostname or IP address of the vCenter server.
- 10
- The name of the user for accessing the server. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere.
- 11
- The password associated with the vSphere user.
- 12
- The vSphere datacenter.
- 13
- The default vSphere datastore to use.
- 14
- Optional: For installer-provisioned infrastructure, the absolute path of an existing folder where the installation program creates the virtual machines, for example,
/<datacenter_name>/vm/<folder_name>/<subfolder_name>. If you do not provide this value, the installation program creates a top-level folder in the datacenter virtual machine folder that is named with the infrastructure ID. If you are providing the infrastructure for the cluster, omit this parameter. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- The pull secret that you obtained from OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 17
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).
11.5.8.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
11.5.9. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
11.5.10. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it. - Create the Ignition config files for your cluster.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster. Remove the Kubernetes manifest files that define the control plane machines and compute machineSets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the MachineSet files to create compute machines by using the machine API, but you must update references to them to match your environment.
11.5.11. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
11.5.11.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
11.5.12. Creating the Ignition config files
Because you must manually start the cluster machines, you must generate the Ignition config files that the cluster needs to make its machines.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Obtain the Ignition config files:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantIf you created an
install-config.yamlfile, specify the directory that contains it. Otherwise, specify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.5.13. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in VMware vSphere. If you plan to use the cluster identifier as the name of your virtual machine folder, you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
11.5.14. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
Before you install a cluster that contains user-provisioned infrastructure on VMware vSphere, you must create RHCOS machines on vSphere hosts for it to use.
Prerequisites
- You have obtained the Ignition config files for your cluster.
- You have access to an HTTP server that you can access from your computer and that the machines that you create can access.
- You have created a vSphere cluster.
Procedure
-
Upload the bootstrap Ignition config file, which is named
<installation_directory>/bootstrap.ign, that the installation program created to your HTTP server. Note the URL of this file. Save the following secondary Ignition config file for your bootstrap node to your computer as
<installation_directory>/merge-bootstrap.ign:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the URL of the bootstrap Ignition config file that you hosted.
When you create the virtual machine (VM) for the bootstrap machine, you use this Ignition config file.
Locate the following Ignition config files that the installation program created:
-
<installation_directory>/master.ign -
<installation_directory>/worker.ign -
<installation_directory>/merge-bootstrap.ign
-
Convert the Ignition config files to Base64 encoding. Later in this procedure, you must add these files to the extra configuration parameter
guestinfo.ignition.config.datain your VM.For example, if you use a Linux operating system, you can use the
base64command to encode the files.base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64
$ base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64
$ base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64
$ base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS OVA image. Images are available from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The filename contains the OpenShift Container Platform version number in the format
rhcos-vmware.<architecture>.ova.In the vSphere Client, create a folder in your datacenter to store your VMs.
- Click the VMs and Templates view.
- Right-click the name of your datacenter.
- Click New Folder → New VM and Template Folder.
-
In the window that is displayed, enter the folder name. If you did not specify an existing folder in the
install-config.yamlfile, then create a folder with the same name as the infrastructure ID. You use this folder name so vCenter dynamically provisions storage in the appropriate location for its Workspace configuration.
In the vSphere Client, create a template for the OVA image and then clone the template as needed.
NoteIn the following steps, you create a template and then clone the template for all of your cluster machines. You then provide the location for the Ignition config file for that cloned machine type when you provision the VMs.
- From the Hosts and Clusters tab, right-click your cluster name and select Deploy OVF Template.
- On the Select an OVF tab, specify the name of the RHCOS OVA file that you downloaded.
-
On the Select a name and folder tab, set a Virtual machine name for your template, such as
Template-RHCOS. Click the name of your vSphere cluster and select the folder you created in the previous step. - On the Select a compute resource tab, click the name of your vSphere cluster.
On the Select storage tab, configure the storage options for your VM.
- Select Thin Provision or Thick Provision, based on your storage preferences.
-
Select the datastore that you specified in your
install-config.yamlfile.
- On the Select network tab, specify the network that you configured for the cluster, if available.
When creating the OVF template, do not specify values on the Customize template tab or configure the template any further.
ImportantDo not start the original VM template. The VM template must remain off and must be cloned for new RHCOS machines. Starting the VM template configures the VM template as a VM on the platform, which prevents it from being used as a template that machine sets can apply configurations to.
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
control-plane-0orcompute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
On the Select a compute resource tab, select the name of a host in your datacenter.
For a bootstrap machine, specify the URL of the bootstrap Ignition config file that you hosted.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
Optional: Override default DHCP networking in vSphere. To enable static IP networking:
Set your static IP configuration:
export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"
$ export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example command
export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"
$ export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
guestinfo.afterburn.initrd.network-kargsproperty before booting a VM from an OVA in vSphere:govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"$ govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: In the event of cluster performance issues, from the Latency Sensitivity list, select High. Ensure that your VM’s CPU and memory reservation have the following values:
- Memory reservation value must be equal to its configured memory size.
- CPU reservation value must be at least the number of low latency virtual CPUs multiplied by the measured physical CPU speed.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Locate the base-64 encoded files that you created previously in this procedure, and paste the contents of the base64-encoded Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type.
- Complete the configuration and power on the VM.
Create the rest of the machines for your cluster by following the preceding steps for each machine.
ImportantYou must create the bootstrap and control plane machines at this time. Because some pods are deployed on compute machines by default, also create at least two compute machines before you install the cluster.
11.5.15. Creating more Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
You can create more compute machines for your cluster that uses user-provisioned infrastructure on VMware vSphere.
Prerequisites
- Obtain the base64-encoded Ignition file for your compute machines.
- You have access to the vSphere template that you created for your cluster.
Procedure
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template’s name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
compute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
- On the Select a compute resource tab, select the name of a host in your datacenter.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
- From the Latency Sensitivity list, select High.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Paste the contents of the base64-encoded compute Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type. Also, make sure to select the correct network under Add network adapter if there are multiple networks available.
- Complete the configuration and power on the VM.
- Continue to create more compute machines for your cluster.
11.5.16. Disk partitioning
In most cases, data partitions are originally created by installing RHCOS, rather than by installing another operating system. In such cases, the OpenShift Container Platform installer should be allowed to configure your disk partitions.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the vSphere installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
11.5.17. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
11.5.18. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.5.19. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
11.5.19.1. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
11.5.19.2. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
11.5.19.3. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.5.19.3.1. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
11.5.20. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
You can add extra compute machines after the cluster installation is completed by following Adding compute machines to vSphere.
11.5.21. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
11.5.22. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.5.23. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
11.6. Installing a cluster on vSphere in a restricted network
In OpenShift Container Platform 4.6, you can install a cluster on VMware vSphere infrastructure in a restricted network by creating an internal mirror of the installation release content.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
11.6.1. Prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
- Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide the ReadWriteMany access mode.
- Review details about the OpenShift Container Platform installation and update processes.
- The OpenShift Container Platform installer requires access to port 443 on the vCenter and ESXi hosts. You verified that port 443 is accessible.
- If you use a firewall, you confirmed with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteIf you are configuring a proxy, be sure to also review this site list.
11.6.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
11.6.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
11.6.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.6.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.6.5. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
11.6.6. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 11.11. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 11.12. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
The VM in your restricted network must have access to vCenter so that it can provision and manage nodes, persistent volume claims (PVCs), and other resources. Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
11.6.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
11.6.8. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.6.9. Creating the RHCOS image for restricted network installations
Download the Red Hat Enterprise Linux CoreOS (RHCOS) image to install OpenShift Container Platform on a restricted network VMware vSphere environment.
Prerequisites
- Obtain the OpenShift Container Platform installation program. For a restricted network installation, the program is on your mirror registry host.
Procedure
- Log in to the Red Hat Customer Portal’s Product Downloads page.
Under Version, select the most recent release of OpenShift Container Platform 4.6 for RHEL 8.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available.
- Download the Red Hat Enterprise Linux CoreOS (RHCOS) - vSphere image.
- Upload the image you downloaded to a location that is accessible from the bastion server.
The image is now available for a restricted installation. Note the image name or location for use in OpenShift Container Platform deployment.
11.6.10. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on VMware vSphere.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
Have the
imageContentSourcesvalues that were generated during mirror registry creation. - Obtain the contents of the certificate for your mirror registry.
- Retrieve a Red Hat Enterprise Linux CoreOS (RHCOS) image and upload it to an accessible location.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
- Select the default vCenter datastore to use.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
- Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
In the
install-config.yamlfile, set the value ofplatform.vsphere.clusterOSImageto the image location or name. For example:platform: vsphere: clusterOSImage: http://mirror.example.com/images/rhcos-43.81.201912131630.0-vmware.x86_64.ova?sha256=ffebbd68e8a1f2a245ca19522c16c86f67f9ac8e4e0c1f0a812b068b16f7265dplatform: vsphere: clusterOSImage: http://mirror.example.com/images/rhcos-43.81.201912131630.0-vmware.x86_64.ova?sha256=ffebbd68e8a1f2a245ca19522c16c86f67f9ac8e4e0c1f0a812b068b16f7265dCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<mirror_host_name>, specify the registry domain name that you specified in the certificate for your mirror registry, and for<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.
Add the image content resources, which look like this excerpt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To complete these values, use the
imageContentSourcesthat you recorded during mirror registry creation.
-
Make any other modifications to the
install-config.yamlfile that you require. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
11.6.10.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
11.6.10.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters and hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
11.6.10.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
11.6.10.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
11.6.10.1.4. Additional VMware vSphere configuration parameters
Additional VMware vSphere configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The fully-qualified hostname or IP address of the vCenter server. | String |
|
| The user name to use to connect to the vCenter instance with. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere. | String |
|
| The password for the vCenter user name. | String |
|
| The name of the datacenter to use in the vCenter instance. | String |
|
| The name of the default datastore to use for provisioning volumes. | String |
|
| Optional. The absolute path of an existing folder where the installation program creates the virtual machines. If you do not provide this value, the installation program creates a folder that is named with the infrastructure ID in the datacenter virtual machine folder. |
String, for example, |
|
| The network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured. | String |
|
| The vCenter cluster to install the OpenShift Container Platform cluster in. | String |
|
| The virtual IP (VIP) address that you configured for control plane API access. |
An IP address, for example |
|
| The virtual IP (VIP) address that you configured for cluster ingress. |
An IP address, for example |
11.6.10.1.5. Optional VMware vSphere machine pool configuration parameters
Optional VMware vSphere machine pool configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. |
An HTTP or HTTPS URL, optionally with a SHA-256 checksum. For example, |
|
| The size of the disk in gigabytes. | Integer |
|
| The total number of virtual processor cores to assign a virtual machine. | Integer |
|
|
The number of cores per socket in a virtual machine. The number of virtual sockets on the virtual machine is | Integer |
|
| The size of a virtual machine’s memory in megabytes. | Integer |
11.6.10.2. Sample install-config.yaml file for an installer-provisioned VMware vSphere cluster
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4 7
- Optional: Provide additional configuration for the machine pool parameters for the compute and control plane machines.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The vSphere cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- 10
- The location of the Red Hat Enterprise Linux CoreOS (RHCOS) image that is accessible from the bastion server.
- 11
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 12
- Provide the contents of the certificate file that you used for your mirror registry.
- 13
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
11.6.10.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
11.6.11. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the location of your customized./install-config.yamlfile. - 2
- To view different installation details, specify
warn,debug, orerrorinstead ofinfo.When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.
+
The cluster access and credential information also outputs to <installation_directory>/.openshift_install.log when an installation succeeds.
+
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
+
You must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
11.6.12. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
11.6.12.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.6.12.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>11.6.12.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>11.6.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.6.14. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
11.6.15. Creating registry storage
After you install the cluster, you must create storage for the Registry Operator.
11.6.15.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
11.6.15.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.6.15.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.6.16. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.6.17. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
11.7. Installing a cluster on vSphere in a restricted network with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere infrastructure that you provision in a restricted network.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
The steps for performing a user-provisioned infrastructure installation are provided as an example only. Installing a cluster with infrastructure you provide requires knowledge of the vSphere platform and the installation process of OpenShift Container Platform. Use the user-provisioned infrastructure installation instructions as a guide; you are free to create the required resources through other methods.
11.7.1. Prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
-
Provision persistent storage for your cluster. To deploy a private image registry, your storage must provide
ReadWriteManyaccess modes. - Review details about the OpenShift Container Platform installation and update processes.
- Completing the installation requires that you upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA on vSphere hosts. The machine from which you complete this process requires access to port 443 on the vCenter and ESXi hosts. You verified that port 443 is accessible.
- If you use a firewall, you confirmed with the administrator that port 443 is accessible. Control plane nodes must be able to reach vCenter and ESXi hosts on port 443 for the installation to succeed.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
11.7.2. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
11.7.2.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
11.7.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
11.7.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
| Optional: Networking (NSX-T) | vSphere 6.5U3 or vSphere 6.7U2 and later | vSphere 6.5U3 or vSphere 6.7U2+ are required for OpenShift Container Platform. VMware’s NSX Container Plug-in (NCP) 3.0.2 is certified with OpenShift Container Platform 4.6 and NSX-T 3.x+. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
11.7.5. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
11.7.5.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
All virtual machines must reside in the same datastore and in the same folder as the installer.
11.7.5.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
11.7.5.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
11.7.5.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
11.7.6. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
11.7.6.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 11.67. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 11.68. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
Ethernet adaptor hardware address requirements
When provisioning VMs for the cluster, the ethernet interfaces configured for each VM must use a MAC address from the VMware Organizationally Unique Identifier (OUI) allocation ranges:
-
00:05:69:00:00:00to00:05:69:FF:FF:FF -
00:0c:29:00:00:00to00:0c:29:FF:FF:FF -
00:1c:14:00:00:00to00:1c:14:FF:FF:FF -
00:50:56:00:00:00to00:50:56:FF:FF:FF
If a MAC address outside the VMware OUI is used, the cluster installation will not succeed.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
11.7.6.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 11.13. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 11.14. Sample DNS zone database for reverse records
11.7.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
11.7.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
-
Obtain the
imageContentSourcessection from the output of the command to mirror the repository. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.-
Unless you use a registry that RHCOS trusts by default, such as
docker.io, you must provide the contents of the certificate for your mirror repository in theadditionalTrustBundlesection. In most cases, you must provide the certificate for your mirror. -
You must include the
imageContentSourcessection from the output of the command to mirror the repository.
-
Unless you use a registry that RHCOS trusts by default, such as
Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
11.7.8.1. Sample install-config.yaml file for VMware vSphere
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but the compute section is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Although both sections currently define a single machine pool, it is possible that future versions of OpenShift Container Platform will support defining multiple compute pools during installation. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The fully-qualified hostname or IP address of the vCenter server.
- 10
- The name of the user for accessing the server. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere.
- 11
- The password associated with the vSphere user.
- 12
- The vSphere datacenter.
- 13
- The default vSphere datastore to use.
- 14
- Optional: For installer-provisioned infrastructure, the absolute path of an existing folder where the installation program creates the virtual machines, for example,
/<datacenter_name>/vm/<folder_name>/<subfolder_name>. If you do not provide this value, the installation program creates a top-level folder in the datacenter virtual machine folder that is named with the infrastructure ID. If you are providing the infrastructure for the cluster, omit this parameter. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 17
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 18
- Provide the contents of the certificate file that you used for your mirror registry.
- 19
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
11.7.8.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
11.7.9. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program. For a restricted network installation, these files are on your mirror host.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines and compute machine sets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the machine set files to create compute machines by using the machine API, but you must update references to them to match your environment.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
11.7.10. Configuring chrony time service
You must set the time server and related settings used by the chrony time service (chronyd) by modifying the contents of the chrony.conf file and passing those contents to your nodes as a machine config.
Procedure
Create the contents of the
chrony.conffile and encode it as base64. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify any valid, reachable time source, such as the one provided by your DHCP server.
Example output
ICAgIHNlcnZlciBjbG9jay5yZWRoYXQuY29tIGlidXJzdAogICAgZHJpZnRmaWxlIC92YXIvbGli L2Nocm9ueS9kcmlmdAogICAgbWFrZXN0ZXAgMS4wIDMKICAgIHJ0Y3N5bmMKICAgIGxvZ2RpciAv dmFyL2xvZy9jaHJvbnkK
ICAgIHNlcnZlciBjbG9jay5yZWRoYXQuY29tIGlidXJzdAogICAgZHJpZnRmaWxlIC92YXIvbGli L2Nocm9ueS9kcmlmdAogICAgbWFrZXN0ZXAgMS4wIDMKICAgIHJ0Y3N5bmMKICAgIGxvZ2RpciAv dmFyL2xvZy9jaHJvbnkKCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
MachineConfigobject file, replacing the base64 string with the one you just created. This example adds the file tomasternodes. You can change it toworkeror make an additional MachineConfig for theworkerrole. Create MachineConfig files for each type of machine that your cluster uses:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify an octal value mode for the
modefield in the machine config file. After creating the file and applying the changes, themodeis converted to a decimal value. You can check the YAML file with the commandoc get mc <mc-name> -o yaml.
- Make a backup copy of the configuration files.
Apply the configurations in one of two ways:
-
If the cluster is not up yet, after you generate manifest files, add this file to the
<installation_directory>/openshiftdirectory, and then continue to create the cluster. If the cluster is already running, apply the file:
oc apply -f ./99-masters-chrony-configuration.yaml
$ oc apply -f ./99-masters-chrony-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
If the cluster is not up yet, after you generate manifest files, add this file to the
11.7.11. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in VMware vSphere. If you plan to use the cluster identifier as the name of your virtual machine folder, you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
11.7.12. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
Before you install a cluster that contains user-provisioned infrastructure on VMware vSphere, you must create RHCOS machines on vSphere hosts for it to use.
Prerequisites
- You have obtained the Ignition config files for your cluster.
- You have access to an HTTP server that you can access from your computer and that the machines that you create can access.
- You have created a vSphere cluster.
Procedure
-
Upload the bootstrap Ignition config file, which is named
<installation_directory>/bootstrap.ign, that the installation program created to your HTTP server. Note the URL of this file. Save the following secondary Ignition config file for your bootstrap node to your computer as
<installation_directory>/merge-bootstrap.ign:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the URL of the bootstrap Ignition config file that you hosted.
When you create the virtual machine (VM) for the bootstrap machine, you use this Ignition config file.
Locate the following Ignition config files that the installation program created:
-
<installation_directory>/master.ign -
<installation_directory>/worker.ign -
<installation_directory>/merge-bootstrap.ign
-
Convert the Ignition config files to Base64 encoding. Later in this procedure, you must add these files to the extra configuration parameter
guestinfo.ignition.config.datain your VM.For example, if you use a Linux operating system, you can use the
base64command to encode the files.base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64
$ base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64
$ base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64
$ base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS OVA image. Images are available from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The filename contains the OpenShift Container Platform version number in the format
rhcos-vmware.<architecture>.ova.In the vSphere Client, create a folder in your datacenter to store your VMs.
- Click the VMs and Templates view.
- Right-click the name of your datacenter.
- Click New Folder → New VM and Template Folder.
-
In the window that is displayed, enter the folder name. If you did not specify an existing folder in the
install-config.yamlfile, then create a folder with the same name as the infrastructure ID. You use this folder name so vCenter dynamically provisions storage in the appropriate location for its Workspace configuration.
In the vSphere Client, create a template for the OVA image and then clone the template as needed.
NoteIn the following steps, you create a template and then clone the template for all of your cluster machines. You then provide the location for the Ignition config file for that cloned machine type when you provision the VMs.
- From the Hosts and Clusters tab, right-click your cluster name and select Deploy OVF Template.
- On the Select an OVF tab, specify the name of the RHCOS OVA file that you downloaded.
-
On the Select a name and folder tab, set a Virtual machine name for your template, such as
Template-RHCOS. Click the name of your vSphere cluster and select the folder you created in the previous step. - On the Select a compute resource tab, click the name of your vSphere cluster.
On the Select storage tab, configure the storage options for your VM.
- Select Thin Provision or Thick Provision, based on your storage preferences.
-
Select the datastore that you specified in your
install-config.yamlfile.
- On the Select network tab, specify the network that you configured for the cluster, if available.
When creating the OVF template, do not specify values on the Customize template tab or configure the template any further.
ImportantDo not start the original VM template. The VM template must remain off and must be cloned for new RHCOS machines. Starting the VM template configures the VM template as a VM on the platform, which prevents it from being used as a template that machine sets can apply configurations to.
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
control-plane-0orcompute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
On the Select a compute resource tab, select the name of a host in your datacenter.
For a bootstrap machine, specify the URL of the bootstrap Ignition config file that you hosted.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
Optional: Override default DHCP networking in vSphere. To enable static IP networking:
Set your static IP configuration:
export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"
$ export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example command
export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"
$ export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
guestinfo.afterburn.initrd.network-kargsproperty before booting a VM from an OVA in vSphere:govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"$ govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: In the event of cluster performance issues, from the Latency Sensitivity list, select High. Ensure that your VM’s CPU and memory reservation have the following values:
- Memory reservation value must be equal to its configured memory size.
- CPU reservation value must be at least the number of low latency virtual CPUs multiplied by the measured physical CPU speed.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Locate the base-64 encoded files that you created previously in this procedure, and paste the contents of the base64-encoded Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type.
- Complete the configuration and power on the VM.
Create the rest of the machines for your cluster by following the preceding steps for each machine.
ImportantYou must create the bootstrap and control plane machines at this time. Because some pods are deployed on compute machines by default, also create at least two compute machines before you install the cluster.
11.7.13. Creating more Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
You can create more compute machines for your cluster that uses user-provisioned infrastructure on VMware vSphere.
Prerequisites
- Obtain the base64-encoded Ignition file for your compute machines.
- You have access to the vSphere template that you created for your cluster.
Procedure
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template’s name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
compute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
- On the Select a compute resource tab, select the name of a host in your datacenter.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
- From the Latency Sensitivity list, select High.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Paste the contents of the base64-encoded compute Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type. Also, make sure to select the correct network under Add network adapter if there are multiple networks available.
- Complete the configuration and power on the VM.
- Continue to create more compute machines for your cluster.
11.7.14. Disk partitioning
In most cases, data partitions are originally created by installing RHCOS, rather than by installing another operating system. In such cases, the OpenShift Container Platform installer should be allowed to configure your disk partitions.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the vSphere installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
11.7.15. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
11.7.16. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.7.17. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
11.7.18. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
11.7.18.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
11.7.18.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
11.7.18.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
11.7.18.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
11.7.18.2.3. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
11.7.19. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
- Register your cluster on the Cluster registration page.
You can add extra compute machines after the cluster installation is completed by following Adding compute machines to vSphere.
11.7.20. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
11.7.21. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
11.7.22. Next steps
- Customize your cluster.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
11.8. Uninstalling a cluster on vSphere that uses installer-provisioned infrastructure
You can remove a cluster that you deployed in your VMware vSphere instance by using installer-provisioned infrastructure.
When you run the openshift-install destroy cluster command to uninstall OpenShift Container Platform, vSphere volumes are not automatically deleted. The cluster administrator must manually find the vSphere volumes and delete them.
11.8.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
Chapter 12. Installing on VMC
12.1. Installing a cluster on VMC
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere by deploying it to VMware Cloud (VMC) on AWS.
Once you have configured your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.1.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Allocate two IP addresses, outside the DHCP range, and configure them with reverse DNS records.
-
A DNS record for
api.<cluster_name>.<base_domain>pointing to the allocated IP address. -
A DNS record for
*.apps.<cluster_name>.<base_domain>pointing to the allocated IP address.
-
A DNS record for
Configure the following firewall rules:
- An ANY:ANY firewall rule between the OpenShift Container Platform compute network and the Internet. This is used by nodes and applications to download container images.
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.1.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.1.2. vSphere prerequisites
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
12.1.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.1.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.1.5. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
12.1.6. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 12.1. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 12.2. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
12.1.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
12.1.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
12.1.9. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.1.10. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Provide values at the prompts:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
Select the default vCenter datastore to use.
NoteDatastore and cluster names cannot exceed 60 characters; therefore, ensure the combined string length does not exceed the 60 character limit.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
NoteDatastore and cluster names cannot exceed 60 characters; therefore, ensure the combined string length does not exceed the 60 character limit.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
ImportantUse the
openshift-installcommand from the bastion hosted in the VMC environment.NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
12.1.11. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
12.1.11.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.1.11.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>12.1.11.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.1.12. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.1.13. Creating registry storage
After you install the cluster, you must create storage for the registry Operator.
12.1.13.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
12.1.13.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.1.13.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.1.13.2.2. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
12.1.14. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
12.1.15. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.1.16. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
12.2. Installing a cluster on VMC with customizations
In OpenShift Container Platform version 4.6, you can install a cluster on your VMware vSphere instance using installer-provisioned infrastructure by deploying it to VMware Cloud (VMC) on AWS.
Once you configure your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
To customize the OpenShift Container Platform installation, you modify parameters in the install-config.yaml file before you install the cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.2.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Allocate two IP addresses, outside the DHCP range, and configure them with reverse DNS records.
-
A DNS record for
api.<cluster_name>.<base_domain>pointing to the allocated IP address. -
A DNS record for
*.apps.<cluster_name>.<base_domain>pointing to the allocated IP address.
-
A DNS record for
Configure the following firewall rules:
- An ANY:ANY firewall rule between the OpenShift Container Platform compute network and the Internet. This is used by nodes and applications to download container images.
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.2.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.2.2. vSphere prerequisites
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
12.2.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.2.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.2.5. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
12.2.6. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 12.3. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 12.4. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
12.2.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
12.2.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
12.2.9. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.2.10. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on VMware vSphere.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
- Select the default vCenter datastore to use.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
- Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
12.2.10.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
12.2.10.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters and hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
12.2.10.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
12.2.10.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
12.2.10.1.4. Additional VMware vSphere configuration parameters
Additional VMware vSphere configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The fully-qualified hostname or IP address of the vCenter server. | String |
|
| The user name to use to connect to the vCenter instance with. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere. | String |
|
| The password for the vCenter user name. | String |
|
| The name of the datacenter to use in the vCenter instance. | String |
|
| The name of the default datastore to use for provisioning volumes. | String |
|
| Optional. The absolute path of an existing folder where the installation program creates the virtual machines. If you do not provide this value, the installation program creates a folder that is named with the infrastructure ID in the datacenter virtual machine folder. |
String, for example, |
|
| The network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured. | String |
|
| The vCenter cluster to install the OpenShift Container Platform cluster in. | String |
|
| The virtual IP (VIP) address that you configured for control plane API access. |
An IP address, for example |
|
| The virtual IP (VIP) address that you configured for cluster ingress. |
An IP address, for example |
12.2.10.1.5. Optional VMware vSphere machine pool configuration parameters
Optional VMware vSphere machine pool configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. |
An HTTP or HTTPS URL, optionally with a SHA-256 checksum. For example, |
|
| The size of the disk in gigabytes. | Integer |
|
| The total number of virtual processor cores to assign a virtual machine. | Integer |
|
|
The number of cores per socket in a virtual machine. The number of virtual sockets on the virtual machine is | Integer |
|
| The size of a virtual machine’s memory in megabytes. | Integer |
12.2.10.2. Sample install-config.yaml file for an installer-provisioned VMware vSphere cluster
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4 7
- Optional: Provide additional configuration for the machine pool parameters for the compute and control plane machines.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The vSphere cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
12.2.10.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
12.2.11. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantUse the
openshift-installcommand from the bastion hosted in the VMC environment.NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
12.2.12. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
12.2.12.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.2.12.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>12.2.12.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.2.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.2.14. Creating registry storage
After you install the cluster, you must create storage for the Registry Operator.
12.2.14.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
12.2.14.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.2.14.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.2.14.2.2. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
12.2.15. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
12.2.16. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.2.17. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
12.3. Installing a cluster on VMC with network customizations
In OpenShift Container Platform version 4.6, you can install a cluster on your VMware vSphere instance using installer-provisioned infrastructure with customized network configuration options by deploying it to VMware Cloud (VMC) on AWS.
Once you configure your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
By customizing your OpenShift Container Platform network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing VXLAN configurations. To customize the installation, you modify parameters in the install-config.yaml file before you install the cluster. You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.3.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Allocate two IP addresses, outside the DHCP range, and configure them with reverse DNS records.
-
A DNS record for
api.<cluster_name>.<base_domain>pointing to the allocated IP address. -
A DNS record for
*.apps.<cluster_name>.<base_domain>pointing to the allocated IP address.
-
A DNS record for
Configure the following firewall rules:
- An ANY:ANY firewall rule between the OpenShift Container Platform compute network and the Internet. This is used by nodes and applications to download container images.
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.3.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.3.2. vSphere prerequisites
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
12.3.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.3.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.3.5. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
12.3.6. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 12.5. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 12.6. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
12.3.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
12.3.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
12.3.9. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.3.10. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on VMware vSphere.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
- Select the default vCenter datastore to use.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
- Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
-
Modify the
install-config.yamlfile. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
12.3.10.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
12.3.10.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters and hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
12.3.10.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
12.3.10.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
12.3.10.1.4. Additional VMware vSphere configuration parameters
Additional VMware vSphere configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The fully-qualified hostname or IP address of the vCenter server. | String |
|
| The user name to use to connect to the vCenter instance with. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere. | String |
|
| The password for the vCenter user name. | String |
|
| The name of the datacenter to use in the vCenter instance. | String |
|
| The name of the default datastore to use for provisioning volumes. | String |
|
| Optional. The absolute path of an existing folder where the installation program creates the virtual machines. If you do not provide this value, the installation program creates a folder that is named with the infrastructure ID in the datacenter virtual machine folder. |
String, for example, |
|
| The network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured. | String |
|
| The vCenter cluster to install the OpenShift Container Platform cluster in. | String |
|
| The virtual IP (VIP) address that you configured for control plane API access. |
An IP address, for example |
|
| The virtual IP (VIP) address that you configured for cluster ingress. |
An IP address, for example |
12.3.10.1.5. Optional VMware vSphere machine pool configuration parameters
Optional VMware vSphere machine pool configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. |
An HTTP or HTTPS URL, optionally with a SHA-256 checksum. For example, |
|
| The size of the disk in gigabytes. | Integer |
|
| The total number of virtual processor cores to assign a virtual machine. | Integer |
|
|
The number of cores per socket in a virtual machine. The number of virtual sockets on the virtual machine is | Integer |
|
| The size of a virtual machine’s memory in megabytes. | Integer |
12.3.10.2. Sample install-config.yaml file for an installer-provisioned VMware vSphere cluster
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4 7
- Optional: Provide additional configuration for the machine pool parameters for the compute and control plane machines.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The vSphere cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
12.3.10.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
12.3.11. Network configuration phases
When specifying a cluster configuration prior to installation, there are several phases in the installation procedures when you can modify the network configuration:
- Phase 1
After entering the
openshift-install create install-configcommand. In theinstall-config.yamlfile, you can customize the following network-related fields:-
networking.networkType -
networking.clusterNetwork -
networking.serviceNetwork networking.machineNetworkFor more information on these fields, refer to "Installation configuration parameters".
NoteSet the
networking.machineNetworkto match the CIDR that the preferred NIC resides in.
-
- Phase 2
-
After entering the
openshift-install create manifestscommand. If you must specify advanced network configuration, during this phase you can define a customized Cluster Network Operator manifest with only the fields you want to modify.
You cannot override the values specified in phase 1 in the install-config.yaml file during phase 2. However, you can further customize the cluster network provider during phase 2.
12.3.12. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster.
12.3.13. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
12.3.13.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
12.3.14. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantUse the
openshift-installcommand from the bastion hosted in the VMC environment.NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
12.3.15. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
12.3.15.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.3.15.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>12.3.15.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.3.16. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.3.17. Creating registry storage
After you install the cluster, you must create storage for the registry Operator.
12.3.17.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
12.3.17.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.3.17.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.3.17.2.2. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
12.3.18. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
12.3.19. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.3.20. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
12.4. Installing a cluster on VMC in a restricted network
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere infrastructure in a restricted network by deploying it to VMware Cloud (VMC) on AWS.
Once you configure your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.4.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Allocate two IP addresses, outside the DHCP range, and configure them with reverse DNS records.
-
A DNS record for
api.<cluster_name>.<base_domain>pointing to the allocated IP address. -
A DNS record for
*.apps.<cluster_name>.<base_domain>pointing to the allocated IP address.
-
A DNS record for
Configure the following firewall rules:
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.4.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.4.2. vSphere prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteIf you are configuring a proxy, be sure to also review this site list.
12.4.3. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
12.4.3.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
12.4.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.4.5. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.4.6. Network connectivity requirements
You must configure the network connectivity between machines to allow OpenShift Container Platform cluster components to communicate.
Review the following details about the required network ports.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| virtual extensible LAN (VXLAN) |
|
| Geneve | |
|
|
Host level services, including the node exporter on ports | |
|
| IPsec IKE packets | |
|
| IPsec NAT-T packets | |
| TCP/UDP |
| Kubernetes node port |
| ESP | N/A | IPsec Encapsulating Security Payload (ESP) |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
12.4.7. vCenter requirements
Before you install an OpenShift Container Platform cluster on your vCenter that uses infrastructure that the installer provisions, you must prepare your environment.
Required vCenter account privileges
To install an OpenShift Container Platform cluster in a vCenter, the installation program requires access to an account with privileges to read and create the required resources. Using an account that has global administrative privileges is the simplest way to access all of the necessary permissions.
If you cannot use an account with global administrative privileges, you must create roles to grant the privileges necessary for OpenShift Container Platform cluster installation. While most of the privileges are always required, some are required only if you plan for the installation program to provision a folder to contain the OpenShift Container Platform cluster on your vCenter instance, which is the default behavior. You must create or amend vSphere roles for the specified objects to grant the required privileges.
An additional role is required if the installation program is to create a vSphere virtual machine folder.
Example 12.7. Roles and privileges required for installation
| vSphere object for role | When required | Required privileges |
|---|---|---|
| vSphere vCenter | Always |
|
| vSphere vCenter Cluster | Always |
|
| vSphere Datastore | Always |
|
| vSphere Port Group | Always |
|
| Virtual Machine Folder | Always |
|
| vSphere vCenter Datacenter | If the installation program creates the virtual machine folder |
|
Additionally, the user requires some ReadOnly permissions, and some of the roles require permission to propogate the permissions to child objects. These settings vary depending on whether or not you install the cluster into an existing folder.
Example 12.8. Required permissions and propagation settings
| vSphere object | Folder type | Propagate to children | Permissions required |
|---|---|---|---|
| vSphere vCenter | Always | False | Listed required privileges |
| vSphere vCenter Datacenter | Existing folder | False |
|
| Installation program creates the folder | True | Listed required privileges | |
| vSphere vCenter Cluster | Always | True | Listed required privileges |
| vSphere vCenter Datastore | Always | False | Listed required privileges |
| vSphere Switch | Always | False |
|
| vSphere Port Group | Always | False | Listed required privileges |
| vSphere vCenter Virtual Machine Folder | Existing folder | True | Listed required privileges |
For more information about creating an account with only the required privileges, see vSphere Permissions and User Management Tasks in the vSphere documentation.
Using OpenShift Container Platform with vMotion
If you intend on using vMotion in your vSphere environment, consider the following before installing a OpenShift Container Platform cluster.
OpenShift Container Platform generally supports compute-only vMotion. Using Storage vMotion can cause issues and is not supported.
To help ensure the uptime of your compute and control plane nodes, it is recommended that you follow the VMware best practices for vMotion. It is also recommended to use VMware anti-affinity rules to improve the availability of OpenShift Container Platform during maintenance or hardware issues.
For more information about vMotion and anti-affinity rules, see the VMware vSphere documentation for vMotion networking requirements and VM anti-affinity rules.
- If you are using vSphere volumes in your pods, migrating a VM across datastores either manually or through Storage vMotion causes, invalid references within OpenShift Container Platform persistent volume (PV) objects. These references prevent affected pods from starting up and can result in data loss.
- Similarly, OpenShift Container Platform does not support selective migration of VMDKs across datastores, using datastore clusters for VM provisioning or for dynamic or static provisioning of PVs, or using a datastore that is part of a datastore cluster for dynamic or static provisioning of PVs.
Cluster resources
When you deploy an OpenShift Container Platform cluster that uses installer-provisioned infrastructure, the installation program must be able to create several resources in your vCenter instance.
A standard OpenShift Container Platform installation creates the following vCenter resources:
- 1 Folder
- 1 Tag category
- 1 Tag
Virtual machines:
- 1 template
- 1 temporary bootstrap node
- 3 control plane nodes
- 3 compute machines
Although these resources use 856 GB of storage, the bootstrap node is destroyed during the cluster installation process. A minimum of 800 GB of storage is required to use a standard cluster.
If you deploy more compute machines, the OpenShift Container Platform cluster will use more storage.
Cluster limits
Available resources vary between clusters. The number of possible clusters within a vCenter is limited primarily by available storage space and any limitations on the number of required resources. Be sure to consider both limitations to the vCenter resources that the cluster creates and the resources that you require to deploy a cluster, such as IP addresses and networks.
Networking requirements
You must use DHCP for the network and ensure that the DHCP server is configured to provide persistent IP addresses to the cluster machines.
Persistent IP addresses are not available before the installation begins. Allocate a DHCP range and, after installation, manually replace the allocation with the persistent IP addresses.
The VM in your restricted network must have access to vCenter so that it can provision and manage nodes, persistent volume claims (PVCs), and other resources. Additionally, you must create the following networking resources before you install the OpenShift Container Platform cluster:
It is recommended that each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server that is discoverable via DHCP. Installation is possible without an NTP server. However, asynchronous server clocks will cause errors, which NTP server prevents.
Required IP Addresses
An installer-provisioned vSphere installation requires these static IP addresses:
- The API address is used to access the cluster API.
- The Ingress address is used for cluster ingress traffic.
- The control plane node addresses are used when upgrading a cluster from version 4.5 to 4.6.
You must provide these IP addresses to the installation program when you install the OpenShift Container Platform cluster.
DNS records
You must create DNS records for two static IP addresses in the appropriate DNS server for the vCenter instance that hosts your OpenShift Container Platform cluster. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify when you install the cluster. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| API VIP |
| This DNS A/AAAA or CNAME record must point to the load balancer for the control plane machines. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Ingress VIP |
| A wildcard DNS A/AAAA or CNAME record that points to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. This record must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
12.4.8. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
12.4.9. Adding vCenter root CA certificates to your system trust
Because the installation program requires access to your vCenter’s API, you must add your vCenter’s trusted root CA certificates to your system trust before you install an OpenShift Container Platform cluster.
Procedure
-
From the vCenter home page, download the vCenter’s root CA certificates. Click Download trusted root CA certificates in the vSphere Web Services SDK section. The
<vCenter>/certs/download.zipfile downloads. Extract the compressed file that contains the vCenter root CA certificates. The contents of the compressed file resemble the following file structure:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Add the files for your operating system to the system trust. For example, on a Fedora operating system, run the following command:
cp certs/lin/* /etc/pki/ca-trust/source/anchors
# cp certs/lin/* /etc/pki/ca-trust/source/anchorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Update your system trust. For example, on a Fedora operating system, run the following command:
update-ca-trust extract
# update-ca-trust extractCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.4.10. Creating the RHCOS image for restricted network installations
Download the Red Hat Enterprise Linux CoreOS (RHCOS) image to install OpenShift Container Platform on a restricted network VMware vSphere environment.
Prerequisites
- Obtain the OpenShift Container Platform installation program. For a restricted network installation, the program is on your mirror registry host.
Procedure
- Log in to the Red Hat Customer Portal’s Product Downloads page.
Under Version, select the most recent release of OpenShift Container Platform 4.6 for RHEL 8.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available.
- Download the Red Hat Enterprise Linux CoreOS (RHCOS) - vSphere image.
- Upload the image you downloaded to a location that is accessible from the bastion server.
The image is now available for a restricted installation. Note the image name or location for use in OpenShift Container Platform deployment.
12.4.11. Creating the installation configuration file
You can customize the OpenShift Container Platform cluster you install on VMware vSphere.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
-
Have the
imageContentSourcesvalues that were generated during mirror registry creation. - Obtain the contents of the certificate for your mirror registry.
- Retrieve a Red Hat Enterprise Linux CoreOS (RHCOS) image and upload it to an accessible location.
Procedure
Create the
install-config.yamlfile.Change to the directory that contains the installation program and run the following command:
./openshift-install create install-config --dir <installation_directory>
$ ./openshift-install create install-config --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantSpecify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
At the prompts, provide the configuration details for your cloud:
Optional: Select an SSH key to use to access your cluster machines.
NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.- Select vsphere as the platform to target.
- Specify the name of your vCenter instance.
Specify the user name and password for the vCenter account that has the required permissions to create the cluster.
The installation program connects to your vCenter instance.
- Select the datacenter in your vCenter instance to connect to.
- Select the default vCenter datastore to use.
- Select the vCenter cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- Select the network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured.
- Enter the virtual IP address that you configured for control plane API access.
- Enter the virtual IP address that you configured for cluster ingress.
- Enter the base domain. This base domain must be the same one that you used in the DNS records that you configured.
- Enter a descriptive name for your cluster. The cluster name must be the same one that you used in the DNS records that you configured.
- Paste the pull secret from the Red Hat OpenShift Cluster Manager.
In the
install-config.yamlfile, set the value ofplatform.vsphere.clusterOSImageto the image location or name. For example:platform: vsphere: clusterOSImage: http://mirror.example.com/images/rhcos-43.81.201912131630.0-vmware.x86_64.ova?sha256=ffebbd68e8a1f2a245ca19522c16c86f67f9ac8e4e0c1f0a812b068b16f7265dplatform: vsphere: clusterOSImage: http://mirror.example.com/images/rhcos-43.81.201912131630.0-vmware.x86_64.ova?sha256=ffebbd68e8a1f2a245ca19522c16c86f67f9ac8e4e0c1f0a812b068b16f7265dCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the
install-config.yamlfile to provide the additional information that is required for an installation in a restricted network.Update the
pullSecretvalue to contain the authentication information for your registry:pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'pullSecret: '{"auths":{"<mirror_host_name>:5000": {"auth": "<credentials>","email": "you@example.com"}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow For
<mirror_host_name>, specify the registry domain name that you specified in the certificate for your mirror registry, and for<credentials>, specify the base64-encoded user name and password for your mirror registry.Add the
additionalTrustBundleparameter and value.additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----
additionalTrustBundle: | -----BEGIN CERTIFICATE----- ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ -----END CERTIFICATE-----Copy to Clipboard Copied! Toggle word wrap Toggle overflow The value must be the contents of the certificate file that you used for your mirror registry, which can be an existing, trusted certificate authority or the self-signed certificate that you generated for the mirror registry.
Add the image content resources, which look like this excerpt:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow To complete these values, use the
imageContentSourcesthat you recorded during mirror registry creation.
-
Make any other modifications to the
install-config.yamlfile that you require. You can find more information about the available parameters in the Installation configuration parameters section. Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the installation process. If you want to reuse the file, you must back it up now.
12.4.11.1. Installation configuration parameters
Before you deploy an OpenShift Container Platform cluster, you provide parameter values to describe your account on the cloud platform that hosts your cluster and optionally customize your cluster’s platform. When you create the install-config.yaml installation configuration file, you provide values for the required parameters through the command line. If you customize your cluster, you can modify the install-config.yaml file to provide more details about the platform.
After installation, you cannot modify these parameters in the install-config.yaml file.
The openshift-install command does not validate field names for parameters. If an incorrect name is specified, the related file or object is not created, and no error is reported. Ensure that the field names for any parameters that are specified are correct.
12.4.11.1.1. Required configuration parameters
Required installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
|
The API version for the | String |
|
|
The base domain of your cloud provider. The base domain is used to create routes to your OpenShift Container Platform cluster components. The full DNS name for your cluster is a combination of the |
A fully-qualified domain or subdomain name, such as |
|
|
Kubernetes resource | Object |
|
|
The name of the cluster. DNS records for the cluster are all subdomains of |
String of lowercase letters and hyphens ( |
|
|
The configuration for the specific platform upon which to perform the installation: | Object |
|
| Get a pull secret from the Red Hat OpenShift Cluster Manager to authenticate downloading container images for OpenShift Container Platform components from services such as Quay.io. |
|
12.4.11.1.2. Network configuration parameters
You can customize your installation configuration based on the requirements of your existing network infrastructure. For example, you can expand the IP address block for the cluster network or provide different IP address blocks than the defaults.
Only IPv4 addresses are supported.
| Parameter | Description | Values |
|---|---|---|
|
| The configuration for the cluster network. | Object Note
You cannot modify parameters specified by the |
|
| The cluster network provider Container Network Interface (CNI) plug-in to install. |
Either |
|
| The IP address blocks for pods.
The default value is If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
|
|
|
Required if you use An IPv4 network. |
An IP address block in Classless Inter-Domain Routing (CIDR) notation. The prefix length for an IPv4 block is between |
|
|
The subnet prefix length to assign to each individual node. For example, if | A subnet prefix.
The default value is |
|
|
The IP address block for services. The default value is The OpenShift SDN and OVN-Kubernetes network providers support only a single IP address block for the service network. | An array with an IP address block in CIDR format. For example: networking: serviceNetwork: - 172.30.0.0/16 |
|
| The IP address blocks for machines. If you specify multiple IP address blocks, the blocks must not overlap. | An array of objects. For example: networking: machineNetwork: - cidr: 10.0.0.0/16 |
|
|
Required if you use | An IP network block in CIDR notation.
For example, Note
Set the |
12.4.11.1.3. Optional configuration parameters
Optional installation configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| A PEM-encoded X.509 certificate bundle that is added to the nodes' trusted certificate store. This trust bundle may also be used when a proxy has been configured. | String |
|
| The configuration for the machines that comprise the compute nodes. | Array of machine-pool objects. For details, see the following "Machine-pool" table. |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heteregeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of compute machines, which are also known as worker machines, to provision. |
A positive integer greater than or equal to |
|
| The configuration for the machines that comprise the control plane. |
Array of |
|
|
Determines the instruction set architecture of the machines in the pool. Currently, heterogeneous clusters are not supported, so all pools must specify the same architecture. Valid values are | String |
|
|
Whether to enable or disable simultaneous multithreading, or Important If you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. |
|
|
|
Required if you use |
|
|
|
Required if you use |
|
|
| The number of control plane machines to provision. |
The only supported value is |
|
| The Cloud Credential Operator (CCO) mode. If no mode is specified, the CCO dynamically tries to determine the capabilities of the provided credentials, with a preference for mint mode on the platforms where multiple modes are supported. Note Not all CCO modes are supported for all cloud providers. For more information on CCO modes, see the Cloud Credential Operator entry in the Red Hat Operators reference content. |
|
|
|
Enable or disable FIPS mode. The default is Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the Note If you are using Azure File storage, you cannot enable FIPS mode. |
|
|
| Sources and repositories for the release-image content. |
Array of objects. Includes a |
|
|
Required if you use | String |
|
| Specify one or more repositories that may also contain the same images. | Array of strings |
|
| How to publish or expose the user-facing endpoints of your cluster, such as the Kubernetes API, OpenShift routes. |
Setting this field to Important
If the value of the field is set to |
|
| The SSH key or keys to authenticate access your cluster machines. Note
For production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your | One or more keys. For example: sshKey: <key1> <key2> <key3> |
12.4.11.1.4. Additional VMware vSphere configuration parameters
Additional VMware vSphere configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The fully-qualified hostname or IP address of the vCenter server. | String |
|
| The user name to use to connect to the vCenter instance with. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere. | String |
|
| The password for the vCenter user name. | String |
|
| The name of the datacenter to use in the vCenter instance. | String |
|
| The name of the default datastore to use for provisioning volumes. | String |
|
| Optional. The absolute path of an existing folder where the installation program creates the virtual machines. If you do not provide this value, the installation program creates a folder that is named with the infrastructure ID in the datacenter virtual machine folder. |
String, for example, |
|
| The network in the vCenter instance that contains the virtual IP addresses and DNS records that you configured. | String |
|
| The vCenter cluster to install the OpenShift Container Platform cluster in. | String |
|
| The virtual IP (VIP) address that you configured for control plane API access. |
An IP address, for example |
|
| The virtual IP (VIP) address that you configured for cluster ingress. |
An IP address, for example |
12.4.11.1.5. Optional VMware vSphere machine pool configuration parameters
Optional VMware vSphere machine pool configuration parameters are described in the following table:
| Parameter | Description | Values |
|---|---|---|
|
| The location from which the installer downloads the RHCOS image. You must set this parameter to perform an installation in a restricted network. |
An HTTP or HTTPS URL, optionally with a SHA-256 checksum. For example, |
|
| The size of the disk in gigabytes. | Integer |
|
| The total number of virtual processor cores to assign a virtual machine. | Integer |
|
|
The number of cores per socket in a virtual machine. The number of virtual sockets on the virtual machine is | Integer |
|
| The size of a virtual machine’s memory in megabytes. | Integer |
12.4.11.2. Sample install-config.yaml file for an installer-provisioned VMware vSphere cluster
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4 7
- Optional: Provide additional configuration for the machine pool parameters for the compute and control plane machines.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The vSphere cluster to install the OpenShift Container Platform cluster in. The installation program uses the root resource pool of the vSphere cluster as the default resource pool.
- 10
- The location of the Red Hat Enterprise Linux CoreOS (RHCOS) image that is accessible from the bastion server.
- 11
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 12
- Provide the contents of the certificate file that you used for your mirror registry.
- 13
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
12.4.11.3. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
12.4.12. Deploying the cluster
You can install OpenShift Container Platform on a compatible cloud platform.
You can run the create cluster command of the installation program only once, during initial installation.
Prerequisites
- Configure an account with the cloud platform that hosts your cluster.
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster.
Procedure
Change to the directory that contains the installation program and initialize the cluster deployment:
./openshift-install create cluster --dir <installation_directory> \ --log-level=info$ ./openshift-install create cluster --dir <installation_directory> \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantUse the
openshift-installcommand from the bastion hosted in the VMC environment.NoteIf the cloud provider account that you configured on your host does not have sufficient permissions to deploy the cluster, the installation process stops, and the missing permissions are displayed.
When the cluster deployment completes, directions for accessing your cluster, including a link to its web console and credentials for the
kubeadminuser, display in your terminal.Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe cluster access and credential information also outputs to
<installation_directory>/.openshift_install.logwhen an installation succeeds.Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
ImportantYou must not delete the installation program or the files that the installation program creates. Both are required to delete the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
12.4.13. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
12.4.13.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.4.13.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>12.4.13.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.4.14. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.4.15. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
12.4.16. Creating registry storage
After you install the cluster, you must create storage for the Registry Operator.
12.4.16.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
12.4.16.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.4.16.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.4.17. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.4.18. Next steps
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
12.5. Installing a cluster on VMC with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere infrastructure that you provision by deploying it to VMware Cloud (VMC) on AWS.
Once you configure your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.5.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Configure the following firewall rules:
- An ANY:ANY firewall rule between the OpenShift Container Platform compute network and the Internet. This is used by nodes and applications to download container images.
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.5.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.5.2. vSphere prerequisites
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
12.5.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.5.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.5.5. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
12.5.5.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
12.5.5.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
12.5.5.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
12.5.5.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
12.5.6. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
12.5.6.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 12.46. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 12.47. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
12.5.6.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 12.9. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 12.10. Sample DNS zone database for reverse records
12.5.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
12.5.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
12.5.9. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
12.5.9.1. Sample install-config.yaml file for VMware vSphere
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but the compute section is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Although both sections currently define a single machine pool, it is possible that future versions of OpenShift Container Platform will support defining multiple compute pools during installation. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The fully-qualified hostname or IP address of the vCenter server.
- 10
- The name of the user for accessing the server. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere.
- 11
- The password associated with the vSphere user.
- 12
- The vSphere datacenter.
- 13
- The default vSphere datastore to use.
- 14
- Optional: For installer-provisioned infrastructure, the absolute path of an existing folder where the installation program creates the virtual machines, for example,
/<datacenter_name>/vm/<folder_name>/<subfolder_name>. If you do not provide this value, the installation program creates a top-level folder in the datacenter virtual machine folder that is named with the infrastructure ID. If you are providing the infrastructure for the cluster, omit this parameter. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- The pull secret that you obtained from OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 17
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).
12.5.9.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
12.5.10. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines and compute machine sets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the machine set files to create compute machines by using the machine API, but you must update references to them to match your environment.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.5.11. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in VMware Cloud on AWS. If you plan to use the cluster identifier as the name of your virtual machine folder, you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
12.5.12. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
Before you install a cluster that contains user-provisioned infrastructure on VMware vSphere, you must create RHCOS machines on vSphere hosts for it to use.
Prerequisites
- You have obtained the Ignition config files for your cluster.
- You have access to an HTTP server that you can access from your computer and that the machines that you create can access.
- You have created a vSphere cluster.
Procedure
-
Upload the bootstrap Ignition config file, which is named
<installation_directory>/bootstrap.ign, that the installation program created to your HTTP server. Note the URL of this file. Save the following secondary Ignition config file for your bootstrap node to your computer as
<installation_directory>/merge-bootstrap.ign:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the URL of the bootstrap Ignition config file that you hosted.
When you create the virtual machine (VM) for the bootstrap machine, you use this Ignition config file.
Locate the following Ignition config files that the installation program created:
-
<installation_directory>/master.ign -
<installation_directory>/worker.ign -
<installation_directory>/merge-bootstrap.ign
-
Convert the Ignition config files to Base64 encoding. Later in this procedure, you must add these files to the extra configuration parameter
guestinfo.ignition.config.datain your VM.For example, if you use a Linux operating system, you can use the
base64command to encode the files.base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64
$ base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64
$ base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64
$ base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS OVA image. Images are available from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The filename contains the OpenShift Container Platform version number in the format
rhcos-vmware.<architecture>.ova.In the vSphere Client, create a folder in your datacenter to store your VMs.
- Click the VMs and Templates view.
- Right-click the name of your datacenter.
- Click New Folder → New VM and Template Folder.
-
In the window that is displayed, enter the folder name. If you did not specify an existing folder in the
install-config.yamlfile, then create a folder with the same name as the infrastructure ID. You use this folder name so vCenter dynamically provisions storage in the appropriate location for its Workspace configuration.
In the vSphere Client, create a template for the OVA image and then clone the template as needed.
NoteIn the following steps, you create a template and then clone the template for all of your cluster machines. You then provide the location for the Ignition config file for that cloned machine type when you provision the VMs.
- From the Hosts and Clusters tab, right-click your cluster name and select Deploy OVF Template.
- On the Select an OVF tab, specify the name of the RHCOS OVA file that you downloaded.
-
On the Select a name and folder tab, set a Virtual machine name for your template, such as
Template-RHCOS. Click the name of your vSphere cluster and select the folder you created in the previous step. - On the Select a compute resource tab, click the name of your vSphere cluster.
On the Select storage tab, configure the storage options for your VM.
- Select Thin Provision or Thick Provision, based on your storage preferences.
-
Select the datastore that you specified in your
install-config.yamlfile.
- On the Select network tab, specify the network that you configured for the cluster, if available.
When creating the OVF template, do not specify values on the Customize template tab or configure the template any further.
ImportantDo not start the original VM template. The VM template must remain off and must be cloned for new RHCOS machines. Starting the VM template configures the VM template as a VM on the platform, which prevents it from being used as a template that machine sets can apply configurations to.
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
control-plane-0orcompute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
On the Select a compute resource tab, select the name of a host in your datacenter.
For a bootstrap machine, specify the URL of the bootstrap Ignition config file that you hosted.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
Optional: Override default DHCP networking in vSphere. To enable static IP networking:
Set your static IP configuration:
export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"
$ export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example command
export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"
$ export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
guestinfo.afterburn.initrd.network-kargsproperty before booting a VM from an OVA in vSphere:govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"$ govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: In the event of cluster performance issues, from the Latency Sensitivity list, select High. Ensure that your VM’s CPU and memory reservation have the following values:
- Memory reservation value must be equal to its configured memory size.
- CPU reservation value must be at least the number of low latency virtual CPUs multiplied by the measured physical CPU speed.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Locate the base-64 encoded files that you created previously in this procedure, and paste the contents of the base64-encoded Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type.
- Complete the configuration and power on the VM.
Create the rest of the machines for your cluster by following the preceding steps for each machine.
ImportantYou must create the bootstrap and control plane machines at this time. Because some pods are deployed on compute machines by default, also create at least two compute machines before you install the cluster.
12.5.13. Creating more Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
You can create more compute machines for your cluster that uses user-provisioned infrastructure on VMware vSphere.
Prerequisites
- Obtain the base64-encoded Ignition file for your compute machines.
- You have access to the vSphere template that you created for your cluster.
Procedure
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template’s name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
compute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
- On the Select a compute resource tab, select the name of a host in your datacenter.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
- From the Latency Sensitivity list, select High.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Paste the contents of the base64-encoded compute Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type. Also, make sure to select the correct network under Add network adapter if there are multiple networks available.
- Complete the configuration and power on the VM.
- Continue to create more compute machines for your cluster.
12.5.14. Disk partitioning
In most cases, data partitions are originally created by installing RHCOS, rather than by installing another operating system. In such cases, the OpenShift Container Platform installer should be allowed to configure your disk partitions.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the vSphere installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
12.5.15. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
12.5.15.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.5.15.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>12.5.15.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>12.5.16. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
12.5.17. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.5.18. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
12.5.19. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
12.5.19.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
12.5.19.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.5.19.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.5.19.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
12.5.19.2.3. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
12.5.20. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
You can add extra compute machines after the cluster installation is completed by following Adding compute machines to vSphere.
12.5.21. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
12.5.22. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.5.23. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
12.6. Installing a cluster on VMC with user-provisioned infrastructure and network customizations
In OpenShift Container Platform version 4.6, you can install a cluster on your VMware vSphere instance using infrastructure you provision with customized network configuration options by deploying it to VMware Cloud (VMC) on AWS.
Once you configure your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
By customizing your network configuration, your cluster can coexist with existing IP address allocations in your environment and integrate with existing VXLAN configurations. You must set most of the network configuration parameters during installation, and you can modify only kubeProxy configuration parameters in a running cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.6.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Configure the following firewall rules:
- An ANY:ANY firewall rule between the OpenShift Container Platform compute network and the Internet. This is used by nodes and applications to download container images.
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.6.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.6.2. vSphere prerequisites
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
- If you use a firewall, you must configure it to access Red Hat Insights.
12.6.3. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.6.4. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.6.5. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
12.6.5.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
12.6.5.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
12.6.5.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
12.6.5.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
12.6.6. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
12.6.6.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 12.54. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 12.55. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
12.6.6.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 12.11. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 12.12. Sample DNS zone database for reverse records
12.6.7. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program.
12.6.8. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
12.6.9. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
12.6.9.1. Sample install-config.yaml file for VMware vSphere
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but the compute section is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Although both sections currently define a single machine pool, it is possible that future versions of OpenShift Container Platform will support defining multiple compute pools during installation. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The fully-qualified hostname or IP address of the vCenter server.
- 10
- The name of the user for accessing the server. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere.
- 11
- The password associated with the vSphere user.
- 12
- The vSphere datacenter.
- 13
- The default vSphere datastore to use.
- 14
- Optional: For installer-provisioned infrastructure, the absolute path of an existing folder where the installation program creates the virtual machines, for example,
/<datacenter_name>/vm/<folder_name>/<subfolder_name>. If you do not provide this value, the installation program creates a top-level folder in the datacenter virtual machine folder that is named with the infrastructure ID. If you are providing the infrastructure for the cluster, omit this parameter. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- The pull secret that you obtained from OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 17
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).
12.6.9.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
12.6.10. Specifying advanced network configuration
You can use advanced configuration customization to integrate your cluster into your existing network environment by specifying additional configuration for your cluster network provider. You can specify advanced network configuration only before you install the cluster.
Modifying the OpenShift Container Platform manifest files created by the installation program is not supported. Applying a manifest file that you create, as in the following procedure, is supported.
Prerequisites
-
Create the
install-config.yamlfile and complete any modifications to it. - Create the Ignition config files for your cluster.
Procedure
Change to the directory that contains the installation program and create the manifests:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the name of the directory that contains the
install-config.yamlfile for your cluster.
Create a stub manifest file for the advanced network configuration that is named
cluster-network-03-config.ymlin the<installation_directory>/manifests/directory:Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
<installation_directory>-
Specifies the directory name that contains the
manifests/directory for your cluster.
Open the
cluster-network-03-config.ymlfile in an editor and specify the advanced network configuration for your cluster, such as in the following example:Specify a different VXLAN port for the OpenShift SDN network provider
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Save the
cluster-network-03-config.ymlfile and quit the text editor. -
Optional: Back up the
manifests/cluster-network-03-config.ymlfile. The installation program deletes themanifests/directory when creating the cluster. Remove the Kubernetes manifest files that define the control plane machines and compute machineSets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the MachineSet files to create compute machines by using the machine API, but you must update references to them to match your environment.
12.6.11. Cluster Network Operator configuration
The configuration for the cluster network is specified as part of the Cluster Network Operator (CNO) configuration and stored in a custom resource (CR) object that is named cluster. The CR specifies the fields for the Network API in the operator.openshift.io API group.
The CNO configuration inherits the following fields during cluster installation from the Network API in the Network.config.openshift.io API group and these fields cannot be changed:
clusterNetwork- IP address pools from which pod IP addresses are allocated.
serviceNetwork- IP address pool for services.
defaultNetwork.type- Cluster network provider, such as OpenShift SDN or OVN-Kubernetes.
You can specify the cluster network provider configuration for your cluster by setting the fields for the defaultNetwork object in the CNO object named cluster.
12.6.11.1. Cluster Network Operator configuration object
The fields for the Cluster Network Operator (CNO) are described in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The name of the CNO object. This name is always |
|
|
| A list specifying the blocks of IP addresses from which pod IP addresses are allocated and the subnet prefix length assigned to each individual node in the cluster. For example:
This value is ready-only and specified in the |
|
|
| A block of IP addresses for services. The OpenShift SDN and OVN-Kubernetes Container Network Interface (CNI) network providers support only a single IP address block for the service network. For example: spec: serviceNetwork: - 172.30.0.0/14
This value is ready-only and specified in the |
|
|
| Configures the Container Network Interface (CNI) cluster network provider for the cluster network. |
|
|
| The fields for this object specify the kube-proxy configuration. If you are using the OVN-Kubernetes cluster network provider, the kube-proxy configuration has no effect. |
defaultNetwork object configuration
The values for the defaultNetwork object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
Either Note OpenShift Container Platform uses the OpenShift SDN Container Network Interface (CNI) cluster network provider by default. |
|
|
| This object is only valid for the OpenShift SDN cluster network provider. |
|
|
| This object is only valid for the OVN-Kubernetes cluster network provider. |
Configuration for the OpenShift SDN CNI cluster network provider
The following table describes the configuration fields for the OpenShift SDN Container Network Interface (CNI) cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
|
Configures the network isolation mode for OpenShift SDN. The default value is
The values |
|
|
| The maximum transmission unit (MTU) for the VXLAN overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all VXLAN packets. The default value is If you are running in a virtualized environment with existing nodes that are part of another VXLAN network, then you might be required to change this. For example, when running an OpenShift SDN overlay on top of VMware NSX-T, you must select an alternate port for the VXLAN, because both SDNs use the same default VXLAN port number.
On Amazon Web Services (AWS), you can select an alternate port for the VXLAN between port |
Example OpenShift SDN configuration
Configuration for the OVN-Kubernetes CNI cluster network provider
The following table describes the configuration fields for the OVN-Kubernetes CNI cluster network provider.
| Field | Type | Description |
|---|---|---|
|
|
| The maximum transmission unit (MTU) for the Geneve (Generic Network Virtualization Encapsulation) overlay network. This is detected automatically based on the MTU of the primary network interface. You do not normally need to override the detected MTU. If the auto-detected value is not what you expected it to be, confirm that the MTU on the primary network interface on your nodes is correct. You cannot use this option to change the MTU value of the primary network interface on the nodes.
If your cluster requires different MTU values for different nodes, you must set this value to This value cannot be changed after cluster installation. |
|
|
|
The port to use for all Geneve packets. The default value is |
Example OVN-Kubernetes configuration
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081
defaultNetwork:
type: OVNKubernetes
ovnKubernetesConfig:
mtu: 1400
genevePort: 6081kubeProxyConfig object configuration
The values for the kubeProxyConfig object are defined in the following table:
| Field | Type | Description |
|---|---|---|
|
|
|
The refresh period for Note
Because of performance improvements introduced in OpenShift Container Platform 4.3 and greater, adjusting the |
|
|
|
The minimum duration before refreshing kubeProxyConfig:
proxyArguments:
iptables-min-sync-period:
- 0s
|
12.6.12. Creating the Ignition config files
Because you must manually start the cluster machines, you must generate the Ignition config files that the cluster needs to make its machines.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the pull secret for your cluster. For a restricted network installation, these files are on your mirror host.
Procedure
Obtain the Ignition config files:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the directory name to store the files that the installation program creates.
ImportantIf you created an
install-config.yamlfile, specify the directory that contains it. Otherwise, specify an empty directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.6.13. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in VMware Cloud on AWS. If you plan to use the cluster identifier as the name of your virtual machine folder, you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
12.6.14. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
Before you install a cluster that contains user-provisioned infrastructure on VMware vSphere, you must create RHCOS machines on vSphere hosts for it to use.
Prerequisites
- You have obtained the Ignition config files for your cluster.
- You have access to an HTTP server that you can access from your computer and that the machines that you create can access.
- You have created a vSphere cluster.
Procedure
-
Upload the bootstrap Ignition config file, which is named
<installation_directory>/bootstrap.ign, that the installation program created to your HTTP server. Note the URL of this file. Save the following secondary Ignition config file for your bootstrap node to your computer as
<installation_directory>/merge-bootstrap.ign:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the URL of the bootstrap Ignition config file that you hosted.
When you create the virtual machine (VM) for the bootstrap machine, you use this Ignition config file.
Locate the following Ignition config files that the installation program created:
-
<installation_directory>/master.ign -
<installation_directory>/worker.ign -
<installation_directory>/merge-bootstrap.ign
-
Convert the Ignition config files to Base64 encoding. Later in this procedure, you must add these files to the extra configuration parameter
guestinfo.ignition.config.datain your VM.For example, if you use a Linux operating system, you can use the
base64command to encode the files.base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64
$ base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64
$ base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64
$ base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS OVA image. Images are available from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The filename contains the OpenShift Container Platform version number in the format
rhcos-vmware.<architecture>.ova.In the vSphere Client, create a folder in your datacenter to store your VMs.
- Click the VMs and Templates view.
- Right-click the name of your datacenter.
- Click New Folder → New VM and Template Folder.
-
In the window that is displayed, enter the folder name. If you did not specify an existing folder in the
install-config.yamlfile, then create a folder with the same name as the infrastructure ID. You use this folder name so vCenter dynamically provisions storage in the appropriate location for its Workspace configuration.
In the vSphere Client, create a template for the OVA image and then clone the template as needed.
NoteIn the following steps, you create a template and then clone the template for all of your cluster machines. You then provide the location for the Ignition config file for that cloned machine type when you provision the VMs.
- From the Hosts and Clusters tab, right-click your cluster name and select Deploy OVF Template.
- On the Select an OVF tab, specify the name of the RHCOS OVA file that you downloaded.
-
On the Select a name and folder tab, set a Virtual machine name for your template, such as
Template-RHCOS. Click the name of your vSphere cluster and select the folder you created in the previous step. - On the Select a compute resource tab, click the name of your vSphere cluster.
On the Select storage tab, configure the storage options for your VM.
- Select Thin Provision or Thick Provision, based on your storage preferences.
-
Select the datastore that you specified in your
install-config.yamlfile.
- On the Select network tab, specify the network that you configured for the cluster, if available.
When creating the OVF template, do not specify values on the Customize template tab or configure the template any further.
ImportantDo not start the original VM template. The VM template must remain off and must be cloned for new RHCOS machines. Starting the VM template configures the VM template as a VM on the platform, which prevents it from being used as a template that machine sets can apply configurations to.
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
control-plane-0orcompute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
On the Select a compute resource tab, select the name of a host in your datacenter.
For a bootstrap machine, specify the URL of the bootstrap Ignition config file that you hosted.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
Optional: Override default DHCP networking in vSphere. To enable static IP networking:
Set your static IP configuration:
export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"
$ export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example command
export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"
$ export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
guestinfo.afterburn.initrd.network-kargsproperty before booting a VM from an OVA in vSphere:govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"$ govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: In the event of cluster performance issues, from the Latency Sensitivity list, select High. Ensure that your VM’s CPU and memory reservation have the following values:
- Memory reservation value must be equal to its configured memory size.
- CPU reservation value must be at least the number of low latency virtual CPUs multiplied by the measured physical CPU speed.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Locate the base-64 encoded files that you created previously in this procedure, and paste the contents of the base64-encoded Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type.
- Complete the configuration and power on the VM.
Create the rest of the machines for your cluster by following the preceding steps for each machine.
ImportantYou must create the bootstrap and control plane machines at this time. Because some pods are deployed on compute machines by default, also create at least two compute machines before you install the cluster.
12.6.15. Creating more Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
You can create more compute machines for your cluster that uses user-provisioned infrastructure on VMware vSphere.
Prerequisites
- Obtain the base64-encoded Ignition file for your compute machines.
- You have access to the vSphere template that you created for your cluster.
Procedure
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template’s name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
compute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
- On the Select a compute resource tab, select the name of a host in your datacenter.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
- From the Latency Sensitivity list, select High.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Paste the contents of the base64-encoded compute Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type. Also, make sure to select the correct network under Add network adapter if there are multiple networks available.
- Complete the configuration and power on the VM.
- Continue to create more compute machines for your cluster.
12.6.16. Disk partitioning
In most cases, data partitions are originally created by installing RHCOS, rather than by installing another operating system. In such cases, the OpenShift Container Platform installer should be allowed to configure your disk partitions.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the vSphere installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
12.6.17. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
12.6.18. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.6.19. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
12.6.20. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
12.6.20.1. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
12.6.20.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.6.20.2.1. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring the registry for vSphere.
12.6.21. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
You can add extra compute machines after the cluster installation is completed by following Adding compute machines to vSphere.
12.6.22. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
12.6.23. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.6.24. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
12.7. Installing a cluster on VMC in a restricted network with user-provisioned infrastructure
In OpenShift Container Platform version 4.6, you can install a cluster on VMware vSphere infrastructure that you provision in a restricted network by deploying it to VMware Cloud (VMC) on AWS.
Once you configure your VMC environment for OpenShift Container Platform deployment, you use the OpenShift Container Platform installation program from the bastion management host, co-located in the VMC environment. The installation program and control plane automates the process of deploying and managing the resources needed for the OpenShift Container Platform cluster.
OpenShift Container Platform supports deploying a cluster to a single VMware vCenter only. Deploying a cluster with machines/machine sets on multiple vCenters is not supported.
12.7.1. Setting up VMC for vSphere
You can install OpenShift Container Platform on VMware Cloud (VMC) on AWS hosted vSphere clusters to enable applications to be deployed and managed both on-premise and off-premise, across the hybrid cloud.
You must configure several options in your VMC environment prior to installing OpenShift Container Platform on VMware vSphere. Ensure your VMC environment has the following prerequisites:
- Create a non-exclusive, DHCP-enabled, NSX-T network segment and subnet. Other virtual machines (VMs) can be hosted on the subnet, but at least eight IP addresses must be available for the OpenShift Container Platform deployment.
Configure the following firewall rules:
- An ANY:ANY firewall rule between the installation host and the software-defined data center (SDDC) management network on port 443. This allows you to upload the Red Hat Enterprise Linux CoreOS (RHCOS) OVA during deployment.
- An HTTPS firewall rule between the OpenShift Container Platform compute network and vCenter. This connection allows OpenShift Container Platform to communicate with vCenter for provisioning and managing nodes, persistent volume claims (PVCs), and other resources.
You must have the following information to deploy OpenShift Container Platform:
-
The OpenShift Container Platform cluster name, such as
vmc-prod-1. -
The base DNS name, such as
companyname.com. -
If not using the default, the pod network CIDR and services network CIDR must be identified, which are set by default to
10.128.0.0/14and172.30.0.0/16, respectively. These CIDRs are used for pod-to-pod and pod-to-service communication and are not accessible externally; however, they must not overlap with existing subnets in your organization. The following vCenter information:
- vCenter hostname, username, and password
-
Datacenter name, such as
SDDC-Datacenter -
Cluster name, such as
Cluster-1 - Network name
Datastore name, such as
WorkloadDatastoreNoteIt is recommended to move your vSphere cluster to the VMC
Compute-ResourcePoolresource pool after your cluster installation is finished.
-
The OpenShift Container Platform cluster name, such as
A Linux-based host deployed to VMC as a bastion.
- The bastion host can be Red Hat Enterprise Linux (RHEL) or any another Linux-based host; it must have Internet connectivity and the ability to upload an OVA to the ESXi hosts.
Download and install the OpenShift CLI tools to the bastion host.
-
The
openshift-installinstallation program -
The OpenShift CLI (
oc) tool
-
The
You cannot use the VMware NSX Container Plugin for Kubernetes (NCP), and NSX is not used as the OpenShift SDN. The version of NSX currently available with VMC is incompatible with the version of NCP certified with OpenShift Container Platform.
However, the NSX DHCP service is used for virtual machine IP management with the full-stack automated OpenShift Container Platform deployment and with nodes provisioned, either manually or automatically, by the Machine API integration with vSphere. Additionally, NSX firewall rules are created to enable access with the OpenShift Container Platform cluster and between the bastion host and the VMC vSphere hosts.
12.7.1.1. VMC Sizer tool
VMware Cloud on AWS is built on top of AWS bare metal infrastructure; this is the same bare metal infrastructure which runs AWS native services. When a VMware cloud on AWS software-defined data center (SDDC) is deployed, you consume these physical server nodes and run the VMware ESXi hypervisor in a single tenant fashion. This means the physical infrastructure is not accessible to anyone else using VMC. It is important to consider how many physical hosts you will need to host your virtual infrastructure.
To determine this, VMware provides the VMC on AWS Sizer. With this tool, you can define the resources you intend to host on VMC:
- Types of workloads
- Total number of virtual machines
Specification information such as:
- Storage requirements
- vCPUs
- vRAM
- Overcommit ratios
With these details, the sizer tool can generate a report, based on VMware best practices, and recommend your cluster configuration and the number of hosts you will need.
12.7.2. vSphere prerequisites
Create a registry on your mirror host and obtain the
imageContentSourcesdata for your version of OpenShift Container Platform.ImportantBecause the installation media is on the mirror host, you can use that computer to complete all installation steps.
- Provision block registry storage. For more information on persistent storage, see Understanding persistent storage.
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall and plan to use telemetry, you must configure the firewall to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
12.7.3. About installations in restricted networks
In OpenShift Container Platform 4.6, you can perform an installation that does not require an active connection to the Internet to obtain software components. Restricted network installations can be completed using installer-provisioned infrastructure or user-provisioned infrastructure, depending on the cloud platform to which you are installing the cluster.
If you choose to perform a restricted network installation on a cloud platform, you still require access to its cloud APIs. Some cloud functions, like Amazon Web Service’s Route 53 DNS and IAM services, require internet access. Depending on your network, you might require less Internet access for an installation on bare metal hardware or on VMware vSphere.
To complete a restricted network installation, you must create a registry that mirrors the contents of the OpenShift Container Platform registry and contains the installation media. You can create this registry on a mirror host, which can access both the Internet and your closed network, or by using other methods that meet your restrictions.
Because of the complexity of the configuration for user-provisioned installations, consider completing a standard user-provisioned infrastructure installation before you attempt a restricted network installation using user-provisioned infrastructure. Completing this test installation might make it easier to isolate and troubleshoot any issues that might arise during your installation in a restricted network.
12.7.3.1. Additional limits
Clusters in restricted networks have the following additional limitations and restrictions:
-
The
ClusterVersionstatus includes anUnable to retrieve available updateserror. - By default, you cannot use the contents of the Developer Catalog because you cannot access the required image stream tags.
12.7.4. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to obtain the images that are necessary to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
12.7.5. VMware vSphere infrastructure requirements
You must install the OpenShift Container Platform cluster on a VMware vSphere version 6 or 7 instance that meets the requirements for the components that you use.
| Component | Minimum supported versions | Description |
|---|---|---|
| Hypervisor | vSphere 6.5 and later with HW version 13 | This version is the minimum version that Red Hat Enterprise Linux CoreOS (RHCOS) supports. See the Red Hat Enterprise Linux 8 supported hypervisors list. |
| Storage with in-tree drivers | vSphere 6.5 and later | This plug-in creates vSphere storage by using the in-tree storage drivers for vSphere included in OpenShift Container Platform. |
If you use a vSphere version 6.5 instance, consider upgrading to 6.7U3 or 7.0 before you install OpenShift Container Platform.
You must ensure that the time on your ESXi hosts is synchronized before you install OpenShift Container Platform. See Edit Time Configuration for a Host in the VMware documentation.
12.7.6. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
12.7.6.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
12.7.6.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
12.7.6.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
12.7.6.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
12.7.7. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
12.7.7.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 12.67. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 12.68. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
12.7.7.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 12.13. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 12.14. Sample DNS zone database for reverse records
12.7.8. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
12.7.9. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
-
Obtain the
imageContentSourcessection from the output of the command to mirror the repository. - Obtain the contents of the certificate for your mirror registry.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.-
Unless you use a registry that RHCOS trusts by default, such as
docker.io, you must provide the contents of the certificate for your mirror repository in theadditionalTrustBundlesection. In most cases, you must provide the certificate for your mirror. -
You must include the
imageContentSourcessection from the output of the command to mirror the repository.
-
Unless you use a registry that RHCOS trusts by default, such as
Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
12.7.9.1. Sample install-config.yaml file for VMware vSphere
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but the compute section is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Although both sections currently define a single machine pool, it is possible that future versions of OpenShift Container Platform will support defining multiple compute pools during installation. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading, or
hyperthreading. By default, simultaneous multithreading is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable simultaneous multithreading in some cluster machines, you must disable it in all cluster machines.ImportantIf you disable simultaneous multithreading, ensure that your capacity planning accounts for the dramatically decreased machine performance. Your machines must use at least 8 CPUs and 32 GB of RAM if you disable simultaneous multithreading.
- 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- The fully-qualified hostname or IP address of the vCenter server.
- 10
- The name of the user for accessing the server. This user must have at least the roles and privileges that are required for static or dynamic persistent volume provisioning in vSphere.
- 11
- The password associated with the vSphere user.
- 12
- The vSphere datacenter.
- 13
- The default vSphere datastore to use.
- 14
- Optional: For installer-provisioned infrastructure, the absolute path of an existing folder where the installation program creates the virtual machines, for example,
/<datacenter_name>/vm/<folder_name>/<subfolder_name>. If you do not provide this value, the installation program creates a top-level folder in the datacenter virtual machine folder that is named with the infrastructure ID. If you are providing the infrastructure for the cluster, omit this parameter. - 15
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 16
- For
<local_registry>, specify the registry domain name, and optionally the port, that your mirror registry uses to serve content. For exampleregistry.example.comorregistry.example.com:5000. For<credentials>, specify the base64-encoded user name and password for your mirror registry. - 17
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses. - 18
- Provide the contents of the certificate file that you used for your mirror registry.
- 19
- Provide the
imageContentSourcessection from the output of the command to mirror the repository.
12.7.9.2. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. You must include vCenter’s IP address and the IP range that you use for its machines. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
12.7.10. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program. For a restricted network installation, these files are on your mirror host.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
Remove the Kubernetes manifest files that define the control plane machines and compute machine sets:
rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yaml
$ rm -f openshift/99_openshift-cluster-api_master-machines-*.yaml openshift/99_openshift-cluster-api_worker-machineset-*.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because you create and manage these resources yourself, you do not have to initialize them.
- You can preserve the machine set files to create compute machines by using the machine API, but you must update references to them to match your environment.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
12.7.11. Extracting the infrastructure name
The Ignition config files contain a unique cluster identifier that you can use to uniquely identify your cluster in VMware Cloud on AWS. If you plan to use the cluster identifier as the name of your virtual machine folder, you must extract it.
Prerequisites
- You obtained the OpenShift Container Platform installation program and the pull secret for your cluster.
- You generated the Ignition config files for your cluster.
-
You installed the
jqpackage.
Procedure
To extract and view the infrastructure name from the Ignition config file metadata, run the following command:
jq -r .infraID <installation_directory>/metadata.json
$ jq -r .infraID <installation_directory>/metadata.json1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
openshift-vw9j6
openshift-vw9j61 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The output of this command is your cluster name and a random string.
12.7.12. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
Before you install a cluster that contains user-provisioned infrastructure on VMware vSphere, you must create RHCOS machines on vSphere hosts for it to use.
Prerequisites
- You have obtained the Ignition config files for your cluster.
- You have access to an HTTP server that you can access from your computer and that the machines that you create can access.
- You have created a vSphere cluster.
Procedure
-
Upload the bootstrap Ignition config file, which is named
<installation_directory>/bootstrap.ign, that the installation program created to your HTTP server. Note the URL of this file. Save the following secondary Ignition config file for your bootstrap node to your computer as
<installation_directory>/merge-bootstrap.ign:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the URL of the bootstrap Ignition config file that you hosted.
When you create the virtual machine (VM) for the bootstrap machine, you use this Ignition config file.
Locate the following Ignition config files that the installation program created:
-
<installation_directory>/master.ign -
<installation_directory>/worker.ign -
<installation_directory>/merge-bootstrap.ign
-
Convert the Ignition config files to Base64 encoding. Later in this procedure, you must add these files to the extra configuration parameter
guestinfo.ignition.config.datain your VM.For example, if you use a Linux operating system, you can use the
base64command to encode the files.base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64
$ base64 -w0 <installation_directory>/master.ign > <installation_directory>/master.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64
$ base64 -w0 <installation_directory>/worker.ign > <installation_directory>/worker.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64
$ base64 -w0 <installation_directory>/merge-bootstrap.ign > <installation_directory>/merge-bootstrap.64Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS OVA image. Images are available from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download an image with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image version that matches your OpenShift Container Platform version if it is available.
The filename contains the OpenShift Container Platform version number in the format
rhcos-vmware.<architecture>.ova.In the vSphere Client, create a folder in your datacenter to store your VMs.
- Click the VMs and Templates view.
- Right-click the name of your datacenter.
- Click New Folder → New VM and Template Folder.
-
In the window that is displayed, enter the folder name. If you did not specify an existing folder in the
install-config.yamlfile, then create a folder with the same name as the infrastructure ID. You use this folder name so vCenter dynamically provisions storage in the appropriate location for its Workspace configuration.
In the vSphere Client, create a template for the OVA image and then clone the template as needed.
NoteIn the following steps, you create a template and then clone the template for all of your cluster machines. You then provide the location for the Ignition config file for that cloned machine type when you provision the VMs.
- From the Hosts and Clusters tab, right-click your cluster name and select Deploy OVF Template.
- On the Select an OVF tab, specify the name of the RHCOS OVA file that you downloaded.
-
On the Select a name and folder tab, set a Virtual machine name for your template, such as
Template-RHCOS. Click the name of your vSphere cluster and select the folder you created in the previous step. - On the Select a compute resource tab, click the name of your vSphere cluster.
On the Select storage tab, configure the storage options for your VM.
- Select Thin Provision or Thick Provision, based on your storage preferences.
-
Select the datastore that you specified in your
install-config.yamlfile.
- On the Select network tab, specify the network that you configured for the cluster, if available.
When creating the OVF template, do not specify values on the Customize template tab or configure the template any further.
ImportantDo not start the original VM template. The VM template must remain off and must be cloned for new RHCOS machines. Starting the VM template configures the VM template as a VM on the platform, which prevents it from being used as a template that machine sets can apply configurations to.
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
control-plane-0orcompute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
On the Select a compute resource tab, select the name of a host in your datacenter.
For a bootstrap machine, specify the URL of the bootstrap Ignition config file that you hosted.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
Optional: Override default DHCP networking in vSphere. To enable static IP networking:
Set your static IP configuration:
export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"
$ export IPCFG="ip=<ip>::<gateway>:<netmask>:<hostname>:<iface>:none nameserver=srv1 [nameserver=srv2 [nameserver=srv3 [...]]]"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example command
export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"
$ export IPCFG="ip=192.168.100.101::192.168.100.254:255.255.255.0:::none nameserver=8.8.8.8"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Set the
guestinfo.afterburn.initrd.network-kargsproperty before booting a VM from an OVA in vSphere:govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"$ govc vm.change -vm "<vm_name>" -e "guestinfo.afterburn.initrd.network-kargs=${IPCFG}"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Optional: In the event of cluster performance issues, from the Latency Sensitivity list, select High. Ensure that your VM’s CPU and memory reservation have the following values:
- Memory reservation value must be equal to its configured memory size.
- CPU reservation value must be at least the number of low latency virtual CPUs multiplied by the measured physical CPU speed.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Locate the base-64 encoded files that you created previously in this procedure, and paste the contents of the base64-encoded Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type.
- Complete the configuration and power on the VM.
Create the rest of the machines for your cluster by following the preceding steps for each machine.
ImportantYou must create the bootstrap and control plane machines at this time. Because some pods are deployed on compute machines by default, also create at least two compute machines before you install the cluster.
12.7.13. Creating more Red Hat Enterprise Linux CoreOS (RHCOS) machines in vSphere
You can create more compute machines for your cluster that uses user-provisioned infrastructure on VMware vSphere.
Prerequisites
- Obtain the base64-encoded Ignition file for your compute machines.
- You have access to the vSphere template that you created for your cluster.
Procedure
After the template deploys, deploy a VM for a machine in the cluster.
- Right-click the template’s name and click Clone → Clone to Virtual Machine.
-
On the Select a name and folder tab, specify a name for the VM. You might include the machine type in the name, such as
compute-1. - On the Select a name and folder tab, select the name of the folder that you created for the cluster.
- On the Select a compute resource tab, select the name of a host in your datacenter.
- Optional: On the Select storage tab, customize the storage options.
- On the Select clone options, select Customize this virtual machine’s hardware.
On the Customize hardware tab, click VM Options → Advanced.
- From the Latency Sensitivity list, select High.
Click Edit Configuration, and on the Configuration Parameters window, click Add Configuration Params. Define the following parameter names and values:
-
guestinfo.ignition.config.data: Paste the contents of the base64-encoded compute Ignition config file for this machine type. -
guestinfo.ignition.config.data.encoding: Specifybase64. -
disk.EnableUUID: SpecifyTRUE.
-
- In the Virtual Hardware panel of the Customize hardware tab, modify the specified values as required. Ensure that the amount of RAM, CPU, and disk storage meets the minimum requirements for the machine type. Also, make sure to select the correct network under Add network adapter if there are multiple networks available.
- Complete the configuration and power on the VM.
- Continue to create more compute machines for your cluster.
12.7.14. Disk partitioning
In most cases, data partitions are originally created by installing RHCOS, rather than by installing another operating system. In such cases, the OpenShift Container Platform installer should be allowed to configure your disk partitions.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the vSphere installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
12.7.15. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
12.7.16. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.7.17. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
12.7.18. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
12.7.18.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
12.7.18.2. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
12.7.18.2.1. Configuring registry storage for VMware vSphere
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster on VMware vSphere.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have "100Gi" capacity.
Testing shows issues with using the NFS server on RHEL as storage backend for core services. This includes the OpenShift Container Registry and Quay, Prometheus for monitoring storage, and Elasticsearch for logging storage. Therefore, using RHEL NFS to back PVs used by core services is not recommended.
Other NFS implementations on the marketplace might not have these issues. Contact the individual NFS implementation vendor for more information on any testing that was possibly completed against these OpenShift Container Platform core components.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.
Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
12.7.18.2.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
12.7.18.2.3. Configuring block registry storage for VMware vSphere
To allow the image registry to use block storage types such as vSphere Virtual Machine Disk (VMDK) during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only1replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
Create a
pvc.yamlfile with the following contents to define a VMware vSpherePersistentVolumeClaimobject:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A unique name that represents the
PersistentVolumeClaimobject. - 2
- The namespace for the
PersistentVolumeClaimobject, which isopenshift-image-registry. - 3
- The access mode of the persistent volume claim. With
ReadWriteOnce, the volume can be mounted with read and write permissions by a single node. - 4
- The size of the persistent volume claim.
Create the
PersistentVolumeClaimobject from the file:oc create -f pvc.yaml -n openshift-image-registry
$ oc create -f pvc.yaml -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Edit the registry configuration so that it references the correct PVC:
oc edit config.imageregistry.operator.openshift.io -o yaml
$ oc edit config.imageregistry.operator.openshift.io -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Creating a custom PVC allows you to leave the
claimfield blank for the default automatic creation of animage-registry-storagePVC.
For instructions about configuring registry storage so that it references the correct PVC, see Configuring registry storage for VMware vSphere.
12.7.19. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
- Register your cluster on the Cluster registration page.
You can add extra compute machines after the cluster installation is completed by following Adding compute machines to vSphere.
12.7.20. Backing up VMware vSphere volumes
OpenShift Container Platform provisions new volumes as independent persistent disks to freely attach and detach the volume on any node in the cluster. As a consequence, it is not possible to back up volumes that use snapshots, or to restore volumes from snapshots. See Snapshot Limitations for more information.
Procedure
To create a backup of persistent volumes:
- Stop the application that is using the persistent volume.
- Clone the persistent volume.
- Restart the application.
- Create a backup of the cloned volume.
- Delete the cloned volume.
12.7.21. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
12.7.22. Next steps
- Customize your cluster.
-
Configure image streams for the Cluster Samples Operator and the
must-gathertool. - Learn how to use Operator Lifecycle Manager (OLM) on restricted networks.
- If the mirror registry that you used to install your cluster has a trusted CA, add it to the cluster by configuring additional trust stores.
- If necessary, you can opt out of remote health reporting.
12.8. Uninstalling a cluster on VMC
You can remove a cluster installed on VMware vSphere infrastructure that you deployed to VMware Cloud (VMC) on AWS by using installer-provisioned infrastructure.
12.8.1. Removing a cluster that uses installer-provisioned infrastructure
You can remove a cluster that uses installer-provisioned infrastructure from your cloud.
After uninstallation, check your cloud provider for any resources not removed properly, especially with User Provisioned Infrastructure (UPI) clusters. There might be resources that the installer did not create or that the installer is unable to access.
Prerequisites
- Have a copy of the installation program that you used to deploy the cluster.
- Have the files that the installation program generated when you created your cluster.
Procedure
From the directory that contains the installation program on the computer that you used to install the cluster, run the following command:
./openshift-install destroy cluster \ --dir <installation_directory> --log-level info
$ ./openshift-install destroy cluster \ --dir <installation_directory> --log-level info1 2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must specify the directory that contains the cluster definition files for your cluster. The installation program requires the
metadata.jsonfile in this directory to delete the cluster.-
Optional: Delete the
<installation_directory>directory and the OpenShift Container Platform installation program.
Chapter 13. Installing on any platform
13.1. Installing a cluster on any platform
In OpenShift Container Platform version 4.6, you can install a cluster on any infrastructure that you provision, including virtualization and cloud environments.
Review the information in the guidelines for deploying OpenShift Container Platform on non-tested platforms before you attempt to install an OpenShift Container Platform cluster in virtualized or cloud environments.
13.1.1. Prerequisites
- Review details about the OpenShift Container Platform installation and update processes.
If you use a firewall, you must configure it to allow the sites that your cluster requires access to.
NoteBe sure to also review this site list if you are configuring a proxy.
13.1.2. Internet access for OpenShift Container Platform
In OpenShift Container Platform 4.6, you require access to the Internet to install your cluster.
You must have Internet access to:
- Access OpenShift Cluster Manager to download the installation program and perform subscription management. If the cluster has internet access and you do not disable Telemetry, that service automatically entitles your cluster.
- Access Quay.io to obtain the packages that are required to install your cluster.
- Obtain the packages that are required to perform cluster updates.
If your cluster cannot have direct Internet access, you can perform a restricted network installation on some types of infrastructure that you provision. During that process, you download the content that is required and use it to populate a mirror registry with the packages that you need to install a cluster and generate the installation program. With some installation types, the environment that you install your cluster in will not require Internet access. Before you update the cluster, you update the content of the mirror registry.
13.1.3. Machine requirements for a cluster with user-provisioned infrastructure
For a cluster that contains user-provisioned infrastructure, you must deploy all of the required machines.
13.1.3.1. Required machines
The smallest OpenShift Container Platform clusters require the following hosts:
- One temporary bootstrap machine
- Three control plane, or master, machines
- At least two compute machines, which are also known as worker machines.
The cluster requires the bootstrap machine to deploy the OpenShift Container Platform cluster on the three control plane machines. You can remove the bootstrap machine after you install the cluster.
To maintain high availability of your cluster, use separate physical hosts for these cluster machines.
The bootstrap and control plane machines must use Red Hat Enterprise Linux CoreOS (RHCOS) as the operating system. However, the compute machines can choose between Red Hat Enterprise Linux CoreOS (RHCOS) or Red Hat Enterprise Linux (RHEL) 7.9.
Note that RHCOS is based on Red Hat Enterprise Linux (RHEL) 8 and inherits all of its hardware certifications and requirements. See Red Hat Enterprise Linux technology capabilities and limits.
13.1.3.2. Network connectivity requirements
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config files from the Machine Config Server. During the initial boot, the machines require either a DHCP server or that static IP addresses be set in order to establish a network connection to download their Ignition config files. Additionally, each OpenShift Container Platform node in the cluster must have access to a Network Time Protocol (NTP) server. If a DHCP server provides NTP servers information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
13.1.3.3. Minimum resource requirements
Each cluster machine must meet the following minimum requirements:
| Machine | Operating System | vCPU [1] | Virtual RAM | Storage | IOPS [2] |
|---|---|---|---|---|---|
| Bootstrap | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Control plane | RHCOS | 4 | 16 GB | 100 GB | 300 |
| Compute | RHCOS or RHEL 7.9 | 2 | 8 GB | 100 GB | 300 |
- One vCPU is equivalent to one physical core when simultaneous multithreading (SMT), or hyperthreading, is not enabled. When enabled, use the following formula to calculate the corresponding ratio: (threads per core × cores) × sockets = vCPUs.
- OpenShift Container Platform and Kubernetes are sensitive to disk performance, and faster storage is recommended, particularly for etcd on the control plane nodes which require a 10 ms p99 fsync duration. Note that on many cloud platforms, storage size and IOPS scale together, so you might need to over-allocate storage volume to obtain sufficient performance.
13.1.3.4. Certificate signing requests management
Because your cluster has limited access to automatic machine management when you use infrastructure that you provision, you must provide a mechanism for approving cluster certificate signing requests (CSRs) after installation. The kube-controller-manager only approves the kubelet client CSRs. The machine-approver cannot guarantee the validity of a serving certificate that is requested by using kubelet credentials because it cannot confirm that the correct machine issued the request. You must determine and implement a method of verifying the validity of the kubelet serving certificate requests and approving them.
13.1.4. Creating the user-provisioned infrastructure
Before you deploy an OpenShift Container Platform cluster that uses user-provisioned infrastructure, you must create the underlying infrastructure.
Prerequisites
- Review the OpenShift Container Platform 4.x Tested Integrations page before you create the supporting infrastructure for your cluster.
Procedure
- Configure DHCP or set static IP addresses on each node.
- Provision the required load balancers.
- Configure the ports for your machines.
- Configure DNS.
- Ensure network connectivity.
13.1.4.1. Networking requirements for user-provisioned infrastructure
All the Red Hat Enterprise Linux CoreOS (RHCOS) machines require network in initramfs during boot to fetch Ignition config from the machine config server.
During the initial boot, the machines require either a DHCP server or that static IP addresses be set on each host in the cluster in order to establish a network connection, which allows them to download their Ignition config files.
It is recommended to use the DHCP server to manage the machines for the cluster long-term. Ensure that the DHCP server is configured to provide persistent IP addresses and host names to the cluster machines.
The Kubernetes API server must be able to resolve the node names of the cluster machines. If the API servers and worker nodes are in different zones, you can configure a default DNS search zone to allow the API server to resolve the node names. Another supported approach is to always refer to hosts by their fully-qualified domain names in both the node objects and all DNS requests.
You must configure the network connectivity between machines to allow cluster components to communicate. Each machine must be able to resolve the host names of all other machines in the cluster.
| Protocol | Port | Description |
|---|---|---|
| ICMP | N/A | Network reachability tests |
| TCP |
| Metrics |
|
|
Host level services, including the node exporter on ports | |
|
| The default ports that Kubernetes reserves | |
|
| openshift-sdn | |
| UDP |
| VXLAN and Geneve |
|
| VXLAN and Geneve | |
|
|
Host level services, including the node exporter on ports | |
| TCP/UDP |
| Kubernetes node port |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| Kubernetes API |
| Protocol | Port | Description |
|---|---|---|
| TCP |
| etcd server and peer ports |
Network topology requirements
The infrastructure that you provision for your cluster must meet the following network topology requirements.
OpenShift Container Platform requires all nodes to have internet access to pull images for platform containers and provide telemetry data to Red Hat.
Load balancers
Before you install OpenShift Container Platform, you must provision two load balancers that meet the following requirements:
API load balancer: Provides a common endpoint for users, both human and machine, to interact with and configure the platform. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the API routes.
- A stateless load balancing algorithm. The options vary based on the load balancer implementation.
ImportantDo not configure session persistence for an API load balancer.
Configure the following ports on both the front and back of the load balancers:
Expand Table 13.5. API load balancer Port Back-end machines (pool members) Internal External Description 6443Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane. You must configure the
/readyzendpoint for the API server health check probe.X
X
Kubernetes API server
22623Bootstrap and control plane. You remove the bootstrap machine from the load balancer after the bootstrap machine initializes the cluster control plane.
X
Machine config server
NoteThe load balancer must be configured to take a maximum of 30 seconds from the time the API server turns off the
/readyzendpoint to the removal of the API server instance from the pool. Within the time frame after/readyzreturns an error or becomes healthy, the endpoint must have been removed or added. Probing every 5 or 10 seconds, with two successful requests to become healthy and three to become unhealthy, are well-tested values.Application Ingress load balancer: Provides an Ingress point for application traffic flowing in from outside the cluster. Configure the following conditions:
- Layer 4 load balancing only. This can be referred to as Raw TCP, SSL Passthrough, or SSL Bridge mode. If you use SSL Bridge mode, you must enable Server Name Indication (SNI) for the Ingress routes.
- A connection-based or session-based persistence is recommended, based on the options available and types of applications that will be hosted on the platform.
Configure the following ports on both the front and back of the load balancers:
Expand Table 13.6. Application Ingress load balancer Port Back-end machines (pool members) Internal External Description 443The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTPS traffic
80The machines that run the Ingress router pods, compute, or worker, by default.
X
X
HTTP traffic
If the true IP address of the client can be seen by the load balancer, enabling source IP-based session persistence can improve performance for applications that use end-to-end TLS encryption.
A working configuration for the Ingress router is required for an OpenShift Container Platform cluster. You must configure the Ingress router after the control plane initializes.
NTP configuration
OpenShift Container Platform clusters are configured to use a public Network Time Protocol (NTP) server by default. If you want to use a local enterprise NTP server, or if your cluster is being deployed in a disconnected network, you can configure the cluster to use a specific time server. For more information, see the documentation for Configuring chrony time service.
If a DHCP server provides NTP server information, the chrony time service on the Red Hat Enterprise Linux CoreOS (RHCOS) machines read the information and can sync the clock with the NTP servers.
13.1.4.2. User-provisioned DNS requirements
DNS is used for name resolution and reverse name resolution. DNS A/AAAA or CNAME records are used for name resolution and PTR records are used for reverse name resolution. The reverse records are important because Red Hat Enterprise Linux CoreOS (RHCOS) uses the reverse records to set the host name for all the nodes. Additionally, the reverse records are used to generate the certificate signing requests (CSR) that OpenShift Container Platform needs to operate.
The following DNS records are required for an OpenShift Container Platform cluster that uses user-provisioned infrastructure. In each record, <cluster_name> is the cluster name and <base_domain> is the cluster base domain that you specify in the install-config.yaml file. A complete DNS record takes the form: <component>.<cluster_name>.<base_domain>..
| Component | Record | Description |
|---|---|---|
| Kubernetes API |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
|
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the load balancer for the control plane machines. These records must be resolvable from all the nodes within the cluster. Important The API server must be able to resolve the worker nodes by the host names that are recorded in Kubernetes. If the API server cannot resolve the node names, then proxied API calls can fail, and you cannot retrieve logs from pods. | |
| Routes |
| Add a wildcard DNS A/AAAA or CNAME record that refers to the load balancer that targets the machines that run the Ingress router pods, which are the worker nodes by default. These records must be resolvable by both clients external to the cluster and from all the nodes within the cluster. |
| Bootstrap |
| Add a DNS A/AAAA or CNAME record, and a DNS PTR record, to identify the bootstrap machine. These records must be resolvable by the nodes within the cluster. |
| Master hosts |
| DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the control plane nodes (also known as the master nodes). These records must be resolvable by the nodes within the cluster. |
| Worker hosts |
| Add DNS A/AAAA or CNAME records and DNS PTR records to identify each machine for the worker nodes. These records must be resolvable by the nodes within the cluster. |
You can use the nslookup <hostname> command to verify name resolution. You can use the dig -x <ip_address> command to verify reverse name resolution for the PTR records.
The following example of a BIND zone file shows sample A records for name resolution. The purpose of the example is to show the records that are needed. The example is not meant to provide advice for choosing one name resolution service over another.
Example 13.1. Sample DNS zone database
The following example BIND zone file shows sample PTR records for reverse name resolution.
Example 13.2. Sample DNS zone database for reverse records
13.1.5. Generating an SSH private key and adding it to the agent
If you want to perform installation debugging or disaster recovery on your cluster, you must provide an SSH key to both your ssh-agent and the installation program. You can use this key to access the bootstrap machine in a public cluster to troubleshoot installation issues.
In a production environment, you require disaster recovery and debugging.
You can use this key to SSH into the master nodes as the user core. When you deploy the cluster, the key is added to the core user’s ~/.ssh/authorized_keys list.
You must use a local key, not one that you configured with platform-specific approaches such as AWS key pairs.
Procedure
If you do not have an SSH key that is configured for password-less authentication on your computer, create one. For example, on a computer that uses a Linux operating system, run the following command:
ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>$ ssh-keygen -t ed25519 -N '' \ -f <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name, such as
~/.ssh/id_rsa, of the new SSH key. If you have an existing key pair, ensure your public key is in the your~/.sshdirectory.
Running this command generates an SSH key that does not require a password in the location that you specified.
NoteIf you plan to install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the
x86_64architecture, do not create a key that uses theed25519algorithm. Instead, create a key that uses thersaorecdsaalgorithm.Start the
ssh-agentprocess as a background task:eval "$(ssh-agent -s)"
$ eval "$(ssh-agent -s)"Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Agent pid 31874
Agent pid 31874Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf your cluster is in FIPS mode, only use FIPS-compliant algorithms to generate the SSH key. The key must be either RSA or ECDSA.
Add your SSH private key to the
ssh-agent:ssh-add <path>/<file_name>
$ ssh-add <path>/<file_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)
Identity added: /home/<you>/<path>/<file_name> (<computer_name>)Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the path and file name for your SSH private key, such as
~/.ssh/id_rsa
Next steps
- When you install OpenShift Container Platform, provide the SSH public key to the installation program. If you install a cluster on infrastructure that you provision, you must provide this key to your cluster’s machines.
13.1.6. Obtaining the installation program
Before you install OpenShift Container Platform, download the installation file on a local computer.
Prerequisites
- You have a computer that runs Linux or macOS, with 500 MB of local disk space
Procedure
- Access the Infrastructure Provider page on the OpenShift Cluster Manager site. If you have a Red Hat account, log in with your credentials. If you do not, create an account.
- Select your infrastructure provider.
Navigate to the page for your installation type, download the installation program for your operating system, and place the file in the directory where you will store the installation configuration files.
ImportantThe installation program creates several files on the computer that you use to install your cluster. You must keep the installation program and the files that the installation program creates after you finish installing the cluster. Both files are required to delete the cluster.
ImportantDeleting the files created by the installation program does not remove your cluster, even if the cluster failed during installation. To remove your cluster, complete the OpenShift Container Platform uninstallation procedures for your specific cloud provider.
Extract the installation program. For example, on a computer that uses a Linux operating system, run the following command:
tar xvf openshift-install-linux.tar.gz
$ tar xvf openshift-install-linux.tar.gzCopy to Clipboard Copied! Toggle word wrap Toggle overflow - Download your installation pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
13.1.7. Installing the OpenShift CLI by downloading the binary
You can install the OpenShift CLI (oc) in order to interact with OpenShift Container Platform from a command-line interface. You can install oc on Linux, Windows, or macOS.
If you installed an earlier version of oc, you cannot use it to complete all of the commands in OpenShift Container Platform 4.6. Download and install the new version of oc.
13.1.7.1. Installing the OpenShift CLI on Linux
You can install the OpenShift CLI (oc) binary on Linux by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Linux Client entry and save the file.
Unpack the archive:
tar xvzf <file>
$ tar xvzf <file>Copy to Clipboard Copied! Toggle word wrap Toggle overflow Place the
ocbinary in a directory that is on yourPATH.To check your
PATH, execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>13.1.7.2. Installing the OpenShift CLI on Windows
You can install the OpenShift CLI (oc) binary on Windows by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 Windows Client entry and save the file.
- Unzip the archive with a ZIP program.
Move the
ocbinary to a directory that is on yourPATH.To check your
PATH, open the command prompt and execute the following command:path
C:\> pathCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
C:\> oc <command>13.1.7.3. Installing the OpenShift CLI on macOS
You can install the OpenShift CLI (oc) binary on macOS by using the following procedure.
Procedure
- Navigate to the OpenShift Container Platform downloads page on the Red Hat Customer Portal.
- Select the appropriate version in the Version drop-down menu.
- Click Download Now next to the OpenShift v4.6 MacOSX Client entry and save the file.
- Unpack and unzip the archive.
Move the
ocbinary to a directory on your PATH.To check your
PATH, open a terminal and execute the following command:echo $PATH
$ echo $PATHCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After you install the OpenShift CLI, it is available using the oc command:
oc <command>
$ oc <command>13.1.8. Manually creating the installation configuration file
For installations of OpenShift Container Platform that use user-provisioned infrastructure, you manually generate your installation configuration file.
Prerequisites
- Obtain the OpenShift Container Platform installation program and the access token for your cluster.
Procedure
Create an installation directory to store your required installation assets in:
mkdir <installation_directory>
$ mkdir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantYou must create a directory. Some installation assets, like bootstrap X.509 certificates have short expiration intervals, so you must not reuse an installation directory. If you want to reuse individual files from another cluster installation, you can copy them into your directory. However, the file names for the installation assets might change between releases. Use caution when copying installation files from an earlier OpenShift Container Platform version.
Customize the following
install-config.yamlfile template and save it in the<installation_directory>.NoteYou must name this configuration file
install-config.yaml.Back up the
install-config.yamlfile so that you can use it to install multiple clusters.ImportantThe
install-config.yamlfile is consumed during the next step of the installation process. You must back it up now.
You can customize the install-config.yaml file to specify more details about your OpenShift Container Platform cluster’s platform or modify the values of the required parameters.
- 1
- The base domain of the cluster. All DNS records must be sub-domains of this base and include the cluster name.
- 2 5
- The
controlPlanesection is a single mapping, but thecomputesection is a sequence of mappings. To meet the requirements of the different data structures, the first line of thecomputesection must begin with a hyphen,-, and the first line of thecontrolPlanesection must not. Only one control plane pool is used. - 3 6
- Whether to enable or disable simultaneous multithreading (SMT), or
hyperthreading. By default, SMT is enabled to increase the performance of your machines' cores. You can disable it by setting the parameter value toDisabled. If you disable SMT, you must disable it in all cluster machines; this includes both control plane and compute machines.NoteSimultaneous multithreading (SMT) is enabled by default. If SMT is not enabled in your BIOS settings, the
hyperthreadingparameter has no effect.ImportantIf you disable
hyperthreading, whether in the BIOS or in theinstall-config.yaml, ensure that your capacity planning accounts for the dramatically decreased machine performance. - 4
- You must set the value of the
replicasparameter to0. This parameter controls the number of workers that the cluster creates and manages for you, which are functions that the cluster does not perform when you use user-provisioned infrastructure. You must manually deploy worker machines for the cluster to use before you finish installing OpenShift Container Platform. - 7
- The number of control plane machines that you add to the cluster. Because the cluster uses this values as the number of etcd endpoints in the cluster, the value must match the number of control plane machines that you deploy.
- 8
- The cluster name that you specified in your DNS records.
- 9
- A block of IP addresses from which pod IP addresses are allocated. This block must not overlap with existing physical networks. These IP addresses are used for the pod network. If you need to access the pods from an external network, you must configure load balancers and routers to manage the traffic.Note
Class E CIDR range is reserved for a future use. To use the Class E CIDR range, you must ensure your networking environment accepts the IP addresses within the Class E CIDR range.
- 10
- The subnet prefix length to assign to each individual node. For example, if
hostPrefixis set to23, then each node is assigned a/23subnet out of the givencidr, which allows for 510 (2^(32 - 23) - 2) pod IPs addresses. If you are required to provide access to nodes from an external network, configure load balancers and routers to manage the traffic. - 11
- The IP address pool to use for service IP addresses. You can enter only one IP address pool. This block must not overlap with existing physical networks. If you need to access the services from an external network, configure load balancers and routers to manage the traffic.
- 12
- You must set the platform to
none. You cannot provide additional platform configuration variables for your platform. - 13
- Whether to enable or disable FIPS mode. By default, FIPS mode is not enabled. If FIPS mode is enabled, the Red Hat Enterprise Linux CoreOS (RHCOS) machines that OpenShift Container Platform runs on bypass the default Kubernetes cryptography suite and use the cryptography modules that are provided with RHCOS instead.Important
The use of FIPS Validated / Modules in Process cryptographic libraries is only supported on OpenShift Container Platform deployments on the
x86_64architecture. - 14
- The pull secret from the Red Hat OpenShift Cluster Manager. This pull secret allows you to authenticate with the services that are provided by the included authorities, including Quay.io, which serves the container images for OpenShift Container Platform components.
- 15
- The public portion of the default SSH key for the
coreuser in Red Hat Enterprise Linux CoreOS (RHCOS).NoteFor production OpenShift Container Platform clusters on which you want to perform installation debugging or disaster recovery, specify an SSH key that your
ssh-agentprocess uses.
13.1.8.1. Configuring the cluster-wide proxy during installation
Production environments can deny direct access to the Internet and instead have an HTTP or HTTPS proxy available. You can configure a new OpenShift Container Platform cluster to use a proxy by configuring the proxy settings in the install-config.yaml file.
Prerequisites
-
You have an existing
install-config.yamlfile. You reviewed the sites that your cluster requires access to and determined whether any of them need to bypass the proxy. By default, all cluster egress traffic is proxied, including calls to hosting cloud provider APIs. You added sites to the
Proxyobject’sspec.noProxyfield to bypass the proxy if necessary.NoteThe
Proxyobjectstatus.noProxyfield is populated with the values of thenetworking.machineNetwork[].cidr,networking.clusterNetwork[].cidr, andnetworking.serviceNetwork[]fields from your installation configuration.For installations on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure, and Red Hat OpenStack Platform (RHOSP), the
Proxyobjectstatus.noProxyfield is also populated with the instance metadata endpoint (169.254.169.254).
Procedure
Edit your
install-config.yamlfile and add the proxy settings. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- A proxy URL to use for creating HTTP connections outside the cluster. The URL scheme must be
http. - 2
- A proxy URL to use for creating HTTPS connections outside the cluster.
- 3
- A comma-separated list of destination domain names, IP addresses, or other network CIDRs to exclude from proxying. Preface a domain with
.to match subdomains only. For example,.y.commatchesx.y.com, but noty.com. Use*to bypass the proxy for all destinations. - 4
- If provided, the installation program generates a config map that is named
user-ca-bundlein theopenshift-confignamespace to hold the additional CA certificates. If you provideadditionalTrustBundleand at least one proxy setting, theProxyobject is configured to reference theuser-ca-bundleconfig map in thetrustedCAfield. The Cluster Network Operator then creates atrusted-ca-bundleconfig map that merges the contents specified for thetrustedCAparameter with the RHCOS trust bundle. TheadditionalTrustBundlefield is required unless the proxy’s identity certificate is signed by an authority from the RHCOS trust bundle.
NoteThe installation program does not support the proxy
readinessEndpointsfield.- Save the file and reference it when installing OpenShift Container Platform.
The installation program creates a cluster-wide proxy that is named cluster that uses the proxy settings in the provided install-config.yaml file. If no proxy settings are provided, a cluster Proxy object is still created, but it will have a nil spec.
Only the Proxy object named cluster is supported, and no additional proxies can be created.
13.1.9. Configuring a three-node cluster
You can optionally install and run three-node clusters in OpenShift Container Platform with no workers. This provides smaller, more resource efficient clusters for cluster administrators and developers to use for development, production, and testing.
Procedure
Edit the
install-config.yamlfile to set the number of compute replicas, which are also known as worker replicas, to0, as shown in the followingcomputestanza:compute: - name: worker platform: {} replicas: 0compute: - name: worker platform: {} replicas: 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.1.10. Creating the Kubernetes manifest and Ignition config files
Because you must modify some cluster definition files and manually start the cluster machines, you must generate the Kubernetes manifest and Ignition config files that the cluster needs to make its machines.
The installation configuration file transforms into the Kubernetes manifests. The manifests wrap into the Ignition configuration files, which are later used to create the cluster.
-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Prerequisites
- You obtained the OpenShift Container Platform installation program.
-
You created the
install-config.yamlinstallation configuration file.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the installation directory that contains theinstall-config.yamlfile you created.
If you are installing a three-node cluster, skip the following step to allow the control plane nodes to be schedulable.
+
When you configure control plane nodes from the default unschedulable to schedulable, additional subscriptions are required. This is because control plane nodes then become worker nodes.
Check that the
mastersSchedulableparameter in the<installation_directory>/manifests/cluster-scheduler-02-config.ymlKubernetes manifest file is set tofalse. This setting prevents pods from being scheduled on the control plane machines:-
Open the
<installation_directory>/manifests/cluster-scheduler-02-config.ymlfile. -
Locate the
mastersSchedulableparameter and ensure that it is set tofalse. - Save and exit the file.
-
Open the
To create the Ignition configuration files, run the following command from the directory that contains the installation program:
./openshift-install create ignition-configs --dir <installation_directory>
$ ./openshift-install create ignition-configs --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the same installation directory.
The following files are generated in the directory:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
13.1.11. Installing RHCOS and starting the OpenShift Container Platform bootstrap process
To install OpenShift Container Platform on bare metal infrastructure that you provision, you must install Red Hat Enterprise Linux CoreOS (RHCOS) on the machines. When you install RHCOS, you must provide the Ignition config file that was generated by the OpenShift Container Platform installation program for the type of machine you are installing. If you have configured suitable networking, DNS, and load balancing infrastructure, the OpenShift Container Platform bootstrap process begins automatically after the RHCOS machines have rebooted.
To install RHCOS on the machines, follow either the steps to use an ISO image or network PXE booting.
The compute node deployment steps included in this installation document are RHCOS-specific. If you choose instead to deploy RHEL-based compute nodes, you take responsibility for all operating system life cycle management and maintenance, including performing system updates, applying patches, and completing all other required tasks. Use of RHEL 7 compute machines is deprecated and planned for removal in a future release of OpenShift Container Platform 4.
You can configure RHCOS during ISO and PXE installations by using the following methods:
-
Kernel arguments: You can use kernel arguments to provide installation-specific information. For example, you can specify the locations of the RHCOS installation files that you uploaded to your HTTP server and the location of the Ignition config file for the type of node you are installing. For a PXE installation, you can use the
APPENDparameter to pass the arguments to the kernel of the live installer. For an ISO installation, you can interrupt the live installation boot process to add the kernel arguments. In both installation cases, you can use specialcoreos.inst.*arguments to direct the live installer, as well as standard installation boot arguments for turning standard kernel services on or off. -
Ignition configs: OpenShift Container Platform Ignition config files (
*.ign) are specific to the type of node you are installing. You pass the location of a bootstrap, control plane, or compute node Ignition config file during the RHCOS installation so that it takes effect on first boot. In special cases, you can create a separate, limited Ignition config to pass to the live system. That Ignition config could do a certain set of tasks, such as reporting success to a provisioning system after completing installation. This special Ignition config is consumed by thecoreos-installerto be applied on first boot of the installed system. Do not provide the standard control plane and compute node Ignition configs to the live ISO directly. -
coreos-installer: You can boot the live ISO installer to a shell prompt, which allows you to prepare the permanent system in a variety of ways before first boot. In particular, you can run thecoreos-installercommand to identify various artifacts to include, work with disk partitions, and set up networking. In some cases, you can configure features on the live system and copy them to the installed system.
Whether to use an ISO or PXE install depends on your situation. A PXE install requires an available DHCP service and more preparation, but can make the installation process more automated. An ISO install is a more manual process and can be inconvenient if you are setting up more than a few machines.
As of OpenShift Container Platform 4.6, the RHCOS ISO and other installation artifacts provide support for installation on disks with 4K sectors.
13.1.11.1. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines using an ISO image
Before you install a cluster on infrastructure that you provision, you must create RHCOS machines for it to use. You can use an ISO image to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Have access to an HTTP server that can be accessed from your computer, and from the machines that you create.
Procedure
Upload the control plane, compute, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS images that are required for your preferred method of installing operating system instances from the RHCOS image mirror page.
ImportantThe RHCOS images might not change with every release of OpenShift Container Platform. You must download images with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Use the image versions that match your OpenShift Container Platform version if they are available. Use only ISO images for this procedure. RHCOS qcow2 images are not supported for this installation type.
ISO file names resemble the following example:
rhcos-<version>-live.<architecture>.isoUse the ISO to start the RHCOS installation. Use one of the following installation options:
- Burn the ISO image to a disk and boot it directly.
- Use ISO redirection via a LOM interface.
-
Boot the ISO image. You can interrupt the installation boot process to add kernel arguments. However, for this ISO procedure you should use the
coreos-installercommand instead of adding kernel arguments. If you run the live installer without options or interruption, the installer boots up to a shell prompt on the live system, ready for you to install RHCOS to disk. -
Review the Advanced RHCOS installation reference section for different ways of configuring features, such as networking and disk partitions, before running the
coreos-installer. Run the
coreos-installercommand. At a minimum, you must identify the Ignition config file location for your node type, and the location of the disk you are installing to. Here is an example:sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sda$ sudo coreos-installer install \ --ignition-url=https://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow - After RHCOS installs, the system reboots. During the system reboot, it applies the Ignition config file that you specified.
Continue to create the other machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
13.1.11.2. Creating Red Hat Enterprise Linux CoreOS (RHCOS) machines by PXE or iPXE booting
Before you install a cluster that uses manually-provisioned RHCOS nodes, such as bare metal, you must create RHCOS machines for it to use. You can use PXE or iPXE booting to create the machines.
Prerequisites
- Obtain the Ignition config files for your cluster.
- Configure suitable PXE or iPXE infrastructure.
- Have access to an HTTP server that you can access from your computer.
Procedure
Upload the master, worker, and bootstrap Ignition config files that the installation program created to your HTTP server. Note the URLs of these files.
ImportantYou can add or change configuration settings in your Ignition configs before saving them to your HTTP server. If you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
Obtain the RHCOS
kernel,initramfsandrootfsfiles from the RHCOS image mirror page.ImportantThe RHCOS artifacts might not change with every release of OpenShift Container Platform. You must download artifacts with the highest version that is less than or equal to the OpenShift Container Platform version that you install. Only use the appropriate
kernel,initramfs, androotfsartifacts described below for this procedure. RHCOS qcow2 images are not supported for this installation type.The file names contain the OpenShift Container Platform version number. They resemble the following examples:
-
kernel:rhcos-<version>-live-kernel-<architecture> -
initramfs:rhcos-<version>-live-initramfs.<architecture>.img -
rootfs:rhcos-<version>-live-rootfs.<architecture>.img
-
Upload the additional files that are required for your booting method:
-
For traditional PXE, upload the
kernelandinitramfsfiles to your TFTP server and therootfsfile to your HTTP server. For iPXE, upload the
kernel,initramfs, androotfsfiles to your HTTP server.ImportantIf you plan to add more compute machines to your cluster after you finish installation, do not delete these files.
-
For traditional PXE, upload the
- Configure the network boot infrastructure so that the machines boot from their local disks after RHCOS is installed on them.
Configure PXE or iPXE installation for the RHCOS images.
Modify one of the following example menu entries for your environment and verify that the image and Ignition files are properly accessible:
For PXE:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the location of the live
kernelfile that you uploaded to your HTTP server. The URL must be HTTP, TFTP, or FTP; HTTPS and NFS are not supported. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
initrdparameter value is the location of theinitramfsfile, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. You can also add more kernel arguments to theAPPENDline to configure networking or other boot options.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to theAPPENDline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.For iPXE:
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img boot
kernel http://<HTTP_server>/rhcos-<version>-live-kernel-<architecture> initrd=main coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.install_dev=/dev/sda coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign1 2 initrd --name main http://<HTTP_server>/rhcos-<version>-live-initramfs.<architecture>.img3 bootCopy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify locations of the RHCOS files that you uploaded to your HTTP server. The
kernelparameter value is the location of thekernelfile, theinitrd=mainargument is needed for booting on UEFI systems, thecoreos.live.rootfs_urlparameter value is the location of therootfsfile, and thecoreos.inst.ignition_urlparameter value is the location of the bootstrap Ignition config file. - 2
- If you use multiple NICs, specify a single interface in the
ipoption. For example, to use DHCP on a NIC that is namedeno1, setip=eno1:dhcp. - 3
- Specify the location of the
initramfsfile that you uploaded to your HTTP server.
NoteThis configuration does not enable serial console access on machines with a graphical console. To configure a different console, add one or more
console=arguments to thekernelline. For example, addconsole=tty0 console=ttyS0to set the first PC serial port as the primary console and the graphical console as a secondary console. For more information, see How does one set up a serial terminal and/or console in Red Hat Enterprise Linux?.
If you use PXE UEFI, perform the following actions:
Provide the
shimx64.efiandgrubx64.efiEFI binaries and thegrub.cfgfile that are required for booting the system.Extract the necessary EFI binaries by mounting the RHCOS ISO to your host and then mounting the
images/efiboot.imgfile to your host:mkdir -p /mnt/iso
$ mkdir -p /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mkdir -p /mnt/efiboot
$ mkdir -p /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop rhcos-installer.x86_64.iso /mnt/iso
$ mount -o loop rhcos-installer.x86_64.iso /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efiboot
$ mount -o loop,ro /mnt/iso/images/efiboot.img /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow From the
efiboot.imgmount point, copy theEFI/redhat/shimx64.efiandEFI/redhat/grubx64.efifiles to your TFTP server:cp /mnt/efiboot/EFI/redhat/shimx64.efi .
$ cp /mnt/efiboot/EFI/redhat/shimx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow cp /mnt/efiboot/EFI/redhat/grubx64.efi .
$ cp /mnt/efiboot/EFI/redhat/grubx64.efi .Copy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/efiboot
$ umount /mnt/efibootCopy to Clipboard Copied! Toggle word wrap Toggle overflow umount /mnt/iso
$ umount /mnt/isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow -
Copy the
EFI/redhat/grub.cfgfile that is included in the RHCOS ISO to your TFTP server.
Edit the
grub.cfgfile to include arguments similar to the following:menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }menuentry 'Install Red Hat Enterprise Linux CoreOS' --class fedora --class gnu-linux --class gnu --class os { linuxefi rhcos-<version>-live-kernel-<architecture> coreos.inst.install_dev=/dev/sda coreos.live.rootfs_url=http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img coreos.inst.ignition_url=http://<HTTP_server>/bootstrap.ign initrdefi rhcos-<version>-live-initramfs.<architecture>.img }Copy to Clipboard Copied! Toggle word wrap Toggle overflow where:
rhcos-<version>-live-kernel-<architecture>-
Specifies the
kernelfile that you uploaded to your TFTP server. http://<HTTP_server>/rhcos-<version>-live-rootfs.<architecture>.img- Specifies the location of the live rootfs image that you uploaded to your HTTP server.
http://<HTTP_server>/bootstrap.ign- Specifies the location of the bootstrap Ignition config file that you uploaded to your HTTP server.
rhcos-<version>-live-initramfs.<architecture>.img-
Specifies the location of the
initramfsfile that you uploaded to your TFTP server.
NoteFor more information on how to configure a PXE server for UEFI boot, see the Red Hat Knowledgebase article: How to configure/setup a PXE server for UEFI boot for Red Hat Enterprise Linux?.
Continue to create the machines for your cluster.
ImportantYou must create the bootstrap and control plane machines at this time. If the control plane machines are not made schedulable, which is the default, also create at least two compute machines before you install the cluster.
13.1.11.3. Advanced Red Hat Enterprise Linux CoreOS (RHCOS) installation configuration
A key benefit for manually provisioning the Red Hat Enterprise Linux CoreOS (RHCOS) nodes for OpenShift Container Platform is to be able to do configuration that is not available through default OpenShift Container Platform installation methods. This section describes some of the configurations that you can do using techniques that include:
- Passing kernel arguments to the live installer
-
Running
coreos-installermanually from the live system - Embedding Ignition configs in an ISO
The advanced configuration topics for manual Red Hat Enterprise Linux CoreOS (RHCOS) installations detailed in this section relate to disk partitioning, networking, and using Ignition configs in different ways.
13.1.11.3.1. Using advanced networking options for PXE and ISO installations
Networking for OpenShift Container Platform nodes uses DHCP by default to gather all necessary configuration settings. To set up static IP addresses or configure special settings, such as bonding, you can do one of the following:
- Pass special kernel parameters when you boot the live installer.
- Use a machine config to copy networking files to the installed system.
- Configure networking from a live installer shell prompt, then copy those settings to the installed system so that they take effect when the installed system first boots.
To configure a PXE or iPXE installation, use one of the following options:
- See the "Advanced RHCOS installation reference" tables.
- Use a machine config to copy networking files to the installed system.
To configure an ISO installation, use the following procedure.
Procedure
- Boot the ISO installer.
-
From the live system shell prompt, configure networking for the live system using available RHEL tools, such as
nmcliornmtui. Run the
coreos-installercommand to install the system, adding the--copy-networkoption to copy networking configuration. For example:coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sda$ coreos-installer install --copy-network \ --ignition-url=http://host/worker.ign /dev/sdaCopy to Clipboard Copied! Toggle word wrap Toggle overflow ImportantThe
--copy-networkoption only copies networking configuration found under/etc/NetworkManager/system-connections. In particular, it does not copy the system hostname.- Reboot into the installed system.
13.1.11.3.2. Disk partitioning
The disk partitions are created on OpenShift Container Platform cluster nodes during the Red Hat Enterprise Linux CoreOS (RHCOS) installation. Each RHCOS node of a particular architecture uses the same partition layout, unless the default partitioning configuration is overridden. During the RHCOS installation, the size of the root file system is increased to use the remaining available space on the target device.
However, there are two cases where you might want to intervene to override the default partitioning when installing an OpenShift Container Platform node:
Create separate partitions: For greenfield installations on an empty disk, you might want to add separate storage to a partition. This is officially supported for making
/varor a subdirectory of/var, such as/var/lib/etcd, a separate partition, but not both.ImportantKubernetes supports only two filesystem partitions. If you add more than one partition to the original configuration, Kubernetes cannot monitor all of them.
-
Retain existing partitions: For a brownfield installation where you are reinstalling OpenShift Container Platform on an existing node and want to retain data partitions installed from your previous operating system, there are both boot arguments and options to
coreos-installerthat allow you to retain existing data partitions.
13.1.11.3.2.1. Creating a separate /var partition
In general, disk partitioning for OpenShift Container Platform should be left to the installer. However, there are cases where you might want to create separate partitions in a part of the filesystem that you expect to grow.
OpenShift Container Platform supports the addition of a single partition to attach storage to either the /var partition or a subdirectory of /var. For example:
-
/var/lib/containers: Holds container-related content that can grow as more images and containers are added to a system. -
/var/lib/etcd: Holds data that you might want to keep separate for purposes such as performance optimization of etcd storage. -
/var: Holds data that you might want to keep separate for purposes such as auditing.
Storing the contents of a /var directory separately makes it easier to grow storage for those areas as needed and reinstall OpenShift Container Platform at a later date and keep that data intact. With this method, you will not have to pull all your containers again, nor will you have to copy massive log files when you update systems.
Because /var must be in place before a fresh installation of Red Hat Enterprise Linux CoreOS (RHCOS), the following procedure sets up the separate /var partition by creating a machine config that is inserted during the openshift-install preparation phases of an OpenShift Container Platform installation.
Procedure
Create a directory to hold the OpenShift Container Platform installation files:
mkdir $HOME/clusterconfig
$ mkdir $HOME/clusterconfigCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run
openshift-installto create a set of files in themanifestandopenshiftsubdirectories. Answer the system questions as you are prompted:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Create a
MachineConfigobject and add it to a file in theopenshiftdirectory. For example, name the file98-var-partition.yaml, change the disk device name to the name of the storage device on theworkersystems, and set the storage size as appropriate. This example places the/vardirectory on a separate partition:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The storage device name of the disk that you want to partition.
- 2
- When adding a data partition to the boot disk, a minimum value of 25000 mebibytes is recommended. The root file system is automatically resized to fill all available space up to the specified offset. If no value is specified, or if the specified value is smaller than the recommended minimum, the resulting root file system will be too small, and future reinstalls of RHCOS might overwrite the beginning of the data partition.
- 3
- The size of the data partition in mebibytes.
- 4
- The name of the mount unit must match the directory specified in the
Where=directive. For example, for a filesystem mounted on/var/lib/containers, the unit must be namedvar-lib-containers.mount. - 5
- The
prjquotamount option must be enabled for filesystems used for container storage.
NoteWhen creating a separate
/varpartition, you cannot use different instance types for worker nodes, if the different instance types do not have the same device name.Run
openshift-installagain to create Ignition configs from a set of files in themanifestandopenshiftsubdirectories:openshift-install create ignition-configs --dir $HOME/clusterconfig ls $HOME/clusterconfig/
$ openshift-install create ignition-configs --dir $HOME/clusterconfig $ ls $HOME/clusterconfig/ auth bootstrap.ign master.ign metadata.json worker.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Now you can use the Ignition config files as input to the ISO or PXE manual installation procedures to install Red Hat Enterprise Linux CoreOS (RHCOS) systems.
13.1.11.3.2.2. Retaining existing partitions
For an ISO installation, you can add options to the coreos-installer command line that causes the installer to maintain one or more existing partitions. For a PXE installation, you can APPEND coreos.inst.* options to preserve partitions.
Saved partitions might be partitions from an existing OpenShift Container Platform system that has data partitions that you want to keep. Here are a few tips:
- If you save existing partitions, and those partitions do not leave enough space for RHCOS, installation will fail without damaging the saved partitions.
- Identify the disk partitions you want to keep either by partition label or by number.
For an ISO installation
This example preserves any partition in which the partition label begins with data (data*):
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partlabel 'data*' /dev/sda
The following example illustrates running the coreos-installer in a way that preserves the sixth (6) partition on the disk:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sda
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign \
--save-partindex 6 /dev/sdaThis example preserves partitions 5 and higher:
coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
# coreos-installer install --ignition-url http://10.0.2.2:8080/user.ign
--save-partindex 5- /dev/sda
In the previous examples where partition saving is used, coreos-installer recreates the partition immediately.
For a PXE installation
This APPEND option preserves any partition in which the partition label begins with 'data' ('data*'):
coreos.inst.save_partlabel=data*
coreos.inst.save_partlabel=data*
This APPEND option preserves partitions 5 and higher:
coreos.inst.save_partindex=5-
coreos.inst.save_partindex=5-
This APPEND option preserves partition 6:
coreos.inst.save_partindex=6
coreos.inst.save_partindex=613.1.11.3.3. Identifying Ignition configs
When doing an RHCOS manual installation, there are two types of Ignition configs that you can provide, with different reasons for providing each one:
Permanent install Ignition config: Every manual RHCOS installation needs to pass one of the Ignition config files generated by
openshift-installer, such asbootstrap.ign,master.ignandworker.ign, to carry out the installation.ImportantIt is not recommended to modify these files.
For PXE installations, you pass the Ignition configs on the
APPENDline using thecoreos.inst.ignition_url=option. For ISO installations, after the ISO boots to the shell prompt, you identify the Ignition config on thecoreos-installercommand line with the--ignition-url=option. In both cases, only HTTP and HTTPS protocols are supported.Live install Ignition config: This type must be created manually and should be avoided if possible, as it is not supported by Red Hat. With this method, the Ignition config passes to the live install medium, runs immediately upon booting, and performs setup tasks before and/or after the RHCOS system installs to disk. This method should only be used for performing tasks that must be performed once and not applied again later, such as with advanced partitioning that cannot be done using a machine config.
For PXE or ISO boots, you can create the Ignition config and
APPENDtheignition.config.url=option to identify the location of the Ignition config. You also need to appendignition.firstboot ignition.platform.id=metalor theignition.config.urloption will be ignored.
13.1.11.3.3.1. Embedding an Ignition config in the RHCOS ISO
You can embed a live install Ignition config directly in an RHCOS ISO image. When the ISO image is booted, the embedded config will be applied automatically.
Procedure
-
Download the
coreos-installerbinary from the following image mirror page: https://mirror.openshift.com/pub/openshift-v4/clients/coreos-installer/latest/. Retrieve the RHCOS ISO image and the Ignition config file, and copy them into an accessible directory, such as
/mnt:cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ chmod 644 /mnt/rhcos-<version>-live.x86_64.iso
# cp rhcos-<version>-live.x86_64.iso bootstrap.ign /mnt/ # chmod 644 /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Run the following command to embed the Ignition config into the ISO:
./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.iso# ./coreos-installer iso ignition embed -i /mnt/bootstrap.ign \ /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now use that ISO to install RHCOS using the specified live install Ignition config.
ImportantUsing
coreos-installer iso ignition embedto embed a file generated byopenshift-installer, such asbootstrap.ign,master.ignandworker.ign, is unsupported and not recommended.To show the contents of the embedded Ignition config and direct it into a file, run:
./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ign
# ./coreos-installer iso ignition show /mnt/rhcos-<version>-live.x86_64.iso > mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow diff -s bootstrap.ign mybootstrap.ign
# diff -s bootstrap.ign mybootstrap.ignCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Files bootstrap.ign and mybootstrap.ign are identical
Files bootstrap.ign and mybootstrap.ign are identicalCopy to Clipboard Copied! Toggle word wrap Toggle overflow To remove the Ignition config and return the ISO to its pristine state so you can reuse it, run:
./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.iso
# ./coreos-installer iso ignition remove /mnt/rhcos-<version>-live.x86_64.isoCopy to Clipboard Copied! Toggle word wrap Toggle overflow You can now embed another Ignition config into the ISO or use the ISO in its pristine state.
13.1.11.3.4. Advanced RHCOS installation reference
This section illustrates the networking configuration and other advanced options that allow you to modify the Red Hat Enterprise Linux CoreOS (RHCOS) manual installation process. The following tables describe the kernel arguments and command-line options you can use with the RHCOS live installer and the coreos-installer command.
Routing and bonding options at RHCOS boot prompt
If you install RHCOS from an ISO image, you can add kernel arguments manually when you boot that image to configure the node’s networking. If no networking arguments are used, the installation defaults to using DHCP.
When adding networking arguments, you must also add the rd.neednet=1 kernel argument.
The following table describes how to use ip=, nameserver=, and bond= kernel arguments for live ISO installs.
Ordering is important when adding kernel arguments: ip=, nameserver=, and then bond=.
Routing and bonding options for ISO
The following table provides examples for configuring networking of your Red Hat Enterprise Linux CoreOS (RHCOS) nodes. These are networking options that are passed to the dracut tool during system boot. For more information about the networking options supported by dracut, see the dracut.cmdline manual page.
| Description | Examples |
|---|---|
|
To configure an IP address, either use DHCP (
|
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none nameserver=4.4.4.41 |
|
Specify multiple network interfaces by specifying multiple |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=10.10.10.3::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure routes to additional networks by setting an If the additional network gateway is different from the primary network gateway, the default gateway must be the primary network gateway. | To configure the default gateway: ip=::10.10.10.254:::: To configure the route for the additional network: rd.route=20.20.20.0/24:20.20.20.254:enp2s0 |
| Disable DHCP on a single interface, such as when there are two or more network interfaces and only one interface is being used. |
ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp1s0:none ip=::::core0.example.com:enp2s0:none |
| You can combine DHCP and static IP configurations on systems with multiple network interfaces. |
ip=enp1s0:dhcp ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0:none |
|
Optional: You can configure VLANs on individual interfaces by using the | To configure a VLAN on a network interface and use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:enp2s0.100:none vlan=enp2s0.100:enp2s0 To configure a VLAN on a network interface and to use DHCP: ip=enp2s0.100:dhcp vlan=enp2s0.100:enp2s0 |
|
You can provide multiple DNS servers by adding a |
nameserver=1.1.1.1 nameserver=8.8.8.8 |
|
Optional: Bonding multiple network interfaces to a single interface is supported using the
|
To configure the bonded interface to use DHCP, set the bond’s IP address to bond=bond0:em1,em2:mode=active-backup ip=bond0:dhcp To configure the bonded interface to use a static IP address, enter the specific IP address you want and related information. For example: bond=bond0:em1,em2:mode=active-backup ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0:none |
|
Optional: You can configure VLANs on bonded interfaces by using the | To configure the bonded interface with a VLAN and to use DHCP: ip=bond0.100:dhcp bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 To configure the bonded interface with a VLAN and to use a static IP address: ip=10.10.10.2::10.10.10.254:255.255.255.0:core0.example.com:bond0.100:none bond=bond0:em1,em2:mode=active-backup vlan=bond0.100:bond0 |
|
Optional: Network teaming can be used as an alternative to bonding by using the
Note Teaming is planned to be deprecated when RHCOS switches to an upcoming version of RHEL. For more information, see this Red Hat Knowledgebase Article. | To configure a network team: team=team0:em1,em2 ip=team0:dhcp |
coreos.inst boot options for ISO or PXE install
While you can pass most standard installation boot arguments to the live installer, there are several arguments that are specific to the RHCOS live installer.
- For ISO, these options can be added by interrupting the RHCOS installer.
-
For PXE or iPXE, these options must be added to the
APPENDline before starting the PXE kernel. You cannot interrupt a live PXE install.
The following table shows the RHCOS live installer boot options for ISO and PXE installs.
| Argument | Description |
|---|---|
|
|
Required. The block device on the system to install to. It is recommended to use the full path, such as |
|
| Optional: The URL of the Ignition config to embed into the installed system. If no URL is specified, no Ignition config is embedded. |
|
| Optional: Comma-separated labels of partitions to preserve during the install. Glob-style wildcards are permitted. The specified partitions do not need to exist. |
|
|
Optional: Comma-separated indexes of partitions to preserve during the install. Ranges |
|
|
Optional: Permits the OS image that is specified by |
|
| Optional: Download and install the specified RHCOS image.
|
|
| Optional: The system will not reboot after installing. Once the install finishes, you will receive a prompt that allows you to inspect what is happening during installation. This argument should not be used in production environments and is intended for debugging purposes only. |
|
|
Optional: The Ignition platform ID of the platform the RHCOS image is being installed on. Default is |
|
|
Optional: The URL of the Ignition config for the live boot. For example, this can be used to customize how |
coreos-installer options for ISO install
You can also install RHCOS by invoking the coreos-installer command directly from the command line. The kernel arguments in the previous table provide a shortcut for automatically invoking coreos-installer at boot time, but you can pass similar arguments directly to coreos-installer when running it from a shell prompt.
The following table shows the options and subcommands you can pass to the coreos-installer command from a shell prompt during a live install.
| Command-line options | |
| Option | Description |
|
| Specify the image URL manually. |
|
| Specify a local image file manually. |
|
| Embed an Ignition config from a file. |
|
| Embed an Ignition config from a URL. |
|
|
Digest |
|
| Override the Ignition platform ID. |
|
| Append the default kernel argument. |
|
| Delete the default kernel argument. |
|
| Copy the network configuration from the install environment. Important
The |
|
|
For use with |
|
| Save partitions with this label glob. |
|
| Save partitions with this number or range. |
|
| Force offline installation. |
|
| Skip signature verification. |
|
| Allow Ignition URL without HTTPS or hash. |
|
|
Target CPU architecture. Default is |
|
| Do not clear partition table on error. |
|
| Print help information. |
| Command-line argument | |
| Argument | Description |
|
| The destination device. |
| coreos-installer embedded Ignition commands | |
| Command | Description |
|
| Embed an Ignition config in an ISO image. |
|
| Show the embedded Ignition config from an ISO image. |
|
| Remove the embedded Ignition config from an ISO image. |
| coreos-installer ISO Ignition options | |
| Option | Description |
|
| Overwrite an existing Ignition config. |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
| coreos-installer PXE Ignition commands | |
| Command | Description |
| Note that not all of these options are accepted by all subcommands. | |
|
| Wrap an Ignition config in an image. |
|
| Show the wrapped Ignition config in an image. |
|
|
Show the wrapped Ignition config in an |
| coreos-installer PXE Ignition options | |
| Option | Description |
|
|
The Ignition config to be used. Default is |
|
| Write the ISO to a new output file. |
|
| Print help information. |
13.1.12. Creating the cluster
To create the OpenShift Container Platform cluster, you wait for the bootstrap process to complete on the machines that you provisioned by using the Ignition config files that you generated with the installation program.
Prerequisites
- Create the required infrastructure for the cluster.
- You obtained the installation program and generated the Ignition config files for your cluster.
- You used the Ignition config files to create RHCOS machines for your cluster.
- Your machines have direct Internet access or have an HTTP or HTTPS proxy available.
Procedure
Monitor the bootstrap process:
./openshift-install --dir <installation_directory> wait-for bootstrap-complete \ --log-level=info$ ./openshift-install --dir <installation_directory> wait-for bootstrap-complete \1 --log-level=info2 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resources
INFO Waiting up to 30m0s for the Kubernetes API at https://api.test.example.com:6443... INFO API v1.19.0 up INFO Waiting up to 30m0s for bootstrapping to complete... INFO It is now safe to remove the bootstrap resourcesCopy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Kubernetes API server signals that it has been bootstrapped on the control plane machines.
After bootstrap process is complete, remove the bootstrap machine from the load balancer.
ImportantYou must remove the bootstrap machine from the load balancer at this point. You can also remove or reformat the machine itself.
13.1.13. Logging in to the cluster by using the CLI
You can log in to your cluster as a default system user by exporting the cluster kubeconfig file. The kubeconfig file contains information about the cluster that is used by the CLI to connect a client to the correct cluster and API server. The file is specific to a cluster and is created during OpenShift Container Platform installation.
Prerequisites
- You deployed an OpenShift Container Platform cluster.
-
You installed the
ocCLI.
Procedure
Export the
kubeadmincredentials:export KUBECONFIG=<installation_directory>/auth/kubeconfig
$ export KUBECONFIG=<installation_directory>/auth/kubeconfig1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Verify you can run
occommands successfully using the exported configuration:oc whoami
$ oc whoamiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
system:admin
system:adminCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.1.14. Approving the certificate signing requests for your machines
When you add machines to a cluster, two pending certificate signing requests (CSRs) are generated for each machine that you added. You must confirm that these CSRs are approved or, if necessary, approve them yourself. The client requests must be approved first, followed by the server requests.
Prerequisites
- You added machines to your cluster.
Procedure
Confirm that the cluster recognizes the machines:
oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0
NAME STATUS ROLES AGE VERSION master-0 Ready master 63m v1.19.0 master-1 Ready master 63m v1.19.0 master-2 Ready master 64m v1.19.0Copy to Clipboard Copied! Toggle word wrap Toggle overflow The output lists all of the machines that you created.
NoteThe preceding output might not include the compute nodes, also known as worker nodes, until some CSRs are approved.
Review the pending CSRs and ensure that you see the client requests with the
PendingorApprovedstatus for each machine that you added to the cluster:oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...
NAME AGE REQUESTOR CONDITION csr-8b2br 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending csr-8vnps 15m system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow In this example, two machines are joining the cluster. You might see more approved CSRs in the list.
If the CSRs were not approved, after all of the pending CSRs for the machines you added are in
Pendingstatus, approve the CSRs for your cluster machines:NoteBecause the CSRs rotate automatically, approve your CSRs within an hour of adding the machines to the cluster. If you do not approve them within an hour, the certificates will rotate, and more than two certificates will be present for each node. You must approve all of these certificates. Once the client CSR is approved, the Kubelet creates a secondary CSR for the serving certificate, which requires manual approval. Then, subsequent serving certificate renewal requests are automatically approved by the
machine-approverif the Kubelet requests a new certificate with identical parameters.NoteFor clusters running on platforms that are not machine API enabled, such as bare metal and other user-provisioned infrastructure, you must implement a method of automatically approving the kubelet serving certificate requests (CSRs). If a request is not approved, then the
oc exec,oc rsh, andoc logscommands cannot succeed, because a serving certificate is required when the API server connects to the kubelet. Any operation that contacts the Kubelet endpoint requires this certificate approval to be in place. The method must watch for new CSRs, confirm that the CSR was submitted by thenode-bootstrapperservice account in thesystem:nodeorsystem:admingroups, and confirm the identity of the node.To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs --no-run-if-empty oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteSome Operators might not become available until some CSRs are approved.
Now that your client requests are approved, you must review the server requests for each machine that you added to the cluster:
oc get csr
$ oc get csrCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...
NAME AGE REQUESTOR CONDITION csr-bfd72 5m26s system:node:ip-10-0-50-126.us-east-2.compute.internal Pending csr-c57lv 5m26s system:node:ip-10-0-95-157.us-east-2.compute.internal Pending ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow If the remaining CSRs are not approved, and are in the
Pendingstatus, approve the CSRs for your cluster machines:To approve them individually, run the following command for each valid CSR:
oc adm certificate approve <csr_name>
$ oc adm certificate approve <csr_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
<csr_name>is the name of a CSR from the list of current CSRs.
To approve all pending CSRs, run the following command:
oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approve$ oc get csr -o go-template='{{range .items}}{{if not .status}}{{.metadata.name}}{{"\n"}}{{end}}{{end}}' | xargs oc adm certificate approveCopy to Clipboard Copied! Toggle word wrap Toggle overflow
After all client and server CSRs have been approved, the machines have the
Readystatus. Verify this by running the following command:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIt can take a few minutes after approval of the server CSRs for the machines to transition to the
Readystatus.
Additional information
- For more information on CSRs, see Certificate Signing Requests.
13.1.15. Initial Operator configuration
After the control plane initializes, you must immediately configure some Operators so that they all become available.
Prerequisites
- Your control plane has initialized.
Procedure
Watch the cluster components come online:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Configure the Operators that are not available.
13.1.15.1. Disabling the default OperatorHub sources
Operator catalogs that source content provided by Red Hat and community projects are configured for OperatorHub by default during an OpenShift Container Platform installation. In a restricted network environment, you must disable the default catalogs as a cluster administrator.
Procedure
Disable the sources for the default catalogs by adding
disableAllDefaultSources: trueto theOperatorHubobject:oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'$ oc patch OperatorHub cluster --type json \ -p '[{"op": "add", "path": "/spec/disableAllDefaultSources", "value": true}]'Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Alternatively, you can use the web console to manage catalog sources. From the Administration → Cluster Settings → Global Configuration → OperatorHub page, click the Sources tab, where you can create, delete, disable, and enable individual sources.
13.1.15.2. Image registry removed during installation
On platforms that do not provide shareable object storage, the OpenShift Image Registry Operator bootstraps itself as Removed. This allows openshift-installer to complete installations on these platform types.
After installation, you must edit the Image Registry Operator configuration to switch the managementState from Removed to Managed.
The Prometheus console provides an ImageRegistryRemoved alert, for example:
"Image Registry has been removed. ImageStreamTags, BuildConfigs and DeploymentConfigs which reference ImageStreamTags may not work as expected. Please configure storage and update the config to Managed state by editing configs.imageregistry.operator.openshift.io."
13.1.15.3. Image registry storage configuration
The Image Registry Operator is not initially available for platforms that do not provide default storage. After installation, you must configure your registry to use storage so that the Registry Operator is made available.
Instructions are shown for configuring a persistent volume, which is required for production clusters. Where applicable, instructions are shown for configuring an empty directory as the storage location, which is available for only non-production clusters.
Additional instructions are provided for allowing the image registry to use block storage types by using the Recreate rollout strategy during upgrades.
13.1.15.3.1. Configuring registry storage for bare metal and other manual installations
As a cluster administrator, following installation you must configure your registry to use storage.
Prerequisites
- Cluster administrator permissions.
- A cluster that uses manually-provisioned Red Hat Enterprise Linux CoreOS (RHCOS) nodes, such as bare metal.
Persistent storage provisioned for your cluster, such as Red Hat OpenShift Container Storage.
ImportantOpenShift Container Platform supports
ReadWriteOnceaccess for image registry storage when you have only one replica. To deploy an image registry that supports high availability with two or more replicas,ReadWriteManyaccess is required.- Must have 100Gi capacity.
Procedure
To configure your registry to use storage, change the
spec.storage.pvcin theconfigs.imageregistry/clusterresource.NoteWhen using shared storage, review your security settings to prevent outside access.
Verify that you do not have a registry pod:
oc get pod -n openshift-image-registry
$ oc get pod -n openshift-image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow NoteIf the storage type is
emptyDIR, the replica number cannot be greater than1.Check the registry configuration:
oc edit configs.imageregistry.operator.openshift.io
$ oc edit configs.imageregistry.operator.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
storage: pvc: claim:storage: pvc: claim:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Leave the
claimfield blank to allow the automatic creation of animage-registry-storagePVC.Check the
clusteroperatorstatus:oc get clusteroperator image-registry
$ oc get clusteroperator image-registryCopy to Clipboard Copied! Toggle word wrap Toggle overflow Ensure that your registry is set to managed to enable building and pushing of images.
Run:
oc edit configs.imageregistry/cluster
$ oc edit configs.imageregistry/clusterCopy to Clipboard Copied! Toggle word wrap Toggle overflow Then, change the line
managementState: Removed
managementState: RemovedCopy to Clipboard Copied! Toggle word wrap Toggle overflow to
managementState: Managed
managementState: ManagedCopy to Clipboard Copied! Toggle word wrap Toggle overflow
13.1.15.3.2. Configuring storage for the image registry in non-production clusters
You must configure storage for the Image Registry Operator. For non-production clusters, you can set the image registry to an empty directory. If you do so, all images are lost if you restart the registry.
Procedure
To set the image registry storage to an empty directory:
oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'$ oc patch configs.imageregistry.operator.openshift.io cluster --type merge --patch '{"spec":{"storage":{"emptyDir":{}}}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow WarningConfigure this option for only non-production clusters.
If you run this command before the Image Registry Operator initializes its components, the
oc patchcommand fails with the following error:Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not found
Error from server (NotFound): configs.imageregistry.operator.openshift.io "cluster" not foundCopy to Clipboard Copied! Toggle word wrap Toggle overflow Wait a few minutes and run the command again.
13.1.15.3.3. Configuring block registry storage
To allow the image registry to use block storage types during upgrades as a cluster administrator, you can use the Recreate rollout strategy.
Block storage volumes are supported but not recommended for use with the image registry on production clusters. An installation where the registry is configured on block storage is not highly available because the registry cannot have more than one replica.
Procedure
To set the image registry storage as a block storage type, patch the registry so that it uses the
Recreaterollout strategy and runs with only one (1) replica:oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'$ oc patch config.imageregistry.operator.openshift.io/cluster --type=merge -p '{"spec":{"rolloutStrategy":"Recreate","replicas":1}}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Provision the PV for the block storage device, and create a PVC for that volume. The requested block volume uses the ReadWriteOnce (RWO) access mode.
- Edit the registry configuration so that it references the correct PVC.
13.1.16. Completing installation on user-provisioned infrastructure
After you complete the Operator configuration, you can finish installing the cluster on infrastructure that you provide.
Prerequisites
- Your control plane has initialized.
- You have completed the initial Operator configuration.
Procedure
Confirm that all the cluster components are online with the following command:
watch -n5 oc get clusteroperators
$ watch -n5 oc get clusteroperatorsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, the following command notifies you when all of the clusters are available. It also retrieves and displays credentials:
./openshift-install --dir <installation_directory> wait-for install-complete
$ ./openshift-install --dir <installation_directory> wait-for install-complete1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
<installation_directory>, specify the path to the directory that you stored the installation files in.
Example output
INFO Waiting up to 30m0s for the cluster to initialize...
INFO Waiting up to 30m0s for the cluster to initialize...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The command succeeds when the Cluster Version Operator finishes deploying the OpenShift Container Platform cluster from Kubernetes API server.
Important-
The Ignition config files that the installation program generates contain certificates that expire after 24 hours, which are then renewed at that time. If the cluster is shut down before renewing the certificates and the cluster is later restarted after the 24 hours have elapsed, the cluster automatically recovers the expired certificates. The exception is that you must manually approve the pending
node-bootstrappercertificate signing requests (CSRs) to recover kubelet certificates. See the documentation for Recovering from expired control plane certificates for more information. - It is recommended that you use Ignition config files within 12 hours after they are generated because the 24-hour certificate rotates from 16 to 22 hours after the cluster is installed. By using the Ignition config files within 12 hours, you can avoid installation failure if the certificate update runs during installation.
Confirm that the Kubernetes API server is communicating with the pods.
To view a list of all pods, use the following command:
oc get pods --all-namespaces
$ oc get pods --all-namespacesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow View the logs for a pod that is listed in the output of the previous command by using the following command:
oc logs <pod_name> -n <namespace>
$ oc logs <pod_name> -n <namespace>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the pod name and namespace, as shown in the output of the previous command.
If the pod logs display, the Kubernetes API server can communicate with the cluster machines.
13.1.17. Telemetry access for OpenShift Container Platform
In OpenShift Container Platform 4.6, the Telemetry service, which runs by default to provide metrics about cluster health and the success of updates, requires internet access. If your cluster is connected to the internet, Telemetry runs automatically, and your cluster is registered to OpenShift Cluster Manager.
After you confirm that your OpenShift Cluster Manager inventory is correct, either maintained automatically by Telemetry or manually by using OpenShift Cluster Manager, use subscription watch to track your OpenShift Container Platform subscriptions at the account or multi-cluster level.
13.1.18. Next steps
- Customize your cluster.
- If necessary, you can opt out of remote health reporting.
- Set up your registry and configure registry storage.
Chapter 14. Installation configuration
14.1. Supported installation methods for different platforms
You can perform different types of installations on different platforms.
Not all installation options are supported for all platforms, as shown in the following tables.
| AWS | Azure | GCP | OpenStack | RHV | Bare metal | vSphere | VMC | IBM Z | IBM Power | |
|---|---|---|---|---|---|---|---|---|---|---|
| Default | ||||||||||
| Custom | ||||||||||
| Network Operator | ||||||||||
| Restricted network | ||||||||||
| Private clusters | ||||||||||
| Existing virtual private networks | ||||||||||
| Government regions |
14.2. Customizing nodes
Although directly making changes to OpenShift Container Platform nodes is discouraged, there are times when it is necessary to implement a required low-level security, networking, or performance feature. Direct changes to OpenShift Container Platform nodes can be done by:
-
Creating machine configs that are included in manifest files to start up a cluster during
openshift-install. - Creating machine configs that are passed to running OpenShift Container Platform nodes via the Machine Config Operator.
The following sections describe features that you might want to configure on your nodes in this way.
14.2.1. Adding day-1 kernel arguments
Although it is often preferable to modify kernel arguments as a day-2 activity, you might want to add kernel arguments to all master or worker nodes during initial cluster installation. Here are some reasons you might want to add kernel arguments during cluster installation so they take effect before the systems first boot up:
- You want to disable a feature, such as SELinux, so it has no impact on the systems when they first come up.
Disabling SELinux on RHCOS is not supported.
- You need to do some low-level network configuration before the systems start.
To add kernel arguments to master or worker nodes, you can create a MachineConfig object and inject that object into the set of manifest files used by Ignition during cluster setup.
For a listing of arguments you can pass to a RHEL 8 kernel at boot time, see Kernel.org kernel parameters. It is best to only add kernel arguments with this procedure if they are needed to complete the initial OpenShift Container Platform installation.
Procedure
Change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Decide if you want to add kernel arguments to worker or control plane nodes (also known as the master nodes).
In the
openshiftdirectory, create a file (for example,99-openshift-machineconfig-master-kargs.yaml) to define aMachineConfigobject to add the kernel settings. This example adds aloglevel=7kernel argument to control plane nodes:Copy to Clipboard Copied! Toggle word wrap Toggle overflow You can change
mastertoworkerto add kernel arguments to worker nodes instead. Create a separate YAML file to add to both master and worker nodes.
You can now continue on to create the cluster.
14.2.2. Adding kernel modules to nodes
For most common hardware, the Linux kernel includes the device driver modules needed to use that hardware when the computer starts up. For some hardware, however, modules are not available in Linux. Therefore, you must find a way to provide those modules to each host computer. This procedure describes how to do that for nodes in an OpenShift Container Platform cluster.
When a kernel module is first deployed by following these instructions, the module is made available for the current kernel. If a new kernel is installed, the kmods-via-containers software will rebuild and deploy the module so a compatible version of that module is available with the new kernel.
The way that this feature is able to keep the module up to date on each node is by:
- Adding a systemd service to each node that starts at boot time to detect if a new kernel has been installed and
- If a new kernel is detected, the service rebuilds the module and installs it to the kernel
For information on the software needed for this procedure, see the kmods-via-containers github site.
A few important issues to keep in mind:
- This procedure is Technology Preview.
-
Software tools and examples are not yet available in official RPM form and can only be obtained for now from unofficial
github.comsites noted in the procedure. - Third-party kernel modules you might add through these procedures are not supported by Red Hat.
-
In this procedure, the software needed to build your kernel modules is deployed in a RHEL 8 container. Keep in mind that modules are rebuilt automatically on each node when that node gets a new kernel. For that reason, each node needs access to a
yumrepository that contains the kernel and related packages needed to rebuild the module. That content is best provided with a valid RHEL subscription.
14.2.2.1. Building and testing the kernel module container
Before deploying kernel modules to your OpenShift Container Platform cluster, you can test the process on a separate RHEL system. Gather the kernel module’s source code, the KVC framework, and the kmod-via-containers software. Then build and test the module. To do that on a RHEL 8 system, do the following:
Procedure
Register a RHEL 8 system:
subscription-manager register
# subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Attach a subscription to the RHEL 8 system:
subscription-manager attach --auto
# subscription-manager attach --autoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install software that is required to build the software and container:
yum install podman make git -y
# yum install podman make git -yCopy to Clipboard Copied! Toggle word wrap Toggle overflow Clone the
kmod-via-containersrepository:Create a folder for the repository:
mkdir kmods; cd kmods
$ mkdir kmods; cd kmodsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Clone the repository:
git clone https://github.com/kmods-via-containers/kmods-via-containers
$ git clone https://github.com/kmods-via-containers/kmods-via-containersCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Install a KVC framework instance on your RHEL 8 build host to test the module. This adds a
kmods-via-containersystemd service and loads it:Change to the
kmod-via-containersdirectory:cd kmods-via-containers/
$ cd kmods-via-containers/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Install the KVC framework instance:
sudo make install
$ sudo make installCopy to Clipboard Copied! Toggle word wrap Toggle overflow Reload the systemd manager configuration:
sudo systemctl daemon-reload
$ sudo systemctl daemon-reloadCopy to Clipboard Copied! Toggle word wrap Toggle overflow
Get the kernel module source code. The source code might be used to build a third-party module that you do not have control over, but is supplied by others. You will need content similar to the content shown in the
kvc-simple-kmodexample that can be cloned to your system as follows:cd .. ; git clone https://github.com/kmods-via-containers/kvc-simple-kmod
$ cd .. ; git clone https://github.com/kmods-via-containers/kvc-simple-kmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow Edit the configuration file,
simple-kmod.conffile, in this example, and change the name of the Dockerfile toDockerfile.rhel:Change to the
kvc-simple-kmoddirectory:cd kvc-simple-kmod
$ cd kvc-simple-kmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow Rename the Dockerfile:
cat simple-kmod.conf
$ cat simple-kmod.confCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example Dockerfile
KMOD_CONTAINER_BUILD_CONTEXT="https://github.com/kmods-via-containers/kvc-simple-kmod.git" KMOD_CONTAINER_BUILD_FILE=Dockerfile.rhel KMOD_SOFTWARE_VERSION=dd1a7d4 KMOD_NAMES="simple-kmod simple-procfs-kmod"
KMOD_CONTAINER_BUILD_CONTEXT="https://github.com/kmods-via-containers/kvc-simple-kmod.git" KMOD_CONTAINER_BUILD_FILE=Dockerfile.rhel KMOD_SOFTWARE_VERSION=dd1a7d4 KMOD_NAMES="simple-kmod simple-procfs-kmod"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Create an instance of
kmods-via-containers@.servicefor your kernel module,simple-kmodin this example:sudo make install
$ sudo make installCopy to Clipboard Copied! Toggle word wrap Toggle overflow Enable the
kmods-via-containers@.serviceinstance:sudo kmods-via-containers build simple-kmod $(uname -r)
$ sudo kmods-via-containers build simple-kmod $(uname -r)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Enable and start the systemd service:
sudo systemctl enable kmods-via-containers@simple-kmod.service --now
$ sudo systemctl enable kmods-via-containers@simple-kmod.service --nowCopy to Clipboard Copied! Toggle word wrap Toggle overflow Review the service status:
sudo systemctl status kmods-via-containers@simple-kmod.service
$ sudo systemctl status kmods-via-containers@simple-kmod.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
● kmods-via-containers@simple-kmod.service - Kmods Via Containers - simple-kmod Loaded: loaded (/etc/systemd/system/kmods-via-containers@.service; enabled; vendor preset: disabled) Active: active (exited) since Sun 2020-01-12 23:49:49 EST; 5s ago...● kmods-via-containers@simple-kmod.service - Kmods Via Containers - simple-kmod Loaded: loaded (/etc/systemd/system/kmods-via-containers@.service; enabled; vendor preset: disabled) Active: active (exited) since Sun 2020-01-12 23:49:49 EST; 5s ago...Copy to Clipboard Copied! Toggle word wrap Toggle overflow
To confirm that the kernel modules are loaded, use the
lsmodcommand to list the modules:lsmod | grep simple_
$ lsmod | grep simple_Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
simple_procfs_kmod 16384 0 simple_kmod 16384 0
simple_procfs_kmod 16384 0 simple_kmod 16384 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Optional. Use other methods to check that the
simple-kmodexample is working:Look for a "Hello world" message in the kernel ring buffer with
dmesg:dmesg | grep 'Hello world'
$ dmesg | grep 'Hello world'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
[ 6420.761332] Hello world from simple_kmod.
[ 6420.761332] Hello world from simple_kmod.Copy to Clipboard Copied! Toggle word wrap Toggle overflow Check the value of
simple-procfs-kmodin/proc:sudo cat /proc/simple-procfs-kmod
$ sudo cat /proc/simple-procfs-kmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
simple-procfs-kmod number = 0
simple-procfs-kmod number = 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow Run the
spkutcommand to get more information from the module:sudo spkut 44
$ sudo spkut 44Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Going forward, when the system boots this service will check if a new kernel is running. If there is a new kernel, the service builds a new version of the kernel module and then loads it. If the module is already built, it will just load it.
14.2.2.2. Provisioning a kernel module to OpenShift Container Platform
Depending on whether or not you must have the kernel module in place when OpenShift Container Platform cluster first boots, you can set up the kernel modules to be deployed in one of two ways:
-
Provision kernel modules at cluster install time (day-1): You can create the content as a
MachineConfigobject and provide it toopenshift-installby including it with a set of manifest files. - Provision kernel modules via Machine Config Operator (day-2): If you can wait until the cluster is up and running to add your kernel module, you can deploy the kernel module software via the Machine Config Operator (MCO).
In either case, each node needs to be able to get the kernel packages and related software packages at the time that a new kernel is detected. There are a few ways you can set up each node to be able to obtain that content.
- Provide RHEL entitlements to each node.
-
Get RHEL entitlements from an existing RHEL host, from the
/etc/pki/entitlementdirectory and copy them to the same location as the other files you provide when you build your Ignition config. -
Inside the Dockerfile, add pointers to a
yumrepository containing the kernel and other packages. This must include new kernel packages as they are needed to match newly installed kernels.
14.2.2.2.1. Provision kernel modules via a MachineConfig object
By packaging kernel module software with a MachineConfig object, you can deliver that software to worker or master nodes at installation time or via the Machine Config Operator.
First create a base Ignition config that you would like to use. At installation time, the Ignition config will contain the ssh public key to add to the authorized_keys file for the core user on the cluster. To add the MachineConfig object later via the MCO instead, the SSH public key is not required. For both type, the example simple-kmod service creates a systemd unit file, which requires a kmods-via-containers@simple-kmod.service.
The systemd unit is a workaround for an upstream bug and makes sure that the kmods-via-containers@simple-kmod.service gets started on boot:
Register a RHEL 8 system:
subscription-manager register
# subscription-manager registerCopy to Clipboard Copied! Toggle word wrap Toggle overflow Attach a subscription to the RHEL 8 system:
subscription-manager attach --auto
# subscription-manager attach --autoCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install software needed to build the software:
yum install podman make git -y
# yum install podman make git -yCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create an Ignition config file that creates a systemd unit file:
Create a directory to host the Ignition config file:
mkdir kmods; cd kmods
$ mkdir kmods; cd kmodsCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the Ignition config file that creates a systemd unit file:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteYou must add your public SSH key to the
baseconfig.ignfile to use the file duringopenshift-install. The public SSH key is not needed if you create theMachineConfigobject using the MCO.
Create a base MCO YAML snippet that uses the following configuration:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow NoteThe
mc-base.yamlis set to deploy the kernel module onworkernodes. To deploy on master nodes, change the role fromworkertomaster. To do both, you could repeat the whole procedure using different file names for the two types of deployments.Get the
kmods-via-containerssoftware:Clone the
kmods-via-containersrepository:git clone https://github.com/kmods-via-containers/kmods-via-containers
$ git clone https://github.com/kmods-via-containers/kmods-via-containersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Clone the
kvc-simple-kmodrepository:git clone https://github.com/kmods-via-containers/kvc-simple-kmod
$ git clone https://github.com/kmods-via-containers/kvc-simple-kmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
Get your module software. In this example,
kvc-simple-kmodis used: Create a fakeroot directory and populate it with files that you want to deliver via Ignition, using the repositories cloned earlier:
Create the directory:
FAKEROOT=$(mktemp -d)
$ FAKEROOT=$(mktemp -d)Copy to Clipboard Copied! Toggle word wrap Toggle overflow Change to the
kmod-via-containersdirectory:cd kmods-via-containers
$ cd kmods-via-containersCopy to Clipboard Copied! Toggle word wrap Toggle overflow Install the KVC framework instance:
make install DESTDIR=${FAKEROOT}/usr/local CONFDIR=${FAKEROOT}/etc/$ make install DESTDIR=${FAKEROOT}/usr/local CONFDIR=${FAKEROOT}/etc/Copy to Clipboard Copied! Toggle word wrap Toggle overflow Change to the
kvc-simple-kmoddirectory:cd ../kvc-simple-kmod
$ cd ../kvc-simple-kmodCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the instance:
make install DESTDIR=${FAKEROOT}/usr/local CONFDIR=${FAKEROOT}/etc/$ make install DESTDIR=${FAKEROOT}/usr/local CONFDIR=${FAKEROOT}/etc/Copy to Clipboard Copied! Toggle word wrap Toggle overflow
Get a tool called
filetranspilerand dependent software:cd .. ; sudo yum install -y python3
$ cd .. ; sudo yum install -y python3 git clone https://github.com/ashcrow/filetranspiler.gitCopy to Clipboard Copied! Toggle word wrap Toggle overflow Generate a final machine config YAML (
mc.yaml) and have it include the base Ignition config, base machine config, and the fakeroot directory with files you would like to deliver:./filetranspiler/filetranspile -i ./baseconfig.ign \ -f ${FAKEROOT} --format=yaml --dereference-symlinks \ | sed 's/^/ /' | (cat mc-base.yaml -) > 99-simple-kmod.yaml$ ./filetranspiler/filetranspile -i ./baseconfig.ign \ -f ${FAKEROOT} --format=yaml --dereference-symlinks \ | sed 's/^/ /' | (cat mc-base.yaml -) > 99-simple-kmod.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow If the cluster is not up yet, generate manifest files and add this file to the
openshiftdirectory. If the cluster is already running, apply the file as follows:oc create -f 99-simple-kmod.yaml
$ oc create -f 99-simple-kmod.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Your nodes will start the
kmods-via-containers@simple-kmod.serviceservice and the kernel modules will be loaded.To confirm that the kernel modules are loaded, you can log in to a node (using
oc debug node/<openshift-node>, thenchroot /host). To list the modules, use thelsmodcommand:lsmod | grep simple_
$ lsmod | grep simple_Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
simple_procfs_kmod 16384 0 simple_kmod 16384 0
simple_procfs_kmod 16384 0 simple_kmod 16384 0Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.2.3. Encrypting disks during installation
You can enable encryption for the boot disks on the control plane and compute nodes at installation time. OpenShift Container Platform supports the Trusted Platform Module (TPM) v2 and Tang encryption modes.
- TPM v2: This is the preferred mode. TPM v2 stores passphrases in a secure cryptoprocessor contained within a server. You can use this mode to prevent the boot disk data on a cluster node from being decrypted if the disk is removed from the server.
- Tang: Tang and Clevis are server and client components that enable network-bound disk encryption (NBDE). You can bind the boot disk data on your cluster nodes to a Tang server. This prevents the data from being decrypted unless the nodes are on a secure network where the Tang server can be accessed. Clevis is an automated decryption framework that is used to implement the decryption on the client side.
The use of Tang encryption mode to encrypt your disks is only supported for bare metal and vSphere installations on user-provisioned infrastructure.
When the TPM v2 or Tang encryption modes are enabled, the RHCOS boot disks are encrypted using the LUKS2 format.
This feature:
- Is available for installer-provisioned infrastructure and user-provisioned infrastructure deployments
- Is supported on Red Hat Enterprise Linux CoreOS (RHCOS) systems only
- Sets up disk encryption during the manifest installation phase so all data written to disk, from first boot forward, is encrypted
-
Encrypts data on the root filesystem only (
/dev/mapper/coreos-luks-rooton/) - Requires no user intervention for providing passphrases
- Uses AES-256-CBC encryption
Follow one of the two procedures to enable disk encryption for the nodes in your cluster.
14.2.3.1. Enabling TPM v2 disk encryption
Use the following procedure to enable TPM v2 mode disk encryption during an OpenShift Container Platform installation.
Prerequisites
- You have downloaded the OpenShift Container Platform installation program on your installation node.
Procedure
- Check to see if TPM v2 encryption needs to be enabled in the BIOS on each node. This is required on most Dell systems. Check the manual for your computer.
On your installation node, change to the directory that contains the installation program and generate the Kubernetes manifests for the cluster:
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<installation_directory>with the path to the directory that you want to store the installation files in.
Create machine config files to encrypt the boot disks for the control plane or compute nodes using the TPM v2 encryption mode.
To configure encryption on the control plane nodes, save the following machine config sample to a file in the
<installation_directory>/openshiftdirectory. For example, name the file99-openshift-master-tpmv2-encryption.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To configure encryption on the compute nodes, save the following machine config sample to a file in the
<installation_directory>/openshiftdirectory. For example, name the file99-openshift-worker-tpmv2-encryption.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Create a backup copy of the YAML files. The original YAML files are consumed when you create the Ignition config files.
- Continue with the remainder of the OpenShift Container Platform installation.
14.2.3.2. Enabling Tang disk encryption
Use the following procedure to enable Tang mode disk encryption during an OpenShift Container Platform installation.
Prerequisites
- You have downloaded the OpenShift Container Platform installation program on your installation node.
- You have access to a Red Hat Enterprise Linux (RHEL) 8 machine that can be used to generate a thumbprint of the Tang exchange key.
Procedure
- Set up a Tang server or access an existing one. See Network-bound disk encryption for instructions.
Add kernel arguments to configure networking when you do the Red Hat Enterprise Linux CoreOS (RHCOS) installations for your cluster. For example, to configure DHCP networking, identify
ip=dhcp, or set static networking when you add parameters to the kernel command line. For both DHCP and static networking, you also must provide therd.neednet=1kernel argument.ImportantSkipping this step causes the second boot to fail.
Install the
clevispackage on a RHEL 8 machine, if it is not already installed:sudo yum install clevis
$ sudo yum install clevisCopy to Clipboard Copied! Toggle word wrap Toggle overflow
On the RHEL 8 machine, run the following command to generate a thumbprint of the exchange key. Replace
http://tang.example.com:7500with the URL of your Tang server:clevis-encrypt-tang '{"url":"http://tang.example.com:7500"}' < /dev/null > /dev/null$ clevis-encrypt-tang '{"url":"http://tang.example.com:7500"}' < /dev/null > /dev/null1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- In this example,
tangd.socketis listening on port7500on the Tang server.
NoteThe
clevis-encrypt-tangcommand is used in this step only to generate a thumbprint of the exchange key. No data is being passed to the command for encryption at this point, so/dev/nullis provided as an input instead of plain text. The encrypted output is also sent to/dev/null, because it is not required for this procedure.Example output
The advertisement contains the following signing keys: PLjNyRdGw03zlRoGjQYMahSZGu9
The advertisement contains the following signing keys: PLjNyRdGw03zlRoGjQYMahSZGu91 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- The thumbprint of the exchange key.
When the
Do you wish to trust these keys? [ynYN]prompt displays, typeY.NoteRHEL 8 provides Clevis version 15, which uses the SHA-1 hash algorithm to generate thumbprints. Some other distributions provide Clevis version 17 or later, which use the SHA-256 hash algorithm for thumbprints. You must use a Clevis version that uses SHA-1 to create the thumbprint, to prevent Clevis binding issues when you install Red Hat Enterprise Linux CoreOS (RHCOS) on your OpenShift Container Platform cluster nodes.
Create a Base64 encoded file, replacing the URL of the Tang server (
url) and thumbprint (thp) you just generated:Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
ewogInVybCI6ICJodHRwOi8vdGFuZy5leGFtcGxlLmNvbTo3NTAwIiwgCiAidGhwIjogIlBMak55UmRHdzAzemxSb0dqUVlNYWhTWkd1OSIgCn0K
ewogInVybCI6ICJodHRwOi8vdGFuZy5leGFtcGxlLmNvbTo3NTAwIiwgCiAidGhwIjogIlBMak55UmRHdzAzemxSb0dqUVlNYWhTWkd1OSIgCn0KCopy to Clipboard Copied! Toggle word wrap Toggle overflow If you have not yet generated the Kubernetes manifests, change to the directory that contains the installation program on your installation node and create them:
Example output
./openshift-install create manifests --dir <installation_directory>
$ ./openshift-install create manifests --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Replace
<installation_directory>with the path to the directory that you want to store the installation files in.
Create machine config files to encrypt the boot disks for the control plane or compute nodes using the Tang encryption mode.
To configure encryption on the control plane nodes, save the following machine config sample to a file in the
<installation_directory>/openshiftdirectory. For example, name the file99-openshift-master-tang-encryption.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow To configure encryption on the compute nodes, save the following machine config sample to a file in the
<installation_directory>/openshiftdirectory. For example, name the file99-openshift-worker-tang-encryption.yaml:Copy to Clipboard Copied! Toggle word wrap Toggle overflow
- Create a backup copy of the YAML files. The original YAML files are consumed when you create the Ignition config files.
- Continue with the remainder of the OpenShift Container Platform installation.
14.2.4. Configuring a RAID-enabled data volume
You can enable software RAID partitioning to provide an external data volume.
Procedure
Create a machine config in the
<installation_directory>/openshiftdirectory that configures a data volume by using software RAID. In this example, it is calledraid1-alt-storage.yaml:Sample RAID 1 on secondary disks configuration file
Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- If you choose a different mount point, you must update the unit name to correspond to your mount point. Otherwise the unit will not activate. You can generate a matching unit name with
echo $(systemd-escape -p $mountpoint).mountwhere$mountpointis your chosen mount point.
14.2.5. Configuring chrony time service
You can set the time server and related settings used by the chrony time service (chronyd) by modifying the contents of the chrony.conf file and passing those contents to your nodes as a machine config.
Procedure
Create the contents of the
chrony.conffile and encode it as base64. For example:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify any valid, reachable time source, such as the one provided by your DHCP server. Alternately, you can specify any of the following NTP servers:
1.rhel.pool.ntp.org,2.rhel.pool.ntp.org, or3.rhel.pool.ntp.org.
Example output
ICAgIHNlcnZlciBjbG9jay5yZWRoYXQuY29tIGlidXJzdAogICAgZHJpZnRmaWxlIC92YXIvbGli L2Nocm9ueS9kcmlmdAogICAgbWFrZXN0ZXAgMS4wIDMKICAgIHJ0Y3N5bmMKICAgIGxvZ2RpciAv dmFyL2xvZy9jaHJvbnkK
ICAgIHNlcnZlciBjbG9jay5yZWRoYXQuY29tIGlidXJzdAogICAgZHJpZnRmaWxlIC92YXIvbGli L2Nocm9ueS9kcmlmdAogICAgbWFrZXN0ZXAgMS4wIDMKICAgIHJ0Y3N5bmMKICAgIGxvZ2RpciAv dmFyL2xvZy9jaHJvbnkKCopy to Clipboard Copied! Toggle word wrap Toggle overflow Create the
MachineConfigobject file, replacing the base64 string with the one you just created. This example adds the file tomasternodes. You can change it toworkeror make an additional MachineConfig for theworkerrole. Create MachineConfig files for each type of machine that your cluster uses:Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify an octal value mode for the
modefield in the machine config file. After creating the file and applying the changes, themodeis converted to a decimal value. You can check the YAML file with the commandoc get mc <mc-name> -o yaml.
- Make a backup copy of the configuration files.
Apply the configurations in one of two ways:
-
If the cluster is not up yet, after you generate manifest files, add this file to the
<installation_directory>/openshiftdirectory, and then continue to create the cluster. If the cluster is already running, apply the file:
oc apply -f ./99-masters-chrony-configuration.yaml
$ oc apply -f ./99-masters-chrony-configuration.yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow
-
If the cluster is not up yet, after you generate manifest files, add this file to the
14.3. Available cluster customizations
You complete most of the cluster configuration and customization after you deploy your OpenShift Container Platform cluster. A number of configuration resources are available.
You modify the configuration resources to configure the major features of the cluster, such as the image registry, networking configuration, image build behavior, and the identity provider.
For current documentation of the settings that you control by using these resources, use the oc explain command, for example oc explain builds --api-version=config.openshift.io/v1
14.3.1. Cluster configuration resources
All cluster configuration resources are globally scoped (not namespaced) and named cluster.
| Resource name | Description |
|---|---|
|
| Provides API server configuration such as certificates and certificate authorities. |
|
| Controls the identity provider and authentication configuration for the cluster. |
|
| Controls default and enforced configuration for all builds on the cluster. |
|
| Configures the behavior of the web console interface, including the logout behavior. |
|
| Enables FeatureGates so that you can use Tech Preview features. |
|
| Configures how specific image registries should be treated (allowed, disallowed, insecure, CA details). |
|
| Configuration details related to routing such as the default domain for routes. |
|
| Configures identity providers and other behavior related to internal OAuth server flows. |
|
| Configures how projects are created including the project template. |
|
| Defines proxies to be used by components needing external network access. Note: not all components currently consume this value. |
|
| Configures scheduler behavior such as policies and default node selectors. |
14.3.2. Operator configuration resources
These configuration resources are cluster-scoped instances, named cluster, which control the behavior of a specific component as owned by a particular Operator.
| Resource name | Description |
|---|---|
|
| Controls console appearance such as branding customizations |
|
| Configures internal image registry settings such as public routing, log levels, proxy settings, resource constraints, replica counts, and storage type. |
|
| Configures the Samples Operator to control which example image streams and templates are installed on the cluster. |
14.3.3. Additional configuration resources
These configuration resources represent a single instance of a particular component. In some cases, you can request multiple instances by creating multiple instances of the resource. In other cases, the Operator can use only a specific resource instance name in a specific namespace. Reference the component-specific documentation for details on how and when you can create additional resource instances.
| Resource name | Instance name | Namespace | Description |
|---|---|---|---|
|
|
|
| Controls the Alertmanager deployment parameters. |
|
|
|
| Configures Ingress Operator behavior such as domain, number of replicas, certificates, and controller placement. |
14.3.4. Informational Resources
You use these resources to retrieve information about the cluster. Do not edit these resources directly.
| Resource name | Instance name | Description |
|---|---|---|
|
|
|
In OpenShift Container Platform 4.6, you must not customize the |
|
|
| You cannot modify the DNS settings for your cluster. You can view the DNS Operator status. |
|
|
| Configuration details allowing the cluster to interact with its cloud provider. |
|
|
| You cannot modify your cluster networking after installation. To customize your network, follow the process to customize networking during installation. |
14.3.5. Updating the global cluster pull secret
You can update the global pull secret for your cluster by either replacing the current pull secret or appending a new pull secret.
The procedure is required when users use a separate registry to store images than the registry used during installation.
Cluster resources must adjust to the new pull secret, which can temporarily limit the usability of the cluster.
Updating the global pull secret will cause node reboots while the Machine Config Operator (MCO) syncs the changes.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole.
Procedure
Optional: To append a new pull secret to the existing pull secret, complete the following steps:
Enter the following command to download the pull secret:
oc get secret/pull-secret -n openshift-config --template='{{index .data ".dockerconfigjson" | base64decode}}' ><pull_secret_location>$ oc get secret/pull-secret -n openshift-config --template='{{index .data ".dockerconfigjson" | base64decode}}' ><pull_secret_location>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Provide the path to the pull secret file.
Enter the following command to add the new pull secret:
oc registry login --registry="<registry>" \ --auth-basic="<username>:<password>" \ --to=<pull_secret_location>
$ oc registry login --registry="<registry>" \1 --auth-basic="<username>:<password>" \2 --to=<pull_secret_location>3 Copy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, you can perform a manual update to the pull secret file.
Enter the following command to update the global pull secret for your cluster:
oc set data secret/pull-secret -n openshift-config --from-file=.dockerconfigjson=<pull_secret_location>
$ oc set data secret/pull-secret -n openshift-config --from-file=.dockerconfigjson=<pull_secret_location>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Provide the path to the new pull secret file.
This update is rolled out to all nodes, which can take some time depending on the size of your cluster. During this time, nodes are drained and pods are rescheduled on the remaining nodes.
14.4. Configuring your firewall
If you use a firewall, you must configure it so that OpenShift Container Platform can access the sites that it requires to function. You must always grant access to some sites, and you grant access to more if you use Red Hat Insights, the Telemetry service, a cloud to host your cluster, and certain build strategies.
14.4.1. Configuring your firewall for OpenShift Container Platform
Before you install OpenShift Container Platform, you must configure your firewall to grant access to the sites that OpenShift Container Platform requires.
There are no special configuration considerations for services running on only controller nodes versus worker nodes.
Procedure
Allowlist the following registry URLs:
Expand URL Port Function registry.redhat.io443, 80
Provides core container images
quay.io443, 80
Provides core container images
*.quay.io443, 80
Provides core container images
*.openshiftapps.com443, 80
Provides Red Hat Enterprise Linux CoreOS (RHCOS) images
When you add a site, such as
quay.io, to your allowlist, do not add a wildcard entry, such as*.quay.io, to your denylist. In most cases, image registries use a content delivery network (CDN) to serve images. If a firewall blocks access, then image downloads are denied when the initial download request is redirected to a hostname such ascdn01.quay.io.CDN hostnames, such as
cdn01.quay.io, are covered when you add a wildcard entry, such as*.quay.io, in your allowlist.- Allowlist any site that provides resources for a language or framework that your builds require.
If you do not disable Telemetry, you must grant access to the following URLs to access Red Hat Insights:
Expand URL Port Function cert-api.access.redhat.com443, 80
Required for Telemetry
api.access.redhat.com443, 80
Required for Telemetry
infogw.api.openshift.com443, 80
Required for Telemetry
console.redhat.com/api/ingress443, 80
Required for Telemetry and for
insights-operatorIf you use Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP) to host your cluster, you must grant access to the URLs that provide the cloud provider API and DNS for that cloud:
Expand Cloud URL Port Function AWS
*.amazonaws.com443, 80
Required to access AWS services and resources. Review the AWS Service Endpoints in the AWS documentation to determine the exact endpoints to allow for the regions that you use.
GCP
*.googleapis.com443, 80
Required to access GCP services and resources. Review Cloud Endpoints in the GCP documentation to determine the endpoints to allow for your APIs.
accounts.google.com443, 80
Required to access your GCP account.
Azure
management.azure.com443, 80
Required to access Azure services and resources. Review the Azure REST API reference in the Azure documentation to determine the endpoints to allow for your APIs.
*.blob.core.windows.net443, 80
Required to download Ignition files.
login.microsoftonline.com443, 80
Required to access Azure services and resources. Review the Azure REST API reference in the Azure documentation to determine the endpoints to allow for your APIs.
Allowlist the following URLs:
Expand URL Port Function mirror.openshift.com443, 80
Required to access mirrored installation content and images. This site is also a source of release image signatures, although the Cluster Version Operator needs only a single functioning source.
storage.googleapis.com/openshift-release443, 80
A source of release image signatures, although the Cluster Version Operator needs only a single functioning source.
*.apps.<cluster_name>.<base_domain>443, 80
Required to access the default cluster routes unless you set an ingress wildcard during installation.
quayio-production-s3.s3.amazonaws.com443, 80
Required to access Quay image content in AWS.
api.openshift.com443, 80
Required both for your cluster token and to check if updates are available for the cluster.
art-rhcos-ci.s3.amazonaws.com443, 80
Required to download Red Hat Enterprise Linux CoreOS (RHCOS) images.
console.redhat.com/openshift443, 80
Required for your cluster token.
registry.access.redhat.com443, 80
Required for
odoCLI.sso.redhat.com443, 80
The
https://console.redhat.com/openshiftsite uses authentication fromsso.redhat.comOperators require route access to perform health checks. Specifically, the authentication and web console Operators connect to two routes to verify that the routes work. If you are the cluster administrator and do not want to allow
*.apps.<cluster_name>.<base_domain>, then allow these routes:-
oauth-openshift.apps.<cluster_name>.<base_domain> -
console-openshift-console.apps.<cluster_name>.<base_domain>, or the hostname that is specified in thespec.route.hostnamefield of theconsoles.operator/clusterobject if the field is not empty.
-
Allowlist the following URLs for optional third-party content:
Expand URL Port Function registry.connect.redhat.com443, 80
Required for all third-party images and certified operators.
rhc4tp-prod-z8cxf-image-registry-us-east-1-evenkyleffocxqvofrk.s3.dualstack.us-east-1.amazonaws.com443, 80
Provides access to container images hosted on
registry.connect.redhat.comoso-rhc4tp-docker-registry.s3-us-west-2.amazonaws.com443, 80
Required for Sonatype Nexus, F5 Big IP operators.
If you use a default Red Hat Network Time Protocol (NTP) server allow the following URLs:
-
1.rhel.pool.ntp.org -
2.rhel.pool.ntp.org -
3.rhel.pool.ntp.org
-
If you do not use a default Red Hat NTP server, verify the NTP server for your platform and allow it in your firewall.
14.5. Configuring a private cluster
After you install an OpenShift Container Platform version 4.6 cluster, you can set some of its core components to be private.
14.5.1. About private clusters
By default, OpenShift Container Platform is provisioned using publicly-accessible DNS and endpoints. You can set the DNS, Ingress Controller, and API server to private after you deploy your cluster.
DNS
If you install OpenShift Container Platform on installer-provisioned infrastructure, the installation program creates records in a pre-existing public zone and, where possible, creates a private zone for the cluster’s own DNS resolution. In both the public zone and the private zone, the installation program or cluster creates DNS entries for *.apps, for the Ingress object, and api, for the API server.
The *.apps records in the public and private zone are identical, so when you delete the public zone, the private zone seamlessly provides all DNS resolution for the cluster.
Ingress Controller
Because the default Ingress object is created as public, the load balancer is internet-facing and in the public subnets. You can replace the default Ingress Controller with an internal one.
API server
By default, the installation program creates appropriate network load balancers for the API server to use for both internal and external traffic.
On Amazon Web Services (AWS), separate public and private load balancers are created. The load balancers are identical except that an additional port is available on the internal one for use within the cluster. Although the installation program automatically creates or destroys the load balancer based on API server requirements, the cluster does not manage or maintain them. As long as you preserve the cluster’s access to the API server, you can manually modify or move the load balancers. For the public load balancer, port 6443 is open and the health check is configured for HTTPS against the /readyz path.
On Google Cloud Platform, a single load balancer is created to manage both internal and external API traffic, so you do not need to modify the load balancer.
On Microsoft Azure, both public and private load balancers are created. However, because of limitations in current implementation, you just retain both load balancers in a private cluster.
14.5.2. Setting DNS to private
After you deploy a cluster, you can modify its DNS to use only a private zone.
Procedure
Review the
DNScustom resource for your cluster:oc get dnses.config.openshift.io/cluster -o yaml
$ oc get dnses.config.openshift.io/cluster -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Note that the
specsection contains both a private and a public zone.Patch the
DNScustom resource to remove the public zone:oc patch dnses.config.openshift.io/cluster --type=merge --patch='{"spec": {"publicZone": null}}'$ oc patch dnses.config.openshift.io/cluster --type=merge --patch='{"spec": {"publicZone": null}}' dns.config.openshift.io/cluster patchedCopy to Clipboard Copied! Toggle word wrap Toggle overflow Because the Ingress Controller consults the
DNSdefinition when it createsIngressobjects, when you create or modifyIngressobjects, only private records are created.ImportantDNS records for the existing Ingress objects are not modified when you remove the public zone.
Optional: Review the
DNScustom resource for your cluster and confirm that the public zone was removed:oc get dnses.config.openshift.io/cluster -o yaml
$ oc get dnses.config.openshift.io/cluster -o yamlCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
14.5.3. Setting the Ingress Controller to private
After you deploy a cluster, you can modify its Ingress Controller to use only a private zone.
Procedure
Modify the default Ingress Controller to use only an internal endpoint:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
ingresscontroller.operator.openshift.io "default" deleted ingresscontroller.operator.openshift.io/default replaced
ingresscontroller.operator.openshift.io "default" deleted ingresscontroller.operator.openshift.io/default replacedCopy to Clipboard Copied! Toggle word wrap Toggle overflow The public DNS entry is removed, and the private zone entry is updated.
14.5.4. Restricting the API server to private
After you deploy a cluster to Amazon Web Services (AWS) or Microsoft Azure, you can reconfigure the API server to use only the private zone.
Prerequisites
-
Install the OpenShift CLI (
oc). -
Have access to the web console as a user with
adminprivileges.
Procedure
In the web portal or console for AWS or Azure, take the following actions:
Locate and delete appropriate load balancer component.
- For AWS, delete the external load balancer. The API DNS entry in the private zone already points to the internal load balancer, which uses an identical configuration, so you do not need to modify the internal load balancer.
-
For Azure, delete the
api-internalrule for the load balancer.
-
Delete the
api.$clustername.$yourdomainDNS entry in the public zone.
Remove the external load balancers:
ImportantYou can run the following steps only for an installer-provisioned infrastructure (IPI) cluster. For a user-provisioned infrastructure (UPI) cluster, you must manually remove or disable the external load balancers.
From your terminal, list the cluster machines:
oc get machine -n openshift-machine-api
$ oc get machine -n openshift-machine-apiCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow You modify the control plane machines, which contain
masterin the name, in the following step.Remove the external load balancer from each control plane machine.
Edit a control plane
Machineobject to remove the reference to the external load balancer:oc edit machines -n openshift-machine-api <master_name>
$ oc edit machines -n openshift-machine-api <master_name>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- Specify the name of the control plane, or master,
Machineobject to modify.
Remove the lines that describe the external load balancer, which are marked in the following example, and save and exit the object specification:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow -
Repeat this process for each of the machines that contains
masterin the name.
Chapter 15. Validating an installation
You can check the status of an OpenShift Container Platform cluster after an installation by following the procedures in this document.
15.1. Reviewing the installation log
You can review a summary of an installation in the OpenShift Container Platform installation log. If an installation succeeds, the information required to access the cluster is included in the log.
Prerequisites
- You have access to the installation host.
Procedure
Review the
.openshift_install.loglog file in the installation directory on your installation host:cat <install_dir>/.openshift_install.log
$ cat <install_dir>/.openshift_install.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Cluster credentials are included at the end of the log if the installation is successful, as outlined in the following example:
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
15.2. Viewing the image pull source
For clusters with unrestricted network connectivity, you can view the source of your pulled images by using a command on a node, such as crictl images.
However, for disconnected installations, to view the source of pulled images, you must review the CRI-O logs to locate the Trying to access log entry, as shown in the following procedure. Other methods to view the image pull source, such as the crictl images command, show the non-mirrored image name, even though the image is pulled from the mirrored location.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole.
Procedure
Review the CRI-O logs for a master or worker node:
oc adm node-logs <node_name> -u crio
$ oc adm node-logs <node_name> -u crioCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
The
Trying to accesslog entry indicates where the image is being pulled from.... Mar 17 02:52:50 ip-10-0-138-140.ec2.internal crio[1366]: time="2021-08-05 10:33:21.594930907Z" level=info msg="Pulling image: quay.io/openshift-release-dev/ocp-release:4.8.4-ppc64le" id=abcd713b-d0e1-4844-ac1c-474c5b60c07c name=/runtime.v1alpha2.ImageService/PullImage Mar 17 02:52:50 ip-10-0-138-140.ec2.internal crio[1484]: time="2021-03-17 02:52:50.194341109Z" level=info msg="Trying to access \"li0317gcp1.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\"" Mar 17 02:52:50 ip-10-0-138-140.ec2.internal crio[1484]: time="2021-03-17 02:52:50.226788351Z" level=info msg="Trying to access \"li0317gcp1.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\"" ...
... Mar 17 02:52:50 ip-10-0-138-140.ec2.internal crio[1366]: time="2021-08-05 10:33:21.594930907Z" level=info msg="Pulling image: quay.io/openshift-release-dev/ocp-release:4.8.4-ppc64le" id=abcd713b-d0e1-4844-ac1c-474c5b60c07c name=/runtime.v1alpha2.ImageService/PullImage Mar 17 02:52:50 ip-10-0-138-140.ec2.internal crio[1484]: time="2021-03-17 02:52:50.194341109Z" level=info msg="Trying to access \"li0317gcp1.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\"" Mar 17 02:52:50 ip-10-0-138-140.ec2.internal crio[1484]: time="2021-03-17 02:52:50.226788351Z" level=info msg="Trying to access \"li0317gcp1.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\"" ...Copy to Clipboard Copied! Toggle word wrap Toggle overflow The log might show the image pull source twice, as shown in the preceding example.
If your
ImageContentSourcePolicyobject lists multiple mirrors, OpenShift Container Platform attempts to pull the images in the order listed in the configuration, for example:Trying to access \"li0317gcp1.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\" Trying to access \"li0317gcp2.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\"
Trying to access \"li0317gcp1.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\" Trying to access \"li0317gcp2.mirror-registry.qe.gcp.devcluster.openshift.com:5000/ocp/release@sha256:1926eae7cacb9c00f142ec98b00628970e974284b6ddaf9a6a086cb9af7a6c31\"Copy to Clipboard Copied! Toggle word wrap Toggle overflow
15.3. Getting cluster version, status, and update details
You can view the cluster version and status by running the oc get clusterversion command. If the status shows that the installation is still progressing, you can review the status of the Operators for more information.
You can also list the current update channel and review the available cluster updates.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole. -
You have installed the OpenShift CLI (
oc).
Procedure
Obtain the cluster version and overall status:
oc get clusterversion
$ oc get clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version 4.6.4 True False 6m25s Cluster version is 4.6.4
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS version 4.6.4 True False 6m25s Cluster version is 4.6.4Copy to Clipboard Copied! Toggle word wrap Toggle overflow The example output indicates that the cluster has been installed successfully.
If the cluster status indicates that the installation is still progressing, you can obtain more detailed progress information by checking the status of the Operators:
oc get clusteroperators.config.openshift.io
$ oc get clusteroperators.config.openshift.ioCopy to Clipboard Copied! Toggle word wrap Toggle overflow View a detailed summary of cluster specifications, update availability, and update history:
oc describe clusterversion
$ oc describe clusterversionCopy to Clipboard Copied! Toggle word wrap Toggle overflow List the current update channel:
oc get clusterversion -o jsonpath='{.items[0].spec}{"\n"}'$ oc get clusterversion -o jsonpath='{.items[0].spec}{"\n"}'Copy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
{"channel":"stable-4.6","clusterID":"245539c1-72a3-41aa-9cec-72ed8cf25c5c","upstream":"https://api.openshift.com/api/upgrades_info/v1/graph"}{"channel":"stable-4.6","clusterID":"245539c1-72a3-41aa-9cec-72ed8cf25c5c","upstream":"https://api.openshift.com/api/upgrades_info/v1/graph"}Copy to Clipboard Copied! Toggle word wrap Toggle overflow Review the available cluster updates:
oc adm upgrade
$ oc adm upgradeCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
15.4. Querying the status of the cluster nodes by using the CLI
You can verify the status of the cluster nodes after an installation.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole. -
You have installed the OpenShift CLI (
oc).
Procedure
List the status of the cluster nodes. Verify that the output lists all of the expected control plane and compute nodes and that each node has a
Readystatus:oc get nodes
$ oc get nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow Review CPU and memory resource availability for each cluster node:
oc adm top nodes
$ oc adm top nodesCopy to Clipboard Copied! Toggle word wrap Toggle overflow Example output
Copy to Clipboard Copied! Toggle word wrap Toggle overflow
15.5. Reviewing the cluster status from the OpenShift Container Platform web console
You can review the following information in the Overview page in the OpenShift Container Platform web console:
- The general status of your cluster
- The status of the control plane, cluster Operators, and storage
- CPU, memory, file system, network transfer, and pod availability
- The API address of the cluster, the cluster ID, and the name of the provider
- Cluster version information
- Cluster update status, including details of the current update channel and available updates
- A cluster inventory detailing node, pod, storage class, and persistent volume claim (PVC) information
- A list of ongoing cluster activities and recent events
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole.
Procedure
- In the Administrator perspective, navigate to Home → Overview.
15.6. Reviewing the cluster status from Red Hat OpenShift Cluster Manager
You can review detailed information about the status of your cluster in the OpenShift Cluster Manager.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole.
Procedure
In the Administrator perspective, navigate to Home → Overview → Details → OpenShift Cluster Manager to open the Overview page for the cluster in OpenShift Cluster Manager.
NoteAlternatively, you can navigate to OpenShift Cluster Manager directly and select your cluster ID from the list of available clusters.
In the Overview page, review the following information about your cluster:
- vCPU and memory availability and resource usage
- The cluster ID, status, type, location, and the provider name
- Node counts by node type
- Cluster version details, the creation date of the cluster, and the name of the cluster owner
- The life cycle support status of the cluster
- Subscription information, including the service level agreement (SLA) status, the subscription unit type, the production status of the cluster, the subscription obligation, and the service level
- A cluster history
Navigate to the Monitoring page to review the following information:
- A list of any issues that have been detected
- A list of alerts that are firing
- The cluster Operator status and version
- Cluster resource usage
Navigate to the Insights page to review the following information provided by Red Hat Insights:
- Potential issues that your cluster might be exposed to, categorized by risk level
- Health-check status by category
15.7. Checking cluster resource availability and utilization
OpenShift Container Platform provides a comprehensive set of monitoring dashboards that help you understand the state of cluster components.
In the Administrator perspective, you can access dashboards for core OpenShift Container Platform components, including:
- etcd
- Kubernetes compute resources
- Kubernetes network resources
- Prometheus
- Dashboards relating to cluster and node performance
Figure 15.1. Example compute resources dashboard
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole.
Procedure
- In the Administrator perspective in the OpenShift Container Platform web console, navigate to Monitoring → Dashboards.
- Choose a dashboard in the Dashboard list. Some dashboards, such as the etcd dashboard, produce additional sub-menus when selected.
- Optional: Select a time range for the graphs in the Time Range list.
- Optional: Select a Refresh Interval.
- Hover over each of the graphs within a dashboard to display detailed information about specific items.
15.8. Listing alerts that are firing
Alerts provide notifications when a set of defined conditions are true in an OpenShift Container Platform cluster. You can review the alerts that are firing in your cluster by using the Alerting UI in the OpenShift Container Platform web console.
Prerequisites
-
You have access to the cluster as a user with the
cluster-adminrole.
Procedure
- In the Administrator perspective, navigate to the Monitoring → Alerting → Alerts page.
- Review the alerts that are firing, including their Severity, State, and Source.
- Select an alert to view more detailed information in the Alert Details page.
15.9. Next steps
- See Troubleshooting installations if you experience issues when installing your cluster.
- After installing OpenShift Container Platform, you can further expand and customize your cluster.
Chapter 16. Troubleshooting installation issues
To assist in troubleshooting a failed OpenShift Container Platform installation, you can gather logs from the bootstrap and control plane, or master, machines. You can also get debug information from the installation program.
16.1. Prerequisites
- You attempted to install an OpenShift Container Platform cluster, and installation failed.
16.2. Gathering logs from a failed installation
If you gave an SSH key to your installation program, you can gather data about your failed installation.
You use a different command to gather logs about an unsuccessful installation than to gather logs from a running cluster. If you must gather logs from a running cluster, use the oc adm must-gather command.
Prerequisites
- Your OpenShift Container Platform installation failed before the bootstrap process finished. The bootstrap node is running and accessible through SSH.
-
The
ssh-agentprocess is active on your computer, and you provided the same SSH key to both thessh-agentprocess and the installation program. - If you tried to install a cluster on infrastructure that you provisioned, you must have the fully qualified domain names of the bootstrap and control plane nodes (also known as the master nodes).
Procedure
Generate the commands that are required to obtain the installation logs from the bootstrap and control plane machines:
If you used installer-provisioned infrastructure, change to the directory that contains the installation program and run the following command:
./openshift-install gather bootstrap --dir <installation_directory>
$ ./openshift-install gather bootstrap --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
installation_directoryis the directory you specified when you ran./openshift-install create cluster. This directory contains the OpenShift Container Platform definition files that the installation program creates.
For installer-provisioned infrastructure, the installation program stores information about the cluster, so you do not specify the hostnames or IP addresses.
If you used infrastructure that you provisioned yourself, change to the directory that contains the installation program and run the following command:
./openshift-install gather bootstrap --dir <installation_directory> \ --bootstrap <bootstrap_address> \ --master <master_1_address> \ --master <master_2_address> \ --master <master_3_address>"$ ./openshift-install gather bootstrap --dir <installation_directory> \1 --bootstrap <bootstrap_address> \2 --master <master_1_address> \3 --master <master_2_address> \4 --master <master_3_address>"5 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
installation_directory, specify the same directory you specified when you ran./openshift-install create cluster. This directory contains the OpenShift Container Platform definition files that the installation program creates. - 2
<bootstrap_address>is the fully qualified domain name or IP address of the cluster’s bootstrap machine.- 3 4 5
- For each control plane, or master, machine in your cluster, replace
<master_*_address>with its fully qualified domain name or IP address.
NoteA default cluster contains three control plane machines. List all of your control plane machines as shown, no matter how many your cluster uses.
Example output
INFO Pulling debug logs from the bootstrap machine INFO Bootstrap gather logs captured here "<installation_directory>/log-bundle-<timestamp>.tar.gz"
INFO Pulling debug logs from the bootstrap machine INFO Bootstrap gather logs captured here "<installation_directory>/log-bundle-<timestamp>.tar.gz"Copy to Clipboard Copied! Toggle word wrap Toggle overflow If you open a Red Hat support case about your installation failure, include the compressed logs in the case.
16.3. Manually gathering logs with SSH access to your host(s)
Manually gather logs in situations where must-gather or automated collection methods do not work.
Prerequisites
- You must have SSH access to your host(s).
Procedure
Collect the
bootkube.serviceservice logs from the bootstrap host using thejournalctlcommand by running:journalctl -b -f -u bootkube.service
$ journalctl -b -f -u bootkube.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Collect the bootstrap host’s container logs using the podman logs. This is shown as a loop to get all of the container logs from the host:
for pod in $(sudo podman ps -a -q); do sudo podman logs $pod; done
$ for pod in $(sudo podman ps -a -q); do sudo podman logs $pod; doneCopy to Clipboard Copied! Toggle word wrap Toggle overflow Alternatively, collect the host’s container logs using the
tailcommand by running:tail -f /var/lib/containers/storage/overlay-containers/*/userdata/ctr.log
# tail -f /var/lib/containers/storage/overlay-containers/*/userdata/ctr.logCopy to Clipboard Copied! Toggle word wrap Toggle overflow Collect the
kubelet.serviceandcrio.serviceservice logs from the master and worker hosts using thejournalctlcommand by running:journalctl -b -f -u kubelet.service -u crio.service
$ journalctl -b -f -u kubelet.service -u crio.serviceCopy to Clipboard Copied! Toggle word wrap Toggle overflow Collect the master and worker host container logs using the
tailcommand by running:sudo tail -f /var/log/containers/*
$ sudo tail -f /var/log/containers/*Copy to Clipboard Copied! Toggle word wrap Toggle overflow
16.4. Manually gathering logs without SSH access to your host(s)
Manually gather logs in situations where must-gather or automated collection methods do not work.
If you do not have SSH access to your node, you can access the systems journal to investigate what is happening on your host.
Prerequisites
- Your OpenShift Container Platform installation must be complete.
- Your API service is still functional.
- You have system administrator privileges.
Procedure
Access
journaldunit logs under/var/logby running:oc adm node-logs --role=master -u kubelet
$ oc adm node-logs --role=master -u kubeletCopy to Clipboard Copied! Toggle word wrap Toggle overflow Access host file paths under
/var/logby running:oc adm node-logs --role=master --path=openshift-apiserver
$ oc adm node-logs --role=master --path=openshift-apiserverCopy to Clipboard Copied! Toggle word wrap Toggle overflow
16.5. Getting debug information from the installation program
You can use any of the following actions to get debug information from the installation program.
Look at debug messages from a past installation in the hidden
.openshift_install.logfile. For example, enter:cat ~/<installation_directory>/.openshift_install.log
$ cat ~/<installation_directory>/.openshift_install.log1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
installation_directory, specify the same directory you specified when you ran./openshift-install create cluster.
Change to the directory that contains the installation program and re-run it with
--log-level=debug:./openshift-install create cluster --dir <installation_directory> --log-level debug
$ ./openshift-install create cluster --dir <installation_directory> --log-level debug1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
- For
installation_directory, specify the same directory you specified when you ran./openshift-install create cluster.
16.6. Reinstalling the OpenShift Container Platform cluster
If you are unable to debug and resolve issues in the failed OpenShift Container Platform installation, consider installing a new OpenShift Container Platform cluster. Before starting the installation process again, you must complete thorough cleanup. For a user-provisioned infrastructure (UPI) installation, you must manually destroy the cluster and delete all associated resources. The following procedure is for an installer-provisioned infrastructure (IPI) installation.
Procedure
Destroy the cluster and remove all the resources associated with the cluster, including the hidden installer state files in the installation directory:
./openshift-install destroy cluster --dir <installation_directory>
$ ./openshift-install destroy cluster --dir <installation_directory>1 Copy to Clipboard Copied! Toggle word wrap Toggle overflow - 1
installation_directoryis the directory you specified when you ran./openshift-install create cluster. This directory contains the OpenShift Container Platform definition files that the installation program creates.
Before reinstalling the cluster, delete the installation directory:
rm -rf <installation_directory>
$ rm -rf <installation_directory>Copy to Clipboard Copied! Toggle word wrap Toggle overflow - Follow the procedure for installing a new OpenShift Container Platform cluster.
Chapter 17. Support for FIPS cryptography
You can install an OpenShift Container Platform cluster that uses FIPS Validated / Modules in Process cryptographic libraries on the x86_64 architecture.
For the Red Hat Enterprise Linux CoreOS (RHCOS) machines in your cluster, this change is applied when the machines are deployed based on the status of an option in the install-config.yaml file, which governs the cluster options that a user can change during cluster deployment. With Red Hat Enterprise Linux (RHEL) machines, you must enable FIPS mode when you install the operating system on the machines that you plan to use as worker machines. These configuration methods ensure that your cluster meet the requirements of a FIPS compliance audit: only FIPS Validated / Modules in Process cryptography packages are enabled before the initial system boot.
Because FIPS must be enabled before the operating system that your cluster uses boots for the first time, you cannot enable FIPS after you deploy a cluster.
17.1. FIPS validation in OpenShift Container Platform
OpenShift Container Platform uses certain FIPS Validated / Modules in Process modules within RHEL and RHCOS for the operating system components that it uses. See RHEL7 core crypto components. For example, when users SSH into OpenShift Container Platform clusters and containers, those connections are properly encrypted.
OpenShift Container Platform components are written in Go and built with Red Hat’s golang compiler. When you enable FIPS mode for your cluster, all OpenShift Container Platform components that require cryptographic signing call RHEL and RHCOS cryptographic libraries.
| Attributes | Limitations |
|---|---|
| FIPS support in RHEL 7 operating systems. | The FIPS implementation does not offer a single function that both computes hash functions and validates the keys that are based on that hash. This limitation will continue to be evaluated and improved in future OpenShift Container Platform releases. |
| FIPS support in CRI-O runtimes. | |
| FIPS support in OpenShift Container Platform services. | |
| FIPS Validated / Modules in Process cryptographic module and algorithms that are obtained from RHEL 7 and RHCOS binaries and images. | |
| Use of FIPS compatible golang compiler. | TLS FIPS support is not complete but is planned for future OpenShift Container Platform releases. |
| FIPS support across multiple architectures. |
FIPS is currently only supported on OpenShift Container Platform deployments using the |
17.2. FIPS support in components that the cluster uses
Although the OpenShift Container Platform cluster itself uses FIPS Validated / Modules in Process modules, ensure that the systems that support your OpenShift Container Platform cluster use FIPS Validated / Modules in Process modules for cryptography.
17.2.1. etcd
To ensure that the secrets that are stored in etcd use FIPS Validated / Modules in Process encryption, boot the node in FIPS mode. After you install the cluster in FIPS mode, you can encrypt the etcd data by using the FIPS-approved aes cbc cryptographic algorithm.
17.2.2. Storage
For local storage, use RHEL-provided disk encryption or Container Native Storage that uses RHEL-provided disk encryption. By storing all data in volumes that use RHEL-provided disk encryption and enabling FIPS mode for your cluster, both data at rest and data in motion, or network data, are protected by FIPS Validated / Modules in Process encryption. You can configure your cluster to encrypt the root filesystem of each node, as described in Customizing nodes.
17.2.3. Runtimes
To ensure that containers know that they are running on a host that is using FIPS Validated / Modules in Process cryptography modules, use CRI-O to manage your runtimes. CRI-O supports FIPS mode, in that it configures the containers to know that they are running in FIPS mode.
17.3. Installing a cluster in FIPS mode
To install a cluster in FIPS mode, follow the instructions to install a customized cluster on your preferred infrastructure. Ensure that you set fips: true in the install-config.yaml file before you deploy your cluster.
If you are using Azure File storage, you cannot enable FIPS mode.
To apply AES CBC encryption to your etcd data store, follow the Encrypting etcd data process after you install your cluster.
If you add RHEL nodes to your cluster, ensure that you enable FIPS mode on the machines before their initial boot. See Adding RHEL compute machines to an OpenShift Container Platform cluster and Enabling FIPS Mode in the RHEL 7 documentation.
Legal Notice
Copyright © 2025 Red Hat
OpenShift documentation is licensed under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0).
Modified versions must remove all Red Hat trademarks.
Portions adapted from https://github.com/kubernetes-incubator/service-catalog/ with modifications by Red Hat.
Red Hat, Red Hat Enterprise Linux, the Red Hat logo, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries.
Linux® is the registered trademark of Linus Torvalds in the United States and other countries.
Java® is a registered trademark of Oracle and/or its affiliates.
XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries.
MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries.
Node.js® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project.
The OpenStack® Word Mark and OpenStack logo are either registered trademarks/service marks or trademarks/service marks of the OpenStack Foundation, in the United States and other countries and are used with the OpenStack Foundation’s permission. We are not affiliated with, endorsed or sponsored by the OpenStack Foundation, or the OpenStack community.
All other trademarks are the property of their respective owners.